A Secured Web Services Based E-Commerce Model for SMME Using Digital Identity
|
|
|
- Gyles Lawson
- 6 years ago
- Views:
Transcription
1 International Journal of Advancements in Computing Technology A Secured Web Services Based E-Commerce Model for SMME Using Digital Identity Ashwin B.K *1, Kumaran K *1, Madhu Vishwanatham *2 V, M Sumaithri *1 *1 School of Information Technology and Engineering, VIT University, Vellore , Tamilnadu, India *2 School of Computer Science and Engineering, VIT University, Vellore , Tamilnadu, India ashwinbk@gmail.com, kumarankpl@gmail.com, vmadhuviswanatham@vit.ac.in, maithri.friend@gmail.com doi: /ijact.vol2.issue2.7 Abstract This paper deals with redesigning the existing e-commerce architecture that has provided a platform for the large companies to sell their products so that it can provide a place on internet for Small Medium and Micro Enterprises (SMME) companies to sell their products. E-commerce is to buy and sell the goods or services between vendors and purchasers electronically over the internet. Information shared among traders should have certain level of integrity and also authorization of the people. This paper includes the digital identity of the vendor with the help of MAC address. As the World Wide Web grows faster, the internet traffic automatically increases and so it is necessary to provide a reliable and quick request processing. The paper includes the concept of Web service which makes the request processing more reliable and also, the data transfer in the form of XML makes it easier to transmit and retrieve the information. And also it can be converted to any form required. This new architecture of the e-commerce model helps to achieve all the above with high efficiency. 1. Introduction Keywords: e-commerce, digital identity, MAC address, SMME, web service Electronic commerce, which is commonly known as e-commerce or e-commerce, consists of the buying and selling of goods or services electronically over systems such as the Internet and any other computer networks. Due to widespread Internet usage, the amount of trade conducted electronically has increased extraordinarily. The use of commerce can be understood in this way, supply chain management, spurring and drawing on innovations in electronic funds transfer, internet marketing, and online transaction processing, electronic data interchange (EDI), inventory management systems, and automated data collection systems. Present day electronic commerce typically uses the World Wide Web at some point in the transaction's lifecycle, although it can encompass a wider range of technologies such as as well. Companies like Apple, Microsoft, Dell, HP, Transcend etc sell their products online to the clients directly through their online store. People can buy products directly from the manufacturers and suppliers whereas the Small Medium and Micro Enterprises (SMME) are not able to sell their products in the similar way to that of MNCs i.e. by creating their own online stores. An online store provides a trust among the buyers to believe and purchase the products at high level. A web service is defined as a software system designed to support interoperable machine-to-machine interaction over a network. It is currently the main implementation technology for Service-Oriented Architecture. It provides an interface which is described in a machine-processable format called Web Services Description Language (WSDL). WSDL is Web services are provided by the application service providers. Different heterogeneous systems in the network interact with the web service in a manner prescribed by its description using SOAP (Simple Object Access Protocol) messages. A SOAP message is an XML representation of a method call. It is important that it has independence from programming languages. It is typically conveyed using HTTP with an XML serialization in 79
2 A Secured Web Services Based E-Commerce Model for SMME Using Digital Identity Ashwin B.K, Kumaran K, Madhu Vishwanatham V, M Sumaithri conjunction with other web- related standards. Web services are the Internet Application Programming Interfaces (API) which can be accessed over any network, such as the Internet or World Wide Web, and can be executed on a remote system that hosts the requested services. Authorization is the method of providing different access rights to different users for the resources, which are mostly related to information security and computer security in general and to provide an access control in particular. More formally, it can be said as to authorize is to define an access policy for a specific user. Digital identity refers to the aspect of digital technology that is concerned with the representation of people s online equivalent in online transactions and mediation of people's experience of their own identity and the identity of other people and things. In cryptography, a certificate authority or certification authority (CA) is the entity that issues digital certificates for use by other parties. It can be considered as an example of a trusted third party. This provides the trust worthiness for the user on the service provided. CA s are the basic characteristic of many public key infrastructure (PKI) schemes. There are many commercial CA s that charge for their services. Whereas, there are also several providers issuing digital certificates to the public at no cost. Institutions and governments have their own CA s. 2. Related Work A business model helps in taking away some costly business activities in the value chain, which include advertising, negotiations, ordering, payment and delivery, and assigning them to cybermediaries (e-brokers). This results in decreased involvement of intermediaries in the business process and so the supplier gets more profit. [4] Presents a new business model that gives the resource constrained SMMEs, the necessary capacity to trade competitively on the global market places. This model is a hybrid model of two e-broker models, the virtual community model and the third-party e- broker model. Here, the suppliers form a virtual community to share ICT infrastructures and the cybermediaries come in as the third parties. This business model also contributes towards opening of the numerous opportunities for various new business entities which can act as cybermediaries. Also, the need for delivery of the products sold through the cybermediaries provides business opportunities for companies in freight services industry. ARP Spoofing Detection Technique can be used which actively detects MAC Spoofing in LAN or Internet. [5] Explains how the detection of ARP spoofing is done instantly. And it also provides deduction of other common network attacks like Sniffing, Denial of Service, and Man in the Middle etc. Online payment systems have become increasingly popular due to the widespread use of the internet-based shopping and banking. The ultimate vision for online payments is to provide a system where there exists privacy for information and to ensure that only those parties which require an access to it are only able to obtain the access. Thus it also creates an environment in which every party can trust the identity of all other parties. Also there is a need for the individuals to be able to authorize the transactions. All these concerns are addressed by the SET (Secure Electronic Transactions) standards. [3] Gives a good framework for understanding the issues in online payments and the key technological components that can meet them. [1] SET is a collection of technical specifications jointly owned by visa and master card. Technical input was provided by GTE, IBM, Microsoft, RSA, SAIC and VeriSign. SET makes use of Heavy Security technologies including certification and digital signatures. [2] Explains all the important concepts related to web service and [6] explains in detail about Web Services Architecture. It identifies the functional components and defines the relationships among those components that affect the desired properties of the overall architecture. 3. Our Approach The systems in a network are connected to the server which provides service for both the suppliers and the customers who purchase the products. The suppliers are asked to create an account on the website which will help the supplier to add products. Here, they will be authenticated by using their MAC address, which is considered as the digital identity. The details are entered into the database using SQL queries. Then the data entered will be stored into the supplier s database and the products are sold by any of the cybermediaries who are authorized to sell the products online. The access to the 80
3 International Journal of Advancements in Computing Technology data is provided by the supplier s site with the help of a web service. The entries in supplier s database are converted into XML format and are sent to the cybermediaries on demand. The online sellers can use shopping cart technology to hold the data items which would be purchased by the customer and then generates invoice on confirmation. It is then redirected to the PayPal website to ensure a safe electronic transaction. The interaction between the supplier s site and the cybermediaries is always passive which means that, they are connected to each other only when required. The payment to the supplier is paid from the cybermediaries through the details that reside in the database which provides an environment for the suppliers to sell their products online. 4. Implementation 4.1 Architecture Design The general e-commerce architecture comprises of the three layers where the top layer provides the interface to add the products to sell and the bottom layer presents an interface to sell those products. The middle layer performs operations behind which stores and retrieves data from the database. In our e-commerce model, which is shown below [Fig 1], a little modification is provided in the middle layer. Since the top and bottom layer of the model are not the same service providers. The top layer is the supplier s layer where the web interface is provided for the SMME to add their products to sell online. The bottom layer is divided into two divisions where a cybermediary layer is included to mention that the suppliers and online sellers are different. Cybermediaries are nothing but the website on World Wide Web (WWW) who sells the products and delivers those in time. The second division is the customer layer where the customers who wish to get the service from the cybermediaries to purchase products from the manufacturers with high trust reside. The middle layer is highly modified where it is split into two halves, one provides a web interface for the SMME to add their products and the other provides a web service to all cybermediaries to get the product details. Two processors perform the required task behind; they are the SQL and XML query processor. SQL query processor performs basic insertion and deletion of data with database. XML query processor converts the data retrieved by the SQL query processor in to a XML document. Figure 1: Modified System Architecture 81
4 A Secured Web Services Based E-Commerce Model for SMME Using Digital Identity Ashwin B.K, Kumaran K, Madhu Vishwanatham V, M Sumaithri 4.2 Design of Websites Suppliers Website This website is highly confidential and provides a platform for the owners of the SMME to add their products. This site will also provide the database details to other cybermediaries to help them in selling those products Web Interface The first task to be done is to get the service from the ak.suppliers site which is the owner of the SMME and have to register first. The registration process gets the important details from the supplier such as TIN (TAX INFORMATION NETWORK) number which is unique and provided by the central government. This alone is not enough to authorize the supplier. A certificate is required which is generated on the client machine and the service is provided from the site to download an exe file. On executing the exe file, a certificate file is created and then is requested to upload it to complete their registration. Once the registration is completed the supplier is verified and account is activated. From then they can access the service provided by the website. First, they have to login using their TIN number and password. The server checks the credentials entered and then generates a random value which will be encrypted using the clients MAC address obtained from the certificate uploaded by the client. The supplier is requested to enter the decrypted value and then that is verified with the value that was encrypted to authorize the user. Then, the supplier is recognized and redirected to the control panel which allows the supplier to perform various operations such as adding, editing and deleting a product for sale. It also allows viewing the reports based on request, either total or product wise. The suppliers can successfully logout at any point of usage. The entire process is depicted in the following sequence diagram [Fig 2] MAC Authorization Figure 2: Sequence diagram of Supplier The user who logs in can be easily authenticated using the login details but where as to authorize the user it needs some more operations. Authorization generally takes place by verifying the certificate 82
5 International Journal of Advancements in Computing Technology with the hash code or using the digital identity. Digital identity uses the biometrics since it is always unique but it is costly. A new technique is implemented in this paper, i.e. the concept of using the MAC address for the digital identity purpose. The drawbacks of using the MAC address for recognition is the problem of MAC spoofing. Two kinds of spoofing can occur. One is, changing the MAC address while transmitting over the network and the other is, change of MAC address on their system itself. In the solution provided, we also recovered both the problems faced in the spoofing. Firstly, the client opens the login page and enters the login details; we encrypt using the MAC address and send to the client window. Now the client has to decrypt the encrypted text and then enter the value thus obtained. The entire task is explained in the following sequence diagram [Fig 3].This ensures that we overcome the first kind of MAC spoofing and thus it helps us to use the MAC address as digital identity for authorization purposes Web Service Figure 3: Authorization Process of Supplier This part is very important which makes the transfer of details about the products easy, faster and reliably. A web service provides a service on the supplier site which receives requests from the other cybermediaries and responds to them efficiently. The reply by this web service is just the path of the XML path, which is required. XML doc is generated and kept in common place to access it. The sample format of the XML file is as follows [Fig 4]. <? xml version="1.0" encoding="utf-8"?> -<aksuppliers> - <product> <Item_num>94</Item_num> <Sup_Id>15</Sup_Id> <Name>Motorola</Name> <Domain>Java</Domain> 83
6 A Secured Web Services Based E-Commerce Model for SMME Using Digital Identity Ashwin B.K, Kumaran K, Madhu Vishwanatham V, M Sumaithri Consumers Website <Description>Motion Sense</Description> <Price>7500</Price> <Date_Added>11/8/ :02:56 AM</Date_Added> </product> - <product> <Item_num>93</Item_num> <Sup_Id>15</Sup_Id> <Name>Samsung</Name> <Domain>Java</Domain> <Description>FLIP</Description> <Price>6200</Price> <Date_Added>11/8/ :02:10 AM</Date_Added> </product> - <product> <Item_num>92</Item_num> <Sup_Id>14</Sup_Id> <Name>PC Quest</Name> <Domain>Computers</Domain> <Description>For Developers</Description> <Price>1500</Price> <Date_Added>10/29/ :35:30 PM</Date_Added> </product> - <product> <Item_num>91</Item_num> <Sup_Id>18</Sup_Id> <Name>nokia</Name> <Domain>ordinary</Domain> <Description>bar phone</description> <Price>4500</Price> <Date_Added>9/30/ :29:22 AM</Date_Added> </product> </aksuppliers> Figure 4: Sample data base schema Consumer website in our paper is nothing but the cybermediaries who sells the product and take care of shipping and delivery. The following section gives the basic processes and important information required to establish a web interface to sell the products Web Interface This section explains about the activities carried out in the consumer website (Kumash BAY), the flow of the control with the interface and the basic operations carried on behind. The below diagram [Fig 5] explains about the flow of control on the client side. Firstly, they are asked to register with their login and address of delivery. Once successfully registered they will be able to browse for products and can buy. The products are categorized for easy navigation and once they like the product, they can add that product to their shopping cart. This shopping cart is created on client side once they log in and is destroyed once they log off. Every item they add to the cart allows either increasing or decreasing of the quantity of that particular product. 84
7 International Journal of Advancements in Computing Technology Figure 5: Sequence Diagram of Customers Once the shopping is over the client can view the cart also any time and can check if they are satisfied with the products and their prices. Once they check the details and are satisfied, it is followed by the verification of address and they can now go for payment. The following figure [Fig 6] shows the MAC address verification screen. Figure 6: MAC Address Verification Screen 85
8 A Secured Web Services Based E-Commerce Model for SMME Using Digital Identity Ashwin B.K, Kumaran K, Madhu Vishwanatham V, M Sumaithri In this demonstration we used the electronic payment gateway PayPal and the shopping cart is transferred securely to the PayPal site. In that site the users can finally verify their cart and then they have to login with their PayPal account. The site takes care of secure transaction of the amount to the suppliers account. It has been linked with many popular credit card services such as Visa, Master Card and American express. 4.3 DB Schema The DB schema shown [Fig 7] gives the ER diagrammatic representation of the relationships among the suppliers and the different kinds of products. It is a simple and small schema which can be extended to higher levels. In this schema, the product is the top table and has many dimension tables such as cell phones, computers, and books. These can be further divided into many sub tables such as journals, magazines under the books category. The fields in each table can also be extended if the requirements demand. The schema shown in [Fig 7] belongs to the supplier s site and only the customers database is enough for the kumash bay site if needed more detailed information can be also added. Figure 7: The Product Registry DB Schema 86
9 5. Future Extension International Journal of Advancements in Computing Technology In the paper we explained and have implemented the PayPal for the online payment. Also it can be extended in order to accept different online payment providers, so that it will improve the online payment process and makes the customer s job more flexible. And when a supplier wants to change his system, it results in change of the MAC address as it varies from system to system and is unique. So he might not be able to login. This issue can solved by providing an option of change of system, in which we get a secrete question. If the person provides the correct answer, we then get the new system s MAC Address and replace the old one. Since the suppliers are mostly organizations the change of system problem won t occur frequently. 6. Conclusion The e-commerce model proposed here have more advantages then the previous models since Small, Micro and Medium Enterprises (SMMEs) have direct access to global market for their products. This proposed study of MAC Address as Digital Identity, helped us to understand the concept of using MAC Address as a Digital Identity. It is easy to implement without using any special hardware and it requires just an Ethernet card or wireless card which is used to connect to internet. This helps us to implement digital identity without using any bio metric devices in a cost effective way. 7. References [1] Mark Norris, Steve West, Kevin Gaughan, E-Business Essentials. [2] OASIS,UDDI Version Specifications: UDDI Spec Technical Committee Draft, 2004, [3] Sarkar M, Butler B, Steinfield C, Cybermediaries in Electronic Market space: Toward Theory Building, Journal of Business Research, 41, pp , [4] Sibya M.G., Jembere E, Xulu S.S, Adigun M.O, A Web Service based e-commerce Business Model for Resource Constrained SMMEs, Centre for Mobile e-service for development university of Zululand, RSA. [5] Vivek Ramachanran IIT Guwahati, ARP spoofing Detection-An Active Technique. [6] Web Services Architecture, W3C, URL /#technology. 87
Technologies for Securing the Networked Supply Chain. Alex Deacon Advanced Products and Research Group VeriSign, Inc.
 Technologies for Securing the Networked Supply Chain Alex Deacon Advanced Products and Research Group VeriSign, Inc. Agenda Introduction Security challenges Security technologies in use today Applying
Technologies for Securing the Networked Supply Chain Alex Deacon Advanced Products and Research Group VeriSign, Inc. Agenda Introduction Security challenges Security technologies in use today Applying
Introduction to Web Services & SOA
 References: Web Services, A Technical Introduction, Deitel & Deitel Building Scalable and High Performance Java Web Applications, Barish Service-Oriented Programming (SOP) SOP A programming paradigm that
References: Web Services, A Technical Introduction, Deitel & Deitel Building Scalable and High Performance Java Web Applications, Barish Service-Oriented Programming (SOP) SOP A programming paradigm that
Network Security Essentials
 Network Security Essentials Fifth Edition by William Stallings Chapter 4 Key Distribution and User Authentication No Singhalese, whether man or woman, would venture out of the house without a bunch of
Network Security Essentials Fifth Edition by William Stallings Chapter 4 Key Distribution and User Authentication No Singhalese, whether man or woman, would venture out of the house without a bunch of
Introduction to Web Services & SOA
 References: Web Services, A Technical Introduction, Deitel & Deitel Building Scalable and High Performance Java Web Applications, Barish Web Service Definition The term "Web Services" can be confusing.
References: Web Services, A Technical Introduction, Deitel & Deitel Building Scalable and High Performance Java Web Applications, Barish Web Service Definition The term "Web Services" can be confusing.
AutomationDirect.com Order Import Feature
 AutomationDirect.com Order Import Feature This document describes the requirements to upload a CSV or XML format order file from your system into our AutomationDirect.com E-commerce system to create an
AutomationDirect.com Order Import Feature This document describes the requirements to upload a CSV or XML format order file from your system into our AutomationDirect.com E-commerce system to create an
CS155b: E-Commerce. Lecture 6: Jan. 25, Security and Privacy, Continued
 CS155b: E-Commerce Lecture 6: Jan. 25, 2001 Security and Privacy, Continued FIREWALL A barrier between an internal network & the Internet Protects the internal network from outside attacks Executes administrator-defined
CS155b: E-Commerce Lecture 6: Jan. 25, 2001 Security and Privacy, Continued FIREWALL A barrier between an internal network & the Internet Protects the internal network from outside attacks Executes administrator-defined
Vision Document. Online E-commerce Music CD Store Version 2.0
 Vision Document Online E-commerce Music CD Store Version 2.0 Submitted in partial fulfillment of the requirements of the degree of Master Software Engineering Reshma Sawant CIS 895 MSE Project Kansas State
Vision Document Online E-commerce Music CD Store Version 2.0 Submitted in partial fulfillment of the requirements of the degree of Master Software Engineering Reshma Sawant CIS 895 MSE Project Kansas State
A Step By Step Guide To Use PayPal
 A Step By Step Guide To Use PayPal Table of Contents Introduction... 3 Creating an Account... 4 PayPal Verification... 5 Verification Process... 5 Utility of Each Account... 7 Transfer of Funds... 8 Checking
A Step By Step Guide To Use PayPal Table of Contents Introduction... 3 Creating an Account... 4 PayPal Verification... 5 Verification Process... 5 Utility of Each Account... 7 Transfer of Funds... 8 Checking
Web Services. Brian A. LaMacchia. Software Architect Windows Trusted Platform Technologies Microsoft Corporation
 Web Services Brian A. LaMacchia Software Architect bal@microsoft.com Windows Trusted Platform Technologies Microsoft Corporation CPSC 155b E-Commerce: Doing Business on the Internet March 27, 2003 Five
Web Services Brian A. LaMacchia Software Architect bal@microsoft.com Windows Trusted Platform Technologies Microsoft Corporation CPSC 155b E-Commerce: Doing Business on the Internet March 27, 2003 Five
OKPAY guides INTEGRATION OVERVIEW
 Название раздела OKPAY guides www.okpay.com INTEGRATION OVERVIEW 2012 Contents INTEGRATION OVERVIEW GUIDE Contents 1. Payment System Integration 2. OKPAY Integration Types 2.1. Basic Payment Links and
Название раздела OKPAY guides www.okpay.com INTEGRATION OVERVIEW 2012 Contents INTEGRATION OVERVIEW GUIDE Contents 1. Payment System Integration 2. OKPAY Integration Types 2.1. Basic Payment Links and
 Assistance with University Projects? Research Reports? Writing Skills? We ve got you covered! www.assignmentstudio.net WhatsApp: +61-424-295050 Toll Free: 1-800-794-425 Email: contact@assignmentstudio.net
Assistance with University Projects? Research Reports? Writing Skills? We ve got you covered! www.assignmentstudio.net WhatsApp: +61-424-295050 Toll Free: 1-800-794-425 Email: contact@assignmentstudio.net
SECTION 1 WHAT DO WE DO W ITH YOUR INFORMATION?
 Hasslefreerepartnership.com is serious about protecting your online privacy. This Privacy Statement explains our views and practices concerning privacy, and how they may pertain to you as a user of our
Hasslefreerepartnership.com is serious about protecting your online privacy. This Privacy Statement explains our views and practices concerning privacy, and how they may pertain to you as a user of our
Agent-Enabling Transformation of E-Commerce Portals with Web Services
 Agent-Enabling Transformation of E-Commerce Portals with Web Services Dr. David B. Ulmer CTO Sotheby s New York, NY 10021, USA Dr. Lixin Tao Professor Pace University Pleasantville, NY 10570, USA Abstract:
Agent-Enabling Transformation of E-Commerce Portals with Web Services Dr. David B. Ulmer CTO Sotheby s New York, NY 10021, USA Dr. Lixin Tao Professor Pace University Pleasantville, NY 10570, USA Abstract:
E-commerce security: SSL/TLS, SET and others. 4.1
 E-commerce security: SSL/TLS, SET and others. 4.1 1 Electronic payment systems Purpose: facilitate the safe and secure transfer of monetary value electronically between multiple parties Participating parties:
E-commerce security: SSL/TLS, SET and others. 4.1 1 Electronic payment systems Purpose: facilitate the safe and secure transfer of monetary value electronically between multiple parties Participating parties:
Software Engineering Prof.N.L.Sarda IIT Bombay. Lecture-11 Data Modelling- ER diagrams, Mapping to relational model (Part -II)
 Software Engineering Prof.N.L.Sarda IIT Bombay Lecture-11 Data Modelling- ER diagrams, Mapping to relational model (Part -II) We will continue our discussion on process modeling. In the previous lecture
Software Engineering Prof.N.L.Sarda IIT Bombay Lecture-11 Data Modelling- ER diagrams, Mapping to relational model (Part -II) We will continue our discussion on process modeling. In the previous lecture
Chapter 17 Web Services Additional Topics
 Prof. Dr.-Ing. Stefan Deßloch AG Heterogene Informationssysteme Geb. 36, Raum 329 Tel. 0631/205 3275 dessloch@informatik.uni-kl.de Chapter 17 Web Services Additional Topics Prof. Dr.-Ing. Stefan Deßloch
Prof. Dr.-Ing. Stefan Deßloch AG Heterogene Informationssysteme Geb. 36, Raum 329 Tel. 0631/205 3275 dessloch@informatik.uni-kl.de Chapter 17 Web Services Additional Topics Prof. Dr.-Ing. Stefan Deßloch
WHITE PAPER. OAuth A new era in Identity Management and its Applications. Abstract
 WHITE PAPER OAuth A new era in Identity Management and its Applications Abstract OAuth protocol is a standard which allows end users to share their web resources with the third-party applications without
WHITE PAPER OAuth A new era in Identity Management and its Applications Abstract OAuth protocol is a standard which allows end users to share their web resources with the third-party applications without
Daman isupplier Portal User Guide. Procurement
 Procurement Table of Content 1. Introduction... 4 Benefits associated with using isupplier include:... 4 2. System Requirements... 4 2.1 Recommended Operating System:... 4 2.2 Browser Requirements:...
Procurement Table of Content 1. Introduction... 4 Benefits associated with using isupplier include:... 4 2. System Requirements... 4 2.1 Recommended Operating System:... 4 2.2 Browser Requirements:...
Frequently Asked Questions ORDERING ON MYHERBALIFE.COM INDIA, January 2013
 Click on any of the section headers below to jump to the answers for the questions in that section. If you cannot find the answer to your question, please contact Associate Services at 080-40311444, 10
Click on any of the section headers below to jump to the answers for the questions in that section. If you cannot find the answer to your question, please contact Associate Services at 080-40311444, 10
Project Description MyBay Project
 Project Description MyBay Project University of British Columbia Okanagan COSC 304 - Fall 2007 Team Members: Ali Hatami Jennifer Johnstone Nicholas Blackwell 11/28/2007 1 COSC 304 MyEBAY.DOC TABLE OF CONTENTS
Project Description MyBay Project University of British Columbia Okanagan COSC 304 - Fall 2007 Team Members: Ali Hatami Jennifer Johnstone Nicholas Blackwell 11/28/2007 1 COSC 304 MyEBAY.DOC TABLE OF CONTENTS
New BoundTree.com User Guide Fall Version 6
 New BoundTree.com User Guide Fall 2016 Version 6 Table of Contents Overview Navigating the Home Page Creating an Account Logging into an Existing Account Forgot Your Password? Reviewing Your Account Editing
New BoundTree.com User Guide Fall 2016 Version 6 Table of Contents Overview Navigating the Home Page Creating an Account Logging into an Existing Account Forgot Your Password? Reviewing Your Account Editing
CyberSource Global Payment Management for Magento 2
 CyberSource Global Payment Management for Magento 2 User s Guide Version 2.0.3 January 2018 January 2018 CyberSource Global Payment Management for Magento 2.x 1 Contents Recent Changes... 5 1. Introduction:...
CyberSource Global Payment Management for Magento 2 User s Guide Version 2.0.3 January 2018 January 2018 CyberSource Global Payment Management for Magento 2.x 1 Contents Recent Changes... 5 1. Introduction:...
Unifie X Common Gateway Server (N Tier)
 Unifie X Common Gateway Server (N Tier) M.SUPRIYA Dept of IT, Swami Vivekananda Institute of Technology, Telangana, India ABSTRACT The main objective of this project is to develop a generic tool for Common
Unifie X Common Gateway Server (N Tier) M.SUPRIYA Dept of IT, Swami Vivekananda Institute of Technology, Telangana, India ABSTRACT The main objective of this project is to develop a generic tool for Common
TELCOware Administration Manual Bicom Systems
 I Table of Contents Part I Introduction 1 Part II Setup Wizard 1 1 EULA... 1 2 Server... Details 2 3 Administrator... Details 3 4 Licensing... 4 5 Currency... 5 6 Payment... Methods 6 7 Payment... Settings
I Table of Contents Part I Introduction 1 Part II Setup Wizard 1 1 EULA... 1 2 Server... Details 2 3 Administrator... Details 3 4 Licensing... 4 5 Currency... 5 6 Payment... Methods 6 7 Payment... Settings
WebSphere Commerce Integration with ebay: Using the ebay SDK and Web Services
 WebSphere Commerce Integration with ebay: Using the ebay SDK and Web Services Jaweed Ali Qureshi Sr. Software Engineer jaweed@royalcyber.com Royal Cyber Inc., Malik M. Sarfaraz Software Engineer sarfaraz@royalcyber.com
WebSphere Commerce Integration with ebay: Using the ebay SDK and Web Services Jaweed Ali Qureshi Sr. Software Engineer jaweed@royalcyber.com Royal Cyber Inc., Malik M. Sarfaraz Software Engineer sarfaraz@royalcyber.com
Void Mark E-Commerce Application
 RESEARCH ARTICLE OPEN ACCESS Void Mark E-Commerce Application Mayank Pithwa, Akshay Ghugal, Moni Gupta, Rasika Patil4, Ajay Karare Computer Science & Engineering, Jhulelal Institute of Technology, Rashtrasant
RESEARCH ARTICLE OPEN ACCESS Void Mark E-Commerce Application Mayank Pithwa, Akshay Ghugal, Moni Gupta, Rasika Patil4, Ajay Karare Computer Science & Engineering, Jhulelal Institute of Technology, Rashtrasant
Vision Document 2.0 Online Book Store Phase-II. Vamsi Krishna Mummaneni
 Vision Document 2.0 Online Book Store Phase-II Submitted in partial fulfillment of the requirements of the degree of Master of Software Engineering Vamsi Krishna Mummaneni CIS 895 MSE Project Kansas State
Vision Document 2.0 Online Book Store Phase-II Submitted in partial fulfillment of the requirements of the degree of Master of Software Engineering Vamsi Krishna Mummaneni CIS 895 MSE Project Kansas State
Secure Web Transactions. Sridhar Iyer K R School of Information Technology IIT Bombay
 Secure Web Transactions Sridhar Iyer K R School of Information Technology IIT Bombay sri@it.iitb.ernet.in http://www.it.iitb.ernet.in/~sri Overview Electronic Commerce Underlying Technologies Cryptography
Secure Web Transactions Sridhar Iyer K R School of Information Technology IIT Bombay sri@it.iitb.ernet.in http://www.it.iitb.ernet.in/~sri Overview Electronic Commerce Underlying Technologies Cryptography
Introduction to SSL. Copyright 2005 by Sericon Technology Inc.
 Introduction to SSL The cornerstone of e-commerce is a Web site s ability to prevent eavesdropping on data transmitted to and from its site. Without this, consumers would justifiably be afraid to enter
Introduction to SSL The cornerstone of e-commerce is a Web site s ability to prevent eavesdropping on data transmitted to and from its site. Without this, consumers would justifiably be afraid to enter
Design and Implementation of E-Commerce Site for Online Shopping
 Governors State University OPUS Open Portal to University Scholarship All Capstone Projects Student Capstone Projects Summer 2014 Design and Implementation of E-Commerce Site for Online Shopping Sidhartha
Governors State University OPUS Open Portal to University Scholarship All Capstone Projects Student Capstone Projects Summer 2014 Design and Implementation of E-Commerce Site for Online Shopping Sidhartha
SSL/TLS & 3D Secure. CS 470 Introduction to Applied Cryptography. Ali Aydın Selçuk. CS470, A.A.Selçuk SSL/TLS & 3DSec 1
 SSL/TLS & 3D Secure CS 470 Introduction to Applied Cryptography Ali Aydın Selçuk CS470, A.A.Selçuk SSL/TLS & 3DSec 1 SSLv2 Brief History of SSL/TLS Released in 1995 with Netscape 1.1 Key generation algorithm
SSL/TLS & 3D Secure CS 470 Introduction to Applied Cryptography Ali Aydın Selçuk CS470, A.A.Selçuk SSL/TLS & 3DSec 1 SSLv2 Brief History of SSL/TLS Released in 1995 with Netscape 1.1 Key generation algorithm
Table of Contents. Page 1 of 6 (Last updated 27 April 2017)
 Table of Contents What is Connect?... 2 Physical Access Controls... 2 User Access Controls... 3 Systems Architecture... 4 Application Development... 5 Business Continuity Management... 5 Other Operational
Table of Contents What is Connect?... 2 Physical Access Controls... 2 User Access Controls... 3 Systems Architecture... 4 Application Development... 5 Business Continuity Management... 5 Other Operational
ebxml Transport Routing and Packaging Overview and Requirements
 ebxml Transport Routing and Packaging Overview and Requirements This paper provides an overview of the Transport Routing and Packaging It describes: an overview and description of the scope of the group's
ebxml Transport Routing and Packaging Overview and Requirements This paper provides an overview of the Transport Routing and Packaging It describes: an overview and description of the scope of the group's
Selling items that your customers can download
 Selling items that your customers can download A users guide to using Reason8 to sell items that can be automatically downloaded. 1 19 th October 2005 Background If you are planning to sell items that
Selling items that your customers can download A users guide to using Reason8 to sell items that can be automatically downloaded. 1 19 th October 2005 Background If you are planning to sell items that
Vendor: Microsoft. Exam Code: Exam Name: MTA Security Fundamentals Practice Test. Version: Demo
 Vendor: Microsoft Exam Code: 98-367 Exam Name: MTA Security Fundamentals Practice Test Version: Demo DEMO QUESTION 1 To prevent users from copying data to removable media, you should: A. Lock the computer
Vendor: Microsoft Exam Code: 98-367 Exam Name: MTA Security Fundamentals Practice Test Version: Demo DEMO QUESTION 1 To prevent users from copying data to removable media, you should: A. Lock the computer
Policy Manager for IBM WebSphere DataPower 7.2: Configuration Guide
 Policy Manager for IBM WebSphere DataPower 7.2: Configuration Guide Policy Manager for IBM WebSphere DataPower Configuration Guide SOAPMDP_Config_7.2.0 Copyright Copyright 2015 SOA Software, Inc. All rights
Policy Manager for IBM WebSphere DataPower 7.2: Configuration Guide Policy Manager for IBM WebSphere DataPower Configuration Guide SOAPMDP_Config_7.2.0 Copyright Copyright 2015 SOA Software, Inc. All rights
Getting Started Guide. Prepared by-fatbit Technologies
 Getting Started Guide Prepared by-fatbit Technologies 1 Contents 1. Manage Settings... 3 1.1. General... 4 1.2. Local... 6 1.3. SEO... 7 1.4. Option... 8 1.5. Live Chat... 19 1.6. Third Part API s... 20
Getting Started Guide Prepared by-fatbit Technologies 1 Contents 1. Manage Settings... 3 1.1. General... 4 1.2. Local... 6 1.3. SEO... 7 1.4. Option... 8 1.5. Live Chat... 19 1.6. Third Part API s... 20
Frequently Asked Questions
 Click on any of the frequently asked questions below to display the answer. If you cannot find the answer to your question, please contact Member Services on 08 8154 0200, 9.00 am to 5.00 pm Adelaide time,
Click on any of the frequently asked questions below to display the answer. If you cannot find the answer to your question, please contact Member Services on 08 8154 0200, 9.00 am to 5.00 pm Adelaide time,
Computers and Security
 The contents of this Supporting Material document have been prepared from the Eight units of study texts for the course M150: Date, Computing and Information, produced by The Open University, UK. Copyright
The contents of this Supporting Material document have been prepared from the Eight units of study texts for the course M150: Date, Computing and Information, produced by The Open University, UK. Copyright
Example Azure Implementation for Government Agencies. Indirect tax-filing system. By Alok Jain Azure Customer Advisory Team (AzureCAT)
 Example Azure Implementation for Government Agencies Indirect tax-filing system By Alok Jain Azure Customer Advisory Team (AzureCAT) June 2018 Example Azure Implementation for Government Agencies Contents
Example Azure Implementation for Government Agencies Indirect tax-filing system By Alok Jain Azure Customer Advisory Team (AzureCAT) June 2018 Example Azure Implementation for Government Agencies Contents
Electronic Commerce Working Group report
 RESTRICTED CEFACT/ECAWG/97N012 4 December 1997 Electronic Commerce Ad hoc Working Group (ECAWG) Electronic Commerce Working Group report SOURCE: 10 th ICT Standards Board, Sophia Antipolis, 4 th November
RESTRICTED CEFACT/ECAWG/97N012 4 December 1997 Electronic Commerce Ad hoc Working Group (ECAWG) Electronic Commerce Working Group report SOURCE: 10 th ICT Standards Board, Sophia Antipolis, 4 th November
PayPal Standard Sandbox Testing
 PayPal Standard Sandbox Testing Updated June 2014 2014 GoPrint Systems, Inc., All rights reserved. PayPal Standard Configuration Guide 1 PayPal Standard Sandbox Testing How it works At the developer Sandbox
PayPal Standard Sandbox Testing Updated June 2014 2014 GoPrint Systems, Inc., All rights reserved. PayPal Standard Configuration Guide 1 PayPal Standard Sandbox Testing How it works At the developer Sandbox
Connecting VirtueMart To PayPal (Live)
 Connecting VirtueMart To PayPal (Live) After testing is complete in the PayPal Sandbox and you are satisfied all is well, then its time to disconnect VirtueMart from the PayPal Sandbox and connect Virtuemart
Connecting VirtueMart To PayPal (Live) After testing is complete in the PayPal Sandbox and you are satisfied all is well, then its time to disconnect VirtueMart from the PayPal Sandbox and connect Virtuemart
E-commerce security: SSL/TLS, SET and others. 4.2
 E-commerce security: SSL/TLS, SET and others. 4.2 1 The need of authenticated payment SSL protects credit card details while they are transmitted through Internet but Why trust the Merchant? Once credit
E-commerce security: SSL/TLS, SET and others. 4.2 1 The need of authenticated payment SSL protects credit card details while they are transmitted through Internet but Why trust the Merchant? Once credit
Online Ordering Instructions
 Online Ordering Instructions Supplied By Table of Contents Login... 2 How to Order Products... 2 Shopping Cart... 3 Checkout... 3 My Account... 7 Login Type www.alliancepromotions.com.au in your preferred
Online Ordering Instructions Supplied By Table of Contents Login... 2 How to Order Products... 2 Shopping Cart... 3 Checkout... 3 My Account... 7 Login Type www.alliancepromotions.com.au in your preferred
About the Tutorial. Audience. Prerequisites. Copyright & Disclaimer. Magento
 About the Tutorial Magento is an open source E-commerce software, created by Varien Inc., which is useful for online business. It has a flexible modular architecture and is scalable with many control options
About the Tutorial Magento is an open source E-commerce software, created by Varien Inc., which is useful for online business. It has a flexible modular architecture and is scalable with many control options
Welcome to Cart32, Sincerely, Cart32 Support Team
 Welcome to Cart32, The purpose of the Getting Started Guide is to cover the basic settings required to start using Cart32. There is an Introduction section to familiarize new users with the Cart32 software
Welcome to Cart32, The purpose of the Getting Started Guide is to cover the basic settings required to start using Cart32. There is an Introduction section to familiarize new users with the Cart32 software
WebSphere Commerce Integration with ebay: Using the ebay SDK and Web Services
 WebSphere Commerce Integration with ebay: Using the ebay SDK and Web Services Jaweed Ali Qureshi Sr. Software Engineer jaweed@royalcyber.com Royal Cyber Inc., Malik M. Sarfaraz Software Engineer sarfaraz@royalcyber.com
WebSphere Commerce Integration with ebay: Using the ebay SDK and Web Services Jaweed Ali Qureshi Sr. Software Engineer jaweed@royalcyber.com Royal Cyber Inc., Malik M. Sarfaraz Software Engineer sarfaraz@royalcyber.com
Frequently Asked Questions
 Username and Passwords Q. How do I obtain a Username and Password to Log In to my WisePay Wise Account? A. Every User is provided with a secure Wise Account. This will enable you to make online payments
Username and Passwords Q. How do I obtain a Username and Password to Log In to my WisePay Wise Account? A. Every User is provided with a secure Wise Account. This will enable you to make online payments
Using the Cisco ACE Application Control Engine Application Switches with the Cisco ACE XML Gateway
 Using the Cisco ACE Application Control Engine Application Switches with the Cisco ACE XML Gateway Applying Application Delivery Technology to Web Services Overview The Cisco ACE XML Gateway is the newest
Using the Cisco ACE Application Control Engine Application Switches with the Cisco ACE XML Gateway Applying Application Delivery Technology to Web Services Overview The Cisco ACE XML Gateway is the newest
Empathy Parent Manual
 Empathy Parent Manual www.itschools.co.za Contents Overview... 1 What is Empathy?... 1 How to Order Books... 1 Getting Started: Registration and Login... 1 Registration for New Users... 1 Account Creation...
Empathy Parent Manual www.itschools.co.za Contents Overview... 1 What is Empathy?... 1 How to Order Books... 1 Getting Started: Registration and Login... 1 Registration for New Users... 1 Account Creation...
HOW TO INTEGRATE A PAYPAL BUTTON INTO YOUR WEBSITE
 1 HOW TO INTEGRATE A PAYPAL BUTTON INTO YOUR WEBSITE (c ) Laycock Publishing Limited You have full distribution rights to this publication, provided that it remains unaltered in any way whatsoever, and
1 HOW TO INTEGRATE A PAYPAL BUTTON INTO YOUR WEBSITE (c ) Laycock Publishing Limited You have full distribution rights to this publication, provided that it remains unaltered in any way whatsoever, and
TIS HELP VCCS TECHNICAL INFORMATION SHOP (TIS) INSTRUCTION FOR INDEPENDENT OPERATORS
 VCCS TECHNICAL INFORMATION SHOP (TIS) INSTRUCTION FOR INDEPENDENT OPERATORS CONTENTS 1 INTRODUCTION... 3 1.1 Account set up... 3 1.1.1 Independent operators with TIE access... 3 1.2 Login for registered
VCCS TECHNICAL INFORMATION SHOP (TIS) INSTRUCTION FOR INDEPENDENT OPERATORS CONTENTS 1 INTRODUCTION... 3 1.1 Account set up... 3 1.1.1 Independent operators with TIE access... 3 1.2 Login for registered
IMEI Database. Manufacturer / Brand Owner User Guide. Version September Copyright Notice. Copyright 2015 GSM Association
 IMEI Database Manufacturer / Brand Owner User Guide Version 4.0 01 September 2015 Copyright Notice Copyright 2015 GSM Association GSM and the GSM logo are registered and owned by the GSM Association. Antitrust
IMEI Database Manufacturer / Brand Owner User Guide Version 4.0 01 September 2015 Copyright Notice Copyright 2015 GSM Association GSM and the GSM logo are registered and owned by the GSM Association. Antitrust
How to Set Up Paypal in WPGateway for Selling SSL Certificates with an Automatic Annual Renewal Process
 How to Set Up Paypal in WPGateway for Selling SSL Certificates with an Automatic Annual Renewal Process SSL Certificates Need to be Renewed Annually -- Giving YOU a HUGE Recurring Income Opportunity! Since
How to Set Up Paypal in WPGateway for Selling SSL Certificates with an Automatic Annual Renewal Process SSL Certificates Need to be Renewed Annually -- Giving YOU a HUGE Recurring Income Opportunity! Since
Overview. SSL Cryptography Overview CHAPTER 1
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
B2B Portal User Guide
 B2B Portal User Guide Table of Contents Introduction..3 Logging In.4 Changing your original password......6 Ordering Product....7 Product Waiting Lists......8 Payment Options.. 14 Finalizing your Order...
B2B Portal User Guide Table of Contents Introduction..3 Logging In.4 Changing your original password......6 Ordering Product....7 Product Waiting Lists......8 Payment Options.. 14 Finalizing your Order...
INTEGRATED SECURITY SYSTEM FOR E-GOVERNMENT BASED ON SAML STANDARD
 INTEGRATED SECURITY SYSTEM FOR E-GOVERNMENT BASED ON SAML STANDARD Jeffy Mwakalinga, Prof Louise Yngström Department of Computer and System Sciences Royal Institute of Technology / Stockholm University
INTEGRATED SECURITY SYSTEM FOR E-GOVERNMENT BASED ON SAML STANDARD Jeffy Mwakalinga, Prof Louise Yngström Department of Computer and System Sciences Royal Institute of Technology / Stockholm University
Integrated Security Context Management of Web Components and Services in Federated Identity Environments
 Integrated Security Context Management of Web Components and Services in Federated Identity Environments Apurva Kumar IBM India Research Lab. 4, Block C Vasant Kunj Institutional Area, New Delhi, India-110070
Integrated Security Context Management of Web Components and Services in Federated Identity Environments Apurva Kumar IBM India Research Lab. 4, Block C Vasant Kunj Institutional Area, New Delhi, India-110070
Rail Mall 4.0. User manual
 Rail Mall 4.0 User manual siemens.com/railmall Table of content Rail Mall 4.0 At a glance 3 Search Options 5 Registration at Rail Mall 8 Order Process 11 Wishlist 17 Price and Material Request 20 Miscellaneous
Rail Mall 4.0 User manual siemens.com/railmall Table of content Rail Mall 4.0 At a glance 3 Search Options 5 Registration at Rail Mall 8 Order Process 11 Wishlist 17 Price and Material Request 20 Miscellaneous
Institution Registration
 Institution Registration 1 Centre for Good Governance In the hostel registration form DTWO has to mention hostel name, code, type, address, location, phone number, ASWO details, DDO Bank details, type
Institution Registration 1 Centre for Good Governance In the hostel registration form DTWO has to mention hostel name, code, type, address, location, phone number, ASWO details, DDO Bank details, type
USER GUIDE GRIFFINS.FLASHSEATS.COM
 2012-13 USER GUIDE GRIFFINS.FLASHSEATS.COM FAN ADVANTAGES FAN ADVANTAGES THE ULTIMATE CONVENIENCE o Fans can conveniently swipe in with an electronic ID, eliminating lost or misplaced tickets. o Seats
2012-13 USER GUIDE GRIFFINS.FLASHSEATS.COM FAN ADVANTAGES FAN ADVANTAGES THE ULTIMATE CONVENIENCE o Fans can conveniently swipe in with an electronic ID, eliminating lost or misplaced tickets. o Seats
Boundary control : Access Controls: An access control mechanism processes users request for resources in three steps: Identification:
 Application control : Boundary control : Access Controls: These controls restrict use of computer system resources to authorized users, limit the actions authorized users can taker with these resources,
Application control : Boundary control : Access Controls: These controls restrict use of computer system resources to authorized users, limit the actions authorized users can taker with these resources,
Trusted Computing Group
 Trusted Computing Group Backgrounder May 2003 Copyright 2003 Trusted Computing Group (www.trustedcomputinggroup.org.) All Rights Reserved Trusted Computing Group Enabling the Industry to Make Computing
Trusted Computing Group Backgrounder May 2003 Copyright 2003 Trusted Computing Group (www.trustedcomputinggroup.org.) All Rights Reserved Trusted Computing Group Enabling the Industry to Make Computing
YourStore A GUIDE TO
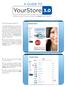 A GUIDE TO YourStore 3.0 Selling contact lenses online has never been easier! This is the homepage of YourStore 3.0. 1. The header displays just your company name as its default. The rectangular space
A GUIDE TO YourStore 3.0 Selling contact lenses online has never been easier! This is the homepage of YourStore 3.0. 1. The header displays just your company name as its default. The rectangular space
Web Services, ebxml and XML Security
 Web Services, ebxml and XML Security Dr David Cheung Director Center for E-Commerce E Infrastructure Development Electronic Commerce Models Business to Customer (B2C) Convenient access to services Business
Web Services, ebxml and XML Security Dr David Cheung Director Center for E-Commerce E Infrastructure Development Electronic Commerce Models Business to Customer (B2C) Convenient access to services Business
Lesson 13 Securing Web Services (WS-Security, SAML)
 Lesson 13 Securing Web Services (WS-Security, SAML) Service Oriented Architectures Module 2 - WS Security Unit 1 Auxiliary Protocols Ernesto Damiani Università di Milano element This element
Lesson 13 Securing Web Services (WS-Security, SAML) Service Oriented Architectures Module 2 - WS Security Unit 1 Auxiliary Protocols Ernesto Damiani Università di Milano element This element
Magento 2 Vendor Split Cart Addon - User Guide
 by CedCommerce Docs - Products User Guides 1 / 11 1. Overview... 3 2. Vendor Split Cart Configuration... 3 3. Front-End View... 4 2 / 11 1. Overview Vendor Split Cart Addon is an add-on of CedCommerce
by CedCommerce Docs - Products User Guides 1 / 11 1. Overview... 3 2. Vendor Split Cart Configuration... 3 3. Front-End View... 4 2 / 11 1. Overview Vendor Split Cart Addon is an add-on of CedCommerce
XML Key Information System for Secure e-trading
 XML Key Information System for Secure e-trading Nam-Je Park, Ki-Young Moon, Sung-Won Sohn Informatoion Security Research Division Electronics Telecommunications Research Institute(ETRI) 161 Gajeong-dong,
XML Key Information System for Secure e-trading Nam-Je Park, Ki-Young Moon, Sung-Won Sohn Informatoion Security Research Division Electronics Telecommunications Research Institute(ETRI) 161 Gajeong-dong,
BUYING A NAME AT SOBRANDABLE?
 BUYING A NAME AT SOBRANDABLE? Read through our Frequently Asked Questions Below: What is a brandable domain name? A brandable domain name is a unique, easily pronounceable and catchy web address that is
BUYING A NAME AT SOBRANDABLE? Read through our Frequently Asked Questions Below: What is a brandable domain name? A brandable domain name is a unique, easily pronounceable and catchy web address that is
Online Stores. STRONGVON Tournament Management System
 Online Stores STRONGVON Tournament Management System 1 Overview An online store on the STRONGVON Tournament Management System is part of the event website where your potential registrants can purchase
Online Stores STRONGVON Tournament Management System 1 Overview An online store on the STRONGVON Tournament Management System is part of the event website where your potential registrants can purchase
Breakdown of Some Common Website Components and Their Costs.
 Breakdown of Some Common Website Components and Their Costs. Breakdown of Some Common Website Components and Their Costs. The cost of a website can vary dramatically based on the specific components included.
Breakdown of Some Common Website Components and Their Costs. Breakdown of Some Common Website Components and Their Costs. The cost of a website can vary dramatically based on the specific components included.
New Account Application
 *Required fields Date: 3/12/2018 GENERAL ACCOUNT DETAILS *Billing Name and Address City State Postal Code *Shipping Name and Address City State Postal Code Tel# Tel# Email Email Contact Name Contact Name
*Required fields Date: 3/12/2018 GENERAL ACCOUNT DETAILS *Billing Name and Address City State Postal Code *Shipping Name and Address City State Postal Code Tel# Tel# Email Email Contact Name Contact Name
Inventions on using LDAP for different purposes- Part-1
 From the SelectedWorks of Umakant Mishra September, 2006 Inventions on using LDAP for different purposes- Part-1 Umakant Mishra Available at: https://works.bepress.com/umakant_mishra/62/ Inventions on
From the SelectedWorks of Umakant Mishra September, 2006 Inventions on using LDAP for different purposes- Part-1 Umakant Mishra Available at: https://works.bepress.com/umakant_mishra/62/ Inventions on
Product Guide SMS PLUS + Copyrights RouteSms Solutions Limited Page 1
 Product Guide SMS PLUS + Copyrights RouteSms Solutions Limited Page 1 Index Contents Page No. Overview 3-4 Gateways 5 Users 6-7 Routing 8 Administrator 9-13 Message Processing Engine 14 About Us 15 Copyrights
Product Guide SMS PLUS + Copyrights RouteSms Solutions Limited Page 1 Index Contents Page No. Overview 3-4 Gateways 5 Users 6-7 Routing 8 Administrator 9-13 Message Processing Engine 14 About Us 15 Copyrights
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide
 Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
SAMS Club Web Sites Online Store
 SAMS Club Web Sites Online Store Last Updated: November 14, 2007 Copyright 2007 Innuity, Inc. All Rights Reserved No part of this document may be reproduced or distributed in any form or by any means,
SAMS Club Web Sites Online Store Last Updated: November 14, 2007 Copyright 2007 Innuity, Inc. All Rights Reserved No part of this document may be reproduced or distributed in any form or by any means,
Introduction. Logging In. https://portal.format.co.nz/login/trt
 Introduction Welcome to the Tidd Ross Todd On-line Ordering System. This site has been created with the intention to assist users with the following: placing orders viewing work in progress searching for
Introduction Welcome to the Tidd Ross Todd On-line Ordering System. This site has been created with the intention to assist users with the following: placing orders viewing work in progress searching for
SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security
 SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security Consider 2. Based on DNS, identified the IP address of www.cuhk.edu.hk is 137.189.11.73. 1. Go to http://www.cuhk.edu.hk 3. Forward the
SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security Consider 2. Based on DNS, identified the IP address of www.cuhk.edu.hk is 137.189.11.73. 1. Go to http://www.cuhk.edu.hk 3. Forward the
ADERP ISUPPLIER PORTAL USER MANUAL VERSION 1.2
 ADERP ISUPPLIER PORTAL USER MANUAL VERSION 1.2 Document Control Change Record 4 Date Author Version Change Reference 12-Dec-2016 DOF 1.0 08-Feb-2017 DOF 1.1 Updated with new URL links 23-Mar-2017 DOF 1.2
ADERP ISUPPLIER PORTAL USER MANUAL VERSION 1.2 Document Control Change Record 4 Date Author Version Change Reference 12-Dec-2016 DOF 1.0 08-Feb-2017 DOF 1.1 Updated with new URL links 23-Mar-2017 DOF 1.2
Contents. 7.0 Electronic Business Transactions Detroit Edison Website Communications Website Content 2
 Contents 7.0 Electronic Business Transactions 2 7.1 Detroit Edison Website Communications 2 7.1.1 Website Content 2 7.2 EBT Communications 3 7.2.1 Establishing XML with Detroit Edison 3 7.2.2 XML Transactions
Contents 7.0 Electronic Business Transactions 2 7.1 Detroit Edison Website Communications 2 7.1.1 Website Content 2 7.2 EBT Communications 3 7.2.1 Establishing XML with Detroit Edison 3 7.2.2 XML Transactions
Trusted Identities. Foundational to Cloud Services LILA KEE CHIEF PRODUCT OFFICER GLOBALSIGN
 Trusted Identities Foundational to Cloud Services LILA KEE CHIEF PRODUCT OFFICER GLOBALSIGN WHAT YOU WILL LEARN TODAY Strong identity verification as a security measure and business enabler Authentication
Trusted Identities Foundational to Cloud Services LILA KEE CHIEF PRODUCT OFFICER GLOBALSIGN WHAT YOU WILL LEARN TODAY Strong identity verification as a security measure and business enabler Authentication
New Value Chain through Service Platform
 New Value Chain through Service Platform Oct. 24 th 2008 Ryozo Ito Senior Executive Consultant Hewlett-Packard Japan Technology for better business outcomes 2008 Hewlett-Packard Development Company, L.P.
New Value Chain through Service Platform Oct. 24 th 2008 Ryozo Ito Senior Executive Consultant Hewlett-Packard Japan Technology for better business outcomes 2008 Hewlett-Packard Development Company, L.P.
WebStore. Resellers. Brief User Guide. Invite. Self-Register. Log-In. Lost Password. Support. SIPHON 31 May Resellers must be invited to use
 Resellers WebStore Brief User Guide Invite Resellers must be invited to use the SIPHON WebStore. This is important as we need to approve your email address against your account. If you would like to register
Resellers WebStore Brief User Guide Invite Resellers must be invited to use the SIPHON WebStore. This is important as we need to approve your email address against your account. If you would like to register
Cryptography (Overview)
 Cryptography (Overview) Some history Caesar cipher, rot13 substitution ciphers, etc. Enigma (Turing) Modern secret key cryptography DES, AES Public key cryptography RSA, digital signatures Cryptography
Cryptography (Overview) Some history Caesar cipher, rot13 substitution ciphers, etc. Enigma (Turing) Modern secret key cryptography DES, AES Public key cryptography RSA, digital signatures Cryptography
Semantic Web. Semantic Web Services. Morteza Amini. Sharif University of Technology Spring 90-91
 بسمه تعالی Semantic Web Semantic Web Services Morteza Amini Sharif University of Technology Spring 90-91 Outline Semantic Web Services Basics Challenges in Web Services Semantics in Web Services Web Service
بسمه تعالی Semantic Web Semantic Web Services Morteza Amini Sharif University of Technology Spring 90-91 Outline Semantic Web Services Basics Challenges in Web Services Semantics in Web Services Web Service
LESS WORK, WORK LESS. The simpliest way to manage ticket based events ONLINE TICKETING
 ONLINE TICKETING LESS WORK, WORK LESS The simpliest way to manage ticket based events Watching cricket matches, concerts, plays etc., is exciting and awe-inspiring; acquiring tickets to attend these events
ONLINE TICKETING LESS WORK, WORK LESS The simpliest way to manage ticket based events Watching cricket matches, concerts, plays etc., is exciting and awe-inspiring; acquiring tickets to attend these events
key distribution requirements for public key algorithms asymmetric (or public) key algorithms
 topics: cis3.2 electronic commerce 24 april 2006 lecture # 22 internet security (part 2) finish from last time: symmetric (single key) and asymmetric (public key) methods different cryptographic systems
topics: cis3.2 electronic commerce 24 april 2006 lecture # 22 internet security (part 2) finish from last time: symmetric (single key) and asymmetric (public key) methods different cryptographic systems
Vendor Portal User Guide
 Vendor Portal User Guide Version 1.3.208 Taulia Inc. 420 Taylor Street, 4 th Floor San Francisco, CA 94102 Phone +1 (415) 376 8280 Fax +1 (415) 639 6439 Taulia GmbH Bundesallee 171 10715 Berlin, Germany
Vendor Portal User Guide Version 1.3.208 Taulia Inc. 420 Taylor Street, 4 th Floor San Francisco, CA 94102 Phone +1 (415) 376 8280 Fax +1 (415) 639 6439 Taulia GmbH Bundesallee 171 10715 Berlin, Germany
e-abbott 2017 User Manual Updated
 e-abbott 2017 User Manual Updated 8-25-2017 1 2017, Abbott USA. All rights reserved Information used in this document is subject to change without notice. No part of this document can be reproduced or
e-abbott 2017 User Manual Updated 8-25-2017 1 2017, Abbott USA. All rights reserved Information used in this document is subject to change without notice. No part of this document can be reproduced or
Remote Key Loading Spread security. Unlock efficiency
 Remote Key Loading Spread security. Unlock efficiency Cut costs increase security A smarter way to do business The hacker community is growing increasingly sophisticated which means the financial community
Remote Key Loading Spread security. Unlock efficiency Cut costs increase security A smarter way to do business The hacker community is growing increasingly sophisticated which means the financial community
Overview of HoundMart eprocurement Module and Benefits
 Contents Overview of HoundMart eprocurement Module and Benefits... 1 Purpose of this Guide... 1 Access HoundMart Application... 2 HoundMart Home Page Overview... 3 Shop using Hosted Catalog... 4 Notification
Contents Overview of HoundMart eprocurement Module and Benefits... 1 Purpose of this Guide... 1 Access HoundMart Application... 2 HoundMart Home Page Overview... 3 Shop using Hosted Catalog... 4 Notification
CyberSource Global Payment Management
 CyberSource Global Payment Management Magento 2.x Implementation Guide Version 1.1.0 August 2017 Extract Use this guide to install and configure the CyberSource extension for Magento 2.x. Contents Recent
CyberSource Global Payment Management Magento 2.x Implementation Guide Version 1.1.0 August 2017 Extract Use this guide to install and configure the CyberSource extension for Magento 2.x. Contents Recent
TTFX Manager Portal for MetaTrader 4 Manager's manual V 1.0.0
 TTFX Manager Portal for MetaTrader 4 Manager's manual V 1.0.0 Table of contents: 1 Login to the system... 3 1.1 Password recovery... 3 1.2 User management... 4 1.2.1 Password change... 4 1.2.2 Logout...
TTFX Manager Portal for MetaTrader 4 Manager's manual V 1.0.0 Table of contents: 1 Login to the system... 3 1.1 Password recovery... 3 1.2 User management... 4 1.2.1 Password change... 4 1.2.2 Logout...
Introduction : Motivation. 1.Introduction to theoretical concepts. 2. Micropayment : PayWord. 3. Streamobile : Videos streaming implementation
 Cyril MAILLET Computer Science Last Year Project STREAMOBILE PROJECT : Videos Streaming over the Internet Tutor : Josep Domingo-Ferrer Supervision : Antoni Martínez-Ballesté Francesc Sebé 1 Last Year Project
Cyril MAILLET Computer Science Last Year Project STREAMOBILE PROJECT : Videos Streaming over the Internet Tutor : Josep Domingo-Ferrer Supervision : Antoni Martínez-Ballesté Francesc Sebé 1 Last Year Project
Certificate-based authentication for data security
 Technical white paper Certificate-based authentication for data security Table of Contents Introduction... 2 Analogy: A simple checking account... 2 Verifying a digital certificate... 2 Summary... 8 Important
Technical white paper Certificate-based authentication for data security Table of Contents Introduction... 2 Analogy: A simple checking account... 2 Verifying a digital certificate... 2 Summary... 8 Important
X-AFFILIATE module for X-Cart 4.0.x
 X-AFFILIATE module for X-Cart 4.0.x Partner Interface Reference Manual Revision Date: 2004-11-22 Copyright 2001-2004 Ruslan R. Fazliev. All rights reserved. TABLE OF CONTENTS GENERAL INFORMATION...3 REGISTRATION...4
X-AFFILIATE module for X-Cart 4.0.x Partner Interface Reference Manual Revision Date: 2004-11-22 Copyright 2001-2004 Ruslan R. Fazliev. All rights reserved. TABLE OF CONTENTS GENERAL INFORMATION...3 REGISTRATION...4
CHANGES TO THIS POLICY
 Privacy Policy Your personal and corporate privacy is important to FunkyCouture.com. This privacy policy ( Policy ) applies to the FunkyCouture.com e Web sites and services and tells you how personal and
Privacy Policy Your personal and corporate privacy is important to FunkyCouture.com. This privacy policy ( Policy ) applies to the FunkyCouture.com e Web sites and services and tells you how personal and
Analysis of OpenFlow Networks.
 Analysis of OpenFlow Networks. Vikram Kulkarni Jayesh Kawli Introduction: Enterprise data center networks are rapidly reaching a breaking point, because of the data center network scale and complexity
Analysis of OpenFlow Networks. Vikram Kulkarni Jayesh Kawli Introduction: Enterprise data center networks are rapidly reaching a breaking point, because of the data center network scale and complexity
Ariba Network Quick Start Guide for Suppliers
 Ariba Network Quick Start Guide for Suppliers Table of Contents Managing Roles and Users...3 Creating a Role... 3 Creating a User... 5 Modifying a User... 7 Account Configuration...8 Company Profile...
Ariba Network Quick Start Guide for Suppliers Table of Contents Managing Roles and Users...3 Creating a Role... 3 Creating a User... 5 Modifying a User... 7 Account Configuration...8 Company Profile...
