Developers Integration Lab (DIL) Certificate Installation Instructions. Version 1.6
|
|
|
- Mabel Richardson
- 5 years ago
- Views:
Transcription
1 Developers Integration Lab (DIL) Certificate Installation Instructions Version 1.6 May 28, 2014
2 REVISION HISTORY REVISION DATE DESCRIPTION September 2011 First Draft Release DIL Certificate Installation Instructions September 2011 Updated certificate download link examples November 2012 First Publication Release DIL Certificate Installation Instructions January 2013 Addition of section describing how to import alternate certificates for use with other environments January 2013 Added general grammatical changes May 2013 Included additional steps for Certificate Set Up July 2013 Added section March 2014 Updated to accommodate new Cert Download Password field in Participant table May 2014 Updated with the instructions to download certificates with user provided passwords i
3 TABLE OF CONTENTS 1. INTRODUCTION PURPOSE SCOPE DOCUMENT DESCRIPTION REFERENCED DOCUMENTS PROBLEM DESCRIPTION & GOALS INSTRUCTIONS REQUIRED INFORMATION DOWNLOAD YOUR CERTIFICATE DOWNLOAD THE CA CERTIFICATES NON-FIPS INSTALLATION (WINDOWS / GLASSFISH) SETUP YOUR WORK FOLDER KEYSTORE AND TRUSTSTORE INSTALL THE CERTIFICATES (GLASSFISH) UPDATE GLASSFISH DOMAIN CONFIGURATION VERIFY GLASSFISH DOMAIN CONFIGURATION USE OF ALTERNATIVE CERTIFICATES CERTIFICATE REVOCATION LIST (CRL) CHECKING FIPS INSTALLATION (RED HAT LINUX / JBOSS) SETUP YOUR WORK FOLDER NSS DATASTORE UPDATE JBOSS SERVER CONFIGURATION VERIFY JBOSS SERVER CONFIGURATION ii
4 1. INTRODUCTION 1.1 PURPOSE This document provides the required steps to download, install, and configure a DIL Certificate. 1.2 SCOPE The instructions in this document are applicable to all participants, both internal and external, in the DIL environment. 2. DOCUMENT DESCRIPTION This document includes the following sections: Section 1.0 Introduction Section 2.0 Document Description Section 3.0 Referenced Documents Section 4.0 Problem Description & Goals Section 5.0 Instructions 3. REFERENCED DOCUMENTS N/A 4. PROBLEM DESCRIPTION & GOALS Communication between gateways requires a secured transport mechanism. This is accomplished by SSL certificates issued to each gateway server AEGIS.net is a Certificate Authority with the ability to issue SSL certificates using the following hierarchy: AEGISROOTCA AEGISDILCA [Issued Server Certificate] The hierarchy mentioned above is the three-level certificate architecture used within the DIL. All SSL certificates are of the type PKS-12, however you can add your own private certificate under the trust chain as well. If you are planning on using the Private Cert provided by the DIL, please skip over section
5 If you change your machine name at any time, you will need to generate a new certificate. This can be done by notifying the development team at DIL_Support@aegis.net. 5. INSTRUCTIONS These instructions are intended for use by a participant within the DIL environment. The participant must first complete the self-registration of their DIL account. 5.1 REQUIRED INFORMATION 1. The participant must provide the full machine name of the gateway server as part of their Gateway Profile. a. Example of machine name machine.domain.com 2. The participant s CA account information is then defined as: a. Your account name will be your machine name; e.g. machine.domain.com. 5.2 DOWNLOAD YOUR CERTIFICATE 1. Upon registering a Test System and the associated host/machine name(s) with DIL, you can download a certificate for each registered host/machine name. To do so, click on the Download Certificates button located at the bottom of the Test system page. 2. Download Certificate page will be displayed with the list of registered host/machine names and a provision to enter password for each certificate. Enter a password for each certificate and click on Save Password button at the top right corner of the page. Note: The length of the password should be min of 6 characters. 3. Once the submitted password information is saved, please download your machine s private certificate by clicking on the machine name You will now be prompted with a browser dialog to either open or save. Note that if your browser is configured to save by default, you may not see this window. Save your certificate file to your local machine. a. Your certificate file name will be your gateway machine name with a.p12 extension; e.g. machine.domain.com.p12 2
6 b. If the install fails, please contact DIL Help Desk Support. 5.3 DOWNLOAD THE CA CERTIFICATES Your certificate is the end of a three-part chain. You need to download the other two certificate parts: AEGISROOTCA and AEGISDILCA. 1. Select the following link on the Download Certificate page to download the AEGISROOTCA: Please download the DIL Root certificate here AEGISROOTCA.pem 2. Select the following link on the Download Certificate page to download the AEGISDILCA: Please download the DIL Cross certificate here AEGISDILCA.pem 5.4 NON-FIPS INSTALLATION (Windows / Glassfish) SETUP YOUR WORK FOLDER Windows XP/2003 Server 64 bit is the operating system and Glassfish is the target application server for these instructions. 1. Create a work folder; e.g. C:\Sun\AppServer\certificaterequest 2. Copy all certificates generated and downloaded from the AEGIS.net CA site to your work folder. 3. Copy the cacerts.jks truststore from the Glassfish domain config folder: C:\Sun\AppServer\domains\domain1\config\cacerts.jks 4. Open a command prompt window and change directory to your work folder KEYSTORE AND TRUSTSTORE Execute the following commands to generate your keystore and install the certificates to your keystore and truststore. Replace the text <pkcs12_file> with the name of the downloaded machine keystore file including the file extension. IMPORT PKCS12 KEYSTORE TO JAVA KEYSTORE keytool -importkeystore -srckeystore <pkcs12_file> -srcstoretype PKCS12 - deststoretype JKS -destkeystore gateway.jks 3
7 * You will be prompted to enter your password three (3) times. After correctly entering your password you should have an output similar to this: Enter destination keystore password: Re-enter new password: Enter source keystore password: Entry for alias <machine_cert> successfully imported. Import command completed: 1 entries successfully imported, 0 entries failed or cancelled NOTE: The source keystore password above is the password that you provided for your machine certificate in the DIL application. Use the same password for the destination keystore password for easy remembrance. VERIFY JAVA KEYSTORE keytool -list -v -keystore gateway.jks > gatewaylist * You will be prompted to enter your password. This will list the private key details. Examine the output to insure there are no errors. IMPORT CHAIN OF TRUST CERTIFICATES TO THE TRUSTSTORE keytool -import -v -trustcacerts -alias AEGISROOTCA -file AEGISROOTCA.pem -keystore cacerts.jks -keypass changeit -storepass changeit * Enter yes or y to the prompt. You should see the following output: Trust this certificate? [no]: yes Certificate was added to keystore NOTE: The keypass value is the literal value changeit. The storepass value is the password specific to the machine or IP address registered with the DIL. keytool -import -v -trustcacerts -alias AEGISDILCA -file AEGISDILCA.pem - keystore cacerts.jks -keypass changeit -storepass changeit * No input is required. You should see the following output: Certificate was added to keystore NOTE: The keypass value is the literal value changeit. The storepass value is the password specific to the machine or IP address registered with the DIL. keytool -importkeystore -srckeystore <pkcs12_file> -srcstoretype PKCS12 - deststoretype JKS -destkeystore cacerts.jks 4
8 * You will be prompted to enter the truststore password followed by your password. You should see the following output: Enter destination keystore password: Enter source keystore password: Entry for alias <machine_cert> successfully imported. Import command completed: 1 entries successfully imported, 0 entries failed or cancelled VERIFY THE TRUSTSTORE CONTENTS keytool -list -keystore cacerts.jks > cacertslist * You will be prompted to enter the truststore password. This will list all of the trusted certificates. Examine the output to insure the imported certificates are present aegisrootca, aegisdilca andmachine cert. IMPORT ALL CERTIFICATES TO YOUR KEYSTORE keytool -import -v -trustcacerts -alias AEGISROOTCA -file AEGISROOTCA.pem -keystore gateway.jks -keypass <JKS_Keystore_password> -storepass < JKS_Keystore_password> * Enter yes or y to the prompt. You should see the following output: Trust this certificate? [no]: yes Certificate was added to keystore keytool -import -v -trustcacerts -alias AEGISDILCA -file AEGISDILCA.pem - keystore gateway.jks -keypass < JKS_Keystore_password> -storepass < JKS_Keystore_password> * No input is required. You should see the following output: Certificate was added to keystore VERIFY KEYSTORE CONTENTS keytool -list -keystore gateway.jks > gatewaylist2 * You will be prompted to enter your password. This will list all of the trusted certificates. Examine the output to insure the imported certificates are present aegisrootca, aegisdilca and the machine cert INSTALL THE CERTIFICATES (GLASSFISH) 1. Copy the keystore and truststore files from your work folder to the Glassfish domain config folder: C:\Sun\AppServer\domains\domain1\config\gateway.jks C:\Sun\AppServer\domains\domain1\config\cacerts.jks 5
9 5.4.4 UPDATE GLASSFISH DOMAIN CONFIGURATION Modify the domain.xml Glassfish configuration file to now use your new keystore. 1. Locate and update all key.alias values to your certificate alias; i.e. <machine>.domain.com. 2. Update the following <jvm-options> settings related to your keystore: -Djavax.net.ssl.keyStore=${com.sun.aas.instanceRoot}/config/gateway.jks -Djavax.net.ssl.keyStorePassword=<machine> -DSERVER_KEY_ALIAS=<machine>.domain.com -DCLIENT_KEY_ALIAS=<machine>.domain.com - Dcom.sun.enterprise.security.httpsOutboundKeyAlias=<machine>.domain.com NOTE: <machine>.domain.com is an example alias name. The actual alias name for your certificate is your registered machine name by default. You can verify this using the keytool command keytool list keystore gateway.jks storepass <key_store_password> VERIFY GLASSFISH DOMAIN CONFIGURATION 1. Start your Glassfish server. 2. Examine the server logs after the application server start up is complete and verify that there are no errors USE OF ALTERNATIVE CERTIFICATES You may store and use additional, alternate certificates in your keystore and truststore files if your test system has the need to communicate with other testing environments. An example of this would be if your test system will also be used for onboard testing with the ehealth Exchange (formerly the NwHIN). The DIL Certificate Architecture mirrors that of the ehealth Exchange in that it relies on 3 levels, the Root Certificate, Cross Certificate, and finally the Private certificate. This Chain of Trust, i.e. the Root and Cross certificates validates and trusts the private certificate. You must first successfully obtain the required ehealth Exchange Root Certificate, Cross Certificate, and their Private certificate. Please refer to the 6
10 CONNECT Open Source Wiki page, Certificate Setup, for specific instructions. This page is found at: The following steps are those that are needed to add these certificates to your existing keystore and truststore files: C:\Sun\AppServer\domains\domain1\config\gateway.jks C:\Sun\AppServer\domains\domain1\config\cacerts.jks IMPORT THE WEB SERVICE [PRIVATE] CERTIFICATE: keytool -import -v -trustcacerts -alias gateway -file servercert.bin -keystore gateway.jks -keypass changeit -storepass changeit * The -keypass and storepass passwords need to match those of the servercert.bin and gateway.jks respectively. IMPORT CHAIN OF TRUST CERTIFICATES TO THE TRUSTSTORE keytool -import -v -trustcacerts -alias entrust -file cacert.crt -keystore cacerts.jks - keypass changeit -storepass changeit * The -keypass and storepass passwords need to match those of the cacert.crt and cacerts.jks respectively. * Enter yes or y to the prompt. You should see the following output: Trust this certificate? [no]: yes Certificate was added to keystore [Storing cacerts.jks] keytool -import -v -trustcacerts -alias entrust-cross -file cross.crt -keystore cacerts.jks -keypass changeit -storepass changeit * The -keypass and storepass passwords need to match those of the cross.crt and cacerts.jks respectively. * No input is required. You should see the following output: Certificate was added to keystore [Storing cacerts.jks] 7
11 5.4.7 Certificate Revocation List (CRL) Checking Certificate Revocation Lists (CRLs) are lists of certificates that are no longer valid or that have been revoked by a Certification Authority (CA). Each gateway must implement either Online Certificate Status Protocol (OCSP) based certificate revocation checking or use CRLs against an NHIN-governed CA to determine the revocation status of each certificate. To enable the CRL checking in glassfish application server, add the following two JVM options in the domain.xml file as the two properties would remain false by default. You will need JDK 6 update 18 or later versions for supporting CRL checking. <jvm-options>-dcom.sun.net.ssl.checkrevocation=true</jvm-options> <jvm-options>-dcom.sun.security.enablecrldp=true</jvm-options> For debugging certification issues, add the following jvm option in domain.xml <jvm-options>-djava.security.debug=certpath</jvm-options> For other application servers, please check your server documentation regarding enabling CRL checking. FOR CRL checking, you need to open port 9345 at firewall so that you can have access to CRL list at SDILCA,O=AEGISnetInc,C=US. 5.5 FIPS INSTALLATION (Red Hat Linux / JBoss) The following set of instructions is intended for users utilizing FIPS mode enabled on the participant machine SETUP YOUR WORK FOLDER Red Hat Enterprise Linux is the operating system and Glassfish or JBoss are the target application servers for these instructions. The Mozilla NSS datastore database is installed in the directory /opt/fipsdb for these instructions. 1. Create a work folder; e.g. /opt/fipsdb/cert 2. Copy all certificates generated and downloaded from the AEGIS CA site to your work folder. 3. Open a command prompt window and change directory to your work folder. 8
12 5.5.2 NSS DATASTORE Execute the following commands to import your server certificate and the AEGIS DIL and ROOT CA certificates to your NSS datastore. Replace the text <machine> with the value of your machine name. DISABLE FIPS MODE modutil -fips false -dbdir /opt/fipsdb * FIPS Mode must be disabled before making any modifications to prevent corruption of the NSS datastore. You will be prompted to continue. Simply press the Enter key again. You should see the following output: WARNING: Performing this operation while the browser is running could cause corruption of your security databases. If the browser is currently running, you should exit browser before continuing this operation. Type 'q <enter>' to abort, or <enter> to continue: FIPS mode disabled. IMPORT PKCS12 SERVER CERTIFICATE TO THE NSS DATASTORE pk12util -i <machine>.domain.com.p12 -n <machine>.domain.com -d /opt/fipsdb * You will be prompted to enter the NSS password. After correctly entering that password, you will be prompted to enter the password for your server certificate. After correctly entering that password you should have an output similar to this: Enter Password or Pin for "NSS Certificate DB": Enter password for PKCS12 file: pk12util: PKCS12 IMPORT SUCCESSFUL IMPORT THE AEGIS ROOT AND DIL CA CERTIFICATES certutil -A -n "AEGISROOTCA" -t "TC,," -i AEGISROOTCA.pem -d /opt/fipsdb certutil -A -n "AEGISDILCA" -t "TC,," -i AEGISDILCA.pem -d /opt/fipsdb * No input is required. CONFIRM THE CONTENTS OF YOUR NSS DATABASE certutil -L -d /opt/fipsdb * No input is required. This will list all of the certificates. Examine the output to insure the imported certificates are present aegisrootca, aegisdilca and <machine>.domain.com. You should see the following output: 9
13 Certificate Nickname <machine>.domain.com AEGISDILCA AEGISROOTCA Trust Attributes SSL,S/MIME,JAR/XPI u,u,u TC,, TC,, VERIFY THE CERTIFICATE CHAIN IS CORRECT vfychain -d /opt/fipsdb <machine>.domain.com * No input is required. This will verify that the certificate chain has been correctly established. You should see the following output: Chain is good! ENABLE FIPS MODE modutil -fips true -dbdir /opt/fipsdb * FIPS Mode must be enabled before (re)starting the application server. You should see the following output: WARNING: Performing this operation while the browser is running could cause corruption of your security databases. If the browser is currently running, you should exit browser before continuing this operation. Type 'q <enter>' to abort, or <enter> to continue: FIPS mode enabled UPDATE JBOSS SERVER CONFIGURATION Follow the FIPS Red Hat Linux / JBoss configuration instructions for CONNECT 3.2: VERIFY JBOSS SERVER CONFIGURATION 1. Start your JBoss server. 2. Examine the server logs after the application server start up is complete and verify that there are no certificate errors. 10
SSL/TLS Certificate Generation
 SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 16/02/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 16/02/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
OIOIDWS Integration testing
 1 of 6 07-09-2010 16:39 OIOIDWS Integration testing This document describes how to install and configure the OIOIDWS components and run a few manual tests based on them. The test setup consists of the
1 of 6 07-09-2010 16:39 OIOIDWS Integration testing This document describes how to install and configure the OIOIDWS components and run a few manual tests based on them. The test setup consists of the
SSL/TLS Certificate Generation
 SSL/TLS Certificate Generation Last updated: 11/01/2016 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion of an Existing Certificate Chain Available
SSL/TLS Certificate Generation Last updated: 11/01/2016 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion of an Existing Certificate Chain Available
SSL/TLS Certificate Generation
 SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 08/03/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 08/03/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
Public Key Enabling Oracle Weblogic Server
 DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
SAML with ADFS Setup Guide
 SAML with ADFS Setup Guide Version 1.0 Corresponding Software Version: 4.2 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval of the Celonis
SAML with ADFS Setup Guide Version 1.0 Corresponding Software Version: 4.2 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval of the Celonis
Wildcard Certificates
 Wildcard Certificates Importing PKCS#12 and.pfx files Important: GoPrint requires the certificate chain password to be trustno1 When importing certificates into the Java Keystore generated on another certificate
Wildcard Certificates Importing PKCS#12 and.pfx files Important: GoPrint requires the certificate chain password to be trustno1 When importing certificates into the Java Keystore generated on another certificate
Provisioning Certificates
 CHAPTER 8 The Secure Socket Layer (SSL) protocol secures the network communication and allows data to be encrypted before transmission and provides security. Many application servers and web servers support
CHAPTER 8 The Secure Socket Layer (SSL) protocol secures the network communication and allows data to be encrypted before transmission and provides security. Many application servers and web servers support
Configuring the RTP Server
 Configuring the RTP Server To configure the RTP Server you can click on the little cog in the lower right hand corner of the banner area at the top of the window (If the RTP Server is running you will
Configuring the RTP Server To configure the RTP Server you can click on the little cog in the lower right hand corner of the banner area at the top of the window (If the RTP Server is running you will
Configure DNA Center Assurance for Cisco ISE Integration
 Configure DNA Center Assurance for Cisco ISE Integration If your network uses Cisco ISE for user authentication, you can configure DNA Center Assurance for Cisco ISE integration. This will allow you to
Configure DNA Center Assurance for Cisco ISE Integration If your network uses Cisco ISE for user authentication, you can configure DNA Center Assurance for Cisco ISE integration. This will allow you to
Configure Cisco DNA Assurance
 Basic Workflow for Configuring Cisco DNA Assurance, on page 1 Assurance and Cisco ISE Integration, on page 2 Assurance Application, on page 6 Basic Workflow for Configuring Cisco DNA Assurance Before you
Basic Workflow for Configuring Cisco DNA Assurance, on page 1 Assurance and Cisco ISE Integration, on page 2 Assurance Application, on page 6 Basic Workflow for Configuring Cisco DNA Assurance Before you
Managing Administrative Security
 5 CHAPTER 5 Managing Administrative Security This chapter describes how to manage administrative security by using the secure administration feature. This chapter assumes that you are familiar with security
5 CHAPTER 5 Managing Administrative Security This chapter describes how to manage administrative security by using the secure administration feature. This chapter assumes that you are familiar with security
Configuring NiFi Authentication and Proxying with Apache Knox
 3 Configuring NiFi Authentication and Proxying with Apache Knox Date of Publish: 2018-08-13 http://docs.hortonworks.com Contents...3 Configuring NiFi for Knox Authentication... 3 Configuring Knox for NiFi...
3 Configuring NiFi Authentication and Proxying with Apache Knox Date of Publish: 2018-08-13 http://docs.hortonworks.com Contents...3 Configuring NiFi for Knox Authentication... 3 Configuring Knox for NiFi...
How to use an EPR certificate with the MESH client
 Document filename: How to use an EPR certificate with the MESH client Directorate / Programme Operations and Assurance Services Project Spine Services/ MESH Document Reference Project Manager
Document filename: How to use an EPR certificate with the MESH client Directorate / Programme Operations and Assurance Services Project Spine Services/ MESH Document Reference Project Manager
SAML 2.0 SSO. Set up SAML 2.0 SSO. SAML 2.0 Terminology. Prerequisites
 SAML 2.0 SSO Agiloft integrates with a variety of SAML authentication providers, or Identity Providers (IdPs). SAML-based SSO is a leading method for providing federated access to multiple applications
SAML 2.0 SSO Agiloft integrates with a variety of SAML authentication providers, or Identity Providers (IdPs). SAML-based SSO is a leading method for providing federated access to multiple applications
Configuring SSL for EPM /4 Products (Cont )
 Configuring SSL for EPM 11.1.2.3/4 Products (Cont ) Configure IIS for SSL If you have a server certificate with its private key skip creating the Certificate Request and continue with Complete Certificate
Configuring SSL for EPM 11.1.2.3/4 Products (Cont ) Configure IIS for SSL If you have a server certificate with its private key skip creating the Certificate Request and continue with Complete Certificate
Configuring CA WA Agent for Application Services to Work with IBM WebSphere Application Server 8.x
 Configuring CA WA Agent for Application Services to Work with IBM WebSphere Application Server 8.x Kiran Chinthala Jan 02 2015 Table of Contents Scope... 3 Why is this configuration necessary?... 3 1.
Configuring CA WA Agent for Application Services to Work with IBM WebSphere Application Server 8.x Kiran Chinthala Jan 02 2015 Table of Contents Scope... 3 Why is this configuration necessary?... 3 1.
eroaming platform Secure Connection Guide
 eroaming platform Secure Connection Guide Contents 1. Revisions overview... 3 2. Abbrevations... 4 3. Preconditions... 5 3.1. OpenSSL... 5 3.2. Requirements for your PKCS10 CSR... 5 3.3. Java Keytool...
eroaming platform Secure Connection Guide Contents 1. Revisions overview... 3 2. Abbrevations... 4 3. Preconditions... 5 3.1. OpenSSL... 5 3.2. Requirements for your PKCS10 CSR... 5 3.3. Java Keytool...
ADFS Setup (SAML Authentication)
 ADFS Setup (SAML Authentication) Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval
ADFS Setup (SAML Authentication) Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval
SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release [December] [2016]
![SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release [December] [2016] SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release [December] [2016]](/thumbs/74/70834213.jpg) SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release 12.3.0.0.0 [December] [2016] Table of Contents 1. SSL OR TLS CONFIGURATION... 1-1 1.1 INTRODUCTION... 1-1 1.2 REFERENCE SITES...
SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release 12.3.0.0.0 [December] [2016] Table of Contents 1. SSL OR TLS CONFIGURATION... 1-1 1.1 INTRODUCTION... 1-1 1.2 REFERENCE SITES...
SSO Authentication with ADFS SAML 2.0. Ephesoft Transact Documentation
 SSO Authentication with ADFS SAML 2.0 Ephesoft Transact Documentation 2017 Table of Contents Prerequisites... 1 Tools Used... 1 Setup... 1 Generating Server Certificates to Set Up SSL/TLS... 1 Creating
SSO Authentication with ADFS SAML 2.0 Ephesoft Transact Documentation 2017 Table of Contents Prerequisites... 1 Tools Used... 1 Setup... 1 Generating Server Certificates to Set Up SSL/TLS... 1 Creating
Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface
 Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface Release 7.1 Revised: March 5, 2013 1:53 pm This document describes the
Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface Release 7.1 Revised: March 5, 2013 1:53 pm This document describes the
Enabling Secure Sockets Layer for a Microsoft SQL Server JDBC Connection
 Enabling Secure Sockets Layer for a Microsoft SQL Server JDBC Connection Secure Sockets Layer (SSL) is the standard security technology for establishing an encrypted link between a web server and a browser.
Enabling Secure Sockets Layer for a Microsoft SQL Server JDBC Connection Secure Sockets Layer (SSL) is the standard security technology for establishing an encrypted link between a web server and a browser.
CA Spectrum. Common Access Card Authentication Solution Guide. Release 9.4
 CA Spectrum Common Access Card Authentication Solution Guide Release 9.4 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the
CA Spectrum Common Access Card Authentication Solution Guide Release 9.4 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the
Application notes for supporting third-party certificate in Avaya Aura System Manager 6.3.x and 7.0.x. Issue 1.3. November 2017
 Application notes for supporting third-party certificate in Avaya Aura System Manager 6.3.x and 7.0.x Issue 1.3 November 2017 THE INFORMATION PROVIDED IN HEREIN IS PROVIDED AS IS WITHOUT ANY EXPRESS OR
Application notes for supporting third-party certificate in Avaya Aura System Manager 6.3.x and 7.0.x Issue 1.3 November 2017 THE INFORMATION PROVIDED IN HEREIN IS PROVIDED AS IS WITHOUT ANY EXPRESS OR
SSL Configuration: an example. July 2016
 SSL Configuration: an example July 2016 This document details a walkthrough example of SSL configuration in an EM managed mongodb environment. SSL certificates are used to enforce certificate based security
SSL Configuration: an example July 2016 This document details a walkthrough example of SSL configuration in an EM managed mongodb environment. SSL certificates are used to enforce certificate based security
FileAudit Plus. Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in FileAudit Plus
 Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in : Step
Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in : Step
MSE System and Appliance Hardening Guidelines
 MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
Oracle iplanet Web Server Integration Guide
 Oracle iplanet Web Server Integration Guide Document Information Document Part Number 007-012078-001 (Rev C) Release Date November 2015 Trademarks All intellectual property is protected by copyright. All
Oracle iplanet Web Server Integration Guide Document Information Document Part Number 007-012078-001 (Rev C) Release Date November 2015 Trademarks All intellectual property is protected by copyright. All
How to convert.crt SSL Certificate to.pfx format (with openssl Linux command) and Import newly generated.pfx to Windows IIS Webserver
 How to convert.crt SSL Certificate to.pfx format (with openssl Linux command) and Import newly generated.pfx to Windows IIS Webserver Author : admin 1. Converting to.crt to.pfx file format with OpenSSL
How to convert.crt SSL Certificate to.pfx format (with openssl Linux command) and Import newly generated.pfx to Windows IIS Webserver Author : admin 1. Converting to.crt to.pfx file format with OpenSSL
Oracle Insurance Policy Administration Configuration of SAML 1.1 Between OIPA and OIDC
 Oracle Insurance Policy Administration Configuration of SAML 1.1 Between OIPA and OIDC Version 10.1.0.0 Documentation Part Number: E55027-01 June, 2014 Copyright 2009, 2014, Oracle and/or its affiliates.
Oracle Insurance Policy Administration Configuration of SAML 1.1 Between OIPA and OIDC Version 10.1.0.0 Documentation Part Number: E55027-01 June, 2014 Copyright 2009, 2014, Oracle and/or its affiliates.
HP Operations Orchestration
 HP Operations Orchestration Software Version: 10.20 Windows and Linux Operating Systems Hardening Guide Document Release Date: November 2014 Software Release Date: November 2014 Legal Notices Warranty
HP Operations Orchestration Software Version: 10.20 Windows and Linux Operating Systems Hardening Guide Document Release Date: November 2014 Software Release Date: November 2014 Legal Notices Warranty
AUTHORIZED DOCUMENTATION. Installation Guide. Novell Cloud Manager 1.1. December 8,
 AUTHORIZED DOCUMENTATION Installation Guide Novell Cloud Manager 1.1 December 8, 2010 www.novell.com Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use
AUTHORIZED DOCUMENTATION Installation Guide Novell Cloud Manager 1.1 December 8, 2010 www.novell.com Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use
Securing U2 Soap Server
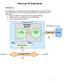 Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Web Service Integration
 SOAP Service, page 1 Rest Service, page 2 SOAP Service Web Services Element Web services are a common way for any kind of application to communicate with externally hosted servers to retrieve information
SOAP Service, page 1 Rest Service, page 2 SOAP Service Web Services Element Web services are a common way for any kind of application to communicate with externally hosted servers to retrieve information
StreamServe Persuasion SP4 StreamStudio
 StreamServe Persuasion SP4 StreamStudio Administrator s guide Rev A StreamServe Persuasion SP4 StreamStudio Administrator s guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent
StreamServe Persuasion SP4 StreamStudio Administrator s guide Rev A StreamServe Persuasion SP4 StreamStudio Administrator s guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent
SAML-Based SSO Configuration
 Prerequisites, page 1 SAML SSO Configuration Workflow, page 5 Reconfigure OpenAM SSO to SAML SSO After an Upgrade, page 9 Prerequisites NTP Setup In SAML SSO, Network Time Protocol (NTP) enables clock
Prerequisites, page 1 SAML SSO Configuration Workflow, page 5 Reconfigure OpenAM SSO to SAML SSO After an Upgrade, page 9 Prerequisites NTP Setup In SAML SSO, Network Time Protocol (NTP) enables clock
VSP16. Venafi Security Professional 16 Course 04 April 2016
 VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
S/MIME on Good for Enterprise MS Online Certificate Status Protocol. Installation and Configuration Notes. Updated: November 10, 2011
 S/MIME on Good for Enterprise MS Online Certificate Status Protocol Installation and Configuration Notes Updated: November 10, 2011 Installing the Online Responder service... 1 Preparing the environment...
S/MIME on Good for Enterprise MS Online Certificate Status Protocol Installation and Configuration Notes Updated: November 10, 2011 Installing the Online Responder service... 1 Preparing the environment...
BusinessObjects Enterprise XI Release 1 and Release 2
 BusinessObjects Enterprise XI Release 1 and Release 2 Overview Contents This document provides information and instructions for setting up Lightweight Directory Access Protocol (LDAP) authentication in
BusinessObjects Enterprise XI Release 1 and Release 2 Overview Contents This document provides information and instructions for setting up Lightweight Directory Access Protocol (LDAP) authentication in
Using Certificates with HP Network Automation
 Using Certificates with HP Network Automation HP Network Automation / October 2010 This document provides an overview of how certificates are used within HP Network Automation (NA), including information
Using Certificates with HP Network Automation HP Network Automation / October 2010 This document provides an overview of how certificates are used within HP Network Automation (NA), including information
How to Configure SSL Interception in the Firewall
 Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted traffic to allow Application Control features (such as the Virus Scanner, ATD, URL Filter, Safe Search,
Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted traffic to allow Application Control features (such as the Virus Scanner, ATD, URL Filter, Safe Search,
FortiNAC. Analytics SSL Certificates. Version: 5.x Date: 8/28/2018. Rev: D
 FortiNAC Analytics SSL Certificates Version: 5.x Date: 8/28/2018 Rev: D 1 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET KNOWLEDGE BASE http://kb.fortinet.com
FortiNAC Analytics SSL Certificates Version: 5.x Date: 8/28/2018 Rev: D 1 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET KNOWLEDGE BASE http://kb.fortinet.com
Configuring Oracle Java CAPS for SSL Support
 Configuring Oracle Java CAPS for SSL Support Part No: 821 2544 March 2011 Copyright 2008, 2011, Oracle and/or its affiliates. All rights reserved. License Restrictions Warranty/Consequential Damages Disclaimer
Configuring Oracle Java CAPS for SSL Support Part No: 821 2544 March 2011 Copyright 2008, 2011, Oracle and/or its affiliates. All rights reserved. License Restrictions Warranty/Consequential Damages Disclaimer
Veritas Access Software-Defined Storage (SDS) Management Platform Solutions Guide
 Veritas Access Software-Defined Storage (SDS) Management Platform Solutions Guide Linux 7.4 Veritas Access Software-Defined Storage (SDS) Management Platform Solutions Guide Last updated: 2018-07-24 Document
Veritas Access Software-Defined Storage (SDS) Management Platform Solutions Guide Linux 7.4 Veritas Access Software-Defined Storage (SDS) Management Platform Solutions Guide Last updated: 2018-07-24 Document
X-road MISP2 installation and configuration guide. Version 1.20
 X-road MISP2 installation and configuration guide Version 1.20 Contents 1. Introduction... 3 2. Environment requirements... 3 3.MISP2 Installation... 3 3.1. Java... 3 3.2. PostgreSQL... 3 3.3. Apache Tomcat
X-road MISP2 installation and configuration guide Version 1.20 Contents 1. Introduction... 3 2. Environment requirements... 3 3.MISP2 Installation... 3 3.1. Java... 3 3.2. PostgreSQL... 3 3.3. Apache Tomcat
McAfee Cloud Identity Manager Installation Guide For McAfee Cloud Identity Manager v3.1 August 2012
 McAfee Cloud Identity Manager Installation Guide For McAfee Cloud Identity Manager v3.1 August 2012 Order Number: 326712-005US COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARK
McAfee Cloud Identity Manager Installation Guide For McAfee Cloud Identity Manager v3.1 August 2012 Order Number: 326712-005US COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARK
Keytool and Certificate Management
 Keytool and Certificate Management A guide to utilizing keytool to assist with Certificates for emedny SOAP 2/16/2013 TABLE OF CONTENTS TABLE OF CONTENTS 1 Introduction... 3 2 Creating a Certificate Signing
Keytool and Certificate Management A guide to utilizing keytool to assist with Certificates for emedny SOAP 2/16/2013 TABLE OF CONTENTS TABLE OF CONTENTS 1 Introduction... 3 2 Creating a Certificate Signing
Prepaid Online Vending System. XMLVend 2.1 Test Suite Setup Instructions
 Prepaid Online Vending System XMLVend 2.1 Test Suite Setup Instructions Contents SOFTWARE REQUIRED... 5 SETUP JAVA JDK... 5 TOMCAT SETUP FOR XML... 6 INTERCEPTOR... 8 SETTING UP SSL... 9 SETTING UP THE
Prepaid Online Vending System XMLVend 2.1 Test Suite Setup Instructions Contents SOFTWARE REQUIRED... 5 SETUP JAVA JDK... 5 TOMCAT SETUP FOR XML... 6 INTERCEPTOR... 8 SETTING UP SSL... 9 SETTING UP THE
HPE Enterprise Integration Module for SAP Solution Manager 7.1
 HPE Enterprise Integration Module for SAP Solution Manager 7.1 Software Version: 12.55 User Guide Document Release Date: August 2017 Software Release Date: August 2017 HPE Enterprise Integration Module
HPE Enterprise Integration Module for SAP Solution Manager 7.1 Software Version: 12.55 User Guide Document Release Date: August 2017 Software Release Date: August 2017 HPE Enterprise Integration Module
OCSP Client Tool V2.2 User Guide
 Ascertia Limited 40 Occam Road Surrey Research Park Guildford Surrey GU2 7YG Tel: +44 1483 685500 Fax: +44 1483 573704 www.ascertia.com OCSP Client Tool V2.2 User Guide Document Version: 2.2.0.2 Document
Ascertia Limited 40 Occam Road Surrey Research Park Guildford Surrey GU2 7YG Tel: +44 1483 685500 Fax: +44 1483 573704 www.ascertia.com OCSP Client Tool V2.2 User Guide Document Version: 2.2.0.2 Document
Security configuration of the mail server IBM
 Security configuration of the mail server IBM ii Security configuration of the mail server Contents Security configuration of the mail server 1 Configuration of the SSL client to trust the SMTP server
Security configuration of the mail server IBM ii Security configuration of the mail server Contents Security configuration of the mail server 1 Configuration of the SSL client to trust the SMTP server
How to Configure Mutual Authentication using X.509 Certificate in SMP SAP Mobile Platform (3.X)
 How to Configure Mutual Authentication using X.509 Certificate in SMP SAP Mobile Platform (3.X) Author: Ali Chalhoub Global Support Architect Engineer Date: July 2, 2015 Document History: Document Version
How to Configure Mutual Authentication using X.509 Certificate in SMP SAP Mobile Platform (3.X) Author: Ali Chalhoub Global Support Architect Engineer Date: July 2, 2015 Document History: Document Version
SSL/TLS Certificate Check
 Administration Guide Supplemental SSL/TLS Certificate Check for BEMS and Blackberry Work Product Version: 2.5 Updated: 23-Jan-17 2017 BlackBerry Limited. Trademarks, including but not limited to BLACKBERRY,
Administration Guide Supplemental SSL/TLS Certificate Check for BEMS and Blackberry Work Product Version: 2.5 Updated: 23-Jan-17 2017 BlackBerry Limited. Trademarks, including but not limited to BLACKBERRY,
Advanced Integration TLS Certificate on the NotifySCM Server
 Advanced Integration TLS Certificate on the NotifySCM Server TABLE OF CONTENTS 1 Enable a TLS Connection Between NotifySCM and a Reverse Proxy... 3 1.1 Generate a self-signed certificate... 3 1.2 Install
Advanced Integration TLS Certificate on the NotifySCM Server TABLE OF CONTENTS 1 Enable a TLS Connection Between NotifySCM and a Reverse Proxy... 3 1.1 Generate a self-signed certificate... 3 1.2 Install
Using ISE 2.2 Internal Certificate Authority (CA) to Deploy Certificates to Cisco Platform Exchange Grid (pxgrid) Clients
 Using ISE 2.2 Internal Certificate Authority (CA) to Deploy Certificates to Cisco Platform Exchange Grid (pxgrid) Clients Author: John Eppich Table of Contents About this Document... 4 Using ISE 2.2 Internal
Using ISE 2.2 Internal Certificate Authority (CA) to Deploy Certificates to Cisco Platform Exchange Grid (pxgrid) Clients Author: John Eppich Table of Contents About this Document... 4 Using ISE 2.2 Internal
IBM Workplace TM Collaboration Services
 IBM Workplace TM Collaboration Services Version 2.5 Mobile Client Guide G210-1962-00 Terms of Use Disclaimer THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS PROVIDED FOR INFORMATIONAL PURPOSES ONLY.
IBM Workplace TM Collaboration Services Version 2.5 Mobile Client Guide G210-1962-00 Terms of Use Disclaimer THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS PROVIDED FOR INFORMATIONAL PURPOSES ONLY.
IBM Presentations: Implementing SSL Security in WebSphere Partner Gateway
 IBM Software Group IBM Presentations: Implementing SSL Security in WebSphere Partner Gateway Presenter: Max Terpolilli WPG L2 Support WebSphere Support Technical Exchange Agenda IBM Software Group Digital
IBM Software Group IBM Presentations: Implementing SSL Security in WebSphere Partner Gateway Presenter: Max Terpolilli WPG L2 Support WebSphere Support Technical Exchange Agenda IBM Software Group Digital
Participant User Guide, Version 2.6
 Developers Integration Lab (DIL) Participant User Guide, Version 2.6 3/17/2013 REVISION HISTORY Author Date Description of Change 0.1 Laura Edens Mario Hyland 9/19/2011 Initial Release 1.0 Michael Brown
Developers Integration Lab (DIL) Participant User Guide, Version 2.6 3/17/2013 REVISION HISTORY Author Date Description of Change 0.1 Laura Edens Mario Hyland 9/19/2011 Initial Release 1.0 Michael Brown
Venafi Server Agent Agent Overview
 Venafi Server Agent Agent Overview Venafi Server Agent Agent Intro Agent Architecture Agent Grouping Agent Prerequisites Agent Registration Process What is Venafi Agent? The Venafi Agent is a client/server
Venafi Server Agent Agent Overview Venafi Server Agent Agent Intro Agent Architecture Agent Grouping Agent Prerequisites Agent Registration Process What is Venafi Agent? The Venafi Agent is a client/server
DataFlux Secure 2.5. Administrator s Guide. Second Edition. SAS Documentation
 DataFlux Secure 2.5 Administrator s Guide Second Edition SAS Documentation This page is intentionally blank DataFlux Secure 2.5 Administrator s Guide Second Edition Applies to: DataFlux Authentication
DataFlux Secure 2.5 Administrator s Guide Second Edition SAS Documentation This page is intentionally blank DataFlux Secure 2.5 Administrator s Guide Second Edition Applies to: DataFlux Authentication
Please select your version
 Installation Guide Please select your version Installation Instructions for Tomcat using PKCS#7 format Installation Instructions for Tomcat using X.509 format Installation Instructions for Tomcat using
Installation Guide Please select your version Installation Instructions for Tomcat using PKCS#7 format Installation Instructions for Tomcat using X.509 format Installation Instructions for Tomcat using
Configuring Ambari Authentication with LDAP/AD
 3 Configuring Ambari Authentication with LDAP/AD Date of Publish: 2018-07-15 http://docs.hortonworks.com Contents Configuring Ambari Authentication for LDAP/AD... 3 Configuring Ambari to authenticate external
3 Configuring Ambari Authentication with LDAP/AD Date of Publish: 2018-07-15 http://docs.hortonworks.com Contents Configuring Ambari Authentication for LDAP/AD... 3 Configuring Ambari to authenticate external
Bugzilla ID: Bugzilla Summary:
 Bugzilla ID: Bugzilla Summary: CAs wishing to have their certificates included in Mozilla products must 1) Comply with the requirements of the Mozilla CA certificate policy (http://www.mozilla.org/projects/security/certs/policy/)
Bugzilla ID: Bugzilla Summary: CAs wishing to have their certificates included in Mozilla products must 1) Comply with the requirements of the Mozilla CA certificate policy (http://www.mozilla.org/projects/security/certs/policy/)
HP Enterprise Integration Module for SAP Solution Manager
 HP Enterprise Integration Module for SAP Solution Manager Software Version: 12.01 User Guide Document Release Date: March 2015 Software Release Date: March 2015 Legal Notices Warranty The only warranties
HP Enterprise Integration Module for SAP Solution Manager Software Version: 12.01 User Guide Document Release Date: March 2015 Software Release Date: March 2015 Legal Notices Warranty The only warranties
User guide NotifySCM Installer
 User guide NotifySCM Installer TABLE OF CONTENTS 1 Overview... 3 2 Office 365 Users synchronization... 3 3 Installation... 5 4 Starting the server... 17 2 P a g e 1 OVERVIEW This user guide provides instruction
User guide NotifySCM Installer TABLE OF CONTENTS 1 Overview... 3 2 Office 365 Users synchronization... 3 3 Installation... 5 4 Starting the server... 17 2 P a g e 1 OVERVIEW This user guide provides instruction
Creating an authorized SSL certificate
 Creating an authorized SSL certificate for MeetingSphere Meeting Center Server MeetingSphere Meeting Center Server requires an authorized SSL certificate by which its Meeting center is identified, and
Creating an authorized SSL certificate for MeetingSphere Meeting Center Server MeetingSphere Meeting Center Server requires an authorized SSL certificate by which its Meeting center is identified, and
Configuring Ambari Authentication with LDAP/AD
 3 Date of Publish: 2018-07-15 http://docs.hortonworks.com Contents Configuring Ambari Authentication for LDAP/AD... 3 Configuring Ambari to authenticate external users... 3 Preparing for LDAPS integration...
3 Date of Publish: 2018-07-15 http://docs.hortonworks.com Contents Configuring Ambari Authentication for LDAP/AD... 3 Configuring Ambari to authenticate external users... 3 Preparing for LDAPS integration...
This PDF Document was generated for free by the Aloaha PDF Suite If you want to learn how to make your own PDF Documents visit:
 INSTALLING AND CONFIGURING A WINDOWS SERVER 2003 ENTERPRISE CERTIFICATION AUTHORITY Certification Authorities can issue certificates to users and computers for a variety of purposes. In the context of
INSTALLING AND CONFIGURING A WINDOWS SERVER 2003 ENTERPRISE CERTIFICATION AUTHORITY Certification Authorities can issue certificates to users and computers for a variety of purposes. In the context of
6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename
 6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename Certificate formats (DER, PEM, PKCS #12) 6.2 Certificate Authorities
6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename Certificate formats (DER, PEM, PKCS #12) 6.2 Certificate Authorities
ENTRUST CONNECTOR Installation and Configuration Guide Version April 21, 2017
 ENTRUST CONNECTOR Installation and Configuration Guide Version 0.5.1 April 21, 2017 2017 CygnaCom Solutions, Inc. All rights reserved. Contents What is Entrust Connector... 4 Installation... 5 Prerequisites...
ENTRUST CONNECTOR Installation and Configuration Guide Version 0.5.1 April 21, 2017 2017 CygnaCom Solutions, Inc. All rights reserved. Contents What is Entrust Connector... 4 Installation... 5 Prerequisites...
Configuring IBM WebSphere Application Server 7 for Secure Sockets Layer and Client-Certificate Authentication on SAS 9.3 Enterprise BI Server Web
 Configuring IBM WebSphere Application Server 7 for Secure Sockets Layer and Client-Certificate Authentication on SAS 9.3 Enterprise BI Server Web Applications Configuring IBM WebSphere 7 for SSL and Client-Certificate
Configuring IBM WebSphere Application Server 7 for Secure Sockets Layer and Client-Certificate Authentication on SAS 9.3 Enterprise BI Server Web Applications Configuring IBM WebSphere 7 for SSL and Client-Certificate
Symantec PKI Enterprise Gateway Deployment Guide. v8.15
 Symantec PKI Enterprise Gateway Deployment Guide v8.15 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo and are trademarks or registered
Symantec PKI Enterprise Gateway Deployment Guide v8.15 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo and are trademarks or registered
IBM Security Identity Governance and Intelligence. SDI-based IBM Security Privileged Identity Manager adapter Installation and Configuration Guide IBM
 IBM Security Identity Governance and Intelligence SDI-based IBM Security Privileged Identity Manager adapter Installation and Configuration Guide IBM IBM Security Identity Governance and Intelligence
IBM Security Identity Governance and Intelligence SDI-based IBM Security Privileged Identity Manager adapter Installation and Configuration Guide IBM IBM Security Identity Governance and Intelligence
JAVA - DRI Connection Test Manual
 JAVA - DRI Connection Test Manual This is a step by step guide on how to access the DRI Web service with native Java. 1. Install the NetBeans IDE Since the DRI Web service is developed in.net WCF, interoperability
JAVA - DRI Connection Test Manual This is a step by step guide on how to access the DRI Web service with native Java. 1. Install the NetBeans IDE Since the DRI Web service is developed in.net WCF, interoperability
Hitachi ID Systems Inc Identity Manager 8.2.6
 Systems Inc RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 5, 2014 Product Information Partner Name Hitachi ID Systems Inc Web Site www.hitachi-id.com Product Name Identity
Systems Inc RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 5, 2014 Product Information Partner Name Hitachi ID Systems Inc Web Site www.hitachi-id.com Product Name Identity
How to use the MESH Certificate Enrolment Tool
 Document filename: How to use the MESH Certificate Enrolment Tool Directorate / Programme Operations and Project Assurance Services Spine Services/ MESH Document Reference Project Manager Andrew
Document filename: How to use the MESH Certificate Enrolment Tool Directorate / Programme Operations and Project Assurance Services Spine Services/ MESH Document Reference Project Manager Andrew
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
Configuring Java CAPS for SSL Support
 Configuring Java CAPS for SSL Support Part No: 820 3503 11 June 2010 Copyright 2008, 2010, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under
Configuring Java CAPS for SSL Support Part No: 820 3503 11 June 2010 Copyright 2008, 2010, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
Installation 1. DLM Installation. Date of Publish:
 1 DLM Installation Date of Publish: 2018-05-18 http://docs.hortonworks.com Contents Installation overview...3 Setting Up the Local Repository for Your DLM Installation... 3 Set up a local repository for
1 DLM Installation Date of Publish: 2018-05-18 http://docs.hortonworks.com Contents Installation overview...3 Setting Up the Local Repository for Your DLM Installation... 3 Set up a local repository for
Entrust Connector (econnector) Venafi Trust Protection Platform
 Entrust Connector (econnector) For Venafi Trust Protection Platform Installation and Configuration Guide Version 1.0.5 DATE: 17 November 2017 VERSION: 1.0.5 Copyright 2017. All rights reserved Table of
Entrust Connector (econnector) For Venafi Trust Protection Platform Installation and Configuration Guide Version 1.0.5 DATE: 17 November 2017 VERSION: 1.0.5 Copyright 2017. All rights reserved Table of
DIL 3.0 Release Notes
 Developers Integration Lab (DIL) September 19, 2014 REVISION HISTORY Date Description of Change 1.0 9/18/2014 Initial publication 1 TABLE OF CONTENTS 1.0 INTRODUCTION... 3 Document Purpose... 3 System
Developers Integration Lab (DIL) September 19, 2014 REVISION HISTORY Date Description of Change 1.0 9/18/2014 Initial publication 1 TABLE OF CONTENTS 1.0 INTRODUCTION... 3 Document Purpose... 3 System
GlobalForms SSL Installation Tech Brief
 127 Church Street, New Haven, CT 06510 O: (203) 789-0889 E: sales@square-9.com www.square-9.com GlobalForms SSL Installation Guide The following guide will give an overview of how to generate and install
127 Church Street, New Haven, CT 06510 O: (203) 789-0889 E: sales@square-9.com www.square-9.com GlobalForms SSL Installation Guide The following guide will give an overview of how to generate and install
Obtaining a Google Maps API Key. v1.0. By GoNorthWest. 15 December 2011
 Obtaining a Google Maps API Key v1.0 By GoNorthWest 15 December 2011 If you are creating an Android application that uses maps in it (which is a very cool feature to have!), you re going to need a Google
Obtaining a Google Maps API Key v1.0 By GoNorthWest 15 December 2011 If you are creating an Android application that uses maps in it (which is a very cool feature to have!), you re going to need a Google
Upgrading Big Data Management to Version Update 2 for Cloudera CDH
 Upgrading Big Data Management to Version 10.1.1 Update 2 for Cloudera CDH Copyright Informatica LLC 2017. Informatica, the Informatica logo, and Informatica Cloud are trademarks or registered trademarks
Upgrading Big Data Management to Version 10.1.1 Update 2 for Cloudera CDH Copyright Informatica LLC 2017. Informatica, the Informatica logo, and Informatica Cloud are trademarks or registered trademarks
SAP Edge Services, cloud edition Streaming Service - Configuration Guide Version 1803
 SAP Edge Services, cloud edition Streaming Service - Configuration Guide Version 1803 Public TABLE OF CONTENTS 1 INTRODUCTION... 3 2 PREREQUISITES... 3 2.1 JAVA_HOME... 3 2.2 Python (version 2.7.x 64-bit)...
SAP Edge Services, cloud edition Streaming Service - Configuration Guide Version 1803 Public TABLE OF CONTENTS 1 INTRODUCTION... 3 2 PREREQUISITES... 3 2.1 JAVA_HOME... 3 2.2 Python (version 2.7.x 64-bit)...
SECARDEO. certbox. Help-Manual. Secardeo GmbH Release:
 certbox Help-Manual Secardeo GmbH Release: 02.12.2014 certbox Help Manual 02.12.2014 Table of Contents 1 Search and retrieve Public Key Certificates... 1 1.1 Search by an e-mail address... 1 1.2 Download
certbox Help-Manual Secardeo GmbH Release: 02.12.2014 certbox Help Manual 02.12.2014 Table of Contents 1 Search and retrieve Public Key Certificates... 1 1.1 Search by an e-mail address... 1 1.2 Download
SSH Communications Tectia SSH
 Secured by RSA Implementation Guide for 3rd Party PKI Applications Last Modified: December 8, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product
Secured by RSA Implementation Guide for 3rd Party PKI Applications Last Modified: December 8, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product
Integration Guide. SafeNet Authentication Client. Using SAC CBA for VMware Horizon 6 Client
 SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
Upgrading Big Data Management to Version Update 2 for Hortonworks HDP
 Upgrading Big Data Management to Version 10.1.1 Update 2 for Hortonworks HDP Copyright Informatica LLC 2017. Informatica, the Informatica logo, and Informatica Big Data Management are trademarks or registered
Upgrading Big Data Management to Version 10.1.1 Update 2 for Hortonworks HDP Copyright Informatica LLC 2017. Informatica, the Informatica logo, and Informatica Big Data Management are trademarks or registered
Managing AON Security
 CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
Genesys Security Deployment Guide. What You Need
 Genesys Security Deployment Guide What You Need 12/27/2017 Contents 1 What You Need 1.1 TLS Certificates 1.2 Generating Certificates using OpenSSL and Genesys Security Pack 1.3 Generating Certificates
Genesys Security Deployment Guide What You Need 12/27/2017 Contents 1 What You Need 1.1 TLS Certificates 1.2 Generating Certificates using OpenSSL and Genesys Security Pack 1.3 Generating Certificates
On-demand target, up and running
 On-demand target, up and running ii On-demand target, up and running Contents Chapter 1. Assumptions........ 1 Chapter 2. Overview......... 3 Chapter 3. Component purpose.... 5 Chapter 5. Starting a session
On-demand target, up and running ii On-demand target, up and running Contents Chapter 1. Assumptions........ 1 Chapter 2. Overview......... 3 Chapter 3. Component purpose.... 5 Chapter 5. Starting a session
How to Set Up External CA VPN Certificates
 To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
Oracle Oracle Identity Manager 11g
 RSA SecurID Ready Implementation Guide Partner Information Last Modified: August 24, 2014 Product Information Partner Name Web Site Product Name Version & Platform Product Description Oracle www.oracle.com
RSA SecurID Ready Implementation Guide Partner Information Last Modified: August 24, 2014 Product Information Partner Name Web Site Product Name Version & Platform Product Description Oracle www.oracle.com
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
Skywire LTE CAT1 AWS IoT with TLS User Manual
 Skywire LTE CAT1 AWS IoT with TLS User Manual NimbeLink Corp Updated: January 2017 PN 30168 rev 6 NimbeLink Corp. 2017. All rights reserved. 1 Table of Contents Table of Contents 2 Introduction 3 Overview
Skywire LTE CAT1 AWS IoT with TLS User Manual NimbeLink Corp Updated: January 2017 PN 30168 rev 6 NimbeLink Corp. 2017. All rights reserved. 1 Table of Contents Table of Contents 2 Introduction 3 Overview
PKI Cert Creation via Good Control: Reference Implementation
 PKI Cert Creation via Good Control: Reference Implementation Legal Notice Copyright 2016 BlackBerry Limited. All rights reserved. All use is subject to license terms posted at http://us.blackberry.com/legal/legal.html.
PKI Cert Creation via Good Control: Reference Implementation Legal Notice Copyright 2016 BlackBerry Limited. All rights reserved. All use is subject to license terms posted at http://us.blackberry.com/legal/legal.html.
Configuring SAML-based Single Sign-on for Informatica Web Applications
 Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
