Notice! Updated presentation materials are available online at: Rain Forest Puppy / Wiretrip.
|
|
|
- Lewis Arnold
- 5 years ago
- Views:
Transcription
1 Notice! Updated presentation materials are available online at:
2 Assessing the web A look at the tools used to secure online applications Rain Forest Puppy rfp@wiretrip.net
3 Why target the web? It s everywhere! Mobile phones, cars, watches, toasters Safe bet the protocol will not become obsolete anytime soon New technology is being implemented/retrofitted on top (e.g. SOAP, WebDAV) Protocol fundamentally not suited to do a majority of what it s doing today ( kludge job galore)
4 Problem areas in HTTP The protocol is extremely simple; therefore, it is easy to (mis)code your own HTTP server Lack of experience coding public-service, multiuser applications Multitude of involved technologies Stateless nature
5 The stateless problem The HTTP protocol doesn t include the mechanisms needed to have data persistence between requests People are left to implement there own attempt at data persistence (retrofit state onto the stateless protocol) Same typical problems reoccur due to everyone reinventing the wheel Extremely difficult, if not impossible, to invent tools that can automatically assess such custom implementations
6 Tools as they exist today
7 Vulnerability scanners Look for a known list of vulnerable applications or technologies Do not (can not) engage/scan custom applications and configurations General vulnerability scanners: ISS, Cybercop, Nessus Web-specific vulnerability scanners: WebInspect, whisker
8 Proxy monitors HTTP proxy which monitors traffic, looking for web vulnerabilities as they pass Can analyze custom applications with the help of a user Examples: AppScan, RFProxy
9 Quick spotlight Sanctium AppScan proxy that passively monitors for potential problems Philip Stoev s ELZA scripting tool used to interact with web applications Spi Dynamic s WebInspect vulnerability scanner that crawls website eeye Retina CHAM can be used to methodically check for buffer overflows General vulnerability scanners Nessus, ISS, Cybercop, HackerShield, etc
10 The coming of whisker
11 whisker 1.x Released October 20, 1999 Competition : VoidEye, cgichk, billions of homecoded scanners Coded out of shear annoyance by currently-available scanners
12 whisker 1.x design goals Scriptable: easily updated by just about anyone Intelligent: conditional scanning, reduction of false positives, directory checking Flexible: easily adapted to custom configurations Bonus features: IDS evasion, virtual hosts, authentication brute forcing
13 whisker 1.x fallout Very few people actually wrote new scripts; those capable of writing scripts seemed capable of writing full code Still requires some forethought and tweaking to fully assess custom configurations Code design could be improved; some functionality was still lacking Limited to file-existence scanning
14 Back to the drawing board
15 Various personal observations Most people shifted to a new scanner when old one became outdated People reusing whisker s sendraw() HTTP code To be viable, scripting support had to be full-featured People tend to (poorly) recode common functionality in web exploits and demonstration code
16 So how about a new approach A well-documented and full-featured library of components useful to assessing web applications Replaces the limited-scripting model with the full capabilities of a real programming language Lends better to the custom nature of web applications
17 And thus whisker 2.x..a.k.a. libwhisker All whisker functionality has been modularized into various Perl functions Scripts now have the full processing power of Perl to use for logic evaluations Perl is relatively cross-platform portable Since those who coded their own whisker 1.x scan scripts seemed capable of coding Perl, this isn t a large loss in my eyes
18 I can t code, what good does an API do me? Directly? Not much good. However, there are three important points that do affect you: Modular nature of whisker will hopefully spark new interest in development and contribution (I can t continue to be a one-puppy-show) If people use libwhisker as a basis for their code, you indirectly receive the stability in other programs A script that demonstrates the API will be included; however, this script will serve all the functions of the normal whisker scanner
19 Peek into libwhisker
20 HTTP module The core of whisker, passes a request to a server and receives the response Capable of handling HTTP 0.9, 1.0, and 1.1 connections HTTP 1.1 keep-alive/connection reuse Receive chunked encoding Full integrated HTTP proxy and virtual host support Complete cross-platform timeout support Transparent data handling (PUT, POST, etc) Handles HTTP 100 Continue responses
21 HTTP module cont. All aspects are completely customizable for ultimate control Controlled by a single structure (Perl hash) How easy is it to make a simple web request? use libwhisker; my %in, %out; whttp::request_init(\%in); $in{ whisker }->{ uri }= /some/webpage.htm ; $in{ whisker }->{ host }= ; whttp::do_request(\%in,\%out); print $out{ whisker }->{ http_resp };
22 Other modules Auth: basic, MD5, and NTLM authentication support routines BruteURL: brute forcing support HTML: HTML parsing routines Crawl: site/link crawling Encode: various encoding routines (hex, Unicode, etc) DAV: WebDAV request wrappers FrontPage: MS FrontPage client emulation IDS: anti-ids routines (6 new methods for a total of 15 anti-ids tactics)
23 Sounds good, when can I play? Today! The preview release of whisker 2.0 (whisker pr2) can be downloaded from: The preview release is meant to introduce the concept of libwhisker, and hopefully solicit developers willing to work on and contribute to the project further. Not all modules and/or functionality will be in the preview release.
24 How about a demonstration of libwhisker? I suppose I could, but demonstrating an API can be quite boring (particularly to non-coders). The preview release does not include any demonstration scripts it is just the API. So for the non-coders in the crowd, you may feel left out. However, I don t want anyone to feel left out, so.
25 Let s play: using RFProxy
26 First off, what is RFProxy? RFProxy is a web assessment tool to be used by an individual to help identify and exploit vulnerabilities in online applications. It accomplishes this task by acting as an HTTP proxy, essentially extending the features of the user s normal browser to be more suited for security testing.
27 RFProxy vs. other tools There are other proxy-based tools currently available to help assess web applications (in particular, Sanctium s AppScan) AppScan passively monitors passing HTTP traffic, looking for vulnerabilies RFProxy, on the other hand, actively interacts with the HTTP traffic (e.g. rewriting the HTML)
28 What can RFProxy do? Hidden form fields become visible (and editable) Radio, checkbox, and select fields can have arbitrary values Maxlength limitations are removed Javascript value checking is removed Arbitrary headers can be added, deleted, or modified (such as Referer) Cookies can be added, deleted or modified Requests can be captured, modified, and replayed Plus tons of support tools are available via web interface
29 RFProxy uses Testing dependencies on client-imposed limitations (such as form field values and Javascript checks) Evaluating state tracking and authentication mechanisms Looking for potential ways to perform abusive or fraudulent online transactions
30 Eyecandy: RFProxy demo
31 RFProxy development RFProxy will eventually be built on libwhisker More passive-monitoring intelligence is planned for future releases RFProxy will take advantage of the same pool of resources as libwhisker
32 Questions
33 Thanks Rain Forest Puppy
Assessing the web: finally tools that don t suck
 Assessing the web: finally tools that don t suck Whisker 1.4 is getting quite old and outdated Last year @ CanSecWest I discussed the limitations of CGI scanning, and introduced RFProxy There weren t many
Assessing the web: finally tools that don t suck Whisker 1.4 is getting quite old and outdated Last year @ CanSecWest I discussed the limitations of CGI scanning, and introduced RFProxy There weren t many
IronWASP (Iron Web application Advanced Security testing Platform)
 IronWASP (Iron Web application Advanced Security testing Platform) 1. Introduction: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability
IronWASP (Iron Web application Advanced Security testing Platform) 1. Introduction: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability
GOING WHERE NO WAFS HAVE GONE BEFORE
 GOING WHERE NO WAFS HAVE GONE BEFORE Andy Prow Aura Information Security Sam Pickles Senior Systems Engineer, F5 Networks NZ Agenda: WTF is a WAF? View from the Trenches Example Attacks and Mitigation
GOING WHERE NO WAFS HAVE GONE BEFORE Andy Prow Aura Information Security Sam Pickles Senior Systems Engineer, F5 Networks NZ Agenda: WTF is a WAF? View from the Trenches Example Attacks and Mitigation
RKN 2015 Application Layer Short Summary
 RKN 2015 Application Layer Short Summary HTTP standard version now: 1.1 (former 1.0 HTTP /2.0 in draft form, already used HTTP Requests Headers and body counterpart: answer Safe methods (requests): GET,
RKN 2015 Application Layer Short Summary HTTP standard version now: 1.1 (former 1.0 HTTP /2.0 in draft form, already used HTTP Requests Headers and body counterpart: answer Safe methods (requests): GET,
OWASP TOP Release. Andy Willingham June 12, 2018 OWASP Cincinnati
 OWASP TOP 10 2017 Release Andy Willingham June 12, 2018 OWASP Cincinnati Agenda A quick history lesson The Top 10(s) Web Mobile Privacy Protective Controls Why have a Top 10? Software runs the world (infrastructure,
OWASP TOP 10 2017 Release Andy Willingham June 12, 2018 OWASP Cincinnati Agenda A quick history lesson The Top 10(s) Web Mobile Privacy Protective Controls Why have a Top 10? Software runs the world (infrastructure,
Manipulating Web Application Interfaces a New Approach to Input Validation Testing. AppSec DC Nov 13, The OWASP Foundation
 Manipulating Web Application Interfaces a New Approach to Input Validation Testing Felipe Moreno-Strauch AppSec DC Nov 13, 2009 felipe@wobot.org http://groundspeed.wobot.org The Foundation http://www.owasp.org
Manipulating Web Application Interfaces a New Approach to Input Validation Testing Felipe Moreno-Strauch AppSec DC Nov 13, 2009 felipe@wobot.org http://groundspeed.wobot.org The Foundation http://www.owasp.org
java -jar Xmx2048mb /Applications/burpsuite_pro_v1.5.jar
 Training: An Introduction to Burp Suite Part One By Mike Sheward Burp suite provides a solid platform for launching a web application security assessment. In this guide we re going to introduce the features
Training: An Introduction to Burp Suite Part One By Mike Sheward Burp suite provides a solid platform for launching a web application security assessment. In this guide we re going to introduce the features
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
hack 2002 rain forest puppy / wiretrip / rfp.labs
 hack 2002 rain forest puppy / wiretrip / rfp.labs rfp@wiretrip.net Security is a war as well as an art form: you need to be methodical and militant, but also creative and flexible. - ancient rfp.labs
hack 2002 rain forest puppy / wiretrip / rfp.labs rfp@wiretrip.net Security is a war as well as an art form: you need to be methodical and militant, but also creative and flexible. - ancient rfp.labs
Lecture 9a: Sessions and Cookies
 CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
Solutions Business Manager Web Application Security Assessment
 White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
Certified Network Security Open Source Software Developer VS-1145
 Certified Network Security Open Source Software Developer VS-1145 www.vskills.in Certified Network Security Open Source Software Developer Certified Network Security Open Source Software Developer Certification
Certified Network Security Open Source Software Developer VS-1145 www.vskills.in Certified Network Security Open Source Software Developer Certified Network Security Open Source Software Developer Certification
CNIT 129S: Securing Web Applications. Ch 3: Web Application Technologies
 CNIT 129S: Securing Web Applications Ch 3: Web Application Technologies HTTP Hypertext Transfer Protocol (HTTP) Connectionless protocol Client sends an HTTP request to a Web server Gets an HTTP response
CNIT 129S: Securing Web Applications Ch 3: Web Application Technologies HTTP Hypertext Transfer Protocol (HTTP) Connectionless protocol Client sends an HTTP request to a Web server Gets an HTTP response
INNOV-09 How to Keep Hackers Out of your Web Application
 INNOV-09 How to Keep Hackers Out of your Web Application Michael Solomon, CISSP PMP CISM Solomon Consulting Inc. www.solomonconsulting.com What is a Web Application? Any access to your data via the Internet
INNOV-09 How to Keep Hackers Out of your Web Application Michael Solomon, CISSP PMP CISM Solomon Consulting Inc. www.solomonconsulting.com What is a Web Application? Any access to your data via the Internet
Object Visibility: Making the Necessary Connections
 Object Visibility: Making the Necessary Connections Reprinted from the October 1991 issue of The Smalltalk Report Vol. 2, No. 2 By: Rebecca J. Wirfs-Brock An exploratory design is by no means complete.
Object Visibility: Making the Necessary Connections Reprinted from the October 1991 issue of The Smalltalk Report Vol. 2, No. 2 By: Rebecca J. Wirfs-Brock An exploratory design is by no means complete.
How to perform the DDoS Testing of Web Applications
 How to perform the DDoS Testing of Web Applications Peerlyst November 02, 2017 Nasrumminallah Zeeshan (zeeshan@nzwriter.com) A Denial of Service (DoS) attack is consisted of carrying out traffic flooding
How to perform the DDoS Testing of Web Applications Peerlyst November 02, 2017 Nasrumminallah Zeeshan (zeeshan@nzwriter.com) A Denial of Service (DoS) attack is consisted of carrying out traffic flooding
Thinking about the concept
 Agenda Thinking about the concept Introduction Types of defensive technology Raising the bar Typical assessment methodology Attacks Conclusion Thinking about the concept We re from South Africa: Robbery
Agenda Thinking about the concept Introduction Types of defensive technology Raising the bar Typical assessment methodology Attacks Conclusion Thinking about the concept We re from South Africa: Robbery
Presented By Rick Deacon DEFCON 15 August 3-5, 2007
 Hacking Social Lives: MySpace.com Presented By Rick Deacon DEFCON 15 August 3-5, 2007 A Quick Introduction Full-time IT Specialist at a CPA firm located in Beachwood, OH. Part-time Student at Lorain County
Hacking Social Lives: MySpace.com Presented By Rick Deacon DEFCON 15 August 3-5, 2007 A Quick Introduction Full-time IT Specialist at a CPA firm located in Beachwood, OH. Part-time Student at Lorain County
The goal of this book is to teach you how to use Adobe Integrated
 Clearing the AIR The goal of this book is to teach you how to use Adobe Integrated Runtime (AIR) to create desktop applications. You can use JavaScript or ActionScript to develop AIR applications, and
Clearing the AIR The goal of this book is to teach you how to use Adobe Integrated Runtime (AIR) to create desktop applications. You can use JavaScript or ActionScript to develop AIR applications, and
HTTP Reading: Section and COS 461: Computer Networks Spring 2013
 HTTP Reading: Section 9.1.2 and 9.4.3 COS 461: Computer Networks Spring 2013 1 Recap: Client-Server Communication Client sometimes on Initiates a request to the server when interested E.g., Web browser
HTTP Reading: Section 9.1.2 and 9.4.3 COS 461: Computer Networks Spring 2013 1 Recap: Client-Server Communication Client sometimes on Initiates a request to the server when interested E.g., Web browser
Thinking about the concept
 Agenda Thinking about the concept Introduction Types of defensive technology Raising the bar Typical assessment methodology Attacks Examples Conclusion Thinking about the concept We re from South Africa:
Agenda Thinking about the concept Introduction Types of defensive technology Raising the bar Typical assessment methodology Attacks Examples Conclusion Thinking about the concept We re from South Africa:
Enabling Performance & Stress Test throughout the Application Lifecycle
 Enabling Performance & Stress Test throughout the Application Lifecycle March 2010 Poor application performance costs companies millions of dollars and their reputation every year. The simple challenge
Enabling Performance & Stress Test throughout the Application Lifecycle March 2010 Poor application performance costs companies millions of dollars and their reputation every year. The simple challenge
Web insecurity Security strategies General security Listing of server-side risks Language specific security. Web Security.
 Web Security Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming Web Security Slide 1/25 Outline Web insecurity Security strategies General security Listing of server-side risks Language
Web Security Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming Web Security Slide 1/25 Outline Web insecurity Security strategies General security Listing of server-side risks Language
Application Security through a Hacker s Eyes James Walden Northern Kentucky University
 Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
OWASP TOP 10. By: Ilia
 OWASP TOP 10 By: Ilia Alshanetsky @iliaa ME, MYSELF & I PHP Core Developer Author of Guide to PHP Security Security Aficionado WEB SECURITY THE CONUNDRUM USABILITY SECURITY YOU CAN HAVE ONE ;-) OPEN WEB
OWASP TOP 10 By: Ilia Alshanetsky @iliaa ME, MYSELF & I PHP Core Developer Author of Guide to PHP Security Security Aficionado WEB SECURITY THE CONUNDRUM USABILITY SECURITY YOU CAN HAVE ONE ;-) OPEN WEB
Developing a Network:
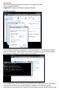 Developing a Network: This is setting up IP addresses in properties in Local Area Connection in the Network and Sharing Centre in Control Panel. I deselected all of the networks checkboxes accept the TCP/IP4
Developing a Network: This is setting up IP addresses in properties in Local Area Connection in the Network and Sharing Centre in Control Panel. I deselected all of the networks checkboxes accept the TCP/IP4
Base64 The Security Killer
 Base64 The Security Killer Kevin Fiscus NWN Corporation Session ID: DAS-203 Session Classification: Intermediate A Short (Made Up) Security Story Helix Pharmaceuticals is concerned about security Industrial
Base64 The Security Killer Kevin Fiscus NWN Corporation Session ID: DAS-203 Session Classification: Intermediate A Short (Made Up) Security Story Helix Pharmaceuticals is concerned about security Industrial
Design for Testability of Web Applications Manager s Perspective
 Design for Testability of Web Applications Manager s Perspective Raghav S. Nandyal Chief Executive Officer SITARA Technologies Pvt. Ltd. 3-6-460 Gokul Kunj, #304 Street No. 5 Himayatnagar Hyderabad AP
Design for Testability of Web Applications Manager s Perspective Raghav S. Nandyal Chief Executive Officer SITARA Technologies Pvt. Ltd. 3-6-460 Gokul Kunj, #304 Street No. 5 Himayatnagar Hyderabad AP
Human vs Artificial intelligence Battle of Trust
 Human vs Artificial intelligence Battle of Trust Hemil Shah Co-CEO & Director Blueinfy Solutions Pvt Ltd About Hemil Shah hemil@blueinjfy.net Position -, Co-CEO & Director at BlueInfy Solutions, - Founder
Human vs Artificial intelligence Battle of Trust Hemil Shah Co-CEO & Director Blueinfy Solutions Pvt Ltd About Hemil Shah hemil@blueinjfy.net Position -, Co-CEO & Director at BlueInfy Solutions, - Founder
Device Fingerprinting
 Device Fingerprinting Report 1 Contents 1 Project and Functional Aspects... 2 1.1 Overview... 2 1.2 Assessment... 2 2 Technical Aspects... 4 2.1 Exploits... 4 2.2 Implementations... 6 2.2.1 Fingerprinting
Device Fingerprinting Report 1 Contents 1 Project and Functional Aspects... 2 1.1 Overview... 2 1.2 Assessment... 2 2 Technical Aspects... 4 2.1 Exploits... 4 2.2 Implementations... 6 2.2.1 Fingerprinting
Screw You and the Script You Rode in On
 Screw You and the Script You Rode in On David Byrne Managing Consultant dbyrne@trustwave.com Presented by: Charles Henderson Director, Application Security Services chenderson@trustwave.com Introductions
Screw You and the Script You Rode in On David Byrne Managing Consultant dbyrne@trustwave.com Presented by: Charles Henderson Director, Application Security Services chenderson@trustwave.com Introductions
Testing Exploit-Prevention Mechanisms in Anti-Malware Products
 Testing Exploit-Prevention Mechanisms in Anti-Malware Products Andreas Marx & Maik Morgenstern AV-Test GmbH, Magdeburg, Germany http://www.av-test.org Presented at the CARO Workshop 2009 in Budapest, Hungary
Testing Exploit-Prevention Mechanisms in Anti-Malware Products Andreas Marx & Maik Morgenstern AV-Test GmbH, Magdeburg, Germany http://www.av-test.org Presented at the CARO Workshop 2009 in Budapest, Hungary
Web Application Attacks
 Web Application Attacks What can an attacker do and just how hard is it? By Damon P. Cortesi IOActive, Inc. Comprehensive Computer Security Services www.ioactive.com cortesi:~
Web Application Attacks What can an attacker do and just how hard is it? By Damon P. Cortesi IOActive, Inc. Comprehensive Computer Security Services www.ioactive.com cortesi:~
Rain forest puppy. Hack/03 - Australia
 Rain forest puppy Hack/03 - Australia RFP s collection of random misconceptions Misconception: The annual pen-test is sufficient Difference between a pen-test and an assessment What can the hackers do
Rain forest puppy Hack/03 - Australia RFP s collection of random misconceptions Misconception: The annual pen-test is sufficient Difference between a pen-test and an assessment What can the hackers do
BIG-IP Application Security Manager : Getting Started. Version 12.1
 BIG-IP Application Security Manager : Getting Started Version 12.1 Table of Contents Table of Contents Introduction to Application Security Manager...5 What is Application Security Manager?...5 When to
BIG-IP Application Security Manager : Getting Started Version 12.1 Table of Contents Table of Contents Introduction to Application Security Manager...5 What is Application Security Manager?...5 When to
WHY CSRF WORKS. Implicit authentication by Web browsers
 WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
Surveyor Getting Started Guide
 Surveyor Getting Started Guide This Getting Started Guide shows you how you can get the most out of Surveyor from start to finish. Surveyor can accomplish a number of tasks that will be extremely beneficial
Surveyor Getting Started Guide This Getting Started Guide shows you how you can get the most out of Surveyor from start to finish. Surveyor can accomplish a number of tasks that will be extremely beneficial
Web Application Firewall Subscription on Cyberoam UTM appliances
 On-Appliance Reporting Web Application Firewall Subscription on Cyberoam UTM appliances Protecting Web Applications from hackers Application Visibility and Control Bandwidth Management Firewall Web Application
On-Appliance Reporting Web Application Firewall Subscription on Cyberoam UTM appliances Protecting Web Applications from hackers Application Visibility and Control Bandwidth Management Firewall Web Application
State of jquery Fall John Resig
 State of jquery Fall 2010 John Resig State of the Project New Releases jquery 1.4.3 / jquery 1.4.4 Official Plugins: jquery Templating jquery Data Linking jquery Mobile jquery 1.4.3 JSLint Modularity
State of jquery Fall 2010 John Resig State of the Project New Releases jquery 1.4.3 / jquery 1.4.4 Official Plugins: jquery Templating jquery Data Linking jquery Mobile jquery 1.4.3 JSLint Modularity
Develop Mobile Front Ends Using Mobile Application Framework A - 2
 Develop Mobile Front Ends Using Mobile Application Framework A - 2 Develop Mobile Front Ends Using Mobile Application Framework A - 3 Develop Mobile Front Ends Using Mobile Application Framework A - 4
Develop Mobile Front Ends Using Mobile Application Framework A - 2 Develop Mobile Front Ends Using Mobile Application Framework A - 3 Develop Mobile Front Ends Using Mobile Application Framework A - 4
Application Layer Attacks. Application Layer Attacks. Application Layer. Application Layer. Internet Protocols. Application Layer.
 Application Layer Attacks Application Layer Attacks Week 2 Part 2 Attacks Against Programs Application Layer Application Layer Attacks come in many forms and can target each of the 5 network protocol layers
Application Layer Attacks Application Layer Attacks Week 2 Part 2 Attacks Against Programs Application Layer Application Layer Attacks come in many forms and can target each of the 5 network protocol layers
Web Security. Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le
 Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Attacking CAPTCHAs for Fun and Profit
 Attacking Author: Gursev Singh Kalra Managing Consultant Foundstone Professional Services Table of Contents Attacking... 1 Table of Contents... 2 Introduction... 3 A Strong CAPTCHA Implementation... 3
Attacking Author: Gursev Singh Kalra Managing Consultant Foundstone Professional Services Table of Contents Attacking... 1 Table of Contents... 2 Introduction... 3 A Strong CAPTCHA Implementation... 3
Ethical Hacking and Countermeasures: Web Applications, Second Edition. Chapter 3 Web Application Vulnerabilities
 Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
A framework to 0wn the Web - part I -
 A framework to 0wn the Web - part I - Andrés Riancho andres@bonsai-sec.com SecTor Toronto, Canada - 2009 Copyright 2008 CYBSEC. All rights reserved. andres@bonsai-sec:~$ whoami Web Application Security
A framework to 0wn the Web - part I - Andrés Riancho andres@bonsai-sec.com SecTor Toronto, Canada - 2009 Copyright 2008 CYBSEC. All rights reserved. andres@bonsai-sec:~$ whoami Web Application Security
WEB SECURITY WORKSHOP TEXSAW Presented by Solomon Boyd and Jiayang Wang
 WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
ReST 2000 Roy Fielding W3C
 Outline What is ReST? Constraints in ReST REST Architecture Components Features of ReST applications Example of requests in REST & SOAP Complex REST request REST Server response Real REST examples REST
Outline What is ReST? Constraints in ReST REST Architecture Components Features of ReST applications Example of requests in REST & SOAP Complex REST request REST Server response Real REST examples REST
Cookie Security. Myths and Misconceptions. David Johansson OWASP London 30 Nov. 2017
 Cookie Security Myths and Misconceptions David Johansson OWASP London 30 Nov. 2017 About Me David Johansson (@securitybits) Security consultant with 10 years in AppSec Helping clients design and build
Cookie Security Myths and Misconceptions David Johansson OWASP London 30 Nov. 2017 About Me David Johansson (@securitybits) Security consultant with 10 years in AppSec Helping clients design and build
Security Solution. Web Application
 Web Application Security Solution Netsparker is a web application security solution that can be deployed on premise, on demand or a combination of both. Unlike other web application security scanners,
Web Application Security Solution Netsparker is a web application security solution that can be deployed on premise, on demand or a combination of both. Unlike other web application security scanners,
HTTP/2: What You Need to Know. Robert
 HTTP/2: What You Need to Know Robert Boedigheimer @boedie About Me Web developer since 1995 Pluralsight Author 3 rd Degree Black Belt, Tae Kwon Do ASP.NET MVP boedie@outlook.com @boedie weblogs.asp.net/boedie
HTTP/2: What You Need to Know Robert Boedigheimer @boedie About Me Web developer since 1995 Pluralsight Author 3 rd Degree Black Belt, Tae Kwon Do ASP.NET MVP boedie@outlook.com @boedie weblogs.asp.net/boedie
Executive Summary. Flex Bounty Program Overview. Bugcrowd Inc Page 2 of 7
 CANVAS by Instructure Bugcrowd Flex Program Results December 01 Executive Summary Bugcrowd Inc was engaged by Instructure to perform a Flex Bounty program, commonly known as a crowdsourced penetration
CANVAS by Instructure Bugcrowd Flex Program Results December 01 Executive Summary Bugcrowd Inc was engaged by Instructure to perform a Flex Bounty program, commonly known as a crowdsourced penetration
Technical Report. Improving GeoServer Security. Ing. Andrea Aime Ing. Simone Giannecchini GeoSolutions S.A.S. 20/12/2010 Version 01.
 Technical Report 2010 Improving GeoServer Ing. Andrea Aime Ing. Simone Giannecchini. 20/12/2010 Version 01.00 Contents Record of Changes... 4 Securing GeoServer... 5 Introduction... 5 The external proxy
Technical Report 2010 Improving GeoServer Ing. Andrea Aime Ing. Simone Giannecchini. 20/12/2010 Version 01.00 Contents Record of Changes... 4 Securing GeoServer... 5 Introduction... 5 The external proxy
OWASP Thailand. Proxy Caches and Web Application Security. OWASP AppSec Asia October 21, Using the Recent Google Docs 0-Day as an Example
 Proxy Caches and Web Application Security Using the Recent Google Docs 0-Day as an Example Tim Bass, CISSP Chapter Leader, Thailand +66832975101, tim@unix.com AppSec Asia October 21, 2008 Thailand Worldwide
Proxy Caches and Web Application Security Using the Recent Google Docs 0-Day as an Example Tim Bass, CISSP Chapter Leader, Thailand +66832975101, tim@unix.com AppSec Asia October 21, 2008 Thailand Worldwide
Penetration Testing. James Walden Northern Kentucky University
 Penetration Testing James Walden Northern Kentucky University Topics 1. What is Penetration Testing? 2. Rules of Engagement 3. Penetration Testing Process 4. Map the Application 5. Analyze the Application
Penetration Testing James Walden Northern Kentucky University Topics 1. What is Penetration Testing? 2. Rules of Engagement 3. Penetration Testing Process 4. Map the Application 5. Analyze the Application
Hypertext Transport Protocol HTTP/1.1
 Hypertext Transport Protocol HTTP/1.1 Jim Gettys Digital Equipment Corporation, ISBU Visiting Scientist, World Wide Web Consortium 10/17/96 20-Apr-01 1 Acknowledgments HTTP/1.1 Authors Roy Fielding (UCI)
Hypertext Transport Protocol HTTP/1.1 Jim Gettys Digital Equipment Corporation, ISBU Visiting Scientist, World Wide Web Consortium 10/17/96 20-Apr-01 1 Acknowledgments HTTP/1.1 Authors Roy Fielding (UCI)
WEB APPLICATION SCANNERS. Evaluating Past the Base Case
 WEB APPLICATION SCANNERS Evaluating Past the Base Case GREG OSE PATRICK TOOMEY Presenter Intros Overview An overview of web application scanners Why is it hard to evaluate scanner efficacy? Prior Work
WEB APPLICATION SCANNERS Evaluating Past the Base Case GREG OSE PATRICK TOOMEY Presenter Intros Overview An overview of web application scanners Why is it hard to evaluate scanner efficacy? Prior Work
Man-In-The-Browser Attacks. Daniel Tomescu
 Man-In-The-Browser Attacks Daniel Tomescu 1 About me Work and education: Pentester @ KPMG Romania Moderator @ Romanian Security Team MSc. Eng. @ University Politehnica of Bucharest OSCP, CREST CRT Interests:
Man-In-The-Browser Attacks Daniel Tomescu 1 About me Work and education: Pentester @ KPMG Romania Moderator @ Romanian Security Team MSc. Eng. @ University Politehnica of Bucharest OSCP, CREST CRT Interests:
Web Application Penetration Testing
 Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
Kishin Fatnani. Founder & Director K-Secure. Workshop : Application Security: Latest Trends by Cert-In, 30 th Jan, 2009
 Securing Web Applications: Defense Mechanisms Kishin Fatnani Founder & Director K-Secure Workshop : Application Security: Latest Trends by Cert-In, 30 th Jan, 2009 1 Agenda Current scenario in Web Application
Securing Web Applications: Defense Mechanisms Kishin Fatnani Founder & Director K-Secure Workshop : Application Security: Latest Trends by Cert-In, 30 th Jan, 2009 1 Agenda Current scenario in Web Application
CERN Web Application Detection
 CERN Web Application Detection Refactoring and release as open source software by Piotr Lizończyk Supervised by Sebastian Łopieński and Dr. Stefan Lüders Summer Students Programme 2015 Geneva, 28. August
CERN Web Application Detection Refactoring and release as open source software by Piotr Lizończyk Supervised by Sebastian Łopieński and Dr. Stefan Lüders Summer Students Programme 2015 Geneva, 28. August
CS 161 Computer Security
 Paxson Spring 2017 CS 161 Computer Security Discussion 12 Week of April 24, 2017 Question 1 Detection strategies (20 min) Suppose you are responsible for detecting attacks on the UC Berkeley network, and
Paxson Spring 2017 CS 161 Computer Security Discussion 12 Week of April 24, 2017 Question 1 Detection strategies (20 min) Suppose you are responsible for detecting attacks on the UC Berkeley network, and
N different strategies to automate OWASP ZAP
 OWASP BUCHAREST APPSEC CONFERENCE 13 OCTOBER 2017 The OWASP Foundation http://www.owasp.org N different strategies to automate OWASP ZAP The OWASP Zed Attack Proxy Marudhamaran Gunasekaran Zap Contributor
OWASP BUCHAREST APPSEC CONFERENCE 13 OCTOBER 2017 The OWASP Foundation http://www.owasp.org N different strategies to automate OWASP ZAP The OWASP Zed Attack Proxy Marudhamaran Gunasekaran Zap Contributor
5/10/2009. Introduction. The light-saber is a Jedi s weapon not as clumsy or random as a blaster.
 The Hacking Protocols and The Hackers Sword The light-saber is a Jedi s weapon not as clumsy or random as a blaster. Obi-Wan Kenobi, Star Wars: Episode IV Slide 2 Introduction Why are firewalls basically
The Hacking Protocols and The Hackers Sword The light-saber is a Jedi s weapon not as clumsy or random as a blaster. Obi-Wan Kenobi, Star Wars: Episode IV Slide 2 Introduction Why are firewalls basically
Developer Resources: PIN2
 Administrative Technology Services Technology and Data Services Developer Resources: PIN2 Contents Introduction... 2 Registering an Application... 2 Information Required for Registration... 3 Information
Administrative Technology Services Technology and Data Services Developer Resources: PIN2 Contents Introduction... 2 Registering an Application... 2 Information Required for Registration... 3 Information
AppGate 11.0 RELEASE NOTES
 Changes in 11.0 AppGate 11.0 RELEASE NOTES 1. New packet filter engine. The server-side IP tunneling packet filter engine has been rewritten from scratch, reducing memory usage drastically and improving
Changes in 11.0 AppGate 11.0 RELEASE NOTES 1. New packet filter engine. The server-side IP tunneling packet filter engine has been rewritten from scratch, reducing memory usage drastically and improving
CONTENTS IN DETAIL. FOREWORD by HD Moore ACKNOWLEDGMENTS INTRODUCTION 1 THE ABSOLUTE BASICS OF PENETRATION TESTING 1 2 METASPLOIT BASICS 7
 CONTENTS IN DETAIL FOREWORD by HD Moore xiii PREFACE xvii ACKNOWLEDGMENTS xix Special Thanks... xx INTRODUCTION xxi Why Do A Penetration Test?... xxii Why Metasploit?... xxii A Brief History of Metasploit...
CONTENTS IN DETAIL FOREWORD by HD Moore xiii PREFACE xvii ACKNOWLEDGMENTS xix Special Thanks... xx INTRODUCTION xxi Why Do A Penetration Test?... xxii Why Metasploit?... xxii A Brief History of Metasploit...
Adon'tbe an Adobe victim
 Adon'tbe an Adobe victim An overview of how recent Adobe-related flaws affect your web application Joshua Stabiner EY Agenda Introductions Background Cross-site scripting (PDF) Overview Exploit Mitigation
Adon'tbe an Adobe victim An overview of how recent Adobe-related flaws affect your web application Joshua Stabiner EY Agenda Introductions Background Cross-site scripting (PDF) Overview Exploit Mitigation
3D on the Web Why We Need Declarative 3D Arguments for an W3C Incubator Group
 3D on the Web Why We Need Declarative 3D Arguments for an W3C Incubator Group Philipp Slusallek Johannes Behr Kristian Sons German Research Center for Artificial Intelligence (DFKI) Intel Visual Computing
3D on the Web Why We Need Declarative 3D Arguments for an W3C Incubator Group Philipp Slusallek Johannes Behr Kristian Sons German Research Center for Artificial Intelligence (DFKI) Intel Visual Computing
Computer Networks. Wenzhong Li. Nanjing University
 Computer Networks Wenzhong Li Nanjing University 1 Chapter 8. Internet Applications Internet Applications Overview Domain Name Service (DNS) Electronic Mail File Transfer Protocol (FTP) WWW and HTTP Content
Computer Networks Wenzhong Li Nanjing University 1 Chapter 8. Internet Applications Internet Applications Overview Domain Name Service (DNS) Electronic Mail File Transfer Protocol (FTP) WWW and HTTP Content
Notes From The field
 Notes From The field tools and usage experiences Jarkko Holappa Antti Laulajainen Copyright The Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the License.
Notes From The field tools and usage experiences Jarkko Holappa Antti Laulajainen Copyright The Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the License.
Protocol Buffers, grpc
 Protocol Buffers, grpc Szolgáltatásorientált rendszerintegráció Service-Oriented System Integration Dr. Balázs Simon BME, IIT Outline Remote communication application level vs. transport level protocols
Protocol Buffers, grpc Szolgáltatásorientált rendszerintegráció Service-Oriented System Integration Dr. Balázs Simon BME, IIT Outline Remote communication application level vs. transport level protocols
RiskSense Attack Surface Validation for Web Applications
 RiskSense Attack Surface Validation for Web Applications 2018 RiskSense, Inc. Keeping Pace with Digital Business No Excuses for Not Finding Risk Exposure We needed a faster way of getting a risk assessment
RiskSense Attack Surface Validation for Web Applications 2018 RiskSense, Inc. Keeping Pace with Digital Business No Excuses for Not Finding Risk Exposure We needed a faster way of getting a risk assessment
Website Report for test.com
 NeatWidget contact@neatwidget.com.au neatwidget.com.au Website Report for test.com This report grades your website on the strength of a range of important factors such as on-page optimization, off-page
NeatWidget contact@neatwidget.com.au neatwidget.com.au Website Report for test.com This report grades your website on the strength of a range of important factors such as on-page optimization, off-page
Introduction to Ethical Hacking
 Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
Application Design and Development: October 30
 M149: Database Systems Winter 2018 Lecturer: Panagiotis Liakos Application Design and Development: October 30 1 Applications Programs and User Interfaces very few people use a query language to interact
M149: Database Systems Winter 2018 Lecturer: Panagiotis Liakos Application Design and Development: October 30 1 Applications Programs and User Interfaces very few people use a query language to interact
GEL Scripts Advanced. Your Guides: Ben Rimmasch, Yogesh Renapure
 GEL Scripts Advanced Your Guides: Ben Rimmasch, Yogesh Renapure Introductions 2 Take 5 Minutes Turn to a Person Near You Introduce Yourself Agenda 3 Accessing JAVA Classes and Methods SOAP Web Services
GEL Scripts Advanced Your Guides: Ben Rimmasch, Yogesh Renapure Introductions 2 Take 5 Minutes Turn to a Person Near You Introduce Yourself Agenda 3 Accessing JAVA Classes and Methods SOAP Web Services
Instructions 1 Elevation of Privilege Instructions
 Instructions 1 Elevation of Privilege Instructions Draw a diagram of the system you want to threat model before you deal the cards. Deal the deck to 3-6 players. Play starts with the 3 of Tampering. Play
Instructions 1 Elevation of Privilege Instructions Draw a diagram of the system you want to threat model before you deal the cards. Deal the deck to 3-6 players. Play starts with the 3 of Tampering. Play
Web Application Security
 Web Application Security Rajendra Kachhwaha rajendra1983@gmail.com October 16, 2015 Lecture 16: 1/ 14 Outline Browser Security Principles: 1 Cross Site Scripting (XSS) 2 Types of XSS 3 Lecture 16: 2/ 14
Web Application Security Rajendra Kachhwaha rajendra1983@gmail.com October 16, 2015 Lecture 16: 1/ 14 Outline Browser Security Principles: 1 Cross Site Scripting (XSS) 2 Types of XSS 3 Lecture 16: 2/ 14
Integrating Tools Into the SDLC
 Integrating Tools Into the SDLC SecAppDev 2007 The problem Too many organizations have either: Failed to try software security tools at all Tried tools, but became overwhelmed Tools relegated to shelfware
Integrating Tools Into the SDLC SecAppDev 2007 The problem Too many organizations have either: Failed to try software security tools at all Tried tools, but became overwhelmed Tools relegated to shelfware
How to Stay Safe on Public Wi-Fi Networks
 How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
SPOOFING. Information Security in Systems & Networks Public Development Program. Sanjay Goel University at Albany, SUNY Fall 2006
 SPOOFING Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Determine relevance of
SPOOFING Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Determine relevance of
Computer Networks. HTTP and more. Jianping Pan Spring /20/17 CSC361 1
 Computer Networks HTTP and more Jianping Pan Spring 2017 1/20/17 CSC361 1 First things first W1 due next Monday (Jan 23) submit a single PDF file through connex Noah posted a docx for for questions on
Computer Networks HTTP and more Jianping Pan Spring 2017 1/20/17 CSC361 1 First things first W1 due next Monday (Jan 23) submit a single PDF file through connex Noah posted a docx for for questions on
Lecture 7b: HTTP. Feb. 24, Internet and Intranet Protocols and Applications
 Internet and Intranet Protocols and Applications Lecture 7b: HTTP Feb. 24, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu WWW - HTTP/1.1 Web s application layer protocol
Internet and Intranet Protocols and Applications Lecture 7b: HTTP Feb. 24, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu WWW - HTTP/1.1 Web s application layer protocol
Risk Intelligence. Quick Start Guide - Data Breach Risk
 Risk Intelligence Quick Start Guide - Data Breach Risk Last Updated: 19 September 2018 --------------------------- 2018 CONTENTS Introduction 1 Data Breach Prevention Lifecycle 2 Choosing a Scan Deployment
Risk Intelligence Quick Start Guide - Data Breach Risk Last Updated: 19 September 2018 --------------------------- 2018 CONTENTS Introduction 1 Data Breach Prevention Lifecycle 2 Choosing a Scan Deployment
This is CS50. Harvard College Fall Quiz 1 Answer Key
 Quiz 1 Answer Key Answers other than the below may be possible. Know Your Meme. 0. True or False. 1. T 2. F 3. F 4. F 5. T Attack. 6. By never making assumptions as to the length of users input and always
Quiz 1 Answer Key Answers other than the below may be possible. Know Your Meme. 0. True or False. 1. T 2. F 3. F 4. F 5. T Attack. 6. By never making assumptions as to the length of users input and always
Building a Web-based Health Promotion Database
 6 th International Conference on Applied Informatics Eger, Hungary, January 27 31, 2004. Building a Web-based Health Promotion Database Ádám Rutkovszky University of Debrecen, Faculty of Economics Department
6 th International Conference on Applied Informatics Eger, Hungary, January 27 31, 2004. Building a Web-based Health Promotion Database Ádám Rutkovszky University of Debrecen, Faculty of Economics Department
Web Programming. Based on Notes by D. Hollinger Also Java Network Programming and Distributed Computing, Chs.. 9,10 Also Online Java Tutorial, Sun.
 Web Programming Based on Notes by D. Hollinger Also Java Network Programming and Distributed Computing, Chs.. 9,10 Also Online Java Tutorial, Sun. 1 World-Wide Wide Web (Tim Berners-Lee & Cailliau 92)
Web Programming Based on Notes by D. Hollinger Also Java Network Programming and Distributed Computing, Chs.. 9,10 Also Online Java Tutorial, Sun. 1 World-Wide Wide Web (Tim Berners-Lee & Cailliau 92)
Switch What s New in Switch New features. Fixes and improvements. Date: March 22, 2018 What s New In Switch 2018
 Date: March 22, 2018 What s New In Switch 2018 Enfocus BVBA Kortrijksesteenweg 1095 9051 Gent Belgium +32 (0)9 216 98 01 info@enfocus.com Switch 2018 What s New in Switch 2018. This document lists all
Date: March 22, 2018 What s New In Switch 2018 Enfocus BVBA Kortrijksesteenweg 1095 9051 Gent Belgium +32 (0)9 216 98 01 info@enfocus.com Switch 2018 What s New in Switch 2018. This document lists all
DenyAll Protect. accelerating. Web Application & Services Firewalls. your applications. DenyAll Protect
 DenyAll Protect DenyAll Protect Web Application & Services Firewalls Securing Sécuring & accelerating your applications Corporate or ecommerce website, email, collaborative tools, enterprise application
DenyAll Protect DenyAll Protect Web Application & Services Firewalls Securing Sécuring & accelerating your applications Corporate or ecommerce website, email, collaborative tools, enterprise application
Learning to Provide Modern Solutions
 1 Learning to Provide Modern Solutions Over the course of this book, you will learn to enhance your existing applications to modernize the output of the system. To do this, we ll take advantage of the
1 Learning to Provide Modern Solutions Over the course of this book, you will learn to enhance your existing applications to modernize the output of the system. To do this, we ll take advantage of the
Positive Security Model for Web Applications, Challenges. Ofer Shezaf OWASP IL Chapter leader CTO, Breach Security
 Positive Security Model for Web Applications, Challenges and Promise Ofer Shezaf OWASP IL Chapter leader CTO, Breach Security Introduction Breach Security, Inc. Breach Security is the market leader in
Positive Security Model for Web Applications, Challenges and Promise Ofer Shezaf OWASP IL Chapter leader CTO, Breach Security Introduction Breach Security, Inc. Breach Security is the market leader in
CYSE 411/AIT 681 Secure Software Engineering. Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun
 CYSE 411/AIT 681 Secure Software Engineering Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun Reading This lecture [McGraw]: Ch. 7-9 2 Seven Touchpoints 1. Code review 2. Architectural
CYSE 411/AIT 681 Secure Software Engineering Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun Reading This lecture [McGraw]: Ch. 7-9 2 Seven Touchpoints 1. Code review 2. Architectural
4. Risk-Based Security Testing. Reading. CYSE 411/AIT 681 Secure Software Engineering. Seven Touchpoints. Application of Touchpoints
 Reading This lecture [McGraw]: Ch. 7-9 CYSE 411/AIT 681 Secure Software Engineering Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun 2 Seven Touchpoints Application of Touchpoints
Reading This lecture [McGraw]: Ch. 7-9 CYSE 411/AIT 681 Secure Software Engineering Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun 2 Seven Touchpoints Application of Touchpoints
Session 8. Reading and Reference. en.wikipedia.org/wiki/list_of_http_headers. en.wikipedia.org/wiki/http_status_codes
 Session 8 Deployment Descriptor 1 Reading Reading and Reference en.wikipedia.org/wiki/http Reference http headers en.wikipedia.org/wiki/list_of_http_headers http status codes en.wikipedia.org/wiki/_status_codes
Session 8 Deployment Descriptor 1 Reading Reading and Reference en.wikipedia.org/wiki/http Reference http headers en.wikipedia.org/wiki/list_of_http_headers http status codes en.wikipedia.org/wiki/_status_codes
Life, the Universe, and CSS Tests XML Prague 2018
 It turns out that the answer to the ultimate question of life, the Universe, and CSS Tests isn t a number. It is, in fact, multiple numbers. It is the answers to: How many test results are correct? How
It turns out that the answer to the ultimate question of life, the Universe, and CSS Tests isn t a number. It is, in fact, multiple numbers. It is the answers to: How many test results are correct? How
Automatically Checking for Session Management Vulnerabilities in Web Applications
 Regular Paper Automatically Checking for Session Management Vulnerabilities in Web Applications Yusuke Takamatsu 1,a) Yuji Kosuga 2 Kenji Kono 1,3 Received: July 4, 2012, Accepted: October 17, 2012 Abstract:
Regular Paper Automatically Checking for Session Management Vulnerabilities in Web Applications Yusuke Takamatsu 1,a) Yuji Kosuga 2 Kenji Kono 1,3 Received: July 4, 2012, Accepted: October 17, 2012 Abstract:
Migration to Service Oriented Architecture Using Web Services Whitepaper
 WHITE PAPER Migration to Service Oriented Architecture Using Web Services Whitepaper Copyright 2004-2006, HCL Technologies Limited All Rights Reserved. cross platform GUI for web services Table of Contents
WHITE PAPER Migration to Service Oriented Architecture Using Web Services Whitepaper Copyright 2004-2006, HCL Technologies Limited All Rights Reserved. cross platform GUI for web services Table of Contents
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition. Chapter 3 Investigating Web Attacks
 Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
IoT in 2016: a serious overview of IoT today and a technical preview of HoneyVNC. By Yonathan Klijnsma
 IoT in 2016: a serious overview of IoT today and a technical preview of HoneyVNC By Yonathan Klijnsma Yonathan Klijnsma Senior Threat Intelligence Analyst Perform threat intelligence analysis at keeping
IoT in 2016: a serious overview of IoT today and a technical preview of HoneyVNC By Yonathan Klijnsma Yonathan Klijnsma Senior Threat Intelligence Analyst Perform threat intelligence analysis at keeping
