Erays: Reverse Engineering Ethereum s Opaque Smart Contracts
|
|
|
- Robert Bates
- 5 years ago
- Views:
Transcription
1 Erays: Reverse Engineering Ethereum s Opaque Smart Contracts Yi Zhou, Deepak Kumar, Surya Bakshi, Joshua Mason, Andrew Miller, Michael Bailey University of Illinois Urbana-Champaign 1
2 Introduction: Ethereum 2
3 Introduction: Ethereum Smart Contracts Computer programs on the blockchain Written in high level language (Solidity) Executed in the Ethereum Virtual Machine (EVM) 3
4 Solidity Code contract dummy { uint s; function foo(uint a) public returns (uint) { while (a < s) { if (a > 10) { a += 1; } else { a += 2; } } return a; } } 4
5 Compiled Contract e5763ffffffff7c fbebd b600080fd5b e fd5b a565b f35b60005b a f565b b606d565b a a7a fc9f61669f3d0fe36966d60c64042dec36a23ac 89e6b4ebe1752f2c7ca
6 EVM Bytecode PUSH1 0x80 PUSH1 0x40 MSTORE PUSH1 0x04 CALLDATASIZE LT PUSH1 0x3e JUMPI PUSH4 0xffffffff PUSH29 0x PUSH1 0x00 CALLDATALOAD 6
7 Problem: Opaque/proprietary contracts EVM bytecode is not easily understandable High level source code is not always available Contract functionality remains opaque/proprietary 7
8 Ecosystem: Total Count: 1,024,886 Unique Count: 34,328 How many contracts are there? 8
9 Ecosystem: How many contracts are opaque/proprietary? 10,387 Solidity Source Files Collected (from Etherscan) 35 Versions (v0.1.3 to v0.4.19) of Solidity Compilers Used 88,426 Unique Binaries Compiled 9
10 Ecosystem: Measuring Opacity Contracts Total 1,024,886 Unique 34,328 (100.0%) Unique Transparent 7,734 (22.5%) Unique Opaque 26,594 (77.5%) 10
11 Ecosystem: Measuring Opacity Contracts Total 1,024,886 Unique 34,328 (100.0%) Unique Transparent 7,734 (22.5%) Unique Opaque 26,594 (77.5%) 11
12 Erays 12
13 Erays: System Design Control Flow Graph Recovery Lifting Optimization Aggregation Control Flow Structure Recovery 13
14 Control Flow Graph Recovery Identify basic block boundaries JUMPDEST PUSH1 0x0 JUMPDEST PUSH1 0x0 SLOAD DUP3 LT ISZERO PUSH1 0x93 JUMPI 1 14
15 Control Flow Graph Recovery Identify basic block boundaries JUMPDEST PUSH1 0x0 JUMPDEST PUSH1 0x0 SLOAD DUP3 LT ISZERO PUSH1 0x93 JUMPI 1 15
16 Control Flow Graph Recovery Identify basic block boundaries Organize basic blocks into a CFG Emulate the contract using a stack model Explore the contract in a manner similar to Depth First Search Record stack images at each block entrance 1 16
17 JUMPDEST PUSH1 0x88 JUMPI PUSH1 0x93 JUMPI PUSH1 0x8f JUMP PUSH1 0x6d JUMP return Control Flow Graph Recovery 17
18 JUMPDEST PUSH1 0x88 JUMPI PUSH1 0x93 JUMPI PUSH1 0x8f JUMP PUSH1 0x6d JUMP return Control Flow Graph Recovery 18
19 JUMPDEST PUSH1 0x88 JUMPI PUSH1 0x93 JUMPI PUSH1 0x8f JUMP PUSH1 0x6d JUMP return Control Flow Graph Recovery 19
20 JUMPDEST PUSH1 0x88 JUMPI PUSH1 0x93 JUMPI PUSH1 0x8f JUMP PUSH1 0x6d JUMP return Control Flow Graph Recovery 20
21 JUMPDEST PUSH1 0x88 JUMPI PUSH1 0x93 JUMPI PUSH1 0x8f JUMP PUSH1 0x6d JUMP return Control Flow Graph Recovery 21
22 JUMPDEST PUSH1 0x88 JUMPI PUSH1 0x93 JUMPI PUSH1 0x8f JUMP PUSH1 0x6d JUMP return Control Flow Graph Recovery 22
23 JUMPDEST PUSH1 0x88 JUMPI PUSH1 0x93 JUMPI PUSH1 0x8f JUMP PUSH1 0x6d JUMP return Control Flow Graph Recovery 23
24 JUMPDEST PUSH1 0x88 JUMPI PUSH1 0x93 JUMPI PUSH1 0x8f JUMP PUSH1 0x6d JUMP return Control Flow Graph Recovery 24
25 JUMPDEST PUSH1 0x88 JUMPI PUSH1 0x93 JUMPI PUSH1 0x8f JUMP PUSH1 0x6d JUMP return Control Flow Graph Recovery 25
26 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) $s2 Map stack slots to registers $s1 $s
27 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) ADD $s2 0x2 Map stack slots to registers Assign registers to each bytecode (using stack height) $s1 0x3 $s0 0xb
28 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) ADD $s2 0x2 Map stack slots to registers Assign registers to each bytecode (using stack height) $s1 0x3 $s0 0xb
29 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) ADD $s2 0x2 + 0x3 Map stack slots to registers Assign registers to each bytecode (using stack height) $s1 $s0 0xb
30 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) ADD $s2 0x5 Map stack slots to registers Assign registers to each bytecode (using stack height) $s1 $s0 0xb
31 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) $s2 ADD Map stack slots to registers Assign registers to each bytecode (using stack height) $s1 0x5 $s0 0xb
32 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) $s2 ADD $s1, $s2, $s1 Map stack slots to registers Assign registers to each bytecode (using stack height) $s1 0x5 $s0 0xb
33 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) Map stack slots to registers Assign registers to each bytecode (using stack height) PUSH1 SLOAD DUP3 LT ISZERO PUSH1 JUMPI 0x0 0x
34 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) Map stack slots to registers Assign registers to each bytecode (using stack height) MOVE $s4, 0x0 SLOAD $s4, [$s4] MOVE $s5, $s2 LT $s4, $s5, $s4 ISZERO $s4, $s4 MOVE $s5, 0x93 JUMPI $s5, $s
35 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) Introduce new instructions
36 Lifting: Stack-based to Register-based Convert stack-based operations into register-based representation (R. Vallee-Rai 1999) Introduce new instructions INTCALL, INTRET MOVE ASSERT NEQ, GEQ, LEQ, SL, SR
37 Optimization: Removing Redundancy Global optimizations (1973 G. Kildall) MOVE $s4, 0x0 SLOAD $s4, [$s4] MOVE $s5, $s2 LT $s4, $s5, $s4 ISZERO $s4, $s4 MOVE $s5, 0x93 JUMPI $s5, $s
38 Optimization: Removing Redundancy Global optimizations (1973 G. Kildall) Constant propagation MOVE $s4, 0x0 SLOAD $s4, [0x0] MOVE $s5, $s2 LT $s4, $s5, $s4 ISZERO $s4, $s4 MOVE $s5, 0x93 JUMPI 0x93, $s
39 Optimization: Removing Redundancy Global optimizations (1973 G. Kildall) Constant propagation Copy propagation MOVE $s4, 0x0 SLOAD $s4, [0x0] MOVE $s5, $s2 LT $s4, $s2, $s4 ISZERO $s4, $s4 MOVE $s5, 0x93 JUMPI 0x93, $s
40 Optimization: Removing Redundancy Global optimizations (1973 G. Kildall) Constant propagation Copy propagation Dead code elimination -- SLOAD $s4, [0x0] -- LT $s4, $s2, $s4 ISZERO $s4, $s4 -- JUMPI 0x93, $s
41 Optimization: Removing Redundancy Global optimizations (1973 G. Kildall) Constant propagation Copy propagation Dead code elimination -- SLOAD $s4, [0x0] -- LT $s4, $s2, $s4 ISZERO $s4, $s4 -- JUMPI 0x93, $s4 Local optimizations
42 Optimization: Removing Redundancy Global optimizations (1973 G. Kildall) Constant propagation Copy propagation Dead code elimination -- SLOAD $s4, [0x0] GEQ $s4, $s2, $s4 -- JUMPI 0x93, $s4 Local optimizations
43 Optimization: Removing Redundancy Global optimizations (1973 G. Kildall) Constant propagation SLOAD $s4, [0x0] GEQ $s4, $s2, $s4 JUMPI 0x93, $s4 Copy propagation Dead code elimination Local optimizations
44 Aggregation: Condensing the Output Convert register-based instructions into three address form SLOAD $s4, [0x0] GEQ $s4, $s2, $s4 JUMPI 0x93, $s
45 Aggregation: Condensing the Output Convert register-based instructions into three address form $s4 = S[0x0] $s4 = $s2 $s4 if ($s4) goto 0x
46 Aggregation: Condensing the Output Convert register-based instructions into three address form Aggregate instructions into nested expressions (R. Vallee-Rai 1999) $s4 = S[0x0] $s4 = $s2 $s4 if ($s4) goto 0x
47 Aggregation: Condensing the Output Convert register-based instructions into three address form Aggregate instructions into nested expressions (R. Vallee-Rai 1999) -- $s4 = $s2 S[0x0] if ($s4) goto 0x
48 Aggregation: Condensing the Output Convert register-based instructions into three address form Aggregate instructions into nested expressions (R. Vallee-Rai 1999) if ($s2 S[0x0]) goto 0x
49 Aggregation: Condensing the Output Convert register-based instructions into three address form if ($s2 S[0x0]) goto 0x93 Aggregate instructions into nested expressions (R. Vallee-Rai 1999)
50 Control Flow Structure Recovery Separate each public function subgraph Use structural analysis (M. Sharir 1980) Match subgraphs to control constructs (while, if then else) Collapse matched subgraphs
51 ASSERT(0 == msg.value) $s2 = C[0x4] if ($s2 >= S[0x0]) goto 0x93 if ($s2 <= 0xa) goto 0x88 $s2 = 0x1 + $s2 goto 0x8f $s2 = 0x2 + $s2 goto 0x6d M[$m] = $s2 RETURN($m, 0x20) Control Flow Structure Recovery 51
52 ASSERT(0 == msg.value) $s2 = C[0x4] if ($s2 >= S[0x0]) goto 0x93 if ($s2 <= 0xa) { $s2 = 0x2 + $s2 } else { $s2 = 0x1 + $s2 } goto 0x6d M[$m] = $s2 RETURN($m, 0x20) Control Flow Structure Recovery 52
53 ASSERT(0 == msg.value) $s2 = C[0x4] if ($s2 >= S[0x0]) goto 0x93 if ($s2 <= 0xa) { $s2 = 0x2 + $s2 } else { $s2 = 0x1 + $s2 } goto 0x6d M[$m] = $s2 RETURN($m, 0x20) Control Flow Structure Recovery 53
54 ASSERT(0 == msg.value) $s2 = C[0x4] while (0x1) { if ($s2 >= S[0x0]) break if ($s2 <= 0xa) { $s2 = 0x2 + $s2 } else { $s2 = 0x1 + $s2 } } M[$m] = $s2 RETURN($m, 0x20) Control Flow Structure Recovery 54
55 ASSERT(0 == msg.value) $s2 = C[0x4] while (0x1) { if ($s2 >= S[0x0]) break if ($s2 <= 0xa) { $s2 = 0x2 + $s2 } else { $s2 = 0x1 + $s2 } } M[$m] = $s2 RETURN($m, 0x20) Control Flow Structure Recovery 55
56 Validation Construct test cases using historical transactions Leverage Geth to generate the expected transaction output Execute our representation and compare the output 56
57 Validation Construct test cases using historical transactions Leverage Geth to generate the expected transaction output Transactions Total 15,855 (100.0 %) Execute our representation and compare the output 57
58 Validation Construct test cases using historical transactions Leverage Geth to generate the expected transaction output Transactions Total 15,855 (100.0 %) Success 15,345 (96.8%) Execute our representation and compare the output 58
59 Validation Construct test cases using historical transactions Leverage Geth to generate the expected transaction output Execute our representation and compare the output Transactions Total 15,855 (100.0 %) Success 15,345 (96.8%) Failures 510 (3.2%) 59
60 Validation Construct test cases using historical transactions Leverage Geth to generate the expected transaction output Execute our representation and compare the output Transactions Total 15,855 (100.0 %) Success 15,345 (96.8%) Failures 510 (3.2%) Construction Failures 196 (1.2%) 60
61 Validation Construct test cases using historical transactions Leverage Geth to generate the expected transaction output Execute our representation and compare the output Transactions Total 15,855 (100.0 %) Success 15,345 (96.8%) Failures 510 (3.2%) Construction Failures 196 (1.2%) Comparison Failures 314 (2.0%) 61
62 Use Case 62
63 Erays: Function Fuzzy Hash Binary X Function A Function B Function C 63
64 Erays: Function Fuzzy Hash Binary X Function A Hash A 0x746f7563 Compute Fuzzy Hash Function B Function C 64
65 Erays: Function Fuzzy Hash Binary X Function A Function B Function C Hash A 0x746f7563 Hash B 0x d Hash C 0x
66 Erays: Code Sharing Binary X Function A Function B Function C Hash A 0x746f7563 Hash B 0x d Hash C 0x Binary Y Function B Function D Hash D 0x
67 Case Studies 67
68 Case Study: High Value Contracts Look for opaque contracts with large Ether balance ~ $590M Multi-signature wallets likely used by the Gemini exchange Multi-Signature Wallet: signature scheme requiring k-of-n signatures. Security best practice for large sums of money 68
69 Case Study: High Value Contracts Look for opaque contracts with large Ether balance ~ $590M / 3 contracts Multi-signature wallets likely used by the Gemini exchange Interesting, time-dependent withdrawal policies Multi-Signature Wallet: signature scheme requiring k-of-n signatures. Security best practice for large sums of money 69
70 Time Dependency Hazard Found block.timestamp used in contract Erays reveals it is used to control the delay of withdrawal requests Useful auditing tool, even for opaque contracts 70
71 Case Study: Duplicate Contracts Look for opaque contracts with the most instances Exchange user wallets Poloniex: ~350,000 contracts Yunbi: ~90,000 contracts A different approach to handling user funds 71
72 Case Study: EtherDelta Arbitrage Decentralized token exchanges (DEX) operate entirely on-chain Etherdelta
73 Case Study: EtherDelta Arbitrage Decentralized token exchanges (DEX) operate entirely on-chain Etherdelta Arbitrageur Behavior Evidence of arbitrageurs DEX
74 Case Study: EtherDelta Arbitrage Decentralized token exchanges (DEX) operate entirely on-chain Etherdelta Arbitrageur Behavior Evidence of arbitrageurs Executing a buy/sell mismatch for a profit DEX
75 Case Study: EtherDelta Arbitrage Bots Arbitrageurs must publish gadgets to facilitate arbitrage Create functions to validate the order and new trade Implement atomic batch trades (or fail) Arbitrageur Behavior Buy/Sell Trades Gadg. Assert or revert both trades DEX
76 Case Study: CryptoKitties 76
77 77
78 Case Study: CryptoKitties On-chain game code is published with source code Game mechanism well understood 78
79 Case Study: CryptoKitties Developers who know the algorithm aren t allowed to play the game! 79
80 Case Study: CryptoKitties Developers who know the algorithm aren t allowed to play the game! So obviously we had to target this function 80
81 Case Study: CryptoKitties Matron bits Randomness(block hash) Sire The block hash is used to inject random mutations into genes and to select a parent for a gene Child 81
82 Case Study: CryptoKitties Matron bits Randomness(block hash) Sire The block hash is used to inject random mutations into genes and to select a parent for a gene Found a more effective breeding strategy Child 82
83 Case Study: CryptoKitties Matron bits Randomness(block hash) Sire The block hash is used to inject random mutations into genes and to select a parent for a gene Found a more effective breeding strategy 5 4 Child 3 2 Don t rely on security through obscurity! 83
84 Conclusion Ethereum smart contract ecosystem is largely opaque ~ 1M contracts, 34K unique, 77.5% unique opaque 84
85 Conclusion Ethereum smart contract ecosystem is largely opaque ~ 1M contracts, 34K unique, 77.5% unique opaque Erays converts EVM bytecode into higher level representations yizhou7@illinois.edu 85
86 Conclusion Ethereum smart contract ecosystem is largely opaque ~ 1M contracts, 34K unique, 77.5% unique opaque Erays converts EVM bytecode into higher level representations yizhou7@illinois.edu The utility of Erays is demonstrated in several case studies High value wallets, exchange user wallets, arbitrage bots, CryptoKitties secret algorithm 86
Smart!= Secure - Breaking Ethereum Smart Contracts. Elliot Ward & Jake Humphries
 Smart!= Secure - Breaking Ethereum Smart Contracts Elliot Ward & Jake Humphries Elliot Ward Senior Security Consultant @elliotjward eward@gdssecurity.com Jake Humphries Security Consultant @jake_151 jhumphries@gdssecurity.com
Smart!= Secure - Breaking Ethereum Smart Contracts Elliot Ward & Jake Humphries Elliot Ward Senior Security Consultant @elliotjward eward@gdssecurity.com Jake Humphries Security Consultant @jake_151 jhumphries@gdssecurity.com
Declarative Static Analysis of Smart Contracts
 Declarative Static Analysis of Smart Contracts securify.ch Quentin Hibon Blockchain Security Engineer, ChainSecurity Smart Contract Bugs in the News Low-level Code Solidity High-level languages Vyper compilation
Declarative Static Analysis of Smart Contracts securify.ch Quentin Hibon Blockchain Security Engineer, ChainSecurity Smart Contract Bugs in the News Low-level Code Solidity High-level languages Vyper compilation
The power of Blockchain: Smart Contracts. Foteini Baldimtsi
 The power of Blockchain: Smart Contracts Foteini Baldimtsi The Blockchain at the heart of a cryptocurrency Alice sends 2 John sends 1 Dave sends 5 to Bob to Eve to Alice Bob sends 1 Eve sends 4 to Dave
The power of Blockchain: Smart Contracts Foteini Baldimtsi The Blockchain at the heart of a cryptocurrency Alice sends 2 John sends 1 Dave sends 5 to Bob to Eve to Alice Bob sends 1 Eve sends 4 to Dave
Lecture 10. A2 - will post tonight - due in two weeks
 Lecture 10 A2 - will post tonight - due in two weeks The DAO - $72M USD in Ether Decentralized Dragon's Den or Shark's Tank A pot of money that you could contribute to and receive voting shares for You
Lecture 10 A2 - will post tonight - due in two weeks The DAO - $72M USD in Ether Decentralized Dragon's Den or Shark's Tank A pot of money that you could contribute to and receive voting shares for You
An Analysis of Atomic Swaps on and between Ethereum Blockchains Research Project I
 An Analysis of Atomic Swaps on and between Ethereum Blockchains Research Project I Master of System and Network Engineering Informatics Institute, University of Amsterdam Peter Bennink Lennart van Gijtenbeek
An Analysis of Atomic Swaps on and between Ethereum Blockchains Research Project I Master of System and Network Engineering Informatics Institute, University of Amsterdam Peter Bennink Lennart van Gijtenbeek
Porosity: A Decompiler For Blockchain-Based Smart Contracts Bytecode
 Porosity: A Decompiler For Blockchain-Based Smart Contracts Bytecode Matt Suiche Comae Technologies m@comae.io July 7, 2017 Abstract Ethereum is gaining a significant popularity in the blockchain community,
Porosity: A Decompiler For Blockchain-Based Smart Contracts Bytecode Matt Suiche Comae Technologies m@comae.io July 7, 2017 Abstract Ethereum is gaining a significant popularity in the blockchain community,
scompile: Critical Path Identification and Analysis for Smart Contracts
 scompile: Critical Path Identification and Analysis for Smart Contracts Jialiang Chang, Bo Gao, Hao Xiao, Jun Sun and Zijiang Yang Department of Computer Science Western Michigan University, Kalamazoo,
scompile: Critical Path Identification and Analysis for Smart Contracts Jialiang Chang, Bo Gao, Hao Xiao, Jun Sun and Zijiang Yang Department of Computer Science Western Michigan University, Kalamazoo,
Christian Rossow CISPA, Saarland University, Saarland Informatics Campus. Johannes Krupp CISPA, Saarland University, Saarland Informatics Campus
 TEETHER: Gnawing at Ethereum to Automatically Exploit Smart Contracts Johannes Krupp CISPA, Saarland University, Saarland Informatics Campus Christian Rossow CISPA, Saarland University, Saarland Informatics
TEETHER: Gnawing at Ethereum to Automatically Exploit Smart Contracts Johannes Krupp CISPA, Saarland University, Saarland Informatics Campus Christian Rossow CISPA, Saarland University, Saarland Informatics
Porosity Decompiling Ethereum Smart-Contracts. Matt Suiche Founder, Comae Technologies
 Porosity Decompiling Ethereum Smart-Contracts Matt Suiche (@msuiche) Founder, Comae Technologies m@comae.io Whoami @msuiche Comae Technologies OPCDE - www.opcde.com First time in Vegas since BlackHat 2011
Porosity Decompiling Ethereum Smart-Contracts Matt Suiche (@msuiche) Founder, Comae Technologies m@comae.io Whoami @msuiche Comae Technologies OPCDE - www.opcde.com First time in Vegas since BlackHat 2011
Active Planning Committee John Lindsay, Patent Attorney Tony Schuman, Investment Advisor Todd Russell, Gov t Contract Opportunities
 Agenda 11:30-11:45 Check-In, networking 11:45-12:45 12:45 Announcements, Networking Active Planning Committee John Lindsay, Patent Attorney Tony Schuman, Investment Advisor Todd Russell, Gov t Contract
Agenda 11:30-11:45 Check-In, networking 11:45-12:45 12:45 Announcements, Networking Active Planning Committee John Lindsay, Patent Attorney Tony Schuman, Investment Advisor Todd Russell, Gov t Contract
TABLE OF CONTENTS 1.0 TOKEN SALE SUMMARY INTRODUCTION HOW TO BUY LION HOW TO BUY LION WITH METAMASK
 TABLE OF CONTENTS 1.0 TOKEN SALE SUMMARY... 2 2.0 INTRODUCTION... 3 3.0 HOW TO BUY LION... 3 3.1 HOW TO BUY LION WITH METAMASK... 3 3.2 HOW TO BUY LION WITH MYETHERWALLET... 5 4.0 HOW TO CHECK YOUR LION
TABLE OF CONTENTS 1.0 TOKEN SALE SUMMARY... 2 2.0 INTRODUCTION... 3 3.0 HOW TO BUY LION... 3 3.1 HOW TO BUY LION WITH METAMASK... 3 3.2 HOW TO BUY LION WITH MYETHERWALLET... 5 4.0 HOW TO CHECK YOUR LION
Porosity. Decompiling Ethereum Smart-Contracts. Matt Suiche Founder, Comae Technologies Tel Aviv (BLUEHATIL) 23 January, 2018
 Porosity Decompiling Ethereum Smart-Contracts Matt Suiche (@msuiche) Founder, Comae Technologies m@comae.io Tel Aviv (BLUEHATIL) 23 January, 2018 Whoami @msuiche Comae Technologies OPCDE Conference (Dubai,
Porosity Decompiling Ethereum Smart-Contracts Matt Suiche (@msuiche) Founder, Comae Technologies m@comae.io Tel Aviv (BLUEHATIL) 23 January, 2018 Whoami @msuiche Comae Technologies OPCDE Conference (Dubai,
Gnosis Safe Documentation. Gnosis
 Gnosis Aug 14, 2018 Content 1 Learn more about Gnosis Safe 3 1.1 Smart Contract Overview........................................ 3 1.2 Services Overview............................................ 10
Gnosis Aug 14, 2018 Content 1 Learn more about Gnosis Safe 3 1.1 Smart Contract Overview........................................ 3 1.2 Services Overview............................................ 10
Porosity Decompiling Ethereum Smart-Contracts. Matt Suiche Founder, Comae Technologies
 Porosity Decompiling Ethereum Smart-Contracts Matt Suiche (@msuiche) Founder, Comae Technologies m@comae.io Whoami @msuiche Comae Technologies OPCDE - www.opcde.com First time in Vegas since BlackHat 2011
Porosity Decompiling Ethereum Smart-Contracts Matt Suiche (@msuiche) Founder, Comae Technologies m@comae.io Whoami @msuiche Comae Technologies OPCDE - www.opcde.com First time in Vegas since BlackHat 2011
For further information about the GRID token sale, please visit gridplus.io/token-sale.
 1 1 Introduction Thank you for your interest in purchasing GRID tokens. The following information has been organized to help you complete your purchase using MyEtherWallet, Mist, or MetaMask. For further
1 1 Introduction Thank you for your interest in purchasing GRID tokens. The following information has been organized to help you complete your purchase using MyEtherWallet, Mist, or MetaMask. For further
Blockchain! What consultants should know about it. Daniel
 Blockchain! What consultants should know about it. Daniel Karzel @ Workshop Overview Quick overview of what is planned for the workshop. What you get out of this workshop Workshop goals Understand what
Blockchain! What consultants should know about it. Daniel Karzel @ Workshop Overview Quick overview of what is planned for the workshop. What you get out of this workshop Workshop goals Understand what
DTX Token. Starter guide
 DTX Token Starter guide 2 Choosing for the DTX token to buy and sell sensor data enables you to perform real microtransactions on DataBroker DAO. Every beginning is difficult, but this step-by-step introduction
DTX Token Starter guide 2 Choosing for the DTX token to buy and sell sensor data enables you to perform real microtransactions on DataBroker DAO. Every beginning is difficult, but this step-by-step introduction
LECTURE 2 BLOCKCHAIN TECHNOLOGY EVOLUTION
 LECTURE 2 BLOCKCHAIN TECHNOLOGY EVOLUTION THE PAST: THE VENDING MACHINE DAYS NEW USE CASES Namecoin 2011 Bytecoin 2012 Dogecoin 2013 Decentralized domain name service Privacy, first to use the CryptoNote
LECTURE 2 BLOCKCHAIN TECHNOLOGY EVOLUTION THE PAST: THE VENDING MACHINE DAYS NEW USE CASES Namecoin 2011 Bytecoin 2012 Dogecoin 2013 Decentralized domain name service Privacy, first to use the CryptoNote
TABLE OF CONTENTS 1.0 TOKEN SALE SUMMARY INTRODUCTION HOW TO BUY LION HOW TO BUY LION WITH METAMASK
 TABLE OF CONTENTS 1.0 TOKEN SALE SUMMARY... 2 2.0 INTRODUCTION... 3 3.0 HOW TO BUY LION... 3 3.1 HOW TO BUY LION WITH METAMASK... 3 3.2 HOW TO BUY LION WITH MYETHERWALLET... 5 4.0 HOW TO CHECK YOUR LION
TABLE OF CONTENTS 1.0 TOKEN SALE SUMMARY... 2 2.0 INTRODUCTION... 3 3.0 HOW TO BUY LION... 3 3.1 HOW TO BUY LION WITH METAMASK... 3 3.2 HOW TO BUY LION WITH MYETHERWALLET... 5 4.0 HOW TO CHECK YOUR LION
A SYSTEM FOR ENABLING SHORT-TERM FINANCING
 A SYSTEM FOR ENABLING SHORT-TERM FINANCING 5 The present invention relates generally to a system and method for enabling short-term financing, and finds particular, although not exclusive, utility in invoice
A SYSTEM FOR ENABLING SHORT-TERM FINANCING 5 The present invention relates generally to a system and method for enabling short-term financing, and finds particular, although not exclusive, utility in invoice
Virtual Machine Tutorial
 Virtual Machine Tutorial CSA2201 Compiler Techniques Gordon Mangion Virtual Machine A software implementation of a computing environment in which an operating system or program can be installed and run.
Virtual Machine Tutorial CSA2201 Compiler Techniques Gordon Mangion Virtual Machine A software implementation of a computing environment in which an operating system or program can be installed and run.
Smart Contract Vulnerabilities The most interesting transactions on the Ethereum network
 Smart Contract Vulnerabilities The most interesting transactions on the Ethereum network Hi! Hai! I m maurelian ConsenSys Diligence This talk will be: Storytelling meets vulnerability postmortems First,
Smart Contract Vulnerabilities The most interesting transactions on the Ethereum network Hi! Hai! I m maurelian ConsenSys Diligence This talk will be: Storytelling meets vulnerability postmortems First,
Page Total
 Page 2 3 4 5 6 7 8 9 Total Mark FIRST NAME LAST (FAMILY) NAME STUDENT NUMBER INSE 6630 Fall 2017 Duration: 3 hours One single-sided letter-sized reference sheet of paper is allowed Write answers in the
Page 2 3 4 5 6 7 8 9 Total Mark FIRST NAME LAST (FAMILY) NAME STUDENT NUMBER INSE 6630 Fall 2017 Duration: 3 hours One single-sided letter-sized reference sheet of paper is allowed Write answers in the
DIGITAL ASSET RESEARCH
 Our Digital Assets Primer is a more in-depth look at the underlying technology behind digital assets, using two of the largest cryptocurrencies, in terms of network values, Bitcoin and Ethereum, as examples.
Our Digital Assets Primer is a more in-depth look at the underlying technology behind digital assets, using two of the largest cryptocurrencies, in terms of network values, Bitcoin and Ethereum, as examples.
Theta Token - SLIVER.tv Deposit Guide
 Theta Token - SLIVER.tv Deposit Guide Introduction & Overview In this guide we ll detail how you can acquire Theta Tokens (THETA) and deposit them to SLIVER.tv. The process can be confusing at first, but
Theta Token - SLIVER.tv Deposit Guide Introduction & Overview In this guide we ll detail how you can acquire Theta Tokens (THETA) and deposit them to SLIVER.tv. The process can be confusing at first, but
Learn Blockchain Programming. Ali Dorri
 Learn Blockchain Programming Ali Dorri Traditional Programming Server runs the code User may or may not know the code Complicated algorithms Database Code to be executed Request Response DApps: Distributed
Learn Blockchain Programming Ali Dorri Traditional Programming Server runs the code User may or may not know the code Complicated algorithms Database Code to be executed Request Response DApps: Distributed
A living programming environment for a living blockchain
 A living programming environment for a living blockchain by Santiago Bragagnolo - PharoDays - 2017 santiago.bragagnolo@gmail.com santiago.bragagnolo@inria.fr skype:santiago.bragagnolo @sbragagnolo Disclaimer!
A living programming environment for a living blockchain by Santiago Bragagnolo - PharoDays - 2017 santiago.bragagnolo@gmail.com santiago.bragagnolo@inria.fr skype:santiago.bragagnolo @sbragagnolo Disclaimer!
Token Sale. Participation guide
 Token Sale Participation guide 2 As the DataBroker DAO token sale is closing in, we want to inform our future participants on how to properly take part in our presale on 19th of March. At first glance,
Token Sale Participation guide 2 As the DataBroker DAO token sale is closing in, we want to inform our future participants on how to properly take part in our presale on 19th of March. At first glance,
ContractFuzzer: Fuzzing Smart Contracts for Vulnerability Detection *#
 ContractFuzzer: Fuzzing Smart Contracts for Vulnerability Detection *# Bo Jiang School of Computer Science and Engineering Beihang University Beijing, China jiangbo@buaa.edu.cn Ye Liu School of Computer
ContractFuzzer: Fuzzing Smart Contracts for Vulnerability Detection *# Bo Jiang School of Computer Science and Engineering Beihang University Beijing, China jiangbo@buaa.edu.cn Ye Liu School of Computer
Ergo platform overview
 December 2018 Dmitry Meshkov Ergo platform overview Outline Ergo vision Decentralization Survivability Applicability Roadmap 2 Part 1 Ergo vision 3 History Research and Scorex framework development Testnet
December 2018 Dmitry Meshkov Ergo platform overview Outline Ergo vision Decentralization Survivability Applicability Roadmap 2 Part 1 Ergo vision 3 History Research and Scorex framework development Testnet
Ethereum. Campbell R. Harvey* Duke University and NBER. Ashwin Ramachandran Duke University. Brent Xu ConsenSys. Innovation and Cryptoventures
 Innovation and Cryptoventures Ethereum Campbell R. Harvey* Duke University and NBER Ashwin Ramachandran Duke University Brent Xu ConsenSys February 12, 2018 1 2 Overview Ethereum Basics Under the hood
Innovation and Cryptoventures Ethereum Campbell R. Harvey* Duke University and NBER Ashwin Ramachandran Duke University Brent Xu ConsenSys February 12, 2018 1 2 Overview Ethereum Basics Under the hood
Blockhead Open Service Broker Jonathan Berkhahn Swetha Repakula IBM
 Blockhead Open Service Broker Jonathan Berkhahn Swetha Repakula IBM The Blockhead Open Service Broker Jonathan Berkhahn: jaberkha@us.ibm.com Swetha Repakula: srepaku@us.ibm.com IBM Blockchain 3 1. Deploy
Blockhead Open Service Broker Jonathan Berkhahn Swetha Repakula IBM The Blockhead Open Service Broker Jonathan Berkhahn: jaberkha@us.ibm.com Swetha Repakula: srepaku@us.ibm.com IBM Blockchain 3 1. Deploy
Technical Specifications for Platform Development
 Technical Specifications for Platform Development Contents 1. General Information about the Product... 2 2. Software Requirements... 3 2.1. Functional Requirements... 3 2.2. Server Requirements... 4 3.
Technical Specifications for Platform Development Contents 1. General Information about the Product... 2 2. Software Requirements... 3 2.1. Functional Requirements... 3 2.2. Server Requirements... 4 3.
Instruction for creating an Ethereum based wallet and MUH ICO participation
 Instruction for creating an Ethereum based wallet and MUH ICO participation MUST HAVE TOKEN 1. Create your EHT Wallet In order to participate to the MUH ICO, you must have an Ethereum based wallet. You
Instruction for creating an Ethereum based wallet and MUH ICO participation MUST HAVE TOKEN 1. Create your EHT Wallet In order to participate to the MUH ICO, you must have an Ethereum based wallet. You
ETHEREUM META. Whitepaper 2018/2019. A decentralized token with privacy features. Ethereum Meta team
 ETHEREUM META A decentralized token with privacy features Ethereum Meta team Whitepaper 2018/2019 Table of contents 1. Introduction 2. Goal 3. Economic model 4. How it works 5. Specifications 6. Zero-
ETHEREUM META A decentralized token with privacy features Ethereum Meta team Whitepaper 2018/2019 Table of contents 1. Introduction 2. Goal 3. Economic model 4. How it works 5. Specifications 6. Zero-
Off-Whitepaper. Ethereum. Micah Dameron. Abstract
 Off-Whitepaper Ethereum Micah Dameron Beautiful is better than ugly. Explicit is better than implicit. Simple is better than complex. Complex is better than complicated. The Zen of Python Abstract The
Off-Whitepaper Ethereum Micah Dameron Beautiful is better than ugly. Explicit is better than implicit. Simple is better than complex. Complex is better than complicated. The Zen of Python Abstract The
Securify: Practical Security Analysis of Smart Contracts
 Securify: Practical Security Analysis of Smart Contracts https://securify.ch Dr. Petar Tsankov Scientific Researcher, ICE center, ETH Zurich Co-founder and Chief Scientist, ChainSecurity AG http://www.ptsankov.com/
Securify: Practical Security Analysis of Smart Contracts https://securify.ch Dr. Petar Tsankov Scientific Researcher, ICE center, ETH Zurich Co-founder and Chief Scientist, ChainSecurity AG http://www.ptsankov.com/
CSE 401/M501 Compilers
 CSE 401/M501 Compilers Intermediate Representations Hal Perkins Autumn 2018 UW CSE 401/M501 Autumn 2018 G-1 Agenda Survey of Intermediate Representations Graphical Concrete/Abstract Syntax Trees (ASTs)
CSE 401/M501 Compilers Intermediate Representations Hal Perkins Autumn 2018 UW CSE 401/M501 Autumn 2018 G-1 Agenda Survey of Intermediate Representations Graphical Concrete/Abstract Syntax Trees (ASTs)
Formal Verification of Smart Contracts: Short Paper
 Formal Verification of Smart Contracts: Short Paper Karthikeyan Bhargavan, Antoine Delignat-Lavaud, Cédric Fournet, Anitha Gollamudi, Georges Gonthier, Nadim Kobeissi, Natalia Kulatova, Aseem Rastogi,
Formal Verification of Smart Contracts: Short Paper Karthikeyan Bhargavan, Antoine Delignat-Lavaud, Cédric Fournet, Anitha Gollamudi, Georges Gonthier, Nadim Kobeissi, Natalia Kulatova, Aseem Rastogi,
How Can I See My ENJ? 15. Acquiring Ether (ETH) 16
 Create New MEW Account 2 Step 1: Go to https://www.myetherwallet.com/ 2 Step 2: Go to the New Wallet Tab 2 Step 3: Enter a Strong Password 3 Step 4: Save Your Keystore File 3 Step 5 (optional): Backup
Create New MEW Account 2 Step 1: Go to https://www.myetherwallet.com/ 2 Step 2: Go to the New Wallet Tab 2 Step 3: Enter a Strong Password 3 Step 4: Save Your Keystore File 3 Step 5 (optional): Backup
EthIR: A Framework for High-Level Analysis of Ethereum Bytecode
 EthIR: A Framework for High-Level Analysis of Ethereum Bytecode Elvira Albert, Pablo Gordillo, Benjamin Livshits, Albert Rubio, and Ilya Sergey Abstract. Analyzing Ethereum bytecode, rather than the source
EthIR: A Framework for High-Level Analysis of Ethereum Bytecode Elvira Albert, Pablo Gordillo, Benjamin Livshits, Albert Rubio, and Ilya Sergey Abstract. Analyzing Ethereum bytecode, rather than the source
Do You Trust a Mutated Binary? Drew Bernat Correct Relocation
 Correct Relocation: Do You Trust a Mutated Binary? Drew Bernat bernat@cs.wisc.edu April 30, 2007 Correct Relocation Binary Manipulation We want to: Insert new code Modify or delete code These operations
Correct Relocation: Do You Trust a Mutated Binary? Drew Bernat bernat@cs.wisc.edu April 30, 2007 Correct Relocation Binary Manipulation We want to: Insert new code Modify or delete code These operations
BLOCKCHAIN CADEC Pär Wenåker & Peter Larsson
 BLOCKCHAIN CADEC 2018 - Pär Wenåker & Peter Larsson BITCOIN BITCOIN PAPER Posted 31/10 2008 Bitcoin v0.1 released Satoshi Nakamoto satoshi at vistomail.com Thu Jan 8 14:27:40 EST 2009 Previous message:
BLOCKCHAIN CADEC 2018 - Pär Wenåker & Peter Larsson BITCOIN BITCOIN PAPER Posted 31/10 2008 Bitcoin v0.1 released Satoshi Nakamoto satoshi at vistomail.com Thu Jan 8 14:27:40 EST 2009 Previous message:
kasko2go Token Contract Audit
 Version 1.0 / 17.04.2018 kasko2go Token Contract Audit inacta AG Eugen Lechner Cédric Walter Index 1. Introduction 2 2. Scope 2 3. Executive Summary
Version 1.0 / 17.04.2018 kasko2go Token Contract Audit inacta AG Eugen Lechner Cédric Walter Index 1. Introduction 2 2. Scope 2 3. Executive Summary
THE B+ TREE INDEX. CS 564- Spring ACKs: Jignesh Patel, AnHai Doan
 THE B+ TREE INDEX CS 564- Spring 2018 ACKs: Jignesh Patel, AnHai Doan WHAT IS THIS LECTURE ABOUT? The B+ tree index Basics Search/Insertion/Deletion Design & Cost 2 INDEX RECAP We have the following query:
THE B+ TREE INDEX CS 564- Spring 2018 ACKs: Jignesh Patel, AnHai Doan WHAT IS THIS LECTURE ABOUT? The B+ tree index Basics Search/Insertion/Deletion Design & Cost 2 INDEX RECAP We have the following query:
Ergo platform: from prototypes to a survivable cryptocurrency
 January 2019 Dmitry Meshkov Ergo platform: from prototypes to a survivable cryptocurrency Outline Ergo Consensus Light Storage vision protocol clients fee Voting Smart Monetary Roadmap system contracts
January 2019 Dmitry Meshkov Ergo platform: from prototypes to a survivable cryptocurrency Outline Ergo Consensus Light Storage vision protocol clients fee Voting Smart Monetary Roadmap system contracts
Oyente: Making Smart Contracts Smarter
 Oyente: Making Smart Contracts Smarter Loi Luu, Duc-Hiep Chu, Hrishi Olickel Prateek Saxena, Aquinas Hobor National University of Singapore, Yale-NUS College Programming securely is hard Security can be
Oyente: Making Smart Contracts Smarter Loi Luu, Duc-Hiep Chu, Hrishi Olickel Prateek Saxena, Aquinas Hobor National University of Singapore, Yale-NUS College Programming securely is hard Security can be
arxiv: v1 [cs.dc] 5 Jan 2019
![arxiv: v1 [cs.dc] 5 Jan 2019 arxiv: v1 [cs.dc] 5 Jan 2019](/thumbs/93/113433528.jpg) An Empirical Study of Speculative Concurrency in Ethereum Smart Contracts Vikram Saraph and Maurice Herlihy January 8, 19 arxiv:191.176v1 [cs.dc] 5 Jan 19 Abstract We use historical data to estimate the
An Empirical Study of Speculative Concurrency in Ethereum Smart Contracts Vikram Saraph and Maurice Herlihy January 8, 19 arxiv:191.176v1 [cs.dc] 5 Jan 19 Abstract We use historical data to estimate the
Ergo platform. Dmitry Meshkov
 Ergo platform Dmitry Meshkov Prehistory Motivation Theory Practice Provably secure 1000 currencies New features Ad-hoc solutions Impractical Security issues Motivation Theory Provably secure New features
Ergo platform Dmitry Meshkov Prehistory Motivation Theory Practice Provably secure 1000 currencies New features Ad-hoc solutions Impractical Security issues Motivation Theory Provably secure New features
Ethereum. Smart Contracts Programming Model
 Cryptocurrency Technologies Recall: Bitcoin scripting: non Turing-complete limited/limiting Solutions: Add application-specific functionality in scripting of altcoin Create altcoin with Turing-complete
Cryptocurrency Technologies Recall: Bitcoin scripting: non Turing-complete limited/limiting Solutions: Add application-specific functionality in scripting of altcoin Create altcoin with Turing-complete
Building Applications on the Ethereum Blockchain
 Building Applications on the Ethereum Blockchain Eoin Woods Endava @eoinwoodz licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 1 Agenda Blockchain Recap Ethereum Application
Building Applications on the Ethereum Blockchain Eoin Woods Endava @eoinwoodz licensed under a Creative Commons Attribution-ShareAlike 4.0 International License 1 Agenda Blockchain Recap Ethereum Application
ICO smart contracts Documentation
 ICO smart contracts Documentation Release 0.1 Mikko Ohtamaa Feb 05, 2018 Contents: 1 Introduction 3 2 Contracts 7 3 Installation 9 4 Command line commands 13 5 Interacting with deployed smart contracts
ICO smart contracts Documentation Release 0.1 Mikko Ohtamaa Feb 05, 2018 Contents: 1 Introduction 3 2 Contracts 7 3 Installation 9 4 Command line commands 13 5 Interacting with deployed smart contracts
CSE P 501 Compilers. Intermediate Representations Hal Perkins Spring UW CSE P 501 Spring 2018 G-1
 CSE P 501 Compilers Intermediate Representations Hal Perkins Spring 2018 UW CSE P 501 Spring 2018 G-1 Administrivia Semantics/types/symbol table project due ~2 weeks how goes it? Should be caught up on
CSE P 501 Compilers Intermediate Representations Hal Perkins Spring 2018 UW CSE P 501 Spring 2018 G-1 Administrivia Semantics/types/symbol table project due ~2 weeks how goes it? Should be caught up on
Bitcoin and Blockchain
 Bitcoin and Blockchain COS 418: Distributed Systems Lecture 18 Zhenyu Song [Credit: Selected content adapted from Michael Freedman. Slides refined by Chris Hodsdon and Theano Stavrinos] Why Bitcoin? All
Bitcoin and Blockchain COS 418: Distributed Systems Lecture 18 Zhenyu Song [Credit: Selected content adapted from Michael Freedman. Slides refined by Chris Hodsdon and Theano Stavrinos] Why Bitcoin? All
Privacy based Public Key Infrastructure (PKI) using Smart Contract in Blockchain Technology
 2 nd Advanced Workshop on Blockchain, IIT Bombay Privacy based Public Key Infrastructure (PKI) using Smart Contract in Blockchain Technology Sivakumar.P M.Tech (CSE), Sem-III, NIT Trichy Guide:- Dr Kunwar
2 nd Advanced Workshop on Blockchain, IIT Bombay Privacy based Public Key Infrastructure (PKI) using Smart Contract in Blockchain Technology Sivakumar.P M.Tech (CSE), Sem-III, NIT Trichy Guide:- Dr Kunwar
CLN CLN TOKEN SALE. How to Participate Using MyEtherWallter
 CLN CLN TOKEN SALE How to Participate Using MyEtherWallter Colu Technologies DLT limited 3 Table of Contents Introduction 4 Create New Account 5 Step 1: Go to https://www.myetherwallet.com 5 Step 2: Go
CLN CLN TOKEN SALE How to Participate Using MyEtherWallter Colu Technologies DLT limited 3 Table of Contents Introduction 4 Create New Account 5 Step 1: Go to https://www.myetherwallet.com 5 Step 2: Go
Introduction to Blockchain
 Diogo Trentini e Lauro Gripa Neto Introduction to Blockchain www.magrathealabs.com source: Scott Adams' Dilbert source: Gartner Inc. SUMMARY 1. 2. 3. 4. 5. Introduction Theoretical concepts Applications
Diogo Trentini e Lauro Gripa Neto Introduction to Blockchain www.magrathealabs.com source: Scott Adams' Dilbert source: Gartner Inc. SUMMARY 1. 2. 3. 4. 5. Introduction Theoretical concepts Applications
Intermediate Code Generation
 Intermediate Code Generation In the analysis-synthesis model of a compiler, the front end analyzes a source program and creates an intermediate representation, from which the back end generates target
Intermediate Code Generation In the analysis-synthesis model of a compiler, the front end analyzes a source program and creates an intermediate representation, from which the back end generates target
Technical Analysis of Established Blockchain Systems
 Technical Analysis of Established Blockchain Systems Florian Haffke, 20.11.2017, Munich Chair of Software Engineering for Business Information Systems (sebis) Faculty of Informatics Technische Universität
Technical Analysis of Established Blockchain Systems Florian Haffke, 20.11.2017, Munich Chair of Software Engineering for Business Information Systems (sebis) Faculty of Informatics Technische Universität
Muzika Studio now supports Ethereum and Ontology network, and users can choose to login to either Testnet or Mainnet.
 Muzika Studio Muzika Studio allows artists to manage their wallets and create Smart Contract for their digital music products, including music sheets and sound sources. The application also provides an
Muzika Studio Muzika Studio allows artists to manage their wallets and create Smart Contract for their digital music products, including music sheets and sound sources. The application also provides an
SECURITY AUDIT REPORT
 PUBLIC REPORT SECURITY AUDIT REPORT of Smart Contracts December 27, 2017 Produced by for Table of Contents Foreword... 1 Introduction... 2 TGE overview... 2 Token distribution... 3 Extra features... 3
PUBLIC REPORT SECURITY AUDIT REPORT of Smart Contracts December 27, 2017 Produced by for Table of Contents Foreword... 1 Introduction... 2 TGE overview... 2 Token distribution... 3 Extra features... 3
Token sale is live now
 The new Operating System of $7.6 trillion Healthcare Industry Token sale is live now PLEASE FOLLOW THE INSTRUCTIONS CAREFULLY IN ORDER THAT YOU WILL BE ABLE TO SAFELY PARTICIPATE IN ETHEAL TOKEN SALE.
The new Operating System of $7.6 trillion Healthcare Industry Token sale is live now PLEASE FOLLOW THE INSTRUCTIONS CAREFULLY IN ORDER THAT YOU WILL BE ABLE TO SAFELY PARTICIPATE IN ETHEAL TOKEN SALE.
Who wants to be a millionaire? A class in creating your own cryptocurrency
 DEVNET-3626 Who wants to be a millionaire? A class in creating your own cryptocurrency Tom Davies, Sr. Manager, DevNet Sandbox Vallard Benincosa, Software Engineer Cisco Spark How Questions? Use Cisco
DEVNET-3626 Who wants to be a millionaire? A class in creating your own cryptocurrency Tom Davies, Sr. Manager, DevNet Sandbox Vallard Benincosa, Software Engineer Cisco Spark How Questions? Use Cisco
Synapse: Decentralized Intelligence
 Synapse: Decentralized Intelligence A Decentralized Data and Machine Learning Network Dan P. Gailey Version 1.0 Abstract Discusses the architecture and protocol specifications for building the infrastructure
Synapse: Decentralized Intelligence A Decentralized Data and Machine Learning Network Dan P. Gailey Version 1.0 Abstract Discusses the architecture and protocol specifications for building the infrastructure
IoT security based on the DPK platform
 Zz S E C U M O B I. WHITE PAPER IoT security based on the DPK platform Powered by Ethereum David Khoury Elie Kfoury ABSTRACT Public key distribution remains one of the main security weaknesses in many
Zz S E C U M O B I. WHITE PAPER IoT security based on the DPK platform Powered by Ethereum David Khoury Elie Kfoury ABSTRACT Public key distribution remains one of the main security weaknesses in many
SMARTDATA: Leveraging Blockchain to Securely Capture & Verify Scientific Provenance Data
 UT DALLAS Erik Jonsson School of Engineering & Computer Science SMARTDATA: Leveraging Blockchain to Securely Capture & Verify Scientific Provenance Data Dr.Murat Kantarcioglu Joint work with Aravind Ramachandran
UT DALLAS Erik Jonsson School of Engineering & Computer Science SMARTDATA: Leveraging Blockchain to Securely Capture & Verify Scientific Provenance Data Dr.Murat Kantarcioglu Joint work with Aravind Ramachandran
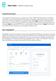
How to buy LIVE Token with Ethereum and Bitcoin step by step
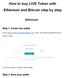 How to buy LIVE Token with Ethereum and Bitcoin step by step Ethereum Step 1. Create new wallet. Go to https://www.myetherwallet.com/, think of a strong password and enter it here: Click the button Create
How to buy LIVE Token with Ethereum and Bitcoin step by step Ethereum Step 1. Create new wallet. Go to https://www.myetherwallet.com/, think of a strong password and enter it here: Click the button Create
CFG (Control flow graph)
 CFG (Control flow graph) Class B T12 오지은 200814189 신승우 201011340 이종선 200811448 Introduction to CFG Algorithm to construct Control Flow Graph Statement of Purpose Q & A Introduction to CFG Algorithm to
CFG (Control flow graph) Class B T12 오지은 200814189 신승우 201011340 이종선 200811448 Introduction to CFG Algorithm to construct Control Flow Graph Statement of Purpose Q & A Introduction to CFG Algorithm to
GENESIS VISION NETWORK
 GENESIS VISION NETWORK Contents 1. Description of the problem 7 11. Trust management 15 2. The problem with smart contracts 8 12. GVN Token 16 3. Centralised exchanges against decentralised 8 13. Deposit
GENESIS VISION NETWORK Contents 1. Description of the problem 7 11. Trust management 15 2. The problem with smart contracts 8 12. GVN Token 16 3. Centralised exchanges against decentralised 8 13. Deposit
OW TO PARTICIPAT HOW TO PARTICIPATE
 OW TO PARTICIPAT HOW TO PARTICIPATE How to take part in FTEC Pre-sale and Token Sale? We will publish token sale address on our official ftec.io and ftec.ai websites accurate on the day of Pre-sale and
OW TO PARTICIPAT HOW TO PARTICIPATE How to take part in FTEC Pre-sale and Token Sale? We will publish token sale address on our official ftec.io and ftec.ai websites accurate on the day of Pre-sale and
Blockchain & Smart Contracts Introduction. Dr. Sebastian Bürgel
 Blockchain & Smart Contracts Introduction Dr. Sebastian Bürgel Does the following make sense? State-of-the-Art Trade Finance (2017) http://blog.zuehlke.com/en/how-the-blockchain-can-disrupt-trade-finance/
Blockchain & Smart Contracts Introduction Dr. Sebastian Bürgel Does the following make sense? State-of-the-Art Trade Finance (2017) http://blog.zuehlke.com/en/how-the-blockchain-can-disrupt-trade-finance/
Unblockable Chains. Is Blockchain the ultimate malicious infrastructure? Omer Zohar
 Unblockable Chains Is Blockchain the ultimate malicious infrastructure? Omer Zohar #WhoAmI Researching malware backbones for the past decade Following blockchain eco-system since 2013 Finally had some
Unblockable Chains Is Blockchain the ultimate malicious infrastructure? Omer Zohar #WhoAmI Researching malware backbones for the past decade Following blockchain eco-system since 2013 Finally had some
HIGH ACCESSIBILITY BLOCKCHAINS THROUGH TOKEN BASED PROOF-OF-STAKE MICRO COMMUNICATION CHANNELS
 HIGH ACCESSIBILITY BLOCKCHAINS THROUGH TOKEN BASED PROOF-OF-STAKE MICRO COMMUNICATION CHANNELS Written by Nelson Hunter Prendergast and Forrest Marshall Dated 3/26/2018 This white paper is a preliminary
HIGH ACCESSIBILITY BLOCKCHAINS THROUGH TOKEN BASED PROOF-OF-STAKE MICRO COMMUNICATION CHANNELS Written by Nelson Hunter Prendergast and Forrest Marshall Dated 3/26/2018 This white paper is a preliminary
Enjin Coin Yellow Paper
 Enjin Coin Yellow Paper Q4 2017, Minimum Viable Product (Oct 1 - Dec 31) Version 1.0 - Updated November 2, 2017 This yellow paper outlines Enjin Coin's initial milestones in 2017 and a technical summary
Enjin Coin Yellow Paper Q4 2017, Minimum Viable Product (Oct 1 - Dec 31) Version 1.0 - Updated November 2, 2017 This yellow paper outlines Enjin Coin's initial milestones in 2017 and a technical summary
HowtobuyHUMToken. Table of Contents. Beforeproceedingwiththepurchase Pre-saleguideusingMyEtherWallet Pre-saleguideusingMetamask
 HowtobuyHUMToken Table of Contents Beforeproceedingwiththepurchase Pre-saleguideusingMyEtherWallet Pre-saleguideusingMetamask Before proceeding with the purchase If you have been registered on our whitelist,
HowtobuyHUMToken Table of Contents Beforeproceedingwiththepurchase Pre-saleguideusingMyEtherWallet Pre-saleguideusingMetamask Before proceeding with the purchase If you have been registered on our whitelist,
FXY TOKEN SMART CONTRACT AUDIT RESULTS FOR FIXY NETWORK LTD
 FXY TOKEN SMART CONTRACT AUDIT RESULTS FOR FIXY NETWORK LTD 04/05/2018 Made in Germany by chainsulting.de Seite 1 von 26 Change history Version Date Author Changes 1.0 05.04.2017 Chainsulting Audit created
FXY TOKEN SMART CONTRACT AUDIT RESULTS FOR FIXY NETWORK LTD 04/05/2018 Made in Germany by chainsulting.de Seite 1 von 26 Change history Version Date Author Changes 1.0 05.04.2017 Chainsulting Audit created
BLOCKCHAIN Blockchains and Transactions Part II A Deeper Dive
 BLOCKCHAIN Blockchains and Transactions Part II A Deeper Dive www.blockchaintrainingalliance.com Blockchain Page 3 Blockchain is NOT Bitcoin Page 4 Transactions Page 5 Multi-Signature Addresses An Address
BLOCKCHAIN Blockchains and Transactions Part II A Deeper Dive www.blockchaintrainingalliance.com Blockchain Page 3 Blockchain is NOT Bitcoin Page 4 Transactions Page 5 Multi-Signature Addresses An Address
Smart Contract Security Tips. Ethereum devcon2 Sep Joseph Chow
 Smart Contract Security Tips Ethereum devcon2 Sep 20 2016 - Joseph Chow One line of code spurred a series of momentous events in blockchain history June 12 2016 Community resource: for the community,
Smart Contract Security Tips Ethereum devcon2 Sep 20 2016 - Joseph Chow One line of code spurred a series of momentous events in blockchain history June 12 2016 Community resource: for the community,
A New Internet for Decentralized Apps
 A New Internet for Decentralized Apps ETC Summit 2017-11-13 Hong Kong Larry Salibra A new internet for decentralized apps About Me 1. Core Developer, Blockstack: Blockstack Explorer (AngularJS) Blockstack
A New Internet for Decentralized Apps ETC Summit 2017-11-13 Hong Kong Larry Salibra A new internet for decentralized apps About Me 1. Core Developer, Blockstack: Blockstack Explorer (AngularJS) Blockstack
Technical Description. Platform SRG community
 Technical Description Platform SRG community SRG Application The SRG platform consists of two architectural paradigms: the client server of centralized architecture that is used in most online applications,
Technical Description Platform SRG community SRG Application The SRG platform consists of two architectural paradigms: the client server of centralized architecture that is used in most online applications,
Previous Name: D3. Fourth Estate. A secure, decentralized news data storing and sharing solution for journalists
 Previous Name: D3 Fourth Estate A secure, decentralized news data storing and sharing solution for journalists Aaron Chong Remini Yip International Student Blockchain Competition s Presentation 1 Problem
Previous Name: D3 Fourth Estate A secure, decentralized news data storing and sharing solution for journalists Aaron Chong Remini Yip International Student Blockchain Competition s Presentation 1 Problem
Callisto Network Whitepaper
 Callisto Network Whitepaper Revision 1.3, 10 June 2018, Dexaran, Ethereum Commonwealth co-authors : Methw, Crika-Ivan; Callisto Team This document is intended to formally describe the features and concepts
Callisto Network Whitepaper Revision 1.3, 10 June 2018, Dexaran, Ethereum Commonwealth co-authors : Methw, Crika-Ivan; Callisto Team This document is intended to formally describe the features and concepts
CMa simple C Abstract Machine
 CMa simple C Abstract Machine CMa architecture An abstract machine has set of instructions which can be executed in an abstract hardware. The abstract hardware may be seen as a collection of certain data
CMa simple C Abstract Machine CMa architecture An abstract machine has set of instructions which can be executed in an abstract hardware. The abstract hardware may be seen as a collection of certain data
FLIP Token (FLP) How to Participate in the FLIP Token (FLP) Sale Event. 1 Disclaimer 2. 2 What You Will Need 2
 FLIP Token (FLP) How to Participate in the FLIP Token (FLP) Sale Event 1 Disclaimer 2 2 What You Will Need 2 3 Create a New MEW Account 2 Step 1: Go to https://www.myetherwallet.com 3 Step 2: Go to the
FLIP Token (FLP) How to Participate in the FLIP Token (FLP) Sale Event 1 Disclaimer 2 2 What You Will Need 2 3 Create a New MEW Account 2 Step 1: Go to https://www.myetherwallet.com 3 Step 2: Go to the
OPEN PLATFORM OPEN WHITEPAPER OPEN. All rights reserved.
 OPEN PLATFORM OPEN WHITEPAPER!1 2017 OPEN. All rights reserved. Table Of Contents Abstract 3 Introduction 4 Decentralized Approach 7 Architectural Design Approach 9 Key Terms 11 OPEN API Architecture 13
OPEN PLATFORM OPEN WHITEPAPER!1 2017 OPEN. All rights reserved. Table Of Contents Abstract 3 Introduction 4 Decentralized Approach 7 Architectural Design Approach 9 Key Terms 11 OPEN API Architecture 13
QUADCORECHAIN. White Paper ver.1
 QUADCORECHAIN White Paper ver.1 INTRO QuadCoreChain is designed to be a smart contract, crypto currency platform, decentralizing Live Streaming of Video. The platform ecosystem is to create favorable conditions
QUADCORECHAIN White Paper ver.1 INTRO QuadCoreChain is designed to be a smart contract, crypto currency platform, decentralizing Live Streaming of Video. The platform ecosystem is to create favorable conditions
Japannext PTS OUCH Trading Specification for Equities
 Japannext PTS OUCH Trading Specification for Equities Version 1.8 Updated 8 November 2017 Table of Contents Introduction...3 Overview...3 Fault Redundancy...3 Service Configuration...3 Data Types...3 Inbound
Japannext PTS OUCH Trading Specification for Equities Version 1.8 Updated 8 November 2017 Table of Contents Introduction...3 Overview...3 Fault Redundancy...3 Service Configuration...3 Data Types...3 Inbound
Cryptocurrencies for Investigators
 Cryptocurrencies for Investigators By Nick Furneaux CSITech Ltd Course Description Cryptocurrencies in their many forms, based on the blockchain concept, are here to stay and will increasingly pervade
Cryptocurrencies for Investigators By Nick Furneaux CSITech Ltd Course Description Cryptocurrencies in their many forms, based on the blockchain concept, are here to stay and will increasingly pervade
FanChain Contract Audit
 FanChain Contract Audit by Hosho, May 2018 Executive Summary This document outlines the overall security of FanChain s smart contract as evaluated by Hosho s Smart Contract auditing team. The scope of
FanChain Contract Audit by Hosho, May 2018 Executive Summary This document outlines the overall security of FanChain s smart contract as evaluated by Hosho s Smart Contract auditing team. The scope of
ENEE 457: E-Cash and Bitcoin
 ENEE 457: E-Cash and Bitcoin Charalampos (Babis) Papamanthou cpap@umd.edu Money today Any problems? Cash is cumbersome and can be forged Credit card transactions require centralized online bank are not
ENEE 457: E-Cash and Bitcoin Charalampos (Babis) Papamanthou cpap@umd.edu Money today Any problems? Cash is cumbersome and can be forged Credit card transactions require centralized online bank are not
Block Gas Limits vs. Transactional Throughput: A Performance Analysis of the Ubiq Platform
 Block Gas Limits vs. Transactional Throughput: A Performance Analysis of the Ubiq Platform Whiteblock, Inc. Abstract The following report outlines a performance benchmarking analysis for the Ubiq blockchain
Block Gas Limits vs. Transactional Throughput: A Performance Analysis of the Ubiq Platform Whiteblock, Inc. Abstract The following report outlines a performance benchmarking analysis for the Ubiq blockchain
Client-Server Architecture PlusUltra beyond the Blockchain
 1--------------------------------------------Table of Contents 2--------------------------------------------PlusUltra Single Sign On 3--------------------------------------------Client-Server Architecture
1--------------------------------------------Table of Contents 2--------------------------------------------PlusUltra Single Sign On 3--------------------------------------------Client-Server Architecture
Secure Token Development and Deployment. Dmitry Khovratovich and Mikhail Vladimirov, University of Luxembourg and ABDK Consulting
 Secure Token Development and Deployment Dmitry Khovratovich and Mikhail Vladimirov, University of Luxembourg and ABDK Consulting ERC-20 tokens and ICO ERC-20 standard: developed in late 2015, de-facto
Secure Token Development and Deployment Dmitry Khovratovich and Mikhail Vladimirov, University of Luxembourg and ABDK Consulting ERC-20 tokens and ICO ERC-20 standard: developed in late 2015, de-facto
Table of contents. Technical Features. Our approach. Technical Overview. Stage 1 (Using Ethereum blockchain) Participants. Data Owner.
 Table of contents Technical Features Our approach Technical Overview Stage 1 (Using Ethereum blockchain) Participants Data Owner Data Verifier Marketplace Data Buyer Creditor Data Platform Architecture
Table of contents Technical Features Our approach Technical Overview Stage 1 (Using Ethereum blockchain) Participants Data Owner Data Verifier Marketplace Data Buyer Creditor Data Platform Architecture
TURING COMPLETE BITCOIN SCRIPT. White Paper CRAIG WRIGHT, NCHAIN. Electronic copy available at:
 TURING COMPLETE BITCOIN SCRIPT White Paper CRAIG WRIGHT, NCHAIN Electronic copy available at: https://ssrn.com/abstract=3160279 Contents Executive Summary... 2 Functional Specification... 3 Technical Specification...
TURING COMPLETE BITCOIN SCRIPT White Paper CRAIG WRIGHT, NCHAIN Electronic copy available at: https://ssrn.com/abstract=3160279 Contents Executive Summary... 2 Functional Specification... 3 Technical Specification...
The promise and peril of smart contracts
 The promise and peril of smart contracts Joseph Bonneau Department of Computer Science New York University Understanding smart contracts The Bitcoin ledger track (mostly) payments time Create 25 coins
The promise and peril of smart contracts Joseph Bonneau Department of Computer Science New York University Understanding smart contracts The Bitcoin ledger track (mostly) payments time Create 25 coins
Problem: Equivocation!
 Bitcoin: 10,000 foot view Bitcoin and the Blockchain New bitcoins are created every ~10 min, owned by miner (more on this later) Thereafter, just keep record of transfers e.g., Alice pays Bob 1 BTC COS
Bitcoin: 10,000 foot view Bitcoin and the Blockchain New bitcoins are created every ~10 min, owned by miner (more on this later) Thereafter, just keep record of transfers e.g., Alice pays Bob 1 BTC COS
How to Buy TRVR Tokens
 How to Buy TRVR Tokens To participate in the distribution of TRVR tokens, you must send Ethers (ETH) to the address of the Token Sale smart contract. This process requires a MyEtherWallet and MetaMask
How to Buy TRVR Tokens To participate in the distribution of TRVR tokens, you must send Ethers (ETH) to the address of the Token Sale smart contract. This process requires a MyEtherWallet and MetaMask
How to use Fusioncoin Wallet
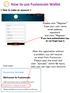 How to use Fusioncoin Wallet < How to make an account > Please click Register Type your user name, email address, password and click Register If you have authentication key, do not forget type it. (Email
How to use Fusioncoin Wallet < How to make an account > Please click Register Type your user name, email address, password and click Register If you have authentication key, do not forget type it. (Email
SmartPool: practical decentralized pool mining. Loi Luu, Yaron Velner, Jason Teutsch, and Prateek Saxena August 18, 2017
 SmartPool: practical decentralized pool mining Loi Luu, Yaron Velner, Jason Teutsch, and Prateek Saxena August 18, 2017 Mining pools Miners role in cryptocurrencies Definition: A cryptocurrency is a decentralized
SmartPool: practical decentralized pool mining Loi Luu, Yaron Velner, Jason Teutsch, and Prateek Saxena August 18, 2017 Mining pools Miners role in cryptocurrencies Definition: A cryptocurrency is a decentralized
