IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment
|
|
|
- Lynette Eaton
- 6 years ago
- Views:
Transcription
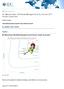
1 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS IDC MARKETSCAPE EXCERPT FEATURES: DXC IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide Managed Security Services Vendor Assessment Source: IDC, 2017 Please see the Appendix for detailed methodology, market definition, and scoring criteria. August 2017, IDC #US e
2 IN THIS EXCERPT The content for this excerpt was taken directly from IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment (Doc # US ). All or parts of the following sections are included in this excerpt: IDC Opinion, IDC MarketScape Vendor Inclusion Criteria, Essential Guidance, Vendor Summary Profile, Appendix and Learn More. Also included is Figure 1. IDC OPINION The managed security services (MSS) market continues to evolve rapidly. Within just the past few years, even the past 18 months, managed security services providers (MSSPs) have added more capabilities and advanced security services to assist organizations in defending against and responding to today's attacks. Using the IDC MarketScape model, IDC has compared 12 organizations that offer MSS worldwide. Through in-depth MSSP interviews and more than 20 interviews with providers' customers, IDC learned that all the providers included in this study have the necessary capabilities to deliver traditional worldwide MSS. However, most are now able to go beyond the traditional services areas, incorporating advanced services such as distributed denial of service (DDoS), web application security, identity access management (IAM), managed security and information event management (SIEM), and managed security operation center (SOC) (see Appendix for further details) into their propositions. By its very nature, inclusion in this rating study indicates that participants are top-rated global providers and should be considered for managed security services. Furthermore, as a result of this IDC MarketScape evaluation, IDC identified the following eight companies as Leaders: IBM, BT, Verizon, AT&T, Accenture, Deloitte, DXC Technology, and SecureWorks. The group of Major Players consists of Symantec, Wipro, HCL, and NTT Security. Given the rapid pace of development within the MSS market, it is important that all providers continue to develop upon MSS capabilities and go beyond the traditional offerings. This is essential to keep pace with the development of the market, let alone remaining ahead of the chasing pack. Through more granular evaluation, IDC found that each provider possesses some unique strengths and weaknesses when compared with its peer group. At a high level, the major differences centered on their strategies for the next 12 months. Many of the providers now offer a breadth of complementary security transformation services to assist customers with digital transformation. Other factors that were looked at include pricing, marketing, security operation centers staffing, and customer portal capabilities. IDC believes that the following areas will drive the MSS market forward while providing vendors with the opportunity to hone a differentiated proposition: Complementary services that provide customizable opportunities for assistance in security transformation and maturity; these can include enabling security within a customer's journey to the cloud Cloud monitoring, visibility, and management capabilities that seamlessly enable hybrid implementations Flexible consumption models that match customers' preferences for integrating MSSP expertise, processes, and technology Pricing models that support the end customer's buying preference Mobility and IoT solutions Advanced detection methods and analytics techniques, including advanced detection and response capabilities, threat intelligence, and big data 2017 IDC #US e 2
3 Robust customer support, including incident response (IR) and forensics, to assist with recovery from breaches Customer portal and reporting capabilities Security orchestration and automation technologies to provide more efficient incident response workflow Security operations centers Advanced methods of acquiring and retaining security talent IDC MARKETSCAPE VENDOR INCLUSION CRITERIA IDC collected and analyzed data on 12 MSSPs within the 2016 IDC MarketScape worldwide managed security services market assessment. While the market arena for MSS is broad and there are many suppliers that offer these services, IDC narrowed the field of participants for this study based on the following criteria: Service capability across the MSS life cycle. Each service provider was required to possess full-service MSS delivery capabilities (see the Appendix section for an explanation of MSS). Revenue. Each service provider was required to have 2015 total MSS global revenue in excess of $180 million and a SOC presence in each of three regions the Americas, EMEA, and APAC in addition to having a minimum of five SOCs. Geographic presence. Each vendor was required to have MSS delivery capability in each of three regions: the Americas, EMEA, and APAC. ADVICE FOR TECHNOLOGY BUYERS Buyers face complex choices in selecting an MSSP because of the number of providers and a multitude of variables: breadth and depth of offerings; staffing, capabilities, and locations; complementary services, onboarding methods, service-level agreements (SLAs), payment options, customer portal capabilities, customer service delivery methods, partnerships, and more. Given the pace of technology change, buyers should evaluate current and future MSSP offerings along with the MSSPs' product/service/investment road maps. This is important to be sure that future offerings align with anticipated business and cost projections. It can be expensive and disruptive to change providers, so it is worthwhile for buyers to take the time to find the right fit, no matter how many security services are being outsourced. An MSSP's customer satisfaction surveys, pricing benchmarks, use cases, proofs of concept, and/or best practices can aid the decision process. To enhance the decision-making process in vendor selection, IDC recommends that buyers bear in mind the following considerations: Evaluate the MSS research and development (R&D) road map. Many organizations are embarking on a digital transformation journey and are changing the way they operate, deliver services, and interact with their customers. It is imperative that an MSSP supports these organizations by providing trusted relationships and the security services needed to achieve their goals. Forward-looking MSSPs are paying attention to these changes and are enhancing their proposition around themes such as cloud evolution, incident response, forensics, advanced detection techniques, threat intelligence, artificial intelligence, machine learning, and big data analytics. Organizations need to evaluate an MSSP's future road map strategies 2017 IDC #US e 3
4 and determine whether the MSSP will be able to provide the security support necessitated by digital transformation. For example, cloud monitoring services are becoming more important as organizations adopt cloud. A knock-on effect of this change is that identity access management will be a critical factor as more applications move to the cloud and users move to hybrid clouds. A further example is provided by the trend of MSSPs seeking to implement software-defined networking (SDN) and network function virtualization (NFV) technologies as a means to create internal cost efficiencies and provide more nimble and flexible services. Review cloud adoption strategy and future security strategy. Workloads are shifting to multiple cloud platforms. This makes it important to select an MSSP that can deliver the offerings that best fit your business needs and can be flexible to meet future changes occurring within your infrastructure. Many MSSPs are working with customers to help them move to the cloud securely and successfully, perhaps as part of broader IT services engagements. In fact, for some enterprises and public entities, this has become a top priority. MSSPs are working with customers to expand the delivery of cloud offerings, and they are helping organizations with management and monitoring using on-premises equipment for log collection. Organizations are looking for ways to monitor their infrastructures as well as applications when delivered through public cloud platforms such as AWS and Azure. While on-premises has been a stable delivery model for MSSPs, ongoing cloud migrations are driving the demand for MSSPS to offer hosted and even cloud-based delivery models. Leverage threat intelligence and big data analytics. Cyberattacks are only going to increase in frequency and severity. Organizations can no longer afford a "do the minimum" security strategy, which is simply not sufficient to thwart advanced persistent threats, distributed denial of service, identity theft, and other sophisticated attack strategies. A commonsense best practice in retaliation to mitigate against these advanced attacks is to acquire and use reliable, "predictive" intelligence that results from a robust combination of technology and expertise. Buyers may want to evaluate MSSP capabilities such as large databases (for long-term analysis), data aggregation and correlation, user behavior- and heuristic-based detection (versus signature-based detection), anomaly detection, machine learning, emulation/sandboxing, virtual containerization, forensics, detection, and response tools. Buyers should look at how threat intelligence is being analyzed and distributed and whether MSSPs are using big data platforms such as Hadoop or Elastic Stack. Many MSSPs are investing in decreasing the human impact by automating data-related processes and analysis, which in turn will lead to faster decisions and response times. Buyers should look at how these MSSPS are investing in big data analytics, in growing their specialized skilled pool of researchers, adding dark web analytics, and cognitive and artificial intelligence. Review customer portals. Portals are the primary conduits of information between MSSPs and their customers, and they determine the scope and ease of visibility and control. Portals can be a competitive differentiator, and as such, they should be able to satisfy broad user requirements. Many providers are revamping their MSSP portals to make them user friendly and easy to navigate with visualization tools and customizable reporting capabilities. In addition, portals typically include real-time data analysis and advanced analytic capabilities to improve investigation workflow for purposes of enhancing detection and response times. Increasingly, portals include role-based access, querying of security and information event management data with broad correlation capabilities, and real-time chat or instant messaging. MSSPs are expanding search and communication, self-service capabilities, and in-depth reporting and enhancing visibility for customers. MSSPs should be able to demonstrate how their MSS are integrated into the portal and how the portal can be customized for different types of users (e.g., executives and security personnel) IDC #US e 4
5 Consider security expertise and customer engagement. Buyers should consider how the engagement will occur between them and an MSSP once the services are established. It is important that the MSSP acts as a trusted advisor and as an extension to the customer's IT team. Buyers may want to review whether staff augmentation is needed to support their initiatives and bring on staff to work with them on-premises or evaluate the expertise of the analysts being provided to them. MSSPs should be investing in cybersecurity proficiency and acquiring and retaining security talent. Investments in training and retention methods are important differentiation in a competitive marketplace. Evaluate complementary services. MSSPs included in this study offer some or all of the following services that are complementary to MSS: assessment of architecture and design, breach management, incident response, forensics, and compliance services. Some MSSPs offer additional services such as security transformation, IoT, adversary simulation, security awareness training, and cloud security. Buyers should consider an MSSP that can help develop, strengthen, and continue to evaluate their security programs. Enterprises must have a strategy to respond to incidents and collect forensic evidence for legal and/or compliance reasons. A preemptive strategy is even better one that does not treat all security threats as equal and apportions resources based on a current-state/future-state risk analysis. Review package security solutions. Security is becoming important not only in large enterprises but also in small to midsize organizations that are looking for lower cost, bundled security solutions. Services such as DDoS protection can be bundled with internet services and so forth. Small to midsize organizations should evaluate providers that will be able to provide these bundled services and products at a reasonable cost. Investigate flexible pricing methods. MSSPs typically offer their customers a number of pricing models. Ordinarily, a customer will choose to pay per device, by consumption of data (utility price option), or per IP pricing options. As MSS starts to downstream into midsize and smaller businesses, pricing models are becoming more flexible to accommodate the differences in scale and prioritization of smaller enterprises in comparison with larger ones. For example, some MSSPs are looking at newer and more innovative approaches. These include pricing per change request, logs/events collected, device-volume basis for which different tiers are offered, or pay-as-you-go pricing. Further, some MSSPs are investigating prepaid concepts, which hold some similarities in comparison with incident response "retainer" contracts. For example, customers can pay for a certain number of credits in advance using a standard rate. They allocate those credits against the activities they want at different times throughout the contract. With the introduction of new technologies, buyers need to be aware of the new pricing models and evaluate what will work best for their organizations. Review security orchestration and automation technologies. Providers are investing in automation and orchestration of technologies. The new techniques have a variety of benefits that can help customers order new services on demand and provide a more efficient workflow for analyzing threats. Buyers should be aware of what the MSSP road map looks like in implementing these new efficient technologies. Determine which SOC implementation matches business requirements. The types of SOC implementations are: In-region: A standalone SOC in a country or region Follow the sun (FTS): A type of global workflow in which tasks are passed around daily at the end of work shifts among work sites that may be in different time zones Global: Workflow that occurs in one global location in a 24 x 7 and multishift arrangement Some combination of in-region, FTS, and global SOC 2017 IDC #US e 5
6 More advanced MSSPs are able to offer a combination of SOC service delivery models in order to create a smooth handoff of change orders, tickets, and implementation as well as to create monitoring redundancy. In-region SOCs allow customer data to be retained in that region or country, which satisfies data privacy concerns and, in some cases, data sovereignty laws. To stay at the forefront of threat intelligence, however, MSSPs need to provide for anonymized meta-level data to leave the region or country for correlation purposes. FTS creates an advantage for MSSPs with international or multinational clients (MNCs) that require around-the-clock monitoring and management. The single-shift nature often associated with FTS allows employees to live their lives without working a nighttime shift and can create a cost benefit for the customer. The disadvantage of FTS can be a lack of consistency in support around handoff processes, installations, and incidents as well as in a possible lack of monitoring redundancy. Finally, FTS allows for localization of talent, which satisfies clients that prefer in-region language support and cultural perspective. However, there can be disconnects between each SOC in the rotation, and these cultural/language barriers can become an obstacle. IDC believes the highest tier of MSSPs, which are on the cutting edge of a truly global MSS delivery (versus international see the Terminology section), can satisfy regional data privacy concerns and the facilitation of an MNC security strategy with a combination of in-region, FTS, and global SOC structure. VENDOR SUMMARY PROFILES This section briefly explains IDC's key observations resulting in a vendor's position in the IDC MarketScape. While every vendor is evaluated against each of the criteria outlined in the Appendix, the description here provides a summary of each vendor's strengths and challenges. IDC reviewed 12 MSSPs against current capabilities and future strategy criteria as part of its IDC MarketScape on the worldwide MSS market. IDC also conducted customer interviews of more than 20 vendor customers to obtain feedback on how the vendors performed in delivering MSS. Vendors participating in the analysis are Accenture, AT&T, BT, DXC Technology, Deloitte, HCL Technologies, IBM, NTT Security, SecureWorks, Symantec, Wipro, and Verizon. DXC Technology According to IDC analysis and buyer perception, DXC Technology is considered an IDC MarketScape Leader worldwide. In early 2017, CSC and Hewlett Packard Enterprise (HPE) combined to create a service provider named DXC Technology. CSC is a multinational corporation based in the state of Virginia that provides IT services and professional services. Hewlett Packard Enterprise is located in Palo Alto, California. For this research, IDC has analyzed DXC Technology as HPE's capabilities and then combined CSC's capabilities into its future strategy. As of today, both offerings are still separate but will be consolidating their offerings starting in 2Q17. These two companies together bring significant mass and expertise to the MSSP landscape. Both companies bring capabilities to the other to strengthen and fill gaps in the overall offering. For example, HPE has nine SOCs globally, with two in EMEA, four in the Americas, and three in the APJ region. All of the SOCs function on a 24 x 7 x 365 model, with in-region pairing for support of regional clients in a model that ensures client familiarity and failover in case of disaster. The support model is used by some providers where the support for customers includes level one SOC 2017 IDC #US e 6
7 analysts along with higher senior level SOC analysts. They are all grouped around a small number of clients within the same industry and can also be assigned to just one large enterprise client. CSC brings six global SOCs all managed under a 24 x 7 x 365 workflow model. The SOC locations include three in APJ, two in the United Kingdom, and one in the United States many supporting both public sector and commercial clients. HPE describes one of its key differentiators as the combination of its security advisory, threat intelligence, and managed security services capabilities. This is particularly beneficial to organizations that are looking for an end-to-end, advisory-led approach, especially in meeting country-specific data privacy requirements. HPE is focused on helping organizations through security transformation, security maturity improvement, and managed services for those clients that require hybrid or ongoing comanaged services. These capabilities are supported by a full portfolio of MSS services that provide clients device and operational management of their security infrastructure, monitoring, and incident response. HPE believes that the combination in the MSS business of one player that can offer an integrated proposition between advisory, security management, security monitoring, and incident response is offering significant value to its customers from both a detection and a response perspective. CSC differentiates itself in the market by being a vendor independent end-to-end IT services company. CSC has developed cloud partnerships to offer cloud security services. CSC is creating cloud security solutions that can be deployed in virtual, public, and private cloud environments. In addition, CSC has also invested in a similar security monitoring offering to HPE called Integrated Security Operations (ISecOps) that will further integrate with client's workflow and the remediation processes. This new capability provides a set of cybersecurity operational processes and advanced workflows built on top of the ServiceNow platform. As DXC Technology consolidates its offerings and platforms for MSS, IDC expects a blend of detection and response capabilities from HPE and workflow, orchestration, and response capabilities from CSC. Strengths Both companies have a stable reputation and brand name. The combination of CSC and HPE will result in a span of new capabilities and complement some service gaps lacking in each. HPE's advisory and consulting services and CSC's strong partnerships will also enable DXC Technology to make a leap in creating new cloud security services as well as improve automation and orchestration techniques. Challenges DXC Technology could further enhance its advanced detection and analytic technologies such as behavioral and heuristic-based detection techniques and big data analytics, which we understand has been in progress on the HPE side. IDC anticipates that the new company may run into challenges related to retaining employees and transitioning customers to new processes. APPENDIX The security landscape is complex and challenging an understatement, given the number of moving parts that are involved in defending an enterprise from cyberattacks. IDC recommends that companies undertake a holistic, enterprisewide security posture that is proactive and predictive IDC #US e 7
8 It's a daunting effort, however, to sustain the necessary level of threat intelligence and advanced analytics capabilities along with the skills to interpret and act on findings. In-house 24 x 7 security solutions are expensive, and security talent is scarce. As a result, organizations debate "build versus buy," and many are turning to MSSPs. A security services provider can allow organizations to meet several objectives: Transfer the cost of ownership, thereby reducing capex and transferring the budget to opex Create a predictable expense with a regular cadence in the budget cycle Enable a dedicated application of technology, processes, and people to the rapidly changing threat landscape Implement best practices that are evolving with a rapidly changing threat landscape Benefit from "strength in numbers" from an intelligence perspective The rise in frequency and complexity of attacks and the need for increasingly sophisticated security solutions have led to a new echelon of MSS that IDC is calling MSS 2.0. An MSSP 2.0 is further "up the stack" than MSSPs that are offering MSS 1.0 services, which include the following: Log monitoring Basic managed and monitored services (firewalls and intrusion detection services/intrusion prevention services) Unified threat management Identity and access management Vulnerability scanning MSSPs 1.0 may also offer advanced services such as DDoS, managed SIEM, and managed SOC. MSSPs 2.0 deliver basic and advanced MSS plus professional/complementary services (for more details, see the Market Definition section). They are also investing in mobile/iot, cloud, threat intelligence/big data analytics, incident response/forensics, and advanced detection techniques. Cloud, mobile/iot, and big data are three of four pillars that IDC has identified as top trends. The fourth pillar, social media, doesn't factor into this IDC MarketScape; however, advanced MSSP capabilities can help detect, analyze, and protect against security threats in the social media arena. Security, in general, is complicated by the shortage of security talent. Innovative MSSPs focus on short- and long-term employee acquisition, training, and retention using both traditional and progressive practices. Some of their tactics are apprentice programs, scholarships, in-house universities, university partnerships, and flexible career paths. Further, regulatory requirements continue to evolve, and MSSPs can provide the expertise and evidence needed for oversight and compliance based on industry-standard certifications. Businesses increasingly are turning to MSSPs to monitor and manage some or all of their security needs. Based on IDC market sizing, the MSS market is expected to continue to see growth in double digits in coming years. Reading an IDC MarketScape Graph For the purposes of this analysis, IDC divided potential key measures for success into two primary categories: capabilities and strategies IDC #US e 8
9 Positioning on the y-axis reflects the vendor's current capabilities and menu of services and how well aligned the vendor is to customer needs. The capabilities category focuses on the capabilities of the company and product today, here and now. Under this category, IDC analysts will look at how well a vendor is building/delivering capabilities that enable it to execute its chosen strategy in the market. Positioning on the x-axis, or strategies axis, indicates how well the vendor's future strategy aligns with what customers will require in three to five years. The strategies category focuses on high-level decisions and underlying assumptions about offerings, customer segments, and business and go-tomarket plans for the next three to five years. The size of the individual vendor markers in the IDC MarketScape represents the market share of each individual vendor within the specific market segment being assessed. IDC MarketScape Methodology IDC MarketScape criteria selection, weightings, and vendor scores represent well-researched IDC judgment about the market and specific vendors. IDC analysts tailor the range of standard characteristics by which vendors are measured through structured discussions, surveys, and interviews with market leaders, participants, and end users. Market weightings are based on user interviews, buyer surveys, and the input of a review board of IDC experts in each market. IDC analysts base individual vendor scores, and ultimately vendor positions on the IDC MarketScape, on detailed surveys and interviews with the vendors, publicly available information, and end-user experiences in an effort to provide an accurate and consistent assessment of each vendor's characteristics, behavior, and capability. Market Definition Managed Security Services For the purposes of this research, IDC defines managed security services as "the around-the-clock remote management or monitoring of IT security functions delivered via remote security operations centers (SOCs), not through personnel onsite." Exceptions and Inclusions Managed security services can include complementary consulting and advisory activities that are typically defined under professional security services. The study did seek to understand whether the MSSPs offer complementary services as IDC believes these services are critical to the evolution and maturity of MSS. The MSSPs in this study do provide complementary services; although, there is no standard approach for how they are offered. Commonly, an initial assessment is bundled with the onboarding fees, and some may bundle other services. Most, however, offer complementary services as optional add-ons and may charge separately for them. Complementary services surveyed in the study include breach management, incident response, forensics, compliance services, and assessment of architecture and design. Not all MSSPs provide all of these services. Some MSSPs provide all of the listed complementary services and others such as managed security testing, application security testing, advisory services, integration services, and data privacy assessment IDC #US e 9
10 Terminology Managed security and information event management (managed SIEM). This managed onpremises event collector transmits the raw log data to an MSSP's SOC for analysis, reporting, and archiving. This is an advanced, niche capability that is offered currently by half of the participants in this study. Managed SOC. A security operations center includes the people, processes, and technologies involved in detecting, containing, and remediating security threats. Some MSSPs take over the operation of SOCs that their customers have built and no longer want to manage. This is an advanced, niche offering that is offered currently by a majority of the participants in this study. Security operations center types: LEARN MORE In-region. A standalone SOC in a country or region Follow the sun. A type of global workflow in which tasks are passed around daily at the end of work shifts among sites that may be in different time zones Global. Workflow that occurs in one global location in a 24 x 7 multishift arrangement Related Research IDC MarketScape: Western Europe Managed Security Services 2017 Vendor Assessment (forthcoming) Worldwide DDoS Prevention Products and Services Forecast, (IDC #US , May 2017) IDC MarketScape: U.S. Emerging Managed Security Services 2016 Vendor Assessment (IDC #US , August 2016) Synopsis This IDC study presents a vendor assessment of providers offering managed security services (MSS) through the IDC MarketScape model. The assessment reviews both quantitative and qualitative characteristics that define current market demands and expected buyer needs for MSS. The evaluation is based on a comprehensive and rigorous framework that assesses how each vendor stacks up to one another, and the framework highlights the key factors that are expected to be the most significant for achieving success in the MSS market over the short term and the long term. "The security landscape is changing rapidly, and organizations continue to struggle to maintain their own in-house security solutions and staff. As a result, organizations are turning to managed security service providers (MSSPs) to deliver a wide span of security capabilities and consulting services, which include predicative threat intelligence and advanced detection and analysis expertise that are necessary to overcome the security challenges happening today as well as prepare organizations against future attacks. The MSSP market is highly competitive, and many MSSPs have a breadth of security services in their MSS portfolio. The differentiation among these MSSPs will be tied around their flexibility in delivering security services and advanced MSS capabilities and how these MSSPs can continue to assist organizations with their security needs today and in the future." Martha Vazquez, senior research analyst, Infrastructure Services 2017 IDC #US e 10
11 About IDC International Data Corporation (IDC) is the premier global provider of market intelligence, advisory services, and events for the information technology, telecommunications and consumer technology markets. IDC helps IT professionals, business executives, and the investment community make factbased decisions on technology purchases and business strategy. More than 1,100 IDC analysts provide global, regional, and local expertise on technology and industry opportunities and trends in over 110 countries worldwide. For 50 years, IDC has provided strategic insights to help our clients achieve their key business objectives. IDC is a subsidiary of IDG, the world's leading technology media, research, and events company. Global Headquarters 5 Speen Street Framingham, MA USA idc-community.com Copyright and Trademark Notice This IDC research document was published as part of an IDC continuous intelligence service, providing written research, analyst interactions, telebriefings, and conferences. Visit to learn more about IDC subscription and consulting services. To view a list of IDC offices worldwide, visit Please contact the IDC Hotline at , ext (or ) or sales@idc.com for information on applying the price of this document toward the purchase of an IDC service or for information on additional copies or web rights. IDC and IDC MarketScape are trademarks of International Data Group, Inc. Copyright 2017 IDC. Reproduction is forbidden unless authorized. All rights reserved.
IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS MARKETSCAPE EXCERPT WAS CREATED FOR BT IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS MARKETSCAPE EXCERPT WAS CREATED FOR BT IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment Chad Huston Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES: WIPRO IDC
IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment Chad Huston Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES: WIPRO IDC
IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES DELL EMC IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES DELL EMC IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape: Worldwide Managed Security Services 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2014 Vendor Assessment Christina Richmond THIS IDC MARKETSCAPE EXCERPT FEATURES: AT&T IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2014 Vendor Assessment Christina Richmond THIS IDC MARKETSCAPE EXCERPT FEATURES: AT&T IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment Leslie Rosenberg THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment Leslie Rosenberg THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2014 Vendor Assessment Ali Zaidi Gard Little THIS IDC MARKETSCAPE EXCERPT FEATURES: HCL IDC MARKETSCAPE
IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2014 Vendor Assessment Ali Zaidi Gard Little THIS IDC MARKETSCAPE EXCERPT FEATURES: HCL IDC MARKETSCAPE
IDC MarketScape: Worldwide Service Providers 2018 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Service Providers 2018 Vendor Assessment Courtney Munroe THIS IDC MARKETSCAPE EXCERPT FEATURES NTT COMMUNICATIONS IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Service Providers 2018 Vendor Assessment Courtney Munroe THIS IDC MARKETSCAPE EXCERPT FEATURES NTT COMMUNICATIONS IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment Robert Palmer Allison Correia THIS IDC MARKETSCAPE EXCERPT FEATURES: HP IDC MARKETSCAPE FIGURE
IDC MarketScape IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment Robert Palmer Allison Correia THIS IDC MARKETSCAPE EXCERPT FEATURES: HP IDC MARKETSCAPE FIGURE
Predictive Insight, Automation and Expertise Drive Added Value for Managed Services
 Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
IDC MarketScape: Worldwide Mobile Threat Management Software Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Mobile Threat Management Software 2018 2019 Vendor Assessment Phil Hochmuth THIS IDC MARKETSCAPE EXCERPT FEATURES LOOKOUT IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Mobile Threat Management Software 2018 2019 Vendor Assessment Phil Hochmuth THIS IDC MARKETSCAPE EXCERPT FEATURES LOOKOUT IDC MARKETSCAPE FIGURE FIGURE 1 IDC
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment Jennifer Koppy THIS IDC MARKETSCAPE EXCERPT FEATURES PANDUIT CORPORATION IDC MARKETSCAPE FIGURE FIGURE
IDC MarketScape IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment Jennifer Koppy THIS IDC MARKETSCAPE EXCERPT FEATURES PANDUIT CORPORATION IDC MARKETSCAPE FIGURE FIGURE
RSA Solution Brief. Managing Risk Within Advanced Security Operations. RSA Solution Brief
 RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE
 DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
Worldwide Datacenter Automation Software 2013 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Datacenter Automation Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide datacenter automation software submarket of the workload scheduling
COMPETITIVE ANALYSIS Worldwide Datacenter Automation Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide datacenter automation software submarket of the workload scheduling
IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide Managed Security Services Vendor Assessment
IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide Managed Security Services Vendor Assessment
The Emerging Role of a CDN in Facilitating Secure Cloud Deployments
 White Paper The Emerging Role of a CDN in Facilitating Secure Cloud Deployments Sponsored by: Fastly Robert Ayoub August 2017 IDC OPINION The ongoing adoption of cloud services and the desire for anytime,
White Paper The Emerging Role of a CDN in Facilitating Secure Cloud Deployments Sponsored by: Fastly Robert Ayoub August 2017 IDC OPINION The ongoing adoption of cloud services and the desire for anytime,
Making hybrid IT simple with Capgemini and Microsoft Azure Stack
 Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
PREPARE FOR TAKE OFF. Accelerate your organisation s journey to the Cloud.
 PREPARE FOR TAKE OFF Accelerate your organisation s journey to the Cloud. cloud. Contents Introduction Program & Governance BJSS Cloud Readiness Assessment: Intro Platforms & Development BJSS Cloud Readiness
PREPARE FOR TAKE OFF Accelerate your organisation s journey to the Cloud. cloud. Contents Introduction Program & Governance BJSS Cloud Readiness Assessment: Intro Platforms & Development BJSS Cloud Readiness
How to Write an MSSP RFP. White Paper
 How to Write an MSSP RFP White Paper Tables of Contents Introduction 3 Benefits Major Items of On-Premise to Consider SIEM Before Solutions Security Writing an RFP and Privacy 45 Benefits Building an of
How to Write an MSSP RFP White Paper Tables of Contents Introduction 3 Benefits Major Items of On-Premise to Consider SIEM Before Solutions Security Writing an RFP and Privacy 45 Benefits Building an of
SOLUTION BRIEF RSA ARCHER IT & SECURITY RISK MANAGEMENT
 RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
White Paper. How to Write an MSSP RFP
 White Paper How to Write an MSSP RFP https://www.solutionary.com (866) 333-2133 Contents 3 Introduction 3 Why a Managed Security Services Provider? 5 Major Items to Consider Before Writing an RFP 5 Current
White Paper How to Write an MSSP RFP https://www.solutionary.com (866) 333-2133 Contents 3 Introduction 3 Why a Managed Security Services Provider? 5 Major Items to Consider Before Writing an RFP 5 Current
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
I D C T E C H N O L O G Y S P O T L I G H T
 I D C T E C H N O L O G Y S P O T L I G H T P ow e ring Digital Transfor m a t i o n T h r ough the C l o u d - R e a d y E n t e r p rise September 2016 Adapted from Developing a Cloud Strategy for Digital
I D C T E C H N O L O G Y S P O T L I G H T P ow e ring Digital Transfor m a t i o n T h r ough the C l o u d - R e a d y E n t e r p rise September 2016 Adapted from Developing a Cloud Strategy for Digital
Symantec Data Center Transformation
 Symantec Data Center Transformation A holistic framework for IT evolution As enterprises become increasingly dependent on information technology, the complexity, cost, and performance of IT environments
Symantec Data Center Transformation A holistic framework for IT evolution As enterprises become increasingly dependent on information technology, the complexity, cost, and performance of IT environments
New Zealand Government IBM Infrastructure as a Service
 New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
DATA SHEET RSA NETWITNESS PLATFORM PROFESSIONAL SERVICES ACCELERATE TIME-TO-VALUE & MAXIMIZE ROI
 DATA SHEET RSA NETWITNESS PLATFORM PROFESSIONAL SERVICES ACCELERATE TIME-TO-VALUE & MAXIMIZE ROI EXECUTIVE SUMMARY The shortage of cybersecurity skills Organizations continue to face a shortage of IT skill
DATA SHEET RSA NETWITNESS PLATFORM PROFESSIONAL SERVICES ACCELERATE TIME-TO-VALUE & MAXIMIZE ROI EXECUTIVE SUMMARY The shortage of cybersecurity skills Organizations continue to face a shortage of IT skill
Government IT Modernization and the Adoption of Hybrid Cloud
 Government IT Modernization and the Adoption of Hybrid Cloud An IDC InfoBrief, Sponsored by VMware June 2018 Federal and National Governments Are at an Inflection Point Federal and national governments
Government IT Modernization and the Adoption of Hybrid Cloud An IDC InfoBrief, Sponsored by VMware June 2018 Federal and National Governments Are at an Inflection Point Federal and national governments
Intent-Based Networking in the Limelight with Cisco's Launch of Catalyst 9000 Series Ethernet Switches
 MARKET NOTE Intent-Based Networking in the Limelight with Cisco's Launch of Catalyst 9000 Series Ethernet Switches Nolan Greene Rohit Mehra EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Cisco Intent-Based
MARKET NOTE Intent-Based Networking in the Limelight with Cisco's Launch of Catalyst 9000 Series Ethernet Switches Nolan Greene Rohit Mehra EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Cisco Intent-Based
Akamai: Turning Enterprise Security Inside Out
 VENDOR PROFILE Akamai: Turning Enterprise Security Inside Out Christina Richmond Duncan Brown IDC OPINION Akamai is a leader in content delivery network (CDN) services. The company has built a web security
VENDOR PROFILE Akamai: Turning Enterprise Security Inside Out Christina Richmond Duncan Brown IDC OPINION Akamai is a leader in content delivery network (CDN) services. The company has built a web security
Text Messaging Helps Your Small Business Perform Big
 White Paper Text Messaging Helps Your Small Business Perform Big Sponsored by: AT&T Denise Lund August 2017 IN THIS WHITE PAPER This white paper introduces small businesses to the benefits of communicating
White Paper Text Messaging Helps Your Small Business Perform Big Sponsored by: AT&T Denise Lund August 2017 IN THIS WHITE PAPER This white paper introduces small businesses to the benefits of communicating
CloudGenix: Application-Centric SD-WAN
 Vendor Profile CloudGenix: Application-Centric SD-WAN Ksenia Efimova IDC OPINION The software-defined WAN (SD-WAN) market has started to mature as companies begin to understand the advantages of SD-WAN
Vendor Profile CloudGenix: Application-Centric SD-WAN Ksenia Efimova IDC OPINION The software-defined WAN (SD-WAN) market has started to mature as companies begin to understand the advantages of SD-WAN
SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM
 SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM OVERVIEW The Verizon 2016 Data Breach Investigations Report highlights that attackers are regularly outpacing the defenders.
SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM OVERVIEW The Verizon 2016 Data Breach Investigations Report highlights that attackers are regularly outpacing the defenders.
Business Continuity & Disaster Recovery
 knowledge partner MARKET INSIGHT Business Continuity & Disaster Recovery Considerations for Saudi Organizations /mobily @MobilyBusiness 056 010 0901 I business.sales@mobily.com.sa About Us Mobily; the
knowledge partner MARKET INSIGHT Business Continuity & Disaster Recovery Considerations for Saudi Organizations /mobily @MobilyBusiness 056 010 0901 I business.sales@mobily.com.sa About Us Mobily; the
Accelerate Your Enterprise Private Cloud Initiative
 Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Optimizing Infrastructure Management with Predictive Analytics: The Red Hat Insights Approach
 White Paper Optimizing Infrastructure Management with Predictive Analytics: The Red Hat Insights Approach Sponsored by: Red Hat Tim Grieser January 2018 IN THIS WHITE PAPER This IDC White Paper discusses
White Paper Optimizing Infrastructure Management with Predictive Analytics: The Red Hat Insights Approach Sponsored by: Red Hat Tim Grieser January 2018 IN THIS WHITE PAPER This IDC White Paper discusses
Symantec Security Monitoring Services
 24x7 real-time security monitoring and protection Protect corporate assets from malicious global threat activity before it impacts your network. Partnering with Symantec skilled and experienced analysts
24x7 real-time security monitoring and protection Protect corporate assets from malicious global threat activity before it impacts your network. Partnering with Symantec skilled and experienced analysts
Incident Response Services to Help You Prepare for and Quickly Respond to Security Incidents
 Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats.
 IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats. Enhancing cost to serve and pricing maturity Keeping up with quickly evolving ` Internet threats
IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats. Enhancing cost to serve and pricing maturity Keeping up with quickly evolving ` Internet threats
INTELLIGENCE DRIVEN GRC FOR SECURITY
 INTELLIGENCE DRIVEN GRC FOR SECURITY OVERVIEW Organizations today strive to keep their business and technology infrastructure organized, controllable, and understandable, not only to have the ability to
INTELLIGENCE DRIVEN GRC FOR SECURITY OVERVIEW Organizations today strive to keep their business and technology infrastructure organized, controllable, and understandable, not only to have the ability to
Securing Your Digital Transformation
 Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Run the business. Not the risks.
 Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
Continuous protection to reduce risk and maintain production availability
 Industry Services Continuous protection to reduce risk and maintain production availability Managed Security Service Answers for industry. Managing your industrial cyber security risk requires world-leading
Industry Services Continuous protection to reduce risk and maintain production availability Managed Security Service Answers for industry. Managing your industrial cyber security risk requires world-leading
DATACENTER SERVICES DATACENTER
 SERVICES SOLUTION SUMMARY ALL CHANGE React, grow and innovate faster with Computacenter s agile infrastructure services Customers expect an always-on, superfast response. Businesses need to release new
SERVICES SOLUTION SUMMARY ALL CHANGE React, grow and innovate faster with Computacenter s agile infrastructure services Customers expect an always-on, superfast response. Businesses need to release new
RSA ADVANCED SOC SERVICES
 RSA ADVANCED SOC SERVICES Consulting services to improve threat detection and response EXECUTIVE SUMMARY A holistic approach to enhanced cybersecurity operations This service is for organizations needing
RSA ADVANCED SOC SERVICES Consulting services to improve threat detection and response EXECUTIVE SUMMARY A holistic approach to enhanced cybersecurity operations This service is for organizations needing
THE SIX ESSENTIAL CAPABILITIES OF AN ANALYTICS-DRIVEN SIEM
 THE SIX ESSENTIAL CAPABILITIES OF AN ANALYTICS-DRIVEN SIEM Modern threats demand analytics-driven security and continuous monitoring Legacy SIEMs are Stuck in the Past Finding a mechanism to collect, store
THE SIX ESSENTIAL CAPABILITIES OF AN ANALYTICS-DRIVEN SIEM Modern threats demand analytics-driven security and continuous monitoring Legacy SIEMs are Stuck in the Past Finding a mechanism to collect, store
Healthcare IT Modernization and the Adoption of Hybrid Cloud
 Healthcare IT Modernization and the Adoption of Hybrid Cloud An IDC InfoBrief, Sponsored by VMware June 2018 Executive Summary The healthcare industry is facing unprecedented changes brought about by a
Healthcare IT Modernization and the Adoption of Hybrid Cloud An IDC InfoBrief, Sponsored by VMware June 2018 Executive Summary The healthcare industry is facing unprecedented changes brought about by a
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS. Security Without Compromise
 DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
Evolution For Enterprises In A Cloud World
 Evolution For Enterprises In A Cloud World Foreword Cloud is no longer an unseen, futuristic technology that proves unattainable for enterprises. Rather, it s become the norm; a necessity for realizing
Evolution For Enterprises In A Cloud World Foreword Cloud is no longer an unseen, futuristic technology that proves unattainable for enterprises. Rather, it s become the norm; a necessity for realizing
RSA NetWitness Suite Respond in Minutes, Not Months
 RSA NetWitness Suite Respond in Minutes, Not Months Overview One can hardly pick up a newspaper or turn on the news without hearing about the latest security breaches. The Verizon 2015 Data Breach Investigations
RSA NetWitness Suite Respond in Minutes, Not Months Overview One can hardly pick up a newspaper or turn on the news without hearing about the latest security breaches. The Verizon 2015 Data Breach Investigations
RSA INCIDENT RESPONSE SERVICES
 RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
IT Consulting and Implementation Services
 PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
WITH ACTIVEWATCH EXPERT BACKED, DETECTION AND THREAT RESPONSE BENEFITS HOW THREAT MANAGER WORKS SOLUTION OVERVIEW:
 SOLUTION OVERVIEW: ALERT LOGIC THREAT MANAGER WITH ACTIVEWATCH EXPERT BACKED, DETECTION AND THREAT RESPONSE Protecting your business assets and sensitive data requires regular vulnerability assessment,
SOLUTION OVERVIEW: ALERT LOGIC THREAT MANAGER WITH ACTIVEWATCH EXPERT BACKED, DETECTION AND THREAT RESPONSE Protecting your business assets and sensitive data requires regular vulnerability assessment,
THE STATE OF IT TRANSFORMATION FOR TELECOMMUNICATIONS
 THE STATE OF IT TRANSFORMATION FOR TELECOMMUNICATIONS An Analysis by Dell EMC and VMware Dell EMC and VMware are helping IT groups at telecommunication organizations transform to business-focused service
THE STATE OF IT TRANSFORMATION FOR TELECOMMUNICATIONS An Analysis by Dell EMC and VMware Dell EMC and VMware are helping IT groups at telecommunication organizations transform to business-focused service
Supporting the Cloud Transformation of Agencies across the Public Sector
 SOLUTION SERVICES Supporting the Cloud Transformation of Agencies across the Public Sector BRIEF Digital transformation, aging IT infrastructure, the Modernizing Government Technology (MGT) Act, the Datacenter
SOLUTION SERVICES Supporting the Cloud Transformation of Agencies across the Public Sector BRIEF Digital transformation, aging IT infrastructure, the Modernizing Government Technology (MGT) Act, the Datacenter
Optimisation drives digital transformation
 January 2017 Executive summary Forward-thinking business leaders are challenging their organisations to achieve transformation by harnessing digital technologies with organisational, operational, and business
January 2017 Executive summary Forward-thinking business leaders are challenging their organisations to achieve transformation by harnessing digital technologies with organisational, operational, and business
Gain Control Over Your Cloud Use with Cisco Cloud Consumption Professional Services
 Solution Overview Gain Control Over Your Cloud Use with Cisco Cloud Consumption Professional Services OPTIMIZE YOUR CLOUD SERVICES TO DRIVE BETTER BUSINESS OUTCOMES Reduce Cloud Business Risks and Costs
Solution Overview Gain Control Over Your Cloud Use with Cisco Cloud Consumption Professional Services OPTIMIZE YOUR CLOUD SERVICES TO DRIVE BETTER BUSINESS OUTCOMES Reduce Cloud Business Risks and Costs
CYBER RESILIENCE & INCIDENT RESPONSE
 CYBER RESILIENCE & INCIDENT RESPONSE www.nccgroup.trust Introduction The threat landscape has changed dramatically over the last decade. Once the biggest threats came from opportunist attacks and preventable
CYBER RESILIENCE & INCIDENT RESPONSE www.nccgroup.trust Introduction The threat landscape has changed dramatically over the last decade. Once the biggest threats came from opportunist attacks and preventable
Three Key Challenges Facing ISPs and Their Enterprise Clients
 Three Key Challenges Facing ISPs and Their Enterprise Clients GRC, enterprise services, and ever-evolving hybrid infrastructures are all dynamic and significant challenges to the ISP s enterprise clients.
Three Key Challenges Facing ISPs and Their Enterprise Clients GRC, enterprise services, and ever-evolving hybrid infrastructures are all dynamic and significant challenges to the ISP s enterprise clients.
Hybrid IT for SMBs. HPE addressing SMB and channel partner Hybrid IT demands ANALYST ANURAG AGRAWAL REPORT : HPE. October 2018
 V REPORT : HPE Hybrid IT for SMBs HPE addressing SMB and channel partner Hybrid IT demands October 2018 ANALYST ANURAG AGRAWAL Data You Can Rely On Analysis You Can Act Upon HPE addressing SMB and partner
V REPORT : HPE Hybrid IT for SMBs HPE addressing SMB and channel partner Hybrid IT demands October 2018 ANALYST ANURAG AGRAWAL Data You Can Rely On Analysis You Can Act Upon HPE addressing SMB and partner
RSA INCIDENT RESPONSE SERVICES
 RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
NEXT GENERATION SECURITY OPERATIONS CENTER
 DTS SOLUTION NEXT GENERATION SECURITY OPERATIONS CENTER SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 - SUCCESS FACTORS SOC 2.0 - FUNCTIONAL COMPONENTS DTS SOLUTION SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 Protecting
DTS SOLUTION NEXT GENERATION SECURITY OPERATIONS CENTER SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 - SUCCESS FACTORS SOC 2.0 - FUNCTIONAL COMPONENTS DTS SOLUTION SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 Protecting
Professional Services for Cloud Management Solutions
 Professional Services for Cloud Management Solutions Accelerating Your Cloud Management Capabilities CEOs need people both internal staff and thirdparty providers who can help them think through their
Professional Services for Cloud Management Solutions Accelerating Your Cloud Management Capabilities CEOs need people both internal staff and thirdparty providers who can help them think through their
Choosing the Right Cloud. ebook
 Choosing the Right Cloud ebook Contents Choosing the Right Cloud...3 The Cloud Explained: Public Cloud...4 The Cloud Explained: Private Cloud...5 Assessing Workload Characteristics...6 Right Application.
Choosing the Right Cloud ebook Contents Choosing the Right Cloud...3 The Cloud Explained: Public Cloud...4 The Cloud Explained: Private Cloud...5 Assessing Workload Characteristics...6 Right Application.
Atlantis Computing Adds the Ability to Address Classic Server Workloads
 FLASH Atlantis Computing Adds the Ability to Address Classic Server Workloads Eric Burgener Brett Waldman IN THIS FLASH This IDC Flash discusses Atlantis Computing's In-Memory Storage technology and how
FLASH Atlantis Computing Adds the Ability to Address Classic Server Workloads Eric Burgener Brett Waldman IN THIS FLASH This IDC Flash discusses Atlantis Computing's In-Memory Storage technology and how
Total Cost of Ownership: Benefits of the OpenText Cloud
 Total Cost of Ownership: Benefits of the OpenText Cloud OpenText Managed Services in the Cloud delivers on the promise of a digital-first world for businesses of all sizes. This paper examines how organizations
Total Cost of Ownership: Benefits of the OpenText Cloud OpenText Managed Services in the Cloud delivers on the promise of a digital-first world for businesses of all sizes. This paper examines how organizations
Best Practices in Securing a Multicloud World
 Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
SIEM: Five Requirements that Solve the Bigger Business Issues
 SIEM: Five Requirements that Solve the Bigger Business Issues After more than a decade functioning in production environments, security information and event management (SIEM) solutions are now considered
SIEM: Five Requirements that Solve the Bigger Business Issues After more than a decade functioning in production environments, security information and event management (SIEM) solutions are now considered
Automated Infrastructure Management Powers Future-Ready Enterprise Clouds
 WHITE PAPER Automated Infrastructure Management Powers Future-Ready Enterprise Clouds Sponsored by: Dell Mary Johnston Turner April 2016 Richard L. Villars IDC OPINION Future-ready enterprises continually
WHITE PAPER Automated Infrastructure Management Powers Future-Ready Enterprise Clouds Sponsored by: Dell Mary Johnston Turner April 2016 Richard L. Villars IDC OPINION Future-ready enterprises continually
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com INSIGHT VERITAS: Expanding the Storage Foundations and Building Utility Computing Rhoda Phillips Bill
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com INSIGHT VERITAS: Expanding the Storage Foundations and Building Utility Computing Rhoda Phillips Bill
TRUE SECURITY-AS-A-SERVICE
 TRUE SECURITY-AS-A-SERVICE To effectively defend against today s cybercriminals, organizations must look at ways to expand their ability to secure and maintain compliance across their evolving IT infrastructure.
TRUE SECURITY-AS-A-SERVICE To effectively defend against today s cybercriminals, organizations must look at ways to expand their ability to secure and maintain compliance across their evolving IT infrastructure.
Cisco Start. IT solutions designed to propel your business
 Cisco Start IT solutions designed to propel your business Small and medium-sized businesses (SMBs) typically have very limited resources to invest in new technologies. With every IT investment made, they
Cisco Start IT solutions designed to propel your business Small and medium-sized businesses (SMBs) typically have very limited resources to invest in new technologies. With every IT investment made, they
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS
 Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
Cyber Group Deploys EMC ViPR for Next-Generation SaaS Application Infrastructure
 Buyer Case Study Cyber Group Deploys EMC ViPR for Next-Generation SaaS Application Infrastructure Laura DuBois IDC OPINION 3rd Platform computing has given rise to massive scale datacenters architected
Buyer Case Study Cyber Group Deploys EMC ViPR for Next-Generation SaaS Application Infrastructure Laura DuBois IDC OPINION 3rd Platform computing has given rise to massive scale datacenters architected
IDC MarketScape: Canadian Data Centre Operations and Management 2016 Vendor Assessment
 IDC MarketScape IDC MarketScape: Canadian Data Centre Operations and Management 2016 Vendor Assessment Mark Schrutt IN THIS EXCERPT The content for this excerpt was taken directly from the IDC MarketScape:
IDC MarketScape IDC MarketScape: Canadian Data Centre Operations and Management 2016 Vendor Assessment Mark Schrutt IN THIS EXCERPT The content for this excerpt was taken directly from the IDC MarketScape:
Securing Digital Transformation
 September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
Cybersecurity. Securely enabling transformation and change
 Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
HPE Partner Ready Digital Marketing Program
 HPE Partner Ready Digital Marketing Program Accelerating your digital marketing proficiency and execution to drive business growth Collaborate Get started Table of Contents Changing B2B Buyer Behavior
HPE Partner Ready Digital Marketing Program Accelerating your digital marketing proficiency and execution to drive business growth Collaborate Get started Table of Contents Changing B2B Buyer Behavior
Incident Response Services
 Services Enhanced with Supervised Machine Learning and Human Intelligence Empowering clients to stay one step ahead of the adversary. Secureworks helps clients enable intelligent actions to outsmart and
Services Enhanced with Supervised Machine Learning and Human Intelligence Empowering clients to stay one step ahead of the adversary. Secureworks helps clients enable intelligent actions to outsmart and
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e n t e r I n f r a s t r
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e n t e r I n f r a s t r
Vendor Snapshot 2017: HP Inc. on Print and Document Security Services
 MARKET NOTE Vendor Snapshot 2017: HP Inc. on Print and Document Security Services Robert Palmer Allison Correia EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Vendor Snapshot 2017 HP Inc. on Print and
MARKET NOTE Vendor Snapshot 2017: HP Inc. on Print and Document Security Services Robert Palmer Allison Correia EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Vendor Snapshot 2017 HP Inc. on Print and
RFP/RFI Questions for Managed Security Services. Sample MSSP RFP Template
 RFP/RFI Questions for Managed Security Services Sample MSSP RFP Template Table of Contents Request for Proposal Template Overview 1 Introduction... 1 How to Use this Document... 1 Suggested RFP Outline
RFP/RFI Questions for Managed Security Services Sample MSSP RFP Template Table of Contents Request for Proposal Template Overview 1 Introduction... 1 How to Use this Document... 1 Suggested RFP Outline
I D C T E C H N O L O G Y S P O T L I G H T. V i r t u a l and Cloud D a t a Center Management
 I D C T E C H N O L O G Y S P O T L I G H T Orchestration S i m p l i f i es and Streamlines V i r t u a l and Cloud D a t a Center Management January 2013 Adapted from Systems Management Software Purchasing
I D C T E C H N O L O G Y S P O T L I G H T Orchestration S i m p l i f i es and Streamlines V i r t u a l and Cloud D a t a Center Management January 2013 Adapted from Systems Management Software Purchasing
IDC MarketScape: Worldwide Endpoint Specialized Threat Analysis and Protection 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Endpoint Specialized Threat Analysis and Protection 2017 Vendor Assessment Robert Westervelt THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE
IDC MarketScape IDC MarketScape: Worldwide Endpoint Specialized Threat Analysis and Protection 2017 Vendor Assessment Robert Westervelt THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE
GDPR: An Opportunity to Transform Your Security Operations
 GDPR: An Opportunity to Transform Your Security Operations McAfee SIEM solutions improve breach detection and response Is your security operations GDPR ready? General Data Protection Regulation (GDPR)
GDPR: An Opportunity to Transform Your Security Operations McAfee SIEM solutions improve breach detection and response Is your security operations GDPR ready? General Data Protection Regulation (GDPR)
SECURITY SERVICES SECURITY
 SECURITY SERVICES SECURITY SOLUTION SUMMARY Computacenter helps organisations safeguard data, simplify compliance and enable users with holistic security solutions With users, data and devices dispersed
SECURITY SERVICES SECURITY SOLUTION SUMMARY Computacenter helps organisations safeguard data, simplify compliance and enable users with holistic security solutions With users, data and devices dispersed
MITIGATE CYBER ATTACK RISK
 SOLUTION BRIEF MITIGATE CYBER ATTACK RISK CONNECTING SECURITY, RISK MANAGEMENT & BUSINESS TEAMS TO MINIMIZE THE WIDESPREAD IMPACT OF A CYBER ATTACK DIGITAL TRANSFORMATION CREATES NEW RISKS As organizations
SOLUTION BRIEF MITIGATE CYBER ATTACK RISK CONNECTING SECURITY, RISK MANAGEMENT & BUSINESS TEAMS TO MINIMIZE THE WIDESPREAD IMPACT OF A CYBER ATTACK DIGITAL TRANSFORMATION CREATES NEW RISKS As organizations
Six Weeks to Security Operations The AMP Story. Mike Byrne Cyber Security AMP
 Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
Choosing the Right Cloud Computing Model for Data Center Management
 Choosing the Right Cloud Computing Model for Data Center Management www.nsi1.com NETWORK SOLUTIONS INCOPORATED NS1.COM UPDATING YOUR NETWORK SOLUTION WITH CISCO DNA CENTER 1 Section One Cloud Computing
Choosing the Right Cloud Computing Model for Data Center Management www.nsi1.com NETWORK SOLUTIONS INCOPORATED NS1.COM UPDATING YOUR NETWORK SOLUTION WITH CISCO DNA CENTER 1 Section One Cloud Computing
Cloud Computing: Making the Right Choice for Your Organization
 Cloud Computing: Making the Right Choice for Your Organization A decade ago, cloud computing was on the leading edge. Now, 95 percent of businesses use cloud technology, and Gartner says that by 2020,
Cloud Computing: Making the Right Choice for Your Organization A decade ago, cloud computing was on the leading edge. Now, 95 percent of businesses use cloud technology, and Gartner says that by 2020,
Service. Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution
 Service SM Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution Product Protecting sensitive data is critical to being
Service SM Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution Product Protecting sensitive data is critical to being
Networking for a smarter data center: Getting it right
 IBM Global Technology Services October 2011 Networking for a smarter data center: Getting it right Planning the network needed for a dynamic infrastructure 2 Networking for a smarter data center: Getting
IBM Global Technology Services October 2011 Networking for a smarter data center: Getting it right Planning the network needed for a dynamic infrastructure 2 Networking for a smarter data center: Getting
Service Provider Consulting
 From Microsoft Services 1 Industry Overview More and more businesses are looking to outsource IT, decrease management requirements and ultimately save money. With worldwide public cloud spending expected
From Microsoft Services 1 Industry Overview More and more businesses are looking to outsource IT, decrease management requirements and ultimately save money. With worldwide public cloud spending expected
New Zealand Government IbM Infrastructure as a service
 New Zealand Government IbM Infrastructure as a service Global leverage / local experts World-class Scalable Agile Flexible Fast Secure What are we offering? IBM New Zealand Government Infrastructure as
New Zealand Government IbM Infrastructure as a service Global leverage / local experts World-class Scalable Agile Flexible Fast Secure What are we offering? IBM New Zealand Government Infrastructure as
SIEM Solutions from McAfee
 SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
to Enhance Your Cyber Security Needs
 Our Service to Enhance Your Cyber Security Needs Since the business critical systems by its nature are ON all of the time and the increasingly connected world makes you open your organization to everything
Our Service to Enhance Your Cyber Security Needs Since the business critical systems by its nature are ON all of the time and the increasingly connected world makes you open your organization to everything
Security-as-a-Service: The Future of Security Management
 Security-as-a-Service: The Future of Security Management EVERY SINGLE ATTACK THAT AN ORGANISATION EXPERIENCES IS EITHER ON AN ENDPOINT OR HEADING THERE 65% of CEOs say their risk management approach is
Security-as-a-Service: The Future of Security Management EVERY SINGLE ATTACK THAT AN ORGANISATION EXPERIENCES IS EITHER ON AN ENDPOINT OR HEADING THERE 65% of CEOs say their risk management approach is
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 BUYER CASE STUDY INTRUST Implements F5 Networks BIG-IP Lucinda Borovick IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com One of the more
BUYER CASE STUDY INTRUST Implements F5 Networks BIG-IP Lucinda Borovick IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com One of the more
