Trust Management. 4Ll Springer. Peter Herrmann Valerie Issarny Simon Shiu (Eds.)
|
|
|
- Amie Ford
- 6 years ago
- Views:
Transcription
1 Peter Herrmann Valerie Issarny Simon Shiu (Eds.) Trust Management Third International Conference, itrust 2005 Paris, France, May 23-26, 2005 Proceedings 4Ll Springer
2 Table of Contents Third International Conference on Trust Management I Keynote Addresses Foraging for Trust: Exploring Rationality and the Stag Hunt Game Steven 0. Kimbrough 1 Trust, Untrust, Distrust and Mistrust - An Exploration of the Dark(er) Side Stephen Marsh, Mark R. Dibben 17 II Full Papers Security and Trust in the Italian Legal Digital Signature Framework Stefano Zanero 34 Specifying Legal Risk Scenarios Using the CORAS Threat Modelling Language Fredrik Vraalsen, Mass Soldal Lund, Tobias Mahler, Xavier Parent, Ketil St0len 45 On Deciding to Trust Michael Michalakopoulos, Maria Fasli 61 Trust Management Survey Sini Ruohomaa, Lea Kutvonen 77 Can We Manage Trust? Audun J0sang, Claudia Keser, Theo Dimitrakos 93 Operational Models for Reputation Servers David W. Chadwick 108 A Representation Model of Trust Relationships with Delegation Extensions Isaac Agudo, Javier Lopez, Jose A. Montenegro 116
3 X Table of Contents Affect and Trust Lewis Hassell 131 Reinventing Forgiveness: A Formal Investigation of Moral Facilitation Asimina Vasalou, Jeremy Pitt 146 Modeling Social and Individual Trust in Requirements Engineering Methodologies Paolo Giorgini, Fabio Massacci, John Mylopoulos, Nicola Zannone 161 Towards a Generic Trust Model - Comparison of Various Trust Update Algorithms Michael Kinateder, Ernesto Baschny, Kurt Rothermel 177 A Probabilistic Trust Model for Handling Inaccurate Reputation Sources Jigar Patel, W. T. Luke Teacy, Nicholas R. Jennings, Michael Luck 193 Trust as a Key to Improving Recommendation Systems Georgios Pitsilis, Lindsay Marshall 210 Alleviating the Sparsity Problem of Collaborative Filtering Using Trust Inferences Manos Papagelis, Dimitris Plexousakis, Themistoklis Kutsuras 224 Experience-Based Trust: Enabling Effective Resource Selection in a Grid Environment Nathan Griffiths'-Kuo-Ming Chao 240 Interactive Credential Negotiation for Stateful Business Processes Hristo Koshutanski, Fabio Massacci 256 An Evidence Based Architecture for Efficient, Attack-Resistant Computational Trust Dissemination in Peer-to-Peer Networks David Ingram 273 Towards an Evaluation Methodology for Computational Trust Systems Ciardn Bryce, Nathan Dimmock, Karl Krukow, Jean-Marc Seigneur, Vinny Cahill, Waleed Wagealla 289 Trusted Computing: Strengths Weaknesses and Further Opportunities for Enhancing Privacy Siani Pearson 305
4 Table of Contents XI Trust Transfer: Encouraging Self-recommendations Without Sybil Attack Jean-Marc Seigneur, Alan Gray, Christian Damsgaard Jensen 321 Privacy-Preserving Search and Updates for Outsourced Tree-Structured Data on Untrusted Servers Tran Khanh Dang 338 III Short Papers Persistent and Dynamic Trust: Analysis and the Related Impact of Trusted Platforms Siani Pearson, Marco Casassa Mont, Stephen Crane 355 Risk Models for Trust-Based Access Control (TBAC) Nathan Dimmock, Jean Bacon, David Ingram, Ken Moody 364 Combining Trust and Risk to Reduce the Cost of Attacks Daniel Cvrcek, Ken Moody 372 IWTrust: Improving User Trust in Answers from the Web Ilya Zaihrayeu, Paulo Pinheiro da Silva, Deborah L. McGuinness IV Demonstration Overviews Trust Record: High-Level Assurance and Compliance Adrian Baldwin, Yolanta Beres, David Plaquin, Simon Shiu.... ) Implementation of the SECURE Trust Engine Ciardn Bryce, Paul Couderc, Jean-Marc Seigneur, Vinny Cahill The CORAS Tool for Security Risk Analysis Fredrik Vraalsen, Folker den Braber, Mass Soldal Lund, Ketil St0len 402 Towards a Grid Platform Enabling Dynamic Virtual Organisations for Business Applications Theo Dimitrakos, G. Laria, I. Djordjevic, N. Romano, F. D'Andria, V. Trpkovski, P. Kearney, M. Gaeta, P. Ritrovato, L. Schubert, B. Serhan, L. Titkov, S. Wesner 406
5 XII Table of Contents Multimedia Copyright Protection Platform Demonstrator Miguel Soriano, Marcel Fernandez, Elisa Sayrol, Joan Tomas, Joan Casanellas, Josep Pegueroles, Juan Hernandez-Serrano 411 ST-Tool: A CASE Tool for Modeling and Analyzing Trust Requirements P. Giorgini, F. Massacci, J. Mylopoulos, A. Siena, N. Zannone 415 The VoteSecure Secure Internet Voting System Periklis Akritidis, Yiannis Chatzikian, Manos Dramitinos, Evangelos Michalopoulos, Dimitrios Tsigos, Nikolaos Ventouras 420 Author Index 425
Report on Dissemination Activities and Plan
 Deliverable. 23 Report on Dissemination Activities and Plan......... WP14 Dissemination Michael Wilson, CCLRC July 2005 Version 1 TrustCoM A trust and Contract Management framework enabling secure collaborative
Deliverable. 23 Report on Dissemination Activities and Plan......... WP14 Dissemination Michael Wilson, CCLRC July 2005 Version 1 TrustCoM A trust and Contract Management framework enabling secure collaborative
CORAS for Research of Considering the Integration Risk Management with ISO/IEC 27005
 CORAS for Research of Considering the Integration Risk Management with ISO/IEC 27005 Ya-Ping Fu 1, 4, Kwo-Jean Farn 1, 2, 3, Chung-Huang Yang 1, 4 1. 1 Chinese Cryptology and Information Security Association,
CORAS for Research of Considering the Integration Risk Management with ISO/IEC 27005 Ya-Ping Fu 1, 4, Kwo-Jean Farn 1, 2, 3, Chung-Huang Yang 1, 4 1. 1 Chinese Cryptology and Information Security Association,
CORAS for the Research of ISAC
 International Conference on Convergence and Hybrid Information Technology 2008 CORAS for the Research of ISAC Ya-Ping Fu #, Kwo-Jean Farn *+, Chung-Huang Yang # Chinese Cryptology and Information Security
International Conference on Convergence and Hybrid Information Technology 2008 CORAS for the Research of ISAC Ya-Ping Fu #, Kwo-Jean Farn *+, Chung-Huang Yang # Chinese Cryptology and Information Security
Tool-Supported Cyber-Risk Assessment
 Tool-Supported Cyber-Risk Assessment Security Assessment for Systems, Services and Infrastructures (SASSI'15) Bjørnar Solhaug (SINTEF ICT) Berlin, September 15, 2015 1 Me Bjørnar Solhaug Bjornar.Solhaug@sintef.no
Tool-Supported Cyber-Risk Assessment Security Assessment for Systems, Services and Infrastructures (SASSI'15) Bjørnar Solhaug (SINTEF ICT) Berlin, September 15, 2015 1 Me Bjørnar Solhaug Bjornar.Solhaug@sintef.no
Recommendation-Based Trust Model in P2P Network Environment
 Recommendation-Based Trust Model in P2P Network Environment Yueju Lei, Guangxi Chen To cite this version: Yueju Lei, Guangxi Chen. Recommendation-Based Trust Model in P2P Network Environment. Zhongzhi
Recommendation-Based Trust Model in P2P Network Environment Yueju Lei, Guangxi Chen To cite this version: Yueju Lei, Guangxi Chen. Recommendation-Based Trust Model in P2P Network Environment. Zhongzhi
A Model Transformation from Misuse Cases to Secure Tropos
 A Model Transformation from Misuse Cases to Secure Tropos Naved Ahmed 1, Raimundas Matulevičius 1, and Haralambos Mouratidis 2 1 Institute of Computer Science, University of Tartu, Estonia {naved,rma}@ut.ee
A Model Transformation from Misuse Cases to Secure Tropos Naved Ahmed 1, Raimundas Matulevičius 1, and Haralambos Mouratidis 2 1 Institute of Computer Science, University of Tartu, Estonia {naved,rma}@ut.ee
Trustworthiness of Data on the Web
 Trustworthiness of Data on the Web Olaf Hartig Humboldt-Universität zu Berlin Department of Computer Science hartig@informatik.hu-berlin.de Abstract: We aim for an evolution of the Web of data to a Web
Trustworthiness of Data on the Web Olaf Hartig Humboldt-Universität zu Berlin Department of Computer Science hartig@informatik.hu-berlin.de Abstract: We aim for an evolution of the Web of data to a Web
Identifiers, Privacy and Trust in the Internet of Services
 Identifiers, Privacy and Trust in the Internet of Services Leonardo A. Martucci, Sebastian Ries, and Max Mühlhäuser Technische Universität Darmstadt, CASED Mornewegstr. 32, DE-64293, Darmstadt, Germany
Identifiers, Privacy and Trust in the Internet of Services Leonardo A. Martucci, Sebastian Ries, and Max Mühlhäuser Technische Universität Darmstadt, CASED Mornewegstr. 32, DE-64293, Darmstadt, Germany
La ricerca europea sulla sicurezza in grande azienda ICT Italiana
 La ricerca europea sulla sicurezza in grande azienda ICT Italiana Seconda Giornata della Sicurezza Informatica in Sardegna Auditorium Parco Tecnologico di Pula 5 Novembre 2008 Domenico Presenza (domenico.presenza@eng.it)
La ricerca europea sulla sicurezza in grande azienda ICT Italiana Seconda Giornata della Sicurezza Informatica in Sardegna Auditorium Parco Tecnologico di Pula 5 Novembre 2008 Domenico Presenza (domenico.presenza@eng.it)
 [Publication 4] Zheng Yan and Piotr Cofta, A Mechanism for Trust Sustainability among Trusted Computing Platforms", In Proceedings of the 1 st International Conference on Trust and Privacy in Digital Business
[Publication 4] Zheng Yan and Piotr Cofta, A Mechanism for Trust Sustainability among Trusted Computing Platforms", In Proceedings of the 1 st International Conference on Trust and Privacy in Digital Business
Federated Authentication for E-Infrastructures
 Federated Authentication for E-Infrastructures A growing challenge for on-line e-infrastructures is to manage an increasing number of user accounts, ensuring that accounts are only used by their intended
Federated Authentication for E-Infrastructures A growing challenge for on-line e-infrastructures is to manage an increasing number of user accounts, ensuring that accounts are only used by their intended
Integrating OpenID with proxy re-encryption to enhance privacy in cloud-based identity services
 Integrating OpenID with proxy re-encryption to enhance privacy in cloud-based identity services David Nuñez, Isaac Agudo, and Javier Lopez Network, Information and Computer Security Laboratory (NICS Lab)
Integrating OpenID with proxy re-encryption to enhance privacy in cloud-based identity services David Nuñez, Isaac Agudo, and Javier Lopez Network, Information and Computer Security Laboratory (NICS Lab)
38050 Povo Trento (Italy), Via Sommarive 14 IWTRUST: IMPROVING USER TRUST IN ANSWERS FROM THE WEB
 UNIVERSITY OF TRENTO DEPARTMENT OF INFORMATION AND COMMUNICATION TECHNOLOGY 38050 Povo Trento (Italy), Via Sommarive 14 http://www.dit.unitn.it IWTRUST: IMPROVING USER TRUST IN ANSWERS FROM THE WEB Ilya
UNIVERSITY OF TRENTO DEPARTMENT OF INFORMATION AND COMMUNICATION TECHNOLOGY 38050 Povo Trento (Italy), Via Sommarive 14 http://www.dit.unitn.it IWTRUST: IMPROVING USER TRUST IN ANSWERS FROM THE WEB Ilya
A Survey On Privacy Conflict Detection And Resolution In Online Social Networks
 A Survey On Privacy Conflict Detection And Resolution In Online Social Networks Miss. Patare Tanuja Vilas 1, Prof.N.G.Pardeshi 2 1 PG Student, SRES COE, Kopargaon, SPPU, Maharashtra, India 2 Assistant
A Survey On Privacy Conflict Detection And Resolution In Online Social Networks Miss. Patare Tanuja Vilas 1, Prof.N.G.Pardeshi 2 1 PG Student, SRES COE, Kopargaon, SPPU, Maharashtra, India 2 Assistant
A privacy-enhancing technology:
 A privacy-enhancing technology: sticky policies Privacy-Enhancing Technologies / DD3344 Guillermo Rodríguez Cano Stockholm, November 12th, 2012 what are they? how do they work? what are their problems?
A privacy-enhancing technology: sticky policies Privacy-Enhancing Technologies / DD3344 Guillermo Rodríguez Cano Stockholm, November 12th, 2012 what are they? how do they work? what are their problems?
OASIS: Architecture, Model and Management of Policy
 OASIS: Architecture, Model and Management of Policy Ken Moody Computer Laboratory, University of Cambridge 1 Overview OASIS : Architecture, Model and Policy 1. background to the research people, projects
OASIS: Architecture, Model and Management of Policy Ken Moody Computer Laboratory, University of Cambridge 1 Overview OASIS : Architecture, Model and Policy 1. background to the research people, projects
Contents. 1 A Tribute to Antoni Olivé on the Occasion of His Retirement... 1 Janis Bubenko, Colette Rolland and Arne Sølvberg
 Contents 1 A Tribute to Antoni Olivé on the Occasion of His Retirement....... 1 Janis Bubenko, Colette Rolland and Arne Sølvberg 2 30 Years of Contributions to Conceptual Modeling............... 7 Jordi
Contents 1 A Tribute to Antoni Olivé on the Occasion of His Retirement....... 1 Janis Bubenko, Colette Rolland and Arne Sølvberg 2 30 Years of Contributions to Conceptual Modeling............... 7 Jordi
IEEE 2013 JAVA PROJECTS Contact No: KNOWLEDGE AND DATA ENGINEERING
 IEEE 2013 JAVA PROJECTS www.chennaisunday.com Contact No: 9566137117 KNOWLEDGE AND DATA ENGINEERING (DATA MINING) 1. A Fast Clustering-Based Feature Subset Selection Algorithm for High Dimensional Data
IEEE 2013 JAVA PROJECTS www.chennaisunday.com Contact No: 9566137117 KNOWLEDGE AND DATA ENGINEERING (DATA MINING) 1. A Fast Clustering-Based Feature Subset Selection Algorithm for High Dimensional Data
Federated authentication for e-infrastructures
 Federated authentication for e-infrastructures 5 September 2014 Federated Authentication for E-Infrastructures Jisc Published under the CC BY 4.0 licence creativecommons.org/licenses/by/4.0/ Contents Introduction
Federated authentication for e-infrastructures 5 September 2014 Federated Authentication for E-Infrastructures Jisc Published under the CC BY 4.0 licence creativecommons.org/licenses/by/4.0/ Contents Introduction
MANAGEMENT OF INFORMATION SECURITY INCIDENTS
 MANAGEMENT OF INFORMATION SECURITY INCIDENTS PhD. Eng Daniel COSTIN Polytechnic University of Bucharest ABSTRACT Reporting information security events. Reporting information security weaknesses. Responsible
MANAGEMENT OF INFORMATION SECURITY INCIDENTS PhD. Eng Daniel COSTIN Polytechnic University of Bucharest ABSTRACT Reporting information security events. Reporting information security weaknesses. Responsible
Security Analysis Part I: Basics
 Security Analysis Part I: Basics Ketil Stølen, SINTEF & UiO CORAS 1 Acknowledgments The research for the contents of this tutorial has partly been funded by the European Commission through the FP7 project
Security Analysis Part I: Basics Ketil Stølen, SINTEF & UiO CORAS 1 Acknowledgments The research for the contents of this tutorial has partly been funded by the European Commission through the FP7 project
Input to ORMS TC Definitions and reference model proposals, Use cases. Daniela Bourges Waldegg
 Input to ORMS TC Definitions and reference model proposals, Use cases Daniela Bourges Waldegg dbw@zurich.ibm.com Reputation definitions Reputation definitions Reputation is a collective evaluation of an
Input to ORMS TC Definitions and reference model proposals, Use cases Daniela Bourges Waldegg dbw@zurich.ibm.com Reputation definitions Reputation definitions Reputation is a collective evaluation of an
INTRUSION DETECTION AND CORRELATION. Challenges and Solutions
 INTRUSION DETECTION AND CORRELATION Challenges and Solutions Advances in Information Security Sushil Jajodia Consulting editor Center for Secure Information Systems George Mason University Fairfax, VA
INTRUSION DETECTION AND CORRELATION Challenges and Solutions Advances in Information Security Sushil Jajodia Consulting editor Center for Secure Information Systems George Mason University Fairfax, VA
"Charting the Course... Certified Information Systems Auditor (CISA) Course Summary
 Course Summary Description In this course, you will perform evaluations of organizational policies, procedures, and processes to ensure that an organization's information systems align with overall business
Course Summary Description In this course, you will perform evaluations of organizational policies, procedures, and processes to ensure that an organization's information systems align with overall business
An Integrated Framework for Multi-layer Certification-based Assurance
 1 An Integrated Framework for Multi-layer Certification-based Assurance ACSAC 2014 - Layered Assurance Workshop New Orleans, Louisiana, USA. December 2014 Authors: Rajesh Harjani, Marcos Arjona, Javier
1 An Integrated Framework for Multi-layer Certification-based Assurance ACSAC 2014 - Layered Assurance Workshop New Orleans, Louisiana, USA. December 2014 Authors: Rajesh Harjani, Marcos Arjona, Javier
Featuring Trust and Reputation Management Systems for Constrained Hardware Devices*
 Featuring Trust and Reputation Management Systems for Constrained Hardware Devices* Rodrigo Román, M. Carmen Fernández-Gago, Javier López University of Málaga, Spain *(Wireless Sensor Networks) Contents
Featuring Trust and Reputation Management Systems for Constrained Hardware Devices* Rodrigo Román, M. Carmen Fernández-Gago, Javier López University of Málaga, Spain *(Wireless Sensor Networks) Contents
AARC Overview. Licia Florio, David Groep. 21 Jan presented by David Groep, Nikhef.
 AARC Overview Licia Florio, David Groep 21 Jan 2015 presented by David Groep, Nikhef AARC? Authentication and Authorisation for Research and Collaboration support the collaboration model across institutional
AARC Overview Licia Florio, David Groep 21 Jan 2015 presented by David Groep, Nikhef AARC? Authentication and Authorisation for Research and Collaboration support the collaboration model across institutional
TATA: Towards Anonymous Trusted Authentication
 TATA: Towards Anonymous Trusted Authentication Daniele Quercia, Stephen Hailes, Licia Capra Department of Computer Science, University College London, London, WC1E 6BT, UK {D.Quercia, S.Hailes, L.Capra}@cs.ucl.ac.uk
TATA: Towards Anonymous Trusted Authentication Daniele Quercia, Stephen Hailes, Licia Capra Department of Computer Science, University College London, London, WC1E 6BT, UK {D.Quercia, S.Hailes, L.Capra}@cs.ucl.ac.uk
You ve been breached: Now What? Minnesota s Data Breach Preparation and Notification for Electronic Data
 You ve been breached: Now What? Minnesota s Data Breach Preparation and Notification for Electronic Data Enterprise IT Management Initiative State of Minnesota Jenna Covey, jenna.covey@state.mn.us, 651-201-1199
You ve been breached: Now What? Minnesota s Data Breach Preparation and Notification for Electronic Data Enterprise IT Management Initiative State of Minnesota Jenna Covey, jenna.covey@state.mn.us, 651-201-1199
Course Design Document. IS436: Data Security and Privacy. Version 1.0
 Course Design Document IS436: Data Security and Privacy Version 1.0 7 July 2014 Table of Content 1 Versions History... 3 2 Overview of Data Security and Privacy Course... 3 2.1 Synopsis... 3 2.2 Prerequisites...
Course Design Document IS436: Data Security and Privacy Version 1.0 7 July 2014 Table of Content 1 Versions History... 3 2 Overview of Data Security and Privacy Course... 3 2.1 Synopsis... 3 2.2 Prerequisites...
SCION: A Secure Multipath Interdomain Routing Architecture. Adrian Perrig Network Security Group, ETH Zürich
 SCION: A Secure Multipath Interdomain Routing Architecture Adrian Perrig Network Security Group, ETH Zürich SCION: Next-generation Internet Architecture Path-aware networking: sender knows packet s path
SCION: A Secure Multipath Interdomain Routing Architecture Adrian Perrig Network Security Group, ETH Zürich SCION: Next-generation Internet Architecture Path-aware networking: sender knows packet s path
Network-Aware Evaluation Environment for Reputation Systems
 Network-Aware Evaluation Environment for Reputation Systems Alessandro Celestini, Rocco Nicola, Francesco Tiezzi To cite this version: Alessandro Celestini, Rocco Nicola, Francesco Tiezzi Network-Aware
Network-Aware Evaluation Environment for Reputation Systems Alessandro Celestini, Rocco Nicola, Francesco Tiezzi To cite this version: Alessandro Celestini, Rocco Nicola, Francesco Tiezzi Network-Aware
FORMAL ASPECTS IN SECURITY AND TRUST
 FORMAL ASPECTS IN SECURITY AND TRUST IFIP - The International Federation for Information Processing IFIP was founded in 1960 under the auspices of UNESCO, following the First World Computer Congress held
FORMAL ASPECTS IN SECURITY AND TRUST IFIP - The International Federation for Information Processing IFIP was founded in 1960 under the auspices of UNESCO, following the First World Computer Congress held
Five steps to securing personal data online Gary Shipsey Managing Director
 Five steps to securing personal data online Gary Shipsey Managing Director 25 September 2014 Agenda Learn from the mistakes of others and protect personal information online. 1 2 Where does your information
Five steps to securing personal data online Gary Shipsey Managing Director 25 September 2014 Agenda Learn from the mistakes of others and protect personal information online. 1 2 Where does your information
A Framework for Managing Crime and Fraud
 A Framework for Managing Crime and Fraud ASIS International Asia Pacific Security Forum & Exhibition Macau, December 4, 2013 Torsten Wolf, CPP Head of Group Security Operations Agenda Introduction Economic
A Framework for Managing Crime and Fraud ASIS International Asia Pacific Security Forum & Exhibition Macau, December 4, 2013 Torsten Wolf, CPP Head of Group Security Operations Agenda Introduction Economic
Certified Information Systems Auditor (CISA)
 Certified Information Systems Auditor (CISA) 1. Domain 1 The Process of Auditing Information Systems Provide audit services in accordance with IT audit standards to assist the organization in protecting
Certified Information Systems Auditor (CISA) 1. Domain 1 The Process of Auditing Information Systems Provide audit services in accordance with IT audit standards to assist the organization in protecting
Developing an integrated approach to the analysis of MOD cyber-related risks
 Developing an integrated approach to the analysis of MOD cyber-related risks Colette Jeffery, James Tate Defence Science Technology Laboratory COST Expert Judgement Meeting 12 to 14 October 2016 COVERING
Developing an integrated approach to the analysis of MOD cyber-related risks Colette Jeffery, James Tate Defence Science Technology Laboratory COST Expert Judgement Meeting 12 to 14 October 2016 COVERING
Introduction and Charge
 GENI and Security Deborah Frincke, PNNL, co-chair Matt Bishop, UCD, co-chair Chen-Nee Chuah, UCD, community collaborator Karl Levitt, NSF, NSF co-ordinator Mike Reiter, CMU, GENI security leader and provider
GENI and Security Deborah Frincke, PNNL, co-chair Matt Bishop, UCD, co-chair Chen-Nee Chuah, UCD, community collaborator Karl Levitt, NSF, NSF co-ordinator Mike Reiter, CMU, GENI security leader and provider
Key Findings from the Global State of Information Security Survey 2017 Indonesian Insights
 www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
PRIVACY POLICY TABLE OF CONTENTS. Last updated October 05, 2018
 PRIVACY POLICY Last updated October 05, 2018 Thank you for choosing to be part of Vistalytics Inc., ( Company, we, us, or our ). We are committed to protecting your personal information and your right
PRIVACY POLICY Last updated October 05, 2018 Thank you for choosing to be part of Vistalytics Inc., ( Company, we, us, or our ). We are committed to protecting your personal information and your right
PERVASIVE AUTHENTICATION AND AUTHORIZATION INFRASTRUCTURES FOR MOBILE USERS USING PERVASIVE-PKI
 PERVASIVE AUTHENTICATION AND AUTHORIZATION INFRASTRUCTURES FOR MOBILE USERS USING PERVASIVE-PKI Ms. Sneha R. Kaware M.E First Year, computer science and Engineering, H.V.P.M college of Engg & Tech, Amravati,
PERVASIVE AUTHENTICATION AND AUTHORIZATION INFRASTRUCTURES FOR MOBILE USERS USING PERVASIVE-PKI Ms. Sneha R. Kaware M.E First Year, computer science and Engineering, H.V.P.M college of Engg & Tech, Amravati,
An Extension of Business Process Model and Notation for Security Risk Management
 An Extension of Business Process Model and Notation for Security Risk Management Olga Altuhhova, Raimundas Matulevičius and Naved Ahmed Institute of Computer Science, University of Tartu J. Liivi 2, 50409
An Extension of Business Process Model and Notation for Security Risk Management Olga Altuhhova, Raimundas Matulevičius and Naved Ahmed Institute of Computer Science, University of Tartu J. Liivi 2, 50409
Net Trust: User-Centered Detection of Pharming, Phishing and Fraud. L Jean Camp
 Net Trust: User-Centered Detection of Pharming, Phishing and Fraud L Jean Camp www.ljean.com Core Problem Statement How to inform individual assessments of trustworthiness of a potential online transaction.
Net Trust: User-Centered Detection of Pharming, Phishing and Fraud L Jean Camp www.ljean.com Core Problem Statement How to inform individual assessments of trustworthiness of a potential online transaction.
Welcome to EXE th International Workshop on Executable Modeling October 14, 2018, Copenhagen, Denmark. Organizers:
 Welcome to EXE 2018 4th International Workshop on Executable Modeling October 14, 2018, Copenhagen, Denmark Tanja Mayerhofer TU Wien, Austria Jeff Gray University of Alabama, USA Organizers: Philip Langer
Welcome to EXE 2018 4th International Workshop on Executable Modeling October 14, 2018, Copenhagen, Denmark Tanja Mayerhofer TU Wien, Austria Jeff Gray University of Alabama, USA Organizers: Philip Langer
Personal & Trusted Cloud
 Inria Saclay-IDF November 7th, 2016 Colloque Inria CAPPRIS Personal & Trusted Cloud Nicolas Anciaux, SMIS team, Inria Saclay-IDF/UVSQ Towards a personal and trusted cloud Current model wrt. management
Inria Saclay-IDF November 7th, 2016 Colloque Inria CAPPRIS Personal & Trusted Cloud Nicolas Anciaux, SMIS team, Inria Saclay-IDF/UVSQ Towards a personal and trusted cloud Current model wrt. management
The PKI Secure Kernel Protection Profile. Version 1.1 evaluated
 The PKI Secure Kernel Protection Profile Version 1.1 evaluated April 4, 2002 ii This document is the first of a series of Protection Profiles to cover a Public Key Infrastructure architecture. It has been
The PKI Secure Kernel Protection Profile Version 1.1 evaluated April 4, 2002 ii This document is the first of a series of Protection Profiles to cover a Public Key Infrastructure architecture. It has been
Best Practices in Securing Your Customer Data in Salesforce, Force.com & Chatter
 White Paper Best Practices in Securing Your Customer Data in Salesforce, Force.com & Chatter Overcoming Security, Privacy & Compliance Concerns 333 W. San Carlos Street San Jose, CA 95110 Table of Contents
White Paper Best Practices in Securing Your Customer Data in Salesforce, Force.com & Chatter Overcoming Security, Privacy & Compliance Concerns 333 W. San Carlos Street San Jose, CA 95110 Table of Contents
An Architecture for Distributed OASIS Services
 An Architecture for Distributed OASIS Services John H Hine Walt Yao Jean Bacon Ken Moody Victoria University of Wellington, NZ Computer Laboratory, Cambridge, UK 0 Overview An Architecture for Distributed
An Architecture for Distributed OASIS Services John H Hine Walt Yao Jean Bacon Ken Moody Victoria University of Wellington, NZ Computer Laboratory, Cambridge, UK 0 Overview An Architecture for Distributed
How to ensure control and security when moving to SaaS/cloud applications
 How to ensure control and security when moving to SaaS/cloud applications Stéphane Hurtaud Partner Information & Technology Risk Deloitte Laurent de la Vaissière Directeur Information & Technology Risk
How to ensure control and security when moving to SaaS/cloud applications Stéphane Hurtaud Partner Information & Technology Risk Deloitte Laurent de la Vaissière Directeur Information & Technology Risk
Counted Total Percent Ballots Registered Percent % 8,365. Counted Total Percent Ballots Registered Percent
 Page 1 Number : 37,460 of 842,263 = 4.45% Reporting: 582 of 582 = 100.00% DEM - UNITED STATES SENATOR, Vote For 1 RON KIRK 4,610 61.22% 18,123 61.89% 22,733 61.75% KEN BENTSEN 852 11.31% 2,779 9.49% 3,631
Page 1 Number : 37,460 of 842,263 = 4.45% Reporting: 582 of 582 = 100.00% DEM - UNITED STATES SENATOR, Vote For 1 RON KIRK 4,610 61.22% 18,123 61.89% 22,733 61.75% KEN BENTSEN 852 11.31% 2,779 9.49% 3,631
A Tool for Managing Evolving Security Requirements
 A Tool for Managing Evolving Security Requirements Gábor Bergmann 1, Fabio Massacci 2, Federica Paci 2, Thein Tun 3, Dániel Varró 1, and Yijun Yu 3 1 DMIS - Budapest University of Technology and Economics,
A Tool for Managing Evolving Security Requirements Gábor Bergmann 1, Fabio Massacci 2, Federica Paci 2, Thein Tun 3, Dániel Varró 1, and Yijun Yu 3 1 DMIS - Budapest University of Technology and Economics,
At a Glance. Introducing Security Metrics
 At a Glance PART I Introducing Security Metrics 1 What Is a Security Metric?... 3 2 Designing Effective Security Metrics... 25 3 Understanding Data... 55 Case Study 1: In Search of Enterprise Metrics...
At a Glance PART I Introducing Security Metrics 1 What Is a Security Metric?... 3 2 Designing Effective Security Metrics... 25 3 Understanding Data... 55 Case Study 1: In Search of Enterprise Metrics...
Achilles System Certification (ASC) from GE Digital
 Achilles System Certification (ASC) from GE Digital Frequently Asked Questions GE Digital Achilles System Certification FAQ Sheet 1 Safeguard your devices and meet industry benchmarks for industrial cyber
Achilles System Certification (ASC) from GE Digital Frequently Asked Questions GE Digital Achilles System Certification FAQ Sheet 1 Safeguard your devices and meet industry benchmarks for industrial cyber
SOCIAL NETWORKING IN TODAY S BUSINESS WORLD
 SOCIAL NETWORKING IN TODAY S BUSINESS WORLD AGENDA Review the use of social networking applications within the business environment Review current trends in threats, attacks and incidents Understand how
SOCIAL NETWORKING IN TODAY S BUSINESS WORLD AGENDA Review the use of social networking applications within the business environment Review current trends in threats, attacks and incidents Understand how
Privacy Preserving Ranked Multi-Keyword Search for Multiple Data Owners in Cloud Computing
 S.NO PROJECT CODE IEEE JAVA PROJECT TITLES DOMAIN 1 NEO1501 A Hybrid Cloud Approach for Secure Authorized Deduplication 2 NEO1502 A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud
S.NO PROJECT CODE IEEE JAVA PROJECT TITLES DOMAIN 1 NEO1501 A Hybrid Cloud Approach for Secure Authorized Deduplication 2 NEO1502 A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud
Innovations in Federal Statistics: Combining Data Sources While Protecting Privacy
 Innovations in Federal Statistics: Combining Data Sources While Protecting Privacy Brian A. Harris-Kojetin, Deputy Director, Committee on National Statistics Washington, DC June 5, 2017 Acknowledgements
Innovations in Federal Statistics: Combining Data Sources While Protecting Privacy Brian A. Harris-Kojetin, Deputy Director, Committee on National Statistics Washington, DC June 5, 2017 Acknowledgements
Overview of Provenance on the Web
 Overview of Provenance on the Web by the W3C Provenance Incubator Group Semantic Web Activity World Wide Web Consortium http://www.w3.org/2005/incubator/prov/wiki Special thanks to contributing group members:
Overview of Provenance on the Web by the W3C Provenance Incubator Group Semantic Web Activity World Wide Web Consortium http://www.w3.org/2005/incubator/prov/wiki Special thanks to contributing group members:
Summer Assignment for BTEC Level 3 Nationals in Information Technology
 Summer Assignment for BTEC Level 3 Nationals in Information Technology Deadline for Independent Learning Activity: Friday 14 th September 2018 (scroll to bottom) Exam Board: Pearson BTEC Level 3 Extended
Summer Assignment for BTEC Level 3 Nationals in Information Technology Deadline for Independent Learning Activity: Friday 14 th September 2018 (scroll to bottom) Exam Board: Pearson BTEC Level 3 Extended
Tropos: Security. Agent-Oriented Software Engineering course Laurea Specialistica in Informatica A.A
 Tropos: Security Paolo Giorgini Department of Information and Communication Technology University of Trento - Italy http://www.dit.unitn.it/~pgiorgio Agent-Oriented Software Engineering course Laurea Specialistica
Tropos: Security Paolo Giorgini Department of Information and Communication Technology University of Trento - Italy http://www.dit.unitn.it/~pgiorgio Agent-Oriented Software Engineering course Laurea Specialistica
Dr Nick Papanikolaou e-security Group International Digital Laboratory WMG, University of Warwick
 Towards Integrated t Policy Management for Privacy Dr Nick Papanikolaou e-security Group International Digital Laboratory WMG, University of Warwick http://go.warwick.ac.uk/nikos Context t Joint work with
Towards Integrated t Policy Management for Privacy Dr Nick Papanikolaou e-security Group International Digital Laboratory WMG, University of Warwick http://go.warwick.ac.uk/nikos Context t Joint work with
Trust4All: a Trustworthy Middleware Platform for Component Software
 Proceedings of the 7th WSEAS International Conference on Applied Informatics and Communications, Athens, Greece, August 24-26, 2007 124 Trust4All: a Trustworthy Middleware Platform for Component Software
Proceedings of the 7th WSEAS International Conference on Applied Informatics and Communications, Athens, Greece, August 24-26, 2007 124 Trust4All: a Trustworthy Middleware Platform for Component Software
Integrated Key Exchange Protocol Capable of Revealing Spoofing and Resisting Dictionary Attacks
 Integrated Key Exchange Protocol Capable of Revealing Spoofing and Resisting Dictionary Attacks David Lai and Zhongwei Zhang Department of Mathematics and Computing, University of Southern Queensland,
Integrated Key Exchange Protocol Capable of Revealing Spoofing and Resisting Dictionary Attacks David Lai and Zhongwei Zhang Department of Mathematics and Computing, University of Southern Queensland,
Grid Security Policy
 CERN-EDMS-428008 Version 5.7a Page 1 of 9 Joint Security Policy Group Grid Security Policy Date: 10 October 2007 Version: 5.7a Identifier: https://edms.cern.ch/document/428008 Status: Released Author:
CERN-EDMS-428008 Version 5.7a Page 1 of 9 Joint Security Policy Group Grid Security Policy Date: 10 October 2007 Version: 5.7a Identifier: https://edms.cern.ch/document/428008 Status: Released Author:
IoT Security Foundation (IoTSF)
 IoT Security Foundation (IoTSF) Introduction 10/03/2017 Public 1 IoT: What more can be said? $: The economic impact of the Internet of Things will be measured in $trillions. : The number of connected devices
IoT Security Foundation (IoTSF) Introduction 10/03/2017 Public 1 IoT: What more can be said? $: The economic impact of the Internet of Things will be measured in $trillions. : The number of connected devices
Integrating Security in the Development Process with UML
 1 ntegrating Security in the Development Process with UML Folker den Braber SNTEF CT, Norway Mass Soldal Lund SNTEF CT, Norway Ketil Stølen SNTEF CT, Norway Fredrik Vraalsen SNTEF CT, Norway NTRODUCTON
1 ntegrating Security in the Development Process with UML Folker den Braber SNTEF CT, Norway Mass Soldal Lund SNTEF CT, Norway Ketil Stølen SNTEF CT, Norway Fredrik Vraalsen SNTEF CT, Norway NTRODUCTON
COMESA CYBER SECURITY PROGRAM KHARTOUM, SUDAN
 COMESA CYBER SECURITY PROGRAM KHARTOUM, SUDAN 24-27 July 2016 1 CONTENT INTRODUCTION POLICY OBJECTIVES POLICY AND LEGISLATIVE PRINCIPLES CYBER SECURITY STRATEGY CHALLENGES AND OPPORTUNITIES CAPACITY BUILDING
COMESA CYBER SECURITY PROGRAM KHARTOUM, SUDAN 24-27 July 2016 1 CONTENT INTRODUCTION POLICY OBJECTIVES POLICY AND LEGISLATIVE PRINCIPLES CYBER SECURITY STRATEGY CHALLENGES AND OPPORTUNITIES CAPACITY BUILDING
LEA Workshop. Champika Wijayatunga & George Kuo, APNIC Wellington, New Zealand 09, May, 2013
 LEA Workshop Champika Wijayatunga & George Kuo, APNIC Wellington, New Zealand 09, May, 2013 Agenda Introduction to APNIC Know about APNIC Internet Policy Development How the Internet Policies are developed
LEA Workshop Champika Wijayatunga & George Kuo, APNIC Wellington, New Zealand 09, May, 2013 Agenda Introduction to APNIC Know about APNIC Internet Policy Development How the Internet Policies are developed
A Case For OneSwarm. Tom Anderson University of Washington.
 A Case For OneSwarm Tom Anderson University of Washington http://oneswarm.cs.washington.edu/ With: Jarret Falkner, Tomas Isdal, Alex Jaffe, John P. John, Arvind Krishnamurthy, Harsha Madhyastha and Mike
A Case For OneSwarm Tom Anderson University of Washington http://oneswarm.cs.washington.edu/ With: Jarret Falkner, Tomas Isdal, Alex Jaffe, John P. John, Arvind Krishnamurthy, Harsha Madhyastha and Mike
MCGILL UNIVERSITY/PEOPIL CONFERENCE DUBLIN OCTOBER 2018
 Cyber Security: Airport risk and liability Jean-Michel Fobe Adrian Cioranu MCGILL UNIVERSITY/PEOPIL Conference on International Aviation & Liability DUBLIN 19-20 Airport cybersecurity concerns Airport
Cyber Security: Airport risk and liability Jean-Michel Fobe Adrian Cioranu MCGILL UNIVERSITY/PEOPIL Conference on International Aviation & Liability DUBLIN 19-20 Airport cybersecurity concerns Airport
INTRUSION DETECTION IN DISTRIBUTED SYSTEMS An Abstraction-Based Approach
 INTRUSION DETECTION IN DISTRIBUTED SYSTEMS An Abstraction-Based Approach Library of Congress Cataloging-in-Publication ISBN 978-1-4613-5091-0 ISBN 978-1-4615-0467-2 (ebook) DOI 10.1007/978-1-4615-0467-2
INTRUSION DETECTION IN DISTRIBUTED SYSTEMS An Abstraction-Based Approach Library of Congress Cataloging-in-Publication ISBN 978-1-4613-5091-0 ISBN 978-1-4615-0467-2 (ebook) DOI 10.1007/978-1-4615-0467-2
Sybil defenses via social networks
 Sybil defenses via social networks Abhishek University of Oslo, Norway 19/04/2012 1 / 24 Sybil identities Single user pretends many fake/sybil identities i.e., creating multiple accounts observed in real-world
Sybil defenses via social networks Abhishek University of Oslo, Norway 19/04/2012 1 / 24 Sybil identities Single user pretends many fake/sybil identities i.e., creating multiple accounts observed in real-world
Defining Computer Security Incident Response Teams
 Defining Computer Security Incident Response Teams Robin Ruefle January 2007 ABSTRACT: A computer security incident response team (CSIRT) is a concrete organizational entity (i.e., one or more staff) that
Defining Computer Security Incident Response Teams Robin Ruefle January 2007 ABSTRACT: A computer security incident response team (CSIRT) is a concrete organizational entity (i.e., one or more staff) that
Web Service Recommendation Using Hybrid Approach
 e-issn 2455 1392 Volume 2 Issue 5, May 2016 pp. 648 653 Scientific Journal Impact Factor : 3.468 http://www.ijcter.com Web Service Using Hybrid Approach Priyanshi Barod 1, M.S.Bhamare 2, Ruhi Patankar
e-issn 2455 1392 Volume 2 Issue 5, May 2016 pp. 648 653 Scientific Journal Impact Factor : 3.468 http://www.ijcter.com Web Service Using Hybrid Approach Priyanshi Barod 1, M.S.Bhamare 2, Ruhi Patankar
Software Quality and Infrastructure Protection for Diffuse Computing
 FY2001 ONR CIP/SW URI Software Quality and Infrastructure Protection for Diffuse Computing Principal Investigator: Andre Scedrov Institution: University of Pennsylvania URL: http://www.cis.upenn.edu/spyce
FY2001 ONR CIP/SW URI Software Quality and Infrastructure Protection for Diffuse Computing Principal Investigator: Andre Scedrov Institution: University of Pennsylvania URL: http://www.cis.upenn.edu/spyce
Bromium: Virtualization-Based Security
 Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
Patient Information Security
 Patient Information Security An overview of practice and procedure UK CAB Meeting 13th April 2012 Nathan Lea Senior Research Associate CHIME, UCL Overview - Questions that have been asked What happens
Patient Information Security An overview of practice and procedure UK CAB Meeting 13th April 2012 Nathan Lea Senior Research Associate CHIME, UCL Overview - Questions that have been asked What happens
Contributors. Acknowledgements Abbreviations
 Contributors Foreword Acknowledgements Abbreviations xi xvii xix xxi 1 Introduction 1 Chimay J. Anumba and Kirti Ruikar 1.1 Context 1 1.2 Structure of the book 2 References 4 2 Fundamentals of e-business
Contributors Foreword Acknowledgements Abbreviations xi xvii xix xxi 1 Introduction 1 Chimay J. Anumba and Kirti Ruikar 1.1 Context 1 1.2 Structure of the book 2 References 4 2 Fundamentals of e-business
CCISO Blueprint v1. EC-Council
 CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
Security Secure Information Sharing
 ASD Convention Workshop 6 e-standards: a Strategic Asset across the Value Chain Security Secure Information Sharing Steve SHEPHERD Executive Director UK CeB Istanbul, 6 October 2011 1 Information security
ASD Convention Workshop 6 e-standards: a Strategic Asset across the Value Chain Security Secure Information Sharing Steve SHEPHERD Executive Director UK CeB Istanbul, 6 October 2011 1 Information security
RELATIONSHIP AND CLOUD FACTORS AFFECTING GOVERNMENT CONFIDENCE IN THE PUBLIC CLOUD
 RELATIONSHIP AND CLOUD FACTORS AFFECTING GOVERNMENT CONFIDENCE IN THE PUBLIC CLOUD *Waleed Alghanim, **Dr. Feng Chen *PhD candidate, School of Computer Science and Informatics, De Montfort University,
RELATIONSHIP AND CLOUD FACTORS AFFECTING GOVERNMENT CONFIDENCE IN THE PUBLIC CLOUD *Waleed Alghanim, **Dr. Feng Chen *PhD candidate, School of Computer Science and Informatics, De Montfort University,
Security & Trust in Smart Cities. A Min Tjoa Vienna University of Technology & SBA Research
 Security & Trust in Smart Cities A Min Tjoa Vienna University of Technology & SBA Research Overview General Intro Smart City / Digital Trust Activities Quest for Specific Smart City Activities Quest for
Security & Trust in Smart Cities A Min Tjoa Vienna University of Technology & SBA Research Overview General Intro Smart City / Digital Trust Activities Quest for Specific Smart City Activities Quest for
PROPAGATING TRUST IN THE WEB SERVICES FRAMEWORK
 PROPAGATING TRUST IN THE WEB SERVICES FRAMEWORK Anitta Thomas and Lucas Venter School of Computing UNISA thomaa@unisa.ac.za ventelm@unisa.ac.za ABSTRACT In this paper, we discuss one possible way of establishing
PROPAGATING TRUST IN THE WEB SERVICES FRAMEWORK Anitta Thomas and Lucas Venter School of Computing UNISA thomaa@unisa.ac.za ventelm@unisa.ac.za ABSTRACT In this paper, we discuss one possible way of establishing
Safeguarding unclassified controlled technical information (UCTI)
 Safeguarding unclassified controlled technical information (UCTI) An overview Government Contract Services Bulletin Safeguarding UCTI An overview On November 18, 2013, the Department of Defense (DoD) issued
Safeguarding unclassified controlled technical information (UCTI) An overview Government Contract Services Bulletin Safeguarding UCTI An overview On November 18, 2013, the Department of Defense (DoD) issued
Curriculum Vitae. Affiliation : National Council of Research, Institute of Informatics and Telematics, Security group.
 Curriculum Vitae 1 Personal Information Name and Surname : Artsiom Yautsiukhin Gender : Male Family status : married; Date of birth : 09 November 1981 place of birth : Gomel, Republic of Belarus Citizenship
Curriculum Vitae 1 Personal Information Name and Surname : Artsiom Yautsiukhin Gender : Male Family status : married; Date of birth : 09 November 1981 place of birth : Gomel, Republic of Belarus Citizenship
Auditing and Monitoring in an Effective Institutional Compliance Program
 Auditing and Monitoring in an Effective Institutional Compliance Program 6 th Conference for Effective Compliance Systems in Higher Education Presented by David B. Crawford, Audit Manager Emeritus The
Auditing and Monitoring in an Effective Institutional Compliance Program 6 th Conference for Effective Compliance Systems in Higher Education Presented by David B. Crawford, Audit Manager Emeritus The
Final Project Report. Abstract. Document information
 Final Project Report Document information Project Title ATM Security Coordination and Support Project Number 16.06.02 Project Manager EUROCONTROL Deliverable Name Final Project Report Deliverable ID D100
Final Project Report Document information Project Title ATM Security Coordination and Support Project Number 16.06.02 Project Manager EUROCONTROL Deliverable Name Final Project Report Deliverable ID D100
arxiv: v1 [cs.cr] 30 May 2014
![arxiv: v1 [cs.cr] 30 May 2014 arxiv: v1 [cs.cr] 30 May 2014](/thumbs/74/70929876.jpg) ROMEO: ReputatiOn Model Enhancing OpenID Simulator Ginés Dólera Tormo 1, Félix Gómez Mármol 1, and Gregorio Martínez Pérez 2 arxiv:1405.7831v1 [cs.cr] 30 May 2014 1 NEC Europe Ltd., Kurfürsten-Anlage 36,
ROMEO: ReputatiOn Model Enhancing OpenID Simulator Ginés Dólera Tormo 1, Félix Gómez Mármol 1, and Gregorio Martínez Pérez 2 arxiv:1405.7831v1 [cs.cr] 30 May 2014 1 NEC Europe Ltd., Kurfürsten-Anlage 36,
Threat Based Defence Alonso Jose da Silva II. GRC & Cyber Security Conference - Bringing the Silos
 Threat Based Defence Alonso Jose da Silva II Objectives What we will discuss Threat-based defence: principles and function Running a threat intelligence cycle Case study - financial services fraud About
Threat Based Defence Alonso Jose da Silva II Objectives What we will discuss Threat-based defence: principles and function Running a threat intelligence cycle Case study - financial services fraud About
Initiative. Copyright Techdemocracy, 2017
 A Initiative 1 A Initiative 2 November 2 nd, 2017 Ken Pfeil / Gautam Dev 3 What is the purpose of the ACRG? The alliance purpose is to establish a standard framework for risk measurement, reporting and
A Initiative 1 A Initiative 2 November 2 nd, 2017 Ken Pfeil / Gautam Dev 3 What is the purpose of the ACRG? The alliance purpose is to establish a standard framework for risk measurement, reporting and
Novel Design and Implementation of Self Organizing Trust Model for Peer - Peer Systems
 Novel Design and Implementation of Self Organizing Trust Model for Peer - Peer Systems E. Latha M.Tech, Dept of Software Engineering (SE), Vinuthna Institute of Technology & Sciences. Abstract: This paper
Novel Design and Implementation of Self Organizing Trust Model for Peer - Peer Systems E. Latha M.Tech, Dept of Software Engineering (SE), Vinuthna Institute of Technology & Sciences. Abstract: This paper
Voting in the Colony Governance Protocol. Elena Dimitrova & Dr. Aron Fischer
 Voting in the Colony Governance Protocol Elena Dimitrova & Dr. Aron Fischer What is Colony? Colony is a platform for decentralised governance. It s about working together: coordination and collaboration.
Voting in the Colony Governance Protocol Elena Dimitrova & Dr. Aron Fischer What is Colony? Colony is a platform for decentralised governance. It s about working together: coordination and collaboration.
Objectives of the Security Policy Project for the University of Cyprus
 Objectives of the Security Policy Project for the University of Cyprus 1. Introduction 1.1. Objective The University of Cyprus intends to upgrade its Internet/Intranet security architecture. The University
Objectives of the Security Policy Project for the University of Cyprus 1. Introduction 1.1. Objective The University of Cyprus intends to upgrade its Internet/Intranet security architecture. The University
Trust is the Foundations for Computer Security
 Christian Damsgaard Jensen Department of Applied Mathematics and Computer Science Technical University of Denmark Christian.Jensen@imm.dtu.dk Security and Trust Computer security is sometimes divided into:
Christian Damsgaard Jensen Department of Applied Mathematics and Computer Science Technical University of Denmark Christian.Jensen@imm.dtu.dk Security and Trust Computer security is sometimes divided into:
Catching Inside Attackers
 Catching Inside Attackers Balancing Forensic Detectability and Privacy of Employees Jens Lindemann, Ephraim Zimmer, Dominik Herrmann, Hannes Federrath October 29, 2015 2014 US state of cybercrime survey
Catching Inside Attackers Balancing Forensic Detectability and Privacy of Employees Jens Lindemann, Ephraim Zimmer, Dominik Herrmann, Hannes Federrath October 29, 2015 2014 US state of cybercrime survey
IT Division Organization Chart Executive Overview
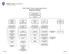 Executive Overview Vice President for Information Technology Bret Ellis Application Academic Technology Infrastructure IT Business Information Security Associate Director Peter Waite Director Associate
Executive Overview Vice President for Information Technology Bret Ellis Application Academic Technology Infrastructure IT Business Information Security Associate Director Peter Waite Director Associate
Pilots to support guest users solutions
 08-12-2016 Deliverable DSA1.1 Contractual Date: 31-07-2016 Actual Date: 08-12-2016 Grant Agreement No.: 653965 Work Package: SA1 Task Item: SA1.1 Pilot on Guest Identities Partner: GARR Document Code:
08-12-2016 Deliverable DSA1.1 Contractual Date: 31-07-2016 Actual Date: 08-12-2016 Grant Agreement No.: 653965 Work Package: SA1 Task Item: SA1.1 Pilot on Guest Identities Partner: GARR Document Code:
Application security: Anticipate the threat to reduce costs and guarantee business agility
 Application security: Anticipate the threat to reduce costs and guarantee business agility 73% of security incidents concern a web or mobile application 1. How safe is your corporate data? Hackers have
Application security: Anticipate the threat to reduce costs and guarantee business agility 73% of security incidents concern a web or mobile application 1. How safe is your corporate data? Hackers have
Mobile Agent Security. Chris Rygaard, CTO Aramira TM Corporation
 Mobile Agent Security Chris Rygaard, CTO Aramira TM Corporation 1 Agenda Security requirements Trusted third party Multi-jump security Trusted source Itinerary assurance Encrypted computing Signed code
Mobile Agent Security Chris Rygaard, CTO Aramira TM Corporation 1 Agenda Security requirements Trusted third party Multi-jump security Trusted source Itinerary assurance Encrypted computing Signed code
IT Division Organization Chart Executive Overview
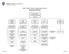 Executive Overview Vice President for Information Technology Bret Ellis Application Academic Technology Infrastructure IT Business Information Security Associate Director Peter Waite Director Associate
Executive Overview Vice President for Information Technology Bret Ellis Application Academic Technology Infrastructure IT Business Information Security Associate Director Peter Waite Director Associate
Statistical Trust Establishment in Wireless Sensor Networks
 Statistical Trust Establishment in Wireless Sensor Networks Matthew J. Probst and Sneha Kumar Kasera School of Computing, University of Utah Email: {mprobst, kasera}@cs.utah.edu Abstract We present a new
Statistical Trust Establishment in Wireless Sensor Networks Matthew J. Probst and Sneha Kumar Kasera School of Computing, University of Utah Email: {mprobst, kasera}@cs.utah.edu Abstract We present a new
