Virtual Private Cloud. User Guide. Issue 21 Date HUAWEI TECHNOLOGIES CO., LTD.
|
|
|
- Gervais Benson
- 5 years ago
- Views:
Transcription
1 Issue 21 Date HUAWEI TECHNOLOGIES CO., LTD.
2 Copyright Huawei Technologies Co., Ltd All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of Huawei Technologies Co., Ltd. Trademarks and Permissions and other Huawei trademarks are trademarks of Huawei Technologies Co., Ltd. All other trademarks and trade names mentioned in this document are the property of their respective holders. Notice The purchased products, services and features are stipulated by the contract made between Huawei and the customer. All or part of the products, services and features described in this document may not be within the purchase scope or the usage scope. Unless otherwise specified in the contract, all statements, information, and recommendations in this document are provided "AS IS" without warranties, guarantees or representations of any kind, either express or implied. The information in this document is subject to change without notice. Every effort has been made in the preparation of this document to ensure accuracy of the contents, but all statements, information, and recommendations in this document do not constitute a warranty of any kind, express or implied. Huawei Technologies Co., Ltd. Address: Website: Huawei Industrial Base Bantian, Longgang Shenzhen People's Republic of China support@huawei.com Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. i
3 Contents Contents 1 VPC and Subnet Network Planning Creating a VPC Modifying a VPC Creating a Subnet for the VPC Modifying a Subnet Deleting a VPC Deleting a VPN Connection Deleting a Subnet Deleting a VPC Managing VPC Tags Managing Subnet Tags Exporting VPC Information IPv4 and IPv6 Dual-Stack Network (OBT) Security Differences Between Security Groups and Network ACLs Security Group Security Group Overview Default Security Groups and Security Group Rules Creating a Security Group Adding a Security Group Rule Fast-Adding Security Group Rules Replicating a Security Group Rule Modifying a Security Group Rule Deleting a Security Group Rule Importing and Exporting Security Group Rules Deleting a Security Group Adding Instances to and Removing Them from a Security Group Viewing the Security Group of an ECS Changing the Security Group of an ECS Common Ports Used by ECSs Security Group Configuration Examples Security Group Configuration Examples Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. ii
4 Contents Enabling ECSs in Different Security Groups to Communicate with Each Other Through an Internal Network Enabling Specified IP Addresses to Remotely Access ECSs in a Security Group Remotely Connecting to Linux ECSs Using SSH Remotely Connecting to Windows ECSs Using RDP Enabling Communication Between ECSs Hosting a Website on ECSs Enabling an ECS to Function as a DNS Server Uploading or Downloading Files using FTP Network ACL Creating a Network ACL Adding a Network ACL Rule Associating Subnets with a Network ACL Disassociating a Subnet from a Network ACL Changing the Sequence of a Network ACL Rule Modifying a Network ACL Rule Enabling or Disabling a Network ACL Rule Deleting a Network ACL Rule Viewing a Network ACL Modifying a Network ACL Enabling or Disabling a Network ACL Deleting a Network ACL Elastic IP Address Assigning an EIP and Binding It to an ECS Unbinding an EIP from an ECS and Releasing the EIP Managing EIP Tags Modifying EIP Bandwidth IPv6 EIP (OBT) Shared Bandwidth Shared Bandwidth Overview Buying a Shared Bandwidth Adding EIPs to a Shared Bandwidth Removing EIPs from a Shared Bandwidth Modifying a Shared Bandwidth Deleting a Shared Bandwidth Shared Data Package Shared Data Package Overview Buying a Shared Data Package Custom Route Custom Route Overview Example Custom Route in a VPC Example Custom Route Outside a VPC Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. iii
5 Contents 6.4 Configuring an SNAT Server Adding a Route Querying a Route Modifying a Route Deleting a Route VPC Peering Connection VPC Peering Connection Creation VPC Peering Connection Configuration Plans Creating a VPC Peering Connection with Another VPC of Your Own Creating a VPC Peering Connection with a VPC of Another Tenant Viewing VPC Peering Connections Modifying a VPC Peering Connection Deleting a VPC Peering Connection Viewing Routes Configured for a VPC Peering Connection on the Peering Connection Details Page Viewing Routes Configured for a VPC Peering Connection in the VPC Peering Route Table Deleting a Route on the VPC Peering Connection Details Page Deleting a Route from the VPC Peering Route Table Direct Connect Virtual IP Address Virtual IP Address Overview Assigning a Virtual IP Address Binding a Virtual IP Address with an EIP or ECS Accessing a Virtual IP Address using an EIP Using a VPN to Access the Virtual IP Address Using a Direct Connect Connection to Access the Virtual IP Address Using a VPC Peering Connection to Access the Virtual IP Address Disabling Source and Destination Check (HA Load Balancing Cluster Scenario) Releasing a Virtual IP Address NAT gateway Monitoring Supported Metrics Viewing Metrics Creating an Alarm Rule Auditing Supported VPC Operations Viewing Audit Logs A Change History Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. iv
6 1 VPC and Subnet 1 VPC and Subnet 1.1 Network Planning Before creating VPCs, plan the number of VPCs, the number of subnets, IP address ranges, and connectivity options required based on your service requirements. How Do I Plan the Number of VPCs Required? A VPC is region-specific. By default, VPCs in different regions cannot communicate with one another through an internal network, different VPCs in the same region cannot communicate with one another through an internal network, but AZs in the same VPC can communicate with one another through an internal network. One VPC If your services do not require network isolation, you can create only one VPC. Multiple VPCs If you have multiple service environments in a region and each service environment requires an isolated network, you can create a VPC for each service environment. You can use a VPC peering connection as shown in Figure 1-1 to enable communication between two VPCs. Figure 1-1 VPC peering connection Default VPC Quota By default, you can create a maximum of five VPCs in your cloud account. If the quota cannot meet your service requirements, submit a service ticket to request quota increase. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 1
7 1 VPC and Subnet How Do I Plan Subnets? A subnet is a range of IP addresses in your VPC. All resources in a VPC must belong to specific subnets. Each subnet CIDR block (IP address range) in a VPC must be unique. After a subnet is created, its CIDR block (IP address range) cannot be modified. A VPC supports the following CIDR blocks. The subnet CIDR block must be within the VPC CIDR block, and the allowed block size is of a subnet is between a /16 netmask and /28 netmask. Table 1-1 VPC CIDR blocks CIDR Block Available Private IP Addresses (Reserved IP Addresses Not Included) ,777, ,048, ,532 Subnet Planning If you only need to plan subnets for VPCs, and communication between VPCs and infrastructure networks and between VPCs and IDCs are not required, you can create subnets within any of the preceding CIDR blocks. If your VPC needs to communicate with an on-premises IDC through a VPN or Direct Connect connection, the local IP address range (VPC CIDR block) cannot overlap with the remote IP address range (your IDC CIDR block). Therefore, when creating a VPC or subnet, ensure that the new CIDR block does not overlap with an existing CIDR block of your IDC. When determining the size of a VPC or subnet CIDR block, ensure that the number of available IP addresses on the CIDR block meet your service requirements. We recommend that you create different subnets for different service modules in a VPC. For example, you can create different subnets for web, application, and database servers. The web server is in a publicly accessible subnet, and application and database servers are in non-publically accessible subnets. You can leverage network ACLs to help control access to the servers in each subnet. Default Subnet Quota By default, you can create a maximum of 100 subnets in your cloud account. If the number of subnets cannot meet your service requirements, submit a service ticket to request quota increase. How Do I Plan Routing Policies? A route table contains a set of rules, called routes, that are used to control where inbound and outbound subnet traffic is forwarded in a VPC. When you create a VPC, it automatically has a default route table, which enables internal communication within a VPC. If you do not need to explicitly control how each subnet routes inbound and outbound traffic, you can use the default route table and do not configure custom routes. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 2
8 1 VPC and Subnet If you need to explicitly control how each subnet routes inbound and outbound traffic in a VPC, you can add custom routes to the route table. How Do I Connect to an On-Premises IDC If you require interconnection between a VPC and an on-premises IDC, ensure that the VPC does not have a matching or overlapping IP address range with the on-premises IDC to be connected. The following figure shows that VPC 1 is in North China and that VPC 2 and VPC 3 are in East China. VPC 1 needs to connect to the user IDC in Beijing through a VPN connection that routes traffic over the Internet. VPC 2 needs to connect to the user IDC in Shanghai through a Direct Connect connection. In addition, VPC 2 and VPC 3 in the East China region need to communicate with each other through a VPC peering connection. Figure 1-2 Connections to on-premises IDCs Note the following when planning CIDR blocks for VPC 1, VPC 2, and VPC 3. The CIDR block of VPC 1 cannot overlap with the CIDR blocks of the user IDC in Beijing. The CIDR block of VPC 2 cannot overlap with the CIDR blocks of the IDC in Shanghai. The CIDR blocks of VPC 2 and VPC 3 cannot overlap. How Do I Access the Internet? Use EIPs to enable a small number of ECSs to access the Internet. When only a few ECSs need to access the Internet, you can bind the EIPs to the ECSs. Then, the ECSs can connect to the Internet. You can dynamically unbind the EIPs from the ECSs and bind the EIPs to NAT gateways and load balancers to enable them to access the Internet. EIP management is easy. Different EIPs can use the same shared bandwidth, reducing your bandwidth costs. Use NAT gateways to enable a large number of ECSs to access the Internet. When a large number of ECSs need to access the Internet, the public cloud system provides network address translation (NAT) gateways for the ECSs. With NAT gateways, you do not Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 3
9 1 VPC and Subnet need to assign an EIP to each ECS, which reduces management costs incurred by an excessive number of EIPs. A NAT gateway offers both the source network address translation (SNAT) and destination network address translation (DNAT) functions. SNAT allows multiple ECSs in the same VPC to share one or more EIPs to access the Internet. The SNAT function reduces management costs and prevents the EIPs of ECSs from being exposed to the Internet. SNAT supports a maximum of 1 million concurrent connections and 30,000 new connections. DNAT can implement port-level data forwarding. It maps EIP ports to ECS ports to enable the ECSs in a VPC to share the same EIP and bandwidth to provide Internet-accessible services. Use ELB to access the Internet If there are a large number of highly concurrent requests. In high-concurrency scenarios, such as e-commerce, you can use load balancers provided by the ELB service to evenly distribute access traffic across multiple ECSs, allowing a large number of users to concurrently access your business system or application. ELB is deployed in cluster mode and provides fault tolerance for your applications by automatically balancing traffic across multiple availability zones (AZs). You can also take advantage of deep integration with the Auto Scaling (AS) service, which enables automatic scaling based on service traffic and ensures service stability and reliability. Use VPN or Direct Connect to extend your self-hosted IDC into the cloud over the Internet. For customers with self-hosted IDC equipment rooms, not all businesses of the customers will be migrated to the cloud because the customers want to reuse their legacy devices and require smooth business evolution. Then, you can use VPN or Direct Connect to interconnect your VPC and on-premises IDC. A VPN connection routes traffic through the Internet, which allows you to use a private network with the price of the public network. A Direct Connect connection is a dedicated, private network connection that provides you with more efficient data transmission and more consistent network experience than Internet-based connections. 1.2 Creating a VPC A VPC provides an isolated virtual network for ECSs. You can configure and manage the network as required. When creating a VPC, you can create one or more subnets as required. 3. On the console homepage, under Network, click. 4. On the Dashboard page, click Create VPC. 5. On the Create VPC page, set parameters as prompted. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 4
10 1 VPC and Subnet Table 1-2 VPC parameter description Parameter Description Example Value Region Specifies the desired region. Regions are geographic areas isolated from each other. Resources are region-specific and cannot be used across regions through internal network connections. For low network latency and quick resource access, select the nearest region. CN North-Beijing1 Name Specifies the VPC name. VPC-001 CIDR Block Enterprise Project Tag Specifies the CIDR block for the VPC. The CIDR block of a subnet can be the same as the CIDR block for the VPC (for a single subnet in the VPC) or a subset (for multiple subnets in the VPC). The following CIDR blocks are supported: Specifies the enterprise project to which the VPC belongs. By default, the VPC belongs to the Default project. Specifies the VPC tag, which consists of a key and value pair. You can add a maximum of ten tags to each VPC. The tag key and value must meet the requirements listed in Table /16 Default Key: vpc_key1 Value: vpc-01 Name Specifies the subnet name. Subnet CIDR Block Gateway Specifies the CIDR block for the subnet. This value must be within the VPC CIDR range. Specifies the gateway address of the subnet / Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 5
11 1 VPC and Subnet Parameter Description Example Value DNS Server Address Tag The external DNS server address is used by default. If you need to change the DNS server address, ensure that the configured DNS server address is available. Specifies the subnet tag, which consists of a key and value pair. You can add a maximum of ten tags to each subnet. The tag key and value must meet the requirements listed in Table Key: subnet_key1 Value: subnet-01 Table 1-3 VPC tag key and value requirements Parameter Requirements Example Value Key Value Cannot be left blank. Must be unique for the same VPC and can be the same for different VPCs. Can contain a maximum of 36 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. Can contain a maximum of 43 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. vpc_key1 vpc-01 Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 6
12 1 VPC and Subnet Table 1-4 Subnet tag key and value requirements Parameter Requirements Example Value Key Value Cannot be left blank. Must be unique for each subnet. Can contain a maximum of 36 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. Can contain a maximum of 43 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. subnet_key1 subnet Confirm the current configuration and click Create Now. 1.3 Modifying a VPC If the VPC CIDR block conflicts with the subnet CIDR block of a VPN created in the VPC, you can modify the VPC to change its CIDR range. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the row that contains the VPC to be modified and click Modify in the Operation column. 6. In the displayed dialog box, modify parameters as prompted. You can change the VPC name and VPC CIDR block. Figure 1-3 shows the page for you to modify a VPC. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 7
13 1 VPC and Subnet Figure 1-3 Modifying a VPC 7. Click OK. 1.4 Creating a Subnet for the VPC You can add subnets during VPC creation. If required, you can also create subnets for an existing VPC. The created subnet is configured with DHCP by default. After an ECS using this VPC starts, the ECS automatically obtains an IP address using DHCP. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the VPC for which a subnet is to be created and click the VPC name. 6. On the displayed Subnets tab, click Create Subnet. 7. In the Create Subnet area, set parameters as prompted. Table 1-5 Parameter description Parameter Description Example Value Name Specifies the subnet name. Subnet CIDR Block Specifies the CIDR block for the subnet. This value must be within the VPC CIDR range /24 Gateway Specifies the gateway address of the subnet Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 8
14 1 VPC and Subnet Parameter Description Example Value Tag Specifies the subnet tag, which consists of a key and value pair. You can add a maximum of ten tags to each subnet. The tag key and value must meet the requirements listed in Table 1-6. Key: subnet_key1 Value: subnet-01 Table 1-6 Subnet tag key and value requirements Parameter Requirements Example Value Key Value Cannot be left blank. Must be unique for each subnet. Can contain a maximum of 36 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. Can contain a maximum of 43 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. subnet_key1 subnet The external DNS server address is used by default. If you need to change the DNS server address, select Custom for Advanced Settings and configure the DNS server addresses. You must ensure that the configured DNS server addresses are available. 9. Click OK. Precautions After a subnet is created, five IP addresses in the subnet will be reserved and cannot be used. For example, in a subnet with CIDR block /24, the following IP addresses are reserved: : Network address : Gateway address : Reserved for the system interface. This IP address is used by the VPC for external communication : DHCP service address : Network broadcast address. If you set Advanced Settings to Custom during subnet creation, the reserved IP addresses may be different from the preceding default ones. The system will reserve five IP addresses based on your subnet settings. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 9
15 1 VPC and Subnet 1.5 Modifying a Subnet If the DHCP policy or DNS server address configured for a subnet during subnet creation needs to be modified, you can modify the subnet. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the VPC for which a subnet is to be modified and click the VPC name. 6. In the subnet list, locate the target subnet and click Modify. Modify the parameters as prompted in the dialog box shown in Figure 1-4. Figure 1-4 Modify Subnet Table 1-7 Parameter description Parameter Description Example Value Name Specifies the subnet name. Subnet DNS Server Address 1 Specifies the IP address of DNS server 1. You can leave it blank. By default, the external DNS server address is used. N/A Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 10
16 1 VPC and Subnet Parameter Description Example Value DNS Server Address 2 Specifies the IP address of DNS server 2. You can leave it blank. By default, the external DNS server address is used. N/A 7. Click OK. 1.6 Deleting a VPC Deleting a VPN Connection Deleting a Subnet Prerequisites You can delete a VPN connection to release network resources if it is no longer required. 2. On the console homepage, under Network, click Virtual Private Network. 3. In the navigation pane on the left, choose Virtual Private Network > VPN Connections. 4. On the VPN Connection page, locate the target VPN connection and click Delete. 5. Click OK in the displayed dialog box. You can delete a subnet to release network resources if the subnet is no longer required. A subnet cannot be deleted if it is being used by an ECS, VPN, or private IP address. To delete a subnet in these cases, you must first delete the ECS, VPN, or private IP address. The following resources using the subnet have been deleted: ECS BMS CCE cluster RDS instance Workspace MRS cluster DCS instance Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 11
17 1 VPC and Subnet Elastic load balancer VPN Private IP address Custom route NAT gateway Check and delete related resources on the management console Deleting a VPC Impact on the System 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the VPC from which a subnet is to be deleted and click the VPC name. 6. On the Subnet page, locate the target subnet and click Delete. 7. Click OK in the displayed dialog box. You can delete a VPC to release network resources if the VPC is no longer required. A VPC cannot be deleted if it contains subnets, Direct Connect connections, custom routes, VPC peering connections, or VPNs. To delete the VPC, you must first delete the resources. For details about how to delete a subnet, see Deleting a Subnet. For details about how to delete a VPN, see Deleting a VPN Connection. For details about how to disable a Direct Connect connection, see the Direct Connect. For details about how to delete a custom route, see 6.8 Deleting a Route. For details about how to delete a VPC peering connection, 7.7 Deleting a VPC Peering Connection. If EIPs exist, the last VPC cannot be deleted. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the row that contains the VPC to be deleted and click Delete in the Operation column. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 12
18 1 VPC and Subnet 6. Click OK in the displayed dialog box. 1.7 Managing VPC Tags A VPC tag identifies a VPC. Tags can be added to VPCs to facilitate VPC identification and administration. You can add a tag to a VPC when creating the VPC. Alternatively, you can add a tag to a created VPC on the VPC details page. A maximum of ten tags can be added to each VPC. A tag consists of a key and value pair. Table 1-8 lists the tag key and value requirements. Table 1-8 VPC tag key and value requirements Parameter Requirements Example Value Key Value Cannot be left blank. Must be unique for the same VPC and can be the same for different VPCs. Can contain a maximum of 36 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. Can contain a maximum of 43 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. vpc_key1 vpc-01 Search for VPCs by Tag Key and Value on the Page Showing the VPC List. 3. Under Network, click. 4. In the navigation pane on the left, click. 5. In the upper right corner of the VPC list, click Search by Tag. 6. In the displayed area, enter the tag key and value of the VPC you are looking for. Both the tag key and value must be specified. The system automatically displays the VPCs you are looking for if both the tag key and value are matched. 7. Click + to add the entered tag key and value. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 13
19 1 VPC and Subnet You can add multiple tag keys and values to refine your search results. If you add more than one tag to search for VPCs, the VPCs containing all specified tags will be displayed. 8. Click Search. The system displays the VPCs you are looking for based on the entered tag keys and values. Add, Delete, Edit, and View Tags on the Tags Tab of a VPC. 3. Under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the VPC whose tags are to be managed and click the VPC name. The page showing details about the particular VPC is displayed. 6. Click the Tags tab and perform desired operations on tags. View tags. On the Tags tab, you can view details about tags added to the current VPC, including the number of tags and the key and value of each tag. Add a tag. Click Add Tag in the upper left corner. In the displayed Add Tag dialog box, enter the tag key and value, and click OK. Edit a tag. Locate the row that contains the tag to be edited, and click Edit in the Operation column. Enter the new tag key and value, and click OK. Delete a tag. 1.8 Managing Subnet Tags Locate the row that contains the tag to be deleted, and click Delete in the Operation column. In the displayed Delete Tag dialog box, click OK. A subnet tag identifies a subnet. Tags can be added to subnets to facilitate subnet identification and administration. You can add a tag to a subnet when creating the subnet. Alternatively, you can add a tag to a created subnet on the subnet details page. A maximum of ten tags can be added to each subnet. A tag consists of a key and value pair. Table 1-9 lists the tag key and value requirements. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 14
20 1 VPC and Subnet Table 1-9 Subnet tag key and value requirements Parameter Requirements Example Value Key Value Cannot be left blank. Must be unique for each subnet. Can contain a maximum of 36 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. Can contain a maximum of 43 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. subnet_key1 subnet-01 Search for subnets by Tag Key and Value on the Page Showing the subnet List. 3. Under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the VPC containing the target subnet and click the VPC name. 6. In the upper right corner of the subnet list, click Search by Tag. 7. Enter the tag key of the subnet to be queried. Both the tag key and value must be specified. The system automatically displays the subnets you are looking for if both the tag key and value are matched. 8. Click + to add the entered tag key and value. You can add multiple tag keys and values to refine your search results. If you add more than one tag to search for subnets, the subnets containing all specified tags will be displayed. 9. Click Search. The system displays the subnets you are looking for based on the entered tag keys and values. Add, Delete, Edit, and View Tags on the Tags Tab of a Subnet. 3. Under Network, click. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 15
21 1 VPC and Subnet 4. In the navigation pane on the left, click. 5. On the page, locate the VPC containing the target subnet and click the VPC name. 6. Click the name of the target subnet. 7. On the subnet details page, click the Tags tab and perform desired operations on tags. View tags. On the Tags tab, you can view details about tags added to the current subnet, including the number of tags and the key and value of each tag. Add a tag. Click Add Tag in the upper left corner. In the displayed Add Tag dialog box, enter the tag key and value, and click OK. Edit a tag. Locate the row that contains the tag to be edited, and click Edit in the Operation column. Enter the new tag key and value, and click OK. Delete a tag. Locate the row that contains the tag to be deleted, and click Delete in the Operation column. In the displayed Delete Tag dialog box, click OK. 1.9 Exporting VPC Information Information about all VPCs under your account can be exported as an Excel file to a local directory. This file records the names, ID, status, IP address ranges of VPCs, and the number of subnets. 3. Under Network, click. 4. In the navigation pane on the left, click. 5. In the upper right corner of the VPC list, click. The system will automatically export information about all VPCs under your account in the current region as an Excel file to a local directory IPv4 and IPv6 Dual-Stack Network (OBT) Overview IPv4 and IPv6 dual-stack allows your resources, such as ECSs, to use both the IPv4 and IPv6 addresses for private and public network communication. Private IPv4 addresses are used for internal access between ECSs. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 16
22 1 VPC and Subnet Application EIPs can be bound to private IPv4 addresses for Internet access. IPv6 addresses are used for internal access between ECSs in the same VPC that have both IPv4 and IPv6 addresses. IPv6 addresses are used to access IPv6 networks on the Internet. If your application needs to provide services for users who use IPv6 clients, you can use IPv6 EIPs or the IPv4 and IPv6 dual-stack function. If your application needs to both provide services for users who use IPv6 clients and analyze the access request data, you can use only the IPv4 and IPv6 dual-stack function. If internal communication is required between your application systems or between your application system and another system (such as the database system), you can use only the IPv4 and IPv6 dual-stack function. Applying to Participate in the IPv6 Address (Open Beta Test) OBT The IPv6 address function is now in the OBT. To apply to participate in the OBT, you can click under Network on the console homepage and click Try Now on the page shown in Figure 1-5. After your application is approved, you can use both IPv4 and IPv6 addresses. Figure 1-5 Participating in the OBT Basic Operations NOTE The basic operations for IPv4 and IPv6 dual-stack networks are the same as those for IPv4 networks. Only some parameters are different. You can check the console pages for details. Creating an IPv6 Subnet Create an IPv6 subnet by following the instructions provided in 1.4 Creating a Subnet for the VPC. You must ensure that Enable is selected for IPv6 CIDR Block. An IPv6 CIDR block will be automatically assigned to the subnet. IPv6 cannot be disabled after the subnet is created. Currently, you are not allowed to specify a custom IPv6 CIDR block. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 17
23 1 VPC and Subnet Figure 1-6 Creating an IPv6 subnet Viewing In-Use IPv6 Addresses In the subnet list, click the target subnet name. On the displayed page, view in-use IPv6 addresses on the In-Use IP Addresses tab. Adding a Security Group Rule (IPv6) Add a security group rule with Type set to IPv6 and Source or Destination set to an IPv6 address or IPv6 CIDR block. Figure 1-7 Adding a security group rule (IPv6) Adding a Network ACL Rule (IPv6) Add a network ACL rule with Type set to IPv6 and Source and Destination set to IPv6 addresses or IPv6 CIDR blocks. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 18
24 1 VPC and Subnet Figure 1-8 Adding a network ACL rule (IPv6) Purchasing an EIP (IPv6) You can purchase an IPv6 EIP or convert an IPv4 EIP into an IPv6 EIP. For details, see 3.5 IPv6 EIP (OBT). Adding an IPv6 EIP or Dual-Stack NIC IPv6 Address to a Shared Bandwidth Add an IPv6 EIP or dual-stack NIC IPv6 address to a shared bandwidth by following the instructions provided in 4.3 Adding EIPs to a Shared Bandwidth. Figure 1-9 Adding a dual-stack NIC IPv6 address to a shared bandwidth Adding a Route (IPv6) Add a route with Destination set to an IPv6 address and Next Hop set to an IPv6 address or CIDR block. For details about how to add a route, see 6.5 Adding a Route. If the destination is an IPv6 CIDR block, the next hop can only be an IP address in the same VPC as the IPv6 CIDR block. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 19
25 1 VPC and Subnet Figure 1-10 Add Route Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 20
26 2 Security 2 Security 2.1 Differences Between Security Groups and Network ACLs You can configure security groups and network ACLs to increase the security of ECSs in your VPC. Figure 2-1 shows how security groups and network ACLs work in a VPC. Security groups protect ECSs. Network ACLs protect subnets. Figure 2-1 Security groups and network ACLs Table 2-1 describes the differences between security groups and network ACLs. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 21
27 2 Security Table 2-1 Differences between security groups and network ACLs Category Security Group Network ACL Targets Operates at the ECS level. Operates at the subnet level. Rules Only supports Allow rules. Supports Allow and Deny rules. Priority How to Use Packets If security group rules conflict, the overlapping elements of these rules take effect. Automatically applies to ECSs in the security group that is selected during ECS creation. You must select a security group when creating ECSs. Only supports packet filtering based on the 3-tuple (protocol, port, and peer IP address). If network ACL rules conflict, the rule with the highest priority takes effect. Applies to all ECSs in the subnets associated with the network ACL. Selecting a network ACL is not allowed during subnet creation. You must create a network ACL, associate subnets with it, add inbound and outbound network rules, and enable network ACL. The network ACL then takes effect for the associated subnets and ECSs in the subnets. Only supports packet filtering based on the 5-tuple (protocol, source port, destination port, source IP address, and destination IP address). 2.2 Security Group Security Group Overview Security Group Basics A security group is a collection of access control rules for ECSs that have the same security protection requirements and are mutually trusted in a VPC. After a security group is created, you can create different access rules for the security group to protect the ECSs that are added to this security group. Your account automatically comes with a default security group. The default security group allows all outbound traffic, denies all inbound traffic, and allows all traffic between ECSs in the group. Your ECSs in the security group can communicate with each other without the need to add rules. You can directly use the default security group. For details, see Default Security Groups and Security Group Rules. You can also create custom security groups to meet your specific service requirements. For details, see Creating a Security Group. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 22
28 2 Security Security Group Rules Security Group Constraints After a security group is created, you can add rule to or remove them from the security group. A rule applies either to inbound traffic (ingress) or outbound traffic (egress). After ECSs are added to the security group, they are protected by the security group rules. Each security group has default rules. For details, see Table 2-2. You can also customize security group rules. For details, see Adding a Security Group Rule. By default, you can create a maximum of 100 security groups in your cloud account. By default, each security group can have a maximum of 50 security group rules. By default, an ECS or an ECS extension NIC can be added to a maximum of five security groups. When creating a private network load balancer, you need to select a desired security group. Do not delete the default security group rules or ensure that the following requirements are met: Outbound rule: allows only data packets to the selected security group or only data packets from the peer load balancer. Inbound rule: allows only data packets from the selected security group or only data packets from the peer load balancer Default Security Groups and Security Group Rules Your account automatically comes with a default security group. The default security group allows all outbound traffic, denies all inbound traffic, and allows all traffic between ECSs in the group. Your ECSs in the security group can communicate with each other without the need to add rules. Figure 2-2 shows the default security group. Figure 2-2 Default security group Table 2-2 describes the default rules for a default security group. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 23
29 2 Security Table 2-2 Default security group rules Transfer Direction Protocol Port/Range Source/Destination Description Outbound All All Destination: /0 Allow all outbound traffic. Inbound All All Source: ID of the current security group (for example, sgxxxxx) Allow communication among ECSs within the security group and deny all inbound traffic (incoming data packets). Inbound TCP 22 Source: /0 Allow all IP addresses to access Linux ECSs over SSH. Inbound TCP 3389 Source: /0 Allow all IP addresses to access Windows ECSs over RDP Creating a Security Group To improve ECS access security, you can create a security group, define security group rules, and add ECSs in the VPC to the security group. We recommend that you allocate ECSs that have different Internet access policies to different security groups. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Security Group. 5. On the Security Group page, click Create Security Group. 6. In the Create Security Group area, set the parameters as prompted. Table 2-3 lists the parameters to be configured. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 24
30 2 Security Table 2-3 Parameter description Parameter Description Example Value Name Enterprise Project Description Specifies the security group name. This parameter is mandatory. The security group name can contain a maximum of 64 characters, which may consist of letters, digits, underscores (_), hyphens (-), and periods (.). The name cannot contain spaces. NOTE You can change the security group name after a security group is created. It is recommended that you use different names for different security groups. Specifies the enterprise project to which the security group belongs. By default, the security group belongs to the Default project. Provides supplementary information about the security group. This parameter is optional. The security group description can contain a maximum of 255 characters and cannot contain angle brackets (<) or (>). sg-318b Default N/A 7. Click OK Adding a Security Group Rule After a security group is created, you can add rule to or remove them from the security group. A rule applies either to inbound traffic (ingress) or outbound traffic (egress). After ECSs are added to the security group, they are protected by the security group rules. Inbound rules control incoming traffic to ECSs in the security group. Outbound rules control outgoing traffic from ECSs in the security group. For details about security group rule configuration examples, see Security Group Configuration Examples. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Security Group. 5. On the Security Group page, locate the target security group and click Manage Rule in the Operation column to switch to the page for managing inbound and outbound rules. 6. On the inbound rule tab, click Add Rule. In the displayed dialog box, set required parameters to add an inbound rule. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 25
31 2 Security You can click + to add more inbound rules. Figure 2-3 Add Inbound Rule Table 2-4 Inbound rule parameter description Parameter Description Example Value Protocol/Application Specifies the network protocol. TCP Port & Source Description Port: specifies the port or port range over which the traffic that can reach your ECS. The value ranges from 1 to For details about common ports, see Common Ports Used by ECSs. Source: specifies the source of the security group rule. The value can be another security group, a CIDR block, or a single IP address. For example: xxx.xxx.xxx.xxx/32 (IPv4 address) xxx.xxx.xxx.0/24 (CIDR block) /0 (any IP address) Provides supplementary information about the security group rule. This parameter is optional. The security group description can contain a maximum of 255 characters and cannot contain angle brackets (<) or (>). 22 or /0 default N/A 7. On the outbound rule tab, click Add Rule. In the displayed dialog box, set required parameters to add an outbound rule. You can click + to add more outbound rules. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 26
32 2 Security Figure 2-4 Add Outbound Rule Table 2-5 Outbound rule parameter description Parameter Description Example Value Protocol/Application Specifies the network protocol. TCP Port & Destination Description Port: specifies the port or port range over which the traffic that can leave your ECS. The value ranges from 1 to For details about common ports, see Common Ports Used by ECSs. Destination: specifies the destination of the security group rule. The value can be another security group, a CIDR block, or a single IP address. For example: xxx.xxx.xxx.xxx/32 (IPv4 address) xxx.xxx.xxx.0/24 (CIDR block) /0 (any IP address) Provides supplementary information about the security group rule. This parameter is optional. The security group description can contain a maximum of 255 characters and cannot contain angle brackets (<) or (>). 22 or /0 default N/A Verification After required security group rules are added, you can verify that the rules take effect. For example, you have deployed a website on ECSs. Users need to access your website over HTTP and port 80, and you have added the security group rule shown in Table 2-6. Table 2-6 Security group rule Protocol/Application Transfer Direction Port/Range Source TCP Inbound 80 (HTTP) /0 Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 27
33 2 Security Linux ECS Perform the following steps to verify the security group rule on a Linux ECS: 1. Log in to the ECS. 2. Run the following command to check whether TCP port 80 is monitored: netstat -an grep 80 If command output shown in Figure 2-5 is displayed, TCP port 80 is monitored. Figure 2-5 Command output for the Linux ECS 3. Enter EIP in the address box of the browser and press Enter. The security group rule takes effect if the requested page can be accessed. Windows ECS Perform the following steps to verify the security group rule on a Windows ECS: 1. Log in to the ECS. 2. Choose Start > Accessories > Command Prompt. 3. Run the following command to check whether TCP port 80 is monitored: netstat -an findstr 80 If command output shown in Figure 2-6 is displayed, TCP port 80 is monitored. Figure 2-6 Command output for the Windows ECS 4. Enter EIP in the address box of the browser and press Enter. The security group rule takes effect if the requested page can be accessed Fast-Adding Security Group Rules Quickly add multiple security group rules with different protocols and ports. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Security Group. 5. On the Security Group page, locate the target security group and click Manage Rule in the Operation column to switch to the page for managing inbound and outbound rules. 6. On the inbound rule tab, click Fast-Add Rule. In the displayed dialog box, select required protocols and ports to add multiple rules at a time. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 28
34 2 Security Figure 2-7 Fast-Add Inbound Rule 7. On the outbound rule tab, click Fast-Add Rule. In the displayed dialog box, select required protocols and ports to add multiple rules at a time. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 29
35 2 Security Figure 2-8 Fast-Add Outbound Rule Replicating a Security Group Rule Replicate an existing security group rule to generate a new rule. When replicating a security group rule, you can modify it. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Security Group. 5. On the Security Group page, click the security group name. 6. On the displayed page, locate the row that contains the security group rule to be replicated, and click Replicate in the Operation column. You can modify the security group rule as required to quickly generate a new rule. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 30
36 2 Security Modifying a Security Group Rule Modify an existing security group rule. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Security Group. 5. On the Security Group page, click the security group name. 6. On the displayed page, locate the row that contains the security group rule to be modified, and click Modify in the Operation column Deleting a Security Group Rule If the source of an inbound security group rule or destination of an outbound security group rule needs to be changed, you can first delete the security group rule and add a new one. NOTE Security group rules use the whitelist mechanism. After security group rules are deleted, ECS access failures may occur. You must exercise caution when deleting security group rules. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Security Group. 5. On the Security Group page, click the security group name. 6. If you do not need a security group rule, locate the row that contains the target rule, and click Delete. 7. Click OK in the displayed dialog box. Delete Multiple Security Group Rules at a Time. You can also select multiple security group rules and click Delete above the security group rule list to delete multiple rules at a time Importing and Exporting Security Group Rules If you want to quickly apply the rules of a security group to another security group or modify multiple rules of the current security group at a time, you can import and export the rules. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 31
37 2 Security Inbound and outbound security group rules are exported to an Excel file. NOTE When modifying exported security group rules, you can only modify existing fields in the exported file and cannot add new fields or modify the field names. Otherwise, the exported file cannot be imported into the system. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Security Group. 5. On the Security Group page, click the security group name. 6. On the displayed page, export and import security group rules. Click to export all rules of the current security group to an Excel file. Click to import security group rules in an Excel file to the current security group Deleting a Security Group You can delete a security group to release resources if the security group is no longer required. NOTE The default security group cannot be deleted. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the Security Group page, locate the target security group, and click Delete. 6. Click OK in the displayed dialog box Adding Instances to and Removing Them from a Security Group After a security group is created, you can add instances, including servers and extension NICs, to the security group to protect the instances. If the instances are not required, you can also remove them from the security group. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 32
38 2 Security You can add multiple instances to or remove them from a security group. Adding Instances to a Security Group 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Security Group. 5. On the Security Group page, click Manage Instance in the Operation column. 6. On the Servers tab, click Add and add one or more servers to the current security group. 7. On the Extension NICs tab, click Add and add one or more extension NICs to the current security group. Removing Instances from a Security Group 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Security Group. 5. On the Security Group page, click Manage Instance in the Operation column. 6. On the Servers tab, locate the target server and click Remove in the Operation column to remove the server from current security group. 7. On the Extension NICs tab, locate the target extension NIC and click Remove in the Operation column to remove the NIC from the current security group. Removing multiple instances from a security group Select multiple servers and click Remove above the server list to remove multiple servers from the current security group at a time. Select multiple extension NICs and click Remove above the extension NIC list to remove the extension NICs from the current security group at a time Viewing the Security Group of an ECS View inbound and outbound rules of a security group used by an ECS. 3. Under Computing, click Elastic Cloud Server. 4. In the ECS list, click the name of the target ECS. 5. Click the Security Groups tab and view information about the security group used by the ECS. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 33
39 2 Security Changing the Security Group of an ECS Change the security group associated with an ECS NIC. 3. Under Computing, click Elastic Cloud Server. 4. In the ECS list, click the name of the target ECS. 5. Click the Security Groups tab. Then, click Change Security Group. 6. Select the new security group to be associated with the ECS NIC. You can select multiple security groups. In such a case, the access rules of all the selected security groups apply on the ECS. NOTE 7. Click OK. Using multiple security groups may deteriorate ECS network performance. We recommend that you select no more than five security groups for each ECS Common Ports Used by ECSs Table 2-7 lists the common ports used by ECSs. You can configure security group rules to allow traffic to and from specified ECS ports. For details, see Adding a Security Group Rule. Table 2-7 Common ports used by ECSs Protocol Port Description FTP 21 An FTP port used to upload and download files SSH 22 An SSH port used to remotely connect to Linux ECSs Telnet 23 A port used to remotely log in to ECSs using Telnet HTTP 80 A port used to access websites over HTTP POP3 110 A port used to receive s using Post Office Protocol version 3 (POP3) IMAP 143 A port used to receive s using Internet Message Access Protocol (IMAP) HTTPS 443 A port used to access websites over HTTPS SQL Server 1433 A TCP port of the Microsoft SQL Server for providing services SQL Server 1434 A UDP port of the Microsoft SQL Server for returning the TCP/IP port number used by the SQL Server Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 34
40 2 Security Protocol Port Description Oracle 1521 Oracle database communications port, which must be enabled on the ECSs where Oracle SQL Server is deployed MySQL 3306 A port used by MySQL databases to provide services Windows Server Remote Desktop Services 3389 Windows Server Remote Desktop Services port, which can be used to connect to Windows ECSs Proxy 8080 Proxy port 8080 used in the WWW proxy service for web browsing. If you use port 8080, you need to add :8080 after the IP address when you visit a website or use a proxy server. After Apache Tomcat is installed, the default service port is NetBIOS 137, 138, and 139 NetBIOS is often used for Windows files, printer sharing, and Samba. Ports 137 and 138: UDP ports that are used when transferring files using Network Neighborhood (My Network Places) Port 139: Connections from this port try to access the NetBIOS/SMB service. Some Ports Inaccessible Symptom: Users in some areas cannot access some ports in the public cloud system. Analysis: Ports listed in the following table are high-risk ports and are blocked by default. Table 2-8 High-risk ports Protocol Port TCP 42, 135, 137, 138, 139, 444, 445, 593, 1025, 1068, 1434, 3127, 3128, 3129, 3130, 4444, 5554, 5800, 5900, and 9996 UDP 135 to 139, 1026, 1027, 1028, 1068, 1433, 1434, 5554, and 9996 Solution: It is recommended that you use ports not listed in the table for your services. 2.3 Security Group Configuration Examples Security Group Configuration Examples Common security group configuration examples are as follows: Enable ECSs in different security groups to communicate with each other through an internal network. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 35
41 2 Security In this scenario, resources on an ECS in a security group need to be copied to another ECS in another security group. The two ECSs are in the same VPC. We recommend that you enable internal network communication between the ECSs and then copy resources. For details about security group configuration, see Enabling ECSs in Different Security Groups to Communicate with Each Other Through an Internal Network. Enable specified IP addresses to remotely access ECSs in a security group. To prevent ECSs from being attacked, you can change the port number for remote login and configure security group rules that allow only specified IP addresses to remotely access the ECSs. For details about security group configuration, see Enabling Specified IP Addresses to Remotely Access ECSs in a Security Group. Remotely connecting to Linux ECSs using SSH. After creating Linux ECSs, you can add a security group rule to enable remote SSH access to the Linux ECSs. For details about security group configuration, see Remotely Connecting to Linux ECSs Using SSH. Remotely connecting to Windows ECSs using RDP. After creating Windows ECSs, you can add a security group rule to enable remote RDP access to the Windows ECSs. For details about security group configuration, see Remotely Connecting to Windows ECSs Using RDP. Enabling communication between ECSs. After creating ECSs, you need to add a security group rule so that you can run the ping command to test communication between the ECSs. For details about security group configuration, see Enabling Communication Between ECSs. Host a website on ECSs. If you deploy a website on your ECSs and require that your website be accessed over HTTP or HTTPS, you can add the following rules to the security group used by the ECSs functions as the web servers. For details about security group configuration, see Hosting a Website on ECSs. Enable an ECS to function as a DNS server. If you need to use an ECS as the DNS server, you must allow TCP and UDP access from port 53 to the DNS server. You can add the following rules to the security group used by your ECS. For details about security group configuration, see Enabling an ECS to Function as a DNS Server. Upload or download files using FTP. If you want to use File Transfer Protocol (FTP) to upload files to or download files from ECSs, you need to add a security group rule. For details about security group configuration, see Uploading or Downloading Files using FTP. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 36
42 2 Security Enabling ECSs in Different Security Groups to Communicate with Each Other Through an Internal Network Example scenario: In this scenario, resources on an ECS in a security group need to be copied to another ECS in another security group. The two ECSs are in the same VPC. We recommend that you enable internal network communication between the ECSs and then copy resources. Security group configuration: In the same VPC, ECSs in the same security group can communicate with one another by default, and no additional configuration is required. However, ECSs in different security groups cannot communicate with each other by default. You must add security group rules to enable the ECSs to communicate with one another through an internal network. You can add an inbound rule to each security group containing the ECSs to allow access from ECSs in the other security group. The security group rule is as follows. Protocol Transfer Direction Port Range/ICMP Type Source Protocol to be used for internal network communication. Supported values are TCP, UDP, ICMP, and All. Inbound Port number, port number range, or ICMP protocol type IPv4 address, IPv4 CIDR block, or ID of another security group Enabling Specified IP Addresses to Remotely Access ECSs in a Security Group Example scenario: To prevent ECSs from being attacked, you can change the port number for remote login and configure security group rules that allow only specified IP addresses to remotely access the ECSs. Security group configuration: To allow IP address to remotely access Linux ECSs in a security group over the SSH protocol and port 22, you can configure the following security group rule. Protocol Transfer Direction Port/Range Source SSH (22) Inbound 22 IPv4 address, IPv4 CIDR block, or ID of another security group For example, Remotely Connecting to Linux ECSs Using SSH Example scenario: Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 37
43 2 Security After creating Linux ECSs, you can add a security group rule to enable remote SSH access to the Linux ECSs. NOTE The default security group comes with this rule. If you use the default security group, you do not need to configure the rule again. Security group configuration: Protocol Transfer Direction Port/Range Source SSH (22) Inbound / Remotely Connecting to Windows ECSs Using RDP Example scenario: After creating Windows ECSs, you can add a security group rule to enable remote RDP access to the Windows ECSs. NOTE The default security group comes with this rule. If you use the default security group, you do not need to configure the rule again. Security group configuration: Protocol Transfer Direction Port/Range Source RDP (3389) Inbound / Enabling Communication Between ECSs Example scenario: After creating ECSs, you need to add a security group rule so that you can run the ping command to test communication between the ECSs. Security group configuration: Protocol Transfer Direction Port/Range Source ICMP Inbound All / Hosting a Website on ECSs Example scenario: If you deploy a website on your ECSs and require that your website be accessed over HTTP or HTTPS, you can add the following rules to the security group used by the ECSs functions as the web servers. Security group configuration: Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 38
44 2 Security Protocol Transfer Direction Port/Range Source TCP Inbound 80 (HTTP) /0 TCP Inbound 443 (HTTPS) / Enabling an ECS to Function as a DNS Server Example scenario: If you need to use an ECS as the DNS server, you must allow TCP and UDP access from port 53 to the DNS server. You can add the following rules to the security group used by your ECS. Security group configuration: Protocol Transfer Direction Port/Range Source TCP Inbound /0 UDP Inbound / Uploading or Downloading Files using FTP Example scenario: If you want to use File Transfer Protocol (FTP) to upload files to or download files from ECSs, you need to add a security group rule. NOTE You must first install the FTP server program on the ECSs and check whether ports 20 and 21 are working properly. Security group configuration: Protocol Transfer Direction Port/Range Source FTP Inbound /0 2.4 Network ACL Creating a Network ACL A network access control list (ACL) is an optional layer of security and provides stateful access control services. Based on inbound and outbound rules, the network ACL determines whether data packets are allowed in or out of any associated subnet. You can create a custom Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 39
45 2 Security network ACL. By default, a newly created network ACL is disabled. It does not have subnets associated with it nor does it have any inbound or outbound rules. Each user can create a maximum of 200 network ACLs by default. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. 5. In the right pane displayed, click Create Network ACL. 6. In the displayed Create Network ACL area shown in Figure 2-9, enter network ACL information as prompted. Table 2-9 lists the parameters to be configured. Figure 2-9 Create Network ACL Table 2-9 Parameter description Parameter Description Example Value Name Description Specifies the network ACL name. This parameter is mandatory. The network ACL name contains a maximum of 64 characters, which may consist of letters, digits, underscores (_), and hyphens (-). The name cannot contain spaces. Provides supplementary information about the network ACL. This parameter is optional. The network ACL description can contain a maximum of 255 characters and cannot contain angle brackets (<) or (>). fw-92d3 N/A 7. Click OK. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 40
46 2 Security The network ACL is created Adding a Network ACL Rule Add an inbound or outbound network ACL rule based on your network security requirements. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. 5. Locate the target network ACL in the right pane, and click the network ACL name to switch to the page showing details of that particular network ACL. 6. On the Inbound Rules or Outbound Rules tab, click Add Rule to add an inbound or outbound rule. You can click + to add more rules. Table 2-10 Parameter description Parameter Description Example Value Action Protocol Source Specifies the action in the network ACL. This parameter is mandatory. You can select a value from the drop-down list. Specifies the protocol supported by the network ACL. This parameter is mandatory. You can select a value from the drop-down list. The value can be TCP, UDP, All, or ICMP. If All or ICMP is selected, you do not need to specify port information. Specifies the source IP address from which the traffic is permitted. The default value is /0, which indicates that traffic from all IP addresses is permitted. For example: xxx.xxx.xxx.xxx/32 (IP address) xxx.xxx.xxx.0/24 (CIDR block) /0 (any IP address) Permit TCP /0 Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 41
47 2 Security Parameter Description Example Value Source Port Range Destination Destination Port Range Description Specifies the source port number or port number range. The value ranges from 0 to For a port number range, enter two port numbers connected by a hyphen (-). For example, You must specify this parameter if TCP or UDP is selected for Protocol. Specifies the destination IP address to which the traffic is permitted. The default value is /0, which indicates that traffic to all IP addresses is permitted. For example: xxx.xxx.xxx.xxx/32 (IP address) xxx.xxx.xxx.0/24 (CIDR block) /0 (any IP address) Specifies the destination port number or port number range. The value ranges from 0 to For a port number range, enter two port numbers connected by a hyphen (-). For example, You must specify this parameter if TCP or UDP is selected for Protocol. Provides supplementary information about the network ACL rule. This parameter is optional. The network ACL rule description can contain a maximum of 255 characters and cannot contain angle brackets (<) or (>). 22 or /0 22 or N/A 7. Click OK. The network ACL rule is added. The procedure for adding an outbound rule is the same as that for adding an inbound rule Associating Subnets with a Network ACL On the page showing network ACL details, associate desired subnets with a network ACL. After a network ACL is associated with a subnet, the network ACL denies all traffic to and from the subnet until you add rules to allow traffic. 3. On the console homepage, under Network, click. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 42
48 2 Security 4. In the navigation pane on the left, click Network ACL. 5. Locate the target network ACL in the right pane, and click the network ACL name to switch to the page showing details of that particular network ACL. 6. On the displayed page, click the Associated Subnets tab. 7. On the Associated Subnets page, click Associate. The page shown in Figure 2-10 is displayed. Figure 2-10 Associate Subnet 8. On the displayed page, select the subnets to be associated with the network ACL, and click OK. The selected subnets are associated with the network ACL. NOTE Subnets that have already been associated with network ACLs will not be displayed on the page for you to select. One-click subnet association and disassociation are not currently supported. Furthermore, a subnet can only be associated with one network ACL. If you want to reassociate a subnet that has already been associated with another network ACL, you must first disassociate the subnet from the original network ACL Disassociating a Subnet from a Network ACL Disassociate a subnet from a network ACL when necessary. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 43
49 2 Security 5. Locate the target network ACL in the right pane, and click the network ACL name to switch to the page showing details of that particular network ACL. 6. On the displayed page, click the Associated Subnets tab. 7. On the Associated Subnets page, locate the target network ACL and click Disassociate in the Operation column. 8. Click OK in the displayed dialog box. The subnet is disassociated from the network ACL Changing the Sequence of a Network ACL Rule If multiple network ACL rules conflict, the rules in the front take precedence. If you need a rule to take effect before or after a specific rule, you can insert that rule before or after the specific rule. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. 5. Locate the target network ACL in the right pane, and click the network ACL name to switch to the page showing details of that particular network ACL. 6. On the Inbound Rules or Outbound Rules tab, locate the target rule, click More in the Operation column, and select Insert Rule Above or Insert Rule Below. 7. In the displayed dialog box, configure required parameters and click OK. The network ACL rule is inserted. The procedure for inserting an outbound network ACL rule is the same as that for inserting an inbound network ACL rule Modifying a Network ACL Rule Modify an inbound or outbound network ACL rule based on your network security requirements. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. 5. Locate the target network ACL in the right pane, and click the network ACL name to switch to the page showing details of that particular network ACL. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 44
50 2 Security 6. On the Inbound Rules or Outbound Rules tab, locate the target rule and click Modify in the Operation column. In the displayed dialog box, configure parameters as prompted. Table 2-11 lists the parameters to be configured. Table 2-11 Parameter description Parameter Description Example Value Action Protocol Source Source Port Range Destination Destination Port Range Specifies the action in the network ACL. This parameter is mandatory. You can select a value from the drop-down list. Specifies the protocol supported by the network ACL. This parameter is mandatory. You can select a value from the drop-down list. The value can be TCP, UDP, All, or ICMP. If All or ICMP is selected, you do not need to specify port information. Specifies the source IP address from which the traffic is permitted. The default value is /0, which indicates that traffic from all IP addresses is permitted. For example: xxx.xxx.xxx.xxx/32 (IP address) xxx.xxx.xxx.0/24 (CIDR block) /0 (any IP address) Specifies the source port number or port number range. The value ranges from 0 to For a port number range, enter two port numbers connected by a hyphen (-). For example, You must specify this parameter if TCP or UDP is selected for Protocol. Specifies the destination IP address to which the traffic is permitted. The default value is /0, which indicates that traffic to all IP addresses is permitted. For example: xxx.xxx.xxx.xxx/32 (IP address) xxx.xxx.xxx.0/24 (CIDR block) /0 (any IP address) Specifies the destination port number or port number range. The value ranges from 0 to For a port number range, enter two port numbers connected by a hyphen (-). For example, You must specify this parameter if TCP or UDP is selected for Protocol. Permit TCP /0 22 or /0 22 or Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 45
51 2 Security Parameter Description Example Value Description Provides supplementary information about the network ACL rule. This parameter is optional. The network ACL rule description can contain a maximum of 255 characters and cannot contain angle brackets (<) or (>). N/A 7. Click OK. The network ACL rule is modified. The procedure for modifying an outbound network ACL rule is the same as that for modifying an inbound rule Enabling or Disabling a Network ACL Rule Enable or disable an inbound or outbound network ACL rule based on your network security requirements. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. 5. Locate the target network ACL in the right pane, and click the network ACL name to switch to the page showing details of that particular network ACL. 6. On the Inbound Rules or Outbound Rules tab, locate the target rule and click Enable or Disable in the Operation column. 7. Click OK in the displayed dialog box. The rule is enabled or disabled. The procedure for enabling or disabling an outbound network ACL rule is the same as that for enabling or disabling an inbound network ACL rule Deleting a Network ACL Rule Delete an inbound or outbound network ACL rule based on your network security requirements. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 46
52 2 Security 5. Locate the target network ACL in the right pane, and click the network ACL name to switch to the page showing details of that particular network ACL. 6. On the Inbound Rules or Outbound Rules tab, locate the target rule and click Delete in the Operation column. 7. Click OK in the displayed dialog box. The network ACL rule is deleted Viewing a Network ACL View details about a network ACL. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. 5. Locate the target network ACL in the right pane, and click the network ACL name to switch to the page showing details of that particular network ACL. 6. On the displayed page, click the Associated Subnets, Inbound Rules, and Outbound Rules tabs one by one to view details about subnet associations, inbound network ACL rules, and outbound network ACL rules Modifying a Network ACL Modify the name and description of a network ACL. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. 5. Locate the target network ACL in the right pane, and click the network ACL name to switch to the page showing details of that particular network ACL. 6. On the displayed page, click on the right of Name and edit the network ACL name. 7. Click to save the new network ACL name. 8. Click on the right of Description and edit the network ACL description. 9. Click to save the new network ACL description. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 47
53 2 Security Enabling or Disabling a Network ACL Enable or disable an inbound or outbound network ACL rule based on your network security requirements. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. 5. Locate the required network ACL in the right pane, and click Enable or Disable in the Operation column. 6. Click OK in the displayed dialog box. The network ACL is enabled or disabled Deleting a Network ACL Delete a network ACL when it is no longer required. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Network ACL. 5. Locate the target network ACL in the right pane and click Delete in the Operation column. 6. Click OK in the displayed dialog box. The network ACL is deleted. NOTE After a network ACL is deleted, associated subnets are disassociated and added rules are deleted from the network ACL. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 48
54 3 Elastic IP Address 3 Elastic IP Address 3.1 Assigning an EIP and Binding It to an ECS You can assign an EIP and bind it to an ECS to enable the ECS to access the Internet. Assign an EIP. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Elastic IP. 5. On the Elastic IP page, click Buy EIP. 6. Set the parameters as prompted. Table 3-1 Parameter description Parameter Description Example Value Region Specifies the desired region. Regions are geographic areas isolated from each other. Resources are region-specific and cannot be used across regions through internal network connections. For low network latency and quick resource access, select the nearest region. CN North-Beijing1 Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 49
55 3 Elastic IP Address Parameter Description Example Value Type Billing Mode Tag Select Bandwidth Bandwidth Name Bandwidth Type Billed By Bandwidth Size Dynamic BGP: When changes occur on a network using dynamic BGP, routing protocols provide automatic, real-time optimization of network configurations, ensuring network stability and optimal user experience. Static BGP: When changes occur on a network using static BGP, carriers cannot adjust network configurations in real time to ensure optimal user experience. The following billing modes are available: Yearly/Monthly Pay-per-use Specifies the EIP tag that consists of a key and value pair. The tag key and value must meet the requirements listed in Table 3-2. Specifies whether you can use existing bandwidth or allocate new bandwidth. Specifies the name of the bandwidth. The following bandwidth types are available: Dedicated: The bandwidth can be used by only one EIP. Shared: The bandwidth can be allocated to multiple EIPs and can be shared among the EIPs. Specifies whether the bandwidth is charged by bandwidth size or by traffic. Specifies the bandwidth size in Mbit/s. Dynamic BGP Pay-per-use Key: Ipv4_key1 Value: Allocate new bandwidth Dedicated Bandwidth 100 Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 50
56 3 Elastic IP Address Parameter Description Example Value Quantity Enterprise Project You must specify the required duration if Billing Mode is set to Yearly/Monthly. You can set the number of EIPs to be assigned only when Billing Mode is set to Pay-per-use. Specifies the enterprise project to which the EIP belongs. By default, an EIP belongs to the Default project. 1 Default Table 3-2 EIP tag requirements Parameter Requirements Example Value Key Value Cannot be left blank. Must be unique for each EIP. Can contain a maximum of 36 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. Can contain a maximum of 43 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. Ipv4_key NOTE 7. Click Next. Only outbound bandwidth is limited. To buy a pay-per-use EIP, if you want to use the shared bandwidth, you can only select an existing shared bandwidth from the Bandwidth Name drop-down list. If the Bandwidth Name option is grayed out, there is no available bandwidth for you to choose. Allocate required bandwidth first. 8. Click Submit. If you allocate new bandwidth to buy an EIP, you also need to buy the bandwidth. Bind an EIP. 9. On the Elastic IP page, locate the row that contains the target EIP, and click Bind. 10. Select the desired instance. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 51
57 3 Elastic IP Address 11. Click OK in the displayed dialog box. 3.2 Unbinding an EIP from an ECS and Releasing the EIP If you no longer need the EIP, unbind it from the ECS and release the EIP to avoid wasting network resources. EIPs assigned and bound to load balancers in the ELB service are displayed in the EIP list of the VPC service, but you cannot unbind these EIPs from the load balancers. Only unbound EIPs can be released. To release bound EIPs, you must first unbind them. Unbind an EIP. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Elastic IP. 5. On the Elastic IP page, locate the row that contains the target EIP, and click Unbind. 6. Click OK in the displayed dialog box. Release an EIP. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Elastic IP. 5. On the Elastic IP page, locate the row that contains the target EIP, and click Release. 6. Click OK in the displayed dialog box. Unbind multiple EIPs at a time. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Elastic IP. 5. On the Elastic IP page, select the EIPs to be unbound. 6. Click Unbind above the EIP list. 7. Click OK in the displayed dialog box. Release multiple EIPs at a time. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 52
58 3 Elastic IP Address 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Elastic IP. 5. On the Elastic IP page, select the EIPs to be released. 6. Click Release above the EIP list. 7. Click OK in the displayed dialog box. 3.3 Managing EIP Tags Tags can be added to EIPs to facilitate EIP identification and administration. You can add a tag to an EIP when assigning the EIP. Alternatively, you can add a tag to an assigned EIP on the EIP details page. A maximum of ten tags can be added to each EIP. A tag consists of a key and value pair. Table 3-3 lists the tag key and value requirements. Table 3-3 EIP tag requirements Parameter Requirements Example Value Key Value Cannot be left blank. Must be unique for each EIP. Can contain a maximum of 36 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. Can contain a maximum of 43 characters. Cannot contain equal signs (=), asterisks (*), left angle brackets (<), right angle brackets (>), backslashes (\), commas (,), vertical bars ( ), and slashes (/), and the first and last characters cannot be spaces. Ipv4_key Search for EIPs by Tag Key and Value on the Page Showing the EIP List. 3. Under Network, click. 4. In the navigation pane on the left, click Elastic IP. 5. In the upper right corner of the EIP list, click Search by Tag. 6. In the displayed area, enter the tag key and value of the EIP you are looking for. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 53
59 3 Elastic IP Address Both the tag key and value must be specified. The system automatically displays the EIPs you are looking for if both the tag key and value are matched. 7. Click + to add the entered tag key and value. You can add multiple tag keys and values to refine your search results. If you add more than one tag to search for EIPs, the EIPs containing all specified tags will be displayed. 8. Click Search. The system displays the EIPs you are looking for based on the entered tag keys and values. Add, Delete, Edit, and View Tags on the Tags Tab of an EIP. 3. Under Network, click. 4. In the navigation pane on the left, click Elastic IP. 5. On the Elastic IP page, locate the EIP whose tags are to be managed, and click the IP address. 6. On the page showing EIP details, click the Tags tab and perform desired operations on tags. View tags. On the Tags tab, you can view details about tags added to the current EIP, including the number of tags and the key and value of each tag. Add a tag. Click Add Tag in the upper left corner. In the displayed Add Tag dialog box, enter the tag key and value, and click OK. Edit a tag. Locate the row that contains the tag to be edited, and click Edit in the Operation column. Enter the new tag key and value, and click OK. Delete a tag. 3.4 Modifying EIP Bandwidth Locate the row that contains the tag to be deleted, and click Delete in the Operation column. In the displayed Delete Tag dialog box, click OK. Modify the name and size of the EIP bandwidth. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Elastic IP. 5. Locate the row that contains the target EIP in the EIP list, click More in the Operation column, and select Modify Bandwidth. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 54
60 3 Elastic IP Address 6. Modify the bandwidth parameters as prompted. 7. Click OK. 3.5 IPv6 EIP (OBT) Overview EIPs support both IPv4 and IPv6. You can assign new IPv6 EIPs or convert existing IPv4 EIPs into IPv6 EIPs. After the IPv6 EIP function is enabled, you will obtain an extra IPv6 EIP. External IPv6 addresses can access cloud resources through this IPv6 EIP. Applying to participate in the IPv6 EIP OBT The IPv6 EIP function is now in OBT. You can click Elastic IP under Network on the console homepage and click IPv6 EIP on the page shown in Figure 3-1 to go to the page for applying to participate in the OBT. After your application is approved, you can try IPv6 EIPs. Figure 3-1 Participating in the IPv6 EIP OBT NOTE Currently, security groups and NAT gateways do not support IPv6 EIPs. Assigning an IPv6 EIP Assign an IPv6 EIP by following the steps provided in 3.1 Assigning an EIP and Binding It to an ECS. On the page for assigning EIPs, set IPv6 EIP to Enable, as shown in Figure 3-2. Then, a new IPv6 EIP will be assigned to you. Figure 3-2 IPv6 EIP Enabling IPv6 Conversion If you want to convert an existing IPv4 EIP into an IPv6 EIP, locate the row that contains the EIP in the EIP list, click More in the Operation column, and select Enable IPv6 EIP. Then, the IPv4 EIP will be converted to an IPv6 EIP. After the conversion, the EIP will have both IPv4 and IPv6 addresses. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 55
61 3 Elastic IP Address Configuring the Security Group After IPv6 EIP is enabled, add inbound and outbound security group rules to allow packets to and from IP address range /16. Table 3-4 shows the added security group rules. The IPv6 EIP uses NAT64. NAT64 converts the source IP address in the inbound rule into an IPv4 address in IP address range /16, the source port to a random port, and the destination IP address to an internal private IPv4 address of your local machine. The destination port remains the same. Table 3-4 Security group rules Transfer Direction Protocol/ Application Port and IP Address Inbound All Source: /16 Outbound All Destination: /16 Disabling IPv6 Conversion If you do not need the IPv6 address of an EIP, locate the row that contains the EIP in the EIP list, click More in the Operation column, and select Disable IPv6 EIP. Then, the IPv6 address will be released. After the IPv6 address is released, the EIP has only the IPv4 address. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 56
62 4 Shared Bandwidth 4 Shared Bandwidth 4.1 Shared Bandwidth Overview Shared bandwidth allows multiple EIPs to share the same bandwidth. The system provides region-level bandwidth sharing and multiplexing to enable all ECSs, BMSs, and load balancers that have EIPs bound in a region to use the same bandwidth. When you host a large number of applications on the cloud, if each EIP uses an independent bandwidth, a lot of bandwidths are required, which incurs high bandwidth costs. If all EIPs share the same bandwidth, your network operation costs will be lowered and your system O&M as well as resource statistics will be simplified. Lowered Bandwidth Costs Region-level bandwidth sharing and multiplexing are provided to reduce bandwidth usage and O&M costs. Flexible Operations You can add pay-per-use EIPs to or remove them from a shared bandwidth without paying additional attention to the EIP and bound instance types. Flexible Billing Modes The yearly/monthly and pay-per-use billing modes are provided. 4.2 Buying a Shared Bandwidth Buy a shared bandwidth for use with EIPs. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Shared Bandwidth. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 57
63 4 Shared Bandwidth 5. In the upper right corner, click Buy Shared Bandwidth. On the displayed page, configure parameters as prompted. Table 4-1 Parameter description Parameter Description Example Value Billing Mode Region Bandwidth Name Billed By Bandwidth Size Enterprise Project Quantity Specifies the billing mode of a shared bandwidth. The billing mode can be: Yearly/Monthly: You pay for the bandwidth by year or month before using it. No charges will be incurred for the bandwidth during its validity period. Pay-per-use: You pay for the bandwidth based on the amount of time you use the bandwidth. Specifies the desired region. Regions are geographic areas isolated from each other. Resources are region-specific and cannot be used across regions through internal network connections. For low network latency and quick resource access, select the nearest region. Specifies the name of the shared bandwidth. Specifies the shared bandwidth billing method. The shared bandwidth can be billed by bandwidth. Specifies the shared bandwidth size in Mbit/s. The minimum bandwidth that can be purchased is 5 Mbit/s. Specifies the enterprise project to which the shared bandwidth belongs. By default, the shared bandwidth belongs to the Default project. Specifies the required duration of the shared bandwidth to be purchased. You need to specify this parameter only in yearly/monthly billing mode. Yearly/Monthly CN North-Beijing1 Bandwidth-001 Bandwidth 10 Default 2 months 6. Click Next. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 58
64 4 Shared Bandwidth 4.3 Adding EIPs to a Shared Bandwidth Add EIPs to a shared bandwidth to enable the EIPs to share the bandwidth resources. You can add multiple EIPs to a shared bandwidth at a time. NOTE After an EIP is added to a shared bandwidth, the original bandwidth size used by the EIP will become invalid, and the new EIP bandwidth size will be the same as that of the shared bandwidth. The EIP's original dedicated bandwidth will be deleted, and you will not be charged for the dedicated bandwidth. Currently, a yearly/monthly EIP cannot be added to a shared bandwidth. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Shared Bandwidth. 5. In the shared bandwidth list, locate the row that contains the bandwidth to which EIPs are to be added, click Add EIP in the Operation column, select the EIPs to be added in the displayed dialog box, and click OK. 4.4 Removing EIPs from a Shared Bandwidth Remove EIPs that are no longer required from a shared bandwidth based on your service requirements. NOTE After EIPs are removed from a shared bandwidth, the EIPs will use their original bandwidth sizes used before the EIPs are added to the shared bandwidth. If the size of the shared bandwidth used by the EIPs exceeds the upper limit of the original EIP's bandwidth billed by traffic, the maximum bandwidth size of the EIPs removed from the shared bandwidth will be the upper limit of the EIP's original bandwidth. A yearly/monthly EIP cannot be removed from a shared bandwidth. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Shared Bandwidth. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 59
65 4 Shared Bandwidth 5. In the shared bandwidth list, locate the row that contains the bandwidth from which EIPs are to be removed, click More in the Operation column and select Remove EIP, select the EIPs to be removed in the displayed dialog box, and click OK. 4.5 Modifying a Shared Bandwidth Modify the name, billing item, and size of a shared bandwidth. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Shared Bandwidth. 5. In the shared bandwidth list, locate the row that contains the target shared bandwidth, click Modify in the Operation column, and modify the bandwidth settings on the displayed page. 4.6 Deleting a Shared Bandwidth Delete a pay-per-use shared bandwidth when it is no longer required. NOTE A yearly/monthly shared bandwidth cannot be directly deleted. It can only be unsubscribed in the User Center. Prerequisites Before deleting a shared bandwidth, remove all EIPs associated with it. For details, see 4.4 Removing EIPs from a Shared Bandwidth. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Shared Bandwidth. 5. In the shared bandwidth list, locate the row that contains the pay-per-use shared bandwidth to be deleted, click More in the Operation column, and select Delete. In the displayed dialog box, click OK. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 60
66 5 Shared Data Package 5 Shared Data Package 5.1 Shared Data Package Overview Use Restrictions A shared data package is a traffic package that is easy to use and cost-effective. A shared data package takes effect immediately after you purchase it. The shared data package offsets the traffic fees of the pay-per-use EIP bandwidth billed by traffic until the traffic in the package is used up or the package expires. Two types of packages are available: dynamic BGP and static BGP. The dynamic BGP data packages offset the traffic fees of dynamic BGP bandwidth, and the static BGP data packages offset the traffic fees of static BGP bandwidth. Shared data packages can be purchased yearly or monthly. The yearly data packages offer better discounts. You can have more than one shared data package at a time. The data package with the shortest validity period will be used first. A shared data package cannot be unsubscribed. A shared data package takes effect for all of your pay-per-use EIP bandwidths billed by traffic. You cannot make a shared data package take effect only for a specified EIP bandwidth. 5.2 Buying a Shared Data Package Buy a shared data package for use. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click Shared Data Package. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 61
67 5 Shared Data Package 5. In the upper right corner, click Buy Shared Data Package. On the displayed page, configure parameters as prompted. Table 5-1 Parameter description Parameter Description Example Value Region Type Validity Period Shared Data Package Specifications Usage Duration Quantity Specifies the desired region. Regions are geographic areas isolated from each other. Resources are region-specific and cannot be used across regions through internal network connections. For low network latency and quick resource access, select the nearest region. Specifies shared data package type. Set this parameter based on the bandwidth type of the EIP. The following two types of packages are available: Dynamic BGP: A dynamic BGP data package offsets the traffic fees of dynamic BGP bandwidth Static BGP: A static BGP data package offsets the traffic fees of static BGP bandwidth. Specifies the validity period of the shared data package. You need to select a proper validity period based on your service requirements. A shared data package cannot be unsubscribed and takes effect immediately after you purchase it. Expired shared data packages will longer be available for use. Specifies the size of the shared data package in GB. Specifies the usage duration of the shared data package. Specifies the number of shared data packages you want to purchase. CN North-Beijing1 Static BGP 1 month 10 GB Default 1 6. Click Next. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 62
68 6 Custom Route 6 Custom Route 6.1 Custom Route Overview A custom route is a user-defined routing rule added to a VPC. The route enables ECSs in a VPC that do not have EIPs bound to access the Internet. 6.2 Example Custom Route in a VPC A custom route in a VPC routes traffic originating from ECSs in the VPC to a specified ECS in the same VPC. A custom route in a VPC can be used in the following scenarios: When ECSs in a VPC need to access the Internet, add a custom route to enable the ECSs to access the Internet through the ECS that has an EIP bound. When adding the custom route, set Destination to default value /0 and Next Hop to the private or virtual IP address of the ECS that has an EIP bound in the VPC. When ECSs in a VPC need to access the container network, add a route to enable the ECSs to access the container network through an ECS with the container network configured. When adding the custom route, set Destination to default value /0 or a network segment on the container network and Next Hop to the private or virtual IP address of the ECS with the container network configured in the VPC. The destination of each route must be unique. Accessing the Internet Through a Custom Route Example scenario Two ECSs, ECS1 and ECS2, exist in a VPC. ECS1 has an EIP bound, while ECS2 does not have an EIP bound. You can add a custom route to enable ECS2 to access the Internet through ECS1. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 63
69 6 Custom Route Figure 6-1 Accessing the Internet through a custom route Configuration 1. Table 6-1 lists the example custom route configuration. The destination is default value /0, and the next hop is the ECS1 private or virtual IP address bound with an EIP. Table 6-1 Custom route Destinati on Next Hop /0 ECS1 private or virtual IP address NOTE When you use a custom route to access the Internet, the destination can only be set to default value /0 and cannot be set to a specific public network segment. If the next hop is a virtual IP address, the virtual IP address must have an EIP bound. Otherwise, access to the Internet through this virtual IP address is not allowed. 2. Configure ECS1 as an SNAT server by following the instructions provided in 6.4 Configuring an SNAT Server. Accessing the Container Network on an ECS Through a Custom Route Example scenario Two ECSs, ECS1 and ECS2, exist in a VPC. The container network has been configured for ECS1. If ECS2 needs to access the container network on ECS1, you can add a custom route in a VPC to enable ECS2 to access the container network through ECS1. Figure 6-2 Accessing the container network on an ECS through a custom route Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 64
70 6 Custom Route Configuration 1. Table 6-2 lists the example custom route in a VPC. The destination can be default value /0 or a network segment on the container network, and the next hop is the ECS1 private or virtual IP address bound with an EIP. Table 6-2 Custom route Destination Next Hop /0 ECS1 private or virtual IP address 2. Configure ECS1 as an SNAT server by following the instructions provided in 6.4 Configuring an SNAT Server. 6.3 Example Custom Route Outside a VPC A custom route outside a VPC routes traffic originating outside the VPC to specified ECSs in the VPC. When adding the custom route, set Destination to default value /0 or another network segment. (The network segment cannot conflict with subnet CIDR blocks in the VPC.) The destination of each custom route must be unique. Custom Route Between VPCs Example scenario If a VPC peering connection has been created for two VPCs, VPC1 and VPC2, you can add a custom route for the two VPCs to enable ECSs in VPC2 to access the Internet through an ECS that has an EIP bound in VPC1. Figure 6-3 Custom Route Between VPCs Configuration Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 65
71 6 Custom Route A VPC peering connection has been created between VPC1 and VPC2. Figure 6-4 shows the VPC peering connection configuration. Figure 6-4 VPC peering connection between VPC1 and VPC2 Table 6-3 and Table 6-4 list the VPC peering route tables. Table 6-3 VPC peering route table for VPC1 Destination Next Hop /24 pc-01 Table 6-4 VPC peering route table for VPC2 Destination Next Hop /24 pc /0 pc-01 NOTE In the preceding route tables, value pc-01 indicates the VPC peering connection ID. The value is automatically generated and cannot be configured. Table 6-5 lists the custom route table configuration. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 66
72 6 Custom Route Table 6-5 Custom route table for VPC1 Destination Next Hop /0 ECS1 private or virtual IP address NOTE When you use a custom route to access the Internet, the destination can only be set to default value /0 and cannot be set to a specific public network segment. If the next hop is a virtual IP address, the virtual IP address must have an EIP bound. Otherwise, access to the Internet through this virtual IP address is not allowed. Custom Route Between a VPC and a Direct Connect Connection Example scenario You can add a custom route to forward all packets from a Direct Connect connection to specified servers in the VPC. A custom route needs to be added to the VPC. Table 6-6 lists the custom route configuration. Figure 6-5 Custom route between a VPC and a Direct Connect connection Configuration Table 6-6 lists the custom route configuration. The destination is default value /0, and the next hop is the ECS private or virtual IP address. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 67
73 6 Custom Route Table 6-6 VPC custom route table Destination Next Hop /0 ECS private or virtual IP address 6.4 Configuring an SNAT Server To use the route table function provided by the VPC service, you need to configure SNAT on an ECS to enable other ECSs that do not have EIPs bound in a VPC to access the Internet through this ECS. The configured SNAT function takes effect for all subnets in a VPC. Prerequisites You have obtained the ECS where SNAT is to be deployed. The ECS where SNAT is to be deployed runs the Linux OS. The ECS where SNAT is to be deployed has only one network interface card (NIC) configured. 3. On the console homepage, under Computing, click Elastic Cloud Server. 4. On the displayed page, locate the target ECS in the ECS list and click the ECS name to switch to the page showing ECS details. 5. On the displayed ECS details page, click the NICs tab. 6. Click the NIC IP address. In the displayed area showing the NIC details, disable the source/destination check function. By default, the source/destination check function is enabled. When this function is enabled, the system checks whether source IP addresses contained in the packets sent by ECSs are correct. If the IP addresses are incorrect, the system does not allow the ECSs to send the packets. This mechanism prevents packet spoofing, thereby improving system security. If SNAT is used, the SNAT server needs to forward packets. This mechanism prevents the packet sender from receiving returned packets. Therefore, you need to disable the source/destination check function for SNAT servers. 7. Bind an EIP. Bind an EIP with the private IP address of the ECS. For details, see 3.1 Assigning an EIP and Binding It to an ECS. Bind an EIP with the virtual IP address of the ECS. For details, see 9.3 Binding a Virtual IP Address with an EIP or ECS. 8. On the ECS console, use the remote login function to log in to the ECS on which SNAT is to be configured. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 68
74 6 Custom Route 9. Run the following command and enter the password of user root to switch to user root: su - root 10. Run the following command to check whether the ECS can successfully connect to the Internet: NOTE Before running the command, you must disable the response iptables rule on the ECS where SNAT is deployed and enable the security group rules. ping The ECS can access the Internet if the following information is displayed: [root@localhost ~]# ping PING (xxx.xxx.xxx.xxx) 56(84) bytes of data. 64 bytes from xxx.xxx.xxx.xxx: icmp_seq=1 ttl=51 time=9.34 ms 64 bytes from xxx.xxx.xxx.xxx: icmp_seq=2 ttl=51 time=9.11 ms 64 bytes from xxx.xxx.xxx.xxx: icmp_seq=3 ttl=51 time=8.99 ms 11. Run the following command to check whether IP forwarding of the Linux OS is enabled: cat /proc/sys/net/ipv4/ip_forward In the command output, 1 indicates enabled, and 0 indicates disabled. The default value is 0. If IP forwarding in Linux is enabled, go to step 14. If IP forwarding in Linux is disabled, perform step 12 to enable IP forwarding in Linux. Many OSs support packet routing. Before forwarding packets, OSs change source IP addresses in the packets to OS IP addresses. Therefore, the forwarded packets contain the IP address of the public sender so that the response packets can be sent back in the same path to the initial packet sender. This method is called SNAT. The OSs need to keep track of the packets in which the IP addresses have been changed to ensure that the destination IP addresses in the packets can be rewritten and that packets can be forwarded to the initial packet sender. To achieve these purposes, you need to enable the IP forwarding function and configure SNAT rules. 12. Use the vi editor to open the /etc/sysctl.conf file, change the value of net.ipv4.ip_forward to 1, enter :wq to save the change and exit. 13. Run the following command to make the change take effect: sysctl -p /etc/sysctl.conf 14. Configure SNAT. Run the following command to enable all ECSs on the network segment (for example, /24) to access the Internet using the SNAT function: Figure 6-6 shows the example command. iptables -t nat -A POSTROUTING -o eth0 -s subnet -j SNAT --to nat-instance-ip Figure 6-6 Configuring SNAT 15. Run the following command to check whether the operation is successful: The operation is successful if the information shown in Figure 6-7 (for example, /24) is displayed. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 69
75 6 Custom Route iptables -t nat --list Figure 6-7 Verifying configuration 16. Add a route. For details, see 6.5 Adding a Route. The destination is /0, and the next hop is the private or virtual IP address of the ECS where the SNAT function is deployed. For example, the next hop is Differences Between SNAT Servers and NAT Gateways The NAT Gateway service offers the network address translation (NAT) function for servers, such as Elastic Cloud Servers (ECSs), Bare Metal Servers (BMSs), and Workspace desktops, in a (VPC) or servers that connect to a VPC through Direct Connect or Virtual Private Network (VPN) in local data centers, allowing these servers to access the Internet using elastic IP addresses (EIPs) or to provide services for the Internet. Compared with SNAT, the NAT Gateway service is easy to configure and use. This service can be flexibly deployed across subnets and AZs and supports different NAT gateway specifications. You can click NAT Gateway under Network on the management console to try this service. For details, see the NAT Gateway. 6.5 Adding a Route When ECSs in a VPC need to access the Internet, add a custom route to enable the ECSs to access the Internet through the ECS that has an EIP bound. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the VPC to which a route is to be added and click the VPC name. 6. On the Route Tables tab, click Add Route. 7. Set route information on the displayed page. Destination indicates the destination CIDR block. The default value is /0. If the traffic originates from a VPC, the destination can be a subnet CIDR block in Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 70
76 6 Custom Route this VPC. If the traffic originates from outside the VPC, the destination CIDR block cannot conflict with the existing subnet CIDR blocks in this VPC. The destination of each route must be unique. Next Hop: indicates the IP address of the next hop. Set it to a private IP address or a virtual IP address in a VPC. NOTE 8. Click OK. If the next hop is a virtual IP address, an EIP must be bound to the virtual IP address. Otherwise, access to the Internet through this virtual IP address is not allowed. (A custom route is used to forward traffic from the virtual IP address to the Internet.) 6.6 Querying a Route Query a route that has been added. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the VPC to which the route to be queried belongs and click the VPC name. 6. View information about a single route or all routes in the route list. 6.7 Modifying a Route Modify a route. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the VPC to which the route to be modified belongs and click the VPC name. 6. Click the Route Tables tab. On the displayed page, locate the row that contains the route to be modified, and click Modify in the Operation column. Modify route information in the displayed dialog box. 7. Click OK. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 71
77 6 Custom Route 6.8 Deleting a Route Delete a route if it is no longer required. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click. 5. On the page, locate the VPC to which the route to be deleted belongs and click the VPC name. 6. Click the Route Tables tab. On the displayed page, locate the row that contains the route to be deleted, and click Delete in the Operation column. 7. Click OK in the displayed dialog box. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 72
78 7 VPC Peering Connection 7 VPC Peering Connection 7.1 VPC Peering Connection Creation A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IP addresses. ECSs in either VPC can communicate with each other just as if they were in the same VPC. You can create a VPC peering connection between your own VPCs, or between your VPC and another tenant's VPC within the same region. You cannot create a VPC peering connection between VPCs in different regions. for creating a VPC peering connection with another VPC of your own Figure 7-1 for creating a VPC peering connection with another VPC of your own If you create a VPC peering connection between two VPCs of your own, the system automatically accepts the connection by default. You need to create routes for the local and peer VPCs to enable communication between the two VPCs. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 73
79 7 VPC Peering Connection for creating a VPC peering connection with a VPC of another tenant Figure 7-2 for creating a VPC peering connection with a VPC of another tenant If you create a VPC peering connection between your VPC and another tenant's VPC, the VPC peering connection will be in the Awaiting acceptance state. After the peer tenant accepts the connection, the connection status changes to Accepted. The local and peer tenants must configure the routes required by the VPC peering connection to enable communication between the two VPCs. If the local and peer VPCs have overlapping CIDR blocks, the routes added for the VPC peering connection may be invalid. Before creating a VPC peering connection between two VPCs that have overlapping CIDR blocks, ensure that no subnets in the two VPCs have overlapping CIDR blocks. In this case, the created VPC peering connection enables communication between two subnets in the two VPCs. You can run the ping command to check whether the two VPCs can communicate with each other. 7.2 VPC Peering Connection Configuration Plans To enable two VPCs to communicate with each other, you can create a VPC peering connection between the two VPCs. If the two VPCs have non-overlapping CIDR blocks, you can configure routes that point to entire VPCs for the VPC peering connection. If the two VPCs have overlapping CIDR blocks, you can only configure routes that point to specific subnets of the VPCs for the VPC peering connection. Configurations with Routes to Entire VPCs Configurations with routes to entire VPCs include the following situations: two VPCs peered together and multiple VPCs peered together. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 74
80 7 VPC Peering Connection No matter in which configuration, if you need to configure routes that point to entire VPCs in a VPC peering connection, none of the VPCs involved in the connection can have overlapping CIDR blocks. Otherwise, the VPC peering connection does not take effect because the routes are unreachable. The destination address of the route that points to an entire VPC is the CIDR block of the peer VPC, and the next hop is the VPC peering connection ID. Configurations with Routes to Specific Subnets If VPCs in a VPC peering connection have overlapping CIDR blocks, the peering connection can only be created to enable communication between subnets in the VPCs. If subnets in the VPCs of a VPC peering connection have overlapping network segments, the peering connection does not take effect. To create a VPC peering connection, ensure that the VPCs involved do not contain overlapping subnets. For example, VPC1 and VPC2 have matching CIDR blocks, but the subnets in the two VPCs do not overlap. Then, a VPC peering connection can be created between two subnets that do not overlap with each other in the two VPCs. The route table is used to control the specific subnets for which the VPC peering connection is created. Figure 7-3 shows a VPC peering connection created between two subnets. Routes are required to enable communication between Subnet A in VPC1 and Subnet X in VPC2 in the figure. Figure 7-3 VPC peering connection between Subnet A and Subnet X Figure 7-4 shows the routes configured for the VPC peering connection between Subnet A and Subnet X. After the routes are configured, Subnet A and Subnet X are peered with each other and can communicate with each other. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 75
81 7 VPC Peering Connection Figure 7-4 Route table for the VPC peering connection between Subnet A and Subnet X If two VPCs have overlapping subnets, the VPC peering connection created between the two subnets does not take effect, and the subnets cannot communicate with each other. As shown in Figure 7-5, Subnet B and Subnet Y have matching network segments. Therefore, a VPC peering connection cannot be created between Subnet A and Subnet Y. Figure 7-5 Invalid VPC peering connection If VPC1 is peered with multiple VPCs, for example, VPC2, VPC3, and VPC4, the subnet CIDR blocks of VPC1 cannot overlap with those of VPC2, VPC3, and VPC4. If VPC2, VPC3, and VPC4 have overlapping subnets, a VPC peering connection can be created between only one of these overlapping subnets and a subnet of VPC1. If a VPC peering connection is created between a subnet and the other N subnets, none of the subnets can have overlapping CIDR blocks. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 76
82 7 VPC Peering Connection 7.3 Creating a VPC Peering Connection with Another VPC of Your Own Prerequisites To create a VPC peering connection, first create a request to peer with another VPC. You can request a VPC peering connection with another VPC of your own in the same region. The system automatically accepts the request. Two VPCs in the same region have been created. Create a VPC peering connection. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click VPC Peering. 5. In the right pane displayed, click Create VPC Peering Connection. 6. Configure parameters as prompted. You must select Current tenant for Tenant. Table 7-1 lists the parameters to be configured. Figure 7-6 Creating a VPC peering connection Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 77
83 7 VPC Peering Connection Table 7-1 Parameter description Parameter Description Example Value Name Local VPC Local VPC CIDR Block Tenant Project Name Peer VPC Specifies the name of the VPC peering connection. The name contains a maximum of 64 characters, which consist of letters, digits, hyphens (-), and underscores (_). Specifies the local VPC. You can select one from the drop-down list. Specifies the CIDR block for the local VPC. Specifies the tenant of the VPC to peer with. Current tenant: The VPC peering connection will be created between your local VPC and a VPC of your own in the same region. Other tenant: The VPC peering connection will be created between your local VPC and a VPC of another tenant in the same region. Specifies the project name. The project name of the current project is used by default. Specifies the peer VPC. You can select one from the drop-down list if the VPC peering connection is created between two VPCs of your own. peering-001 vpc_002(0a396cff-8bc b9-267cae5ac460) /24 Current tenant aaa vpc_fab1(65d062b3-40fa f527d2ab) Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 78
84 7 VPC Peering Connection Parameter Description Example Value Peer VPC CIDR Block Specifies the CIDR block for the peer VPC. The local and peer VPCs cannot have matching or overlapping CIDR blocks. Otherwise, the routes added for the VPC peering connection may not take effect /24 7. Click OK. Add routes for a VPC peering connection. If you request a VPC peering connection with a VPC of your own, the system automatically accepts the request. To enable communication between the two VPCs, you need to add routes for the VPC peering connection. 1. On the console homepage, under Network, click. 2. In the navigation pane on the left, click VPC Peering. 3. Locate the target VPC peering connection in the connection list. Figure 7-7 VPC peering connection list 4. Click the name of the VPC peering connection to switch to the page showing details about the connection. 5. On the displayed page, click the Local Routes tab. 6. In the displayed Local Routes area, click Add Local Route. In the displayed dialog box, add a local route. Table 7-2 lists the parameters to be configured. Figure 7-8 Add Local Route Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 79
85 7 VPC Peering Connection Table 7-2 Route parameter description Parameter Description Example Value Destination Next Hop Specifies the destination address. Set it to the peer VPC or subnet CIDR block. Specifies the next hop address. The default value is the VPC peering connection ID. Keep the default value /24 65d062b3-40fa a 7. Click OK to switch to the page showing the VPC peering connection details. 8. On the displayed page, click the Peer Routes tab. 9. In the displayed Peer Routes area, click Add Peer Route and add a route. 10. Click OK in the displayed dialog box. After a VPC peering connection is created, the two VPCs can communicate with each other through private IP addresses. You can run the ping command to check whether the two VPCs can communicate with each other. If two VPCs cannot communicate with each other, check the configuration by following the instructions provided in What Can I Do If VPCs in a VPC Peering Connection Cannot Communicate with Each Other. 7.4 Creating a VPC Peering Connection with a VPC of Another Tenant The VPC service also allows you to create a VPC peering connection with a VPC of another tenant. The two VPCs must be in the same region. If you request a VPC peering connection with a VPC of another tenant in the same region, the peer tenant must accept the request to activate the connection. Create a VPC peering connection. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click VPC Peering. 5. In the right pane displayed, click Create VPC Peering Connection. 6. Configure parameters as prompted. You must select Other tenant for Tenant. Table 7-3 lists the parameters to be configured. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 80
86 7 VPC Peering Connection Table 7-3 Parameter description Parameter Description Example Value Name Local VPC Local VPC CIDR Block Tenant Peer Project ID Peer VPC ID Specifies the name of the VPC peering connection. The name contains a maximum of 64 characters, which consist of letters, digits, hyphens (-), and underscores (_). Specifies the local VPC. You can select one from the drop-down list. Specifies the CIDR block for the local VPC. Specifies the tenant of the VPC to peer with. Current tenant: The VPC peering connection will be created between your local VPC and a VPC of your own in the same region. Other tenant: The VPC peering connection will be created between your local VPC and a VPC of another tenant in the same region. This parameter is available only when Other tenant is selected. For details about how to obtain the project ID, see Obtaining the Project ID. This parameter is available only when Other tenant is selected. Specifies the ID of the peer VPC. peering-001 0a396cff-8bc b9-267cae5ac /24 N/A N/A 65d062b3-40fa f527d2ab 7. Click OK. Accept a VPC peering connection. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 81
87 7 VPC Peering Connection To request a VPC peering connection with a VPC of another tenant, the peer tenant must accept the request to activate the connection. 1. The peer tenant logs in to the management console. 2. On the console homepage, under Network, click. 3. In the navigation pane on the left, click VPC Peering. 4. Locate the target VPC peering connection in the connection list. Figure 7-9 VPC peering connection list 5. Locate the row that contains the target VPC peering connection in the connection list, and click Accept Request in the Operation column. 6. Click OK in the displayed dialog box. Refuse a VPC peering connection. The peer tenant can reject any received VPC peering connection request. After a VPC peering connection request is rejected, the connection will not be established. You must delete the rejected VPC peering connection request before creating a new VPC peering connection between the same VPCs as those in the rejected request. 1. The peer tenant logs in to the management console. 2. On the console homepage, under Network, click. 3. In the navigation pane on the left, click VPC Peering. 4. In the right pane displayed, locate the target VPC peering connection in the connection list. 5. Click Reject Request in the Operation column. 6. Click OK in the displayed dialog box. Add routes for a VPC peering connection. If you request a VPC peering connection with a VPC of another tenant, the peer tenant must accept the request. To enable communication between the two VPCs, you need to add routes for the VPC peering connection. The local tenant can add only the local route because the local tenant does not have the required permission to perform operations on the peer VPC. The peer tenant must add the peer route. The procedure for adding a local route and a peer route is the same. 2. On the console homepage, under Network, click. 3. In the navigation pane on the left, click VPC Peering. 4. Locate the target VPC peering connection in the connection list. 5. Click the name of the VPC peering connection to switch to the page showing details about the connection. 6. On the displayed page, click the Local Routes tab. 7. In the displayed Local Routes area, click Add Local Route. In the displayed dialog box, add a local route. Table 7-4 lists the parameters to be configured. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 82
88 7 VPC Peering Connection Figure 7-10 Add Local Route Table 7-4 Route parameter description Parameter Description Example Value Destination Next Hop Specifies the destination address. Set it to the peer VPC or subnet CIDR block. Specifies the next hop address. The default value is the VPC peering connection ID. Keep the default value /24 65d062b3-40fa a 8. Click OK. The routes are added for the VPC peering connection. After a VPC peering connection is created, the two VPCs can communicate with each other through private IP addresses. You can run the ping command to check whether the two VPCs can communicate with each other. Obtaining the Project ID You can perform the following steps to obtain the project ID on the management console: 2. Select My Credential from the username drop-down list. 3. On the Project List tab, obtain the required project ID. 7.5 Viewing VPC Peering Connections Both the local and peer tenants can view information about the VPC peering connections in the Awaiting acceptance and Accepted states. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 83
89 7 VPC Peering Connection 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click VPC Peering. 5. In the displayed right pane, view the VPC peering connections. You can find the required VPC peering connections by connection status or name. Figure 7-11 VPC peering connection list 6. Click the VPC peering connection name. On the displayed page, view detailed information about the VPC peering connection. 7.6 Modifying a VPC Peering Connection Both the local and peer tenants can modify a VPC peering connection in any state. Currently only the name of a VPC peering connection can be changed. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click VPC Peering. 5. In the displayed right pane, view the VPC peering connections. You can find the required VPC peering connections by connection status or name. Figure 7-12 VPC peering connection list 6. Locate the target VPC peering connection and click More in the Operation column. 7. Click Modify. In the displayed dialog box, modify information about the VPC peering connection. 8. Click OK in the displayed dialog box. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 84
90 7 VPC Peering Connection 7.7 Deleting a VPC Peering Connection Both the local and peer tenants can delete a VPC peering connection in any state. After a VPC peering connection is deleted, routes configured for the connection will be automatically deleted. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click VPC Peering. 5. In the displayed right pane, view the VPC peering connections. You can find the required VPC peering connections by connection status or name. Figure 7-13 VPC peering connection list 6. Locate the target VPC peering connection and click More in the Operation column. 7. Click Delete to delete the VPC peering connection. 8. Click OK in the displayed dialog box. 7.8 Viewing Routes Configured for a VPC Peering Connection on the Peering Connection Details Page After routes are added for a VPC peering connection, both the local and peer tenants can view information about the routes on the page showing details about the VPC peering connection. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click VPC Peering. 5. Locate the target VPC peering connection in the connection list. Figure 7-14 VPC peering connection list Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 85
91 7 VPC Peering Connection 6. Click the name of the VPC peering connection to switch to the page showing details about the connection. 7. On the displayed page, click the Local Routes tab and view information about the local route added for the VPC peering connection. 8. On the page showing details about the VPC peering connection, click the Peer Routes tab and view information about the peer route added for the VPC peering connection. 7.9 Viewing Routes Configured for a VPC Peering Connection in the VPC Peering Route Table After routes are added for a VPC peering connection, both the local and peer tenants can view information about the routes in the VPC peering route table. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click VPC Peering. 5. Locate the target VPC peering connection in the connection list and click the connection name. 6. On the displayed page showing details about the connection, view routes added to the connection Deleting a Route on the VPC Peering Connection Details Page After routes are added for a VPC peering connection, both the local and peer tenants can delete the routes on the page showing details about the peering connection. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click VPC Peering. 5. Locate the target VPC peering connection in the connection list. Figure 7-15 VPC peering connection list Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 86
92 7 VPC Peering Connection 6. Click the name of the VPC peering connection to switch to the page showing details about the connection. 7. On the displayed page, click the Local Routes tab and view information about the local route added for the VPC peering connection. 8. On the Local Routes page, locate the target local route, and click Delete in the Operation column. 9. Click OK in the displayed dialog box. 10. On the page showing details about the VPC peering connection, click the Peer Routes tab and view information about the peer route added for the VPC peering connection. 11. On the Peer Routes page, locate the target peer route, and click Delete in the Operation column. 12. Click OK in the displayed dialog box Deleting a Route from the VPC Peering Route Table After routes are added for a VPC peering connection, both the local and peer tenants can delete the routes from the VPC peering route table. 3. On the console homepage, under Network, click. 4. In the navigation pane on the left, click VPC Peering. 5. Locate the target VPC peering connection in the connection list and click the connection name. 6. Locate the row that contains the target route, and click Delete in the Operation column. 7. Click OK in the displayed dialog box. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 87
93 8 Direct Connect 8 Direct Connect Direct Connect allows you to establish a dedicated network connection between your data center and the cloud platform. With Direct Connect, you can establish a private connection between the cloud platform and your data center, office, or collocation environment, which can reduce your network latency and provide a more consistent network experience than Internet-based connections. For more information about Direct Connect, see the Direct Connect. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 88
94 9 Virtual IP Address 9 Virtual IP Address 9.1 Virtual IP Address Overview What Is a Virtual IP Address? Networking A virtual IP address is an IP address that is not allocated to an actual NIC of an ECS. An ECS can have both private and virtual IP addresses. You can access the ECS through any IP address. A virtual IP address has the same network access capabilities as a private IP address, including layer 2 and layer 3 communication between VPCs, peering connections between VPCs, and Internet access through EIPs, VPN connections, and Direct Connect connections. Virtual IP addresses are used for active and standby switchover of ECSs to achieve high availability. If the active ECS is faulty and cannot provide services, the virtual IP address is dynamically switched to the standby ECS to provide services. This section describes two typical networking modes. Networking mode 1: HA mode Scenario example: If you want to improve service high availability and avoid single points of failure, you can use ECSs that are deployed to work in the active/standby mode or one active and multiple standby modes. These ECSs use the same virtual IP address. If the active ECS is faulty, the standby ECS takes over services from the active ECS and continues to provide services. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 89
95 9 Virtual IP Address Figure 9-1 Networking diagram of the HA mode Bind two ECSs in the same subnet to the same virtual IP address. Configure Keepalived for the two ECSs to work in the active/standby mode. For details about Keepalived configurations, see the common configuration methods in the industry. Networking mode 2: HA load balancing cluster (direct routing mode) Scenario example: If you want to build a high-availability load balancing cluster, use Keepalived and make LVS nodes work as direct routers. Figure 9-2 HA load balancing cluster Bind two ECSs to the same virtual IP address. Configure the two ECSs to be LVS nodes working as direct routers and configure Keepalived for the two LVS nodes to work in the active/standby mode. The two ECSs function as dispatchers to evenly forward requests to backend servers. Configure other two ECSs as backend servers. Issue 21 ( ) Copyright Huawei Technologies Co., Ltd. 90
Virtual Private Cloud. User Guide. Issue 03 Date
 Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
Elastic Load Balance. User Guide. Issue 01 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 01 Date 2018-04-30 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue 01 Date 2018-04-30 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Anti-DDoS. User Guide (Paris) Issue 01 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 01 Date 2018-08-15 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 01 Date 2018-08-15 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
How to set up a Virtual Private Cloud (VPC)
 Date published: 15.06.2018 Estimated reading time: 20 minutes Authors: Editorial Team The bookmarks and navigation in this tutorial are optimized for Adobe Reader. How to set up a Virtual Private Cloud
Date published: 15.06.2018 Estimated reading time: 20 minutes Authors: Editorial Team The bookmarks and navigation in this tutorial are optimized for Adobe Reader. How to set up a Virtual Private Cloud
Virtual Private Network. Network User Guide. Issue 05 Date
 Issue 05 Date 2018-03-30 Contents Contents 1 Overview... 1 1.1 Concepts... 1 1.1.1 VPN... 1 1.1.2 IPsec VPN...1 1.2 Application Scenarios...2 1.3 Billing Standards... 3 1.4 VPN Reference Standards and
Issue 05 Date 2018-03-30 Contents Contents 1 Overview... 1 1.1 Concepts... 1 1.1.1 VPN... 1 1.1.2 IPsec VPN...1 1.2 Application Scenarios...2 1.3 Billing Standards... 3 1.4 VPN Reference Standards and
Virtual Private Cloud. User Guide
 Alibaba Cloud provides a default VPC and VSwitch for you in the situation that you do not have any existing VPC and VSwitch to use when creating a cloud product instance. A default VPC and VSwitch will
Alibaba Cloud provides a default VPC and VSwitch for you in the situation that you do not have any existing VPC and VSwitch to use when creating a cloud product instance. A default VPC and VSwitch will
Amazon Virtual Private Cloud. Getting Started Guide
 Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Amazon Virtual Private Cloud Getting Started Guide Amazon Virtual Private Cloud: Getting Started Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks
Elastic Load Balancing. User Guide. Date
 Date 2018-07-20 Contents Contents 1 Product Description... 4 1.1 What Is Elastic Load Balancing (ELB)?... 4 1.2 Load Balancer Type... 4 1.3 Basic Architecture... 5 1.3.1 Classic Load Balancer... 5 1.3.2
Date 2018-07-20 Contents Contents 1 Product Description... 4 1.1 What Is Elastic Load Balancing (ELB)?... 4 1.2 Load Balancer Type... 4 1.3 Basic Architecture... 5 1.3.1 Classic Load Balancer... 5 1.3.2
Domain Name Service. FAQs. Issue 07 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 07 Date 2019-03-05 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 07 Date 2019-03-05 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Web Cloud Solution. User Guide. Issue 01. Date
 Issue 01 Date 2017-05-30 Contents Contents 1 Overview... 3 1.1 What Is Web (CCE+RDS)?... 3 1.2 Why You Should Choose Web (CCE+RDS)... 3 1.3 Concept and Principle... 4... 5 2.1 Required Services... 5 2.2
Issue 01 Date 2017-05-30 Contents Contents 1 Overview... 3 1.1 What Is Web (CCE+RDS)?... 3 1.2 Why You Should Choose Web (CCE+RDS)... 3 1.3 Concept and Principle... 4... 5 2.1 Required Services... 5 2.2
Advanced Anti-DDoS. User Guide. Issue 17 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 17 Date 2018-08-13 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 17 Date 2018-08-13 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Database Security Service. FAQs. Issue 19 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 19 Date 2019-04-08 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 19 Date 2019-04-08 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
SAP Business One. User Guide. Issue 04 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 04 Date 2018-12-31 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 04 Date 2018-12-31 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Workspace. User Guide (Administrators) Issue 19 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 19 Date 2018-10-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 19 Date 2018-10-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Workspace. User Guide (Administrators) Issue 18 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 18 Date 2018-08-17 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 18 Date 2018-08-17 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Elastic Load Balance. User Guide. Issue 14 Date
 Issue 14 Date 2018-02-28 Contents Contents 1 Overview... 1 1.1 Basic Concepts... 1 1.1.1 Elastic Load Balance... 1 1.1.2 Public Network Load Balancer...1 1.1.3 Private Network Load Balancer... 2 1.1.4
Issue 14 Date 2018-02-28 Contents Contents 1 Overview... 1 1.1 Basic Concepts... 1 1.1.1 Elastic Load Balance... 1 1.1.2 Public Network Load Balancer...1 1.1.3 Private Network Load Balancer... 2 1.1.4
Live Streaming Accelerator. Quick Start. Issue 03 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 03 Date 2018-08-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 03 Date 2018-08-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Workspace. User Guide (Administrators) Issue 04 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 04 Date 2018-10-12 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 04 Date 2018-10-12 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Overview. AWS networking services including: VPC Extend your network into a virtual private cloud. EIP Elastic IP
 Networking in AWS 2017 Amazon Web Services, Inc. and its affiliates. All rights served. May not be copied, modified, or distributed in whole or in part without the express consent of Amazon Web Services,
Networking in AWS 2017 Amazon Web Services, Inc. and its affiliates. All rights served. May not be copied, modified, or distributed in whole or in part without the express consent of Amazon Web Services,
Direct Connect. User Guide. Issue 4 Date
 Issue 4 Date 2017-10-30 Contents Contents 1 Change History... 1 2 Overview... 6 2.1 What Is Direct Connect?...6 2.2 Direct Connect Application Scenarios... 6 2.3 Charging Standards...7 3 Getting Started...
Issue 4 Date 2017-10-30 Contents Contents 1 Change History... 1 2 Overview... 6 2.1 What Is Direct Connect?...6 2.2 Direct Connect Application Scenarios... 6 2.3 Charging Standards...7 3 Getting Started...
Unified Load Balance. User Guide. Issue 04 Date
 Issue 04 Date 2017-09-06 Contents Contents 1 Overview... 1 1.1 Basic Concepts... 1 1.1.1 Unified Load Balance...1 1.1.2 Listener... 1 1.1.3 Health Check... 2 1.1.4 Region...2 1.1.5 Project...2 1.2 Functions...
Issue 04 Date 2017-09-06 Contents Contents 1 Overview... 1 1.1 Basic Concepts... 1 1.1.1 Unified Load Balance...1 1.1.2 Listener... 1 1.1.3 Health Check... 2 1.1.4 Region...2 1.1.5 Project...2 1.2 Functions...
vcloud Air - Virtual Private Cloud OnDemand Networking Guide
 vcloud Air - Virtual Private Cloud OnDemand Networking Guide vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
vcloud Air - Virtual Private Cloud OnDemand Networking Guide vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Domain Name Service. Product Description. Issue 03 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 03 Date 2018-08-15 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 03 Date 2018-08-15 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Amazon Virtual Private Cloud. User Guide API Version
 Amazon Virtual Private Cloud User Guide Amazon Web Services Amazon Virtual Private Cloud: User Guide Amazon Web Services Copyright 2012 Amazon Web Services LLC or its affiliates. All rights reserved. The
Amazon Virtual Private Cloud User Guide Amazon Web Services Amazon Virtual Private Cloud: User Guide Amazon Web Services Copyright 2012 Amazon Web Services LLC or its affiliates. All rights reserved. The
Anti-DDoS. FAQs. Issue 11 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 11 Date 2018-05-28 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 11 Date 2018-05-28 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
25 Best Practice Tips for architecting Amazon VPC
 25 Best Practice Tips for architecting Amazon VPC 25 Best Practice Tips for architecting Amazon VPC Amazon VPC is one of the most important feature introduced by AWS. We have been using AWS from 2008 and
25 Best Practice Tips for architecting Amazon VPC 25 Best Practice Tips for architecting Amazon VPC Amazon VPC is one of the most important feature introduced by AWS. We have been using AWS from 2008 and
Vulnerability Scan Service. User Guide. Issue 20 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 20 Date 2018-08-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 20 Date 2018-08-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Anti-DDoS. User Guide. Issue 05 Date
 Issue 05 Date 2017-02-08 Contents Contents 1 Introduction... 1 1.1 Functions... 1 1.2 Application Scenarios...1 1.3 Accessing and Using Anti-DDoS... 2 1.3.1 How to Access Anti-DDoS...2 1.3.2 How to Use
Issue 05 Date 2017-02-08 Contents Contents 1 Introduction... 1 1.1 Functions... 1 1.2 Application Scenarios...1 1.3 Accessing and Using Anti-DDoS... 2 1.3.1 How to Access Anti-DDoS...2 1.3.2 How to Use
Cloud Stream Service. User Guide. Issue 18 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 18 Date 2018-11-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 18 Date 2018-11-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
HUAWEI Secospace USG Series User Management and Control White Paper
 Doc. code HUAWEI Secospace USG Series User Management and Control White Paper Issue 1.0 Date 2014-03-27 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2012. All rights reserved.
Doc. code HUAWEI Secospace USG Series User Management and Control White Paper Issue 1.0 Date 2014-03-27 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2012. All rights reserved.
Relational Database Service. User Guide. Issue 05 Date
 Issue 05 Date 2017-02-08 Contents Contents 1 Introduction... 1 1.1 Concepts... 2 1.1.1 RDS... 2 1.1.2 DB Cluster... 2 1.1.3 DB Instance... 2 1.1.4 DB Backup... 3 1.1.5 DB Snapshot... 3 1.2 RDS DB Instances...
Issue 05 Date 2017-02-08 Contents Contents 1 Introduction... 1 1.1 Concepts... 2 1.1.1 RDS... 2 1.1.2 DB Cluster... 2 1.1.3 DB Instance... 2 1.1.4 DB Backup... 3 1.1.5 DB Snapshot... 3 1.2 RDS DB Instances...
Virtual Private Cloud. VPC Product Introduction
 Product overview This document contains the following topics: - VPC overview - Basic architecture - VPC benefits VPC overview The Alibaba Cloud Virtual Private Cloud (VPC) is a private network established
Product overview This document contains the following topics: - VPC overview - Basic architecture - VPC benefits VPC overview The Alibaba Cloud Virtual Private Cloud (VPC) is a private network established
Object Storage Service. Product Introduction. Issue 04 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 04 Date 2017-12-20 HUAWEI TECHNOLOGIES CO., LTD. 2017. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue 04 Date 2017-12-20 HUAWEI TECHNOLOGIES CO., LTD. 2017. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
CDN. Product Description. Issue 03 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 03 Date 2018-08-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 03 Date 2018-08-30 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
SAP HANA. HA and DR Guide. Issue 03 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 03 Date 2018-05-23 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 03 Date 2018-05-23 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Workspace. User Guide (Administrators) Date
 Date 2018-11-12 Contents Contents 1 Introduction... 1 1.1 Concepts... 1 1.1.1...1 1.1.2 Software Client... 2 1.1.3 Mobile Terminal... 2 1.1.4 Infrastructure Server... 2 1.1.5 AD Management Server... 2
Date 2018-11-12 Contents Contents 1 Introduction... 1 1.1 Concepts... 1 1.1.1...1 1.1.2 Software Client... 2 1.1.3 Mobile Terminal... 2 1.1.4 Infrastructure Server... 2 1.1.5 AD Management Server... 2
25 Best Practice Tips for architecting Amazon VPC. 25 Best Practice Tips for architecting Amazon VPC. Harish Ganesan- CTO- 8KMiles
 25 Best Practice Tips for architecting Amazon VPC 25 Best Practice Tips for architecting Amazon VPC Amazon VPC is one of the most important feature introduced by AWS. We have been using AWS from 2008 and
25 Best Practice Tips for architecting Amazon VPC 25 Best Practice Tips for architecting Amazon VPC Amazon VPC is one of the most important feature introduced by AWS. We have been using AWS from 2008 and
Third-Party Client (s3fs) User Guide
 Issue 02 Date 2017-09-28 HUAWEI TECHNOLOGIES CO., LTD. 2017. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue 02 Date 2017-09-28 HUAWEI TECHNOLOGIES CO., LTD. 2017. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Amazon Web Services Hands- On VPC
 Amazon Web Services Hands- On VPC Copyright 2011-2015, Amazon Web Services, All Rights Reserved Page 1 Table of Contents Overview... 3 Create a VPC... 3 VPC Object Walkthrough... 6 Your VPCs... 6 Subnets...
Amazon Web Services Hands- On VPC Copyright 2011-2015, Amazon Web Services, All Rights Reserved Page 1 Table of Contents Overview... 3 Create a VPC... 3 VPC Object Walkthrough... 6 Your VPCs... 6 Subnets...
Third-Party Client (s3fs) User Guide
 Issue 02 Date 2017-09-28 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue 02 Date 2017-09-28 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
FunctionGraph. Best Practices. Issue 05 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 05 Date 2018-09-12 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 05 Date 2018-09-12 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
HUAWEI USG6000 Series Next-Generation Firewall Technical White Paper VPN HUAWEI TECHNOLOGIES CO., LTD. Issue 1.1. Date
 HUAWEI USG6000 Series Next-Generation Firewall Technical White Paper VPN Issue 1.1 Date 2014-03-14 HUAWEI TECHNOLOGIES CO., LTD. 2014. All rights reserved. No part of this document may be reproduced or
HUAWEI USG6000 Series Next-Generation Firewall Technical White Paper VPN Issue 1.1 Date 2014-03-14 HUAWEI TECHNOLOGIES CO., LTD. 2014. All rights reserved. No part of this document may be reproduced or
NGF0502 AWS Student Slides
 NextGen Firewall AWS Use Cases Barracuda NextGen Firewall F Implementation Guide Architectures and Deployments Based on four use cases Edge Firewall Secure Remote Access Office to Cloud / Hybrid Cloud
NextGen Firewall AWS Use Cases Barracuda NextGen Firewall F Implementation Guide Architectures and Deployments Based on four use cases Edge Firewall Secure Remote Access Office to Cloud / Hybrid Cloud
Amazon Virtual Private Cloud. VPC Peering Guide
 Amazon Virtual Private Cloud VPC Peering Guide Amazon Virtual Private Cloud: VPC Peering Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and
Amazon Virtual Private Cloud VPC Peering Guide Amazon Virtual Private Cloud: VPC Peering Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and
Configuring AWS for Zerto Virtual Replication
 Configuring AWS for Zerto Virtual Replication VERSION 1 MARCH 2018 Table of Contents 1. Prerequisites... 2 1.1. AWS Prerequisites... 2 1.2. Additional AWS Resources... 3 2. AWS Workflow... 3 3. Setting
Configuring AWS for Zerto Virtual Replication VERSION 1 MARCH 2018 Table of Contents 1. Prerequisites... 2 1.1. AWS Prerequisites... 2 1.2. Additional AWS Resources... 3 2. AWS Workflow... 3 3. Setting
FortiMail AWS Deployment Guide
 FortiMail AWS Deployment Guide FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE & SUPPORT https://support.fortinet.com
FortiMail AWS Deployment Guide FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE & SUPPORT https://support.fortinet.com
lab Highly Available and Fault Tolerant Architecture for Web Applications inside a VPC V1.01 AWS Certified Solutions Architect Associate lab title
 lab lab title Highly Available and Fault Tolerant Architecture for Web Applications inside a VPC V1.01 Course title AWS Certified Solutions Architect Associate Table of Contents Contents Table of Contents...
lab lab title Highly Available and Fault Tolerant Architecture for Web Applications inside a VPC V1.01 Course title AWS Certified Solutions Architect Associate Table of Contents Contents Table of Contents...
EdgeConnect for Amazon Web Services (AWS)
 Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Amazon Virtual Private Cloud. VPC Peering
 Amazon Virtual Private Cloud VPC Peering Amazon Virtual Private Cloud: VPC Peering Table of Contents What is VPC Peering?... 1 VPC Peering Basics... 1 VPC Peering Connection Lifecycle... 2 Multiple VPC
Amazon Virtual Private Cloud VPC Peering Amazon Virtual Private Cloud: VPC Peering Table of Contents What is VPC Peering?... 1 VPC Peering Basics... 1 VPC Peering Connection Lifecycle... 2 Multiple VPC
Building a Modular and Scalable Virtual Network Architecture with Amazon VPC
 Building a Modular and Scalable Virtual Network Architecture with Amazon VPC Quick Start Reference Deployment Santiago Cardenas Solutions Architect, AWS Quick Start Reference Team August 2016 (revisions)
Building a Modular and Scalable Virtual Network Architecture with Amazon VPC Quick Start Reference Deployment Santiago Cardenas Solutions Architect, AWS Quick Start Reference Team August 2016 (revisions)
My Account. User Guide. Issue 01 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 01 Date 2018-09-28 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 01 Date 2018-09-28 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
ForeScout CounterACT. (AWS) Plugin. Configuration Guide. Version 1.3
 ForeScout CounterACT Hybrid Cloud Module: Amazon Web Services (AWS) Plugin Version 1.3 Table of Contents Amazon Web Services Plugin Overview... 4 Use Cases... 5 Providing Consolidated Visibility... 5 Dynamic
ForeScout CounterACT Hybrid Cloud Module: Amazon Web Services (AWS) Plugin Version 1.3 Table of Contents Amazon Web Services Plugin Overview... 4 Use Cases... 5 Providing Consolidated Visibility... 5 Dynamic
Security Group Guardrails for AWS
 Turbot HQ, Inc 1732 1st Ave #20232 New York, NY 10128 USA info@turbot.com https://turbot.com +1 973 922 0297 Overview Security Groups are a critical control point in applications on AWS. Turbot provides
Turbot HQ, Inc 1732 1st Ave #20232 New York, NY 10128 USA info@turbot.com https://turbot.com +1 973 922 0297 Overview Security Groups are a critical control point in applications on AWS. Turbot provides
AD SSO Technical White Paper
 Issue V1.0 Date 2017-02-28 Huawei Technologies Co., Ltd. 2017. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue V1.0 Date 2017-02-28 Huawei Technologies Co., Ltd. 2017. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Deploy the Firepower Management Center Virtual On the AWS Cloud
 Deploy the Firepower Management Center Virtual On the AWS Cloud Amazon Virtual Private Cloud (Amazon VPC) enables you to launch Amazon Web Services (AWS) resources into a virtual network that you define.
Deploy the Firepower Management Center Virtual On the AWS Cloud Amazon Virtual Private Cloud (Amazon VPC) enables you to launch Amazon Web Services (AWS) resources into a virtual network that you define.
Cloudera s Enterprise Data Hub on the Amazon Web Services Cloud: Quick Start Reference Deployment October 2014
 Cloudera s Enterprise Data Hub on the Amazon Web Services Cloud: Quick Start Reference Deployment October 2014 Karthik Krishnan Page 1 of 20 Table of Contents Table of Contents... 2 Abstract... 3 What
Cloudera s Enterprise Data Hub on the Amazon Web Services Cloud: Quick Start Reference Deployment October 2014 Karthik Krishnan Page 1 of 20 Table of Contents Table of Contents... 2 Abstract... 3 What
H3C SecPath Series High-End Firewalls
 H3C SecPath Series High-End Firewalls NAT and ALG Configuration Guide Hangzhou H3C Technologies Co., Ltd. http://www.h3c.com Software version: SECPATHF1000SAI&F1000AEI&F1000ESI-CMW520-R3721 SECPATH5000FA-CMW520-F3210
H3C SecPath Series High-End Firewalls NAT and ALG Configuration Guide Hangzhou H3C Technologies Co., Ltd. http://www.h3c.com Software version: SECPATHF1000SAI&F1000AEI&F1000ESI-CMW520-R3721 SECPATH5000FA-CMW520-F3210
How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud
 How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud The Barracuda NG Firewall can run as a virtual appliance in the Amazon cloud as a gateway device for Amazon EC2 instances in an
How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud The Barracuda NG Firewall can run as a virtual appliance in the Amazon cloud as a gateway device for Amazon EC2 instances in an
CloudEdge Deployment Guide
 Hillstone Networks, Inc. CloudEdge Deployment Guide Version 5.5R3P1 Copyright 2016Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice. The software
Hillstone Networks, Inc. CloudEdge Deployment Guide Version 5.5R3P1 Copyright 2016Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice. The software
Object Storage Service. Client Guide (OBS Browser) Issue 10 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 10 Date 2018-07-15 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue 10 Date 2018-07-15 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
SIOS DataKeeper Cluster Edition on the AWS Cloud
 SIOS DataKeeper Cluster Edition on the AWS Cloud Quick Start Reference Deployment April 2017 Last update: May 2017 (revisions) SIOS Technology Corp. AWS Quick Start Reference Team Contents Overview...
SIOS DataKeeper Cluster Edition on the AWS Cloud Quick Start Reference Deployment April 2017 Last update: May 2017 (revisions) SIOS Technology Corp. AWS Quick Start Reference Team Contents Overview...
SAM 8.0 SP2 Deployment at AWS. Version 1.0
 SAM 8.0 SP2 Deployment at AWS Version 1.0 Publication Date July 2011 Copyright 2011 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and
SAM 8.0 SP2 Deployment at AWS Version 1.0 Publication Date July 2011 Copyright 2011 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and
Huawei CloudEngine Series. VXLAN Technology White Paper. Issue 06 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 06 Date 2016-07-28 HUAWEI TECHNOLOGIES CO., LTD. 2016. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue 06 Date 2016-07-28 HUAWEI TECHNOLOGIES CO., LTD. 2016. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Amazon AppStream 2.0: SOLIDWORKS Deployment Guide
 2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
esight V300R001C10 SLA Technical White Paper Issue 01 Date HUAWEI TECHNOLOGIES CO., LTD.
 V300R001C10 Issue 01 Date 2013-12-10 HUAWEI TECHNOLOGIES CO., LTD. 2013. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written
V300R001C10 Issue 01 Date 2013-12-10 HUAWEI TECHNOLOGIES CO., LTD. 2013. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written
vcloud Director Tenant Portal Guide vcloud Director 8.20
 vcloud Director Tenant Portal Guide vcloud Director 8.20 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
vcloud Director Tenant Portal Guide vcloud Director 8.20 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
How to Install Forcepoint NGFW in Amazon AWS TECHNICAL DOCUMENT
 How to Install Forcepoint NGFW in Amazon AWS TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS... 1 TEST NETWORK DIAGRAM... 2 PREPARING YOUR VPC... 3 IP addressing... 3 Virtual Private Cloud (VPC)...
How to Install Forcepoint NGFW in Amazon AWS TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS... 1 TEST NETWORK DIAGRAM... 2 PREPARING YOUR VPC... 3 IP addressing... 3 Virtual Private Cloud (VPC)...
Amazon AppStream 2.0: Getting Started Guide
 2018 Amazon AppStream 2.0: Getting Started Guide Build an Amazon AppStream 2.0 environment to stream desktop applications to your users April 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide
2018 Amazon AppStream 2.0: Getting Started Guide Build an Amazon AppStream 2.0 environment to stream desktop applications to your users April 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide
NetApp Cloud Volumes Service for AWS
 NetApp Cloud Volumes Service for AWS AWS Account Setup Cloud Volumes Team, NetApp, Inc. March 29, 2019 Abstract This document provides instructions to set up the initial AWS environment for using the NetApp
NetApp Cloud Volumes Service for AWS AWS Account Setup Cloud Volumes Team, NetApp, Inc. March 29, 2019 Abstract This document provides instructions to set up the initial AWS environment for using the NetApp
AWS Networking Fundamentals
 AWS Networking Fundamentals Tom Adamski Specialist Solutions Architect, AWS Traditional Network WAN VPN VPN Fiber Applications Applications AWS Network VPN WAN (AWS Direct Connect) VPN Fiber Applications
AWS Networking Fundamentals Tom Adamski Specialist Solutions Architect, AWS Traditional Network WAN VPN VPN Fiber Applications Applications AWS Network VPN WAN (AWS Direct Connect) VPN Fiber Applications
CloudEdge SG6000-VM Installation Guide
 Hillstone Networks, Inc. CloudEdge SG6000-VM Installation Guide Version 5.5R1 Copyright 2015Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice.
Hillstone Networks, Inc. CloudEdge SG6000-VM Installation Guide Version 5.5R1 Copyright 2015Hillstone Networks, Inc.. All rights reserved. Information in this document is subject to change without notice.
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
PVS Deployment in the Cloud. Last Updated: June 17, 2016
 PVS Deployment in the Cloud Last Updated: June 17, 2016 Contents Amazon Web Services Introduction 3 Software Requirements 4 Set up a NAT Gateway 5 Install PVS on the NAT Gateway 11 Example Deployment 12
PVS Deployment in the Cloud Last Updated: June 17, 2016 Contents Amazon Web Services Introduction 3 Software Requirements 4 Set up a NAT Gateway 5 Install PVS on the NAT Gateway 11 Example Deployment 12
vcloud Director User's Guide 04 OCT 2018 vcloud Director 9.5
 vcloud Director User's Guide 04 OCT 2018 vcloud Director 9.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
vcloud Director User's Guide 04 OCT 2018 vcloud Director 9.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
Creating your Virtual Data Centre
 Creating your Virtual Data Centre VPC Fundamentals and Connectivity Options Paul Burne, Senior Technical Account Manager, Enterprise Support - 28 th June 2017 2016, Amazon Web Services, Inc. or its Affiliates.
Creating your Virtual Data Centre VPC Fundamentals and Connectivity Options Paul Burne, Senior Technical Account Manager, Enterprise Support - 28 th June 2017 2016, Amazon Web Services, Inc. or its Affiliates.
Huawei FusionCloud Desktop Solution 5.3. Branch Technical White Paper. Issue 01. Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 01 Date 2015-06-30 HUAWEI TECHNOLOGIES CO., LTD. 2015. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue 01 Date 2015-06-30 HUAWEI TECHNOLOGIES CO., LTD. 2015. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Remote Desktop Gateway on the AWS Cloud
 Remote Desktop Gateway on the AWS Cloud Quick Start Reference Deployment Santiago Cardenas Solutions Architect, AWS Quick Start Team April 2014 Last update: June 2017 (revisions) This guide is also available
Remote Desktop Gateway on the AWS Cloud Quick Start Reference Deployment Santiago Cardenas Solutions Architect, AWS Quick Start Team April 2014 Last update: June 2017 (revisions) This guide is also available
OceanStor 9000 InfiniBand Technical White Paper. Issue V1.01 Date HUAWEI TECHNOLOGIES CO., LTD.
 OceanStor 9000 Issue V1.01 Date 2014-03-29 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2014. All rights reserved. No part of this document may be reproduced or transmitted in
OceanStor 9000 Issue V1.01 Date 2014-03-29 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2014. All rights reserved. No part of this document may be reproduced or transmitted in
Deploy VPN IPSec Tunnels on Oracle Cloud Infrastructure. White Paper September 2017 Version 1.0
 Deploy VPN IPSec Tunnels on Oracle Cloud Infrastructure White Paper September 2017 Version 1.0 Disclaimer The following is intended to outline our general product direction. It is intended for information
Deploy VPN IPSec Tunnels on Oracle Cloud Infrastructure White Paper September 2017 Version 1.0 Disclaimer The following is intended to outline our general product direction. It is intended for information
ForeScout Amazon Web Services (AWS) Plugin
 ForeScout Amazon Web Services (AWS) Plugin Version 1.1.1 and above Table of Contents Amazon Web Services Plugin Overview... 4 Use Cases... 5 Providing Consolidated Visibility... 5 Dynamic Segmentation
ForeScout Amazon Web Services (AWS) Plugin Version 1.1.1 and above Table of Contents Amazon Web Services Plugin Overview... 4 Use Cases... 5 Providing Consolidated Visibility... 5 Dynamic Segmentation
Mediant Cloud Edition (CE)
 Installation Manual AudioCodes Mediant Family of Session Border Controllers (SBC) Mediant Cloud Edition (CE) Session Border Controller Version 7.2 Installation Manual Contents Table of Contents 1 Introduction...
Installation Manual AudioCodes Mediant Family of Session Border Controllers (SBC) Mediant Cloud Edition (CE) Session Border Controller Version 7.2 Installation Manual Contents Table of Contents 1 Introduction...
Configuring a Palo Alto Firewall in AWS
 Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Cloud Services. Introduction
 Introduction adi Digital have developed a resilient, secure, flexible, high availability Software as a Service (SaaS) cloud platform. This Platform provides a simple to use, cost effective and convenient
Introduction adi Digital have developed a resilient, secure, flexible, high availability Software as a Service (SaaS) cloud platform. This Platform provides a simple to use, cost effective and convenient
Horizon DaaS Platform 6.1 Service Provider Installation - vcloud
 Horizon DaaS Platform 6.1 Service Provider Installation - vcloud This guide provides information on how to install and configure the DaaS platform Service Provider appliances using vcloud discovery of
Horizon DaaS Platform 6.1 Service Provider Installation - vcloud This guide provides information on how to install and configure the DaaS platform Service Provider appliances using vcloud discovery of
HUAWEI AR Series SEP Technical White Paper HUAWEI TECHNOLOGIES CO., LTD. Issue 1.0. Date
 HUAWEI AR Series SEP Technical White Paper Issue 1.0 Date 2015-01-19 HUAWEI TECHNOLOGIES CO., LTD. 2015. All rights reserved. No part of this document may be reproduced or transmitted in any form or by
HUAWEI AR Series SEP Technical White Paper Issue 1.0 Date 2015-01-19 HUAWEI TECHNOLOGIES CO., LTD. 2015. All rights reserved. No part of this document may be reproduced or transmitted in any form or by
SecBlade Firewall Cards NAT Configuration Examples
 SecBlade Firewall Cards NAT Configuration Examples Keywords: NAT, PAT, private IP address, public IP address, IP address pool Abstract: This document describes the characteristics, applications scenarios,
SecBlade Firewall Cards NAT Configuration Examples Keywords: NAT, PAT, private IP address, public IP address, IP address pool Abstract: This document describes the characteristics, applications scenarios,
1. Click on "IaaS" to advance to the Windows Azure Scenario. 2. Click to configure the "CloudNet" Virtual Network
 Introduction to the Virtual Network Lab Scenario Steps Description 1. Click on "IaaS" to advance to the Windows Azure Scenario Windows Azure Infrastructure Services ( IaaS ) provides us with the capability
Introduction to the Virtual Network Lab Scenario Steps Description 1. Click on "IaaS" to advance to the Windows Azure Scenario Windows Azure Infrastructure Services ( IaaS ) provides us with the capability
unisys Unisys Stealth(cloud) for Amazon Web Services Deployment Guide Release 2.0 May
 unisys Unisys Stealth(cloud) for Amazon Web Services Deployment Guide Release 2.0 May 2016 8205 5658-002 NO WARRANTIES OF ANY NATURE ARE EXTENDED BY THIS DOCUMENT. Any product or related information described
unisys Unisys Stealth(cloud) for Amazon Web Services Deployment Guide Release 2.0 May 2016 8205 5658-002 NO WARRANTIES OF ANY NATURE ARE EXTENDED BY THIS DOCUMENT. Any product or related information described
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Data Ingestion Service. SDK Development Guide. Issue 03 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 03 Date 2018-06-12 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue 03 Date 2018-06-12 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
MyIGW Main. Oregon. MyVPC /16. MySecurityGroup / us-west-2b. Type Port Source SSH /0 HTTP
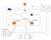 MyIGW Main Oregon MyVPC 10.0.0.0/16 10.0.1.0/24 10.0.1.0 -- us-west-2a MySecurityGroup 10.0.2.0/24 10.0.2.0 -- us-west-2b MyWebServer1 MyDBServer DMZ MyInternetRouteTable 0.0.0.0/0 IGW Type Port Source
MyIGW Main Oregon MyVPC 10.0.0.0/16 10.0.1.0/24 10.0.1.0 -- us-west-2a MySecurityGroup 10.0.2.0/24 10.0.2.0 -- us-west-2b MyWebServer1 MyDBServer DMZ MyInternetRouteTable 0.0.0.0/0 IGW Type Port Source
Creating Application Containers
 This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 2 About Application Container Templates, page 5 Creating
This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 2 About Application Container Templates, page 5 Creating
VMware Cloud on AWS Getting Started. 18 DEC 2017 VMware Cloud on AWS
 VMware Cloud on AWS Getting Started 18 DEC 2017 VMware Cloud on AWS You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about
VMware Cloud on AWS Getting Started 18 DEC 2017 VMware Cloud on AWS You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about
Service Portal User Guide
 FUJITSU Cloud Service K5 IaaS Service Portal User Guide Version 1.4 FUJITSU LIMITED All Rights Reserved, Copyright FUJITSU LIMITED 2015-2016 K5IA-DC-M-005-001E Preface Purpose of This Manual This manual
FUJITSU Cloud Service K5 IaaS Service Portal User Guide Version 1.4 FUJITSU LIMITED All Rights Reserved, Copyright FUJITSU LIMITED 2015-2016 K5IA-DC-M-005-001E Preface Purpose of This Manual This manual
Huawei FusionCloud Desktop Solution 5.1 Resource Reuse Technical White Paper HUAWEI TECHNOLOGIES CO., LTD. Issue 01.
 Huawei FusionCloud Desktop Solution 5.1 Resource Reuse Technical White Paper Issue 01 Date 2014-03-26 HUAWEI TECHNOLOGIES CO., LTD. 2014. All rights reserved. No part of this document may be reproduced
Huawei FusionCloud Desktop Solution 5.1 Resource Reuse Technical White Paper Issue 01 Date 2014-03-26 HUAWEI TECHNOLOGIES CO., LTD. 2014. All rights reserved. No part of this document may be reproduced
Flexible Engine. Startup Guide
 Flexible Engine Startup Guide This guide presents the deployment of a web server accessible from the internet and its database, on the Flexible Engine platform 2017 Orange Business Services version July
Flexible Engine Startup Guide This guide presents the deployment of a web server accessible from the internet and its database, on the Flexible Engine platform 2017 Orange Business Services version July
AWS VPC Cloud Environment Setup
 AWS VPC Cloud Environment Setup Table of Contents Introduction 3 Requirements 5 Step 1: VPC Deployment Setup 10 Step 2: Launching a VNS3 Controller 15 Instance VNS3 Configuration Document Links 19 2 Introduction
AWS VPC Cloud Environment Setup Table of Contents Introduction 3 Requirements 5 Step 1: VPC Deployment Setup 10 Step 2: Launching a VNS3 Controller 15 Instance VNS3 Configuration Document Links 19 2 Introduction
Installation of Informatica Services on Amazon EC2
 Installation of Informatica Services on Amazon EC2 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Installation of Informatica Services on Amazon EC2 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Distributed Message Service. User Guide. Issue 14 Date
 Issue 14 Date 2018-08-15 Contents Contents 1 Getting Started... 1 1.1 Creating a Queue... 1 1.2 Creating a Consumer Group... 3 1.3 Creating a Message...4 1.4 Retrieving Messages...6 2 Managing Queues and
Issue 14 Date 2018-08-15 Contents Contents 1 Getting Started... 1 1.1 Creating a Queue... 1 1.2 Creating a Consumer Group... 3 1.3 Creating a Message...4 1.4 Retrieving Messages...6 2 Managing Queues and
vcloud Director User's Guide
 vcloud Director 8.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
vcloud Director 8.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
