Security Analysis of Lightweight Authentication Protocol from WISTP ,2) P, Xiao FuP P, Chen Dan-weiP P, Wang Ru-chuanP
|
|
|
- Hugh Webb
- 5 years ago
- Views:
Transcription
1 P P P Security Analysis of Lightweight Authentication Protocol from WISTP 23,2,3),2),2),2) Wang Shao-HuiP P, Xiao FuP P, hen Dan-weiP P, Wang Ru-chuanP P 2) ) P(ollege of omputer, Nanjing University of Posts and Telecommunications, Nanjing 223, hina) P(Jiangsu High Technology Research ey Laboratory for Wireless Sensor Networks, Nanjing 23, hina) 3) P( Network and Data Security ey Laboratory of Sichuan Province, hengdu 654, hina) Abstract One of the key problems in Radio Frequency Identification (RFID) is security and privacy. any RFID authentication protocols have been proposed to preserve security and privacy of the system. Nevertheless, most of these protocols are analyzed and it is shown that they can not provide security against some RFID attacks. In WISTP 23, a new lightweight authentication protocol using AES S-box and some special function is presented. The new protocol has a good implementation in resource constrained tags. In this paper, we give the security analysis on this new authentication protocol. After impersonating the valid reader to query the tag and collecting the responses, we can deduce all the secrets shared between the reader and tag through analyzing the messages. The attack utilizes the structure of the invertible function and the property of the special function introduced in the new protocol. ey words RFID; Lightweight Authentication; Privacy; Active Attack Introduction Radio Frequency Identification (RFID) systems are used for automated identification of objects and people. Applications that use RFID technology include warehouse management, logistics, railroad car tracking, product identification, library books check-in/check-out, asset tracking, passport and credit cards, etc. Privacy and security is one of the key problems in RFID, because the communication between the reader and the tag are more vulnerable to malicious adversaries. The possible security threats to RFID systems include denial of service (DoS), man in the middle (I), counterfeiting, spoofing, eavesdropping, traffic analysis, traceability, de-synchronization etc. An effective and flexible way to assure privacy and security is to adopt authentication protocols. The low cost deployment demand for RFID tags forces the lack of resources for performing true cryptographic operations to provide security. It is worthwhile to study ultra-lightweight authentication protocols which require tags to involve only simple bitwise operations such as bitwise XOR, bitwise OR, bitwise AND and rotation. However, providing lightweight security in RFID systems is not a trivial task. Several ultra-lightweight protocols have already been proposed. However, they all have certain flaws and vulnerabilities. Vajda and Buttyan [] have proposed a set of extremely lightweight challenge response authentication algorithms. These can be used for authenticating the tags, but they may be easily attacked by a powerful adversary. Juels [2] proposed a solution based on the use of pseudonyms, without using any hash function. But after a set of authentication sessions, the list of pseudonyms will need to be reused or updated through an out-of-band channel, which limits the practicality of this scheme. A family of ultralightweight mutual authentication protocols have been proposed, but later it
2 was reported that these protocols are vulnerable to variable attacks, such as passive attack, desynchronization attack and full-disclosure attack[3-3]. One of the reasons for the vulnerabilities of these protocols is the imbalance of some triangular operations like bitwise OR and bitwise AND, and the operations used can not provide good cryptographic property. Recently, Dusart and Traore proposed a lightweight authentication protocol for Low-ost RFID Tags(named D-T protocol) in the conference of WISTP 23[4]. The protocol utilizes the security qualities of the AES S-Boxes[5] to build a function, and the authors claim the new protocol can provide good Strict Avalanche property, and can resist many passive or active attacks. In this paper, we examine the security of D-T protocol. An active attack on D-T protocol is proposed, in which we first collect some authentication messages through impersonating valid reader to query the tag; then using the property of the f function introduced in D-T protocol, we can obtain all the secret key bytes. The number we need to query the tag is less than 248, so we conclude D-T can not provide privacy guarantee as claimed. The rest of the paper is organized as follows: We describe the D-T protocol in section 2, and the detail security analysis of D-T is presented in section 3, and show how to extract all the secrets shared by the reader and the tag; onclusion is given in section 4. 2 Description of D-T Protocol D-T protocol utilizes the challenge-response authentication model, which uses a noninvertible function h. In D-T protocol, to verify the identity of the tag, the reader R and the tag T shares secret key. D-T protocol is proceeded as follows: Step. The reader R generates and sends the challenge = (,,..., 5) to the tag T, where i are bytes randomly chosen. Step 2. The tag computes and sends t = ID h ( ), t2 = h ( ), where ID is the identity of the tag. Step 3. The reader polls all the secrets to compute h ( ), and retrieves the identity of the tag. Finally authentication of the tag can be verified by checking hid ( ). To provide mutual authentication, D-T protocol can be adapted with a slightly modification: In Step 2, a challenge ' is sent with the tag s response, and the reader should respond with the computation of h ( ) ' ID. Description of function h. Function h is composed of f Function and S function, and S function is chosen as the AES[5] SubBytes function. Let =,,..., 5 be a 6-byte vector, then S ( ) = (SubBytes( ),SubBytes( ),...,SubBytes( 5)). ID
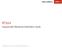
3 f function takes two input bytes, and produces one byte output f : F256 F256 F256 : f( x, y) = [[ x ((255 y) << )] + 6 [((255 x) ( y >> )) mod6]]mod 256 where is the bitwise Exclusive Or, + represents the classical integer addition, n >> divides n by 2, n << multiplies n by 2. Let i,,...,5 be a vector index and j,2,3,4 a round index, and =,,..., 5 is a vector of 6 bytes. The following functions is defined: F ( ) = f(, ) and F j ( ) = ( F j ( ), F j ( ),..., F j 5( )) j i i j ( i+ 2 )mod6 To compute h ( ), First the challenge is Xored to the key, and we can obtain D= = (,..., ). The first state 5 5 Then, the following values are calculated: is initialized by = SD ( ). =, =, 2 2 SF ( ( )) SF ( ( )) = SF = SF ( ( )), ( ( )). Finally, the function h ( ) is denoted as h ( ) = = (,,..., 5). 3 Security Analysis of D-T Protocol Suppose the secret key is = (,,..., 5), in this section we give a security analysis of the D-T protocol and show how to deduce the secret key from h ( ). 3. Analysis of the D-T Protocol We first give some observations about the f function and S function. Observation. As to f function, given y, f ( x, y) f( x, y) for any different x and x ; while given x and y, there exists a unique y ' satisfying f ( xy, ) = f( xy, '). Observation 2. As to S function, SubBytes is a bijective function mapping F 256 to F 256. From the description of D-T protocol, we know 4 is calculated as figure shows. Here 2k is obtained from 2k and + ( k =,,...,7 ): 2k
4 Fig. calculation of 4 From the above observation, we can obtain the following conclusion: onclusion. Given the challenge = (,,..., 5), we denote h ( ) as (,,..., ). Then we poll the second byte over the field F 256, and the other 4 4 4,,,5 bytes unchanged, we can get another unique challenge = (,,..., ) satisfying 5 =. 4 4,, Proof. From the observation and observation 2, we know there must exist satisfying =. ombined with the calculation of,,, we know 4 =. In addition, we 4 4,, know the value is unique, because if, we also know,, and 2 2,, because of observation, thus 3 3,,. 4 4,, Using the conclusion, we present the following algorithm to deduce the second key byte from h ( ). Algorithm Recovery of the second key byte Step. A random challenge = (,,..., 5) is chosen, and we obtain (,,..., ) 4 4 4,,,5 Step 2. Try all the other challenge ' = (, ',..., 5), where the second value ' is polled from to 255, and the other values are the same as, this step will stop if we find satisfying. Now we get (, ) and 4 4,, (, ), which have =.,, Step 3. we try all the possible and, and output the pairs satisfying: f(subbytes( ),SubBytes( )) = f(subbytes( ),SubBytes( ))
5 Step 4. Usually, there are many possible outputs of the Step 3, we can change the first and second bytes of the challenge in Step, then proceed Step 2 and Step 3 to filter out the wrong possible values. 3.2 Experiment Results and complexity analysis We give an experiment as appendix shows, here = xa7, = x92; we first take = x37 and = xb7, and we can get another = 2. The number of the possible pairs (, ) is 52, and possible values of are 67 and 46; Then we change the first and second byte of challenge as = xa6 and = x79, and = 8, and possible values of are 57 and 46. So we can deduce the value of is 46. In our attack, we can not obtain the value of the first secret byte, and the number of the possible value of the second byte is always 2. So after trying the algorithm two times, we can obtain the value of. Using the same method, we can deduce all the bytes of the secret. When attacking the RFID D-T authentication protocol using algorithm, the attack complexity is coming from the number to query the tag. As the experiment shows, to obtain, we query the tag about = 2 times, so we almost have to query the tag = 2 times to obtain all the secret. To reduce the query number, we can get the remaining 32 bits in brute force way after obtaining 2 bytes secrets, and the query number is about = 644. In fact, we can reduce the query number as the way of birthday attack. We query the tag challenge = (,,..., 5), where is randomly chosen and the other values are constant. From the birthday attack, we know after query 3 challenges, we must have at least 2 pairs of = (,,..., ), = (,,..., ) and = (,,..., ), = (,,..., ) satisfying what we need, then the total number we need is about = 2 (32=56 if brute force attack considered). 4 onclusion In this paper, we give the active attack on the new proposed lightweight authentication protocol at WISTP 23. We first impersonate the valid reader to query the tag, and send some special challenges and collect the corresponding responses. Utilizing the structure of the h
6 function and the property of the f function, we can deduce all the secrets shared between the reader and the tag. The attack complexity is to query the tag about 2 times, and in the real attack, the number is much shorter than this value. So we conclude the new protocol is not secure enough to use in reality. How to reduce the analysis complexity and analyze the protocol theoretically will be considered in the future work. Acknowledgments This work is supported by the Priority Academic Program Development of Jiangsu Higher Education Institutions(PAPD), National Natural Science Funds (Grant No.6938) and Nanjing University of Post and Telecommunication Funds (Grant No. NY264). References [] Vajda I, Buttyan, L (23) Lightweight authentication protocols for low-cost RFID tags. In: the Second Workshop on Security in Ubiquitous omputing. Seattle, Washington. [2] Juels, A (25) inimalist ryptography for Low-ost RFID Tags (Extended Abstract). In: Fourth onference on Security in ommunication Network. Amalfi. [3] Peris-Lopez P, Hernandez-astro J, Tapiador JE, Ribagorda A (26) LAP: a real lightweight mutual authentication protocol for low-cost RFID tags. In: Workshop on RFID Security 26. Graz, Austria. [4] Peris-Lopez P, Hernandez-astro J, Tapiador JE, Ribagorda A (26) 2AP: a minimalist mutual-authentication protocol for lowcost RFID tags. In: 26 International onference on Ubiquitous Intelligence and omputing. Wuhan, hina. [5] hien HY (27) SASI: A New Ultralightweight RFID Authentication Protocol Providing Strong Authentication and Strong Integrity. IEEE Transactions on Dependable and Secure omputing 4(4): [6] Sadighian A, Jalili, R (29) AFAP: Anonymous forward-secure mutual authentication protocols for RFID systems. In: Third IEEE International onference on Emerging Security Information, Systems and Technologies. Athens, Glyfada. [7] Sadighian A, Jalili, R (28) FLAP: A fast lightweight mutual authentication protocol for RFID systems. In: 6th IEEE International onference on Networks. New Delhi, India. [8] Peris-Lopez P, Hernandez-astro J, Tapiador JE, Ribagorda A (28) Advances in ultralightweight cryptography for low-cost RFID tags: Gossamer protocol. In: 9th International Workshop on Information Security Applications. Jeju Island, orea. [9] Li T, Wang G (27) Security analysis of two ultra-lightweight RFID authentication protocols. In: 22nd International Information Security onference. Sandton, South Africa. [] Safkhani, Naderi, Bagher N (2) ryptanalysis of AFAP. IEIE Electronics Express 7(7): [] Bárász, Boros B, Ligeti P, Lója, Nagy D (27) Passive Attack Against the 2AP utual Authentication Protocol for RFID Tags. In: First International EURASIP Workshop on RFID Technology. Vienna, Austria. [2] Phan RW (29) ryptanalysis of a new ultralightweight RFID authenticaion protocol SASI. IEEE Transactions on Dependable and Secure omputing 6(4): [3] Avoine G, arpent X, artin B (2) Strong authentication and strong integrity (SASI) is not that strong. In: Workshop on RFID Security - RFIDSec'. Istanbul. [4] Dusart P, Traore s. Lightweight Authentication Protocolfor Low-ost RFID Tags. L. avallaro and D. Gollmann (Eds.): WISTP 23, LNS 7886, pp , 23. [5] Daemen, J., Rijmen, V.: The Design of Rijndael: AES - The Advanced Encryption Standard. Springer (22). Appendix. #include<stdio.h> void main()
7 int x,y,z,z2,z,z2,z,z,x,y,k,k,i,j,k; k=xa7; k=x92; x=x37; y=xb7; int number=; int sbox[256] = // A B D E F x63, x7c, x77, x7b, xf2, x6b, x6f, xc5, x3, x, x67, x2b, xfe, xd7, xab, x76, // xca, x82, xc9, x7d, xfa, x59, x47, xf, xad, xd4, xa2, xaf, x9c, xa4, x72, xc, // xb7, xfd, x93, x26, x36, x3f, xf7, xcc, x34, xa5, xe5, xf, x7, xd8, x3, x5, //2 x4, xc7, x23, xc3, x8, x96, x5, x9a, x7, x2, x8, xe2, xeb, x27, xb2, x75, //3 x9, x83, x2c, xa, xb, x6e, x5a, xa, x52, x3b, xd6, xb3, x29, xe3, x2f, x84, //4 x53, xd, x, xed, x2, xfc, xb, x5b, x6a, xcb, xbe, x39, x4a, x4c, x58, xcf, //5 xd, xef, xaa, xfb, x43, x4d, x33, x85, x45, xf9, x2, x7f, x5, x3c, x9f, xa8, //6 x5, xa3, x4, x8f, x92, x9d, x38, xf5, xbc, xb6, xda, x2, x, xff, xf3, xd2, //7 xcd, xc, x3, xec, x5f, x97, x44, x7, xc4, xa7, x7e, x3d, x64, x5d, x9, x73, //8 x6, x8, x4f, xdc, x22, x2a, x9, x88, x46, xee, xb8, x4, xde, x5e, xb, xdb, //9 xe, x32, x3a, xa, x49, x6, x24, x5c, xc2, xd3, xac, x62, x9, x95, xe4, x79, //A xe7, xc8, x37, x6d, x8d, xd5, x4e, xa9, x6c, x56, xf4, xea, x65, x7a, xae, x8, //B xba, x78, x25, x2e, xc, xa6, xb4, xc6, xe8, xdd, x74, xf, x4b, xbd, x8b, x8a, // x7, x3e, xb5, x66, x48, x3, xf6, xe, x6, x35, x57, xb9, x86, xc, xd, x9e, //D xe, xf8, x98, x, x69, xd9, x8e, x94, x9b, xe, x87, xe9, xce, x55, x28, xdf, //E x8c, xa, x89, xd, xbf, xe6, x42, x68, x4, x99, x2d, xf, xb, x54, xbb, x6 ; //F x=sbox[x^k]; y=sbox[y^k]; z=x^((255-y)<<); z2=6(((255-x)^(y>>))%6); z=(z+z2)%256; printf("%d,",z); for(i=;i<256;i++) y=sbox[i^k]; z=x^((255-y)<<); z2=6(((255-x)^(y>>))%6); z=(z+z2)%256; if(z==z) printf("%d,",i);
8 printf("\n"); for(j=;j<256;j++) for(k=;k<256;k++) x=sbox[x37^j]; y=sbox[2^k]; y=sbox[83^k]; z=x^((255-y)<<); z2=6(((255-x)^(y>>))%6); z=(z+z2)%256; z=x^((255-y)<<); z2=6(((255-x)^(y>>))%6); z=(z+z2)%256; if(z==z) printf("%d,%d number++; printf("\n%d,",number); ",j,k);
Chapter 2: Secret Key
 Chapter 2: Secret Key Basics Block or Stream? Secret Key Methods Salting AES Key Entropy Prof Bill Buchanan OBE http://asecuritysite.com/crypto02 http://asecuritysite.com/encryption Conclusion Encryption
Chapter 2: Secret Key Basics Block or Stream? Secret Key Methods Salting AES Key Entropy Prof Bill Buchanan OBE http://asecuritysite.com/crypto02 http://asecuritysite.com/encryption Conclusion Encryption
GNetPlus Communication Protocol
 Basic Package (BINARY VERSION) Master Query Package (HOST) Field Header Address Query Function Data length DATA BYTES Error Check Desc SOH 0~255 0~255 0~255 CRC16_Low CRC16_Hi Size 1 BYTE 1 BYTE 1 BYTE
Basic Package (BINARY VERSION) Master Query Package (HOST) Field Header Address Query Function Data length DATA BYTES Error Check Desc SOH 0~255 0~255 0~255 CRC16_Low CRC16_Hi Size 1 BYTE 1 BYTE 1 BYTE
Keywords: CRC, CRC-7, cyclic redundancy check, industrial output, PLC, programmable logic controller, C code, CRC generation, microprocessor, switch
 Keywords: CRC, CRC-7, cyclic redundancy check, industrial output, PLC, programmable logic controller, C code, CRC generation, microprocessor, switch APPLICATION NOTE 6002 CRC PROGRAMMING FOR THE MAX14900E
Keywords: CRC, CRC-7, cyclic redundancy check, industrial output, PLC, programmable logic controller, C code, CRC generation, microprocessor, switch APPLICATION NOTE 6002 CRC PROGRAMMING FOR THE MAX14900E
variable 1. Start of Packet - is used to provide synchronization when parsing packets. Always 0xFC
 DreamScreen V2 WiFi UDP Protocol The DreamScreen-WiFi platform uses UDP unicasting and broadcasting over the WLAN to provide communication. Port 8888 is used for both sending and receiving. The DreamScreen
DreamScreen V2 WiFi UDP Protocol The DreamScreen-WiFi platform uses UDP unicasting and broadcasting over the WLAN to provide communication. Port 8888 is used for both sending and receiving. The DreamScreen
MTR-4. C8 Command to MODBUS Bridge User Manual F-1, No. 631, Chung Der Road, Sec 1, Taichung Taiwan.
 MTR-4 C8 Command to MODBUS Bridge User Manual 404 19F-1, No. 631, Chung Der Road, Sec 1, Taichung Taiwan. TEL:886-4-2238-0698 FAX:886-4-2238-0891 Web Site:http://www.monicon.com.tw E-mail: sales@monicon.com.tw
MTR-4 C8 Command to MODBUS Bridge User Manual 404 19F-1, No. 631, Chung Der Road, Sec 1, Taichung Taiwan. TEL:886-4-2238-0698 FAX:886-4-2238-0891 Web Site:http://www.monicon.com.tw E-mail: sales@monicon.com.tw
Cryptanalysis and Improvement of a New. Ultra-lightweight RFID Authentication. Protocol with Permutation
 Applied Mathematical Sciences, Vol. 7, 2013, no. 69, 3433-3444 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ams.2013.211587 Cryptanalysis and Improvement of a New Ultra-lightweight RFID Authentication
Applied Mathematical Sciences, Vol. 7, 2013, no. 69, 3433-3444 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ams.2013.211587 Cryptanalysis and Improvement of a New Ultra-lightweight RFID Authentication
CTT MODBUS-RTU COMMUNICATION PROTOCOL TEMPERATURE MONITOR DEVICE
 INSTRUCTION MANUAL IM149-U v0.92 CTT MODBUS-RTU COMMUNICATION PROTOCOL TEMPERATURE MONITOR DEVICE Firmware version: v3.0 or higher MODBUS PROTOCOL Modbus is a master-slave communication protocol able to
INSTRUCTION MANUAL IM149-U v0.92 CTT MODBUS-RTU COMMUNICATION PROTOCOL TEMPERATURE MONITOR DEVICE Firmware version: v3.0 or higher MODBUS PROTOCOL Modbus is a master-slave communication protocol able to
variable 1. Start of Packet - is used to provide synchronization when parsing packets. Always 0xFC
 DreamScreen V2 WiFi UDP Protocol Rev 2 The DreamScreen-WiFi platform uses UDP unicasting and broadcasting over the WLAN to provide communication. Port 8888 is used for both sending and receiving. The DreamScreen
DreamScreen V2 WiFi UDP Protocol Rev 2 The DreamScreen-WiFi platform uses UDP unicasting and broadcasting over the WLAN to provide communication. Port 8888 is used for both sending and receiving. The DreamScreen
SIMCom_3G_CSD_Application Note_V1.00
 SIMCom_3G_CSD_Application Note_V1.00 Document Title: SIMCom_3G_CSD_Application Note Version: 1.00 Date: Status: Document Control ID: Release SIMCom_3G_CSD_Application Note_V1.00 General Notes SIMCom offers
SIMCom_3G_CSD_Application Note_V1.00 Document Title: SIMCom_3G_CSD_Application Note Version: 1.00 Date: Status: Document Control ID: Release SIMCom_3G_CSD_Application Note_V1.00 General Notes SIMCom offers
MCW Application Notes 24 th February 2017
 MCW Application Notes 24 th February 2017 www.motorcontrolwarehouse.co.uk Document number MCW-HEDY-001 Revision 0.1 Author Gareth Lloyd Product HEDY HD700 Title Summary HEDY HD700 Modbus Serial Communications
MCW Application Notes 24 th February 2017 www.motorcontrolwarehouse.co.uk Document number MCW-HEDY-001 Revision 0.1 Author Gareth Lloyd Product HEDY HD700 Title Summary HEDY HD700 Modbus Serial Communications
Signed/Unsigned Integer Arithmetic in C. Vineel Kovvuri
 Signed/Unsigned Integer Arithmetic in C Vineel Kovvuri http://vineelkovvuri.com Contents 1 Introduction 2 2 How signed-ness is represented in the hardware? 2 3 How signed-ness is interpreted in assembly?
Signed/Unsigned Integer Arithmetic in C Vineel Kovvuri http://vineelkovvuri.com Contents 1 Introduction 2 2 How signed-ness is represented in the hardware? 2 3 How signed-ness is interpreted in assembly?
Yet Another Ultralightweight Authentication Protocol that is Broken
 Yet Another Ultralightweight Authentication Protocol that is Broken Gildas Avoine, Xavier Carpent Université catholique de Louvain B-1348 Louvain-la-Neuve Belgium Abstract Eghdamian and Samsudin published
Yet Another Ultralightweight Authentication Protocol that is Broken Gildas Avoine, Xavier Carpent Université catholique de Louvain B-1348 Louvain-la-Neuve Belgium Abstract Eghdamian and Samsudin published
Verve IPAC Plug-in Wireless AC Module. Software Setup 3. DolphinView Software 3. Preparations 4 Transmit LINK Signals 4.
 Verve IPAC Plug-in Wireless AC Module Wireless Linking & Configuration Guide Table of Contents IPAC Configuration Settings 2 Configuration Settings Reference Table 2 Software Setup 3 DolphinView Software
Verve IPAC Plug-in Wireless AC Module Wireless Linking & Configuration Guide Table of Contents IPAC Configuration Settings 2 Configuration Settings Reference Table 2 Software Setup 3 DolphinView Software
RS-232 Control of the Advantage EQ281/8, EQ282/8 and Advantage SMS200
 RS-232 Control of the Advantage EQ281/8, EQ282/8 and Advantage SMS200 Biamp Systems, 14130 N.W. Science Park, Portland, Oregon 97229 U.S.A. (503) 641-7287 an affiliate of Rauland-Borg Corp. Introduction
RS-232 Control of the Advantage EQ281/8, EQ282/8 and Advantage SMS200 Biamp Systems, 14130 N.W. Science Park, Portland, Oregon 97229 U.S.A. (503) 641-7287 an affiliate of Rauland-Borg Corp. Introduction
TBS Unify Pro / SmartAudio
 TBS Unify Pro / SmartAudio 02.12..2017 Revision 08 SmartAudio uses single wire half duplex communication based on UART. In Idle mode both host and VTX define the SmartAudio pin as input. If the host want
TBS Unify Pro / SmartAudio 02.12..2017 Revision 08 SmartAudio uses single wire half duplex communication based on UART. In Idle mode both host and VTX define the SmartAudio pin as input. If the host want
Ethernet to Digital I/O and Analog Input. (Model: IP-IO)
 Ethernet to Digital I/O and Analog Input (Model: IP-IO) Feature: Operation voltage : DC 7V ~ 36V. Analog Interface: Interface : 3.3V levels compatibility. Resolution : 16-bits Σ-Δ A/D converters. Accuracy
Ethernet to Digital I/O and Analog Input (Model: IP-IO) Feature: Operation voltage : DC 7V ~ 36V. Analog Interface: Interface : 3.3V levels compatibility. Resolution : 16-bits Σ-Δ A/D converters. Accuracy
imetos LoRa Data payload structure
 imetos LoRa Data payload structure Pessl Instruments, GmbH Version 1.0, 06-2018 Content 1. SCOPE OF THIS DOCUMENT... 2 2. PARSING THE DATA FROM THE PAYLOAD VERSUS API DATA ACCESS... 3 3. IMETOS LORA FIRMWARE
imetos LoRa Data payload structure Pessl Instruments, GmbH Version 1.0, 06-2018 Content 1. SCOPE OF THIS DOCUMENT... 2 2. PARSING THE DATA FROM THE PAYLOAD VERSUS API DATA ACCESS... 3 3. IMETOS LORA FIRMWARE
Modbus Protocol Guide for ZP2 Series Control Panels
 Modbus Protocol Guide for ZP2 Series Control Panels P/N 00-3243-505-2603-01 ISS 14DEC15 Copyright Trademarks and patents Manufacturer Version REV 01 Certification 2015 UTC Fire & Security. All rights reserved.
Modbus Protocol Guide for ZP2 Series Control Panels P/N 00-3243-505-2603-01 ISS 14DEC15 Copyright Trademarks and patents Manufacturer Version REV 01 Certification 2015 UTC Fire & Security. All rights reserved.
1 SETTING UP GENERAL FUNCTION TYPE PROTOCOL MESSAGES COMMAND RETURN CODES... 6 TRANSACTION EXAMPLES...
 1 SETTING UP... 3 1.1 RS232 CONTROL CABLES...3 1.2 RS232 SETTINGS...3 2 GENERAL... 4 3 FUNCTION TYPE... 4 4 PROTOCOL MESSAGES... 4 4.1 MESSAGE FORMATS...4 4.1.1 Message Head...4 4.1.2 Message Body...5
1 SETTING UP... 3 1.1 RS232 CONTROL CABLES...3 1.2 RS232 SETTINGS...3 2 GENERAL... 4 3 FUNCTION TYPE... 4 4 PROTOCOL MESSAGES... 4 4.1 MESSAGE FORMATS...4 4.1.1 Message Head...4 4.1.2 Message Body...5
RS232C Serial Interface for Pirani Diaphragm and Pirani Standard Gauges. Caution. binary 8 data bits 1 stop bit no parity bit no handshake
 General Information The Serial Interface allows the communication of the digital Agilent Pirani Capacitance Diaphragm Gauges (PCG-750, PCG-752) and the digital Agilent Pirani Standard Gauges (PVG-550,
General Information The Serial Interface allows the communication of the digital Agilent Pirani Capacitance Diaphragm Gauges (PCG-750, PCG-752) and the digital Agilent Pirani Standard Gauges (PVG-550,
Technical Specification. Third Party Control Protocol. AV Revolution
 Technical Specification Third Party Control Protocol AV Revolution Document AM-TS-120308 Version 1.0 Page 1 of 31 DOCUMENT DETAILS Document Title: Technical Specification, Third Party Control Protocol,
Technical Specification Third Party Control Protocol AV Revolution Document AM-TS-120308 Version 1.0 Page 1 of 31 DOCUMENT DETAILS Document Title: Technical Specification, Third Party Control Protocol,
Input Channels: 4 differential or four single-ended. Address / Baud rate / range configurable by the user
 DAM-Series User Manual Amazing Electronic (HK) Limited User s Manual Overview: DAM module is a new generation data acquisition and control system based on modular embedded systems. Adopting standard DIN35
DAM-Series User Manual Amazing Electronic (HK) Limited User s Manual Overview: DAM module is a new generation data acquisition and control system based on modular embedded systems. Adopting standard DIN35
Highlights. FP51 (FPGA based 1T 8051 core)
 Copyright 2017 PulseRain Technology, LLC. FP51 (FPGA based 1T 8051 core) 10555 Scripps Trl, San Diego, CA 92131 858-877-3485 858-408-9550 http://www.pulserain.com Highlights 1T 8051 Core Intel MCS-51 Compatible
Copyright 2017 PulseRain Technology, LLC. FP51 (FPGA based 1T 8051 core) 10555 Scripps Trl, San Diego, CA 92131 858-877-3485 858-408-9550 http://www.pulserain.com Highlights 1T 8051 Core Intel MCS-51 Compatible
DULCOMETER Multi-parameter Controller dialog DACa
 Software manual DULCOMETER Multi-parameter Controller dialog DACa Modbus RTU EN Valid only in combination with the operating instructions for the Multi-parameter Controller dialog DACa. A2100 Please carefully
Software manual DULCOMETER Multi-parameter Controller dialog DACa Modbus RTU EN Valid only in combination with the operating instructions for the Multi-parameter Controller dialog DACa. A2100 Please carefully
CSEE bit AES decryption. Shrivathsa Bhargav Larry Chen Abhinandan Majumdar Shiva Ramudit. Spring 2008 Project Design Document
 CSEE 4840 128-bit AES decryption Shrivathsa Bhargav Larry Chen Abhinandan Majumdar Shiva Ramudit Spring 2008 Project Design Document CSEE 4840 Table of contents Abstract 1 1. Introduction 1 2. Hardware
CSEE 4840 128-bit AES decryption Shrivathsa Bhargav Larry Chen Abhinandan Majumdar Shiva Ramudit Spring 2008 Project Design Document CSEE 4840 Table of contents Abstract 1 1. Introduction 1 2. Hardware
Request for Comments: XXXX November Registration of a Georgian Character Set draft-giasher-geostd8-00.txt
 Internet draft Gia Shervashidze Network Working Group Georgian Internet Avenue Request for Comments: XXXX November 2001 Registration of a Georgian Character Set draft-giasher-geostd8-00.txt Status of this
Internet draft Gia Shervashidze Network Working Group Georgian Internet Avenue Request for Comments: XXXX November 2001 Registration of a Georgian Character Set draft-giasher-geostd8-00.txt Status of this
Diagnostic Port Serial Interface for Capacitance Diaphragm Gauges
 Communication Protocol Diagnostic Port Serial Interface for Capacitance Diaphragm Gauges CDG025D-X3 4-20 ma Current Loop Stripe CDG045Dhs Stripe CDG100Dhs tira84e1 (2017-05) 1 General Information The Diagnostic
Communication Protocol Diagnostic Port Serial Interface for Capacitance Diaphragm Gauges CDG025D-X3 4-20 ma Current Loop Stripe CDG045Dhs Stripe CDG100Dhs tira84e1 (2017-05) 1 General Information The Diagnostic
//
 ----------------------------------------------------------------------------------- Filename: FixedMath.h ----------------------------------------------------------------------------------- -----------------------------------------------------------------------------------
----------------------------------------------------------------------------------- Filename: FixedMath.h ----------------------------------------------------------------------------------- -----------------------------------------------------------------------------------
APPENDIX- A REFERENCE IMPLEMENTATION OF BSF-128 ===============================================================
 APPENDICES A p p e n d i c e s P a g e 144 A p p e n d i c e s P a g e 145 APPENDIX- A REFERENCE IMPLEMENTATION OF BSF-128 =============================================================== REFERENCE IMPLEMENTATION
APPENDICES A p p e n d i c e s P a g e 144 A p p e n d i c e s P a g e 145 APPENDIX- A REFERENCE IMPLEMENTATION OF BSF-128 =============================================================== REFERENCE IMPLEMENTATION
DMTME Multimeters. Communication protocol. Technical specification V1.2 ABB
 DMTME Multimeters Communication protocol ABB 1 Setting up DMTME serial communication.3 1.1 Serial network ID programming...3 1.2 RS-485 communication interface...3 1.3 Serial line connection...3 2 Communication
DMTME Multimeters Communication protocol ABB 1 Setting up DMTME serial communication.3 1.1 Serial network ID programming...3 1.2 RS-485 communication interface...3 1.3 Serial line connection...3 2 Communication
Heat meter PolluStat M-bus communication protocol description
 Heat meter PolluStat M-bus communication protocol description 1 1. General structure of protocol 1.1. General features of protocol Meter uses a M-bus protocol. Default baud rate: 2400 bps, Even, 1 Stop.
Heat meter PolluStat M-bus communication protocol description 1 1. General structure of protocol 1.1. General features of protocol Meter uses a M-bus protocol. Default baud rate: 2400 bps, Even, 1 Stop.
AquaCER with TTL OUTPUT
 INSTRUCTION MANUAL AquaCER with TTL OUTPUT DESCRIPTION: The AquaCER TTL is a hydrostatic pressure transmitter, with a capacitive ceramic sensor, and can withstand very high burst pressures. The applied
INSTRUCTION MANUAL AquaCER with TTL OUTPUT DESCRIPTION: The AquaCER TTL is a hydrostatic pressure transmitter, with a capacitive ceramic sensor, and can withstand very high burst pressures. The applied
JDICON 400/500 JDICON 401/501. B Interface Description. Universal process controller
 JDICON 400/500 Universal process controller JDICON 401/501 Universal profile controller Universal profile generator B 70.3570.2 Interface Description 10.99/00371593 Contents 1 Introduction 5 1.1 Preface...
JDICON 400/500 Universal process controller JDICON 401/501 Universal profile controller Universal profile generator B 70.3570.2 Interface Description 10.99/00371593 Contents 1 Introduction 5 1.1 Preface...
Intro (with some history) Issues ow, ow, ow, ow, ow, ow, ow, ow, Disclosure/Timeline CHIASMUS cipher
 Intro (with some history) Issues ow, ow, ow, ow, ow, ow, ow, ow, Disclosure/Timeline CHIASMUS cipher We made this: Erik Tews, Julian Wälde, and me independent discovery by Felix Schuster ECB first discovered
Intro (with some history) Issues ow, ow, ow, ow, ow, ow, ow, ow, Disclosure/Timeline CHIASMUS cipher We made this: Erik Tews, Julian Wälde, and me independent discovery by Felix Schuster ECB first discovered
Protocol for Privacy Protection in IoT
 Security Analysis of Fan et al. Lightweight RFID Authentication Protocol for Privacy Protection in IoT Seyed Farhad Aghili and Hamid Mala Department of Information Technology Engineering, Faculty of Computer
Security Analysis of Fan et al. Lightweight RFID Authentication Protocol for Privacy Protection in IoT Seyed Farhad Aghili and Hamid Mala Department of Information Technology Engineering, Faculty of Computer
The Roboteq Modbus Implementation User Manual
 The Roboteq Modbus Implementation User Manual V1.1, December 21, 2017 Visit www.roboteq.com to download the latest revision of this manual Copyright 2017 Roboteq, Inc Copyright Roboteq Inc. 2018. All Rights
The Roboteq Modbus Implementation User Manual V1.1, December 21, 2017 Visit www.roboteq.com to download the latest revision of this manual Copyright 2017 Roboteq, Inc Copyright Roboteq Inc. 2018. All Rights
RS-232 Control of the Advantage DRI
 RS-232 Control of the Advantage DRI Biamp Systems, 14130 N.W. Science Park, Portland, Oregon 97229 U.S.A. (503) 641-7287 an affiliate of Rauland-Borg Corp. Introduction This document contains technical
RS-232 Control of the Advantage DRI Biamp Systems, 14130 N.W. Science Park, Portland, Oregon 97229 U.S.A. (503) 641-7287 an affiliate of Rauland-Borg Corp. Introduction This document contains technical
RS232C / RS485C Serial Interface for Cold Cathode and Cold Cathode Pirani Gauges
 Communication Protocol RS232C / RS485C Serial Interface for Cold Cathode and Cold Cathode Pirani Gauges MAG500, MAG504 MPG500, MPG504 tira83e1-a (2017-06) 1 General Information The Serial Interface allows
Communication Protocol RS232C / RS485C Serial Interface for Cold Cathode and Cold Cathode Pirani Gauges MAG500, MAG504 MPG500, MPG504 tira83e1-a (2017-06) 1 General Information The Serial Interface allows
SPARC INTERNATIONAL. Version1 SPARC Keyboard Specification
 SPARC INTERNATIONAL Version1 SPARC Keyboard Specification SPARC International, Inc. 3333 Bowers Ave., Suite 280, Santa Clara, CA 95054-3913, 408-748-9111. FAX 408-748-9777 1999, SPARC International Inc.
SPARC INTERNATIONAL Version1 SPARC Keyboard Specification SPARC International, Inc. 3333 Bowers Ave., Suite 280, Santa Clara, CA 95054-3913, 408-748-9111. FAX 408-748-9777 1999, SPARC International Inc.
Cryptanalysis of Some RFID Authentication Protocols
 20 JOURNAL OF COMMUNICATIONS, VOL. 3, NO. 7, DECEMBER 2008 Cryptanalysis of Some RFID Authentication Protocols Tianjie Cao, Peng Shen School of Computer, China University of Mining and Technology Sanhuannanlu,
20 JOURNAL OF COMMUNICATIONS, VOL. 3, NO. 7, DECEMBER 2008 Cryptanalysis of Some RFID Authentication Protocols Tianjie Cao, Peng Shen School of Computer, China University of Mining and Technology Sanhuannanlu,
on a 35 mm top-hat rail (in accordance with DIN EN TH35) Ambient temperature Operation: C Storage: C
 Data sheet PCD1.B1020-A20 E-Line RIO 16DI, 4Rel Starting with FW 1.08.xx The L-Serie E-Line RIO modules are controlled via the RS-485 serial communication protocols S-Bus and Modbus for decentralised automation
Data sheet PCD1.B1020-A20 E-Line RIO 16DI, 4Rel Starting with FW 1.08.xx The L-Serie E-Line RIO modules are controlled via the RS-485 serial communication protocols S-Bus and Modbus for decentralised automation
App Note Application Note: State-Driven Control of a dpasp using a Microchip PIC.
 Rev: 1.0.1 Date: 8 th July 2009 App Note - 207 Application Note: State-Driven Control of a dpasp using a Microchip PIC. This application note contains a total 3 files, if you have only this pdf text document,
Rev: 1.0.1 Date: 8 th July 2009 App Note - 207 Application Note: State-Driven Control of a dpasp using a Microchip PIC. This application note contains a total 3 files, if you have only this pdf text document,
M2M/DMTME Instruments Communication protocol. Technical specification V.2.1 2CSG445011D0201
 M2M/DMTME Instruments Communication protocol 2CSG445011D0201 1 Setting up M2M/DMTME serial communication... 3 1.1 Serial network ID programming... 3 1.2 RS-485 communication interface... 3 1.3 Serial line
M2M/DMTME Instruments Communication protocol 2CSG445011D0201 1 Setting up M2M/DMTME serial communication... 3 1.1 Serial network ID programming... 3 1.2 RS-485 communication interface... 3 1.3 Serial line
Security Analysis of Two Ultra-Lightweight RFID Authentication Protocols
 Security Analysis of Two Ultra-Lightweight RFID Authentication Protocols Tieyan Li and Guilin Wang Systems and Security Department Institute for Infocomm Research (I 2 R) 21 Heng Mui Keng Terrace, Singapore
Security Analysis of Two Ultra-Lightweight RFID Authentication Protocols Tieyan Li and Guilin Wang Systems and Security Department Institute for Infocomm Research (I 2 R) 21 Heng Mui Keng Terrace, Singapore
TCG Algorithm Registry
 Family 2.0" Level 00 Revision 01.27 September 26, 2017 Committee Draft Contact: admin@trustedcomputinggroup.org Work in Progress: This document is an intermediate draft for comment only and is subject
Family 2.0" Level 00 Revision 01.27 September 26, 2017 Committee Draft Contact: admin@trustedcomputinggroup.org Work in Progress: This document is an intermediate draft for comment only and is subject
RS232C / RS485C Serial Interface for Pirani Capacitance Diaphragm and Pirani Standard Gauges
 Communication Protocol RS232C / RS485C Serial Interface for Pirani Capacitance Diaphragm and Pirani Standard Gauges PCG550, PCG552, PCG554 PSG550, PSG552, PSG554 RS485C RS232C tira59e1-a (2017-04) 1 General
Communication Protocol RS232C / RS485C Serial Interface for Pirani Capacitance Diaphragm and Pirani Standard Gauges PCG550, PCG552, PCG554 PSG550, PSG552, PSG554 RS485C RS232C tira59e1-a (2017-04) 1 General
// and verify that there is a sine wave with frequency <FREQUENCY> and
 F330DC_IDA0_SineWave.c Copyright 2006 Silicon Laboratories, Inc. http:www.silabs.com Program Description: This program outputs a sine wave using IDA0. IDA0's output is scheduled to update at a rate determined
F330DC_IDA0_SineWave.c Copyright 2006 Silicon Laboratories, Inc. http:www.silabs.com Program Description: This program outputs a sine wave using IDA0. IDA0's output is scheduled to update at a rate determined
UNPACKING THE PACKED UNPACKER: REVERSING AN ANDROID ANTI-ANALYSIS NATIVE LIBRARY Maddie Stone Google, USA
 3 5 October UNPACKING THE PACKED UNPACKER: REVERSING AN ANDROID ANTI-ANALYSIS NATIVE LIBRARY Maddie Stone Google, USA ABSTRACT maddiestone@google.com Malware authors implement many different techniques
3 5 October UNPACKING THE PACKED UNPACKER: REVERSING AN ANDROID ANTI-ANALYSIS NATIVE LIBRARY Maddie Stone Google, USA ABSTRACT maddiestone@google.com Malware authors implement many different techniques
Computer Control of the Advantage DRC 4+4
 Computer Control of the Advantage DRC 4+4 Biamp Systems, 14130 N.W. Science Park, Portland, Oregon 97229 U.S.A. (503) 641-7287 an affiliate of Rauland-Borg Corp. Introduction This document contains technical
Computer Control of the Advantage DRC 4+4 Biamp Systems, 14130 N.W. Science Park, Portland, Oregon 97229 U.S.A. (503) 641-7287 an affiliate of Rauland-Borg Corp. Introduction This document contains technical
BENCHTOP INSTRUMENT. Digital AC/DC Power Meter. Operation Manual V1.0
 BENCHTOP INSTRUMENT Digital AC/DC Power Meter Operation Manual V1.0 Default Setup Item Default Remark Version 0 Model No. Address 1 1 ~ 255 decimal Baud Rate 96 3 bps, 6 bps, 12 bps, 24 bps, 48 bps, 96
BENCHTOP INSTRUMENT Digital AC/DC Power Meter Operation Manual V1.0 Default Setup Item Default Remark Version 0 Model No. Address 1 1 ~ 255 decimal Baud Rate 96 3 bps, 6 bps, 12 bps, 24 bps, 48 bps, 96
Modbus Map: Conext XW/XW+ Device
 Map: Conext XW/XW+ Device 503-0246-01-01 Revision A.3 UNINTENDED OPERATION WARNING The use of this product with communications requires expertise in the design, operation, and programming of the device.
Map: Conext XW/XW+ Device 503-0246-01-01 Revision A.3 UNINTENDED OPERATION WARNING The use of this product with communications requires expertise in the design, operation, and programming of the device.
ADV7610 SOFTWARE MANUAL SOFTWARE MANUAL. Documentation of the Register Maps. Rev. 0
 ADV7610 SOFTWAE MANUAL Documentation of the egister Maps SOFTWAE MANUAL ev. 0 April 2013 egister Map TABLE OF CONTENTS Introduction... 3 Legal Terms and Conditions... 3 1 egister Tables... 4 1.1 IO...
ADV7610 SOFTWAE MANUAL Documentation of the egister Maps SOFTWAE MANUAL ev. 0 April 2013 egister Map TABLE OF CONTENTS Introduction... 3 Legal Terms and Conditions... 3 1 egister Tables... 4 1.1 IO...
Motors I Automation I Energy I Transmission & Distribution I Coatings. Modbus RTU CFW701. User s Manual
 Motors I Automation I Energy I Transmission & Distribution I Coatings Modbus RTU CFW701 User s Manual Modbus RTU User s Manual Series: CFW701 Language: English Document Number: 10001538593 / 00 Publication
Motors I Automation I Energy I Transmission & Distribution I Coatings Modbus RTU CFW701 User s Manual Modbus RTU User s Manual Series: CFW701 Language: English Document Number: 10001538593 / 00 Publication
PCD1.W5200-A20. E-Line S-Serie RIO 8AO. Features. General technical data. Dimensions and installation
 Data sheet www.sbc-support.com PCD1.W5200-A20 E-Line S-Serie RI 8A The S-Serie E-Line RI modules are controlled via the RS-485 serial communication protocols S-Bus and Modbus for decentralised automation
Data sheet www.sbc-support.com PCD1.W5200-A20 E-Line S-Serie RI 8A The S-Serie E-Line RI modules are controlled via the RS-485 serial communication protocols S-Bus and Modbus for decentralised automation
PCD1.A2000-A20. E-Line S-Serie RIO 6Rel 16A. Features. General technical data. Dimensions and installation
 Data sheet www.sbc-support.com PCD1.A2000-A20 E-Line S-Serie RI 6Rel 16A The S-Serie E-Line RI modules are controlled via the RS-485 serial communication protocols S-Bus and Modbus for decentralised automation
Data sheet www.sbc-support.com PCD1.A2000-A20 E-Line S-Serie RI 6Rel 16A The S-Serie E-Line RI modules are controlled via the RS-485 serial communication protocols S-Bus and Modbus for decentralised automation
Efficient RFID Authentication protocol for Ubiquitous Computing Environment
 Efficient RFID Authentication protocol for Ubiquitous Computing Environment Eun Young Choi 1, Su Mi Lee 1, and Dong Hoon Lee 2 Center for Information Security Technologies(CIST), Korea University, 1, 5-Ka,
Efficient RFID Authentication protocol for Ubiquitous Computing Environment Eun Young Choi 1, Su Mi Lee 1, and Dong Hoon Lee 2 Center for Information Security Technologies(CIST), Korea University, 1, 5-Ka,
HDLC BCC 15.1 Data Link Protocol Description
 Data Link Protocol Description by Daniel L. Henry Revision 1.1 October 9, 2011 Copyright 2000-2011 by Daniel L. Henry Revision History Rev. Date Changed By Reason for Change 1.0 5/9/03 Dan L. Henry Made
Data Link Protocol Description by Daniel L. Henry Revision 1.1 October 9, 2011 Copyright 2000-2011 by Daniel L. Henry Revision History Rev. Date Changed By Reason for Change 1.0 5/9/03 Dan L. Henry Made
StarPRNT ios SDK User s Manual
 StarPRNT ios SDK User s Manual Abstract This paper provides information about the StarPRNT ios SDK. It provides guidelines for our customers to build the StarPRNT application. Version History Release Date
StarPRNT ios SDK User s Manual Abstract This paper provides information about the StarPRNT ios SDK. It provides guidelines for our customers to build the StarPRNT application. Version History Release Date
Modbus communication protocol
 TIP Thüringer Industrie Produkte GmbH Bahnhofstraße 26 99842 Ruhla GERMANY Tel. : +49 (0)36929/64029-0 Fax : +49 (0)36929/64029-99 info@stromzaehler.de www.stromzaehler.de Modbus communication protocol
TIP Thüringer Industrie Produkte GmbH Bahnhofstraße 26 99842 Ruhla GERMANY Tel. : +49 (0)36929/64029-0 Fax : +49 (0)36929/64029-99 info@stromzaehler.de www.stromzaehler.de Modbus communication protocol
ADV7612 SOFTWARE MANUAL SOFTWARE MANUAL. Documentation of the Register Maps. Rev. A
 ADV7612 SOFTWAE MANUAL Documentation of the egister Maps SOFTWAE MANUAL ev. A December 2013 TABLE OF CONTENTS egister Map Introduction... 3 Legal Terms and Conditions... 3 1 egister Tables... 4 1.1 IO...
ADV7612 SOFTWAE MANUAL Documentation of the egister Maps SOFTWAE MANUAL ev. A December 2013 TABLE OF CONTENTS egister Map Introduction... 3 Legal Terms and Conditions... 3 1 egister Tables... 4 1.1 IO...
Modbus RTU CFW100. User s Manual. Phone: Fax: Web: -
 Modbus RTU CFW100 User s Manual Modbus RTU User s Manual Series: CFW100 Language: English Document Number: 10002909455 / 00 Publication Date: 06/2014 CONTENTS CONTENTS... 3 ABOUT THIS MANUAL... 5 ABBREVIATIONS
Modbus RTU CFW100 User s Manual Modbus RTU User s Manual Series: CFW100 Language: English Document Number: 10002909455 / 00 Publication Date: 06/2014 CONTENTS CONTENTS... 3 ABOUT THIS MANUAL... 5 ABBREVIATIONS
 Low visibility of Cyber Threats Invisible Attacks VPN, AD, PtH, PtT Invisible Network Traffic Google Drive, Dropbox Invisible Malware Task schedule, Wmi, Powershell 2016 Verint systems inc. All rights
Low visibility of Cyber Threats Invisible Attacks VPN, AD, PtH, PtT Invisible Network Traffic Google Drive, Dropbox Invisible Malware Task schedule, Wmi, Powershell 2016 Verint systems inc. All rights
GSA GAT PROTOCOL V Game Authentication Terminal
 GSA GAT PROTOCOL V3.50.0 Game Authentication Terminal Gaming Standards Association GAT Technical Committee Released: 2010/12/13 Document ID: gsa-p0093.001.00 GAMINGSTANDARDS.COM GSA GAT Protocol, Document
GSA GAT PROTOCOL V3.50.0 Game Authentication Terminal Gaming Standards Association GAT Technical Committee Released: 2010/12/13 Document ID: gsa-p0093.001.00 GAMINGSTANDARDS.COM GSA GAT Protocol, Document
Motors I Automation I Energy I Transmission & Distribution I Coatings. Modbus RTU CFW300. User s Manual
 Motors I Automation I Energy I Transmission & Distribution I Coatings Modbus RTU CFW300 User s Manual Modbus RTU User s Manual Series: CFW300 Language: English Document Number: 10003806158 / 02 Publication
Motors I Automation I Energy I Transmission & Distribution I Coatings Modbus RTU CFW300 User s Manual Modbus RTU User s Manual Series: CFW300 Language: English Document Number: 10003806158 / 02 Publication
Description. thanos ModBus. thanos SR ModBus
 thanos ModBus & thanos SR ModBus Thermokon Sensortechnik GmbH - www.thermokon.de - email@thermokon.de 1 Index of changes Revision Date A B C 25.7.211 First draft 12.9.211 Version LQ added 22.9.211 Additional
thanos ModBus & thanos SR ModBus Thermokon Sensortechnik GmbH - www.thermokon.de - email@thermokon.de 1 Index of changes Revision Date A B C 25.7.211 First draft 12.9.211 Version LQ added 22.9.211 Additional
CS 4400 Fall 2018 Midterm Exam 2 Practice (Version 2)
 CS 4400 Fall 2018 Midterm Exam 2 Practice (Version 2) Name: Instructions You will have eighty minutes to complete the actual open-book, opennote exam. Electronic devices will be allowed only to consult
CS 4400 Fall 2018 Midterm Exam 2 Practice (Version 2) Name: Instructions You will have eighty minutes to complete the actual open-book, opennote exam. Electronic devices will be allowed only to consult
ID: Sample Name: Q3dY56x3hp Cookbook: defaultlinuxfilecookbook.jbs Time: 04:08:56 Date: 21/08/2018 Version:
 ID: 73304 Sample : Q3dY56x3hp Cookbook: defaultlinuxfilecookbook.jbs Time: 04:08:56 Date: 21/08/2018 Version: 23.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection
ID: 73304 Sample : Q3dY56x3hp Cookbook: defaultlinuxfilecookbook.jbs Time: 04:08:56 Date: 21/08/2018 Version: 23.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection
MODBUS Communication Protocol
 MODBUS Communication Protocol for counters with integrated MODBUS or ETHERNET interface 7E.78/86 0212 7E.68 0212 7E.64 0210 7E.78/86 0412 7E.68 0412 6A and 80A 3phase counters with RS485 serial communication.
MODBUS Communication Protocol for counters with integrated MODBUS or ETHERNET interface 7E.78/86 0212 7E.68 0212 7E.64 0210 7E.78/86 0412 7E.68 0412 6A and 80A 3phase counters with RS485 serial communication.
Technical Information. Command overview of Vision Systems
 Technical Information Command overview of Vision Systems Image analysis command Grab image 0x01 X X X X Shutter speed 0x07 X X X X Synchronous flash 0x49 X X X X Video mode 0x00 X X Display 0x05 X X X
Technical Information Command overview of Vision Systems Image analysis command Grab image 0x01 X X X X Shutter speed 0x07 X X X X Synchronous flash 0x49 X X X X Video mode 0x00 X X Display 0x05 X X X
PLC Lite Host Message Protocol Specification
 PLC Lite Host Message Protocol Specification Version 0.6 Oct. 20, 2014 Copyright Texas Instruments Incorporated, 2009-2014 The information and/or drawings set forth in this document and all rights in and
PLC Lite Host Message Protocol Specification Version 0.6 Oct. 20, 2014 Copyright Texas Instruments Incorporated, 2009-2014 The information and/or drawings set forth in this document and all rights in and
#include <stdio.h> // // Global CONSTANTS
 Distance.c Author: Baylor Electromechanical Systems Operates on an external 18.432 MHz oscillator. Target: Cygnal Educational Development Board / C8051F020 Tool chain: KEIL C51 6.03 / KEIL EVAL C51 Utilizes
Distance.c Author: Baylor Electromechanical Systems Operates on an external 18.432 MHz oscillator. Target: Cygnal Educational Development Board / C8051F020 Tool chain: KEIL C51 6.03 / KEIL EVAL C51 Utilizes
Motors I Automation I Energy I Transmission & Distribution I Coatings. Modbus RTU CFW500. User s Manual
 Motors I Automation I Energy I Transmission & Distribution I Coatings Modbus RTU CFW500 User s Manual Modbus RTU User s Manual Series: CFW500 Language: English Document Number: 10002253377 / 00 Publication
Motors I Automation I Energy I Transmission & Distribution I Coatings Modbus RTU CFW500 User s Manual Modbus RTU User s Manual Series: CFW500 Language: English Document Number: 10002253377 / 00 Publication
RTX64. Supported Network Interface Cards
 RTX64 Supported Network Interface Cards 2017 IntervalZero, Inc. IZ-DOC-X64-0088-R34 October 2017 The Supported Network Interface Cards guide lists the NIC drivers that are provided with RTX64 for use with
RTX64 Supported Network Interface Cards 2017 IntervalZero, Inc. IZ-DOC-X64-0088-R34 October 2017 The Supported Network Interface Cards guide lists the NIC drivers that are provided with RTX64 for use with
RTX64. Supported Network Interface Cards IntervalZero, Inc. IZ-DOC-X R32 March 2017
 RTX64 Supported Network Interface Cards 2017 IntervalZero, Inc. IZ-DOC-X64-0088-R32 March 2017 The Supported Network Interface Cards guide lists the NIC drivers that are provided with RTX64 for use with
RTX64 Supported Network Interface Cards 2017 IntervalZero, Inc. IZ-DOC-X64-0088-R32 March 2017 The Supported Network Interface Cards guide lists the NIC drivers that are provided with RTX64 for use with
Cryptanalysis and Improvement on a New RFID Mutual Authentication Protocol Compatible with EPC Standard
 Cryptanalysis and Improvement on a New RFID Mutual Authentication Protocol Compatible with EPC Standard Mohammad Hassan Habibi Faculty of Electrical Engineering, I.H University Tehran, Iran mohamad.h.habibi@gmail.com
Cryptanalysis and Improvement on a New RFID Mutual Authentication Protocol Compatible with EPC Standard Mohammad Hassan Habibi Faculty of Electrical Engineering, I.H University Tehran, Iran mohamad.h.habibi@gmail.com
Mahesh V. Tripunitara and Samuel S. Wagsta, Jr. COAST Laboratory. Purdue University. COAST TR-98/01.
 The Compression Functions of SHA, MD, MD4 and MD5 are not Ane Mahesh V. Tripunitara and Samuel S. Wagsta, Jr. COAST Laboratory Purdue University West Lafayette, IN 47907-198 ftripunit,sswg@cs.purdue.edu
The Compression Functions of SHA, MD, MD4 and MD5 are not Ane Mahesh V. Tripunitara and Samuel S. Wagsta, Jr. COAST Laboratory Purdue University West Lafayette, IN 47907-198 ftripunit,sswg@cs.purdue.edu
Security Analysis of a PUF based RFID Authentication Protocol
 Security Analysis of a PUF based RFID Authentication Protocol Masoumeh Safkhani 1, Nasour Bagheri 2 and Majid Naderi 1 1 Electrical Engineering Department, Iran University of Science and Technology, Tehran,
Security Analysis of a PUF based RFID Authentication Protocol Masoumeh Safkhani 1, Nasour Bagheri 2 and Majid Naderi 1 1 Electrical Engineering Department, Iran University of Science and Technology, Tehran,
Primitive Specification for SSS Philip Hawkes, Michael Paddon, Gregory G. Rose, Miriam Wiggers de Vries
 Primitive Specification for SSS Philip Hawkes, Michael Paddon, Gregory G. Rose, Miriam Wiggers de Vries {phawkes,mwp,ggr,miriamw}@qualcomm.com Qualcomm Australia Level 3, 230 Victoria Rd Gladesville NSW
Primitive Specification for SSS Philip Hawkes, Michael Paddon, Gregory G. Rose, Miriam Wiggers de Vries {phawkes,mwp,ggr,miriamw}@qualcomm.com Qualcomm Australia Level 3, 230 Victoria Rd Gladesville NSW
Specifiche generali protocollo MODBUS-RTU Rev. 10 (inglese) REVISIONS
 Modbus-RTU Protocol (Mach Smart / Smart Più) Page 1 of 18 Specifiche generali protocollo MODBUS-RTU Rev. 10 (inglese) Written: U. T. ing. M. Bandini / A. Sangiorgi Verified: A. Q. sig. F. Adinolfi Approved:
Modbus-RTU Protocol (Mach Smart / Smart Più) Page 1 of 18 Specifiche generali protocollo MODBUS-RTU Rev. 10 (inglese) Written: U. T. ing. M. Bandini / A. Sangiorgi Verified: A. Q. sig. F. Adinolfi Approved:
MODEL TDAI-2170 INTEGRATED AMPLIFIER EXTERNAL CONTROL MANUAL
 MODEL TDAI-2170 INTEGRATED AMPLIFIER EXTERNAL CONTROL MANUAL Serial Settings The serial port settings are always 8 data bits, no parity and one stop bit with a baud rate of 115200. Commands and Requests
MODEL TDAI-2170 INTEGRATED AMPLIFIER EXTERNAL CONTROL MANUAL Serial Settings The serial port settings are always 8 data bits, no parity and one stop bit with a baud rate of 115200. Commands and Requests
JMY607H User's Manual
 JMY607H User's Manual (Revision 3.42) Jinmuyu Electronics Co. LTD 2011/6/27 Please read this manual carefully before using. If any problem, please mail to: Jinmuyu@vip.sina.com Contents 1 Product introduction...
JMY607H User's Manual (Revision 3.42) Jinmuyu Electronics Co. LTD 2011/6/27 Please read this manual carefully before using. If any problem, please mail to: Jinmuyu@vip.sina.com Contents 1 Product introduction...
Interface Card, Interface Box, Datalogger & Interface. Bedienungsanleitung. Kommunikationsprotokoll. Operating Instructions. Communications protocol
 Interface Card, Interface Box, Datalogger & Interface D GB Bedienungsanleitung Kommunikationsprotokoll Operating Instructions Communications protocol 42,0410,1318 022005 Table of contents General remarks...
Interface Card, Interface Box, Datalogger & Interface D GB Bedienungsanleitung Kommunikationsprotokoll Operating Instructions Communications protocol 42,0410,1318 022005 Table of contents General remarks...
IEC /104 Communications Protocol
 expertmeter High Performance Analyzer PM180 IEC60870-5-101/104 Communications Protocol Reference Guide BG0593 Rev. A1 Every effort has been made to ensure that the material herein is complete and accurate.
expertmeter High Performance Analyzer PM180 IEC60870-5-101/104 Communications Protocol Reference Guide BG0593 Rev. A1 Every effort has been made to ensure that the material herein is complete and accurate.
THE KEY RECOVERY ATTACKS CRYPTOGRAPHY IMPLEMENTATIONS AGAINST COMMERCIAL WHITE BOX SANGHWAN AHN(H2SPICE), LINE CORPORATION
 THE KEY RECOVERY ATTACKS AGAINST COMMERCIAL WHITE BOX CRYPTOGRAPHY IMPLEMENTATIONS SANGHWAN AHN(H2SPICE), LINE CORPORATION AGENDA Introduction WHITE-BOX CRYPTOGRAPHY White-box Cryptanalysis Conclusion
THE KEY RECOVERY ATTACKS AGAINST COMMERCIAL WHITE BOX CRYPTOGRAPHY IMPLEMENTATIONS SANGHWAN AHN(H2SPICE), LINE CORPORATION AGENDA Introduction WHITE-BOX CRYPTOGRAPHY White-box Cryptanalysis Conclusion
Cryptanalysis of improved Yeh et al. s authentication Protocol: An EPC Class-1 Generation-2 standard compliant protocol
 Cryptanalysis of improved Yeh et al. s authentication Protocol: An EPC Class-1 Generation-2 standard compliant protocol Masoumeh Safkhani 1, Nasour Bagheri 2, Somitra Kumar Sanadhya 3, Majid Naderi 1 1
Cryptanalysis of improved Yeh et al. s authentication Protocol: An EPC Class-1 Generation-2 standard compliant protocol Masoumeh Safkhani 1, Nasour Bagheri 2, Somitra Kumar Sanadhya 3, Majid Naderi 1 1
CSCI 2212: Intermediate Programming / C Chapter 15
 ... /34 CSCI 222: Intermediate Programming / C Chapter 5 Alice E. Fischer October 9 and 2, 25 ... 2/34 Outline Integer Representations Binary Integers Integer Types Bit Operations Applying Bit Operations
... /34 CSCI 222: Intermediate Programming / C Chapter 5 Alice E. Fischer October 9 and 2, 25 ... 2/34 Outline Integer Representations Binary Integers Integer Types Bit Operations Applying Bit Operations
Analysing the Molva and Di Pietro Private RFID Authentication Scheme
 Proceedings - NN - RFIDSec08 Analysing the Molva and Di Pietro Private RFID Authentication Scheme Mate Soos INRIA Rhône-Alpes Abstract. The private RFID authentication scheme by Molva and Di Pietro uses
Proceedings - NN - RFIDSec08 Analysing the Molva and Di Pietro Private RFID Authentication Scheme Mate Soos INRIA Rhône-Alpes Abstract. The private RFID authentication scheme by Molva and Di Pietro uses
Efficient RFID authentication scheme for supply chain applications
 University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2010 Efficient RFID authentication scheme for supply chain applications
University of Wollongong Research Online Faculty of Informatics - Papers (Archive) Faculty of Engineering and Information Sciences 2010 Efficient RFID authentication scheme for supply chain applications
SIRKOM'Digital'Signage'Div.''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''MedeaWiz 'Sprite' High'Definition'Video'Player' User'Manual'
 . MedeaWiz Sprite HighDefinitionVideoPlayer UserManual FWversion20161229 Manualversion1.06 Notethatthismanualmaychangeperiodically Pleasegotowww.MedeaWiz.comforthelatestversion 0 P age . Table&of&Contents&
. MedeaWiz Sprite HighDefinitionVideoPlayer UserManual FWversion20161229 Manualversion1.06 Notethatthismanualmaychangeperiodically Pleasegotowww.MedeaWiz.comforthelatestversion 0 P age . Table&of&Contents&
DATA SHEET. article numbers P125-1b & P125-1g
 LC 16.2 TREND DATA SHEET article numbers P125-1b & P125-1g Pottery House, Pottery Road, Dun Laoghaire, Co. Dublin, Ireland. Tel: +353-1-2350279 Fax: +353-1-2350361 Am Gneisenauflöz 6, 66538 Neunkirchen,
LC 16.2 TREND DATA SHEET article numbers P125-1b & P125-1g Pottery House, Pottery Road, Dun Laoghaire, Co. Dublin, Ireland. Tel: +353-1-2350279 Fax: +353-1-2350361 Am Gneisenauflöz 6, 66538 Neunkirchen,
We are IntechOpen, the world s leading publisher of Open Access books Built by scientists, for scientists. International authors and editors
 We are IntechOpen, the world s leading publisher of Open Access books Built by scientists, for scientists 3,500 108,000 1.7 M Open access books available International authors and editors Downloads Our
We are IntechOpen, the world s leading publisher of Open Access books Built by scientists, for scientists 3,500 108,000 1.7 M Open access books available International authors and editors Downloads Our
Attacks on a Lightweight Mutual Authentication Protocol under EPC C-1 G-2 Standard
 Attacks on a Lightweight Mutual Authentication Protocol under EPC C-1 G-2 Standard Mohammad Habibi, Mahdi Alagheband, Mohammad Aref To cite this version: Mohammad Habibi, Mahdi Alagheband, Mohammad Aref.
Attacks on a Lightweight Mutual Authentication Protocol under EPC C-1 G-2 Standard Mohammad Habibi, Mahdi Alagheband, Mohammad Aref To cite this version: Mohammad Habibi, Mahdi Alagheband, Mohammad Aref.
Using the USB and Serial Interfaces
 Using the USB and Serial Interfaces PulsON 300 and 400 Series TIME DOMAIN Cummings Research Park 4955 Corporate Drive Suite 101 Huntsville, AL 35805 USA http://www.timedomain.com Tel: +1 256.922.9229 +1
Using the USB and Serial Interfaces PulsON 300 and 400 Series TIME DOMAIN Cummings Research Park 4955 Corporate Drive Suite 101 Huntsville, AL 35805 USA http://www.timedomain.com Tel: +1 256.922.9229 +1
Salsa20 security. Daniel J. Bernstein
 Salsa20 security Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago Chicago, IL 60607 7045 snuffle@box.cr.yp.to 1 Introduction
Salsa20 security Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago Chicago, IL 60607 7045 snuffle@box.cr.yp.to 1 Introduction
ANM071. Keypad decoding technique using TSC80251G1. 1. Description 2. TSC80251G Keyboard interrupt Power down mode
 Keypad decoding technique using TSC80251G1 by François Fosse Technical Marketing Engineer Temic France 1. Description This application note demonstrates the use of a matrix keypad including wake up from
Keypad decoding technique using TSC80251G1 by François Fosse Technical Marketing Engineer Temic France 1. Description This application note demonstrates the use of a matrix keypad including wake up from
A Specification for Rijndael, the AES Algorithm
 A Specification for Rijndael, the AES Algorithm 1. Notation and Conventions 1.1 Rijndael Inputs and Outputs The input, output and cipher key for Rijndael are sequences containing 128, 160, 192, 224 or
A Specification for Rijndael, the AES Algorithm 1. Notation and Conventions 1.1 Rijndael Inputs and Outputs The input, output and cipher key for Rijndael are sequences containing 128, 160, 192, 224 or
ECE251: Intro to Microprocessors Name: Solutions Mid Term Exam October 4, 2018
 ECE251: Intro to Microprocessors Name: Solutions Mid Term Exam October 4, 2018 (PRINT) Instructions: No calculators, books, or cell phones; do not communicate with any other student. One side of a single
ECE251: Intro to Microprocessors Name: Solutions Mid Term Exam October 4, 2018 (PRINT) Instructions: No calculators, books, or cell phones; do not communicate with any other student. One side of a single
RTX64. Supported Network Interface Cards
 RTX64 Supported Network Interface Cards 2016 IntervalZero, Inc. IZ-DOC-X64-0088-R31 November 2016 This document provides a listing of the NIC drivers that are provided with RTX64 for use with the RT-TCP/IP
RTX64 Supported Network Interface Cards 2016 IntervalZero, Inc. IZ-DOC-X64-0088-R31 November 2016 This document provides a listing of the NIC drivers that are provided with RTX64 for use with the RT-TCP/IP
Protocol Description. thanos ModBus. thanos SR ModBus
 Protocol Description thanos ModBus & thanos SR ModBus Thermokon Sensortechnik Gmb - www.thermokon.de - email@thermokon.de 1 Index of changes Revision Date Description A B C 25.7.211 First draft 12.9.211
Protocol Description thanos ModBus & thanos SR ModBus Thermokon Sensortechnik Gmb - www.thermokon.de - email@thermokon.de 1 Index of changes Revision Date Description A B C 25.7.211 First draft 12.9.211
HGLAP : Hierarchical Group-index based Lightweight Authentication Protocol for Distributed RFID system
 HGLAP : Hierarchical Group-index based Lightweight Authentication Protocol for Distributed RFID system JeaCheol Ha 1, HwanKoo Kim 1, JeaHoon Park 2, SangJae Moon 2, Juanma Gonzalez Nieto 3, and Colin Boyd
HGLAP : Hierarchical Group-index based Lightweight Authentication Protocol for Distributed RFID system JeaCheol Ha 1, HwanKoo Kim 1, JeaHoon Park 2, SangJae Moon 2, Juanma Gonzalez Nieto 3, and Colin Boyd
