Seattle Cisco Users Group
|
|
|
- Corey Cunningham
- 6 years ago
- Views:
Transcription
1 Seattle Cisco Users Group CCNA Lab Project #3 Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP June 10, 2011
2 Table of Contents 1. Introduction The CCNA Certification Purpose of the Lab Project Overview Basic Topology Lab Access Lab Exercises Initial Configuration Tasks Local Device Interface Configuration Tasks Routing Protocol Configuration Tasks Network Address Translation Tasks Security Configuration Tasks Answer Key Initial Configuration Tasks Local Device Interface Configuration Tasks Routing Protocol Configuration Tasks Network Address Translation Tasks Security Configuration Tasks Final Configurations R1 Configuration R2 Configuration R3 Configuration R4 Configuration SW1 Configuration...64
3 1. Introduction 1.1. The CCNA Certification Source: The Cisco Certified Network Associate certification has traditionally been the point of entry for many network engineers into the world of Cisco networking. In 2007, Cisco created a new entry-level certification entitled the CCENT, or Cisco Certified Entry Level Technician. To achieve the CCNA certification, candidates must successfully pass the CCNA exam (single exam), or the two Interconnecting Cisco Networking Devices exams ( and ). The CCNA certification validates the skill-sets needed to configure and operate mediumsized routed and/or switched internetworks, including (but not limited to) the following topic areas: Mitigation of basic security threats Wireless networking Frame-Relay Wide Area Networks OSPF/EIGRP/RIPV2 IP Routing Virtual Local Area Networks (VLANs) Ethernet Local Area Networks Access Control Lists (ACL s) Internet Protocol Version Purpose of the Lab Project A thorough understanding of networking concepts is the foundation upon which understanding is essentially built. While theoretical knowledge is important, the application of that knowledge is equally important, and forms the basis for effective performance in real-world environments. Early versions of the CCNA-level certification exams concentrated on factual knowledge, while current exams utilize realistic scenarios that reflect more hands on experiences. To satisfy these types of requirements, CCNA students need practical, experience-based exercises.
4 1.3. Overview The well-known CCIE Lab exam is composed of an eight-hour set of configuration scenarios designed to test the absolute limits of a candidate s practical knowledge. While the tasks do not represent best-practice applications, the challenges certainly demand a thorough knowledge of every technical aspect involved in networking. As the current exam pass-rates will demonstrate, only the most well-prepared participants will possess the discipline and skills to successfully complete the exam requirements. Mirroring the same demands at a level appropriate to the CCNA certification, the CCNA project seeks to create an environment for hands-on experience necessary to successfully complete the certification exam environment Basic Topology The CCNA project involves the use of four routers and three switches to emulate the complexity of a medium-sized routed and switched network. The topology involves three separate locations/sites across a simulated Internet VPN Wide Area Network (WAN) as well as distinct Local Area Networks (LANs). In addition, Internet access is included at each site to mirror real-world applications Lab Access
5 The Seattle Cisco Users Group ( provides study opportunities through CCNA study groups, usually held twice a year. At present, INX ( a premier Cisco Gold Partner), provides Internet-based access to lab equipment designed to satisfy the requirements of the CCNA project outlined here. An SSL-based clientless Virtual Private Network (VPN) allows secure access to a lab environment compatible with the project requirements. The lab is accessible at and requires username/password access arranged in advance. The portal appears as follows:
6 2. Lab Exercises 2.1. Initial Configuration Tasks The CCNA project requires certain basic configuration information in order to function properly. These requirements lay the foundation of successful completion of all later tasks Basic Information All VLAN, IP Addressing, and interface addressing requirements are as follows: Configure Device Host Names All devices used in the project require host names as part of the requirements. Use the following naming conventions: Routers: RX (X=Site Number) Switches: SWX (X=Site Number) Internet Router, Site 3: R Configure Device Access
7 Each device within the overall lab environment has different methods of access that must be configured and secured accordingly. Configure each access method as follows: Console Access o Create login process to go directly to privileged mode o Use password Cisco123 o No requirement to enter a password to access AUX Access (router only) o Create login process to enter exec mode o Use password Cisco123 o Login required VTY Access (telnet/ssh) o Create login process to enter exec mode o Use password Cisco123 o Login required Configure Basic Security Settings All devices within a network must implement certain basic security settings in order to ensure consistent operation. Configure these settings as follows: Enable Secret o Cisco devices require a second password to enter privileged mode, which can be enable (not encrypted) or enable secret (encrypted) o Set the enable secret password to Cisco123 o Do not set the enable (non-encrypted) password Secure telnet/ssh access o Create an access-list to telnet access from outside the network but permit ssh from outside the network o Apply the access list in the appropriate location on all devices Configure Other Basic Device Settings Specific device settings can simplify management and operation within the network. Configure these settings as follows: Set clocks on all devices to Pacific Time, including Daylight Savings Time settings Disable devices from using DNS lookups Enable web-based access on all devices and set to port 8080 Set login message to Welcome to the CCNA VPN Lab Set all devices to update their clocks based on the time configured on R Local Device Interface Configuration Tasks
8 Every networking device in the environment has multiple interfaces that require specific configuration tasks in order to provide connectivity to resources VLAN Interfaces All sites have multiple VLAN segments that require configuration to be applied on the LAN switch as well as the site router. Configure the following VLANs at each site in the topology: Management VLAN: Used for managing all remote devices by resources at the central data center (R1/R2/R3 Only) o Set the VLAN ID to X (X=Site Number) o Name the VLAN MANAGEMENT VLAN o Create IP addressing to allow for 4 usable Hosts Production VLAN: Used for normal network operations o Set the VLAN ID to XX (X=Site Number) o Name the VLAN PRODUCTION VLAN o Create IP addressing to allow for 32 usable Hosts o Add R4 to R3 s Production VLAN Internet VLAN: Used for providing Internet access through the Internet connection at all sites o Set the VLAN ID to 99 o Name the VLAN INTERNET VLAN o Create IP addressing to allow for 4 usable Hosts Loopback Interfaces Loopback interfaces are logical interfaces that do not go down unless the device itself is no longer operational. Tying device processes to loopback interfaces prevent intermittent issues resulting from links going up and down. Create a loopback interface for each router in the network Assign the name Loopback 0 to each loopback interface Assign IP subnet for a single host: 10.Y.Y.Y (Y=device number) GRE VPN WAN Interfaces WAN connectivity between sites is provided through a VPN. Configure VPN access on the Internet interfaces as follows:
9 Internet WAN Interfaces Create a full-mesh tunnel configuration between all sites Specify GRE IP Encapsulation for the tunnels Specify the source as Fa0/0.99 Specify the destination using the Internet VLAN address of the neighboring router Assign IP addresses per diagram, with 8 usable hosts per subnet All sites receive their Internet access locally through an Ethernet handoff: Create subinterfaces using 99 as the reference number reference (e.g., FastEthernet 0/0.99) Specify ISL (R1/R2/R3) or 802.1Q (R4) Trunking Encapsulation and 99 as the VLAN ID Assign IP addresses per diagram, with 6 usable hosts per subnet 2.3. Routing Protocol Configuration Tasks Multiple routing protocols are in use throughout the network and require careful configuration to ensure correct operation. Refer to the following diagram as a reference point: SEACUG CCNA Study Group CCNA Lab Project Site 1 Site 2 R1 Internet GRE EIGRP R2 RIP V2 SW2 SW1 Site 3 R3 OSPF R4 SW EIGRP Configuration EIGRP is the primary routing configuration in use throughout the network, and must be operational at all three sites. Configure EIGRP routing as follows:
10 R1 EIGRP Configuration o Use AS Number 1003 o Enable EIGRP on all GRE tunnel interfaces o Disable auto summarization R2 EIGRP Configuration o Use AS Number 1003 o Enable EIGRP on all GRE tunnel interfaces o Enable EIGRP on Loopback and VLAN interfaces o Disable auto summarization R3 EIGRP Configuration o Use AS Number 1003 o Enable EIGRP on all GRE tunnel interfaces o Disable auto summarization OSPF Configuration OSPF is running between R3 and R4 for connectivity at a campus location. Configure routing as follows: R3 OSPF Configuration o Place the Loopback interface in area 3 o Place all local VLAN interfaces in area 3 o Do not specify the router-id R4 OSPF Configuration o Place all local VLAN interfaces and the loopback interface in area 3 o Do not specify the router-id Redistribution and Tuning Configuration With multiple routing protocols in use, full connectivity must be created between protocols to allow consistent communication. Configure as follows: Redistribute EIGRP into OSPF using a route map to ensure only the internal routes are permitted Perform redistribution on R1 so that all RIP interfaces will be accessible to the EIGRP process Do not configure any static routes to accomplish this task
11 Verify full reachability: 2.4. Network Address Translation Tasks o Ping all other devices in the network from each device o Successfully telnet to all devices in the network from each device All sites within the network utilize addressing from the RFC 1918 Private Addressing space, which are not valid on the Internet. In order to have full Internet connectivity, all internal addressing must be mapped to globally routable addressing space. In addition, an internal web server at Site 2 must also be accessible from the Internet Configure Port Address Translation for All Internal Hosts Configure Port Address Translation/Overloading on R1,R2, & R3 on the Internet Interface Static Network Address Translation for an Server on R2 services were previously enabled on R2 and accessible from within the internal network, but need to be available on the Internet for monitoring and management purposes. Using static a NAT entry, point connections to R2 s Production VLAN address Security Configuration Tasks Preventing unauthorized access to devices on the network may be supplied in part by the external ASA firewall, but additional measured need to be implemented to protect information assets Create and apply an access that will only allow internal devices to access the management VLAN on all devices. The company s information security policy stipulates that no users outside of the company are permitted to access internal resources. To prevent unauthorized access, disallow all outside users from accessing the hosts within the protected network Block outbound SMTP access from all sites Unsecured (SMTP) s are a source of security concerns for the management team and they have elected not to permit it anywhere on the network. Configure the appropriate packet filters/access-lists to block all SMTP outbound from all sites.
12 Block outbound TFTP access from Site 2 Site 2 contains sensitive data that must not be sent outside the network, and TFTP is considered a security risk. Configure the appropriate packet filters/access-lists to block all TFTP outbound from all sites Block all external access trying to reach the management VLAN Remote access has been provided at the primary corporate location for the purpose of managing all internal network resources. Because of the sensitive nature of the data at the corporate locations, external access to the Management VLANs is not permitted by the security policy. Construct an access list to block any attempt at access from the Internet interface.
13 3. Answer Key The following section outlines detailed, step-by-step solutions to the previous configuration requirements. This allows students to compare their own devices against the answers, keeping in mind that some minor differences may exist. In the SEACUG lab environment, for example, only a single switch is utilized for the topology. Answers are displayed in bold following restatement of the original configuration tasks Initial Configuration Tasks Basic Information All VLAN, IP Addressing, and interface addressing requirements are as follows: ANSWERS: All configuration tasks utilize these addressing specifications Configure Device Host Names ANSWERS: All devices used in the project require host names as part of the requirements. Use the following naming conventions: Routers: RX (X=Site Number) Switches: SWX (X=Site Number) Internet Router, Site 3: R4
14 R1 Hostname R1 (lab may already have hostname(s) configured) R2 Hostname R2 (lab may already have hostname(s) configured) R3 Hostname R3 (lab may already have hostname(s) configured) R4 Hostname R4 (lab may already have hostname(s) configured) SW1 Hostname SW1 (lab may already have hostname(s) configured) ** If using three switches, substitute SW2, SW3, etc. for additional switches ** Configure Device Access ANSWERS: Each device within the overall lab environment has different methods of access that must be configured and secured accordingly. Configure each access method as follows: Console Access o Create login process to go directly to privileged mode o Use password Cisco123 o No requirement to enter a password to access ** The privilege level command sets the default permission level available ** ** The password command specifies the access password ** ** The login command causes a required login process; no login disables it ** R1 line con 0 password cisco privilege level 15 no login R2
15 line con 0 password cisco privilege level 15 no login R3 line con 0 password cisco privilege level 15 no login R4 line con 0 password cisco privilege level 15 no login SW1 line con 0 password cisco privilege level 15 no login ** If using three switches, duplicate configuration for additional switches ** ANSWERS: AUX Access (router only) o Create login process to enter exec mode o Use password Cisco123 o Login required ** The password command specifies the access password ** ** The login command causes a required login process; no login disables it ** R1 line aux 0 password cisco login R2 line aux 0 password cisco login
16 R3 line aux 0 password cisco login R4 line aux 0 password cisco login ANSWERS: VTY Access (telnet/ssh) o Create login process to enter exec mode o Use password Cisco123 o Login required ** Available VTY lines vary by device, each of which is configurable separately** ** Programming multiple VTY requires specifying the range, the 2620 has 181 ** ** The login command causes a required login process; no login disables it ** R1 line vty password Cisco123 login R2 line vty password Cisco123 login R3 line vty password Cisco123 login R4 line vty password Cisco123 login
17 SW1 line vty 0 15 password Cisco123 login ** If using three switches, duplicate configuration for additional switches ** Configure Basic Security Settings ANSWERS: All devices within a network must implement certain basic security settings in order to ensure consistent operation. Configure these settings as follows: Enable Secret o Cisco devices require a second password to enter privileged mode, which can be enable (not encrypted) or enable secret (encrypted) o Set the enable secret password to Cisco123 o Do not set the enable (non-encrypted) password ** The enable secret command encrypts the password even in the configuration ** ** Remember that the passwords you specify are case sensitive ** R1 Enable secret Cisco123 R2 Enable secret Cisco123 R3 Enable secret Cisco123 R4 Enable secret cisco SW1 Enable secret Cisco123 ** If using three switches, duplicate configuration for additional switches **
18 Secure telnet/ssh access o Create an access-list to telnet access from outside the network but permit ssh from outside the network o Apply the access list in the appropriate location on all devices ANSWERS: ** Access control utilizes access lists for these types of functions ** ** Standard access lists (1-99) filter only by source ** ** Extended access lists ( ) can filter by source, destination, TCP/UDP, etc. ** **At the end of every access list an implicit deny all statement ** ** Specifying all addresses ranges in use will satisfy the requirements ** ** Applying the list on the Internet VLAN (fa0/0.99) is best, using the ip access-group command ** R1 access-list 101 deny tcp any any eq telnet access-list 101 permit tcp any any eq 22 access-list 101 permit ip any any int fa0/0.99 ip access-group 101 in R2 access-list 101 deny tcp any any eq telnet access-list 101 permit tcp any any eq 22 access-list 101 permit ip any any int fa0/0.99 ip access-group 101 in R3 access-list 101 deny tcp any any eq telnet access-list 101 permit tcp any any eq 22 access-list 101 permit ip any any int fa0/0.99 ip access-group 101 in ** If using three switches, duplicate configuration for additional switches ** Configure Other Basic Device Settings
19 ANSWERS: Specific device settings can simplify management and operation within the network. Configure these settings as follows: Set clocks on all devices to Pacific Time, including Daylight Savings Time settings Disable devices from using DNS lookups Enable web-based access on all devices and set to port 8080 Set login message to Welcome to the CCNA VPN Lab Set all devices to update their clocks based on the time configured on R4 ** Setting the system clock is one function done from the command line, not global configuration mode, using the set clock timezone command ** ** Disabling DNS lookups on a device is helpful especially f you mistype a command. The no ip domain-lookup command disables this function** ** Web-based device access is another way to program/monitor devices, with other settings as well. The ip http server command enables this. Setting a non-default port is accomplished using the ip http port command** ** Displaying a welcome message is another helpful functional that should be used whenever possible. The message of the day is configured using the command banner motd, with the # symbol acting as delimiters ** R1 clock timezone PST -8 clock summer-time PDT date Mar :00 Nov :00 no ip domain lookup banner motd #Welcome to the CCNA VPN Lab# ntp server R2 clock timezone PST -8 clock summer-time PDT date Mar :00 Nov :00 no ip domain lookup banner motd #Welcome to the CCNA VPN Lab# ntp server R3 clock timezone PST -8 clock summer-time PDT date Mar :00 Nov :00 no ip domain lookup banner motd #Welcome to the CCNA VPN Lab# ntp server
20 R4 ntp master no ip domain lookup banner motd #Welcome to the CCNA VPN Lab# SW1 clock timezone PST -8 clock summer-time PDT date Mar :00 Nov :00 no ip domain lookup banner motd #Welcome to the CCNA VPN Lab# ntp server ** If using three switches, duplicate configuration for additional switches ** 3.2. Local Device Interface Configuration Tasks Every networking device in the environment has multiple interfaces that require specific configuration tasks in order to provide connectivity to resources VLAN Interfaces ANSWERS: All sites have multiple VLAN segments that require configuration to be applied on the LAN switch as well as the site router. Configure the following VLANs at each site in the topology: ** Both the routers and switch(es) require separate and distinct configuration for creating and processing VLANs. The following outline demonstrates the switch portion of the configuration ** SW1 First, VLANs must be configured from global configuration mode: vlan 11 vlan 2 vlan 22 vlan 3 vlan 33 vlan 99 To support multiple VLANs, the ports on the switch(es) must be configured for trunking on the connection to the routers:
21 interface fa0/2 switchport trunk encapsulation dot1q switchport mode trunk description Trunk to R1 interface fa0/1 switchport trunk encapsulation dot1q switchport mode trunk description Trunk to R2 interface fa0/3 switchport trunk encapsulation dot1q switchport mode trunk description Trunk to R3 interface fa0/8 switchport trunk encapsulation dot1q switchport mode trunk description Trunk to R4 ** If using three switches, duplicate configuration for additional switches ** ANSWERS: Management VLAN: Used for managing all remote devices by resources at the central data center o Set the VLAN ID to X (X=Site Number) o Name the VLAN MANAGEMENT VLAN o Create IP addressing to allow for 4 usable Hosts ** VLAN configuration on a router interface requires the use of subinterfaces for each configured VLAN. The encapsulation type and VLAN ID/number must also be specified on the subinterface ** ** Choices for an IP subnet depend on the numbers of networks and hosts needed to satisfy requirements. For the Management VLAN, one network is needed, but 5 usable hosts. Subnets could include X (or /28), but that yields 30 usable hosts (too many) X (or /29) gives 6 usable hosts, which is a better choice ** R1 interface fa0/0.1 description Management VLAN encapsulation isl 1 ip address R2
22 interface fa0/0.2 description Management VLAN encapsulation isl 2 ip address R3 interface fa0/0.3 description Management VLAN encapsulation isl 3 ip address ANSWERS: Production VLAN: Used for normal network operations o Set the VLAN ID to XX (X=Site Number) o Name the VLAN PRODUCTION VLAN o Create IP addressing to allow for 32 usable Hosts ** VLAN configuration on a router interface requires the use of subinterfaces for each configured VLAN. The encapsulation type and VLAN ID/number must also be specified on the subinterface ** ** Choices for an IP subnet depend on the numbers of networks and hosts needed to satisfy requirements. For the Production VLAN, one network is needed, but 30 usable hosts. Subnets could include XX (or /27), but that yields 30 usable hosts (too few) XX (or/26) gives 62 usable hosts, which is a better choice ** R1 interface fa0/0.11 description Production VLAN encapsulation isl 11 ip address R2 interface fa0/0.22 description Production VLAN encapsulation isl 22 ip address R3 interface fa0/0.33 description Production VLAN
23 encapsulation isl 33 ip address ANSWERS: Internet VLAN: Used for providing Internet access through the Internet connection at Site 3 (R3/R4) o Set the VLAN ID to 99 o Name the VLAN INTERNET VLAN o Create IP addressing to allow for 4 usable Hosts ** VLAN configuration on a router interface requires the use of subinterfaces for each configured VLAN. The encapsulation type and VLAN ID/number must also be specified on the subinterface. ** R1 interface fa0/0.99 description Internet VLAN encapsulation isl 99 ip address R2 interface fa0/0.99 description Internet VLAN encapsulation isl 99 ip address R3 interface fa0/0.99 description Internet VLAN encapsulation isl ip address R4 interface fa0/0.99 description Internet VLAN encapsulation dot1q 99 ip address Loopback Interfaces (R1/R2/R3 Only)
24 ANSWERS: R1 Loopback interfaces are logical interfaces that do not go down unless the device itself is no longer operational. Tying device processes to loopback interfaces prevent intermittent issues resulting from links going up and down. Create a loopback interface for each router in the network Assign the name Loopback 0 to each loopback interface Assign IP subnet for a single host: 10.Y.Y.Y (Y=device number) interface Loopback0 description Loopback Interface ip address R2 interface Loopback0 description Loopback Interface ip address R3 interface Loopback0 description Loopback Interface ip address GRE Interfaces (R1/R2/R3 Only) ANSWERS: Backup network connectivity is required in the event of failure on the Metro-E service. Configure VPN access on the Internet interfaces as follows: Create a full-mesh tunnel configuration between all sites Specify GRE IP Encapsulation for the tunnels Enable CDP on the tunnels Specify the source as Fa0/0.99 Specify the destination using the Internet VLAN address of the neighboring router Assign IP addresses per diagram, with 8 usable hosts per subnet ** Generic Routing Encapsulation (GRE) is used to tunnel non-ip protocols through an IP environment, and also frequently used in VPN configurations. In a
25 production setting, the addition of IPSec encryption would be necessary to address security concerns ** ** Tunnel interfaces require specifying source and destination endpoints in addition to standard interface commands ** R1 interface Tunnel12 description VPN INTERFACE to R2 ip address tunnel source tunnel destination interface Tunnel13 description VPN INTERFACE to R3 ip address tunnel source tunnel destination R2 interface Tunnel12 description VPN INTERFACE to R1 ip address tunnel source tunnel destination interface Tunnel23 description VPN INTERFACE to R2 ip address tunnel source tunnel destination R3 interface Tunnel13 description VPN INTERFACE to R2 ip address tunnel source tunnel destination interface Tunnel23 description VPN INTERFACE to R1 ip address tunnel source tunnel destination
26 3.3. Routing Protocol Configuration Tasks Multiple routing protocols are in use throughout the network and require careful configuration to ensure correct operation. Refer to the following diagram as a reference point: SEACUG CCNA Study Group CCNA Lab Project Site 1 Site 2 R1 Internet GRE EIGRP R2 RIP V2 SW2 SW1 Site 3 R3 OSPF R4 SW EIGRP Configuration ANSWERS: EIGRP is the primary routing configuration in use throughout the network, and must be operational at all three sites. Configure EIGRP routing as follows: R1 EIGRP Configuration o Use AS Number 1003 o Enable EIGRP on all GRE tunnel interfaces o Disable auto summarization **EIGRP is configured from router configuration mode, which is entered by the command router eigrp <as-number> ** ** Interfaces are placed in EIGRP using the network command, using the best practice of the most specific subnets possible ** ** Automatic network summarization is on by default ** R1
27 router eigrp 1003 network network no auto-summary ANSWERS: R2 EIGRP Configuration o Use AS Number 1003 o Enable EIGRP on all GRE tunnel interfaces o Enable EIGRP on Loopback and VLAN interfaces o Disable auto summarization **EIGRP is configured from router configuration mode, which is entered by the command router eigrp <as-number> ** ** Interfaces are placed in EIGRP using the network command, using the best practice of the most specific subnets possible ** ** Automatic network summarization is on by default ** R2 router eigrp 1003 network network network network network no auto-summary ANSWERS: R3 EIGRP Configuration o Use AS Number 111 o Enable EIGRP on all GRE tunnel interfaces o Disable auto summarization **EIGRP is configured from router configuration mode, which is entered by the command router eigrp <as-number> ** ** Interfaces are placed in EIGRP using the network command, using the best practice of the most specific subnets possible ** ** Automatic network summarization is on by default ** R3 router eigrp 1003 network
28 network no auto-summary OSPF Configuration ANSWERS: OSPF is running between R3 and R4 for connectivity at a campus location. Configure routing as follows: R3 OSPF Configuration o Place the Loopback interface in area 3 o Place all local VLAN interfaces in area 3 o Do not specify the router-id **OSPF is configured from router configuration mode, which is entered by the command router ospf <process-id> ** ** Interfaces are placed in OSPF using the network command, using the best practice of the most specific subnets possible. The loopback and VLAN interfaces should be placed in area 3, and since there is only a single area no area 0 is required ** R3 router ospf 1 log-adjacency-changes network area 3 network area 3 network area 3 ANSWERS: R4 OSPF Configuration o Set Loopback 0 as the OSPF router-id o Place the Metro Ethernet interface in area 0 o Place all local VLAN interfaces and the loopback interface in area 2 ** OSPF is configured from router configuration mode, which is entered by the command router ospf <process-id> ** ** Interfaces are placed in OSPF using the network command, using the best practice of the most specific subnets possible. The loopback and VLAN interfaces should be placed in area 3, and since there is only a single area no area 0 is required **
29 R4 router ospf 1 router-id log-adjacency-changes network area 3 network area Redistribution and Tuning Configuration ANSWERS: R1 With multiple routing protocols in use, full connectivity must be created between protocols to allow consistent communication. Configure as follows: Redistribute EIGRP into OSPF using a route map to ensure only the internal routes are permitted Perform redistribution on R1 so that all RIP interfaces will be accessible to the EIGRP process Do not configure any static routes to accomplish this task Verify full reachability: o Ping all other devices in the network from each device o Successfully telnet to all devices in the network from each device router eigrp 1003 redistribute rip metric R3 access-list 3 permit access-list 3 permit route-map Redistribute-Selective permit 10 match ip address 3 router eigrp 1003 redistribute connected router ospf 1 log-adjacency-changes redistribute eigrp 1003 metric-type 1 subnets route-map Redistribute-Selective Verify full reachability:
30 o Ping all other devices in the network from each device o Successfully telnet to all devices in the network from each device R1 Routing Table During Steady State Operations R1#sh ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is to network /28 is subnetted, 3 subnets D [90/ ] via , 1d14h, Tunnel12 [90/ ] via , 1d14h, Tunnel13 C is directly connected, Tunnel12 C is directly connected, Tunnel /26 is subnetted, 1 subnets C is directly connected, FastEthernet0/ /8 is variably subnetted, 4 subnets, 2 masks D /32 [90/ ] via , 1d14h, Tunnel12 D EX /32 [170/ ] via , 13:36:14, Tunnel13 C /29 is directly connected, FastEthernet0/0.99 C /32 is directly connected, Loopback /26 is subnetted, 1 subnets D [90/ ] via , 1d14h, Tunnel /29 is subnetted, 1 subnets C is directly connected, FastEthernet0/ /29 is subnetted, 1 subnets D [90/ ] via , 1d14h, Tunnel /29 is subnetted, 1 subnets D EX [170/ ] via , 13:36:20, Tunnel /26 is subnetted, 1 subnets D EX [170/ ] via , 13:36:20, Tunnel13 S* /0 [1/0] via Network Address Translation Tasks All sites within the network utilize addressing from the RFC 1918 Private Addressing space, which are not valid on the Internet. In order to have full Internet connectivity, all internal addressing must be mapped to globally routable addressing space. In addition, an internal web server must also be accessible from the Internet
31 Configure Port Address Translation for All Internal Hosts ANSWERS: Configure Port Address Translation/Overloading on R1, R2, & R3 on the Internet Interface. **PAT or IP Address Overloading has several steps for successful configuration: 1. Create an access-list identifying the addresses to be translated 2. Identify the inside and outside interfaces (ip nat inside or outside) 3. Map the access-list to the outside interface using the ip nat inside source list statement** R1 access-list 1 permit access-list 1 permit access-list 1 permit access-list 1 permit access-list 1 permit access-list 1 deny any interface Loopback0 ip nat inside interface Tunnel12 ip nat inside interface Tunnel13 ip nat inside interface FastEthernet0/0.1 ip nat inside interface FastEthernet0/0.11 ip nat inside interface FastEthernet0/0.99 ip nat outside ip nat inside source list 1 interface FastEthernet0/0.99 overload R2 access-list 1 permit access-list 1 permit access-list 1 permit
32 access-list 1 permit access-list 1 permit access-list 1 deny any interface Loopback0 ip nat inside interface Tunnel12 ip nat inside interface Tunnel23 ip nat inside interface FastEthernet0/0.2 ip nat inside interface FastEthernet0/0.22 ip nat inside interface FastEthernet0/0.99 ip nat outside ip nat inside source list 1 interface FastEthernet0/0.99 overload R3 access-list 1 permit access-list 1 permit access-list 1 permit access-list 1 permit access-list 1 permit access-list 1 deny any interface Loopback0 ip nat inside interface Tunnel13 ip nat inside interface Tunnel23 ip nat inside interface FastEthernet0/0.3 ip nat inside interface FastEthernet0/0.33 ip nat inside
33 interface FastEthernet0/0.99 ip nat outside ip nat inside source list 1 interface FastEthernet0/0.99 overload Static Network Address Translation for an SMTP Mail Server on R2 ANSWERS: services were previously enabled on R2 and accessible from within the internal network, but need to be available on the Internet for monitoring and management purposes. Using static a NAT entry, point connections to R2 s Production VLAN address. **Static NAT configuration uses a variation of the ip nat inside statement but applies it to only a single service, including IP, TCP and UDP ** R2 ** Mapping the server uses a static NAT configuration as follows: ** ip nat inside source static tcp interface FastEthernet0/ Security Configuration Tasks Preventing unauthorized access to devices on the network may be supplied in part by the external ASA firewall, but additional measured need to be implemented to protect information assets Create and apply an access that will only allow internal devices to access the management VLAN on all devices at each site. The company s information security policy stipulates that no users outside of the company are permitted to access internal resources. To prevent unauthorized access, disallow all outside users from accessing the hosts within the protected network. ANSWERS: **An extended access-list must be created for the purpose of filtering network traffic. This filter is applied under interfaces using the ip access-group <number> command. **To prevent traffic, placing the access-list filter inbound at the Internet VLAN is the best location**
34 R1 access-list 101 permit ip access-list 101 permit ip access-list 101 permit ip host access-list 101 permit ip access-list 101 permit ip access-list 101 permit ip host access-list 101 deny ip any access-list 101 permit ip any any interface FastEthernet0/0.99 ip access-group 101 in R2 access-list 101 permit ip access-list 101 permit ip access-list 101 permit ip host access-list 101 permit ip access-list 101 permit ip access-list 101 permit ip host access-list 101 deny ip any access-list 101 permit ip any any interface FastEthernet0/0.99 ip access-group 101 in R3 access-list 101 permit ip access-list 101 permit ip access-list 101 permit ip host access-list 101 permit ip access-list 101 permit ip access-list 101 deny ip any access-list 101 permit ip host access-list 101 permit ip any any interface FastEthernet0/0.99 ip access-group 101 in Block SNMP outbound from all devices. SNMP protocols are a source of security concerns for the management team and they have elected not to permit it anywhere on the network. Configure the appropriate packet filters/access-lists to block all SNMP access to/from all sites.
35 ANSWERS: **Standard access-lists filter only by source address, while extended addresses can filter on source, destination, protocol, and TCP/UDP ports ** **Since the implicit deny-any is at the end of an access-list, allowing traffic is required or it will block all packets. Additionally, applying this outbound on the WAN links also makes the most sense ** R1 access-list 102 deny tcp any any eq smtp access-list 102 permit ip any any interface fa0/0.99 ip access-group 102 out R2 access-list 102 deny tcp any any eq smtp access-list 102 permit ip any any interface fa0/0.99 ip access-group 102 out R3 access-list 102 deny tcp any any eq smtp access-list 102 permit ip any any interface fa0/0.99 ip access-group 102 out Block TFTP Outbound from Site 2 Only TFTP is unencrypted and considered undesirable from a security standpoint. Since sensitive data is contained in servers at site 2, this protocol has been disallowed in order to prevent possible security compromises. Construct an access list to block any attempt at access from the Internet and GRE WAN interface. ANSWERS: **Standard access-lists filter only by source address, while extended addresses can filter on source, destination, protocol, and TCP/UDP ports ** **Since the implicit deny-any is at the end of an access-list, allowing traffic is required or it will block all packets. Additionally, applying this on the Internet VLAN
36 and GRE interfaces makes the most sense. These entries need to be in addition to those added previously on R2 ** R2 access-list 102 deny udp any any eq tftp access-list 102 deny tcp any any eq smtp access-list 102 permit ip any any interface fa0/0.99 ip access-group 102 out interface Tunnel12 ip access-group 102 out interface Tunnel23 ip access-group 102 out Block all external access trying to reach the management VLAN Remote access has been provided at the primary corporate location for the purpose of managing all internal network resources. Because of the sensitive nature of the data at the corporate locations, external access to the Management VLANs is not permitted by the security policy. Construct an access list to block any attempt at access from the Internet interface. ANSWERS: This was accomplished using the access-list configured previously
37 4. Final Configurations 4.1. R1 Configuration CONFIGURATION version 12.3 service timestamps debug datetime service timestamps log datetime no service password-encryption hostname R1 boot-start-marker boot system flash boot-end-marker enable secret 5 $1$g943$5FqWqnGK0Cj.ijZ79yNu4/ clock timezone PST -8 clock summer-time PDT date Mar :00 Nov :00 no aaa new-model ip subnet-zero no ip domain lookup ip cef no tag-switching ip propagate-ttl no tag-switching ip interface Loopback0
38 ip address ip nat inside interface Tunnel12 ip address ip access-group 102 out ip nat inside tunnel source tunnel destination interface Tunnel13 ip address ip access-group 102 out ip nat inside tunnel source tunnel destination interface FastEthernet0/0 no ip address duplex auto speed auto interface FastEthernet0/0.1 encapsulation isl 1 ip address no ip redirects ip nat inside no snmp trap link-status interface FastEthernet0/0.11 encapsulation isl 11 ip address no ip redirects ip nat inside no snmp trap link-status interface FastEthernet0/0.99 encapsulation isl 99 ip address ip access-group 101 in ip access-group 102 out no ip redirects ip nat outside no snmp trap link-status interface Serial0/0 no ip address encapsulation frame-relay
39 router eigrp 1003 redistribute rip metric network network no auto-summary router rip passive-interface FastEthernet0/0.99 network network network ip nat inside source list 1 interface FastEthernet0/0.99 overload ip http server ip http port 8080 ip classless ip route no logging trap access-list 1 permit access-list 1 permit access-list 1 permit access-list 1 permit access-list 1 permit access-list 1 deny any access-list 101 deny tcp any any eq telnet access-list 101 permit tcp any any eq 22 access-list 101 permit ip access-list 101 permit ip access-list 101 permit ip host access-list 101 permit ip access-list 101 permit ip access-list 101 permit ip host access-list 101 deny ip any access-list 101 permit ip any any access-list 102 deny tcp any any eq smtp access-list 102 permit ip any any dial-peer cor custom banner motd ^CWelcome to the CCNA VPN Lab^C
40 line con 0 privilege level 15 password Cisco123 line aux 0 password Cisco123 login modem InOut transport input all flowcontrol hardware line vty 0 4 password Cisco123 login line vty password Cisco123 login ntp clock-period ntp server end IP ROUTING TABLE R1#sh ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is to network /28 is subnetted, 3 subnets D [90/ ] via , 2d20h, Tunnel12 [90/ ] via , 2d20h, Tunnel13 C is directly connected, Tunnel12 C is directly connected, Tunnel /26 is subnetted, 1 subnets C is directly connected, FastEthernet0/ /8 is variably subnetted, 4 subnets, 2 masks D /32 [90/ ] via , 2d20h, Tunnel12 D EX /32 [170/ ] via , 1d18h, Tunnel13 C /29 is directly connected, FastEthernet0/0.99 C /32 is directly connected, Loopback0
41 /26 is subnetted, 1 subnets D [90/ ] via , 2d20h, Tunnel /29 is subnetted, 1 subnets C is directly connected, FastEthernet0/ /29 is subnetted, 1 subnets D [90/ ] via , 2d20h, Tunnel /29 is subnetted, 1 subnets D EX [170/ ] via , 1d18h, Tunnel /26 is subnetted, 1 subnets D EX [170/ ] via , 1d18h, Tunnel13 S* /0 [1/0] via EIGRP R1#sh ip eigrp neighbors IP-EIGRP neighbors for process 1003 H Address Interface Hold Uptime SRTT RTO Q Seq (sec) (ms) Cnt Num Tu13 132d20h Tu12 132d20h R1#sh ip eigrp inter IP-EIGRP interfaces for process 1003 Xmit Queue Mean Pacing Time Multicast Pending Interface Peers Un/Reliable SRTT Un/Reliable Flow Timer Routes Tu12 1 0/ / Tu13 1 0/ / R1#sh ip eigrp topology IP-EIGRP Topology Table for AS(1003)/ID( ) Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply, r - reply Status, s - sia Status P /32, 1 successors, FD is via ( /128256), Tunnel12 P /32, 1 successors, FD is via ( /128256), Tunnel13 P /29, 1 successors, FD is via Redistributed ( /0) via ( /28160), Tunnel13 P /32, 1 successors, FD is via Redistributed ( /0) P /26, 1 successors, FD is via ( /28160), Tunnel13 P /26, 1 successors, FD is via Redistributed ( /0)
42 P /29, 1 successors, FD is via Redistributed ( /0) P /29, 1 successors, FD is via ( /28160), Tunnel12 P /29, 1 successors, FD is Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply, r - reply Status, s - sia Status via ( /28160), Tunnel13 P /26, 1 successors, FD is via ( /28160), Tunnel12 P /28, 2 successors, FD is via ( / ), Tunnel13 via ( / ), Tunnel12 P /28, 1 successors, FD is via Connected, Tunnel12 P /28, 1 successors, FD is via Connected, Tunnel13 R1#sh ip protocols Routing Protocol is "eigrp 1003" Outgoing update filter list for all interfaces is not set Incoming update filter list for all interfaces is not set Default networks flagged in outgoing updates Default networks accepted from incoming updates EIGRP metric weight K1=1, K2=0, K3=1, K4=0, K5=0 EIGRP maximum hopcount 100 EIGRP maximum metric variance 1 Redistributing: eigrp 1003, rip EIGRP NSF-aware route hold timer is 240s Automatic network summarization is not in effect Maximum path: 4 Routing for Networks: / /28 Routing Information Sources: Gateway Distance Last Update d08h d08h Distance: internal 90 external 170 Routing Protocol is "rip" Sending updates every 30 seconds, next due in 25 seconds Invalid after 180 seconds, hold down 180, flushed after 240 Outgoing update filter list for all interfaces is not set Incoming update filter list for all interfaces is not set Redistributing: rip
43 Default version control: send version 1, receive any version Interface Send Recv Triggered RIP Key-chain FastEthernet0/ FastEthernet0/ Loopback Automatic network summarization is in effect Maximum path: 4 Routing for Networks: Passive Interface(s): FastEthernet0/0.99 Routing Information Sources: Gateway Distance Last Update Distance: (default is 120) 4.2. R2 Configuration CONFIGURATION version 12.3 service timestamps debug datetime msec service timestamps log datetime no service password-encryption hostname R2 boot-start-marker boot-end-marker enable secret 5 $1$8STC$Sjhm3NtDASbFhCnGnTD2g. clock timezone PST -8 clock summer-time PDT date Mar :00 Nov :00 no aaa new-model ip subnet-zero no ip domain lookup ip cef no tag-switching ip
Seattle Cisco Users Group
 Seattle Cisco Users Group CCNA Lab Project Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP December 18, 2010 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Seattle Cisco Users Group CCNA Lab Project Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP December 18, 2010 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Lab- Troubleshooting Basic EIGRP for 1Pv4
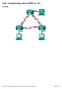 Lab- Troubleshooting Basic EIGRP for 1Pv4 Topology G0/0 G0/0 PC-A PC-C 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 27 Addressing Table efault Gateway
Lab- Troubleshooting Basic EIGRP for 1Pv4 Topology G0/0 G0/0 PC-A PC-C 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 27 Addressing Table efault Gateway
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab 8.5.2: Troubleshooting Enterprise Networks 2
 Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
Lab Configuring Per-Interface Inter-VLAN Routing (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Lab Configuring Basic RIPv2 (Solution)
 (Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
(Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
CIS 83 LAB 3 - EIGRP Rich Simms September 23, Objective. Scenario. Topology
 CIS 83 LAB 3 - EIGRP Rich Simms September 23, 2006 Objective The objective of this lab is to become familiar setting up and configuring EIGRP on three routers. EIGRP is a Cisco proprietary distance-vector
CIS 83 LAB 3 - EIGRP Rich Simms September 23, 2006 Objective The objective of this lab is to become familiar setting up and configuring EIGRP on three routers. EIGRP is a Cisco proprietary distance-vector
The primary audience for this course includes Network Administrators, Network Engineers,
 CCNA COURSE DESCRIPTION: Cisco Certified Network Associate (CCNA) validates the ability to install, configure, operate, and troubleshoot medium-size route and switched networks, including implementation
CCNA COURSE DESCRIPTION: Cisco Certified Network Associate (CCNA) validates the ability to install, configure, operate, and troubleshoot medium-size route and switched networks, including implementation
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only.
 Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
RR> RR> RR>en RR# RR# RR# RR# *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 RR#
 RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
Lab b Simple DMZ Extended Access Lists Instructor Version 2500
 Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
GoCertify Advanced Cisco CCIE Lab Scenario # 1
 GoCertify Advanced Cisco CCIE Lab Scenario # 1 (http://www.gocertify.com) IPexpert, Inc. is a leading provider in on-line Cisco CCNA, CCNP and CCIE training material. For more information please visit
GoCertify Advanced Cisco CCIE Lab Scenario # 1 (http://www.gocertify.com) IPexpert, Inc. is a leading provider in on-line Cisco CCNA, CCNP and CCIE training material. For more information please visit
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF
 Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
LAB1: EIGRP IPv4. EIGRP: Initial Config. Disclaimer
 Page1 AB1: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB1: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Skills Assessment Student Training Exam
 Skills Assessment Student Training Exam Topology Assessment Objectives Part 1: Initialize Devices (2 points, 5 minutes) Part 2: Configure Device Basic Settings (18 points, 20 minutes) Part 3: Configure
Skills Assessment Student Training Exam Topology Assessment Objectives Part 1: Initialize Devices (2 points, 5 minutes) Part 2: Configure Device Basic Settings (18 points, 20 minutes) Part 3: Configure
Implementing EIGRP. Global Knowledge Training LLC L7-1
 L7 Implementing EIGRP Global Knowledge Training LLC L7-1 Objectives In this lab you will configure EIGRP on your pod routers. The core router is already configured for EIGRP. You will first remove the
L7 Implementing EIGRP Global Knowledge Training LLC L7-1 Objectives In this lab you will configure EIGRP on your pod routers. The core router is already configured for EIGRP. You will first remove the
Lab Configuring IPv4 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
(Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
QUESTION/SOLUTION SET LAB 4
 QUESTION/SOLUTION SET LAB 4 CCIE lab Routing & Switching (v4.0) lab:4 Updated Testing Guidelines 1. The equipment on the rack assigned to you is physically Cabled and should not be tempered with. 2. Router
QUESTION/SOLUTION SET LAB 4 CCIE lab Routing & Switching (v4.0) lab:4 Updated Testing Guidelines 1. The equipment on the rack assigned to you is physically Cabled and should not be tempered with. 2. Router
TestOut Routing and Switching Pro - English 6.0.x COURSE OUTLINE. Modified
 TestOut Routing and Switching Pro - English 6.0.x COURSE OUTLINE Modified 2017-07-10 TestOut Routing and Switching Pro Outline- English 6.0.x Videos: 133 (15:42:34) Demonstrations: 78 (7:22:19) Simulations:
TestOut Routing and Switching Pro - English 6.0.x COURSE OUTLINE Modified 2017-07-10 TestOut Routing and Switching Pro Outline- English 6.0.x Videos: 133 (15:42:34) Demonstrations: 78 (7:22:19) Simulations:
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Skills Assessment Student Training
 Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
Interconnecting Cisco Networking Devices Part 1 (ICND1) Course Overview
 Interconnecting Cisco Networking Devices Part 1 (ICND1) Course Overview This course will teach students about building a simple network, establishing internet connectivity, managing network device security,
Interconnecting Cisco Networking Devices Part 1 (ICND1) Course Overview This course will teach students about building a simple network, establishing internet connectivity, managing network device security,
Configuring Dynamic Multipoint VPN Using GRE Over IPsec With OSPF, NAT, and Cisco IOS Firewall
 Configuring Dynamic Multipoint VPN Using GRE Over IPsec With OSPF, NAT, and Cisco IOS Firewall Document ID: 43068 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Configuring Dynamic Multipoint VPN Using GRE Over IPsec With OSPF, NAT, and Cisco IOS Firewall Document ID: 43068 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Interconnecting Cisco Networking Devices Part 1 ICND1
 Interconnecting Cisco Networking Devices Part 1 ICND1 Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco Networking Devices, Part 1 (ICND1) v3.0
Interconnecting Cisco Networking Devices Part 1 ICND1 Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco Networking Devices, Part 1 (ICND1) v3.0
Configuration and Management of Networks
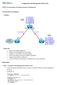 EIGRP Summarization and efault Network Advertisement The lab is built on the topology: Topology Objectives Review a basic EIGRP configuration. onfigure and verify EIGRP auto-summarization. onfigure and
EIGRP Summarization and efault Network Advertisement The lab is built on the topology: Topology Objectives Review a basic EIGRP configuration. onfigure and verify EIGRP auto-summarization. onfigure and
LAB2: Named EIGRP IPv4
 Page1 AB2: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB2: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring IGRP Instructor Version 2500
 Lab 7.3.5 Configuring IGRP Instructor Version 2500 Objective Setup IP an addressing scheme using class C networks. Configure IGRP on routers. Background/Preparation Cable a network similar to the one in
Lab 7.3.5 Configuring IGRP Instructor Version 2500 Objective Setup IP an addressing scheme using class C networks. Configure IGRP on routers. Background/Preparation Cable a network similar to the one in
Lab Student Lab Orientation
 Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
exam. Number: Passing Score: 800 Time Limit: 120 min CISCO Interconnecting Cisco Networking Devices Part 1 (ICND)
 100-105.exam Number: 100-105 Passing Score: 800 Time Limit: 120 min CISCO 100-105 Interconnecting Cisco Networking Devices Part 1 (ICND) Exam A QUESTION 1 Which route source code represents the routing
100-105.exam Number: 100-105 Passing Score: 800 Time Limit: 120 min CISCO 100-105 Interconnecting Cisco Networking Devices Part 1 (ICND) Exam A QUESTION 1 Which route source code represents the routing
Lab Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500
 Lab 9.3.5 Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500 Objective Use the show ip route and show ip protocol commands to diagnose a routing configuration
Lab 9.3.5 Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500 Objective Use the show ip route and show ip protocol commands to diagnose a routing configuration
Configuring Network Access to the GGSN
 CHAPTER 7 This chapter describes how to configure access from the gateway GPRS support node (GGSN) to a serving GPRS support node (SGSN), public data network (PDN), and optionally to a Virtual Private
CHAPTER 7 This chapter describes how to configure access from the gateway GPRS support node (GGSN) to a serving GPRS support node (SGSN), public data network (PDN), and optionally to a Virtual Private
ICND1 v2.0 Interconnecting Cisco Networking Devices Part 1 CCENT & Part of CCNA Rout/Switch
 ICND1 v2.0 Interconnecting Cisco Networking Devices Part 1 CCENT & Part of CCNA Rout/Switch Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco
ICND1 v2.0 Interconnecting Cisco Networking Devices Part 1 CCENT & Part of CCNA Rout/Switch Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco
Sample Business Ready Branch Configuration Listings
 APPENDIX A Sample Business Ready Branch Configuration Listings The following is a sample configuration of a Business Ready Branch. There are many permutations of feature combinations when setting up the
APPENDIX A Sample Business Ready Branch Configuration Listings The following is a sample configuration of a Business Ready Branch. There are many permutations of feature combinations when setting up the
Lab Configuring Dynamic and Static NAT (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
Cisco CCNA (ICND1, ICND2) Bootcamp
 Cisco CCNA (ICND1, ICND2) Bootcamp Course Duration: 5 Days Course Overview This five-day course covers the essential topics of ICND1 and ICND2 in an intensive Bootcamp format. It teaches students the skills
Cisco CCNA (ICND1, ICND2) Bootcamp Course Duration: 5 Days Course Overview This five-day course covers the essential topics of ICND1 and ICND2 in an intensive Bootcamp format. It teaches students the skills
CCNA. Course Catalog
 CCNA Course Catalog 2012-2013 This course is intended for the following audience: Network Administrator Network Engineer Systems Engineer CCNA Exam Candidates Cisco Certified Network Associate (CCNA 640-802)
CCNA Course Catalog 2012-2013 This course is intended for the following audience: Network Administrator Network Engineer Systems Engineer CCNA Exam Candidates Cisco Certified Network Associate (CCNA 640-802)
Lab Configuring Advanced EIGRP for IPv4 Features Topology
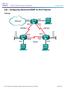 Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0 192.168.1.1 255.255.255.0
Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0 192.168.1.1 255.255.255.0
Lab Configuring Dynamic and Static NAT (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Cisco Press CCIE Practical Studies CCIE Practice Lab: Enchilada Solutions
 Cisco Press CCIE Practical Studies CCIE Practice Lab: Solutions Cisco Press CCIE Practical Studies CCIE Practice Lab: LAB Book Chapter Book Page The 18 1161 Overview... 3 Technical Details... 3 Table 54-1:
Cisco Press CCIE Practical Studies CCIE Practice Lab: Solutions Cisco Press CCIE Practical Studies CCIE Practice Lab: LAB Book Chapter Book Page The 18 1161 Overview... 3 Technical Details... 3 Table 54-1:
COPYRIGHTED MATERIAL. Table of Contents. Assessment Test
 10089.book Page xi Monday, July 23, 2007 3:17 PM Introduction Assessment Test xxiii xxxiii Chapter 1 Internetworking 1 Internetworking Basics 4 Internetworking Models 11 The Layered Approach 12 Advantages
10089.book Page xi Monday, July 23, 2007 3:17 PM Introduction Assessment Test xxiii xxxiii Chapter 1 Internetworking 1 Internetworking Basics 4 Internetworking Models 11 The Layered Approach 12 Advantages
Interconnecting Cisco Networking Devices Part 1 ( )
 Interconnecting Cisco Networking Devices Part 1 (100-101) Exam Description: The 100-101 Interconnecting Cisco Networking Devices Part 1 (ICND1) is a 1.5- hour exam with 50 60 questions. The 100-101 Interconnecting
Interconnecting Cisco Networking Devices Part 1 (100-101) Exam Description: The 100-101 Interconnecting Cisco Networking Devices Part 1 (ICND1) is a 1.5- hour exam with 50 60 questions. The 100-101 Interconnecting
RealCiscoLAB.com. Chapter 2 Lab 2-2, EIGRP Load Balancing. Topology. Objectives. Background. CCNPv6 ROUTE
 RealCiscoLAB.com CCNPv6 ROUTE Chapter 2 Lab 2-2, EIGRP Load Balancing Topology Objectives Background Review a basic EIGRP configuration. Explore the EIGRP topology table. Identify successors, feasible
RealCiscoLAB.com CCNPv6 ROUTE Chapter 2 Lab 2-2, EIGRP Load Balancing Topology Objectives Background Review a basic EIGRP configuration. Explore the EIGRP topology table. Identify successors, feasible
Lab VTY Restriction Instructor Version 2500
 Lab 11.2.6 VTY Restriction Instructor Version 2500 NOTE: The loopback entry in this graphic is not required in the lab. Objective Scenario Use the access-class and line commands to control Telnet access
Lab 11.2.6 VTY Restriction Instructor Version 2500 NOTE: The loopback entry in this graphic is not required in the lab. Objective Scenario Use the access-class and line commands to control Telnet access
Lab Troubleshooting Routing Issues with debug Instructor Version 2500
 Lab 9.3.7 Troubleshooting Routing Issues with debug Instructor Version 2500 Objective Utilize a systematic OSI troubleshooting process to diagnose routing problems. Use various show commands to gather
Lab 9.3.7 Troubleshooting Routing Issues with debug Instructor Version 2500 Objective Utilize a systematic OSI troubleshooting process to diagnose routing problems. Use various show commands to gather
Chapter 2 Lab 2-1, EIGRP Configuration, Bandwidth, and Adjacencies
 Chapter 2 Lab 2-1, EIGRP Configuration, Bandwidth, and Adjacencies Topology Objectives Background Configure EIGRP on multiple routers. Configure the bandwidth command to modify the EIGRP metric. Verify
Chapter 2 Lab 2-1, EIGRP Configuration, Bandwidth, and Adjacencies Topology Objectives Background Configure EIGRP on multiple routers. Configure the bandwidth command to modify the EIGRP metric. Verify
Scenario Labs NETSIM FOR CCNA LAB MANUAL. Scenario Labs. Boson NetSim for CCNA Lab Manual
 NETSIM FOR CCNA LAB MANUAL Welcome to the NetSim. The goal of these labs is to introduce you to the limited number of commands needed to enable a technology, without addressing extra commands that could
NETSIM FOR CCNA LAB MANUAL Welcome to the NetSim. The goal of these labs is to introduce you to the limited number of commands needed to enable a technology, without addressing extra commands that could
Interconnecting Cisco Network Devices Part 1 v2.0 (ICND 1)
 Interconnecting Cisco Network Devices Part 1 v2.0 (ICND 1) COURSE OVERVIEW: Interconnecting Cisco Networking Devices, Part 1 (ICND1) v2.0 is a five-day, instructor-led training course that teaches learners
Interconnecting Cisco Network Devices Part 1 v2.0 (ICND 1) COURSE OVERVIEW: Interconnecting Cisco Networking Devices, Part 1 (ICND1) v2.0 is a five-day, instructor-led training course that teaches learners
Advanced IPv6 Training Course. Lab Manual. v1.3 Page 1
 Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
CONFIGURATION DU SWITCH
 Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
Actual4Test. Actual4test - actual test exam dumps-pass for IT exams
 Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 200-125 Title : CCNA Cisco Certified Network Associate CCNA (v3.0) Vendor : Cisco Version : DEMO Get
Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 200-125 Title : CCNA Cisco Certified Network Associate CCNA (v3.0) Vendor : Cisco Version : DEMO Get
ICND1. Switch Configuration Lab. All configurations have been set to factory defaults for these labs
 ICND1 Switch Configuration Lab TOPOLOGY 3xPC (hosts) 2x2950 (Layer 2 Switches) 1x3560 (Layer 3 Switch) 5x2811 (Routers, unused in this set of labs) All configurations have been set to factory defaults
ICND1 Switch Configuration Lab TOPOLOGY 3xPC (hosts) 2x2950 (Layer 2 Switches) 1x3560 (Layer 3 Switch) 5x2811 (Routers, unused in this set of labs) All configurations have been set to factory defaults
Payload Types At Different OSI Layers: Layer 2 - Frame Layer 3 - Packet Layer 4 - Datagram
 Payload Types At Different OSI Layers: Layer 2 - Frame Layer 3 - Packet Layer 4 - Datagram Default Cisco Terminal Options: 9600 bits/second No hardware flow control 8-bit ASCII No parity 1 stop bit Setting
Payload Types At Different OSI Layers: Layer 2 - Frame Layer 3 - Packet Layer 4 - Datagram Default Cisco Terminal Options: 9600 bits/second No hardware flow control 8-bit ASCII No parity 1 stop bit Setting
CCNA Boot Camp. Course Description
 CCNA Boot Camp Course Description CCNA Boot Camp combines both the Interconnecting Cisco Network Devices Part 1 (ICND1) course and the Interconnecting Cisco Network Devices Part 2 (ICND2) course into one
CCNA Boot Camp Course Description CCNA Boot Camp combines both the Interconnecting Cisco Network Devices Part 1 (ICND1) course and the Interconnecting Cisco Network Devices Part 2 (ICND2) course into one
CCNP TSHOOT. Quick Reference Sheet Exam
 CCNP TSHOOT Quick Reference Sheet Exam 300-135 Chapter 1. Network Principles Troubleshooting Steps Problem Identification Collection of Information Examination and Action Plan Verification Basic Troubleshooting
CCNP TSHOOT Quick Reference Sheet Exam 300-135 Chapter 1. Network Principles Troubleshooting Steps Problem Identification Collection of Information Examination and Action Plan Verification Basic Troubleshooting
Deployment of Cisco IP Mobility Solution on Enterprise Class Teleworker Network
 Deployment Guide Deployment of Cisco IP Mobility Solution on Enterprise Class Teleworker Network The Cisco Service Oriented Network Architecture (SONA) framework helps enterprise customers evolve their
Deployment Guide Deployment of Cisco IP Mobility Solution on Enterprise Class Teleworker Network The Cisco Service Oriented Network Architecture (SONA) framework helps enterprise customers evolve their
UniNets CCNA Security LAB MANUAL UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL UniNets CCNA LAB MANUAL
 UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL Contents: UniNets CCNA Security LAB MANUAL Section 1 Securing Layer 2 Lab 1-1 Configuring Native VLAN on a Trunk Links Lab 1-2 Disabling
UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL Contents: UniNets CCNA Security LAB MANUAL Section 1 Securing Layer 2 Lab 1-1 Configuring Native VLAN on a Trunk Links Lab 1-2 Disabling
Ch. 5 Maintaining and Troubleshooting Routing Solutions. Net412- Network troubleshooting
 Ch. 5 Maintaining and Troubleshooting Routing Solutions Net412- Network troubleshooting Troubleshooting Routing Network Layer Connectivity EIGRP OSPF 2 Network Connectivity Just like we did when we looked
Ch. 5 Maintaining and Troubleshooting Routing Solutions Net412- Network troubleshooting Troubleshooting Routing Network Layer Connectivity EIGRP OSPF 2 Network Connectivity Just like we did when we looked
Course: CCNA Bootcamp (Intensive CCNA)
 Course: CCNA Bootcamp (Intensive CCNA) Duration: 5 Days Description Introduction to Networking course will prepare you for the basic knowledge and in-depth technology of networking design and implementation.
Course: CCNA Bootcamp (Intensive CCNA) Duration: 5 Days Description Introduction to Networking course will prepare you for the basic knowledge and in-depth technology of networking design and implementation.
Cisco Cookbook. Kevin Dooley and IanJ. Brown. O'REILLY 4 Beijing Cambridge Farnham Koln Paris Sebastopol Taipei Tokyo
 Cisco Cookbook Kevin Dooley and IanJ. Brown O'REILLY 4 Beijing Cambridge Farnham Koln Paris Sebastopol Taipei Tokyo Table of Contents Preface xv 1. Router Configuration and File Management 1 1.1 Configuring
Cisco Cookbook Kevin Dooley and IanJ. Brown O'REILLY 4 Beijing Cambridge Farnham Koln Paris Sebastopol Taipei Tokyo Table of Contents Preface xv 1. Router Configuration and File Management 1 1.1 Configuring
Introduction. Lab Diagram
 Introduction The onfiguring EIGRP module provides you with the instructions and isco hardware to develop your hands on skills in EIGRP, including authentication and receiving routes over a wide area network.
Introduction The onfiguring EIGRP module provides you with the instructions and isco hardware to develop your hands on skills in EIGRP, including authentication and receiving routes over a wide area network.
CCNA Security 1.0 Student Packet Tracer Manual
 1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
L2TP IPsec Support for NAT and PAT Windows Clients
 L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
Lab 1-2Connecting to a Cisco Router or Switch via Console. Lab 1-6Basic Graphic Network Simulator v3 Configuration
 MODULE1 GETTING STARTED WITH YOUR CISCO LAB Lab 1-1Identifying Router Components and Accessories Lab 1-2Connecting to a Cisco Router or Switch via Console Lab 1-3Identifying Router & Switch IOS Software
MODULE1 GETTING STARTED WITH YOUR CISCO LAB Lab 1-1Identifying Router Components and Accessories Lab 1-2Connecting to a Cisco Router or Switch via Console Lab 1-3Identifying Router & Switch IOS Software
Table of Contents. Cisco IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example
 Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
Implementing Cisco IP Routing
 300-101 Implementing Cisco IP Routing NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 300-101 Exam on Implementing Cisco IP Routing...
300-101 Implementing Cisco IP Routing NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 300-101 Exam on Implementing Cisco IP Routing...
Cisco Certified Network Associate ( )
 Cisco Certified Network Associate (200-125) Exam Description: The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment that
Cisco Certified Network Associate (200-125) Exam Description: The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment that
DOiT-200v6 VOLUME II. DOiT-200v6 Lab 3 Multi-Topic CCIE-Level Scenario. For CCIE Candidates
 Revision 7.0 (10/20/2005) DOiT-200v6-SCENARIO 3 Page 1 NETMASTERCLASS ROUTING AND SWITCHING CCIE TRACK DOiT-200v6 VOLUME II DOiT-200v6 Lab 3 Multi-Topic CCIE-Level Scenario For CCIE Candidates Revision
Revision 7.0 (10/20/2005) DOiT-200v6-SCENARIO 3 Page 1 NETMASTERCLASS ROUTING AND SWITCHING CCIE TRACK DOiT-200v6 VOLUME II DOiT-200v6 Lab 3 Multi-Topic CCIE-Level Scenario For CCIE Candidates Revision
Connections, addressing and common configuration rules.
 Lab #1 r9-1 s2 e1 3/11 VLAN_21 BGP AS 100 s1 3/1 e0 s0 e0 3/2 s1 VLAN_22 BGP AS 200 r1 r2 Ring 4 r4 s0/1 r3 to0/0 s0/0 s0 s1 OSPF Area 33 to0 e0/0 e0 OSPF Area 4 3/4 b0/0 3/3 VLAN_14 VLAN_13 403 304 c15
Lab #1 r9-1 s2 e1 3/11 VLAN_21 BGP AS 100 s1 3/1 e0 s0 e0 3/2 s1 VLAN_22 BGP AS 200 r1 r2 Ring 4 r4 s0/1 r3 to0/0 s0/0 s0 s1 OSPF Area 33 to0 e0/0 e0 OSPF Area 4 3/4 b0/0 3/3 VLAN_14 VLAN_13 403 304 c15
"Charting the Course... Interconnecting Cisco Networking Devices Accelerated 3.0 (CCNAX) Course Summary
 Description Course Summary The Cisco CCNA curriculum includes a third course, Interconnecting Cisco Networking Devices: Accelerated (CCNAX), consisting of Interconnecting Cisco Networking Devices, Part
Description Course Summary The Cisco CCNA curriculum includes a third course, Interconnecting Cisco Networking Devices: Accelerated (CCNAX), consisting of Interconnecting Cisco Networking Devices, Part
Introduction. Lab Diagram
 Introduction The Troubleshooting routing protocols module provides you with the instructions and isco hardware to develop your hands on skills in troubleshooting routing protocols, specifically EIGRP.
Introduction The Troubleshooting routing protocols module provides you with the instructions and isco hardware to develop your hands on skills in troubleshooting routing protocols, specifically EIGRP.
CCNA Routing and Switching (NI )
 CCNA Routing and Switching (NI400+401) 150 Hours ` Outline The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment that is
CCNA Routing and Switching (NI400+401) 150 Hours ` Outline The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment that is
RealCiscoLAB.com. Inter-VLAN Routing with an Internal Route Processor and Monitoring CEF Functions
 RealCiscoLAB.com CCNPv6 SWITCH Inter-VLAN Routing with an Internal Route Processor and Monitoring CEF Functions Topology Objective Background Route between VLANs using a 3560 switch with an internal route
RealCiscoLAB.com CCNPv6 SWITCH Inter-VLAN Routing with an Internal Route Processor and Monitoring CEF Functions Topology Objective Background Route between VLANs using a 3560 switch with an internal route
Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
ASA 9.x EIGRP Configuration Example
 ASA 9.x EIGRP Configuration Example Contents Introduction Prerequisites Requirements Components Used Background Information Guidelines and Limitations EIGRP and Failover Configure Network Diagram ASDM
ASA 9.x EIGRP Configuration Example Contents Introduction Prerequisites Requirements Components Used Background Information Guidelines and Limitations EIGRP and Failover Configure Network Diagram ASDM
This document is a tutorial related to the Router Emulator which is available at:
 Introduction This document is a tutorial related to the Router Emulator which is available at: http://www.dcs.napier.ac.uk/~bill/router.html A demo is also available at: http://www.dcs.napier.ac.uk/~bill/router_demo.htm
Introduction This document is a tutorial related to the Router Emulator which is available at: http://www.dcs.napier.ac.uk/~bill/router.html A demo is also available at: http://www.dcs.napier.ac.uk/~bill/router_demo.htm
Skills Assessment. CCNA Routing and Switching: Connecting Networks. Topology. Assessment Objectives. Scenario
 Skills Assessment Topology Assessment Objectives Part 1: Configure Device Basic Settings (15 points, 15 minutes) Part 2: Configure PPP Connections (20 points, 10 minutes) Part 3: Configure IPv4 ACL for
Skills Assessment Topology Assessment Objectives Part 1: Configure Device Basic Settings (15 points, 15 minutes) Part 2: Configure PPP Connections (20 points, 10 minutes) Part 3: Configure IPv4 ACL for
EIGRP Lab / lo1. .1 lo / /30
 EIGRP Lab 172,16,1.0/24.1 lo1 192.168.20.0/30.2.1 Merida fa0 fa0 Vargas lo2.1 lo2.5.1 lo1 192.168.30.0/24 172.16.2.0/24 192.168.20.4.0/30 Scenario: Loopback0 is used for RouterID Loopback1 is a virtual
EIGRP Lab 172,16,1.0/24.1 lo1 192.168.20.0/30.2.1 Merida fa0 fa0 Vargas lo2.1 lo2.5.1 lo1 192.168.30.0/24 172.16.2.0/24 192.168.20.4.0/30 Scenario: Loopback0 is used for RouterID Loopback1 is a virtual
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
 Seite von 7 05.0.200 Close Window Assessment System Exam Viewer - CCNA Practice Certification Exam # - (Version 4.0) Below you will find the assessment items as presented on the exam as well as the scoring
Seite von 7 05.0.200 Close Window Assessment System Exam Viewer - CCNA Practice Certification Exam # - (Version 4.0) Below you will find the assessment items as presented on the exam as well as the scoring
CCNA. The knowledge and skills that a learner must have before attending this course are as follows:
 CCNA SRM CCNAX v2.0 CCNA Routing & Switching course is the ultimate training program for engineers pursuing the Cisco Certified Network Associate (CCNA) certification. Cisco has announced an extensive
CCNA SRM CCNAX v2.0 CCNA Routing & Switching course is the ultimate training program for engineers pursuing the Cisco Certified Network Associate (CCNA) certification. Cisco has announced an extensive
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem
 How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
Chapter 4 Lab 4-1, Redistribution Between RIP and OSPF
 hapter 4 Lab 4-1, Redistribution Between RIP and OSPF Topology Objectives Review configuration and verification of RIP and OSPF. onfigure passive interfaces in both RIP and OSPF. Filter routing updates
hapter 4 Lab 4-1, Redistribution Between RIP and OSPF Topology Objectives Review configuration and verification of RIP and OSPF. onfigure passive interfaces in both RIP and OSPF. Filter routing updates
CCNA 4 - Final Exam (B)
 CCNA 4 - Final Exam (B) 1. Identify the factors that contribute to congestion on an Ethernet LAN. (Choose three.) improper placement of enterprise level servers addition of hosts to a physical segment
CCNA 4 - Final Exam (B) 1. Identify the factors that contribute to congestion on an Ethernet LAN. (Choose three.) improper placement of enterprise level servers addition of hosts to a physical segment
Interconnecting Cisco Networking Devices Part 2
 ICND2 Interconnecting Cisco Networking Devices Part 2 Volume 2 Version 1.0 Student Guide Editorial, Production, and Web Services (EPWS): 07.25.07 DISCLAIMER WARRANTY: THIS CONTENT IS BEING PROVIDED AS
ICND2 Interconnecting Cisco Networking Devices Part 2 Volume 2 Version 1.0 Student Guide Editorial, Production, and Web Services (EPWS): 07.25.07 DISCLAIMER WARRANTY: THIS CONTENT IS BEING PROVIDED AS
Lab 3.2 Configuring a Basic GRE Tunnel
 Lab 3.2 onfiguring a Basic GRE Tunnel Learning Objectives onfigure a GRE tunnel onfigure EIGRP on a router onfigure and test routing over the tunnel interfaces Topology iagram Scenario This lab is designed
Lab 3.2 onfiguring a Basic GRE Tunnel Learning Objectives onfigure a GRE tunnel onfigure EIGRP on a router onfigure and test routing over the tunnel interfaces Topology iagram Scenario This lab is designed
CCNA. Murlisona App. Hiralal Lane, Ravivar Karanja, Near Pethe High-School, ,
 CCNA Cisco Certified Network Associate (200-125) Exam DescrIPtion: The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment
CCNA Cisco Certified Network Associate (200-125) Exam DescrIPtion: The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment
CISCO QUAD Cisco CCENT/CCNA/CCDA/CCNA Security (QUAD)
 Our Learning Exclusive Custom exam prep software and materials Exam delivery in classroom with 98% success Course specific thinqtank Learning publications to promote fun exciting learning Extended hours
Our Learning Exclusive Custom exam prep software and materials Exam delivery in classroom with 98% success Course specific thinqtank Learning publications to promote fun exciting learning Extended hours
DOiT-200v6 VOLUME II I2 R2 4 N1. DOiT-200v6 Lab 16 Multi-Topic CCIE-Level Scenario. For CCIE Candidates
 Revision 7.0 (10/26/2005) DOiT-200v6-SCENARIO 16 Page 1 NETMASTERCLASS ROUTING AND SWITCHING CCIE TRACK DOiT-200v6 VOLUME II 4 I2 R2 3 3 R5 I5 3 3 R6 R1 4 N1 4 4 2 2 1 4 I3 R3 3 1 R4 3 N2 N1 I4 1 R7 DOiT-200v6
Revision 7.0 (10/26/2005) DOiT-200v6-SCENARIO 16 Page 1 NETMASTERCLASS ROUTING AND SWITCHING CCIE TRACK DOiT-200v6 VOLUME II 4 I2 R2 3 3 R5 I5 3 3 R6 R1 4 N1 4 4 2 2 1 4 I3 R3 3 1 R4 3 N2 N1 I4 1 R7 DOiT-200v6
CISCO EXAM QUESTIONS & ANSWERS
 CISCO 100-101 EXAM QUESTIONS & ANSWERS Number: 100-101 Passing Score: 800 Time Limit: 120 min File Version: 35.5 http://www.gratisexam.com/ CISCO 100-101 EXAM QUESTIONS & ANSWERS Exam Name: CCNA Interconnecting
CISCO 100-101 EXAM QUESTIONS & ANSWERS Number: 100-101 Passing Score: 800 Time Limit: 120 min File Version: 35.5 http://www.gratisexam.com/ CISCO 100-101 EXAM QUESTIONS & ANSWERS Exam Name: CCNA Interconnecting
Chapter 6 Lab 6-4, BGP Route Reflectors and Route Filters
 Chapter 6 Lab 6-4, BGP Route Reflectors and Route Filters Topology Objectives Background Configure IBGP routers to use a route reflector and a simple route filter. The International Travel Agency maintains
Chapter 6 Lab 6-4, BGP Route Reflectors and Route Filters Topology Objectives Background Configure IBGP routers to use a route reflector and a simple route filter. The International Travel Agency maintains
CCENT Practice Certification Exam # 2 - CCNA Exploration: Accessing the WAN (Version 4.0)
 CCENT Practice Certification Exam # 2 - CCNA Exploration: Accessing the WAN (Version 4.0) 1. Data is being sent from a source PC to a destination server. Which three statements correctly describe the function
CCENT Practice Certification Exam # 2 - CCNA Exploration: Accessing the WAN (Version 4.0) 1. Data is being sent from a source PC to a destination server. Which three statements correctly describe the function
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Bi-directional ADN Deployment Using WCCP with Reflect Client IP [Configuration Sample] Ken Fritz (PSS)
![Bi-directional ADN Deployment Using WCCP with Reflect Client IP [Configuration Sample] Ken Fritz (PSS) Bi-directional ADN Deployment Using WCCP with Reflect Client IP [Configuration Sample] Ken Fritz (PSS)](/thumbs/73/68984394.jpg) Bi-directional ADN Deployment Using WCCP with Reflect Client IP [Configuration Sample] February 17, 2011 Ken Fritz (PSS) Copyright 2011 Blue Coat Systems, Inc. All rights reserved worldwide. No part of
Bi-directional ADN Deployment Using WCCP with Reflect Client IP [Configuration Sample] February 17, 2011 Ken Fritz (PSS) Copyright 2011 Blue Coat Systems, Inc. All rights reserved worldwide. No part of
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Lab Configuring Port Address Translation (PAT) (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Configuring Dynamic Addressing on the GGSN
 CHAPTER 13 This chapter describes how to configure dynamic IP addressing on the gateway GRPS support node (GGSN). Note Dynamic IP addressing is not supported for IPv6 and PPP PDP types. Therefore, the
CHAPTER 13 This chapter describes how to configure dynamic IP addressing on the gateway GRPS support node (GGSN). Note Dynamic IP addressing is not supported for IPv6 and PPP PDP types. Therefore, the
