3.3.4 Connection Framework
|
|
|
- Jessie Warner
- 5 years ago
- Views:
Transcription
1 108 MIDP 2.0 AND THE JTWI Connection Framework What s Optional and What s Not The CLDC provides a Generic Connection Framework (GCF), which is an extensible framework that can be customized by a J2ME profile to support the necessary networking protocols required by that vertical device category. The MIDP 1.0 specification only required support (in other words, a concrete implementation) for the HTTP protocol. The MIDP 2.0 specification extends the support required for networking protocols to include mandatory support for HTTPS. The MIDP 2.0 specification also states that implementations should (where should implies a recommended practice that can be ignored only in exceptional circumstances) provide support for sockets, secure sockets, server sockets and datagrams. Support for serial port access via the CommConnection interface is optional under the MIDP 2.0 specification. Symbian s implementation of MIDP 2.0 complies with the specification, providing implementations for all of the above except the optional serial port access. So, Symbian s MIDP 2.0 currently provides implementations of the following protocols: HTTP HTTPS sockets server sockets secure sockets datagrams. In the following sections we will explore using these connections in a little more detail HTTP and HTTPS Support HTTP connections have been supported since MIDP 1.0. To open an HTTP connection we use the Connector.open() method with a URL of the form So code to open an HttpConnection and obtain an InputStream would look something like this. try{ String url = " HttpConnection conn = (HttpConnection)Connector.open(url); InputStream is = conn.openinputstream(); conn.close() catch(ioexception ioe){
2 MIDP Under the MIDP 2.0 security model, untrusted MIDlets can open an HTTP connection only with explicit user confirmation. Signed MIDlets that require access to an HTTP connection must explicitly request the javax.microedition.io.connector.http permission in the MIDlet-Permissions attribute: MIDlet-Permissions: javax.microedition.io.connector.http, The MIDP 2.0 specification adds the requirement that implementations must support the HTTPS protocol, which implements HTTP over a secure network connection via the Secure Sockets Layer (SSL). Opening an HTTPS connection follows the same pattern as a normal HTTP connection, with the exception that we pass in a connection URL of the form and cast the returned instance to an HttpsConnection object, as in the following example of code for interrogating a secure server for security information associated with the connection. try{ String url = " HttpsConnection hc = (HttpsConnection)Connector.open(url); SecurityInfo info = hc.getsecurityinfo(); String protocolname = info.getprotocolname(); String protocolversion = info.getprotocolversion(); String ciphersuite = info.getciphersuite(); Certificate c = info.getservercertificate(); String name = c.getissuer(); catch(ioexception ioe){ The MIDP 2.0 specification requires that MIDlets in untrusted MIDlet suites be able to open HTTPS connections with User permission. A signed MIDlet suite which contains MIDlets that open HTTPS connections must explicitly request the javax.microedition.io.connector.https permission in its MIDlet-Permissions attribute: MIDlet-Permissions: javax.microedition.io.connector.https, Socket and Server Socket Support Although support for socket connections was an optional part of the MIDP 1.0 specification, MIDP 2.0 now makes support for socket connections a recommended practice. Socket connections come in two forms: client connections in which a socket connection is opened to another host; and server connections in which the system listens on a particular port for
3 110 MIDP 2.0 AND THE JTWI incoming connections from other hosts. The connections are specified using Universal Resource Identifiers (URI). You should be familiar with the syntax of a URI from Web browsing. They have the format <string1>://<string2> where <string1> identifies the communication protocol to be used (e.g. http) and <string2> provides specific details about the connection. The protocol may be one of those supported by the Generic Connection Framework (see Section ). To open a client socket connection to another host we pass a URI of the following form to the connector s open() method: socket:// The host may be specified as a fully qualified hostname or IPv4 address and the port number refers to the connection endpoint on the remote peer. Some sample code is shown below: SocketConnection sc = null; OutputStream out = null; try{ sc = (SocketConnection)Connector.open ("socket://localhost:79"); out = c.openoutputstream(); catch(ioexception ioe){ A server socket connection is used for listening for inbound socket connections. To obtain a server socket connection we can pass a URI in either of the following forms to the connector s open() method: socket://:79 socket:// In the first case the system listens for incoming connections on port 79 (of the local host). In the latter case, the system allocates an available port for the incoming connections. ServerSocketConnection ssc = null; InputStream is = null; try{ ssc = (ServerSocketConnection)Connector.open( socket://:1234 ); SocketConnection sc = (SocketConnection)ssc.acceptAndOpen(); is = sc.openinputstream(); catch(ioexception ioe){
4 MIDP The ServerSocketConnection interface extends the StreamConnectionNotifier interface. To obtain a connection object for an incoming connection the acceptandopen() method must be called on the ServerSocketConnection instance. An inbound socket connection results in the call to the acceptandopen() method, returning a StreamConnection object which can be cast to a SocketConnection as desired. The SocketConnection interface defines several useful methods including: public void setsocketoption(byte option, int value) This allows the developer to set several socket options using the following public static final byte constants defined in SocketConnection: DELAY A value of zero disables the use of Nagle s algorithm written data is not buffered pending acknowledgement of previously written data. This may be desirable when sending and receiving small packets of data, for instance, in a peer-to-peer messenger application. LINGER A non-zero value represents the interval in seconds that the system will continue to try to process queued data after the close() method has been called. After the interval has elapsed the connection will be forcefully closed with a TCP RST. A value of zero disables linger on close. KEEPALIVE If enabled (by a non-zero value), a keepalive probe will be sent to the remote peer after an implementation-specific time interval (the default is two hours) if no other data has been sent or received on the socket during that time interval. The purpose of the probe is to detect if the peer has become unreachable. The peer can respond in one of three ways: a TCP ACK response indicating all is well no action is taken; a TCP RST response indicating the peer has crashed and been rebooted in which case the socket is closed; no response from the remote peer the socket is closed. A value of zero disables this feature. RCVBUF This option is used by the platform s networking code as a hint for the size at which to set the underlying network I/O receiving buffer. SNDBUF This option is used by the platform s networking code as a hint for the size to set the underlying network I/O sending buffer.
5 112 MIDP 2.0 AND THE JTWI A signed MIDlet suite which contains MIDlets which open socket connections must explicitly request the javax.microedition.io. Connector.socket permission (needed to open client connections) and if required the javax.microedition.io.connector. serversocket permission (needed to open server connections), in its MIDlet-Permissions attribute, for example: MIDlet-Permissions: javax.microedition.io.connector.socket, or: MIDlet-Permissions: javax.microedition.io.connector.socket, javax.microedition.io.connector.serversocket, If the protection domain to which the signed MIDlet suite would be bound grants, or potentially grants, these permissions, then the MIDlet suite will be installed and the MIDlets it contains will be able to open socket connections, either automatically or with user permission, depending upon the security policy in effect on the device for the protection domain to which the MIDlet suite has been bound. Whether MIDlets in untrusted MIDlet suites can open socket connections depends on the security policy relating to the untrusted domain in force on the device Secure Socket Support Secure socket connections are client socket connections over SSL. To open a secure socket connection we pass in a hostname (or IPv4 address) and port number to the connector s open() method using the following URI syntax: ssl://hostname:port We can then use the secure socket connection in the same manner as a normal socket connection, for example: try{ SecureConnection sc = (SecureConnection) Connector.open("ssl:// OutputStream out = sc.openoutputstream(); InputStream in = sc.openinputstream(); catch(ioexception ioe){
6 MIDP A signed MIDlet suite that contains MIDlets which open secure connections must explicitly request the javax.microedition.io.connector.ssl permission in its MIDlet-Permissions attribute, for example: MIDlet-Permissions: javax.microedition.io.connector.ssl, If the protection domain to which the signed MIDlet suite would be bound grants, or potentially grants, this permission, the MIDlet suite can be installed and the MIDlets it contains will be able to open secure connections, either automatically or with user permission, depending on the security policy in effect. Whether MIDlets in untrusted MIDlet suites can open secure connections depends on the permissions granted in the untrusted protection domain Datagram Support Symbian s MIDP 2.0 implementation includes support for sending and receiving UDP datagrams. A datagram connection can be opened in client or server mode. Client mode is for sending datagrams to a remote device. To open a client mode datagram connection we use the following URI format: datagram://localhost:1234 Here the port number indicates the port on the target device to which the datagram will be sent. Sample code for sending a datagram is shown below: String message = Hello! ; byte[] payload = message.tostring(); try{ UDPDatagramConnection conn = null; conn = (UDPDatagramConnection) Connector.open( datagram://localhost:1234 ); Datagram datagram = conn.newdatagram(payload, payload.length); conn.send(datagram); catch(ioexception ioe){ Server mode connections are for receiving (and replying to) incoming datagrams. To open a datagram connection in server mode we use a URI of the following form: datagram://:1234
7 114 MIDP 2.0 AND THE JTWI The port number in this case refers to the port on which the local device is listening for incoming datagrams. Sample code for receiving incoming datagrams is given below: try{ UDPDatagramConnection dconn = null; dconn = (UDPDatagramConnection)Connector.open("datagram://:1234"); Datagram dg = dconn.newdatagram(300); while(true){ dconn.receive(dg); byte[] data = dg.getdata(); catch(ioexception ioe){ A signed MIDlet suite which contains MIDlets that open datagram connections must explicitly request the javax.microedition.io.connector.datagram permission (needed to open client connections) and the javax.microedition.io.connector.datagramreceiver permission (needed to open server connections) in its MIDlet- Permissions attribute, for example: MIDlet-Permissions: javax.microedition.io.connector.datagram, or: MIDlet-Permissions: javax.microedition.io.connector.datagramreceiver, or: MIDlet-Permissions: javax.microedition.io.connector.datagram, javax.microedition.io.connector.datagramreceiver, If the protection domain to which the signed MIDlet suite would be bound grants, or potentially grants, the requested permissions, the MIDlet suite can be installed and the MIDlets it contains will be able to open datagram connections, either automatically or with user permission, depending on the security policy in effect. Whether MIDlets in untrusted MIDlet suites can open datagram connections depends on permissions granted to MIDlet suites bound to the untrusted protection domain Security Policy for Network Connections The connections discussed above are part of the Net Access function group (see the Recommended Security Policy for GSM/UMTS Compliant
8 MIDP Devices addendum to the MIDP 2.0 specification). On the Nokia 6600 and Sony Ericsson P900/P908, MIDlets in untrusted MIDlet suites can access the Net Access function group with User permission (explicit confirmation required from the user). On the Sony Ericsson P900/P908, the default User permission is set to session (and is not customizable by the user). On the Nokia 6600, the default User permission is set to oneshot, but can be changed by the user to session or disallowed. The Sony Ericsson P900/P908 supports the trusted protection domain on Organizer firmware versions R2B02 or later. The security policy in effect for MIDlets in MIDlet suites bound to the trusted protection domain on the P900/P908 allows automatic access (Allowed permission) to the Net Access function group connections. At the time of writing, the available firmware release (3.42.1) on the Nokia 6600 only supported the untrusted domain, although future releases will add support for trusted protection domains Practical Networking using Wireless Networks In the spirit of providing practical information, we shall now digress slightly into a discussion of networking on wireless data networks. The most common GSM networks at the time of writing are 2.5 G General Packet Radio Service (GPRS) networks. GPRS networks can be regarded as a private sub-network behind a gateway to the Internet. All current GPRS network providers operate their consumer networks behind Network Address Translation (NAT) gateways and dynamically allocate private IP addresses to mobile terminals on each PDP activation (data session). This has important consequences for application developers wishing to use wireless networking. One consequence is that mobile terminals on a GPRS network typically are unable to receive inbound connections since their private IP addresses are not visible on the Internet. Another issue relates to connection-less communications protocols such as UDP. When a terminal on a GPRS network sends a UDP packet to a remote host on the Internet, the sender address is stripped out of the packet and replaced with the IP address of the gateway and a port number representing the terminal data session. How long this session information remains valid (enabling the remote host to reply to the sender) depends on the NAT gateway. After a limited period of time the gateway will re-allocate that port to another GPRS terminal. Some NAT policies allow for the session information (and thus the allocated port) to remain associated with the GPRS terminal as long as traffic flows through it. Such inactivity timeouts though, vary quite significantly between operators. The most effective way of avoiding complications arising out of operating behind NAT gateways is for developers to use TCP-based protocols such as HTTP. As long as there is an active TCP session in place, the
9 116 MIDP 2.0 AND THE JTWI gateway port will remain allocated to that GPRS terminal by the NAT gateway, enabling two-way traffic between the GPRS terminal and the remote device Socket Demo MIDlet We will finish this section with a simple example using TCP sockets to interrogate a web browser. The Socket Demo MIDlet sends an HTTP GET request to a web server over a client socket connection and then reads and displays the response. The Socket Demo MIDlet consists of two classes, SocketMIDlet extending MIDlet and the ClientConnection class. The source code for the SocketMIDlet class is shown below. import javax.microedition.midlet.*; import javax.microedition.lcdui.*; public class SocketMIDlet extends MIDlet implements CommandListener { private final static String defaulturl = "socket:// private Command exitcommand, sendcommand; private Display display; public TextBox textbox; public SocketMIDlet() { display = Display.getDisplay(this); exitcommand = new Command("Exit", Command.EXIT, 2); sendcommand = new Command("Send request", Command.SCREEN, 1); public void startapp() { textbox = new TextBox("Sockets Demo", defaulturl, 256, TextField.ANY); textbox.addcommand(exitcommand); textbox.addcommand(sendcommand); textbox.setcommandlistener(this); display.setcurrent(textbox); public void commandaction(command c, Displayable s) { if (c == exitcommand) { notifydestroyed(); else if (c == sendcommand) { ClientConnection socketconn = new ClientConnection(this); socketconn.sendmessage(textbox.getstring()); textbox.removecommand(sendcommand); public void pauseapp() { public void destroyapp(boolean unconditional) {
10 MIDP SocketMIDlet sets up the UI and responds to the Send request Command by creating an instance of ClientConnection and invoking its sendmessage() method, passing in a String representing the URL of the required web server. The main work is done in the ClientConnection class: import javax.microedition.io.*; import java.io.*; public class ClientConnection extends Thread { private final static String line1 = "GET /index.html\r\n"; private final static String line2 = "Accept: */*\r\n"; private final static String line3 = "Accept-Language: en-us\r\n"; private final static String line4 = "Accept-Encoding: gzip, deflate\r\n"; private final static String line5 = "User-Agent: Mozilla/4.0 (Compatible; MSIE 5.01; Windows NT)\r\n"; private SocketMIDlet sm = null; private String url = null; private String request = null; public ClientConnection(SocketMIDlet sm) { this.sm = sm; public void sendmessage(string url) { this.url = url; String host = url.substring(url.lastindexof('/') + 1); System.out.println("host is " + host); String hostline = "Host: " + host + "\r\n"; request = line1 + line2 + line3 + line4 + line5 + hostline; start(); public void run() { try{ SocketConnection conn = (SocketConnection)Connector.open(url); DataOutputStream out = conn.opendataoutputstream(); byte[] buf= request.getbytes(); out.write(buf); out.flush(); out.close(); sm.textbox.insert("finished request!\n" + "Receiving response\n", sm.textbox.size()); DataInputStream in = conn.opendatainputstream(); int ch; while ( (ch = in.read())!= -1 && sm.textbox.size() < sm.textbox.getmaxsize()) { String str = new Character((char) ch).tostring(); try { sm.textbox.insert(str, sm.textbox.size()); catch(exception e) { e.printstacktrace();
11 118 MIDP 2.0 AND THE JTWI conn.close(); conn = null; catch(exception e){ e.printstacktrace(); The url parameter of the sendmessage() method has the following form: socket:// The sendmessage() method creates a GET request and then starts a new Thread to create the connection, send the request and read the response. Let us look at the contents of the thread s run() method in more detail. SocketConnection conn = (SocketConnection)Connector.open(url); DataOutputStream out = conn.opendataoutputstream(); byte[] buf= request.getbytes(); out.write(buf); out.flush(); out.close(); A SocketConnection is opened using a URI of the form socket://hostname:port and the returned SocketConnection object is used to get a DataOutputStream. After converting the request to a byte array, this is written to the DataOutputStream using the write() method. The flush() method is then called on the DataOutputStream to ensure any buffered data is written to the connection endpoint. This last step is essential. Symbian s implementation of OutputStream buffers data internally and only writes it to the connection endpoint when the buffer is full, or when the buffer is flushed. Failing to call flush() may result in data never being written to the connection endpoint. Once we have finished with the OutputStream we can close it. Having written the request we are now ready to read the response. We use our SocketConnection to get a DataInputStream and use the read() method to read from it in the standard manner. DataInputStream in = conn.opendatainputstream(); int ch; while ( (ch = in.read())!= -1 && sm.textbox.size() < sm.textbox.getmaxsize()) {
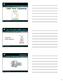
12 MIDP Figure 3.6 Socket Demo MIDlet running on a Nokia The response from the web server should be a stream of raw HTML. We read the stream until our MIDlet s TextBox is full and then close the connection (reading the response in its entirety is likely to be a lengthy process for most web sites!). The screenshots in Figure 3.6 show the Socket Demo MIDlet running on a Nokia Note that the purpose of this sample code is to demonstrate how to use client TCP socket connections. Normally, to make requests to a HTTP server we would use an HttpConnection or HttpsConnection. Also, under the JTWI security policy for GSM/UMTS compliant devices, the implementation of SocketConnection using TCP sockets must throw a SecurityException when an untrusted MIDlet suite attempts to connect on ports 80, 8080 (HTTP) and 443 (HTTPS). Hence the above code is not future-proof for untrusted MIDlet suites The Push Registry Introduction One of the exciting new additions to MIDP 2.0 is the Push Registry API, which allows MIDlets to be launched in response to incoming network connections. Many applications, particularly messaging applications, need to be continuously listening for incoming messages. Previously, to achieve this a Java application would have had to be continually running in the background. Although the listening Java application may itself be small, it would still require an instance of the virtual machine to be running, thus appropriating some of the mobile phone s scarce resources. The JSR 118 recognized the need for an alternative, more resource-effective solution for MIDP 2.0 and so introduced the push registry.
13 120 MIDP 2.0 AND THE JTWI Using the Push Registry The Push Registry API is encapsulated in the javax.microedition. io.pushregistry class. The push registry maintains a list of inbound connections that have been previously registered by installed MIDlets. A MIDlet registers an incoming connection with the push registry either statically at installation via an entry in the JAD file or dynamically (programmatically) via the registerconnection() method. When a MIDlet is running, it handles all the incoming connections (whether registered with the push registry or not). If, however, the MIDlet is not running, the AMS listens for registered incoming connections and launches the MIDlet in response to an incoming connection previously registered by that MIDlet, by invoking the startapp() method. The AMS then hands off the connection to the MIDlet which is then responsible for opening the appropriate connection and handling the I/O. In the case of static registration, the MIDlet registers its interest in incoming connections in the JAD file, in the following format: MIDlet-Push-<n>: <ConnectionURL>, <MIDletClassName>, <AllowedSender> The <ConnectionURL> field specifies the protocol and port for the connection end point in the same URI syntax used as the argument to the Connector.open() method that is used by the MIDlet to process the incoming connection. Examples of <ConnectionURL> entries might be: sms://:1234 socket://:1234 The <MIDletClassName> field contains the package-qualified name of the class that extends javax.microedition.midlet.midlet. This would be the name of the MIDlet class as listed in the application descriptor or manifest file under the MIDlet-<n> entry. The <AllowedSender> field acts as a filter indicating that the AMS should only respond to incoming connections from a specific sender. For the SMS protocol, the <AllowedSender> entry is the phone number of the required sender. For a server socket connection endpoint the <AllowedSender> entry would be an IP address (note in both cases that the sender port number is not included in the filter). The <AllowedSender> syntax supports two wildcard characters: * matches any string including an empty string and? matches any character. Hence the following would be valid entries for the <AllowedSender> field: * * ?
14 MIDP The first entry indicates any IP address, the second entry allows the last three digits of the IP address to take any value, while the last entry allows only the last digit to have any value. So the full entry for the MIDlet-Push-<n> attribute in a JAD file may look something like this: MIDlet-Push-1: sms://:1234, com.symbian.devnet.chatmidlet, * MIDlet-Push-2: socket://:3000, com.symbian.devnet.chatmidlet, * If the request for a static connection registration can not be fulfilled then the AMS must not install the MIDlet. Examples of when a registration request might fail include the requested protocol not being supported by the device, or the requested port number being already allocated to another application. To register a dynamic connection with the AMS we use the static registerconnection() method of PushRegistry: PushRegistry.registerConnection( sms://:1234, com.symbian.devnet.chatmidlet, * ); The arguments take precisely the same format as those used to make up the MIDlet-Push-<n> entry in a JAD or manifest. Upon registration, the dynamic connection behaves in an identical manner to a static connection registered via the application descriptor. To un-register a dynamic connection the static boolean unregisterconnection() method of PushRegistry is used: boolean result = PushRegistry.unregisterConnection(( sms://:1234 ); If the dynamic connection was successfully unregistered a value of true is returned. The AMS will respond to input activity on a registered connection by launching the corresponding MIDlet (assuming that the MIDlet is not already running). The MIDlet should then respond to the incoming connection by launching a thread to handle the incoming data in the startapp() method. Using a separate thread is the recommended practice for avoiding conflicts between blocking I/O operations and the normal user interaction events. For a MIDlet registered for incoming SMS messages, the startapp() method might look something like this: public void startapp() { // List of active connections. String[] connections = PushRegistry.listConnections(true);
15 122 MIDP 2.0 AND THE JTWI for (int i=0; i < connections.length; i++) { if(connections[i].equals( sms://:1234 )){ new Thread(){ public void run(){ Receiver.openReceiver();.start(); One other use of the push registry should be mentioned before we leave this topic. The PushRegistry class provides the register- Alarm() method: public static long registeralarm(string midlet, long time) This allows a running MIDlet to register itself or another MIDlet in the same suite for activation at a given time. The midlet argument is the class name of the MIDlet to be launched at the time specified by the time argument. The launch time is specified in milliseconds since January 1, 1970, 00:00:00 GMT. The push registry may contain only one outstanding activation time entry per MIDlet in each installed MIDlet suite. If a previous activation entry is registered, it will be replaced by the current invocation and the previous value returned. If no previous wakeup time has been set, a zero is returned The Push Registry and the Security Model The PushRegistry is a protected API and, as such, a signed MIDlet suite which registers connections statically or contains MIDlets which register connections and/or alarms, must explicitly request the javax.microedition.io.pushregistry permission in its MIDlet-Permissions attribute, for example: MIDlet-Permissions: javax.microedition.io.pushregistry, Note that a signed MIDlet suite must also explicitly request the permissions necessary to open the connection types of any connections it wishes to register either statically or dynamically. If the protection domain to which the signed MIDlet suite would be bound grants, or potentially grants, the requested permission, the MIDlet suite can be installed and the MIDlets it contains will be able to register and deregister connections, and register alarms, either automatically, or with user permission, depending on the security policy in effect.
16 MIDP Untrusted MIDlets do not require a MIDlet-Permissions entry. Whether access is granted to the Push Registry API will depend on the security policy for the untrusted protection domain in effect on the device. On the Sony Ericsson P900/P908 and Nokia 6600, MIDlets in untrusted MIDlet suites can use the Push Registry APIs (Application Auto-Invocation function group) with user permission. On both the 6600 and the P900/P908, the default user permission is set to session. On the Nokia 6600, the default value can be changed by the user to oneshot or disallowed. For the Sony Ericsson P900/P908, the security policy in effect for MIDlets in MIDlet suites bound to the trusted protection domain allows automatic access to the Push Registry API Symbian s Implementation At the time of writing, the current version of Symbian OS, Version 7.0s, supports the following connection types in its implementation of the MIDP 2.0 push architecture: Server socket Datagram SMS. In Symbian s implementation, all connections that can be registered as push connections are managed by the system AMS, even if they are not requested to be push-enabled by an application. In the case of server connections that spawn off a connected stream due to an incoming connection, the stream connections are also maintained through the system AMS. Future releases of Symbian OS are likely to increase the types of connections supported by the push architecture to include Bluetooth, L2CAP and RFCOMM connections Additions to the LCDUI A Quick Tour The MIDP 2.0 specification introduces a number of new features to the LCDUI toolkit which are designed to give developers more control over their application s user interface. In this section we briefly look at some of them. Display MIDP 2.0 introduces two useful new methods to the Display class which allow MIDlets to control the screen backlight and the vibration of the phone:
Java 2 Micro Edition Server socket and SMS
 Java 2 Micro Edition Server socket and SMS F. Ricci Content Other Connection Types Responding to Incoming Connections Security Permissions Security domains Midlet signing Wireless Messaging Responding
Java 2 Micro Edition Server socket and SMS F. Ricci Content Other Connection Types Responding to Incoming Connections Security Permissions Security domains Midlet signing Wireless Messaging Responding
Java 2 Micro Edition Server socket and SMS. F. Ricci
 Java 2 Micro Edition Server socket and SMS F. Ricci Content Other Connection Types Responding to Incoming Connections Socket and Server Socket Security Permissions Security domains Midlet signing Wireless
Java 2 Micro Edition Server socket and SMS F. Ricci Content Other Connection Types Responding to Incoming Connections Socket and Server Socket Security Permissions Security domains Midlet signing Wireless
J2ME crash course. Harald Holone
 J2ME crash course Harald Holone 2006-01-24 Abstract This article gives a short, hands-on introduction to programming J2ME applications on the MIDP 2.0 platform. Basic concepts, such as configurations,
J2ME crash course Harald Holone 2006-01-24 Abstract This article gives a short, hands-on introduction to programming J2ME applications on the MIDP 2.0 platform. Basic concepts, such as configurations,
Programming Mobile Devices Networking
 Programming Mobile Devices Networking University of Innsbruck WS 2009/2010 thomas.strang@sti2.at Networking in General Internet composed of millions of computers running the Internet Protocol (IP) stack
Programming Mobile Devices Networking University of Innsbruck WS 2009/2010 thomas.strang@sti2.at Networking in General Internet composed of millions of computers running the Internet Protocol (IP) stack
Mobile Systeme Grundlagen und Anwendungen standortbezogener Dienste. Location Based Services in the Context of Web 2.0
 Mobile Systeme Grundlagen und Anwendungen standortbezogener Dienste Location Based Services in the Context of Web 2.0 Department of Informatics - MIN Faculty - University of Hamburg Lecture Summer Term
Mobile Systeme Grundlagen und Anwendungen standortbezogener Dienste Location Based Services in the Context of Web 2.0 Department of Informatics - MIN Faculty - University of Hamburg Lecture Summer Term
Mobile Application Development. Introduction. Dr. Christelle Scharff Pace University, USA
 Mobile Application Development Introduction Dr. Christelle Scharff cscharff@pace.edu Pace University, USA Objectives Getting an overview of the mobile phone market, its possibilities and weaknesses Providing
Mobile Application Development Introduction Dr. Christelle Scharff cscharff@pace.edu Pace University, USA Objectives Getting an overview of the mobile phone market, its possibilities and weaknesses Providing
NOKIA 12 GSM MODULE JAVA TM IMLET PROGRAMMING GUIDE. Copyright Nokia. All rights reserved. Issue
 NOKIA 12 GSM MODULE JAVA TM IMLET PROGRAMMING GUIDE Copyright 2004-2005 Nokia. All rights reserved. Issue 1.1 9231715 Contents ACRONYMS AND TERMS...1 1. ABOUT THIS DOCUMENT...4 2. INTRODUCTION...6 3. NOKIA
NOKIA 12 GSM MODULE JAVA TM IMLET PROGRAMMING GUIDE Copyright 2004-2005 Nokia. All rights reserved. Issue 1.1 9231715 Contents ACRONYMS AND TERMS...1 1. ABOUT THIS DOCUMENT...4 2. INTRODUCTION...6 3. NOKIA
The network connection
 C H A P T E R 1 3 The network connection 13.1 About the Generic Connection Framework 366 13.2 Using the Generic Connection Framework 372 13.3 HTTP-based connections 372 13.4 Socket-based connections 377
C H A P T E R 1 3 The network connection 13.1 About the Generic Connection Framework 366 13.2 Using the Generic Connection Framework 372 13.3 HTTP-based connections 372 13.4 Socket-based connections 377
DAY 3 J2ME March 2007 Aalborg University, Mobile Device Group Mobile Phone Programming
 DAY 3 J2ME Mobile Phone Programming Module 2 Micro (J2ME) Overview Introduction J2ME architecture Introduction 1 J2ME Key Factors Portability: Write once run anywhere Security: Code runs within the confines
DAY 3 J2ME Mobile Phone Programming Module 2 Micro (J2ME) Overview Introduction J2ME architecture Introduction 1 J2ME Key Factors Portability: Write once run anywhere Security: Code runs within the confines
Java 2 Micro Edition Socket, SMS and Bluetooth. F. Ricci 2008/2009
 Java 2 Micro Edition Socket, SMS and Bluetooth F. Ricci 2008/2009 Content Other Connection Types Responding to Incoming Connections Socket and Server Socket Security Permissions Security domains Midlet
Java 2 Micro Edition Socket, SMS and Bluetooth F. Ricci 2008/2009 Content Other Connection Types Responding to Incoming Connections Socket and Server Socket Security Permissions Security domains Midlet
J2ME With Database Connection Program
 J2ME With Database Connection Program Midlet Code: /* * To change this template, choose Tools Templates * and open the template in the editor. package hello; import java.io.*; import java.util.*; import
J2ME With Database Connection Program Midlet Code: /* * To change this template, choose Tools Templates * and open the template in the editor. package hello; import java.io.*; import java.util.*; import
Chapter 13 Add Multimedia to Your MIDlets
 Chapter 13 Add Multimedia to Your MIDlets The Mobile Media API (MMAPI), which extends the functions of Java 2 Platform, Micro Edition (J2ME), allows easy and simple access and control of basic audio and
Chapter 13 Add Multimedia to Your MIDlets The Mobile Media API (MMAPI), which extends the functions of Java 2 Platform, Micro Edition (J2ME), allows easy and simple access and control of basic audio and
Mobile Devices in Software Engineering. Lab 2
 Mobile Devices in Software Engineering Lab 2 Objective The objective of this lab is to: 1. Get you started with network based mobile applications 2. Get you started with persistent storage on mobile devices
Mobile Devices in Software Engineering Lab 2 Objective The objective of this lab is to: 1. Get you started with network based mobile applications 2. Get you started with persistent storage on mobile devices
Who am I? Wireless Online Game Development for Mobile Device. What games can you make after this course? Are you take the right course?
 Who am I? Wireless Online Game Development for Mobile Device Lo Chi Wing, Peter Lesson 1 Email: Peter@Peter-Lo.com I123-1-A@Peter Lo 2007 1 I123-1-A@Peter Lo 2007 2 Are you take the right course? This
Who am I? Wireless Online Game Development for Mobile Device Lo Chi Wing, Peter Lesson 1 Email: Peter@Peter-Lo.com I123-1-A@Peter Lo 2007 1 I123-1-A@Peter Lo 2007 2 Are you take the right course? This
Wireless Java Technology
 Wireless Java Technology Pao-Ann Hsiung National Chung Cheng University Ref: http://developers.sun.com/techtopics/mobility/learning/tutorial/ 1 Contents Overview of Java 2 Platform Overview of J2ME Scope
Wireless Java Technology Pao-Ann Hsiung National Chung Cheng University Ref: http://developers.sun.com/techtopics/mobility/learning/tutorial/ 1 Contents Overview of Java 2 Platform Overview of J2ME Scope
Mobile Information Device Profile (MIDP) Alessandro Cogliati. Helsinki University of Technology Telecommunications Software and Multimedia Laboratory
 Multimedia T-111.5350 Mobile Information Device Profile (MIDP) Alessandro Cogliati Helsinki University of Technology Telecommunications Software and Multimedia Laboratory 1 Outline Java Overview (Editions/Configurations/Profiles)
Multimedia T-111.5350 Mobile Information Device Profile (MIDP) Alessandro Cogliati Helsinki University of Technology Telecommunications Software and Multimedia Laboratory 1 Outline Java Overview (Editions/Configurations/Profiles)
Actual4Test. Actual4test - actual test exam dumps-pass for IT exams
 Actual4Test Actual4test - actual test exam dumps-pass for IT exams Exam : 1Z0-869 Title : Java Mobile Edition 1 Mobile Application Developer Certified Professional Exam Vendors : Oracle Version : DEMO
Actual4Test Actual4test - actual test exam dumps-pass for IT exams Exam : 1Z0-869 Title : Java Mobile Edition 1 Mobile Application Developer Certified Professional Exam Vendors : Oracle Version : DEMO
TAMZ. JavaME. MIDlets. Department of Computer Science VŠB-Technical University of Ostrava
 MIDlets 1 MIDlet A MIDlet is a Java program for embedded devices, more specifically the virtual machine. Generally, these are games and applications that run on a cell phone. MIDlets will (should) run
MIDlets 1 MIDlet A MIDlet is a Java program for embedded devices, more specifically the virtual machine. Generally, these are games and applications that run on a cell phone. MIDlets will (should) run
BVRIT HYDERABAD College of Engineering for Women Department of Information Technology. Hand Out
 BVRIT HYDERABAD College of Engineering for Women Department of Information Technology Hand Out Subject Name: Mobile Application Development Prepared by: 1. S. Rama Devi, Assistant Professor, IT Year and
BVRIT HYDERABAD College of Engineering for Women Department of Information Technology Hand Out Subject Name: Mobile Application Development Prepared by: 1. S. Rama Devi, Assistant Professor, IT Year and
Mobile Station Execution Environment (MExE( MExE) Developing web applications for PDAs and Cellphones. WAP (Wireless Application Protocol)
 Developing web applications for PDAs and Cellphones Mobile Station Execution Environment (MExE( MExE) MExE is a standard for defining various levels of wireless communication These levels are called classmarks
Developing web applications for PDAs and Cellphones Mobile Station Execution Environment (MExE( MExE) MExE is a standard for defining various levels of wireless communication These levels are called classmarks
Developing mobile UI
 Vorlesung Advanced Topics in HCI (Mensch-Maschine-Interaktion 2) Ludwig-Maximilians-Universität München LFE Medieninformatik Albrecht Schmidt & Andreas Butz WS2003/2004 http://www.medien.informatik.uni-muenchen.de/
Vorlesung Advanced Topics in HCI (Mensch-Maschine-Interaktion 2) Ludwig-Maximilians-Universität München LFE Medieninformatik Albrecht Schmidt & Andreas Butz WS2003/2004 http://www.medien.informatik.uni-muenchen.de/
Lab Exercise 4. Please follow the instruction in Workshop Note 4 to complete this exercise.
 Lab Exercise 4 Please follow the instruction in Workshop Note 4 to complete this exercise. 1. Turn on your computer and startup Windows XP (English version), download and install J2ME Wireless Toolkit
Lab Exercise 4 Please follow the instruction in Workshop Note 4 to complete this exercise. 1. Turn on your computer and startup Windows XP (English version), download and install J2ME Wireless Toolkit
CPSC 441 Assignment-3 Discussion. Department of Computer Science University of Calgary
 CPSC 441 Assignment-3 Discussion Department of Computer Science University of Calgary Overview of FastFTP protocol TCP for Initial Handshake Port: 2245 Port: 4576 You may choose any free port >1024 at
CPSC 441 Assignment-3 Discussion Department of Computer Science University of Calgary Overview of FastFTP protocol TCP for Initial Handshake Port: 2245 Port: 4576 You may choose any free port >1024 at
DAY 3 J2ME Aalborg University, Mobile Device Group. Mobile. Mobile Phone Programming
 DAY 3 J2ME Mobile Phone Programming Java 2 Micro Edition (J2ME) Overview Introduction J2ME architecture MIDlets Application development Introduction J2ME Key Factors Portability: Write once run anywhere
DAY 3 J2ME Mobile Phone Programming Java 2 Micro Edition (J2ME) Overview Introduction J2ME architecture MIDlets Application development Introduction J2ME Key Factors Portability: Write once run anywhere
CPSC 441 Assignment-3 Discussion. Department of Computer Science University of Calgary
 CPSC 441 Assignment-3 Discussion Department of Computer Science University of Calgary Overview of FastFTP protocol TCP for Initial Handshake Port: 1111 Port: 4444 UDP for File Content Transfer Port: 3333
CPSC 441 Assignment-3 Discussion Department of Computer Science University of Calgary Overview of FastFTP protocol TCP for Initial Handshake Port: 1111 Port: 4444 UDP for File Content Transfer Port: 3333
Accessing DB2 Everyplace using J2ME devices, part 1
 Accessing DB2 Everyplace using J2ME devices, part 1 Skill Level: Intermediate Naveen Balani (naveenbalani@rediffmail.com) Developer 08 Apr 2004 This two-part tutorial assists developers in developing DB2
Accessing DB2 Everyplace using J2ME devices, part 1 Skill Level: Intermediate Naveen Balani (naveenbalani@rediffmail.com) Developer 08 Apr 2004 This two-part tutorial assists developers in developing DB2
Outlines. Networking in Java. Internet hardware structure. Networking Diagram. IP Address. Networking in Java. Networking basics
 G52APR Application programming Networking in Java Michael Li http://www.cs.nott.ac.uk/~jwl/g52apr Outlines Networking basics Network architecture IP address and port Server-client model TCP and UDP protocol
G52APR Application programming Networking in Java Michael Li http://www.cs.nott.ac.uk/~jwl/g52apr Outlines Networking basics Network architecture IP address and port Server-client model TCP and UDP protocol
WebSphere MQ Telemetry Java Classes Version 1.1
 WebSphere MQ Telemetry Java Classes Version 1.1 15 May, 2003 SupportPac author Ian Harwood Jonathan Woodford ian_harwood@uk.ibm.com jonathanw@uk.ibm.com Property of IBM ii Take Note! Before using this
WebSphere MQ Telemetry Java Classes Version 1.1 15 May, 2003 SupportPac author Ian Harwood Jonathan Woodford ian_harwood@uk.ibm.com jonathanw@uk.ibm.com Property of IBM ii Take Note! Before using this
Mensch-Maschine-Interaktion 2
 Mensch-Maschine-Interaktion 2 Übung 5 (12./14./15. Juni 2007) Arnd Vitzthum - arnd.vitzthum@ifi.lmu.de Amalienstr. 17, Raum 501 Dominic Bremer - bremer@cip.ifi.lmu.de Java ME Overview (I) Java ME slim
Mensch-Maschine-Interaktion 2 Übung 5 (12./14./15. Juni 2007) Arnd Vitzthum - arnd.vitzthum@ifi.lmu.de Amalienstr. 17, Raum 501 Dominic Bremer - bremer@cip.ifi.lmu.de Java ME Overview (I) Java ME slim
Configuring Health Monitoring
 CHAPTER1 This chapter describes how to configure health monitoring on the ACE to track the state of a server by sending out probes. Also referred to as out-of-band health monitoring, the ACE verifies the
CHAPTER1 This chapter describes how to configure health monitoring on the ACE to track the state of a server by sending out probes. Also referred to as out-of-band health monitoring, the ACE verifies the
protocols September 15,
 Contents SCI 351 4 Protocols, WWW Internet applications WWW, document technology Lennart Herlaar Original slides by Piet van Oostrum September 15, 2003 SCI351-4 1 X SCI351-4 1 X Internet applications How
Contents SCI 351 4 Protocols, WWW Internet applications WWW, document technology Lennart Herlaar Original slides by Piet van Oostrum September 15, 2003 SCI351-4 1 X SCI351-4 1 X Internet applications How
JAVA - NETWORKING (SOCKET PROGRAMMING)
 JAVA - NETWORKING (SOCKET PROGRAMMING) http://www.tutorialspoint.com/java/java_networking.htm Copyright tutorialspoint.com The term network programming refers to writing programs that execute across multiple
JAVA - NETWORKING (SOCKET PROGRAMMING) http://www.tutorialspoint.com/java/java_networking.htm Copyright tutorialspoint.com The term network programming refers to writing programs that execute across multiple
OBJECT ORIENTED PROGRAMMING
 1 OBJECT ORIENTED PROGRAMMING Lecture 14 Networking Basics Outline 2 Networking Basics Socket IP Address DNS Client/Server Networking Class & Interface URL Demonstrating URL Networking 3 Java is practically
1 OBJECT ORIENTED PROGRAMMING Lecture 14 Networking Basics Outline 2 Networking Basics Socket IP Address DNS Client/Server Networking Class & Interface URL Demonstrating URL Networking 3 Java is practically
Chapter 2 Applications and
 Chapter 2 Applications and Layered Architectures Sockets Socket API API (Application Programming Interface) Provides a standard set of functions that can be called by applications Berkeley UNIX Sockets
Chapter 2 Applications and Layered Architectures Sockets Socket API API (Application Programming Interface) Provides a standard set of functions that can be called by applications Berkeley UNIX Sockets
JSR 248 Mobile Service Architecture Change Log
 JSR 248 Mobile Service Architecture CHANGE LOG 1 (7) JSR 248 Mobile Service Architecture Change Log # Change Description Reason Spec Status version 1 Section: 6.3.3.2 Mandatory ContactList Attributes ATTR_NONE
JSR 248 Mobile Service Architecture CHANGE LOG 1 (7) JSR 248 Mobile Service Architecture Change Log # Change Description Reason Spec Status version 1 Section: 6.3.3.2 Mandatory ContactList Attributes ATTR_NONE
Wireless Messaging API (WMA)
 Wireless Messaging API (WMA) for Java 2 Micro Edition Version 1.1 JSR 120 Expert Group JSR-120-EG@JCP.ORG Java Community Process (JCP) ii Java TM Wireless Messaging API (WMA) Specification ( Specification
Wireless Messaging API (WMA) for Java 2 Micro Edition Version 1.1 JSR 120 Expert Group JSR-120-EG@JCP.ORG Java Community Process (JCP) ii Java TM Wireless Messaging API (WMA) Specification ( Specification
Sortware Comprehension and Μaintenance
 Department of Management and Technology Sortware Comprehension and Μaintenance Wireless IRC project Design of a new feature Wireless Irc s Design Presentation Brief explanation of Midlet Suites function
Department of Management and Technology Sortware Comprehension and Μaintenance Wireless IRC project Design of a new feature Wireless Irc s Design Presentation Brief explanation of Midlet Suites function
MOTOROKR E6/E6e Java ME Developer Guide. Version 02.00
 MOTOROKR E6/E6e Version 02.00 Copyright 2007, Motorola, Inc. All rights reserved. This documentation may be printed and copied solely for use in developing products for Motorola products. In addition,
MOTOROKR E6/E6e Version 02.00 Copyright 2007, Motorola, Inc. All rights reserved. This documentation may be printed and copied solely for use in developing products for Motorola products. In addition,
Advanced Java Programming. Networking
 Advanced Java Programming Networking Eran Werner and Ohad Barzilay Tel-Aviv University Advanced Java Programming, Spring 2006 1 Overview of networking Advanced Java Programming, Spring 2006 2 TCP/IP protocol
Advanced Java Programming Networking Eran Werner and Ohad Barzilay Tel-Aviv University Advanced Java Programming, Spring 2006 1 Overview of networking Advanced Java Programming, Spring 2006 2 TCP/IP protocol
SUN. Sun Certified Mobile Application Developer for the Java 2 Platform, Micro Edition, Version 1.0
 SUN 310-110 Sun Certified Mobile Application Developer for the Java 2 Platform, Micro Edition, Version 1.0 Download Full Version : https://killexams.com/pass4sure/exam-detail/310-110 QUESTION: 332 Given:
SUN 310-110 Sun Certified Mobile Application Developer for the Java 2 Platform, Micro Edition, Version 1.0 Download Full Version : https://killexams.com/pass4sure/exam-detail/310-110 QUESTION: 332 Given:
Lab Exercise 7. Please follow the instruction in Workshop Note 7 to complete this exercise.
 Lab Exercise 7 Please follow the instruction in Workshop Note 7 to complete this exercise. 1. Turn on your computer and startup Windows XP (English version), download and install J2ME Wireless Toolkit
Lab Exercise 7 Please follow the instruction in Workshop Note 7 to complete this exercise. 1. Turn on your computer and startup Windows XP (English version), download and install J2ME Wireless Toolkit
Java Networking (sockets)
 Java Networking (sockets) Rui Moreira Links: http://java.sun.com/docs/books/tutorial/networking/toc.html#sockets http://www.javaworld.com/javaworld/jw-12-1996/jw-12-sockets_p.html Networking Computers
Java Networking (sockets) Rui Moreira Links: http://java.sun.com/docs/books/tutorial/networking/toc.html#sockets http://www.javaworld.com/javaworld/jw-12-1996/jw-12-sockets_p.html Networking Computers
COMP 213. Advanced Object-oriented Programming. Lecture 20. Network Programming
 COMP 213 Advanced Object-oriented Programming Lecture 20 Network Programming Network Programming A network consists of several computers connected so that data can be sent from one to another. Network
COMP 213 Advanced Object-oriented Programming Lecture 20 Network Programming Network Programming A network consists of several computers connected so that data can be sent from one to another. Network
CS September 2017
 Machine vs. transport endpoints IP is a network layer protocol: packets address only the machine IP header identifies source IP address, destination IP address Distributed Systems 01r. Sockets Programming
Machine vs. transport endpoints IP is a network layer protocol: packets address only the machine IP header identifies source IP address, destination IP address Distributed Systems 01r. Sockets Programming
Distributed Systems Recitation 2. Tamim Jabban
 15-440 Distributed Systems Recitation 2 Tamim Jabban Project 1 Involves creating a Distributed File System (DFS) Released yesterday When/If done with PS1, start reading the handout Today: Socket communication!
15-440 Distributed Systems Recitation 2 Tamim Jabban Project 1 Involves creating a Distributed File System (DFS) Released yesterday When/If done with PS1, start reading the handout Today: Socket communication!
Distributed Systems Recitation 2. Tamim Jabban
 15-440 Distributed Systems Recitation 2 Tamim Jabban Agenda Communication via Sockets in Java (this enables you to complete PS1 and start P1 (goes out today!)) Multi-threading in Java Coding a full Client-Server
15-440 Distributed Systems Recitation 2 Tamim Jabban Agenda Communication via Sockets in Java (this enables you to complete PS1 and start P1 (goes out today!)) Multi-threading in Java Coding a full Client-Server
CSCD 330 Network Programming Spring 2018
 CSCD 330 Network Programming Spring 2018 Lecture 6 Application Layer Socket Programming in Java Reading for Java Client/Server see Relevant Links Some Material in these slides from J.F Kurose and K.W.
CSCD 330 Network Programming Spring 2018 Lecture 6 Application Layer Socket Programming in Java Reading for Java Client/Server see Relevant Links Some Material in these slides from J.F Kurose and K.W.
Connecting to a Server Implementing Servers Making URL Connections Advanced Socket Programming
 Course Name: Advanced Java Lecture 11 Topics to be covered Connecting to a Server Implementing Servers Making URL Connections Advanced Socket Programming Introduction Internet and WWW have emerged as global
Course Name: Advanced Java Lecture 11 Topics to be covered Connecting to a Server Implementing Servers Making URL Connections Advanced Socket Programming Introduction Internet and WWW have emerged as global
Distributed Systems. 27. Firewalls and Virtual Private Networks Paul Krzyzanowski. Rutgers University. Fall 2013
 Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Introduction to Information Science and Technology 2017 Networking II. Sören Schwertfeger 师泽仁
 II Sören Schwertfeger 师泽仁 Outline Review Network Layer Routing Transport Layer Applications HTTP Demos Internet: Huge network of networks Billions of hosts (computers) Internet Structure Network Edge:
II Sören Schwertfeger 师泽仁 Outline Review Network Layer Routing Transport Layer Applications HTTP Demos Internet: Huge network of networks Billions of hosts (computers) Internet Structure Network Edge:
Interprocess Communication
 Interprocess Communication Nicola Dragoni Embedded Systems Engineering DTU Informatics 4.2 Characteristics, Sockets, Client-Server Communication: UDP vs TCP 4.4 Group (Multicast) Communication The Characteristics
Interprocess Communication Nicola Dragoni Embedded Systems Engineering DTU Informatics 4.2 Characteristics, Sockets, Client-Server Communication: UDP vs TCP 4.4 Group (Multicast) Communication The Characteristics
Chapter 10. IO Streams
 Chapter 10 IO Streams Java I/O The Basics Java I/O is based around the concept of a stream Ordered sequence of information (bytes) coming from a source, or going to a sink Simplest stream reads/writes
Chapter 10 IO Streams Java I/O The Basics Java I/O is based around the concept of a stream Ordered sequence of information (bytes) coming from a source, or going to a sink Simplest stream reads/writes
Java Support for developing TCP Network Based Programs
 Java Support for developing TCP Network Based Programs 1 How to Write a Network Based Program (In Java) As mentioned, we will use the TCP Transport Protocol. To communicate over TCP, a client program and
Java Support for developing TCP Network Based Programs 1 How to Write a Network Based Program (In Java) As mentioned, we will use the TCP Transport Protocol. To communicate over TCP, a client program and
Wireless Messaging API (WMA)
 Wireless Messaging API (WMA) for Java 2 Micro Edition Version 1.0 Public Review Draft (0.8) JSR 120 Expert Group JSR-120-EG@JCP.ORG Java Community Process (JCP) Copyright Notice Copyright 1999-2002 Sun
Wireless Messaging API (WMA) for Java 2 Micro Edition Version 1.0 Public Review Draft (0.8) JSR 120 Expert Group JSR-120-EG@JCP.ORG Java Community Process (JCP) Copyright Notice Copyright 1999-2002 Sun
Software Development & Education Center. Java Platform, Micro Edition. (Mobile Java)
 Software Development & Education Center Java Platform, Micro Edition (Mobile Java) Detailed Curriculum UNIT 1: Introduction Understanding J2ME Configurations Connected Device Configuration Connected, Limited
Software Development & Education Center Java Platform, Micro Edition (Mobile Java) Detailed Curriculum UNIT 1: Introduction Understanding J2ME Configurations Connected Device Configuration Connected, Limited
OBA Developer s Guide, Doc.no: 3/ KRD Uen, Rev B
 2%$'HYHORSHU V *XLGH &RQWHQWV 1 Introduction...3 1.1 Who Should Read this Document?...3 1.2 Updates Since Last Revision...3 1.3 Terminology...3 2 Mobitex Network Information...5 3 MASC/OBA...6 3.1 Application
2%$'HYHORSHU V *XLGH &RQWHQWV 1 Introduction...3 1.1 Who Should Read this Document?...3 1.2 Updates Since Last Revision...3 1.3 Terminology...3 2 Mobitex Network Information...5 3 MASC/OBA...6 3.1 Application
Internet and Mobile Services 2 - Java 2 Micro Edition. F. Ricci 2009/2010
 Internet and Mobile Services 2 - Java 2 Micro Edition F. Ricci 2009/2010 Content Mobile applications Why Java on mobile devices Three main Java environments Java 2 Micro Edition Configurations and profiles
Internet and Mobile Services 2 - Java 2 Micro Edition F. Ricci 2009/2010 Content Mobile applications Why Java on mobile devices Three main Java environments Java 2 Micro Edition Configurations and profiles
Kea Messages Manual. Kea Messages Manual
 Kea Messages Manual i Kea Messages Manual Kea Messages Manual ii Copyright 2011-2015 Internet Systems Consortium, Inc. Kea Messages Manual iii Contents 1 Introduction 1 2 Kea Log Messages 2 2.1 ALLOC Module....................................................
Kea Messages Manual i Kea Messages Manual Kea Messages Manual ii Copyright 2011-2015 Internet Systems Consortium, Inc. Kea Messages Manual iii Contents 1 Introduction 1 2 Kea Log Messages 2 2.1 ALLOC Module....................................................
What HTTP is : it forms elements (.html..xml) with programs (processes) running on the server (e.g. java) and on clients (e.g. javascript), cookies).
 Beyond HTTP Up to this point we have been dealing with software tools that run on browsers and communicate to a server that generates files that can be interpreted by the browser What HTTP is : it forms
Beyond HTTP Up to this point we have been dealing with software tools that run on browsers and communicate to a server that generates files that can be interpreted by the browser What HTTP is : it forms
TFTP and FTP Basics BUPT/QMUL
 TFTP and FTP Basics BUPT/QMUL 2017-04-24 Agenda File transfer and access TFTP (Trivial File Transfer Protocol) FTP (File Transfer Protocol) NFS (Network File System) 2 File Transfer And Access 3 File Transfer
TFTP and FTP Basics BUPT/QMUL 2017-04-24 Agenda File transfer and access TFTP (Trivial File Transfer Protocol) FTP (File Transfer Protocol) NFS (Network File System) 2 File Transfer And Access 3 File Transfer
Developing Mobile Applications
 Developing Mobile Applications J2ME Java 2 Micro Edition 1 Virtual machines portable apps virtual machine native apps operating system hardware 2 Java - important issues Symbolic language not a random
Developing Mobile Applications J2ME Java 2 Micro Edition 1 Virtual machines portable apps virtual machine native apps operating system hardware 2 Java - important issues Symbolic language not a random
Computer Networks - A Simple HTTP proxy -
 Computer Networks - A Simple HTTP proxy - Objectives The intent of this assignment is to help you gain a thorough understanding of: The interaction between browsers and web servers The basics of the HTTP
Computer Networks - A Simple HTTP proxy - Objectives The intent of this assignment is to help you gain a thorough understanding of: The interaction between browsers and web servers The basics of the HTTP
Java.net Package and Classes(Url, UrlConnection, HttpUrlConnection)
 Java.net Package and Classes(Url, UrlConnection, HttpUrlConnection) Sisoft Technologies Pvt Ltd SRC E7, Shipra Riviera Bazar, Gyan Khand-3, Indirapuram, Ghaziabad Website: www.sisoft.in Email:info@sisoft.in
Java.net Package and Classes(Url, UrlConnection, HttpUrlConnection) Sisoft Technologies Pvt Ltd SRC E7, Shipra Riviera Bazar, Gyan Khand-3, Indirapuram, Ghaziabad Website: www.sisoft.in Email:info@sisoft.in
Java 2 Micro Edition
 Java 2 Micro Edition F.Ricci Content Why Java on mobile devices Three main Java environments Java 2 Micro Edition Configurations and profiles Optional packages Generic connection framework Application
Java 2 Micro Edition F.Ricci Content Why Java on mobile devices Three main Java environments Java 2 Micro Edition Configurations and profiles Optional packages Generic connection framework Application
Oracle Exam 1z0-869 Java Mobile Edition 1 Mobile Application Developer Certified Professional Exam Version: 6.0 [ Total Questions: 340 ]
![Oracle Exam 1z0-869 Java Mobile Edition 1 Mobile Application Developer Certified Professional Exam Version: 6.0 [ Total Questions: 340 ] Oracle Exam 1z0-869 Java Mobile Edition 1 Mobile Application Developer Certified Professional Exam Version: 6.0 [ Total Questions: 340 ]](/thumbs/74/70551461.jpg) s@lm@n Oracle Exam 1z0-869 Java Mobile Edition 1 Mobile Application Developer Certified Professional Exam Version: 6.0 [ Total Questions: 340 ] Topic 1, Volume A Question No : 1 - (Topic 1) How would a
s@lm@n Oracle Exam 1z0-869 Java Mobile Edition 1 Mobile Application Developer Certified Professional Exam Version: 6.0 [ Total Questions: 340 ] Topic 1, Volume A Question No : 1 - (Topic 1) How would a
Widget security model based on MIDP and Web Application based on a security model with TLS/SSL and XMLDsig
 Widget security model based on MIDP and Web Application based on a security model with TLS/SSL and XMLDsig Claes Nilsson Technology Area Group Leader Web Browsing Marcus Liwell Technology Area Group Leader
Widget security model based on MIDP and Web Application based on a security model with TLS/SSL and XMLDsig Claes Nilsson Technology Area Group Leader Web Browsing Marcus Liwell Technology Area Group Leader
Info 408 Distributed Applications programming 2 nd semester of 2017/2018 Credits: 5 Lecturer: Dr. Antoun Yaacoub
 Lebanese University Faculty of Science I Master 1 degree Computer Science Info 408 Distributed Applications programming 2 nd semester of 2017/2018 Credits: 5 Lecturer: Dr. Antoun Yaacoub Starting Network
Lebanese University Faculty of Science I Master 1 degree Computer Science Info 408 Distributed Applications programming 2 nd semester of 2017/2018 Credits: 5 Lecturer: Dr. Antoun Yaacoub Starting Network
Introduction to Java.net Package. CGS 3416 Java for Non Majors
 Introduction to Java.net Package CGS 3416 Java for Non Majors 1 Package Overview The package java.net contains class and interfaces that provide powerful infrastructure for implementing networking applications.
Introduction to Java.net Package CGS 3416 Java for Non Majors 1 Package Overview The package java.net contains class and interfaces that provide powerful infrastructure for implementing networking applications.
Mobile Devices in Software Engineering. Lab 3
 Mobile Devices in Software Engineering Lab 3 Objective The objective of this lab is to: 1. Test various GUI components on your device 2. Continue to develop application on mobile devices Experiment 1 In
Mobile Devices in Software Engineering Lab 3 Objective The objective of this lab is to: 1. Test various GUI components on your device 2. Continue to develop application on mobile devices Experiment 1 In
1Z0-869
 1Z0-869 Passing Score: 800 Time Limit: 4 min Exam A QUESTION 1 How would a MIDlet that uses a GameCanvas efficiently update only a small region of the screen, from the data in the off-screen buffer? A.
1Z0-869 Passing Score: 800 Time Limit: 4 min Exam A QUESTION 1 How would a MIDlet that uses a GameCanvas efficiently update only a small region of the screen, from the data in the off-screen buffer? A.
Faculty of Computer Science and Information Systems Jazan University MOBILE COMPUTING (CNET 426) LAB MANUAL (MOBILE APPLICATION DEVELOPMENT LAB)
 Faculty of Computer Science and Information Systems Jazan University MOBILE COMPUTING (CNET 426) LAB MANUAL (MOBILE APPLICATION DEVELOPMENT LAB) (Updated February 2017) Revised and Updated By: Dr SHAMS
Faculty of Computer Science and Information Systems Jazan University MOBILE COMPUTING (CNET 426) LAB MANUAL (MOBILE APPLICATION DEVELOPMENT LAB) (Updated February 2017) Revised and Updated By: Dr SHAMS
ICS 351: Networking Protocols
 ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
Policy Based Device Access Security Position Paper to Device Access Policy Working Group
 1 (8) Policy Based Device Access Security Position Paper to Device Access Policy Working Group 2 (8) 1. INTRODUCTION Nokia has implemented a policy-based device access security model for its Web runtime
1 (8) Policy Based Device Access Security Position Paper to Device Access Policy Working Group 2 (8) 1. INTRODUCTION Nokia has implemented a policy-based device access security model for its Web runtime
Vipera OTA Provisioning Server
 Vipera Inc 200 Page Mill Road Palo Alto, CA 94306. USA www.vipera.com info@vipera.com Vipera OTA Provisioning Server Technical Overview Version 1.0 The Vipera provisioning portal allows content providers
Vipera Inc 200 Page Mill Road Palo Alto, CA 94306. USA www.vipera.com info@vipera.com Vipera OTA Provisioning Server Technical Overview Version 1.0 The Vipera provisioning portal allows content providers
Distributed Systems COMP 212. Lecture 8 Othon Michail
 Distributed Systems COMP 212 Lecture 8 Othon Michail HTTP Protocol Hypertext Transfer Protocol Used to transmit resources on the WWW HTML files, image files, query results, Identified by Uniform Resource
Distributed Systems COMP 212 Lecture 8 Othon Michail HTTP Protocol Hypertext Transfer Protocol Used to transmit resources on the WWW HTML files, image files, query results, Identified by Uniform Resource
Lecture 2-ter. 2. A communication example Managing a HTTP v1.0 connection. Managing a HTTP request. transport session. Step 1 - opening transport
 Lecture 2-ter. 2 A communication example Managing a HTTP v1.0 connection Managing a HTTP request User digits URL and press return (or clicks ). What happens (HTTP 1.0): 1. opens a TCP transport session
Lecture 2-ter. 2 A communication example Managing a HTTP v1.0 connection Managing a HTTP request User digits URL and press return (or clicks ). What happens (HTTP 1.0): 1. opens a TCP transport session
Acknowledgments Introduction p. 1 The Wireless Internet Revolution p. 1 Why Java Technology for Wireless Devices? p. 2 A Bit of History p.
 Figures p. xiii Foreword p. xv Preface p. xvii Acknowledgments p. xxi Introduction p. 1 The Wireless Internet Revolution p. 1 Why Java Technology for Wireless Devices? p. 2 A Bit of History p. 3 J2ME Standardization
Figures p. xiii Foreword p. xv Preface p. xvii Acknowledgments p. xxi Introduction p. 1 The Wireless Internet Revolution p. 1 Why Java Technology for Wireless Devices? p. 2 A Bit of History p. 3 J2ME Standardization
Technical Manual. Motorola C381p Handset J2ME Developer Guide. Version 01.00
 Technical Manual Motorola C381p Handset J2ME Developer Guide Version 01.00 Table of Contents Table of Contents TABLE OF CONTENTS... 2 TABLE OF FIGURES... 6 INDEX OF TABLES... 7 TABLE OF CODE SAMPLES...
Technical Manual Motorola C381p Handset J2ME Developer Guide Version 01.00 Table of Contents Table of Contents TABLE OF CONTENTS... 2 TABLE OF FIGURES... 6 INDEX OF TABLES... 7 TABLE OF CODE SAMPLES...
Single Sign On for Local Devices. Application Programmer Interface (API) Guide
 Single Sign On for Local Devices Application Programmer Interface (API) Guide Issue 1 June 2013 ABSTRACT This document provides the API for the SSO-LD (Single Sign-On for Local Devices) capability, to
Single Sign On for Local Devices Application Programmer Interface (API) Guide Issue 1 June 2013 ABSTRACT This document provides the API for the SSO-LD (Single Sign-On for Local Devices) capability, to
Master Project. Push To Chat. Realized by. The Quang Nguyen. Supervisor. Professor Jean-Yves Le Boudec (EPFL, LCA) Assistant
 Master Project Push To Chat Realized by The Quang Nguyen Supervisor Professor Jean-Yves Le Boudec (EPFL, LCA) Assistant Alaeddine El Fawal (EPFL, LCA) Ecole Polytechnique Fédérale de Lausanne (EPFL) Winter
Master Project Push To Chat Realized by The Quang Nguyen Supervisor Professor Jean-Yves Le Boudec (EPFL, LCA) Assistant Alaeddine El Fawal (EPFL, LCA) Ecole Polytechnique Fédérale de Lausanne (EPFL) Winter
Lecture 3: Socket Programming
 Lecture 3: Socket Programming Prof. Shervin Shirmohammadi SITE, University of Ottawa Fall 2005 CEG4183/ELG4183 3-1 Sockets From a logical perspective, a Socket is a communication end point. It is not a
Lecture 3: Socket Programming Prof. Shervin Shirmohammadi SITE, University of Ottawa Fall 2005 CEG4183/ELG4183 3-1 Sockets From a logical perspective, a Socket is a communication end point. It is not a
OPC UA Configuration Manager PTC Inc. All Rights Reserved.
 2017 PTC Inc. All Rights Reserved. 2 Table of Contents 1 Table of Contents 2 4 Overview 4 5 Project Properties - OPC UA 5 Server Endpoints 7 Trusted Clients 9 Discovery Servers 10 Trusted Servers 11 Instance
2017 PTC Inc. All Rights Reserved. 2 Table of Contents 1 Table of Contents 2 4 Overview 4 5 Project Properties - OPC UA 5 Server Endpoints 7 Trusted Clients 9 Discovery Servers 10 Trusted Servers 11 Instance
Networking and Security
 Chapter 03 Networking and Security Mr. Nilesh Vishwasrao Patil Government Polytechnic Ahmednagar Socket Network socket is an endpoint of an interprocess communication flow across a computer network. Sockets
Chapter 03 Networking and Security Mr. Nilesh Vishwasrao Patil Government Polytechnic Ahmednagar Socket Network socket is an endpoint of an interprocess communication flow across a computer network. Sockets
Internet Protocol. Chapter 5 Protocol Layering. Juho Kim Graduate School of Information & Technology Sogang University
 Internet Protocol Chapter 5 Protocol Layering Juho Kim Graduate School of Information & Technology Sogang University Department of of Computer Science and and Engineering, Sogang University Page 1 CAD
Internet Protocol Chapter 5 Protocol Layering Juho Kim Graduate School of Information & Technology Sogang University Department of of Computer Science and and Engineering, Sogang University Page 1 CAD
Programming Methods Dr Robert Harle
 Programming Methods Dr Robert Harle IA NST CS and CST Lent 2008/09 Handout 4 Our Motivating Example We re going to make the world s simplest web server It s not going to challenge apache etc But it will
Programming Methods Dr Robert Harle IA NST CS and CST Lent 2008/09 Handout 4 Our Motivating Example We re going to make the world s simplest web server It s not going to challenge apache etc But it will
IT 341: Introduction to System
 IT 341: Introduction to System Administration Private IP Addresses and the Internet Using IP Addresses to Communicate Over the Internet Network Address Translation Private IP Addresses and the Internet
IT 341: Introduction to System Administration Private IP Addresses and the Internet Using IP Addresses to Communicate Over the Internet Network Address Translation Private IP Addresses and the Internet
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
Introduction to computer networking
 Introduction to computer networking First part of the assignment Academic year 2017-2018 Abstract In this assignment, students will have to implement a client-server application using Java Sockets. The
Introduction to computer networking First part of the assignment Academic year 2017-2018 Abstract In this assignment, students will have to implement a client-server application using Java Sockets. The
Mobile Services 2 - Java 2 Micro Edition. F. Ricci
 Mobile Services 2 - Java 2 Micro Edition F. Ricci Content Why Java on mobile devices Three main Java environments Java 2 Micro Edition Configurations and profiles Optional packages Generic connection framework
Mobile Services 2 - Java 2 Micro Edition F. Ricci Content Why Java on mobile devices Three main Java environments Java 2 Micro Edition Configurations and profiles Optional packages Generic connection framework
Sequence Number. Acknowledgment Number. Data
 CS 455 TCP, Page 1 Transport Layer, Part II Transmission Control Protocol These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang's courses at GMU can make
CS 455 TCP, Page 1 Transport Layer, Part II Transmission Control Protocol These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang's courses at GMU can make
Mobile Services 2 - Java 2 Micro Edition. F. Ricci 2008/2009
 Mobile Services 2 - Java 2 Micro Edition F. Ricci 2008/2009 Content Mobile applications Why Java on mobile devices Three main Java environments Java 2 Micro Edition Configurations and profiles Optional
Mobile Services 2 - Java 2 Micro Edition F. Ricci 2008/2009 Content Mobile applications Why Java on mobile devices Three main Java environments Java 2 Micro Edition Configurations and profiles Optional
ST.MARTIN'S ENGINEERING COLLEGE Dhulapally,Secunderabad-014
 ST.MARTIN'S ENGINEERING COLLEGE Dhulapally,Secunderabad-014 INFORMATION TECHNOLOGY TUTORIAL QUESTION BANK Course Title Course Code Regulation Course Structure Team of Instructors Mobile Application Development
ST.MARTIN'S ENGINEERING COLLEGE Dhulapally,Secunderabad-014 INFORMATION TECHNOLOGY TUTORIAL QUESTION BANK Course Title Course Code Regulation Course Structure Team of Instructors Mobile Application Development
Cisco Expressway with Jabber Guest
 Cisco Expressway with Jabber Guest Deployment Guide First Published: Decemeber 2016 Cisco Expressway X8.9 Cisco Jabber Guest Server 10.6.9 (or later) Cisco Systems, Inc. www.cisco.com Contents Preface
Cisco Expressway with Jabber Guest Deployment Guide First Published: Decemeber 2016 Cisco Expressway X8.9 Cisco Jabber Guest Server 10.6.9 (or later) Cisco Systems, Inc. www.cisco.com Contents Preface
Chapter 4: Processes
 Chapter 4: Processes Process Concept Process Scheduling Operations on Processes Cooperating Processes Interprocess Communication Communication in Client-Server Systems 4.1 Process Concept An operating
Chapter 4: Processes Process Concept Process Scheduling Operations on Processes Cooperating Processes Interprocess Communication Communication in Client-Server Systems 4.1 Process Concept An operating
CS434/534: Topics in Networked (Networking) Systems
 CS434/534: Topics in Networked (Networking) Systems WSN/Mobile Systems Yang (Richard) Yang Computer Science Department Yale University 208A Watson Email: yry@cs.yale.edu http://zoo.cs.yale.edu/classes/cs434/
CS434/534: Topics in Networked (Networking) Systems WSN/Mobile Systems Yang (Richard) Yang Computer Science Department Yale University 208A Watson Email: yry@cs.yale.edu http://zoo.cs.yale.edu/classes/cs434/
GIVE W INGS TO YOUR IDEAS
 GIVE W INGS TO YOUR IDEAS Using TCP and UDP under Open-AT Revision: 001 Date: June 2003 PLUG IN TO THE WIRELESS WORLD Author: Wavecom Support Consultant Date: 23 th June 2005 APN Content Level BASIC INTERMEDIATE
GIVE W INGS TO YOUR IDEAS Using TCP and UDP under Open-AT Revision: 001 Date: June 2003 PLUG IN TO THE WIRELESS WORLD Author: Wavecom Support Consultant Date: 23 th June 2005 APN Content Level BASIC INTERMEDIATE
Inspirel. YAMI4 Requirements. For YAMI4Industry, v page 1
 YAMI4 Requirements For YAMI4Industry, v.1.3.1 www.inspirel.com info@inspirel.com page 1 Table of Contents Document scope...3 Architectural elements...3 Serializer...3 Socket...3 Input buffer...4 Output
YAMI4 Requirements For YAMI4Industry, v.1.3.1 www.inspirel.com info@inspirel.com page 1 Table of Contents Document scope...3 Architectural elements...3 Serializer...3 Socket...3 Input buffer...4 Output
JAVA. Java Micro Edition
 JAVA Java Micro Edition Overview predecessors Personal Java (1997) Embedded Java (1998) JME definition via JCP JCP Java Community Process JME is not a single SW package a set of technologies and specifications
JAVA Java Micro Edition Overview predecessors Personal Java (1997) Embedded Java (1998) JME definition via JCP JCP Java Community Process JME is not a single SW package a set of technologies and specifications
A socket is a software endpoint that establishes bidirectional communication between a server program and one or more client programs.
 PART 24 Java Network Applications 24.1 Java Socket Programming A socket is a software endpoint that establishes bidirectional communication between a server program and one or more client programs. A server
PART 24 Java Network Applications 24.1 Java Socket Programming A socket is a software endpoint that establishes bidirectional communication between a server program and one or more client programs. A server
Spirent Datum Mobile Client Guide J2ME
 Spirent Datum Mobile Client Guide J2ME Spirent Communications 5280 Corporate Drive, Suite A100 Frederick, MD 21703 Document Version: 1.3 Contents 1 Introduction... 3 1.1 Datum Mobile for J2ME Installation
Spirent Datum Mobile Client Guide J2ME Spirent Communications 5280 Corporate Drive, Suite A100 Frederick, MD 21703 Document Version: 1.3 Contents 1 Introduction... 3 1.1 Datum Mobile for J2ME Installation
