The Changing DNS Market: A Technical Perspective
|
|
|
- Evan Jones
- 5 years ago
- Views:
Transcription
1 The Changing DNS Market: A Technical Perspective Johan Ihrén Netnod October 6, 2016 Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 1 / 15
2 Introduction When I started to prepare this talk I quickly realised that there is a significant overlap with the talk I presented at the Netnod meeting a year ago. So I will just reuse the intro... Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 2 / 15
3 Once upon a time DNS was simple In the early days, DNS was not considered a problem (but rather a solution) the only thing needed was the DNS server of course it was both authoritative and recursive everyone behaved nicely (at least regarding DNS) for a long time there was often only one server and only one implementation DNS server Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 3 / 15
4 Once upon a time DNS was simple In the early days, DNS was not considered a problem (but rather a solution) the only thing needed was the DNS server of course it was both authoritative and recursive everyone behaved nicely (at least regarding DNS) for a long time there was often only one server and only one implementation (BIND4.7.2beta26 if I remember correctly) However, things went south over time: good guys started doing bad things (split-dns, strange forwarding setups, policy-based responses, lots of rope everywhere) bad guys showed up doing bad things (also with DNS) The major reason that DNS is becoming a problem is that there is not sufficient revenue to match the increasing cost of operation. Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 3 / 15
5 Changes During the last few years a number of changes, some technical, some not so technical, have been propagating through the DNS community. DNS Anycast has become a staple technology root, TLDs and also Enterprises DDOS attacks have become a routine issue Static configurations are disappearing More and more behaviour modifying features outside the DNS protocol are used to tweak responses in various ways System complexity is exploding... that was actually the key point of the talk a year ago Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 4 / 15
6 Changes: Dynamic Configurations DNS is migrating from a static service (or set of services) that is configured via a static config file to a dynamic service that is configured in other ways : configuration via database configuration via APIs scriptable configs with CLI access to the nameserver Interestingly, two of the most interesting new recursive servers (PDNS Recursor and Knot-DNS Resolver) provide high-level scripting of configs via built in Lua support. while I m all for Lua, it is clear that being able to script entire new functions that modify the server behaviour... will be used in creative ways also, this breaks the old assumption that server behaviour can be understood from the config file. Now there s a running config and a written config and they can be different Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 5 / 15
7 Changes: Emergence of DNS APIs The DNS space consolidates. Fewer providers provide service for vast numbers of zones (authoritative service) or vast numbers of users (recursive service), but always with vast numbers of servers. In practice, the configuration file is disappearing sorry to have to break it to you, but the days of manual hacking named.conf are over today a requirement on DNS service is API access What is that? Well, there are provisioning APIs (adding and removing zones, modifying content of zones, etc) stats APIs (returning statistics and sometimes pretty graphics) management APIs (managing servers, modifying policies, etc) With the APIs follow new needs for authentication, etc Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 6 / 15
8 Changes: Behaviour From Policy, Not Zone Content Another major change in DNS service is the increasing breakage of the assumption that the contents of the zone defines the answer that the stub resolver (i.e. the end user) should get. There are an increasing amount of policy knobs in the authoritative space: geography-based responses, multiple levels of split-dns (now also with DNSSEC), etc And even more in the recursive area: RPZ (response-policy-zones) all sorts of local overrides that modify the response received from the authoritative servers loadable modules and scripting support specifically designed for reponse modification Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 7 / 15
9 Recent Market Changes All of the above are mostly technical changes. And there will always be technical changes, and the good ideas propagate while the bad ideas (hopefully) die out before they spread too far. But what about market changes? Well, there is one massive change happening right now: The cost for anycast service has now reached such a [low] price level that it is becoming very difficult to make a business case for DNS service unless the volume is really large and the coverage is global What will the consequences of this change be? Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 8 / 15
10 Market Penetration Thresholds Are Interesting Things History is full of examples where change started gradually... but when it reached a certain threshold there was a cascade effect at first only a few, wealthy, families had phones... but when a threshold was reached everyone had to get one at first only geeks and university students had ... but when the threshold was reached everyone had to get ... cars, Internet access, credit cards, etc, etc At some point we will reach a threshold where basically everyone zone owners, registrars, web and hosting providers, etc switch to DNS service from a dedicated DNS provider rather than fiddling with a bunch of servers on their own I believe that we are either at that point or very close to it Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 9 / 15
11 Advantages of Anycast For Everyone The market will inevitably become more professional The general quality of the DNS name space will increase and the number of outages and issues will decrease General DDOS resilience will increase (although no one with a sane mind will be willing to guarantee ability to withstand a large attack) Outages due to the nameserver is broken will mostly disappear as a source of problems but other sources like broken zones, etc, obviously remain Previously hidden brokenness (like broken zones) is exposed Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 10 / 15
12 Zone Quality On our recently launched Enterprise platform we have already seen customer zones that are broken the zone transfer from the customer master to our distribution infrastructure fails, because our nameservers refuse to accept the broken zone that such broken zones exist at all is likely a sign of old name server software (that doesn t do sufficient correctness verification) in the short run it is a problem for the customer relation However, in the long run it is good that these broken zones get detected and fixed, as this will improve quality of the overall DNS name space... assuming, of course, that they do get fixed Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 11 / 15
13 Disadvantages of Anycast For Everyone Smaller providers will be edged out of the market The cost (to the remaining providers) of moving all the data for millions of zones of minor importance to lots of servers around the world will be impossible to recover The problem definition will change from the nameserver is broken, we need to fix it to how do I achieve XXX via the API from DNS provider YYY? We will replace one source of problems (configuring and operating nameservers) with another (integration of the various DNS provider APIs) this will require a mostly new skill set in the community Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 12 / 15
14 Risk Of Mono Culture? Closed Source? DNS has a long tradition of relying on open source implementations. Most of the major implementations (BIND, NSD, etc) have always been open source. there is also a large fringe of mostly open source nameservers, with various quirks and feature. it is certainly a rich culture (despite the huge BIND user base) Will a rapid migration towards professional DNS services provided by a limited number of providers change this? probably yes (as in some implementations will die), but not enough to make the risks of mono culture a real concern My concern is instead the trend towards closed source implementations that implement various extensions to DNS as a means to distinguish themselves from the competition Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 13 / 15
15 Some Predictions for the Future (this is so last year!) 1 The drivers for further DNS evolution remain DNS service and routing is becoming more and more mixed up due to prevalent use of anycast, both for authoritative and for recursive service DNS will continue to become an ever more complex service with increasing complexity more and more of the regional level DNS service will be edged out 2 DNS is becoming a more professionalised service with a smaller number of large scale providers 3 DNS consulting will remain a good field of work Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 14 / 15
16 Some Updated Predictions for the Future 1 The drivers for further DNS evolution remain DNS service and routing is becoming more and more mixed up due to prevalent use of anycast, both for authoritative and for recursive service, but customers won t care, no longer their problem DNS will continue to become an ever more complex service with increasing complexity more and more of the the market forces will ensure that regional level DNS service will be edged out will die within five years time 2 DNS is becoming a more professionalised service with a smaller number of large scale providers and an increasing dependence on closed source implementations 3 DNS consulting will remain a good field of work largely be replaced by API integration work with no nameserver configuration, perhaps there will be more attention on the actual DNS data? Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 14 / 15
17 DNS Anycast Services For The Enterprise Market As you all must have heard by now, Netnod has launched the DNS Anycast Services that has been chosen by a large number of major cctlds also to the Enterprise market... but with a completely new provisioning infrastructure to be able to cater to millions of small zones... rather than just a single (large) zone which was typical from a TLD customer In the Nordic region we believe that we are already able to provide a significantly better service at a lower cost than any other DNS provider As we continue our rollout the same will be true for an increasing number of markets Talk to one of our resellers if this sounds interesting Netnod Customer Mtg, October 6, 2016, Changing DNS Market: A Tech Perspective, johani@netnod.se 15 / 15
A Better Way to a Redundant DNS.
 WHITEPAPE R A Better Way to a Redundant DNS. +1.855.GET.NSONE (6766) NS1.COM 2019.02.12 Executive Summary DNS is a mission critical application for every online business. In the words of Gartner If external
WHITEPAPE R A Better Way to a Redundant DNS. +1.855.GET.NSONE (6766) NS1.COM 2019.02.12 Executive Summary DNS is a mission critical application for every online business. In the words of Gartner If external
ICANN and Technical Work: Really? Yes! Steve Crocker DNS Symposium, Madrid, 13 May 2017
 ICANN and Technical Work: Really? Yes! Steve Crocker DNS Symposium, Madrid, 13 May 2017 Welcome, everyone. I appreciate the invitation to say a few words here. This is an important meeting and I think
ICANN and Technical Work: Really? Yes! Steve Crocker DNS Symposium, Madrid, 13 May 2017 Welcome, everyone. I appreciate the invitation to say a few words here. This is an important meeting and I think
DNSSEC Deployment Issues
 DNSSEC Deployment Issues Johan Ihrén, Autonomica AB Outline The very, very, very short summary is that as the protocol phase is over deployment issues need to be sorted out requires new participants as
DNSSEC Deployment Issues Johan Ihrén, Autonomica AB Outline The very, very, very short summary is that as the protocol phase is over deployment issues need to be sorted out requires new participants as
BEST PRACTICES FOR IMPROVING EXTERNAL DNS RESILIENCY AND PERFORMANCE
 BEST PRACTICES FOR IMPROVING EXTERNAL DNS RESILIENCY AND PERFORMANCE 12-07-2016 BEST PRACTICES FOR IMPROVING EXTERNAL DNS RESILIENCY AND PERFORMANCE Your external DNS is a mission critical business resource.
BEST PRACTICES FOR IMPROVING EXTERNAL DNS RESILIENCY AND PERFORMANCE 12-07-2016 BEST PRACTICES FOR IMPROVING EXTERNAL DNS RESILIENCY AND PERFORMANCE Your external DNS is a mission critical business resource.
Re-engineering the DNS One Resolver at a Time. Paul Wilson Director General APNIC channeling Geoff Huston Chief Scientist
 Re-engineering the DNS One Resolver at a Time Paul Wilson Director General APNIC channeling Geoff Huston Chief Scientist 1 In this presentation I ll talk about the DNS, and the root server infrastructure
Re-engineering the DNS One Resolver at a Time Paul Wilson Director General APNIC channeling Geoff Huston Chief Scientist 1 In this presentation I ll talk about the DNS, and the root server infrastructure
DNS SECURITY BEST PRACTICES
 White Paper DNS SECURITY BEST PRACTICES Highlights Have alternative name server software ready to use Keep your name server software up-to-date Use DNSSEC-compliant and TSIG-compliant name server software
White Paper DNS SECURITY BEST PRACTICES Highlights Have alternative name server software ready to use Keep your name server software up-to-date Use DNSSEC-compliant and TSIG-compliant name server software
(DNS, and DNSSEC and DDOS) Geoff Huston APNIC
 D* (DNS, and DNSSEC and DDOS) Geoff Huston APNIC How to be bad 2 How to be bad Host and application-based exploits abound And are not going away anytime soon! And there are attacks on the Internet infrastructure
D* (DNS, and DNSSEC and DDOS) Geoff Huston APNIC How to be bad 2 How to be bad Host and application-based exploits abound And are not going away anytime soon! And there are attacks on the Internet infrastructure
Rolling the Root. Geoff Huston APNIC Labs March 2016
 Rolling the Root Geoff Huston APNIC Labs March 2016 Use of DNSSEC Validation in Today s Internet Why is this relevant? Because the root zone managers are preparing to roll the DNS Root Zone Key Signing
Rolling the Root Geoff Huston APNIC Labs March 2016 Use of DNSSEC Validation in Today s Internet Why is this relevant? Because the root zone managers are preparing to roll the DNS Root Zone Key Signing
DNS Survival Guide. Artyom Gavrichenkov
 DNS Survival Guide Artyom Gavrichenkov A bit of a history: DNS 1983: (int32)*host_str; A bit of a history: DNS 1983: (int32)*host_str; 1997-2017: load balancing geobalancing ASN policies
DNS Survival Guide Artyom Gavrichenkov A bit of a history: DNS 1983: (int32)*host_str; A bit of a history: DNS 1983: (int32)*host_str; 1997-2017: load balancing geobalancing ASN policies
BIG-IP DNS Services: Implementations. Version 12.0
 BIG-IP DNS Services: Implementations Version 12.0 Table of Contents Table of Contents Configuring DNS Express...11 What is DNS Express?...11 About configuring DNS Express...11 Configuring DNS Express
BIG-IP DNS Services: Implementations Version 12.0 Table of Contents Table of Contents Configuring DNS Express...11 What is DNS Express?...11 About configuring DNS Express...11 Configuring DNS Express
The DNS of Things. A. 2001:19b8:10 1:2::f5f5:1d Q. WHERE IS Peter Silva Sr. Technical Marketing
 The DNS of Things Peter Silva Sr. Technical Marketing Manager @psilvas Q. WHERE IS WWW.F5.COM? A. 2001:19b8:10 1:2::f5f5:1d Advanced threats Software defined everything SDDC/Cloud Internet of Things Mobility
The DNS of Things Peter Silva Sr. Technical Marketing Manager @psilvas Q. WHERE IS WWW.F5.COM? A. 2001:19b8:10 1:2::f5f5:1d Advanced threats Software defined everything SDDC/Cloud Internet of Things Mobility
WHITE PAPER. Why Infoblox for DDI. It is time to migrate from BIND and Microsoft
 WHITE PAPER Why Infoblox for DDI It is time to migrate from BIND and Microsoft In many organizations the core services that enable reliable connectivity and access to the internet are based on free and
WHITE PAPER Why Infoblox for DDI It is time to migrate from BIND and Microsoft In many organizations the core services that enable reliable connectivity and access to the internet are based on free and
BIG-IP DNS Services: Implementations. Version 12.1
 BIG-IP DNS Services: Implementations Version 12.1 Table of Contents Table of Contents Configuring DNS Express...9 What is DNS Express?...9 About configuring DNS Express...9 Configuring DNS Express to
BIG-IP DNS Services: Implementations Version 12.1 Table of Contents Table of Contents Configuring DNS Express...9 What is DNS Express?...9 About configuring DNS Express...9 Configuring DNS Express to
THE CYBERSECURITY LITERACY CONFIDENCE GAP
 CONFIDENCE: SECURED WHITE PAPER THE CYBERSECURITY LITERACY CONFIDENCE GAP ADVANCED THREAT PROTECTION, SECURITY AND COMPLIANCE Despite the fact that most organizations are more aware of cybersecurity risks
CONFIDENCE: SECURED WHITE PAPER THE CYBERSECURITY LITERACY CONFIDENCE GAP ADVANCED THREAT PROTECTION, SECURITY AND COMPLIANCE Despite the fact that most organizations are more aware of cybersecurity risks
LANCOM Techpaper Smart WLAN controlling
 The widespread use of wireless access points and wireless routers provides great convenience and flexibility in network access for businesses, universities and other organizations. In recent years, wireless
The widespread use of wireless access points and wireless routers provides great convenience and flexibility in network access for businesses, universities and other organizations. In recent years, wireless
How do we make the transition less painful? IPv6 & recursive resolvers:
 How do we make the transition less painful? IPv6 & recursive resolvers: 11.5.2009 Overview of the problem IPv6 rollout may not impact production IPv4 Rolling out dedicated IPv6 hostnames is not a good
How do we make the transition less painful? IPv6 & recursive resolvers: 11.5.2009 Overview of the problem IPv6 rollout may not impact production IPv4 Rolling out dedicated IPv6 hostnames is not a good
DSC on top of PacketQ
 DSC on top of PacketQ Johan Ihrén Netnod October 14, 2012 OARC meeting, Toronto, October 14, 2012, DSC on top of PacketQ, johani@netnod.se 1 / 9 DSC Why DSC? De-facto standard, especially among TLDs Why
DSC on top of PacketQ Johan Ihrén Netnod October 14, 2012 OARC meeting, Toronto, October 14, 2012, DSC on top of PacketQ, johani@netnod.se 1 / 9 DSC Why DSC? De-facto standard, especially among TLDs Why
In the Domain Name System s language, rcode 0 stands for: no error condition.
 12/2017 SIMPLE, FAST, RESILIENT In the Domain Name System s language, rcode 0 stands for: no error condition. If a DNS server answers a query with this result code, the service is running properly. This
12/2017 SIMPLE, FAST, RESILIENT In the Domain Name System s language, rcode 0 stands for: no error condition. If a DNS server answers a query with this result code, the service is running properly. This
IANA Developments ccnso, Wellington Kim Davies Internet Assigned Numbers Authority
 IANA Developments ccnso, Wellington 2006 Kim Davies Internet Assigned Numbers Authority Coming up: Brief Update IANA Development Work Goals Very Brief Update on IANA Operations Yoshiko Chong joined our
IANA Developments ccnso, Wellington 2006 Kim Davies Internet Assigned Numbers Authority Coming up: Brief Update IANA Development Work Goals Very Brief Update on IANA Operations Yoshiko Chong joined our
The ISP Column A column on things Internet. Three DNS articles: 3. Helping Resolvers to help the DNS. RFC8192 Aggressive NSEC Caching
 The ISP Column A column on things Internet Geoff Huston November 2017 Three DNS articles: 3. Helping Resolvers to help the DNS In this final article of a trio that looks at today s hot topics in the DNS,
The ISP Column A column on things Internet Geoff Huston November 2017 Three DNS articles: 3. Helping Resolvers to help the DNS In this final article of a trio that looks at today s hot topics in the DNS,
Hoda Rohani Anastasios Poulidis Supervisor: Jeroen Scheerder. System and Network Engineering July 2014
 Hoda Rohani Anastasios Poulidis Supervisor: Jeroen Scheerder System and Network Engineering July 2014 DNS Main Components Server Side: Authoritative Servers Resolvers (Recursive Resolvers, cache) Client
Hoda Rohani Anastasios Poulidis Supervisor: Jeroen Scheerder System and Network Engineering July 2014 DNS Main Components Server Side: Authoritative Servers Resolvers (Recursive Resolvers, cache) Client
State of Cloud Survey GERMANY FINDINGS
 2011 State of Cloud Survey GERMANY FINDINGS CONTENTS Executive Summary... 4 Methodology... 6 Finding 1: Cloud security is top goal and top concern.................................. 8 Finding 2: IT staff
2011 State of Cloud Survey GERMANY FINDINGS CONTENTS Executive Summary... 4 Methodology... 6 Finding 1: Cloud security is top goal and top concern.................................. 8 Finding 2: IT staff
A paper on DNSSEC - NSEC3 with Opt-Out
 A paper on DNSSEC - NSEC3 with Opt-Out DNSSEC A Way Forward for TLD Registries Method for faster adoption of DNSSEC Providing greater security with minimal impact on customers, registries and Zone Management
A paper on DNSSEC - NSEC3 with Opt-Out DNSSEC A Way Forward for TLD Registries Method for faster adoption of DNSSEC Providing greater security with minimal impact on customers, registries and Zone Management
Internet Engineering Task Force (IETF) Request for Comments: 7706 Category: Informational ISSN: November 2015
 Internet Engineering Task Force (IETF) Request for Comments: 7706 Category: Informational ISSN: 2070-1721 W. Kumari Google P. Hoffman ICANN November 2015 Decreasing Access Time to Root Servers by Running
Internet Engineering Task Force (IETF) Request for Comments: 7706 Category: Informational ISSN: 2070-1721 W. Kumari Google P. Hoffman ICANN November 2015 Decreasing Access Time to Root Servers by Running
Experience from a Swedish Agency and a Nordic operator
 Experience from a Swedish Agency and a Nordic operator fredrik@xpd.se Overview Skatteverket (Swedish Tax Agency) End user perspective TDC Registrar perspective Skatteverket Why DNSSEC? How to deploy? What
Experience from a Swedish Agency and a Nordic operator fredrik@xpd.se Overview Skatteverket (Swedish Tax Agency) End user perspective TDC Registrar perspective Skatteverket Why DNSSEC? How to deploy? What
August 14th, 2018 PRESENTED BY:
 August 14th, 2018 PRESENTED BY: APPLICATION LAYER ATTACKS 100% 80% 60% 40% 20% 0% DNS is the second most targeted protocol after HTTP. DNS DoS techniques range from: Flooding requests to a given host.
August 14th, 2018 PRESENTED BY: APPLICATION LAYER ATTACKS 100% 80% 60% 40% 20% 0% DNS is the second most targeted protocol after HTTP. DNS DoS techniques range from: Flooding requests to a given host.
Rolling the Root KSK. Geoff Huston. APNIC Labs. September 2017
 Rolling the Root KSK Geoff Huston APNIC Labs September 2017 Will this break the Internet? Why? If we stuff up this trust anchor key roll then resolvers that perform DNSSEC validation will fail to provide
Rolling the Root KSK Geoff Huston APNIC Labs September 2017 Will this break the Internet? Why? If we stuff up this trust anchor key roll then resolvers that perform DNSSEC validation will fail to provide
IDN Deployment Test Results
 IDN Deployment Test Results Lars-Johan Liman Autonomica AB Abstract Autonomica AB has, under a contract with ICANN, investigated whether the addition of top level domains containing encoded internationalized
IDN Deployment Test Results Lars-Johan Liman Autonomica AB Abstract Autonomica AB has, under a contract with ICANN, investigated whether the addition of top level domains containing encoded internationalized
Global Deep Scans Measuring vulnerability levels across organizations, industries, and countries
 Global Deep Scans Measuring vulnerability levels across organizations, industries, and countries Fabian Bräunlein Luca Melette SRLabs Template v12 Motivation for this
Global Deep Scans Measuring vulnerability levels across organizations, industries, and countries Fabian Bräunlein Luca Melette SRLabs Template v12 Motivation for this
Test Automation. Fundamentals. Mikó Szilárd
 Test Automation Fundamentals Mikó Szilárd 2016 EPAM 2 Blue-chip clients rely on EPAM 3 SCHEDULE 9.12 Intro 9.19 Unit testing 1 9.26 Unit testing 2 10.03 Continuous integration 1 10.10 Continuous integration
Test Automation Fundamentals Mikó Szilárd 2016 EPAM 2 Blue-chip clients rely on EPAM 3 SCHEDULE 9.12 Intro 9.19 Unit testing 1 9.26 Unit testing 2 10.03 Continuous integration 1 10.10 Continuous integration
An introduction to the VDI landscape
 The : An Virtual desktop infrastructures are quickly gaining popularity in the IT industry as end users are now able to connect to their desktops from any location, at any time. This e-guide, from SearchVirtualDesktop.com,
The : An Virtual desktop infrastructures are quickly gaining popularity in the IT industry as end users are now able to connect to their desktops from any location, at any time. This e-guide, from SearchVirtualDesktop.com,
Domain Name System (DNS) Session 2: Resolver Operation and debugging. Joe Abley AfNOG Workshop, AIS 2017, Nairobi
 Domain Name System (DNS) Session 2: Resolver Operation and debugging Joe Abley AfNOG Workshop, AIS 2017, Nairobi DNS Resolver Operation How Resolvers Work (1)! If we've dealt with this query before recently,
Domain Name System (DNS) Session 2: Resolver Operation and debugging Joe Abley AfNOG Workshop, AIS 2017, Nairobi DNS Resolver Operation How Resolvers Work (1)! If we've dealt with this query before recently,
UDP-based Amplification Attacks and its Mitigations
 UDP-based Amplification Attacks and its Mitigations Yoshiaki Kasahara kasahara@nc.kyushu-u.ac.jp 1/21/2014 APAN 37th in Bandung, Indonesia 1 Summary If you have servers with global IP addresses 1. Make
UDP-based Amplification Attacks and its Mitigations Yoshiaki Kasahara kasahara@nc.kyushu-u.ac.jp 1/21/2014 APAN 37th in Bandung, Indonesia 1 Summary If you have servers with global IP addresses 1. Make
This time. Digging into. Networking. Protocols. Naming DNS & DHCP
 This time Digging into Networking Protocols Naming DNS & DHCP Naming IP addresses allow global connectivity But they re pretty useless for humans! Can t be expected to pick their own IP address Can t be
This time Digging into Networking Protocols Naming DNS & DHCP Naming IP addresses allow global connectivity But they re pretty useless for humans! Can t be expected to pick their own IP address Can t be
USING TRANSACTION SIGNATURES (TSIG) FOR SECURE DNS SERVER COMMUNICATION
 USING TRANSACTION SIGNATURES (TSIG) FOR SECURE DNS SERVER COMMUNICATION 11-30-2016 USING TRANSACTION SIGNATURES (TSIG) FOR SECURE DNS SERVER COMMUNICATION Transaction Signatures (TSIG) provide a secure
USING TRANSACTION SIGNATURES (TSIG) FOR SECURE DNS SERVER COMMUNICATION 11-30-2016 USING TRANSACTION SIGNATURES (TSIG) FOR SECURE DNS SERVER COMMUNICATION Transaction Signatures (TSIG) provide a secure
Virtualization. Q&A with an industry leader. Virtualization is rapidly becoming a fact of life for agency executives,
 Virtualization Q&A with an industry leader Virtualization is rapidly becoming a fact of life for agency executives, as the basis for data center consolidation and cloud computing and, increasingly, as
Virtualization Q&A with an industry leader Virtualization is rapidly becoming a fact of life for agency executives, as the basis for data center consolidation and cloud computing and, increasingly, as
Cloud DNS. High Performance under any traffic conditions from anywhere in the world. Reliable. Performance
 Cloud DNS High Performance under any traffic conditions from anywhere in the world Secure DNS System Reduce vulnerability to spoofing and distributed denial of service (DDoS) attacks Reliable Performance
Cloud DNS High Performance under any traffic conditions from anywhere in the world Secure DNS System Reduce vulnerability to spoofing and distributed denial of service (DDoS) attacks Reliable Performance
RIPE NCC Technical Services. Kaveh Ranjbar, Chief Information Officer
 RIPE NCC Kaveh Ranjbar, Chief Information Officer MENOG 15 Dubai, UAE 2 April 2015 Overview 2 RIPE Atlas K-root expansion DNS services RIPEstat Research Mostly global services, accessible by everyone -
RIPE NCC Kaveh Ranjbar, Chief Information Officer MENOG 15 Dubai, UAE 2 April 2015 Overview 2 RIPE Atlas K-root expansion DNS services RIPEstat Research Mostly global services, accessible by everyone -
Flexible Testbed for Recursive Resolver Software
 Flexible Testbed for Recursive Resolver Software Paul Hoffman DNS-OARC 27, San Jose, CA 30 September 2017 v1 1 Overview The resolver server testbed The test root creator Use case: getting ready for the
Flexible Testbed for Recursive Resolver Software Paul Hoffman DNS-OARC 27, San Jose, CA 30 September 2017 v1 1 Overview The resolver server testbed The test root creator Use case: getting ready for the
The Interactive Guide to Protecting Your Election Website
 The Interactive Guide to Protecting Your Election Website 1 INTRODUCTION Cloudflare is on a mission to help build a better Internet. Cloudflare is one of the world s largest networks. Today, businesses,
The Interactive Guide to Protecting Your Election Website 1 INTRODUCTION Cloudflare is on a mission to help build a better Internet. Cloudflare is one of the world s largest networks. Today, businesses,
DOMAIN NAME SECURITY EXTENSIONS
 DOMAIN NAME SECURITY EXTENSIONS The aim of this paper is to provide information with regards to the current status of Domain Name System (DNS) and its evolution into Domain Name System Security Extensions
DOMAIN NAME SECURITY EXTENSIONS The aim of this paper is to provide information with regards to the current status of Domain Name System (DNS) and its evolution into Domain Name System Security Extensions
CSC 574 Computer and Network Security. DNS Security
 CSC 574 Computer and Network Security DNS Security Alexandros Kapravelos kapravelos@ncsu.edu (Derived from slides by Will Enck and Micah Sherr) A primer on routing Routing Problem: How do Alice s messages
CSC 574 Computer and Network Security DNS Security Alexandros Kapravelos kapravelos@ncsu.edu (Derived from slides by Will Enck and Micah Sherr) A primer on routing Routing Problem: How do Alice s messages
THE BUSINESS CASE FOR OUTSIDE-IN DATA CENTER SECURITY
 THE BUSINESS CASE FOR OUTSIDE-IN DATA CENTER SECURITY DATA CENTER WEB APPS NEED MORE THAN IP-BASED DEFENSES AND NEXT-GENERATION FIREWALLS table of contents.... 2.... 4.... 5 A TechTarget White Paper Does
THE BUSINESS CASE FOR OUTSIDE-IN DATA CENTER SECURITY DATA CENTER WEB APPS NEED MORE THAN IP-BASED DEFENSES AND NEXT-GENERATION FIREWALLS table of contents.... 2.... 4.... 5 A TechTarget White Paper Does
Keeping DNS parents and children in sync at Internet Speed! Ólafur Guðmundsson
 Keeping DNS parents and children in sync at Internet Speed! Ólafur Guðmundsson olafur@cloudflare.com How long does it take to? Post a new selfie on Facebook and all your friends to be notified few seconds
Keeping DNS parents and children in sync at Internet Speed! Ólafur Guðmundsson olafur@cloudflare.com How long does it take to? Post a new selfie on Facebook and all your friends to be notified few seconds
ICANN Start, Episode 1: Redirection and Wildcarding. Welcome to ICANN Start. This is the show about one issue, five questions:
 Recorded in October, 2009 [Music Intro] ICANN Start, Episode 1: Redirection and Wildcarding Welcome to ICANN Start. This is the show about one issue, five questions: What is it? Why does it matter? Who
Recorded in October, 2009 [Music Intro] ICANN Start, Episode 1: Redirection and Wildcarding Welcome to ICANN Start. This is the show about one issue, five questions: What is it? Why does it matter? Who
Preparing your network for the next wave of innovation
 Preparing your network for the next wave of innovation The future is exciting. Ready? 2 Executive brief For modern businesses, every day brings fresh challenges and opportunities. You must be able to adapt
Preparing your network for the next wave of innovation The future is exciting. Ready? 2 Executive brief For modern businesses, every day brings fresh challenges and opportunities. You must be able to adapt
DHCP, DNS & IP Address Management. Bart Busschots
 DHCP, DNS & IP Address Management Bart Busschots Outline The Back-story How did we get to where we were? What was the problem? Why the need for change? Scope & Requirements What must we have? What would
DHCP, DNS & IP Address Management Bart Busschots Outline The Back-story How did we get to where we were? What was the problem? Why the need for change? Scope & Requirements What must we have? What would
Outline Key Management CS 239 Computer Security February 9, 2004
 Outline Key Management CS 239 Computer Security February 9, 2004 Properties of keys Key management Key servers Certificates Page 1 Page 2 Introduction Properties of Keys It doesn t matter how strong your
Outline Key Management CS 239 Computer Security February 9, 2004 Properties of keys Key management Key servers Certificates Page 1 Page 2 Introduction Properties of Keys It doesn t matter how strong your
WYSIWON T The XML Authoring Myths
 WYSIWON T The XML Authoring Myths Tony Stevens Turn-Key Systems Abstract The advantages of XML for increasing the value of content and lowering production costs are well understood. However, many projects
WYSIWON T The XML Authoring Myths Tony Stevens Turn-Key Systems Abstract The advantages of XML for increasing the value of content and lowering production costs are well understood. However, many projects
Newsletter. More UDRP (Uniform Domain Name Dispute- Resolution Policy) Cases at WIPO in 2016 than Issue 9 December 2016
 Newsletter Issue 9 December 2016 More UDRP (Uniform Domain Name Dispute- Resolution Policy) Cases at WIPO in 2016 than 2015 There is still well over a month remaining in 2016, and it looks like there are
Newsletter Issue 9 December 2016 More UDRP (Uniform Domain Name Dispute- Resolution Policy) Cases at WIPO in 2016 than 2015 There is still well over a month remaining in 2016, and it looks like there are
Draft Applicant Guidebook, v3
 Draft Applicant Guidebook, v3 Module 5 Please note that this is a discussion draft only. Potential applicants should not rely on any of the proposed details of the new gtld program as the program remains
Draft Applicant Guidebook, v3 Module 5 Please note that this is a discussion draft only. Potential applicants should not rely on any of the proposed details of the new gtld program as the program remains
Technical Description: Nixu Registry Server
 Technical Description: Nixu Registry Server Nixu Software Oy Ltd A Nixu Group Company Keilaranta 15 FI-02150 Espoo Finland 1 1. Overview of Nixu Registry Server Nixu Registry Server is a Domain Name Registry
Technical Description: Nixu Registry Server Nixu Software Oy Ltd A Nixu Group Company Keilaranta 15 FI-02150 Espoo Finland 1 1. Overview of Nixu Registry Server Nixu Registry Server is a Domain Name Registry
9 th CA 2E/CA Plex Worldwide Developer Conference 1
 1 Introduction/Welcome Message Organizations that are making major changes to or replatforming an application need to dedicate considerable resources ot the QA effort. In this session we will show best
1 Introduction/Welcome Message Organizations that are making major changes to or replatforming an application need to dedicate considerable resources ot the QA effort. In this session we will show best
Top of Minds Report series Data Warehouse The six levels of integration
 Top of Minds Report series Data Warehouse The six levels of integration Recommended reading Before reading this report it is recommended to read ToM Report Series on Data Warehouse Definitions for Integration
Top of Minds Report series Data Warehouse The six levels of integration Recommended reading Before reading this report it is recommended to read ToM Report Series on Data Warehouse Definitions for Integration
What s new in SketchUp Pro?
 What s new in SketchUp Pro? SketchUp Pro (Desktop) Making Information Modeling Useful Ultimately, we think BIM is about using information in your model to make better buildings. Our focus is to help users
What s new in SketchUp Pro? SketchUp Pro (Desktop) Making Information Modeling Useful Ultimately, we think BIM is about using information in your model to make better buildings. Our focus is to help users
CPS122 Lecture: Course Intro; Introduction to Object-Orientation
 Objectives: CPS122 Lecture: Course Intro; Introduction to Object-Orientation 1. To introduce the course requirements and procedures. 2. To introduce fundamental concepts of OO: object, class Materials:
Objectives: CPS122 Lecture: Course Intro; Introduction to Object-Orientation 1. To introduce the course requirements and procedures. 2. To introduce fundamental concepts of OO: object, class Materials:
Rock-solid Internet infrastructure. (Yeah, we keep our stuff in bunkers.)
 Rock-solid Internet infrastructure. (Yeah, we keep our stuff in bunkers.) WHO DO YOU TRUST TO GET THE JOB DONE? Innovation at the core of the Internet When it comes to Internet services, you need a partner
Rock-solid Internet infrastructure. (Yeah, we keep our stuff in bunkers.) WHO DO YOU TRUST TO GET THE JOB DONE? Innovation at the core of the Internet When it comes to Internet services, you need a partner
That KSK Roll. Geoff Huston APNIC Labs
 That KSK Roll Geoff Huston APNIC Labs The DNS may look simple But with the DNS, looks are very deceiving So lets talk DNSSEC DNSSEC introduces digital signatures into the DNS It allows a DNS resolver to
That KSK Roll Geoff Huston APNIC Labs The DNS may look simple But with the DNS, looks are very deceiving So lets talk DNSSEC DNSSEC introduces digital signatures into the DNS It allows a DNS resolver to
Copyright ECSC Group plc 2017 ECSC - UNRESTRICTED
 Copyright ECSC Group plc 2017 ECSC - UNRESTRICTED ECSC - UNRESTRICTED Introduction A Web Application Firewall (WAF) is, in our experience, the most important layer of defence against a wide range of attacks
Copyright ECSC Group plc 2017 ECSC - UNRESTRICTED ECSC - UNRESTRICTED Introduction A Web Application Firewall (WAF) is, in our experience, the most important layer of defence against a wide range of attacks
Q&A TAKING ENTERPRISE SECURITY TO THE NEXT LEVEL. An interview with John Summers, Enterprise VP and GM, Akamai
 TAKING ENTERPRISE SECURITY TO THE NEXT LEVEL An interview with John Summers, Enterprise VP and GM, Akamai Q&A What are the top things that business leaders need to understand about today s cybersecurity
TAKING ENTERPRISE SECURITY TO THE NEXT LEVEL An interview with John Summers, Enterprise VP and GM, Akamai Q&A What are the top things that business leaders need to understand about today s cybersecurity
DNS Risk Framework Update
 Text Text 14 October 2014 DNS Risk Framework Update John Crain & Jacks Khawaja Chief SSR Officer; Enterprise Risk Director Agenda Text History Moving Forward Text History Defined Resiliency Model Text
Text Text 14 October 2014 DNS Risk Framework Update John Crain & Jacks Khawaja Chief SSR Officer; Enterprise Risk Director Agenda Text History Moving Forward Text History Defined Resiliency Model Text
DNS Flag day. A tale of five cctlds. Hugo Salgado,.CL Sebastián Castro,.NZ DNS-OARC 29, Amsterdam
 DNS Flag day A tale of five cctlds Hugo Salgado,.CL Sebastián Castro,.NZ DNS-OARC 29, Amsterdam 1 What is EDNS? RFC 6891 Defines a backward compatible mechanism to signal support for new DNS options Original
DNS Flag day A tale of five cctlds Hugo Salgado,.CL Sebastián Castro,.NZ DNS-OARC 29, Amsterdam 1 What is EDNS? RFC 6891 Defines a backward compatible mechanism to signal support for new DNS options Original
The F5 Intelligent DNS Scale Reference Architecture
 The F5 Intelligent DNS Scale Reference Architecture End-to-end DNS delivery solutions from F5 maximize the use of organizational resources, while remaining agile and intelligent enough to scale and support
The F5 Intelligent DNS Scale Reference Architecture End-to-end DNS delivery solutions from F5 maximize the use of organizational resources, while remaining agile and intelligent enough to scale and support
HyperLogLog inspired three-minute scan of DNSSEC delegations worldwide. DNS-OARC 26,
 HyperLogLog inspired three-minute scan of DNSSEC delegations worldwide DNS-OARC 26, Madrid @PowerDNS_Bert bert.hubert@powerdns.com Agenda DNSSEC: existing measurements for secured delegations Actively
HyperLogLog inspired three-minute scan of DNSSEC delegations worldwide DNS-OARC 26, Madrid @PowerDNS_Bert bert.hubert@powerdns.com Agenda DNSSEC: existing measurements for secured delegations Actively
Paper. Delivering Strong Security in a Hyperconverged Data Center Environment
 Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
SURFnet What we re doing and what we ve found so far
 DNSSEC @ SURFnet What we re doing and what we ve found so far Paul Dekkers paul.dekkers [at] surfnet.nl October 20th 2009 Overview - First half: - Why we think DNSSEC matters - Second half: - What we are
DNSSEC @ SURFnet What we re doing and what we ve found so far Paul Dekkers paul.dekkers [at] surfnet.nl October 20th 2009 Overview - First half: - Why we think DNSSEC matters - Second half: - What we are
THE AUTHORITATIVE GUIDE TO DNS TERMINOLOGY
 Ebook: THE AUTHORITATIVE GUIDE TO DNS TERMINOLOGY From A Record & DNS to Zones 603 668 4998 Your Master List of Key DNS Terms As more users and more online services (sites, microservices, connected things,
Ebook: THE AUTHORITATIVE GUIDE TO DNS TERMINOLOGY From A Record & DNS to Zones 603 668 4998 Your Master List of Key DNS Terms As more users and more online services (sites, microservices, connected things,
NIC Chile Secondary DNS Service History and Evolution
 NIC Chile Secondary DNS Service History and Evolution Marco Díaz OARC Buenos Aires 2016 A little bit of history NIC Chile started to offer secondary service as a way to improve the local Internet. Launched
NIC Chile Secondary DNS Service History and Evolution Marco Díaz OARC Buenos Aires 2016 A little bit of history NIC Chile started to offer secondary service as a way to improve the local Internet. Launched
Imperva Incapsula Survey: What DDoS Attacks Really Cost Businesses
 Survey Imperva Incapsula Survey: What DDoS Attacks Really Cost Businesses BY: TIM MATTHEWS 2016, Imperva, Inc. All rights reserved. Imperva and the Imperva logo are trademarks of Imperva, Inc. Contents
Survey Imperva Incapsula Survey: What DDoS Attacks Really Cost Businesses BY: TIM MATTHEWS 2016, Imperva, Inc. All rights reserved. Imperva and the Imperva logo are trademarks of Imperva, Inc. Contents
Types of Software Testing: Different Testing Types with Details
 Types of Software Testing: Different Testing Types with Details What are the different Types of Software Testing? We, as testers are aware of the various types of Software Testing such as Functional Testing,
Types of Software Testing: Different Testing Types with Details What are the different Types of Software Testing? We, as testers are aware of the various types of Software Testing such as Functional Testing,
How we measure IPv6. Geoff Huston, Joao Damas George Michalson APNIC. George Michaelson. Geoff Huston. Joao Damas. APNIC Labs
 How we measure IPv6 George Michaelson Geoff Huston, Joao Damas George Michalson APNIC Geoff Huston Joao Damas APNIC Labs Background Measurement is a big topic in today s Internet Reliable, unbiased, open
How we measure IPv6 George Michaelson Geoff Huston, Joao Damas George Michalson APNIC Geoff Huston Joao Damas APNIC Labs Background Measurement is a big topic in today s Internet Reliable, unbiased, open
Enterprise Overview. Benefits and features of Cloudflare s Enterprise plan FLARE
 Enterprise Overview Benefits and features of s Enterprise plan 1 888 99 FLARE enterprise@cloudflare.com www.cloudflare.com This paper summarizes the benefits and features of s Enterprise plan. State of
Enterprise Overview Benefits and features of s Enterprise plan 1 888 99 FLARE enterprise@cloudflare.com www.cloudflare.com This paper summarizes the benefits and features of s Enterprise plan. State of
I'm Andy Glover and this is the Java Technical Series of. the developerworks podcasts. My guest is Brian Jakovich. He is the
 I'm Andy Glover and this is the Java Technical Series of the developerworks podcasts. My guest is Brian Jakovich. He is the director of Elastic Operations for Stelligent. He and I are going to talk about
I'm Andy Glover and this is the Java Technical Series of the developerworks podcasts. My guest is Brian Jakovich. He is the director of Elastic Operations for Stelligent. He and I are going to talk about
Is Your Data Safe In The Cloud?
 WHITE PAPER ShareFile by Citrix Sponsored by Is Your Data Safe In The Cloud? Security and data loss concerns are widespread. By Jesse Lipson VP, GM of Data Sharing ShareFile Citrix Systems, Inc. www.sharefile.com
WHITE PAPER ShareFile by Citrix Sponsored by Is Your Data Safe In The Cloud? Security and data loss concerns are widespread. By Jesse Lipson VP, GM of Data Sharing ShareFile Citrix Systems, Inc. www.sharefile.com
MARRAKECH RSSAC Public Session. MARRAKECH RSSAC Public Session Wednesday, March 09, :00 to 15:30 WET ICANN55 Marrakech, Morocco
 Wednesday, March 09, 2016 14:00 to 15:30 WET ICANN55 Marrakech, Morocco UNIDTIFIED MALE: Good afternoon, everybody. We ve got lots of room at the table if anybody wants to come up, join us. We won t put
Wednesday, March 09, 2016 14:00 to 15:30 WET ICANN55 Marrakech, Morocco UNIDTIFIED MALE: Good afternoon, everybody. We ve got lots of room at the table if anybody wants to come up, join us. We won t put
Creating and Testing Your IT Recovery Plan
 WHITEPAPER Creating and Testing Your IT Recovery Plan Regular tests of your IT disaster recovery plan can mean the difference between a temporary inconvenience or going out of business. quorum. 201 Quorum,
WHITEPAPER Creating and Testing Your IT Recovery Plan Regular tests of your IT disaster recovery plan can mean the difference between a temporary inconvenience or going out of business. quorum. 201 Quorum,
Understanding Virtual System Data Protection
 Understanding Virtual System Data Protection Server virtualization is the most important new technology introduced in the data center in the past decade. It has changed the way we think about computing
Understanding Virtual System Data Protection Server virtualization is the most important new technology introduced in the data center in the past decade. It has changed the way we think about computing
A Brief Overview. Vanessa Evans
 A Brief Overview Vanessa Evans Then Established Oct 1994 by 5 member ISPs Objective to keep UK traffic in UK Encourage co-operation amongst competitors Housed in external independent facilities Telehouse
A Brief Overview Vanessa Evans Then Established Oct 1994 by 5 member ISPs Objective to keep UK traffic in UK Encourage co-operation amongst competitors Housed in external independent facilities Telehouse
Why load test your Flex application?
 Why load test your Flex application? Your Flex application is new and exciting, but how well does it perform under load? Abstract As the trend to implement Web 2.0 technologies continues to grow and spread
Why load test your Flex application? Your Flex application is new and exciting, but how well does it perform under load? Abstract As the trend to implement Web 2.0 technologies continues to grow and spread
Understanding Managed Services
 Understanding Managed Services The buzzword relating to IT Support is Managed Services, and every day more and more businesses are jumping on the bandwagon. But what does managed services actually mean
Understanding Managed Services The buzzword relating to IT Support is Managed Services, and every day more and more businesses are jumping on the bandwagon. But what does managed services actually mean
The hidden cost of smart buildings
 Real estate The hidden cost of smart buildings Cybersecurity Risk Understanding cyber risk for asset managers and owners November 2017 Contents Section Page Asset management issues for boards 01 Smart
Real estate The hidden cost of smart buildings Cybersecurity Risk Understanding cyber risk for asset managers and owners November 2017 Contents Section Page Asset management issues for boards 01 Smart
NINE MYTHS ABOUT. DDo S PROTECTION
 NINE S ABOUT DDo S PROTECTION NINE S ABOUT DDOS PROTECTION The trajectory of DDoS attacks is clear: yearly increases in total DDoS attacks, an ever-growing number of attack vectors, and billions of potentially
NINE S ABOUT DDo S PROTECTION NINE S ABOUT DDOS PROTECTION The trajectory of DDoS attacks is clear: yearly increases in total DDoS attacks, an ever-growing number of attack vectors, and billions of potentially
Test How to Succeed in Test Automation Björn Hagström & Davor Crnomat, Testway AB
 Test How to Succeed in Test Automation Björn Hagström & Davor Crnomat, Testway AB Introduction The need for Automation Cost of Automation Plan to Automate Tools Test Approach Summary The Need for Automation
Test How to Succeed in Test Automation Björn Hagström & Davor Crnomat, Testway AB Introduction The need for Automation Cost of Automation Plan to Automate Tools Test Approach Summary The Need for Automation
cctld Best Practices & Considerations John Crain Internet Corporation for Assigned Names and Numbers
 cctld Best Practices & Considerations John Crain Internet Corporation for Assigned Names and Numbers cctld as a public trust cctlds are designated to operators who will operate them in the best interests
cctld Best Practices & Considerations John Crain Internet Corporation for Assigned Names and Numbers cctld as a public trust cctlds are designated to operators who will operate them in the best interests
Where s my DNS? Sara Dickinson IDS 2. Where s my DNS?
 Sara Dickinson sara@sinodun.com Stub to recursive The DNS protocol is evolving DoT: DNS-over-TLS DoH: DNS-over-HTTPS (WIP) DoT RFC7858 standard May 2016 Implemented to-date in standard open source DNS
Sara Dickinson sara@sinodun.com Stub to recursive The DNS protocol is evolving DoT: DNS-over-TLS DoH: DNS-over-HTTPS (WIP) DoT RFC7858 standard May 2016 Implemented to-date in standard open source DNS
You will discuss topics related to ethical hacking, information risks, and security techniques which hackers will seek to circumvent.
 IDPS Effectiveness and Primary Takeaways You will discuss topics related to ethical hacking, information risks, and security techniques which hackers will seek to circumvent. IDPS Effectiveness and Primary
IDPS Effectiveness and Primary Takeaways You will discuss topics related to ethical hacking, information risks, and security techniques which hackers will seek to circumvent. IDPS Effectiveness and Primary
TOP TEN DNS ATTACKS PROTECTING YOUR ORGANIZATION AGAINST TODAY S FAST-GROWING THREATS
 TOP TEN DNS ATTACKS PROTECTING YOUR ORGANIZATION AGAINST TODAY S FAST-GROWING THREATS 1 Introduction Your data and infrastructure are at the heart of your business. Your employees, business partners, and
TOP TEN DNS ATTACKS PROTECTING YOUR ORGANIZATION AGAINST TODAY S FAST-GROWING THREATS 1 Introduction Your data and infrastructure are at the heart of your business. Your employees, business partners, and
Independent Solution Review AppEnsure for Citrix Monitoring
 Independent Solution Review AppEnsure for Citrix Monitoring Pawel Serwan, organizer of Polish Citrix Users Group Monitoring is always one of the most important topics that you have to define during implementation
Independent Solution Review AppEnsure for Citrix Monitoring Pawel Serwan, organizer of Polish Citrix Users Group Monitoring is always one of the most important topics that you have to define during implementation
Why Machine Learning is More Likely to Cure Cancer Than to Stop Malware WHITE PAPER
 Why Machine Learning is More Likely to Cure Cancer Than to Stop Malware WHITE PAPER Introduction Machine Learning (ML) is based around the idea machines can learn from data. ML techniques have been around
Why Machine Learning is More Likely to Cure Cancer Than to Stop Malware WHITE PAPER Introduction Machine Learning (ML) is based around the idea machines can learn from data. ML techniques have been around
Hosting Provider Migrates from VMware to Hyper-V, Trims Licensing Significantly
 Hosting Provider Migrates from VMware to Hyper-V, Trims Licensing Significantly Overview Country or Region: Norway and Sweden Industry: IT services Customer Profile TeleComputing provides hosting, system
Hosting Provider Migrates from VMware to Hyper-V, Trims Licensing Significantly Overview Country or Region: Norway and Sweden Industry: IT services Customer Profile TeleComputing provides hosting, system
Top Priority for Hybrid IT
 Make Your Enterprise Network a Top Priority for Hybrid IT Hybrid IT has become a vital element in enterprises digital transformation strategy. But putting in place a hybrid IT framework is one thing, and
Make Your Enterprise Network a Top Priority for Hybrid IT Hybrid IT has become a vital element in enterprises digital transformation strategy. But putting in place a hybrid IT framework is one thing, and
3. The DNSSEC Primer. Data Integrity (hashes) Authenticated Denial of Existence (NSEC,
 3. The DNSSEC Primer Authentication (keys, signatures) Data Integrity (hashes) Chain of Trust (root zone, when signed) Authenticated Denial of Existence (NSEC, NSEC3) DNS Authoritative ROOT SERVERS TLD
3. The DNSSEC Primer Authentication (keys, signatures) Data Integrity (hashes) Chain of Trust (root zone, when signed) Authenticated Denial of Existence (NSEC, NSEC3) DNS Authoritative ROOT SERVERS TLD
I certify that this DNS record set is correct Problem: how to certify a negative response, i.e. that a record doesn t exist?
 RRSIG: I certify that this DNS record set is correct Problem: how to certify a negative response, i.e. that a record doesn t exist? NSEC: I certify that there are no DNS records (of type X) whose record
RRSIG: I certify that this DNS record set is correct Problem: how to certify a negative response, i.e. that a record doesn t exist? NSEC: I certify that there are no DNS records (of type X) whose record
2008 DNS Cache Poisoning Vulnerability Cairo, Egypt November 2008
 2008 DNS Cache Poisoning Vulnerability Cairo, Egypt November 2008 Kim Davies Manager, Root Zone Services Internet Corporation for Assigned Names & Numbers How do you attack the DNS? A typical DNS query
2008 DNS Cache Poisoning Vulnerability Cairo, Egypt November 2008 Kim Davies Manager, Root Zone Services Internet Corporation for Assigned Names & Numbers How do you attack the DNS? A typical DNS query
Securing Wireless Mobile Devices. Lamaris Davis. East Carolina University 11/15/2013
 Securing Wireless Mobile Devices Lamaris Davis East Carolina University 11/15/2013 Attract As more employees prefer to use mobile devices in the workplace, organizations are starting to adopt the Bring
Securing Wireless Mobile Devices Lamaris Davis East Carolina University 11/15/2013 Attract As more employees prefer to use mobile devices in the workplace, organizations are starting to adopt the Bring
Seifferth GmbH: Faster Prototyping with 3D Scanners
 Application Note Seifferth GmbH: Faster Prototyping with 3D Scanners Site / Country: Spechtsbrunn, Germany GOM System: ATOS Capsule GOM Software: ATOS Professional, GOM Inspect Professional Company s field
Application Note Seifferth GmbH: Faster Prototyping with 3D Scanners Site / Country: Spechtsbrunn, Germany GOM System: ATOS Capsule GOM Software: ATOS Professional, GOM Inspect Professional Company s field
IPv6 Neighbor Discovery (ND) Problems with Layer-2 Multicast State
 DRAFT IPv6 Neighbor Discovery (ND) Problems with Layer-2 Multicast State Jeff Wheeler jsw@inconcepts.biz The Problem MLD-snooping is much like IGMP-snooping but for IPv6 It keeps unnecessary multicast
DRAFT IPv6 Neighbor Discovery (ND) Problems with Layer-2 Multicast State Jeff Wheeler jsw@inconcepts.biz The Problem MLD-snooping is much like IGMP-snooping but for IPv6 It keeps unnecessary multicast
View of the Google Drive of User root: His Google Drive contains a folder named Collaborative shared with 2 colleagues (Emmanuel and AllCases)
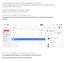 There are big differences of behavior between Google Drive and OneDrive. This article explains the main issue when migrating from Google Drive to One Drive and the solution Cloudiway offers to solve this
There are big differences of behavior between Google Drive and OneDrive. This article explains the main issue when migrating from Google Drive to One Drive and the solution Cloudiway offers to solve this
DEFENCE IN DEPTH HOW ANTIVIRUS, TRADITIONAL FIREWALLS, AND DNS FIREWALLS WORK TOGETHER
 DEFENCE IN DEPTH HOW ANTIVIRUS, TRADITIONAL FIREWALLS, AND DNS FIREWALLS WORK TOGETHER D-Zone DNS Firewall 18-10-20171 EXECUTIVE SUMMARY Cyber attacks continue to grow at an alarming rate with ransomware
DEFENCE IN DEPTH HOW ANTIVIRUS, TRADITIONAL FIREWALLS, AND DNS FIREWALLS WORK TOGETHER D-Zone DNS Firewall 18-10-20171 EXECUTIVE SUMMARY Cyber attacks continue to grow at an alarming rate with ransomware
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS. Security Without Compromise
 DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
