[MS-SSTP]: Secure Socket Tunneling Protocol (SSTP)
|
|
|
- Caitlin Washington
- 6 years ago
- Views:
Transcription
1 [MS-SSTP]: Secure Socket Tunneling Protocol (SSTP) This topic lists the Errata found in [MS-SSTP] since it was last published. Since this topic is updated frequently, we recommend that you subscribe to these RSS or Atom feeds to receive update notifications. Errata are subject to the same terms as the Open Specifications documentation referenced. RSS Atom Errata below are for Protocol Document Version V /10/16. Errata 2015/11/23 In Section 2.2.4, SSTP Attributes, clarified the attribute-specific data. (variable): A variable-length field with length equal to field Length minus 4 that contains the attribute-specific data. (variable): A variable-length field with length equal to field Length minus 4 that contains the attribute-specific data. The different attribute-specific data are described in sections to The fields "Reserved", "Attribute ID", "LengthPacket" have been repeated in those sections for complete illustration. 2015/11/23 In Section 2.2.2, SSTP Control Packet, corrected the Attribute field lengths. Attribute 1 (4 bytes): MUST contain the first attribute. Attribute 2 (4 bytes): MUST contain the second attribute. Attribute N (variable): An ordered list of variable-sized attributes that compose an SSTP control message. Each attribute MUST follow the format as specified in section
2 Attributes (variable): An ordered list of variable-sized attributes that compose an SSTP control message. Each attribute MUST follow the format as specified in section /11/23 In Section 2.2.8, Status Info Attribute, changed the Attribute ID field value from 0x2 to 0x02. Attribute ID (1 byte): An 8-bit (1-byte) field that is used to specify the type of attribute; its value MUST be 0x2 for the Status Info attribute. Attribute ID (1 byte): An 8-bit (1-byte) field that is used to specify the type of attribute; its value MUST be 0x02 for the Status Info attribute. 2015/11/23 In Section 2.2.9, Call Connect Request Message (SSTP_MSG_CALL_CONNECT_REQUEST), specified the length value in the Length field description. Length (12 bits): A 12-bit unsigned integer in network byte order that MUST specify the length, in bytes, of the entire message. Length (12 bits): A 12-bit unsigned integer in network byte order that contains the value 0x00e for the length of the entire message. 2015/11/23 In Section 2.2.6, Crypto Binding Request Attribute, in the Hash Protocol Bitmask field description, clarified how the bits are defined. Hash Protocol Bitmask (1 byte): This 1-byte bitmask field is used (with the ServerHashProtocolSupported state variable described in section 3.3.1) to specify the hashing methods allowed by the server that the client uses to compute the Compound MAC in the
3 Crypto Binding attribute. For more information, see section The following bits are defined. CERT_HASH_PROTOCOL_SHA1 CERT_HASH_PROTOCOL_SHA256 0x01 0x02 Hash Protocol Bitmask (1 byte): This 1-byte bitmask field is used (with the ServerHashProtocolSupported state variable described in section 3.3.1) to specify the hashing methods allowed by the server that the client uses to compute the Compound MAC in the Crypto Binding attribute. For more information, see section The following bits are defined. A 1 MUST be placed in the appropriate bit position to select the supported hash protocol. The server MUST select at least one hash protocol. If the server selects both the SHA256 and the SHA1 hash protocols and the client supports both hash protocols (as indicated by the value of the ClientHashProtocolSupported state variable described in section 3.2.1), then the client MUST select the SHA256 protocol. For more information about how the client processes the Hash Protocol Bitmask when it receives a Call Connect Acknowledge message, see section B A Where the bits are defined as: A B Description CERT_HASH_PROTOCOL_SHA1 is enabled when A=1 and is disabled when A=0. CERT_HASH_PROTOCOL_SHA256 is enabled when B=1 and is disabled when B= /11/23 In Section , Call Connect Negative Acknowledgment Message (SSTP_MSG_CALL_CONNECT_NAK), and Section , Call Abort Message (SSTP_MSG_CALL_ABORT), removed a value from the Status field tables. In Section , Call Connect Negative Acknowledgment Message (SSTP_MSG_CALL_CONNECT_NAK), changed from:
4 ATTRIB_STATUS_VALUE_NOT_SUPPORTED 0x x a ATTRIB_STATUS_VALUE_NOT_SUPPORTED 0x x a In Section , Call Abort Message (SSTP_MSG_CALL_ABORT), changed from: ATTRIB_STATUS_NEGOTIATION_TIMEOUT 0x x A ATTRIB_STATUS_NEGOTIATION_TIMEOUT 0x
5 * Date format: YYYY/MM/DD
[MS-WSUSOD]: Windows Server Update Services Protocols Overview
![[MS-WSUSOD]: Windows Server Update Services Protocols Overview [MS-WSUSOD]: Windows Server Update Services Protocols Overview](/thumbs/94/122350109.jpg) [MS-WSUSOD]: Windows Server Update Services Protocols Overview This topic lists the found in [MS-WSUSOD] since it was last published. Since this topic is updated frequently, we recommend that you subscribe
[MS-WSUSOD]: Windows Server Update Services Protocols Overview This topic lists the found in [MS-WSUSOD] since it was last published. Since this topic is updated frequently, we recommend that you subscribe
[MS-CFB]: Compound File Binary File Format
![[MS-CFB]: Compound File Binary File Format [MS-CFB]: Compound File Binary File Format](/thumbs/75/72690559.jpg) [MS-CFB]: Compound File Binary File Format This topic lists the Errata found in the MS-CFB document since it was last published. Since this topic is updated frequently, we recommend that you subscribe
[MS-CFB]: Compound File Binary File Format This topic lists the Errata found in the MS-CFB document since it was last published. Since this topic is updated frequently, we recommend that you subscribe
[MS-FSCC]: File System Control Codes
![[MS-FSCC]: File System Control Codes [MS-FSCC]: File System Control Codes](/thumbs/72/67360938.jpg) [MS-FSCC]: File System Control Codes This topic lists the Errata found in the MS-FSCC document since it was last published. Since this topic is updated frequently, we recommend that you subscribe to these
[MS-FSCC]: File System Control Codes This topic lists the Errata found in the MS-FSCC document since it was last published. Since this topic is updated frequently, we recommend that you subscribe to these
[MS-SSTP]: Secure Socket Tunneling Protocol (SSTP) Intellectual Property Rights Notice for Open Specifications Documentation
![[MS-SSTP]: Secure Socket Tunneling Protocol (SSTP) Intellectual Property Rights Notice for Open Specifications Documentation [MS-SSTP]: Secure Socket Tunneling Protocol (SSTP) Intellectual Property Rights Notice for Open Specifications Documentation](/thumbs/74/69907241.jpg) [MS-SSTP]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
[MS-SSTP]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
[MS-NLMP]: NT LAN Manager (NTLM) Authentication Protocol
![[MS-NLMP]: NT LAN Manager (NTLM) Authentication Protocol [MS-NLMP]: NT LAN Manager (NTLM) Authentication Protocol](/thumbs/78/78170003.jpg) [MS-NLMP]: NT LAN Manager (NTLM) Authentication Protocol This topic lists the Errata found in [MS-NLMP] since it was last published. Since this topic is updated frequently, we recommend that you subscribe
[MS-NLMP]: NT LAN Manager (NTLM) Authentication Protocol This topic lists the Errata found in [MS-NLMP] since it was last published. Since this topic is updated frequently, we recommend that you subscribe
[MS-RDPBCGR]: Remote Desktop Protocol: Basic Connectivity and Graphics Remoting
![[MS-RDPBCGR]: Remote Desktop Protocol: Basic Connectivity and Graphics Remoting [MS-RDPBCGR]: Remote Desktop Protocol: Basic Connectivity and Graphics Remoting](/thumbs/78/77516618.jpg) [MS-RDPBCGR]: Remote Desktop Protocol: Basic Connectivity and Graphics Remoting This topic lists the Errata found in [MS-RDPBCGR] since it was last published. Since this topic is updated frequently, we
[MS-RDPBCGR]: Remote Desktop Protocol: Basic Connectivity and Graphics Remoting This topic lists the Errata found in [MS-RDPBCGR] since it was last published. Since this topic is updated frequently, we
[MS-TDS]: Tabular Data Stream Protocol
![[MS-TDS]: Tabular Data Stream Protocol [MS-TDS]: Tabular Data Stream Protocol](/thumbs/91/105591823.jpg) [MS-TDS]: Tabular Data Stream Protocol This topic lists the Errata found in [MS-TDS] since it was last published. Since this topic is updated frequently, we recommend that you subscribe to these RSS or
[MS-TDS]: Tabular Data Stream Protocol This topic lists the Errata found in [MS-TDS] since it was last published. Since this topic is updated frequently, we recommend that you subscribe to these RSS or
[MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3
![[MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3 [MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3](/thumbs/72/67433777.jpg) [MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3 This topic lists the Errata found in [MS-SMB2] since it was last published. Since this topic is updated frequently, we recommend that you
[MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3 This topic lists the Errata found in [MS-SMB2] since it was last published. Since this topic is updated frequently, we recommend that you
[MS-RMPR]: Rights Management Services (RMS): Client-to-Server Protocol
![[MS-RMPR]: Rights Management Services (RMS): Client-to-Server Protocol [MS-RMPR]: Rights Management Services (RMS): Client-to-Server Protocol](/thumbs/77/75870195.jpg) [MS-RMPR]: Rights Management Services (RMS): Client-to-Server Protocol This topic lists the Errata found in [MS-RMPR] since it was last published. Since this topic is updated frequently, we recommend that
[MS-RMPR]: Rights Management Services (RMS): Client-to-Server Protocol This topic lists the Errata found in [MS-RMPR] since it was last published. Since this topic is updated frequently, we recommend that
[MS-SAMR]: Security Account Manager (SAM) Remote Protocol (Clientto-Server)
![[MS-SAMR]: Security Account Manager (SAM) Remote Protocol (Clientto-Server) [MS-SAMR]: Security Account Manager (SAM) Remote Protocol (Clientto-Server)](/thumbs/78/77739548.jpg) [MS-SAMR]: Security Account Manager (SAM) Remote Protocol (Clientto-Server) This topic lists the Errata found in [MS-SAMR] since it was last published. Since this topic is updated frequently, we recommend
[MS-SAMR]: Security Account Manager (SAM) Remote Protocol (Clientto-Server) This topic lists the Errata found in [MS-SAMR] since it was last published. Since this topic is updated frequently, we recommend
[MS-ADTS]: Active Directory Technical Specification
![[MS-ADTS]: Active Directory Technical Specification [MS-ADTS]: Active Directory Technical Specification](/thumbs/77/74931854.jpg) [MS-ADTS]: Active Directory Technical Specification This topic lists the Errata found in the MS-ADTS document since it was last published. Since this topic is updated frequently, we recommend that you
[MS-ADTS]: Active Directory Technical Specification This topic lists the Errata found in the MS-ADTS document since it was last published. Since this topic is updated frequently, we recommend that you
[MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3
![[MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3 [MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3](/thumbs/95/125416711.jpg) [MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3 This topic lists the Errata found in [MS-SMB2] since it was last published. Since this topic is updated frequently, we recommend that you
[MS-SMB2]: Server Message Block (SMB) Protocol Versions 2 and 3 This topic lists the Errata found in [MS-SMB2] since it was last published. Since this topic is updated frequently, we recommend that you
Binary Encodings for JavaScript Object Notation: JSON-B, JSON-C, JSON-D
 Internet Engineering Task Force P. Hallam-Baker Internet-Draft Comodo Group Inc. Intended status: Standards Track June 11, 2013 Expires: December 13, 2013 Binary Encodings for JavaScript Object Notation:
Internet Engineering Task Force P. Hallam-Baker Internet-Draft Comodo Group Inc. Intended status: Standards Track June 11, 2013 Expires: December 13, 2013 Binary Encodings for JavaScript Object Notation:
Configuring System MTU
 Restrictions for System MTU, on page 1 Information About the MTU, on page 1 How to Configure MTU, on page 2 Configuration Examples for System MTU, on page 4 Additional References for System MTU, on page
Restrictions for System MTU, on page 1 Information About the MTU, on page 1 How to Configure MTU, on page 2 Configuration Examples for System MTU, on page 4 Additional References for System MTU, on page
IPsec NAT Transparency
 The feature introduces support for IP Security (IPsec) traffic to travel through Network Address Translation (NAT) or Port Address Translation (PAT) points in the network by addressing many known incompatibilities
The feature introduces support for IP Security (IPsec) traffic to travel through Network Address Translation (NAT) or Port Address Translation (PAT) points in the network by addressing many known incompatibilities
Peer Content Caching and Retrieval: Hosted Cache Protocol
 [MS-PCHC]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
[MS-PCHC]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
SSH Algorithms for Common Criteria Certification
 The feature provides the list and order of the algorithms that are allowed for Common Criteria Certification. This module describes how to configure the encryption, Message Authentication Code (MAC), and
The feature provides the list and order of the algorithms that are allowed for Common Criteria Certification. This module describes how to configure the encryption, Message Authentication Code (MAC), and
HTTPS--HTTP Server and Client with SSL 3.0
 The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS XE software. SSL provides server authentication, encryption, and message
The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS XE software. SSL provides server authentication, encryption, and message
Crypto Templates. Crypto Template Parameters
 This chapter describes how to configure and use StarOS crypto templates. The CLI Crypto Template Configuration Mode is used to configure an IKEv2 IPSec policy. It includes most of the IPSec parameters
This chapter describes how to configure and use StarOS crypto templates. The CLI Crypto Template Configuration Mode is used to configure an IKEv2 IPSec policy. It includes most of the IPSec parameters
HTTPS--HTTP Server and Client with SSL 3.0
 The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
Operating Omega ATS and Lynx ATS. QUOTE TRANSFER PROTOCOL (QTP) SPECIFICATION v 1.05
 Operating Omega ATS and Lynx ATS QUOTE TRANSFER PROTOCOL (QTP) SPECIFICATION v 1.05 Revision History Date Revision Description of Change April 15, 2016 1.00 Created April 27, 2016 1.01 Edits made to document.
Operating Omega ATS and Lynx ATS QUOTE TRANSFER PROTOCOL (QTP) SPECIFICATION v 1.05 Revision History Date Revision Description of Change April 15, 2016 1.00 Created April 27, 2016 1.01 Edits made to document.
ICC. BACnet MS/TP Server Driver Manual INDUSTRIAL CONTROL COMMUNICATIONS, INC Industrial Control Communications, Inc.
 INDUSTRIAL CONTROL COMMUNICATIONS, INC. BACnet MS/TP Server Driver Manual August 17, 2017 2017 Industrial Control Communications, Inc. TABLE OF CONTENTS 1 BACnet MS/TP Server... 2 1.1 Overview... 2 1.2
INDUSTRIAL CONTROL COMMUNICATIONS, INC. BACnet MS/TP Server Driver Manual August 17, 2017 2017 Industrial Control Communications, Inc. TABLE OF CONTENTS 1 BACnet MS/TP Server... 2 1.1 Overview... 2 1.2
IPsec NAT Transparency
 sec NAT Transparency First Published: November 25, 2002 Last Updated: March 1, 2011 The sec NAT Transparency feature introduces support for Security (sec) traffic to travel through Network Address Translation
sec NAT Transparency First Published: November 25, 2002 Last Updated: March 1, 2011 The sec NAT Transparency feature introduces support for Security (sec) traffic to travel through Network Address Translation
[MS-NFPS]: Near Field Proximity: Sharing Protocol
![[MS-NFPS]: Near Field Proximity: Sharing Protocol [MS-NFPS]: Near Field Proximity: Sharing Protocol](/thumbs/77/76458020.jpg) [MS-NFPS]: Near Field Proximity: Sharing Protocol Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation
[MS-NFPS]: Near Field Proximity: Sharing Protocol Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation
Wide Area Network Device Presence Protocol (WAN DPP)
 [MS-GRVWDPP]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages,
[MS-GRVWDPP]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages,
[MS-NFPS]: Near Field Proximity: Sharing Protocol. Intellectual Property Rights Notice for Open Specifications Documentation
![[MS-NFPS]: Near Field Proximity: Sharing Protocol. Intellectual Property Rights Notice for Open Specifications Documentation [MS-NFPS]: Near Field Proximity: Sharing Protocol. Intellectual Property Rights Notice for Open Specifications Documentation](/thumbs/83/88234948.jpg) [MS-NFPS]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
[MS-NFPS]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
mysabinet is an additional, value-adding function available on the new Sabinet Legal Platform where the user can set up a personal profile.
 mysabinet User Guide mysabinet is an additional, value-adding function available on the new Sabinet Legal Platform where the user can set up a personal profile. mysabinet users will be able to create and
mysabinet User Guide mysabinet is an additional, value-adding function available on the new Sabinet Legal Platform where the user can set up a personal profile. mysabinet users will be able to create and
8K GM Scale Improvement
 The feature supports optimization of the Cooperative Protocol (COOP) announcement messages by increasing the number of Group Members (GM) to 8000. Finding Feature Information, page 1 Prerequisites for,
The feature supports optimization of the Cooperative Protocol (COOP) announcement messages by increasing the number of Group Members (GM) to 8000. Finding Feature Information, page 1 Prerequisites for,
Lecture 8: Other IPC Mechanisms. CSC 469H1F Fall 2006 Angela Demke Brown
 Lecture 8: Other IPC Mechanisms CSC 469H1F Fall 2006 Angela Demke Brown Topics Messages through sockets / pipes Receiving notification of activity Generalizing the event notification mechanism Kqueue Semaphores
Lecture 8: Other IPC Mechanisms CSC 469H1F Fall 2006 Angela Demke Brown Topics Messages through sockets / pipes Receiving notification of activity Generalizing the event notification mechanism Kqueue Semaphores
Topics. Lecture 8: Other IPC Mechanisms. Socket IPC. Unix Communication
 Topics Lecture 8: Other IPC Mechanisms CSC 469H1F Fall 2006 Angela Demke Brown Messages through sockets / pipes Receiving notification of activity Generalizing the event notification mechanism Kqueue Semaphores
Topics Lecture 8: Other IPC Mechanisms CSC 469H1F Fall 2006 Angela Demke Brown Messages through sockets / pipes Receiving notification of activity Generalizing the event notification mechanism Kqueue Semaphores
Flow-Based per Port-Channel Load Balancing
 The feature allows different flows of traffic over a Gigabit EtherChannel (GEC) interface to be identified based on the packet header and then mapped to the different member links of the port channel.
The feature allows different flows of traffic over a Gigabit EtherChannel (GEC) interface to be identified based on the packet header and then mapped to the different member links of the port channel.
Encrypted Vendor-Specific Attributes
 The feature provides users with a way to centrally manage filters at a RADIUS server and supports the following types of string vendor-specific attributes (VSAs): Tagged String VSA, on page 2 (similar
The feature provides users with a way to centrally manage filters at a RADIUS server and supports the following types of string vendor-specific attributes (VSAs): Tagged String VSA, on page 2 (similar
DHCP Server RADIUS Proxy
 The Dynamic Host Configuration Protocol (DHCP) Server RADIUS Proxy is a RADIUS-based address assignment mechanism in which a DHCP server authorizes remote clients and allocates addresses based on replies
The Dynamic Host Configuration Protocol (DHCP) Server RADIUS Proxy is a RADIUS-based address assignment mechanism in which a DHCP server authorizes remote clients and allocates addresses based on replies
[MS-RDPEMC]: Remote Desktop Protocol: Multiparty Virtual Channel Extension
![[MS-RDPEMC]: Remote Desktop Protocol: Multiparty Virtual Channel Extension [MS-RDPEMC]: Remote Desktop Protocol: Multiparty Virtual Channel Extension](/thumbs/72/67796662.jpg) [MS-RDPEMC]: Remote Desktop Protocol: Multiparty Virtual Channel Extension Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications
[MS-RDPEMC]: Remote Desktop Protocol: Multiparty Virtual Channel Extension Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications
Dynamic Multipoint VPN (DMVPN) Troubleshooting Scenarios
 Dynamic Multipoint VPN (DMVPN) Troubleshooting Scenarios Luke Bibby, CCIE #45527 Introduction This small workbook is meant to provide additional practice with troubleshooting Dynamic Multipoint VPN (DMVPN)
Dynamic Multipoint VPN (DMVPN) Troubleshooting Scenarios Luke Bibby, CCIE #45527 Introduction This small workbook is meant to provide additional practice with troubleshooting Dynamic Multipoint VPN (DMVPN)
IPsec Dead Peer Detection PeriodicMessage Option
 IPsec Dead Peer Detection PeriodicMessage Option The IPsec Dead Peer Detection Periodic Message Option feature allows you to configure your router to query the liveliness of its Internet Key Exchange (IKE)
IPsec Dead Peer Detection PeriodicMessage Option The IPsec Dead Peer Detection Periodic Message Option feature allows you to configure your router to query the liveliness of its Internet Key Exchange (IKE)
TABLE OF CONTENTS Click link to go to information
 Tips for Users TABLE OF CONTENTS Click link to go to information TIPS showing screen shots (pp. 2-7) Show events in your time zone Select month to display Change appearance of the display Get event information
Tips for Users TABLE OF CONTENTS Click link to go to information TIPS showing screen shots (pp. 2-7) Show events in your time zone Select month to display Change appearance of the display Get event information
Configuring Cache Services Using the Web Cache Communication Protocol
 Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
[MS-WFDAA]: Intellectual Property Rights Notice for Open Specifications Documentation
![[MS-WFDAA]: Intellectual Property Rights Notice for Open Specifications Documentation [MS-WFDAA]: Intellectual Property Rights Notice for Open Specifications Documentation](/thumbs/78/78265095.jpg) [MS-WFDAA]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
[MS-WFDAA]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
Configuration Summary
 POWER ACT NETWORK PIX Firewall SERIES How to configure dynamic IPSec tunneling Configuration Summary This document describes configuring an NSE initiated IPSec tunnel from behind a NAT device to a VPN
POWER ACT NETWORK PIX Firewall SERIES How to configure dynamic IPSec tunneling Configuration Summary This document describes configuring an NSE initiated IPSec tunnel from behind a NAT device to a VPN
Release Notes LexisNexis Early Data Analyzer, Version Enhancements Resolved Issues Current Issues Release Information
 Release Notes LexisNexis Early Data Analyzer, Version 2.0.1.97 Enhancements Resolved Issues Release Information LexisNexis Early Data Analyzer Release Notes No part of this work may be reproduced or transmitted
Release Notes LexisNexis Early Data Analyzer, Version 2.0.1.97 Enhancements Resolved Issues Release Information LexisNexis Early Data Analyzer Release Notes No part of this work may be reproduced or transmitted
Sending MAC Address Function
 Application Note Sending MAC Address Function Version 1.1 Sollae Systems Co., Ltd. www.eztcp.com Contents CONTENTS... - 1-1 OVERVIEW... - 2-1.1 Overview... - 2-1.2 Using Unique ID for Serial Devices...
Application Note Sending MAC Address Function Version 1.1 Sollae Systems Co., Ltd. www.eztcp.com Contents CONTENTS... - 1-1 OVERVIEW... - 2-1.1 Overview... - 2-1.2 Using Unique ID for Serial Devices...
Internet Key Exchange
 CHAPTER16 The help topics in this section describe the (IKE) configuration screens. (IKE) What Do You Want to Do? (IKE) is a standard method for arranging for secure, authenticated communications. IKE
CHAPTER16 The help topics in this section describe the (IKE) configuration screens. (IKE) What Do You Want to Do? (IKE) is a standard method for arranging for secure, authenticated communications. IKE
ECC: Peer-to-Peer Electronic Cash with Trustless Network Services
 ECC: Peer-to-Peer Electronic Cash with Trustless Network Services Greg Griffith October 2017 (griffith@cryptounited.io) https://www.ecc.network ECC: Peer-to-Peer Electronic Cash with Trustless Network
ECC: Peer-to-Peer Electronic Cash with Trustless Network Services Greg Griffith October 2017 (griffith@cryptounited.io) https://www.ecc.network ECC: Peer-to-Peer Electronic Cash with Trustless Network
[MS-FSSHTTPD]: Binary Data Format for File Synchronization via SOAP. Intellectual Property Rights Notice for Open Specifications Documentation
![[MS-FSSHTTPD]: Binary Data Format for File Synchronization via SOAP. Intellectual Property Rights Notice for Open Specifications Documentation [MS-FSSHTTPD]: Binary Data Format for File Synchronization via SOAP. Intellectual Property Rights Notice for Open Specifications Documentation](/thumbs/76/73419323.jpg) [MS-FSSHTTPD]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
[MS-FSSHTTPD]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
Cisco Unified Operating System Administration Web Interface for Cisco Emergency Responder
 Cisco Unified Operating System Administration Web Interface for Cisco Emergency Responder These topics describe the Cisco Unified Operating System (OS) Administration web interface for Cisco Emergency
Cisco Unified Operating System Administration Web Interface for Cisco Emergency Responder These topics describe the Cisco Unified Operating System (OS) Administration web interface for Cisco Emergency
[MS-SSP]: Intellectual Property Rights Notice for Open Specifications Documentation
![[MS-SSP]: Intellectual Property Rights Notice for Open Specifications Documentation [MS-SSP]: Intellectual Property Rights Notice for Open Specifications Documentation](/thumbs/75/72960029.jpg) [MS-SSP]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages,
[MS-SSP]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages,
Configuring Online Diagnostics
 Finding Feature Information, page 1 Information About, page 1 How to Configure Online Diagnostics, page 2 Monitoring and Maintaining Online Diagnostics, page 6 Configuration Examples for Online Diagnostic
Finding Feature Information, page 1 Information About, page 1 How to Configure Online Diagnostics, page 2 Monitoring and Maintaining Online Diagnostics, page 6 Configuration Examples for Online Diagnostic
Configuring SDM Templates
 Information About, on page 1 How to Configure SDM Templates, on page 2 Monitoring and Maintaining SDM Templates, on page 3 Configuration Examples for SDM Templates, on page 4 Additional References for
Information About, on page 1 How to Configure SDM Templates, on page 2 Monitoring and Maintaining SDM Templates, on page 3 Configuration Examples for SDM Templates, on page 4 Additional References for
No Trade Secrets. Microsoft does not claim any trade secret rights in this documentation.
 [MS-FSSHTTPD]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages,
[MS-FSSHTTPD]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages,
[MS-PROPSTORE]: Property Store Binary File Format. Intellectual Property Rights Notice for Open Specifications Documentation
![[MS-PROPSTORE]: Property Store Binary File Format. Intellectual Property Rights Notice for Open Specifications Documentation [MS-PROPSTORE]: Property Store Binary File Format. Intellectual Property Rights Notice for Open Specifications Documentation](/thumbs/75/71551116.jpg) [MS-PROPSTORE]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
[MS-PROPSTORE]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
V+ Custom Socket I/O Driver
 V+ Custom Socket I/O Driver Table of Contents 1 Revision History... 3 2 Overview... 4 2.1 Important Notes... 4 2.2 INPUT/OUTPUT... 4 2.3 BYTE ORDERING... 4 2.4 DATABASE FILE I/O... 4 2.5 NETWORK CONFIGURATION...
V+ Custom Socket I/O Driver Table of Contents 1 Revision History... 3 2 Overview... 4 2.1 Important Notes... 4 2.2 INPUT/OUTPUT... 4 2.3 BYTE ORDERING... 4 2.4 DATABASE FILE I/O... 4 2.5 NETWORK CONFIGURATION...
Configuring SDM Templates
 Finding Feature Information, on page 1 Information About, on page 1 How to Configure SDM Templates, on page 3 Monitoring and Maintaining SDM Templates, on page 4 Configuration Examples for SDM Templates,
Finding Feature Information, on page 1 Information About, on page 1 How to Configure SDM Templates, on page 3 Monitoring and Maintaining SDM Templates, on page 4 Configuration Examples for SDM Templates,
Troubleshooting ISG with Session Monitoring and Distributed Conditional Debugging
 Troubleshooting ISG with Session Monitoring and Distributed Conditional Debugging Intelligent Services Gateway (ISG) is a software feature set that provides a structured framework in which edge devices
Troubleshooting ISG with Session Monitoring and Distributed Conditional Debugging Intelligent Services Gateway (ISG) is a software feature set that provides a structured framework in which edge devices
IPSec Network Applications
 This chapter describes several methods for implementing IPSec within various network applications. Topics discussed in this chapter include: Implementing IPSec for PDN Access Applications, page 1 Implementing
This chapter describes several methods for implementing IPSec within various network applications. Topics discussed in this chapter include: Implementing IPSec for PDN Access Applications, page 1 Implementing
Configuring DHCP for WLANs
 Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 1 Information About the Dynamic Host Configuration Protocol, page 2 How to Configure DHCP for WLANs, page 4 Additional
Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 1 Information About the Dynamic Host Configuration Protocol, page 2 How to Configure DHCP for WLANs, page 4 Additional
[MS-RDPELE]: Remote Desktop Protocol: Licensing Extension. Intellectual Property Rights Notice for Open Specifications Documentation
![[MS-RDPELE]: Remote Desktop Protocol: Licensing Extension. Intellectual Property Rights Notice for Open Specifications Documentation [MS-RDPELE]: Remote Desktop Protocol: Licensing Extension. Intellectual Property Rights Notice for Open Specifications Documentation](/thumbs/75/72327082.jpg) [MS-RDPELE]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
[MS-RDPELE]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
Contextual Configuration Diff Utility
 The feature provides the ability to perform a line-by-line comparison of any two configuration files (accessible through the Cisco IOS XE Integrated File System [IFS]) and generate a list of the differences
The feature provides the ability to perform a line-by-line comparison of any two configuration files (accessible through the Cisco IOS XE Integrated File System [IFS]) and generate a list of the differences
Restrictions for Disabling Flow Cache Entries in NAT and NAT64
 The feature allows you to disable flow cache entries for dynamic and static Network Address Translation (NAT) translations. Disabling flow cache entries for dynamic and static translations saves memory
The feature allows you to disable flow cache entries for dynamic and static Network Address Translation (NAT) translations. Disabling flow cache entries for dynamic and static translations saves memory
1.1 How to Install Prerequisites
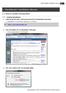 1 1 SharpReader Installation Manual 1.1 How to Install Prerequisites 1.1.1 Installing SharpReader 1. Using the internet, open a web browser and access to SharpReader s home page.. SharpReader is an RSS/Atom
1 1 SharpReader Installation Manual 1.1 How to Install Prerequisites 1.1.1 Installing SharpReader 1. Using the internet, open a web browser and access to SharpReader s home page.. SharpReader is an RSS/Atom
Beginning C Programming for Engineers
 Beginning Programming for Engineers R. Lindsay Todd Lecture 6: Bit Operations R. Lindsay Todd () Beginning Programming for Engineers Beg 6 1 / 32 Outline Outline 1 Place Value Octal Hexadecimal Binary
Beginning Programming for Engineers R. Lindsay Todd Lecture 6: Bit Operations R. Lindsay Todd () Beginning Programming for Engineers Beg 6 1 / 32 Outline Outline 1 Place Value Octal Hexadecimal Binary
RADIUS Route Download
 The feature allows users to configure their network access server (NAS) to direct RADIUS authorization. Finding Feature Information, page 1 Prerequisites for, page 1 Information About, page 1 How to Configure,
The feature allows users to configure their network access server (NAS) to direct RADIUS authorization. Finding Feature Information, page 1 Prerequisites for, page 1 Information About, page 1 How to Configure,
Contents. Introduction. Prerequisites. Background Information
 Contents Introduction Prerequisites Background Information Limitation Configure Network Diagram Initial configuration R2 R3 IPSec configuration R2 EzPM configuration Workaround Verify Troubleshooting Related
Contents Introduction Prerequisites Background Information Limitation Configure Network Diagram Initial configuration R2 R3 IPSec configuration R2 EzPM configuration Workaround Verify Troubleshooting Related
Configuring Secure Socket Layer HTTP
 This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
Configuring Secure Socket Layer HTTP
 This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
Object Tracking: IPv6 Route Tracking
 The feature expands the Enhanced Object Tracking (EOT) functionality to allow the tracking of IPv6 routes. Finding Feature Information, page 1 Restrictions for, page 1 Information About, page 2 How to
The feature expands the Enhanced Object Tracking (EOT) functionality to allow the tracking of IPv6 routes. Finding Feature Information, page 1 Restrictions for, page 1 Information About, page 2 How to
Computer Network Programming
 Computer Network Programming SCTP Overview Dr. Sam Hsu Computer Science & Engineering Florida Atlantic University SCTP Overview Introduction Motivations Architectural & Functional Views Packet & Chunk
Computer Network Programming SCTP Overview Dr. Sam Hsu Computer Science & Engineering Florida Atlantic University SCTP Overview Introduction Motivations Architectural & Functional Views Packet & Chunk
Quality of Service for VPNs
 The QoS for VPNs feature provides a solution for making Cisco IOS QoS services operate in conjunction with tunneling and encryption on an interface. Cisco IOS software can classify packets and apply the
The QoS for VPNs feature provides a solution for making Cisco IOS QoS services operate in conjunction with tunneling and encryption on an interface. Cisco IOS software can classify packets and apply the
Cboe FX ECN ITCH Protocol-v1.65
 Cboe FX ECN ITCH Protocol-v1.65 1 CONTENTS Contents 1 Itch Session Management Protocol................................... 3 1.1 Data Types............................................ 3 1.2 Server to Client
Cboe FX ECN ITCH Protocol-v1.65 1 CONTENTS Contents 1 Itch Session Management Protocol................................... 3 1.1 Data Types............................................ 3 1.2 Server to Client
AToM Graceful Restart
 AToM Graceful Restart Last Updated: November 29, 2011 The AToM Graceful Restart feature assists neighboring routers that have nonstop forwarding (NSF), stateful switchover (SSO) and graceful restart (GR)
AToM Graceful Restart Last Updated: November 29, 2011 The AToM Graceful Restart feature assists neighboring routers that have nonstop forwarding (NSF), stateful switchover (SSO) and graceful restart (GR)
Configurable Number of Simultaneous Packets per Flow
 Configurable Number of Simultaneous Packets per Flow In zone-based policy firewalls, the number of simultaneous packets per flow is restricted to 25 and packets that exceed the limit are dropped. The dropping
Configurable Number of Simultaneous Packets per Flow In zone-based policy firewalls, the number of simultaneous packets per flow is restricted to 25 and packets that exceed the limit are dropped. The dropping
Cboe FX ECN ITCH Protocol-v1.68
 Cboe FX ECN ITCH Protocol-v1.68 1 CONTENTS Contents 1 Itch Session Management Protocol................................... 3 1.1 Data Types............................................ 3 1.2 Server to Client
Cboe FX ECN ITCH Protocol-v1.68 1 CONTENTS Contents 1 Itch Session Management Protocol................................... 3 1.1 Data Types............................................ 3 1.2 Server to Client
Encrypted Vendor-Specific Attributes
 Encrypted Vendor-Specific Attributes Last Updated: January 15, 2012 The Encrypted Vendor-Specific Attributes feature provides users with a way to centrally manage filters at a RADIUS server and supports
Encrypted Vendor-Specific Attributes Last Updated: January 15, 2012 The Encrypted Vendor-Specific Attributes feature provides users with a way to centrally manage filters at a RADIUS server and supports
Predownloading an Image to Access Points
 Finding Feature Information, page 1 Predownloading an Image to an Access Point, page 1 Restrictions for Predownloading an Image to an Access Point, page 2 How to Predownload an Image to an Access Point,
Finding Feature Information, page 1 Predownloading an Image to an Access Point, page 1 Restrictions for Predownloading an Image to an Access Point, page 2 How to Predownload an Image to an Access Point,
Per-Flow Admission. Finding Feature Information. Prerequisites for Per-Flow Admission
 The feature provides explicit controls to limit packet flow into a WAN edge in order to protect already admitted flows on the routing/wan edge. Finding Feature Information, page 1 Prerequisites for, page
The feature provides explicit controls to limit packet flow into a WAN edge in order to protect already admitted flows on the routing/wan edge. Finding Feature Information, page 1 Prerequisites for, page
Configuring Location Settings
 Finding Feature Information, page 1 Information About, page 1 How to Configure Location Settings, page 2 Monitoring Location Settings and NMSP Settings, page 6 Examples: Location Settings Configuration,
Finding Feature Information, page 1 Information About, page 1 How to Configure Location Settings, page 2 Monitoring Location Settings and NMSP Settings, page 6 Examples: Location Settings Configuration,
Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location What to bring:
 ECE 120 Midterm 1 HKN Review Session Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location: Your Room on Compass What to bring: icard, pens/pencils, Cheat sheet (Handwritten) Overview of Review Binary IEEE
ECE 120 Midterm 1 HKN Review Session Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location: Your Room on Compass What to bring: icard, pens/pencils, Cheat sheet (Handwritten) Overview of Review Binary IEEE
The IPsec protocols. Overview
 The IPsec protocols -- components and services -- modes of operation -- Security Associations -- Authenticated Header (AH) -- Encapsulated Security Payload () (c) Levente Buttyán (buttyan@crysys.hu) Overview
The IPsec protocols -- components and services -- modes of operation -- Security Associations -- Authenticated Header (AH) -- Encapsulated Security Payload () (c) Levente Buttyán (buttyan@crysys.hu) Overview
Bulk Logging and Port Block Allocation
 The feature allocates a block of ports for translation instead of allocating individual ports. This feature is supported only in carrier-grade Network Address Translation (CGN) mode. This module provides
The feature allocates a block of ports for translation instead of allocating individual ports. This feature is supported only in carrier-grade Network Address Translation (CGN) mode. This module provides
Cisco CSR 1000V VxLAN Support 2
 Cisco CSR 1000V VxLAN Support Cisco CSR 1000V VxLAN Support 2 Finding Feature Information 2 Introduction 2 Prerequisites for Cisco CSR 1000V VxLAN Support 2 Configuring the Cisco CSR 1000V as a VxLAN Layer
Cisco CSR 1000V VxLAN Support Cisco CSR 1000V VxLAN Support 2 Finding Feature Information 2 Introduction 2 Prerequisites for Cisco CSR 1000V VxLAN Support 2 Configuring the Cisco CSR 1000V as a VxLAN Layer
Microcontroller Systems. ELET 3232 Topic 8: Structures, Arrays, & Pointers
 Microcontroller Systems ELET 3232 Topic 8: Structures, Arrays, & Pointers 1 Agenda Become familiar with and apply: Arrays Structures Pointers 2 Array Arrays A data set of a particular data type All elements
Microcontroller Systems ELET 3232 Topic 8: Structures, Arrays, & Pointers 1 Agenda Become familiar with and apply: Arrays Structures Pointers 2 Array Arrays A data set of a particular data type All elements
Autoroute Announce and Forwarding Adjacencies For OSPFv3
 Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Autoroute Announce and Forwarding Adjacencies For OSPFv3
 Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Cisco Unified Operating System Administration Web Interface
 Cisco Unified Operating System Administration Web Interface ServerGroup, page 1 Hardware, page 2 Network Configuration, page 3 Software Packages, page 4 System, page 5 IP Preferences, page 6 Ethernet Configuration,
Cisco Unified Operating System Administration Web Interface ServerGroup, page 1 Hardware, page 2 Network Configuration, page 3 Software Packages, page 4 System, page 5 IP Preferences, page 6 Ethernet Configuration,
Desktop Crawls. Document Feeds. Document Feeds. Information Retrieval
 Information Retrieval INFO 4300 / CS 4300! Web crawlers Retrieving web pages Crawling the web» Desktop crawlers» Document feeds File conversion Storing the documents Removing noise Desktop Crawls! Used
Information Retrieval INFO 4300 / CS 4300! Web crawlers Retrieving web pages Crawling the web» Desktop crawlers» Document feeds File conversion Storing the documents Removing noise Desktop Crawls! Used
Configuring Ethernet Management Port
 Prerequisites for Ethernet Management Ports, page 1 Information About the Ethernet Management Port, page 1 How to Configure the Ethernet Management Port, page 4 Example for Configuring IP Address on Ethernet
Prerequisites for Ethernet Management Ports, page 1 Information About the Ethernet Management Port, page 1 How to Configure the Ethernet Management Port, page 4 Example for Configuring IP Address on Ethernet
Quick Talking to ControlLogix (PCCC-style)
 Quick Talking to ControlLogix (PCCC-style) 1 Packet Formats 1.1 TCP Socket The explicit unconnected messaging we are doing uses a normal TCP socket opened to remote TCP port xaf12 ( or 44818 decimal).
Quick Talking to ControlLogix (PCCC-style) 1 Packet Formats 1.1 TCP Socket The explicit unconnected messaging we are doing uses a normal TCP socket opened to remote TCP port xaf12 ( or 44818 decimal).
IP Overlapping Address Pools
 The feature improves flexibility in assigning IP addresses dynamically. This feature allows you to configure overlapping IP address pool groups to create different address spaces and concurrently use the
The feature improves flexibility in assigning IP addresses dynamically. This feature allows you to configure overlapping IP address pool groups to create different address spaces and concurrently use the
Internet Engineering Task Force (IETF) Request for Comments: ISSN: March 2016
 Internet Engineering Task Force (IETF) T. Mizrahi Request for Comments: 7822 Marvell Updates: 5905 D. Mayer Category: Standards Track Network Time Foundation ISSN: 2070-1721 March 2016 Abstract Network
Internet Engineering Task Force (IETF) T. Mizrahi Request for Comments: 7822 Marvell Updates: 5905 D. Mayer Category: Standards Track Network Time Foundation ISSN: 2070-1721 March 2016 Abstract Network
Certificate to ISAKMP Profile Mapping
 The feature enables you to assign an Internet Security Association and Key Management Protocol (ISAKMP) profile to a peer on the basis of the contents of arbitrary fields in the certificate. In addition,
The feature enables you to assign an Internet Security Association and Key Management Protocol (ISAKMP) profile to a peer on the basis of the contents of arbitrary fields in the certificate. In addition,
GPRS Tunneling Protocol V2 Support
 General Packet Radio Service (GPRS) Tunneling Protocol Version 2 (GTPv2) is introduced by the 3rd Generation Partnership Project (3GPP) Technical Specification (TS) 29.274, which modifies and enhances
General Packet Radio Service (GPRS) Tunneling Protocol Version 2 (GTPv2) is introduced by the 3rd Generation Partnership Project (3GPP) Technical Specification (TS) 29.274, which modifies and enhances
IPv6 Support for LDAP
 The Lightweight Directory Access Protocol (LDAP) is an application protocol for accessing and maintaining distributed directory information services over an IP network. The feature module describes the
The Lightweight Directory Access Protocol (LDAP) is an application protocol for accessing and maintaining distributed directory information services over an IP network. The feature module describes the
RADIUS Logical Line ID
 The feature, also known as the Logical Line Identification (LLID) Blocking feature enables administrators to track their customers on the basis of the physical lines on which customer calls originate.
The feature, also known as the Logical Line Identification (LLID) Blocking feature enables administrators to track their customers on the basis of the physical lines on which customer calls originate.
SSL VPN - IPv6 Support
 The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, on page 1 Prerequisites
The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, on page 1 Prerequisites
SSL VPN - IPv6 Support
 The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, page 1 Prerequisites for,
The feature implements support for IPv6 transport over IPv4 SSL VPN session between a client, such as Cisco AnyConnect Mobility Client, and SSL VPN. Finding Feature Information, page 1 Prerequisites for,
[MC-NBFX]: .NET Binary Format: XML Data Structure. Intellectual Property Rights Notice for Open Specifications Documentation
![[MC-NBFX]: .NET Binary Format: XML Data Structure. Intellectual Property Rights Notice for Open Specifications Documentation [MC-NBFX]: .NET Binary Format: XML Data Structure. Intellectual Property Rights Notice for Open Specifications Documentation](/thumbs/76/73453629.jpg) [MC-NBFX]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
[MC-NBFX]: Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes Open Specifications documentation ( this documentation ) for protocols,
Final Exam. 11 May 2018, 120 minutes, 26 questions, 100 points
 Name: CS520 Final Exam 11 May 2018, 120 minutes, 26 questions, 100 points The exam is closed book and notes. Please keep all electronic devices turned off and out of reach. Note that a question may require
Name: CS520 Final Exam 11 May 2018, 120 minutes, 26 questions, 100 points The exam is closed book and notes. Please keep all electronic devices turned off and out of reach. Note that a question may require
Configuring DHCP. Finding Feature Information. Information About DHCP. DHCP Server. DHCP Relay Agent
 Finding Feature Information, page 1 Information About DHCP, page 1 How to Configure DHCP Features, page 8 Server Port-Based Address Allocation, page 17 Finding Feature Information Your software release
Finding Feature Information, page 1 Information About DHCP, page 1 How to Configure DHCP Features, page 8 Server Port-Based Address Allocation, page 17 Finding Feature Information Your software release
IP Addressing: DHCP Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 920 Series)
 IP Addressing: DHCP Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 920 Series) First Published: 2014-07-29 Last Modified: 2014-11-22 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive
IP Addressing: DHCP Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 920 Series) First Published: 2014-07-29 Last Modified: 2014-11-22 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive
Dynamic Bandwidth Sharing
 The Cisco cbr series router enables dynamic bandwidth sharing (DBS) on integrated cable (IC) and wideband (WB) cable interfaces. Finding Feature Information Your software release may not support all the
The Cisco cbr series router enables dynamic bandwidth sharing (DBS) on integrated cable (IC) and wideband (WB) cable interfaces. Finding Feature Information Your software release may not support all the
