HP Data Protector 6.1 software VMware Integration Installation Best Practice
|
|
|
- Cynthia Cunningham
- 6 years ago
- Views:
Transcription
1 HP Data Protector 6.1 software VMware Integration Installation Best Practice Guidelines for installation of the HP Data Protector VMware Integration on ESX servers Executive summary... 3 Introduction... 3 A sample HP Data Protector Cell with VMware ESX server as Data Protector Client... 4 Different ways to install the HP Data Protector VMware Integration on an ESX Server... 5 Installation procedures flow... 6 Installation Method A Data Protector Installation Server... 7 Installation Method B Media directly attached to the ESX server B1: Using a local DVD Drive B2: Using local USB stick Installation Method C Data copied on the ESX Server C1: With the DVD C2: With the VMware Datastore Browser C3: Locally mounted ISO image C4: Packed Depot file Installation Method D Remotely attached Data Source D1: Remote DVD D2: Remote ISO-image Troubleshooting Problems Problem: push installation Push installation with the Data Protector Installation Server generates the error message Problem: error message: No medium found Problem: scp does not work or man-in-the-middle attack Problem: installation works but the import of the client failed Problem: util_vmware does not work correctly How to enable Inet debugs on ESX Useful troubleshooting commands Firewall problems Date and time Appendix A Enabling SSH-login on an ESX Server Firewall configuration DVDs and downloadable binaries Downloadable binaries For more information
2 2
3 Executive summary This white paper provides information on how to plan and install the HP Data Protector VMware Integration in different ways. Introduction HP Data Protector software is a backup and disaster recovery application that provides reliable data protection and high accessibility for your fast-growing business data. Data Protector offers comprehensive backup and restore functionality specifically tailored for enterprise-wide and distributed environments. Data Protector can be used in environments ranging from a single system to thousands of systems on several sites. Due to the network component concept of Data Protector, elements of the backup infrastructure can be placed in the topology according to user requirements. The numerous backup options and alternatives to setting up a backup infrastructure allow the implementation of virtually any configuration you want. HP Data Protector enables you to perform backup to a large number of backup devices simultaneously. It supports high-end devices in very large libraries. Various backup possibilities, such as local backup, network backup, online backup, disk image backup, synthetic backup, backup with object mirroring, and built-in support for parallel data streams allow you to tune your backups to best fit your requirements. Since HP Data Protector 6.1, a fully automated integration for backing up VMware virtual machines is available. To enable the snapshot backup feature, you need to install the VMware Integration on the ESX server. This can be done in different ways, for example, if a network is already in place or if a Data Protector UNIX Installation Server is available. This white paper discusses the different ways for installing the Data Protector package and shows the pros and cons of each method. You can choose the method which fits your requirements. At the end of this white paper, a troubleshooting chapter lists error messages and necessary steps for fixing these problems. 3
4 A sample HP Data Protector Cell with VMware ESX server as Data Protector Client Figure 1 shows a Data Protector Cell in a typical ESX environment. For simplicity, only two ESX servers are shown. For the Snapshot and Suspend backup method, install the DP VMware Integration on the ESX Server. For the VCB-Image and VCB-File backup method, install the DP VMware Integration on the VCB Proxy Server. For restoring from Snapshot/Suspend and VCB-Image backups, install the DP/VMware integration on the ESX server. For restoring from VCB-File- backups, install DP VMware integration on the destination system, which is usually the Virtual Machine from which the backup was performed. An installation on the VMware Virtual Center Server (vcenter Server) is optional. Note: It is recommended to install the DP VMware Integration on the vcenter Server. Data Protector contacts the vcenter Server to get a list of all VMs and its hosting ESX servers. This allows the use of VMotion without any impact on already scheduled backups. Figure 1: Overview Table1 shows where the integration has to be installed for the different methods. 4
5 Table 1: Installation Targets for Data Protector VMware Integration Different ways to install the HP Data Protector VMware Integration on an ESX Server Table 2 shows the advantages and disadvantages of the different installation methods. Table 2: Pros and cons of the different ways of installing the Data Protector VMware Integration 5
6 Installation procedures flow Figure 2 shows the required steps for the different installation methods: Figure 2: Required steps for the different installation methods 6
7 Installation Method A Data Protector Installation Server Prepare the ESX Server to get access 1. You can access the ESX server either through the console or through remote access tools (such as Putty or ReflectionX). These remote access tools are based on the SSH protocol. By default SSH is blocked by the ESX server. To enable the login on the ESX server with SSH, see Appendix A: Enable SSH-login on ESX Server. 2. The push-installation of the Data Protector-VMware integration requires a Data Protector UNIX Installation Server and an SSH connection between the Installation Server and the ESX server. 3. Create a public/private key pair: To create an SSH key pair on the Data Protector UNIX Installation Server, the command sshkeygen has to be processed. Do not enter a passphrase. #ssh-keygen Generating a public/private rsa key pair. Please be patient... Key generation may take a few minutes Enter file in which to save the key (//.ssh/id_rsa): Created directory '//.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in //.ssh/id_rsa. Your public key has been saved in //.ssh/id_rsa.pub. The key fingerprint is: 33:15:17:5c:c0:83:52:76:7a:3b:13:ef:57:04:c9:6c root@server Explanations: The file //.ssh/id_rsa contains the private key. The default location was chosen, so it is stored in the ssh-directory of root user (<$HOME>/.ssh). 33:15:17:5c:c0:83:52:76:7a:3b:13:ef:57:04:c9:6c is the fingerprint of the Data Protector Installation Server, server.domain.com. 4. Check the newly generated files: # cd /.ssh # ls -la -rw root sys 1679 Apr 26 14:12 id_rsa -rw-r--r-- 1 root sys 393 Apr 26 14:12 id_rsa.pub 5. To establish the SSH connection with the DP-client (ESX-server), append the public key to the file <$HOME>/.ssh/authorized_keys on the ESX server. This can be easily done as follows: Transfer the id_rsa.pub file to a temporary location on the ESX server: # scp id_rsa.pub root@esx.domain.com:.ssh/ The authenticity of host 'esx.domain.com(16.xx.yy.zz)' can't be established. RSA key fingerprint is 3d:d2:1b:5e:7e:56:7e:b3:4d:9c:74 :ff:0d:f4:64:b0. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'esx.domain.com,16.xx.yy.zz' (RSA) to the list of known hosts. root@esx.domain.com's password: id_rsa.pub 100% KB/s 0.4KB/s 00:00 Max throughput:0.4kb/s Possible WARNING: REMOTE HOST IDENTIFICATION 7
8 See Troubleshooting Man-in-the-middle attack on page 17. Error message: scp:.ssh/: Is a directory The scp command fails because there is no.ssh directory on the ESX server. Solution: On the ESX server, login with root. Create a directory: # mkdir.ssh Apply the correct setting to the.ssh directory: # chmod 600.ssh 6. Append the key manually: #cat id_rsa.pub >> authorized_keys (The file authorized_keys will be created if it is not already available.) 7. Make a simple test to check that the SSH connection is working. From the Data Protector Installation Server, ask the ESX server via the SSH connection for the date and time: # ssh esx.domain.com date Thu Apr 21 17:56:33 CET 2009 Note: The remote system must not ask for a passphrase or the Data Protector installation will fail. 8. Firewall configuration. By default, the firewall from the ESX server blocks the port To open this port, perform the following command: # esxcfg-firewall -openport 5555,tcp,in,HP-DataProtector See Appendix A: Firewall settings for additional information. 9. Set the omnirc variable OB2_SSH_ENABLED. Before the installation can start, set the omnirc variable OB2_SSH_ENABLED on the Installation Server to 1. Extract from the omnirc file: # OB2_SSH_ENABLED=1 # Default: 0 # Allows SSH protocol to be used for remote installation of DP agents. This # secures the remote connections while distributing the agents. Set this variable # on Installation Server host. This is applicable only on UNIX platforms You can find the.omnirc file on HP-UX, Linux and Solaris at: /opt/omni/.omnirc. If there is no.omnirc file, copy the file.omnirc.tmpl to.omnirc. 10.Open the Data Protector GUI: Go to the Client context and right-click Add client : 8
9 The platform of the target system is UNIX. When you have entered the name of the ESX server and selected the VMware Integration, the installation starts. After the installation the client is automatically added into the Data Protector Cell. 9
10 Installation Method B Media directly attached to the ESX server B1: Using a local DVD Drive Prepare the ESX Server to get access 1. You can access the ESX server either through the console or through remote access tools (such as Putty or ReflectionX). These remote access tools are based on the SSH protocol. By default SSH is blocked by the ESX server. To enable the login on the ESX server with SSH, see Appendix A: Enable SSH-login on ESX Server. 2. Firewall configuration. For Data Protector, the port 5555 needs to be open. By default, the firewall on the ESX server blocks the port. To open it, execute the following command: # esxcfg-firewall -openport 5555,tcp,in,HP-DataProtector See Appendix A: Firewall settings for more information. 3. Insert and mount the DVD: HP-UX B If the directory /mnt/cdrom does not exist, create it with the command: # mkdir /mnt/cdrom Then mount the drive: # mount t auto /dev/cdrom /mnt/cdrom You can identify the DVD Drive by checking the directory listing of /dev: # ls -l /dev 4. Go to the Local Install directory on the DVD drive: # cd /mnt/cdrom/local_install 5. Start the installation: # /mnt/cdrom/local_install/ommnisetup.sh install vmware 6. Check the installation: # rpm qa grep i OB2 OB2-CORE-A OB2-VMW-A Umount the cdrom: # cd / # umount /mnt/cdrom 8. Import the ESX server as client to the Cell Manager: Open the Data Protector GUI, go to the context menu, right-click on clients, select import client... Note: If the port 5555 on the firewall is already open, you can combine the import step (8) with the installation step (5). Additionally the DA and the MA are installed: # /mnt/cdrom/local_install/ommnisetup.sh server cellmanager.domain.com install da,ma,vmware where cellmanager.domain.com is the name of the Cell Manager. 10
11 B2: Using local USB stick 1. Copy the whole DVD onto an USB stick (can be done with a Windows PC). 2. Prepare the ESX Server to get access. See step1 of B1: Using a local DVD drive. 3. Firewall configuration. See step 2 of B1: Using a local DVD drive. 4. Insert the USB stick in an USB port from the ESX server and wait a couple of seconds. 5. Login on the ESX server and use the fdisk command to see the used USB-port(s). In the output below the local disk is also shown. One differentiator can be the size of the device. Here the USB stick has 16 GB and the disk 36.4 GB. In cases where many devices are listed, it may be difficult to identify the USB stick. In this case, perform the command fdisk l before inserting the USB stick and the output of the command will be redirected in a file. Insert the USB stick and perform the command again. Using a command like diff, you can identify the USB stick. # fdisk -l Disk /dev/sda: 16.0 GB, bytes 254 heads, 63 sectors/track, 1956 cylinders Units = cylinders of * 512 = bytes Device Boot Start End Blocks Id System /dev/sda c Win95 FAT32 (LBA) Disk /dev/cciss/c0d0: 36.4 GB, bytes 255 heads, 32 sectors/track, 8716 cylinders Units = cylinders of 8160 * 512 = bytes Device Boot Start End Blocks Id System /dev/cciss/c0d0p1 * Linux /dev/cciss/c0d0p Linux /dev/cciss/c0d0p fb Unknown /dev/cciss/c0d0p f Win95 Ext'd (LBA) /dev/cciss/c0d0p Linux swap /dev/cciss/c0d0p Linux /dev/cciss/c0d0p fc Unknown 6. Mount the USB device. Create a mount point if one is not already available: # mkdir /mnt/cdrom Now mount the USB stick: # mount -t auto /dev/sda1 /mnt/usb 7. Once the USB device is mounted, follow the steps 5-8 from B1: Using a local DVD drive.. 8. Unmount the USB-stick: # cd / # umount /mnt/usb 11
12 Installation Method C Data copied on the ESX Server C1: With the DVD 1. Prepare the ESX Server to get access. See step1 of B1: Using a local DVD drive. 2. Firewall configuration. See step 2 of B1: Using a local DVD drive. 3. Mount the DVD. See step 3 of B1: Using a local DVD drive. 4. Copy the HP-UX and the LOCAL INSTALL directory on the ESX server # cp -r /dvdrom/platform_dir/dp_depot directory # cp -r /dvdrom/platform_dir/local_install directory For further details see the HP Data Protector A Installation and licensing guide Local installation of UNIX clients Running the installation from the hard disk. 5. Proceed with the installation as described in steps 4-8 of B1: Using a local DVD drive. C2: With the VMware Datastore Browser With the VMware Infrastructure Client, every Datastore that belongs to the ESX server can be browsed. A feature of the Datastore Browser is that it allows exchange of data in both directions, between the system running the Infrastructure Client and the ESX server. You can use this to upload the Data Protector installation bits directly on the ESX server, without any UNIX command. To install the DP VMware integration agent, it is enough to upload the hpux_pa depot and the LOCAL_INSTALL directory. The directory where the data is stored is: /vmfs/volumes/datastore directory The procedure is identical to section C1: With the DVD, except for step 4. Note that the omnisetup.sh file may have a different location in this case, such as: </vmfs/volumes/<datastore>/local_install>. C3: Locally mounted ISO image Under ESX, an ISO-Image can be mounted like a CD-ROM. For this, you must place the ISO image on the ESX server. You can copy the ISO image with the VMware Datastore browser (see C2: Data copied on the ESX server with the VMware Datastore browser) or with FTP. To use FTP, open the firewall on the ESX server: # esxcfg-firewall -allowoutgoing then use ftp to fetch the ISO file from a remote system. Close the firewall afterwards with: # esxcfg-firewall -blockoutgoing 12
13 Or set the firewall back to default: # esxcfg-firewall r 1. Assuming that an ISO image B iso has been copied onto the ESX server in the directory /vm/iso_depot/dp_6.10, and a mount point such as /mnt/dp-iso has been created, to mount the ISO image use the command: # mount -o loop /vm/iso_depot/dp_6.10/b iso /mnt/dp-iso 2. Proceed with the installation as described in steps 5-8 of B1: Using a local DVD drive Note: See Appendix A: Firewall settings for additional information about firewall configuration. C4: Packed Depot file To reduce the total amount of data, simply extract and compress the directories hpux_pa and LOCAL_INSTALL from the DVD. 1. Extract the resulting gzipped tarfile on the ESX server with the following command: # gunzip -c DP-Depot.tar.gz tar xvf 2. Proceed with the installation as described in steps 5-8 of B1: Using a local DVD drive. Note: See Appendix A: Firewall settings for additional information about firewall configuration 13
14 Installation Method D Remotely attached Data Source D1: Remote DVD HP s ilo (integrated Lights Out) allows you to connecting a remote DVD-drive to the ESX server. The PC or laptop from which the ilo is reached needs a DVD drive, which you can use as an installation drive for the Data Protector VMware Integration. 1. Insert the DVD in the local PC drive. 2. Connect with a web browser to the ilo from the ESX server. With ilo: Under the tab Virtual devices click Virtual Media and select the local DVD drive. With ilo2 you can mount a DVD directly using the Integrated Remote Console. The following screen shows the top right corner of the Console window. Click on the drive symbol to open the selection menu. 3. On the console, check for drives under /mnt: # ll /mnt 4. Mount the DVD: # mount /dev/cdrom /mnt/cdrom1 5. Go to the LOCAL_INSTALL directory: # cd /mnt/cdrom1/local_install 6. Start the installation: # /mnt/cdrom1/local_install/omnisetup.sh install vmware 14
15 7. Unmount the DVD: # cd / # umount /mnt/cdrom1 8. Check the installation. See step 6 of B1: Using a local DVD drive. 9. Firewall configuration. See step 2 of B1: Using a local DVD drive. 10.Import the ESX server as client to the Cell Manager. See step 8 of B1: Using a local DVD drive. D2: Remote ISO-image HP s ilo and ilo2 not only allow you to connect a DVD drive from the local PC, you can also mount a directory that holds an ISO image. This directory need not be a directory on the PC, it could be a mapped network drive. This means the installation runs directly from a foreign ISOstore onto the ESX server. There is no need to copy any data first. Note that the network can slow down the installation process. The procedure is similar to D1: Remote DVD, but instead of a local Media Drive, select a local ISO image file. There are two possible sources: an ISO image created from the DVD B , and the ISO image B iso which you can download from the web. See Appendix A: DVDs and downloadable bits. With ilo: Click Connect. If the connection works properly, the drive logo becomes green. The mount and installations steps are similar to D1: LOCAL DVD With ilo2 using the Integrated Remote Console you can mount an ISO image directly from a directory. The following screen shows the top right corner of the Console window. Click on the drive symbol to open the selection menu. For example, click Mount next to a folder symbol to browse the local system and select an ISO image. 15
16 16
17 Troubleshooting This section covers the following: Problems, see page 17 How to enable Inet debugs on ESX, see page 18 Useful troubleshooting commands, see page 19 Problems Problem: push installation Push installation with the Data Protector Installation Server generates the error message: [Critical] <esx.domain.com> [110:24] Client esx.domain.com : client not responding. [Critical] <esx.domain.com> Error connecting to client esx.domain.com Skipping client! Possible reason The omnirc variable OB2_SSH_ENABLED is not set to 1. Problem: error message: No medium found During local installation, using a local DVD drive, the following error message occurs during the mount step of the DVD: Mount: block device /dev/cdrom is write-protected, mounting read-only Mount: No medium found Action To check for a DVD drive: # dmesg grep i dvd cdrom_read_toc: Model string: HL-DT-STCD-RW/DVD DRIVE GCC-C10N To check for a CD drive: # dmesg grep i cd hda: CRN-8245B, ATAPI CD/DVD-ROM drive hda: attached ide-cdrom driver hda: ATAPI 24X CD-ROM drive, 128kB Cache Uniform CD-ROM driver Revision: 3.12 The message text shows that this is not a DVD-drive. Possible solutions Exchange the CD drive with a DVD-drive. Use a USB stick instead of a DVD. If ILO is available, mount the DVD remotely. Install remotely with the Data Protector Installation Server. Problem: scp does not work or man-in-the-middle attack Action If an ESX server has been reinstalled, the system will have a new fingerprint. The scp command checks the fingerprints that are stored in the file /.ssh/known_hosts on the Installation Server. To delete the old entry, search for the host name and IP address in the known_host file. If the content is encrypted check the line given in the message below. Offending key in /.ssh/known_hosts:3 # scp id_rsa.pub root@esx.domain.com:.ssh/ 17
18 @ WARNING: REMOTE HOST IDENTIFICATION IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that the RSA host key has just been changed. The fingerprint for the RSA key sent by the remote host is d0:3f:56:3f:9e:92:8c:20:fa:b9:02:ce:75:b9:bf:b6. Please contact your system administrator. Add correct host key in /.ssh/known_hosts to get rid of this message. Offending key in /.ssh/known_hosts:3 RSA host key for esx.domain.com has changed and you have requested strict checking. Host key verification failed. lost connection It may be that there are two entries for one host in the known_hosts file, one with an IP address and one with the host name. Problem: installation works but the import of the client failed Possible reason The firewall blocks the 5555 port. Action You can open the port with the following command executed on the ESX Server: # esxcfg-firewall --openport 5555,tcp,in,HP-DataProtector Problem: util_vmware does not work correctly Error message: *RETVAL1602 [111] Connection refused This error message occurs because the Cell Manager could not be reached. Action Check the firewall setting on the ESX server and the Cell Manager. How to enable Inet debugs on ESX 1. On the ESX host go to /etc/xinetd.d: # cd /etc/xinetd.d 2. Edit the file omni: server_args = inet -log /usr/omni/log/inet.log -debug inet.txt 3. Reload the services: # /etc/init.d/xinetd reload 4. Restart the services : # /etc/init.d/xinetd restart 18
19 Useful troubleshooting commands Firewall problems To isolate network problems, it could be helpful to switch off the whole firewall on the ESX server: # esxcfg-firewall --AllowOutgoing # esxcfg-firewall --AllowIncoming After the tests, switch the firewall back on: # esxcfg-firewall --BlockOutgoing # esxcfg-firewall - BlockIncoming To check the ports: # esxcfg-firewall q Date and time Date and time should be synchronized on all systems. The time on the ESX server can be quickly adjusted with the date command: # date Tue Apr 21 11:16:51 CEST 2009 Use the same format to change the date: # date --set="wed Apr 22 11:18:00" Wed Apr 22 11:18:00 CEST 2009 To enable the ntp service, go to: 19
20 Appendix A This section covers the following: Enabling SSH-login on an ESX Server, see below Firewall configuration, see page 20 DVDs and downloadable binaries, see page 22 For more information, see page 23 Enabling SSH-login on an ESX Server 1. Login via the console. To enable SSH login access, use the console. For example, with the help of the ilo Remote Console (part of the HP server): The password that you need to enter here was provided during the ESX installation. 2. Enable root login. In the file: /etc/ssh/sshd_config, set the parameter PermitRootLogin to yes. Note: Do not confuse this with the ssh_config file in the same directory. 3. Restart the SSH-daemon. To make the changes active, restart the ssh-deamon: # /etc/init.d/sshd restart or # service sshd restart Note: If you want to disable root login for SSH, change the file sshd_config back and restart the SSH daemon. However, this will block patching the ESX Server by a Data Protector Installation Server. Firewall configuration Data Protector uses by default only two dedicated ports: 5555 (Inet) and 5556 (Java GUI). All other ports used by Data Protector are dynamically allocated in the range of 1024 to In cases where firewalls become important, this range can be restricted to a smaller number of usable ports. The esxcfg-firewall command and two omnirc variables can be used to define a narrower range of ports. It is possible to use the esxccfg-firewall command manually to open ports for an application. However, especially if many ESX servers have to be installed, it is preferable to create an xml file in the directory /etc/vmware/firewall that opens one or more ports or port ranges. 20
21 The following is an example configuration of an ESX server and a Cell Manager with open ports 5555 and Create a file, such as DataProtector-ports, and insert: <ConfigRoot> <service> <id>hp DataProtector</id> <rule id='0000'> <direction>inbound</direction> <protocol>tcp</protocol> <port type='dst'>5555</port> <flags>-m state --state NEW</flags> </rule> <rule id='0001'> <direction>outbound</direction> <protocol>tcp</protocol> <port type='dst'>5555</port> <flags>-m state --state NEW</flags> </rule> <rule id='0002'> <direction>inbound</direction> <protocol>tcp</protocol> <port type='dst'> <begin>42000</begin> <end>42100</end> </port> <flags>-m state --state NEW</flags> </rule> <rule id='0003'> <direction>outbound</direction> <protocol>tcp</protocol> <port type='dst'> <begin>42000</begin> <end>42100</end> </port> <flags>-m state --state NEW</flags> </rule> </service> </ConfigRoot> With the command # esxcfg-firewall e HP DataProtector the file DataProtector-ports.xml is read and ESX opens the ports. HP DataProtector is the name given in line #3 as the service ID. Show the configuration of the firewall: # esxcfg-firewall q Check the configured ports for Data Protector on the VirtualInfrastructure Client: Now configure Data Protector: 21
22 1. On the ESX server, set the omnirc variable OB2PORTRANGE: OB2PORTRANGE= Make the same changes on the Cell Manager 3. Restart the services on the Cell Manager with omnisv stop and omnisv start. This completes the configuration. You can check the configuration of the ESX server and the ports directly from the command line on the ESX server. Foe example, to configure the ESX server in Data Protector with standard security: #/opt/omni/lbin/util_vmware.exe config security 0 user root password secret port 443 \ webroot /sdk If the command runs successfully, a file is created on the Cell Manager under <Data_Protector_home>\config\server\Integ\Config\VMware\hostname%_OB2GLOBAL which contains the configuration and the encrypted login credential. Note: The range of with100 ports in the example above is quite large. This can be reduced to a smaller number. It is also not necessarily to start at 42000; it can be anywhere in the range 1024 to As well as the OB2PORTRANGE variable, there is OB2PORTRANGSPEC, which can be used to define dedicated port ranges for dedicated Data Protector agents. For more information, see: For installation of the VMware: HP Data Protector Integration guide for VMware Virtual Infrastructure, Sybase, Network Node Manager, and Network Data Management Protocol Server For configuring omnirc variables: HP Data Protector online Help For open ports and port ranges on Data Protector: search the Data Protector online Help index How to Limit a Port Range and About Firewall Support For open port on ESX servers: ontext=server_config&file=sc_security_servcon.17.6.html DVDs and downloadable binaries DVD-set (contains 3 DVDs), product number: B6960MA Windows B HP-UX B Solaris & Linux B Downloadable binaries Evaluations & Demos Evaluation Software HP Data Protector v6.1 Overview: DVD, HP DP 6.1 for Windows B tar.gz MB CD, HP DP 6.1 Media Operations B iso MB ESD, HP DP 6.1 for HP-UX-PA B tar.gz MB ESD, HP DP 6.1 for HP-UX-IA B tar.gz MB ESD, HP DP 6.1 for Linux B tar.gz MB ESD, HP DP 6.1 for Solaris B tar.gz MB 22
23 23 For more information On Data Protector: On installation: see the Data Protector online Help index: setting up openssh or see the HP Data Protector Installation and licensing guide, Setting up OpenSSH On SSH: see the official web page available in multiple languages en, de, fr, ja, nl
FEPS. SSH Access with Two-Factor Authentication. RSA Key-pairs
 FEPS SSH Access with Two-Factor Authentication RSA Key-pairs access.eps.surrey.ac.uk Contents: Introduction - 3 RSA Key-pairs - 3 Where can I use my RSA Key-Pair? - 3 Step 1 Prepare to generate your RSA
FEPS SSH Access with Two-Factor Authentication RSA Key-pairs access.eps.surrey.ac.uk Contents: Introduction - 3 RSA Key-pairs - 3 Where can I use my RSA Key-Pair? - 3 Step 1 Prepare to generate your RSA
ssh and handson Matsuzaki maz Yoshinobu 1
 ssh and handson Matsuzaki maz Yoshinobu maz@iij.ad.jp 1 Secure Shell (ssh) Replacement for unsecure tools/protocols rsh and telnet Usually listen on tcp/22 Whole communication is encrypted
ssh and handson Matsuzaki maz Yoshinobu maz@iij.ad.jp 1 Secure Shell (ssh) Replacement for unsecure tools/protocols rsh and telnet Usually listen on tcp/22 Whole communication is encrypted
Linux Network Administration
 Secure Remote Connections with OpenSSH Objective At the conclusion of this module, the student will be able to: Configure the ssh daemon start, stop, and restart sshd 17 January 2005 NETW 111 - SSH 2 SSH
Secure Remote Connections with OpenSSH Objective At the conclusion of this module, the student will be able to: Configure the ssh daemon start, stop, and restart sshd 17 January 2005 NETW 111 - SSH 2 SSH
Secure SHell Explained!
 Open Gurus How To Secure SHell Explained! Here re some insights into SSH (Secure Shell), an essential tool for accessing remote machines. S SH is used to access or log in to a remote machine on the network,
Open Gurus How To Secure SHell Explained! Here re some insights into SSH (Secure Shell), an essential tool for accessing remote machines. S SH is used to access or log in to a remote machine on the network,
Upgrading Prime Optical
 CHAPTER 6 You cannot perform a full upgrade from an earlier Cisco Transport Manager (CTM) or Prime Optical release. This section describes how to use the Cisco Prime Optical 9.8 Data Migrator wizard to
CHAPTER 6 You cannot perform a full upgrade from an earlier Cisco Transport Manager (CTM) or Prime Optical release. This section describes how to use the Cisco Prime Optical 9.8 Data Migrator wizard to
Cryptography Application : SSH. Cyber Security & Network Security March, 2017 Dhaka, Bangladesh
 Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
This is a guide about using Putty on Windows with OpenSSH on Linux. You would learn about how to:
 1 of 7 5/16/2011 5:37 PM Submitted by: Man-wai CHANG Update by: Man-wai CHANG Date Submitted: 31 May 2006 Document Version: 1.0 Last Updated: 08/01/2010 13:48:54 Last Updated: 02/02/2008 23:46:43 This
1 of 7 5/16/2011 5:37 PM Submitted by: Man-wai CHANG Update by: Man-wai CHANG Date Submitted: 31 May 2006 Document Version: 1.0 Last Updated: 08/01/2010 13:48:54 Last Updated: 02/02/2008 23:46:43 This
Technical Whitepaper. NetBackup PureDisk Technical Product Management. PureDisk Remote Office Protection. Export to NetBackup Feature
 Technical Whitepaper NetBackup PureDisk Technical Product Management PureDisk Remote Office Protection Export to NetBackup Feature 09 May 2007 Document Information Copyright The copyright to this document
Technical Whitepaper NetBackup PureDisk Technical Product Management PureDisk Remote Office Protection Export to NetBackup Feature 09 May 2007 Document Information Copyright The copyright to this document
Installing and Upgrading Cisco Network Registrar Virtual Appliance
 CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
HP Data Protector A Support for Windows Vista and Windows Server 2008 Clients Whitepaper
 HP Data Protector A.06.00 Support for Windows Vista and Windows Server 2008 Clients Whitepaper 1 Index Introduction... 3 Data Protector A.06.00 Installation on Windows Vista and Windows Server 2008 systems...
HP Data Protector A.06.00 Support for Windows Vista and Windows Server 2008 Clients Whitepaper 1 Index Introduction... 3 Data Protector A.06.00 Installation on Windows Vista and Windows Server 2008 systems...
Ubuntu Manually Mount Cdrom Drive Command Line Vmware
 Ubuntu Manually Mount Cdrom Drive Command Line Vmware On Windows 7 (64-bit) I installed VMware Player and then Ubuntu 12.04, then Mount the virtual CD drive, Launch a terminal, Use tar to uncompress. I
Ubuntu Manually Mount Cdrom Drive Command Line Vmware On Windows 7 (64-bit) I installed VMware Player and then Ubuntu 12.04, then Mount the virtual CD drive, Launch a terminal, Use tar to uncompress. I
How to Enable SFTP on MPE
 How to Enable SFTP on MPE an Allegro Consultants Whitepaper some acknowledgements and a list of prerequisites. That we can run SFTP on MPE is due to the outstanding efforts of folks like Mark Klein, Mark
How to Enable SFTP on MPE an Allegro Consultants Whitepaper some acknowledgements and a list of prerequisites. That we can run SFTP on MPE is due to the outstanding efforts of folks like Mark Klein, Mark
Project #6: Using ssh, scp and sftp with Key-Based Authentication
 Project #6: Using ssh, scp and sftp with Key-Based Authentication ssh, scp and sftp Going beyond Password Protection Creating Keys Creating Keys with a Passphrase Using Key-Based Authentication in Our
Project #6: Using ssh, scp and sftp with Key-Based Authentication ssh, scp and sftp Going beyond Password Protection Creating Keys Creating Keys with a Passphrase Using Key-Based Authentication in Our
An Overview of SSH. Presentation to Linux Users of Victoria. Melbourne, August 26, 2017
 An Overview of SSH Presentation to Linux Users of Victoria Melbourne, August 26, 2017 http://levlafayette.com Utilisation and Rationale The most common use of SSH (secure shell) is remote login access
An Overview of SSH Presentation to Linux Users of Victoria Melbourne, August 26, 2017 http://levlafayette.com Utilisation and Rationale The most common use of SSH (secure shell) is remote login access
SSH. What is Safely 6/19/ June 2018 PacNOG 22, Honiara, Solomon Islands Supported by:
 SSH 25-29 June 2018 PacNOG 22, Honiara, Solomon Islands Supported by: Issue Date: Revision: 1 What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows
SSH 25-29 June 2018 PacNOG 22, Honiara, Solomon Islands Supported by: Issue Date: Revision: 1 What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows
This is Worksheet and Assignment 12. Disks, Partitions, and File Systems
 This is Worksheet and Assignment 12 This is a combined Worksheet and Assignment.. Quizzes and tests may refer to work done in this Worksheet and Assignment; save your answers. You will use a checking program
This is Worksheet and Assignment 12 This is a combined Worksheet and Assignment.. Quizzes and tests may refer to work done in this Worksheet and Assignment; save your answers. You will use a checking program
CST8207: GNU/Linux Operating Systems I Lab Nine Disks, Partitions, and File Systems Part 2. Disks, Partitions, and File Systems - Part 2 of 2
 Student Name: Lab Section: Disks, Partitions, and File Systems - Part 2 of 2 1 Due Date - Upload to Blackboard by 8:30am Monday April 9, 2012 Submit the completed lab to Blackboard following the Rules
Student Name: Lab Section: Disks, Partitions, and File Systems - Part 2 of 2 1 Due Date - Upload to Blackboard by 8:30am Monday April 9, 2012 Submit the completed lab to Blackboard following the Rules
Siemens PLM Software. HEEDS MDO Setting up a Windows-to- Windows Compute Resource.
 Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Windows Compute Resource www.redcedartech.com. Setting up a Windows-to-Windows Compute Resource Contents Introduction 1 On Remote Machine
Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Windows Compute Resource www.redcedartech.com. Setting up a Windows-to-Windows Compute Resource Contents Introduction 1 On Remote Machine
Cryptography Application : SSH. 7 Sept 2017, Taichung, Taiwan
 Cryptography Application : SSH 7 Sept 2017, Taichung, Taiwan What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows Who I Am The Traffic is Encrypted
Cryptography Application : SSH 7 Sept 2017, Taichung, Taiwan What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows Who I Am The Traffic is Encrypted
Guideline for the installation of C-MOR Video Surveillance Virtual Machine on VMware ESX Server
 This guideline illustrates the installation of the C-MOR Video Surveillance Virtual Machine on VMware ESX Server. This manual applies to C-MOR version 4 with 64 bit operating system. First download the
This guideline illustrates the installation of the C-MOR Video Surveillance Virtual Machine on VMware ESX Server. This manual applies to C-MOR version 4 with 64 bit operating system. First download the
Setting up a Chaincoin Masternode
 Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
NexentaStor VVOL
 NexentaStor 5.1.1 VVOL Admin Guide Date: January, 2018 Software Version: NexentaStor 5.1.1 VVOL Part Number: 3000-VVOL-5.1.1-000065-A Table of Contents Preface... 3 Intended Audience 3 References 3 Document
NexentaStor 5.1.1 VVOL Admin Guide Date: January, 2018 Software Version: NexentaStor 5.1.1 VVOL Part Number: 3000-VVOL-5.1.1-000065-A Table of Contents Preface... 3 Intended Audience 3 References 3 Document
Lab E2: bypassing authentication and resetting passwords
 Lab E2: bypassing authentication and resetting passwords TTM4175 September 7, 2015 The purpose of this lab is to learn about techniques for bypassing the authentication and access control of Windows and
Lab E2: bypassing authentication and resetting passwords TTM4175 September 7, 2015 The purpose of this lab is to learn about techniques for bypassing the authentication and access control of Windows and
Using Symantec NetBackup 6.5 with Symantec Security Information Manager 4.7
 Using Symantec NetBackup 6.5 with Symantec Security Information Manager 4.7 Using Symantec NetBackup with Symantec Security Information Manager Legal Notice Copyright 2010 Symantec Corporation. All rights
Using Symantec NetBackup 6.5 with Symantec Security Information Manager 4.7 Using Symantec NetBackup with Symantec Security Information Manager Legal Notice Copyright 2010 Symantec Corporation. All rights
SSH SECURITY. If you ve never used SSH before on a computer, the chances are very high that
 SSH SECURITY If you ve never used SSH before on a computer, the chances are very high that when you tried to play along with the previous section you encountered a strange notification that may have looked
SSH SECURITY If you ve never used SSH before on a computer, the chances are very high that when you tried to play along with the previous section you encountered a strange notification that may have looked
Adobe Marketing Cloud Using FTP and sftp with the Adobe Marketing Cloud
 Adobe Marketing Using FTP and sftp with the Adobe Marketing Contents Using FTP and sftp with the Adobe Marketing...3 Setting Up FTP Accounts Hosted by Adobe...3 Classifications...3 Data Sources...4 Data
Adobe Marketing Using FTP and sftp with the Adobe Marketing Contents Using FTP and sftp with the Adobe Marketing...3 Setting Up FTP Accounts Hosted by Adobe...3 Classifications...3 Data Sources...4 Data
OpenNebula 4.6 Quickstart CentOS 6 and ESX 5.x
 OpenNebula 4.6 Quickstart CentOS 6 and ESX 5.x Release 4.6 OpenNebula Project June 12, 2014 CONTENTS 1 Package Layout 3 2 Step 1. Infrastructure Set-up 5 3 Step 2. OpenNebula Front-end Set-up 7 4 Step
OpenNebula 4.6 Quickstart CentOS 6 and ESX 5.x Release 4.6 OpenNebula Project June 12, 2014 CONTENTS 1 Package Layout 3 2 Step 1. Infrastructure Set-up 5 3 Step 2. OpenNebula Front-end Set-up 7 4 Step
Siemens PLM Software. HEEDS MDO Setting up a Windows-to- Linux Compute Resource.
 Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Linux Compute Resource www.redcedartech.com. Contents Introduction 1 On Remote Machine B 2 Installing the SSH Server 2 Configuring the SSH
Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Linux Compute Resource www.redcedartech.com. Contents Introduction 1 On Remote Machine B 2 Installing the SSH Server 2 Configuring the SSH
Backup App V7. Quick Start Guide for Windows
 Backup App V7 Quick Start Guide for Windows Revision History Date Descriptions Type of modification 30 Jun 2016 First Draft New 25 Nov 2016 Added Restore Options to Ch 8 Restoring Data; Combined Technical
Backup App V7 Quick Start Guide for Windows Revision History Date Descriptions Type of modification 30 Jun 2016 First Draft New 25 Nov 2016 Added Restore Options to Ch 8 Restoring Data; Combined Technical
How to Use This Lab Manual
 3 Contents How to Use This Lab Manual........................................ 5 Lab 1: Setting Up the Student System.................................. 7 Lab 2: Installing Fedora............................................
3 Contents How to Use This Lab Manual........................................ 5 Lab 1: Setting Up the Student System.................................. 7 Lab 2: Installing Fedora............................................
OpenNebula 4.4 Quickstart CentOS 6 and ESX 5.x. OpenNebula Project
 OpenNebula 4.4 Quickstart CentOS 6 and ESX 5.x OpenNebula Project December 17, 2013 Copyright 2013 OpenNebula Project, C12G Labs. All rights reserved. Although the information in this document has been
OpenNebula 4.4 Quickstart CentOS 6 and ESX 5.x OpenNebula Project December 17, 2013 Copyright 2013 OpenNebula Project, C12G Labs. All rights reserved. Although the information in this document has been
Installing Prime Optical
 5 CHAPTER This section describes how to install Cisco Prime Optical 9.8 with an Oracle 11g database. To ensure a successful installation, use the checklist provided in the Installation Scenarios and Checklists,
5 CHAPTER This section describes how to install Cisco Prime Optical 9.8 with an Oracle 11g database. To ensure a successful installation, use the checklist provided in the Installation Scenarios and Checklists,
Security with SSH. Network Startup Resource Center
 Security with SSH Network Startup Resource Center http://www.nsrc.org/ These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
Security with SSH Network Startup Resource Center http://www.nsrc.org/ These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
Linux Administration
 Linux Administration This course will cover all aspects of Linux Certification. At the end of the course delegates will have the skills required to administer a Linux System. It is designed for professionals
Linux Administration This course will cover all aspects of Linux Certification. At the end of the course delegates will have the skills required to administer a Linux System. It is designed for professionals
Reset the Admin Password with the ExtraHop Rescue CD
 Reset the Admin Password with the ExtraHop Rescue CD Published: 2018-01-19 This guide explains how to reset the administration password on physical and virtual ExtraHop appliances with the ExtraHop Rescue
Reset the Admin Password with the ExtraHop Rescue CD Published: 2018-01-19 This guide explains how to reset the administration password on physical and virtual ExtraHop appliances with the ExtraHop Rescue
Installation of Cisco Business Edition 6000H/M
 Installation Overview, page 1 Installation Task Flow of Cisco Business Edition 6000H/M, page 2 Installation Overview This chapter describes the tasks that you must perform to install software on your Business
Installation Overview, page 1 Installation Task Flow of Cisco Business Edition 6000H/M, page 2 Installation Overview This chapter describes the tasks that you must perform to install software on your Business
SmartCash SmartNode Setup Guide v1.2. Windows 10. Date: 13/01/2018. By (Jazz) yoyomonkey
 SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
How to install the software of ZNS8022
 How to install the software of ZNS8022 1. Please connect ZNS8022 to your PC after finished assembly. 2. Insert Installation CD to your CD-ROM drive and initiate the auto-run program. The wizard will run
How to install the software of ZNS8022 1. Please connect ZNS8022 to your PC after finished assembly. 2. Insert Installation CD to your CD-ROM drive and initiate the auto-run program. The wizard will run
SmartCash SmartNode Setup Guide V1.2 Windows 10 13/01/2018 By (Jazz) yoyomonkey Page 1
 SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
Installing on a Virtual Machine
 Release 8.5 Revised: 6/20/13 See the Quick Start for Installing and Configuring Cisco Unified MeetingPlace Release 8.5 module for information about the order in which to install and configure the Cisco
Release 8.5 Revised: 6/20/13 See the Quick Start for Installing and Configuring Cisco Unified MeetingPlace Release 8.5 module for information about the order in which to install and configure the Cisco
Configuring SSH Public Key Authentication
 6AOSCG0060-29A January 2014 Configuration Guide Configuring SSH Public Key Authentication This guide describes how to configure and use Secure Shell (SSH) public key authentication on products running
6AOSCG0060-29A January 2014 Configuration Guide Configuring SSH Public Key Authentication This guide describes how to configure and use Secure Shell (SSH) public key authentication on products running
Install ISE on a VMware Virtual Machine
 ISE Features Not Supported in a Virtual Machine, page 1 Supported VMware Versions, page 1 Support for VMware vmotion, page 2 Support for Open Virtualization Format, page 2 Virtual Machine Requirements,
ISE Features Not Supported in a Virtual Machine, page 1 Supported VMware Versions, page 1 Support for VMware vmotion, page 2 Support for Open Virtualization Format, page 2 Virtual Machine Requirements,
Upgrading Software and Firmware
 APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
Backup and Restore Technical Note
 Technical Note VERSION: 1.0 UPDATED: July 2017 Copyright Notices Copyright 2002-2017 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks
Technical Note VERSION: 1.0 UPDATED: July 2017 Copyright Notices Copyright 2002-2017 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks
SmartCash SmartNode SCRIPT Setup Guide v2.2. Windows 10. Date: 20/02/2018. By (Jazz) yoyomonkey
 SmartCash SmartNode SCRIPT Setup Guide v2.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at
SmartCash SmartNode SCRIPT Setup Guide v2.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at
Install ISE on a VMware Virtual Machine
 Supported VMware Versions, page 1 Support for VMware vmotion, page 1 Support for Open Virtualization Format, page 2 Virtual Machine Requirements, page 3 Virtual Machine Resource and Performance Checks,
Supported VMware Versions, page 1 Support for VMware vmotion, page 1 Support for Open Virtualization Format, page 2 Virtual Machine Requirements, page 3 Virtual Machine Resource and Performance Checks,
SSH and keys. Network Startup Resource Center
 SSH and keys Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
SSH and keys Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
RG-MACC_2.0 Installation Manual
 RG-MACC_2.0 Installation Manual Ruijie Networks Co., Ltd all rights reserved 1 Copyright Clarify Copyright ownership belongs to Ruijie, shall not be reproduced, copied, or used in other ways without permission.
RG-MACC_2.0 Installation Manual Ruijie Networks Co., Ltd all rights reserved 1 Copyright Clarify Copyright ownership belongs to Ruijie, shall not be reproduced, copied, or used in other ways without permission.
Virtual Data Center (vdc) Manual
 Virtual Data Center (vdc) Manual English Version 1.0 Page 1 of 43 Content 1 HOW TO USE CLOUD PORTAL (VMWARE VIRTUAL DATA CENTER)... 3 2 VMWARE SYSTEM DETAILS... 5 3 HOW TO MANAGE VIRTUAL MACHINE... 6 Edit
Virtual Data Center (vdc) Manual English Version 1.0 Page 1 of 43 Content 1 HOW TO USE CLOUD PORTAL (VMWARE VIRTUAL DATA CENTER)... 3 2 VMWARE SYSTEM DETAILS... 5 3 HOW TO MANAGE VIRTUAL MACHINE... 6 Edit
Veritas System Recovery 18 Linux Edition README
 Veritas System Recovery 18 Linux Edition README ===================================================================== ====== Veritas(TM) System Recovery 18 Linux Edition README =====================================================================
Veritas System Recovery 18 Linux Edition README ===================================================================== ====== Veritas(TM) System Recovery 18 Linux Edition README =====================================================================
The following table lists the supported upgrade paths to Cisco Finesse Release 11.5(1).
 Supported Paths, page 1 Aligned Partitions Support, page 1 Perform, page 2 Perform Rollback, page 4 Supported Paths The following table lists the supported upgrade paths to Cisco Finesse Release 11.5(1).
Supported Paths, page 1 Aligned Partitions Support, page 1 Perform, page 2 Perform Rollback, page 4 Supported Paths The following table lists the supported upgrade paths to Cisco Finesse Release 11.5(1).
Installing the Product Software
 CHAPTER 1 The Cisco Configuration Engine is a network management software that acts as a configuration service for automating the deployment, management, and upgrading of network devices and services.
CHAPTER 1 The Cisco Configuration Engine is a network management software that acts as a configuration service for automating the deployment, management, and upgrading of network devices and services.
What is Secure. Authenticated I know who I am talking to. Our communication is Encrypted
 Crypto App - SSH 1 What is Secure Authenticated I know who I am talking to Our communication is Encrypted Telnet clear text Servers Terminal clear text Routers SSH encrypted channel encrypted text Servers
Crypto App - SSH 1 What is Secure Authenticated I know who I am talking to Our communication is Encrypted Telnet clear text Servers Terminal clear text Routers SSH encrypted channel encrypted text Servers
HySecure Quick Start Guide. HySecure 5.0
 HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
Disaster Recovery Workflow
 CHAPTER 4 InMage CDP starts with the FX/VX agent, also known as "DataTap," which is used to monitor all writes to disk. A small amount of memory on the source machine is reserved by the DataTap (250MB).
CHAPTER 4 InMage CDP starts with the FX/VX agent, also known as "DataTap," which is used to monitor all writes to disk. A small amount of memory on the source machine is reserved by the DataTap (250MB).
BACKUP APP V7 MICROSOFT SYSTEM BACKUP AND RESTORE GUIDE
 V7 MICROSOFT SYSTEM BACKUP AND RESTORE GUIDE Revision History Date Descriptions Type of modification 27 July 2016 First Draft New 3 Feb 2017 Added instructions and screen shots for Encryption New key handling
V7 MICROSOFT SYSTEM BACKUP AND RESTORE GUIDE Revision History Date Descriptions Type of modification 27 July 2016 First Draft New 3 Feb 2017 Added instructions and screen shots for Encryption New key handling
SSH. Partly a tool, partly an application Features:
 Internet security SSH 1 Secure Shell: SSH Partly a tool, partly an application Features: Encrypted login and shell connections Easy, drop-in replacements for rlogin, rsh, rcp Multiple means of authentication
Internet security SSH 1 Secure Shell: SSH Partly a tool, partly an application Features: Encrypted login and shell connections Easy, drop-in replacements for rlogin, rsh, rcp Multiple means of authentication
2-1-1 ssh Secure SHell
 2-1-1 ssh Secure SHell Using Public Key Cryptography Keying, Key Exchange, and Session Setup Communicate Safely with Remote Systems What is Safely Authentication I am Assured of Which Host I am Talking
2-1-1 ssh Secure SHell Using Public Key Cryptography Keying, Key Exchange, and Session Setup Communicate Safely with Remote Systems What is Safely Authentication I am Assured of Which Host I am Talking
Release Notes. LiveVault. Contents. Version Revision 0
 Version 7.60 Release Notes Revision 0 This document describes new features for LiveVault 7.60. You can retrieve the latest available product documentation from Autonomy s Knowledge Base on the Customer
Version 7.60 Release Notes Revision 0 This document describes new features for LiveVault 7.60. You can retrieve the latest available product documentation from Autonomy s Knowledge Base on the Customer
Installing Cisco MSE in a VMware Virtual Machine
 Installing Cisco MSE in a VMware Virtual Machine This chapter describes how to install and deploy a Cisco Mobility Services Engine (MSE) virtual appliance. Cisco MSE is a prebuilt software solution that
Installing Cisco MSE in a VMware Virtual Machine This chapter describes how to install and deploy a Cisco Mobility Services Engine (MSE) virtual appliance. Cisco MSE is a prebuilt software solution that
Configuration Note. AudioCodes One Voice for Microsoft Skype for Business. CloudBond 365. Backup and Restore Functionality. Version 9.
 7 Configuration Note AudioCodes One Voice for Microsoft Skype for Business CloudBond 365 Backup and Restore Functionality Version 9.5 Update 4 Configuration Note Contents Table of Contents 1 Introduction...
7 Configuration Note AudioCodes One Voice for Microsoft Skype for Business CloudBond 365 Backup and Restore Functionality Version 9.5 Update 4 Configuration Note Contents Table of Contents 1 Introduction...
2-1-1 ssh Secure SHell
 2-1-1 ssh Secure SHell Using Public Key Cryptography Keying, Key Exchange, and Session Setup 1 Communicate Safely with Remote Systems 2 What is Safely Authentication I am Assured of Which Host I am Talking
2-1-1 ssh Secure SHell Using Public Key Cryptography Keying, Key Exchange, and Session Setup 1 Communicate Safely with Remote Systems 2 What is Safely Authentication I am Assured of Which Host I am Talking
Eaton LanSafe LanSafe installation and configuration guide for VMware ESX 3 virtual architecture
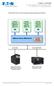 Eaton LanSafe LanSafe installation and configuration guide for VMware ESX 3 virtual architecture VMware ESX server host and guest operating systems architecture Virtual/ Guest OS 1 (Windows) Applications,
Eaton LanSafe LanSafe installation and configuration guide for VMware ESX 3 virtual architecture VMware ESX server host and guest operating systems architecture Virtual/ Guest OS 1 (Windows) Applications,
Interview Room Management System Administrator Manual
 Technical Support Interview Room Management System Administrator Manual www.casecracker.com support@casecracker.com (720) 442-7072 Table of Contents 1. System Overview 1 2. Users and Groups 1 3. Setup
Technical Support Interview Room Management System Administrator Manual www.casecracker.com support@casecracker.com (720) 442-7072 Table of Contents 1. System Overview 1 2. Users and Groups 1 3. Setup
Cryptography - SSH. Network Security Workshop May 2017 Phnom Penh, Cambodia
 Cryptography - SSH Network Security Workshop 29-31 May 2017 Phnom Penh, Cambodia What is Safely Authentication I know who I am talking with Our communication is Encrypted Telnet Servers Terminal Routers
Cryptography - SSH Network Security Workshop 29-31 May 2017 Phnom Penh, Cambodia What is Safely Authentication I know who I am talking with Our communication is Encrypted Telnet Servers Terminal Routers
Install ISE on a VMware Virtual Machine
 ISE Features Not Supported in a Virtual Machine, page 1 Supported VMware Versions, page 1 Support for VMware vmotion, page 2 Support for Open Virtualization Format, page 2 Virtual Machine Requirements,
ISE Features Not Supported in a Virtual Machine, page 1 Supported VMware Versions, page 1 Support for VMware vmotion, page 2 Support for Open Virtualization Format, page 2 Virtual Machine Requirements,
vsphere Replication for Disaster Recovery to Cloud
 vsphere Replication for Disaster Recovery to Cloud vsphere Replication 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
vsphere Replication for Disaster Recovery to Cloud vsphere Replication 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Cryptography - SSH. Network Security Workshop. 3-5 October 2017 Port Moresby, Papua New Guinea
 Cryptography - SSH Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 What is Secure Authentication I know who I am talking to Our communication is Encrypted Telnet Servers Terminal
Cryptography - SSH Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 What is Secure Authentication I know who I am talking to Our communication is Encrypted Telnet Servers Terminal
ExpressCluster X 2.0 for Linux
 ExpressCluster X 2.0 for Linux Installation and Configuration Guide 03/31/2009 3rd Edition Revision History Edition Revised Date Description First 2008/04/25 New manual Second 2008/10/15 This manual has
ExpressCluster X 2.0 for Linux Installation and Configuration Guide 03/31/2009 3rd Edition Revision History Edition Revised Date Description First 2008/04/25 New manual Second 2008/10/15 This manual has
Administration GUIDE. Virtual Server idataagent (VMware) Published On: 11/19/2013 V10 Service Pack 4A Page 1 of 225
 Administration GUIDE Virtual Server idataagent (VMware) Published On: 11/19/2013 V10 Service Pack 4A Page 1 of 225 User Guide - Virtual Server idataagent (VMware) Table of Contents System Requirements
Administration GUIDE Virtual Server idataagent (VMware) Published On: 11/19/2013 V10 Service Pack 4A Page 1 of 225 User Guide - Virtual Server idataagent (VMware) Table of Contents System Requirements
PRODUCT DOCUMENTATION. Backup & Replication v5.0. User Guide.
 PRODUCT DOCUMENTATION User Guide Backup & Replication v5.0 www.nakivo.com Table of Contents Solution Architecture... 4 Deployment...11 System Requirements... 12 Deployment Scenarios... 15 Installing NAKIVO
PRODUCT DOCUMENTATION User Guide Backup & Replication v5.0 www.nakivo.com Table of Contents Solution Architecture... 4 Deployment...11 System Requirements... 12 Deployment Scenarios... 15 Installing NAKIVO
Deploying Cisco UCS Central
 This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
V Workstation Imaging
 V Workstation Imaging The following sections provide information on Novell ZENworks Desktop Management Workstation Imaging procedures and features. Chapter 50, Common Imaging Deployment Strategies, on
V Workstation Imaging The following sections provide information on Novell ZENworks Desktop Management Workstation Imaging procedures and features. Chapter 50, Common Imaging Deployment Strategies, on
System Manager Unit (SMU) Hardware Reference
 System Manager Unit (SMU) Hardware Reference MK-92HNAS065-02 Notices and Disclaimer Copyright 2015 Hitachi Data Systems Corporation. All rights reserved. The performance data contained herein was obtained
System Manager Unit (SMU) Hardware Reference MK-92HNAS065-02 Notices and Disclaimer Copyright 2015 Hitachi Data Systems Corporation. All rights reserved. The performance data contained herein was obtained
Install ISE on a VMware Virtual Machine
 Supported VMware Versions, page 1 Support for VMware vmotion, page 1 Support for Open Virtualization Format, page 2 Virtual Machine Requirements, page 3 Virtual Machine Resource and Performance Checks,
Supported VMware Versions, page 1 Support for VMware vmotion, page 1 Support for Open Virtualization Format, page 2 Virtual Machine Requirements, page 3 Virtual Machine Resource and Performance Checks,
Managed Backup Service VMware Console Plug-In and ESX Server Agent Version Release Notes
 Managed Backup Service VMware Console Plug-In and ESX Server Agent Version 5.60.2298 Release Notes 1 1 Overview This document contains release notes for this release of the VMware Console Plug-In for the
Managed Backup Service VMware Console Plug-In and ESX Server Agent Version 5.60.2298 Release Notes 1 1 Overview This document contains release notes for this release of the VMware Console Plug-In for the
RAK831 Pilot Gateway User Manual V1.0
 RAK831 Pilot Gateway User Manual V1.0 Shenzhen Rakwireless Technology Co., Ltd www.rakwireless.com info@rakwireless.com 2018 Rakwireless all rights reserved. in this document, the actual company and product
RAK831 Pilot Gateway User Manual V1.0 Shenzhen Rakwireless Technology Co., Ltd www.rakwireless.com info@rakwireless.com 2018 Rakwireless all rights reserved. in this document, the actual company and product
Introduction to Linux Workshop 2. The George Washington University SEAS Computing Facility
 Introduction to Linux Workshop 2 The George Washington University SEAS Computing Facility Course Goals SSH and communicating with other machines Public/Private key generation,.ssh directory, and the config
Introduction to Linux Workshop 2 The George Washington University SEAS Computing Facility Course Goals SSH and communicating with other machines Public/Private key generation,.ssh directory, and the config
vsphere Replication for Disaster Recovery to Cloud vsphere Replication 6.5
 vsphere Replication for Disaster Recovery to Cloud vsphere Replication 6.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
vsphere Replication for Disaster Recovery to Cloud vsphere Replication 6.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
MarketC - Masternode Setup Guide
 MarketC - Masternode Setup Guide Preface In this guide we will be focusing on setting up a masternode for Marketc (CMK). This guide will focus on a typical "hot node" / "cold wallet" scenario. The "hot
MarketC - Masternode Setup Guide Preface In this guide we will be focusing on setting up a masternode for Marketc (CMK). This guide will focus on a typical "hot node" / "cold wallet" scenario. The "hot
Disk Imaging with Knoppix
 Introduction This document explains how to use the CD-ROM bootable version of Linux, named Knoppix, to make and restore images of computer hard drives. Knoppix makes a very good system recovery tool for
Introduction This document explains how to use the CD-ROM bootable version of Linux, named Knoppix, to make and restore images of computer hard drives. Knoppix makes a very good system recovery tool for
HP Supporting the HP ProLiant Storage Server Product Family.
 HP HP0-698 Supporting the HP ProLiant Storage Server Product Family https://killexams.com/pass4sure/exam-detail/hp0-698 QUESTION: 1 What does Volume Shadow Copy provide?. A. backup to disks B. LUN duplication
HP HP0-698 Supporting the HP ProLiant Storage Server Product Family https://killexams.com/pass4sure/exam-detail/hp0-698 QUESTION: 1 What does Volume Shadow Copy provide?. A. backup to disks B. LUN duplication
VMware vcenter/esxi Guest Virtual Machine Backup & Restore Guide. 11 September 2017
 VMware vcenter/esxi Guest Virtual Machine Backup & Restore Guide 11 September 2017 Copyright Notice The use and copying of this product is subject to a license agreement. Any other use is prohibited. No
VMware vcenter/esxi Guest Virtual Machine Backup & Restore Guide 11 September 2017 Copyright Notice The use and copying of this product is subject to a license agreement. Any other use is prohibited. No
Backup APP v7. Office 365 Exchange Online Backup & Restore Guide for Mac OS X
 Backup APP v7 Office 365 Exchange Online Backup & Restore Guide for Mac OS X Revision History Date Descriptions Type of modification 5 Apr 2017 First Draft New Table of Contents 1 Overview... 1 About This
Backup APP v7 Office 365 Exchange Online Backup & Restore Guide for Mac OS X Revision History Date Descriptions Type of modification 5 Apr 2017 First Draft New Table of Contents 1 Overview... 1 About This
Virtualization with VMware ESX and VirtualCenter SMB to Enterprise
 Virtualization with VMware ESX and VirtualCenter SMB to Enterprise This class is an intense, five-day introduction to virtualization using VMware s immensely popular Virtual Infrastructure suite including
Virtualization with VMware ESX and VirtualCenter SMB to Enterprise This class is an intense, five-day introduction to virtualization using VMware s immensely popular Virtual Infrastructure suite including
OpenManage Integration for VMware vcenter Quick Install Guide for vsphere Client, Version 2.3.1
 OpenManage Integration for VMware vcenter Quick Install Guide for vsphere Client, Version 2.3.1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use
OpenManage Integration for VMware vcenter Quick Install Guide for vsphere Client, Version 2.3.1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use
Upgrading the Server Software
 APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.5.0, page B-2 Obtaining
APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.5.0, page B-2 Obtaining
FireFox. CIS 231 Windows 10 Install Lab # 3. 1) Use either Chrome of Firefox to access the VMware vsphere web Client.
 CIS 231 Windows 10 Install Lab # 3 1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click Advanced
CIS 231 Windows 10 Install Lab # 3 1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click Advanced
IBM Spectrum Protect for Virtual Environments Version Data Protection for VMware Installation Guide IBM
 IBM Spectrum Protect for Virtual Environments Version 8.1.6 Data Protection for VMware Installation Guide IBM IBM Spectrum Protect for Virtual Environments Version 8.1.6 Data Protection for VMware Installation
IBM Spectrum Protect for Virtual Environments Version 8.1.6 Data Protection for VMware Installation Guide IBM IBM Spectrum Protect for Virtual Environments Version 8.1.6 Data Protection for VMware Installation
Install ISE on a VMware Virtual Machine
 Supported VMware Versions, page 1 Support for VMware vmotion, page 1 Support for Open Virtualization Format, page 2 Virtual Machine Requirements, page 2 Virtual Machine Resource and Performance Checks,
Supported VMware Versions, page 1 Support for VMware vmotion, page 1 Support for Open Virtualization Format, page 2 Virtual Machine Requirements, page 2 Virtual Machine Resource and Performance Checks,
Quick Start Guide TABLE OF CONTENTS COMMCELL ARCHITECTURE OVERVIEW COMMCELL SOFTWARE DEPLOYMENT INSTALL THE COMMSERVE SOFTWARE
 Page 1 of 35 Quick Start Guide TABLE OF CONTENTS This Quick Start Guide is designed to help you install and use a CommCell configuration to which you can later add other components. COMMCELL ARCHITECTURE
Page 1 of 35 Quick Start Guide TABLE OF CONTENTS This Quick Start Guide is designed to help you install and use a CommCell configuration to which you can later add other components. COMMCELL ARCHITECTURE
Virtual Infrastructure Web Access Administrator s Guide Update 2 and later for ESX Server 3.5 and VirtualCenter 2.5
 Virtual Infrastructure Web Access Administrator s Guide Update 2 and later for ESX Server 3.5 and VirtualCenter 2.5 Virtual Infrastructure Web Access Administrator s Guide Virtual Infrastructure Web Access
Virtual Infrastructure Web Access Administrator s Guide Update 2 and later for ESX Server 3.5 and VirtualCenter 2.5 Virtual Infrastructure Web Access Administrator s Guide Virtual Infrastructure Web Access
Using iscsi with BackupAssist. User Guide
 User Guide Contents 1. Introduction... 2 Documentation... 2 Terminology... 2 Advantages of iscsi... 2 Supported environments... 2 2. Overview... 3 About iscsi... 3 iscsi best practices with BackupAssist...
User Guide Contents 1. Introduction... 2 Documentation... 2 Terminology... 2 Advantages of iscsi... 2 Supported environments... 2 2. Overview... 3 About iscsi... 3 iscsi best practices with BackupAssist...
Micro Focus VisiBroker Installation Guide
 Micro Focus VisiBroker 8.5.5 Installation Guide Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright Micro Focus 2009-2018 All rights reserved. MICRO
Micro Focus VisiBroker 8.5.5 Installation Guide Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright Micro Focus 2009-2018 All rights reserved. MICRO
Hp Data Protector 7 Admin Guide File Type
 HP DATA PROTECTOR 7 ADMIN GUIDE FILE TYPE PDF - Are you looking for hp data protector 7 admin guide file type Books? Now, you will be happy that at this time hp data protector 7 admin guide file type PDF
HP DATA PROTECTOR 7 ADMIN GUIDE FILE TYPE PDF - Are you looking for hp data protector 7 admin guide file type Books? Now, you will be happy that at this time hp data protector 7 admin guide file type PDF
VMware vsphere Storage Appliance Installation and Configuration
 VMware vsphere Storage Appliance Installation and Configuration vsphere Storage Appliance 1.0 vsphere 5.0 This document supports the version of each product listed and supports all subsequent versions
VMware vsphere Storage Appliance Installation and Configuration vsphere Storage Appliance 1.0 vsphere 5.0 This document supports the version of each product listed and supports all subsequent versions
HP Data Protector 7.0 Virtualization Support Matrix
 HP Data Protector 7.0 Virtualization Support Matrix Version: 3.5 Date: September 2014 The combinations of Data Protector component + operating system and/or application versions listed in this support
HP Data Protector 7.0 Virtualization Support Matrix Version: 3.5 Date: September 2014 The combinations of Data Protector component + operating system and/or application versions listed in this support
Virtual Server Agent for VMware VMware VADP Virtualization Architecture
 Virtual Server Agent for VMware VMware VADP Virtualization Architecture Published On: 11/19/2013 V10 Service Pack 4A Page 1 of 18 VMware VADP Virtualization Architecture - Virtual Server Agent for VMware
Virtual Server Agent for VMware VMware VADP Virtualization Architecture Published On: 11/19/2013 V10 Service Pack 4A Page 1 of 18 VMware VADP Virtualization Architecture - Virtual Server Agent for VMware
WebSphere Application Server V7: Centralized Installation Manager
 Chapter 4 of WebSphere Application Server V7 Administration and Configuration Guide, SG24-7615 WebSphere Application Server V7: Centralized Installation Manager (New in V7) The Centralized Installation
Chapter 4 of WebSphere Application Server V7 Administration and Configuration Guide, SG24-7615 WebSphere Application Server V7: Centralized Installation Manager (New in V7) The Centralized Installation
VisiBroker 8.5. Installation Guide
 VisiBroker 8.5 Installation Guide Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright Micro Focus 2009-2016. All rights reserved. VisiBroker contains
VisiBroker 8.5 Installation Guide Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright Micro Focus 2009-2016. All rights reserved. VisiBroker contains
