ADAPTABLE SERVICES AND APPLICATIONS FOR NETWORKS
|
|
|
- Mabel Thornton
- 5 years ago
- Views:
Transcription
1 ADAPTABLE SERVICES AND APPLICATIONS FOR NETWORKS Josep Polo and Jaime Delgado Universität Pompeu Fabra. Technology Department, Psg. de Circumvallaciö, 8, Barcelona, Spain Abstract: New services and applications that use extensively telecommunication networks are currently developed. They need an open access to the telecommunication networks for adapting to them. An API (Application Programming Interface) that permits this objective is the Parlay/OS A API. Operators offer tools that facilitate the development of applications and services, but these tools are different, so it is not possible to develop a unique application for different operators. To solve this great inconvenience, we propose a solution to permit interoperability among different development tools. Key words: Parlay; OSA; network; application; service. 1. INTRODUCTION The use of netv^ork services is growing. In order to facilitate their development an API that offers many advantages is Parlay and Open Service Access (OSA). This API facilitates the services development, but it is still very complex, difficult and hard to use. Many operators and service providers offer different development tools, SDKs (Software Development Kit), that facilitate the development and implementation phases. This document begins with an introduction about the Parlay/OSA (P/OSA) API and it shows its complexity. Then, it demonstrates how a service can be developed using those tools more easily that directly with the API. We show one application for each SDK. Later, we propose a solution to interoperability among different SDKs. We suggest a method to develop a unique service to be used in several SDKs, and finally we obtain some conclusions.
2 14 Josep Polo and Jaime Delgado 2. PARLAY/OSA OVERVIEW Parlay and OSA (P/OSA) are an open API for communications networks. This API can support present and future networks. It provides a layer of abstraction for service developers. It enables telecom operators and service providers to offer the same services for all existing underlying networks: mobile, fixed and IP networks, without adapting the application to network specific protocols. This API permits to obtain network-related context information, it can facilitate value-added services development, it can make network communications simpler and powerful, independently of which type of network. 2.1 Description The P/OSA model is split into three main entities [12]: The client application: the application developed by a third party can access to the network features through the P/OSA interface. The framework: it offers support functions. For instance, security, integrity and management features. The services: they offer access to network features. For instance mobility, messaging, terminal management, user interaction and call control. P/OSA has several interfaces to allow access to different network functionalities or services [12]: Framework, Call control, Data session control, User interaction. Mobility, Generic messaging, Terminal capabilities, Connectivity management, Account management. Charging, Policy management, Presence and availability management. 2.2 Application architecture When developing a service to use P/OSA, it has three main steps: Authentication: before the application can use the network services, the application and the framework authenticate each other. Authentication prevents unauthorized access to the services and permits to determine the privileges and permissions to the application. Service selection: after the authentication phase, the application can select the service interface to use. It is usual to sign an agreement before use of the interface. The application can select the service to use. Service use: if the previous phases have concluded properly, the application can use the selected service. To obtain a general idea on interface use, we shall explain only the first step. This step is common for all developing services or applications and before it can use any network service there must be an authentication step.
3 Adaptable Services and Applications for Networks This step has several phases: The application performs an initial contact to the framework. In this first contact the application requests authentication. The framework answers with the authentication to be used. Then the application requests authentication from the framework. After the previous authentication, the framework requests authentication from the application. When the application and framework have authenticated each other, the application can select the service interface to use. This corresponds to the service selection step. These phases correspond to many operations. The authentication step is a quite simple operation. The other steps are usually more complicated and large, depending on the service. The previous authentication step description is enough to show a good idea of the use of P/OSA. From the previous paragraphs it can be concluded that the direct use of P/OSA can be very complicated, tedious, difficult and long effort. To solve this situation, few libraries exist. They shield the details of P/OSA use. They provide abstraction from the original API. Usually, these libraries are developed to use Java APIs. 1^ 3. DEVELOPMENT TOOLS Many operators have developed tools that facilitate the effort to create applications. Usually, these tools are composed by a SDK and a simulator. Those SDKs and simulators share characteristics. The most important are: Java software libraries. P/OSA defines a language-independent API and they use the Object Management Group (OMG) [6] Unified Modelling Language (UML) and Interface Definition Language (IDL) [5] that is based on the OMG's CORE A LDL. Using Java libraries permits the abstraction from the CORBA. Partial emulation of P/OSA APIs. The systems don't support all P/OSA interfaces. They are enough for developing and testing most applications. They can run on an off-line way, no network connection is needed if a simulator is used. This can permit an easy application development. They have a similar structure. They offer a Java library, which simplify the development, but the application can use CORBA, if necessary. To simplicity and avoid confusion, we show only two of them to obtain a general idea of their use. They are: Lucent - MiLife ISG SDK [5] (MI SDK) and Ericsson NRG SDK [1] (EN SDK).
4 16 Josep Polo and Jaime Delgado 4. SERVICE AND APPLICATION IMPLEMENTATION Services and applications have three big parts, when using these systems: Initialization. In this step the application initializes all needed processes and obtains all resources for the correct operation, and interacts with the framework, which enables an application to obtain and release service managers. Main functionality. This is the most important part of the application. In this step the application interacts with the network to do the features for those it is developed. It uses service managers to send requests to the network, and receives responses from the network. Finalization. The application stops interacting with the network. The service managers are released and framework access is terminated. All applications have the first and third phases (initialization and finalization) very similar, but the actually important step is the second one (main functionality). Each application has this phase different. To show how to implement a service or application using these tools, we explain the main steps necessaries for a simple sample application. We think that it is enough to have a good idea how a service can be developed. 4.1 Sample application The sample application demonstrates the framework. It obtains and shows available services defined in the network. The basic steps of each three main parts of this application are: Initialization. - Prepare the resources and add components and read the configuration - Initiate the access to the framework Main functionality. - Obtain the names of all available service types - Obtain a service manager Finalization. - Releases a service manager by terminating its service level agreement - Release the system resources obtained in the initialization phase Following sections show the most important operations to use each SDK Lucent - MiLife ISG SDK We focus on how to use the MI SDK to obtain the desired P/OSA functionality. We only describe the operations that perform those functions. The interfaces use (see section 2.2) has three main steps: authentication, service selection and service use. The first step, authentication, correspond
5 Adaptable Services and Applications for Networks 17 to the initial operations, before the service use. The first step can be done using the class FrameworkAdapterFactory. A framework adapter can be created using this class. The sentence is: FrameworkAdapterObject = FrameworkAdapterlnstance,createFrameworkAdapter (validauthenticationcredentials); The FrameworkAdapter is an interface that defines the framework classes. A reference to this interface can be obtained by the previous method. The validauthenticationcredentials are parameters that have been set to proper values. This single operation performs that first step, authentication. The needed operations, if P/OSA is used directly, are related in section 2.2. It can be seen that this class performs most work and simplifies the application development. The following operation is to obtain the available services. This can be done using the method listservices. The sentence to use is: String[] object = FrameworkAdapterObject.listServices(); This method returns a list of available services. The next operation is to obtain the service adapter. This operation can be done using a method specific to the wanted service. For instance, if we want to select the User Location service, the sentence to use is: serviceadapter = FrameworkAdapterObject.selectUserLocationService(); This service permits to obtain the geographical location of users, but if we want to select the Messaging service, to manage, send or receive messages, the sentence to use is: serviceadapter = FrameworkAdapterObject.selectMessagingService() ; As we can see, each service is selected using a specific method. Then the service can be used. When the services are no longer needed, it is necessary to release resources. This operation begins with the method destroy. The sentence to use is: serviceadapter. destroy (); It allows this adapter to clean up when it is no longer used. The releasing operation continues using the method endaccess that releases resources used by the framework. The sentence to use is: FrameworkAdapterOb ject. endaccess (). It ends the access session. Finally, the method to use is destroy. This method allows the FrameworkAdapter to clean up when it is no longer used. The sentence to use is: FrameworkAdapterOb ject. destroy ();
6 18 Josep Polo and Jaime Delgado Ericsson NRG SDK In this section we focus on how to use the EN SDK to obtain the desired P/OSA functionahty. The first step can be done using the class FWproxy. This class is for handling interaction with the framework, which enables an application to obtain and release service managers. The sentence to use is: FwproxyObject = new Fwproxy(configuration); The configuration has been set previously to proper values. The following operation is to obtain the available services. This can be done using the method listservicetypes of the class FWproxy. The sentence to use is: String[] object = FwproxyObject.listServiceTypes(); The FwproxyOb ject is the previously object created. This operation returns the names of all available service types. The next operation is to obtain the service manager. This operation can be done using the method obtainscf of the class FWproxy. The sentence to use is: IpServiceObject = FwproxyObject.obtainSCF(UserLocation) ; The UserLocation is the service to use. This operation returns a service manager. In this example, this service allows application to obtain the geographical location of users. Or if we want to manage, send or receive messages, for instance, then the sentence is: IpServiceObject = FwproxyObject,obtainSCF(Message); When the service is no longer needed, it is necessary to release resources. This operation begins using the method releasescf of Fwproxy. The sentence to use is: FwproxyObject.releaseSCF(IpServiceObject); The releasing operation continues using the method endaccess that releases resources used by the framework. It belongs to the class FWproxy. The sentence to use is: FwproxyOb ject. endaccess (); The method to releases all resources is dispose of the class FWproxy. FwproxyObject.dispose(); 5. INTEROPERABILITY In the previous sections we have seen that those SDKs are different. Due to this reason, a unique application cannot be used with different SDKs. It is necessary to develop different applications, one for each SDK. Those applications are nearly equal except the use of P/OSA interface through SDK
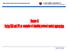
7 Adaptable Services and Applications for Networks 19 Java libraries. To isolate the developing application from the particular SDK used we propose to use an interface that hides the particular implementation of each SDK. This interface is in a preliminary status. In this section we present the first results, that where introduced in [8]. This interface shows to developing application unique classes to access P/OSA interfaces, independently of which library used. In following sections we show a possible implementation of this interface. This interface can consists in a set of unique classes with different implementations. This can be done in Java using abstract classes. The new developing application uses the abstract classes and depending on which SDK we want to use, we utilize an implementation or another. All particular details are encapsulated on each implementation. Following sections show this interface applied to the framework. There is an abstract framework class and two no abstract framework classes, one for each SDK. 5.1 Framework abstract class The abstract classes contain a definition for all SDKs, These classes have the methods to access the P/OSA interfaces to be used by the application. Figure 1 shows a possible abstract class for the framework that contains the definition of few methods, it is not complete. They are some of the initialization and finalization steps methods. None of then is implemented, because the implementation depends on the particular SDK used. act. String i 1 i act. void endacce Figure 1. Framework abstract class. This abstract class defines a neutral framework. As we can see, there is not any constructor. The constructor task will be done by next classes. They create the framework object: a FrameworkAdapterFactory (MI SDK) or a Fwproxy (EN SDK). This class only contains method definitions that apply on the created object. It is necessary to define more abstract classes for all those classes that exist in each Java library. For instance, when the framework is successful accessed, next step is to obtain the service manager. In MI SDK is a service dependent class (UserLocationAdapter, MessagingAdapter, etc.) and in EN SDK is an IpService. 5.2 ISG framework class When using MI SDK we actually want to use FrameworkAdapter.
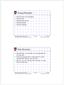
8 20 Josep Polo and Jaime Delgado We define a class that inherits from the abstract class all its methods, it implements them and adds the framework constructor. Figure 2 shows a possible implementation of the framework if MI SDK is used. public class ISGFramework extends Framework ( FrameworkAdapter fwisg; // ISG framework public ISGFramework{) ( // ISG constructor FrameworkAdapterFactory.createFrameworkAdapter{"Sample","psw"); ) public String [) list Services() { return fwlsg.1 ist Services() ; // list the available ISG services ) public void endaccess () ( fwisg.endaccess(); // releases resources used by the ISG framework public void destroy () ( fwisg.destroy 0 ; // disposes the ISG ) } Figure 2. ISG framework class. framework As we can see, all general methods (abstract methods in framework class, Figure 1) use the particular methods defined in MI SDK. Most methods are very simple: they use MI SDK methods directly. For instance destroy method uses the dispose ISG method. Section shows the MI SDK methods listed in Figure 2. Not all methods are so simple as shown, but to demonstrate the essence of this interface, this example is enough. 5.3 NRG framework class public class NRGFramework extends Framework { FWproxy fwnrg; // NRG framework public NRGFramework () f // constructor Configuration. INSTANCE. loadc con figu ration.ini") ; fwnrg = new FWproxy (Configuration.INSTANCE) ; // NRG constructor } public String (] 1istServices () I return fwnrg.1 istservicetypes() ; // list the available NRG services public void endaccess ()( fwnrg.endaccess(); // releases resources used by the NRG framework ) public void destroy () f fwnrg.dispose(); // disposes the NRG framework Figure 3. NRG framework class. When using EN SDK we actually have to use Fwproxy. As previous class, we define a class that inherit from the abstract class all its methods and adds the framework constructor. Figure 3 shows a possible implementation of the framework class if EN SDK is used. 5.4 The application The application corresponds to the developed application. This sample is
9 Adaptable Services and Applications for Networks 21 very simple and only creates the framework, then obtain an available service list, it shows them and finally release all sources. Figure 4 shows this simple application. (String[] args) ( amework object t; // list of avaliable fw = new ISGFranieworkC); // ISG framework creator servicelist = fw.listservices(); // obtains the service list for (Int i-0; 1 < service!, ist. length; i + t) Systerii.out.println("Service =" + servlcelist(il); // sho fw.endaccess(); // releases resources used by the framework fw,destroy(); // disposes the framework Figure 4. Sample application. As we can see, only at the application beginning there is an explicit indication of which SDK we are using. Then, later the application doesn't care about that question. All methods used are those in the abstract class (Figure 1), but when the application runs, the real methods used are those in the ISG framework class (Figure 2) if the MI SDK is used or the NRG framework class (Figure 3) if the NE SDK is used. 6. CONCLUSIONS The objective of P/OSA is to open an interface network to third parties, to permit developing new applications and services. We have shown that it is very powerful to develop new applications that use the telecommunication networks, although those interfaces shield most of the detail and eliminates most effort, those interfaces are very complex, difficult and hard to use. Several SDKs exist that solve these obstacles. They permit to use the Java language, simplifying the portability of the applications. This fact permits the use of very different terminals and resources, expanding, in a wide way, the use and reuse of the developed applications. These SDKs have simulators that permit to develop application without accessing to a network. They can be done in a stand-alone way, without the difficulty that can add the fact to access a real network. Those tools have a disadvantage: they don't support all interfaces defined in P/OSA, but they are enough for developing and test most applications. We have shown the main steps that are necessary for developing an application: initialization, main functionality and finalization. We have applied those steps to a sample application to two SDKs: Lucent - MiLife ISG SDK and Ericsson NRG SDK. We have developed two sample applications, one for each SDK. They are only different when accessing to P/OSA functionality. So, it is necessary to develop an application for each SDK intended to use. To isolate the application from the particular SDK we propose to use an interface that hides the particular implementation of each SDK.
10 22 Josep Polo and Jaime Delgado This interface is composed by a set of abstract classes that define a generic use of P/OSA and different implementations, depending on which SDKs want to be used. We have shown a partial implementation of this interface and we have applied to a sample application to show their structure and use. The whole interface is more complicated than that shown in this document, but this one is enough to show its philosophy and the way to develop applications. This is only a preliminary work. We are currently working to expand these results: extend the interface to the whole SDK and to cover more SDKs. It is expected that few parts of SDKs will be more difficult to implement than others, and that few SDKs will be more complex than others. Due to this reason, we cannot assure that we will be able to apply this interface to all existing SDKs. We are currently working on these problems and we will report our results in the future. ACKNOWLEDGEMENTS This work has been partly supported by the Spanish administration (AgentWeb project, TIC ) and is being developed within VISNET (IST , a European Network of Excellence, funded under the European Commission 1ST FP6 program. REFERENCES 1. Ericsson NRG Simulator and Software Development Kit (SDK) 2. ETSI ES Vl.2.1 ( ) Open Service Access (OSA); Application Programming Interface (API) 3. MiLife"^^ ISG SDK 3.0 Documentation. CTID+2019-STID SOID+966- LOCL+l,00.html 4. Ard-Jan Moerdijk, Lucas Klostermann. Opening the Networkswith Parlay/OSA: Standards and Aspects Behind the APIs. IEEE Network. May/June Stephen M. Mueller. APIs and Protocols for Convergent Network Services. McGraw Hill. USA Object Manager Group, 7. The Open API Solutions Application Test Suite 8. J. Polo, J. Delgado. An easy way to develop mobile and wireless applications. 7^^ Int. Conf. Mobile and Wireless Communications Networks. To be published (Sep. 2005). 9. The 3rd Generation Partnership Project (3GPP) E. Vanem et al. Managing heterogeneous services and devices with the device unifying service. Implemented with Parlay APIs.8^*^ Int. Sym. Integrated Networks Manag., U.E. Vanem et al. Realising Service Portability with the Device Unifying Service using Parlay API. International Conference on Communications, J. Zuidweg. Next generation intelligent networks. Boston [etc.]: Artech House, cop
Telecommunication Services Engineering Lab. Roch H. Glitho
 1 Introduction Signaling protocol neutral service engineering technology Service architecture applicable to NGNs using any signalling protocol Next Generation signalling protocols SIP H.323 Example already
1 Introduction Signaling protocol neutral service engineering technology Service architecture applicable to NGNs using any signalling protocol Next Generation signalling protocols SIP H.323 Example already
Simple Service Developed with Ericsson OSA/Parlay Simulator
 Mobile Open Society through Wireless Telecommunications MOST International Conference 7-8 October 2002, Warsaw, Poland Simple Service Developed with Ericsson OSA/Parlay Simulator Michał Rój, Jarosław Domaszewicz
Mobile Open Society through Wireless Telecommunications MOST International Conference 7-8 October 2002, Warsaw, Poland Simple Service Developed with Ericsson OSA/Parlay Simulator Michał Rój, Jarosław Domaszewicz
Analysis of Effectiveness of Open Service Architecture for Fixed and Mobile Convergence
 Analysis of Effectiveness of Open Service Architecture for Fixed and Mobile Convergence Kyung-Hyu Lee* Jeung-Heon Hahn* Electronics and Telecommunications Research Institute* Email: {khyulee, stevehahn
Analysis of Effectiveness of Open Service Architecture for Fixed and Mobile Convergence Kyung-Hyu Lee* Jeung-Heon Hahn* Electronics and Telecommunications Research Institute* Email: {khyulee, stevehahn
Parlay Service Access Requirements
 Parlay Service Access Requirements Candidate Version 1.0 01 Dec 2009 Open Mobile Alliance OMA-RD-PSA-V1_0-20091201-C [OMA-Template-Spec-20080430-I] OMA-RD-PSA-V1_0-20091201-C Page 2 (2) Use of this document
Parlay Service Access Requirements Candidate Version 1.0 01 Dec 2009 Open Mobile Alliance OMA-RD-PSA-V1_0-20091201-C [OMA-Template-Spec-20080430-I] OMA-RD-PSA-V1_0-20091201-C Page 2 (2) Use of this document
INSE 7110 Winter 2008 Value Added Services Engineering in Next Generation Networks Week #6, Lecture 6. Roch H. Glitho- Ericsson/Concordia University
 INSE 7110 Winter 2008 Value Added Services Engineering in Next Generation Networks Week #6, Lecture 6 1 efinition... Signaling protocol neutral architecture Service architecture applicable to networks
INSE 7110 Winter 2008 Value Added Services Engineering in Next Generation Networks Week #6, Lecture 6 1 efinition... Signaling protocol neutral architecture Service architecture applicable to networks
Parlay Service Access Architecture
 Parlay Service Access Architecture Approved Version 1.0 27 Apr 2010 Open Mobile Alliance OMA-AD-Parlay_Service_Access-V1_0-20100427-A OMA-AD-Parlay_Service_Access-V1_0-20100427-A Page 2 (10) Use of this
Parlay Service Access Architecture Approved Version 1.0 27 Apr 2010 Open Mobile Alliance OMA-AD-Parlay_Service_Access-V1_0-20100427-A OMA-AD-Parlay_Service_Access-V1_0-20100427-A Page 2 (10) Use of this
ETSI TS V4.5.0 ( )
 TS 129 198-7 V4.5.0 (2003-03) Technical Specification Universal Mobile Telecommunications System (UMTS); Open Service Access (OSA) Application Programming Interface (API); Part 7: Terminal capabilities
TS 129 198-7 V4.5.0 (2003-03) Technical Specification Universal Mobile Telecommunications System (UMTS); Open Service Access (OSA) Application Programming Interface (API); Part 7: Terminal capabilities
ITU-T Y Next generation network evolution phase 1 Overview
 I n t e r n a t i o n a l T e l e c o m m u n i c a t i o n U n i o n ITU-T Y.2340 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (09/2016) SERIES Y: GLOBAL INFORMATION INFRASTRUCTURE, INTERNET PROTOCOL
I n t e r n a t i o n a l T e l e c o m m u n i c a t i o n U n i o n ITU-T Y.2340 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (09/2016) SERIES Y: GLOBAL INFORMATION INFRASTRUCTURE, INTERNET PROTOCOL
ETSI ES V1.1.1 ( )
 ES 201 915-7 V1.1.1 (2002-02) Standard Open Service Access (OSA); Application Programming Interface (API); Part 7: Terminal Capabilities SCF 2 ES 201 915-7 V1.1.1 (2002-02) Reference DES/SPAN-120070-7
ES 201 915-7 V1.1.1 (2002-02) Standard Open Service Access (OSA); Application Programming Interface (API); Part 7: Terminal Capabilities SCF 2 ES 201 915-7 V1.1.1 (2002-02) Reference DES/SPAN-120070-7
Appendix A - Glossary(of OO software term s)
 Appendix A - Glossary(of OO software term s) Abstract Class A class that does not supply an implementation for its entire interface, and so consequently, cannot be instantiated. ActiveX Microsoft s component
Appendix A - Glossary(of OO software term s) Abstract Class A class that does not supply an implementation for its entire interface, and so consequently, cannot be instantiated. ActiveX Microsoft s component
IP-PBX for Service Oriented Architectures Communications Web Services
 NEC Sphere Communications, Inc. 300 Tristate International, 150 Lincolnshire, IL 60069 www.necsphere.com IP-PBX for Service Oriented Architectures Communications Web Services Introduction Enterprise communications
NEC Sphere Communications, Inc. 300 Tristate International, 150 Lincolnshire, IL 60069 www.necsphere.com IP-PBX for Service Oriented Architectures Communications Web Services Introduction Enterprise communications
Converging towards Service Centric Networks: Requirements for a Service Delivery Platform Framework
 Converging towards Centric Networks: Requirements for a Delivery Platform Framework Rolan Christian and Hu Hanrahan Centre for Telecommunications Access and s 1 School of Electrical and Information Engineering
Converging towards Centric Networks: Requirements for a Delivery Platform Framework Rolan Christian and Hu Hanrahan Centre for Telecommunications Access and s 1 School of Electrical and Information Engineering
Component-Level Design. Slides copyright 1996, 2001, 2005, 2009 by Roger S. Pressman. For non-profit educational use only
 Chapter 10 Component-Level Design Slide Set to accompany Software Engineering: A Practitioner s Approach, 7/e by Roger S. Pressman Slides copyright 1996, 2001, 2005, 2009 by Roger S. Pressman For non-profit
Chapter 10 Component-Level Design Slide Set to accompany Software Engineering: A Practitioner s Approach, 7/e by Roger S. Pressman Slides copyright 1996, 2001, 2005, 2009 by Roger S. Pressman For non-profit
Developing OSA-based Applications over the Interworking WLAN and Cellular Network Environment
 Developing OSA-based s over the Interworking WLAN and Cellular Network Environment Chung-Ming Huang, Tz-Heng Hsu, and Chih-Wen Chao Laboratory of Multimedia Mobile Networking Department of Computer Science
Developing OSA-based s over the Interworking WLAN and Cellular Network Environment Chung-Ming Huang, Tz-Heng Hsu, and Chih-Wen Chao Laboratory of Multimedia Mobile Networking Department of Computer Science
A Consumer Premises End User Interface for OSA/Parlay Applications Thabo Machethe
 A Consumer Premises End User Interface for OSA/Parlay Applications Thabo Machethe A project report submitted to the Faculty of Engineering, University of the Witwatersrand, Johannesburg, in partial fulfilment
A Consumer Premises End User Interface for OSA/Parlay Applications Thabo Machethe A project report submitted to the Faculty of Engineering, University of the Witwatersrand, Johannesburg, in partial fulfilment
IP PBX for Service Oriented Architectures Communications Web Services
 IP PBX for Service Oriented Architectures Communications Web Services.......... Introduction Enterprise communications have traditionally been provided by closed, stand-alone PBX systems. Installed in
IP PBX for Service Oriented Architectures Communications Web Services.......... Introduction Enterprise communications have traditionally been provided by closed, stand-alone PBX systems. Installed in
Service Architecture for 3rd Party Operator s Participation
 Service Architecture for 3rd Party Operator s Participation F. Sarabchi, A. H. Darvishan, H. Yeganeh, and H. Ahmadian Abstract Next generation networks with the idea of convergence of service and control
Service Architecture for 3rd Party Operator s Participation F. Sarabchi, A. H. Darvishan, H. Yeganeh, and H. Ahmadian Abstract Next generation networks with the idea of convergence of service and control
Defining Generic Architectural Requirements for the Service Delivery Platform
 Defining Generic Architectural Requirements for the Service Delivery Platform Rolan Christian and Hu Hanrahan Centre for Telecommunications Access and Services 1 School of Electrical and Information Engineering
Defining Generic Architectural Requirements for the Service Delivery Platform Rolan Christian and Hu Hanrahan Centre for Telecommunications Access and Services 1 School of Electrical and Information Engineering
Quality of Service Management for the Virtual Home Environment
 Quality of Service Management for the Virtual Home Environment Alvin Yew, Christos Bohoris, Antonio Liotta and George Pavlou Centre for Communication Systems Research, School of Electronics, Computing
Quality of Service Management for the Virtual Home Environment Alvin Yew, Christos Bohoris, Antonio Liotta and George Pavlou Centre for Communication Systems Research, School of Electronics, Computing
JAIN TM and Open Networks
 JAIN TM and Open Networks A white paper describing the positioning of the JAIN Application Programming Interfaces (APIs) within open network architectures August 2003 http://java.sun.com/products/jain
JAIN TM and Open Networks A white paper describing the positioning of the JAIN Application Programming Interfaces (APIs) within open network architectures August 2003 http://java.sun.com/products/jain
IP Multimedia Subsystem Part 5 Marek Średniawa
 IP Multimedia Subsystem Part 5 Marek Średniawa mareks@tele.pw.edu.pl Institute of Telecommunications Project is co-financed by European Union within the European Social Fund 1 Identification in IMS Identities
IP Multimedia Subsystem Part 5 Marek Średniawa mareks@tele.pw.edu.pl Institute of Telecommunications Project is co-financed by European Union within the European Social Fund 1 Identification in IMS Identities
Element: Relations: Topology: no constraints.
 The Module Viewtype The Module Viewtype Element: Elements, Relations and Properties for the Module Viewtype Simple Styles Call-and-Return Systems Decomposition Style Uses Style Generalization Style Object-Oriented
The Module Viewtype The Module Viewtype Element: Elements, Relations and Properties for the Module Viewtype Simple Styles Call-and-Return Systems Decomposition Style Uses Style Generalization Style Object-Oriented
Software interoperability in the NGN Service layer
 Software interoperability in the NGN Service layer Dave Penkler CTO OpenCall, HP 2004 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice Presentation
Software interoperability in the NGN Service layer Dave Penkler CTO OpenCall, HP 2004 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice Presentation
Final draft ETSI ES V1.4.1 ( )
 Final draft ES 202 915-6 V1.4.1 (2006-10) Standard Open Service Access (OSA); Application Programming Interface (API); Part 6: Mobility SCF (Parlay 4) 2 Final draft ES 202 915-6 V1.4.1 (2006-10) Reference
Final draft ES 202 915-6 V1.4.1 (2006-10) Standard Open Service Access (OSA); Application Programming Interface (API); Part 6: Mobility SCF (Parlay 4) 2 Final draft ES 202 915-6 V1.4.1 (2006-10) Reference
IMS signalling for multiparty services based on network level multicast
 IMS signalling for multiparty services based on network level multicast Ivan Vidal, Ignacio Soto, Francisco Valera, Jaime Garcia, Arturo Azcorra UniversityCarlosIIIofMadrid Av.Universidad,30 E-28911, Madrid,
IMS signalling for multiparty services based on network level multicast Ivan Vidal, Ignacio Soto, Francisco Valera, Jaime Garcia, Arturo Azcorra UniversityCarlosIIIofMadrid Av.Universidad,30 E-28911, Madrid,
Object Security. Model Driven Security. Ulrich Lang, Rudolf Schreiner. Protection of Resources in Complex Distributed Systems
 Object Security TM The Security Policy Company Protection of Resources in Complex Distributed Systems Ulrich Lang, Rudolf Schreiner ObjectSecurity Ltd. University of Cambridge Agenda COACH Project Model
Object Security TM The Security Policy Company Protection of Resources in Complex Distributed Systems Ulrich Lang, Rudolf Schreiner ObjectSecurity Ltd. University of Cambridge Agenda COACH Project Model
A Business Model for Dynamic Composition of Telecommunication Web Services
 WEB SERVICES IN TELECOMMUNICATIONS A Business Model for Dynamic Composition of Telecommunication Web Services Rajesh Karunamurthy and Ferhat Khendek, Concordia University Roch H. Glitho, Ericsson and Concordia
WEB SERVICES IN TELECOMMUNICATIONS A Business Model for Dynamic Composition of Telecommunication Web Services Rajesh Karunamurthy and Ferhat Khendek, Concordia University Roch H. Glitho, Ericsson and Concordia
CERTIFICATION SUCCESS GUIDE ENTERPRISE ARCHITECT FOR JAVA 2 PLATFORM, ENTERPRISE EDITION (J2EE ) TECHNOLOGY
 SUN CERTIFICATION CERTIFICATION SUCCESS GUIDE ENTERPRISE ARCHITECT FOR JAVA 2 PLATFORM, ENTERPRISE EDITION (J2EE ) TECHNOLOGY TABLE OF CONTENTS Introduction..............................................
SUN CERTIFICATION CERTIFICATION SUCCESS GUIDE ENTERPRISE ARCHITECT FOR JAVA 2 PLATFORM, ENTERPRISE EDITION (J2EE ) TECHNOLOGY TABLE OF CONTENTS Introduction..............................................
An Architecture for User Location in Heterogeneous Mobile Networks
 An Architecture for User Location in Heterogeneous Mobile Networks Maarten Wegdam 1,2, Jeroen van Bemmel 1, Ko Lagerberg 1, Peter Leijdekkers 3 1 Lucent Technologies, Bell Labs Advanced Technologies EMEA
An Architecture for User Location in Heterogeneous Mobile Networks Maarten Wegdam 1,2, Jeroen van Bemmel 1, Ko Lagerberg 1, Peter Leijdekkers 3 1 Lucent Technologies, Bell Labs Advanced Technologies EMEA
Use of Mobile Agents for IPR Management and Negotiation
 Use of Mobile Agents for Management and Negotiation Isabel Gallego 1, 2, Jaime Delgado 1, Roberto García 1 1 Universitat Pompeu Fabra (UPF), Departament de Tecnologia, La Rambla 30-32, E-08002 Barcelona,
Use of Mobile Agents for Management and Negotiation Isabel Gallego 1, 2, Jaime Delgado 1, Roberto García 1 1 Universitat Pompeu Fabra (UPF), Departament de Tecnologia, La Rambla 30-32, E-08002 Barcelona,
MMS MM1 Stage. 3 Using OMA/WAP COPYRIGHT. 3GPP2 X.S Version 2.0 Version Date: June 2004
 3GPP2 X.S0016-310-0 Version 2.0 Version Date: June 2004 MMS MM1 Stage 3 Using OMA/WAP COPYRIGHT 3GPP2 and its Organizational Partners claim copyright in this document and individual Organizational Partners
3GPP2 X.S0016-310-0 Version 2.0 Version Date: June 2004 MMS MM1 Stage 3 Using OMA/WAP COPYRIGHT 3GPP2 and its Organizational Partners claim copyright in this document and individual Organizational Partners
VHO project Background Information
 VHO project Background Information Raimo Vuopionperä (ph.d.) Research Manager, NomadicLab (Ericsson Research Lab @ Finland), Ericsson Research, Corporate Unit Contents Multiple Access Why, What & Definitions
VHO project Background Information Raimo Vuopionperä (ph.d.) Research Manager, NomadicLab (Ericsson Research Lab @ Finland), Ericsson Research, Corporate Unit Contents Multiple Access Why, What & Definitions
INTERNAL ASSESSMENT TEST III Answer Schema
 INTERNAL ASSESSMENT TEST III Answer Schema Subject& Code: Object-Oriented Modeling and Design (15CS551) Sem: V ISE (A & B) Q. No. Questions Marks 1. a. Ans Explain the steps or iterations involved in object
INTERNAL ASSESSMENT TEST III Answer Schema Subject& Code: Object-Oriented Modeling and Design (15CS551) Sem: V ISE (A & B) Q. No. Questions Marks 1. a. Ans Explain the steps or iterations involved in object
FIPA Agent Management Support for Mobility Specification
 1 2 3 4 5 6 FOUNDATION FOR INTELLIGENT PHYSICAL AGENTS FIPA Management Support for Mobility Specification 7 8 Document title FIPA Management Support for Mobility Specification Document number PC000087B
1 2 3 4 5 6 FOUNDATION FOR INTELLIGENT PHYSICAL AGENTS FIPA Management Support for Mobility Specification 7 8 Document title FIPA Management Support for Mobility Specification Document number PC000087B
MDA and Integration of Legacy Systems: An Industrial Case Study
 MDA and Integration of Legacy Systems: An Industrial Case Study Parastoo Mohagheghi 1, Jan Pettersen Nytun 2, Selo 2, Warsun Najib 2 1 Ericson Norway-Grimstad, Postuttak, N-4898, Grimstad, Norway 1 Department
MDA and Integration of Legacy Systems: An Industrial Case Study Parastoo Mohagheghi 1, Jan Pettersen Nytun 2, Selo 2, Warsun Najib 2 1 Ericson Norway-Grimstad, Postuttak, N-4898, Grimstad, Norway 1 Department
Topic : Object Oriented Design Principles
 Topic : Object Oriented Design Principles Software Engineering Faculty of Computing Universiti Teknologi Malaysia Objectives Describe the differences between requirements activities and design activities
Topic : Object Oriented Design Principles Software Engineering Faculty of Computing Universiti Teknologi Malaysia Objectives Describe the differences between requirements activities and design activities
Example: Fibonacci Numbers
 Example: Fibonacci Numbers Write a program which determines F n, the (n + 1)-th Fibonacci number. The first 10 Fibonacci numbers are 0, 1, 1, 2, 3, 5, 8, 13, 21, and 34. The sequence of Fibonacci numbers
Example: Fibonacci Numbers Write a program which determines F n, the (n + 1)-th Fibonacci number. The first 10 Fibonacci numbers are 0, 1, 1, 2, 3, 5, 8, 13, 21, and 34. The sequence of Fibonacci numbers
Using Workflow-based Systems for e-services Provision
 29 Using Workflow-based Systems for e-services Provision Silvia Llorente and Jaime Delgado Distributed Multimedia Applications Group, Universitat Pompeu Fabra ( UPF) [silvia.llorente, jaime.delgadoj@tecn.upfes
29 Using Workflow-based Systems for e-services Provision Silvia Llorente and Jaime Delgado Distributed Multimedia Applications Group, Universitat Pompeu Fabra ( UPF) [silvia.llorente, jaime.delgadoj@tecn.upfes
3GPP TS V7.0.0 ( )
 TS 23.198 V7.0.0 (2006-06) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network and Terminals; Open Service Access (OSA); Stage 2 (Release 7) The present
TS 23.198 V7.0.0 (2006-06) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network and Terminals; Open Service Access (OSA); Stage 2 (Release 7) The present
3.Constructors and Destructors. Develop cpp program to implement constructor and destructor.
 3.Constructors and Destructors Develop cpp program to implement constructor and destructor. Constructors A constructor is a special member function whose task is to initialize the objects of its class.
3.Constructors and Destructors Develop cpp program to implement constructor and destructor. Constructors A constructor is a special member function whose task is to initialize the objects of its class.
ETSI TS V8.0.0 ( ) Technical Specification
 TS 123 611 V8.0.0 (2009-01) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; TISPAN; XML Document Management; Architecture
TS 123 611 V8.0.0 (2009-01) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; TISPAN; XML Document Management; Architecture
An Object-Dependent and Context Constraints-Aware Access Control Approach Based on RBAC
 An Object-Dependent and Context Constraints-Aware Access Control Approach Based on RBAC Xiaoli Ren, Lu Liu and Chenggong Lv School of Economics & Management, Beihang University, Beijing 100083, P.R. China
An Object-Dependent and Context Constraints-Aware Access Control Approach Based on RBAC Xiaoli Ren, Lu Liu and Chenggong Lv School of Economics & Management, Beihang University, Beijing 100083, P.R. China
The Specifications Exchange Service of an RM-ODP Framework
 The Specifications Exchange Service of an RM-ODP Framework X. Blanc (*+), M-P. Gervais(*), J. Le Delliou(+) (*)Laboratoire d'informatique de Paris 6-8 rue du Capitaine Scott F75015 PARIS (+)EDF Research
The Specifications Exchange Service of an RM-ODP Framework X. Blanc (*+), M-P. Gervais(*), J. Le Delliou(+) (*)Laboratoire d'informatique de Paris 6-8 rue du Capitaine Scott F75015 PARIS (+)EDF Research
Using XACML for access control in Social Networks
 Using XACML for access control in Social Networks Anna Carreras, Eva Rodríguez, Jaime Delgado Distributed Multimedia Applications Group (DMAG) Universitat Politècnica de Catalunya (UPC) Jordi Girona 1-3,
Using XACML for access control in Social Networks Anna Carreras, Eva Rodríguez, Jaime Delgado Distributed Multimedia Applications Group (DMAG) Universitat Politècnica de Catalunya (UPC) Jordi Girona 1-3,
Incorporating applications to a Service Oriented Architecture
 Proceedings of the 5th WSEAS Int. Conf. on System Science and Simulation in Engineering, Tenerife, Canary Islands, Spain, December 16-18, 2006 401 Incorporating applications to a Service Oriented Architecture
Proceedings of the 5th WSEAS Int. Conf. on System Science and Simulation in Engineering, Tenerife, Canary Islands, Spain, December 16-18, 2006 401 Incorporating applications to a Service Oriented Architecture
Access Control for Shared Resources
 Access Control for Shared Resources Erik Wilde and Nick Nabholz Computer Engineering and Networks Laboratory (TIK) Swiss Federal Institute of Technology (ETH Zürich) Abstract Access control for shared
Access Control for Shared Resources Erik Wilde and Nick Nabholz Computer Engineering and Networks Laboratory (TIK) Swiss Federal Institute of Technology (ETH Zürich) Abstract Access control for shared
A Java Execution Simulator
 A Java Execution Simulator Steven Robbins Department of Computer Science University of Texas at San Antonio srobbins@cs.utsa.edu ABSTRACT This paper describes JES, a Java Execution Simulator that allows
A Java Execution Simulator Steven Robbins Department of Computer Science University of Texas at San Antonio srobbins@cs.utsa.edu ABSTRACT This paper describes JES, a Java Execution Simulator that allows
Distributed Systems. Bina Ramamurthy. 6/13/2005 B.Ramamurthy 1
 Distributed Systems Bina Ramamurthy 6/13/2005 B.Ramamurthy 1 Introduction Distributed system is the one in which hardware and software components at networked computers communicate and coordinate their
Distributed Systems Bina Ramamurthy 6/13/2005 B.Ramamurthy 1 Introduction Distributed system is the one in which hardware and software components at networked computers communicate and coordinate their
3GPP TS V9.0.0 ( )
 Technical Specification 3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; Telecommunication management; Configuration Management (CM); Generic network resources
Technical Specification 3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; Telecommunication management; Configuration Management (CM); Generic network resources
ITU-T Q Signalling architecture and requirements for IP-based short message service over ITU-T defined NGN
 I n t e r n a t i o n a l T e l e c o m m u n i c a t i o n U n i o n ITU-T Q.3053 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (03/2017) SERIES Q: SWITCHING AND SIGNALLING, AND ASSOCIATED MEASUREMENTS
I n t e r n a t i o n a l T e l e c o m m u n i c a t i o n U n i o n ITU-T Q.3053 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (03/2017) SERIES Q: SWITCHING AND SIGNALLING, AND ASSOCIATED MEASUREMENTS
A Secure Next Generation Service Platform: Parlay
 A Secure Next Generation Service Platform: Parlay T-Systems, Gerald.Lorang@t-systems.com OMG DOCsec Workshop 2003.03.07 Seite 1 Overview of the Presentation Introduction Prerequisites PKI Architecture
A Secure Next Generation Service Platform: Parlay T-Systems, Gerald.Lorang@t-systems.com OMG DOCsec Workshop 2003.03.07 Seite 1 Overview of the Presentation Introduction Prerequisites PKI Architecture
DevOps for Software-Defined Telecom Infrastructures. draft-unify-nfvrg-devops-01
 DevOps for Software-Defined Telecom Infrastructures draft-unify-nfvrg-devops-01 C. Meirosu, A. Manzalini, J. Kim, R. Steinert, S. Sharma, G. Marchetto, I. Pappafili UNIFY is co-funded by the European Commission
DevOps for Software-Defined Telecom Infrastructures draft-unify-nfvrg-devops-01 C. Meirosu, A. Manzalini, J. Kim, R. Steinert, S. Sharma, G. Marchetto, I. Pappafili UNIFY is co-funded by the European Commission
XML Web Services Basics
 MSDN Home XML Web Services Basics Page Options Roger Wolter Microsoft Corporation December 2001 Summary: An overview of the value of XML Web services for developers, with introductions to SOAP, WSDL, and
MSDN Home XML Web Services Basics Page Options Roger Wolter Microsoft Corporation December 2001 Summary: An overview of the value of XML Web services for developers, with introductions to SOAP, WSDL, and
In this Lecture you will Learn: Design Patterns. Patterns vs. Frameworks. Patterns vs. Frameworks
 In this Lecture you will Learn: Design Patterns Chapter 15 What types of patterns have been identified in software development How to apply design patterns during software development The benefits and
In this Lecture you will Learn: Design Patterns Chapter 15 What types of patterns have been identified in software development How to apply design patterns during software development The benefits and
Model Driven Architecture and Rhapsody
 Model Driven Architecture and Rhapsody Dr. Bruce Powel Douglass Chief Evangelist Telelogic Model Driven Architecture and Rhapsody Abstract MDA, short for Model Driven Architecture, is a unification by
Model Driven Architecture and Rhapsody Dr. Bruce Powel Douglass Chief Evangelist Telelogic Model Driven Architecture and Rhapsody Abstract MDA, short for Model Driven Architecture, is a unification by
What is CORBA? CORBA (Common Object Request Broker Architecture) is a distributed object-oriented client/server platform.
 CORBA What is CORBA? CORBA (Common Object Request Broker Architecture) is a distributed object-oriented client/server platform. It includes: an object-oriented Remote Procedure Call (RPC) mechanism object
CORBA What is CORBA? CORBA (Common Object Request Broker Architecture) is a distributed object-oriented client/server platform. It includes: an object-oriented Remote Procedure Call (RPC) mechanism object
ETSI TS V ( ) Technical Specification
 TS 132 601 V10.0.0 (2011-04) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; Telecommunication management; Configuration
TS 132 601 V10.0.0 (2011-04) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; Telecommunication management; Configuration
PTT + IMS = PTM - Towards Community/Presence-based IMS Multimedia Services
 PTT + IMS = PTM - Towards Community/Presence-based IMS Multimedia Services Niklas Blum Fraunhofer Institute FOKUS Next Generation Network Integration Kaiserin-Augusta-Allee 31, 10589 Berlin, Germany niklas.blum@fokus.fraunhofer.de
PTT + IMS = PTM - Towards Community/Presence-based IMS Multimedia Services Niklas Blum Fraunhofer Institute FOKUS Next Generation Network Integration Kaiserin-Augusta-Allee 31, 10589 Berlin, Germany niklas.blum@fokus.fraunhofer.de
An Efficient DECT-Mobile IP Interworking for Mobile Computing
 An Efficient DECT-Mobile IP Interworking for Mobile Computing Anthony Lo *, Winston Seah * and Edwin Schreuder + * Centre for Wireless Communications 1, National University of Singapore, 20 Science Park
An Efficient DECT-Mobile IP Interworking for Mobile Computing Anthony Lo *, Winston Seah * and Edwin Schreuder + * Centre for Wireless Communications 1, National University of Singapore, 20 Science Park
Introduction to Object- Oriented Programming
 Introduction to Object- Oriented Programming Reusing this material This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike 4.0 International License. http://creativecommons.org/licenses/by-nc-sa/4.0/deed.en_us
Introduction to Object- Oriented Programming Reusing this material This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike 4.0 International License. http://creativecommons.org/licenses/by-nc-sa/4.0/deed.en_us
The EU OPEN meter project
 Open Public Extended Network ing 7 TH FRAMEWORK PROGRAMME The EU project ERGEG workshop on Smart Metering Authors: Date: Nicolas Arcauz 14th December 2009, Brussels ENERGY 2008.7.1.1 Official Journal of
Open Public Extended Network ing 7 TH FRAMEWORK PROGRAMME The EU project ERGEG workshop on Smart Metering Authors: Date: Nicolas Arcauz 14th December 2009, Brussels ENERGY 2008.7.1.1 Official Journal of
Object-Oriented Design Lecture 3 CSU 370 Fall 2007 (Pucella) Friday, Sep 14, 2007
 Object-Oriented Design Lecture 3 CSU 370 Fall 2007 (Pucella) Friday, Sep 14, 2007 Java We will be programming in Java in this course. Partly because it is a reasonable language, and partly because you
Object-Oriented Design Lecture 3 CSU 370 Fall 2007 (Pucella) Friday, Sep 14, 2007 Java We will be programming in Java in this course. Partly because it is a reasonable language, and partly because you
System types. Distributed systems
 System types 1 Personal systems that are designed to run on a personal computer or workstation Distributed systems where the system software runs on a loosely integrated group of cooperating processors
System types 1 Personal systems that are designed to run on a personal computer or workstation Distributed systems where the system software runs on a loosely integrated group of cooperating processors
03. DECORATOR PATTERN. Design Eye for the Inheritance Guy
 BIM492 DESIGN PATTERNS 03. DECORATOR PATTERN Design Eye for the Inheritance Guy Welcome to Starbuzz Coffee Starbuzz Coffee is the fastest growing coffee shop around --> if you see one, look across the
BIM492 DESIGN PATTERNS 03. DECORATOR PATTERN Design Eye for the Inheritance Guy Welcome to Starbuzz Coffee Starbuzz Coffee is the fastest growing coffee shop around --> if you see one, look across the
Oracle Tuxedo. CORBA Technical Articles 11g Release 1 ( ) March 2010
 Oracle Tuxedo CORBA Technical Articles 11g Release 1 (11.1.1.1.0) March 2010 Oracle Tuxedo CORBA Technical Articles, 11g Release 1 (11.1.1.1.0) Copyright 1996, 2010, Oracle and/or its affiliates. All rights
Oracle Tuxedo CORBA Technical Articles 11g Release 1 (11.1.1.1.0) March 2010 Oracle Tuxedo CORBA Technical Articles, 11g Release 1 (11.1.1.1.0) Copyright 1996, 2010, Oracle and/or its affiliates. All rights
Picolo: A Simple Python Framework for Introducing Component Principles
 Picolo: A Simple Python Framework for Introducing Component Principles Raphaël Marvie LIFL University of Lille 1 (France) raphael.marvie@lifl.fr Abstract Components have now become a cornerstone of software
Picolo: A Simple Python Framework for Introducing Component Principles Raphaël Marvie LIFL University of Lille 1 (France) raphael.marvie@lifl.fr Abstract Components have now become a cornerstone of software
Project #1 rev 2 Computer Science 2334 Fall 2013 This project is individual work. Each student must complete this assignment independently.
 Project #1 rev 2 Computer Science 2334 Fall 2013 This project is individual work. Each student must complete this assignment independently. User Request: Create a simple magazine data system. Milestones:
Project #1 rev 2 Computer Science 2334 Fall 2013 This project is individual work. Each student must complete this assignment independently. User Request: Create a simple magazine data system. Milestones:
Digital (Virtual) Identities in Daidalos and beyond. Amardeo Sarma NEC Laboratories Europe
 Digital (Virtual) Identities in Daidalos and beyond Amardeo Sarma NEC Laboratories Europe Who wants to pay for more Bandwidth? More Access Bandwidth? No one pays extra for volume or time plain usage is
Digital (Virtual) Identities in Daidalos and beyond Amardeo Sarma NEC Laboratories Europe Who wants to pay for more Bandwidth? More Access Bandwidth? No one pays extra for volume or time plain usage is
ETSI TR V1.1.1 ( )
 TR 102 314-3 V1.1.1 (2005-03) Technical Report Fixed network Multimedia Messaging Service (F-MMS); PSTN/ISDN; Part 3: Network architecture and interconnection 2 TR 102 314-3 V1.1.1 (2005-03) Reference
TR 102 314-3 V1.1.1 (2005-03) Technical Report Fixed network Multimedia Messaging Service (F-MMS); PSTN/ISDN; Part 3: Network architecture and interconnection 2 TR 102 314-3 V1.1.1 (2005-03) Reference
Federated Identity Management and Network Virtualization
 Federated Identity Management and Network Virtualization Yang Cui and Kostas Pentikousis 3rd ETSI Future Networks Workshop 10 April 2013 Sophia Antipolis, France The opinions expressed in this presentation
Federated Identity Management and Network Virtualization Yang Cui and Kostas Pentikousis 3rd ETSI Future Networks Workshop 10 April 2013 Sophia Antipolis, France The opinions expressed in this presentation
ETSI TR V1.1.1 ( )
 TR 101 303 V1.1.1 (2001-06) Technical Report Telecommunications and Internet Protocol Harmonization Over Networks (TIPHON); Service and Network Management Framework; Overview and Introduction 2 TR 101
TR 101 303 V1.1.1 (2001-06) Technical Report Telecommunications and Internet Protocol Harmonization Over Networks (TIPHON); Service and Network Management Framework; Overview and Introduction 2 TR 101
ETSI TS V6.0.0 ( )
 TS 129 199-7 V6.0.0 (2004-09) Technical Specification Universal Mobile Telecommunications System (UMTS); Open Service Access (OSA); Parlay X web services; Part 7: Account management (3GPP TS 29.199-07
TS 129 199-7 V6.0.0 (2004-09) Technical Specification Universal Mobile Telecommunications System (UMTS); Open Service Access (OSA); Parlay X web services; Part 7: Account management (3GPP TS 29.199-07
Distributed systems. Distributed Systems Architectures. System types. Objectives. Distributed system characteristics.
 Distributed systems Distributed Systems Architectures Virtually all large computer-based systems are now distributed systems. Information processing is distributed over several computers rather than confined
Distributed systems Distributed Systems Architectures Virtually all large computer-based systems are now distributed systems. Information processing is distributed over several computers rather than confined
A Report on RMI and RPC Submitted by Sudharshan Reddy B
 A Report on RMI and RPC Submitted by Sudharshan Reddy B Abstract: This report mainly explains the RMI and RPC technologies. In the first part of the paper the RMI technology is briefly explained and in
A Report on RMI and RPC Submitted by Sudharshan Reddy B Abstract: This report mainly explains the RMI and RPC technologies. In the first part of the paper the RMI technology is briefly explained and in
Standardization Trends of the Next Generation Network in ETSI TISPAN
 Standardization Trends of the Next Generation Network in ETSI TISPAN Akira Kurokawa and Isao Higashi Abstract International standardization of the Next Generation Network is being actively discussed in
Standardization Trends of the Next Generation Network in ETSI TISPAN Akira Kurokawa and Isao Higashi Abstract International standardization of the Next Generation Network is being actively discussed in
Modular Design of Call Control Layer in Telephony Software
 8 Modular Design of Call Control Layer in Telephony Software Ilija Basicevic University of Novi Sad, Faculty of Technical Sciences Novi Sad, 21000, Serbia Abstract An important property of a telephony
8 Modular Design of Call Control Layer in Telephony Software Ilija Basicevic University of Novi Sad, Faculty of Technical Sciences Novi Sad, 21000, Serbia Abstract An important property of a telephony
CORBA Object Transaction Service
 CORBA Object Transaction Service Telcordia Contact: Paolo Missier paolo@research.telcordia.com +1 (973) 829 4644 March 29th, 1999 An SAIC Company Telcordia Technologies Proprietary Internal Use Only This
CORBA Object Transaction Service Telcordia Contact: Paolo Missier paolo@research.telcordia.com +1 (973) 829 4644 March 29th, 1999 An SAIC Company Telcordia Technologies Proprietary Internal Use Only This
PRINCIPLES OF SOFTWARE BIM209DESIGN AND DEVELOPMENT 00. WELCOME TO OBJECTVILLE. Speaking the Language of OO
 PRINCIPLES OF SOFTWARE BIM209DESIGN AND DEVELOPMENT 00. WELCOME TO OBJECTVILLE Speaking the Language of OO COURSE INFO Instructor : Alper Bilge TA : Gökhan Çıplak-Ahmet Alkılınç Time : Tuesdays 2-5pm Location
PRINCIPLES OF SOFTWARE BIM209DESIGN AND DEVELOPMENT 00. WELCOME TO OBJECTVILLE Speaking the Language of OO COURSE INFO Instructor : Alper Bilge TA : Gökhan Çıplak-Ahmet Alkılınç Time : Tuesdays 2-5pm Location
Object-Oriented Software Engineering Practical Software Development using UML and Java
 Object-Oriented Software Engineering Practical Software Development using UML and Java Chapter 5: Modelling with Classes Lecture 5 5.1 What is UML? The Unified Modelling Language is a standard graphical
Object-Oriented Software Engineering Practical Software Development using UML and Java Chapter 5: Modelling with Classes Lecture 5 5.1 What is UML? The Unified Modelling Language is a standard graphical
Formalising the NGN Application Layer
 Formalising the NGN Application Layer Doron Horwitz and Prof. Hu Hanrahan Centre for Telecommunications Access and Services * School of Electrical and Information Engineering University of The Witwatersrand,
Formalising the NGN Application Layer Doron Horwitz and Prof. Hu Hanrahan Centre for Telecommunications Access and Services * School of Electrical and Information Engineering University of The Witwatersrand,
Towards Generating Domain-Specific Model Editors with Complex Editing Commands
 Towards Generating Domain-Specific Model Editors with Complex Editing Commands Gabriele Taentzer Technical University of Berlin Germany gabi@cs.tu-berlin.de May 10, 2006 Abstract Domain specific modeling
Towards Generating Domain-Specific Model Editors with Complex Editing Commands Gabriele Taentzer Technical University of Berlin Germany gabi@cs.tu-berlin.de May 10, 2006 Abstract Domain specific modeling
Capturing and Formalizing SAF Availability Management Framework Configuration Requirements
 Capturing and Formalizing SAF Availability Management Framework Configuration Requirements A. Gherbi, P. Salehi, F. Khendek and A. Hamou-Lhadj Electrical and Computer Engineering, Concordia University,
Capturing and Formalizing SAF Availability Management Framework Configuration Requirements A. Gherbi, P. Salehi, F. Khendek and A. Hamou-Lhadj Electrical and Computer Engineering, Concordia University,
ETSI TS V ( )
 TS 32 4 V5.0.0 (208-07) TECHNICAL SPECIFICATION Digital cellular telecommunications system (Phase 2+) (GSM); Universal Mobile Telecommunications System (UMTS); LTE; Telecommunication management; Subscription
TS 32 4 V5.0.0 (208-07) TECHNICAL SPECIFICATION Digital cellular telecommunications system (Phase 2+) (GSM); Universal Mobile Telecommunications System (UMTS); LTE; Telecommunication management; Subscription
Using the TASKING Software Platform for AURIX
 Using the TASKING Software Platform for AURIX MA160-869 (v1.0) November 13, 2017 Copyright 2017 TASKING BV. All rights reserved. You are permitted to print this document provided that (1) the use of such
Using the TASKING Software Platform for AURIX MA160-869 (v1.0) November 13, 2017 Copyright 2017 TASKING BV. All rights reserved. You are permitted to print this document provided that (1) the use of such
Develop Unified SNMP, XML, CLI, and Web-based Management for Embedded Real-Time Systems with MIBGuide
 1 Overview Develop Unified SNMP, XML, CLI, and Web-based Management for Embedded Real-Time Systems with MIBGuide SNMP Research International, Inc. Knoxville, Tennessee 1 Overview Support for remote management
1 Overview Develop Unified SNMP, XML, CLI, and Web-based Management for Embedded Real-Time Systems with MIBGuide SNMP Research International, Inc. Knoxville, Tennessee 1 Overview Support for remote management
ETSI TS V9.0.0 ( ) Technical Specification
 TS 123 198 V9.0.0 (2010-01) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; Open Service Access (OSA); Stage 2 (3GPP
TS 123 198 V9.0.0 (2010-01) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; Open Service Access (OSA); Stage 2 (3GPP
Concepts of Programming Languages
 Concepts of Programming Languages Lecture 10 - Object-Oriented Programming Patrick Donnelly Montana State University Spring 2014 Patrick Donnelly (Montana State University) Concepts of Programming Languages
Concepts of Programming Languages Lecture 10 - Object-Oriented Programming Patrick Donnelly Montana State University Spring 2014 Patrick Donnelly (Montana State University) Concepts of Programming Languages
New Value Chain through Service Platform
 New Value Chain through Service Platform Oct. 24 th 2008 Ryozo Ito Senior Executive Consultant Hewlett-Packard Japan Technology for better business outcomes 2008 Hewlett-Packard Development Company, L.P.
New Value Chain through Service Platform Oct. 24 th 2008 Ryozo Ito Senior Executive Consultant Hewlett-Packard Japan Technology for better business outcomes 2008 Hewlett-Packard Development Company, L.P.
Performance Evaluation of Java And C++ Distributed Applications In A CORBA Environment
 Performance Evaluation of Java And C++ Distributed Applications In A CORBA Environment Sanjay P. Ahuja Roger Eggen Cheryl Daucher Department of Computer and Information Sciences University of North Florida
Performance Evaluation of Java And C++ Distributed Applications In A CORBA Environment Sanjay P. Ahuja Roger Eggen Cheryl Daucher Department of Computer and Information Sciences University of North Florida
Requirements and capabilities for. NGN services Marco Carugi Nortel Networks March 2005 Jeju Island, South Korea
 Requirements and capabilities for Phone: +33-1-6955-7027 Email: marco.carugi@nortel.com NGN services Marco Carugi Nortel Networks 14-15 March 2005 Jeju Island, South Korea Outline NGN Services Service
Requirements and capabilities for Phone: +33-1-6955-7027 Email: marco.carugi@nortel.com NGN services Marco Carugi Nortel Networks 14-15 March 2005 Jeju Island, South Korea Outline NGN Services Service
IST 1 st Call project eperspace Towards the era of personal services at home and everywhere
 IST 1 st Call project eperspace Towards the era of personal services at home and everywhere Adam Kapovits Eurescom, Germany eperspace objectives 4 main focus areas/goals: 1. The Home Platform providing
IST 1 st Call project eperspace Towards the era of personal services at home and everywhere Adam Kapovits Eurescom, Germany eperspace objectives 4 main focus areas/goals: 1. The Home Platform providing
Authentication with OAuth 2.0
 Authentication with OAuth 2.0 The OAuth 2.0 specification defines a delegation protocol that is useful for conveying authorization decisions across a network of web-enabled applications and APIs. OAuth
Authentication with OAuth 2.0 The OAuth 2.0 specification defines a delegation protocol that is useful for conveying authorization decisions across a network of web-enabled applications and APIs. OAuth
COLDIC, a Lexicographic Platform for LMF Compliant Lexica
 COLDIC, a Lexicographic Platform for LMF Compliant Lexica Núria Bel, Sergio Espeja, Montserrat Marimon, Marta Villegas Institut Universitari de Lingüística Aplicada Universitat Pompeu Fabra Pl. de la Mercè,
COLDIC, a Lexicographic Platform for LMF Compliant Lexica Núria Bel, Sergio Espeja, Montserrat Marimon, Marta Villegas Institut Universitari de Lingüística Aplicada Universitat Pompeu Fabra Pl. de la Mercè,
Data Structures and Algorithms Design Goals Implementation Goals Design Principles Design Techniques. Version 03.s 2-1
 Design Principles Data Structures and Algorithms Design Goals Implementation Goals Design Principles Design Techniques 2-1 Data Structures Data Structure - A systematic way of organizing and accessing
Design Principles Data Structures and Algorithms Design Goals Implementation Goals Design Principles Design Techniques 2-1 Data Structures Data Structure - A systematic way of organizing and accessing
DISCRETE COMPUTER SIMULATION WITH JAVA
 DISCRETE COMPUTER SIMULATION WITH JAVA Ricardo Augusto Cassel Department of Management Science - The Management School - Lancaster University Lancaster, LA1 4YX, United Kingdom Michael Pidd Department
DISCRETE COMPUTER SIMULATION WITH JAVA Ricardo Augusto Cassel Department of Management Science - The Management School - Lancaster University Lancaster, LA1 4YX, United Kingdom Michael Pidd Department
Chapter 15: Object Oriented Programming
 Chapter 15: Object Oriented Programming Think Java: How to Think Like a Computer Scientist 5.1.2 by Allen B. Downey How do Software Developers use OOP? Defining classes to create objects UML diagrams to
Chapter 15: Object Oriented Programming Think Java: How to Think Like a Computer Scientist 5.1.2 by Allen B. Downey How do Software Developers use OOP? Defining classes to create objects UML diagrams to
Object Fundamentals. Kenneth M. Anderson University of Colorado, Boulder CSCI 4448/6448 Lecture 2 08/30/2007
 Object Fundamentals Kenneth M. Anderson University of Colorado, Boulder CSCI 4448/6448 Lecture 2 08/30/2007 1 Lecture Goals Introduce basic concepts, terminology, and notations for object-oriented analysis,
Object Fundamentals Kenneth M. Anderson University of Colorado, Boulder CSCI 4448/6448 Lecture 2 08/30/2007 1 Lecture Goals Introduce basic concepts, terminology, and notations for object-oriented analysis,
ENABLING DISTRIBUTED QOS MANAGEMENT UTILIZING ACTIVE NETWORK TECHNOLOGY An algorithm for QoS provisioning using active networks
 ENABLING DISTRIBUTED QOS MANAGEMENT UTILIZING ACTIVE NETWORK TECHNOLOGY An algorithm for QoS provisioning using active networks Stavros Vrontis, Irene Sygkouna, Maria Chantzara and Eystathios Sykas National
ENABLING DISTRIBUTED QOS MANAGEMENT UTILIZING ACTIVE NETWORK TECHNOLOGY An algorithm for QoS provisioning using active networks Stavros Vrontis, Irene Sygkouna, Maria Chantzara and Eystathios Sykas National
Design and Implementation of a Service Discovery Architecture in Pervasive Systems
 Design and Implementation of a Service Discovery Architecture in Pervasive Systems Vincenzo Suraci 1, Tiziano Inzerilli 2, Silvano Mignanti 3, University of Rome La Sapienza, D.I.S. 1 vincenzo.suraci@dis.uniroma1.it
Design and Implementation of a Service Discovery Architecture in Pervasive Systems Vincenzo Suraci 1, Tiziano Inzerilli 2, Silvano Mignanti 3, University of Rome La Sapienza, D.I.S. 1 vincenzo.suraci@dis.uniroma1.it
CORBA and COM TIP. Two practical techniques for object composition. X LIU, School of Computing, Napier University
 CORBA and COM TIP Two practical techniques for object composition X LIU, School of Computing, Napier University CORBA Introduction Common Object Request Broker Architecture (CORBA) is an industry-standard
CORBA and COM TIP Two practical techniques for object composition X LIU, School of Computing, Napier University CORBA Introduction Common Object Request Broker Architecture (CORBA) is an industry-standard
