(MSM) (LCM) Binding LSA arrive. Join. Membership Status Machine. Leadership Consensus Machine. Leader unreachable. Leader changed.
|
|
|
- Rosamond Ross
- 6 years ago
- Views:
Transcription
1 Group Leader Election under Link-State Routing Yih Huang and Philip K. McKinley Department of Computer Science Michigan State University East Lansing, Michigan fhuangyih, Abstract In this work, we place the problem of group leader election in a context \inside the network," meaning that participants in the election process are network switches/routers, rather than hosts. A robust solution to the problem, called the Network Leader Election (NLE) protocol, is proposed for use in networks based on link-state routing (LSR). The protocol is robust, for it achieves leadership consensus in the presence of adverse events, such as leader failures and network partitioning. The correctness of the protocol can be proved formally. A simulation study reveals that the NLE protocol incurs low overhead in handling leader failures and in group creation. In addition, it is shown how important network functions, including hierarchical routing, address resolution, and multicast core management, can benet from the NLE protocol. 1 Introduction The problem of leader election concerns the selection of a distinguished member from a set of computing systems that are interconnected by a network. This problem has been extensively studied in the context of distributed computing systems. Generally speaking, solutions to the problem are distributed \host-level" algorithms that make use of various network services, such as reliable delivery of messages, in order to monitor the working status of the established leader or cast ballots for a new leader. Well-known contributions in This work was supported in part by DOE grant DE-FG2-93ER25167 and by NSF grants CCR , CDA , and CDA this area include the Bully algorithm [1] and the Ring algorithm [2]. In this paper, we address the leader election problem as it occurs \inside" the network. The participants in the election process are assumed to be switches (or, interchangeably in this work, routers), rather than hosts or application processes. Solutions to this problem are intended to support underlying network functions, as opposed to being directly invoked by user applications. Whereas a host-level election protocol typically considers the underlying network as a \black box," a networklevel election protocol can see and take advantage of the internal operation of the network, in particular, the underlying routing protocol. Network functions that can make use of an ecient leader election protocol are several. In this paper, we focus on three examples. First, in Asynchronous Transfer Mode (ATM) networks and other hierarchical networks, switches in a low-level subnetwork (called a routing domain) select a switch to represent the domain in the next routing level [3]; a solution to this domain leader election problem supports routing operations within the network. Second, many addressmapping services, such as the mapping between group addresses and member addresses [4] and the mapping between network addresses and link-layer addresses [5], use a central server approach; a solution to the server assignment problem selects a leader to undertake the server responsibilities. Third, some IP multicast protocols, such as CBT [6] and PIM [7], identify a network node, called a core node, as the trac transit center for each multicast group; a solution to this multicast core management problem supports multicast services provided by the network. A common requirement of solutions to the above problems is fault tolerance: since network functions/services are expected to survive not
2 only single-point failures, but also component failures that partition the network, the solutions to these problems must also survive these adverse scenarios. Our proposed solution, called the Network Leader Election (NLE) protocol, is based on link-state routing (LSR) [8, 9], an increasingly popular type of network routing. Under LSR, the local status of each switch, including its ID and incident links, is learned by the network via the broadcasting, or ooding, of link-state advertisements (LSAs). Based on received advertisements, each switch locally maintains a complete topology image of the network, which it uses to make routing decisions. Prominent LSR protocols include the Open Shortest Path First (OSPF) protocol [8] for use in the Internet and the Private Network-to-Network Interface (PNNI) standard [3] for ATM networks. The proposed NLE protocol extends LSR to include group-leader binding LSAs, which are used by group members to advertise their choice of leader. Upon receiving such an LSA, other switches in the network either accept this selection, or choose and advertise an alternative leader. The objective of the NLE protocol is to achieve network-wide consensus on leader bindings. Moreover, the NLE protocol achieves the following properties in fault tolerance: 1. [Leadership Consensus Property] Given a group G and a network that has been partitioned into a set of segments S 1 ; S 2 ; : : : ; S k, k 1, there will be consensus on the leader binding for G within each segment S i, and that leader will be an operational switch within the segment. 2. [Mutual Consensus Property] By requiring group members to report to the established leader, the NLE protocol ensures that, within each network segment S i, the leader maintains a member list for the group that includes those, and only those, group members in S i. It is to be noted that, when the network is not partitioned, the above consensus properties hold throughout the network. Results of a simulation study show that these features can be achieved with minimum protocol overhead. The remainder of this paper is organized as follows. Section 2 reviews the operation of LSR and a previous network-level leader election method, the ATM domain leader election protocol, that satises the two consensus properties discussed above. The design of the NLE protocol is presented in Section 3. The performance of the NLE protocol and that of the ATM domain leader election protocol are compared via simulation in Section 4. In Section 5, we discuss the application of the NLE protocol to the address resolution problem and to the multicast core management problem; included are simulation results regarding the performance of NLE in creating multicast groups. Finally, conclusions are given in Section 6. 2 Background 2.1 Link-State Routing A routing protocol disseminates network information that switches use to nd paths for relaying communication trac. In the case of LSR, complete knowledge of the network is made available to all switches. For this purpose, every switch broadcasts throughout the network its local state, including the ID of the switch, links incident to the switch, bandwidth of individual links, and so forth. Since the network images must be updated in response to network dynamics, every switch constantly monitors its local state and immediately advertises any changes. For example, when a link fails, the value of its working state changes from ON to OFF, producing a link-down LSA from each of the two switches connected to that link. Similarly, link-up LSAs will be ooded when the link later returns to a functional state. Although it may be tempting to represent the states of switches in a similar manner to that of links (for example, \switch-up/switch-down" LSAs), such states are not dened in LSR. The reason is that an LSR protocol cannot distinguish a failed node from one that becomes unreachable due to failed links. To illustrate, let us consider the example shown in Figure 1(a). Assume that node X has crashed. The ve switches that are neighbors of X (A, B, C, D, and Y ) detect the lack of response on the ve links incident to X, and subsequently ood ve link-down LSAs. The network as perceived by switch A (and any other switch other than X and Y ) after the link-down LSAs have been ooded is depicted in Figure 1(b). Switch A will receive only four of the link-down LSAs because switch Y, which advertises the failure of the (X; Y ) link, has been isolated from the rest of the network. As shown, the con- guration stored at switch A does not reect the true state of the network. This example illustrates that an LSR protocol cannot determine whether a switch has failed or not. Instead, the protocol should be concerned with \reachability" of the switch. As we shall see, the NLE protocol relies on the underlying LSR protocol to provide such \leader reachability" information that is needed in handling leader failures and network partitions. Likewise, member reachability information is used by the leader to handle member failures.
3 D A X C (a) Node X crashes. B Y (b) The perception of the network at node A. Figure 1. Indeterministic of node failure. We emphasize that LSR-based protocols, including the NLE protocol, are not intended for direct implementation in very large networks or internets. LSR itself is generally intended for use in a set of networks under one administrative authority (in Internet terminology, an Autonomous System) which typically contains a few hundred switches and possibly several thousand hosts. In order to apply such protocols to larger networks, a routing hierarchy can be introduced. The combination of an LSR protocol and a routing hierarchy has been adopted by the ATM PNNI standard [3], as discussed next. 2.2 Domain Leader Election in ATM Networks ATM is a connection-oriented communication technology that relays small xed-size cells in hardware. As a telecommunications standard, ATM adopts a hierarchical routing method to cope with the routing complexities of networks that are national or even global in scope. In this approach, a large network is divided into segments, called routing domains, and the routing decision is divided into two levels, high-level inter-domain routing and low-level intra-domain routing. Given a source/destination pair, inter-domain routing determines a path comprising a series of domains from the source domain to the destination domain. Within each domain on this path, intra-domain routing determines a path that comprises a series of switches that connect the two domains on either side. In the ATM Private Network-Network Interface (PNNI) standard [3], switches in a domain use LSR to perform intra-domain routing, and elect a leader switch to represent the domain in inter-domain routing. The domain leader election protocol dened in the current ATM standard [3] is LSR-based. In this protocol, each switch maintains two election-related states: leader priority and preferred leader. The former is manually congured to determine the rank of the switch. To determine its preferred leader, every switch X A Y independently searches its local domain image, the topology image of the domain, for the switch that has the highest leader priority among reachable switches within the domain. Like other LSR switch states, values of the two states at all switches within the domain are ooded throughout the domain and constitute parts of the local domain images at switches. If a switch identies itself as the preferred leader, after waiting for a period of time, it inspects its local domain image for the preferred leaders of the other switches. When unanimity is achieved, the candidate advertises its leader status. As an example, let us consider a routing domain where the administrator congures a default leader X with leader priority 3 and a backup leader Y with priority 2. The remaining switches are congured with priority 1. We assume that the leadership of X has been established, that is, the current preferred leaders of all switches are X. Now consider what happens when the leader X fails. In this case, neighboring switches of X notice the unresponsiveness of X- incident links and ood link-down LSAs. With these LSAs, every operational switch nds X unreachable, and searches through its local domain image for a switch with the next highest priority. In this example, the result would be Y with priority 2. All switches change their preferred leader to Y and advertise this information. These advertisements could be considered as \ballots," which switch Y must collect before claiming itself the new leader. The current ATM election protocol can handle leader failures, and if every switch periodically advertises its preferred leader, the protocol achieves the leadership and mutual consensus properties dened earlier However, the protocol is relatively expensive in terms of bandwidth, since every switch must perform ooding, and it is restricted to a xed leader selection method (namely, its leader ranking scheme). In the NLE protocol, only a small number of leader candidates perform ooding; other members in the group use point-to-point messages, rather than LSAs, to cast ballots. Further, the NLE protocol is designed to operate independently of the leader selection criteria used by dierent groups, enabling its use as a single election protocol to support a variety of network functions. 3 The NLE Protocol 3.1 Overview The operation of the NLE protocol is summarized below. Since some decision-making processes of the NLE protocol, such as the leader selection policy, are ap-
4 plication dependent, we discuss the protocol operation in the context of the domain leader election problem. Adaptation of the protocol to other problems is discussed in Section For every group g, each switch x maintains a leader binding Binding x (g), whose value is a triple (Leader x (g); Source x (g); Stamp x (g)), where Leader x (g) is the leader of the group g as perceived by x, Source x (g) is the switch that suggested this binding, and Stamp x (g) is the timestamp associated with the binding. The goal of the NLE protocol is to maintain consensus on Binding x (g) values across the network. 2. When a switch x joins a group g, it searches for the Leader x (g) entry in its local database. If the entry is not found, group g is said to be unbound at x. In this case, switch x selects a switch c as the leader of the group according to a leader selection policy, sets Leader x (g) to c, and broadcasts this binding. For the domain leader election problem, the leader selection policy selects a reachable switch with the highest leader priority. 3. Once the switch x has a Leader x (g) entry, it sends a JOIN-REQUEST message to switch Leader x (g). The join operation will not be considered successful until the return of a JOIN-ACK from the Leader x (g). Further, the switch x must re-join g (that is, repeat the join process) each time the Leader x (g) value changes. 4. When a switch x leaves a group g, it sends a QUIT-REQUEST to switch Leader x (g). Again, the quit process does not not nish until the corresponding QUIT-ACK returns from Leader x (g). 5. When Leader x (g) = x, switch x acts as the leader of the group g: it processes JOIN- REQUEST/QUIT-REQUEST messages, and returns appropriate acknowledgments. Further, via join and quit requests from members, the leader maintains a member list for g, denoted as ML x (g). A member of g will be dropped from ML x (g) if it becomes unreachable from the leader x. We point out that, since members are required to re-join the group each time a new leader is elected, a new member list will be compiled at the new leader. Member lists are not required at switches other than the leader. 6. When a switch x that is a member of a group g nds the switch Leader x (g) unreachable, switch x selects and broadcasts a new leader binding for g. To avoid a rush of new leader bindings from all members of g, a delay timer of random length is used to postpone the re-selection task. Typically, one member wakes up before others and advertises a new binding. The remaining members simply accept the binding and re-join the group. 7. Even when switch Leader x (g) is still reachable from x, the switch x may decide, according to application-specic leader performance criteria, to select and advertise a new leader for group g. Given a group g, an objection policy determines when a switch objects to the current leader binding and selects a new leader. For the domain leader election problem, a switch objects to the current domain leader when it discovers a reachable switch has a higher leader priority than does the current leader. 8. Each switch periodically advertises a list of groups for which it is the leader. Formally, switch x periodically advertises a list of group IDs, G x, where a group g 2 G x if and only if Leader x (g) = x. 3.2 State Machines and Events At a switch x, the NLE protocol denes two nite state machines (FSMs) for each active group g: a Membership Status Machine, denoted as MSM(x; g), and a Leadership Consensus Machine, denoted as LCM(x; g). Both LCM(x; g) and MSM(x; g) machines access the Binding x (g) entry; such accesses are assumed to be atomic to avoid race conditions. Figure 2 shows the events processed by the two machines. The LCM(x; g) processes incoming leader bindings for the group g, and reacts to events that indicate problems with the current leader, such as leader-unreachable events and objection events dened by the objection policy. The MSM(x; g) handles join and quit events and is responsible for ensuring that the current leader, Leader x (g), holds correct information regarding the membership status of the switch x. The MSM(x; g) also processes leader-change events, which are raised whenever the LCM(x; g) accepts a new binding for group g. Join Quit Membership Status Machine (MSM) Leader changed Leadership Consensus Machine (LCM) Binding LSA arrive Leader unreachable Objection events Figure 2. The nite state machines in NLE.
5 3.3 The Operation of LCM The state transition diagram for the LCM is depicted in Figure 3. As shown, an LCM comprises four states: EMPTY, PENDING, REMOTE, and LOCAL. The EMPTY state is the initial state of LCMs. When there is no binding regarding g at x, the LCM(x; g) is in the EMPTY state; the values of Leader x (g) and Source x (g) are undened, and the value of the Stamp x (g) is dened to be zero. An LCM(x; g) is in the LOCAL state when Leader x (g) = x, and in the REMOTE state when Leader x (g) 6= x. The LCM sometimes uses a timer to postpone the task of leader selection. When this happens, the machine enters the PENDING state, waiting for time-out. New Leader(g) not x proposed or accepted PENDING REMOTE Leader(g) unreachable New Leader(g) not x accepted. New Leader(g)=x proposed/accepted New leader(g) not x acccepted, or proposed due to objection New Leader(g)=x accepted, or proposed due to objection EMPTY New Leader(g)=x accepted Member unreachable, JOIN REQUEST or JOIN ACK received LOCAL Figure 3. The leadership consensus machine at a switch x for a group g (LCM(x; g)). A binding LSA is a pair (g; (c; s; t)), where the rst element g species the group and the second element (c; s; t) is the value of this binding. The LCM processes binding LSAs according to the rules below: A1 An incoming binding LSA ` = (g; (c; s; t)) will be accepted at a switch x if (t; s) > (Stamp x (g); Source x (g)), otherwise it is rejected at x. (The comparison is in lexicographical order.) This rule guarantees that more recent bindings override old ones but that the reverse will not happen. When ` is accepted, its value (c; s; t) becomes the value of Binding x (g). Subsequently, the LCM(x; g) enters either the LOCAL or RE- MOTE state, depending whether new Leader x (g) is x or not. A2 When a switch x proposes and advertises a leader c for a group g it 1) increases the Stamp x (g) by one, 2) sets Source x (g) to x and Leader x (g) to c, and 3) oods a binding LSA (g; Binding x (g)). The LCM(x; g) then enters either the LOCAL or REMOTE state, depending on whether new Leader x (g) is x or not. There are two situations where the LCM(x; g) may use Rule A2 to propose and advertise new leader bindings for the group g: when the Leader x (g) becomes unreachable, and when an objection event is raised according to the objection policy. In the latter case, the LCM proposes a new leader only if the machine is in the REMOTE or LOCAL state. When the current leader of g becomes unreachable from a switch x, the switch is triggered to select and advertise a new leader. To avoid a rush of simultaneous leader binding LSAs from group members, the LCM(x; g) sets up a delay timer and enters the PENDING state. There are two ways for the LCM to leave the PENDING state: 1) the timer res, and the machine selects/advertises a new leader according to Rule A2, or 2) an \acceptable" binding LSA arrives before time-out. In case 2, the delay timer is canceled, and the LCM processes the LSA according to Rule A1. We will discuss the eects of various timer values in Section 4. When the LCM(x; g) enters the LOCAL state, switch x must create a member list for group g and process JOIN-REQUEST/QUIT-REQUEST messages from members of g. The member list of g is created every time LCM(x; g) enters the LOCAL state, and is destroyed every time LCM(x; g) leaves that state. JOIN-REQUEST/QUIT-REQUEST messages will be acknowledged and used to update the member list when LCM(x; g) is in the LOCAL state, but are discarded silently when the machine is in any other state. When an unreachability event concerns a switch y that is not the leader of the group g, the action of LCM(x; g) depends on whether x considers itself to be the leader. If so (that is, x = Leader x (g)), x removes y from the member list of g; otherwise, it discards the event. 3.4 The Operation of MSM The MSM at a switch x for a group g, denoted as MSM(x; g), reacts to join(g) and quit(g) events. An MSM has four states: MEMBER, JOINING, NON- MEMBER, and LEAVING, among which the NON- MEMBER state is the initial state. With respect to a group g, the MSM at a switch x is in JOINING state if it wishes to join the group but has not completed the \registration" procedure, namely, the exchange of JOIN-REQUEST and JOIN-ACK messages with the leader, Leader x (g). After the JOIN-ACK message is received, the joining member enters the MEMBER state. Dened similarly, a member of g is in the LEAVING state during the exchange of QUIT- REQUEST and QUIT-ACK messages with the leader, and will enter the NON-MEMBER state after completion. Retransmissions of REQUEST messages may be necessary to ensure successful delivery. The MSM does not deal directly with the leader-
6 Non Member Join(g): send JOIN REQUEST Joining Leader changed or ack times out: send JOIN REQUEST QUIT ACK received from Leader(g) Quit(g): send QUIT REQUEST JOIN ACK received from Leader(g) Leader changed: send JOIN REQUEST Leader changed or ack times out: send QUIT REQUEST Leaving Quit(g): send QUIT REQUEST Member Figure 4. The membership status machine at a switch x for a group g (MSM(x; g)). unreachable events. However, when the LCM(x; g) changes the leader binding due to leader-unreachable events or other objection events, it generates a leaderchange event to be handled by the MSM(x; g). If the switch is a member of the group g, the switch must re-join the group, that is, the MSM(x; g) machine enters the JOINING state so that JOIN-REQUEST and JOIN-ACK messages are exchanged with the new leader. If a switch x joins a group g when the LCM(x; g) is in the EMPTY state, the switch must select and advertise a leader for the group, following the procedure dened in Rule A2. For every switch v in the network, including LCM(x; g), this advertisement will be received by LCM(v; g). 3.5 Proof of Correctness The correctness of the NLE protocol, specically, that it exhibits the leadership consensus property and the mutual consensus property, can be proved formally. Details are omitted here due to space limitations, but can be found in a companion technical report [1]. 4 Performance Evaluation In this section, we investigate the performance of the NLE protocol in handling leader failures. Specically, the NLE protocol is compared against the ATM domain leader election protocol [3]. In our simulations, networks comprising up to 4 switches were used. For each network size, 4 graphs were generated randomly, and two simulation sessions were conducted on each graph. Table 1 shows the characteristics of the graphs generated. In the table, the symbol T f denotes the worst-case time to perform a ooding operation in a given network. The following ooding protocol is assumed: LSAs arriving at a switch for the rst time are forwarded along all incident links, except the incoming one. LSAs arriving at a switch for the second time are dropped silently. LSAs are forwarded to neighboring switches one by one. For each LSA forwarding, we used software overheads as measured on the ATM testbed in our laboratory. The testbed comprises Sun SPARC- 1 workstations equipped with Fore SBA-2 adapters and connected by three Fore ASX-1 switches. From these measurements, we obtained the gure 6 sec, which includes the overhead at both the sending and receiving switches. Network Avg. Avg. Tf size degree diameter (in ms) Table 1. Characteristics of randomly generated graphs. We consider two metrics for the performance of leader election: the leader-binding convergence time and the number of leader binding LSAs produced for an election. The former refers to the length of the period from the moment the election begins to the moment that all network switches agree on the same leader node. (When an election is held due to the failure of the current leader, the election begins at the moment the leader fails.) The latter measures the number of leader-binding LSAs that are sent before consensus on the leader node is reached. In addition, we measured the bandwidth consumption of the two approaches. This is motivated by the fact that switches use point-to-point messages to cast ballots in the NLE protocol, but must use ooding operations in the ATM election protocol. As discussed, the NLE protocol uses a random timer to delay the ooding of new leader binding LSAs when the current leader fails. In this study, we assumed that the current leader crashes at time, and that delay
7 timers are uniformly distributed between and a simulation parameter max delay. We used max delay values of.1 seconds, 1 seconds, and 1 seconds. The results regarding the metric of the number of bindings are plotted in Figure 5(a). Even the very short maximum delay value (.1 seconds) introduces fewer than 16 bindings in 4-switch networks. When the maximum delay is set to 1 second, fewer than 3 bindings are generated in large networks. When the maximum delay value of 1 seconds is used, only one binding is created in almost all simulation sessions. Although not shown in the gure, the current ATM election protocol produces N preferred-leader LSAs, the equivalent of binding LSAs, in an N-switch network for every leader failure event. The results for convergence time are plotted in Figure 5(b). For this performance metric, the shorter the maximum delay value, the faster the convergence, since a short maximum delay value produces early time-out of the delay timers, and hence switches take less time to ood new leader bindings. Also, the larger the network size, the faster the binding converge; not surprisingly, a large number of switches that set up random delay timers tends to produce one that times out quickly. The results for bandwidth consumption are plotted in Figures 6(a) and (b). Bandwidth consumption is measured by counting the total number of links traversed by every LSA and JOIN-REQUEST/ACK messages associated with the election. Figure 6(a) shows the results of the NLE protocol, which uses ooding operations to broadcast leader bindings and point-topoint messages to cast ballots (that is, to send JOIN- REQUEST messages). The curves in Figure 6(a) conform with those in Figure 5(a), that is, the more concurrent bindings produced, the more bandwidth consumed. The bandwidth consumption of the ATM election protocol is signicantly larger than that of the NLE protocol, as shown in Figure 6(b). In summary, compared to the ATM leader election protocol, the NLE protocol incurs far fewer ooding operations and consumes a small fraction of the bandwidth. We further emphasize that the ATM leader election protocol requires every switch to periodically advertise its preferred leader, while the NLE protocol requires only the leader to periodically broadcast its leader status. We conclude that the NLE protocol is more ecient than the ATM leader election protocol, while being equally robust. No. of Bindings Convergence time (in ms) sec max delay 1 sec max delay 1 sec max delay (a) number of bindings..1 sec max delay 1 sec max delay 1 sec max delay (b) convergence time. Figure 5. Performance of the NLE protocol. 5 Other Potential Uses of The NLE Protocol 5.1 Multicast Address Resolution In the last several years, a great deal of research has addressed the issue of implementing IP over new link layer protocols, such as ATM/AAL5. One of the dif- cult tasks in implementing IP over ATM networks is how to handle multicast addressing. Whereas IP allows a source node to send a datagram to an abstract multicast group address, the current ATM standard does not support such an abstraction. Rather, ATM supports multicasting through point-to-multipoint unidirectional virtual channels, which require the sender to explicitly establish a connection to each destination. One approach to this problem is to use a Multicast Address Resolution Server (MARS) [4], a central server that acts as a registry, associating IP multicast group identiers with the ATM interfaces representing the members of the groups. The MARS is queried when an IP multicast address needs to be resolved, and hosts and routers must update the MARS when they join and leave groups. As a centralized solution, however, the potential for MARS failure is an important issue.
8 No. of msg. forwardings No. of msg. forwardings sec max delay 1 sec max delay 1 sec max delay (a) NLE bandwidth. ATM NLE,.1 sec max delay (b) ATM bandwidth. Figure 6. Bandwidth usage of alternative election protocols. The approach described in [4] is to manually congure nodes with the addresses of one or more backup MARS nodes that they can contact in descending order of preference. An alternative method is to use an election protocol, such as NLE, to \automatically" handle MARS failures and, just as important, accommodate network partitions. Such an implementation might work as follows. A specic group identier (call it MARS-GID) is reserved for the election of the MARS; every switch is assumed to be a member of this group. The selection and objection policies of the MARS follow a ranking scheme similar to those for domain leader election. If the current MARS crashes, the NLE protocol is used to establish consensus on a new Leader x (MARS-GID) binding. For the new MARS to operate properly, member lists must be re-collected. To this end, every switch in the network maintains an interested multicast addresses (IMA) list, M x = fm 1 ; m 2 ; : : : ; m k g, where each element m i is a multicast address that one or more of the attached hosts is interested in. This list is usually maintained by a local membership management protocol, such as the IGMP [11]. Since every switch must send a JOIN-REQUEST to a newly elected MARS, reconstruction of member lists at the MARS can be implemented by augmenting each JOIN- REQUEST message from switch x to include a copy of M x. The consensus properties of the NLE protocol guarantee that, should the network be partitioned, there will be a MARS within each segment that maintains multicast group member lists for those, and only those, switches in the segment. 5.2 Multicast Core Management The Internet supports multicast communication, the delivery of a message from a single source to multiple destinations, and group addressing, whereby a set of hosts can be referred to by a multicast group address. Some prominent IP multicast protocols, such as CBT [6] and PIM [7], associate a multicast trac transit center, or core node, with each multicast group. In such approaches, datagrams destined to a multicast group are rst forwarded to the core node, from which they are distributed along a multicast tree to reach group members. A new member joins the group by sending a JOIN-REQUEST message toward the core node. The path traversed by the message denes a tree branch to reach the new member. An example of this join process is shown in Figure 7. Figure 7(a) shows the shortest path P from a joining member X to the core node. The result of this join operation is shown in Figure 7(b). Core node The joining member (a) a shortest path from the joining member to the core. Figure 7. protocols. X Group member P: the shortest path from X to the core Intermediate node (b) the resultant tree. Member join operation in the CBT/PIM We point out that CBT/PIM JOIN-REQUEST messages are not issued by host members. Rather, when a host joins a group, it is its ingress switch, the point at which the host is attached to the network, that sends the request on behalf of the host. That switch consequently becomes a switch member of the multicast group, and need not send further JOIN- REQUEST messages when other attached hosts sub-
9 sequently join the group. In the following discussion, the term member refers to switch member. The association of the core node with a multicast group can be modeled as a leader election problem, and the NLE protocol can be applied. One approach is as follows. We assume that a core election is held whenever a multicast group is created (that is, when the rst member joins), and that a new core is elected if the current core fails. Regarding the core/leader selection policy, we can assume that the default is the random member policy [12]: whenever a member is required to select and advertise a core node (including group creation time), the member simply recommends itself. A number of other core selection policies are discussed in [12] and could be incorporated into the NLE protocol. As with the applications discussed earlier, the mutual consensus property of the NLE protocol enables arbitrary multicast groups to handle network partitions and re-unications. The maintenance of the leader binding of every active group at every switch in a network may raise the concern of scalability. In [13], we describe another coremanagement method that addresses this issue by using the NLE protocol to select a central server to maintain the leader bindings of all active groups. The method presented above, however, has an advantage in groupjoin time, because joining switches do not have to query a server to resolve leader-group bindings. This feature is important to situations where members of a group join and exit at a high rate. 5.3 Performance of Multicast Group Creation When the NLE protocol is used in domain leader election and MARS election, all switches in the network are members of the (single) group, and the group is assumed to be created at network initialization, a relatively rare event. In the case of multicast core management, on the other hand, there are many multicast groups directly tied to applications. More importantly, group creation time may be important to the performance of those applications. Therefore, we conducted a study to evaluate the performance of the NLE protocol when a multicast group is created. As in the previous performance study, we are interested in two performance metrics: convergence time and the number of binding LSAs. It turns out that the convergence time in this case is quite predictable, as shown in the following theorem. Theorem 1 Given the ooding diameter T f of a network (the worst-case time to nish a ooding operation), the convergence time for group creation under NLE is less then 2T f, assuming that no network component failures occur during group creation. Proof: See [1]. 2 To investigate the number of binding LSAs produced by group creation, we simulated the creation periods of multicast sessions with M participants. The arrival time of each participant is normally distributed with mean zero, the predetermined startup time of the group. The standard deviation value is set in such a way that 99% of the participants arrive within a predetermined time interval; this interval will simply be called an arrival interval. We used arrival intervals of lengths 1 second and.1 seconds. A switch joins the multicast group when its rst attached participating host arrives. In a simulation session, the size of the participant population, M, is controlled by the participant-to-switch ratio; we used the values of 1 and 1 in this investigation. As such, our simulation study covers a wide range of participant population sizes, from 1 (obtained by 1-switch networks with 1 participant per switch) to 4 (obtained by 4-switch networks with 1 participants per switch). Simulation sessions involving a small number of participants could represent teleconferencing applications, whereas those involving very large population sizes may represent Distributed Interactive Simulation (DIS) applications. The combination of very short arrival intervals with very large population sizes produces extremely busy group creation periods, in order to stress the NLE protocol. Figure 8 shows the results of this study. Figure 8(a) plots the results when using the.1 seconds arrival interval. The worst case in the gure is only 3., meaning that even when 4 participants join a multicast group within.1 seconds, the NLE protocol produces only three leader binding LSAs. Figure 8(b) plots the results for the 1 second arrival interval. As shown, this relatively longer (but still very short) arrival interval produces virtually no redundant bindings, that is, there is one leader binding produced per group creation event. We believe that the results in Figure 8 demonstrate that the NLE protocol is a viable method for handling many real-world situations. 6 Conclusion We have considered a long-established distributed computing problem in a novel context. Specically, the leader election problem has been studied in a context where participants of the election process are network switches and applications of the problem are
10 No. of Bindings No. of Bindings :1 host-to-switch ratio 1:1 host-to-switch ratio (a).1 seconds arrival intervals :1 host-to-switch ratio 1:1 host-to-switch ratio (b) 1 second arrival intervals. Figure 8. Number of bindings generated for group creation. network functions, including, among others, hierarchical routing, address resolution, and multicast communication. The proposed solution, called the Network Leader Election protocol, models the groupleader binding problem as a consensus problem under link state routing. In this model, the local network images at switches are extended with leader binding entries, whose network-wide consistency is guaranteed by the protocol. The correctness of the NLE protocol, including its leadership consensus property and the mutual consensus property, can be proved formally. Our simulation studies reveal that the NLE protocol incurs minimal overheads for multicast group creation and moderate overheads to handle leader failures. The performance of the NLE protocol compares favorably with a previous network group leader election protocol for ATM networks. Further Information addresses are ftp://ftp.cps.msu.edu/pub/crg and References [1] H. Garcia-Molina, \Elections in a distributed computing system," IEEE Trans. on Computers, vol. 31, pp. 48{59, January [2] N. Fredrickson and N. Lynch, \Electing a leader in a synchronous ring," Journal of the ACM, vol. 34, pp. 98{115, January [3] ATM Forum, \Private network-network interface specication version 1.." ATM Forum technical specication af-pnni-55., March [4] G. Armitage, \Support for multicast over UNI 3./3.1 based ATM networks." Internet RFC 222, November [5] M. Laubach, \Classical IP and ARP over ATM." Internet RFC 1577, January [6] A. Ballardie, \Core based trees (CBT) multicast routing architecture." Internet draft, March [7] S. Deering, D. L. Estrin, D. Farinacci, V. Jacobson, C.-G. Liu, and L. Wei, \The PIM architecture for wide-area multicast routing," IEEE/ACM Trans. on Networking, vol. 4, pp. 153{162, April [8] J. Moy, \OSPF version 2." Internet RFC 1583, March [9] J. M. McQuillan, I. Richer, and E. C. Rosen, \The new routing algorithm for the ARPANET," IEEE Transactions on Communications, pp. 711{719, MAY 198. [1] Y. Huang and P. K. McKinley, \Group leader election under link-state routing," Tech. Rep. MSU-CPS-97-14, Department of Computer Science, Michigan State University, East Lansing, Michigan, April [11] S. Deering, \Host extensions for IP multicasting." Internet RFC 1112, August [12] K. L. Calvert, E. W. Zegura, and M. J. Donahoo, \Core selection methods for multicast routing," in Proceedings of IEEE ICCCN '95, (Las Vegas, Nevada), [13] Y. Huang and P. K. McKinley, \LCM: A multicast core management protocol for link-state routing networks," Tech. Rep. MSU-CPS-97-3, Department of Computer Science, Michigan State University, East Lansing, Michigan, August A number of related papers and technical reports of the Communications Research Group at Michigan State University are available via anonymous ftp and world-wide web. The respective
MC member other network node. Link used by the MC Link not used by the MC. Cell forwarding at X: cell forwarding. cell arrivial
 Switch-Aided Flooding Operations in ATM Networks Yih Huang and Philip K. McKinley Department of Computer Science Michigan State University East Lansing, Michigan 48824 fhuangyih, mckinleyg@cps.msu.edu
Switch-Aided Flooding Operations in ATM Networks Yih Huang and Philip K. McKinley Department of Computer Science Michigan State University East Lansing, Michigan 48824 fhuangyih, mckinleyg@cps.msu.edu
Connection Link Connection Member Intermediate Switch. Connection Link Receiver member Intermediate Switch Source member
 Proceedings of the 996 IEEE International Conference on Distributed Computing Systems, pp 5-, Hong Kong, May 996 A Lightweight Protocol for Multipoint Connections under Link-State Routing Yih Huang and
Proceedings of the 996 IEEE International Conference on Distributed Computing Systems, pp 5-, Hong Kong, May 996 A Lightweight Protocol for Multipoint Connections under Link-State Routing Yih Huang and
\Classical" RSVP and IP over ATM. Steven Berson. April 10, Abstract
 \Classical" RSVP and IP over ATM Steven Berson USC Information Sciences Institute April 10, 1996 Abstract Integrated Services in the Internet is rapidly becoming a reality. Meanwhile, ATM technology is
\Classical" RSVP and IP over ATM Steven Berson USC Information Sciences Institute April 10, 1996 Abstract Integrated Services in the Internet is rapidly becoming a reality. Meanwhile, ATM technology is
draft-ietf-idmr-pim-sm-guidelines-00.ps 2 Abstract This document provides guidelines and recommendations for the incremental deployment of Protocol In
 1 Protocol Independent Multicast-Sparse Mode (PIM-SM): Deployment Guidelines Deborah Estrin Ahmed Helmy David Thaler Liming Wei Computer Science Dept/ISI University of Southern Calif. Los Angeles, CA 90089
1 Protocol Independent Multicast-Sparse Mode (PIM-SM): Deployment Guidelines Deborah Estrin Ahmed Helmy David Thaler Liming Wei Computer Science Dept/ISI University of Southern Calif. Los Angeles, CA 90089
Enhancement of the CBT Multicast Routing Protocol
 Enhancement of the CBT Multicast Routing Protocol Seok Joo Koh and Shin Gak Kang Protocol Engineering Center, ETRI, Korea E-mail: sjkoh@pec.etri.re.kr Abstract In this paper, we propose a simple practical
Enhancement of the CBT Multicast Routing Protocol Seok Joo Koh and Shin Gak Kang Protocol Engineering Center, ETRI, Korea E-mail: sjkoh@pec.etri.re.kr Abstract In this paper, we propose a simple practical
Tag Switching. Background. Tag-Switching Architecture. Forwarding Component CHAPTER
 CHAPTER 23 Tag Switching Background Rapid changes in the type (and quantity) of traffic handled by the Internet and the explosion in the number of Internet users is putting an unprecedented strain on the
CHAPTER 23 Tag Switching Background Rapid changes in the type (and quantity) of traffic handled by the Internet and the explosion in the number of Internet users is putting an unprecedented strain on the
QoS-Aware Hierarchical Multicast Routing on Next Generation Internetworks
 QoS-Aware Hierarchical Multicast Routing on Next Generation Internetworks Satyabrata Pradhan, Yi Li, and Muthucumaru Maheswaran Advanced Networking Research Laboratory Department of Computer Science University
QoS-Aware Hierarchical Multicast Routing on Next Generation Internetworks Satyabrata Pradhan, Yi Li, and Muthucumaru Maheswaran Advanced Networking Research Laboratory Department of Computer Science University
Routing in High Speed Networks. Technical Report Edition 1.0. John Crawford and Gill Waters.
 Low Cost Quality of Service Multicast Routing in High Speed Networks Technical Report 13-97 - Edition 1.0 John Crawford and Gill Waters J.S.Crawford@ukc.ac.uk, A.G.Waters@ukc.ac.uk Computing Laboratory
Low Cost Quality of Service Multicast Routing in High Speed Networks Technical Report 13-97 - Edition 1.0 John Crawford and Gill Waters J.S.Crawford@ukc.ac.uk, A.G.Waters@ukc.ac.uk Computing Laboratory
DHCP for IPv6. Palo Alto, CA Digital Equipment Company. Nashua, NH mentions a few directions about the future of DHCPv6.
 DHCP for IPv6 Charles E. Perkins and Jim Bound Sun Microsystems, Inc. Palo Alto, CA 94303 Digital Equipment Company Nashua, NH 03062 Abstract The Dynamic Host Conguration Protocol (DHCPv6) provides a framework
DHCP for IPv6 Charles E. Perkins and Jim Bound Sun Microsystems, Inc. Palo Alto, CA 94303 Digital Equipment Company Nashua, NH 03062 Abstract The Dynamic Host Conguration Protocol (DHCPv6) provides a framework
An Evaluation of Shared Multicast Trees with Multiple Active Cores
 Brigham Young University BYU ScholarsArchive All Faculty Publications 2001-07-01 An Evaluation of Shared Multicast Trees with Multiple Active Cores Daniel Zappala daniel_zappala@byu.edu Aaron Fabbri Follow
Brigham Young University BYU ScholarsArchive All Faculty Publications 2001-07-01 An Evaluation of Shared Multicast Trees with Multiple Active Cores Daniel Zappala daniel_zappala@byu.edu Aaron Fabbri Follow
Processor. Flit Buffer. Router
 Path-Based Multicast Communication in Wormhole-Routed Unidirectional Torus Networks D. F. Robinson, P. K. McKinley, and B. H. C. Cheng Technical Report MSU-CPS-94-56 October 1994 (Revised August 1996)
Path-Based Multicast Communication in Wormhole-Routed Unidirectional Torus Networks D. F. Robinson, P. K. McKinley, and B. H. C. Cheng Technical Report MSU-CPS-94-56 October 1994 (Revised August 1996)
Network Layer, Part 2 Routing. Terminology
 Network Layer, Part Routing These slides are created by Dr. Huang of George Mason University. Students registered in Dr. Huang s courses at GMU can make a single machine readable copy and print a single
Network Layer, Part Routing These slides are created by Dr. Huang of George Mason University. Students registered in Dr. Huang s courses at GMU can make a single machine readable copy and print a single
ITEC310 Computer Networks II
 ITEC310 Computer Networks II Chapter 22 Network Layer:, and Routing Department of Information Technology Eastern Mediterranean University Objectives 2/131 After completing this chapter you should be able
ITEC310 Computer Networks II Chapter 22 Network Layer:, and Routing Department of Information Technology Eastern Mediterranean University Objectives 2/131 After completing this chapter you should be able
MULTICAST EXTENSIONS TO OSPF (MOSPF)
 MULTICAST EXTENSIONS TO OSPF (MOSPF) Version 2 of the Open Shortest Path First (OSPF) routing protocol is defined in RFC-1583. It is an Interior Gateway Protocol (IGP) specifically designed to distribute
MULTICAST EXTENSIONS TO OSPF (MOSPF) Version 2 of the Open Shortest Path First (OSPF) routing protocol is defined in RFC-1583. It is an Interior Gateway Protocol (IGP) specifically designed to distribute
Supporting IP Multicast for Mobile Hosts. Yu Wang Weidong Chen. Southern Methodist University. May 8, 1998.
 Supporting IP Multicast for Mobile Hosts Yu Wang Weidong Chen Southern Methodist University fwy,wcheng@seas.smu.edu May 8, 1998 Abstract IP Multicast is an ecient mechanism of delivering a large amount
Supporting IP Multicast for Mobile Hosts Yu Wang Weidong Chen Southern Methodist University fwy,wcheng@seas.smu.edu May 8, 1998 Abstract IP Multicast is an ecient mechanism of delivering a large amount
Extensions to RTP to support Mobile Networking: Brown, Singh 2 within the cell. In our proposed architecture [3], we add a third level to this hierarc
![Extensions to RTP to support Mobile Networking: Brown, Singh 2 within the cell. In our proposed architecture [3], we add a third level to this hierarc Extensions to RTP to support Mobile Networking: Brown, Singh 2 within the cell. In our proposed architecture [3], we add a third level to this hierarc](/thumbs/88/114904400.jpg) Extensions to RTP to support Mobile Networking Kevin Brown Suresh Singh Department of Computer Science Department of Computer Science University of South Carolina Department of South Carolina Columbia,
Extensions to RTP to support Mobile Networking Kevin Brown Suresh Singh Department of Computer Science Department of Computer Science University of South Carolina Department of South Carolina Columbia,
Planning for Information Network
 Planning for Information Network Lecture 8: Network Routing Protocols Assistant Teacher Samraa Adnan Al-Asadi 1 Routing protocol features There are many ways to characterize routing protocols, including
Planning for Information Network Lecture 8: Network Routing Protocols Assistant Teacher Samraa Adnan Al-Asadi 1 Routing protocol features There are many ways to characterize routing protocols, including
Open Shortest Path First (OSPF)
 CHAPTER 42 Open Shortest Path First (OSPF) Background Open Shortest Path First (OSPF) is a routing protocol developed for Internet Protocol (IP) networks by the interior gateway protocol (IGP) working
CHAPTER 42 Open Shortest Path First (OSPF) Background Open Shortest Path First (OSPF) is a routing protocol developed for Internet Protocol (IP) networks by the interior gateway protocol (IGP) working
Parallel Routing Table Computation for Scalable IP Routers
 Parallel Routing Table Computation for Scalable IP Routers Xipeng Xiao and Lionel M. Ni Department of Computer Science 3115 Engineering Building Michigan State University East Lansing, MI 48824-1226 {xiaoxipe,
Parallel Routing Table Computation for Scalable IP Routers Xipeng Xiao and Lionel M. Ni Department of Computer Science 3115 Engineering Building Michigan State University East Lansing, MI 48824-1226 {xiaoxipe,
Table of Contents 1 PIM Configuration 1-1
 Table of Contents 1 PIM Configuration 1-1 PIM Overview 1-1 Introduction to PIM-DM 1-2 How PIM-DM Works 1-2 Introduction to PIM-SM 1-4 How PIM-SM Works 1-5 Introduction to Administrative Scoping in PIM-SM
Table of Contents 1 PIM Configuration 1-1 PIM Overview 1-1 Introduction to PIM-DM 1-2 How PIM-DM Works 1-2 Introduction to PIM-SM 1-4 How PIM-SM Works 1-5 Introduction to Administrative Scoping in PIM-SM
Multicast Technology White Paper
 Multicast Technology White Paper Keywords: Multicast, IGMP, IGMP Snooping, PIM, MBGP, MSDP, and SSM Mapping Abstract: The multicast technology implements high-efficiency point-to-multipoint data transmission
Multicast Technology White Paper Keywords: Multicast, IGMP, IGMP Snooping, PIM, MBGP, MSDP, and SSM Mapping Abstract: The multicast technology implements high-efficiency point-to-multipoint data transmission
Table of Contents 1 Static Routing Configuration RIP Configuration 2-1
 Table of Contents 1 Static Routing Configuration 1-1 Introduction 1-1 Static Route 1-1 Default Route 1-1 Application Environment of Static Routing 1-1 Configuring a Static Route 1-2 Configuration Prerequisites
Table of Contents 1 Static Routing Configuration 1-1 Introduction 1-1 Static Route 1-1 Default Route 1-1 Application Environment of Static Routing 1-1 Configuring a Static Route 1-2 Configuration Prerequisites
A Protocol for Scalable Loop-Free Multicast Routing. M. Parsa, and J.J. Garcia-Luna-Aceves. Abstract
 A Protocol for Scalable Loop-Free Multicast Routing M. Parsa, and J.J. Garcia-Luna-Aceves Abstract In network multimedia applications, such as multiparty teleconferencing, users often need to send the
A Protocol for Scalable Loop-Free Multicast Routing M. Parsa, and J.J. Garcia-Luna-Aceves Abstract In network multimedia applications, such as multiparty teleconferencing, users often need to send the
Performance of Multihop Communications Using Logical Topologies on Optical Torus Networks
 Performance of Multihop Communications Using Logical Topologies on Optical Torus Networks X. Yuan, R. Melhem and R. Gupta Department of Computer Science University of Pittsburgh Pittsburgh, PA 156 fxyuan,
Performance of Multihop Communications Using Logical Topologies on Optical Torus Networks X. Yuan, R. Melhem and R. Gupta Department of Computer Science University of Pittsburgh Pittsburgh, PA 156 fxyuan,
21. Distributed Algorithms
 21. Distributed Algorithms We dene a distributed system as a collection of individual computing devices that can communicate with each other [2]. This denition is very broad, it includes anything, from
21. Distributed Algorithms We dene a distributed system as a collection of individual computing devices that can communicate with each other [2]. This denition is very broad, it includes anything, from
What is Multicasting? Multicasting Fundamentals. Unicast Transmission. Agenda. L70 - Multicasting Fundamentals. L70 - Multicasting Fundamentals
 What is Multicasting? Multicasting Fundamentals Unicast transmission transmitting a packet to one receiver point-to-point transmission used by most applications today Multicast transmission transmitting
What is Multicasting? Multicasting Fundamentals Unicast transmission transmitting a packet to one receiver point-to-point transmission used by most applications today Multicast transmission transmitting
Table of Contents 1 OSPF Configuration 1-1
 Table of Contents 1 OSPF Configuration 1-1 Introduction to OSPF 1-1 Basic Concepts 1-2 OSPF Area Partition 1-4 Router Types 1-7 Classification of OSPF Networks 1-9 DR and BDR 1-9 OSPF Packet Formats 1-11
Table of Contents 1 OSPF Configuration 1-1 Introduction to OSPF 1-1 Basic Concepts 1-2 OSPF Area Partition 1-4 Router Types 1-7 Classification of OSPF Networks 1-9 DR and BDR 1-9 OSPF Packet Formats 1-11
A Fault-Tolerant P2P-based Protocol for Logical Networks Interconnection
 A Fault-Tolerant P2P-based Protocol for Logical Networks Interconnection Jaime Lloret 1, Juan R. Diaz 2, Fernando Boronat 3 and Jose M. Jiménez 4 Department of Communications, Polytechnic University of
A Fault-Tolerant P2P-based Protocol for Logical Networks Interconnection Jaime Lloret 1, Juan R. Diaz 2, Fernando Boronat 3 and Jose M. Jiménez 4 Department of Communications, Polytechnic University of
Virtual Multi-homing: On the Feasibility of Combining Overlay Routing with BGP Routing
 Virtual Multi-homing: On the Feasibility of Combining Overlay Routing with BGP Routing Zhi Li, Prasant Mohapatra, and Chen-Nee Chuah University of California, Davis, CA 95616, USA {lizhi, prasant}@cs.ucdavis.edu,
Virtual Multi-homing: On the Feasibility of Combining Overlay Routing with BGP Routing Zhi Li, Prasant Mohapatra, and Chen-Nee Chuah University of California, Davis, CA 95616, USA {lizhi, prasant}@cs.ucdavis.edu,
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
GMNF-DVMRP: AN ENHANCED VERSION OF DISTANCE VECTOR MULTICAST ROUTING PROTOCOL
 GMNF-DVMRP: AN ENHANCED VERSION OF DISTANCE VECTOR MULTICAST ROUTING PROTOCOL YUAN-CHENG LAI YING-DAR LIN AND WEI-CHE YU Department of Computer and Information Science, National Chiao Tung University,
GMNF-DVMRP: AN ENHANCED VERSION OF DISTANCE VECTOR MULTICAST ROUTING PROTOCOL YUAN-CHENG LAI YING-DAR LIN AND WEI-CHE YU Department of Computer and Information Science, National Chiao Tung University,
Table of Contents 1 MSDP Configuration 1-1
 Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring Basic Functions of MSDP
Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring Basic Functions of MSDP
IPv6 Routing: OSPFv3
 Open Shortest Path First version 3 (OSPFv3) is an IPv4 and IPv6 link-state routing protocol that supports IPv6 and IPv4 unicast address families (AFs). Finding Feature Information, page 1 Prerequisites
Open Shortest Path First version 3 (OSPFv3) is an IPv4 and IPv6 link-state routing protocol that supports IPv6 and IPv4 unicast address families (AFs). Finding Feature Information, page 1 Prerequisites
Study and Comparison of Mesh and Tree- Based Multicast Routing Protocols for MANETs
 Study and Comparison of Mesh and Tree- Based Multicast Routing Protocols for MANETs Rajneesh Gujral Associate Proffesor (CSE Deptt.) Maharishi Markandeshwar University, Mullana, Ambala Sanjeev Rana Associate
Study and Comparison of Mesh and Tree- Based Multicast Routing Protocols for MANETs Rajneesh Gujral Associate Proffesor (CSE Deptt.) Maharishi Markandeshwar University, Mullana, Ambala Sanjeev Rana Associate
Failure Tolerance. Distributed Systems Santa Clara University
 Failure Tolerance Distributed Systems Santa Clara University Distributed Checkpointing Distributed Checkpointing Capture the global state of a distributed system Chandy and Lamport: Distributed snapshot
Failure Tolerance Distributed Systems Santa Clara University Distributed Checkpointing Distributed Checkpointing Capture the global state of a distributed system Chandy and Lamport: Distributed snapshot
IP Multicast Technology Overview
 IP multicast is a bandwidth-conserving technology that reduces traffic by delivering a single stream of information simultaneously to potentially thousands of businesses and homes. Applications that take
IP multicast is a bandwidth-conserving technology that reduces traffic by delivering a single stream of information simultaneously to potentially thousands of businesses and homes. Applications that take
An Efficient DECT-Mobile IP Interworking for Mobile Computing
 An Efficient DECT-Mobile IP Interworking for Mobile Computing Anthony Lo *, Winston Seah * and Edwin Schreuder + * Centre for Wireless Communications 1, National University of Singapore, 20 Science Park
An Efficient DECT-Mobile IP Interworking for Mobile Computing Anthony Lo *, Winston Seah * and Edwin Schreuder + * Centre for Wireless Communications 1, National University of Singapore, 20 Science Park
Table of Contents 1 MSDP Configuration 1-1
 Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Multi-Instance MSDP 1-7 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring
Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Multi-Instance MSDP 1-7 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring
Design and Implementation of an Anycast Efficient QoS Routing on OSPFv3
 Design and Implementation of an Anycast Efficient QoS Routing on OSPFv3 Han Zhi-nan Yan Wei Zhang Li Wang Yue Computer Network Laboratory Department of Computer Science & Technology, Peking University
Design and Implementation of an Anycast Efficient QoS Routing on OSPFv3 Han Zhi-nan Yan Wei Zhang Li Wang Yue Computer Network Laboratory Department of Computer Science & Technology, Peking University
BLM6196 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS
 BLM696 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Prof. Dr. Hasan Hüseyin BALIK (7 th Week) 7. Routing 7.Outline Routing in Packet-Switching Networks Examples: Routing in ARPANET Internet Routing Protocols
BLM696 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Prof. Dr. Hasan Hüseyin BALIK (7 th Week) 7. Routing 7.Outline Routing in Packet-Switching Networks Examples: Routing in ARPANET Internet Routing Protocols
Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s
 Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s M. Nagaratna Assistant Professor Dept. of CSE JNTUH, Hyderabad, India V. Kamakshi Prasad Prof & Additional Cont. of. Examinations
Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s M. Nagaratna Assistant Professor Dept. of CSE JNTUH, Hyderabad, India V. Kamakshi Prasad Prof & Additional Cont. of. Examinations
Ecient Processor Allocation for 3D Tori. Wenjian Qiao and Lionel M. Ni. Department of Computer Science. Michigan State University
 Ecient Processor llocation for D ori Wenjian Qiao and Lionel M. Ni Department of Computer Science Michigan State University East Lansing, MI 4884-107 fqiaow, nig@cps.msu.edu bstract Ecient allocation of
Ecient Processor llocation for D ori Wenjian Qiao and Lionel M. Ni Department of Computer Science Michigan State University East Lansing, MI 4884-107 fqiaow, nig@cps.msu.edu bstract Ecient allocation of
Enhancement of the CBT Multicast Routing Protocol
 Enhancement of the CBT Multicast Routing Protocol Seok Joo Koh and Shin Gak Kang Protocol Engineering Center, ETRI, Korea E- mail: sj ko h @ pcc.c t ri.rc.k Abstract In this paper, we propose a simple
Enhancement of the CBT Multicast Routing Protocol Seok Joo Koh and Shin Gak Kang Protocol Engineering Center, ETRI, Korea E- mail: sj ko h @ pcc.c t ri.rc.k Abstract In this paper, we propose a simple
Multiple LAN Internet Protocol Converter (MLIC) for Multimedia Conferencing
 Multiple LAN Internet Protocol Converter (MLIC) for Multimedia Conferencing Tat Chee Wan (tcwan@cs.usm.my) R. Sureswaran (sures@cs.usm.my) K. Saravanan (sara@network2.cs.usm.my) Network Research Group
Multiple LAN Internet Protocol Converter (MLIC) for Multimedia Conferencing Tat Chee Wan (tcwan@cs.usm.my) R. Sureswaran (sures@cs.usm.my) K. Saravanan (sara@network2.cs.usm.my) Network Research Group
Configuring IP Multicast Routing
 34 CHAPTER This chapter describes how to configure IP multicast routing on the Cisco ME 3400 Ethernet Access switch. IP multicasting is a more efficient way to use network resources, especially for bandwidth-intensive
34 CHAPTER This chapter describes how to configure IP multicast routing on the Cisco ME 3400 Ethernet Access switch. IP multicasting is a more efficient way to use network resources, especially for bandwidth-intensive
Open Shortest Path Firts -2 OSPF-2 (RFC As mentioned before, there are two basic routing algorithms. rst one, distance ve
 Layer Routing - IV Network OSPF-2 Yatindra Nath Singh ynsingh@ieee.org Dept. Of Electrical Engineering IIT Kanpur-208016 22 August 2001 1 Open Shortest Path Firts -2 OSPF-2 (RFC 2328 - http://www.ietf.org/)
Layer Routing - IV Network OSPF-2 Yatindra Nath Singh ynsingh@ieee.org Dept. Of Electrical Engineering IIT Kanpur-208016 22 August 2001 1 Open Shortest Path Firts -2 OSPF-2 (RFC 2328 - http://www.ietf.org/)
FB(9,3) Figure 1(a). A 4-by-4 Benes network. Figure 1(b). An FB(4, 2) network. Figure 2. An FB(27, 3) network
 Congestion-free Routing of Streaming Multimedia Content in BMIN-based Parallel Systems Harish Sethu Department of Electrical and Computer Engineering Drexel University Philadelphia, PA 19104, USA sethu@ece.drexel.edu
Congestion-free Routing of Streaming Multimedia Content in BMIN-based Parallel Systems Harish Sethu Department of Electrical and Computer Engineering Drexel University Philadelphia, PA 19104, USA sethu@ece.drexel.edu
Routing Protocols in MANETs
 Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Efficient Hybrid Multicast Routing Protocol for Ad-Hoc Wireless Networks
 Efficient Hybrid Multicast Routing Protocol for Ad-Hoc Wireless Networks Jayanta Biswas and Mukti Barai and S. K. Nandy CAD Lab, Indian Institute of Science Bangalore, 56, India {jayanta@cadl, mbarai@cadl,
Efficient Hybrid Multicast Routing Protocol for Ad-Hoc Wireless Networks Jayanta Biswas and Mukti Barai and S. K. Nandy CAD Lab, Indian Institute of Science Bangalore, 56, India {jayanta@cadl, mbarai@cadl,
A Performance Evaluation Architecture for Hierarchical PNNI and Performance Evaluation of Different Aggregation Algorithms in Large ATM Networks
 A Performance Evaluation Architecture for Hierarchical PNNI and Performance Evaluation of Different Aggregation Algorithms in Large ATM Networks Gowri Dhandapani 07/17/2000 Organization PNNI Basics Motivation
A Performance Evaluation Architecture for Hierarchical PNNI and Performance Evaluation of Different Aggregation Algorithms in Large ATM Networks Gowri Dhandapani 07/17/2000 Organization PNNI Basics Motivation
Routing protocols in WSN
 Routing protocols in WSN 1.1 WSN Routing Scheme Data collected by sensor nodes in a WSN is typically propagated toward a base station (gateway) that links the WSN with other networks where the data can
Routing protocols in WSN 1.1 WSN Routing Scheme Data collected by sensor nodes in a WSN is typically propagated toward a base station (gateway) that links the WSN with other networks where the data can
A FRAMEWORK FOR PERFORMANCE CHARACTERIZATION AND ENHANCEMENT OF THE OSPF ROUTING PROTOCOL
 A FRAMEWORK FOR PERFORMANCE CHARACTERIZATION AND ENHANCEMENT OF THE OSPF ROUTING PROTOCOL H. El-Sayed, M. Ahmed, M. Jaseemuddin, D. Petriu UAE University, Al-Ain P.O.Box, UAE, helsayed@uaeu.ac.ae, CIENA
A FRAMEWORK FOR PERFORMANCE CHARACTERIZATION AND ENHANCEMENT OF THE OSPF ROUTING PROTOCOL H. El-Sayed, M. Ahmed, M. Jaseemuddin, D. Petriu UAE University, Al-Ain P.O.Box, UAE, helsayed@uaeu.ac.ae, CIENA
Distributed Systems Multicast & Group Communication Services
 Distributed Systems 600.437 Multicast & Group Communication Services Department of Computer Science The Johns Hopkins University 1 Multicast & Group Communication Services Lecture 3 Guide to Reliable Distributed
Distributed Systems 600.437 Multicast & Group Communication Services Department of Computer Science The Johns Hopkins University 1 Multicast & Group Communication Services Lecture 3 Guide to Reliable Distributed
Byzantine Consensus in Directed Graphs
 Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Top-Down Network Design
 Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Original slides by Cisco Press & Priscilla Oppenheimer Selection Criteria for Switching and Routing Protocols Network traffic
Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Original slides by Cisco Press & Priscilla Oppenheimer Selection Criteria for Switching and Routing Protocols Network traffic
Advanced Networking. Multicast
 Advanced Networking Multicast Renato Lo Cigno Renato.LoCigno@dit.unitn.it Homepage: disi.unitn.it/locigno/index.php/teaching-duties/advanced-networking Multicasting Addresses that refer to group of hosts
Advanced Networking Multicast Renato Lo Cigno Renato.LoCigno@dit.unitn.it Homepage: disi.unitn.it/locigno/index.php/teaching-duties/advanced-networking Multicasting Addresses that refer to group of hosts
WSN Routing Protocols
 WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
Enhanced Cores Based Tree for Many-to-Many IP Multicasting
 Enhanced Cores Based Tree for Many-to-Many IP Multicasting In this paper, we propose a simple and practical scheme for many-to-many IP multicasting. The proposed scheme is based on the core based tree
Enhanced Cores Based Tree for Many-to-Many IP Multicasting In this paper, we propose a simple and practical scheme for many-to-many IP multicasting. The proposed scheme is based on the core based tree
Operation Manual Routing Protocol. Table of Contents
 Table of Contents Table of Contents Chapter 1 IP Routing Protocol Overview... 1-1 1.1 Introduction to IP Route and Routing Table... 1-1 1.1.1 IP Route... 1-1 1.1.2 Routing Table... 1-1 1.2 Routing Management
Table of Contents Table of Contents Chapter 1 IP Routing Protocol Overview... 1-1 1.1 Introduction to IP Route and Routing Table... 1-1 1.1.1 IP Route... 1-1 1.1.2 Routing Table... 1-1 1.2 Routing Management
Unit 3: Dynamic Routing
 Unit 3: Dynamic Routing Basic Routing The term routing refers to taking a packet from one device and sending it through the network to another device on a different network. Routers don t really care about
Unit 3: Dynamic Routing Basic Routing The term routing refers to taking a packet from one device and sending it through the network to another device on a different network. Routers don t really care about
Configuring Bidirectional PIM
 Configuring Bidirectional PIM This chapter describes how to configure the Bidirectional PIM (bidir-pim) feature. Bidir-PIM is a variant of the Protocol Independent Multicast (PIM) suite of routing protocols
Configuring Bidirectional PIM This chapter describes how to configure the Bidirectional PIM (bidir-pim) feature. Bidir-PIM is a variant of the Protocol Independent Multicast (PIM) suite of routing protocols
Network Layer: Routing
 Network Layer: Routing The Problem A B R 1 R 2 R 4 R 3 Goal: for each destination, compute next hop 1 Lecture 9 2 Basic Assumptions Trivial solution: Flooding Dynamic environment: links and routers unreliable:
Network Layer: Routing The Problem A B R 1 R 2 R 4 R 3 Goal: for each destination, compute next hop 1 Lecture 9 2 Basic Assumptions Trivial solution: Flooding Dynamic environment: links and routers unreliable:
AODV-PA: AODV with Path Accumulation
 -PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
-PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS
 A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS Tzu-Chiang Chiang,, Ching-Hung Yeh, Yueh-Min Huang and Fenglien Lee Department of Engineering Science, National Cheng-Kung University, Taiwan,
A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS Tzu-Chiang Chiang,, Ching-Hung Yeh, Yueh-Min Huang and Fenglien Lee Department of Engineering Science, National Cheng-Kung University, Taiwan,
Distributed Synchronization. EECS 591 Farnam Jahanian University of Michigan
 Distributed Synchronization EECS 591 Farnam Jahanian University of Michigan Reading List Tanenbaum Chapter 5.1, 5.4 and 5.5 Clock Synchronization Distributed Election Mutual Exclusion Clock Synchronization
Distributed Synchronization EECS 591 Farnam Jahanian University of Michigan Reading List Tanenbaum Chapter 5.1, 5.4 and 5.5 Clock Synchronization Distributed Election Mutual Exclusion Clock Synchronization
On the Impact of Route Processing and MRAI Timers on BGP Convergence Times
 On the Impact of Route Processing and MRAI Timers on BGP Convergence Times Shivani Deshpande and Biplab Sikdar Department of ECSE, Rensselaer Polytechnic Institute, Troy, NY 12180 Abstract Fast convergence
On the Impact of Route Processing and MRAI Timers on BGP Convergence Times Shivani Deshpande and Biplab Sikdar Department of ECSE, Rensselaer Polytechnic Institute, Troy, NY 12180 Abstract Fast convergence
Coordination 1. To do. Mutual exclusion Election algorithms Next time: Global state. q q q
 Coordination 1 To do q q q Mutual exclusion Election algorithms Next time: Global state Coordination and agreement in US Congress 1798-2015 Process coordination How can processes coordinate their action?
Coordination 1 To do q q q Mutual exclusion Election algorithms Next time: Global state Coordination and agreement in US Congress 1798-2015 Process coordination How can processes coordinate their action?
Configuring IP Multicast Routing
 39 CHAPTER This chapter describes how to configure IP multicast routing on the Catalyst 3560 switch. IP multicasting is a more efficient way to use network resources, especially for bandwidth-intensive
39 CHAPTER This chapter describes how to configure IP multicast routing on the Catalyst 3560 switch. IP multicasting is a more efficient way to use network resources, especially for bandwidth-intensive
Link State Routing. Link State Packets. Link State Protocol. Link State Protocols Basic ideas Problems and pitfalls
 Link State Routing In particular OSPF Karst Koymans Informatics Institute University of Amsterdam (version 16.3, 2017/03/09 11:25:31) Tuesday, March 7, 2017 Link State Protocols Basic ideas Problems and
Link State Routing In particular OSPF Karst Koymans Informatics Institute University of Amsterdam (version 16.3, 2017/03/09 11:25:31) Tuesday, March 7, 2017 Link State Protocols Basic ideas Problems and
McGill University - Faculty of Engineering Department of Electrical and Computer Engineering
 McGill University - Faculty of Engineering Department of Electrical and Computer Engineering ECSE 494 Telecommunication Networks Lab Prof. M. Coates Winter 2003 Experiment 5: LAN Operation, Multiple Access
McGill University - Faculty of Engineering Department of Electrical and Computer Engineering ECSE 494 Telecommunication Networks Lab Prof. M. Coates Winter 2003 Experiment 5: LAN Operation, Multiple Access
Enhanced IGRP. Chapter Goals. Enhanced IGRP Capabilities and Attributes CHAPTER
 40 CHAPTER Chapter Goals Identify the four key technologies employed by (EIGRP). Understand the Diffusing Update Algorithm (DUAL), and describe how it improves the operational efficiency of EIGRP. Learn
40 CHAPTER Chapter Goals Identify the four key technologies employed by (EIGRP). Understand the Diffusing Update Algorithm (DUAL), and describe how it improves the operational efficiency of EIGRP. Learn
Multicast Communications. Tarik Čičić, 4. March. 2016
 Multicast Communications Tarik Čičić, 4. March. 06 Overview One-to-many communication, why and how Algorithmic approach: Steiner trees Practical algorithms Multicast tree types Basic concepts in multicast
Multicast Communications Tarik Čičić, 4. March. 06 Overview One-to-many communication, why and how Algorithmic approach: Steiner trees Practical algorithms Multicast tree types Basic concepts in multicast
Distributed System Chapter 16 Issues in ch 17, ch 18
 Distributed System Chapter 16 Issues in ch 17, ch 18 1 Chapter 16: Distributed System Structures! Motivation! Types of Network-Based Operating Systems! Network Structure! Network Topology! Communication
Distributed System Chapter 16 Issues in ch 17, ch 18 1 Chapter 16: Distributed System Structures! Motivation! Types of Network-Based Operating Systems! Network Structure! Network Topology! Communication
Characteristics of Mult l ip i ro r ce c ssors r
 Characteristics of Multiprocessors A multiprocessor system is an interconnection of two or more CPUs with memory and input output equipment. The term processor in multiprocessor can mean either a central
Characteristics of Multiprocessors A multiprocessor system is an interconnection of two or more CPUs with memory and input output equipment. The term processor in multiprocessor can mean either a central
Architecture-Dependent Tuning of the Parameterized Communication Model for Optimal Multicasting
 Architecture-Dependent Tuning of the Parameterized Communication Model for Optimal Multicasting Natawut Nupairoj and Lionel M. Ni Department of Computer Science Michigan State University East Lansing,
Architecture-Dependent Tuning of the Parameterized Communication Model for Optimal Multicasting Natawut Nupairoj and Lionel M. Ni Department of Computer Science Michigan State University East Lansing,
Distributed systems. Lecture 6: distributed transactions, elections, consensus and replication. Malte Schwarzkopf
 Distributed systems Lecture 6: distributed transactions, elections, consensus and replication Malte Schwarzkopf Last time Saw how we can build ordered multicast Messages between processes in a group Need
Distributed systems Lecture 6: distributed transactions, elections, consensus and replication Malte Schwarzkopf Last time Saw how we can build ordered multicast Messages between processes in a group Need
How did IP Multicast get so complicated?
 How did IP Multicast get so complicated? Mark Handley ACIRI mjh@aciri.org Overview IP Multicast Service Model Multicast Addresses DVMRP (1988-1993) Broadcast and Prune PIM-DM (~1993) DVMRP for "real" routers
How did IP Multicast get so complicated? Mark Handley ACIRI mjh@aciri.org Overview IP Multicast Service Model Multicast Addresses DVMRP (1988-1993) Broadcast and Prune PIM-DM (~1993) DVMRP for "real" routers
Broadcast and Multicast Routing
 Broadcast and Multicast Routing Daniel Zappala CS 460 Computer Networking Brigham Young University Group Communication 2/34 How can the Internet provide efficient group communication? send the same copy
Broadcast and Multicast Routing Daniel Zappala CS 460 Computer Networking Brigham Young University Group Communication 2/34 How can the Internet provide efficient group communication? send the same copy
1 Introduction Multicast communication is an ecient method for disseminating data in a multicast group with a sender and a set of receivers. Many mult
 GSGC: An Ecient Gossip-Style Garbage Collection Scheme for Scalable Reliable Multicast Katherine Guo, Mark Hayden, Robbert van Renesse, Werner Vogels and Kenneth P. Birman Department of Computer Science
GSGC: An Ecient Gossip-Style Garbage Collection Scheme for Scalable Reliable Multicast Katherine Guo, Mark Hayden, Robbert van Renesse, Werner Vogels and Kenneth P. Birman Department of Computer Science
Helsinki University of Technology Telecommunications Laboratory. OSPF Routing Protocol Licenciate course seminar paper
 Helsinki University of Technology Telecommunications Laboratory OSPF Routing Protocol Licenciate course seminar paper Shkumbin I. Hamiti, 08.10.1996 Communications Laboratory, TKK-HUT email: bini#tiltu.hut.fi
Helsinki University of Technology Telecommunications Laboratory OSPF Routing Protocol Licenciate course seminar paper Shkumbin I. Hamiti, 08.10.1996 Communications Laboratory, TKK-HUT email: bini#tiltu.hut.fi
On Checkpoint Latency. Nitin H. Vaidya. In the past, a large number of researchers have analyzed. the checkpointing and rollback recovery scheme
 On Checkpoint Latency Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 E-mail: vaidya@cs.tamu.edu Web: http://www.cs.tamu.edu/faculty/vaidya/ Abstract
On Checkpoint Latency Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 E-mail: vaidya@cs.tamu.edu Web: http://www.cs.tamu.edu/faculty/vaidya/ Abstract
Coordination and Agreement
 Coordination and Agreement Nicola Dragoni Embedded Systems Engineering DTU Informatics 1. Introduction 2. Distributed Mutual Exclusion 3. Elections 4. Multicast Communication 5. Consensus and related problems
Coordination and Agreement Nicola Dragoni Embedded Systems Engineering DTU Informatics 1. Introduction 2. Distributed Mutual Exclusion 3. Elections 4. Multicast Communication 5. Consensus and related problems
Table of Contents. Cisco Introduction to EIGRP
 Table of Contents Introduction to EIGRP...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 What is IGRP?...2 What is EIGRP?...2 How Does EIGRP Work?...2 EIGRP
Table of Contents Introduction to EIGRP...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 What is IGRP?...2 What is EIGRP?...2 How Does EIGRP Work?...2 EIGRP
Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
Technion - Computer Science Department - Technical Report LCCN
 Technion - Israel Institute of Technology Computer Science Department Laboratory for Computer Communication Networking Distributed Network Control for Optical Networks by R. Ramaswami and A. Segall LCCN
Technion - Israel Institute of Technology Computer Science Department Laboratory for Computer Communication Networking Distributed Network Control for Optical Networks by R. Ramaswami and A. Segall LCCN
Protocol Independent Multicast (PIM): Protocol Specication. Deborah Estrin. Ching-gung Liu. January 11, Status of This Memo
 Protocol Independent Multicast (PIM): Protocol Specication Stephen Deering Xerox PARC 3333 Coyoty Hill Road Palo Alto, CA 94304 deering@parc.xerox.com Van Jacobson Lawrence Berkeley Laboratory 1 Cyclotron
Protocol Independent Multicast (PIM): Protocol Specication Stephen Deering Xerox PARC 3333 Coyoty Hill Road Palo Alto, CA 94304 deering@parc.xerox.com Van Jacobson Lawrence Berkeley Laboratory 1 Cyclotron
Charles Perkins Nokia Research Center 2 July Mobility Support in IPv6 <draft-ietf-mobileip-ipv6-14.txt> Status of This Memo
 IETF Mobile IP Working Group INTERNET-DRAFT David B. Johnson Rice University Charles Perkins Nokia Research Center 2 July 2000 Mobility Support in IPv6 Status of This
IETF Mobile IP Working Group INTERNET-DRAFT David B. Johnson Rice University Charles Perkins Nokia Research Center 2 July 2000 Mobility Support in IPv6 Status of This
IPv6 PIM-DM configuration example 36 IPv6 PIM-SM non-scoped zone configuration example 39 IPv6 PIM-SM admin-scoped zone configuration example 42 IPv6
 Contents Configuring IPv6 PIM 1 Overview 1 IPv6 PIM-DM overview 1 IPv6 PIM-SM overview 3 IPv6 BIDIR-PIM overview 8 IPv6 administrative scoping overview 11 IPv6 PIM-SSM overview 13 Relationship among IPv6
Contents Configuring IPv6 PIM 1 Overview 1 IPv6 PIM-DM overview 1 IPv6 PIM-SM overview 3 IPv6 BIDIR-PIM overview 8 IPv6 administrative scoping overview 11 IPv6 PIM-SSM overview 13 Relationship among IPv6
Routing Protocol - IS-IS
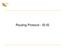 Routing Protocol - IS-IS What is IS-IS? Intermediate System to Intermediate System intra-domain routing protocol :: IS, ES Is a Link State Protocol Is a dynamic routing protocol based on SPF routing algorithm
Routing Protocol - IS-IS What is IS-IS? Intermediate System to Intermediate System intra-domain routing protocol :: IS, ES Is a Link State Protocol Is a dynamic routing protocol based on SPF routing algorithm
n = 2 n = 1 µ λ n = 0
 A Comparison of Allocation Policies in Wavelength Routing Networks Yuhong Zhu, George N. Rouskas, Harry G. Perros Department of Computer Science, North Carolina State University Abstract We consider wavelength
A Comparison of Allocation Policies in Wavelength Routing Networks Yuhong Zhu, George N. Rouskas, Harry G. Perros Department of Computer Science, North Carolina State University Abstract We consider wavelength
Configuring MSDP. MSDP overview. How MSDP works. MSDP peers
 Contents Configuring MSDP 1 MSDP overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 6 Configuring basic MSDP functions 7 Configuration prerequisites
Contents Configuring MSDP 1 MSDP overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 6 Configuring basic MSDP functions 7 Configuration prerequisites
Internet Engineering Task Force (IETF) Request for Comments: Category: Experimental February 2014 ISSN:
 Internet Engineering Task Force (IETF) A. Retana Request for Comments: 7137 S. Ratliff Updates: 5820 Cisco Systems, Inc. Category: Experimental February 2014 ISSN: 2070-1721 Use of the OSPF-MANET Interface
Internet Engineering Task Force (IETF) A. Retana Request for Comments: 7137 S. Ratliff Updates: 5820 Cisco Systems, Inc. Category: Experimental February 2014 ISSN: 2070-1721 Use of the OSPF-MANET Interface
Routing, Routing Algorithms & Protocols
 Routing, Routing Algorithms & Protocols Computer Networks Lecture 6 http://goo.gl/pze5o8 Circuit-Switched and Packet-Switched WANs 2 Circuit-Switched Networks Older (evolved from telephone networks), a
Routing, Routing Algorithms & Protocols Computer Networks Lecture 6 http://goo.gl/pze5o8 Circuit-Switched and Packet-Switched WANs 2 Circuit-Switched Networks Older (evolved from telephone networks), a
Routing Overview for Firepower Threat Defense
 Path Determination This chapter describes underlying concepts of how routing behaves within the Cisco Firepower Threat Defense, and the routing protocols that are supported. Routing is the act of moving
Path Determination This chapter describes underlying concepts of how routing behaves within the Cisco Firepower Threat Defense, and the routing protocols that are supported. Routing is the act of moving
Distributed Systems Fault Tolerance
 Distributed Systems Fault Tolerance [] Fault Tolerance. Basic concepts - terminology. Process resilience groups and failure masking 3. Reliable communication reliable client-server communication reliable
Distributed Systems Fault Tolerance [] Fault Tolerance. Basic concepts - terminology. Process resilience groups and failure masking 3. Reliable communication reliable client-server communication reliable
J. A. Drew Hamilton, Jr., Ph.D. Director, Information Assurance Laboratory and Associate Professor Computer Science & Software Engineering
 Auburn Information Assurance Laboratory J. A. Drew Hamilton, Jr., Ph.D. Director, Information Assurance Laboratory and Associate Professor Computer Science & Software Engineering 107 Dunstan Hall Auburn
Auburn Information Assurance Laboratory J. A. Drew Hamilton, Jr., Ph.D. Director, Information Assurance Laboratory and Associate Professor Computer Science & Software Engineering 107 Dunstan Hall Auburn
Multicast Communications
 Multicast Communications Multicast communications refers to one-to-many or many-tomany communications. Unicast Broadcast Multicast Dragkedja IP Multicasting refers to the implementation of multicast communication
Multicast Communications Multicast communications refers to one-to-many or many-tomany communications. Unicast Broadcast Multicast Dragkedja IP Multicasting refers to the implementation of multicast communication
Implementations of Dijkstra's Algorithm. Based on Multi-Level Buckets. November Abstract
 Implementations of Dijkstra's Algorithm Based on Multi-Level Buckets Andrew V. Goldberg NEC Research Institute 4 Independence Way Princeton, NJ 08540 avg@research.nj.nec.com Craig Silverstein Computer
Implementations of Dijkstra's Algorithm Based on Multi-Level Buckets Andrew V. Goldberg NEC Research Institute 4 Independence Way Princeton, NJ 08540 avg@research.nj.nec.com Craig Silverstein Computer
OSPF Protocol Overview on page 187. OSPF Standards on page 188. OSPF Area Terminology on page 188. OSPF Routing Algorithm on page 190
 Chapter 17 OSPF Protocol Overview The Open Shortest Path First (OSPF) protocol is an interior gateway protocol (IGP) that routes packets within a single autonomous system (AS). OSPF uses link-state information
Chapter 17 OSPF Protocol Overview The Open Shortest Path First (OSPF) protocol is an interior gateway protocol (IGP) that routes packets within a single autonomous system (AS). OSPF uses link-state information
Distributed minimum spanning tree problem
 Distributed minimum spanning tree problem Juho-Kustaa Kangas 24th November 2012 Abstract Given a connected weighted undirected graph, the minimum spanning tree problem asks for a spanning subtree with
Distributed minimum spanning tree problem Juho-Kustaa Kangas 24th November 2012 Abstract Given a connected weighted undirected graph, the minimum spanning tree problem asks for a spanning subtree with
