Configuring Commonly Used IP ACLs
|
|
|
- Theodora Anne Young
- 5 years ago
- Views:
Transcription
1 Configuring Commonly Used IP ACLs Document ID: Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a Select Host to Access the Network Allow Access to a Range of Contiguous IP Addresses Deny Telnet Traffic (TCP, Port 23) Allow Only Internal Networks to Initiate a TCP Session Deny FTP Traffic (TCP, Port 21) Allow FTP Traffic (Active FTP) Allow FTP Traffic (Passive FTP) Allow Pings (ICMP) Allow HTTP, Telnet, Mail, POP3, FTP Allow DNS Permit Routing Updates Debug Traffic Based on ACL MAC Address Filtering Verify Troubleshoot Related Information Introduction This document provides sample configurations for commonly used IP Access Control Lists (ACLs), which filter IP packets based on: Source address Destination address Type of packet Any combination of these items In order to filter network traffic, ACLs control whether routed packets are forwarded or blocked at the router interface. Your router examines each packet to determine whether to forward or drop the packet based on the criteria that you specify within the ACL. ACL criteria include: Source address of the traffic Destination address of the traffic Upper layer protocol Complete these steps to construct an ACL as the examples in this document show: 1. Create an ACL. 2. Apply the ACL to an interface.
2 The IP ACL is a sequential collection of permit and deny conditions that applies to an IP packet. The router tests packets against the conditions in the ACL one at a time. The first match determines whether the Cisco IOS Software accepts or rejects the packet. Because the Cisco IOS Software stops testing conditions after the first match, the order of the conditions is critical. If no conditions match, the router rejects the packet because of an implicit deny all clause. These are examples of IP ACLs that can be configured in Cisco IOS Software: Standard ACLs Extended ACLs Dynamic (lock and key) ACLs IP named ACLs Reflexive ACLs Time based ACLs that use time ranges Commented IP ACL entries Context based ACLs Authentication proxy Turbo ACLs Distributed time based ACLs This document discusses some commonly used standard and extended ACLs. Refer to Configuring IP Access Lists for more information on different types of ACLs supported in Cisco IOS Software and how to configure and edit ACLs. The command syntax format of a standard ACL is access list access list number {permit deny} {host source source wildcard any}. Standard ACLs (registered customers only) control traffic by comparing the source address of the IP packets to the addresses configured in the ACL. Extended ACLs (registered customers only) control traffic by comparing the source and destination addresses of the IP packets to the addresses configured in the ACL. You can also make extended ACLs more granular and configured to filter traffic by criteria such as: Protocol Port numbers Differentiated services code point (DSCP) value Precedence value State of the synchronize sequence number (SYN) bit The command syntax formats of extended ACLs are: IP access list access list number [dynamic dynamic name [timeout minutes]] {deny permit} protocol source source wildcard destination destination wildcard [precedence precedence] [tos tos] [log log input] [time range time range name][fragments] Internet Control Message Protocol (ICMP) access list access list number [dynamic dynamic name [timeout minutes]] {deny permit} icmp source source wildcard destination destination wildcard [icmp type
3 Transport Control Protocol (TCP) [icmp code] [icmp message]] [precedenceprecedence] [tos tos] [log log input] [time range time range name][fragments] access list access list number [dynamic dynamic name [timeout minutes]] {deny permit} tcp source source wildcard [operator [port]] destination destination wildcard [operator [port]] [established] [precedence precedence] [tos tos] [log log input] [time range time range name][fragments] User Datagram Protocol (UDP) access list access list number [dynamic dynamic name [timeout minutes]] {deny permit} udp source source wildcard [operator [port]] destination destination wildcard [operator [port]] [precedence precedence] [tos tos] [log log input] [time range time range name][fragments] Refer to IP Services Commands for the command reference for an ACL. Prerequisites Requirements Ensure that you meet this requirement before you attempt this configuration: Basic understanding of IP addressing Refer to IP Addressing and Subnetting for New Users for additional information. Components Used This document is not restricted to specific software and hardware versions. Conventions Refer to Cisco Technical Tips Conventions for more information on document conventions. Configuration Examples These configuration examples use the most common IP ACLs. Note: Use the Command Lookup Tool (registered customers only) to find more information on the commands used in this document. Allow a Select Host to Access the Network This figure shows a select host being granted permission to access the network. All traffic sourced from Host B destined to NetA is permitted, and all other traffic sourced from NetB destined to NetA is denied.
4 The output on the table shows how the network grants access to the host. This output shows that: The configuration allows only the host with the IP address through the Ethernet 0 interface on. This host has access to the IP services of NetA. No other host in NetB has access to NetA. No deny statement is configured in the ACL. By default, there is an implicit deny all clause at the end of every ACL. Anything that is not explicitly permitted is denied. hostname ip access group 1 in access list 1 permit host Note: The ACL filters IP packets from NetB to NetA, except packets sourced from NetB. Packets destined to Host B from NetA are still permitted. Note: The ACL access list 1 permit is another way to configure the same rule. Deny a Select Host to Access the Network This figure shows that traffic sourced from Host B destined to NetA is denied, while all other traffic from the NetB to access NetA is permitted. This configuration denies all packets from host /32 through Ethernet 0 on and permits everything else. You must use the command access list 1 permit any to explicitly permit everything else because there is an implicit deny all clause with every ACL. hostname ip access group 1 in access list 1 deny host access list 1 permit any
5 Note: The order of statements is critical to the operation of an ACL. If the order of the entries is reversed as this command shows, the first line matches every packet source address. Therefore, the ACL fails to block host /32 from accessing NetA. access list 1 permit any access list 1 deny host Allow Access to a Range of Contiguous IP Addresses This figure shows that all hosts in NetB with the network address /24 can access network /24 in NetA. This configuration allows the IP packets with an IP header that has a source address in the network /24 and a destination address in the network /24 access to NetA. There is the implicit deny all clause at the end of the ACL which denies all other traffic passage through Ethernet 0 inbound on. hostname ip access group 101 in access list 101 permit ip Note: In the command access list 101 permit ip , the " " is the inverse mask of network with mask ACLs use the inverse mask to know how many bits in the network address need to match. In the table, the ACL permits all hosts with source addresses in the /24 network and destination addresses in the /24 network. Refer to the Masks section of Configuring IP Access Lists for more information on the mask of a network address and how to calculate the inverse mask needed for ACLs. Deny Telnet Traffic (TCP, Port 23) In order to meet higher security concerns, you might have to disable Telnet access to your private network from the public network. This figure shows how Telnet traffic from NetB (public) destined to NetA (private) is denied, which permits NetA to initiate and establish a Telnet session with NetB while all other IP traffic is permitted.
6 Telnet uses TCP, port 23. This configuration shows that all TCP traffic destined to NetA for port 23 is blocked, and all other IP traffic is permitted. hostname access list 102 deny tcp any any eq 23 access list 102 permit ip any any Allow Only Internal Networks to Initiate a TCP Session This figure shows that TCP traffic sourced from NetA destined to NetB is permitted, while TCP traffic from NetB destined to NetA is denied. The purpose of the ACL in this example is to: Allow hosts in NetA to initiate and establish a TCP session to hosts in NetB. Deny hosts in NetB from initiating and establishing a TCP session destined to hosts in NetA. This configuration allows a datagram to pass through interface Ethernet 0 inbound on when the datagram has: Acknowledged (ACK) or reset (RST) bits set (indicating an established TCP session) A destination port value greater than 1023 hostname access list 102 permit tcp any any gt 1023 established Since most of the well known ports for IP services use values less than 1023, any datagram with a destination port less than 1023 or an ACK/RST bit not set is denied by ACL 102. Therefore, when a host from NetB
7 initiates a TCP connection by sending the first TCP packet (without synchronize/start packet (SYN/RST) bit set) for a port number less than 1023, it is denied and the TCP session fails. The TCP sessions initiated from NetA destined to NetB are permitted because they have ACK/RST bit set for returning packets and use port values greater than Refer to RFC 1700 for a complete list of ports. Deny FTP Traffic (TCP, Port 21) This figure shows that FTP (TCP, port 21) and FTP data (port 20 ) traffic sourced from NetB destined to NetA is denied, while all other IP traffic is permitted. FTP uses port 21 and port 20. TCP traffic destined to port 21 and port 20 is denied and everything else is explicitly permitted. hostname access list 102 deny tcp any any eq ftp access list 102 deny tcp any any eq ftp data access list 102 permit ip any any Allow FTP Traffic (Active FTP) FTP can operate in two different modes named active and passive. Refer to FTP Operation to understand how active and passive FTP works. When FTP operates in active mode, the FTP server uses port 21 for control and port 20 for data. FTP server ( ) is located in NetA. This figure shows that FTP (TCP, port 21) and FTP data (port 20 ) traffic sourced from NetB destined to FTP server ( ) is permitted, while all other IP traffic is denied. hostname
8 access list 102 permit tcp any host eq ftp access list 102 permit tcp any host eq ftp data established interface ethernet1 ip access group 110 in access list 110 permit host eq ftp any established access list 110 permit host eq ftp data any Allow FTP Traffic (Passive FTP) FTP can operate in two different modes named active and passive. Refer to FTP Operation in order to understand how active and passive FTP works. When FTP operates in passive mode, the FTP server uses port 21 for control and the dynamic ports greater than or equal to 1024 for data. FTP server ( ) is located in NetA. This figure shows that FTP (TCP, port 21) and FTP data (ports greater than or equal to 1024) traffic sourced from NetB destined to FTP server ( ) is permitted, while all other IP traffic is denied. hostname access list 102 permit tcp any host eq ftp access list 102 permit tcp any host gt 1024 interface ethernet1 ip access group 110 in access list 110 permit host eq ftp any established access list 110 permit host gt 1024 any established Allow Pings (ICMP) This figure shows that ICMP sourced from NetA destined to NetB is permitted, and pings sourced from NetB destined to NetA are denied.
9 This configuration permits only echo reply (ping response) packets to come in on interface Ethernet 0 from NetB towards NetA. However, the configuration blocks all echo request ICMP packets when pings are sourced in NetB and destined to NetA. Therefore, hosts in NetA can ping hosts in NetB, but hosts in NetB cannot ping hosts in NetA. hostname access list 102 permit icmp any any echo reply Allow HTTP, Telnet, Mail, POP3, FTP This figure shows that only HTTP, Telnet, Simple Mail Transfer Protocol (SMTP), POP3, and FTP traffic are permitted, and the rest of the traffic sourced from NetB destined to NetA is denied. This configuration permits TCP traffic with destination port values that match WWW (port 80), Telnet (port 23), SMTP (port 25), POP3 (port 110), FTP (port 21), or FTP data (port 20). Notice an implicit deny all clause at the end of an ACL denies all other traffic, which does not match the permit clauses. hostname access list 102 permit tcp any any eq www access list 102 permit tcp any any eq telnet access list 102 permit tcp any any eq smtp access list 102 permit tcp any any eq pop3 access list 102 permit tcp any any eq 21 access list 102 permit tcp any any eq 20
10 Allow DNS This figure shows that only Domain Name System (DNS) traffic is permitted, and the rest of the traffic sourced from NetB destined to NetA is denied. This configuration permits TCP traffic with destination port value 53. The implicit deny all clause at the end of an ACL denies all other traffic, which does not match the permit clauses. hostname access list 112 permit udp any any eq domain access list 112 permit udp any eq domain any access list 112 permit tcp any any eq domain access list 112 permit tcp any eq domain any Permit Routing Updates When you apply an in bound ACL on to an interface, ensure that routing updates are not filtered out. Use the relevant ACL from this list to permit routing protocol packets: Issue this command to permit Routing Information Protocol (RIP): access list 102 permit udp any any eq rip Issue this command to permit Interior Gateway Routing Protocol (IGRP): access list 102 permit igrp any any Issue this command to permit Enhanced IGRP (EIGRP): access list 102 permit eigrp any any Issue this command to permit Open Shortest Path First (OSPF): access list 102 permit ospf any any Issue this command to permit Border Gateway Protocol (BGP): access list 102 permit tcp any any eq 179 access list 102 permit tcp any eq 179 any
11 Debug Traffic Based on ACL The use of debug commands requires the allocation of system resources like memory and processing power and in extreme situations can cause a heavily loaded system to stall. Use debug commands with care. Use an ACL in order to selectively define the traffic that needs to be examined to reduce the impact of thedebug command. Such a configuration does not filter any packets. This configuration turns on the debug ip packet command only for packets between the hosts and (config)#access list 199 permit tcp host host (config)#access list 199 permit tcp host host (config)#end #debug ip packet 199 detail IP packet debugging is on (detailed) for access list 199 Refer to Important Information on Debug Commands for additional information on the impact of debug commands. Refer to the Use the Debug Command section of Understanding the Ping and Traceroute Commands for additional information on the use of ACLs with debug commands. MAC Address Filtering You can filter frames with a particular MAC layer station source or destination address. Any number of addresses can be configured into the system without a performance penalty. In order to filter by MAC layer address, use this command in global configuration mode: Router#config terminal bridge irb bridge 1 protocol ieee bridge 1 route ip Apply the bridge protocol to an interface that you need to filter traffic along with the access list created: Router#int fa0/0 no ip address bridge group 1 {input address list 700 output address list 700} exit Create a Bridged Virtual Interface and apply the IP address that is assigned to the Ethernet interface: Router#int bvi1 ip address exit access list 700 deny <mac address> access list 700 permit ffff.ffff.ffff With this configuration, the router only allows the mac addresses configured on the access list 700. With the access list, deny the MAC adddress that can not have access and then permit the rest. Note: Create every line of access list for each MAC address.
12 Verify There is currently no verification procedure available for this configuration. Troubleshoot There is currently no specific troubleshooting information available for this configuration. Related Information Configuring IP Access Lists Access Lists Support Page IP Routing Support Page IP Routed Protocols Support Page Technical Support & Documentation Cisco Systems Contacts & Feedback Help Site Map Cisco Systems, Inc. All rights reserved. Terms & Conditions Privacy Statement Cookie Policy Trademarks of Cisco Systems, Inc. Updated: Jan 28, 2008 Document ID: 26448
Document ID: Introduction. Prerequisites. Requirements. Components Used. Conventions
 Products & Services Configuring IP Access Lists Document ID: 23602 Contents Introduction Prerequisites Requirements Components Used Conventions ACL Concepts Masks ACL Summarization Process ACLs Define
Products & Services Configuring IP Access Lists Document ID: 23602 Contents Introduction Prerequisites Requirements Components Used Conventions ACL Concepts Masks ACL Summarization Process ACLs Define
Router and ACL ACL Filter traffic ACL: The Three Ps One ACL per protocol One ACL per direction One ACL per interface
 CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
7 Filtering and Firewalling
 7 Filtering and Firewalling 7.1 Introduction Security is becoming a major concern in IT, and A major concern in networking and the Internet, and wireless systems are probably more open to abuse than any
7 Filtering and Firewalling 7.1 Introduction Security is becoming a major concern in IT, and A major concern in networking and the Internet, and wireless systems are probably more open to abuse than any
Table of Contents. Cisco Configuring IP Access Lists
 Table of Contents Configuring IP Access Lists...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2 ACL Concepts...2 Masks...2 ACL Summarization...3 Process ACLs...4
Table of Contents Configuring IP Access Lists...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2 ACL Concepts...2 Masks...2 ACL Summarization...3 Process ACLs...4
IP Services Commands. Cisco IOS IP Command Reference, Volume 1 of 3: Addressing and Services IP1R-157
 Use the commands in this chapter to configure various IP services. For configuration information and examples on IP services, refer to the Configuring IP Services chapter of the Cisco IOS IP Configuration
Use the commands in this chapter to configure various IP services. For configuration information and examples on IP services, refer to the Configuring IP Services chapter of the Cisco IOS IP Configuration
Information about Network Security with ACLs
 This chapter describes how to configure network security on the switch by using access control lists (ACLs), which in commands and tables are also referred to as access lists. Finding Feature Information,
This chapter describes how to configure network security on the switch by using access control lists (ACLs), which in commands and tables are also referred to as access lists. Finding Feature Information,
Context Based Access Control (CBAC): Introduction and Configuration
 Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Configuring IP Session Filtering (Reflexive Access Lists)
 Configuring IP Session Filtering (Reflexive Access Lists) This chapter describes how to configure reflexive access lists on your router. Reflexive access lists provide the ability to filter network traffic
Configuring IP Session Filtering (Reflexive Access Lists) This chapter describes how to configure reflexive access lists on your router. Reflexive access lists provide the ability to filter network traffic
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Using NAT in Overlapping Networks
 Using NAT in Overlapping Networks Document ID: 13774 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Related Information
Using NAT in Overlapping Networks Document ID: 13774 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Related Information
This appendix contains job aids and supplements for the following topics: Extending IP Addressing Job Aids Supplement 1: Addressing Review Supplement
 This appendix contains job aids and supplements for the following topics: Extending IP Addressing Job Aids Supplement 1: Addressing Review Supplement 2: IP Access Lists Supplement 3: OSPF Supplement 4:
This appendix contains job aids and supplements for the following topics: Extending IP Addressing Job Aids Supplement 1: Addressing Review Supplement 2: IP Access Lists Supplement 3: OSPF Supplement 4:
Appendix B Policies and Filters
 Appendix B Policies and Filters NOTE: This appendix does not describe Access Control Lists (ACLs) or IPX SAP ACLs, which are additional methods for filtering packets. See Software-Based IP Access Control
Appendix B Policies and Filters NOTE: This appendix does not describe Access Control Lists (ACLs) or IPX SAP ACLs, which are additional methods for filtering packets. See Software-Based IP Access Control
IP Services Commands. Network Protocols Command Reference, Part 1 P1R-95
 IP Services Commands Use the commands in this chapter to configure various IP services. For configuration information and examples on IP services, refer to the Configuring IP Services chapter of the Network
IP Services Commands Use the commands in this chapter to configure various IP services. For configuration information and examples on IP services, refer to the Configuring IP Services chapter of the Network
Configuring IPv6 ACLs
 CHAPTER 37 When the Cisco ME 3400 Ethernet Access switch is running the metro IP access image, you can filter IP Version 6 (IPv6) traffic by creating IPv6 access control lists (ACLs) and applying them
CHAPTER 37 When the Cisco ME 3400 Ethernet Access switch is running the metro IP access image, you can filter IP Version 6 (IPv6) traffic by creating IPv6 access control lists (ACLs) and applying them
Implementing Firewall Technologies
 Implementing Firewall Technologies Network firewalls separate protected from non-protected areas preventing unauthorized users from accessing protected network resources. Technologies used: ACLs Standard,
Implementing Firewall Technologies Network firewalls separate protected from non-protected areas preventing unauthorized users from accessing protected network resources. Technologies used: ACLs Standard,
CCNA Access List Questions
 CCNA Access List Questions Here you will find answers to CCNA Access list questions Note: If you are not sure about how to use Access list, please read my Access list tutorial Question 1 Your boss is learning
CCNA Access List Questions Here you will find answers to CCNA Access list questions Note: If you are not sure about how to use Access list, please read my Access list tutorial Question 1 Your boss is learning
Access Control List Overview
 Access lists filter network traffic by controlling the forwarding or blocking of packets at the interface of a device. A device examines each packet to determine whether to forward or drop that packet,
Access lists filter network traffic by controlling the forwarding or blocking of packets at the interface of a device. A device examines each packet to determine whether to forward or drop that packet,
Extended ACL Configuration Mode Commands
 Extended ACL Configuration Mode Commands To create and modify extended access lists on a WAAS device for controlling access to interfaces or applications, use the ip access-list extended global configuration
Extended ACL Configuration Mode Commands To create and modify extended access lists on a WAAS device for controlling access to interfaces or applications, use the ip access-list extended global configuration
Implementing Access Lists and Prefix Lists
 An access control list (ACL) consists of one or more access control entries (ACE) that collectively define the network traffic profile. This profile can then be referenced by Cisco IOS XR softwarefeatures
An access control list (ACL) consists of one or more access control entries (ACE) that collectively define the network traffic profile. This profile can then be referenced by Cisco IOS XR softwarefeatures
Access List Commands
 Access List Commands This module describes the Cisco IOS XR software commands used to configure IP Version 4 (IPv4) and IP Version 6 (IPv6) access lists. An access control list (ACL) consists of one or
Access List Commands This module describes the Cisco IOS XR software commands used to configure IP Version 4 (IPv4) and IP Version 6 (IPv6) access lists. An access control list (ACL) consists of one or
Prof. Bill Buchanan Room: C.63
 Wireless LAN CO72047 Unit 7: Filtering Prof. Bill Buchanan Contact: w.buchanan@napier.ac.uk Room: C.63 Telephone: X2759 MSN Messenger: w_j_buchanan@hotmail.com WWW: http://www.dcs.napier.ac.uk/~bill http://buchananweb.co.uk
Wireless LAN CO72047 Unit 7: Filtering Prof. Bill Buchanan Contact: w.buchanan@napier.ac.uk Room: C.63 Telephone: X2759 MSN Messenger: w_j_buchanan@hotmail.com WWW: http://www.dcs.napier.ac.uk/~bill http://buchananweb.co.uk
Object Groups for ACLs
 The feature lets you classify users, devices, or protocols into groups and apply those groups to access control lists (ACLs) to create access control policies for those groups. This feature lets you use
The feature lets you classify users, devices, or protocols into groups and apply those groups to access control lists (ACLs) to create access control policies for those groups. This feature lets you use
Access List Commands
 Access List Commands This module describes the Cisco IOS XR software commands used to configure IP Version 4 (IPv4) and IP Version 6 (IPv6) access lists. An access control list (ACL) consists of one or
Access List Commands This module describes the Cisco IOS XR software commands used to configure IP Version 4 (IPv4) and IP Version 6 (IPv6) access lists. An access control list (ACL) consists of one or
Chapter 4 Software-Based IP Access Control Lists (ACLs)
 Chapter 4 Software-Based IP Access Control Lists (ACLs) This chapter describes software-based ACLs, which are ACLs that processed traffic in software or CPU. (This type of ACL was also referred to as flow-based
Chapter 4 Software-Based IP Access Control Lists (ACLs) This chapter describes software-based ACLs, which are ACLs that processed traffic in software or CPU. (This type of ACL was also referred to as flow-based
Configuring an IP ACL
 9 CHAPTER This chapter describes how to configure IP access control lists (ACLs). This chapter includes the following sections: Information About ACLs, page 9-1 Prerequisites for IP ACLs, page 9-5 Guidelines
9 CHAPTER This chapter describes how to configure IP access control lists (ACLs). This chapter includes the following sections: Information About ACLs, page 9-1 Prerequisites for IP ACLs, page 9-5 Guidelines
IPv6 Access Control Lists
 Access lists determine what traffic is blocked and what traffic is forwarded at device interfaces and allow filtering of traffic based on source and destination addresses, and inbound and outbound traffic
Access lists determine what traffic is blocked and what traffic is forwarded at device interfaces and allow filtering of traffic based on source and destination addresses, and inbound and outbound traffic
Reflexive Access List Commands
 Reflexive Access List Commands This chapter describes reflexive access list commands, which are used to configure IP session filtering. IP session filtering provides the ability to filter IP packets based
Reflexive Access List Commands This chapter describes reflexive access list commands, which are used to configure IP session filtering. IP session filtering provides the ability to filter IP packets based
Object Groups for ACLs
 The feature lets you classify users, devices, or protocols into groups and apply those groups to access control lists (ACLs) to create access control policies for those groups. This feature lets you use
The feature lets you classify users, devices, or protocols into groups and apply those groups to access control lists (ACLs) to create access control policies for those groups. This feature lets you use
Access List Commands
 This chapter describes the Cisco IOS XR software commands used to configure IP Version 4 (IPv4) and IP Version 6 (IPv6) access lists on Cisco ASR 9000 Series Aggregation Services Routers. An access control
This chapter describes the Cisco IOS XR software commands used to configure IP Version 4 (IPv4) and IP Version 6 (IPv6) access lists on Cisco ASR 9000 Series Aggregation Services Routers. An access control
NAT Support for Multiple Pools Using Route Maps
 NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
ipv6 hello-interval eigrp
 ipv6 hello-interval eigrp ipv6 hello-interval eigrp To configure the hello interval for the Enhanced Interior Gateway Routing Protocol (EIGRP) for IPv6 routing process designated by an autonomous system
ipv6 hello-interval eigrp ipv6 hello-interval eigrp To configure the hello interval for the Enhanced Interior Gateway Routing Protocol (EIGRP) for IPv6 routing process designated by an autonomous system
This appendix contains job aids and supplementary information that cover the following topics:
 2237xxc.fm Page 2 Friday, December 1, 2006 3:36 PM This appendix contains job aids and supplementary information that cover the following topics: IPv4 Addresses and Subnetting Job Aid Decimal-to-Binary
2237xxc.fm Page 2 Friday, December 1, 2006 3:36 PM This appendix contains job aids and supplementary information that cover the following topics: IPv4 Addresses and Subnetting Job Aid Decimal-to-Binary
Access Rules. Controlling Network Access
 This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
Object Groups for ACLs
 The feature lets you classify users, devices, or protocols into groups and apply these groups to access control lists (ACLs) to create access control policies for these groups. This feature lets you use
The feature lets you classify users, devices, or protocols into groups and apply these groups to access control lists (ACLs) to create access control policies for these groups. This feature lets you use
Implementing Traffic Filtering with ACLs
 Implementing Traffic Filtering with ACLs Managing Network Device Security 2013 Cisco Systems, Inc. ICND1 3-36 How can you restrict Internet access for PC2? 2013 Cisco Systems, Inc. ICND1 3-37 ACL operation
Implementing Traffic Filtering with ACLs Managing Network Device Security 2013 Cisco Systems, Inc. ICND1 3-36 How can you restrict Internet access for PC2? 2013 Cisco Systems, Inc. ICND1 3-37 ACL operation
Creating an IP Access List to Filter IP Options, TCP Flags, or Noncontiguous Ports
 Creating an IP Access List to Filter IP Options, TCP Flags, or Noncontiguous Ports First Published: August 18, 2006 Last Updated: July 31, 2009 This module describes how to use an IP access list to filter
Creating an IP Access List to Filter IP Options, TCP Flags, or Noncontiguous Ports First Published: August 18, 2006 Last Updated: July 31, 2009 This module describes how to use an IP access list to filter
Inspection of Router-Generated Traffic
 Inspection of Router-Generated Traffic The Inspection of Router-Generated Traffic feature allows Context-Based Access Control (CBAC) to inspect traffic that is originated by or destined to the router on
Inspection of Router-Generated Traffic The Inspection of Router-Generated Traffic feature allows Context-Based Access Control (CBAC) to inspect traffic that is originated by or destined to the router on
Object Groups for ACLs
 Object Groups for ACLs Last Updated: January 18, 2012 The Object Groups for ACLs feature lets you classify users, devices, or protocols into groups and apply those groups to access control lists (ACLs)
Object Groups for ACLs Last Updated: January 18, 2012 The Object Groups for ACLs feature lets you classify users, devices, or protocols into groups and apply those groups to access control lists (ACLs)
ACL Rule Configuration on the WAP371
 Article ID: 5089 ACL Rule Configuration on the WAP371 Objective A network access control list (ACL) is an optional layer of security that acts as a firewall for controlling traffic in and out of a subnet.
Article ID: 5089 ACL Rule Configuration on the WAP371 Objective A network access control list (ACL) is an optional layer of security that acts as a firewall for controlling traffic in and out of a subnet.
IP Access List Overview
 Access control lists (ACLs) perform packet filtering to control which packets move through a network and to where. The packet filtering provides security by helping to limit the network traffic, restrict
Access control lists (ACLs) perform packet filtering to control which packets move through a network and to where. The packet filtering provides security by helping to limit the network traffic, restrict
IP Access List Overview
 Access control lists (ACLs) perform packet filtering to control which packets move through the network and where. Such control provides security by helping to limit network traffic, restrict the access
Access control lists (ACLs) perform packet filtering to control which packets move through the network and where. Such control provides security by helping to limit network traffic, restrict the access
Cisco CCNA ACL Part II
 Cisco CCNA ACL Part II Cisco CCNA Access List Applications This slide illustrates common uses for IP access lists. While this chapter focuses on IP access lists, the concept of access lists as mechanisms
Cisco CCNA ACL Part II Cisco CCNA Access List Applications This slide illustrates common uses for IP access lists. While this chapter focuses on IP access lists, the concept of access lists as mechanisms
2002, Cisco Systems, Inc. All rights reserved.
 2002, Cisco Systems, Inc. All rights reserved. Configuring IP Access Lists 2002, Cisco Systems, Inc. All All rights reserved. ICND v2.0 6-2 2 Objectives Upon completing this lesson, you will be able to:
2002, Cisco Systems, Inc. All rights reserved. Configuring IP Access Lists 2002, Cisco Systems, Inc. All All rights reserved. ICND v2.0 6-2 2 Objectives Upon completing this lesson, you will be able to:
Advanced Security and Forensic Computing
 Advanced Security and Forensic Computing Unit 2: Network Security Elements Dr Dr Bill Buchanan, Reader, School of of Computing. >Unit 2: 2: Network Security Elements Advanced Security and Forensic Computing
Advanced Security and Forensic Computing Unit 2: Network Security Elements Dr Dr Bill Buchanan, Reader, School of of Computing. >Unit 2: 2: Network Security Elements Advanced Security and Forensic Computing
Firewall Stateful Inspection of ICMP
 The feature categorizes Internet Control Management Protocol Version 4 (ICMPv4) messages as either malicious or benign. The firewall uses stateful inspection to trust benign ICMPv4 messages that are generated
The feature categorizes Internet Control Management Protocol Version 4 (ICMPv4) messages as either malicious or benign. The firewall uses stateful inspection to trust benign ICMPv4 messages that are generated
Lab - Troubleshooting ACL Configuration and Placement Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem
 How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
6 Network Security Elements
 6 Network Security Elements http://www.asecuritysite.com/security/information/chapter06 6.1 Objectives The key objectives of this unit are to: Provide an overview of security devices and infrastructures.
6 Network Security Elements http://www.asecuritysite.com/security/information/chapter06 6.1 Objectives The key objectives of this unit are to: Provide an overview of security devices and infrastructures.
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Configuring IP Version 6
 CHAPTER 24 Configuring IP Version 6 Internet Protocol version 6 (IPv6), formerly called IPng (next generation), is the latest version of IP. IPv6 offers many advantages over the previous version of IP,
CHAPTER 24 Configuring IP Version 6 Internet Protocol version 6 (IPv6), formerly called IPng (next generation), is the latest version of IP. IPv6 offers many advantages over the previous version of IP,
Configuring IP Services
 CHAPTER 8 Configuring IP Services This chapter describes how to configure optional IP services supported by the Cisco Optical Networking System (ONS) 15304. For a complete description of the commands in
CHAPTER 8 Configuring IP Services This chapter describes how to configure optional IP services supported by the Cisco Optical Networking System (ONS) 15304. For a complete description of the commands in
Wireless LANs (CO72047) Bill Buchanan, Reader, School of Computing.
 Bill Buchanan, Reader, School of Computing. W.Buchanan (1) Lab setup W.Buchanan (2) W.Buchanan (3) Console Server Con Cisco Aironet 1200 192.168.1.100 Port 2001 Con Cisco Aironet 1200 192.168.1.100 Port
Bill Buchanan, Reader, School of Computing. W.Buchanan (1) Lab setup W.Buchanan (2) W.Buchanan (3) Console Server Con Cisco Aironet 1200 192.168.1.100 Port 2001 Con Cisco Aironet 1200 192.168.1.100 Port
TCP/IP Filtering. Main TCP/IP Filtering Dialog Box. Route Filters Button. Packet Filters Button CHAPTER
 CHAPTER 11 Main Dialog Box To access this dialog box (Figure 11-1), select Global/Filtering/ from the Device View. Figure 11-1 Main Configuration Dialog Box Route Filters Button This button brings up a
CHAPTER 11 Main Dialog Box To access this dialog box (Figure 11-1), select Global/Filtering/ from the Device View. Figure 11-1 Main Configuration Dialog Box Route Filters Button This button brings up a
Configuring Network Security with ACLs
 26 CHAPTER This chapter describes how to use access control lists (ACLs) to configure network security on the Catalyst 4500 series switches. Note For complete syntax and usage information for the switch
26 CHAPTER This chapter describes how to use access control lists (ACLs) to configure network security on the Catalyst 4500 series switches. Note For complete syntax and usage information for the switch
Chapter 6 Global CONFIG Commands
 Chapter 6 Global CONFIG Commands aaa accounting Configures RADIUS or TACACS+ accounting for recording information about user activity and system events. When you configure accounting on an HP device, information
Chapter 6 Global CONFIG Commands aaa accounting Configures RADIUS or TACACS+ accounting for recording information about user activity and system events. When you configure accounting on an HP device, information
Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454
 Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454 Document ID: 65122 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Topology
Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454 Document ID: 65122 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Topology
Routers use access lists to control incoming or outgoing traffic. You should know the following characteristics of an access list.
 8.1. Access List Routers use access lists to control incoming or outgoing traffic. You should know the following characteristics of an access list. Access lists describe the traffic type that will be controlled.
8.1. Access List Routers use access lists to control incoming or outgoing traffic. You should know the following characteristics of an access list. Access lists describe the traffic type that will be controlled.
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands
 PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
Lab 6: Access Lists. Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/ R1
 Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
Access Control List Enhancements on the Cisco Series Router
 Access Control List Enhancements on the Cisco 12000 Series Router Part Number, May 30, 2008 The Cisco 12000 series router filters IP packets using access control lists (ACLs) as a fundamental security
Access Control List Enhancements on the Cisco 12000 Series Router Part Number, May 30, 2008 The Cisco 12000 series router filters IP packets using access control lists (ACLs) as a fundamental security
TCP/IP Networking. Training Details. About Training. About Training. What You'll Learn. Training Time : 9 Hours. Capacity : 12
 TCP/IP Networking Training Details Training Time : 9 Hours Capacity : 12 Prerequisites : There are no prerequisites for this course. About Training About Training TCP/IP is the globally accepted group
TCP/IP Networking Training Details Training Time : 9 Hours Capacity : 12 Prerequisites : There are no prerequisites for this course. About Training About Training TCP/IP is the globally accepted group
Creating an IP Access List to Filter IP Options, TCP Flags, Noncontiguous Ports
 Creating an IP Access List to Filter IP Options, TCP Flags, Noncontiguous Ports This module describes how to use an IP access list to filter IP packets that contain certain IP Options, TCP flags, noncontiguous
Creating an IP Access List to Filter IP Options, TCP Flags, Noncontiguous Ports This module describes how to use an IP access list to filter IP packets that contain certain IP Options, TCP flags, noncontiguous
Prerequisites for Creating an IP Access List to Filter IP Options TCP Flags Noncontiguous Ports
 Creating an IP Access List to Filter IP Options, TCP Flags, Noncontiguous Ports This module describes how to use an IP access list to filter IP packets that contain certain IP Options, TCP flags, noncontiguous
Creating an IP Access List to Filter IP Options, TCP Flags, Noncontiguous Ports This module describes how to use an IP access list to filter IP packets that contain certain IP Options, TCP flags, noncontiguous
Configuring IP Services
 Configuring IP Services This chapter describes how to configure optional IP services. For a complete description of the IP services commands in this chapter, refer to the IP Services s chapter of the Cisco
Configuring IP Services This chapter describes how to configure optional IP services. For a complete description of the IP services commands in this chapter, refer to the IP Services s chapter of the Cisco
TCP /IP Fundamentals Mr. Cantu
 TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
Teacher s Reference Manual
 UNIVERSITY OF MUMBAI Teacher s Reference Manual Subject: Security in Computing Practical with effect from the academic year 2018 2019 Practical 1: Packet Tracer - Configure Cisco Routers for Syslog, NTP,
UNIVERSITY OF MUMBAI Teacher s Reference Manual Subject: Security in Computing Practical with effect from the academic year 2018 2019 Practical 1: Packet Tracer - Configure Cisco Routers for Syslog, NTP,
Lab b Simple DMZ Extended Access Lists Instructor Version 2500
 Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
Adjust Administrative Distance for Route Selection in Cisco IOS Routers Configuration Example
 Adjust Administrative Distance for Route Selection in Cisco IOS Routers Configuration Example Document ID: 113153 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Adjust Administrative Distance for Route Selection in Cisco IOS Routers Configuration Example Document ID: 113153 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Configuring IP SLAs TCP Connect Operations
 This module describes how to configure an IP Service Level Agreements (SLAs) TCP Connect operation to measure the response time taken to perform a TCP Connect operation between a Cisco router and devices
This module describes how to configure an IP Service Level Agreements (SLAs) TCP Connect operation to measure the response time taken to perform a TCP Connect operation between a Cisco router and devices
Sybex CCENT Chapter 12: Security. Instructor & Todd Lammle
 Sybex CCENT 100-101 Chapter 12: Security Instructor & Todd Lammle Chapter 12 Objectives The CCENT Topics Covered in this chapter include: IP Services Describe the types, features, and applications of ACLs
Sybex CCENT 100-101 Chapter 12: Security Instructor & Todd Lammle Chapter 12 Objectives The CCENT Topics Covered in this chapter include: IP Services Describe the types, features, and applications of ACLs
Interconnecting Networks with TCP/IP. 2000, Cisco Systems, Inc. 8-1
 Interconnecting Networks with TCP/IP 2000, Cisco Systems, Inc. 8-1 Objectives Upon completion of this chapter you will be able to perform the following tasks: Identify the IP protocol stack, its protocol
Interconnecting Networks with TCP/IP 2000, Cisco Systems, Inc. 8-1 Objectives Upon completion of this chapter you will be able to perform the following tasks: Identify the IP protocol stack, its protocol
Configuring NAT for IP Address Conservation
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
Understanding and Troubleshooting Idle Timeouts
 Understanding and Troubleshooting Idle Timeouts Document ID: 23423 Contents Introduction Prerequisites Requirements Components Used Conventions Common Problems and Symptoms Idle Timeouts Interesting Traffic
Understanding and Troubleshooting Idle Timeouts Document ID: 23423 Contents Introduction Prerequisites Requirements Components Used Conventions Common Problems and Symptoms Idle Timeouts Interesting Traffic
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
IPv6 Commands: ipv6 h to ipv6 mi
 IPv6 Commands: ipv6 h to ipv6 mi ipv6 hello-interval eigrp, page 3 ipv6 hold-time eigrp, page 5 ipv6 hop-limit, page 7 ipv6 host, page 8 ipv6 icmp error-interval, page 10 ipv6 inspect, page 12 ipv6 inspect
IPv6 Commands: ipv6 h to ipv6 mi ipv6 hello-interval eigrp, page 3 ipv6 hold-time eigrp, page 5 ipv6 hop-limit, page 7 ipv6 host, page 8 ipv6 icmp error-interval, page 10 ipv6 inspect, page 12 ipv6 inspect
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Understanding Access Control Lists (ACLs) Semester 2 v3.1
 1 Understanding Access Control Lists (ACLs) Access Control Lists 2 Access control lists (ACLs) are lists of instructions you apply to a router's interface. These lists tell the router what kinds of packets
1 Understanding Access Control Lists (ACLs) Access Control Lists 2 Access control lists (ACLs) are lists of instructions you apply to a router's interface. These lists tell the router what kinds of packets
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
IP Protocols. ALTTC/Oct
 IP Protocols Internet or IP technology over the years has emerged as the most prominent data communication technology. TCP/IP protocol has become de-facto data comm standard throughout the world. It can
IP Protocols Internet or IP technology over the years has emerged as the most prominent data communication technology. TCP/IP protocol has become de-facto data comm standard throughout the world. It can
Implementing Access Lists and Prefix Lists on Cisco ASR 9000 Series Routers
 Implementing Access Lists and Prefix Lists on Cisco ASR 9000 Series Routers An access control list (ACL) consists of one me access control entries (ACE) that collectively define the netwk traffic profile.
Implementing Access Lists and Prefix Lists on Cisco ASR 9000 Series Routers An access control list (ACL) consists of one me access control entries (ACE) that collectively define the netwk traffic profile.
CompTIA Exam JK0-023 CompTIA Network+ certification Version: 5.0 [ Total Questions: 1112 ]
![CompTIA Exam JK0-023 CompTIA Network+ certification Version: 5.0 [ Total Questions: 1112 ] CompTIA Exam JK0-023 CompTIA Network+ certification Version: 5.0 [ Total Questions: 1112 ]](/thumbs/89/98129936.jpg) s@lm@n CompTIA Exam JK0-023 CompTIA Network+ certification Version: 5.0 [ Total Questions: 1112 ] Topic break down Topic No. of Questions Topic 1: Network Architecture 183 Topic 3: Troubleshooting 140
s@lm@n CompTIA Exam JK0-023 CompTIA Network+ certification Version: 5.0 [ Total Questions: 1112 ] Topic break down Topic No. of Questions Topic 1: Network Architecture 183 Topic 3: Troubleshooting 140
D Commands. Send document comments to This chapter describes the Cisco NX-OS security commands that begin with D.
 This chapter describes the Cisco NX-OS security commands that begin with D. SEC-141 deadtime deadtime To configure the dead-time interval for a RADIUS or TACACS+ server group, use the deadtime command.
This chapter describes the Cisco NX-OS security commands that begin with D. SEC-141 deadtime deadtime To configure the dead-time interval for a RADIUS or TACACS+ server group, use the deadtime command.
VPN Connection through Zone based Firewall Router Configuration Example
 VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
Finding Feature Information
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
Access Control Lists and IP Fragments
 Access Control Lists and IP Fragments Document ID: 8014 Contents Introduction Types of ACL Entries ACL Rules Flowchart How Packets Can Match an ACL Example 1 Example 2 fragments Keyword Scenarios Scenario
Access Control Lists and IP Fragments Document ID: 8014 Contents Introduction Types of ACL Entries ACL Rules Flowchart How Packets Can Match an ACL Example 1 Example 2 fragments Keyword Scenarios Scenario
SE 4C03 Winter Final Examination Answer Key. Instructor: William M. Farmer
 SE 4C03 Winter 2003 Final Examination Answer Key Instructor: William M. Farmer (1) [2 pts.] Both the source and destination IP addresses are used to route IP datagrams. Is this statement true or false?
SE 4C03 Winter 2003 Final Examination Answer Key Instructor: William M. Farmer (1) [2 pts.] Both the source and destination IP addresses are used to route IP datagrams. Is this statement true or false?
A Commands CHAPTER. Commands that are identical to those documented in the Cisco IOS software documentation have been removed from this chapter.
 CHAPTER 1 The commands shown in this chapter apply to the Catalyst 8540 MSR, Catalyst 8510 MSR, and LightStream 1010 ATM switch routers. Where an entire command or certain attributes of a command have
CHAPTER 1 The commands shown in this chapter apply to the Catalyst 8540 MSR, Catalyst 8510 MSR, and LightStream 1010 ATM switch routers. Where an entire command or certain attributes of a command have
Chapter 4: Manipulating Routing
 : Manipulating Routing Updates CCNP ROUTE: Implementing IP Routing ROUTE v6 1 Objectives Describe network performance issues and ways to control routing updates and traffic (3). Describe the purpose of
: Manipulating Routing Updates CCNP ROUTE: Implementing IP Routing ROUTE v6 1 Objectives Describe network performance issues and ways to control routing updates and traffic (3). Describe the purpose of
Committed Access Rate
 Committed Access Rate Feature Summary The Committed Access Rate (CAR) feature performs the following functions: Limits the input or output transmission rate on an interface or subinterface based on a flexible
Committed Access Rate Feature Summary The Committed Access Rate (CAR) feature performs the following functions: Limits the input or output transmission rate on an interface or subinterface based on a flexible
GRE Tunnel with VRF Configuration Example
 GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
PRACTICAL ROUTERS and SWITCHES for ENGINEERS and TECHNICIANS
 PRACTICAL ROUTERS and SWITCHES for ENGINEERS and TECHNICIANS Objectives At the end of this workshop participants will: Be able to configure, maintain and manage routers have a clear practical understanding
PRACTICAL ROUTERS and SWITCHES for ENGINEERS and TECHNICIANS Objectives At the end of this workshop participants will: Be able to configure, maintain and manage routers have a clear practical understanding
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only.
 Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Study Guide. Using ACLs to Secure Networks
 CHAPTER 5 ACLs The Study Guide portion of this chapter uses a combination of matching, multiple-choice, and open-ended question exercises to test your knowledge of the various types of access control lists
CHAPTER 5 ACLs The Study Guide portion of this chapter uses a combination of matching, multiple-choice, and open-ended question exercises to test your knowledge of the various types of access control lists
CSC Network Security
 CSC 474 -- Security Topic 9. Firewalls CSC 474 Dr. Peng Ning 1 Outline Overview of Firewalls Filtering Firewalls Proxy Servers CSC 474 Dr. Peng Ning 2 Overview of Firewalls CSC 474 Dr. Peng Ning 3 1 Internet
CSC 474 -- Security Topic 9. Firewalls CSC 474 Dr. Peng Ning 1 Outline Overview of Firewalls Filtering Firewalls Proxy Servers CSC 474 Dr. Peng Ning 2 Overview of Firewalls CSC 474 Dr. Peng Ning 3 1 Internet
IPv4 ACLs, identified by ACL numbers, fall into four categories, as shown in Table 1. Table 1 IPv4 ACL categories
 Table of Contents ACL Configuration 1 ACL Overview 1 IPv4 ACL Classification 1 IPv4 ACL Rule Order 1 Rule Numbering Step with IPv4 ACLs 3 Effective Time Period of an IPv4 ACL 3 IP Fragments Filtering with
Table of Contents ACL Configuration 1 ACL Overview 1 IPv4 ACL Classification 1 IPv4 ACL Rule Order 1 Rule Numbering Step with IPv4 ACLs 3 Effective Time Period of an IPv4 ACL 3 IP Fragments Filtering with
How to Create an IP Access List to Filter IP Options TCP Flags Noncontiguous Ports or TTL Values,
 Creating an IP Access List to Filter IP Options TCP Flags Noncontiguous Ports or TTL Values This module describes how to use an IP access list to filter IP packets that contain certain IP Options, TCP
Creating an IP Access List to Filter IP Options TCP Flags Noncontiguous Ports or TTL Values This module describes how to use an IP access list to filter IP packets that contain certain IP Options, TCP
HP High-End Firewalls
 HP High-End Firewalls Access Control Configuration Guide Part number: 5998-2648 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
HP High-End Firewalls Access Control Configuration Guide Part number: 5998-2648 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
Chapter 7 Lab 7-2, Using the AS_PATH Attribute
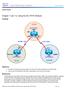 Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Aruba 8320 Configuring ACLs and Classifier Policies Guide for ArubaOS- CX 10.00
 Aruba 8320 Configuring ACLs and Classifier Policies Guide for ArubaOS- CX 10.00 Part Number: 5200-4710a Published: April 2018 Edition: 2 Copyright 2018 Hewlett Packard Enterprise Development LP Notices
Aruba 8320 Configuring ACLs and Classifier Policies Guide for ArubaOS- CX 10.00 Part Number: 5200-4710a Published: April 2018 Edition: 2 Copyright 2018 Hewlett Packard Enterprise Development LP Notices
Configuring NAT for IP Address Conservation
 Configuring NAT for IP Address Conservation Last Updated: November 29, 2012 This module describes how to configure Network Address Translation (NAT) for IP address conservation and configure inside and
Configuring NAT for IP Address Conservation Last Updated: November 29, 2012 This module describes how to configure Network Address Translation (NAT) for IP address conservation and configure inside and
