P2P Streaming: a Study on the Use of Advertisements as Incentives
|
|
|
- Randell Blake
- 6 years ago
- Views:
Transcription
1 P2P Streaming: a Study on the Use of Advertisements as Incentives Bo-Chun Wang, Alix L.H. Chow, Leana Golubchik Department of Computer Science, University of Southern California Nokia Research Center, Beijing, China {bochunwa@usc.edu, alix.chow@nokia.com, leana@usc.edu} ABSTRACT P2P streaming systems, such as PPLive, PPStream, and TVUPlayer, have become popular services with the widespread deployment of broadband networks. However, P2P streaming systems still face free-riding problems, similar to those that have been observed in P2P file sharing systems. Thus, one important problem in providing streaming services is that of providing appropriate incentives for peers to contribute their upload capacity. To this end, we propose the use of advertisements as an incentive for peers to contribute upload capacity. In the proposed framework, peers enjoy the same quality of streamed media, with the difference in quality of service being achieved through different amounts of advertisements viewed, based on the resource contributions to the system. An extensive simulation-based study is performed to evaluate the proposed approach. The results demonstrate that our approach provides appropriate incentives for peers to contribute their resources. Categories and Subject Descriptors C.2 [COMPUTER-COMMUNICATION NETWORKS]: Distributed networks General Terms Design; Performance Keywords P2P streaming systems; incentive; advertisement; token-based;. INTRODUCTION The use of Peer-to-Peer (P2P) technology has led to efficient distribution of content over large scale networks. For instance, Bit- Torrent [] is one of the most successful file sharing applications in use today. In the past few years, P2P-based streaming has become another popular service, with the widespread deployment of broadband networks. P2P-based approaches to streaming have become popular, as compared to traditional client-server-based approached, due to the following advantages: low cost, scalability, and ease of deployment. There are already several P2P streaming applications deployed on the Internet, such as PPLive [3], PP- Stream [5], and TVUPlayer [6]. Moreover, a number of efforts have focused on measurement and analysis of such P2P streaming systems [9, 2, 27]. However, P2P streaming systems still suffer from free-riding problems, i.e., similarly to the free-riding problems observed in P2P file sharing systems. For example, X. Hei et al [9] provide four measurement results of PPlive (two from university campuses and two from residential locations). Peers in one of the residential locations do almost no uploads. These peers may be considered as freeriders. Moreover, they have also shown that deployed streaming systems performance depends on peers with high upload capacities, given that there is significant upload bandwidth heterogeneity on the Internet. In order to provide satisfactory performance, the quantity of peers with high upload capacities in streaming systems should be sufficiently high []. Therefore, the problem of how to provide appropriate incentives for peers to contribute their upload capacity to the system is an important one in the context of P2P-based streaming systems. Although some approaches exist for addressing this problem in the context of P2P file sharing systems, providing incentives in streaming systems can be a more complex problem. For instance, such approaches in file-sharing systems typically provide a reduction in file downloading time as an incentive. However, in streaming systems, a peer s quality of service depends on video quality (e.g., smoothness of video delivery), rather than on how fast the entire stream (e.g., video) can be downloaded. Hence, there is a need for re-considering the problem of providing appropriate incentives for peers to contribute resources in the context of P2P streaming systems. To address the incentives problem in streaming systems, several techniques have been proposed in the literature, such as [, 4 6, 8, 2, 2, 23, 25]. Most of these works use improved video quality as an incentive, achieved through layered coding-based or MDC-based techniques [4, 5, 7]. Briefly, the basic idea here is that peers will have better video quality when they upload more data. (A more detailed description is given in Section 5.) In this paper we consider an alternative direction for providing incentives in P2P streaming systems, namely that of using the amount of advertisements viewed as an incentive to contribute more resources, as described next. Our approach is orthogonal to (and can be combined with) previous efforts whose goals are to provide better video quality (as detailed below). Advertisement supported service has become a popular business
2 model. Many popular systems ask users to watch advertisements before users start to watch videos (e.g., Youtube [7] and Hulu [2]). Since advertisements could provide additional revenue for a service provider in a P2P streaming system, such providers could include advertisements in the distributed content (e.g., as is currently done on television). Since all peers (whether high or low capacity) are concerned with video quality (e.g., in the form of smoothness in data delivery), controlling the amount of advertisements viewed by a peer would be another approach to providing incentives for peers to contribute resources in a P2P streaming system. (In a sense, our system is analogous to having broadcast (free) TV and paid TV channels, e.g., such as HBO. For instance, a user can view movies on a paid TV channel without advertisements, or the user can view the same movie on a free TV channel with advertisements. In our case, the payment" we consider is the peers resource contribution.) Briefly, in our proposed system, peers who contribute more upload capacity view fewer advertisements than peers who contribute less upload resources. Thus, unlike in layered coding/mdc based schemes, low capacity peers can still enjoy good video quality but with more advertisements than higher capacity peers. In this paper, we focus on the architecture of such a system and its evaluation, including issues such as tracking of peers contributions while preventing malicious behavior as well as efficient distribution of advertisements. One important challenge in such a system is accounting for peers contributions, on which the system can in turn base the computation of the amount of advertisements a peer should view. One possible approach is to allow peers to report their own contributions. However, since malicious peers may report more than their actual contribution, such a method is open to abuse by free-riders or malicious peers. Therefore, in this paper, we design token-based schemes to address the problem of determining how much contribution each peer is making. Token-based schemes have been used in P2P file sharing systems [3, 9, 26, 29] as well as other systems. In [3, 26, 29], token-based schemes are considered as a form of credit systems or micro-payment systems, where peers can exchange tokens, as virtual currency, to receive resources or services, and a service provider can charge based on the amount of tokens attained. In [9], token-based schemes are used for two incentive purposes, reputation and payment. Peers should maintain high reputation, otherwise, other peers may refuse to interact with them. In addition, peers pay" with tokens for downloading content and receive tokens for uploading content to other peers. Thus, a free-rider cannot download data due to lack of tokens. In this paper, we adopt the idea of using tokens as payment in designing our system. Our main purpose in utilizing tokens is in creating a mechanism for accounting for peers contributions. Unlike other efforts where tokens are used to limit downloading or support reputation, we use tokens to determine the amount of advertisements peers should view. (The details of our system architecture are given below.) Briefly, in our token-based schemes, a peer pays" with tokens when downloading steaming content. A peer receives tokens, when contributing its upload capacity for streaming data to other peers. Then, the amount of advertisements shown to each peer is based on the number of tokens each peer possesses. The advantage of this token-based approach is that the use of tokens can prevent malicious peers from reporting incorrect contributions. In addition, we insure that malicious peers do not fake" tokens (i.e., generate tokens on their own) through the use of cryptographic-based signatures. Our contributions in this paper can be summarized as follows. We consider the use of advertisements as an incentive in P2P streaming systems for peers to contribute upload resources and propose a corresponding P2P-based streaming system architecture. Since, advertisement supported services are likely to become more and more popular, our approach could provide peers an important incentive for contributing their upload capacity. In Section 3, our simulation-based study demonstrates the utility of this approach - for instance, when peers increase their uploading rate, the system provides reduced amount of advertisement based on true contributions. Moreover, we also focus on efficient distribution of advertisements in Section 3.. We propose a token-based framework as an approach to address the problem of accounting for peers contributions so as to determine the amount of advertisements peers should view (see Section 2). We propose three token-based schemes and explore their characteristics, such as overhead, reliability, management, and resilience to malicious behavior (see discussion in Section 4). In Section 3, we present our simulationbased study that illustrates several useful characteristics of our schemes. These include, a demonstration of how to reduce overhead needed for implementing such token-based schemes in Section 3.2 and what are the trade-offs between overhead reduction and accuracy in Section 3.3. Our results provide system developers with insight into efficient development of P2P-based streaming systems that utilize advertisements as incentives for resource contribution. 2. THE PROPOSED SYSTEM In this section, we present the proposed system which uses advertisements as incentives in a P2P streaming system. In this system, peers view different amounts of advertisements, based on their resource contributions to the system. An advertisement in our system can be any object - e.g., it can be a video clip, flash animation, streamed media, and so on. In general, the type of advertisement is determined by the content provider. For ease of exposition, in this paper we focus on one type of advertisement, namely streamed media. The main challenge in our system is that of determining peers true resource contributions. One possible approach is to allow peers to report their own contributions. However, this method does not prevent malicious peers from reporting incorrect contributions. That is, in order for advertisement-based incentives to produce a desired effect, we need to construct a system where peers contributions can be determined reasonably accurately (at least relative to each other). To this end, we design token-based schemes. schemes include three functions: token generation: How are tokens generated? Our token-based token exchange: How do peers exchange tokens in order to download streamed content? contribution calculation: How are peers contributions calculated, and how is the amount of advertisements peers have to view determined?
3 Streaming Server Token Server Streamed media Tokens Advertisement Peer with high uploading rate ti,p ai,p ti,p+ ai,p+ Figure 2: Time Interval: peer views streaming content during time interval t i,p and views advertisements during time interval a i,p Figure : System Architecture Peer with low uploading rate Pi Pj Pk (a) Since token generation and contribution calculation could be done at the peer-side or the server-side, we consider different combinations and propose the following schemes in this paper: Token generation at Peer-side and Contribution calculation at Peer-side (TPCP) Token generation at Server-side and Contribution calculation at Peer-side (TSCP) Serial Number Timestamp Pi s ID Pj s ID Pk s ID (b)reuse Serial Number Timestamp Pi s ID Pj s ID # of tokens (c)non-reuse Token generation at Peer-side and Contribution calculation at Server-side (TPCS) Figure 3: Token Structure Note that, using different token-based schemes does not affect the quantity of peers contributions. The motivation for considering different schemes is to explore overhead and reliability characteristics of each schemes. The information can help system developers choose appropriate schemes by considering the trade-offs between overhead and reliability. Note that, we do not consider token generation at the server-side and contribution calculation at the serverside because this scheme is completely centralized and is not appropriate for P2P systems. Fig. illustrates our system architecture. The system consists of a streaming server and peers. In the TSCP and TPCS schemes, the system also includes a token server. The streaming server and the token server are managed by the service provider. The streaming server is responsible for generating the streamed content as well as the advertisements, while the token server is responsible for generating tokens or computing peers resource contributions. The sources of advertisements could be the service provider or sponsors. The streaming format considered in the remainder of the paper is single-layer video with substreams, as in [6]. The basic idea of substreams is to encode a video stream into several substreams, each having the same video rate, i.e., the streaming server encodes streamed content into k substreams and distributes k substreams through the P2P system. The main advantage of a system using substreams is that it can be extended to using different coding schemes. In [6], the authors have shown that such a substream-based mechanism can be applied to several different coding schemes, including single-layer video, layered coding-based video, and MDC. Since the use of video quality as an incentive is not our goal here, for simplicity of illustration, we use single-layer video with substreams. However, as noted earlier, our approach can be combined with layered coding-based video or MDC schemes. In the TSCP and TPCS schemes, when a peer wants to join or depart from the overlay system, it has to contact the token server. The token server keeps login information of each peer, as a way of checking whether the peer exists in the system or not. The login information is used when the token server distributes tokens to peers or calculates a peer s contribution. After a peer joins the overlay network, it connects to n neighbors to download streaming content and advertisements. In addition, peers randomly choose new neighbors periodically. In the system, a peer has to provide tokens when it downloads data from other peers. Conversely, it receives tokens from other peers when it streams (uploads) data to them. The amount of data, δ, that a peer can download upon providing one token is determined by the service provider. Moreover, uploading advertisements is also considered as a peer s contribution, since such upload bandwidth contribution can reduce the load on the streaming server. A peer making a greater contribution accordingly receives a greater number of tokens from other peers. In our system, the downloaded content and advertisements are kept in the local cache of a peer. Peers must view advertisements after they have viewed some amount of content. For instance, consider the example in Fig. 2, where peer i views content in the p-th time interval, t i,p. Then, the system displays advertisements of length a i,p which is calculated based on peer i s contribution during t i,p. Therefore, a i,p is different from interval to interval. The length of time interval t i,p is the same for every peer, and it is determined by the service provider. At the end of each time interval, t i,p, peers contributions are calculated and used to determine the amount of advertisements that each peer should view. Below, we describe in detail our token-based schemes and how peers contributions are calculated in our system. For convenience, a summary of notation used in the paper is given in Table.
4 k n δ N t i,p a i,p c i,p r i,p g i,p s i,p f i,p Max(f) Def(f) Min(f) Min(c) Equal(c) number of substreams number of a peer s neighbors amount of data a peer can download per one token number of tokens the token server sends to a peer for each content interval p-th time interval for viewing content p-th time interval for viewing advertisements peer i s contribution during t i,p number of tokens received by peer i during t i,p number of tokens generated by peer i during t i,p number of tokens sent by peer i to other peers during t i,p ratio of advertisement time length to time length of streamed content maximum value of f i,p default value of f i,p minimum value of f i,p a peer s contribution if it is free-rider a peer s contribution while its income is equal to its spending amount Table : Notations list Token generation: Now, we describe how to generate tokens in our system. In the TPCP and TPCS schemes, tokens are generated by peers; tokens are generated by the token server in the TSCP scheme. The corresponding token structure is depicted in Fig. 3(b). Each token has a different serial number and timestamp for uniqueness. Moreover, a token includes the generator s ID and the receiver s ID. In the TSCP scheme, the generator s ID is the token server s ID, e.g., in Fig. 3, peer i is the generator and peer j is the receiver. After peer i generates a token, it encrypts the token to prevent other peers from faking tokens. In the TPCP and TPCS schemes, peers can generate tokens as needed. In the TSCP scheme, tokens are generated by the token server. Then, the token server sends tokens to peers at the start of each content interval, t i,p, as depicted in Fig. 2. The number of tokens sent, N, is sufficient for that peer to download (stream) all content needed for that content interval. Therefore, a peer does not need to generate tokens on its own. Token exchange: The token exchange function is the same for all schemes. When a peer downloads a stream from other peers, it can pay" for it by either (i) using tokens it received from other peers, or by (ii) generating new tokens, e.g., if that peer does not have sufficient tokens accumulated from serving other peers. If a peer pays for content by using received tokens, then the new owner of that token appends its ID to the token (e.g., peer k s ID in Fig. 3(b)). In our system, received tokens can be reused, and a peer does not have to generate new tokens each time it wants to download (stream) content. Contribution calculation: Now, we describe how to calculate peers contributions and how to calculate the amount of advertisement, 9 In our system, we encrypt tokens, rather than use digital signatures. The main reason is that use of encryption results in a more secure protocol than one with digital signatures. We discuss this in more detail in Section 4. a i,p, that each peer should watch. In our system, the amount of advertisement is based on a peer s resource contribution. Therefore, we have to calculate the peers contributions first. Contribution calculation is done at the end of t i,p. In the TPCP scheme, peer s contribution is calculated the at peer-side. The number of tokens received by peer i, r i,p, is regarded as the peer s income, and the number of tokens generated by peer i, g i,p, is considered as the peer s spending amount. Note that, if a peer reuses its received tokens, those tokens are not accounted for in r i,p or g i,p. We define the peer s contribution, c i,p, as the difference between r i,p and g i,p, normalized by time, i.e., c i,p = r i,p g i,p t i,p () In the TPCS scheme, the token server is responsible for calculating contributions. Therefore, peers have to report received tokens to the token server. The definition of a peer s contribution in TPCS is the same as Eq. (). In the TSCP scheme, a peer s contribution is also calculated at the peer-side. However, the definition of a peer s contribution is different from Eq. (). In the TSCP scheme, tokens are generated by the token server. Therefore, a peer s income includes the number of tokens received from the token server, N, and the number of tokens received from other peers, r i,p. A peer s spending amount is the number of tokens sent to other peers, s i,p. A peer s contribution in the TSCP scheme, c i,p, is c i,p = N + ri,p si,p t i,p (2) The method used to calculate a i,p is the same in all schemes. We define f i,p, the ratio of the advertisement time length to the time length of streaming content, e.g., in Fig. 2, f i,p is the ratio of a i,p to t i,p. Intuitively, the value of f i,p is inversely proportional to c i,p. Therefore, there are many functions which can be used to determine the value of f i,p, e.g., exponential, linear, logarithm, etc. This choice depends on how quickly" the system would like to reward" peer contributions, e.g., if an exponential function is used, the value of f i,p would decrease quickly as a peer s contribution increases. In this paper, we use a piecewise linear function, as explained next. We classify peers into three groups based on their c i,p. (The service provider defines default, minimum, and maximum values of f i,p, which are described next.) Intuitively, if a peer is a free-rider who does not contribute resources, its resource contribution is Min(c). The value of Min(c) derived from Eq. () in TPCP and TPCS is g i,p/t i,p, and the value of Min(c) derived from Eq. (2) in TSCP is (N s i,p )/t i,p. Then, a free-rider s f i,p is set to the maximum value, Max(f), if it is the maximum length of advertisements for free-riding. Otherwise, a peer s f i,p decreases as its resource contribution increases. If a peer s income is equal to its spending amount, its c i,p is Equal(c) and its f i,p is set to the default value, Def(f), whereas if a peer s c i,p exceeds a threshold, λ, its f i,p is set to the minimum value, Min(f). The value of Equal(c) derived from Eq. () in TPCP and TPCS is, and the value of Equal(c) derived from Eq. (2) in TSCP is N/t i,p. The definition of f i,p is given in Eq. (3), with a corresponding depiction in Fig. 4.
5 Max(f) Def(f) Min(c) Equal(c) i,p+ Min(c) Def(f) Equal(c) Max(f) Min(c) Equal(c), if c i,p < f i,p = (Def(f) Min(f)) c Equal(c) λ i,p+ Equal(c) Min(f) λ Def(f) Equal(c) λ Min(f), if c i,p < λ, if λ c i,p (3) Max(f) Number of peers : 6: 2: 8: 24: Time f i,p Def(f) Figure 5: Population of peers viewing streaming data in the PPLive system Min(f) Min(c) Equal(c) λ c i,p Figure 4: The function used by the token server to calculate f i,p. Finally, we define the amount of advertisement, a i,p, for each peer i as a i,p = f i,p t i,p. In the TPCP and TSCP schemes, the software at the peer-side calculates each peer s a i,p. In the TPCS scheme, the token server sends each peer a message with its a i,p value. After receiving the a i,p value, the display of advertisements, kept in local cache, begins. In addition, the value of f i,p is reported to the streaming server. The streaming server can use this information to decide on the proportion of advertisements to content, when it distributes streamed media. We define f as the ratio of advertisements to content. In our system, the streaming server chooses f to be equal to the average value of f i,p. Reducing overhead: We, now, discuss the issue of token reuse. In our system, received tokens can be reused, and a peer does not have to generate new tokens each time it wants to download (stream) content. An advantage of reusing tokens is the decreased overhead, particularly the amount of computation needed to perform decryption at the token server (as each token is signed by its generator to prevent malicious users from generating fake tokens). We give an example to demonstrate the computational overhead of decryption, using an Intel Xeon E542 and 32GB of memory. There are strings whose lengths are 5 bytes, and these strings are encrypted by 24 bits RSA. The total time to decrypt these strings is about 4 minutes. Although the token server can afford such computational overhead, reusing tokens can decrease it. We depict the token reporting packet structure of reusing tokens and non-reusing tokens in Fig. 3. The two structures are similar - both include serial number, timestamp, generator s ID, and receiver s ID. The difference is that in the reusing mechanism, there is a signature of the token s new owner". As a result, one drawback of reusing tokens is an increase in token reporting packet s length, as the token s new owner" has to append its signature to the token reporting packet. If tokens cannot be reused, a peer can send a packet which includes several tokens, i.e., the last row of the non-reuse packet structure gives the number of tokens", as depicted in Fig. 3. However, even though a packet can include several tokens, the amount of reported packets in the non-reusing mechanism is still higher than the amount in the reusing mechanism. The reason is that peers have to report every packet in the non-reusing mechanism. We note that, in the reusing mechanism, each packet indicates only one token because the receiver cannot split the packet into two packets with a smaller number of tokens. For example, if peer i sends peer j a packet which indicates 5 tokens, and the packet has been encrypted by peer i, then, peer j cannot divide this packet into two packets with 2 and 3 tokens, respectively, as the packet has been encrypted. This limitation may result in more transmitted packets between peers in the reusing tokens mechanism. In Section 3, we compare the overhead and corresponding performance of the reusing tokens and non-reusing tokens mechanisms. 3. EVALUATION In this section, we evaluate the proposed token-based schemes. The goal of this paper is to explore the utility of an approach that uses advertisements as incentives in P2P streaming systems, rather than exploring such a system s implementation. To this end, we use simulations to demonstrate essential characteristics of our system and to study its characteristics in a more controlled environment. An advantage of using simulations is that we can control different parameters and observe effects of each parameter. We develop a simulator to evaluate the proposed token-based schemes, where we use traces to simulate peer dynamics. The traces are available from the PPLive Project at [4], collected from the PPLive streaming system. Specifically, the PPLive crawler takes system snapshots every ten minutes and records peer IDs. The traces used in our simulation are collected during one day. Fig. 5 depicts the population of peers viewing media during a one day period. The simulator assigns the uploading bandwidth of peers based on the distribution given Table 2, which corresponds to measurements in [8]. Because peers typically do not contribute all of their uploading capacity, by default (i.e., unless otherwise stated) we begin with a conservative view and consider peers contributing 6% of their uploading capacity. We also vary this contribution in our simulations (as detailed below). Furthermore, we assume that the downloading bandwidth of peers is sufficient to stream the video (i.e., greater than the streaming rate). We consider single-layer video in our simulations. As stated in [9], most video rates in PPLive are between 25 kbps and 4 kbps;
6 Upload bandwidth (kbps) Distribution (%) Upload bandwidth (kbps) Distribution(%) Table 2: Uploading bandwidth distribution parameter default value k n δ 5kb t i,p min Max(f) Def(f).3 Min(f). Table 3: Default value of parameters thus, in our simulations, the video rates of streaming content is 3 kbps. The number of substreams is k =, which is the same as in [6], i.e., the video is divided into substreams, each with the same video rate. We assume a peer can download an entire substream from one neighbor. Therefore, in our simulations, peers connect to neighbors simultaneously. A peer randomly chooses new neighbors every 3 seconds. (We do not consider peer selection algorithms here since video quality is not the focus of this work.) In these experiments, the default amount of data a peer can download from its neighbor when paying one token, δ, is 5kb. Moreover, the default value of content interval, t i,p, is minutes (which is similar to content intervals used in TV programs), and the amount of advertisements a peer has to view, a i,p, is calculated at the end of each t i,p. In what follows, we vary the values of δ and t i,p (as detailed below). Table 3 summarizes the default parameter values. We now show evaluation results of our system. All results are based on the following assumptions: tokens are received or reported correctly and there are no malicious attacks. Because tokens are encrypted, we can assume malicious peers cannot fake tokens, and tokens can be received or reported correctly. We discuss malicious behavior in Section 4. In our simulations, we need to set the maximum, default, and minimum values of f i,p. We set Max(f) =. The time length of advertisement a peer views is not greater than the time length of content a peer views. In addition, if peer i is a free-rider, the time length of advertisements it has to view is equal to the time length of content it has viewed. Then, we set Def(f) and Min(f) to.3 and., respectively. We base these on statistics given in [24], which show that from 952 to 2, the average of f i,p of TV programs increased from.5 to.47. Because service providers of P2P streaming systems may provide fewer advertisements than TV, to attract users, we believe these are reasonable settings for Def(f) and Min(f). In addition, in our experiments, we use Min(f) >, motivated as follows. As a service provider can receive revenue from displaying advertisements to peers, it is likely to have peers view some amount of advertisements. We also set λ to g i,p /t i,p in TPCP and TPCS schemes and to (N+s i,p )/t i,p in TSCP scheme - that is, if a peer s received tokens are more than twice of its generated or sent tokens (derived from Eqs. () and (2)), its f i,p =.. Since, the ratio of average uploading bandwidth to streaming rate is less than 2 (in this work), we believe this is a reasonable threshold setting. We illustrate that our system can provide peers differentiated service, using the amount of advertisements they view, based on their resource contributions. Fig. 6 demonstrates the average of f i,p for different peer classes in three token-based schemes. The results of the three schemes are similar because we use the same equation to calculate a peer s contribution. The results are not affected by where tokens are generated and contributions are calculated. Our results show that the average of f i,p decreases as a peer s contribution increases. Since the uploading rate of a peer in the first three classes is less than its downloading rate, its f i,p is higher than Def(f). If a peer wants to view fewer advertisements, it needs to increase its uploading rate. Thus, in the next experiment, we increase a peer s uploading rate from 6% of total uploading capacity to 7% and 8%. The trends of f i,p for different peer classes, under 7% and 8% uploading capacity, are qualitatively similar to those when uploading bandwidth is 6% of the capacity. Therefore, we only depict the average of f i,p in Fig. 7. This figure indicates that the average of f i,p decreases about 28% when a peer increases its uploading rate from 6% to 8% of the capacity. This indicates that we can use advertisements as incentives in P2P streaming systems, i.e., in order to view fewer advertisements, a peer needs to contribute more. 3. Advertisement Distribution Recall that in our system, after peers download advertisements, they are kept in the local cache. If the amount of downloaded advertisement is more than the amount of advertisement a peer has to view, some downloaded advertisements would not be displayed. On the other hand, if the amount of downloaded advertisement is less than the amount of advertisement a peer has to view, some downloaded advertisements would be repeated. Therefore, it is an important consideration for the streaming server to determine how much advertisement should be distributed. That is, distributing too much advertisement data causes network overhead and results in some useless advertisements being downloaded by peers. However, distributing too little advertisement content results in peers viewing a lot of repeated advertisements. This situation may not be satisfactory for a service provider as their profit might depend on how often a particular advertisement is viewed. We now consider simple strategies for advertisement distribution. (More sophisticated techniques are possible but are outside the scope of this paper.) To this end, we define the following two performance metrics: surplus: the ratio of advertisement which is not viewed relative to all of downloaded advertisement. The value of i surplus is [max(f,f i,p) f i,p ], where f is the ratio of advertisement to streamed media content and f i,p is based on a i f peer s contribution; repeat: the ratio of repeated advertisement to all of downloaded advertisement. The value of repeat is i [f i,p min(f,f i,p )]. i f In our experiments, we use three different values of f: Min(f), Max(f), and the average of f i,p, Avg(f), and evaluate their surplus and repeat. Because the results of the three schemes are similar, we show the result from the TPCP scheme only. Based on our experiments, the average of surplus and repeat are depicted in Fig.8 and Fig.9, respectively.
7 f i,p f i,p TPCP TPCS TSCP.2. f i,p f i,p uploading bandwidth (kbps) (a) TPCP uploading bandwidth (kbps) (b) TPCS uploading bandwidth (kbps) (c) TSCP Figure 6: average f i,p for peers with different uploading bandwidth in three schemes The results indicate that using Min(f) as f causes less network overhead, with no surplus advertisements. However, this strategy has to display the same advertisement repeatedly. On the other hand, using Max(f) guarantees that peers do not view repeated advertisement; however, it results in significant surplus in advertisement content. Fig.8 demonstrates that the average surplus advertisement is more than 5% of all downloaded advertisement. One approach to finding a balance between these two metrics is to use Avg(f). Our results indicate that the average of surplus and repeat (when using Avg(f)) are both about.. That is, compared to Min(f) and Max(f), using Avg(f) as f can reduce surplus advertisement, while also reducing repeated advertisement. 3.2 Reusing tokens vs. Non-reusing tokens uploading ratio (%) Figure 7: average f i,p for peers with different uploading ratio in three schemes We now focus on reusing tokens vs. non-reusing tokens mechanisms. In the above experiments, peers were allowed to reuse received tokens. As noted earlier, the main advantage of reusing tokens is to reduce overhead of the system, especially in the TPCS scheme, where peers have to report tokens to the token server. Since each token has been encrypted by its generator, there is significant overhead involved in the token decryption process; hence, it is the motivation for reusing tokens in our system. In this section, we use results from the TPCS scheme. Now, recall that in the nonreuse mechanism, after a peer receives tokens from its neighbors, it reports these tokens to the token server immediately, whereas in the reuse mechanisms, a peer can reuse received tokens. Firstly, we focus on the overhead of these two mechanisms. We first define the following parameter. α: the average number of packets reported to the token server by each peer during time interval t i,p. The value of α is # of packets (# of peers)*t i,p. Since the token server s overhead increases as the value of α increases, our goal is to reduce α. Fig. depicts the value of α in these two mechanisms under different values of δ. In the non-reuse mechanism, α remains constant as a function of δ. The reason for this is that in the non-reuse scheme, each packet can include several tokens, as shown in Fig. 3. Fig. illustrates that α decreases in the reuse mechanism as δ increases. This indicates that the reuse mechanism reports fewer packets than the non-reuse mechanism when δ is sufficiently large (e.g., 25kb and 5kb in our experiments). Hence, reusing tokens can reduce overhead. However, the performance of the reuse mechanism degrades when δ is too small (e.g., kb in our experiments). If δ is too small, a peer has to generate too many tokens. Then, the reuse mechanism behaves worse in terms of overhead than the non-reuse mechanism. Thus, the value of δ should not be too small; otherwise, peers would generate too many tokens, thus increasing the token server s overhead. 3.3 Content Interval, t i,p Now, we focus on the effects of t i,p. If the service provider chooses a small value of t i,p, then the system can reflect peers behavior better. However, if t i,p is too small, the system interrupts peers frequently to display advertisements, which would not lead to good service. Thus, we focus on whether choosing different content in-
8 .6.2 surplus Min(f) Max(f) Avg(f) f difference (%) t i,p (min) Figure 8: The average of surplus by using different f repeat Min(f) Max(f) Avg(f) Figure 9: The average of repeat by using different f α f δ (kb) reuse nonreuse Figure : The value of α under different δ tervals, t i,p, affects accuracy when calculating peers contribution. We also consider overhead at the token server under different t i,p values. Therefore, we use results from the TPCS scheme. We vary t i,p from minute to 2 minutes and calculate f i,p under different t i,p s. We use f i,p with the minute setting as our baseline. Then, we define difference as the difference between f i,p under different t i,p s and the baseline. The equation for difference is i f i,p fi,p baseline i f i,p baseline, and the results are given in Fig.. (Here, we focus on the overall system performance rather than on per class behavior.) Figure : The average of difference under different t i,p difference (%) uploading ratio (%) Figure 2: The average of difference when peer s uploading ratio changes from 6% to %, t i,p = min When t i,p increases, the difference also increases. By using short t i,p, the system can account for peers contributions in real time. On the other hand, if the system updates using longer time intervals, the results represent peers average contributions during t i,p. In addition to t i,p, peers uploading rate also affects results. In Fig.2, t i,p is fixed at min, and a peer s uploading rate changes from 6% of upload capacity to %. The results indicate that the difference increases when a peer increases its uploading rate. When a peer increases its uploading rate to % of the capacity, the average uploading bandwidth is higher than the video rate. Then, a peer has more choices when selecting from which peers to download. Therefore, the number of uploading connections for each peer may change dramatically while the number of downloading connections stays the same. In such a case, the difference may increase. We now consider the token server s overhead under different t i,p s. We depict α, the average number of reported tokens, in Fig.3(a). In addition, we define β as the average number of times each token has been reused, with results depicted in Fig.3(b). Fig.3 demonstrates that α decreases and β increases, when the token server chooses longer t i,p s. The results indicate that using longer t i,p s can reduce overhead at the token server, i.e., tokens can be reused more times when t i,p is longer. 4. DISCUSSION
9 α β t i,p (min) (a) α: the average number of reported tokens t i,p (min) (b) β: the average number of times each token has been reused Figure 3: The overhead in token servers. Extending to multi-layer streaming: Our experiments use singlelayer streaming. However, our token-based schemes can be extended to multi-layer-based streaming. Briefly, in the TPCP and TPCS schemes, a peer with low uploading bandwidth can just download the base layer and generate fewer tokens. A peer with high upload bandwidth can download more enhanced layers and pay more tokens. In the TSCP scheme, the token server sends peers tokens. Although the number of tokens is sufficient to download all streaming content, including base and enhanced layers, a peer with low upload bandwidth can just download the base layer and keep the rest of the tokens. In such a case, its contribution can increase because its s i,p decreases as shown in Eq. (2). The usage depends on a peer s preference. If a peer prefers higher video quality, it can use the tokens to obtain enhanced layers and view more advertisement. Otherwise, a peer can choose lower video quality streaming and view fewer advertisements. Overhead of distributing advertisement: In our system, peers have to download advertisements. When peers connection capacities are poor, distribution of advertisements may make such a situation even worse. There are two possible solutions for solving the problem. The first solution is to pre-load advertisements before peers start to download content. Then, peers can just download content later. The second solution is to display downloaded advertisements repeatedly. Therefore, peers do not have to download new advertisements and can save bandwidth for downloading content. However, the two solutions may conflict with the service provider s profit. The service provider may prefer that peers watch new advertisements each time. In such a case, the service provider can deliver low quality advertisements or different types of advertisements whose sizes are small, such as flash animation, to reduce transmission overhead. Overhead of token decryption: In our system, every token is encrypted to prevent peers from faking tokens. However, decryption is a significant computational overhead in our system. Therefore, in order to reduce such overhead, peers are allowed to reuse tokens. When the length of a token is sufficiently large, an alternative mechanism that can reduce computational overhead is the use of digital signatures. In such a mechanism, peer i uses hash functions to generate a message digest of a token. Then, peer i encrypts the message digest with its private key. The result is peer i s digital signature for the token. Finally, peer i appends the digital signature to the token. After peer j receives this token from peer i, peer j can decrypt the signature by using peer i s public key and verify whether the token is sent by peer i. Because the length of a digital signature is shorter than the length of a token, the overhead of decrypting a digital signature is less than the overhead of decrypting an encrypted token. However, this would prove that a token is sent by a specific peer, but will not prevent peers from faking tokens. After malicious peers receive tokens with digital signatures, they can extract tokens content and fake tokens. In addition, malicious peers can just remove appended digital signatures from tokens and modify tokens. This is in contrast to encryption algorithms where a token can be decrypted only by token servers. Hence, we adopt encryption algorithms. 4. Comparisons between token-based schemes In Section 3, we show that using different schemes does not affect peers contribution. In this paper, the motivation for considering different schemes is to explore several issues. We discuss these issues below. Reliability: First, we discuss reliability characteristics of the three schemes. Among these schemes, TPCP is more reliable than TPCS and TSCP. The reason is that TPCP is a distributed scheme and it does not have to worry about token server failure. However, in the other schemes, the system has to deal with token server failure. In TPCS, the token server is responsible for calculating peers contributions and informing peers about the amount of advertisement they have to watch. If the token server fails, peers do not know how much advertisement they have to watch. To solve this problem, we can set a timer. If the waiting time for a token server s message exceeds the timer, the system starts to display advertisements. The length of advertisements can be based on peers history or the default value set by the service provider. In TSCP, the token server is responsible for delivering tokens to peers. If the token server fails, there are no tokens sent to peers, and peers cannot download data because of lack of tokens. In our future work, we will focus on how to increase system reliability. Overhead: In all token-based schemes, token generation, distribution, and decryption all represent overhead for the system. In TPCP, the overhead is shared by peers. However, in TPCS and TSCP, the token server has to deal with tokens. In TPCS, the token server needs to decrypt tokens before it calculates peers contributions. To reduce decryption overhead, we propose the reusing token mechanism, and our results demonstrate that this mechanism can reduce the amount of reported tokens. In the TSCP scheme, the token server is responsible for encrypting and distributing tokens to peers. To reduce such overhead, the token server can send tokens using a staggered schedule, rather than sending tokens to all peers at once. However, this may reduce system reliability.
10 Token Management: Although TPCS and TSCP are less reliable than TPCP, they result in better token management. In TSCP, tokens are generated by the token server. Therefore, the token server can control the number of tokens distributed to peers and force peers to contribute their resources. In this paper, we assume the number of tokens generated by the token server is enough for peers to download the entire content. In order to force peers to contribute resources, the token server can generate fewer tokens. In such a case, peers would have to contribute more to earn more tokens for downloading the entire content. In TPCS, tokens are reported to the token server. Therefore, the token server has better information about peers contributions and behavior. The information can be used for further system analysis and development. Service providers can use the information to decide how to distribute advertisements and which advertisements should be distributed. In our system, we use the information to determine the amount of advertisements distributed during each time interval. Service providers can use different mechanisms. For example, since service providers must satisfy advertisers needs, they can design a display schedule of advertisements based on how long peers watch advertisements and make sure every advertisement is viewed at least a specific number of times. They can also have several schedules to maximize revenues based on different peers behavior. Another example is that service providers can change system settings based on peers behavior. They can measure how much bandwidth peers are willing to contribute and determine whether they should increase or decrease the amount of advertisements. Such directions are outside the scope of this paper and are part of future efforts. In addition, peers contributions are calculated by the token server in TPCS. It can eliminate falsifying contributions at the peer-side. Malicious attacks: The motivation for using token-based schemes, in addition to reporting contributions by peers, is to determine true peers contributions. Using encrypted tokens can also prevent peers from faking tokens. Here, we discuss some attack methods and show how to protect our system from these attacks. One possible attack is from colluding peers. For instance, a peer with high upload bandwidth can forward its tokens to other peers without receiving uploads, in order to help them increase their contributions. To address this attack, when the system calculates a peer s contribution, it can consider a peer s income and spending amount simultaneously. For example, when malicious peers forward their tokens to others, the tokens would be considered as their spending. When their spending amount increases, their contribution would decrease. Thus, malicious peers would hurt their contributions by forwarding their tokens to other peers. Another solution is for service providers to change contribution calculation functions. We give two possible methods to demonstrate the idea of how to modify such functions. We define t i as the number of tokens peer i has and c i as its contribution. In this paper, we use a linear function to calculate c i. Therefore, one possibility for service providers is to change coefficients of the function. For example, the contribution calculated by the new function, c new i, is c i k, where k is larger than. In such a case, a peer needs k times the number of tokens to maintain the same contribution. Another alternative for service providers is to consider non-liner functions. Then, when a peer receives a token, the increased value of its contribution is different and is based on the number of tokens it has. For example, service providers can use an exponential function to calculate peers contributions (e.g., c new i = e t i ). In such a case, when a peer forwards its tokens to other peers, the decreased value of its contribution may be larger than the increased value of other peers contributions. Therefore, it may cause a significant loss for malicious peers contributions to forward their tokens to others. The solutions may not eliminate colluding attacks totally if a peer has a lot of tokens. However, such solutions can reduce the the number of peers that can participate. Another possible attack in TPCS is to ignore messages from the token server. For this attack, the solution is the same as the method used when the token server is down. The software will display advertisements after a set timer is exceeded. Finally, in TPCP and TSCP, contributions are calculated at the peerside. Therefore, malicious peers may try to modify software parameters, such as Max(f), Def(f), and Min(f), and affect results of contribution calculation. However, to execute such attacks, malicious peers need to modify the software. It is typically difficult (i.e., requires a certain level of expertise) to make such modifications. This issue is outside the scope of this paper and is part of future efforts. 5. RELATED WORK Since P2P streaming services became popular, there has been a number of efforts focusing on measurement and analysis of P2P streaming systems, e.g., as in [9, 2, 27]. For instance, [9] and [27] both focus on the PPLive system [3], where [9] characterizes user behavior and traffic profiles, while [27] indicates characteristics of the PPLive system that are different from those of P2P file-sharing systems. In [2] the authors focus on the Coolstreaming system and discuss various associated issues, including highly skewed resource distribution, excessive start-up time, and high failure rates during flash crowds. These works demonstrate several characteristics of existing P2P streaming systems that could be helpful for improving current streaming systems or designing future systems. Although several deployed systems have a significant number of users, [3, 5, 6, 3], the architectures of these systems are not open. Therefore, a number of other design efforts can be found in the literature, e.g., [22, 28]. For instance, [22] proposes an unstructured, mesh-based system and indicates that in such systems, the tit-fortat mechanism can result in reasonable streaming performance. In [28], the authors investigate a framework for multi-channel P2P streaming systems, which can address two problems, excessively long channel switching delays and poor performance in channels with a small number of peers. One of the main challenges in P2P streaming systems is provision of incentives for users to contribute their resources to the system - these are the efforts that, in terms of a high level goal (i.e., incentives) are closer to ours. A number of efforts have considered this problem, from a variety of perspectives, e.g., [, 4 6, 2, 2, 23]. For instance, [4] and [5] propose layered coding/mdc schemes with a tit-for-tat type strategy. The schemes use video quality as an incentive for peers to increase their upload rates. In [], the authors design an unstructured protocol that can reduce the end-to-end streaming delay and improve delivered content quality. Specifically, they combine a push-pull scheme and a scorebased scheme as an incentive method. In [23], the authors address two main problems in tree-based systems and propose an unstructured swarm overlay system. A credit-based incentive scheme is adopted in order to fully utilize upload bandwidth. In [2] the authors study the effects of a local pairwise incentive mechanism and focus on resource availability and the average quality of paths. The work in [2] demonstrates that a tit-for-tat scheme may not work
improving the performance and robustness of P2P live streaming with Contracts
 MICHAEL PIATEK AND ARVIND KRISHNAMURTHY improving the performance and robustness of P2P live streaming with Contracts Michael Piatek is a graduate student at the University of Washington. After spending
MICHAEL PIATEK AND ARVIND KRISHNAMURTHY improving the performance and robustness of P2P live streaming with Contracts Michael Piatek is a graduate student at the University of Washington. After spending
Improving QoS in BitTorrent-like VoD Systems
 Improving QoS in BitTorrent-like VoD Systems Yan Yang Univ. of Southern California yangyan@usc.edu Alix L.H. Chow Univ. of Southern California lhchow@usc.edu Leana Golubchik Univ. of Southern California
Improving QoS in BitTorrent-like VoD Systems Yan Yang Univ. of Southern California yangyan@usc.edu Alix L.H. Chow Univ. of Southern California lhchow@usc.edu Leana Golubchik Univ. of Southern California
Peer-to-Peer Streaming Systems. Behzad Akbari
 Peer-to-Peer Streaming Systems Behzad Akbari 1 Outline Introduction Scaleable Streaming Approaches Application Layer Multicast Content Distribution Networks Peer-to-Peer Streaming Metrics Current Issues
Peer-to-Peer Streaming Systems Behzad Akbari 1 Outline Introduction Scaleable Streaming Approaches Application Layer Multicast Content Distribution Networks Peer-to-Peer Streaming Metrics Current Issues
SALSA: Super-Peer Assisted Live Streaming Architecture
 SALSA: Super-Peer Assisted Live Streaming Architecture Jongtack Kim School of EECS, INMC Seoul National University Email: jkim@netlab.snu.ac.kr Yugyung Lee School of Computing and Engineering University
SALSA: Super-Peer Assisted Live Streaming Architecture Jongtack Kim School of EECS, INMC Seoul National University Email: jkim@netlab.snu.ac.kr Yugyung Lee School of Computing and Engineering University
An Efficient Scheme for Detecting Malicious Nodes in Mobile ad Hoc Networks
 An Efficient Scheme for Detecting Malicious Nodes in Mobile ad Hoc Networks December 1. 2006 Jong Oh Choi Department of Computer Science Yonsei University jochoi@emerald.yonsei.ac.kr Contents Motivation
An Efficient Scheme for Detecting Malicious Nodes in Mobile ad Hoc Networks December 1. 2006 Jong Oh Choi Department of Computer Science Yonsei University jochoi@emerald.yonsei.ac.kr Contents Motivation
COOCHING: Cooperative Prefetching Strategy for P2P Video-on-Demand System
 COOCHING: Cooperative Prefetching Strategy for P2P Video-on-Demand System Ubaid Abbasi and Toufik Ahmed CNRS abri ab. University of Bordeaux 1 351 Cours de la ibération, Talence Cedex 33405 France {abbasi,
COOCHING: Cooperative Prefetching Strategy for P2P Video-on-Demand System Ubaid Abbasi and Toufik Ahmed CNRS abri ab. University of Bordeaux 1 351 Cours de la ibération, Talence Cedex 33405 France {abbasi,
Master s Thesis. A Construction Method of an Overlay Network for Scalable P2P Video Conferencing Systems
 Master s Thesis Title A Construction Method of an Overlay Network for Scalable P2P Video Conferencing Systems Supervisor Professor Masayuki Murata Author Hideto Horiuchi February 14th, 2007 Department
Master s Thesis Title A Construction Method of an Overlay Network for Scalable P2P Video Conferencing Systems Supervisor Professor Masayuki Murata Author Hideto Horiuchi February 14th, 2007 Department
An Empirical Study of Flash Crowd Dynamics in a P2P-based Live Video Streaming System
 An Empirical Study of Flash Crowd Dynamics in a P2P-based Live Video Streaming System Bo Li,GabrielY.Keung,SusuXie,Fangming Liu,YeSun and Hao Yin Hong Kong University of Science and Technology Tsinghua
An Empirical Study of Flash Crowd Dynamics in a P2P-based Live Video Streaming System Bo Li,GabrielY.Keung,SusuXie,Fangming Liu,YeSun and Hao Yin Hong Kong University of Science and Technology Tsinghua
Peer-to-Peer Streaming of Layered Video: Efficiency, Fairness and Incentive
 1 Peer-to-Peer Streaming of Layered Video: Efficiency, Fairness and Incentive Hao Hu, Yang Guo, and Yong Liu Electrical & Computer Engineering, Polytechnic Institute of NYU, Brooklyn, NY 1121 Research
1 Peer-to-Peer Streaming of Layered Video: Efficiency, Fairness and Incentive Hao Hu, Yang Guo, and Yong Liu Electrical & Computer Engineering, Polytechnic Institute of NYU, Brooklyn, NY 1121 Research
Exploring the Optimal Replication Strategy in P2P-VoD Systems: Characterization and Evaluation
 1 Exploring the Optimal Replication Strategy in P2P-VoD Systems: Characterization and Evaluation Weijie Wu, Student Member, IEEE, and John C.S. Lui, Fellow, IEEE Abstract P2P-Video-on-Demand (P2P-VoD)
1 Exploring the Optimal Replication Strategy in P2P-VoD Systems: Characterization and Evaluation Weijie Wu, Student Member, IEEE, and John C.S. Lui, Fellow, IEEE Abstract P2P-Video-on-Demand (P2P-VoD)
Reduction of Periodic Broadcast Resource Requirements with Proxy Caching
 Reduction of Periodic Broadcast Resource Requirements with Proxy Caching Ewa Kusmierek and David H.C. Du Digital Technology Center and Department of Computer Science and Engineering University of Minnesota
Reduction of Periodic Broadcast Resource Requirements with Proxy Caching Ewa Kusmierek and David H.C. Du Digital Technology Center and Department of Computer Science and Engineering University of Minnesota
Towards Low-Redundancy Push-Pull P2P Live Streaming
 Towards Low-Redundancy Push-Pull P2P Live Streaming Zhenjiang Li, Yao Yu, Xiaojun Hei and Danny H.K. Tsang Department of Electronic and Computer Engineering The Hong Kong University of Science and Technology
Towards Low-Redundancy Push-Pull P2P Live Streaming Zhenjiang Li, Yao Yu, Xiaojun Hei and Danny H.K. Tsang Department of Electronic and Computer Engineering The Hong Kong University of Science and Technology
Deploying VSaaS and Hosted Solutions using CompleteView
 SALIENT SYSTEMS WHITE PAPER Deploying VSaaS and Hosted Solutions using CompleteView Understanding the benefits of CompleteView for hosted solutions and successful deployment architectures. Salient Systems
SALIENT SYSTEMS WHITE PAPER Deploying VSaaS and Hosted Solutions using CompleteView Understanding the benefits of CompleteView for hosted solutions and successful deployment architectures. Salient Systems
Using Layered Video to Provide Incentives in P2P Live Streaming
 Using Video to Provide Incentives in P2P Live Streaming Zhengye Liu, Yanming Shen, Shivendra S. Panwar, Keith W. Ross and Yao Wang Dept. of Electrical and Computer Engineering Dept. of Computer and Information
Using Video to Provide Incentives in P2P Live Streaming Zhengye Liu, Yanming Shen, Shivendra S. Panwar, Keith W. Ross and Yao Wang Dept. of Electrical and Computer Engineering Dept. of Computer and Information
Octoshape. Commercial hosting not cable to home, founded 2003
 Octoshape Commercial hosting not cable to home, founded 2003 Broadcasting fee is paid by broadcasters Free for consumers Audio and Video, 32kbps to 800kbps Mesh based, bit-torrent like, Content Server
Octoshape Commercial hosting not cable to home, founded 2003 Broadcasting fee is paid by broadcasters Free for consumers Audio and Video, 32kbps to 800kbps Mesh based, bit-torrent like, Content Server
Second Generation P2P Live Streaming
 Second Generation P2P Live Streaming Keith Ross Polytechnic Institute of NYU Some P2P success stories BitTorrent ecosystem The most successful open app of the decade Skype The most successful VoIP app
Second Generation P2P Live Streaming Keith Ross Polytechnic Institute of NYU Some P2P success stories BitTorrent ecosystem The most successful open app of the decade Skype The most successful VoIP app
An Analysis of User Dynamics in P2P Live Streaming Services
 An Analysis of User Dynamics in P2P Live Streaming Services Kunwoo Park, Dukhyun Chang, Junghoon Kim, Wonjun Yoon, and Ted Taekyoung Kwon School of Computer Science and Engineering, Seoul National University,
An Analysis of User Dynamics in P2P Live Streaming Services Kunwoo Park, Dukhyun Chang, Junghoon Kim, Wonjun Yoon, and Ted Taekyoung Kwon School of Computer Science and Engineering, Seoul National University,
MoB: A Mobile Bazaar for Wide Area Wireless Services. R.Chakravorty, S.Agarwal, S.Banerjee and I.Pratt mobicom 2005
 MoB: A Mobile Bazaar for Wide Area Wireless Services R.Chakravorty, S.Agarwal, S.Banerjee and I.Pratt mobicom 2005 What is MoB? It is an infrastructure for collaborative wide-area wireless data services.
MoB: A Mobile Bazaar for Wide Area Wireless Services R.Chakravorty, S.Agarwal, S.Banerjee and I.Pratt mobicom 2005 What is MoB? It is an infrastructure for collaborative wide-area wireless data services.
On Minimizing Packet Loss Rate and Delay for Mesh-based P2P Streaming Services
 On Minimizing Packet Loss Rate and Delay for Mesh-based P2P Streaming Services Zhiyong Liu, CATR Prof. Zhili Sun, UniS Dr. Dan He, UniS Denian Shi, CATR Agenda Introduction Background Problem Statement
On Minimizing Packet Loss Rate and Delay for Mesh-based P2P Streaming Services Zhiyong Liu, CATR Prof. Zhili Sun, UniS Dr. Dan He, UniS Denian Shi, CATR Agenda Introduction Background Problem Statement
John L. Miller and Jon Crowcroft NetGames 2010
 John L. Miller and Jon Crowcroft NetGames 2010 1 Motivation Data Capture and Processing Operational Assumptions Simulator Results Conclusions 2 Challenges in DVE s well known Scalability, latency, security
John L. Miller and Jon Crowcroft NetGames 2010 1 Motivation Data Capture and Processing Operational Assumptions Simulator Results Conclusions 2 Challenges in DVE s well known Scalability, latency, security
Optical networking technology
 1 Optical networking technology Technological advances in semiconductor products have essentially been the primary driver for the growth of networking that led to improvements and simplification in the
1 Optical networking technology Technological advances in semiconductor products have essentially been the primary driver for the growth of networking that led to improvements and simplification in the
Chunk Scheduling Strategies In Peer to Peer System-A Review
 Chunk Scheduling Strategies In Peer to Peer System-A Review Sanu C, Deepa S S Abstract Peer-to-peer ( P2P) s t r e a m i n g systems have become popular in recent years. Several peer- to-peer systems for
Chunk Scheduling Strategies In Peer to Peer System-A Review Sanu C, Deepa S S Abstract Peer-to-peer ( P2P) s t r e a m i n g systems have become popular in recent years. Several peer- to-peer systems for
An incentive based approach to detect selfish nodes in Mobile P2P network
 Scholars' Mine Masters Theses Student Research & Creative Works Spring 2011 An incentive based approach to detect selfish nodes in Mobile P2P network Hemanth Meka Follow this and additional works at: http://scholarsmine.mst.edu/masters_theses
Scholars' Mine Masters Theses Student Research & Creative Works Spring 2011 An incentive based approach to detect selfish nodes in Mobile P2P network Hemanth Meka Follow this and additional works at: http://scholarsmine.mst.edu/masters_theses
Routing Protocols in MANETs
 Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
MEASUREMENT STUDY OF A P2P IPTV SYSTEM: SOPCAST
 International Journal of Computer Networking, Wireless and Mobile Communications (IJCNWMC) ISSN 2250 1568 Vol.2, Issue 2 June 2012 72-78 TJPRC Pvt. Ltd., MEASUREMENT STUDY OF A P2P IPTV SYSTEM: SOPCAST
International Journal of Computer Networking, Wireless and Mobile Communications (IJCNWMC) ISSN 2250 1568 Vol.2, Issue 2 June 2012 72-78 TJPRC Pvt. Ltd., MEASUREMENT STUDY OF A P2P IPTV SYSTEM: SOPCAST
Do incentives build robustness in BitTorrent?
 Do incentives build robustness in BitTorrent? ronghui.gu@yale.edu Agenda 2 Introduction BitTorrent Overview Modeling Altruism in BitTorrent Building BitTyrant Evaluation Conclusion Introduction 3 MAIN
Do incentives build robustness in BitTorrent? ronghui.gu@yale.edu Agenda 2 Introduction BitTorrent Overview Modeling Altruism in BitTorrent Building BitTyrant Evaluation Conclusion Introduction 3 MAIN
PeerApp Case Study. November University of California, Santa Barbara, Boosts Internet Video Quality and Reduces Bandwidth Costs
 PeerApp Case Study University of California, Santa Barbara, Boosts Internet Video Quality and Reduces Bandwidth Costs November 2010 Copyright 2010-2011 PeerApp Ltd. All rights reserved 1 Executive Summary
PeerApp Case Study University of California, Santa Barbara, Boosts Internet Video Quality and Reduces Bandwidth Costs November 2010 Copyright 2010-2011 PeerApp Ltd. All rights reserved 1 Executive Summary
Loopback: Exploiting Collaborative Caches for Large-Scale Streaming
 Loopback: Exploiting Collaborative Caches for Large-Scale Streaming Ewa Kusmierek Yingfei Dong David Du Poznan Supercomputing and Dept. of Electrical Engineering Dept. of Computer Science Networking Center
Loopback: Exploiting Collaborative Caches for Large-Scale Streaming Ewa Kusmierek Yingfei Dong David Du Poznan Supercomputing and Dept. of Electrical Engineering Dept. of Computer Science Networking Center
Extreme Computing. BitTorrent and incentive-based overlay networks.
 Extreme Computing BitTorrent and incentive-based overlay networks BitTorrent Today we will focus on BitTorrent The technology really has three aspects A standard that BitTorrent client systems follow Some
Extreme Computing BitTorrent and incentive-based overlay networks BitTorrent Today we will focus on BitTorrent The technology really has three aspects A standard that BitTorrent client systems follow Some
AODV-PA: AODV with Path Accumulation
 -PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
-PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
Sleep/Wake Aware Local Monitoring (SLAM)
 Sleep/Wake Aware Local Monitoring (SLAM) Issa Khalil, Saurabh Bagchi, Ness Shroff Dependable Computing Systems Lab (DCSL) & Center for Wireless Systems and Applications (CWSA) School of Electrical and
Sleep/Wake Aware Local Monitoring (SLAM) Issa Khalil, Saurabh Bagchi, Ness Shroff Dependable Computing Systems Lab (DCSL) & Center for Wireless Systems and Applications (CWSA) School of Electrical and
The Design Trade-offs of BitTorrent-like File Sharing Protocols
 The Design Trade-offs of BitTorrent-like File Sharing Protocols Bin Fan John C.S. Lui Dah-Ming Chiu Abstract The BitTorrent BT file sharing protocol is very popular due to its scalability property and
The Design Trade-offs of BitTorrent-like File Sharing Protocols Bin Fan John C.S. Lui Dah-Ming Chiu Abstract The BitTorrent BT file sharing protocol is very popular due to its scalability property and
Fast and low-cost search schemes by exploiting localities in P2P networks
 J. Parallel Distrib. Comput. 65 (5) 79 74 www.elsevier.com/locate/jpdc Fast and low-cost search schemes by exploiting localities in PP networks Lei Guo a, Song Jiang b, Li Xiao c, Xiaodong Zhang a, a Department
J. Parallel Distrib. Comput. 65 (5) 79 74 www.elsevier.com/locate/jpdc Fast and low-cost search schemes by exploiting localities in PP networks Lei Guo a, Song Jiang b, Li Xiao c, Xiaodong Zhang a, a Department
A Case For OneSwarm. Tom Anderson University of Washington.
 A Case For OneSwarm Tom Anderson University of Washington http://oneswarm.cs.washington.edu/ With: Jarret Falkner, Tomas Isdal, Alex Jaffe, John P. John, Arvind Krishnamurthy, Harsha Madhyastha and Mike
A Case For OneSwarm Tom Anderson University of Washington http://oneswarm.cs.washington.edu/ With: Jarret Falkner, Tomas Isdal, Alex Jaffe, John P. John, Arvind Krishnamurthy, Harsha Madhyastha and Mike
Resource analysis of network virtualization through user and network
 Resource analysis of network virtualization through user and network P.N.V.VAMSI LALA, Cloud Computing, Master of Technology, SRM University, Potheri. Mr.k.Venkatesh, Asst.Professor (Sr.G), Information
Resource analysis of network virtualization through user and network P.N.V.VAMSI LALA, Cloud Computing, Master of Technology, SRM University, Potheri. Mr.k.Venkatesh, Asst.Professor (Sr.G), Information
A Streaming Method with Trick Play on Time Division based Multicast
 A Streaming Method with Trick Play on Time Division based Yoshitaka Nakamura, Kazuki Murakoshi Yoh Shiraishi and Osamu Takahashi School of Systems Information Science, Future University Hakodate, Japan
A Streaming Method with Trick Play on Time Division based Yoshitaka Nakamura, Kazuki Murakoshi Yoh Shiraishi and Osamu Takahashi School of Systems Information Science, Future University Hakodate, Japan
Technical White Paper. Cube Engine Version 1.0
 Technical White Paper Cube Engine Version 1.0 Last Updated: Feb 06. 2018 1 Contents 1. Summary 1) Introduction 2) Overview 2. Features of Cube Chain 1) Cubing 2) Indexing Block 3) Statistics Block 4) Escrow
Technical White Paper Cube Engine Version 1.0 Last Updated: Feb 06. 2018 1 Contents 1. Summary 1) Introduction 2) Overview 2. Features of Cube Chain 1) Cubing 2) Indexing Block 3) Statistics Block 4) Escrow
A connection management protocol for promoting cooperation in Peer-to-Peer networks q
 Available online at www.sciencedirect.com Computer Communications 31 (2008) 240 256 www.elsevier.com/locate/comcom A connection management protocol for promoting cooperation in Peer-to-Peer networks q
Available online at www.sciencedirect.com Computer Communications 31 (2008) 240 256 www.elsevier.com/locate/comcom A connection management protocol for promoting cooperation in Peer-to-Peer networks q
Improving BitTorrent: A Simple Approach
 Improving BitTorrent: A Simple Approach Alix L.H. Chow Univ. of Southern California Leana Golubchik Univ. of Southern California Vishal Misra Columbia University Abstract Measurement studies have shown
Improving BitTorrent: A Simple Approach Alix L.H. Chow Univ. of Southern California Leana Golubchik Univ. of Southern California Vishal Misra Columbia University Abstract Measurement studies have shown
Stochastic Analysis and File Availability Enhancement for BT-like File Sharing Systems
 Stochastic Analysis and File Availability Enhancement for BT-like File Sharing Systems Fan Bin Dah-Ming Chiu John C.S. Lui Abstract In this paper, we present the mathematical analysis of two important
Stochastic Analysis and File Availability Enhancement for BT-like File Sharing Systems Fan Bin Dah-Ming Chiu John C.S. Lui Abstract In this paper, we present the mathematical analysis of two important
Improved dynamic multimedia resource adaptation-based Peer-to-Peer system through locality-based clustering and service
 University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2005 Improved dynamic multimedia resource adaptation-based Peer-to-Peer
University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2005 Improved dynamic multimedia resource adaptation-based Peer-to-Peer
SUMMERY, CONCLUSIONS AND FUTURE WORK
 Chapter - 6 SUMMERY, CONCLUSIONS AND FUTURE WORK The entire Research Work on On-Demand Routing in Multi-Hop Wireless Mobile Ad hoc Networks has been presented in simplified and easy-to-read form in six
Chapter - 6 SUMMERY, CONCLUSIONS AND FUTURE WORK The entire Research Work on On-Demand Routing in Multi-Hop Wireless Mobile Ad hoc Networks has been presented in simplified and easy-to-read form in six
BIPAR: BImodal Power-Aware Routing Protocol For Wireless Sensor Networks
 BIPAR: BImodal Power-Aware Routing Protocol For Wireless Sensor Networks Abstract HANY MORCOS IBRAHIM MATTA AZER BESTAVROS {hmorcos, matta, best}@cs.bu.edu Computer Science Department, Boston University
BIPAR: BImodal Power-Aware Routing Protocol For Wireless Sensor Networks Abstract HANY MORCOS IBRAHIM MATTA AZER BESTAVROS {hmorcos, matta, best}@cs.bu.edu Computer Science Department, Boston University
Contracts: Practical Contribution Incentives for P2P Live Streaming
 Contracts: Practical Contribution Incentives for P2P Live Streaming Michael Piatek, Arvind Krishnamurthy, Arun Venkataramani, Richard Yang, David Zhang, Alexander Jaffe U. of Washington, U. of Massachusetts,
Contracts: Practical Contribution Incentives for P2P Live Streaming Michael Piatek, Arvind Krishnamurthy, Arun Venkataramani, Richard Yang, David Zhang, Alexander Jaffe U. of Washington, U. of Massachusetts,
Cloud Movie: Cloud Based Dynamic Resources Allocation And Parallel Execution On Vod Loading Virtualization
 Cloud Movie: Cloud Based Dynamic Resources Allocation And Parallel Execution On Vod Loading Virtualization Akshatha K T #1 #1 M.Tech 4 th sem (CSE), VTU East West Institute of Technology India. Prasad
Cloud Movie: Cloud Based Dynamic Resources Allocation And Parallel Execution On Vod Loading Virtualization Akshatha K T #1 #1 M.Tech 4 th sem (CSE), VTU East West Institute of Technology India. Prasad
CHAPTER 4 SINGLE LAYER BLACK HOLE ATTACK DETECTION
 58 CHAPTER 4 SINGLE LAYER BLACK HOLE ATTACK DETECTION 4.1 INTRODUCTION TO SLBHAD The focus of this chapter is to detect and isolate Black Hole attack in the MANET (Khattak et al 2013). In order to do that,
58 CHAPTER 4 SINGLE LAYER BLACK HOLE ATTACK DETECTION 4.1 INTRODUCTION TO SLBHAD The focus of this chapter is to detect and isolate Black Hole attack in the MANET (Khattak et al 2013). In order to do that,
Formal Expression of BBc-1 Mechanism and Its Security Analysis
 Formal Expression of BBc-1 Mechanism and Its Security Analysis Jun KURIHARA and Takeshi KUBO kurihara@ieee.org t-kubo@zettant.com October 31, 2017 1 Introduction Bitcoin and its core database/ledger technology
Formal Expression of BBc-1 Mechanism and Its Security Analysis Jun KURIHARA and Takeshi KUBO kurihara@ieee.org t-kubo@zettant.com October 31, 2017 1 Introduction Bitcoin and its core database/ledger technology
Internet Pricing. Abstract. 1 Introduction. 2 Interconnection. Md. Rafiqul Hasan Chowdhury Helsinki University of Technology
 Internet Pricing Md. Rafiqul Hasan Chowdhury Helsinki University of Technology rafiqul.chowdhury@hut.fi Abstract Internet pricing can be seen from two points of view - between service providers and end-users
Internet Pricing Md. Rafiqul Hasan Chowdhury Helsinki University of Technology rafiqul.chowdhury@hut.fi Abstract Internet pricing can be seen from two points of view - between service providers and end-users
HSM: A Hybrid Streaming Mechanism for Delay-tolerant Multimedia Applications Annanda Th. Rath 1 ), Saraswathi Krithivasan 2 ), Sridhar Iyer 3 )
 HSM: A Hybrid Streaming Mechanism for Delay-tolerant Multimedia Applications Annanda Th. Rath 1 ), Saraswathi Krithivasan 2 ), Sridhar Iyer 3 ) Abstract Traditionally, Content Delivery Networks (CDNs)
HSM: A Hybrid Streaming Mechanism for Delay-tolerant Multimedia Applications Annanda Th. Rath 1 ), Saraswathi Krithivasan 2 ), Sridhar Iyer 3 ) Abstract Traditionally, Content Delivery Networks (CDNs)
A DHT-Aided Chunk-Driven Overlay for Scalable and Efficient Peer-to-Peer Live Streaming
 A DHT-Aided Chunk-Driven Overlay for Scalable and Efficient Peer-to-Peer Live Streaming Haiying Shen*, Member, IEEE, Ze Li, Student Member, IEEE, Jin Li, Fellow, IEEE Abstract Internet-based video streaming
A DHT-Aided Chunk-Driven Overlay for Scalable and Efficient Peer-to-Peer Live Streaming Haiying Shen*, Member, IEEE, Ze Li, Student Member, IEEE, Jin Li, Fellow, IEEE Abstract Internet-based video streaming
CC-SCTP: Chunk Checksum of SCTP for Enhancement of Throughput in Wireless Network Environments
 CC-SCTP: Chunk Checksum of SCTP for Enhancement of Throughput in Wireless Network Environments Stream Control Transmission Protocol (SCTP) uses the 32-bit checksum in the common header, by which a corrupted
CC-SCTP: Chunk Checksum of SCTP for Enhancement of Throughput in Wireless Network Environments Stream Control Transmission Protocol (SCTP) uses the 32-bit checksum in the common header, by which a corrupted
Considering Priority in Overlay Multicast Protocols under Heterogeneous Environments
 Considering Priority in Overlay Multicast Protocols under Heterogeneous Environments Michael Bishop and Sanjay Rao Purdue University Kunwadee Sripanidkulchai National Electronics and Computer Technology
Considering Priority in Overlay Multicast Protocols under Heterogeneous Environments Michael Bishop and Sanjay Rao Purdue University Kunwadee Sripanidkulchai National Electronics and Computer Technology
Enhancing Downloading Time By Using Content Distribution Algorithm
 RESEARCH ARTICLE OPEN ACCESS Enhancing Downloading Time By Using Content Distribution Algorithm VILSA V S Department of Computer Science and Technology TKM Institute of Technology, Kollam, Kerala Mailid-vilsavijay@gmail.com
RESEARCH ARTICLE OPEN ACCESS Enhancing Downloading Time By Using Content Distribution Algorithm VILSA V S Department of Computer Science and Technology TKM Institute of Technology, Kollam, Kerala Mailid-vilsavijay@gmail.com
Network-Adaptive Video Coding and Transmission
 Header for SPIE use Network-Adaptive Video Coding and Transmission Kay Sripanidkulchai and Tsuhan Chen Department of Electrical and Computer Engineering, Carnegie Mellon University, Pittsburgh, PA 15213
Header for SPIE use Network-Adaptive Video Coding and Transmission Kay Sripanidkulchai and Tsuhan Chen Department of Electrical and Computer Engineering, Carnegie Mellon University, Pittsburgh, PA 15213
NEUROSEED WHITEPAPER. Version 1.1. May 1, 2018 Contents of the white paper are subject to changes and improvements
 WHITEPAPER Version 1.1 May 1, 2018 Contents of the white paper are subject to changes and improvements ABSTRACT The Fourth Industrial revolution brings the implementation of such technologies like Big
WHITEPAPER Version 1.1 May 1, 2018 Contents of the white paper are subject to changes and improvements ABSTRACT The Fourth Industrial revolution brings the implementation of such technologies like Big
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
A Secure and Dynamic Multi-keyword Ranked Search Scheme over Encrypted Cloud Data
 An Efficient Privacy-Preserving Ranked Keyword Search Method Cloud data owners prefer to outsource documents in an encrypted form for the purpose of privacy preserving. Therefore it is essential to develop
An Efficient Privacy-Preserving Ranked Keyword Search Method Cloud data owners prefer to outsource documents in an encrypted form for the purpose of privacy preserving. Therefore it is essential to develop
The Edge: Delivering the Quality of Experience of Digital Content
 The Edge: Delivering the Quality of Experience of Digital Content 2016 EDITION By Conviva for EdgeConneX As video consumption evolves from single screen to multi-screen, the burden on the Internet and
The Edge: Delivering the Quality of Experience of Digital Content 2016 EDITION By Conviva for EdgeConneX As video consumption evolves from single screen to multi-screen, the burden on the Internet and
Cooperation in Open Distributed Systems. Stefan Schmid
 Cooperation in Open Distributed Systems Stefan Schmid T-Labs, Berlin, July 2, 2009 Distributed Systems 2008/9 Wireless: Many mobile phones today have WLAN (and even Skype) P2P: Olympic games 2008 live-broadcast
Cooperation in Open Distributed Systems Stefan Schmid T-Labs, Berlin, July 2, 2009 Distributed Systems 2008/9 Wireless: Many mobile phones today have WLAN (and even Skype) P2P: Olympic games 2008 live-broadcast
Computation of Multiple Node Disjoint Paths
 Chapter 5 Computation of Multiple Node Disjoint Paths 5.1 Introduction In recent years, on demand routing protocols have attained more attention in mobile Ad Hoc networks as compared to other routing schemes
Chapter 5 Computation of Multiple Node Disjoint Paths 5.1 Introduction In recent years, on demand routing protocols have attained more attention in mobile Ad Hoc networks as compared to other routing schemes
CHAPTER 5 PROPAGATION DELAY
 98 CHAPTER 5 PROPAGATION DELAY Underwater wireless sensor networks deployed of sensor nodes with sensing, forwarding and processing abilities that operate in underwater. In this environment brought challenges,
98 CHAPTER 5 PROPAGATION DELAY Underwater wireless sensor networks deployed of sensor nodes with sensing, forwarding and processing abilities that operate in underwater. In this environment brought challenges,
Understanding the effect of streaming overlay construction on AS level traffic
 Understanding the effect of streaming overlay construction on AS level traffic Reza Motamedi and Reza Rejaie Information and Computer Science Department University of Oregon e-mail: {reza.motamedi,reza}@cs.uoregon.edu
Understanding the effect of streaming overlay construction on AS level traffic Reza Motamedi and Reza Rejaie Information and Computer Science Department University of Oregon e-mail: {reza.motamedi,reza}@cs.uoregon.edu
CSE 486/586 Distributed Systems Peer-to-Peer Architectures
 CSE 486/586 Distributed Systems eer-to-eer Architectures Steve Ko Computer Sciences and Engineering University at Buffalo CSE 486/586 Last Time Gossiping Multicast Failure detection Today s Question How
CSE 486/586 Distributed Systems eer-to-eer Architectures Steve Ko Computer Sciences and Engineering University at Buffalo CSE 486/586 Last Time Gossiping Multicast Failure detection Today s Question How
Imposing fairness in electronic commerce
 www.ijcsi.org 139 Imposing fairness in electronic commerce Using Trusted Third Party for electronic delivery Fahad A. ALQAHTANI Software Technology Research Laboratory De Montfort University,Leicester,United
www.ijcsi.org 139 Imposing fairness in electronic commerce Using Trusted Third Party for electronic delivery Fahad A. ALQAHTANI Software Technology Research Laboratory De Montfort University,Leicester,United
PRIVACY AND TRUST-AWARE FRAMEWORK FOR SECURE ROUTING IN WIRELESS MESH NETWORKS
 PRIVACY AND TRUST-AWARE FRAMEWORK FOR SECURE ROUTING IN WIRELESS MESH NETWORKS 1 PRASHANTH JAYAKUMAR, 2 P.S.KHANAGOUDAR, 3 VINAY KAVERI 1,3 Department of CSE, GIT, Belgaum, 2 Assistant Professor, Dept.
PRIVACY AND TRUST-AWARE FRAMEWORK FOR SECURE ROUTING IN WIRELESS MESH NETWORKS 1 PRASHANTH JAYAKUMAR, 2 P.S.KHANAGOUDAR, 3 VINAY KAVERI 1,3 Department of CSE, GIT, Belgaum, 2 Assistant Professor, Dept.
SEAR: SECURED ENERGY-AWARE ROUTING WITH TRUSTED PAYMENT MODEL FOR WIRELESS NETWORKS
 SEAR: SECURED ENERGY-AWARE ROUTING WITH TRUSTED PAYMENT MODEL FOR WIRELESS NETWORKS S. P. Manikandan 1, R. Manimegalai 2 and S. Kalimuthu 3 1 Department of Computer Science and Engineering, Sri Venkateshwara
SEAR: SECURED ENERGY-AWARE ROUTING WITH TRUSTED PAYMENT MODEL FOR WIRELESS NETWORKS S. P. Manikandan 1, R. Manimegalai 2 and S. Kalimuthu 3 1 Department of Computer Science and Engineering, Sri Venkateshwara
Video Streaming Over the Internet
 Video Streaming Over the Internet 1. Research Team Project Leader: Graduate Students: Prof. Leana Golubchik, Computer Science Department Bassem Abdouni, Adam W.-J. Lee 2. Statement of Project Goals Quality
Video Streaming Over the Internet 1. Research Team Project Leader: Graduate Students: Prof. Leana Golubchik, Computer Science Department Bassem Abdouni, Adam W.-J. Lee 2. Statement of Project Goals Quality
Evaluating Unstructured Peer-to-Peer Lookup Overlays
 Evaluating Unstructured Peer-to-Peer Lookup Overlays Idit Keidar EE Department, Technion Roie Melamed CS Department, Technion ABSTRACT Unstructured peer-to-peer lookup systems incur small constant overhead
Evaluating Unstructured Peer-to-Peer Lookup Overlays Idit Keidar EE Department, Technion Roie Melamed CS Department, Technion ABSTRACT Unstructured peer-to-peer lookup systems incur small constant overhead
Trust Enhanced Cryptographic Role-based Access Control for Secure Cloud Data Storage
 1 Trust Enhanced Cryptographic Role-based Access Control for Secure Cloud Data Storage Lan Zhou,Vijay Varadharajan,and Michael Hitchens Abstract Cloud data storage has provided significant benefits by
1 Trust Enhanced Cryptographic Role-based Access Control for Secure Cloud Data Storage Lan Zhou,Vijay Varadharajan,and Michael Hitchens Abstract Cloud data storage has provided significant benefits by
The Scalability of Swarming Peer-to-Peer Content Delivery
 The Scalability of Swarming Peer-to-Peer Content Delivery Daniel Zappala Brigham Young University zappala@cs.byu.edu with Daniel Stutzbach Reza Rejaie University of Oregon Page 1 Motivation Small web sites
The Scalability of Swarming Peer-to-Peer Content Delivery Daniel Zappala Brigham Young University zappala@cs.byu.edu with Daniel Stutzbach Reza Rejaie University of Oregon Page 1 Motivation Small web sites
Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks
 Mobile Information Systems 9 (23) 295 34 295 DOI.3233/MIS-364 IOS Press Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks Keisuke Goto, Yuya Sasaki, Takahiro
Mobile Information Systems 9 (23) 295 34 295 DOI.3233/MIS-364 IOS Press Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks Keisuke Goto, Yuya Sasaki, Takahiro
ARTICLE IN PRESS. Journal of Network and Computer Applications
 Journal of Network and Computer Applications 32 (29) 666 683 Contents lists available at ScienceDirect Journal of Network and Computer Applications journal homepage: www.elsevier.com/locate/jnca Principles
Journal of Network and Computer Applications 32 (29) 666 683 Contents lists available at ScienceDirect Journal of Network and Computer Applications journal homepage: www.elsevier.com/locate/jnca Principles
The Design and Implementation of a Next Generation Name Service for the Internet (CoDoNS) Presented By: Kamalakar Kambhatla
 The Design and Implementation of a Next Generation Name Service for the Internet (CoDoNS) Venugopalan Ramasubramanian Emin Gün Sirer Presented By: Kamalakar Kambhatla * Slides adapted from the paper -
The Design and Implementation of a Next Generation Name Service for the Internet (CoDoNS) Venugopalan Ramasubramanian Emin Gün Sirer Presented By: Kamalakar Kambhatla * Slides adapted from the paper -
Multimedia Streaming. Mike Zink
 Multimedia Streaming Mike Zink Technical Challenges Servers (and proxy caches) storage continuous media streams, e.g.: 4000 movies * 90 minutes * 10 Mbps (DVD) = 27.0 TB 15 Mbps = 40.5 TB 36 Mbps (BluRay)=
Multimedia Streaming Mike Zink Technical Challenges Servers (and proxy caches) storage continuous media streams, e.g.: 4000 movies * 90 minutes * 10 Mbps (DVD) = 27.0 TB 15 Mbps = 40.5 TB 36 Mbps (BluRay)=
BitTorrent. Masood Khosroshahy. July Tech. Report. Copyright 2009 Masood Khosroshahy, All rights reserved.
 BitTorrent Masood Khosroshahy July 2009 Tech. Report Copyright 2009 Masood Khosroshahy, All rights reserved. www.masoodkh.com Contents Contents 1 Basic Concepts 1 2 Mechanics 3 2.1 Protocols: Tracker and
BitTorrent Masood Khosroshahy July 2009 Tech. Report Copyright 2009 Masood Khosroshahy, All rights reserved. www.masoodkh.com Contents Contents 1 Basic Concepts 1 2 Mechanics 3 2.1 Protocols: Tracker and
Analysis of P2P Storage Systems. March 13, 2009
 Analysis of P2P Storage Systems Réunion du Boréon March 13, 2009 Program Simulating millions of nodes and billions of events: OSA - BROCCOLI - SPREADS. Participants: Judicael, Olivier. P2P storage systems
Analysis of P2P Storage Systems Réunion du Boréon March 13, 2009 Program Simulating millions of nodes and billions of events: OSA - BROCCOLI - SPREADS. Participants: Judicael, Olivier. P2P storage systems
CSE 4/60373: Multimedia Systems
 CSE 4/60373: Multimedia Systems Outline for today 32: Y.-F. Chen, Y. Huang, R. Jana, H. Jiang, M. Rabinovich, J. Rahe, B. Wei, and Z. Xiao. Towards Capacity and Profit Optimization of Video-on-Demand Services
CSE 4/60373: Multimedia Systems Outline for today 32: Y.-F. Chen, Y. Huang, R. Jana, H. Jiang, M. Rabinovich, J. Rahe, B. Wei, and Z. Xiao. Towards Capacity and Profit Optimization of Video-on-Demand Services
SECURED SOCIAL TUBE FOR VIDEO SHARING IN OSN SYSTEM
 ABSTRACT: SECURED SOCIAL TUBE FOR VIDEO SHARING IN OSN SYSTEM J.Priyanka 1, P.Rajeswari 2 II-M.E(CS) 1, H.O.D / ECE 2, Dhanalakshmi Srinivasan Engineering College, Perambalur. Recent years have witnessed
ABSTRACT: SECURED SOCIAL TUBE FOR VIDEO SHARING IN OSN SYSTEM J.Priyanka 1, P.Rajeswari 2 II-M.E(CS) 1, H.O.D / ECE 2, Dhanalakshmi Srinivasan Engineering College, Perambalur. Recent years have witnessed
Providing NPR-Style Time-Shifted Streaming in P2P Systems
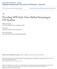 University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln CSE Conference and Workshop Papers Computer Science and Engineering, Department of 11 Providing -Style Time-Shifted Streaming
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln CSE Conference and Workshop Papers Computer Science and Engineering, Department of 11 Providing -Style Time-Shifted Streaming
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks
 A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
T-Chain: A General Incentive Scheme for Cooperative Computing
 : A General Incentive Scheme for Cooperative Computing Kyuyong Shin, Carlee Joe-Wong, Sangtae Ha, Yung Yi, Injong Rhee, Douglas Reeves Korea Military Academy, Princeton University, University of Colorado
: A General Incentive Scheme for Cooperative Computing Kyuyong Shin, Carlee Joe-Wong, Sangtae Ha, Yung Yi, Injong Rhee, Douglas Reeves Korea Military Academy, Princeton University, University of Colorado
Overview of Adaptive TDMA in idx 3.2. May 2015
 Overview of Adaptive TDMA in idx 3.2 May 2015 INTRODUCTION The idirect Adaptive Time Division Multiple Access (TDMA) delivers higher spectral efficiency and greater network versatility by optimally changing
Overview of Adaptive TDMA in idx 3.2 May 2015 INTRODUCTION The idirect Adaptive Time Division Multiple Access (TDMA) delivers higher spectral efficiency and greater network versatility by optimally changing
Study and Comparison of Mesh and Tree- Based Multicast Routing Protocols for MANETs
 Study and Comparison of Mesh and Tree- Based Multicast Routing Protocols for MANETs Rajneesh Gujral Associate Proffesor (CSE Deptt.) Maharishi Markandeshwar University, Mullana, Ambala Sanjeev Rana Associate
Study and Comparison of Mesh and Tree- Based Multicast Routing Protocols for MANETs Rajneesh Gujral Associate Proffesor (CSE Deptt.) Maharishi Markandeshwar University, Mullana, Ambala Sanjeev Rana Associate
Chapter 7 CONCLUSION
 97 Chapter 7 CONCLUSION 7.1. Introduction A Mobile Ad-hoc Network (MANET) could be considered as network of mobile nodes which communicate with each other without any fixed infrastructure. The nodes in
97 Chapter 7 CONCLUSION 7.1. Introduction A Mobile Ad-hoc Network (MANET) could be considered as network of mobile nodes which communicate with each other without any fixed infrastructure. The nodes in
Overlay and P2P Networks. Introduction and unstructured networks. Prof. Sasu Tarkoma
 Overlay and P2P Networks Introduction and unstructured networks Prof. Sasu Tarkoma 14.1.2013 Contents Overlay networks and intro to networking Unstructured networks Overlay Networks An overlay network
Overlay and P2P Networks Introduction and unstructured networks Prof. Sasu Tarkoma 14.1.2013 Contents Overlay networks and intro to networking Unstructured networks Overlay Networks An overlay network
IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL. 21, NO. 8, AUGUST
 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL. 21, NO. 8, AUGUST 2011 1013 Peer-to-Peer Streaming of Layered Video: Efficiency, Fairness and Incentive Hao Hu, Student Member, IEEE,
IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL. 21, NO. 8, AUGUST 2011 1013 Peer-to-Peer Streaming of Layered Video: Efficiency, Fairness and Incentive Hao Hu, Student Member, IEEE,
Substream Trading: Towards an Open P2P Live Streaming System
 Substream Trading: Towards an Open P2P Live Streaming System Zhengye Liu, Yanming Shen, Keith W. Ross, Shivendra S. Panwar, Yao Wang Department of Electrical and Computer Engineering Department of Computer
Substream Trading: Towards an Open P2P Live Streaming System Zhengye Liu, Yanming Shen, Keith W. Ross, Shivendra S. Panwar, Yao Wang Department of Electrical and Computer Engineering Department of Computer
Stretch-Optimal Scheduling for On-Demand Data Broadcasts
 Stretch-Optimal Scheduling for On-Demand Data roadcasts Yiqiong Wu and Guohong Cao Department of Computer Science & Engineering The Pennsylvania State University, University Park, PA 6 E-mail: fywu,gcaog@cse.psu.edu
Stretch-Optimal Scheduling for On-Demand Data roadcasts Yiqiong Wu and Guohong Cao Department of Computer Science & Engineering The Pennsylvania State University, University Park, PA 6 E-mail: fywu,gcaog@cse.psu.edu
On Optimal Media/Video Distribution in Closed P2P-Based IPTV Networks
 San Jose State University From the SelectedWorks of Xiao Su February, 2014 On Optimal Media/Video Distribution in Closed P2P-Based IPTV Networks Hao Cui, Santa Clara University Xiao Su, San Jose State
San Jose State University From the SelectedWorks of Xiao Su February, 2014 On Optimal Media/Video Distribution in Closed P2P-Based IPTV Networks Hao Cui, Santa Clara University Xiao Su, San Jose State
PRIME: Peer-to-Peer Receiver-drIven MEsh-based Streaming
 1 PRIME: Peer-to-Peer Receiver-drIven MEsh-based Streaming Nazanin Magharei, Reza Rejaie Department of Computer and Information Science University of Oregon {nazanin,reza}@cs.uoregon.edu Abstract The success
1 PRIME: Peer-to-Peer Receiver-drIven MEsh-based Streaming Nazanin Magharei, Reza Rejaie Department of Computer and Information Science University of Oregon {nazanin,reza}@cs.uoregon.edu Abstract The success
On Veracious Search In Unsystematic Networks
 On Veracious Search In Unsystematic Networks K.Thushara #1, P.Venkata Narayana#2 #1 Student Of M.Tech(S.E) And Department Of Computer Science And Engineering, # 2 Department Of Computer Science And Engineering,
On Veracious Search In Unsystematic Networks K.Thushara #1, P.Venkata Narayana#2 #1 Student Of M.Tech(S.E) And Department Of Computer Science And Engineering, # 2 Department Of Computer Science And Engineering,
NKN is a new kind of network connectivity protocol & ecosystem powered by blockchain for an open, decentralized, and shared Internet.
 A NEW KIND OF NETWORK NKN is a new kind of network connectivity protocol & ecosystem powered by blockchain for an open, decentralized, and shared Internet. W H Y Shortcomings of today s Internet The Missing
A NEW KIND OF NETWORK NKN is a new kind of network connectivity protocol & ecosystem powered by blockchain for an open, decentralized, and shared Internet. W H Y Shortcomings of today s Internet The Missing
Issues of Long-Hop and Short-Hop Routing in Mobile Ad Hoc Networks: A Comprehensive Study
 Issues of Long-Hop and Short-Hop Routing in Mobile Ad Hoc Networks: A Comprehensive Study M. Tarique, A. Hossain, R. Islam and C. Akram Hossain Dept. of Electrical and Electronic Engineering, American
Issues of Long-Hop and Short-Hop Routing in Mobile Ad Hoc Networks: A Comprehensive Study M. Tarique, A. Hossain, R. Islam and C. Akram Hossain Dept. of Electrical and Electronic Engineering, American
arxiv: v3 [cs.ni] 3 May 2017
![arxiv: v3 [cs.ni] 3 May 2017 arxiv: v3 [cs.ni] 3 May 2017](/thumbs/80/80871209.jpg) Modeling Request Patterns in VoD Services with Recommendation Systems Samarth Gupta and Sharayu Moharir arxiv:1609.02391v3 [cs.ni] 3 May 2017 Department of Electrical Engineering, Indian Institute of Technology
Modeling Request Patterns in VoD Services with Recommendation Systems Samarth Gupta and Sharayu Moharir arxiv:1609.02391v3 [cs.ni] 3 May 2017 Department of Electrical Engineering, Indian Institute of Technology
Doctoral Written Exam in Networking, Fall 2008
 Doctoral Written Exam in Networking, Fall 2008 December 5, 2008 Answer all parts of all questions. There are four multi-part questions, each of equal weight. Turn in your answers by Thursday, December
Doctoral Written Exam in Networking, Fall 2008 December 5, 2008 Answer all parts of all questions. There are four multi-part questions, each of equal weight. Turn in your answers by Thursday, December
CHAPTER 5 ANT-FUZZY META HEURISTIC GENETIC SENSOR NETWORK SYSTEM FOR MULTI - SINK AGGREGATED DATA TRANSMISSION
 CHAPTER 5 ANT-FUZZY META HEURISTIC GENETIC SENSOR NETWORK SYSTEM FOR MULTI - SINK AGGREGATED DATA TRANSMISSION 5.1 INTRODUCTION Generally, deployment of Wireless Sensor Network (WSN) is based on a many
CHAPTER 5 ANT-FUZZY META HEURISTIC GENETIC SENSOR NETWORK SYSTEM FOR MULTI - SINK AGGREGATED DATA TRANSMISSION 5.1 INTRODUCTION Generally, deployment of Wireless Sensor Network (WSN) is based on a many
Understanding Pull-based Method Efficiency in Peer-to-Peer Live Video Streaming over Mesh Networks
 J. Basic. Appl. Sci. Res., 2(11)11626-11643, 2012 2012, TextRoad Publication ISSN 2090-4304 Journal of Basic and Applied Scientific Research www.textroad.com Understanding Pull-based Method Efficiency
J. Basic. Appl. Sci. Res., 2(11)11626-11643, 2012 2012, TextRoad Publication ISSN 2090-4304 Journal of Basic and Applied Scientific Research www.textroad.com Understanding Pull-based Method Efficiency
On the Feasibility of Prefetching and Caching for Online TV Services: A Measurement Study on
 See discussions, stats, and author profiles for this publication at: https://www.researchgate.net/publication/220850337 On the Feasibility of Prefetching and Caching for Online TV Services: A Measurement
See discussions, stats, and author profiles for this publication at: https://www.researchgate.net/publication/220850337 On the Feasibility of Prefetching and Caching for Online TV Services: A Measurement
CCP: Conflicts Check Protocol for Bitcoin Block Security 1
 CCP: Conflicts Check Protocol for Bitcoin Block Security Chen Yang Peking University, China yc900@pku.edu.cn Abstract In this work, we present our early stage results on a Conflicts Check Protocol (CCP)
CCP: Conflicts Check Protocol for Bitcoin Block Security Chen Yang Peking University, China yc900@pku.edu.cn Abstract In this work, we present our early stage results on a Conflicts Check Protocol (CCP)
Understanding Mesh-based Peer-to-Peer Streaming
 Understanding Mesh-based Peer-to-Peer Streaming Nazanin Magharei, Reza Rejaie Department of Computer and Information Science University of Oregon {nazanin,reza}@cs.uoregon.edu ABSTRACT A common approach
Understanding Mesh-based Peer-to-Peer Streaming Nazanin Magharei, Reza Rejaie Department of Computer and Information Science University of Oregon {nazanin,reza}@cs.uoregon.edu ABSTRACT A common approach
