Building secure devices on the intelligent edge with Azure Sphere. Paul Foster, Microsoft Dr Hassan Harb, E.On
|
|
|
- Marcus Foster
- 5 years ago
- Views:
Transcription
1 Building secure devices on the intelligent edge with Azure Sphere Paul Foster, Microsoft Dr Hassan Harb, E.On
2 Microcontrollers (MCUs) low-cost, single chip computers 9 BILLION new MCU devices built and deployed every year
3 Radio 2.4GHz WiFi MCU 192Mhz Cortex-M4 256KB SRAM 1MB NOR FLASH GPIO, I2C, I2S, etc. RTOS (no kernel)
4 Connected devices create profoundly better customer experiences. How does a consumer know the compressor in their fridge needs to be replaced? Option 1 Melted ice cream Option 2 Predictive maintenance
5 Mirai Botnet attack Everyday devices are used to launch an attack that takes down the internet for a day
6 SECURITY IS FOUNDATIONAL It must be built in from the beginning.
7 The 7 properties of highly secured devices Hardware Root of Trust Defense in Depth Small Trusted Computing Base Dynamic Compartments Certificate-Based Authentication Failure Reporting Renewable Security
8 Some properties depend only on hardware support Hardware Root of Trust Hardware Root of Trust Unforgeable cryptographic keys generated and protected by hardware Hardware to protect Device Identity Hardware to Secure Boot Hardware to attest System Integrity
9 Some properties depend on hardware and software Defense in Depth Dynamic Compartments Small Trusted Computing Base Dynamic Compartments Internal barriers limit the reach of any single failure Hardware to Create Barriers Software to Create Compartments
10 Some properties depend on hardware, software and cloud Certificate-Based Authentication Failure Reporting Renewable Security Renewable Security Device security renewed to overcome evolving threats Cloud to Provide Updates Software to Apply Updates Hardware to Prevent Rollbacks
11 Azure Sphere is an end-to-end solution for securing MCU powered devices The Azure Sphere OS with ongoing updates creates a Microsoft-secured software platform Azure Sphere certified MCUs, from our silicon partners, with built-in Microsoft hardware root of trust. The Azure Sphere Security Service guards every Azure Sphere device. It brokers trust, detects emerging threats, and renews device security.
12 Azure Sphere certified MCUs create a secured root of trust for connected, intelligence edge devices C O N N E C T E D with built-in networking S E C U R E D with built-in Microsoft silicon security technology including the Pluton Security Subsystem C R O S S O V E R Cortex-A processing power brought to MCUs for the first time Microsoft Pluton Security Subsystem Firewall ARM Cortex-A optimized for low power FLASH 4MB Firewall SRAM 4MB Network Connection WiFi in first chips Firewall ARM Cortex-M for real time processing C R O S S O V E R Cortex-A processing power brought to MCUs for the first time Firewall Firewall Multiplexed I/O Firewall GPIO PWM TDM I2S UART I2C SPI ADC
13 Azure Sphere MCUs create a secured root of trust for connected, intelligence edge devices Pluton features implemented in silicon include A hardware root of trust that -accelerates common cryptographic operations (ECC and AES) -generates public/private keypairs -implements secure boot (via ECDSA) A dedicated core and memory (TCM) that -resists side-channel attacks that focus on a single core A true random number generator that -defends against low-entropy attacks Measured boot and remote attestation that -uses a digest accumulator register and nonce register
14 Our Silicon Partners
15 The Azure Sphere OS is optimized for IoT, security, and agility Secure Application Containers Compartmentalize code for agility, robustness & security On-chip Cloud Services Provide update, authentication, and connectivity Custom Linux kernel Empowers agile silicon evolution and reuse of code Security Monitor Guards integrity and access to critical resources OS Layer 4 OS Layer 3 OS Layer 2 OS Layer 1 Azure Sphere OS Architecture App Containers for POSIX (on Cortex-A) On-chip Cloud Services HLOS Kernel Security Monitor App Containers for I/O (on Cortex-Ms) Hardware Azure Sphere MCUs
16 SIDE BAR Application platform Cortex-A App runs in Normal World user mode GPIO, UART and other interfaces Communicate with Azure IoT Hub or other clouds Microsoft provides all but app All signed by the Microsoft CA App updates delivered by Microsoft secure pipeline Sideloading during development Manifest file defines capabilities
17 The Azure Sphere Security Service connects and protects every Azure Sphere device OS updates from Microsoft Your app updates Protects your devices and your customers with certificate-based authentication of all communication Azure Detects emerging security threats through automated processing of on-device failures Responds to threats with fully automated on-device updates of OS App and Allows for easy deployment of software OS updates to Azure Sphere powered devices Remote attestation & cert based authentication Azure Sphere Security Service Online app and OS failure reports App data and telemetry Other cloud or on-prem infrastructure App data and telemetry
18 SIDE BAR Azure Sphere scenario Azure DPS
19 Modernize MCU development with Azure Sphere and Visual Studio Simplify development Focus your device development effort on the value you want to create Streamline debugging Experience interactive, context-aware debugging across device and cloud Collaborate across your team Apply tool-assisted collaboration across your entire development organization
20 Demo
21 SIDE BAR Deployment basics SKUs Components and applications Image and Image sets Feeds Device groups
22 Three components. One low price. No subscription required. An Azure Sphere certified MCU The Azure Sphere OS with ongoing on-device OS updates The Azure Sphere Security Service with ongoing on-device security updates
23 en to any MCU manufacturer are licensing our Pluton security subsystem royalty e for use in any chip* Azure Sphere is open en to any innovation U manufacturers are free to innovate with our L d OSS Linux kernel code base en to any cloud ure Sphere devices are free to connect to Azure or any er cloud, proprietary or public for application data
24 Home Energy Management System Hassan Harb #FutureDecoded, London, November 1 st
25 E.ON at a glance 31m customers ~500k connected energy assets ~1m km power grids
26 Trends in the energy sector Decarbonization Decentralization Electrification
27 Trends in the energy sector Decarbonization Decentralization Electrification IoT
28 Internet of energy: Security risk Decarbonization Decentralization Electrification IoT
29 in Mtoe Challenges: Increasing electricity consumption Industry Residential Residential (extrap.) Based on Key world energy statistics 2018 OECD/IEA 2018, Licence: as modified by E.ON Solutions GmbH
30 Challenges: Discrepancy between local generation and consumption PV generation Demand t
31
32 HEMS on azure IoT sphere HEMS edge intelligence
33 HEMS in action: Increase self-sufficiency through load shifting Storage management PV generation Demand modification Demand t
34 Thank you!
35 Get started with Azure Sphere today. Public Preview availability Azure Sphere OS Azure Sphere Security Service Visual Studio tools for Azure Sphere Available Now Azure Sphere development kits from Seeed studios For more information visit:
36 Let s secure the future.
37 Things to do next Session Feedback Please rate this session in the Future Decoded app! Microsoft UK AI Research Report Download the AI Report at Visit our Hands-on Labs on Level 3 Try technology out with on-demand labs and expert help Go deep with Documentation
38 aka.ms/ignitetourlnd
Azure Sphere Transformation. Patrick Ward, Principal Solutions Specialist
 Azure Sphere Transformation Patrick Ward, Principal Solutions Specialist IoT @_pdubya pward@microsoft.com Microcontrollers (MCUs) LOW-COST, SINGLE CHIP COMPUTERS TMS1100: 300 KHz core, 2KB ROM, 64B RAM,
Azure Sphere Transformation Patrick Ward, Principal Solutions Specialist IoT @_pdubya pward@microsoft.com Microcontrollers (MCUs) LOW-COST, SINGLE CHIP COMPUTERS TMS1100: 300 KHz core, 2KB ROM, 64B RAM,
Microsoft Azure Sphere Overview Martin Grossen, Line Manager Microsoft Embedded / IoT Europe 5. June 2018
 Microsoft Azure Sphere Overview Martin Grossen, Line Manager Microsoft Embedded / IoT Europe martin.grossen@avnet.eu 5. June 2018 Prepare for the 2nd wave of Digital Transformation Wave 1: The Microcontroller
Microsoft Azure Sphere Overview Martin Grossen, Line Manager Microsoft Embedded / IoT Europe martin.grossen@avnet.eu 5. June 2018 Prepare for the 2nd wave of Digital Transformation Wave 1: The Microcontroller
Azure Sphere: Fitting Linux Security in 4 MiB of RAM. Ryan Fairfax Principal Software Engineering Lead Microsoft
 Azure Sphere: Fitting Linux Security in 4 MiB of RAM Ryan Fairfax Principal Software Engineering Lead Microsoft Agenda o o o o Intro to Azure Sphere Kernel Customizations User mode services / App Model
Azure Sphere: Fitting Linux Security in 4 MiB of RAM Ryan Fairfax Principal Software Engineering Lead Microsoft Agenda o o o o Intro to Azure Sphere Kernel Customizations User mode services / App Model
Microsoft's IoT Vision and Roadmap. Sam George Director, Azure IoT
 Microsoft's IoT Vision and Roadmap Sam George Director, Azure IoT IoT Enables a Digital Feedback Loop IoT Enables a Digital Feedback Loop The benefits are profound IoT enables a digital feedback loop that
Microsoft's IoT Vision and Roadmap Sam George Director, Azure IoT IoT Enables a Digital Feedback Loop IoT Enables a Digital Feedback Loop The benefits are profound IoT enables a digital feedback loop that
Building a Better Mousetrap:
 Building a Better Mousetrap: Deploying and Managing IoT Solutions for ITPros Anthony Bartolo Sr. Cloud Advocate Microsoft #ITDEVCONNECTIONS ITDEVCONNECTIONS.COM Engage customers Optimize operations p Connected
Building a Better Mousetrap: Deploying and Managing IoT Solutions for ITPros Anthony Bartolo Sr. Cloud Advocate Microsoft #ITDEVCONNECTIONS ITDEVCONNECTIONS.COM Engage customers Optimize operations p Connected
IoT Edge within the IoT Framework
 IoT Edge within the IoT Framework Axel Dittmann Diplom-Betriebswirt (FH) Diplom-Wirtschaftsinformatiker (FH) Global Technical Solution Specialist IOT CISSP, MCP Twitter: @DittmannAxel Waves of Innovation
IoT Edge within the IoT Framework Axel Dittmann Diplom-Betriebswirt (FH) Diplom-Wirtschaftsinformatiker (FH) Global Technical Solution Specialist IOT CISSP, MCP Twitter: @DittmannAxel Waves of Innovation
Connecting Securely to the Cloud
 Connecting Securely to the Cloud Security Primer Presented by Enrico Gregoratto Andrew Marsh Agenda 2 Presentation Speaker Trusting The Connection Transport Layer Security Connecting to the Cloud Enrico
Connecting Securely to the Cloud Security Primer Presented by Enrico Gregoratto Andrew Marsh Agenda 2 Presentation Speaker Trusting The Connection Transport Layer Security Connecting to the Cloud Enrico
Windows IoT Security. Jackie Chang Sr. Program Manager
 Windows IoT Security Jackie Chang Sr. Program Manager Rest Physical access to a device will not give access to data Data & Control Execution Data owner has full control over data processing Motion Transport
Windows IoT Security Jackie Chang Sr. Program Manager Rest Physical access to a device will not give access to data Data & Control Execution Data owner has full control over data processing Motion Transport
Cypress PSoC 6 Microcontrollers
 Cypress PSoC 6 Microcontrollers Purpose-Built for the Internet of Things WWW.CYPRESS.COM/PSOC6 Unmatched Solutions for the Internet of Things EMBEDDED IN TOMORROW The IoT is exploding, with more than 30
Cypress PSoC 6 Microcontrollers Purpose-Built for the Internet of Things WWW.CYPRESS.COM/PSOC6 Unmatched Solutions for the Internet of Things EMBEDDED IN TOMORROW The IoT is exploding, with more than 30
Beyond TrustZone PSA Reed Hinkel Senior Manager Embedded Security Market Development
 Beyond TrustZone PSA Reed Hinkel Senior Manager Embedded Security Market Development Part1 - PSA Tech Seminars 2017 Agenda Platform Security Architecture Architecture overview Trusted Firmware-M IoT Threat
Beyond TrustZone PSA Reed Hinkel Senior Manager Embedded Security Market Development Part1 - PSA Tech Seminars 2017 Agenda Platform Security Architecture Architecture overview Trusted Firmware-M IoT Threat
Provisioning secure Identity for Microcontroller based IoT Devices
 Provisioning secure Identity for Microcontroller based IoT Devices Mark Schaeffer, Sr. Product Marketing Manager, Security Solutions Synergy IoT Platform Business Division, Renesas Electronics, Inc. May
Provisioning secure Identity for Microcontroller based IoT Devices Mark Schaeffer, Sr. Product Marketing Manager, Security Solutions Synergy IoT Platform Business Division, Renesas Electronics, Inc. May
New Approaches to Connected Device Security
 New Approaches to Connected Device Security Erik Jacobson Architecture Marketing Director Arm Arm Techcon 2017 - If you connect it to the Internet, someone will try to hack it. - If what you put on the
New Approaches to Connected Device Security Erik Jacobson Architecture Marketing Director Arm Arm Techcon 2017 - If you connect it to the Internet, someone will try to hack it. - If what you put on the
SiFive Freedom SoCs: Industry s First Open-Source RISC-V Chips
 SiFive Freedom SoCs: Industry s First Open-Source RISC-V Chips Yunsup Lee Co-Founder and CTO High Upfront Cost Has Killed Innovation Our industry needs a fundamental change Total SoC Development Cost Design
SiFive Freedom SoCs: Industry s First Open-Source RISC-V Chips Yunsup Lee Co-Founder and CTO High Upfront Cost Has Killed Innovation Our industry needs a fundamental change Total SoC Development Cost Design
IoT Market: Three Classes of Devices
 IoT Market: Three Classes of Devices Typical Silicon BOM PC-Like Embedded Devices ~100 million units ATM, Retail Point of Service Intel Core $100+ Smart Things ~800 million units PLC, Edge Gateway, Thermostat
IoT Market: Three Classes of Devices Typical Silicon BOM PC-Like Embedded Devices ~100 million units ATM, Retail Point of Service Intel Core $100+ Smart Things ~800 million units PLC, Edge Gateway, Thermostat
Designing Security & Trust into Connected Devices
 Designing Security & Trust into Connected Devices Eric Wang Sr. Technical Marketing Manager Tech Symposia China 2015 November 2015 Agenda Introduction Security Foundations on ARM Cortex -M Security Foundations
Designing Security & Trust into Connected Devices Eric Wang Sr. Technical Marketing Manager Tech Symposia China 2015 November 2015 Agenda Introduction Security Foundations on ARM Cortex -M Security Foundations
Renesas Synergy MCUs Build a Foundation for Groundbreaking Integrated Embedded Platform Development
 Renesas Synergy MCUs Build a Foundation for Groundbreaking Integrated Embedded Platform Development New Family of Microcontrollers Combine Scalability and Power Efficiency with Extensive Peripheral Capabilities
Renesas Synergy MCUs Build a Foundation for Groundbreaking Integrated Embedded Platform Development New Family of Microcontrollers Combine Scalability and Power Efficiency with Extensive Peripheral Capabilities
The challenge with IoT
 1 Agenda The challenge with IoT Sensor to Cloud solution Sensor to Cloud system details SimpleLink Sub-1GHz hardware & software solution Getting started 2 The challenge with IoT We are trying to connect
1 Agenda The challenge with IoT Sensor to Cloud solution Sensor to Cloud system details SimpleLink Sub-1GHz hardware & software solution Getting started 2 The challenge with IoT We are trying to connect
SUSE Linux Entreprise Server for ARM
 FUT89013 SUSE Linux Entreprise Server for ARM Trends and Roadmap Jay Kruemcke Product Manager jayk@suse.com @mr_sles ARM Overview ARM is a Reduced Instruction Set (RISC) processor family British company,
FUT89013 SUSE Linux Entreprise Server for ARM Trends and Roadmap Jay Kruemcke Product Manager jayk@suse.com @mr_sles ARM Overview ARM is a Reduced Instruction Set (RISC) processor family British company,
Titan silicon root of trust for Google Cloud
 Scott Johnson Dominic Rizzo Secure Enclaves Workshop 8/29/2018 Titan silicon root of trust for Google Cloud 1 Cloud Perspective: We need a silicon root of trust Software infrastructure Datacenter equipment
Scott Johnson Dominic Rizzo Secure Enclaves Workshop 8/29/2018 Titan silicon root of trust for Google Cloud 1 Cloud Perspective: We need a silicon root of trust Software infrastructure Datacenter equipment
ArduCAM CC3200 UNO board
 ArduCAM CC3200 UNO board User Guide Rev 1.2, Mar 2017 Table of Contents 1 Introduction... 2 2 Features... 3 3 Pin Definition... 4 4 Getting Started CC3200 with Energia... 5 4.1 Out of the Box Test... 5
ArduCAM CC3200 UNO board User Guide Rev 1.2, Mar 2017 Table of Contents 1 Introduction... 2 2 Features... 3 3 Pin Definition... 4 4 Getting Started CC3200 with Energia... 5 4.1 Out of the Box Test... 5
Designing Security & Trust into Connected Devices
 Designing Security & Trust into Connected Devices Rob Coombs Security Marketing Director TechCon 11/10/15 Agenda Introduction Security Foundations on Cortex-M Security Foundations on Cortex-A Use cases
Designing Security & Trust into Connected Devices Rob Coombs Security Marketing Director TechCon 11/10/15 Agenda Introduction Security Foundations on Cortex-M Security Foundations on Cortex-A Use cases
Securing IoT devices with STM32 & STSAFE Products family. Fabrice Gendreau Secure MCUs Marketing & Application Managers EMEA Region
 Securing IoT devices with STM32 & STSAFE Products family Fabrice Gendreau Secure MCUs Marketing & Application Managers EMEA Region 2 The leading provider of products and solutions for Smart Driving and
Securing IoT devices with STM32 & STSAFE Products family Fabrice Gendreau Secure MCUs Marketing & Application Managers EMEA Region 2 The leading provider of products and solutions for Smart Driving and
The Software of Things T Y S O N T U T T L E C E O S I L I C O N L A B S A S P E N C O R E C E O S U M M I T S H E N Z H E N 8 N O V E M B E R 2018
 The Software of Things T Y S O N T U T T L E C E O S I L I C O N L A B S A S P E N C O R E C E O S U M M I T S H E N Z H E N 8 N O V E M B E R 2018 Most technology we ve built so far was for the Internet
The Software of Things T Y S O N T U T T L E C E O S I L I C O N L A B S A S P E N C O R E C E O S U M M I T S H E N Z H E N 8 N O V E M B E R 2018 Most technology we ve built so far was for the Internet
Windows 10 IoT Core Azure Connectivity and Security
 Windows 10 IoT Core Azure Connectivity and Security Published July 27, 2016 Version 1.0 Table of Contents Introduction... 2 Device identities... 2 Building security into the platform... 3 Security as a
Windows 10 IoT Core Azure Connectivity and Security Published July 27, 2016 Version 1.0 Table of Contents Introduction... 2 Device identities... 2 Building security into the platform... 3 Security as a
Overcoming Hurdles in Wearable Device Designs. John Logan Atmel
 Overcoming Hurdles in Wearable Device Designs John Logan Atmel What is a Wearable New and exciting form factors Touch Screen Clothing Really new and exciting form factors Zoomable Contact Lenses Source,
Overcoming Hurdles in Wearable Device Designs John Logan Atmel What is a Wearable New and exciting form factors Touch Screen Clothing Really new and exciting form factors Zoomable Contact Lenses Source,
A Developer's Guide to Security on Cortex-M based MCUs
 A Developer's Guide to Security on Cortex-M based MCUs 2018 Arm Limited Nazir S Arm Tech Symposia India Agenda Why do we need security? Types of attacks and security assessments Introduction to TrustZone
A Developer's Guide to Security on Cortex-M based MCUs 2018 Arm Limited Nazir S Arm Tech Symposia India Agenda Why do we need security? Types of attacks and security assessments Introduction to TrustZone
mbed OS Update Sam Grove Technical Lead, mbed OS June 2017 ARM 2017
 mbed OS Update Sam Grove Technical Lead, mbed OS June 2017 ARM mbed: Connecting chip to cloud Device software Device services Third-party cloud services IoT device application mbed Cloud Update IoT cloud
mbed OS Update Sam Grove Technical Lead, mbed OS June 2017 ARM mbed: Connecting chip to cloud Device software Device services Third-party cloud services IoT device application mbed Cloud Update IoT cloud
Particle E Series Cloud-integrated hardware platform for cellular IoT devices
 Particle E Series Cloud-integrated hardware platform for cellular IoT devices Particle E Series modules 36.0 x 43.0 x 4.6 mm World s first fully-integrated cellular hardware platform with out-of-box Cloud
Particle E Series Cloud-integrated hardware platform for cellular IoT devices Particle E Series modules 36.0 x 43.0 x 4.6 mm World s first fully-integrated cellular hardware platform with out-of-box Cloud
DesignWare IP for IoT SoC Designs
 DesignWare IP for IoT SoC Designs The Internet of Things (IoT) is connecting billions of intelligent things at our fingertips. The ability to sense countless amounts of information that communicates to
DesignWare IP for IoT SoC Designs The Internet of Things (IoT) is connecting billions of intelligent things at our fingertips. The ability to sense countless amounts of information that communicates to
The next step in IT security after Snowden
 The next step in IT security after Snowden Prof. Dr. (TU NN) Norbert Pohlmann Institute for Internet Security - if(is) Westphalian University of Applied Sciences Gelsenkirchen, Germany www.internet-sicherheit.de
The next step in IT security after Snowden Prof. Dr. (TU NN) Norbert Pohlmann Institute for Internet Security - if(is) Westphalian University of Applied Sciences Gelsenkirchen, Germany www.internet-sicherheit.de
So you think developing an SoC needs to be complex or expensive? Think again
 So you think developing an SoC needs to be complex or expensive? Think again Phil Burr Senior product marketing manager CPU Group NMI - Silicon to Systems: Easy Access ASIC 23 November 2016 Innovation
So you think developing an SoC needs to be complex or expensive? Think again Phil Burr Senior product marketing manager CPU Group NMI - Silicon to Systems: Easy Access ASIC 23 November 2016 Innovation
ARM mbed mbed OS mbed Cloud
 ARM mbed mbed OS mbed Cloud MWC Shanghai 2017 Connecting chip to cloud Device software Device services Third-party cloud services IoT device application mbed Cloud Update IoT cloud applications Analytics
ARM mbed mbed OS mbed Cloud MWC Shanghai 2017 Connecting chip to cloud Device software Device services Third-party cloud services IoT device application mbed Cloud Update IoT cloud applications Analytics
TI SimpleLink dual-band CC1350 wireless MCU
 TI SimpleLink dual-band CC1350 wireless MCU Sub-1 GHz and Bluetooth low energy in a single-chip Presenter Low-Power Connectivity Solutions 1 SimpleLink ultra-low power platform CC2640: Bluetooth low energy
TI SimpleLink dual-band CC1350 wireless MCU Sub-1 GHz and Bluetooth low energy in a single-chip Presenter Low-Power Connectivity Solutions 1 SimpleLink ultra-low power platform CC2640: Bluetooth low energy
Trustzone Security IP for IoT
 Trustzone Security IP for IoT Udi Maor CryptoCell-7xx product manager Systems & Software Group ARM Tech Forum Singapore July 12 th 2017 Why is getting security right for IoT so important? When our everyday
Trustzone Security IP for IoT Udi Maor CryptoCell-7xx product manager Systems & Software Group ARM Tech Forum Singapore July 12 th 2017 Why is getting security right for IoT so important? When our everyday
Product specification
 MJIOT-AMB-03 Product specification 1 MJIOT-AMB-03module appearance 2 目录 1. Product overview...4 1.1 Characteristic... 5 1.2 main parameters...6 1.2 Interface definition... 7 2. appearance and size... 8
MJIOT-AMB-03 Product specification 1 MJIOT-AMB-03module appearance 2 目录 1. Product overview...4 1.1 Characteristic... 5 1.2 main parameters...6 1.2 Interface definition... 7 2. appearance and size... 8
CardOS Secure Elements for Smart Home Applications
 Infineon Security Partner Network Partner Use Case CardOS Secure Elements for Smart Home Applications Using cryptographic functionality provided by ATOS to secure embedded platforms in Smart Home applications.
Infineon Security Partner Network Partner Use Case CardOS Secure Elements for Smart Home Applications Using cryptographic functionality provided by ATOS to secure embedded platforms in Smart Home applications.
DESIGN AND DEPLOY INTELLIGENT, LOW-POWER AND LOW-COST WIRELESS NETWORKS
 DESIGN AND DEPLOY INTELLIGENT, LOW-POWER AND LOW-COST WIRELESS NETWORKS NXP SEMICONDUCTORS & THINGSTREAM GORDON PADKIN, NXP BRUCE JACKSON, THINGSTREAM NEIL HAMILTON, THINGSTREAM MAY 2018 Learn how to develop
DESIGN AND DEPLOY INTELLIGENT, LOW-POWER AND LOW-COST WIRELESS NETWORKS NXP SEMICONDUCTORS & THINGSTREAM GORDON PADKIN, NXP BRUCE JACKSON, THINGSTREAM NEIL HAMILTON, THINGSTREAM MAY 2018 Learn how to develop
Innovation policy for Industry 4.0
 Innovation policy for Industry 4.0 Remarks from Giorgio Mosca Chair of Cybersecurity Steering Committee Confindustria Digitale Director Strategy & Technologies - Security & IS Division, Leonardo Agenda
Innovation policy for Industry 4.0 Remarks from Giorgio Mosca Chair of Cybersecurity Steering Committee Confindustria Digitale Director Strategy & Technologies - Security & IS Division, Leonardo Agenda
Feature Comparison Summary
 Feature Comparison Summary,, and The cloud-ready operating system is the cloud-ready operating system that delivers new layers of security and Azure-inspired innovation for the applications and infrastructure
Feature Comparison Summary,, and The cloud-ready operating system is the cloud-ready operating system that delivers new layers of security and Azure-inspired innovation for the applications and infrastructure
Beyond TrustZone PSA. Rob Coombs Security Director. Part1 - PSA Tech Seminars Arm Limited
 Beyond TrustZone PSA Rob Coombs Security Director Part1 - PSA Tech Seminars 2017 Agenda Platform Security Architecture Architecture overview Trusted Firmware-M IoT Threat models & security analyses Summary
Beyond TrustZone PSA Rob Coombs Security Director Part1 - PSA Tech Seminars 2017 Agenda Platform Security Architecture Architecture overview Trusted Firmware-M IoT Threat models & security analyses Summary
Beyond TrustZone Security Enclaves Reed Hinkel Senior Manager Embedded Security Market Develop
 Beyond TrustZone Security Enclaves Reed Hinkel Senior Manager Embedded Security Market Develop Part2 Security Enclaves Tech Seminars 2017 Agenda New security technology for IoT Security Enclaves CryptoIsland
Beyond TrustZone Security Enclaves Reed Hinkel Senior Manager Embedded Security Market Develop Part2 Security Enclaves Tech Seminars 2017 Agenda New security technology for IoT Security Enclaves CryptoIsland
Introduction to Device Trust Architecture
 Introduction to Device Trust Architecture July 2018 www.globalplatform.org 2018 GlobalPlatform, Inc. THE TECHNOLOGY The Device Trust Architecture is a security framework which shows how GlobalPlatform
Introduction to Device Trust Architecture July 2018 www.globalplatform.org 2018 GlobalPlatform, Inc. THE TECHNOLOGY The Device Trust Architecture is a security framework which shows how GlobalPlatform
RED HAT OPENSHIFT A FOUNDATION FOR SUCCESSFUL DIGITAL TRANSFORMATION
 RED HAT OPENSHIFT A FOUNDATION FOR SUCCESSFUL DIGITAL TRANSFORMATION Stephanos D Bacon Product Portfolio Strategy, Application Platforms Stockholm, 13 September 2017 1 THE PATH TO DIGITAL LEADERSHIP IT
RED HAT OPENSHIFT A FOUNDATION FOR SUCCESSFUL DIGITAL TRANSFORMATION Stephanos D Bacon Product Portfolio Strategy, Application Platforms Stockholm, 13 September 2017 1 THE PATH TO DIGITAL LEADERSHIP IT
Bidirectional wireless communication between IBM Cloud and Bluetooth Low Energy peripherals through SimpleLink Wi-Fi
 Bidirectional wireless communication between IBM Cloud and Bluetooth Low Energy peripherals through SimpleLink Wi-Fi 30.7B connected devices by 2020, 75.4B by 2025 Top IoT concerns Security Complex standards
Bidirectional wireless communication between IBM Cloud and Bluetooth Low Energy peripherals through SimpleLink Wi-Fi 30.7B connected devices by 2020, 75.4B by 2025 Top IoT concerns Security Complex standards
Oberon M2M IoT Platform. JAN 2016
 Oberon M2M IoT Platform JAN 2016 www.imgtec.com Contents Iot Segments and Definitions Targeted Use Cases for IoT Oberon targeted use cases IoT Differentiators IoT Power Management IoT Security Integrated
Oberon M2M IoT Platform JAN 2016 www.imgtec.com Contents Iot Segments and Definitions Targeted Use Cases for IoT Oberon targeted use cases IoT Differentiators IoT Power Management IoT Security Integrated
SICS Software Week, October 2014
 to Fog Securing the Edge SICS Software Week, October 2014 Iain Davidson Digital Networking iain.davidson@freescale.com 1 IoT Landscape Multi-market opportunity Wellbeing/Health Transport Energy Industrial
to Fog Securing the Edge SICS Software Week, October 2014 Iain Davidson Digital Networking iain.davidson@freescale.com 1 IoT Landscape Multi-market opportunity Wellbeing/Health Transport Energy Industrial
Security & Management
 Common Identity Data Platform Security & Management Unified Development Category Azure Technology On-Premise Technology Hybrid Storage Azure Storage StorSimple Hybrid Backup & DR Azure Backup + Azure Site
Common Identity Data Platform Security & Management Unified Development Category Azure Technology On-Premise Technology Hybrid Storage Azure Storage StorSimple Hybrid Backup & DR Azure Backup + Azure Site
The Open Application Platform for Secure Elements.
 The Open Application Platform for Secure Elements. Java Card enables secure elements, such as smart cards and other tamper-resistant security chips, to host applications, called applets, which employ Java
The Open Application Platform for Secure Elements. Java Card enables secure elements, such as smart cards and other tamper-resistant security chips, to host applications, called applets, which employ Java
Security of Embedded Hardware Systems Insight into Attacks and Protection of IoT Devices
 Security of Embedded Hardware Systems Insight into Attacks and Protection of IoT Devices Dr. Johann Heyszl, Head of Hardware Security Department Fraunhofer-Institute for Applied and Integrated Security
Security of Embedded Hardware Systems Insight into Attacks and Protection of IoT Devices Dr. Johann Heyszl, Head of Hardware Security Department Fraunhofer-Institute for Applied and Integrated Security
High-Performance, Highly Secure Networking for Industrial and IoT Applications
 High-Performance, Highly Secure Networking for Industrial and IoT Applications Table of Contents 2 Introduction 2 Communication Accelerators 3 Enterprise Network Lineage Features 5 Example applications
High-Performance, Highly Secure Networking for Industrial and IoT Applications Table of Contents 2 Introduction 2 Communication Accelerators 3 Enterprise Network Lineage Features 5 Example applications
$263 WHITE PAPER. Flexible Key Provisioning with SRAM PUF. Securing Billions of IoT Devices Requires a New Key Provisioning Method that Scales
 WHITE PAPER Flexible Key Provisioning with SRAM PUF SRAM PUF Benefits Uses standard SRAM Device-unique keys No secrets reside on the chip No key material programmed Flexible and scalable Certifications:
WHITE PAPER Flexible Key Provisioning with SRAM PUF SRAM PUF Benefits Uses standard SRAM Device-unique keys No secrets reside on the chip No key material programmed Flexible and scalable Certifications:
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS. Security Without Compromise
 DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
Accelerating IoT with ARM mbed
 Accelerating IoT with ARM mbed Paul Bakker Product Strategy, IoT BU ARM Tech Symposia China 2015 November 2015 Productivity Security Connectivity Management Efficiency 2 Since TechCon Last Year 60K 2014
Accelerating IoT with ARM mbed Paul Bakker Product Strategy, IoT BU ARM Tech Symposia China 2015 November 2015 Productivity Security Connectivity Management Efficiency 2 Since TechCon Last Year 60K 2014
MYD-C437X-PRU Development Board
 MYD-C437X-PRU Development Board MYC-C437X CPU Module as Controller Board Two 0.8mm pitch 100-pin Connectors for Board-to-Board Connections Up to 1GHz TI AM437x Series ARM Cortex-A9 Processors 512MB DDR3
MYD-C437X-PRU Development Board MYC-C437X CPU Module as Controller Board Two 0.8mm pitch 100-pin Connectors for Board-to-Board Connections Up to 1GHz TI AM437x Series ARM Cortex-A9 Processors 512MB DDR3
HEXIWEAR COMPLETE IOT DEVELOPMENT SOLUTION
 HEXIWEAR COMPLETE IOT DEVELOPMENT SOLUTION NXP SEMICONDUCTORS PUBLIC THE ONLY SUPPLIER TO PROVIDE COMPLETE IoT SOLUTIONS DSPs, MCUs & CPUs Suite of Sensors NFC, BLE, Thread, zigbee, sub-ghz Wireless Interconnects
HEXIWEAR COMPLETE IOT DEVELOPMENT SOLUTION NXP SEMICONDUCTORS PUBLIC THE ONLY SUPPLIER TO PROVIDE COMPLETE IoT SOLUTIONS DSPs, MCUs & CPUs Suite of Sensors NFC, BLE, Thread, zigbee, sub-ghz Wireless Interconnects
locuz.com SOC Services
 locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
WAVE ONE MAINFRAME WAVE THREE INTERNET WAVE FOUR MOBILE & CLOUD WAVE TWO PERSONAL COMPUTING & SOFTWARE Arm Limited
 WAVE ONE MAINFRAME WAVE THREE INTERNET WAVE FOUR MOBILE & CLOUD WAVE TWO PERSONAL COMPUTING & SOFTWARE Artificial Intelligence Fifth wave Data-driven computing era IoT Generating data 5G 5G Transporting
WAVE ONE MAINFRAME WAVE THREE INTERNET WAVE FOUR MOBILE & CLOUD WAVE TWO PERSONAL COMPUTING & SOFTWARE Artificial Intelligence Fifth wave Data-driven computing era IoT Generating data 5G 5G Transporting
Custom Silicon for all
 Custom Silicon for all Because Moore s Law only ends once Who is SiFive? Best-in-class team with technology depth and breadth Founders & Execs Key Leaders & Team Yunsup Lee CTO Krste Asanovic Chief Architect
Custom Silicon for all Because Moore s Law only ends once Who is SiFive? Best-in-class team with technology depth and breadth Founders & Execs Key Leaders & Team Yunsup Lee CTO Krste Asanovic Chief Architect
Azure Administrator Role
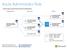 Azure Administrator Role Azure Apps and Infrastructure Certification Fundamentals Expert Azure Solutions Architect Expert Azure Fundamentals (optional) Azure Administrator Azure Developer COMING SOON Azure
Azure Administrator Role Azure Apps and Infrastructure Certification Fundamentals Expert Azure Solutions Architect Expert Azure Fundamentals (optional) Azure Administrator Azure Developer COMING SOON Azure
Beyond TrustZone Part 1 - PSA
 Beyond TrustZone Part 1 - PSA Rob Coombs Security Director, Arm Arm Tech Symposia 2017, Hsinchu Agenda Platform Security Architecture Architecture overview Trusted Firmware-M IoT Threat models & security
Beyond TrustZone Part 1 - PSA Rob Coombs Security Director, Arm Arm Tech Symposia 2017, Hsinchu Agenda Platform Security Architecture Architecture overview Trusted Firmware-M IoT Threat models & security
Feature Comparison Summary
 Feature Comparison Summary, and The cloud-ready operating system Thanks to cloud technology, the rate of change is faster than ever before, putting more pressure on IT. Organizations demand increased security,
Feature Comparison Summary, and The cloud-ready operating system Thanks to cloud technology, the rate of change is faster than ever before, putting more pressure on IT. Organizations demand increased security,
Delivering High-mix, High-volume Secure Manufacturing in the Distribution Channel
 Delivering High-mix, High-volume Secure Manufacturing in the Distribution Channel Steve Pancoast Vice President, Engineering Secure Thingz Inc Rajeev Gulati Vice President and CTO Data IO Corporation 1
Delivering High-mix, High-volume Secure Manufacturing in the Distribution Channel Steve Pancoast Vice President, Engineering Secure Thingz Inc Rajeev Gulati Vice President and CTO Data IO Corporation 1
SIMPLIFYING THE CAR. Helix chassis. Helix chassis. Helix chassis WIND RIVER HELIX CHASSIS WIND RIVER HELIX DRIVE WIND RIVER HELIX CARSYNC
 W I N D R I V E R H E L I X C H A S S I S SIMPLIFYING THE WIND RIVER HELIX CHASSIS Helix Chassis brings together software, technologies, tools, and services to help automotive manufacturers unify, simplify,
W I N D R I V E R H E L I X C H A S S I S SIMPLIFYING THE WIND RIVER HELIX CHASSIS Helix Chassis brings together software, technologies, tools, and services to help automotive manufacturers unify, simplify,
Scott Johnson Dominic Rizzo Parthasarathy Ranganathan Jon McCune Richard Ho. Titan: enabling a transparent silicon root of trust for Cloud
 Scott Johnson Dominic Rizzo Parthasarathy Ranganathan Jon McCune Richard Ho Titan: enabling a transparent silicon root of trust for Cloud 1 Talk outline 01 02 03 04 05 Motivation and problem statement
Scott Johnson Dominic Rizzo Parthasarathy Ranganathan Jon McCune Richard Ho Titan: enabling a transparent silicon root of trust for Cloud 1 Talk outline 01 02 03 04 05 Motivation and problem statement
ARM mbed Towards Secure, Scalable, Efficient IoT of Scale
 ARM mbed Towards Secure, Scalable, Efficient IoT of Scale Kirsi Maansaari Product Manager, ARM Copenhagen/Embedded Everywhere 2016 Faster route to secure IoT from chip to cloud Announced at ARM TechCon
ARM mbed Towards Secure, Scalable, Efficient IoT of Scale Kirsi Maansaari Product Manager, ARM Copenhagen/Embedded Everywhere 2016 Faster route to secure IoT from chip to cloud Announced at ARM TechCon
DICE: Foundational Trust for IoT
 DICE: Foundational Trust for IoT Dennis Mattoon, Microsoft Santa Clara, CA 1 Introduction Modern cyber-attacks are often sophisticated and relentless in their continual efforts to seek out vulnerabilities
DICE: Foundational Trust for IoT Dennis Mattoon, Microsoft Santa Clara, CA 1 Introduction Modern cyber-attacks are often sophisticated and relentless in their continual efforts to seek out vulnerabilities
PUBLIC AND HYBRID CLOUD: BREAKING DOWN BARRIERS
 PUBLIC AND HYBRID CLOUD: BREAKING DOWN BARRIERS Jane R. Circle Manager, Red Hat Global Cloud Provider Program and Cloud Access Program June 28, 2016 WHAT WE'LL DISCUSS TODAY Hybrid clouds and multi-cloud
PUBLIC AND HYBRID CLOUD: BREAKING DOWN BARRIERS Jane R. Circle Manager, Red Hat Global Cloud Provider Program and Cloud Access Program June 28, 2016 WHAT WE'LL DISCUSS TODAY Hybrid clouds and multi-cloud
INTERNET OF THINGS KONTRON
 INTERNET OF THINGS SECURITY @ KONTRON EMBEDDED COMPUTING CONFERENCE 2017 ECC WINTERTHUR SEPTEMBER 5 TH, 2017 AGENDA 01 INTRODUCTION 02 SECURITY LAYERS 03 KONTRON & S&T // 2 WHAT IS IN IT FOR YOU THROUGH
INTERNET OF THINGS SECURITY @ KONTRON EMBEDDED COMPUTING CONFERENCE 2017 ECC WINTERTHUR SEPTEMBER 5 TH, 2017 AGENDA 01 INTRODUCTION 02 SECURITY LAYERS 03 KONTRON & S&T // 2 WHAT IS IN IT FOR YOU THROUGH
Simplifying Multiprotocol Industrial Ethernet Communication. Sandeep Kumar December 2016
 Simplifying Multiprotocol Industrial Ethernet Communication Sandeep Kumar December 2016 1 Agenda Introduction to Industry 4.0 Need & Challenges with Deterministic Industrial Ethernet Changes in Industrial
Simplifying Multiprotocol Industrial Ethernet Communication Sandeep Kumar December 2016 1 Agenda Introduction to Industry 4.0 Need & Challenges with Deterministic Industrial Ethernet Changes in Industrial
Evolution of Cyber Security. Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa
 Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Windows Server Windows Server Windows Server 2008
 2003 2008 2012 Hardware Innovation X86 Symmetric Multi-Processor (SMP) s Affordable servers for the masses Software Innovation Window 2003 SQL 2005 Exchange 2003 Hardware Innovation X64 s Multi-Core s
2003 2008 2012 Hardware Innovation X86 Symmetric Multi-Processor (SMP) s Affordable servers for the masses Software Innovation Window 2003 SQL 2005 Exchange 2003 Hardware Innovation X64 s Multi-Core s
CompTIA CASP (Advanced Security Practitioner)
 CompTIA CASP (Advanced Security Practitioner) Course Length: 5 days (virtual) Click here to view the current class schedule! Overview: The CompTIA Advanced Security Practitioner (CASP) Certification is
CompTIA CASP (Advanced Security Practitioner) Course Length: 5 days (virtual) Click here to view the current class schedule! Overview: The CompTIA Advanced Security Practitioner (CASP) Certification is
Microsoft Azure for AWS Experts
 Microsoft Azure for AWS Experts OD40390B; On-Demand, Video-based Course Description This course provides an in-depth discussion and practical hands-on training of Microsoft Azure Infrastructure Services
Microsoft Azure for AWS Experts OD40390B; On-Demand, Video-based Course Description This course provides an in-depth discussion and practical hands-on training of Microsoft Azure Infrastructure Services
A C H I E V E B O T H W I T H K E Y S I G H T. Company Profile
 A C H I E V E B O T H W I T H K E Y S I G H T 1 W E H E L P Y O U C R E AT E. I N N O VAT E. A N D D E L I V E R W H AT S N E X T. The innovation leader in electronic design and test for over 75 years
A C H I E V E B O T H W I T H K E Y S I G H T 1 W E H E L P Y O U C R E AT E. I N N O VAT E. A N D D E L I V E R W H AT S N E X T. The innovation leader in electronic design and test for over 75 years
Zatara Series ARM ASSP High-Performance 32-bit Solution for Secure Transactions
 1 ARM-BASED ASSP FOR SECURE TRANSACTIONS ZATARA SERIES 32-BIT ARM ASSP PB022106-1008 ZATARA SERIES ADVANTAGE SINGLE-CHIP SOLUTION BEST FEATURE SET IN POS PCIPED PRE-CERTIFIED EMV L1 CERTIFIED TOTAL SOLUTION
1 ARM-BASED ASSP FOR SECURE TRANSACTIONS ZATARA SERIES 32-BIT ARM ASSP PB022106-1008 ZATARA SERIES ADVANTAGE SINGLE-CHIP SOLUTION BEST FEATURE SET IN POS PCIPED PRE-CERTIFIED EMV L1 CERTIFIED TOTAL SOLUTION
Connect with Simplicity
 Connect with Simplicity The power of you + Capitalize on the connectivity potential of the IoT Revolutionize new and established markets Maximize your speed to profit For over 55 years, Fortune 100s and
Connect with Simplicity The power of you + Capitalize on the connectivity potential of the IoT Revolutionize new and established markets Maximize your speed to profit For over 55 years, Fortune 100s and
END NODE DIGITAL The compact ModBus WiFi End Node to network easily industrial machine.
 END NODE DIGITAL The compact ModBus WiFi End Node to network easily industrial machine www.wi-next.com End Node Digital Network easily digital industrial machines and improve the efficiency with Industrial
END NODE DIGITAL The compact ModBus WiFi End Node to network easily industrial machine www.wi-next.com End Node Digital Network easily digital industrial machines and improve the efficiency with Industrial
RENESAS SYNERGY PLATFORM
 RENESAS SYNERGY PLATFORM A complete and qualified embedded MCU software and hardware platform 2018.04 START AHEAD Get to market faster and easier with Renesas Synergy. As the first fully qualified MCU
RENESAS SYNERGY PLATFORM A complete and qualified embedded MCU software and hardware platform 2018.04 START AHEAD Get to market faster and easier with Renesas Synergy. As the first fully qualified MCU
Comprehensive DDoS Attack Protection: Cloud-based, Enterprise Grade Mitigation F5 Silverline
 Comprehensive DDoS Attack Protection: Cloud-based, Enterprise Grade Mitigation F5 Silverline PRESENTED BY: RICH BIBLE, EMEA SILVERLINE SA November 22, 2018 1 2018 F5 NETWORKS DDoS and Application Attack
Comprehensive DDoS Attack Protection: Cloud-based, Enterprise Grade Mitigation F5 Silverline PRESENTED BY: RICH BIBLE, EMEA SILVERLINE SA November 22, 2018 1 2018 F5 NETWORKS DDoS and Application Attack
Connect your IoT device: Bluetooth 5, , NB-IoT
 Connect your IoT device: Bluetooth 5, 802.15.4, NB-IoT Prithi Ramakrishnan Arm TechTalk 2017 IoT connectivity technologies Multiple standards, different applications Throughput Unlicensed >100Mbps Wi-Fi
Connect your IoT device: Bluetooth 5, 802.15.4, NB-IoT Prithi Ramakrishnan Arm TechTalk 2017 IoT connectivity technologies Multiple standards, different applications Throughput Unlicensed >100Mbps Wi-Fi
NEXT GENERATION SECURITY OPERATIONS CENTER
 DTS SOLUTION NEXT GENERATION SECURITY OPERATIONS CENTER SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 - SUCCESS FACTORS SOC 2.0 - FUNCTIONAL COMPONENTS DTS SOLUTION SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 Protecting
DTS SOLUTION NEXT GENERATION SECURITY OPERATIONS CENTER SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 - SUCCESS FACTORS SOC 2.0 - FUNCTIONAL COMPONENTS DTS SOLUTION SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 Protecting
10 Steps to Virtualization
 AN INTEL COMPANY 10 Steps to Virtualization WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Virtualization the creation of multiple virtual machines (VMs) on a single piece of hardware, where
AN INTEL COMPANY 10 Steps to Virtualization WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Virtualization the creation of multiple virtual machines (VMs) on a single piece of hardware, where
ENABLING EMBEDDED UA SECURITY AND DISCOVERY
 ENABLING EMBEDDED UA SECURITY AND DISCOVERY Liam Power Principal Engineer, Embedded Systems Copyright 2014 2012 Matrikon Inc. STATE OF EMBEDDED TECHNOLOGY Copyright 2014 2012 Matrikon Inc. Mountain View,
ENABLING EMBEDDED UA SECURITY AND DISCOVERY Liam Power Principal Engineer, Embedded Systems Copyright 2014 2012 Matrikon Inc. STATE OF EMBEDDED TECHNOLOGY Copyright 2014 2012 Matrikon Inc. Mountain View,
Course Outline. Module 1: Microsoft Azure for AWS Experts Course Overview
 Course Outline Module 1: Microsoft Azure for AWS Experts Course Overview In this module, you will get an overview of Azure services and features including deployment models, subscriptions, account types
Course Outline Module 1: Microsoft Azure for AWS Experts Course Overview In this module, you will get an overview of Azure services and features including deployment models, subscriptions, account types
Transforming Utility Grid Operations with the Internet of Things
 Solution Brief Internet of Things Energy Industry Transforming Utility Grid Operations with the Internet of Things Access key process data in real time to increase situational awareness of grid operations.
Solution Brief Internet of Things Energy Industry Transforming Utility Grid Operations with the Internet of Things Access key process data in real time to increase situational awareness of grid operations.
New STM32WB Series MCU with Built-in BLE 5 and IEEE
 New STM32WB Series MCU with Built-in BLE 5 and IEEE 802.15.4 Make the Choice of STM32WB Series The 7 keys points to make the difference 2 Open 2.4 GHz radio Multi-protocol Dual-core / Full control Ultra-low-power
New STM32WB Series MCU with Built-in BLE 5 and IEEE 802.15.4 Make the Choice of STM32WB Series The 7 keys points to make the difference 2 Open 2.4 GHz radio Multi-protocol Dual-core / Full control Ultra-low-power
Supply Chain Integrity and Security Assurance for ICT. Mats Nilsson
 Supply Chain Integrity and Security Assurance for ICT Mats Nilsson The starting point 2 B Internet users 85% Population coverage 5+ B Mobile subscriptions 10 years of Daily upload E-Books surpassing Print
Supply Chain Integrity and Security Assurance for ICT Mats Nilsson The starting point 2 B Internet users 85% Population coverage 5+ B Mobile subscriptions 10 years of Daily upload E-Books surpassing Print
Build an open hybrid cloud and paint it red and blue
 Build an open hybrid cloud and paint it red and blue Khaled Elbedri Technical sales lead, Microsoft Ismail Dhaoui EMEA Senior Specialist Solutions Architect, Red Hat Tuesday, May 8, 2018 Agenda RH & MS
Build an open hybrid cloud and paint it red and blue Khaled Elbedri Technical sales lead, Microsoft Ismail Dhaoui EMEA Senior Specialist Solutions Architect, Red Hat Tuesday, May 8, 2018 Agenda RH & MS
Designing Security & Trust into Connected Devices
 Designing Security & Trust into Connected Devices Eric Wang Senior Technical Marketing Manager Shenzhen / ARM Tech Forum / The Ritz-Carlton June 14, 2016 Agenda Introduction Security Foundations on Cortex-A
Designing Security & Trust into Connected Devices Eric Wang Senior Technical Marketing Manager Shenzhen / ARM Tech Forum / The Ritz-Carlton June 14, 2016 Agenda Introduction Security Foundations on Cortex-A
Connect Your IoT Device: Bluetooth 5, , NB-IoT
 Connect Your IoT Device: Bluetooth 5, 802.15.4, NB-IoT Craig Tou Business Development Manager, Arm Arm Tech Symposia 2017, Taipei IoT Devices - Everything Connects New classes of connectivity for a new
Connect Your IoT Device: Bluetooth 5, 802.15.4, NB-IoT Craig Tou Business Development Manager, Arm Arm Tech Symposia 2017, Taipei IoT Devices - Everything Connects New classes of connectivity for a new
BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY
 SOLUTION OVERVIEW BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY Every organization is exploring how technology can help it disrupt current operating models, enabling it to better serve
SOLUTION OVERVIEW BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY Every organization is exploring how technology can help it disrupt current operating models, enabling it to better serve
Introduction to Sitara AM437x Processors
 Introduction to Sitara AM437x Processors AM437x: Highly integrated, scalable platform with enhanced industrial communications and security AM4376 AM4378 Software Key Features AM4372 AM4377 High-performance
Introduction to Sitara AM437x Processors AM437x: Highly integrated, scalable platform with enhanced industrial communications and security AM4376 AM4378 Software Key Features AM4372 AM4377 High-performance
Accelerating IoT with ARM mbed
 Accelerating IoT with ARM mbed Zach Shelby VP Marketing Internet of Things Business Unit mbed Connect / Shenzhen, China 15 th Dec 2015 Productivity Security Connectivity Management Efficiency 2 Since TechCon
Accelerating IoT with ARM mbed Zach Shelby VP Marketing Internet of Things Business Unit mbed Connect / Shenzhen, China 15 th Dec 2015 Productivity Security Connectivity Management Efficiency 2 Since TechCon
MYC-C437X CPU Module
 MYC-C437X CPU Module - Up to 1GHz TI AM437x Series ARM Cortex-A9 Processors - 512MB DDR3 SDRAM, 4GB emmc Flash, 32KB EEPROM - Gigabit Ethernet PHY - Power Management IC - Two 0.8mm pitch 100-pin Board-to-Board
MYC-C437X CPU Module - Up to 1GHz TI AM437x Series ARM Cortex-A9 Processors - 512MB DDR3 SDRAM, 4GB emmc Flash, 32KB EEPROM - Gigabit Ethernet PHY - Power Management IC - Two 0.8mm pitch 100-pin Board-to-Board
Windows 10 IoT Overview. Microsoft Corporation
 Windows 10 IoT Overview Microsoft Corporation 25 $7.2 BILLION TRILLION Connected things will by 2020 be in use by 2020 worldwide market for IoT solutions IDC: Worldwide and Regional Internet of Things
Windows 10 IoT Overview Microsoft Corporation 25 $7.2 BILLION TRILLION Connected things will by 2020 be in use by 2020 worldwide market for IoT solutions IDC: Worldwide and Regional Internet of Things
ARM TrustZone for ARMv8-M for software engineers
 ARM TrustZone for ARMv8-M for software engineers Ashok Bhat Product Manager, HPC and Server tools ARM Tech Symposia India December 7th 2016 The need for security Communication protection Cryptography,
ARM TrustZone for ARMv8-M for software engineers Ashok Bhat Product Manager, HPC and Server tools ARM Tech Symposia India December 7th 2016 The need for security Communication protection Cryptography,
HOW CLOUD, MOBILITY AND SHIFTING APP ARCHITECTURES WILL TRANSFORM SECURITY: GAINING THE HOME-COURT ADVANTAGE
 #RSAC SESSION ID: SPO3-T07 HOW CLOUD, MOBILITY AND SHIFTING APP ARCHITECTURES WILL TRANSFORM SECURITY: GAINING THE HOME-COURT ADVANTAGE Tom Corn Senior Vice President/GM Security Products VMware @therealtomcorn
#RSAC SESSION ID: SPO3-T07 HOW CLOUD, MOBILITY AND SHIFTING APP ARCHITECTURES WILL TRANSFORM SECURITY: GAINING THE HOME-COURT ADVANTAGE Tom Corn Senior Vice President/GM Security Products VMware @therealtomcorn
CPS 510 final exam, 4/27/2015
 CPS 510 final exam, 4/27/2015 Your name please: This exam has 25 questions worth 12 points each. For each question, please give the best answer you can in a few sentences or bullets using the lingo of
CPS 510 final exam, 4/27/2015 Your name please: This exam has 25 questions worth 12 points each. For each question, please give the best answer you can in a few sentences or bullets using the lingo of
Accelerating IoT with ARM mbed
 Accelerating IoT with ARM mbed Dr.Krisztián Flautner General Manager / ARM Internet of Things Business Unit ARM Holdings Ltd mbed Sponsored Session / ARM TechCon 2015 11 th Nov 2015 Productivity Security
Accelerating IoT with ARM mbed Dr.Krisztián Flautner General Manager / ARM Internet of Things Business Unit ARM Holdings Ltd mbed Sponsored Session / ARM TechCon 2015 11 th Nov 2015 Productivity Security
How to Build an Appium Continuous Testing Pipeline
 How to Build an Appium Continuous Testing Pipeline Step-by-Step Tutorial November, 2017 Today s speakers Guy Arieli, CTO, Experitest Ruth Zamir Marketing Director Experitest 01 Why do we need continuous
How to Build an Appium Continuous Testing Pipeline Step-by-Step Tutorial November, 2017 Today s speakers Guy Arieli, CTO, Experitest Ruth Zamir Marketing Director Experitest 01 Why do we need continuous
