Cisco Network Visibility Flow Protocol Specification
|
|
|
- Godwin Burke
- 5 years ago
- Views:
Transcription
1 Cisco Network Visibility low Protocol Specification This document contains the protocol specification for the Cisco Network Visibility low (nvzlow for short). This document is property of Cisco Systems, Inc. and is shared under NDA
2 Table of Contents Introduction... 3 Design Goals... 3 Cisco Network Visibility low (nvzlow) Information Elements... 4 Endpoint Exporter IPIX / nvzlow Templates... 6 Endpoint Identity Template (ID 262)... 6 Interface Info Template (ID 265)... 6 IPv4 Per-low Data Template (ID 263)... 7 IPv6 Per-low Data Template (ID 264)... 8 Data Model and Correlation IDs... 9 Implementation Considerations uture Considerations References... 11
3 Introduction This document defines the new IPIX Informational Elements that Cisco Network Visibility low (nvzlow) adds to IPIX (RC ). These data types carry information that is useful for providing better visibility of the endpoint in a network. The new information elements are defined using the abstract data types defined by IPIX (RC 7012, Section 3.1). Design Goals Cisco Network Visibility low, or nvzlow (pronounced: en- vizzy- flow) is designed to provide greater network visibility of endpoints in a lightweight manner. The protocol extends IPIX to include a small set of high- value data in order to convey the following: Mary visited Salesforce.com from an unmanaged Windows laptop using a company approved browser, while she was connected on her local Starbucks Wi- i network. The 5 key visibility categories conveyed by the protocol are: User Device Application Location Destination In order to be included in the protocol, each data element must meet the following requirements: 1. Convey information directly related to the five key visibility categories shown above. 2. Be clear, obvious and of high value to an IT administrator. 3. Is useful to analytics, while not requiring the use of analytics (raw- data value). 4. Easily obtainable information across a wide variety of OS and device types. 5. Lightweight and portable (minimal network, battery or CPU impact; no DPI required; etc.)
4 Cisco Network Visibility low (nvzlow) Information Elements The following table identifies the new Information Elements in the same format as the standard Information Elements defined in All string values shall be encoded in UT- 8. Element IDs below are shown with and without the Enterprise Bit being set. There are 3 templates as part of the nvzlow Protocol: Endpoint ields that are associated with an Endpoint Device, such as OS Name. Interface ields associated with the network interface, such as Adapter Name. low ields associated with the flow itself, such as L4 Bytes Out. Note that some fields will be present in multiple templates for cross correlation purposes. These are mandatory fields, while all others can be either anonymized ( - ) or not sent at all. Element ID with/without enterprise bit Name Data Type Data Type Semantics Description / nvzlowudid octetarray identifier 20 byte Unique ID that identifies the endpoint. Template Member E = Endpoint, I = Interface, = Per low (M) = Mandatory E, I, (M) / nvzlowloggedinuser string default This is logged in user on the device, in E the form Authority\Principle. This is different from username (id: 371), which is user associated with the flow / nvzlowosname string default Name of the operating system. E E.g., Windows, Mac OS X / nvzlowosversion string default Version of the operating system. E E.g., or / nvzlowsystemmanufacturer string default Name of the manufacturer. E E.g., Lenovo / nvzlowsystemtype string default Type of the system. E.g., x86 or x64 E / nvzlowprocessaccount string default Authority\Principle of the process associated with the flow. E.g., ACME\JSmith, <machine>\jsmith / nvzlowparentprocessaccount string default Authority\Principle of the parent of the process associated with the flow. E.g., ACME\JSmith, <machine>\jsmith / nvzlowprocessname string default Name of the process associated with the flow. E.g., firefox.exe / nvzlowprocesshash octetarray default SHA256 hash of the process image on disk associated with the flow / nvzlowparentprocessname string default Name of the parent of process associated with the flow. E.g., explorer.exe / nvzlowparentprocesshash octetarray default SHA256 hash of the process image on disk of the parent process associated with the flow.
5 45112 / nvzlowdnssuffix string default Per- interface DNS suffix configured on the adapter associated with the flow for the endpoint. E.g., cisco.com / nvzlowdestinationhostname string default The QDN (hostname) that resolved to the destination IP on the endpoint. E.g., / nvzlowl4bytecountin unsigned64 totalcounter Total number of incoming bytes on the flow at Layer4 (Transport). [payload only, without L4 headers] / nvzlowl4bytecountout unsigned64 totalcounter Total number of outgoing bytes on the flow at Layer4 (Transport). [payload only, without L4 headers] v2 fields / nvzlowstring string default Generic UT- 8 string info- element for (sent as part of a list) lists / nvzlowloat32 float32 default Generic float32 info- element for lists (sent as part of a list) / nvzlowoctetarray octetarray default Generic octetarray info- element for (sent as part of a list) lists / nvzlowosedition string default The OS Edition, such as Windows 8.1 Enterprise Edition E / nvzlowmodulenamelist basiclist of nvzlowstring / nvzlowmodulehashlist basiclist of nvzlowoctetarray / nvzlowcoordinateslist basiclist of nvzlowloat32 default default default List of 0 or more names of the modules hosted by the process that generated the flow. This can include the main DLLs in common containers such as dllhost, svchost, rundll32, etc. It can also contain other hosted components such as the name of the jar file in a JVM. List of 0 or more SHA256 hashes of the modules associated with the nvzlowmodulenamelist List of 32bit floating point values representing Accuracy, Latitude, Longitude, [Altitude] respectively. Altitude is optional. Coordinate based location information such as GPS, Wi- i Approximation, etc., Accuracy in meters defines the error margin / nvzlowinterfaceinfouid unsigned32 identifier Unique ID for an interface meta- data. Should be used to lookup the interface meta- data from the InterfaceInfo records / nvzlowinterfaceindex unsigned32 default The index of the Network interface as reported by the OS / nvzlowinterfacetype unsigned8 default Interface Type, such as Wired, Wireless, Cellular, VPN, Tunneled, Bluetooth, etc. Enumeration of network types, defined by this spec / nvzlowinterfacename string default Network Interface/Adapter name as reported by the OS / nvzlowinterfacedetailslist basiclist of nvzlowstring default List of name value pair (delimited by =') of other interface attributes of interest. E.g., SSID=internet., I (M) I I I I
6 Endpoint Exporter IPIX / nvzlow Templates An endpoint client exporter, such as Cisco AnyConnect NVM, sends IPIX / Network Visibility low (nvzlow) records based on the following templates. The template section lists the Information Elements in each template. All fields can be anonymized ( - ) or completely absent unless indicated as MANDATORY. There are two revisions of the protocol. Version 2 (additional) elements are marked v2. Endpoint Identity Template (ID 262) The Endpoint Identity Template shall have the following Information Elements. virtualstationname (IPIX standard information element : 350) nvzlowudid (MANDATORY) nvzlowosname nvzlowosversion nvzlowsystemmanufacturer nvzlowsystemtype nvzlowosedition (v2) Interface Info Template (ID 265) Interface Info template records identify each interface instance on the endpoint. Any change in to interface attributes should trigger a new Interface Info record to be sent with corresponding details. Each record (not just an interface) is distinctively identified by a unique ID nvzlowinterfaceinfouid. Each Interface Info record shall have the following information elements: nvzlowudid (MANDATORY) nvzlowinterfaceinfouid (MANDATORY v2) nvzlowinterfaceindex (v2) nvzlowinterfacetype (v2) nvzlowinterfacename (v2) nvzlowinterfacedetailslist (v2) The exporter is expected to send the interface info record with a new UID if any of the attributes changes for an interface or for a new interface. E.g., if the same Wi- i interface connects to a new SSID. The UID is expected to be unique on a given endpoint. InterfaceType has the following values: 1 Wired Ethernet, 2 Wireless (802.11), 3 Bluetooth, 4 Token Ring, 5 ATM (Slip), 6 PPP, 7 Tunnel (generic), 8 VPN, 9 Loopback, 10 NC, 11 Cellular, 15 Unknown/Unspecified
7 IPv4 Per- low Data Template (ID 263) The Per- low Data Template (IPv4) shall have the following Information Elements: protocolidentifier (IPIX standard information element : 4) (MANDATORY) sourceipv4address (IPIX standard information element : 8) (MANDATORY) sourcetransportport (IPIX standard information element : 7) (MANDATORY) destinationipv4address (IPIX standard information element : 12) (MANDATORY) destinationtransportport (IPIX standard information element : 11) (MANDATORY) flowstartseconds (IPIX standard information element : 150) (MANDATORY) flowendseconds (IPIX standard information element : 151) (MANDATORY) nvzlowudid (MANDATORY) nvzlowloggedinuser nvzlowprocessaccount nvzlowprocessname nvzlowprocesshash nvzlowparentprocessaccount nvzlowparentprocessname nvzlowparentprocesshash nvzlowl4bytecountin nvzlowl4bytecountout nvzlowdnssuffix nvzlowdestinationhostname nvzlowinterfaceinfouid (MANDATORY v2) nvzlowmodulenamelist (v2) nvzlowmodulehashlist (v2) nvzlowcoordinateslist (v2)
8 IPv6 Per- low Data Template (ID 264) The Per- low Data Template (IPv6) shall have the following Information Elements. protocolidentifier (IPIX standard information element : 4) (MANDATORY) sourceipv6address (IPIX standard information element : 27) (MANDATORY) sourcetransportport (IPIX standard information element : 7) (MANDATORY) destinationipv6address (IPIX standard information element : 28) (MANDATORY) destinationtransportport (IPIX standard information element : 11) (MANDATORY) flowstartseconds (IPIX standard information element : 150) (MANDATORY) flowendseconds (IPIX standard information element : 151) (MANDATORY) nvzlowudid nvzlowloggedinuser nvzlowprocessaccount nvzlowprocessname nvzlowprocesshash nvzlowparentprocessaccount nvzlowparentprocessname nvzlowparentprocesshash nvzlowl4bytecountin nvzlowl4bytecountout nvzlowdnssuffix nvzlowdestinationhostname nvzlowinterfaceinfouid (MANDATORY v2) nvzlowmodulenamelist (v2) nvzlowmodulehashlist (v2) nvzlowcoordinateslist (v2)
9 Data Model and Correlation IDs The following graphic shows the data model of the nvzlow protocol and how the different correlation IDs are used to associate the different data collections. A collector will likely store 3 sets of data records, one for each collection of data. Analytics and reporting will correlate the 3 sets of data using the UDID as the key across the data sets. Additionally, for interface information, a correlation from the flow record to the interface information record will be done using the Interface UID.
10 Implementation Considerations There are a number of considerations that should be evaluated as part of a solution implementation. Of particular note is data retention and data suppression by an exporter. or example, an exporter should have some means of securely preserving data when it is unable to communicate with the collector (such as when an endpoint is not on the network where the collector is located). Additionally, configurable protocol suppression should be considered for the endpoint exporter. Of particular note is broadcast and multicast traffic as this can be significant. An implementation should allow for the ability to also limit the export of any field that is not marked as mandatory if an administrator so chooses. Anonymization can be done at either the exporter or collector. Note that exporter anonymization would mean that the data will never be recoverable, whereas collector anonymization can preserve the data for forensic needs while still meeting privacy requirements. Exporter anonymization should be done by either excluding the field or sending an empty field with no data or alternatively using an indicative data element, such as ( - ) for a string, to convey it was anonymized. Traffic that is bound to localhost should not be of consideration, unless some local network proxy function, on that endpoint, results in aggregation of flows. or example, a web security proxy running on the endpoint that binds web traffic flows to localhost for redirection to a cloud proxy, might be of interest for a local exporter implementation to consider. Performance impact should be a top consideration. In particular, when collecting and storing data locally or when sending bulk records that were previously stored on an endpoint. An exporter should act as a background service with low CPU and memory utilization. A collector should leverage lightweight hooking technologies and avoid approaches such as packet capture facilities so as to minimize system impact and reduce incompatibilities. Additionally, the exporter should throttle sending of cached records so as to not impact the normal network operation of a device. Caching limits should also be used to minimize impact on an endpoint device in terms of both storage and battery consumption. uture Considerations There are a number of future considerations for the nvzlow protocol. The following are some possible items that will be considered in the near future: Compressed IPIX records Because the nvzlow data set could exceed a single UDP packet, a future implementation might specify a template containing a single element that encapsulates a normal nvzlow flow record in a compressed payload. A collector would first identify the record as containing the single type nvzlowcompressedrecord and then expand that single payload into one of the nvzlow template payloads described above. IPIX over DTLS Endpoints may be in places in the network where integrity, authenticity and privacy are a concern. As such, it is recommended that an exporter and collector support sending and receiving nvzlow IPIX records over DTLS (with the ability to fallback to TLS when DTLS is not possible due to network, firewall or proxy restrictions).
11 Additional Exporter ormats In addition to IPIX, additional formats may be added, such as binary- JSON over HTTPs, to allow for a broader ecosystem of collector technologies. References 1. IP low Information Export (IPIX) Entities [ 2. Specification of the IP low Information Export (IPIX) Protocol for the Exchange of low Information [ 3. Information Model for IP low Information Export (IPIX) [ 4. Exporting Type Information for IP low Information Export (IPIX) Information Elements [ End of document - - -
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
Cisco Stealthwatch Endpoint License with Cisco AnyConnect NVM
 Cisco Stealthwatch Endpoint License with Cisco AnyConnect NVM How to implement the Cisco Stealthwatch Endpoint License with the Cisco AnyConnect Network Visibility Module Table of Contents About This Document...
Cisco Stealthwatch Endpoint License with Cisco AnyConnect NVM How to implement the Cisco Stealthwatch Endpoint License with the Cisco AnyConnect Network Visibility Module Table of Contents About This Document...
Using Access Point Communication Protocols
 Information About Access Point Communication Protocols, page 1 Restrictions for Access Point Communication Protocols, page 2 Configuring Data Encryption, page 2 Viewing CAPWAP Maximum Transmission Unit
Information About Access Point Communication Protocols, page 1 Restrictions for Access Point Communication Protocols, page 2 Configuring Data Encryption, page 2 Viewing CAPWAP Maximum Transmission Unit
Configuring Application Visibility and Control for Cisco Flexible Netflow
 Configuring Application Visibility and Control for Cisco Flexible Netflow First published: July 22, 2011 This guide contains information about the Cisco Application Visibility and Control feature. It also
Configuring Application Visibility and Control for Cisco Flexible Netflow First published: July 22, 2011 This guide contains information about the Cisco Application Visibility and Control feature. It also
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide
 Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
IP - The Internet Protocol. Based on the slides of Dr. Jorg Liebeherr, University of Virginia
 IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
L2 Bridging Across an L3 Network Configuration Example
 L2 Bridging Across an L3 Network Configuration Example Document ID: 116266 Contributed by Atri Basu, Jay Young Taylor, and Mani Ganesan, Cisco TAC Engineers. Jul 09, 2013 Contents Introduction Prerequisites
L2 Bridging Across an L3 Network Configuration Example Document ID: 116266 Contributed by Atri Basu, Jay Young Taylor, and Mani Ganesan, Cisco TAC Engineers. Jul 09, 2013 Contents Introduction Prerequisites
Setup for Cisco Unified Communications Manager
 Setup for Cisco Unified Communications Manager This chapter describes how you can set up Cisco Jabber for ipad using Cisco Unified Communications Manager. System and Network Requirements, page 1 Recommended
Setup for Cisco Unified Communications Manager This chapter describes how you can set up Cisco Jabber for ipad using Cisco Unified Communications Manager. System and Network Requirements, page 1 Recommended
Computer Networking: A Top Down Approach Featuring the. Computer Networks with Internet Technology, William
 Dr. John Keeney 3BA33 TCP/IP protocol architecture with IP OSI Model Layers TCP/IP Protocol Architecture Layers TCP/IP Protocol Suite Application Layer Application Layer Telnet FTP HTTP DNS RIPng SNMP
Dr. John Keeney 3BA33 TCP/IP protocol architecture with IP OSI Model Layers TCP/IP Protocol Architecture Layers TCP/IP Protocol Suite Application Layer Application Layer Telnet FTP HTTP DNS RIPng SNMP
Data Sheet. NCP Secure Entry Mac Client. Next Generation Network Access Technology
 Universal VPN Client Suite for macos/os X Compatible with VPN Gateways (IPsec Standard) macos 10.13, 10.12, OS X 10.11, OS X 10.10 Import of third party configuration files Integrated, dynamic Personal
Universal VPN Client Suite for macos/os X Compatible with VPN Gateways (IPsec Standard) macos 10.13, 10.12, OS X 10.11, OS X 10.10 Import of third party configuration files Integrated, dynamic Personal
Fundamental Issues. System Models and Networking Chapter 2,3. System Models. Architectural Model. Middleware. Bina Ramamurthy
 System Models and Networking Chapter 2,3 Bina Ramamurthy Fundamental Issues There is no global time. All communications are by means of messages. Message communication may be affected by network delays
System Models and Networking Chapter 2,3 Bina Ramamurthy Fundamental Issues There is no global time. All communications are by means of messages. Message communication may be affected by network delays
Remote Access VPN. Remote Access VPN Overview. Licensing Requirements for Remote Access VPN
 Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
AT&T SD-WAN Network Based service quick start guide
 AT&T SD-WAN Network Based service quick start guide After you order your AT&T SD-WAN Network Based service, you can: Create administrator accounts Log in to the SD-WAN orchestrator Configure business policy
AT&T SD-WAN Network Based service quick start guide After you order your AT&T SD-WAN Network Based service, you can: Create administrator accounts Log in to the SD-WAN orchestrator Configure business policy
ExamTorrent. Best exam torrent, excellent test torrent, valid exam dumps are here waiting for you
 ExamTorrent http://www.examtorrent.com Best exam torrent, excellent test torrent, valid exam dumps are here waiting for you Exam : 400-251 Title : CCIE Security Written Exam (v5.0) Vendor : Cisco Version
ExamTorrent http://www.examtorrent.com Best exam torrent, excellent test torrent, valid exam dumps are here waiting for you Exam : 400-251 Title : CCIE Security Written Exam (v5.0) Vendor : Cisco Version
Yes, You can protect your endpoints! Szilard Csordas, Security Consultant scsordas [at] cisco.com
![Yes, You can protect your endpoints! Szilard Csordas, Security Consultant scsordas [at] cisco.com Yes, You can protect your endpoints! Szilard Csordas, Security Consultant scsordas [at] cisco.com](/thumbs/88/115377705.jpg) Yes, You can protect your endpoints! Szilard Csordas, Security Consultant scsordas [at] cisco.com Endpoint Footprint Problem: TOO MANY AGENTS! Anti-Virus/Anti-Spyware agent IPSec/SSLVPN agent Host IPS/FW
Yes, You can protect your endpoints! Szilard Csordas, Security Consultant scsordas [at] cisco.com Endpoint Footprint Problem: TOO MANY AGENTS! Anti-Virus/Anti-Spyware agent IPSec/SSLVPN agent Host IPS/FW
Split DNS. Finding Feature Information
 The feature enables a Cisco device to respond to Domain Name System (DNS) queries using a specific configuration and associated host table cache that are selected based on certain characteristics of the
The feature enables a Cisco device to respond to Domain Name System (DNS) queries using a specific configuration and associated host table cache that are selected based on certain characteristics of the
Ethernet over GRE Tunnels
 The feature allows customers to leverage existing low end residential gateways to provide mobility services to mobile nodes using Proxy Mobile IPv6 (PMIPv6), General Packet Radio Service (GPRS) Tunneling
The feature allows customers to leverage existing low end residential gateways to provide mobility services to mobile nodes using Proxy Mobile IPv6 (PMIPv6), General Packet Radio Service (GPRS) Tunneling
Release Notes. NCP Secure Enterprise Mac Client. 1. New Features and Enhancements. 2. Improvements / Problems Resolved. 3.
 NCP Secure Enterprise Mac Client Service Release 2.05 Build 14711 Date: December 2013 Prerequisites Apple OS X Operating System: The following Apple OS X operating system versions are supported with this
NCP Secure Enterprise Mac Client Service Release 2.05 Build 14711 Date: December 2013 Prerequisites Apple OS X Operating System: The following Apple OS X operating system versions are supported with this
MTA_98-366_Vindicator930
 MTA_98-366_Vindicator930 Number: 98-366 Passing Score: 700 Time Limit: 45 min File Version: 1.0 http://www.gratisexam.com/ Microsoft Technology Associate Networking Fundamentals MTA 98-366 Exam A QUESTION
MTA_98-366_Vindicator930 Number: 98-366 Passing Score: 700 Time Limit: 45 min File Version: 1.0 http://www.gratisexam.com/ Microsoft Technology Associate Networking Fundamentals MTA 98-366 Exam A QUESTION
Split DNS. Finding Feature Information
 The feature enables a Cisco device to respond to Domain Name System (DNS) queries using a specific configuration and associated host table cache that are selected based on certain characteristics of the
The feature enables a Cisco device to respond to Domain Name System (DNS) queries using a specific configuration and associated host table cache that are selected based on certain characteristics of the
Network Working Group. Category: Informational Fraunhofer FOKUS J. Quittek M. Stiemerling NEC P. Aitken Cisco Systems, Inc.
 Network Working Group Request for Comments: 5153 Category: Informational E. Boschi Hitachi Europe L. Mark Fraunhofer FOKUS J. Quittek M. Stiemerling NEC P. Aitken Cisco Systems, Inc. April 2008 IP Flow
Network Working Group Request for Comments: 5153 Category: Informational E. Boschi Hitachi Europe L. Mark Fraunhofer FOKUS J. Quittek M. Stiemerling NEC P. Aitken Cisco Systems, Inc. April 2008 IP Flow
Application Note. Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder )
 Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Network Security. Thierry Sans
 Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
CSC 4900 Computer Networks: Security Protocols (2)
 CSC 4900 Computer Networks: Security Protocols (2) Professor Henry Carter Fall 2017 Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Message Integrity 8.4 End point Authentication
CSC 4900 Computer Networks: Security Protocols (2) Professor Henry Carter Fall 2017 Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Message Integrity 8.4 End point Authentication
Chapter Motivation For Internetworking
 Chapter 17-20 Internetworking Part 1 (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution 1 Motivation For Internetworking LANs Low cost Limited distance WANs High cost Unlimited distance
Chapter 17-20 Internetworking Part 1 (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution 1 Motivation For Internetworking LANs Low cost Limited distance WANs High cost Unlimited distance
Internet Engineering Task Force (IETF) Request for Comments: November 2012
 Internet Engineering Task Force (IETF) Request for Comments: 6759 Category: Informational ISSN: 2070-1721 B. Claise P. Aitken N. Ben-Dvora Cisco Systems, Inc. November 2012 Cisco Systems Export of Application
Internet Engineering Task Force (IETF) Request for Comments: 6759 Category: Informational ISSN: 2070-1721 B. Claise P. Aitken N. Ben-Dvora Cisco Systems, Inc. November 2012 Cisco Systems Export of Application
Examination 2D1392 Protocols and Principles of the Internet 2G1305 Internetworking 2G1507 Kommunikationssystem, fk SOLUTIONS
 Examination 2D1392 Protocols and Principles of the Internet 2G1305 Internetworking 2G1507 Kommunikationssystem, fk Date: January 17 th 2006 at 14:00 18:00 SOLUTIONS 1. General (5p) a) Draw the layered
Examination 2D1392 Protocols and Principles of the Internet 2G1305 Internetworking 2G1507 Kommunikationssystem, fk Date: January 17 th 2006 at 14:00 18:00 SOLUTIONS 1. General (5p) a) Draw the layered
Release Notes. NCP Secure Enterprise Mac Client. 1. New Features and Enhancements. 2. Improvements / Problems Resolved. 3.
 NCP Secure Enterprise Mac Client Service Release 2.05 Rev. 32317 Date: January 2017 Prerequisites Apple OS X Operating System: The following Apple OS X operating system versions are supported with this
NCP Secure Enterprise Mac Client Service Release 2.05 Rev. 32317 Date: January 2017 Prerequisites Apple OS X Operating System: The following Apple OS X operating system versions are supported with this
Stonesoft Management Center. Release Notes Revision A
 Stonesoft Management Center Release Notes 6.1.3 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5 Enhancements
Stonesoft Management Center Release Notes 6.1.3 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5 Enhancements
This version of the des Secure Enterprise MAC Client can be used on Mac OS X 10.7 Lion platform.
 NCP Secure Enterprise MAC Client Service Release 2.02 Build 11 Date: August 2011 1. New Feature Compatibility to Mac OS X 10.7 Lion This version of the des Secure Enterprise MAC Client can be used on Mac
NCP Secure Enterprise MAC Client Service Release 2.02 Build 11 Date: August 2011 1. New Feature Compatibility to Mac OS X 10.7 Lion This version of the des Secure Enterprise MAC Client can be used on Mac
IP Multicast Traffic Measurement Method with IPFIX/PSAMP. Atsushi Kobayashi Yutaka Hirokawa Haruhiko Nishida NTT
 IP Multicast Traffic Measurement Method with /PSAMP Atsushi Kobayashi Yutaka Hirokawa Haruhiko Nishida NTT 1 Outline Introduction Motivation Requirements Main requirements for measurement system in largescale
IP Multicast Traffic Measurement Method with /PSAMP Atsushi Kobayashi Yutaka Hirokawa Haruhiko Nishida NTT 1 Outline Introduction Motivation Requirements Main requirements for measurement system in largescale
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
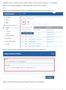 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
INTERNET PROTOCOL SECURITY (IPSEC) GUIDE.
 INTERNET PROTOCOL SECURITY (IPSEC) GUIDE www.insidesecure.com INTRODUCING IPSEC NETWORK LAYER PACKET SECURITY With the explosive growth of the Internet, more and more enterprises are looking towards building
INTERNET PROTOCOL SECURITY (IPSEC) GUIDE www.insidesecure.com INTRODUCING IPSEC NETWORK LAYER PACKET SECURITY With the explosive growth of the Internet, more and more enterprises are looking towards building
YAF(1) Yet Another Flowmeter YAF(1)
 NAME yaf Yet Another Flowmeter SYNOPSIS yaf [--in INPUT_SPECIFIER] [--out OUTPUT_SPECIFIER] [--live LIVE_TYPE] [--ipfix TRANSPORT_PROTOCOL] [--rotate ROTATE_DELAY ] [--lock] [--caplist] [--noerror] [--dag-interface]
NAME yaf Yet Another Flowmeter SYNOPSIS yaf [--in INPUT_SPECIFIER] [--out OUTPUT_SPECIFIER] [--live LIVE_TYPE] [--ipfix TRANSPORT_PROTOCOL] [--rotate ROTATE_DELAY ] [--lock] [--caplist] [--noerror] [--dag-interface]
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
PART X. Internetworking Part 1. (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution)
 PART X Internetworking Part 1 (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution) CS422 Part 10 1 Spring 1999 Motivation For Internetworking LANs Low cost Limited distance WANs High
PART X Internetworking Part 1 (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution) CS422 Part 10 1 Spring 1999 Motivation For Internetworking LANs Low cost Limited distance WANs High
Configuring Web Cache Services By Using WCCP
 CHAPTER 44 Configuring Web Cache Services By Using WCCP This chapter describes how to configure your Catalyst 3560 switch to redirect traffic to wide-area application engines (such as the Cisco Cache Engine
CHAPTER 44 Configuring Web Cache Services By Using WCCP This chapter describes how to configure your Catalyst 3560 switch to redirect traffic to wide-area application engines (such as the Cisco Cache Engine
What s New for Enterprise and Education ios 11, macos High Sierra 10.13, tvos 11, and deployment tools and services
 What s New for Enterprise and Education ios 11, macos High Sierra 10.13, tvos 11, and deployment tools and services September 2017 Introduction This document is a summary of what s new in ios 11, macos
What s New for Enterprise and Education ios 11, macos High Sierra 10.13, tvos 11, and deployment tools and services September 2017 Introduction This document is a summary of what s new in ios 11, macos
Deployment of Cisco IP Mobility Solution on Enterprise Class Teleworker Network
 Deployment Guide Deployment of Cisco IP Mobility Solution on Enterprise Class Teleworker Network The Cisco Service Oriented Network Architecture (SONA) framework helps enterprise customers evolve their
Deployment Guide Deployment of Cisco IP Mobility Solution on Enterprise Class Teleworker Network The Cisco Service Oriented Network Architecture (SONA) framework helps enterprise customers evolve their
CertKiller q
 CertKiller.500-451.28q Number: 500-451 Passing Score: 800 Time Limit: 120 min File Version: 5.3 500-451 Cisco Unified Access Systems Engineer Exam I just passed today with 89%. My sole focus was the VCE.
CertKiller.500-451.28q Number: 500-451 Passing Score: 800 Time Limit: 120 min File Version: 5.3 500-451 Cisco Unified Access Systems Engineer Exam I just passed today with 89%. My sole focus was the VCE.
CSE 461 MIDTERM REVIEW
 CSE 461 MIDTERM REVIEW NETWORK LAYERS & ENCAPSULATION Application Application Transport Transport Network Network Data Link/ Physical Data Link/ Physical APPLICATION LAYER Application Application Used
CSE 461 MIDTERM REVIEW NETWORK LAYERS & ENCAPSULATION Application Application Transport Transport Network Network Data Link/ Physical Data Link/ Physical APPLICATION LAYER Application Application Used
ForeScout CounterACT. Controller Plugin. Configuration Guide. Version 1.0
 ForeScout CounterACT Network Module: Centralized Network Controller Plugin Version 1.0 Table of Contents About the Centralized Network Controller Integration... 4 About This Plugin... 4 How It Works...
ForeScout CounterACT Network Module: Centralized Network Controller Plugin Version 1.0 Table of Contents About the Centralized Network Controller Integration... 4 About This Plugin... 4 How It Works...
Transport Level Security
 2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
ICS 351: Networking Protocols
 ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
L2TP IPsec Support for NAT and PAT Windows Clients
 L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
Communication in Distributed Systems
 Communication in Distributed Systems Sape J. Mullender Huygens Systems Research Laboratory Universiteit Twente Enschede 1 Introduction Functions of Communication Transport data between processes, machines,
Communication in Distributed Systems Sape J. Mullender Huygens Systems Research Laboratory Universiteit Twente Enschede 1 Introduction Functions of Communication Transport data between processes, machines,
Enhancing VMware Horizon View with F5 Solutions
 Enhancing VMware Horizon View with F5 Solutions VMware Horizon View is the leading virtualization solution for delivering desktops as a managed service to a wide range of devices. F5 BIG-IP devices optimize
Enhancing VMware Horizon View with F5 Solutions VMware Horizon View is the leading virtualization solution for delivering desktops as a managed service to a wide range of devices. F5 BIG-IP devices optimize
IPSec. Overview. Overview. Levente Buttyán
 IPSec - brief overview - security associations (SAs) - Authentication Header (AH) protocol - Encapsulated Security Payload () protocol - combining SAs (examples) Overview Overview IPSec is an Internet
IPSec - brief overview - security associations (SAs) - Authentication Header (AH) protocol - Encapsulated Security Payload () protocol - combining SAs (examples) Overview Overview IPSec is an Internet
Operating Systems. 16. Networking. Paul Krzyzanowski. Rutgers University. Spring /6/ Paul Krzyzanowski
 Operating Systems 16. Networking Paul Krzyzanowski Rutgers University Spring 2015 1 Local Area Network (LAN) LAN = communications network Small area (building, set of buildings) Same, sometimes shared,
Operating Systems 16. Networking Paul Krzyzanowski Rutgers University Spring 2015 1 Local Area Network (LAN) LAN = communications network Small area (building, set of buildings) Same, sometimes shared,
VXLAN Overview: Cisco Nexus 9000 Series Switches
 White Paper VXLAN Overview: Cisco Nexus 9000 Series Switches What You Will Learn Traditional network segmentation has been provided by VLANs that are standardized under the IEEE 802.1Q group. VLANs provide
White Paper VXLAN Overview: Cisco Nexus 9000 Series Switches What You Will Learn Traditional network segmentation has been provided by VLANs that are standardized under the IEEE 802.1Q group. VLANs provide
Configuring AVC to Monitor MACE Metrics
 This feature is designed to analyze and measure network traffic for WAAS Express. Application Visibility and Control (AVC) provides visibility for various applications and the network to central network
This feature is designed to analyze and measure network traffic for WAAS Express. Application Visibility and Control (AVC) provides visibility for various applications and the network to central network
Cisco CP Express Wizard
 CHAPTER1 These help topics introduce Cisco Configuration Professional Express (Cisco CP Express) wizard, describe the configurations you can perform with it, and explain the information required in each
CHAPTER1 These help topics introduce Cisco Configuration Professional Express (Cisco CP Express) wizard, describe the configurations you can perform with it, and explain the information required in each
Terminal Services Commands translate lat
 translate lat translate lat To translate a connection request to another protocol connection type when receiving a local-area transport (LAT) request, use the translate lat command in global configuration
translate lat translate lat To translate a connection request to another protocol connection type when receiving a local-area transport (LAT) request, use the translate lat command in global configuration
Internet Engineering Task Force (IETF) Request for Comments: TU Muenchen K. Ishibashi NTT. April 2011
 Internet Engineering Task Force (IETF) Request for Comments: 6183 Updates: 5470 Category: Informational ISSN: 2070-1721 A. Kobayashi NTT B. Claise Cisco Systems, Inc. G. Muenz TU Muenchen K. Ishibashi
Internet Engineering Task Force (IETF) Request for Comments: 6183 Updates: 5470 Category: Informational ISSN: 2070-1721 A. Kobayashi NTT B. Claise Cisco Systems, Inc. G. Muenz TU Muenchen K. Ishibashi
Pulse Desktop Client. Release Notes PDC 5.3R1.1 Build 755. Release, Build Published Document Version. 5.3R1.1, 755 May,
 Pulse Desktop Client Release Notes PDC 5.3R1.1 Build 755 Release, Build Published Document Version 5.3R1.1, 755 May, 2017 2.0 Contents Introduction... 3 Interoperability and Supported Platforms... 3 General
Pulse Desktop Client Release Notes PDC 5.3R1.1 Build 755 Release, Build Published Document Version 5.3R1.1, 755 May, 2017 2.0 Contents Introduction... 3 Interoperability and Supported Platforms... 3 General
Cisco CCIE Security Written.
 Cisco 400-251 CCIE Security Written http://killexams.com/pass4sure/exam-detail/400-251 QUESTION: 193 Which two of the following ICMP types and code should be allowed in a firewall to enable traceroute?
Cisco 400-251 CCIE Security Written http://killexams.com/pass4sure/exam-detail/400-251 QUESTION: 193 Which two of the following ICMP types and code should be allowed in a firewall to enable traceroute?
Addressing and Routing
 Addressing and Routing Andrew Scott a.scott@lancaster.ac.uk Physical/ Hardware Addresses Aka MAC* or link(-layer) address Can only talk to things on same link Unique ID given to every network interface
Addressing and Routing Andrew Scott a.scott@lancaster.ac.uk Physical/ Hardware Addresses Aka MAC* or link(-layer) address Can only talk to things on same link Unique ID given to every network interface
CIS Controls Measures and Metrics for Version 7
 Level One Level Two Level Three Level Four Level Five Level Six 1.1 Utilize an Active Discovery Tool Utilize an active discovery tool to identify devices connected to the organization's network and update
Level One Level Two Level Three Level Four Level Five Level Six 1.1 Utilize an Active Discovery Tool Utilize an active discovery tool to identify devices connected to the organization's network and update
Client Data Tunneling
 Ethernet over GRE Tunnels, on page 1 Proxy Mobile IPv6, on page 9 Ethernet over GRE Tunnels Ethernet over GRE (EoGRE) is a new aggregation solution for aggregating Wi-Fi traffic from hotspots. This solution
Ethernet over GRE Tunnels, on page 1 Proxy Mobile IPv6, on page 9 Ethernet over GRE Tunnels Ethernet over GRE (EoGRE) is a new aggregation solution for aggregating Wi-Fi traffic from hotspots. This solution
High Availability Synchronization PAN-OS 5.0.3
 High Availability Synchronization PAN-OS 5.0.3 Revision B 2013, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Device Configuration... 4 Network Configuration... 9 Objects Configuration...
High Availability Synchronization PAN-OS 5.0.3 Revision B 2013, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Device Configuration... 4 Network Configuration... 9 Objects Configuration...
Intercepting Web Requests
 This chapter contains the following sections: Overview of, on page 1 Tasks for, on page 1 Best Practices for, on page 2 Web Proxy Options for, on page 3 Client Options for Redirecting Web Requests, on
This chapter contains the following sections: Overview of, on page 1 Tasks for, on page 1 Best Practices for, on page 2 Web Proxy Options for, on page 3 Client Options for Redirecting Web Requests, on
Implementing IP in IP Tunnel
 This chapter module provides conceptual and configuration information for IP in IP tunnels on Cisco ASR 9000 Series Router. Note For a complete description of the IP in IP tunnel commands listed in this
This chapter module provides conceptual and configuration information for IP in IP tunnels on Cisco ASR 9000 Series Router. Note For a complete description of the IP in IP tunnel commands listed in this
1. Ultimate Powerful VPN Connectivity
 1.1. Firewall, Proxy and NAT Transparency One of the key features of SoftEther VPN is the transparency for firewalls, proxy servers and NATs (Network Address Translators). NATs are sometimes implemented
1.1. Firewall, Proxy and NAT Transparency One of the key features of SoftEther VPN is the transparency for firewalls, proxy servers and NATs (Network Address Translators). NATs are sometimes implemented
CIS Controls Measures and Metrics for Version 7
 Level 1.1 Utilize an Active Discovery Tool 1.2 Use a Passive Asset Discovery Tool 1.3 Use DHCP Logging to Update Asset Inventory 1.4 Maintain Detailed Asset Inventory 1.5 Maintain Asset Inventory Information
Level 1.1 Utilize an Active Discovery Tool 1.2 Use a Passive Asset Discovery Tool 1.3 Use DHCP Logging to Update Asset Inventory 1.4 Maintain Detailed Asset Inventory 1.5 Maintain Asset Inventory Information
The StrideLinx Remote Access Solution comprises the StrideLinx router, web-based platform, and VPN client.
 Introduction: Intended Audience The StrideLinx Remote Access Solution is designed to offer safe and secure remote access to industrial equipment worldwide for efficient remote troubleshooting, programming
Introduction: Intended Audience The StrideLinx Remote Access Solution is designed to offer safe and secure remote access to industrial equipment worldwide for efficient remote troubleshooting, programming
Troubleshooting Web Authentication on a Wireless LAN Controller (WLC)
 Troubleshooting Web Authentication on a Wireless LAN Controller (WLC) Document ID: 108501 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Web Authentication
Troubleshooting Web Authentication on a Wireless LAN Controller (WLC) Document ID: 108501 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Web Authentication
Contents. Introduction. Prerequisites. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram ASA ISE Step 1. Configure Network Device Step 2. Configure Posture conditions and policies Step 3. Configure Client
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram ASA ISE Step 1. Configure Network Device Step 2. Configure Posture conditions and policies Step 3. Configure Client
Contents. Introduction
 Contents Introduction Prerequisites Requirements Components Used Background Information Cisco Anyconnect Secure Mobility Client Internet Protocol Flow Information Export (IPFIX) IPFIX Collector Splunk
Contents Introduction Prerequisites Requirements Components Used Background Information Cisco Anyconnect Secure Mobility Client Internet Protocol Flow Information Export (IPFIX) IPFIX Collector Splunk
WCCPv2 and WCCP Enhancements
 WCCPv2 and WCCP Enhancements Release 12.0(11)S June 20, 2000 This feature module describes the Web Cache Communication Protocol (WCCP) Enhancements feature and includes information on the benefits of the
WCCPv2 and WCCP Enhancements Release 12.0(11)S June 20, 2000 This feature module describes the Web Cache Communication Protocol (WCCP) Enhancements feature and includes information on the benefits of the
CCNA Questions/Answers IPv6. Select the valid IPv6 address from given ones. (Choose two) A. FE63::0043::11:21 B :2:11.1 C.
 Select the valid IPv6 address from given ones. (Choose two) A. FE63::0043::11:21 B. 191.2.1.2:2:11.1 C. 2001::98 D. 2002:c0a8:101::42 E. :2001:: F. 2002.cb0a:3cdd:1::1 Answer: C, D. 2013 1 Which method
Select the valid IPv6 address from given ones. (Choose two) A. FE63::0043::11:21 B. 191.2.1.2:2:11.1 C. 2001::98 D. 2002:c0a8:101::42 E. :2001:: F. 2002.cb0a:3cdd:1::1 Answer: C, D. 2013 1 Which method
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
OCF Specification Overview Core Technology Specification. OCF 2.0 Release June 2018
 OCF Specification Overview Core Technology Specification OCF 2.0 Release June 2018 Core Framework Topics Outline (1 of 2) Objectives RESTful Architecture OCF Roles Resources Basic Operations Organization
OCF Specification Overview Core Technology Specification OCF 2.0 Release June 2018 Core Framework Topics Outline (1 of 2) Objectives RESTful Architecture OCF Roles Resources Basic Operations Organization
Inspirel. YAMI4 Requirements. For YAMI4Industry, v page 1
 YAMI4 Requirements For YAMI4Industry, v.1.3.1 www.inspirel.com info@inspirel.com page 1 Table of Contents Document scope...3 Architectural elements...3 Serializer...3 Socket...3 Input buffer...4 Output
YAMI4 Requirements For YAMI4Industry, v.1.3.1 www.inspirel.com info@inspirel.com page 1 Table of Contents Document scope...3 Architectural elements...3 Serializer...3 Socket...3 Input buffer...4 Output
Port Mirroring in CounterACT. CounterACT Technical Note
 Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Digital forensics Technical Fundamentals. Saurabh Singh
 Digital forensics Technical Fundamentals Saurabh Singh 159744151 saurabhgcet1989@gmail.com Topics Source of network based evidence Principles of internetworking Internet protocol Suite conclusion Source
Digital forensics Technical Fundamentals Saurabh Singh 159744151 saurabhgcet1989@gmail.com Topics Source of network based evidence Principles of internetworking Internet protocol Suite conclusion Source
2011 Cisco and/or its affiliates. All rights reserved. Cisco Public 1
 2011 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 Cisco AnyConnect as a Service György Ács Regional Security Consultant Mobile User Challenges Mobile and Security Services Web Security
2011 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 Cisco AnyConnect as a Service György Ács Regional Security Consultant Mobile User Challenges Mobile and Security Services Web Security
QoS: Classification, Policing, and Marking on LAC Configuration Guide, Cisco IOS Release 12.4T
 QoS: Classification, Policing, and Marking on LAC Configuration Guide, Cisco IOS Release 12.4T Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
QoS: Classification, Policing, and Marking on LAC Configuration Guide, Cisco IOS Release 12.4T Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Deployment Scenarios for Standalone Content Engines
 CHAPTER 3 Deployment Scenarios for Standalone Content Engines This chapter introduces some sample scenarios for deploying standalone Content Engines in enterprise and service provider environments. This
CHAPTER 3 Deployment Scenarios for Standalone Content Engines This chapter introduces some sample scenarios for deploying standalone Content Engines in enterprise and service provider environments. This
Cisco Virtual Networking Solution for OpenStack
 Data Sheet Cisco Virtual Networking Solution for OpenStack Product Overview Extend enterprise-class networking features to OpenStack cloud environments. A reliable virtual network infrastructure that provides
Data Sheet Cisco Virtual Networking Solution for OpenStack Product Overview Extend enterprise-class networking features to OpenStack cloud environments. A reliable virtual network infrastructure that provides
Introduction to Computer Networks. CS 166: Introduction to Computer Systems Security
 Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Contents. EVPN overview 1
 Contents EVPN overview 1 EVPN network model 1 MP-BGP extension for EVPN 2 Configuration automation 3 Assignment of traffic to VXLANs 3 Traffic from the local site to a remote site 3 Traffic from a remote
Contents EVPN overview 1 EVPN network model 1 MP-BGP extension for EVPN 2 Configuration automation 3 Assignment of traffic to VXLANs 3 Traffic from the local site to a remote site 3 Traffic from a remote
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin,
 Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
COPYRIGHTED MATERIAL. Con t e n t s. Chapter 1 Introduction to Networking 1. Chapter 2 Overview of Networking Components 21.
 Con t e n t s Introduction xix Chapter 1 Introduction to Networking 1 Comparing Logical and Physical Networks.... 1 Networking Home Computers........................................... 2 Networking Small
Con t e n t s Introduction xix Chapter 1 Introduction to Networking 1 Comparing Logical and Physical Networks.... 1 Networking Home Computers........................................... 2 Networking Small
Call Flows for 3G and 4G Mobile IP Users
 This chapter provides various call flows for 3G and 4G mobile IP users, and contains the following sections: Finding Feature Information, on page 1 3G DHCP Discover Call Flow, on page 1 4G DHCP Discover
This chapter provides various call flows for 3G and 4G mobile IP users, and contains the following sections: Finding Feature Information, on page 1 3G DHCP Discover Call Flow, on page 1 4G DHCP Discover
Last time. BGP policy. Broadcast / multicast routing. Link virtualization. Spanning trees. Reverse path forwarding, pruning Tunneling
 Last time BGP policy Broadcast / multicast routing Spanning trees Source-based, group-shared, center-based Reverse path forwarding, pruning Tunneling Link virtualization Whole networks can act as an Internet
Last time BGP policy Broadcast / multicast routing Spanning trees Source-based, group-shared, center-based Reverse path forwarding, pruning Tunneling Link virtualization Whole networks can act as an Internet
Mohammad Hossein Manshaei 1393
 Mohammad Hossein Manshaei manshaei@gmail.com 1393 Mobile IP 2 Mobile Network Layer: Problems and Concerns Entities and Terminology in Mobile IP Mobile Indirect Routing Mobile IP Agent Advertisement Registration
Mohammad Hossein Manshaei manshaei@gmail.com 1393 Mobile IP 2 Mobile Network Layer: Problems and Concerns Entities and Terminology in Mobile IP Mobile Indirect Routing Mobile IP Agent Advertisement Registration
ITdumpsFree. Get free valid exam dumps and pass your exam test with confidence
 ITdumpsFree http://www.itdumpsfree.com Get free valid exam dumps and pass your exam test with confidence Exam : 640-875 Title : Building Cisco Service Provider Next-Generation Networks, Part 1 (SPNGN1)
ITdumpsFree http://www.itdumpsfree.com Get free valid exam dumps and pass your exam test with confidence Exam : 640-875 Title : Building Cisco Service Provider Next-Generation Networks, Part 1 (SPNGN1)
Configuring Cache Services Using the Web Cache Communication Protocol
 Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
Remote Access via Cisco VPN Client
 Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
New Features for ASA Version 9.0(2)
 FIREWALL Features New Features for ASA Version 9.0(2) Cisco Adaptive Security Appliance (ASA) Software Release 9.0 is the latest release of the software that powers the Cisco ASA family. The same core
FIREWALL Features New Features for ASA Version 9.0(2) Cisco Adaptive Security Appliance (ASA) Software Release 9.0 is the latest release of the software that powers the Cisco ASA family. The same core
Configuring L2TP over IPsec
 CHAPTER 62 This chapter describes how to configure L2TP over IPsec on the ASA. This chapter includes the following topics: Information About L2TP over IPsec, page 62-1 Licensing Requirements for L2TP over
CHAPTER 62 This chapter describes how to configure L2TP over IPsec on the ASA. This chapter includes the following topics: Information About L2TP over IPsec, page 62-1 Licensing Requirements for L2TP over
Cisco Plug and Play Feature Guide Cisco Services. Cisco Plug and Play Feature Guide Cisco and/or its affiliates.
 Cisco Services TABLE OF CONTENTS Configuring Cisco Plug and Play... 14 Contents Introduction... 3 Cisco Plug and Play Components... 3 Plug-n-Play Agent... 3 Key Benefits... 4 Plug and Play Server... 4
Cisco Services TABLE OF CONTENTS Configuring Cisco Plug and Play... 14 Contents Introduction... 3 Cisco Plug and Play Components... 3 Plug-n-Play Agent... 3 Key Benefits... 4 Plug and Play Server... 4
Location ID Separation Protocol. Gregory Johnson -
 Location ID Separation Protocol Gregory Johnson - grjohnso@cisco.com LISP - Agenda LISP Overview LISP Operations LISP Use Cases LISP Status (Standards and in the Community) Summary 2 LISP Overview 2010
Location ID Separation Protocol Gregory Johnson - grjohnso@cisco.com LISP - Agenda LISP Overview LISP Operations LISP Use Cases LISP Status (Standards and in the Community) Summary 2 LISP Overview 2010
Foundations of Python
 Foundations of Python Network Programming The comprehensive guide to building network applications with Python Second Edition Brandon Rhodes John Goerzen Apress Contents Contents at a Glance About the
Foundations of Python Network Programming The comprehensive guide to building network applications with Python Second Edition Brandon Rhodes John Goerzen Apress Contents Contents at a Glance About the
Flexible NetFlow Full Flow support
 Flexible NetFlow Full Flow support Last Updated: January 29, 2013 The Flexible NetFlow - Full Flow support feature enables Flexible NetFlow to collect flow records for every packet. Finding Feature Information,
Flexible NetFlow Full Flow support Last Updated: January 29, 2013 The Flexible NetFlow - Full Flow support feature enables Flexible NetFlow to collect flow records for every packet. Finding Feature Information,
A5500 Configuration Guide
 A5500 Configuration Guide Sri Ram Kishore February 2012 Table of contents Gateway Configuration... 3 Accessing your gateway configuration tool... 3 Configuring your broadband Internet access... 3 Configuring
A5500 Configuration Guide Sri Ram Kishore February 2012 Table of contents Gateway Configuration... 3 Accessing your gateway configuration tool... 3 Configuring your broadband Internet access... 3 Configuring
L2TP over IPsec. About L2TP over IPsec/IKEv1 VPN
 This chapter describes how to configure /IKEv1 on the ASA. About /IKEv1 VPN, on page 1 Licensing Requirements for, on page 3 Prerequisites for Configuring, on page 4 Guidelines and Limitations, on page
This chapter describes how to configure /IKEv1 on the ASA. About /IKEv1 VPN, on page 1 Licensing Requirements for, on page 3 Prerequisites for Configuring, on page 4 Guidelines and Limitations, on page
External Logging. Bulk Port Allocation. Restrictions for Bulk Port Allocation
 External logging configures ex and logging of table entries, private bindings that are associated with a particular global IP, and to use Netflow to ex table entries., page 1 Session logging, page Syslog,
External logging configures ex and logging of table entries, private bindings that are associated with a particular global IP, and to use Netflow to ex table entries., page 1 Session logging, page Syslog,
Configuring Virtual Private LAN Services
 Virtual Private LAN Services (VPLS) enables enterprises to link together their Ethernet-based LANs from multiple sites via the infrastructure provided by their service provider. This module explains VPLS
Virtual Private LAN Services (VPLS) enables enterprises to link together their Ethernet-based LANs from multiple sites via the infrastructure provided by their service provider. This module explains VPLS
