An Empirical Study of Vulnerability Rewards Programs
|
|
|
- Harvey Baker
- 5 years ago
- Views:
Transcription
1 An Empirical Study of Vulnerability Rewards Programs Matthew Finifter, Devdatta Akhawe, David Wagner UC Berkeley
2 security development lifecycle
3 A vulnerability remediation strategy is any systematic approach whose goal is to reduce the number of software vulnerabilities. CERT Incident Response Operational Security Defense in Depth Vulnerability Remediation Code Reviews Penetration Testing Dynamic/Static Analysis Tools Bug Bounties?
4
5 Copyright Adam Mein and Chris Evans, Google Inc.
6 There is an active debate over the value and effectiveness of VRPs. A number of vendors, notably Microsoft, Adobe, and Oracle, do not maintain a VRP, with Microsoft arguing that VRPs do not represent the best return on investment on a per-bug basis -- Our paper
7
8 There is an active debate over the value and effectiveness of VRPs. A number of vendors, notably Microsoft, Adobe, and Oracle, do not maintain a VRP, with Microsoft arguing that VRPs do not represent the best return on investment on a per-bug basis
9 Analysis of Chrome & Firefox VRPs From 2 viewpoints Software Vendor today Security Researchers Other analysis of the data Lots of hypotheses We can t do experiments!
10
11 Chrome VRP Firefox VRP Started in Jan 2010 Rewards ranging from $500 to $1337 Amounts increased over time to $1000--$ $31,336 for exceptional reports with patches Started in 1995 by Netscape Rewards increased to $3000 on July 1, 2010 All high/critical vulns get $3000!
12 data
13 Severity, reporter, report Bugs found date by VRP AND affecting stable releases For VRP bugs, Bugs reward amount (always $3K for Found Firefox) using the VRP For stable bugs, Bugs date a patched version available affecting to end-users stable releases
14 Severity An ordinal measure of badness of a security bug Arbitrary code execution with user s privilege on the OS considered critical severity by both browsers Chrome has a privilege separated design and a memory corruption vulnerability in the renderer process is only high severity (same origin bypass) Nearly all memory corruption vulnerabilities in Firefox are critical severity
15 Severity Chrome Stable Chrome Bounty Firefox Stable Firefox Bounty Low Medium High Critical Unknown Total
16 software vendor perspective
17 Finding Bugs
18 Bugs found 27.5% of bugs affecting Chrome releases originate from VRP contributions (371 of 1347), and 24.1% of bugs affecting Firefox releases (148 of 613) result from VRP contributions. Effective! Note that we are only looking at bugs affecting release versions! 140 high/crit Jan-May 13 in Chrome, only 40 found by VRP
19 Bugs found 27.5% of bugs affecting Chrome releases originate from VRP contributions (371 of 1347), and 24.1% of bugs affecting Firefox releases (148 of 613) result from VRP contributions. Effective!
20 Bugs found 27.5% of bugs affecting Chrome releases originate from VRP contributions (371 of 1347), and 24.1% of bugs affecting Firefox releases (148 of 613) result from VRP contributions. Effective! Total bugs found by Chrome VRP: 371 Max found by best internal researcher: found by Firefox VRP (vs 48 by best internal)
21 Bugs found 27.5% of bugs affecting Chrome releases originate from VRP contributions (371 of 1347), and 24.1% of bugs affecting Firefox releases (148 of 613) result from VRP contributions. Effective! But is it cost-effective?
22 Cost
23 Cost of VRP Roughly $400,000 over 3 years for bugs affecting stable releases Chrome Firefox
24 Cost of VRP Chrome Total Cost Stable Firefox Total Cost Stable pre-release pre-release
25 Cost of VRP Chrome total cost: $579,605 ($485/day) $186,839 (32%) for non-release bugs Firefox total cost: $570,000 ($658/day) $126,000 (22%) for non-release bugs Roughly, $190,000/year Comparable to total cost of ONE security engineer $100, % overhead = $500/day But is it cost-effective? YES
26 Community Engagement
27 Community Engagement Get more security bugs from the community
28 Community Engagement: Critical Bugs Chrome Increase in reward amounts Firefox internal (blue) vs external (red)
29 Community Engagement Get more security bugs from the community VRP found more critical bugs in Chrome (release) than Internal researchers For Firefox, internal researchers find the lion s share of critical vulnerabilities Although, VRP impact is improving
30 Given enough eyeballs, all bugs are shallow Linus Law
31 45/46 people only reported 1 high/critical bug
32 Maybe if we offer money?
33 Community Engagement Get more security bugs from the community Get more eyeballs on code Get more diverse bugs from the community Chrome awards amounts ending with 337 for particularly smart/novel vulnerabilities 31 such awards in our dataset Anecdotal evidence that it can lead to more bugs! PinkiePie s exploit => full review of kernel API a large number of similar issues found
34 software vendor perspective
35 From the Software Vendor s view Effective: ~25% of bugs affecting release Cost effective: comparable to ONE developer Community Engagement More bugs from community More eyeballs Diverse bugs leading to finding more issues
36 security researcher perspective
37 Reward Amount
38 Chrome Reward Amounts 95.8% of awards $3000 (Firefox)
39 Reward Amounts Vast majority of rewards for Chrome under $1000 (median: $1000, mean $1156.9) Firefox award is $3000 (high/critical) or $0 Lottery? Low (or possibly negative) expected return on investment of finding bugs But possibility of very large rewards!
40 Repeat Participation
41 First time vs. Repeat Contribution Chrome Firefox First-time (blue) vs repeat (red)
42 VRP as Employment
43 Total Income
44 VRP as Employment The very best earn at the most $47,000 per year Such a person likely to make much more working for Firefox and Chrome Both Google and Mozilla hired researchers found via VRPs Hypothesis: The best security researchers bubble to the top, where a full-time job awaits.
45 security researcher perspective
46 From the Researcher s view Participation in a single VRP program likely not comparable to full-time employment Although, good performance might lead to a job Multiple programs could provide significant income Repeat participation is increasing Suggests that researchers have a good experience with the programs Expected reward in Firefox higher than in Chrome Although, possibility of much higher payoff in Chrome
47 other analysis
48 Severity
49 Severity Chrome Stable Chrome Bounty Firefox Stable Firefox Bounty Low Medium High Critical Unknown Total
50 Fraction of Vulns by Severity High Critical High Critical Hypothesis: This difference is due to privilege separation
51 Time to Patch
52
53
54
55 Hypothesis: This difference is due to privilege separation
56 final thoughts
57
58 Firefox vs Chrome Despite costing roughly the same, the Chrome VRP Identified 3x bugs More popular Similar participation between repeat and firsttime External Researchers competitive with Internal researchers (for bugs in release versions) Why?
59 Possible Reasons Tiered Reward Structure Incentivizes participation, keeps cost low Low variance/mean time to patch Researchers like when bugs get patched quickly Higher Profile for Chrome Pwnium, a high profile event sudden top-ups for rewards Such gamification leads to more participation
60 Recommendations for Vendors VRPs seem cost-effective strategy Try to reduce time-to-patch Consider tiered incentives like Chrome Architecture can have massive impact See impact of privilege separation for Google Chrome
61 thanks Thanks to Dan Veditz and Chris Evans for all their help
Dosh4Vulns: Google's Vulnerability Reward Programs. Adam Mein Chris Evans
 Dosh4Vulns: Google's Vulnerability Reward Programs Adam Mein Chris Evans Who? Chris Evans, Google Engineer, researcher, troublemaker Leads Chrome Security Team Adam Mein, Google Program Manager, troublemaker
Dosh4Vulns: Google's Vulnerability Reward Programs Adam Mein Chris Evans Who? Chris Evans, Google Engineer, researcher, troublemaker Leads Chrome Security Team Adam Mein, Google Program Manager, troublemaker
AN EVALUATION OF THE GOOGLE CHROME EXTENSION SECURITY ARCHITECTURE
 AN EVALUATION OF THE GOOGLE CHROME EXTENSION SECURITY ARCHITECTURE Nicholas Carlini, Adrienne Porter Felt, David Wagner University of California, Berkeley CHROME EXTENSIONS CHROME EXTENSIONS servers servers
AN EVALUATION OF THE GOOGLE CHROME EXTENSION SECURITY ARCHITECTURE Nicholas Carlini, Adrienne Porter Felt, David Wagner University of California, Berkeley CHROME EXTENSIONS CHROME EXTENSIONS servers servers
Open Source Development
 Open Source Development Dr. James A. Bednar jbednar@inf.ed.ac.uk http://homepages.inf.ed.ac.uk/jbednar Dr. Chris Walton cdw@inf.ed.ac.uk http://homepages.inf.ed.ac.uk/cdw SEOC2 Spring 2005: Open Source
Open Source Development Dr. James A. Bednar jbednar@inf.ed.ac.uk http://homepages.inf.ed.ac.uk/jbednar Dr. Chris Walton cdw@inf.ed.ac.uk http://homepages.inf.ed.ac.uk/cdw SEOC2 Spring 2005: Open Source
BROWSER POLICY: DESCRIPTION OF SUPPORT 2 SUPPORTED BROWSERS 2 TIER 2 SUPPORTED BROWSERS 2 UNSUPPORTED BROWSERS 2
 Browser Policy June 2016 Table of Contents BROWSER POLICY: DESCRIPTION OF SUPPORT 2 SUPPORTED BROWSERS 2 TIER 1 SUPPORTED BROWSERS 2 TIER 2 SUPPORTED BROWSERS 2 UNSUPPORTED BROWSERS 2 SCOPE OF APPLICABILITY
Browser Policy June 2016 Table of Contents BROWSER POLICY: DESCRIPTION OF SUPPORT 2 SUPPORTED BROWSERS 2 TIER 1 SUPPORTED BROWSERS 2 TIER 2 SUPPORTED BROWSERS 2 UNSUPPORTED BROWSERS 2 SCOPE OF APPLICABILITY
Mapping Your Requirements to the NIST Cybersecurity Framework. Industry Perspective
 Mapping Your Requirements to the NIST Cybersecurity Framework Industry Perspective 1 Quest has the solutions and services to help your organization identify, protect, detect, respond and recover, better
Mapping Your Requirements to the NIST Cybersecurity Framework Industry Perspective 1 Quest has the solutions and services to help your organization identify, protect, detect, respond and recover, better
Let's cyber: hacking, 0days and vulnerability research. PATROKLOS ARGYROUDIS CENSUS S.A.
 Let's cyber: hacking, 0days and vulnerability research PATROKLOS ARGYROUDIS CENSUS S.A. argp@census-labs.com www.census-labs.com Who am I Researcher at CENSUS S.A. - Vulnerability research, reverse engineering,
Let's cyber: hacking, 0days and vulnerability research PATROKLOS ARGYROUDIS CENSUS S.A. argp@census-labs.com www.census-labs.com Who am I Researcher at CENSUS S.A. - Vulnerability research, reverse engineering,
Practical Patch Compliance
 Practical Patch Compliance Relieving IT Security Audit Pain, From the Data Center to the Desktop Microsoft s System Center Configuration Manager doesn t handle every aspect of Linux/UNIX and third-party
Practical Patch Compliance Relieving IT Security Audit Pain, From the Data Center to the Desktop Microsoft s System Center Configuration Manager doesn t handle every aspect of Linux/UNIX and third-party
Why Crowdsourced Security?
 Why Crowdsourced Security? Highlights There is a fundamental imbalance between the creativity and motivations of cyber attackers, and those of enterprise security defenders. rowdsourced Security is a powerful
Why Crowdsourced Security? Highlights There is a fundamental imbalance between the creativity and motivations of cyber attackers, and those of enterprise security defenders. rowdsourced Security is a powerful
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
Introduction into browser hacking. Andrey Kovalev
 Introduction into browser hacking Andrey Kovalev (@L1kvID) Who am I Security Engineer at Yandex Browser security enthusiast Public speaker (every ZeroNights since 2015) Author of @br0wsec channel (https://t.me/br0wsec)!3
Introduction into browser hacking Andrey Kovalev (@L1kvID) Who am I Security Engineer at Yandex Browser security enthusiast Public speaker (every ZeroNights since 2015) Author of @br0wsec channel (https://t.me/br0wsec)!3
Apr. 10, Vulnerability disclosure and handling processes strengthen security programs
 Joint Comments on "Framework for Improving Critical Infrastructure Cybersecurity" version 1.1 Before the National Institute of Standards and Technology Apr. 10, 2017 We the undersigned companies, civil
Joint Comments on "Framework for Improving Critical Infrastructure Cybersecurity" version 1.1 Before the National Institute of Standards and Technology Apr. 10, 2017 We the undersigned companies, civil
Vulnerability Assessments and Penetration Testing
 CYBERSECURITY Vulnerability Assessments and Penetration Testing A guide to understanding vulnerability assessments and penetration tests. OVERVIEW When organizations begin developing a strategy to analyze
CYBERSECURITY Vulnerability Assessments and Penetration Testing A guide to understanding vulnerability assessments and penetration tests. OVERVIEW When organizations begin developing a strategy to analyze
Secure Coding Techniques
 Secure Coding Techniques "... the world outside your function should be treated as hostile and bent upon your destruction" [Writing Secure Code, Howard and LeBlanc] "Distrust and caution are the parents
Secure Coding Techniques "... the world outside your function should be treated as hostile and bent upon your destruction" [Writing Secure Code, Howard and LeBlanc] "Distrust and caution are the parents
The Cost of Going it Alone Dave Neary
 The Cost of Going it Alone Dave Neary dneary@gnome.org Photo by jucanils@flickr CC by-sa Also: The Cost of Collaboration Act I: Softway 1996-97 OpenNT/Interix: POSIX for NT GCC suite work: - 6-8 man-months
The Cost of Going it Alone Dave Neary dneary@gnome.org Photo by jucanils@flickr CC by-sa Also: The Cost of Collaboration Act I: Softway 1996-97 OpenNT/Interix: POSIX for NT GCC suite work: - 6-8 man-months
The Laws of Vulnerabilities: Patching Progress and how to Expedite It
 The Laws of Vulnerabilities: Patching Progress and how to Expedite It By: Jason Falciola, GCIH, GAWN Technical Account Manager, Northeast IT Roadmap Boston, MA May 25, 2010 Qualys, Inc. www.qualys.com
The Laws of Vulnerabilities: Patching Progress and how to Expedite It By: Jason Falciola, GCIH, GAWN Technical Account Manager, Northeast IT Roadmap Boston, MA May 25, 2010 Qualys, Inc. www.qualys.com
Looking at the big picture on. vulnerabilities. Network Resonance, Inc. Eric Rescorla
 Looking at the big picture on vulnerabilities Eric Rescorla Network Resonance, Inc. The big picture! All software has bugs! Security relevant software has security bugs! Security is a problem in any multi-user
Looking at the big picture on vulnerabilities Eric Rescorla Network Resonance, Inc. The big picture! All software has bugs! Security relevant software has security bugs! Security is a problem in any multi-user
How do you track devices that have been approved for use? Are you automatically alerted if an unapproved device connects to the network?
 Cybersecurity Due Diligence Checklist Control # Control Name Risks Questions for IT 1 Make an Benign Case: Employees Inventory of using unapproved Authorized devices without Devices appropriate security
Cybersecurity Due Diligence Checklist Control # Control Name Risks Questions for IT 1 Make an Benign Case: Employees Inventory of using unapproved Authorized devices without Devices appropriate security
Mozilla position paper on the legislative proposal for an EU Cybersecurity Act
 Mozilla position paper on the legislative proposal for an EU Cybersecurity Act Enhancing cybersecurity through government vulnerability disclosure I. INTRODUCTION This paper provides an overview of Mozilla
Mozilla position paper on the legislative proposal for an EU Cybersecurity Act Enhancing cybersecurity through government vulnerability disclosure I. INTRODUCTION This paper provides an overview of Mozilla
News Flash: Some Things Actually Do Work in Security!!!
 SESSION ID: STR-T07R News Flash: Some Things Actually Do Work in Security!!! John Pescatore Director, Emerging Security Trends SANS Institute @John_Pescatore Largest Breach Ever A Short Reality Break
SESSION ID: STR-T07R News Flash: Some Things Actually Do Work in Security!!! John Pescatore Director, Emerging Security Trends SANS Institute @John_Pescatore Largest Breach Ever A Short Reality Break
Surprisingly Successful: What Really Works in Cyber Defense. John Pescatore, SANS
 Surprisingly Successful: What Really Works in Cyber Defense John Pescatore, SANS 1 Largest Breach Ever 2 The Business Impact Equation All CEOs know stuff happens in business and in security The goal is
Surprisingly Successful: What Really Works in Cyber Defense John Pescatore, SANS 1 Largest Breach Ever 2 The Business Impact Equation All CEOs know stuff happens in business and in security The goal is
The effect of competition intensity on cybersecurity
 The effect of competition intensity on cybersecurity An empirical analysis of security patch release on the web browser market Telecom ParisTech CRESSE 2016 July 2016 A market at the heart of cybersecurity
The effect of competition intensity on cybersecurity An empirical analysis of security patch release on the web browser market Telecom ParisTech CRESSE 2016 July 2016 A market at the heart of cybersecurity
Adobe Flash Player Bit Windows 7 Google Chrome
 Adobe Flash Player 11 64 Bit Windows 7 Google Chrome or later, Latest versions of Safari, Mozilla Firefox, Google Chrome, and Opera, 512MB of RAM, 128MB of graphics memory Note: Flash Player 11.2 is the
Adobe Flash Player 11 64 Bit Windows 7 Google Chrome or later, Latest versions of Safari, Mozilla Firefox, Google Chrome, and Opera, 512MB of RAM, 128MB of graphics memory Note: Flash Player 11.2 is the
Spectre, Meltdown, and the Impact of Security Vulnerabilities on your IT Environment. Orin Jeff Melnick
 Spectre, Meltdown, and the Impact of Security Vulnerabilities on your IT Environment Orin Thomas @orinthomas Jeff Melnick Jeff.Melnick@Netwrix.com In this session Vulnerability types Spectre Meltdown Spectre
Spectre, Meltdown, and the Impact of Security Vulnerabilities on your IT Environment Orin Thomas @orinthomas Jeff Melnick Jeff.Melnick@Netwrix.com In this session Vulnerability types Spectre Meltdown Spectre
Flash Player Update Guide Windows 7 64 Bit Google Chrome
 Flash Player Update Guide Windows 7 64 Bit Google Chrome Adobe makes available a version of Flash Player called the "Extended Support Detects wrong Browser type and OS you have - thinks you are on Windows
Flash Player Update Guide Windows 7 64 Bit Google Chrome Adobe makes available a version of Flash Player called the "Extended Support Detects wrong Browser type and OS you have - thinks you are on Windows
Sandboxing. CS-576 Systems Security Instructor: Georgios Portokalidis Spring 2018
 Sandboxing CS-576 Systems Security Instructor: Georgios Portokalidis Sandboxing Means Isolation Why? Software has bugs Defenses slip Untrusted code Compartmentalization limits interference and damage!
Sandboxing CS-576 Systems Security Instructor: Georgios Portokalidis Sandboxing Means Isolation Why? Software has bugs Defenses slip Untrusted code Compartmentalization limits interference and damage!
WorldShare License Manager Release Notes. Administrative Actions... 2 Follow-up Actions... 2 New Features... 4
 WorldShare License Manager Release Notes Release Date: August 10, 2017 Contents Administrative Actions... 2 Follow-up Actions... 2 New Features... 4 Search for licenses using term of use values... 4 New
WorldShare License Manager Release Notes Release Date: August 10, 2017 Contents Administrative Actions... 2 Follow-up Actions... 2 New Features... 4 Search for licenses using term of use values... 4 New
An Introduction to the Waratek Application Security Platform
 Product Analysis January 2017 An Introduction to the Waratek Application Security Platform The Transformational Application Security Technology that Improves Protection and Operations Highly accurate.
Product Analysis January 2017 An Introduction to the Waratek Application Security Platform The Transformational Application Security Technology that Improves Protection and Operations Highly accurate.
Last time. Security Policies and Models. Trusted Operating System Design. Bell La-Padula and Biba Security Models Information Flow Control
 Last time Security Policies and Models Bell La-Padula and Biba Security Models Information Flow Control Trusted Operating System Design Design Elements Security Features 10-1 This time Trusted Operating
Last time Security Policies and Models Bell La-Padula and Biba Security Models Information Flow Control Trusted Operating System Design Design Elements Security Features 10-1 This time Trusted Operating
EXPLORING MOBILE AND API (IN)SECURITY. Pre-Workshop Software Set-up Guide
 EXPLORING MOBILE AND API (IN)SECURITY Pre-Workshop Software Set-up Guide Abstract To maximize your time learning in this workshop we ask that participants complete some pre-workshop software set-up. This
EXPLORING MOBILE AND API (IN)SECURITY Pre-Workshop Software Set-up Guide Abstract To maximize your time learning in this workshop we ask that participants complete some pre-workshop software set-up. This
Predicting Vulnerable Software Components
 Predicting Vulnerable Software Components Stephan Neuhaus, et. al. 10/29/2008 Stuart A Jaskowiak, CSC 682 1 What's in the paper? Introduction Scope of this Work Components and Vulnerabilities Imports and
Predicting Vulnerable Software Components Stephan Neuhaus, et. al. 10/29/2008 Stuart A Jaskowiak, CSC 682 1 What's in the paper? Introduction Scope of this Work Components and Vulnerabilities Imports and
Live Adversary Simulation: Red and Blue Team Tactics
 SESSION ID: HTA-T06 Live Adversary Simulation: Red and Blue Team Tactics James Lyne Head of R&D SANS Institute @JamesLyne Stephen Sims Security Researcher & Fellow SANS Institute @Steph3nSims Agenda 2
SESSION ID: HTA-T06 Live Adversary Simulation: Red and Blue Team Tactics James Lyne Head of R&D SANS Institute @JamesLyne Stephen Sims Security Researcher & Fellow SANS Institute @Steph3nSims Agenda 2
Virtual machines (e.g., VMware)
 Case studies : Introduction to operating systems principles Abstraction Management of shared resources Indirection Concurrency Atomicity Protection Naming Security Reliability Scheduling Fairness Performance
Case studies : Introduction to operating systems principles Abstraction Management of shared resources Indirection Concurrency Atomicity Protection Naming Security Reliability Scheduling Fairness Performance
Mobile Support Strategy in 2011
 Mobile Support Strategy in 2011 This document details the vision for mobile support in 2011: to provide world class, scalable self-service and community-driven support for mobile Firefox users. These are
Mobile Support Strategy in 2011 This document details the vision for mobile support in 2011: to provide world class, scalable self-service and community-driven support for mobile Firefox users. These are
CYBER SECURITY MALAYSIA AWARDS, CONFERENCE & EXHIBITION (CSM-ACE) Securing Virtual Environments
 CYBER SECURITY MALAYSIA AWARDS, CONFERENCE & EXHIBITION (CSM-ACE) 2010 October 25 29, 2010 Kuala Lumpur Convention Centre Securing Virtual Environments Raimund Genes CTO Trend Micro The Changing Datacenter
CYBER SECURITY MALAYSIA AWARDS, CONFERENCE & EXHIBITION (CSM-ACE) 2010 October 25 29, 2010 Kuala Lumpur Convention Centre Securing Virtual Environments Raimund Genes CTO Trend Micro The Changing Datacenter
Development*Process*for*Secure* So2ware
 Development*Process*for*Secure* So2ware Development Processes (Lecture outline) Emphasis on building secure software as opposed to building security software Major methodologies Microsoft's Security Development
Development*Process*for*Secure* So2ware Development Processes (Lecture outline) Emphasis on building secure software as opposed to building security software Major methodologies Microsoft's Security Development
Meltdown and Spectre Mitigation. By Sathish Damodaran
 Meltdown and Spectre Mitigation By Sathish Damodaran Introduction Meltdown allows attackers to read arbitrary physical memory (including kernel memory) for an unprivileged user process. Meltdown uses out
Meltdown and Spectre Mitigation By Sathish Damodaran Introduction Meltdown allows attackers to read arbitrary physical memory (including kernel memory) for an unprivileged user process. Meltdown uses out
Chrome/OS Security 2014
 Chrome/OS Security 2014 New and future hotness Sumit Gwalani (sumit@chromium.org) Senior Product Manager, Google What do we do? Member of Chrome Security Team Everything Chrome/Chromium: Chrome Browser
Chrome/OS Security 2014 New and future hotness Sumit Gwalani (sumit@chromium.org) Senior Product Manager, Google What do we do? Member of Chrome Security Team Everything Chrome/Chromium: Chrome Browser
Black Hat Webcast Series. C/C++ AppSec in 2014
 Black Hat Webcast Series C/C++ AppSec in 2014 Who Am I Chris Rohlf Leaf SR (Security Research) - Founder / Consultant BlackHat Speaker { 2009, 2011, 2012 } BlackHat Review Board Member http://leafsr.com
Black Hat Webcast Series C/C++ AppSec in 2014 Who Am I Chris Rohlf Leaf SR (Security Research) - Founder / Consultant BlackHat Speaker { 2009, 2011, 2012 } BlackHat Review Board Member http://leafsr.com
Open access or Making money openly. David D. Clark MIT Computer Science and AI Lab January, 2006
 Open access or Making money openly David D. Clark MIT Computer Science and AI Lab January, 2006 Topic? This talk is about: The current debate over open access and network neutrality Proposals to rewrite
Open access or Making money openly David D. Clark MIT Computer Science and AI Lab January, 2006 Topic? This talk is about: The current debate over open access and network neutrality Proposals to rewrite
HP Device as a Service (DaaS)
 HP Device as a Service (DaaS) Smart, simplified computing solutions for today s world. Proud Technology Services Industry Association (TSIA) award winner Managing and securing multi-os environments can
HP Device as a Service (DaaS) Smart, simplified computing solutions for today s world. Proud Technology Services Industry Association (TSIA) award winner Managing and securing multi-os environments can
CERT Development EFFECTIVE RESPONSE
 CERT Development EFFECTIVE RESPONSE CERT Development: EFFECTIVE RESPONSE 2 Effective Response Effective Response Well funded, organized attackers threaten your network IT attacks can result in: Loss of
CERT Development EFFECTIVE RESPONSE CERT Development: EFFECTIVE RESPONSE 2 Effective Response Effective Response Well funded, organized attackers threaten your network IT attacks can result in: Loss of
Microsoft SDL 한국마이크로소프트보안프로그램매니저김홍석부장. Security Development Lifecycle and Building Secure Applications
 Release Conception Microsoft SDL Security Development Lifecycle and Building Secure Applications KRnet 2010 2010. 6. 22. 한국마이크로소프트보안프로그램매니저김홍석부장 Hongseok.Kim@microsoft.com Agenda Applications under Attack
Release Conception Microsoft SDL Security Development Lifecycle and Building Secure Applications KRnet 2010 2010. 6. 22. 한국마이크로소프트보안프로그램매니저김홍석부장 Hongseok.Kim@microsoft.com Agenda Applications under Attack
CONTENTS. Appia Web Meeting Guest Guide (v.1.2)
 CONTENTS Requirements... 2 Operating System... 2 Browser... 2 Bandwidth... 2 Join an Appia Web Meeting... 2 Enter by Telephone... 3 Audio... 3 Webcam... 4 Mute/Unmute... 5 Further Information... 6 Links
CONTENTS Requirements... 2 Operating System... 2 Browser... 2 Bandwidth... 2 Join an Appia Web Meeting... 2 Enter by Telephone... 3 Audio... 3 Webcam... 4 Mute/Unmute... 5 Further Information... 6 Links
BROWSERS OPTIMIZATION
 BROWSERS OPTIMIZATION To allow your browser to function more effectively, we recommend that you Clear your browser cache (delete temporary files) and Remove any compatibility view option previously selected
BROWSERS OPTIMIZATION To allow your browser to function more effectively, we recommend that you Clear your browser cache (delete temporary files) and Remove any compatibility view option previously selected
18-642: Security Mitigation & Validation
 18-642: Security Mitigation & Validation 11/27/2017 Security Migitation & Validation Anti-Patterns for security mitigation & validation Poorly considered password policy Poorly considered privilege management
18-642: Security Mitigation & Validation 11/27/2017 Security Migitation & Validation Anti-Patterns for security mitigation & validation Poorly considered password policy Poorly considered privilege management
An Introduction to Runtime Application Self-Protection (RASP)
 Product Analysis June 2016 An Introduction to Runtime Application Self-Protection (RASP) The Transformational Application Security Technology that Improves Protection and Operations Highly accurate. Easy
Product Analysis June 2016 An Introduction to Runtime Application Self-Protection (RASP) The Transformational Application Security Technology that Improves Protection and Operations Highly accurate. Easy
BCW Web Browser Versions and Update Instructions Updated 5/5/2017
 To remain HIPAA compliant and adhere to DPH security requirements, all BCW providers (public and private) are responsible for ensuring that the web browser on the PC(s) used to access BIBS meet the following
To remain HIPAA compliant and adhere to DPH security requirements, all BCW providers (public and private) are responsible for ensuring that the web browser on the PC(s) used to access BIBS meet the following
The tale of one thousand and one ADSL modems
 The tale of one thousand and one ADSL modems Fabio Assolini, Malware Researcher, twitter.com/assolini Virus Bulletin 2012 Dallas, USA PAGE 2 If we can t attack a computer or a server, we ll attack a router
The tale of one thousand and one ADSL modems Fabio Assolini, Malware Researcher, twitter.com/assolini Virus Bulletin 2012 Dallas, USA PAGE 2 If we can t attack a computer or a server, we ll attack a router
Micro Focus Desktop Containers
 White Paper Security Micro Focus Desktop Containers Whether it s extending the life of your legacy applications, making applications more accessible, or simplifying your application deployment and management,
White Paper Security Micro Focus Desktop Containers Whether it s extending the life of your legacy applications, making applications more accessible, or simplifying your application deployment and management,
Novell ZENworks 7.2 Linux Management
 Product Guide SYSTEMS AND RESOURCE MANAGEMENT www.novell.com Novell ZENworks 7.2 Linux Management Making Your Linux* Resources More Automated, Intelligent and Efficient Novell ZENworks 7.2 Linux Management
Product Guide SYSTEMS AND RESOURCE MANAGEMENT www.novell.com Novell ZENworks 7.2 Linux Management Making Your Linux* Resources More Automated, Intelligent and Efficient Novell ZENworks 7.2 Linux Management
Patching Exploits with Duct Tape: Bypassing Mitigations and Backward Steps
 SESSION ID: EXP-R01 Patching Exploits with Duct Tape: Bypassing Mitigations and Backward Steps James Lyne Global Head of Security Research Sophos / SANS Institute @jameslyne Stephen Sims Security Researcher
SESSION ID: EXP-R01 Patching Exploits with Duct Tape: Bypassing Mitigations and Backward Steps James Lyne Global Head of Security Research Sophos / SANS Institute @jameslyne Stephen Sims Security Researcher
1. Title: Case Study: Successful App Genres in India Subtitle: The most popular types of apps with daily active users
 1. Title: Case Study: Successful App Genres in India Subtitle: The most popular types of apps with daily active users 2. Title: Successful App Categories in India Subtitle: The top 5 app categories with
1. Title: Case Study: Successful App Genres in India Subtitle: The most popular types of apps with daily active users 2. Title: Successful App Categories in India Subtitle: The top 5 app categories with
Web-based Attacks on Local IoT Devices. Gunes Acar Danny Huang Frank Li Arvind Narayanan Nick Feamster
 Web-based Attacks on Local IoT Devices Gunes Acar Danny Huang Frank Li Arvind Narayanan Nick Feamster 1 2 3 How to reach local IoT devices? Public devices (e.g., port forwarding) Local malware Web attacks
Web-based Attacks on Local IoT Devices Gunes Acar Danny Huang Frank Li Arvind Narayanan Nick Feamster 1 2 3 How to reach local IoT devices? Public devices (e.g., port forwarding) Local malware Web attacks
The Rise of the Purple Team
 SESSION ID: AIR-W02 The Rise of the Purple Team Robert Wood Head of Security Nuna @robertwood50 William Bengtson Senior Security Program Manager Nuna @waggie2009 Typical Team Responsibilities Red Vulnerability
SESSION ID: AIR-W02 The Rise of the Purple Team Robert Wood Head of Security Nuna @robertwood50 William Bengtson Senior Security Program Manager Nuna @waggie2009 Typical Team Responsibilities Red Vulnerability
Manual Update Java 7 Version 11 Not Working In Chrome
 Manual Update Java 7 Version 11 Not Working In Chrome Microsoft pushed out 11 update bundles to fix more than two dozen bugs in Windows version 17.0.0 installed after applying the Chrome update and restarting
Manual Update Java 7 Version 11 Not Working In Chrome Microsoft pushed out 11 update bundles to fix more than two dozen bugs in Windows version 17.0.0 installed after applying the Chrome update and restarting
RBS OpenEMR Multisite Setup Improper Access Restriction Remote Code Execution of 5
 RBS-2017-001 OpenEMR Multisite Setup Improper Access Restriction Remote Code Execution 2018-03-22 1 of 5 Vendor / Product Information OpenEMR is a Free and Open Source electronic health records and medical
RBS-2017-001 OpenEMR Multisite Setup Improper Access Restriction Remote Code Execution 2018-03-22 1 of 5 Vendor / Product Information OpenEMR is a Free and Open Source electronic health records and medical
HOW TO SOLVE COMMON PROBLEMS WITH LEGACY ORACLE JAVA VERSIONS IN WINDOWS 10
 TECHNOLOGY TOPIC HOW TO SOLVE COMMON PROBLEMS WITH LEGACY ORACLE JAVA VERSIONS IN WINDOWS 10 Legacy applications programmed in Java are having trouble when introduced to a Windows 10 environment. While
TECHNOLOGY TOPIC HOW TO SOLVE COMMON PROBLEMS WITH LEGACY ORACLE JAVA VERSIONS IN WINDOWS 10 Legacy applications programmed in Java are having trouble when introduced to a Windows 10 environment. While
Application Security Using Runtime Protection
 Application Security Using Runtime Protection How RASP can secure your web applications with point & click protection Waratek Solves the Application Security Problems That No One Else Can Application Security
Application Security Using Runtime Protection How RASP can secure your web applications with point & click protection Waratek Solves the Application Security Problems That No One Else Can Application Security
When Chrome Isn t Chrome
 WHITE PAPER When Chrome Isn t Chrome How to set up browser detection: mobile browsers are complicated INTRODUCTION Your website should be tested in as many mobile browsers as possible so that you catch
WHITE PAPER When Chrome Isn t Chrome How to set up browser detection: mobile browsers are complicated INTRODUCTION Your website should be tested in as many mobile browsers as possible so that you catch
Cloud is the 'Only' Way Forward in Information Security. Leveraging Scale to Make the Unknown Known, in Dev, Sec & Ops.
 George Gerchow, Sumo Logic Chief Information Security Officer Cloud is the 'Only' Way Forward in Information Security. Leveraging Scale to Make the Unknown Known, in Dev, Sec & Ops. Agenda Sumo Security
George Gerchow, Sumo Logic Chief Information Security Officer Cloud is the 'Only' Way Forward in Information Security. Leveraging Scale to Make the Unknown Known, in Dev, Sec & Ops. Agenda Sumo Security
Introduction and Datacenter Topology For Your System
 Introduction and Datacenter Topology For Your System This chapter provides an introduction, a datacenter overview, and VMware vcenter requirements for your system. Introducing Cisco WebEx Meetings Server,
Introduction and Datacenter Topology For Your System This chapter provides an introduction, a datacenter overview, and VMware vcenter requirements for your system. Introducing Cisco WebEx Meetings Server,
A Guide to Closing All Potential VDI Security Gaps
 Brought to you by A Guide to Closing All Potential VDI Security Gaps IT and security leaders are embracing virtual desktop infrastructure (VDI) as a way to improve security for an increasingly diverse
Brought to you by A Guide to Closing All Potential VDI Security Gaps IT and security leaders are embracing virtual desktop infrastructure (VDI) as a way to improve security for an increasingly diverse
SECURING SOFTWARE AGAINST LIBRARY ATTACKS
 SECURING SOFTWARE AGAINST LIBRARY ATTACKS Roland Yap School of Computing National University of Singapore ryap@comp.nus.edu.sg Session ID: DAS W05 Session Classification: Advanced Untrusted Libraries Software
SECURING SOFTWARE AGAINST LIBRARY ATTACKS Roland Yap School of Computing National University of Singapore ryap@comp.nus.edu.sg Session ID: DAS W05 Session Classification: Advanced Untrusted Libraries Software
Ranking Vulnerability for Web Application based on Severity Ratings Analysis
 Ranking Vulnerability for Web Application based on Severity Ratings Analysis Nitish Kumar #1, Kumar Rajnish #2 Anil Kumar #3 1,2,3 Department of Computer Science & Engineering, Birla Institute of Technology,
Ranking Vulnerability for Web Application based on Severity Ratings Analysis Nitish Kumar #1, Kumar Rajnish #2 Anil Kumar #3 1,2,3 Department of Computer Science & Engineering, Birla Institute of Technology,
Executive Summary. Flex Bounty Program Overview. Bugcrowd Inc Page 2 of 7
 CANVAS by Instructure Bugcrowd Flex Program Results December 01 Executive Summary Bugcrowd Inc was engaged by Instructure to perform a Flex Bounty program, commonly known as a crowdsourced penetration
CANVAS by Instructure Bugcrowd Flex Program Results December 01 Executive Summary Bugcrowd Inc was engaged by Instructure to perform a Flex Bounty program, commonly known as a crowdsourced penetration
The Most Dangerous Code in the Browser. Stefan Heule, Devon Rifkin, Alejandro Russo, Deian Stefan
 The Most Dangerous Code in the Browser Stefan Heule, Devon Rifkin, Alejandro Russo, Deian Stefan Modern web experience Modern web experience Modern web experience Web apps Extensions NYTimes Chase AdBlock
The Most Dangerous Code in the Browser Stefan Heule, Devon Rifkin, Alejandro Russo, Deian Stefan Modern web experience Modern web experience Modern web experience Web apps Extensions NYTimes Chase AdBlock
Michel Aubizzierre INFILTRATE Jan 12th 2012
 Michel Aubizzierre INFILTRATE Jan 12th 2012 Seagulls are the security researchers of the sea Unearthing the world s greatest bugs When I say: Automated testing
Michel Aubizzierre INFILTRATE Jan 12th 2012 Seagulls are the security researchers of the sea Unearthing the world s greatest bugs When I say: Automated testing
The Evolution of Chrome Security Architecture. Huan Ren Director, Qihoo 360 Technology Ltd
 The Evolution of Chrome Security Architecture Huan Ren Director, Qihoo 360 Technology Ltd Today s Chrome Architecture Browser GPU Sandbox Policy Renderer Extension Plug In History Initial version: multi-process,
The Evolution of Chrome Security Architecture Huan Ren Director, Qihoo 360 Technology Ltd Today s Chrome Architecture Browser GPU Sandbox Policy Renderer Extension Plug In History Initial version: multi-process,
Threat Modeling. Bart De Win Secure Application Development Course, Credits to
 Threat Modeling Bart De Win bart.dewin@ascure.com Secure Application Development Course, 2009 Credits to Frank Piessens (KUL) for the slides 2 1 Overview Introduction Key Concepts Threats, Vulnerabilities,
Threat Modeling Bart De Win bart.dewin@ascure.com Secure Application Development Course, 2009 Credits to Frank Piessens (KUL) for the slides 2 1 Overview Introduction Key Concepts Threats, Vulnerabilities,
NB TEEN APPRENTICE PROGRAM NBTAP EMPLOYER ACCOUNT: FAQS CONNECTING STUDENTS TO CAREERS IN THE SKILLED TRADES
 NBTAP EMPLOYER ACCOUNT: FAQS TOPICS 1.0 Do I need to set up my Employer Account?... 3 2.0 What do I use my Employer Account for?... 3 3.0 How do I login to my Employer Account?... 3 4.0 How do I reset
NBTAP EMPLOYER ACCOUNT: FAQS TOPICS 1.0 Do I need to set up my Employer Account?... 3 2.0 What do I use my Employer Account for?... 3 3.0 How do I login to my Employer Account?... 3 4.0 How do I reset
Foundations of Software Engineering. Lecture 24: Open Source Claire Le Goues
 Foundations of Software Engineering Lecture 24: Open Source Claire Le Goues 1 Learning goals Understand the terminology free software and explain open source culture and principles. Express an educated
Foundations of Software Engineering Lecture 24: Open Source Claire Le Goues 1 Learning goals Understand the terminology free software and explain open source culture and principles. Express an educated
Table of contents. Abstract. Disclaimer. Scope. Procedure. AS-IS overview. Audit overview. Conclusion. Appendix A. Automated tools reports 12
 1 Table of contents Abstract 3 Disclaimer 3 Scope 3 Procedure 4 AS-IS overview 5 Audit overview 10 Conclusion 11 Disclaimer 12 Appendix A. Automated tools reports 12 2 Abstract In this report, we consider
1 Table of contents Abstract 3 Disclaimer 3 Scope 3 Procedure 4 AS-IS overview 5 Audit overview 10 Conclusion 11 Disclaimer 12 Appendix A. Automated tools reports 12 2 Abstract In this report, we consider
Continuous Professional Development (CPD) Manual
 Continuous Professional Development (CPD) Manual 2019 Version 4.1 TABLE OF CONTENTS Definitions... 2 Continuous Professional Development (CPD)... 3 SCA s commitment to the highest global professional standards...
Continuous Professional Development (CPD) Manual 2019 Version 4.1 TABLE OF CONTENTS Definitions... 2 Continuous Professional Development (CPD)... 3 SCA s commitment to the highest global professional standards...
Cybersecurity Today Avoid Becoming a News Headline
 Cybersecurity Today 2017 Avoid Becoming a News Headline Topics Making News Notable Incidents Current State of Affairs Common Points of Failure Three Quick Wins How to Prepare for and Respond to Cybersecurity
Cybersecurity Today 2017 Avoid Becoming a News Headline Topics Making News Notable Incidents Current State of Affairs Common Points of Failure Three Quick Wins How to Prepare for and Respond to Cybersecurity
Manual Internet Explorer 9 Full Version For Xp Sp2
 Manual Internet Explorer 9 Full Version For Xp Sp2 This page provides the Group Policy Administrative Template files for Internet Explorer. Windows Internet Explorer 9 lets your websites shine and perform
Manual Internet Explorer 9 Full Version For Xp Sp2 This page provides the Group Policy Administrative Template files for Internet Explorer. Windows Internet Explorer 9 lets your websites shine and perform
Efficiency of Java Code for Mobile Application Development
 1. Introduction Mobiles applications are written in many programing codes. Mobile application beginners assume that Java programming best practices are equally applicable to mobiles applications programming.
1. Introduction Mobiles applications are written in many programing codes. Mobile application beginners assume that Java programming best practices are equally applicable to mobiles applications programming.
Seqrite Endpoint Security
 Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Website:
 Chapter - 1: CONTENTS OF ISO 9001:2015 CERTIFIED INTERNAL AUDITOR TRAINING E-LEARNING COURSE Sr. No. The entire e-learning course has 6 main parts as below Lectures Details No. of slides 1. Session 1 :
Chapter - 1: CONTENTS OF ISO 9001:2015 CERTIFIED INTERNAL AUDITOR TRAINING E-LEARNING COURSE Sr. No. The entire e-learning course has 6 main parts as below Lectures Details No. of slides 1. Session 1 :
Reinvent Your 2013 Security Management Strategy
 Reinvent Your 2013 Security Management Strategy Laurent Boutet 18 septembre 2013 Phone:+33 6 25 34 12 01 Email:laurent.boutet@skyboxsecurity.com www.skyboxsecurity.com What are Your Key Objectives for
Reinvent Your 2013 Security Management Strategy Laurent Boutet 18 septembre 2013 Phone:+33 6 25 34 12 01 Email:laurent.boutet@skyboxsecurity.com www.skyboxsecurity.com What are Your Key Objectives for
E-Guide WHAT WINDOWS 10 ADOPTION MEANS FOR IT
 E-Guide WHAT WINDOWS 10 ADOPTION MEANS FOR IT E nterprise adoption of Windows 10 isn t likely to follow the same pattern as for Windows 7, and that s a good thing, writes columnist Brian Madden. And even
E-Guide WHAT WINDOWS 10 ADOPTION MEANS FOR IT E nterprise adoption of Windows 10 isn t likely to follow the same pattern as for Windows 7, and that s a good thing, writes columnist Brian Madden. And even
BETTER Mobile Threat Defense (BMTD)
 BETTER Mobile Threat Defense (BMTD) Powered by BETTER Mobile Security, Inc. Enterprise Challenges Today s enterprise IT managers are looking for better and more efficient ways to empower workforces utilizing
BETTER Mobile Threat Defense (BMTD) Powered by BETTER Mobile Security, Inc. Enterprise Challenges Today s enterprise IT managers are looking for better and more efficient ways to empower workforces utilizing
OfficeSuite UC Connector for Salesforce
 USER TRAINING GUIDE OfficeSuite UC Connector for Salesforce 1 OFFICESUITE UC CONNECTOR FOR SALESFORCE: USER TRAINING GUIDE Table of contents 3 Introduction 4 Operating system, hardware and software requirements
USER TRAINING GUIDE OfficeSuite UC Connector for Salesforce 1 OFFICESUITE UC CONNECTOR FOR SALESFORCE: USER TRAINING GUIDE Table of contents 3 Introduction 4 Operating system, hardware and software requirements
JAVASCRIPT CHARTING. Scaling for the Enterprise with Metric Insights Copyright Metric insights, Inc.
 JAVASCRIPT CHARTING Scaling for the Enterprise with Metric Insights 2013 Copyright Metric insights, Inc. A REVOLUTION IS HAPPENING... 3! Challenges... 3! Borrowing From The Enterprise BI Stack... 4! Visualization
JAVASCRIPT CHARTING Scaling for the Enterprise with Metric Insights 2013 Copyright Metric insights, Inc. A REVOLUTION IS HAPPENING... 3! Challenges... 3! Borrowing From The Enterprise BI Stack... 4! Visualization
Service Design Academy Online Resources Site: A How to Guide.
 Creating an account: From your web browser go to: resources.servicedesignacademy.scot The page shown right will open. Click on the Dundee GovJam2017 link. If you are new to this site, click on the Create
Creating an account: From your web browser go to: resources.servicedesignacademy.scot The page shown right will open. Click on the Dundee GovJam2017 link. If you are new to this site, click on the Create
CSC 2114: Artificial Intelligence Search
 CSC 2114: Artificial Intelligence Search Ernest Mwebaze emwebaze@cit.ac.ug Office: Block A : 3 rd Floor [Slide Credit Dan Klein and Pieter Abbeel for CS188 Intro to AI at UC Berkeley. Reference materials
CSC 2114: Artificial Intelligence Search Ernest Mwebaze emwebaze@cit.ac.ug Office: Block A : 3 rd Floor [Slide Credit Dan Klein and Pieter Abbeel for CS188 Intro to AI at UC Berkeley. Reference materials
Whitepaper. Compatibility Testing - Web Applications YOUR SUCCESS IS OUR FOCUS. Published on: March 2008 Author: Jitendra Saxena
 YOUR SUCCESS IS OUR FOCUS Whitepaper Published on: March 2008 Author: Jitendra Saxena 2009 Hexaware Technologies. All rights reserved. Table of Contents 1. Introduction 2. Situation Analysis 3. Problem
YOUR SUCCESS IS OUR FOCUS Whitepaper Published on: March 2008 Author: Jitendra Saxena 2009 Hexaware Technologies. All rights reserved. Table of Contents 1. Introduction 2. Situation Analysis 3. Problem
Mobile Friendly Website. Checks whether your website is responsive. Out of 10. Out of Social
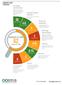 Website Score Overview On-Page Optimization Checks your website for different issues impacting performance and Search Engine Optimization problems. 3 3 WEBSITE SCORE 62 1 1 Competitor Analysis 4.6 5 Analysis
Website Score Overview On-Page Optimization Checks your website for different issues impacting performance and Search Engine Optimization problems. 3 3 WEBSITE SCORE 62 1 1 Competitor Analysis 4.6 5 Analysis
How to manage evolving threats on evolving ICT assets across Enterprise
 How to manage evolving threats on evolving ICT assets across Enterprise Marek Skalicky, CISM, CRISC, Qualys MD for CEE November, 2015 Vaš partner za varovanje informacij Agenda Security STARTs with VISIBILITY
How to manage evolving threats on evolving ICT assets across Enterprise Marek Skalicky, CISM, CRISC, Qualys MD for CEE November, 2015 Vaš partner za varovanje informacij Agenda Security STARTs with VISIBILITY
MRG Effitas Trapmine Exploit Test
 MRG Effitas Trapmine Exploit Test 1 Contents Introduction... 3 Certifications... 3 Tests Applied... 3 Sample sets... 3 Participants... 4 Methodology... 4 Results... 6 Known metasploit samples... 6 In-the-wild
MRG Effitas Trapmine Exploit Test 1 Contents Introduction... 3 Certifications... 3 Tests Applied... 3 Sample sets... 3 Participants... 4 Methodology... 4 Results... 6 Known metasploit samples... 6 In-the-wild
Cross-project defect prediction. Thomas Zimmermann Microsoft Research
 Cross-project defect prediction Thomas Zimmermann Microsoft Research Upcoming Events ICSE 2010: http://www.sbs.co.za/icse2010/ New Ideas and Emerging Results ACM Student Research Competition (SRC) sponsored
Cross-project defect prediction Thomas Zimmermann Microsoft Research Upcoming Events ICSE 2010: http://www.sbs.co.za/icse2010/ New Ideas and Emerging Results ACM Student Research Competition (SRC) sponsored
Assessing Global Security Threat Levels Bryan Lu, Project Manager / Researcher
 I AM NOT A NUMERO! Assessing Global Security Threat Levels Bryan Lu, Project Manager / Researcher 21-23 September 2009 Geneva, Switzerland Numero English: numero or number or No No. or # Spanish: número
I AM NOT A NUMERO! Assessing Global Security Threat Levels Bryan Lu, Project Manager / Researcher 21-23 September 2009 Geneva, Switzerland Numero English: numero or number or No No. or # Spanish: número
Meltdown and Spectre - understanding and mitigating the threats
 Meltdown and Spectre - understanding and mitigating the threats Gratuitous vulnerability logos Jake Williams @MalwareJake SANS / Rendition Infosec sans.org / rsec.us @RenditionSec The sky isn t falling!
Meltdown and Spectre - understanding and mitigating the threats Gratuitous vulnerability logos Jake Williams @MalwareJake SANS / Rendition Infosec sans.org / rsec.us @RenditionSec The sky isn t falling!
Abaqus Student Edition. Installation Instructions
 Product Features And Limitations Abaqus Student Edition Installation Instructions The Abaqus Student Edition consists of Abaqus/Standard, Abaqus/Explicit, and Abaqus/CAE. Full HTML documentation is included.
Product Features And Limitations Abaqus Student Edition Installation Instructions The Abaqus Student Edition consists of Abaqus/Standard, Abaqus/Explicit, and Abaqus/CAE. Full HTML documentation is included.
Manual Update Java 7 Version 11 Not Work In
 Manual Update Java 7 Version 11 Not Work In Chrome Microsoft pushed out 11 update bundles to fix more than two dozen bugs in version 17.0.0 installed after applying the Chrome update and restarting (the
Manual Update Java 7 Version 11 Not Work In Chrome Microsoft pushed out 11 update bundles to fix more than two dozen bugs in version 17.0.0 installed after applying the Chrome update and restarting (the
Google Chrome For Windows Xp 32 Bit Full Version Offline
 Google Chrome For Windows Xp 32 Bit Full Version Offline Support windows All Version. Download Google Chrome 2015 32bit Offline Installer Next. Apple itunes software 2015 For Windows XP, 7 And 8 Download.
Google Chrome For Windows Xp 32 Bit Full Version Offline Support windows All Version. Download Google Chrome 2015 32bit Offline Installer Next. Apple itunes software 2015 For Windows XP, 7 And 8 Download.
Web Programming and Design. MPT Junior Cycle Tutor: Tamara Demonstrators: Aaron, Marion, Hugh
 Web Programming and Design MPT Junior Cycle Tutor: Tamara Demonstrators: Aaron, Marion, Hugh Plan for the next 5 weeks: Introduction to HTML tags Recap on HTML and creating our template file Introduction
Web Programming and Design MPT Junior Cycle Tutor: Tamara Demonstrators: Aaron, Marion, Hugh Plan for the next 5 weeks: Introduction to HTML tags Recap on HTML and creating our template file Introduction
The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS
 The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS WELCOME SANS Institute is presenting the SANS VetSuccess Immersion Academy in the DC Metro area. For transitioning
The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS WELCOME SANS Institute is presenting the SANS VetSuccess Immersion Academy in the DC Metro area. For transitioning
Global Deep Scans Measuring vulnerability levels across organizations, industries, and countries
 Global Deep Scans Measuring vulnerability levels across organizations, industries, and countries Fabian Bräunlein Luca Melette SRLabs Template v12 Motivation for this
Global Deep Scans Measuring vulnerability levels across organizations, industries, and countries Fabian Bräunlein Luca Melette SRLabs Template v12 Motivation for this
The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS
 The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS WELCOME SANS Institute is presenting the SANS VetSuccess Immersion Academy in San Diego. For transitioning
The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS WELCOME SANS Institute is presenting the SANS VetSuccess Immersion Academy in San Diego. For transitioning
Industrial Machinery. Search Marketing Case Study
 Industrial Machinery Search Marketing Case Study 2015-2016 A performance digital marketing consultancy & training academy. Our team comprises of digital researchers, strategists, consultants, usability
Industrial Machinery Search Marketing Case Study 2015-2016 A performance digital marketing consultancy & training academy. Our team comprises of digital researchers, strategists, consultants, usability
