StoRM configuration. namespace.xml
|
|
|
- Stephen Hicks
- 5 years ago
- Views:
Transcription
1 StoRM configuration. namespace.xml 13 November 2007
2 Outline About this talk Mapping concepts Namespace concepts Namespace algorithms Namespace in practise
3 Mapping Concepts Mapping concepts Mapping The mapping functionality is the process of retrieving or building the transport URL (TURL) of a file addressed by a Site URL (SURL) and a grid user credential. The SURL is the logical identifier for a local data entity Data access and data transfer are made through the TURLs The TURL identify a physical location of a replica SRM services retrieve the TURL from a namespace database (like DPNS component in DPM) or build it through other mechanisms (like StoRM)
4 Mapping Concepts Mapping functionalities In StoRM, the mapping functionality is provided by the namespace component (NS). The Namespace component (NS) works without a database. The Namespace component is based on an XML configuration. It relies on the physical storage structure.
5 Namespace Component works without a database.. The basic features of the namespace component are: The configuration is modular and structured (representation is based on XML) The loading and the parsing of the configuration file occurs: at start-up of the back-end service when configuration file is modified An efficient structure of namespace configuration lives in memory. No access to disk or database is performed StoRM is different from the other solution, where typically, for every SRM request a query to the data base have to be done in order to establish the physical location of file and build the correct transfer URL.
6 Mapping parameters Namespace component exposes a simple interface to the other StoRM internal components. The namespace functions use parameters derived from the SRM requests, that are: the grid user credential (a subject or a service acting on behalf of the subject) the SURLs
7 Grid identity credentials Two credential types are supported and managed by Namespace Component: X.509 Distinguished Name (DN) Country Name (C), State (ST), Organization Name (O), Organizational Unit Name (OU), Locality Name (L), Common Name (CN) /C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Riccardo Zappi/ VOMS Fully Qualified Attribute Name /VO/group and Role currently the NS ignore capability and other VOMS attributes.
8 Simple form and Query form Two SURL types are supported by StoRM:
9 Namespace Component Model The Namespace Component is based on three main concepts: 1 NS-File system: is the representation of a Storage Area 2 Mapping rule: represents the basic rule for the mapping functionalities 3 Approachable rule: represents the coarse grain access control to the Storage Area.
10 NS-File system as Storage Area representation The storage area is a logical portion of storage assigned to a VO. In StoRM the SA is defined with NS-file system. The NS-File system contains: SA attributes: SSToken Description, Online Size, Retention Policy,... NS-File System specific attributes: Driver class, FS-Type, Authz-source,...
11 File system as Storage Area representation Storage Area could be shared by different VO. In the StoRM namespace model, this situation is represented with different NS-file system definition, one per VO.
12 Approachable rules Defines, in terms of user credential, which file systems can be approached. Access rules are expressed as regular expression by user DN and FQAN.
13 Approachable rules sample All users: < dn > < /dn > All user with VOMS credentials): < dn > < /dn > < vo name > < vo name > DN rules (all user named John): < dn > CN = John < /dn > VO rules (all users belonging to infngrid): < dn > < /dn > < vo name > infngrid < /vo name >
14 Mapping Rule The Mapping rule represents the relation between the StFN-Root part of the StFN and the NS-File system (addressed by FS-name attribute).
15 Namespace configuration elements High view of the namespace main elements. 1 File system 2 Mapping rule 3 Approachable rule
16 Namespace Algorithm Namespace mapping algorithm
17 Namespace Algorithm A mapping example
18 Namespace built by YAIM StoRM specific variables in YAIM The Namespace Component configuration file is the namespace.xml. During the YAIM configuration a basic namespace.xml is created. It reflects the storage configuration as specified by StoRM specific variables. To further details, please, wait the next session Hand-On where we will have a practical sample.
19 Namespace built by YAIM Adding a SA for a VO Site admin can modify the file namespace.xml created by YAIM for tuning and customization purposes. As generic rule, when you add a new support for a SA you have to add: 1 A NS-file system 2 The corresponding mapping rule, and 3 The corresponding approachable rule. Anyway, during the next session Hands-On we will see a practical example.
20 Notes and Summary StoRM team
Understanding StoRM: from introduction to internals
 Understanding StoRM: from introduction to internals 13 November 2007 Outline Storage Resource Manager The StoRM service StoRM components and internals Deployment configuration Authorization and ACLs Conclusions.
Understanding StoRM: from introduction to internals 13 November 2007 Outline Storage Resource Manager The StoRM service StoRM components and internals Deployment configuration Authorization and ACLs Conclusions.
Introduction to SRM. Riccardo Zappi 1
 Introduction to SRM Grid Storage Resource Manager Riccardo Zappi 1 1 INFN-CNAF, National Center of INFN (National Institute for Nuclear Physic) for Research and Development into the field of Information
Introduction to SRM Grid Storage Resource Manager Riccardo Zappi 1 1 INFN-CNAF, National Center of INFN (National Institute for Nuclear Physic) for Research and Development into the field of Information
Introduction Data Management Jan Just Keijser Nikhef Grid Tutorial, November 2008
 Introduction Data Management Jan Just Keijser Nikhef Grid Tutorial, 13-14 November 2008 Outline Introduction SRM Storage Elements in glite LCG File Catalog (LFC) Information System Grid Tutorial, 13-14
Introduction Data Management Jan Just Keijser Nikhef Grid Tutorial, 13-14 November 2008 Outline Introduction SRM Storage Elements in glite LCG File Catalog (LFC) Information System Grid Tutorial, 13-14
Introduction to LAN Introduction to TDC 363 Lecture 05 Course Outline What is NOS?
 Introduction to LAN TDC 363 Lecture 05 Nt Network rkoprti Operating Systems tm Windows Based Networking NetWare Based Networking Book Reading: Chapters 8 1 Course Outline Network operating system (NOS)
Introduction to LAN TDC 363 Lecture 05 Nt Network rkoprti Operating Systems tm Windows Based Networking NetWare Based Networking Book Reading: Chapters 8 1 Course Outline Network operating system (NOS)
glite Grid Services Overview
 The EPIKH Project (Exchange Programme to advance e-infrastructure Know-How) glite Grid Services Overview Antonio Calanducci INFN Catania Joint GISELA/EPIKH School for Grid Site Administrators Valparaiso,
The EPIKH Project (Exchange Programme to advance e-infrastructure Know-How) glite Grid Services Overview Antonio Calanducci INFN Catania Joint GISELA/EPIKH School for Grid Site Administrators Valparaiso,
Best practices and recommendations for attribute translation from federated authentication to X.509 credentials
 Best practices and recommendations for attribute translation from federated authentication to X.509 credentials Published Date: 13-06-2017 Revision: 1.0 Work Package: Document Code: Document URL: JRA1
Best practices and recommendations for attribute translation from federated authentication to X.509 credentials Published Date: 13-06-2017 Revision: 1.0 Work Package: Document Code: Document URL: JRA1
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
Configuring Microsoft ADAM
 Proven Practice Configuring Microsoft ADAM Product(s): IBM Cognos Series 7 Area of Interest: Security Configuring Microsoft ADAM 2 Copyright Copyright 2008 Cognos ULC (formerly Cognos Incorporated). Cognos
Proven Practice Configuring Microsoft ADAM Product(s): IBM Cognos Series 7 Area of Interest: Security Configuring Microsoft ADAM 2 Copyright Copyright 2008 Cognos ULC (formerly Cognos Incorporated). Cognos
The glite middleware. Presented by John White EGEE-II JRA1 Dep. Manager On behalf of JRA1 Enabling Grids for E-sciencE
 The glite middleware Presented by John White EGEE-II JRA1 Dep. Manager On behalf of JRA1 John.White@cern.ch www.eu-egee.org EGEE and glite are registered trademarks Outline glite distributions Software
The glite middleware Presented by John White EGEE-II JRA1 Dep. Manager On behalf of JRA1 John.White@cern.ch www.eu-egee.org EGEE and glite are registered trademarks Outline glite distributions Software
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
A scalable storage element and its usage in HEP
 AstroGrid D Meeting at MPE 14 15. November 2006 Garching dcache A scalable storage element and its usage in HEP Martin Radicke Patrick Fuhrmann Introduction to dcache 2 Project overview joint venture between
AstroGrid D Meeting at MPE 14 15. November 2006 Garching dcache A scalable storage element and its usage in HEP Martin Radicke Patrick Fuhrmann Introduction to dcache 2 Project overview joint venture between
Automating Administration with Windows PowerShell 2.0
 Automating Administration with Windows PowerShell 2.0 Course No. 10325 5 Days Instructor-led, Hands-on Introduction This course provides students with the knowledge and skills to utilize Windows PowerShell
Automating Administration with Windows PowerShell 2.0 Course No. 10325 5 Days Instructor-led, Hands-on Introduction This course provides students with the knowledge and skills to utilize Windows PowerShell
Cisco Expressway Authenticating Accounts Using LDAP
 Cisco Expressway Authenticating Accounts Using LDAP Deployment Guide Cisco Expressway X8.5 December 2014 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration 4
Cisco Expressway Authenticating Accounts Using LDAP Deployment Guide Cisco Expressway X8.5 December 2014 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration 4
Cisco TelePresence Authenticating Cisco VCS Accounts Using LDAP
 Cisco TelePresence Authenticating Cisco VCS Accounts Using LDAP Deployment Guide Cisco VCS X8.2 D14465.07 June 2014 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration
Cisco TelePresence Authenticating Cisco VCS Accounts Using LDAP Deployment Guide Cisco VCS X8.2 D14465.07 June 2014 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration
An XACML Attribute and Obligation Profile for Authorization Interoperability in Grids
 GWD-C Federated Security fed-sec@ogf.org Rachana Ananthakrishnan, Argonne National Laboratory Gabriele Garzoglio, Fermilab Oscar Koeroo, Nikhef March 11, 2012 Protocol version 1.2 An XACML Attribute and
GWD-C Federated Security fed-sec@ogf.org Rachana Ananthakrishnan, Argonne National Laboratory Gabriele Garzoglio, Fermilab Oscar Koeroo, Nikhef March 11, 2012 Protocol version 1.2 An XACML Attribute and
User Management in Resource Manager
 CHAPTER 8 This section describes how to manage user profiles. Topics in this section include: Overview of User Management, page 8-1 Using User Management, page 8-1 Overview of User Management In Resource
CHAPTER 8 This section describes how to manage user profiles. Topics in this section include: Overview of User Management, page 8-1 Using User Management, page 8-1 Overview of User Management In Resource
YAIM Overview. Bruce Becker Meraka Institute. Co-ordination & Harmonisation of Advanced e-infrastructures for Research and Education Data Sharing
 Co-ordination & Harmonisation of Advanced e-infrastructures for Research and Education Data Sharing Research Infrastructures Grant Agreement n. 306819 YAIM Overview Bruce Becker Meraka Institute Outline
Co-ordination & Harmonisation of Advanced e-infrastructures for Research and Education Data Sharing Research Infrastructures Grant Agreement n. 306819 YAIM Overview Bruce Becker Meraka Institute Outline
DIRAC distributed secure framework
 Journal of Physics: Conference Series DIRAC distributed secure framework To cite this article: A Casajus et al 2010 J. Phys.: Conf. Ser. 219 042033 View the article online for updates and enhancements.
Journal of Physics: Conference Series DIRAC distributed secure framework To cite this article: A Casajus et al 2010 J. Phys.: Conf. Ser. 219 042033 View the article online for updates and enhancements.
An XACML Attribute and Obligation Profile for Authorization Interoperability in Grids
 GWD-CP.205 Federated Security fedsec-cg@ogf.org Rachana Ananthakrishnan, Argonne National Laboratory Gabriele Garzoglio *, Fermilab Oscar Koeroo *, Nikhef January 21, 2013 Protocol version 1.2 An XACML
GWD-CP.205 Federated Security fedsec-cg@ogf.org Rachana Ananthakrishnan, Argonne National Laboratory Gabriele Garzoglio *, Fermilab Oscar Koeroo *, Nikhef January 21, 2013 Protocol version 1.2 An XACML
Scientific data management
 Scientific data management Storage and data management components Application database Certificate Certificate Authorised users directory Certificate Certificate Researcher Certificate Policies Information
Scientific data management Storage and data management components Application database Certificate Certificate Authorised users directory Certificate Certificate Researcher Certificate Policies Information
Active Directory. Learning Objective. Active Directory
 (March 0, 2016) Abdou Illia, Spring 2016 1 Learning Objective Use concepts Namespace DNS Global Catalog Schema Class Tree Forest Organizational Units 2 AD = A Central Database on a Domain Controller for
(March 0, 2016) Abdou Illia, Spring 2016 1 Learning Objective Use concepts Namespace DNS Global Catalog Schema Class Tree Forest Organizational Units 2 AD = A Central Database on a Domain Controller for
Authentication via Active Directory and LDAP
 Authentication via Active Directory and LDAP Overview The LDAP and Active Directory authenticators available in Datameer provide remote authentication services for Datameer users. Administrators can configure
Authentication via Active Directory and LDAP Overview The LDAP and Active Directory authenticators available in Datameer provide remote authentication services for Datameer users. Administrators can configure
SPINOSO Vincenzo. Optimization of the job submission and data access in a LHC Tier2
 EGI User Forum Vilnius, 11-14 April 2011 SPINOSO Vincenzo Optimization of the job submission and data access in a LHC Tier2 Overview User needs Administration issues INFN Bari farm design and deployment
EGI User Forum Vilnius, 11-14 April 2011 SPINOSO Vincenzo Optimization of the job submission and data access in a LHC Tier2 Overview User needs Administration issues INFN Bari farm design and deployment
Edinburgh (ECDF) Update
 Edinburgh (ECDF) Update Wahid Bhimji On behalf of the ECDF Team HepSysMan,10 th June 2010 Edinburgh Setup Hardware upgrades Progress in last year Current Issues June-10 Hepsysman Wahid Bhimji - ECDF 1
Edinburgh (ECDF) Update Wahid Bhimji On behalf of the ECDF Team HepSysMan,10 th June 2010 Edinburgh Setup Hardware upgrades Progress in last year Current Issues June-10 Hepsysman Wahid Bhimji - ECDF 1
SAS Viya 3.4 Administration: Logging
 SAS Viya 3.4 Administration: Logging Logging: Overview............................................................................. 1 Logging: How To...............................................................................
SAS Viya 3.4 Administration: Logging Logging: Overview............................................................................. 1 Logging: How To...............................................................................
Administration Guide
 Administration Guide Version 2.0 November, 2015 Biscom, Inc. 321 Billerica Rd. Chelmsford, MA 01824 tel 978-250-1800 fax 978-250-4449 CONTENTS 1. Initial Configuration and Settings...1 1.1 Application...
Administration Guide Version 2.0 November, 2015 Biscom, Inc. 321 Billerica Rd. Chelmsford, MA 01824 tel 978-250-1800 fax 978-250-4449 CONTENTS 1. Initial Configuration and Settings...1 1.1 Application...
[GSoC Proposal] Securing Airavata API
![[GSoC Proposal] Securing Airavata API [GSoC Proposal] Securing Airavata API](/thumbs/93/113254568.jpg) [GSoC Proposal] Securing Airavata API TITLE: Securing AIRAVATA API ABSTRACT: The goal of this project is to design and implement the solution for securing AIRAVATA API. Particularly, this includes authenticating
[GSoC Proposal] Securing Airavata API TITLE: Securing AIRAVATA API ABSTRACT: The goal of this project is to design and implement the solution for securing AIRAVATA API. Particularly, this includes authenticating
Proxy POP3S. then authentication occurs. POP3S is for a receiving . IMAP4S. and then authentication occurs. SMTPS is for sending .
 Email proxies extend remote email capability to users of Clientless SSL VPN. When users attempt an email session via email proxy, the email client establishes a tunnel using the SSL protocol. The email
Email proxies extend remote email capability to users of Clientless SSL VPN. When users attempt an email session via email proxy, the email client establishes a tunnel using the SSL protocol. The email
Smart Grid Security. Selected Principles and Components. Tony Metke Distinguished Member of the Technical Staff
 Smart Grid Security Selected Principles and Components Tony Metke Distinguished Member of the Technical Staff IEEE PES Conference on Innovative Smart Grid Technologies Jan 2010 Based on a paper by: Anthony
Smart Grid Security Selected Principles and Components Tony Metke Distinguished Member of the Technical Staff IEEE PES Conference on Innovative Smart Grid Technologies Jan 2010 Based on a paper by: Anthony
Grid Authentication and Authorisation Issues. Ákos Frohner at CERN
 Grid Authentication and Authorisation Issues Ákos Frohner at CERN Overview Setting the scene: requirements Old style authorisation: DN based gridmap-files Overview of the EDG components VO user management:
Grid Authentication and Authorisation Issues Ákos Frohner at CERN Overview Setting the scene: requirements Old style authorisation: DN based gridmap-files Overview of the EDG components VO user management:
MCSE Server Infrastructure. This Training Program prepares and enables learners to Pass Microsoft MCSE: Server Infrastructure exams
 MCSE Server Infrastructure This Training Program prepares and enables learners to Pass Microsoft MCSE: Server Infrastructure exams 1. MCSE: Server Infrastructure / Exam 70-413 (Designing and Implementing
MCSE Server Infrastructure This Training Program prepares and enables learners to Pass Microsoft MCSE: Server Infrastructure exams 1. MCSE: Server Infrastructure / Exam 70-413 (Designing and Implementing
NETWRIX PASSWORD EXPIRATION NOTIFIER
 NETWRIX PASSWORD EXPIRATION NOTIFIER ADMINISTRATOR S GUIDE Product Version: 3.3 January 2013 Legal Notice The information in this publication is furnished for information use only, and does not constitute
NETWRIX PASSWORD EXPIRATION NOTIFIER ADMINISTRATOR S GUIDE Product Version: 3.3 January 2013 Legal Notice The information in this publication is furnished for information use only, and does not constitute
CA IdentityMinder. Glossary
 CA IdentityMinder Glossary 12.6.3 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is for your informational
CA IdentityMinder Glossary 12.6.3 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is for your informational
SA1 CILogon pilot - motivation and setup
 SA1 CILogon pilot - motivation and setup Tamas Balogh & Mischa Sallé tamasb@nikhef.nl msalle@nikhef.nl AARC General Meeting, Milan 4 November 2015 Tamas Balogh & Mischa Sallé (Nikhef) 1 / 11 Outline 1
SA1 CILogon pilot - motivation and setup Tamas Balogh & Mischa Sallé tamasb@nikhef.nl msalle@nikhef.nl AARC General Meeting, Milan 4 November 2015 Tamas Balogh & Mischa Sallé (Nikhef) 1 / 11 Outline 1
Active Directory Replicationm
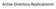 Active Directory Replicationm Site 1 Read/Write copy of Active Directory Database Ntds.dit Site 1 C D All domain controllers host a full replica of the domain information for its own domain Replication:
Active Directory Replicationm Site 1 Read/Write copy of Active Directory Database Ntds.dit Site 1 C D All domain controllers host a full replica of the domain information for its own domain Replication:
CLI users are not listed on the Cisco Prime Collaboration User Management page.
 Cisco Prime Collaboration supports creation of user roles. A user can be assigned the Super Administrator role. A Super Administrator can perform tasks that both system administrator and network administrator
Cisco Prime Collaboration supports creation of user roles. A user can be assigned the Super Administrator role. A Super Administrator can perform tasks that both system administrator and network administrator
Authenticating Cisco VCS accounts using LDAP
 Authenticating Cisco VCS accounts using LDAP Cisco TelePresence Deployment Guide Cisco VCS X6 D14526.04 February 2011 Contents Contents Document revision history... 3 Introduction... 4 Usage... 4 Cisco
Authenticating Cisco VCS accounts using LDAP Cisco TelePresence Deployment Guide Cisco VCS X6 D14526.04 February 2011 Contents Contents Document revision history... 3 Introduction... 4 Usage... 4 Cisco
Architecture Proposal
 Nordic Testbed for Wide Area Computing and Data Handling NORDUGRID-TECH-1 19/02/2002 Architecture Proposal M.Ellert, A.Konstantinov, B.Kónya, O.Smirnova, A.Wäänänen Introduction The document describes
Nordic Testbed for Wide Area Computing and Data Handling NORDUGRID-TECH-1 19/02/2002 Architecture Proposal M.Ellert, A.Konstantinov, B.Kónya, O.Smirnova, A.Wäänänen Introduction The document describes
EGEE and Interoperation
 EGEE and Interoperation Laurence Field CERN-IT-GD ISGC 2008 www.eu-egee.org EGEE and glite are registered trademarks Overview The grid problem definition GLite and EGEE The interoperability problem The
EGEE and Interoperation Laurence Field CERN-IT-GD ISGC 2008 www.eu-egee.org EGEE and glite are registered trademarks Overview The grid problem definition GLite and EGEE The interoperability problem The
Configuring a Virtual-Domain Server with LDAP
 This document provides a recipe for configuring a Mirapoint server to perform LDAP authentication, message routing, and email access proxying. Configuration requires two activities: LDAP Database User
This document provides a recipe for configuring a Mirapoint server to perform LDAP authentication, message routing, and email access proxying. Configuration requires two activities: LDAP Database User
Simplifying Wide-Area Application Development with WheelFS
 Simplifying Wide-Area Application Development with WheelFS Jeremy Stribling In collaboration with Jinyang Li, Frans Kaashoek, Robert Morris MIT CSAIL & New York University Resources Spread over Wide-Area
Simplifying Wide-Area Application Development with WheelFS Jeremy Stribling In collaboration with Jinyang Li, Frans Kaashoek, Robert Morris MIT CSAIL & New York University Resources Spread over Wide-Area
30 Nov Dec Advanced School in High Performance and GRID Computing Concepts and Applications, ICTP, Trieste, Italy
 Advanced School in High Performance and GRID Computing Concepts and Applications, ICTP, Trieste, Italy Why the Grid? Science is becoming increasingly digital and needs to deal with increasing amounts of
Advanced School in High Performance and GRID Computing Concepts and Applications, ICTP, Trieste, Italy Why the Grid? Science is becoming increasingly digital and needs to deal with increasing amounts of
Information Network Systems The application layer. Stephan Sigg
 Information Network Systems The application layer Stephan Sigg Tokyo, November 15, 2012 Introduction 04.10.2012 Introduction to the internet 11.10.2012 The link layer 18.10.2012 The network layer 25.10.2012
Information Network Systems The application layer Stephan Sigg Tokyo, November 15, 2012 Introduction 04.10.2012 Introduction to the internet 11.10.2012 The link layer 18.10.2012 The network layer 25.10.2012
Argus: The Simplified Policy Language
 Argus: The Simplified Policy Language Andrea Ceccanti INFN-CNAF andrea.ceccanti@cnaf.infn.it EGEE 09 September 2009, Barcelona www.eu-egee.org EGEE and glite are registered trademarks Argus High level
Argus: The Simplified Policy Language Andrea Ceccanti INFN-CNAF andrea.ceccanti@cnaf.infn.it EGEE 09 September 2009, Barcelona www.eu-egee.org EGEE and glite are registered trademarks Argus High level
I Tier-3 di CMS-Italia: stato e prospettive. Hassen Riahi Claudio Grandi Workshop CCR GRID 2011
 I Tier-3 di CMS-Italia: stato e prospettive Claudio Grandi Workshop CCR GRID 2011 Outline INFN Perugia Tier-3 R&D Computing centre: activities, storage and batch system CMS services: bottlenecks and workarounds
I Tier-3 di CMS-Italia: stato e prospettive Claudio Grandi Workshop CCR GRID 2011 Outline INFN Perugia Tier-3 R&D Computing centre: activities, storage and batch system CMS services: bottlenecks and workarounds
INDIGO AAI An overview and status update!
 RIA-653549 INDIGO DataCloud INDIGO AAI An overview and status update! Andrea Ceccanti (INFN) on behalf of the INDIGO AAI Task Force! indigo-aai-tf@lists.indigo-datacloud.org INDIGO Datacloud An H2020 project
RIA-653549 INDIGO DataCloud INDIGO AAI An overview and status update! Andrea Ceccanti (INFN) on behalf of the INDIGO AAI Task Force! indigo-aai-tf@lists.indigo-datacloud.org INDIGO Datacloud An H2020 project
Configuring SAML-based Single Sign-on for Informatica Web Applications
 Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
Create OData API for Use With Salesforce Connect
 Create OData API for Use With Salesforce Connect The following steps describe how to set up and configure Jitterbit LIVE API Platform to expose data in an easy to consume, secure form so that Salesforce
Create OData API for Use With Salesforce Connect The following steps describe how to set up and configure Jitterbit LIVE API Platform to expose data in an easy to consume, secure form so that Salesforce
MCSE- Windows Server 2012
 COURSE CONTENT MCSE- Windows Server 2012 Course 20413C: Designing and Implementing a Server Infrastructure 1. Planning Server Upgrade and Migration Considerations for Upgrades and Migrations Creating a
COURSE CONTENT MCSE- Windows Server 2012 Course 20413C: Designing and Implementing a Server Infrastructure 1. Planning Server Upgrade and Migration Considerations for Upgrades and Migrations Creating a
Public Key Enabling Oracle Weblogic Server
 DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
UNIT I. A protocol is a precise set of rules defining how components communicate, the format of addresses, how data is split into packets
 UNIT I Web Essentials: Clients, Servers, and Communication. The Internet- Basic Internet Protocols -The World Wide Web-HTTP request message-response message- Web Clients Web Servers-Case Study. Markup
UNIT I Web Essentials: Clients, Servers, and Communication. The Internet- Basic Internet Protocols -The World Wide Web-HTTP request message-response message- Web Clients Web Servers-Case Study. Markup
Novell Access Manager
 Quick Start AUTHORIZED DOCUMENTATION Novell Access Manager 3.1 SP2 June 11, 2010 www.novell.com Novell Access Manager 3.1 SP2 Quick Start Legal Notices Novell, Inc., makes no representations or warranties
Quick Start AUTHORIZED DOCUMENTATION Novell Access Manager 3.1 SP2 June 11, 2010 www.novell.com Novell Access Manager 3.1 SP2 Quick Start Legal Notices Novell, Inc., makes no representations or warranties
Configuring Ambari Authentication with LDAP/AD
 3 Configuring Ambari Authentication with LDAP/AD Date of Publish: 2018-07-15 http://docs.hortonworks.com Contents Configuring Ambari Authentication for LDAP/AD... 3 Configuring Ambari to authenticate external
3 Configuring Ambari Authentication with LDAP/AD Date of Publish: 2018-07-15 http://docs.hortonworks.com Contents Configuring Ambari Authentication for LDAP/AD... 3 Configuring Ambari to authenticate external
Enabling Semantic Web Programming by Integrating RDF and Common Lisp
 Enabling Semantic Web Programming by Integrating RDF and Common Lisp An Introduction to NRC s Wilbur RDF & DAML Toolkit Ora Lassila Nokia Research Center July 2001 Common Lisp & Frame Systems Traditional
Enabling Semantic Web Programming by Integrating RDF and Common Lisp An Introduction to NRC s Wilbur RDF & DAML Toolkit Ora Lassila Nokia Research Center July 2001 Common Lisp & Frame Systems Traditional
Using an LDAP With ActiveWorkflow
 Table of contents 1 Groups...2 2 People...2 3 Authentication...3 4 Directory Service... 4 4.1 Connection Properties... 5 4.2 User Retrieval Properties...6 4.3 User Attribute Properties...7 4.4 Group Retrieval
Table of contents 1 Groups...2 2 People...2 3 Authentication...3 4 Directory Service... 4 4.1 Connection Properties... 5 4.2 User Retrieval Properties...6 4.3 User Attribute Properties...7 4.4 Group Retrieval
Data Management. Enabling Grids for E-sciencE. Vladimir Slavnic Scientific Computing Laboratory Institute of Physics Belgrade, Serbia
 Data Management Vladimir Slavnic slavnic@scl.rs Scientific Computing Laboratory Institute of Physics Belgrade, Serbia Academic and Educational Grid Initiative of Serbia Feb. 19, 2009 A E G I S www.eu-egee.org
Data Management Vladimir Slavnic slavnic@scl.rs Scientific Computing Laboratory Institute of Physics Belgrade, Serbia Academic and Educational Grid Initiative of Serbia Feb. 19, 2009 A E G I S www.eu-egee.org
NETCONF Client GUI. Client Application Files APPENDIX
 APPENDIX B The NETCONF client is a simple GUI client application that can be used to understand the implementation of the NETCONF protocol in Cisco E-DI. This appendix includes the following information:
APPENDIX B The NETCONF client is a simple GUI client application that can be used to understand the implementation of the NETCONF protocol in Cisco E-DI. This appendix includes the following information:
OLAP Drill-through Table Considerations
 Paper 023-2014 OLAP Drill-through Table Considerations M. Michelle Buchecker, SAS Institute, Inc. ABSTRACT When creating an OLAP cube, you have the option of specifying a drill-through table, also known
Paper 023-2014 OLAP Drill-through Table Considerations M. Michelle Buchecker, SAS Institute, Inc. ABSTRACT When creating an OLAP cube, you have the option of specifying a drill-through table, also known
Configuring Ambari Authentication with LDAP/AD
 3 Date of Publish: 2018-07-15 http://docs.hortonworks.com Contents Configuring Ambari Authentication for LDAP/AD... 3 Configuring Ambari to authenticate external users... 3 Preparing for LDAPS integration...
3 Date of Publish: 2018-07-15 http://docs.hortonworks.com Contents Configuring Ambari Authentication for LDAP/AD... 3 Configuring Ambari to authenticate external users... 3 Preparing for LDAPS integration...
Getting Started with FPM BOPF Integration (FBI)
 Summary Creating a List GUIBB with a Related View Level of complexity: Time required for completion: Beginner 45 min. Author: Sharon Dassa Company: SAP AG Created on: 20 February 2013 www.sap.com Table
Summary Creating a List GUIBB with a Related View Level of complexity: Time required for completion: Beginner 45 min. Author: Sharon Dassa Company: SAP AG Created on: 20 February 2013 www.sap.com Table
DIRAC Distributed Secure Framework
 DIRAC Distributed Secure Framework A Casajus Universitat de Barcelona E-mail: adria@ecm.ub.es R Graciani Universitat de Barcelona E-mail: graciani@ecm.ub.es on behalf of the LHCb DIRAC Team Abstract. DIRAC,
DIRAC Distributed Secure Framework A Casajus Universitat de Barcelona E-mail: adria@ecm.ub.es R Graciani Universitat de Barcelona E-mail: graciani@ecm.ub.es on behalf of the LHCb DIRAC Team Abstract. DIRAC,
EMI Deployment Planning. C. Aiftimiei D. Dongiovanni INFN
 EMI Deployment Planning C. Aiftimiei D. Dongiovanni INFN Outline Migrating to EMI: WHY What's new: EMI Overview Products, Platforms, Repos, Dependencies, Support / Release Cycle Migrating to EMI: HOW Admin
EMI Deployment Planning C. Aiftimiei D. Dongiovanni INFN Outline Migrating to EMI: WHY What's new: EMI Overview Products, Platforms, Repos, Dependencies, Support / Release Cycle Migrating to EMI: HOW Admin
Infoblox VMware vrealize Log Insight Content Pack User Manual Version 1.1
 Infoblox VMware vrealize Log Insight Content Pack User Manual Version 1.1 Release History S# Version Date History 1 1.0 14 May 2015 Initial Version 2 1.1 15 May 2015 IPAM, DHCP and DNS Dashboard changes
Infoblox VMware vrealize Log Insight Content Pack User Manual Version 1.1 Release History S# Version Date History 1 1.0 14 May 2015 Initial Version 2 1.1 15 May 2015 IPAM, DHCP and DNS Dashboard changes
Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ]
![Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ] Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ]](/thumbs/84/90603673.jpg) s@lm@n Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ] Question No : 1 You install Microsoft Dynamics CRM on-premises. The Microsoft Dynamics CRM environment
s@lm@n Microsoft Exam MB2-702 Microsoft Dynamics CRM 2013 Deployment Version: 6.1 [ Total Questions: 90 ] Question No : 1 You install Microsoft Dynamics CRM on-premises. The Microsoft Dynamics CRM environment
ACS 5.x: LDAP Server Configuration Example
 ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
Computer Networks.. By Nidhi Jindal
 Computer Networks APPLICATION LAYER: DNS. By Nidhi Jindal INTRODUCTION A user of an e mail program may know the e mail address of the recipient; however, the IP protocol needs the IP address. The DOMAIN
Computer Networks APPLICATION LAYER: DNS. By Nidhi Jindal INTRODUCTION A user of an e mail program may know the e mail address of the recipient; however, the IP protocol needs the IP address. The DOMAIN
Enterprise Manager: Scalable Oracle Management
 Session id:xxxxx Enterprise Manager: Scalable Oracle John Kennedy System Products, Server Technologies, Oracle Corporation Enterprise Manager 10G Database Oracle World 2003 Agenda Enterprise Manager 10G
Session id:xxxxx Enterprise Manager: Scalable Oracle John Kennedy System Products, Server Technologies, Oracle Corporation Enterprise Manager 10G Database Oracle World 2003 Agenda Enterprise Manager 10G
glideinwms architecture by Igor Sfiligoi, Jeff Dost (UCSD)
 glideinwms architecture by Igor Sfiligoi, Jeff Dost (UCSD) Outline A high level overview of the glideinwms Description of the components 2 glideinwms from 10k feet 3 Refresher - HTCondor A Condor pool
glideinwms architecture by Igor Sfiligoi, Jeff Dost (UCSD) Outline A high level overview of the glideinwms Description of the components 2 glideinwms from 10k feet 3 Refresher - HTCondor A Condor pool
New Topic: Naming. Differences in naming in distributed and non-distributed systems. How to name mobile entities?
 New Topic: Naming Names are used to share resources, uniquely identify entities and refer to locations Need to map from name to the entity it refers to E.g., Browser access to www.cnn.com Use name resolution
New Topic: Naming Names are used to share resources, uniquely identify entities and refer to locations Need to map from name to the entity it refers to E.g., Browser access to www.cnn.com Use name resolution
Windows Server 2008 Administration
 Hands-On Course Description This course provides hands on experience installing and configuring Windows Server 2008 to work with clients including Windows Vista. Students will perform full and core CD-based
Hands-On Course Description This course provides hands on experience installing and configuring Windows Server 2008 to work with clients including Windows Vista. Students will perform full and core CD-based
Certificate Management
 Certificate Management This guide provides information on...... Configuring the NotifyMDM server to use a Microsoft Active Directory Certificate Authority... Using Certificates from Outside Sources...
Certificate Management This guide provides information on...... Configuring the NotifyMDM server to use a Microsoft Active Directory Certificate Authority... Using Certificates from Outside Sources...
CLI users are not listed on the Cisco Prime Collaboration User Management page.
 Cisco Prime Collaboration supports creation of user roles. A user can be assigned the Super Administrator role. A Super Administrator can perform tasks that both system administrator and network administrator
Cisco Prime Collaboration supports creation of user roles. A user can be assigned the Super Administrator role. A Super Administrator can perform tasks that both system administrator and network administrator
Increasing Performance for PowerCenter Sessions that Use Partitions
 Increasing Performance for PowerCenter Sessions that Use Partitions 1993-2015 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying,
Increasing Performance for PowerCenter Sessions that Use Partitions 1993-2015 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying,
EUROPEAN MIDDLEWARE INITIATIVE
 EUROPEAN MIDDLEWARE INITIATIVE VOMS CORE AND WMS SECURITY ASSESSMENT EMI DOCUMENT Document identifier: EMI-DOC-SA2- VOMS_WMS_Security_Assessment_v1.0.doc Activity: Lead Partner: Document status: Document
EUROPEAN MIDDLEWARE INITIATIVE VOMS CORE AND WMS SECURITY ASSESSMENT EMI DOCUMENT Document identifier: EMI-DOC-SA2- VOMS_WMS_Security_Assessment_v1.0.doc Activity: Lead Partner: Document status: Document
Novell Identity Manager
 Role Mapping Administrator User Guide AUTHORIZED DOCUMENTATION Novell Identity Manager 1.0 August 28, 2009 www.novell.com Novell Identity Manager Role Mapping Administrator 1.0 User GuideNovell Identity
Role Mapping Administrator User Guide AUTHORIZED DOCUMENTATION Novell Identity Manager 1.0 August 28, 2009 www.novell.com Novell Identity Manager Role Mapping Administrator 1.0 User GuideNovell Identity
Realms and Identity Policies
 The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 14 Create an Identity Rule, page 15 Manage a Realm, page 17 Manage an Identity
The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 14 Create an Identity Rule, page 15 Manage a Realm, page 17 Manage an Identity
PxM Proof of Concept Configuration. June 2018 Version 3.1
 PxM Proof of Concept Configuration June 2018 Version 3.1 Table of Contents PxM Architecture, Installation & Configuration... 3 PxM Proof of Concept (POC) Guide... 4 Introduction... 4 Prerequisites... 4
PxM Proof of Concept Configuration June 2018 Version 3.1 Table of Contents PxM Architecture, Installation & Configuration... 3 PxM Proof of Concept (POC) Guide... 4 Introduction... 4 Prerequisites... 4
How to configure Sophos for all other clients
 How to configure Sophos Email for all other clients 1. Add Your Domain & Verify Ownership 2. Add Mailboxes to Sophos Email 3. Restrict Delivery to Sophos IP Addresses 4. Modify MX records to point to Sophos
How to configure Sophos Email for all other clients 1. Add Your Domain & Verify Ownership 2. Add Mailboxes to Sophos Email 3. Restrict Delivery to Sophos IP Addresses 4. Modify MX records to point to Sophos
Grid Data Management
 Grid Data Management Data Management Distributed community of users need to access and analyze large amounts of data Fusion community s International ITER project Requirement arises in both simulation
Grid Data Management Data Management Distributed community of users need to access and analyze large amounts of data Fusion community s International ITER project Requirement arises in both simulation
Introduction to SciTokens
 Introduction to SciTokens Brian Bockelman, On Behalf of the SciTokens Team https://scitokens.org This material is based upon work supported by the National Science Foundation under Grant No. 1738962. Any
Introduction to SciTokens Brian Bockelman, On Behalf of the SciTokens Team https://scitokens.org This material is based upon work supported by the National Science Foundation under Grant No. 1738962. Any
Web Services for Integrated Management: a Case Study
 Web Services for Integrated Management: a Case Study Jean-Philippe Martin-Flatin, CERN, Switzerland Pierre-Alain Doffoel, ESCP-EAP, France Mario Jeckle, University of Applied Sciences Furtwangen, Germany
Web Services for Integrated Management: a Case Study Jean-Philippe Martin-Flatin, CERN, Switzerland Pierre-Alain Doffoel, ESCP-EAP, France Mario Jeckle, University of Applied Sciences Furtwangen, Germany
RSA NetWitness Platform
 RSA NetWitness Platform Event Source Log Configuration Guide Sophos UTM Last Modified: Wednesday, October 10, 2018 Event Source Product Information: Vendor: Sophos Event Source: UTM Version: 9.x, 17.x
RSA NetWitness Platform Event Source Log Configuration Guide Sophos UTM Last Modified: Wednesday, October 10, 2018 Event Source Product Information: Vendor: Sophos Event Source: UTM Version: 9.x, 17.x
BIG-IQ Centralized Management: Licensing and Initial Setup. Version 5.0
 BIG-IQ Centralized Management: Licensing and Initial Setup Version 5.0 Table of Contents Table of Contents BIG-IQ System Introduction...5 About BIG-IQ System Management...5 About secure communication
BIG-IQ Centralized Management: Licensing and Initial Setup Version 5.0 Table of Contents Table of Contents BIG-IQ System Introduction...5 About BIG-IQ System Management...5 About secure communication
CS 3201 Computer Networks 2014/2015 Handout: Lab 4
 CS 3201 Computer Networks 2014/2015 Handout: Lab 4 Lab Content: - IP Addressing - IP Ports TCP/IP Fundamentals TCP/IP Settings - TCP/IP is a protocol that requires a little bit of knowledge to configure
CS 3201 Computer Networks 2014/2015 Handout: Lab 4 Lab Content: - IP Addressing - IP Ports TCP/IP Fundamentals TCP/IP Settings - TCP/IP is a protocol that requires a little bit of knowledge to configure
ADFS Authentication and Configuration January 2017
 ADFS Authentication and Configuration January 2017 International Corporation 1 Table of Contents Introduction... 2 Changelog for Configure Active Directory Synchronization... 3 2.1. Changes in Configure
ADFS Authentication and Configuration January 2017 International Corporation 1 Table of Contents Introduction... 2 Changelog for Configure Active Directory Synchronization... 3 2.1. Changes in Configure
and the GridKa mass storage system Jos van Wezel / GridKa
 and the GridKa mass storage system / GridKa [Tape TSM] staging server 2 Introduction Grid storage and storage middleware dcache h and TSS TSS internals Conclusion and further work 3 FZK/GridKa The GridKa
and the GridKa mass storage system / GridKa [Tape TSM] staging server 2 Introduction Grid storage and storage middleware dcache h and TSS TSS internals Conclusion and further work 3 FZK/GridKa The GridKa
Progress in building the International Lattice Data Grid
 Progress in building the International Lattice Data Grid Jefferson Lab, Newport News, VA 23606, USA E-mail: bjoo@jlab.org C.M. Maynard EPCC, School of Physics, Univeristy of Edinburgh, Edinburgh EH9 3JZ,
Progress in building the International Lattice Data Grid Jefferson Lab, Newport News, VA 23606, USA E-mail: bjoo@jlab.org C.M. Maynard EPCC, School of Physics, Univeristy of Edinburgh, Edinburgh EH9 3JZ,
Fundamentals of edirectory
 Warren E. Wyrostek, M.Ed., M.Div., MCNI, MCNE, CDE Fundamentals of edirectory Author: Novell NetWare 6.5 CNA Exam Cram2 http://www.3wscertification.com wyrostekw@msn.com Basics Fundamentals of edirectory
Warren E. Wyrostek, M.Ed., M.Div., MCNI, MCNE, CDE Fundamentals of edirectory Author: Novell NetWare 6.5 CNA Exam Cram2 http://www.3wscertification.com wyrostekw@msn.com Basics Fundamentals of edirectory
StorageGRID Webscale 11.0 Tenant Administrator Guide
 StorageGRID Webscale 11.0 Tenant Administrator Guide January 2018 215-12403_B0 doccomments@netapp.com Table of Contents 3 Contents Administering a StorageGRID Webscale tenant account... 5 Understanding
StorageGRID Webscale 11.0 Tenant Administrator Guide January 2018 215-12403_B0 doccomments@netapp.com Table of Contents 3 Contents Administering a StorageGRID Webscale tenant account... 5 Understanding
Technical Trust Policy
 Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Realms and Identity Policies
 The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 15 Create an Identity Rule, page 15 Manage a Realm, page 20 Manage an Identity
The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 15 Create an Identity Rule, page 15 Manage a Realm, page 20 Manage an Identity
Computing Parable. New Topic: Naming
 Computing Parable The Cow Courtesy: S. Keshav Lecture 10, page 1 New Topic: Naming Names are used to share resources, uniquely identify entities and refer to locations Need to map from name to the entity
Computing Parable The Cow Courtesy: S. Keshav Lecture 10, page 1 New Topic: Naming Names are used to share resources, uniquely identify entities and refer to locations Need to map from name to the entity
Windows Server 2003 Network Administration Goals
 Objectives Differentiate between the different editions of Windows Server 2003 Explain Windows Server 2003 network models and server roles Identify concepts relating to Windows Server 2003 network management
Objectives Differentiate between the different editions of Windows Server 2003 Explain Windows Server 2003 network models and server roles Identify concepts relating to Windows Server 2003 network management
Setting Up Resources in VMware Identity Manager. VMware Identity Manager 2.8
 Setting Up Resources in VMware Identity Manager VMware Identity Manager 2.8 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Setting Up Resources in VMware Identity Manager VMware Identity Manager 2.8 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
User Manual. Active Directory Change Tracker
 User Manual Active Directory Change Tracker Last Updated: March 2018 Copyright 2018 Vyapin Software Systems Private Ltd. All rights reserved. This document is being furnished by Vyapin Software Systems
User Manual Active Directory Change Tracker Last Updated: March 2018 Copyright 2018 Vyapin Software Systems Private Ltd. All rights reserved. This document is being furnished by Vyapin Software Systems
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server
 Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Parallelism. Master 1 International. Andrea G. B. Tettamanzi. Université de Nice Sophia Antipolis Département Informatique
 Parallelism Master 1 International Andrea G. B. Tettamanzi Université de Nice Sophia Antipolis Département Informatique andrea.tettamanzi@unice.fr Andrea G. B. Tettamanzi, 2014 1 Lecture 3 Part a Naming
Parallelism Master 1 International Andrea G. B. Tettamanzi Université de Nice Sophia Antipolis Département Informatique andrea.tettamanzi@unice.fr Andrea G. B. Tettamanzi, 2014 1 Lecture 3 Part a Naming
MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration. Chapter 5 Introduction to DNS in Windows Server 2008
 MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration Chapter 5 Introduction to DNS in Windows Server 2008 Objectives Discuss the basics of the Domain Name System (DNS) and its
MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration Chapter 5 Introduction to DNS in Windows Server 2008 Objectives Discuss the basics of the Domain Name System (DNS) and its
glite Java Authorisation Framework (gjaf) and Authorisation Policy coordination
 glite Java Authorisation Framework (gjaf) and Authorisation Policy coordination Yuri Demchenko University of Amsterdam MWSG meeting EGEE 06 Conference, September 27, 2006, Geneve www.eu-egee.org EGEE and
glite Java Authorisation Framework (gjaf) and Authorisation Policy coordination Yuri Demchenko University of Amsterdam MWSG meeting EGEE 06 Conference, September 27, 2006, Geneve www.eu-egee.org EGEE and
CounterACT User Directory Plugin
 Version 6.1.2 and Above Table of Contents About the User Directory Plugin... 3 Endpoint User Details... 3 Verify Endpoint Authentication... 3 User Directory Inventory... 4 HTTP Login Action... 5 HTTP Sign
Version 6.1.2 and Above Table of Contents About the User Directory Plugin... 3 Endpoint User Details... 3 Verify Endpoint Authentication... 3 User Directory Inventory... 4 HTTP Login Action... 5 HTTP Sign
