Forskning inom datasäkerhet Tomas Olovsson
|
|
|
- Collin Wright
- 5 years ago
- Views:
Transcription
1 Forskning inom datasäkerhet Tomas Olovsson Facts and Figures Employees at department: 160 Faculty members: 75 PhD students: 70 Full time students: 1100 (360 GU) 120 courses at 20 programmes Thirty nationalities represented 1
2 Research Groups Algorithms Bioinformatics Computer Architecture Computer Graphics Communications and Computer Networks Computer Security Dependable Real-Time Systems Distributed Computing Embedded and Networked Processors Formal Methods Functional Programming Language Technology Programming Logic Software Engineering Telecommunication Theory VLSI Circuit Design Networks and Systems security group Wolfgang John Erland Jonsson Tomas Olovsson Philippas Tsigas Marina Papatriantafilou Magnus Almgren Elad Schiller Asrin Javaheri Farnaz Moradi Laleh Pirzadeh Pierre Kleberger Andreas Larsson Zhang Fu 2
3 Security Arena Lindholmen Forskning och Utveckling i TRIPLE HELIX-miljö Akademi Industri Samhälle European Network of Excellence in Managing Threats and Vulnerabilities in the Future Internet ANetwork of Excellence ( ) to work towards solutions and collaborate European level Poli. di Milano (IT) VrijeUniivesriteit (NL) Institute Eurecom(FR) IPP (Bulgaria) TU Vienna (Austria) Chalmers U (Sweden) and with international colleagues around the world Focus Research into malware & fraud, smart environments, and cyber attacks Develop a curriculum for system security, and Report and describe large threats in a yearly report. UEKAE (Turkey) FORTH ICS(Greece) 3
4 Security projects at Chalmers Quantitative modeling and evaluation of security Security and dependability modelling Intrusion Detection Systems Intelligent security logging and monitoring Programming language support for security Formal methods for programming languages Malicious Internet traffic (attacks, spam, ) Denial of Service mitigation techniques Secure sensor networks Decision support systems Safety and Security in transport systems Security Metrics and Modelling Erland Jonsson Laleh Pirzadeh (Vilhelm Verendel) TH SYS U N-U 4
5 What is the problem? Reliability: Own research field Deals with random events failing components, etc. Can with good precision predict how and when a system fails MTTF: Mean time to failure Security: No randomness in events Events are malicious The presence of just one vulnerability can be enough for an attacker Attacks can be tested off-line No measure for security. Certifications and standard compliance used instead System- related Security Metrics Metrics are decomposed into protective, behavioural and correctness: Aprotective metric describes the ability of a system to resist attacks during operation A behaviouralmetric describes to what extent the system delivers its service to its authorized users and denies service to non-authorized users Correctness describes how correct a system is wrt to some reference (very hard) 5
6 Network defence against spam Farnaz Moradi Tomas Olovsson Philippas Tsigas Why Do We Care About Spam? Today,asmuchas90%ofinbound isspam Morethan120billionspammessagesissentperday Estimatedcost ofspamin2007wasonorderof$100billion Symantec s State of spam monthly report Secure and Anti-Spam 6
7 What Is Our Goal? Traditional methods remove spam after it has been received Spam identification software requires large computational resources Goal: Provide network-based protection Stop spam as close to its source as possible To be implemented in small networked devices Method: Study spam characteristics Network-level data No inspection of contents should be needed Use social network techniques to find statistical differences Secure and Anti-Spam Small-world networks Clustering Social network: All other nodes can be reached by a small number of steps Possible to identify outliers, nodes with different clustering behavior. 7
8 Spam differs from Ham Differences are visible within minutes. Spamming nodes can then be identified! Many more characteristics are available and can be used. Misbehaving nodes reveal spammers (number of best friends) Degree distribution for Ham and Spam (i.e. frequency of number of friends) Ham follows a power law: C * k -γ Securing the Connected Car Project: SIGYN II (Vinnova) Volvo Cars, Chalmers, KnowIT, Viktoriainstitutet, SP, Semcon, Alkit Erland Jonsson Tomas Olovsson Pierre Kleberger Asrin Javaheri 8
9 Introductory Example Introductory Example Possible explanations for the crash Bad weather Bambi Too much to drink OR Perhaps a piece of malicious code? Road conditions 9
10 Modern Vehicles Contain computers Electronic control units (ECUs) Internal network used replaces all old cables Network of the size of an office! Why use computers and software? Easy to reproduce, update functionality Supports flexible, advanced functionality: ABS, ESP, Diagnostics and software updates App-store Securing the Connected Car A car today consists of networked computers And tomorrow it will be connected to the Internet... Complementing safety issues with security aspects 10
11 Examples of Services Remote diagnostics Read diagnostic trouble codes Determine what is wrong with the vehicle Control functionality (test hardware and software) Remote software update Install new software in an ECU Provide improved functionality Patch software (bugs) Can we wait 3 years for a patch? 11
12 Why remote softare updates? Volvo recalls 26,000 cars worldwide: Reason: Problems with the software controlling the fuel injection pump. It can under some circumstances render the car impossible to start. Affected models are Volvo S 80, S 60, XC 60, XC 70 and V 70 from 2008 to 2010, all with the T6 turbo engine. Source: Alltommotor.se This is not a Volvo specific problem. All vendors recall cars due to software and other problems. Risks and Consequences Execution of arbitrary code Successful impersonation of portal, intrusion to vehicle Issue arbitrary diagnostics requests or software Update ECU with modified software Disclosure of information Successful intrusion to portal, impersonation of vehicle Gain access to private data Denial of service Targeting portal, communication link or vehicle Cause software updates to fail, diagnostics to report incorrect values Prevent legitimate users from updating potentially vulnerable software 12
13 Summary: Current security projects Quantitative modeling and evaluation of security Security and dependability modelling Intrusion Detection Systems Intelligent security logging and monitoring Programming language support for security Formal methods for programming languages Malicious Internet traffic (attacks, spam, ) Denial of Service mitigation techniques Secure sensor networks Decision support systems Safety and Security in transport systems 13
Secure Intermodal Transport System. Communication and security projects 5/4/2012. Research projects
 Networks and Systems security group 2012 A European Network of Excellence in Managing Threats and Vulnerabilities in the Future Internet Network of Excellence (2010-2014) Work towards solutions and collaborate
Networks and Systems security group 2012 A European Network of Excellence in Managing Threats and Vulnerabilities in the Future Internet Network of Excellence (2010-2014) Work towards solutions and collaborate
Mitigating Cyber Attacks
 Mitigating Cyber Attacks Magnus Almgren Göteborg, 2010-11-17 Postdoc, finansierad av MSB 15 20 years ago Internet starting to reach a wider audience most people did not have emails computer security an
Mitigating Cyber Attacks Magnus Almgren Göteborg, 2010-11-17 Postdoc, finansierad av MSB 15 20 years ago Internet starting to reach a wider audience most people did not have emails computer security an
What the Stack? On Memory Exploitation and Protection in Resource Constrained Automotive Systems
 What the Stack? On Memory Exploitation and Protection in Resource Constrained Automotive Systems Aljoscha Lautenbach Magnus Almgren Tomas Olovsson Dept. of Computer Science and Engineering Chalmers University
What the Stack? On Memory Exploitation and Protection in Resource Constrained Automotive Systems Aljoscha Lautenbach Magnus Almgren Tomas Olovsson Dept. of Computer Science and Engineering Chalmers University
Cybersecurity Challenges for Connected and Automated Vehicles. Robert W. Heller, Ph.D. Program Director R&D, Southwest Research Institute
 Cybersecurity Challenges for Connected and Automated Vehicles Robert W. Heller, Ph.D. Program Director R&D, Southwest Research Institute Cars are becoming complex (and CAV is only part of it) 1965: No
Cybersecurity Challenges for Connected and Automated Vehicles Robert W. Heller, Ph.D. Program Director R&D, Southwest Research Institute Cars are becoming complex (and CAV is only part of it) 1965: No
Structural and Temporal Properties of and Spam Networks
 Technical Report no. 2011-18 Structural and Temporal Properties of E-mail and Spam Networks Farnaz Moradi Tomas Olovsson Philippas Tsigas Department of Computer Science and Engineering Chalmers University
Technical Report no. 2011-18 Structural and Temporal Properties of E-mail and Spam Networks Farnaz Moradi Tomas Olovsson Philippas Tsigas Department of Computer Science and Engineering Chalmers University
Security Policy (EN) v1.3
 Security Policy (EN) v1.3 Author: Erik Klein Langenhorst Date: Sept 21, 2017 Classificatie: 2 Intended for stakeholders only Security Policy (EN) v1.5 Pagina 1 van 9 Version History Version Date Name Changes
Security Policy (EN) v1.3 Author: Erik Klein Langenhorst Date: Sept 21, 2017 Classificatie: 2 Intended for stakeholders only Security Policy (EN) v1.5 Pagina 1 van 9 Version History Version Date Name Changes
Systemic Analyser in Network Threats
 Systemic Analyser in Network Threats www.project-saint.eu @saintprojecteu #saintprojecteu John M.A. Bothos jbothos@iit.demokritos.gr Integrated System Laboratory Institute of Informatics & Telecommunication
Systemic Analyser in Network Threats www.project-saint.eu @saintprojecteu #saintprojecteu John M.A. Bothos jbothos@iit.demokritos.gr Integrated System Laboratory Institute of Informatics & Telecommunication
Education Network Security
 Education Network Security RECOMMENDATIONS CHECKLIST Learn INSTITUTE Education Network Security Recommendations Checklist This checklist is designed to assist in a quick review of your K-12 district or
Education Network Security RECOMMENDATIONS CHECKLIST Learn INSTITUTE Education Network Security Recommendations Checklist This checklist is designed to assist in a quick review of your K-12 district or
Resilient Smart Grids
 Resilient Smart Grids André Teixeira Kaveh Paridari, Henrik Sandberg KTH Royal Institute of Technology, Sweden SPARKS 2nd Stakeholder Workshop Cork, Ireland March 25th, 2015 Legacy Distribution Grids Main
Resilient Smart Grids André Teixeira Kaveh Paridari, Henrik Sandberg KTH Royal Institute of Technology, Sweden SPARKS 2nd Stakeholder Workshop Cork, Ireland March 25th, 2015 Legacy Distribution Grids Main
Insider Threat Detection Including review of 2017 SolarWinds Federal Cybersecurity Survey
 Insider Threat Detection Including review of 2017 SolarWinds Federal Cybersecurity Survey CyberMaryland Conference 2017 Bob Andersen, Sr. Manager Federal Sales Engineering robert.andersen@solarwinds.com
Insider Threat Detection Including review of 2017 SolarWinds Federal Cybersecurity Survey CyberMaryland Conference 2017 Bob Andersen, Sr. Manager Federal Sales Engineering robert.andersen@solarwinds.com
Enhancing infrastructure cybersecurity in Europe Rossella Mattioli Secure Infrastructures and Services
 Enhancing infrastructure cybersecurity in Europe Rossella Mattioli Secure Infrastructures and Services European Union Agency for Network and Information Security Securing Europe s Information society 2
Enhancing infrastructure cybersecurity in Europe Rossella Mattioli Secure Infrastructures and Services European Union Agency for Network and Information Security Securing Europe s Information society 2
European Union Agency for Network and Information Security
 Critical Information Infrastructure Protection in the EU Evangelos Ouzounis Head of Secure Infrastructure and Services Regional Cybersecurity Forum Sofia, Bulgaria 29 th November 2016 European Union Agency
Critical Information Infrastructure Protection in the EU Evangelos Ouzounis Head of Secure Infrastructure and Services Regional Cybersecurity Forum Sofia, Bulgaria 29 th November 2016 European Union Agency
Most Common Security Threats (cont.)
 Most Common Security Threats (cont.) Denial of service (DoS) attack Distributed denial of service (DDoS) attack Insider attacks. Any examples? Poorly designed software What is a zero-day vulnerability?
Most Common Security Threats (cont.) Denial of service (DoS) attack Distributed denial of service (DDoS) attack Insider attacks. Any examples? Poorly designed software What is a zero-day vulnerability?
Hardening Attack Vectors to cars by Fuzzing
 Hardening Attack Vectors to cars by Fuzzing AESIN 2015 Ashley Benn, Regional Sales manager 29 th October, 2015 2015 Synopsys, Inc. 1 Today, there are more than 100m lines of code in cars 2015 Synopsys,
Hardening Attack Vectors to cars by Fuzzing AESIN 2015 Ashley Benn, Regional Sales manager 29 th October, 2015 2015 Synopsys, Inc. 1 Today, there are more than 100m lines of code in cars 2015 Synopsys,
Security Audit What Why
 What A systematic, measurable technical assessment of how the organization's security policy is employed at a specific site Physical configuration, environment, software, information handling processes,
What A systematic, measurable technical assessment of how the organization's security policy is employed at a specific site Physical configuration, environment, software, information handling processes,
Introduction: Distributed Cyberphysical systems with Electricilty Networks as example (& Course Outline)
 MasterClass on Data-driven Support for Cyberphysical systems DAT300, DIT615 Introduction: Distributed Cyberphysical systems with Electricilty Networks as example (& Course Outline) Networks and Systems
MasterClass on Data-driven Support for Cyberphysical systems DAT300, DIT615 Introduction: Distributed Cyberphysical systems with Electricilty Networks as example (& Course Outline) Networks and Systems
Copyright 2011 Trend Micro Inc.
 Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
accelerate your ambition Chris Jenkins
 accelerate your ambition Chris Jenkins Changing landscape of the Security Industry Chris Jenkins European GM Security Dimension Data Business relationships Geographic footprint Revenue USD 700+m 1 NTT
accelerate your ambition Chris Jenkins Changing landscape of the Security Industry Chris Jenkins European GM Security Dimension Data Business relationships Geographic footprint Revenue USD 700+m 1 NTT
Experimental Security Analysis of a Modern Automobile
 Experimental Security Analysis of a Modern Automobile Matthias Lange TU Berlin June 29th, 2010 Matthias Lange (TU Berlin) Experimental Security Analysis of a Modern Automobile June 29th, 2010 1 / 16 Paper
Experimental Security Analysis of a Modern Automobile Matthias Lange TU Berlin June 29th, 2010 Matthias Lange (TU Berlin) Experimental Security Analysis of a Modern Automobile June 29th, 2010 1 / 16 Paper
Securing the future of mobility
 Kaspersky Transportation System Security AVL Software and Functions Securing the future of mobility www.kaspersky.com #truecybersecurity Securing the future of mobility Connected car benefits The need
Kaspersky Transportation System Security AVL Software and Functions Securing the future of mobility www.kaspersky.com #truecybersecurity Securing the future of mobility Connected car benefits The need
Security
 Security +617 3222 2555 info@citec.com.au Security With enhanced intruder technologies, increasingly sophisticated attacks and advancing threats, your data has never been more susceptible to breaches from
Security +617 3222 2555 info@citec.com.au Security With enhanced intruder technologies, increasingly sophisticated attacks and advancing threats, your data has never been more susceptible to breaches from
IT-Security Challenges in the Internet of Things. Christian Graffer Product Manager Endian
 IT-Security Challenges in the Internet of Things Christian Graffer Product Manager Endian Who is Endian? Founded in 2003 at Bolzano, Italy, by a team of experienced network specialists and Linux enthusiasts
IT-Security Challenges in the Internet of Things Christian Graffer Product Manager Endian Who is Endian? Founded in 2003 at Bolzano, Italy, by a team of experienced network specialists and Linux enthusiasts
Symantec & Blue Coat Technical Update Webinar 29. Juni 2017
 Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Securing Dynamic Data Centers. Muhammad Wajahat Rajab, Pre-Sales Consultant Trend Micro, Pakistan &
 Securing Dynamic Data Centers Muhammad Wajahat Rajab, Pre-Sales Consultant Trend Micro, Pakistan & Afghanistan @WajahatRajab Modern Challenges By 2020, 60% of Digital Businesses will suffer Major Service
Securing Dynamic Data Centers Muhammad Wajahat Rajab, Pre-Sales Consultant Trend Micro, Pakistan & Afghanistan @WajahatRajab Modern Challenges By 2020, 60% of Digital Businesses will suffer Major Service
Network Security Monitoring: An Open Community Approach
 Network Security Monitoring: An Open Community Approach IUP- Information Assurance Day, 2011 Greg Porter 11/10/11 Agenda Introduction Current State NSM & Open Community Options Conclusion 2 Introduction
Network Security Monitoring: An Open Community Approach IUP- Information Assurance Day, 2011 Greg Porter 11/10/11 Agenda Introduction Current State NSM & Open Community Options Conclusion 2 Introduction
trend micro smart Protection suites
 solution brochure trend micro smart rotection suites Connected, layered security for complete protection Get smarter security that goes where your users go Your users are increasingly accessing corporate
solution brochure trend micro smart rotection suites Connected, layered security for complete protection Get smarter security that goes where your users go Your users are increasingly accessing corporate
The modern car has 100 million lines of code and over half of new vehicles will be connected by 2020.
 Automotive The modern car has 100 million lines of code and over half of new vehicles will be connected by 2020. Cars are becoming increasingly connected through a range of wireless networks The increased
Automotive The modern car has 100 million lines of code and over half of new vehicles will be connected by 2020. Cars are becoming increasingly connected through a range of wireless networks The increased
Delivering Integrated Cyber Defense for the Cloud Generation Darren Thomson
 Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
13th Florence Rail Forum: Cyber Security in Railways Systems. Immacolata Lamberti Andrea Pepato
 13th Florence Rail Forum: Cyber Security in Railways Systems Immacolata Lamberti Andrea Pepato November 25, 2016 Cyber Security context and Cyber Attacks trend Critical Infrastructures (CIs) are both physical
13th Florence Rail Forum: Cyber Security in Railways Systems Immacolata Lamberti Andrea Pepato November 25, 2016 Cyber Security context and Cyber Attacks trend Critical Infrastructures (CIs) are both physical
The Mimecast Security Risk Assessment Quarterly Report May 2017
 The Mimecast Email Security Risk Assessment Quarterly Report May 2017 The Mimecast Email Security Risk Assessment Quarterly Report May 2017 Many organizations think their current email security systems
The Mimecast Email Security Risk Assessment Quarterly Report May 2017 The Mimecast Email Security Risk Assessment Quarterly Report May 2017 Many organizations think their current email security systems
ACM Retreat - Today s Topics:
 ACM Retreat - Today s Topics: Phase II Cyber Risk Management Services - What s next? Policy Development External Vulnerability Assessment Phishing Assessment Security Awareness Notification Third Party
ACM Retreat - Today s Topics: Phase II Cyber Risk Management Services - What s next? Policy Development External Vulnerability Assessment Phishing Assessment Security Awareness Notification Third Party
Data Privacy in Your Own Backyard
 White paper Data Privacy in Your Own Backyard Staying Secure Under New GDPR Employee Internet Monitoring Rules www.proofpoint.com TABLE OF CONTENTS INTRODUCTION... 3 KEY GDPR PROVISIONS... 4 GDPR AND EMPLOYEE
White paper Data Privacy in Your Own Backyard Staying Secure Under New GDPR Employee Internet Monitoring Rules www.proofpoint.com TABLE OF CONTENTS INTRODUCTION... 3 KEY GDPR PROVISIONS... 4 GDPR AND EMPLOYEE
Security analysis and assessment of threats in European signalling systems?
 Security analysis and assessment of threats in European signalling systems? New Challenges in Railway Operations Dr. Thomas Störtkuhl, Dr. Kai Wollenweber TÜV SÜD Rail Copenhagen, 20 November 2014 Slide
Security analysis and assessment of threats in European signalling systems? New Challenges in Railway Operations Dr. Thomas Störtkuhl, Dr. Kai Wollenweber TÜV SÜD Rail Copenhagen, 20 November 2014 Slide
Juniper Vendor Security Requirements
 Juniper Vendor Security Requirements INTRODUCTION This document describes measures and processes that the Vendor shall, at a minimum, implement and maintain in order to protect Juniper Data against risks
Juniper Vendor Security Requirements INTRODUCTION This document describes measures and processes that the Vendor shall, at a minimum, implement and maintain in order to protect Juniper Data against risks
External Supplier Control Obligations. Cyber Security
 External Supplier Control Obligations Cyber Security Control Title Control Description Why this is important 1. Cyber Security Governance The Supplier must have cyber risk governance processes in place
External Supplier Control Obligations Cyber Security Control Title Control Description Why this is important 1. Cyber Security Governance The Supplier must have cyber risk governance processes in place
Wayward Wi-Fi. How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk
 Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Synology Security Whitepaper
 Synology Security Whitepaper 1 Table of Contents Introduction 3 Security Policy 4 DiskStation Manager Life Cycle Severity Ratings Standards Security Program 10 Product Security Incident Response Team Bounty
Synology Security Whitepaper 1 Table of Contents Introduction 3 Security Policy 4 DiskStation Manager Life Cycle Severity Ratings Standards Security Program 10 Product Security Incident Response Team Bounty
Bradford J. Willke. 19 September 2007
 A Critical Information Infrastructure Protection Approach to Multinational Cyber Security Events Bradford J. Willke 19 September 2007 Overview A framework for national Critical Information Infrastructure
A Critical Information Infrastructure Protection Approach to Multinational Cyber Security Events Bradford J. Willke 19 September 2007 Overview A framework for national Critical Information Infrastructure
Critical Systems. Objectives. Topics covered. Critical Systems. System dependability. Importance of dependability
 Objectives Critical Systems To explain what is meant by a critical system where system failure can have severe human or economic consequence. To explain four dimensions of dependability - availability,
Objectives Critical Systems To explain what is meant by a critical system where system failure can have severe human or economic consequence. To explain four dimensions of dependability - availability,
Locking down a Hitachi ID Suite server
 Locking down a Hitachi ID Suite server 2016 Hitachi ID Systems, Inc. All rights reserved. Organizations deploying Hitachi ID Identity and Access Management Suite need to understand how to secure its runtime
Locking down a Hitachi ID Suite server 2016 Hitachi ID Systems, Inc. All rights reserved. Organizations deploying Hitachi ID Identity and Access Management Suite need to understand how to secure its runtime
Advanced Threat Defense Certification Testing Report. Symantec Corporation Symantec Advanced Threat Protection
 Advanced Threat Defense Certification Testing Report Symantec Advanced Threat Protection ICSA Labs Advanced Threat Defense December 8, 2015 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Symantec Advanced Threat Protection ICSA Labs Advanced Threat Defense December 8, 2015 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Risk-based design for automotive networks. Eric Evenchik, Linklayer labs & Motivum.io Stefano Zanero, Politecnico di Milano & Motivum.
 Risk-based design for automotive networks Eric Evenchik, Linklayer labs & Motivum.io Stefano Zanero, Politecnico di Milano & Motivum.io Who are we Eric Evenchick Stefano Zanero Linklayer Labs (Toronto,
Risk-based design for automotive networks Eric Evenchik, Linklayer labs & Motivum.io Stefano Zanero, Politecnico di Milano & Motivum.io Who are we Eric Evenchick Stefano Zanero Linklayer Labs (Toronto,
Cyber Security for Process Control Systems ABB's view
 Kaspersky ICS Cybersecurity 2017, 2017-09-28 Cyber Security for Process Control Systems ABB's view Tomas Lindström, Cyber Security Manager, ABB Control Technologies Agenda Cyber security for process control
Kaspersky ICS Cybersecurity 2017, 2017-09-28 Cyber Security for Process Control Systems ABB's view Tomas Lindström, Cyber Security Manager, ABB Control Technologies Agenda Cyber security for process control
Vulnerability Management Policy
 Vulnerability Management Policy Document Type: Policy (PLCY) Endorsed By: Information Technology Policy Committee Date: 4/29/2011 Promulgated By: Chancellor Herzog Date: 6/16/2011 I. Introduction IT resources
Vulnerability Management Policy Document Type: Policy (PLCY) Endorsed By: Information Technology Policy Committee Date: 4/29/2011 Promulgated By: Chancellor Herzog Date: 6/16/2011 I. Introduction IT resources
Symantec Ransomware Protection
 Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
Unit 3 Cyber security
 2016 Suite Cambridge TECHNICALS LEVEL 3 IT Unit 3 Cyber security Y/507/5001 Guided learning hours: 60 Version 3 - revised September 2016 ocr.org.uk/it LEVEL 3 UNIT 3: Cyber security Y/507/5001 Guided learning
2016 Suite Cambridge TECHNICALS LEVEL 3 IT Unit 3 Cyber security Y/507/5001 Guided learning hours: 60 Version 3 - revised September 2016 ocr.org.uk/it LEVEL 3 UNIT 3: Cyber security Y/507/5001 Guided learning
The Road to Industry 4.0
 The Road to Industry 4.0 Secure remote access and active cyber protection for industrial machinery Hamburg, May 22, 2017 Fabian Bahr G+D Group Business Units and Divisions G+D Mobile Security Financial
The Road to Industry 4.0 Secure remote access and active cyber protection for industrial machinery Hamburg, May 22, 2017 Fabian Bahr G+D Group Business Units and Divisions G+D Mobile Security Financial
cybersecurity in Europe Rossella Mattioli Secure Infrastructures and Services
 Enhancing infrastructure cybersecurity in Europe Rossella Mattioli Secure Infrastructures and Services European Union Agency for Network and Information Security Securing Europe s Information society 2
Enhancing infrastructure cybersecurity in Europe Rossella Mattioli Secure Infrastructures and Services European Union Agency for Network and Information Security Securing Europe s Information society 2
The Credential Phishing Handbook. Why It Still Works and 4 Steps to Prevent It
 The Credential Phishing Handbook Why It Still Works and 4 Steps to Prevent It Introduction Phishing is more than 20 years old, but still represents more than 90% of targeted attacks. The reason is simple:
The Credential Phishing Handbook Why It Still Works and 4 Steps to Prevent It Introduction Phishing is more than 20 years old, but still represents more than 90% of targeted attacks. The reason is simple:
Threat Modeling. Bart De Win Secure Application Development Course, Credits to
 Threat Modeling Bart De Win bart.dewin@ascure.com Secure Application Development Course, 2009 Credits to Frank Piessens (KUL) for the slides 2 1 Overview Introduction Key Concepts Threats, Vulnerabilities,
Threat Modeling Bart De Win bart.dewin@ascure.com Secure Application Development Course, 2009 Credits to Frank Piessens (KUL) for the slides 2 1 Overview Introduction Key Concepts Threats, Vulnerabilities,
Cyber security tips and self-assessment for business
 Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
EC-Council Certified Incident Handler v2. Prepare to Handle and Respond to Security Incidents EC-COUNCIL CERTIFIED INCIDENT HANDLER 1
 EC-Council Certified Incident Handler v2 Prepare to Handle and Respond to Security Incidents EC-COUNCIL CERTIFIED INCIDENT HANDLER 1 THE CRITICAL NATURE OF INCIDENT HANDLING READINESS An organized and
EC-Council Certified Incident Handler v2 Prepare to Handle and Respond to Security Incidents EC-COUNCIL CERTIFIED INCIDENT HANDLER 1 THE CRITICAL NATURE OF INCIDENT HANDLING READINESS An organized and
CIS 5373 Systems Security
 CIS 5373 Systems Security Topic 1: Introduction to Systems Security Endadul Hoque 1 Why should you care? Security impacts our day-to-day life Become a security-aware user Make safe decisions Become a security-aware
CIS 5373 Systems Security Topic 1: Introduction to Systems Security Endadul Hoque 1 Why should you care? Security impacts our day-to-day life Become a security-aware user Make safe decisions Become a security-aware
Authentication with Privacy for Connected Cars - A research perspective -
 Authentication with Privacy for Connected Cars - A research perspective - Mark Manulis Surrey Centre for Cyber Security, Deputy-Director Department of Computer Science University of Surrey sccs.surrey.ac.uk
Authentication with Privacy for Connected Cars - A research perspective - Mark Manulis Surrey Centre for Cyber Security, Deputy-Director Department of Computer Science University of Surrey sccs.surrey.ac.uk
Presenter Jakob Drescher. Industry. Measures used to protect assets against computer threats. Covers both intentional and unintentional attacks.
 Presenter Jakob Drescher Industry Cyber Security 1 Cyber Security? Measures used to protect assets against computer threats. Covers both intentional and unintentional attacks. Malware or network traffic
Presenter Jakob Drescher Industry Cyber Security 1 Cyber Security? Measures used to protect assets against computer threats. Covers both intentional and unintentional attacks. Malware or network traffic
90% 191 Security Best Practices. Blades. 52 Regulatory Requirements. Compliance Report PCI DSS 2.0. related to this regulation
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on April 16, 2018 15:41 PM O verview 1 90% Compliance About PCI DSS 2.0 PCI-DSS is a legal obligation mandated not by government
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on April 16, 2018 15:41 PM O verview 1 90% Compliance About PCI DSS 2.0 PCI-DSS is a legal obligation mandated not by government
Security in a Converging IT/OT World
 Security in a Converging IT/OT World Introduction Around the winter solstice, darkness comes early to the citizens of Ukraine. On December 23, 2015, it came a little earlier than normal. In mid-afternoon,
Security in a Converging IT/OT World Introduction Around the winter solstice, darkness comes early to the citizens of Ukraine. On December 23, 2015, it came a little earlier than normal. In mid-afternoon,
Securing Information Systems
 Chapter 7 Securing Information Systems 7.1 2007 by Prentice Hall STUDENT OBJECTIVES Analyze why information systems need special protection from destruction, error, and abuse. Assess the business value
Chapter 7 Securing Information Systems 7.1 2007 by Prentice Hall STUDENT OBJECTIVES Analyze why information systems need special protection from destruction, error, and abuse. Assess the business value
Interactive Remote Access FERC Remote Access Study Compliance Workshop October 27, Eric Weston Compliance Auditor Cyber Security.
 Interactive Remote Access Compliance Workshop October 27, 2016 Eric Weston Compliance Auditor Cyber Security 2 Agenda Interactive Remote Access Overview Review of Use Cases and Strategy 1 Interactive Remote
Interactive Remote Access Compliance Workshop October 27, 2016 Eric Weston Compliance Auditor Cyber Security 2 Agenda Interactive Remote Access Overview Review of Use Cases and Strategy 1 Interactive Remote
E-guide Getting your CISSP Certification
 Getting your CISSP Certification Intro to the 10 CISSP domains of the Common Body of Knowledge : The Security Professional (CISSP) is an information security certification that was developed by the International
Getting your CISSP Certification Intro to the 10 CISSP domains of the Common Body of Knowledge : The Security Professional (CISSP) is an information security certification that was developed by the International
MANRS. Mutually Agreed Norms for Routing Security. Jan Žorž
 MANRS Mutually Agreed Norms for Routing Security Jan Žorž The Problem A Routing Security Overview 2 No Day Without an Incident http://bgpstream.com/ 3 Routing Incidents Cause Real World
MANRS Mutually Agreed Norms for Routing Security Jan Žorž The Problem A Routing Security Overview 2 No Day Without an Incident http://bgpstream.com/ 3 Routing Incidents Cause Real World
Threat analysis. Tuomas Aura CS-C3130 Information security. Aalto University, autumn 2017
 Threat analysis Tuomas Aura CS-C3130 Information security Aalto University, autumn 2017 Outline What is security Threat analysis Threat modeling example Systematic threat modeling 2 WHAT IS SECURITY 3
Threat analysis Tuomas Aura CS-C3130 Information security Aalto University, autumn 2017 Outline What is security Threat analysis Threat modeling example Systematic threat modeling 2 WHAT IS SECURITY 3
An Operational Cyber Security Perspective on Emerging Challenges. Michael Misumi CIO Johns Hopkins University Applied Physics Lab (JHU/APL)
 An Operational Cyber Security Perspective on Emerging Challenges Michael Misumi CIO Johns Hopkins University Applied Physics Lab (JHU/APL) Johns Hopkins University Applied Physics Lab (JHU/APL) University
An Operational Cyber Security Perspective on Emerging Challenges Michael Misumi CIO Johns Hopkins University Applied Physics Lab (JHU/APL) Johns Hopkins University Applied Physics Lab (JHU/APL) University
Development of Intrusion Detection System for vehicle CAN bus cyber security
 Development of Intrusion Detection System for vehicle CAN bus cyber security Anastasia Cornelio, Elisa Bragaglia, Cosimo Senni, Walter Nesci Technology Innovation - SSEC 14 Workshop Automotive SPIN Italia
Development of Intrusion Detection System for vehicle CAN bus cyber security Anastasia Cornelio, Elisa Bragaglia, Cosimo Senni, Walter Nesci Technology Innovation - SSEC 14 Workshop Automotive SPIN Italia
Machine-Powered Learning for People-Centered Security
 White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
Defining cybersecurity.
 PREPARING FOR TOMORROW S THREATS 28 September 2016 Andrew Facchini Presales & Product Manager +47 459 07 330 andrew@mnemonic.no Defining cybersecurity. WHO IS MNEMONIC? Founded in 2000 110+ security specialists
PREPARING FOR TOMORROW S THREATS 28 September 2016 Andrew Facchini Presales & Product Manager +47 459 07 330 andrew@mnemonic.no Defining cybersecurity. WHO IS MNEMONIC? Founded in 2000 110+ security specialists
Monthly Cyber Threat Briefing
 Monthly Cyber Threat Briefing January 2016 1 Presenters David Link, PM Risk and Vulnerability Assessments, NCATS Ed Cabrera: VP Cybersecurity Strategy, Trend Micro Jason Trost: VP Threat Research, ThreatStream
Monthly Cyber Threat Briefing January 2016 1 Presenters David Link, PM Risk and Vulnerability Assessments, NCATS Ed Cabrera: VP Cybersecurity Strategy, Trend Micro Jason Trost: VP Threat Research, ThreatStream
IC32E - Pre-Instructional Survey
 Name: Date: 1. What is the primary function of a firewall? a. Block all internet traffic b. Detect network intrusions c. Filter network traffic d. Authenticate users 2. A system that monitors traffic into
Name: Date: 1. What is the primary function of a firewall? a. Block all internet traffic b. Detect network intrusions c. Filter network traffic d. Authenticate users 2. A system that monitors traffic into
Future Challenges and Changes in Industrial Cybersecurity. Sid Snitkin VP Cybersecurity Services ARC Advisory Group
 Future Challenges and Changes in Industrial Cybersecurity Sid Snitkin VP Cybersecurity Services ARC Advisory Group Srsnitkin@ARCweb.com Agenda Industrial Cybersecurity Today Scope, Assumptions and Strategies
Future Challenges and Changes in Industrial Cybersecurity Sid Snitkin VP Cybersecurity Services ARC Advisory Group Srsnitkin@ARCweb.com Agenda Industrial Cybersecurity Today Scope, Assumptions and Strategies
HOLY ANGEL UNIVERSITY COLLEGE OF INFORMATION AND COMMUNICATIONS TECHNOLOGY CYBER SECURITY COURSE SYLLABUS
 HOLY ANGEL UNIVERSITY LLEGE OF INFORMATION AND MMUNICATIONS TECHNOLOGY CYBER SECURITY URSE SYLLABUS Course Code : 6CSEC Prerequisite : 6MPRO2L Course Credit : 3 Units (2 hours LEC,3 hours LAB) Year Level:
HOLY ANGEL UNIVERSITY LLEGE OF INFORMATION AND MMUNICATIONS TECHNOLOGY CYBER SECURITY URSE SYLLABUS Course Code : 6CSEC Prerequisite : 6MPRO2L Course Credit : 3 Units (2 hours LEC,3 hours LAB) Year Level:
Data Communication. Chapter # 5: Networking Threats. By: William Stalling
 Data Communication Chapter # 5: By: Networking Threats William Stalling Risk of Network Intrusion Whether wired or wireless, computer networks are quickly becoming essential to everyday activities. Individuals
Data Communication Chapter # 5: By: Networking Threats William Stalling Risk of Network Intrusion Whether wired or wireless, computer networks are quickly becoming essential to everyday activities. Individuals
Intrusion prevention systems are an important part of protecting any organisation from constantly developing threats.
 Network IPS Overview Intrusion prevention systems are an important part of protecting any organisation from constantly developing threats. By using protocol recognition, identification, and traffic analysis
Network IPS Overview Intrusion prevention systems are an important part of protecting any organisation from constantly developing threats. By using protocol recognition, identification, and traffic analysis
ACS / Computer Security And Privacy. Fall 2018 Mid-Term Review
 ACS-3921-001/4921-001 Computer Security And Privacy Fall 2018 Mid-Term Review ACS-3921/4921-001 Slides Used In The Course A note on the use of these slides: These slides has been adopted and/or modified
ACS-3921-001/4921-001 Computer Security And Privacy Fall 2018 Mid-Term Review ACS-3921/4921-001 Slides Used In The Course A note on the use of these slides: These slides has been adopted and/or modified
Data Security and Privacy : Compliance to Stewardship. Jignesh Patel Solution Consultant,Oracle
 Data Security and Privacy : Compliance to Stewardship Jignesh Patel Solution Consultant,Oracle Agenda Connected Government Security Threats and Risks Defense In Depth Approach Summary Connected Government
Data Security and Privacy : Compliance to Stewardship Jignesh Patel Solution Consultant,Oracle Agenda Connected Government Security Threats and Risks Defense In Depth Approach Summary Connected Government
IT Security Update on Practical Risk Mitigation Strategies
 IT Security Update on Practical Risk Mitigation Strategies Bonnie Bastow, CIA, CISA, CISM Director May 2016 This material was used by Elliott Davis Decosimo during an oral presentation; it is not a complete
IT Security Update on Practical Risk Mitigation Strategies Bonnie Bastow, CIA, CISA, CISM Director May 2016 This material was used by Elliott Davis Decosimo during an oral presentation; it is not a complete
Enhancing the cyber security &
 Enhancing the cyber security & resilience of transport infrastructure in Europe European Union Agency for Network and Information Security Securing Europe s Information society 2 Positioning ENISA activities
Enhancing the cyber security & resilience of transport infrastructure in Europe European Union Agency for Network and Information Security Securing Europe s Information society 2 Positioning ENISA activities
AT&T Endpoint Security
 AT&T Endpoint Security November 2016 Security Drivers Market Drivers Online business 24 x 7, Always on Globalization Virtual Enterprise Business Process / IT Alignment Financial Drivers CapEx / OpEx Reduction
AT&T Endpoint Security November 2016 Security Drivers Market Drivers Online business 24 x 7, Always on Globalization Virtual Enterprise Business Process / IT Alignment Financial Drivers CapEx / OpEx Reduction
Top 10 Global Threat Rank by Source
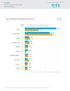 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Customer Agreements, Policies & Service Disclosures for PINE TELEPHONE COMPANY
 Customer Agreements, Policies & Service Disclosures for PINE TELEPHONE COMPANY The FCC requires that PINE TELEPHONE COMPANY INC. (or PINE TELEPHONE) and all providers of Broadband Internet Access services
Customer Agreements, Policies & Service Disclosures for PINE TELEPHONE COMPANY The FCC requires that PINE TELEPHONE COMPANY INC. (or PINE TELEPHONE) and all providers of Broadband Internet Access services
Information Security Controls Policy
 Information Security Controls Policy Classification: Policy Version Number: 1-00 Status: Published Approved by (Board): University Leadership Team Approval Date: 30 January 2018 Effective from: 30 January
Information Security Controls Policy Classification: Policy Version Number: 1-00 Status: Published Approved by (Board): University Leadership Team Approval Date: 30 January 2018 Effective from: 30 January
SIMPLIFYING THE CAR. Helix chassis. Helix chassis. Helix chassis WIND RIVER HELIX CHASSIS WIND RIVER HELIX DRIVE WIND RIVER HELIX CARSYNC
 W I N D R I V E R H E L I X C H A S S I S SIMPLIFYING THE WIND RIVER HELIX CHASSIS Helix Chassis brings together software, technologies, tools, and services to help automotive manufacturers unify, simplify,
W I N D R I V E R H E L I X C H A S S I S SIMPLIFYING THE WIND RIVER HELIX CHASSIS Helix Chassis brings together software, technologies, tools, and services to help automotive manufacturers unify, simplify,
Define information security Define security as process, not point product.
 CSA 223 Network and Web Security Chapter One What is information security. Look at: Define information security Define security as process, not point product. Define information security Information is
CSA 223 Network and Web Security Chapter One What is information security. Look at: Define information security Define security as process, not point product. Define information security Information is
Keep the Door Open for Users and Closed to Hackers
 Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
IT Security Update on Practical Risk Mitigation Strategies
 IT Security Update on Practical Risk Mitigation Strategies Bonnie Bastow, CIA, CISA, CISM Director, Risk Advisory Services, IT Audit & Security April 2016 Elliott Davis Decosimo, LLC Elliott Davis Decosimo,
IT Security Update on Practical Risk Mitigation Strategies Bonnie Bastow, CIA, CISA, CISM Director, Risk Advisory Services, IT Audit & Security April 2016 Elliott Davis Decosimo, LLC Elliott Davis Decosimo,
IBM Security Network Protection Solutions
 Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
Consumerization. Copyright 2014 Trend Micro Inc. IT Work Load
 Complete User Protection Consumerization IT Work Load 2 Then... File/Folder & Removable Media Email & Messaging Web Access Employees IT Admin 3 Now! File/Folder & Removable Media Email & Messaging Web
Complete User Protection Consumerization IT Work Load 2 Then... File/Folder & Removable Media Email & Messaging Web Access Employees IT Admin 3 Now! File/Folder & Removable Media Email & Messaging Web
Security Information & Event Management (SIEM)
 Security Information & Event Management (SIEM) Datasheet SIEM in a nutshell The variety of cyber-attacks is extraordinarily large. Phishing, DDoS attacks in combination with ransomware demanding bitcoins
Security Information & Event Management (SIEM) Datasheet SIEM in a nutshell The variety of cyber-attacks is extraordinarily large. Phishing, DDoS attacks in combination with ransomware demanding bitcoins
IC B01: Internet Security Threat Report: How to Stay Protected
 IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
Intelligent and Secure Network
 Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
U.S. FLEET CYBER COMMAND U.S. TENTH FLEET Managing Cybersecurity Risk
 U.S. FLEET CYBER COMMAND U.S. TENTH FLEET Managing Cybersecurity Risk Neal Miller, Navy Authorizing Official December 13, 2016 UNCLASSIFIED 1 Some Inconvenient Truths The bad guys and gals still only work
U.S. FLEET CYBER COMMAND U.S. TENTH FLEET Managing Cybersecurity Risk Neal Miller, Navy Authorizing Official December 13, 2016 UNCLASSIFIED 1 Some Inconvenient Truths The bad guys and gals still only work
Security+ Guide to Network Security Fundamentals, Fourth Edition. Chapter 1 Introduction to Security
 Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 1 Introduction to Security Objectives Describe the challenges of securing information Define information security and explain why
Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 1 Introduction to Security Objectives Describe the challenges of securing information Define information security and explain why
CoreMax Consulting s Cyber Security Roadmap
 CoreMax Consulting s Cyber Security Roadmap What is a Cyber Security Roadmap? The CoreMax consulting cyber security unit has created a simple process to access the unique needs of each client and allows
CoreMax Consulting s Cyber Security Roadmap What is a Cyber Security Roadmap? The CoreMax consulting cyber security unit has created a simple process to access the unique needs of each client and allows
Supply Chain Integrity and Security Assurance for ICT. Mats Nilsson
 Supply Chain Integrity and Security Assurance for ICT Mats Nilsson The starting point 2 B Internet users 85% Population coverage 5+ B Mobile subscriptions 10 years of Daily upload E-Books surpassing Print
Supply Chain Integrity and Security Assurance for ICT Mats Nilsson The starting point 2 B Internet users 85% Population coverage 5+ B Mobile subscriptions 10 years of Daily upload E-Books surpassing Print
MASP Chapter on Safety and Security
 MASP Chapter on Safety and Security Daniel Watzenig Graz, Austria https://artemis.eu MASP Chapter on Safety & Security Daniel Watzenig daniel.watzenig@v2c2.at Francois Tuot francois.tuot@gemalto.com Antonio
MASP Chapter on Safety and Security Daniel Watzenig Graz, Austria https://artemis.eu MASP Chapter on Safety & Security Daniel Watzenig daniel.watzenig@v2c2.at Francois Tuot francois.tuot@gemalto.com Antonio
Advanced Threat Defense Certification Testing Report. Trend Micro Incorporated Trend Micro Deep Discovery Inspector
 Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Security Solutions. Overview. Business Needs
 Security Solutions Overview Information security is not a one time event. The dynamic nature of computer networks mandates that examining and ensuring information security be a constant and vigilant effort.
Security Solutions Overview Information security is not a one time event. The dynamic nature of computer networks mandates that examining and ensuring information security be a constant and vigilant effort.
Cyber Security. February 13, 2018 (webinar) February 15, 2018 (in-person)
 Cyber Security Presenters: - Brian Everest, Chief Technology Officer, Starport Managed Services - Susan Pawelek, Accountant, Compliance and Registrant Regulation February 13, 2018 (webinar) February 15,
Cyber Security Presenters: - Brian Everest, Chief Technology Officer, Starport Managed Services - Susan Pawelek, Accountant, Compliance and Registrant Regulation February 13, 2018 (webinar) February 15,
Troubleshooting and Cyber Protection Josh Wheeler
 May 4, 2016 Troubleshooting and Cyber Protection Josh Wheeler Network Security Network Security Risks Video Network Security Risks Article Network Security Risks Data stealing or disruption of network
May 4, 2016 Troubleshooting and Cyber Protection Josh Wheeler Network Security Network Security Risks Video Network Security Risks Article Network Security Risks Data stealing or disruption of network
The Top 6 WAF Essentials to Achieve Application Security Efficacy
 The Top 6 WAF Essentials to Achieve Application Security Efficacy Introduction One of the biggest challenges IT and security leaders face today is reducing business risk while ensuring ease of use and
The Top 6 WAF Essentials to Achieve Application Security Efficacy Introduction One of the biggest challenges IT and security leaders face today is reducing business risk while ensuring ease of use and
Overview of Akamai s Personal Data Processing Activities and Role
 Overview of Akamai s Personal Data Processing Activities and Role Last Updated: April 2018 This document is maintained by the Akamai Global Data Protection Office 1 Introduction Akamai is a global leader
Overview of Akamai s Personal Data Processing Activities and Role Last Updated: April 2018 This document is maintained by the Akamai Global Data Protection Office 1 Introduction Akamai is a global leader
