ProxyCap Help. Table of contents. Configuring ProxyCap Proxy Labs
|
|
|
- Merryl Weaver
- 6 years ago
- Views:
Transcription
1 ProxyCap Help 2016 Proxy Labs Table of contents Configuring ProxyCap The Ruleset panel Loading and saving rulesets Delegating ruleset management The Proxies panel The proxy list view Adding, removing and modifying proxies Proxy server properties Setting the proxy type Host name and port Authentication Preferred cipher (SSH only) Host key verification (SSH only) Checking a proxy Setting the default proxy The Chains panel The chain list view Adding, removing and modifying chains Proxy chain properties Checking a chain The Rules panel The rule list view Adding, removing and modifying rules The Quick Add Rule dialog box Routing rule properties Rule Action Programs Destination Ports Destination IP Addresses Destination Hostnames Transports Prioritizing rules Disabling a rule Predefined rules The DNS panel The Miscellaneous panel Controlling product updates notifications Controlling error logging Controlling crash reporting Enabling or disabling ProxyCap Viewing status and logs The Connections screen The SSH Tunnels screen The Error Log screen Configuring ProxyCap This chapter describes all the configuration options in ProxyCap.
2 ProxyCap is configured using the ProxyCap Configuration dialog box that comes up if you right-click on the ProxyCap tray icon and choose Configuration. All settings can be changed at any time. Changes are saved and applied when you close the ProxyCap Configuration dialog box by pressing the OK button. To configure ProxyCap, you must be a member of the Administrators or ProxyCap Admins groups on the local computer. The Ruleset panel The Proxies panel The Chains panel The Rules panel The DNS panel The Miscellaneous panel The Ruleset panel The Ruleset panel allows you to perform some tasks on your proxies, routing rules and DNS settings as a whole. Loading and saving rulesets Delegating ruleset management Loading and saving rulesets You can store your proxies, routing rules and DNS settings in a single file in the PRS format. PRS is a binary file format designed to be understood by ProxyCap only. To load a ruleset from a PRS file, 1. Press the Load button. The Load Ruleset dialog box will come up. 2. Select the PRS file you want to load the ruleset from, then press the Open button. To save your ruleset to a PRS file, 1. Press the Save As button. The Save Ruleset dialog box will come up. 2. Type a file name in the File name box, then press the Save button. Delegating ruleset management The Ruleset management delegation feature allows you to delegate the task of defining and subsequently modifying your proxies, routing rules and DNS settings to your network administrators. When the delegation is turned on, ProxyCap periodically checks for an updated ruleset, and automatically performs updates. You are not allowed to change your proxies, routing rules and DNS settings, unless you turn the delegation off. ProxyCap enforces the above restriction by disabling the corresponding features. To delegate ruleset management, 1. Tick the Delegate ruleset management to a trusted provider box. 2. In the Location field, specify the URL of the PRS file. Note: HTTP and HTTPS URLs are supported. The Proxies panel The Proxies panel allows you to define your proxies. In order for ProxyCap to work, you must specify at least one working proxy. The proxy list view Adding, removing and modifying proxies Proxy server properties
3 Setting the default proxy The proxy list view The proxy list view displays your proxies in a details view. Each row represents a proxy. The Name column shows the display name of the proxy. The Type column shows the type of the proxy. The Hostname column shows the name, or the IP address, of the server the proxy is running on. The Port column shows the port number on the server to connect to. The Attribute column indicates whether the proxy is the default proxy. You can show and hide list view columns. To show or hide a column, right-click the list header, then select or unselect the name of the column you wish to show or hide. If you double-click a row, the Proxy Server Properties dialog box will come up. Adding, removing and modifying proxies To add a proxy, press the New Proxy Server come up. button on the toolbar. The New Proxy Server dialog box will To remove a proxy, select the proxy from the list, then press the Remove button on the toolbar. To change settings for a proxy, select the proxy from the list, then press the Properties toolbar. The Proxy Server Properties dialog box will come up. button on the Proxy server properties The New Proxy Server dialog box allows you to define a new proxy. The Proxy Server Properties dialog box allows you to change settings for an already defined proxy. Setting the proxy type Host name and port Authentication Preferred cipher (SSH only) Host key verification (SSH only) Setting the proxy type The Type combo box allows you to specify the type of the proxy. Selecting HTTP allows you to redirect HTTP connections made by an application through a HTTP proxy. Selecting HTTPS allows you to tunnel applications through a HTTP proxy supporting the CONNECT command, as documented in the Upgrading to TLS Within HTTP/1.1 RFC. Selecting SOCKS4 allows you to tunnel applications through a SOCKS4 proxy server. The original SOCKS4 protocol does not support proxy-side DNS. If you enable proxy-side DNS, ProxyCap will use SOCKS4A - a protocol extension to SOCKS4 which does support proxy-side DNS. NOTE: Not all SOCKS4 proxy servers provide this extension. Selecting SOCKS5 allows you to tunnel applications through a SOCKS5 proxy server. SOCKS5 is the only proxy type that allows you to proxy UDP. Selecting SSH allows you to tunnel applications through a SSH server. All traffic between your computer and the SSH server is encrypted.
4 Host name and port The Hostname box is where you type the name, or the IP address, of the server the proxy is running on. The Port box lets you specify which port number on the server to connect to. Authentication If your proxy requires authentication, you should tick the corresponding box and either provide logon credentials or use the built-in single sign-on (SSO) functionality. In the latter case, the program will try to use the currently logged on credentials to authenticate against the proxy. The authentication methods supported vary depending on the proxy type: With SOCKS5, ProxyCap supports the username/password and GSSAPI authentication methods. The GSSAPI method is implemented using SSPI Kerberos. SOCKS4 can use the Username field, but does not support passwords. With HTTP and HTTPS proxying, ProxyCap supports the Negotiate, NTLM, Digest and Basic authentication schemes. ProxyCap will try to use the most secure authentication method from the list of methods supported on the proxy server. For Negotiate and NTLM, it is assumed that the user belongs to the domain on the target system. You can explicitly specify the domain using the format domain\user. To authenticate using the logged on credentials, tick the Use integrated Windows authentication box. With SSH, ProxyCap supports the password, public key and GSSAPI ( gssapi-with-mic ) authentication methods. If you specify a password, and password authentication is disabled on the SSH server, the program may try to simulate keyboard-interactive authentication. The GSSAPI method is implemented using SSPI Kerberos. For public key authentication, you must import your private key from a key file in the OpenSSH format. Please refer to the documentation of your SSH client application on how to export your private key to the OpenSSH format. Preferred cipher (SSH only) ProxyCap supports a variety of different encryption algorithms, and, with SSH2, allows you to choose which one you prefer to use. This setting has no effect for SSH1. Note that ProxyCap uses SSH2 whenever possible. Host key verification (SSH only) Host key verification is designed to protect you against IP address spoofing. To enable host key verification, tick the Verify server's host key box, and then import the server's public host key from a key file in the OpenSSH format. Some SSH servers have more than one host key of different types and for different versions of the SSH protocol. You can use any of them with ProxyCap provided the server is configured to support the corresponding version of the SSH protocol. OpenSSH stores its public host key files at the following paths: /etc/ssh/ssh_host_rsa_key.pub (SSH2 RSA) /etc/ssh/ssh_host_dsa_key.pub (SSH2 DSA) /etc/ssh/ssh_host_key.pub (SSH1 RSA) If host key verification fails, ProxyCap will disconnect from the server and will log the error to the Session Error Log.
5 Checking a proxy or chain ProxyCap includes an integrated proxy checker that allows you to perform a number of tests on a selected proxy or proxy chain. Depending on the type of the test, you can check the following: availability of the proxy service at the given address validity of the authentication credentials reachability of the given destination host/port connect delay (how long it took to establish the connection) download speed UDP round-trip time To invoke the proxy checker, select an item from the list, then press the Check Setting the default proxy button on the toolbar. The purpose of the default proxy setting is to allow you to switch proxies with a single click of your mouse. To put it in use, whenever you add a redirect routing rule, select the (default) alias from the drop-down list of proxy servers. You cannot change the default proxy from SOCKS5 to a proxy of a different type if the UDP protocol is selected in a redirect rule. To set a proxy as the default proxy, select a proxy from the list, then press the Set as Default toolbar. button on the The Chains panel The Chains panel allows you to create proxy chains. The chain list view Adding, removing and modifying chains Proxy chain properties The chain list view The chain list view displays your proxy chains in a details view. Each row represents a proxy chain. The Name column shows the display name of the proxy chain. The Proxies column shows the proxies the chain consists of, in connection order. You can show and hide list view columns. To show or hide a column, right-click the list header, then select or unselect the name of the column you wish to show or hide. If you double-click a row, the Proxy Chain Properties dialog box will come up. Adding, removing and modifying chains To add a chain, press the New Proxy Chain come up. button on the toolbar. The New Proxy Chain dialog box will To remove a chain, select the chain from the list, then press the Remove button on the toolbar.
6 To change settings for a chain, select the chain from the list, then press the Properties toolbar. The Proxy Chain Properties dialog box will come up. button on the Proxy chain properties The New Proxy Chain dialog box allows you to define a new chain. The Proxy Chain Properties dialog box allows you to change settings for an already defined chain. A proxy chain must contain at least two proxies. The proxies must be positioned in connection order. A proxy chain cannot contain more than one HTTP proxy. A HTTP proxy must be the last in the chain. Checking a proxy or chain ProxyCap includes an integrated proxy checker that allows you to perform a number of tests on a selected proxy or proxy chain. Depending on the type of the test, you can check the following: availability of the proxy service at the given address validity of the authentication credentials reachability of the given destination host/port connect delay (how long it took to establish the connection) download speed UDP round-trip time To invoke the proxy checker, select an item from the list, then press the Check The Rules panel button on the toolbar. The Rules panel allows you to specify which applications will connect to the Internet through a proxy and under what circumstances. By default, all programs connect directly. Rules are examined in ascending order (from top to bottom). If the rule does not match, the next rule in the chain is examined; if it does match, then all following rules are ignored. The rule list view Adding, removing and modifying rules Routing rule properties Prioritizing rules Disabling a rule Predefined rules The rule list view The rule list view displays your routing rules in a details view. Each row represents a rule. The Name column shows the display name of the rule. The Programs column shows the programs to which the rule applies. The special value (all) means that the rule applies to all programs. The IP Addresses column shows the destination IP addresses to which the rule applies. The special value (all) means that the rule applies to all destination IP addresses. The Hostnames column shows the destination hostnames to which the rule applies. The special value (all) means that the rule applies to all destination hostnames. The Ports column shows the destination port numbers to which the rule applies. The special value (all) means that the rule applies to all destination port numbers.
7 The Transports column shows the TCP/IP transport protocol to which the rule applies. The special value (all) means that the rule applies both to TCP and UDP. The Action column contains the rule action and, if the rule action is Redirect through proxy, the name of the proxy. You can show and hide list view columns. To show or hide a column, right-click the list header, then select or unselect the name of the column you wish to show or hide. If you double-click a row, the Routing Rule Propeties dialog box will come up. Adding, removing and modifying rules To add a rule with minimum mouse clicks, press the Quick Add Rule Add Rule dialog box will come up. button on the toolbar. The Quick The Quick Add Rule dialog box exposes only a subset of the features available. It doesn't allow you to define proxy chains, specify multiple programs, etc. To add a rule that utilizes these advanced features, press the New Rule Wizard button on the toolbar. The New Routing Rule wizard will come up. To remove a rule, select the rule from the list, then press the Remove To modify a rule, select the rule from the list, then press the Properties Rule Properties dialog box will come up. button on the toolbar. button on the toolbar. The Routing The Quick Add Rule dialog box The Quick Add Rule dialog box allows you to add a new routing rule with minimum mouse clicks. Rule Action A routing rule can be assigned one of the following actions: Redirect through proxy means to redirect this connection through a specific proxy. You must select the proxy from the dropdown list of proxies. Instead of specifying the proxy explicitly, you can choose the special value (default). Please see Setting the default proxy for more information. If you check the Resolve names remotely checkbox, ProxyCap will force proxy-side DNS. NOTE: If you are doing DNS at the proxy side, you should make sure that your routing rules do not depend on knowing the IP address of a host. If the name is passed on to the proxy, ProxyCap will never know the IP address and cannot check it against your routing rules. The original SOCKS4 protocol does not support proxy-side DNS. If you enable proxy-side DNS, ProxyCap will use SOCKS4A - a protocol extension to SOCKS4 which does support proxy-side DNS. NOTE: Not all SOCKS4 proxy servers provide this extension. Force direct connection means to not redirect this connection through a proxy. Block means to block this connection. The icon on the right represents the selected rule action. The same icons are used in the rule list view to indicate the rule action. Program The Program section allows you to specify the program to which the rule applies. If you want the rule to apply to a specific program, choose Specify, then press the Browse button on the right of the edit box. The Select Program dialog box will come up. Select the executable of the program you want
8 the rule to apply to, then press the Open button. Transports The Transports section lets you control which TCP/IP transport protocols the rule applies to. You must enable at least one protocol. SOCKS5 is the only proxy type that allows you to proxy UDP. If the rule action is Redirect through proxy and the specified proxy is not of the type SOCKS5, the UDP checkbox is grayed out. TCP is then the only available option. Destination Port Range The Destination Port Range section lets you specify which destination ports the rule applies to. You can specify either a single port or an inclusive port range. Destination IP Range The Destination IP Range section lets you specify which destination IP range the rule applies to. Address must be a plain IP address. The mask is a plain number, specifying the number of 1 s (bits) at the left side of the network mask. Thus, a mask of 24 is equivalent to for IPv4 and FFFF:FF00:: for IPv6. When the mask is omitted, single IP assumed. Note that if you enabled proxy-side DNS, the hostname is passed on to the proxy without being resolved. As a result, ProxyCap will never know the IP address and cannot check it against your routing rules. Destination Hostname The Destination Hostname section lets you specify which destination hostname the rule applies to. A hostname must be a fully-qualified domain name. Wildcards are allowed. The asterisk character (*) substitutes for any zero or more characters, and the question mark (?) substitutes for any one character. NOTE: The Quick Add Rule dialog box exposes only a subset of the features available. It doesn't allow you to define proxy chains, specify multiple programs, etc. To add a rule that utilizes these advanced features, use the New Routing Rule wizard. Routing rule properties The New Routing Rule wizard allows you to add a new routing rule. The Routing Rule Properties dialog box allows you modify an existing routing rule. Rule Action Programs Destination Ports Destination IP Addresses Destination Hostnames Transports Rule Action A routing rule can be assigned one of the following actions: Redirect through proxy means to redirect this connection through a proxy. You can specify more than one proxy. In this case, the program will pick a proxy for each connection randomly from the list. Instead of specifying the proxy explicitly, you can choose the special value (default). Please see
9 Setting the default proxy for more information. If you check the &"temp0023.html"> the rule list view to indicate the rule action. Programs The Programs screen allows you to specify the programs to which the rule applies. To add a program, press the Add button on the toolbar. The Select Program dialog box will come up. Select the executable of the program you want to add, then press the Open button. Destination Ports The Destination Ports section lets you specify which destination ports the rule applies to. You can specify either single ports or inclusive port ranges. Destination IP Addresses The Destination IP Addresses screen lets you specify which destination IP addresses the rule applies to. You can specify either single IP addresses or inclusive IP address ranges. Note that if you enabled proxy-side DNS, the hostname is passed on to the proxy without being resolved. As a result, ProxyCap will never know the IP address and cannot check it against your routing rules. Destination Hostnames The Destination Hostnames screen lets you specify which destination hostnames the rule applies to. A hostname must be a fully-qualified domain name. Wildcards are allowed. The asterisk character (*) substitutes for any zero or more characters, and the question mark (?) substitutes for any one character. Transports The Transports screen lets you control which TCP/IP transport protocols the rule applies to. You must enable at least one protocol. SOCKS5 is the only proxy type that allows you to proxy UDP. If the rule action is Redirect through proxy and one or more of the specified proxies are not of the type SOCKS5, the UDP checkbox is grayed out. TCP is then the only available option. Prioritizing rules To raise the priority of a rule, click the rule and the up arrow To lower the priority of a rule, click the rule and the down arrow priority. button until the rule is in the correct priority. button until the rule is in the correct Disabling a rule You can disable a rule instead of removing it. To disable a rule, uncheck the check box on the left of the rule.
10 Predefined rules ProxyCap has the following predefined routing rules that are checked before user-defined rules. If a predefined rule matches, then all user-defined rules are ignored. Programs IP Addresses Hostnames Ports Transports Action (all) (all) (all) (all) Force direct connection (all) ::1 (all) (all) (all) Force direct connection The DNS panel The DNS panel allows you to specify which names must always be resolved locally. A hostname must be a fully-qualified domain name. Wildcards are allowed. The asterisk character (*) substitutes for any zero or more characters, and the question mark (?) substitutes for any one character. ProxyCap ensures that the following names and name groups are always resolved locally: Localhost The name of your computer Names defined in the system_root\system32\drivers\etc\hosts file The Miscellaneous panel The Miscellaneous panel allows you to control options that are not part of the ruleset. Controlling product updates notifications Controlling error logging Controlling crash reporting Controlling product updates notifications By default, ProxyCap is configured to automatically check for updates for itself and notify you when one is available. When prompted, just click the balloon and the ProxyCap Update wizard will come up. You will be given a brief description of the update and three options: Download, Decide later and Skip update. If you select the Download option, the new version will be downloaded and the ProxyCap installer will come up. If you do not want to be notified when an update is available, untick the Notify me when a new version of ProxyCap is available box. Controlling error logging By default, ProxyCap logs proxy connection errors to a temporary log available through the Error Log tab of the ProxyCap Status and Logs dialog box. See The Error Log screen for more information. If you do not want proxy connection errors to be saved, untick the Enable error logging box. Controlling crash reporting Software is complex and, like most complex things, is not perfect. Proxy Labs constantly strives to improve the reliability of the program. As part of that effort, Proxy Labs can gather information from your computer in the form of a report when ProxyCap experiences a serious error aka crash. The crash-reporting information enables the developers of ProxyCap to identify bugs. So, if crash reporting is turned on when a crash occurs,
11 there is a better chance that the bug that caused the crash will be fixed in the near future. Crash reports include the following information: Windows version information. Includes the operating system version. Date and time. Indicates when the error occurred. Software information. Includes the name of the process where the error occurred and the list of loaded modules (DLLs). Error information. Includes the information the system recorded about the error. Winsock configuration. Contains information about the configuration of Windows sockets when the error occurred. If you do not want crash reports to be sent to Proxy Labs, untick the Submit crash reports box. Enabling or disabling ProxyCap To disable ProxyCap, right-click on the ProxyCap tray icon and choose Disable ProxyCap. The grayed-out tray icon indicates that ProxyCap is disabled. Open connections that had been redirected through the proxies prior to ProxyCap being disabled are NOT interrupted. To enable ProxyCap back, right-click on the ProxyCap tray icon and choose Enable ProxyCap ProxyCap may disable itself if it encounters an error that prevents it from functioning properly. When you try to enable ProxyCap, it displays one of the following error messages: Error message: Not all ProxyCap components are loaded. Cause: The ProxyCap Service is not running. Solution: Start the ProxyCap Service or restart Windows. If the error persists, contact support. Error message: Your system configuration is no longer compatible with ProxyCap. Cause: The Winsock configuration was modified by a program or user in such a way that ProxyCap cannot continue to function properly. Solution: Reinstall ProxyCap. If the error persists, then there is a conflict between ProxyCap and some other program installed on your PC. If you have no idea which program it is, contact support. Viewing status and logs ProxyCap enables you to keep track of traffic and events through the ProxyCap Status and Logs dialog box that comes up if you right-click on the ProxyCap tray icon and choose Status and Logs. The Connections screen The SSH Tunnels screen The Error Log screen The amounts of tunneled traffic in each direction and the number of active proxied connections are displayed in the bottom of the dialog box. The traffic figures apply to the current Windows session. The Connections screen The Connections screen lists open connections that were redirected through the proxies. The list includes the following information about each connection: The Time column shows how long the connection is open. The Program column shows the name of the executable for the program which initiated the connection.
12 The Proxy column shows the name of the proxy. The Transport column shows the TCP/IP transport protocol. The Destination column shows the hostname (or IP address) and the port number of the destination. The Sent column shows the amount of data sent through this connection so far. The Received column shows the amount of data received through this connection so far. The Transports column shows the TCP/IP transport protocol to which the rule applies. You can show and hide list view columns. To show or hide a column, right-click the list header, then select or unselect the name of the column you wish to show or hide. The SSH Tunnels screen The SSH Tunnels screen lists established SSH tunnels. The list contains the following information about each tunnel: The Time column shows how long the tunnel is connected. The SSH Server column shows the display name of the SSH server. The Via column shows the display name(s) of the intermediate proxy server(s). The Encryption column shows the name of the encryption algorithm used to encrypt the data. The Channels column shows the number of open channels on the tunnel. Each channel corresponds to a tunneled connection. The Sent column shows the amount of data sent through this connection so far. The Received column shows the amount of data received through this connection so far. The Connection column indicates whether the tunnel connection is permanent or a disconnect was scheduled (see below). Once a tunnel is established, it stays connected even when there are no open channels on the tunnel. The Schedule disconnect command causes ProxyCap to disconnect from the SSH server after a delay. Once the command is issued, ProxyCap waits until there are no open channels on the tunnel. After that, the disconnection is delayed for additional 30 seconds. If no new channels are opened during this period, ProxyCap takes the tunnel down. If a proxied application tries to make a connection after the termination of the tunnel then a new tunnel is created. To issue the Schedule disconnect command for an SSH tunnel, right-click on the row that represents the tunnel, then choose Schedule disconnect from the context menu. You can show and hide list view columns. To show or hide a column, right-click the list header, then select or unselect the name of the column you wish to show or hide.
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
Configuring the VPN Client
 Configuring the VPN Client This chapter explains how to configure the VPN Client. To configure the VPN Client, you enter values for a set of parameters known as a connection entry. The VPN Client uses
Configuring the VPN Client This chapter explains how to configure the VPN Client. To configure the VPN Client, you enter values for a set of parameters known as a connection entry. The VPN Client uses
How to Configure the Barracuda VPN Client for Windows
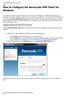 How to Configure the Barracuda VPN Client for Windows Barracuda VPN Control is the user interface of the VPN Client for Windows for configuring VPN profiles and Barracuda VPN adapter settings as well as
How to Configure the Barracuda VPN Client for Windows Barracuda VPN Control is the user interface of the VPN Client for Windows for configuring VPN profiles and Barracuda VPN adapter settings as well as
Setting Up a Cisco Unified Communications Manager SIP Trunk Integration, page 1
 Up a Cisco Unified Communications Manager SIP Trunk Integration This chapter provides instructions for setting up a Cisco Unified Communications Manager SIP trunk integration with Cisco Unity Connection.
Up a Cisco Unified Communications Manager SIP Trunk Integration This chapter provides instructions for setting up a Cisco Unified Communications Manager SIP trunk integration with Cisco Unity Connection.
Realms and Identity Policies
 The following topics describe realms and identity policies: Introduction:, page 1 Creating a Realm, page 5 Creating an Identity Policy, page 11 Creating an Identity Rule, page 15 Managing Realms, page
The following topics describe realms and identity policies: Introduction:, page 1 Creating a Realm, page 5 Creating an Identity Policy, page 11 Creating an Identity Rule, page 15 Managing Realms, page
Parallels Remote Application Server
 Parallels Remote Application Server Parallels Client for Mac User's Guide v16 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
Parallels Remote Application Server Parallels Client for Mac User's Guide v16 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
Managing External Identity Sources
 CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
Configuring Request Authentication and Authorization
 CHAPTER 15 Configuring Request Authentication and Authorization Request authentication and authorization is a means to manage employee use of the Internet and restrict access to online content. This chapter
CHAPTER 15 Configuring Request Authentication and Authorization Request authentication and authorization is a means to manage employee use of the Internet and restrict access to online content. This chapter
Installation Guide. Cimatron Site Manager 2.0 Release Note
 Installation Guide Cimatron Site Manager 2.0 Release Note Installation Guide i Table of Contents Introduction... 1 Cimatron Site Manager Components... 2 Installation... 3 Hardware Requirements... 3 Software
Installation Guide Cimatron Site Manager 2.0 Release Note Installation Guide i Table of Contents Introduction... 1 Cimatron Site Manager Components... 2 Installation... 3 Hardware Requirements... 3 Software
Intercepting Web Requests
 This chapter contains the following sections: Overview of, on page 1 Tasks for, on page 1 Best Practices for, on page 2 Web Proxy Options for, on page 3 Client Options for Redirecting Web Requests, on
This chapter contains the following sections: Overview of, on page 1 Tasks for, on page 1 Best Practices for, on page 2 Web Proxy Options for, on page 3 Client Options for Redirecting Web Requests, on
08 March 2017 NETOP HOST FOR ANDROID USER S GUIDE
 08 March 2017 NETOP HOST FOR ANDROID USER S GUIDE Contents 1 Introduction... 2 1.1 Document Scope... 2 1.2 Technical Specifications... 2 2 Using the Netop Host... 3 2.1 Netop Host Display... 3 2.2 Netop
08 March 2017 NETOP HOST FOR ANDROID USER S GUIDE Contents 1 Introduction... 2 1.1 Document Scope... 2 1.2 Technical Specifications... 2 2 Using the Netop Host... 3 2.1 Netop Host Display... 3 2.2 Netop
Link Gateway Initial Configuration Manual
 Link Gateway Initial Configuration Manual Copyright 2016 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Link Gateway Initial Configuration Manual Copyright 2016 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
User Identity Sources
 The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
BIG-IP Access Policy Manager : Portal Access. Version 12.1
 BIG-IP Access Policy Manager : Portal Access Version 12.1 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...7
BIG-IP Access Policy Manager : Portal Access Version 12.1 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...7
BIG-IP Access Policy Manager : Secure Web Gateway. Version 13.0
 BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
Sophos UTM Web Application Firewall For: Microsoft Exchange Services
 How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
Wireless-G Router User s Guide
 Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Proxifier for Mac v2. User Manual
 Proxifier for Mac v2 User Manual Introduction... 2 What s New in Version 2... 2 Proxifier Migration Notes... 7 Quick Start... 7 Proxy Server Settings... 9 Proxification Rules... 11 Profiles... 13 User
Proxifier for Mac v2 User Manual Introduction... 2 What s New in Version 2... 2 Proxifier Migration Notes... 7 Quick Start... 7 Proxy Server Settings... 9 Proxification Rules... 11 Profiles... 13 User
OPC UA Configuration Manager Help 2010 Kepware Technologies
 OPC UA Configuration Manager Help 2010 Kepware Technologies 1 OPC UA Configuration Manager Help Table of Contents 1 Getting Started... 2 Help Contents... 2 Overview... 2 Server Settings... 2 2 OPC UA Configuration...
OPC UA Configuration Manager Help 2010 Kepware Technologies 1 OPC UA Configuration Manager Help Table of Contents 1 Getting Started... 2 Help Contents... 2 Overview... 2 Server Settings... 2 2 OPC UA Configuration...
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Outlook 2010 Exchange Setup Guide
 Outlook 2010 Outlook Profile Configuration This section provides a quick overview of the settings needed to access Outlook client software and configure Outlook to connect to your hosted Exchange mailbox.
Outlook 2010 Outlook Profile Configuration This section provides a quick overview of the settings needed to access Outlook client software and configure Outlook to connect to your hosted Exchange mailbox.
OPC UA Configuration Manager PTC Inc. All Rights Reserved.
 2017 PTC Inc. All Rights Reserved. 2 Table of Contents 1 Table of Contents 2 4 Overview 4 5 Project Properties - OPC UA 5 Server Endpoints 7 Trusted Clients 9 Discovery Servers 10 Trusted Servers 11 Instance
2017 PTC Inc. All Rights Reserved. 2 Table of Contents 1 Table of Contents 2 4 Overview 4 5 Project Properties - OPC UA 5 Server Endpoints 7 Trusted Clients 9 Discovery Servers 10 Trusted Servers 11 Instance
Webthority can provide single sign-on to web applications using one of the following authentication methods:
 Webthority HOW TO Configure Web Single Sign-On Webthority can provide single sign-on to web applications using one of the following authentication methods: HTTP authentication (for example Kerberos, NTLM,
Webthority HOW TO Configure Web Single Sign-On Webthority can provide single sign-on to web applications using one of the following authentication methods: HTTP authentication (for example Kerberos, NTLM,
Parallels Remote Application Server
 Parallels Remote Application Server Parallels Client for Windows User's Guide v15.5 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
Parallels Remote Application Server Parallels Client for Windows User's Guide v15.5 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
Identity Policies. Identity Policy Overview. Establishing User Identity through Active Authentication
 You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
Using the Certificate Authority Proxy Function
 CHAPTER 10 This chapter provides information on the following topics: Certificate Authority Proxy Function Overview, page 10-1 Cisco Unified IP Phone and CAPF Interaction, page 10-2 CAPF Interaction with
CHAPTER 10 This chapter provides information on the following topics: Certificate Authority Proxy Function Overview, page 10-1 Cisco Unified IP Phone and CAPF Interaction, page 10-2 CAPF Interaction with
NetExtender for SSL-VPN
 NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
Managing Authentication and Identity Services
 You can create access policies based on user identity rather than IP addresses. To enable identity-based services, you configure policies and options to obtain user identity, and then use identity objects
You can create access policies based on user identity rather than IP addresses. To enable identity-based services, you configure policies and options to obtain user identity, and then use identity objects
Dameware ADMINISTRATOR GUIDE. Version Last Updated: October 18, 2017
 ADMINISTRATOR GUIDE Dameware Version 12.0 Last Updated: October 18, 2017 Retrieve the latest version from: https://support.solarwinds.com/success_center/dameware_remote_support_mini_remote_control 2017
ADMINISTRATOR GUIDE Dameware Version 12.0 Last Updated: October 18, 2017 Retrieve the latest version from: https://support.solarwinds.com/success_center/dameware_remote_support_mini_remote_control 2017
Cisco TelePresence Conductor with Cisco Unified Communications Manager
 Cisco TelePresence Conductor with Cisco Unified Communications Manager Deployment Guide XC2.2 Unified CM 8.6.2 and 9.x D14998.09 Revised March 2014 Contents Introduction 4 About this document 4 Further
Cisco TelePresence Conductor with Cisco Unified Communications Manager Deployment Guide XC2.2 Unified CM 8.6.2 and 9.x D14998.09 Revised March 2014 Contents Introduction 4 About this document 4 Further
LiveNX Upgrade Guide from v5.1.2 to v Windows
 LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
VI. Corente Services Client
 VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
Domain Setup Guide. NetBrain Integrated Edition 7.1. All-in-One Appliance
 NetBrain Integrated Edition 7.1 Domain Setup Guide All-in-One Appliance Version 7.1a Last Updated 2018-09-27 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Setting Up
NetBrain Integrated Edition 7.1 Domain Setup Guide All-in-One Appliance Version 7.1a Last Updated 2018-09-27 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Setting Up
The Evolved Office Assistant
 The Evolved Office Assistant USER GUIDE TM 995 Old Eagle School Road Suite 315 Wayne, PA 19087 USA 610.964.8000 www.evolveip.net Release 1.0 Document Version 1 Copyright Notice Copyright 2008 Evolve IP,
The Evolved Office Assistant USER GUIDE TM 995 Old Eagle School Road Suite 315 Wayne, PA 19087 USA 610.964.8000 www.evolveip.net Release 1.0 Document Version 1 Copyright Notice Copyright 2008 Evolve IP,
BIG-IP Access Policy Manager : Portal Access. Version 13.0
 BIG-IP Access Policy Manager : Portal Access Version 13.0 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...
BIG-IP Access Policy Manager : Portal Access Version 13.0 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...
VMware Horizon Client for Chrome Installation and Setup Guide. 15 JUNE 2018 VMware Horizon Client for Chrome 4.8
 VMware Horizon Client for Chrome Installation and Setup Guide 15 JUNE 2018 VMware Horizon Client for Chrome 4.8 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Horizon Client for Chrome Installation and Setup Guide 15 JUNE 2018 VMware Horizon Client for Chrome 4.8 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
KYOCERA Net Admin User Guide
 KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
Upgrade Instructions. NetBrain Integrated Edition 7.1. Two-Server Deployment
 NetBrain Integrated Edition 7.1 Upgrade Instructions Two-Server Deployment Version 7.1a Last Updated 2018-09-04 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Upgrading
NetBrain Integrated Edition 7.1 Upgrade Instructions Two-Server Deployment Version 7.1a Last Updated 2018-09-04 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Upgrading
Hypersocket SSO. Lee Painter HYPERSOCKET LIMITED Unit 1, Vision Business Centre, Firth Way, Nottingham, NG6 8GF, United Kingdom. Getting Started Guide
 Hypersocket SSO Getting Started Guide Lee Painter HYPERSOCKET LIMITED Unit 1, Vision Business Centre, Firth Way, Nottingham, NG6 8GF, United Kingdom Table of Contents PREFACE... 4 DOCUMENT OBJECTIVE...
Hypersocket SSO Getting Started Guide Lee Painter HYPERSOCKET LIMITED Unit 1, Vision Business Centre, Firth Way, Nottingham, NG6 8GF, United Kingdom Table of Contents PREFACE... 4 DOCUMENT OBJECTIVE...
Proxifier v3 for Microsoft Windows Standard and Portable Editions
 Proxifier v3 for Microsoft Windows Standard and Portable Editions User Manual Introduction... 2 What s New in Version 3... 2 Proxifier v2 Migration Notes... 6 Quick Start... 6 Proxy Server Settings...
Proxifier v3 for Microsoft Windows Standard and Portable Editions User Manual Introduction... 2 What s New in Version 3... 2 Proxifier v2 Migration Notes... 6 Quick Start... 6 Proxy Server Settings...
HOL122 Lab 1: Configuring Microsoft Windows Server 2003 RPC Proxy
 HOL122 Lab 1: Configuring Microsoft Windows Server 2003 RPC Proxy Objectives After completing this lab, you will be able to: Install remote procedure call (RPC) over Hypertext Transfer Protocol (HTTP)
HOL122 Lab 1: Configuring Microsoft Windows Server 2003 RPC Proxy Objectives After completing this lab, you will be able to: Install remote procedure call (RPC) over Hypertext Transfer Protocol (HTTP)
DSS User Guide. End User Guide. - i -
 DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
Workspace ONE UEM Certificate Authentication for EAS with ADCS. VMware Workspace ONE UEM 1902
 Workspace ONE UEM Certificate Authentication for EAS with ADCS VMware Workspace ONE UEM 1902 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Workspace ONE UEM Certificate Authentication for EAS with ADCS VMware Workspace ONE UEM 1902 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
ACE Live on RSP: Installation Instructions
 ACE Live on RSP ACE Live on RSP: Installation Instructions These installation instructions apply to OPNET ACE Live on RSP Release 7.1.3. You can find the latest version of this document at the OPNET Support
ACE Live on RSP ACE Live on RSP: Installation Instructions These installation instructions apply to OPNET ACE Live on RSP Release 7.1.3. You can find the latest version of this document at the OPNET Support
Link Platform Manual. Version 5.0 Release Jan 2017
 Version 5.0 Release 4.1.1 Jan 2017 Link Platform Manual Copyright 2017 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system,
Version 5.0 Release 4.1.1 Jan 2017 Link Platform Manual Copyright 2017 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system,
How to Configure a Remote Management Tunnel for an F-Series Firewall
 How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
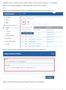 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
ForeScout Extended Module for MaaS360
 Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Proxifier v3 for Microsoft Windows Standard and Portable Editions
 Proxifier v3 for Microsoft Windows Standard and Portable Editions User Manual Introduction... 2 What s New in Version 3... 2 Proxifier v2 Migration Notes... 6 Quick Start... 6 Proxy Server Settings...
Proxifier v3 for Microsoft Windows Standard and Portable Editions User Manual Introduction... 2 What s New in Version 3... 2 Proxifier v2 Migration Notes... 6 Quick Start... 6 Proxy Server Settings...
BackupVault Desktop & Laptop Edition. USER MANUAL For Microsoft Windows
 BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
Protected EAP (PEAP) Application Note
 to users of Microsoft Windows 7: Cisco plug-in software modules such as EAP-FAST and PEAP are compatible with Windows 7. You do not need to upgrade these modules when you upgrade to Windows 7. This document
to users of Microsoft Windows 7: Cisco plug-in software modules such as EAP-FAST and PEAP are compatible with Windows 7. You do not need to upgrade these modules when you upgrade to Windows 7. This document
Copyright and Trademarks
 Copyright and Trademarks Specops Password Reset is a trademark owned by Specops Software. All other trademarks used and mentioned in this document belong to their respective owners. 2 Contents Key Components
Copyright and Trademarks Specops Password Reset is a trademark owned by Specops Software. All other trademarks used and mentioned in this document belong to their respective owners. 2 Contents Key Components
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
The following topics provide more information on user identity. Establishing User Identity Through Passive Authentication
 You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
Guide to Deploying VMware Workspace ONE. DEC 2017 VMware AirWatch 9.2 VMware Identity Manager 3.1
 Guide to Deploying VMware Workspace ONE DEC 2017 VMware AirWatch 9.2 VMware Identity Manager 3.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Guide to Deploying VMware Workspace ONE DEC 2017 VMware AirWatch 9.2 VMware Identity Manager 3.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Guide to Deploying VMware Workspace ONE. VMware Identity Manager VMware AirWatch 9.1
 Guide to Deploying VMware Workspace ONE VMware Identity Manager 2.9.1 VMware AirWatch 9.1 Guide to Deploying VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware
Guide to Deploying VMware Workspace ONE VMware Identity Manager 2.9.1 VMware AirWatch 9.1 Guide to Deploying VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware
Telephony Toolbar Enterprise. User Guide
 Telephony Toolbar Enterprise User Guide Release 4.4 October 2009 Table of Contents 1 Summary of Changes... 7 1.1 Changes for this Release... 7 2 About This Guide... 8 2.1 Open Telephony Toolbar-Corporate...
Telephony Toolbar Enterprise User Guide Release 4.4 October 2009 Table of Contents 1 Summary of Changes... 7 1.1 Changes for this Release... 7 2 About This Guide... 8 2.1 Open Telephony Toolbar-Corporate...
VMware Identity Manager Cloud Deployment. Modified on 01 OCT 2017 VMware Identity Manager
 VMware Identity Manager Cloud Deployment Modified on 01 OCT 2017 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
VMware Identity Manager Cloud Deployment Modified on 01 OCT 2017 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
CHAPTER 7 ADVANCED ADMINISTRATION PC
 ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
29 March 2017 SECURITY SERVER INSTALLATION GUIDE
 29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Pulse Secure Client for Chrome OS
 Pulse Secure Client for Chrome OS Quick Start Guide Published March, 2018 Release 5.2r1 Version 1.6 2018 by Pulse Secure, LLC. All rights reserved 1 Pulse Secure, LLC 2700 Zanker Road, Suite 200 San Jose,
Pulse Secure Client for Chrome OS Quick Start Guide Published March, 2018 Release 5.2r1 Version 1.6 2018 by Pulse Secure, LLC. All rights reserved 1 Pulse Secure, LLC 2700 Zanker Road, Suite 200 San Jose,
Cisco VXC PCoIP Configuration
 As a user or administrator you can interact with your Cisco VXC clients through the embedded HTTPS web interface (the Administrative Web Interface) and On Screen Display (OSD). Users can connect or disconnect
As a user or administrator you can interact with your Cisco VXC clients through the embedded HTTPS web interface (the Administrative Web Interface) and On Screen Display (OSD). Users can connect or disconnect
Cisco TelePresence Conductor with Cisco Unified Communications Manager
 Cisco TelePresence Conductor with Cisco Unified Communications Manager Deployment Guide TelePresence Conductor XC4.0 Unified CM 10.5(2) January 2016 Contents Introduction 6 About this document 6 Related
Cisco TelePresence Conductor with Cisco Unified Communications Manager Deployment Guide TelePresence Conductor XC4.0 Unified CM 10.5(2) January 2016 Contents Introduction 6 About this document 6 Related
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server
 Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Administrator Guide. Find out how to set up and use MyKerio to centralize and unify your Kerio software administration.
 Administrator Guide Find out how to set up and use MyKerio to centralize and unify your Kerio software administration. The information and content in this document is provided for informational purposes
Administrator Guide Find out how to set up and use MyKerio to centralize and unify your Kerio software administration. The information and content in this document is provided for informational purposes
BIG-IP Access Policy Manager : Application Access. Version 13.0
 BIG-IP Access Policy Manager : Application Access Version 13.0 Table of Contents Table of Contents Configuring App Tunnel Access... 5 What are app tunnels?...5 About ACLs to control access from app tunnels...
BIG-IP Access Policy Manager : Application Access Version 13.0 Table of Contents Table of Contents Configuring App Tunnel Access... 5 What are app tunnels?...5 About ACLs to control access from app tunnels...
Realms and Identity Policies
 The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 15 Create an Identity Rule, page 15 Manage a Realm, page 20 Manage an Identity
The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 15 Create an Identity Rule, page 15 Manage a Realm, page 20 Manage an Identity
Server Edition USER MANUAL. For Microsoft Windows
 Server Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft Windows
Server Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft Windows
Certificate authority proxy function
 Certificate authority proxy function This chapter provides information about the certificate authority proxy function. About certificate authority proxy function, page 1 Cisco Unified IP Phone and CAPF
Certificate authority proxy function This chapter provides information about the certificate authority proxy function. About certificate authority proxy function, page 1 Cisco Unified IP Phone and CAPF
Remote Access VPN. Remote Access VPN Overview. Licensing Requirements for Remote Access VPN
 Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
9.4 Authentication Server
 9 Useful Utilities 9.4 Authentication Server The Authentication Server is a password and account management system for multiple GV-VMS. Through the Authentication Server, the administrator can create the
9 Useful Utilities 9.4 Authentication Server The Authentication Server is a password and account management system for multiple GV-VMS. Through the Authentication Server, the administrator can create the
VMware AirWatch Integration with F5 Guide Enabling secure connections between mobile applications and your backend resources
 VMware AirWatch Integration with F5 Guide Enabling secure connections between mobile applications and your backend resources Workspace ONE UEM v9.6 Have documentation feedback? Submit a Documentation Feedback
VMware AirWatch Integration with F5 Guide Enabling secure connections between mobile applications and your backend resources Workspace ONE UEM v9.6 Have documentation feedback? Submit a Documentation Feedback
Accella Toolbar. User Guide. Release 20.0
 Accella Toolbar User Guide Release 20.0 Table of Contents 2 Introduction... 9 2.1 About Accella Toolbar... 9 2.2 About This Guide... 9 2.3 Accessing Toolbar... 9 2.4 First Time Login... 10 2.5 Subsequent
Accella Toolbar User Guide Release 20.0 Table of Contents 2 Introduction... 9 2.1 About Accella Toolbar... 9 2.2 About This Guide... 9 2.3 Accessing Toolbar... 9 2.4 First Time Login... 10 2.5 Subsequent
Configuration Guide SuperStack 3 Firewall L2TP/IPSec VPN Client
 Overview This guide is used as a supplement to the SuperStack 3 Firewall manual, and details how to configure the native Windows VPN client to work with the Firewall, via the Microsoft recommended Layer
Overview This guide is used as a supplement to the SuperStack 3 Firewall manual, and details how to configure the native Windows VPN client to work with the Firewall, via the Microsoft recommended Layer
Server Edition. V8 Peregrine User Manual. for Microsoft Windows
 Server Edition V8 Peregrine User Manual for Microsoft Windows Copyright Notice and Proprietary Information All rights reserved. Attix5, 2015 Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft
Server Edition V8 Peregrine User Manual for Microsoft Windows Copyright Notice and Proprietary Information All rights reserved. Attix5, 2015 Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft
NETOP HOST ON A TERMINAL SERVER
 27.09.2017 NETOP HOST ON A TERMINAL SERVER Contents 1 Introduction... 2 1.1 Incoming traffic... 2 1.2 Outgoing traffic... 2 2 Using a Netop Gateway with the Netop Host on a Terminal Server... 3 2.1 Install
27.09.2017 NETOP HOST ON A TERMINAL SERVER Contents 1 Introduction... 2 1.1 Incoming traffic... 2 1.2 Outgoing traffic... 2 2 Using a Netop Gateway with the Netop Host on a Terminal Server... 3 2.1 Install
Equitrac Integrated for Konica Minolta. Setup Guide Equitrac Corporation
 Equitrac Integrated for Konica Minolta 1.2 Setup Guide 2012 Equitrac Corporation Equitrac Integrated for Konica Minolta Setup Guide Document Revision History Revision Date Revision List November 1, 2012
Equitrac Integrated for Konica Minolta 1.2 Setup Guide 2012 Equitrac Corporation Equitrac Integrated for Konica Minolta Setup Guide Document Revision History Revision Date Revision List November 1, 2012
User Guide. Illustra Connect Version C0
 User Guide Illustra Connect Version.0 8200-114-01 C0 Notice The information in this manual was current when published. The manufacturer reserves the right to revise and improve its products. All specifications
User Guide Illustra Connect Version.0 8200-114-01 C0 Notice The information in this manual was current when published. The manufacturer reserves the right to revise and improve its products. All specifications
Aspera Connect Windows XP, 2003, Vista, 2008, 7. Document Version: 1
 Aspera Connect 2.6.3 Windows XP, 2003, Vista, 2008, 7 Document Version: 1 2 Contents Contents Introduction... 3 Setting Up... 4 Upgrading from a Previous Version...4 Installation... 4 Set Up Network Environment...
Aspera Connect 2.6.3 Windows XP, 2003, Vista, 2008, 7 Document Version: 1 2 Contents Contents Introduction... 3 Setting Up... 4 Upgrading from a Previous Version...4 Installation... 4 Set Up Network Environment...
Managing the VPN Client
 Managing the VPN Client This chapter explains the tasks you can perform to manage connection entries, view and manage event reporting, and upgrade or uninstall the VPN Client software. The management features
Managing the VPN Client This chapter explains the tasks you can perform to manage connection entries, view and manage event reporting, and upgrade or uninstall the VPN Client software. The management features
Configuring Remote Access using the RDS Gateway
 Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
New in Release: Secomea Release 8.0. This document shows the changes from release 7.4 to release 8.0. Version: 1.5, 2018
 New in Release: Secomea Release 8.0 This document shows the changes from release 7.4 to release 8.0. Version: 1.5, 2018 Table of Contents Change log 4 1. Release 8.0 4 Highlights 4 2. General 6 2.1. New
New in Release: Secomea Release 8.0 This document shows the changes from release 7.4 to release 8.0. Version: 1.5, 2018 Table of Contents Change log 4 1. Release 8.0 4 Highlights 4 2. General 6 2.1. New
Microsoft OWA 2010 IIS Integration
 Microsoft OWA 2010 IIS Integration Contents 1 Introduction 2 Compatibility 3 Prerequisites 3.1 Additional Prerequisites for Version 2.9 4 File Downloads 4.1 OWA Filter Change History 5 Architecture 6 Installation
Microsoft OWA 2010 IIS Integration Contents 1 Introduction 2 Compatibility 3 Prerequisites 3.1 Additional Prerequisites for Version 2.9 4 File Downloads 4.1 OWA Filter Change History 5 Architecture 6 Installation
System Administration
 Most of SocialMiner system administration is performed using the panel. This section describes the parts of the panel as well as other administrative procedures including backup and restore, managing certificates,
Most of SocialMiner system administration is performed using the panel. This section describes the parts of the panel as well as other administrative procedures including backup and restore, managing certificates,
VMware Identity Manager Cloud Deployment. DEC 2017 VMware AirWatch 9.2 VMware Identity Manager
 VMware Identity Manager Cloud Deployment DEC 2017 VMware AirWatch 9.2 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Identity Manager Cloud Deployment DEC 2017 VMware AirWatch 9.2 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Remote Desktop Services. Deployment Guide
 Deployment Guide UPDATED: 20 June 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks of KEMP
Deployment Guide UPDATED: 20 June 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks of KEMP
High Availability Options
 , on page 1 Load Balancing, on page 2 Distributed VPN Clustering, Load balancing and Failover are high-availability features that function differently and have different requirements. In some circumstances
, on page 1 Load Balancing, on page 2 Distributed VPN Clustering, Load balancing and Failover are high-availability features that function differently and have different requirements. In some circumstances
Apptix Online Backup by Mozy User Guide
 Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
vrealize Orchestrator Load Balancing
 vrealize Orchestrator Load Balancing Configuration Guide Version 7.0.x T E C H N I C A L W H I T E P A P E R M A Y 2 0 1 6 V E R S I O N 1. 0 Table of Contents Introduction... 4 Load Balancing Concepts...
vrealize Orchestrator Load Balancing Configuration Guide Version 7.0.x T E C H N I C A L W H I T E P A P E R M A Y 2 0 1 6 V E R S I O N 1. 0 Table of Contents Introduction... 4 Load Balancing Concepts...
Cisco TelePresence Conductor with Cisco VCS (Policy Service)
 Cisco TelePresence Conductor with Cisco VCS (Policy Service) Deployment Guide TelePresence Conductor XC3.0 Cisco VCS X8.x Revised January 2015 Contents Introduction 5 About the Cisco TelePresence Conductor
Cisco TelePresence Conductor with Cisco VCS (Policy Service) Deployment Guide TelePresence Conductor XC3.0 Cisco VCS X8.x Revised January 2015 Contents Introduction 5 About the Cisco TelePresence Conductor
Desktop & Laptop Edition
 Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
KYOCERA Net Viewer User Guide
 KYOCERA Net Viewer User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
KYOCERA Net Viewer User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
