Grandstream Networks, Inc. GWN Firewall Features Advanced NAT Configuration Guide
|
|
|
- Alban Cain
- 6 years ago
- Views:
Transcription
1 Grandstream Networks, Inc. GWN Firewall Features Advanced NAT Configuration Guide
2 Table of Content INTRODUCTION... 3 INPUT/OUPUT POLICIES... 4 Overview... 4 Configuration... 4 SNAT (SOURCE NAT)... 6 Overview... 6 Configuration... 6 DNAT (DESTINATION NAT)... 9 Overview... 9 Configuration... 9 NAT SETTINGS TABLE Table of Figures Figure 1: NAT Architecture... 3 Figure 2: Input/Output Policy... 4 Figure 3: General Settings... 5 Figure 4: SNAT... 6 Figure 5: SNAT Example... 7 Figure 6: DNAT... 9 Figure 7: DNAT Example P a g e 2
3 INTRODUCTION A firewall is a set of security measures designed to prevent unauthorized access to a networked computer system. It is like walls in a building construction, because in both cases their purpose is to isolate one "network" or "compartment" from another. To protect private networks and individual machines from the dangers of Internet, a firewall can be employed to filter incoming or outgoing traffic based on a predefined set of rules called firewall policies. Firewall advanced settings on the GWN7000 is used to setup incoming/outgoing filter for WAN ports as well as setting up SNAT and DNAT. Network Address Translation (NAT) technology, is described in RFC1631. Due to the growth of computers connected to the Internet, the pool of public IPv4 addresses was nearly exhausted. It was quickly realized that public IP addresses for the newly built networks would be very short. To remedy this, NAT was invented. NAT technology is the new approach for IP network, that allowed for years to extend many existing networks, instead of giving a public IPv4 address to each machine on the network, private IP addresses was attributed on a Local Area Network and to connect to internet, a public IPv4 is assigned to this network, NAT protocol, as its name stats handle the translation between public and private IPs. Figure 1: NAT Architecture This guide will help you to understand and configure NAT advanced settings on GWN7000 series. The configuration can be done from GWN7000 Web GUI > Firewall Advanced Settings page which provides ability to setup input/output policies for each WAN interface and Network Group; as well as setting configuration for Source and Destination NAT. P a g e 3
4 INPUT/OUPUT POLICIES Overview The Input/Output policy on the GWN7000 set configuration for WAN ports behavior when receiving/sending packets. It allows also to set limits on those ports and to enable MSS Clamping and IP Masquerading. Below figure shows example of packets received by WAN2 port rejected while packets incoming from outside network to WAN1 are processed. Configuration Figure 2: Input/Output Policy NAT input/output policies for each WAN interface or Network Groups can be configured from GWN7000 web GUI > Firewall > Advanced > General Settings. An entry for each created/available network group or network interface can be found on this page, click on next to a WAN interface or Network group to edit its input and output policies. The example below makes WAN port 1 accept any incoming traffic from outside the network. P a g e 4
5 Figure 3: General Settings The following configuration was made on the above example: 1. Select Accept from the Input Policy dropdown list so that any incoming packet to WAN port 1 will be accepted. 2. Select Accept from the Output Policy dropdown list so that any outgoing packet to from WAN port 1 will be accepted. 3. Check the IP Masquerading checkbox to allow internal computers with no known address outside their network, to communicate to the outside. It allows one machine to act on behalf of other machines. 4. Check the MSS Clamping checkbox to provide a method to prevent fragmentation when the MTU value on the communication path is lower than the MSS value. 5. After filling the fields, click on,then to save and apply the settings. By default, the Input Policy is reject which blocks access from WAN port to LAN, unless a port forwarding is set. This is not recommended as it allows unsecure network to access the GWN7000 LAN. P a g e 5
6 SNAT (SOURCE NAT) Overview The GWN7000 provides Source NAT feature, which changes the source address in IP header of a packet. It changes also the source port in the TCP/UDP headers. The typical usage is to change a private address/port into a public address/port for packets leaving the group or WAN port. Configuration Figure 4: SNAT Following actions are available for SNAT from the GWN7000 web GUI under Firewall > Advanced > SNAT To add new SNAT entry, click on. To edit a SNAT entry, click on.. To delete a SNAT rule, click on Below figure provide an example of configuration for SNAT on the GWN7000. P a g e 6
7 Figure 5: SNAT Example P a g e 7
8 The following configuration was made on the above example: 1. Specify a name to identify the SNAT rule. 2. Click on the Enable checkbox to enable the SNAT rule. 3. Select the IP version from the IP Family drop down list. 4. Select the source of incoming traffic from Source Group dropdown list, it could be an internal network group or external traffic from WAN port 1 or Select the Destination Group 6. Select one of the protocols from the Protocol dropdown list, available options are: UDP, TCP, TCP/UDP and All. 7. Enter the device Source IP. 8. Enter the IP that will go out from the GWN7000 to its destination on the Rewrite IP. 9. Enter the source port 10. Enter the rewrite port. 11. Enter the destination IP. 12. Enter the destination port. For more details about other fields explanation please refer to NAT SETTINGS TABLE. P a g e 8
9 DNAT (DESTINATION NAT) Overview The GWN7000 allows users to configure Destination NAT or DNAT, which changes the destination address in IP header of a packet and change the destination port in the TCP/UDP headers. Typical usage of this is to redirect incoming packets with a destination of a public address/port to a private IP address/port inside your network. Configuration Figure 6: DNAT Following actions are available for DNAT from the GWN7000 web GUI under Firewall > Advanced > DNAT To add new DNAT entry, click on. To edit a DNAT entry, click on. To delete a DNAT rule, click on. Below figure provide an example of configuration for DNAT on the GWN7000. P a g e 9
10 Figure 7: DNAT Example P a g e 10
11 The following configuration was made on the above example: 1. Specify a name to identify the SNAT rule. 2. Click on the Enable checkbox to enable the SNAT rule. 3. Select the IP version from the IP Family drop down list. 4. Select the source of incoming traffic from Source Group dropdown list, it could be an internal network group or external traffic from WAN port 1 or Select the Destination Group 6. Select one of the protocols from the Protocol dropdown list, available options are: UDP, TCP, TCP/UDP and All. 7. Enter the device Source IP. 8. Enter the destination IP. 9. Enter the source port 10. Enter the destination port. 11. Enter the IP that will go out from the GWN7000 to its destination on the Rewrite IP. 12. Enter the rewrite port. For more details about other fields explanation please refer to NAT SETTINGS TABLE. P a g e 11
12 NAT SETTINGS TABLE The following table provides explanation about all fields related to NAT configuration. Field Name Enabled IP Family Source Group Destination Group Protocol Source IP Rewrite IP Destination IP Description Specify a name for the NAT entry Check to enable this NAT entry. Select the IP version. Three options are available: IPv4, IPv6 or Any. Select a WAN interface or a LAN group for Source Group, or select All. Select a WAN interface or a LAN group for Destination Group, or select All. Make sure that destination and source groups are different to avoid conflict. Select one of the protocols from dropdown list or All. Available options are: UDP, TCP, TCP/UDP and All. Set the Source IP address. Set the Rewrite IP. The source IP address of the data package from the source group will be updated to this configured IP. Set the Destination IP address. Schedule Start Date Click on icon to schedule a start date for this NAT entry to be applied. Schedule End Date Click on icon to schedule an end date for this NAT entry to end. Schedule Start Time Click on icon to schedule a start time for this NAT entry to be applied. Schedule End Time Click on icon to schedule an end time for this NAT entry to end. Schedule Weekdays List of Weekdays Schedule Days of the Month Treat Time Values as UTC Instead of Local Time Enable NAT Reflection Select the days, on which the NAT entry will be applied, the unselected days will ignore this rule. Enter the days of the months (separated by space) on which the NAT entry will be applied. Example: This will be applied only on 5 th, 10 th and 15 th day monthly. Check to use UTC as time zone for the specified times, instead of using GWN7000 s local time. Check to enable NAT Reflection for this DNAT entry to allow the access of a service via the public IP address from inside the local network. P a g e 12
Configuring the EN-2000 s VPN Firewall
 EN-2000 Reference Manual Document 10 Configuring the EN-2000 s VPN Firewall T his document discusses implementation of firewall rules to support IPsec VPN transmissions in the EN-2000. It presents procedures
EN-2000 Reference Manual Document 10 Configuring the EN-2000 s VPN Firewall T his document discusses implementation of firewall rules to support IPsec VPN transmissions in the EN-2000. It presents procedures
Nat & Publish -
 ...... (Forward) LAN...(Inbound) (outbound)... Nat & Publish...Nat... Publish... Proxy... ... Statefull Packet Filter Nat & Publish /. Firewall Nat : (Forward) LAN (Inbound) (outbound) Proxy Publish Nat.
...... (Forward) LAN...(Inbound) (outbound)... Nat & Publish...Nat... Publish... Proxy... ... Statefull Packet Filter Nat & Publish /. Firewall Nat : (Forward) LAN (Inbound) (outbound) Proxy Publish Nat.
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide
 Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
SLE in Virtual Private Networks
 EN-4000 Reference Manual Document 9 SLE in Virtual Private Networks T his document discusses implementation of Encore Networks Selective Layer Encryption (SLE, patented), a proprietary method of enhancing
EN-4000 Reference Manual Document 9 SLE in Virtual Private Networks T his document discusses implementation of Encore Networks Selective Layer Encryption (SLE, patented), a proprietary method of enhancing
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
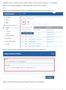 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Example - Allowing SIP-based VoIP Traffic
 This article provides the following examples of how to configure the Barracuda NextGen Firewall X-Series to allow SIP-based VoIP traffic: Allowing SIP-based VoIP Traffic for VoIP Phones Steps for configuring
This article provides the following examples of how to configure the Barracuda NextGen Firewall X-Series to allow SIP-based VoIP traffic: Allowing SIP-based VoIP Traffic for VoIP Phones Steps for configuring
Grandstream Networks, Inc. GWN7000 OpenVPN Site-to-Site VPN Guide
 Grandstream Networks, Inc. GWN7000 OpenVPN Site-to-Site VPN Guide Table of Contents INTRODUCTION... 4 SCENARIO OVERVIEW... 5 CONFIGURATION STEPS... 6 Core Site Configuration... 6 Generate Self-Issued Certificate
Grandstream Networks, Inc. GWN7000 OpenVPN Site-to-Site VPN Guide Table of Contents INTRODUCTION... 4 SCENARIO OVERVIEW... 5 CONFIGURATION STEPS... 6 Core Site Configuration... 6 Generate Self-Issued Certificate
sottotitolo A.A. 2016/17 Federico Reghenzani, Alessandro Barenghi
 Titolo presentazione Piattaforme Software per la Rete sottotitolo Firewall and NAT Milano, XX mese 20XX A.A. 2016/17, Alessandro Barenghi Outline 1) Packet Filtering 2) Firewall management 3) NAT review
Titolo presentazione Piattaforme Software per la Rete sottotitolo Firewall and NAT Milano, XX mese 20XX A.A. 2016/17, Alessandro Barenghi Outline 1) Packet Filtering 2) Firewall management 3) NAT review
Network Address Translation
 Claudio Cicconetti International Master on Communication Networks Engineering 2006/2007 Network Address Translation (NAT) basically provides a mapping between internal (i.e.,
Claudio Cicconetti International Master on Communication Networks Engineering 2006/2007 Network Address Translation (NAT) basically provides a mapping between internal (i.e.,
IPv4 Firewall Rule configuration on Cisco SA540 Security Appliance
 IPv4 Firewall Rule configuration on Cisco SA540 Security Appliance Objective The objective of this document to explain how to configure IPv4 firewall rules on Cisco SA540 Security Appliance. Firewall provide
IPv4 Firewall Rule configuration on Cisco SA540 Security Appliance Objective The objective of this document to explain how to configure IPv4 firewall rules on Cisco SA540 Security Appliance. Firewall provide
Configuring Advanced Firewall Settings
 Configuring Advanced Firewall Settings This section provides advanced firewall settings for configuring detection prevention, dynamic ports, source routed packets, connection selection, and access rule
Configuring Advanced Firewall Settings This section provides advanced firewall settings for configuring detection prevention, dynamic ports, source routed packets, connection selection, and access rule
Introduction to Firewalls using IPTables
 Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
GWN7000 Firmware Release Note IMPORTANT UPGRADING NOTE
 GWN7000 Firmware Release Note IMPORTANT UPGRADING NOTE 2 intermedia upgrading are required from 1.0.1.x to 1.0.2.62. Please refer to 1.0.2.62 release note for upgrading steps. Controller module of any
GWN7000 Firmware Release Note IMPORTANT UPGRADING NOTE 2 intermedia upgrading are required from 1.0.1.x to 1.0.2.62. Please refer to 1.0.2.62 release note for upgrading steps. Controller module of any
Use this section to help you quickly locate a command.
 iii iv v Use this section to help you quickly locate a command. vi Use this list to help you locate examples you d like to try or look at. vii viii This document describes the various deployment, installation,
iii iv v Use this section to help you quickly locate a command. vi Use this list to help you locate examples you d like to try or look at. vii viii This document describes the various deployment, installation,
Configuring NAT Policies
 Configuring NAT Policies Rules > NAT Policies About NAT in SonicOS About NAT Load Balancing About NAT64 Viewing NAT Policy Entries Adding or Editing NAT or NAT64 Policies Deleting NAT Policies Creating
Configuring NAT Policies Rules > NAT Policies About NAT in SonicOS About NAT Load Balancing About NAT64 Viewing NAT Policy Entries Adding or Editing NAT or NAT64 Policies Deleting NAT Policies Creating
Definition of firewall
 Internet Firewalls Definitions: firewall, policy, router, gateway, proxy NAT: Network Address Translation Source NAT, Destination NAT, Port forwarding NAT firewall compromise via UPnP/IGD Packet filtering
Internet Firewalls Definitions: firewall, policy, router, gateway, proxy NAT: Network Address Translation Source NAT, Destination NAT, Port forwarding NAT firewall compromise via UPnP/IGD Packet filtering
On Distributed Communications, Rand Report RM-3420-PR, Paul Baran, August 1964
 The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
Setting the firewall for LAN and DMZ
 Setting the firewall for LAN and DMZ Dokument-ID Version 2.0 Status Date of publication Setting the firewall for LAN and DMZ Final Version 01.2017 1 Contents 1.1 Need 3 1.2 Description 3 1.3 Requirements/limitations
Setting the firewall for LAN and DMZ Dokument-ID Version 2.0 Status Date of publication Setting the firewall for LAN and DMZ Final Version 01.2017 1 Contents 1.1 Need 3 1.2 Description 3 1.3 Requirements/limitations
IPv4 addressing, NAT. Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley.
 IPv4 addressing, NAT http://xkcd.com/195/ Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights
IPv4 addressing, NAT http://xkcd.com/195/ Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights
Networking Potpourri: Plug-n-Play, Next Gen
 Networking Potpourri: Plug-n-Play, Next Gen 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia
Networking Potpourri: Plug-n-Play, Next Gen 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia
Firewalls, Tunnels, and Network Intrusion Detection
 Firewalls, Tunnels, and Network Intrusion Detection 1 Firewalls A firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system.
Firewalls, Tunnels, and Network Intrusion Detection 1 Firewalls A firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system.
firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name
 firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name WAN_IN { default-action drop description "WAN to internal"
firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name WAN_IN { default-action drop description "WAN to internal"
How to Configure Virus Scanning in the Firewall for FTP Traffic
 How to Configure Virus Scanning in the Firewall for FTP Traffic The X-Series Firewall scans FTP traffic for malware on a per-access-rule basis when FTP virus scanning in the firewall is enabled. Both active
How to Configure Virus Scanning in the Firewall for FTP Traffic The X-Series Firewall scans FTP traffic for malware on a per-access-rule basis when FTP virus scanning in the firewall is enabled. Both active
Network Basic v0.1. Network Basic v0.1. Chapter 3 Internet Protocol. Chapter 3. Internet Protocol
 Network Basic v0.1 Chapter 3. Internet Protocol 1 Network Basic v0.1 Chapter 3 Internet Protocol 1. The Role of Network Layer 2. IP Protocol Feature 3. IP Packet Routing 5. DHCP 6. NAT 2 1 네트워크 ICONs 3
Network Basic v0.1 Chapter 3. Internet Protocol 1 Network Basic v0.1 Chapter 3 Internet Protocol 1. The Role of Network Layer 2. IP Protocol Feature 3. IP Packet Routing 5. DHCP 6. NAT 2 1 네트워크 ICONs 3
Quick Note 05. Configuring Port Forwarding to access an IP camera user interface on a TransPort LR54. 7 November 2017
 Quick Note 05 Configuring Port Forwarding to access an IP camera user interface on a TransPort LR54 7 November 2017 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions... 3 1.3 Corrections...
Quick Note 05 Configuring Port Forwarding to access an IP camera user interface on a TransPort LR54 7 November 2017 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions... 3 1.3 Corrections...
How to configure the web access in various Integra interfaces
 How to configure the web access in various Integra interfaces How-to guides for configuring VPNs with GateDefender Integra Panda Security wants to ensure you get the most out of GateDefender Integra. For
How to configure the web access in various Integra interfaces How-to guides for configuring VPNs with GateDefender Integra Panda Security wants to ensure you get the most out of GateDefender Integra. For
How to configure the AT-AR450S Firewall using the Graphical User Interface (GUI)
 How to configure the AT-AR450S Firewall using the Graphical User Interface (GUI) Introduction This document describes the firewall configuration facility available on the AT-AR450S HTTP-based Graphical
How to configure the AT-AR450S Firewall using the Graphical User Interface (GUI) Introduction This document describes the firewall configuration facility available on the AT-AR450S HTTP-based Graphical
Packet Filtering and NAT
 Packet Filtering and NAT Alessandro Barenghi Dipartimento di Elettronica e Informazione Politecnico di Milano barenghi - at - elet.polimi.it May 14, 2014 Lesson contents Overview Netfilter/Iptables Structure
Packet Filtering and NAT Alessandro Barenghi Dipartimento di Elettronica e Informazione Politecnico di Milano barenghi - at - elet.polimi.it May 14, 2014 Lesson contents Overview Netfilter/Iptables Structure
b. Suppose the two packets are to be forwarded to two different output ports. Is it
 Problem-1:[15] Suppose two packets arrive to two different input ports of a router at exactly the same time. Also suppose there are no other packets anywhere in the router. a. Suppose the two packets are
Problem-1:[15] Suppose two packets arrive to two different input ports of a router at exactly the same time. Also suppose there are no other packets anywhere in the router. a. Suppose the two packets are
ICS 451: Today's plan
 ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
IPv6 NAT. Open Source Days 9th-10th March 2013 Copenhagen, Denmark. Patrick McHardy
 IPv6 NAT Open Source Days 9th-10th March 2013 Copenhagen, Denmark Patrick McHardy Netfilter and IPv6 NAT historically http://lists.netfilter.org/pipermail/netfilter/2005-march/059463.html
IPv6 NAT Open Source Days 9th-10th March 2013 Copenhagen, Denmark Patrick McHardy Netfilter and IPv6 NAT historically http://lists.netfilter.org/pipermail/netfilter/2005-march/059463.html
NAT Router Performance Evaluation
 University of Aizu, Graduation Thesis. Mar, 22 17173 1 NAT Performance Evaluation HAYASHI yu-ichi 17173 Supervised by Atsushi Kara Abstract This thesis describes a quantitative analysis of NAT routers
University of Aizu, Graduation Thesis. Mar, 22 17173 1 NAT Performance Evaluation HAYASHI yu-ichi 17173 Supervised by Atsushi Kara Abstract This thesis describes a quantitative analysis of NAT routers
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
vcloud Air - Virtual Private Cloud OnDemand Networking Guide
 vcloud Air - Virtual Private Cloud OnDemand Networking Guide vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
vcloud Air - Virtual Private Cloud OnDemand Networking Guide vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Firewalls. Content. Location of firewalls Design of firewalls. Definitions. Forwarding. Gateways, routers, firewalls.
 Firewalls INFO 404 - Lecture 10 31/03/2009 nfoukia@infoscience.otago.ac.nz Credit: Cameron Kerr : ckerr@cs.otago.ac.nz Definitions Content Gateways, routers, firewalls Location of firewalls Design of firewalls
Firewalls INFO 404 - Lecture 10 31/03/2009 nfoukia@infoscience.otago.ac.nz Credit: Cameron Kerr : ckerr@cs.otago.ac.nz Definitions Content Gateways, routers, firewalls Location of firewalls Design of firewalls
Example - Configuring a Site-to-Site IPsec VPN Tunnel
 Example - Configuring a Site-to-Site IPsec VPN Tunnel To configure a Site-to-Site VPN connection between two Barracuda NextGen X-Series Firewalls, in which one unit (Location 1) has a dynamic Internet
Example - Configuring a Site-to-Site IPsec VPN Tunnel To configure a Site-to-Site VPN connection between two Barracuda NextGen X-Series Firewalls, in which one unit (Location 1) has a dynamic Internet
Grandstream Networks, Inc. GWN7000 PPTP Site-to-Site VPN Guide
 Grandstream Networks, Inc. GWN7000 PPTP Site-to-Site VPN Guide Table of Contents INTRODUCTION... 4 SCENARIO OVERVIEW... 5 CONFIGURATION STEPS... 6 Core Site Configuration... 6 Creating PPTP Users... 6
Grandstream Networks, Inc. GWN7000 PPTP Site-to-Site VPN Guide Table of Contents INTRODUCTION... 4 SCENARIO OVERVIEW... 5 CONFIGURATION STEPS... 6 Core Site Configuration... 6 Creating PPTP Users... 6
NAT and Tunnels. Alessandro Barenghi. May 25, Dipartimento di Elettronica e Informazione Politecnico di Milano barenghi - at - elet.polimi.
 NAT and Tunnels Alessandro Barenghi Dipartimento di Elettronica e Informazione Politecnico di Milano barenghi - at - elet.polimi.it May 25, 2011 Recap By now, you should be familiar with... System administration
NAT and Tunnels Alessandro Barenghi Dipartimento di Elettronica e Informazione Politecnico di Milano barenghi - at - elet.polimi.it May 25, 2011 Recap By now, you should be familiar with... System administration
Firewall. Access Control, Port Forwarding, Custom NAT and Packet Filtering. Applies to the xrd and ADSL Range. APPLICATION NOTE: AN-005-WUK
 APPLICATION NOTE: AN-005-WUK Firewall Access Control, Port Forwarding, Custom NAT and Packet Filtering. Applies to the xrd and ADSL Range. FIREWALL Access Control The Access Control page allows configuration
APPLICATION NOTE: AN-005-WUK Firewall Access Control, Port Forwarding, Custom NAT and Packet Filtering. Applies to the xrd and ADSL Range. FIREWALL Access Control The Access Control page allows configuration
Brocade Vyatta Network OS NAT Configuration Guide, 5.2R1
 CONFIGURATION GUIDE Brocade Vyatta Network OS NAT Configuration Guide, 5.2R1 Supporting Brocade 5600 vrouter, VNF Platform, and Distributed Services Platform 53-1004728-01 24 October 2016 2016, Brocade
CONFIGURATION GUIDE Brocade Vyatta Network OS NAT Configuration Guide, 5.2R1 Supporting Brocade 5600 vrouter, VNF Platform, and Distributed Services Platform 53-1004728-01 24 October 2016 2016, Brocade
SE 4C03 Winter 2005 Network Firewalls
 SE 4C03 Winter 2005 Network Firewalls Mohammed Bashir Khan - 0150805 Last revised 2005-04-04 1.0 Introduction Firewalls are literally walls which are embedded in the external and internal network interface
SE 4C03 Winter 2005 Network Firewalls Mohammed Bashir Khan - 0150805 Last revised 2005-04-04 1.0 Introduction Firewalls are literally walls which are embedded in the external and internal network interface
Avi Networks Technical Reference (16.3)
 Page 1 of 7 view online A TCP/UDP profile determines the type and settings of the network protocol that a subscribing virtual service will use. It sets a number of parameters, such as whether the virtual
Page 1 of 7 view online A TCP/UDP profile determines the type and settings of the network protocol that a subscribing virtual service will use. It sets a number of parameters, such as whether the virtual
Network Security Fundamentals
 Network Security Fundamentals Security Training Course Dr. Charles J. Antonelli The University of Michigan 2013 Network Security Fundamentals Module 6 Firewalls & VPNs Topics Firewall Fundamentals Case
Network Security Fundamentals Security Training Course Dr. Charles J. Antonelli The University of Michigan 2013 Network Security Fundamentals Module 6 Firewalls & VPNs Topics Firewall Fundamentals Case
IPv4 ACLs, identified by ACL numbers, fall into four categories, as shown in Table 1. Table 1 IPv4 ACL categories
 Table of Contents ACL Configuration 1 ACL Overview 1 IPv4 ACL Classification 1 IPv4 ACL Rule Order 1 Rule Numbering Step with IPv4 ACLs 3 Effective Time Period of an IPv4 ACL 3 IP Fragments Filtering with
Table of Contents ACL Configuration 1 ACL Overview 1 IPv4 ACL Classification 1 IPv4 ACL Rule Order 1 Rule Numbering Step with IPv4 ACLs 3 Effective Time Period of an IPv4 ACL 3 IP Fragments Filtering with
ETSF05/ETSF10 Internet Protocols Network Layer Protocols
 ETSF05/ETSF10 Internet Protocols Network Layer Protocols 2016 Jens Andersson Agenda Internetworking IPv4/IPv6 Framentation/Reassembly ICMPv4/ICMPv6 IPv4 to IPv6 transition VPN/Ipsec NAT (Network Address
ETSF05/ETSF10 Internet Protocols Network Layer Protocols 2016 Jens Andersson Agenda Internetworking IPv4/IPv6 Framentation/Reassembly ICMPv4/ICMPv6 IPv4 to IPv6 transition VPN/Ipsec NAT (Network Address
Software Defined Networking
 Software Defined Networking Daniel Zappala CS 460 Computer Networking Brigham Young University Proliferation of Middleboxes 2/16 a router that manipulatees traffic rather than just forwarding it NAT rewrite
Software Defined Networking Daniel Zappala CS 460 Computer Networking Brigham Young University Proliferation of Middleboxes 2/16 a router that manipulatees traffic rather than just forwarding it NAT rewrite
Advanced Security and Forensic Computing
 Advanced Security and Forensic Computing Unit 2: Network Security Elements Dr Dr Bill Buchanan, Reader, School of of Computing. >Unit 2: 2: Network Security Elements Advanced Security and Forensic Computing
Advanced Security and Forensic Computing Unit 2: Network Security Elements Dr Dr Bill Buchanan, Reader, School of of Computing. >Unit 2: 2: Network Security Elements Advanced Security and Forensic Computing
Mapping of Address and Port Using Translation
 The feature provides connectivity to IPv4 hosts across IPv6 domains. Mapping of address and port using translation (MAP-T) is a mechanism that performs double translation (IPv4 to IPv6 and vice versa)
The feature provides connectivity to IPv4 hosts across IPv6 domains. Mapping of address and port using translation (MAP-T) is a mechanism that performs double translation (IPv4 to IPv6 and vice versa)
Technical Support Information
 Technical Support Information Broadband Module/Broadband Module Plus Configuration Guidance Setting up Remote Access to a Network Device (Mail/File Server/Camera Etc) connected to the LAN port of the Broadband
Technical Support Information Broadband Module/Broadband Module Plus Configuration Guidance Setting up Remote Access to a Network Device (Mail/File Server/Camera Etc) connected to the LAN port of the Broadband
Comodo One Software Version 3.8
 rat Comodo One Software Version 3.8 Dome Cloud Firewall Quick Start Guide Guide Version 1.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Dome Cloud Firewall Quick Start This
rat Comodo One Software Version 3.8 Dome Cloud Firewall Quick Start Guide Guide Version 1.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Dome Cloud Firewall Quick Start This
COSC 301 Network Management
 COSC 301 Network Management Lecture 21: Firewalls & NAT Zhiyi Huang Computer Science, University of Otago COSC301 Lecture 21: Firewalls & NAT 1 Today s Focus How to protect an intranet? -- Firewall --
COSC 301 Network Management Lecture 21: Firewalls & NAT Zhiyi Huang Computer Science, University of Otago COSC301 Lecture 21: Firewalls & NAT 1 Today s Focus How to protect an intranet? -- Firewall --
CyberP3i Course Module Series
 CyberP3i Course Module Series Spring 2017 Designer: Dr. Lixin Wang, Associate Professor Firewall Configuration Firewall Configuration Learning Objectives 1. Be familiar with firewalls and types of firewalls
CyberP3i Course Module Series Spring 2017 Designer: Dr. Lixin Wang, Associate Professor Firewall Configuration Firewall Configuration Learning Objectives 1. Be familiar with firewalls and types of firewalls
DEPLOYMENT GUIDE Version 1.1. DNS Traffic Management using the BIG-IP Local Traffic Manager
 DEPLOYMENT GUIDE Version 1.1 DNS Traffic Management using the BIG-IP Local Traffic Manager Table of Contents Table of Contents Introducing DNS server traffic management with the BIG-IP LTM Prerequisites
DEPLOYMENT GUIDE Version 1.1 DNS Traffic Management using the BIG-IP Local Traffic Manager Table of Contents Table of Contents Introducing DNS server traffic management with the BIG-IP LTM Prerequisites
2/22/2016 UTM: How to Open FTPS traffic to a Passive mode FTP Server behind the SonicWALL (SW10094)
 UTM: How to Open FTPS traffic to a Passive mode FTP Server behind the SonicWALL (SW10094) Title UTM: How to Open FTPS traffic to a Passive mode FTP Server behind the SonicWALL Resolution Article Applies
UTM: How to Open FTPS traffic to a Passive mode FTP Server behind the SonicWALL (SW10094) Title UTM: How to Open FTPS traffic to a Passive mode FTP Server behind the SonicWALL Resolution Article Applies
On Distributed Communications, Rand Report RM-3420-PR, Paul Baran, August
 The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
Activating Intrusion Prevention Service
 Activating Intrusion Prevention Service Intrusion Prevention Service Overview Configuring Intrusion Prevention Service Intrusion Prevention Service Overview Intrusion Prevention Service (IPS) delivers
Activating Intrusion Prevention Service Intrusion Prevention Service Overview Configuring Intrusion Prevention Service Intrusion Prevention Service Overview Intrusion Prevention Service (IPS) delivers
How to Make the Client IP Address Available to the Back-end Server
 How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
Configuring NAT for IP Address Conservation
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure the inside and outside source addresses. This module also provides information
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure the inside and outside source addresses. This module also provides information
Worksheet 8. Linux as a router, packet filtering, traffic shaping
 Worksheet 8 Linux as a router, packet filtering, traffic shaping Linux as a router Capable of acting as a router, firewall, traffic shaper (so are most other modern operating systems) Tools: netfilter/iptables
Worksheet 8 Linux as a router, packet filtering, traffic shaping Linux as a router Capable of acting as a router, firewall, traffic shaper (so are most other modern operating systems) Tools: netfilter/iptables
HP High-End Firewalls
 HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2630 Software version: F1000-E/Firewall module: R3166 F5000-A5: R3206 Document version: 6PW101-20120706 Legal and notice information
HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2630 Software version: F1000-E/Firewall module: R3166 F5000-A5: R3206 Document version: 6PW101-20120706 Legal and notice information
Application Note. Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder )
 Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Network security Exercise 9 How to build a wall of fire Linux Netfilter
 Network security Exercise 9 How to build a wall of fire Linux Netfilter Tobias Limmer Computer Networks and Communication Systems Dept. of Computer Sciences, University of Erlangen-Nuremberg, Germany 2.2.
Network security Exercise 9 How to build a wall of fire Linux Netfilter Tobias Limmer Computer Networks and Communication Systems Dept. of Computer Sciences, University of Erlangen-Nuremberg, Germany 2.2.
CS-435 spring semester Network Technology & Programming Laboratory. Stefanos Papadakis & Manolis Spanakis
 CS-435 spring semester 2016 Network Technology & Programming Laboratory University of Crete Computer Science Department Stefanos Papadakis & Manolis Spanakis CS-435 Lecture #4 preview ICMP ARP DHCP NAT
CS-435 spring semester 2016 Network Technology & Programming Laboratory University of Crete Computer Science Department Stefanos Papadakis & Manolis Spanakis CS-435 Lecture #4 preview ICMP ARP DHCP NAT
HP A-F1000-A-EI_A-F1000-S-EI VPN Firewalls
 HP A-F1000-A-EI_A-F1000-S-EI VPN Firewalls NAT Configuration Guide Part number:5998-2649 Document version: 6PW100-20110909 Legal and notice information Copyright 2011 Hewlett-Packard Development Company,
HP A-F1000-A-EI_A-F1000-S-EI VPN Firewalls NAT Configuration Guide Part number:5998-2649 Document version: 6PW100-20110909 Legal and notice information Copyright 2011 Hewlett-Packard Development Company,
Università Ca Foscari Venezia
 Firewalls Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Networks are complex (image from https://netcube.ru) 2 Example: traversal control Three subnetworks:
Firewalls Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Networks are complex (image from https://netcube.ru) 2 Example: traversal control Three subnetworks:
Technical Support Information
 Broadband Module/Broadband Module Plus Configuration Guidance Setting up Remote Access to a Network Device (Mail/File Server/Camera Etc) connected to the DMZ port of the Broadband Module where Multiple
Broadband Module/Broadband Module Plus Configuration Guidance Setting up Remote Access to a Network Device (Mail/File Server/Camera Etc) connected to the DMZ port of the Broadband Module where Multiple
Table of Contents. Cisco How NAT Works
 Table of Contents How NAT Works...1 This document contains Flash animation...1 Introduction...1 Behind the Mask...2 Dynamic NAT and Overloading Examples...5 Security and Administration...7 Multi Homing...9
Table of Contents How NAT Works...1 This document contains Flash animation...1 Introduction...1 Behind the Mask...2 Dynamic NAT and Overloading Examples...5 Security and Administration...7 Multi Homing...9
Network Address Translation. All you want to know about
 Network Address Translation All you want to know about (C) Herbert Haas 2005/03/11 Reasons for NAT Mitigate Internet address depletion Save global addresses (and money) Conserve internal address plan TCP
Network Address Translation All you want to know about (C) Herbert Haas 2005/03/11 Reasons for NAT Mitigate Internet address depletion Save global addresses (and money) Conserve internal address plan TCP
Network layer: Overview. Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing
 Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Network+ Guide to Networks
 Yarmouk University Providing Fundamental ICT Skills for Syrian Refugees (PFISR) Network+ Guide to Networks Dr. Mohammad A. Al-Jarrah jarrah@yu.edu.jo In-Depth TCP/IP Networking Understand methods of network
Yarmouk University Providing Fundamental ICT Skills for Syrian Refugees (PFISR) Network+ Guide to Networks Dr. Mohammad A. Al-Jarrah jarrah@yu.edu.jo In-Depth TCP/IP Networking Understand methods of network
Wireless LANs (CO72047) Bill Buchanan, Reader, School of Computing.
 Bill Buchanan, Reader, School of Computing. W.Buchanan (1) Lab setup W.Buchanan (2) W.Buchanan (3) Console Server Con Cisco Aironet 1200 192.168.1.100 Port 2001 Con Cisco Aironet 1200 192.168.1.100 Port
Bill Buchanan, Reader, School of Computing. W.Buchanan (1) Lab setup W.Buchanan (2) W.Buchanan (3) Console Server Con Cisco Aironet 1200 192.168.1.100 Port 2001 Con Cisco Aironet 1200 192.168.1.100 Port
Network layer: Overview. Network Layer Functions
 Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Outline. IP Address. IP Address. The Internet Protocol. o Hostname & IP Address. o The Address
 Outline IP The Internet Protocol o IP Address IP subnetting CIDR o ARP Protocol o IP Function o Fragmentation o NAT o IPv6 2 IP Address o Hostname & IP Address IP Address o The Address ping www.nu.ac.th
Outline IP The Internet Protocol o IP Address IP subnetting CIDR o ARP Protocol o IP Function o Fragmentation o NAT o IPv6 2 IP Address o Hostname & IP Address IP Address o The Address ping www.nu.ac.th
Scenario: V114 Configuration on Vyatta
 Scenario: V114 Configuration on Vyatta This section steps you through initial system configuration tasks. These are tasks that are required for almost any scenario in which you might use the V114 on the
Scenario: V114 Configuration on Vyatta This section steps you through initial system configuration tasks. These are tasks that are required for almost any scenario in which you might use the V114 on the
 Unit 5: Internet Protocols skong@itt-tech.edutech.edu Internet Protocols She occupied herself with studying a map on the opposite wall because she knew she would have to change trains at some point. Tottenham
Unit 5: Internet Protocols skong@itt-tech.edutech.edu Internet Protocols She occupied herself with studying a map on the opposite wall because she knew she would have to change trains at some point. Tottenham
RipEX Network Address and Port Translation
 Application notes. RipEX Network Address and Port Translation. version 1.0 4/12/2018 RACOM s.r.o. Mirova1283 59231 Nove MestonaMorave CzechRepublic Tel.: +420565659 511 Fax: +420565659 512 E-mail: racom@racom.eu
Application notes. RipEX Network Address and Port Translation. version 1.0 4/12/2018 RACOM s.r.o. Mirova1283 59231 Nove MestonaMorave CzechRepublic Tel.: +420565659 511 Fax: +420565659 512 E-mail: racom@racom.eu
How to Configure a Client-to-Site L2TP/IPsec VPN
 Follow the instructions in this article to configure a client-to-site L2TP/IPsec VPN. With this configuration, IPsec encrypts the payload data of the VPN because L2TP does not provide encryption. In this
Follow the instructions in this article to configure a client-to-site L2TP/IPsec VPN. With this configuration, IPsec encrypts the payload data of the VPN because L2TP does not provide encryption. In this
DEPLOYMENT GUIDE. Load Balancing VMware Unified Access Gateway
 DEPLOYMENT GUIDE Load Balancing VMware Unified Access Gateway Version History Date Version Author Description Compatible Versions Nov 2017 1.0 Matt Mabis Initial Document with How-To Configure F5 LTM with
DEPLOYMENT GUIDE Load Balancing VMware Unified Access Gateway Version History Date Version Author Description Compatible Versions Nov 2017 1.0 Matt Mabis Initial Document with How-To Configure F5 LTM with
RSA NetWitness Logs. F5 Big-IP Advanced Firewall Manager. Event Source Log Configuration Guide. Last Modified: Friday, May 12, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Advanced Firewall Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: Big-IP Advanced
RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Advanced Firewall Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: Big-IP Advanced
4. The transport layer
 4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
Advanced Security and Mobile Networks
 WJ Buchanan. ASMN (1) Advanced Security and Mobile Networks Unit 1: Network Security Application Presentation Session Transport Network Data Link Physical OSI Application Transport Internet Internet model
WJ Buchanan. ASMN (1) Advanced Security and Mobile Networks Unit 1: Network Security Application Presentation Session Transport Network Data Link Physical OSI Application Transport Internet Internet model
Zone-Based Policy Firewall High Availability
 The feature enables you to configure pairs of devices to act as backup for each other. High availability can be configured to determine the active device based on a number of failover conditions. When
The feature enables you to configure pairs of devices to act as backup for each other. High availability can be configured to determine the active device based on a number of failover conditions. When
2Wire IG 2700 ADSL Router. RJ45 connecting cable
 Technical Support Information Case 6. BT 2Wire 2700 ADSL Router (BT Business Hub) configuration to allow a BT Versatility Broadband Module (BBM) IP Gateway connection for VoIP (IP Trunks and IP Extensions)
Technical Support Information Case 6. BT 2Wire 2700 ADSL Router (BT Business Hub) configuration to allow a BT Versatility Broadband Module (BBM) IP Gateway connection for VoIP (IP Trunks and IP Extensions)
NAT (NAPT/PAT), STUN, and ICE
 NAT (NAPT/PAT), STUN, and ICE `Structure of ice II, viewed along the hexagonal c-axis. Hydrogen bonds between the water molecules are shown as dashed lines. Lengths are in angstroms.'' (Hobbs, 1970, p.
NAT (NAPT/PAT), STUN, and ICE `Structure of ice II, viewed along the hexagonal c-axis. Hydrogen bonds between the water molecules are shown as dashed lines. Lengths are in angstroms.'' (Hobbs, 1970, p.
How to Create a VPN Tunnel with the VPN GTI Editor
 How to Create a VPN Tunnel with the VPN GTI Editor VPN services on the Control Center are organized in VPN groups. Create VPN tunnels via drag and drop between two VPN services. To configure an IPv6 VPN
How to Create a VPN Tunnel with the VPN GTI Editor VPN services on the Control Center are organized in VPN groups. Create VPN tunnels via drag and drop between two VPN services. To configure an IPv6 VPN
Design and Performance of the OpenBSD Stateful Packet Filter (pf)
 Usenix 2002 p.1/22 Design and Performance of the OpenBSD Stateful Packet Filter (pf) Daniel Hartmeier dhartmei@openbsd.org Systor AG Usenix 2002 p.2/22 Introduction part of a firewall, working on IP packet
Usenix 2002 p.1/22 Design and Performance of the OpenBSD Stateful Packet Filter (pf) Daniel Hartmeier dhartmei@openbsd.org Systor AG Usenix 2002 p.2/22 Introduction part of a firewall, working on IP packet
Certification. Securing Networks
 Certification Securing Networks UNIT 9 Securing Networks 1 Objectives Explain packet filtering architecture Explain primary filtering command syntax Explain Network Address Translation Provide examples
Certification Securing Networks UNIT 9 Securing Networks 1 Objectives Explain packet filtering architecture Explain primary filtering command syntax Explain Network Address Translation Provide examples
Configuring Flood Protection
 Configuring Flood Protection NOTE: Control Plane flood protection is located on the Firewall Settings > Advanced Settings page. TIP: You must click Accept to activate any settings you select. The Firewall
Configuring Flood Protection NOTE: Control Plane flood protection is located on the Firewall Settings > Advanced Settings page. TIP: You must click Accept to activate any settings you select. The Firewall
SEN366 (SEN374) (Introduction to) Computer Networks
 SEN366 (SEN374) (Introduction to) Computer Networks Prof. Dr. Hasan Hüseyin BALIK (12 th Week) The Internet Protocol 12.Outline Principles of Internetworking Internet Protocol Operation Internet Protocol
SEN366 (SEN374) (Introduction to) Computer Networks Prof. Dr. Hasan Hüseyin BALIK (12 th Week) The Internet Protocol 12.Outline Principles of Internetworking Internet Protocol Operation Internet Protocol
Configuring IP TCP MSS
 Finding Feature Information, page 1 Feature History for IP TCP MSS, page 2 Information About IP TCP MSS, page 2 Licensing Requirements for IP TCP MSS, page 3 Default Settings for IP TCP MSS, page 3 Guidelines
Finding Feature Information, page 1 Feature History for IP TCP MSS, page 2 Information About IP TCP MSS, page 2 Licensing Requirements for IP TCP MSS, page 3 Default Settings for IP TCP MSS, page 3 Guidelines
Assignment 3 Firewalls
 LEIC/MEIC - IST Alameda LEIC/MEIC IST Taguspark Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
LEIC/MEIC - IST Alameda LEIC/MEIC IST Taguspark Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
Network Configuration Example
 Network Configuration Example Configuring Dual-Stack Lite for IPv6 Access Release NCE0025 Modified: 2016-10-12 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net
Network Configuration Example Configuring Dual-Stack Lite for IPv6 Access Release NCE0025 Modified: 2016-10-12 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net
Internet Technology 3/23/2016
 Internet Technology // Network Layer Transport Layer (Layer ) Application-to-application communication Internet Technology Network Layer (Layer ) Host-to-host communication. Network Layer Route Router
Internet Technology // Network Layer Transport Layer (Layer ) Application-to-application communication Internet Technology Network Layer (Layer ) Host-to-host communication. Network Layer Route Router
Configuration Example
 Configuration Example Use NAT for Public Access to Servers with Private IP Addresses on the Private Network Example configuration files created with WSM v11.10.1 Revised 7/21/2015 Use Case In this use
Configuration Example Use NAT for Public Access to Servers with Private IP Addresses on the Private Network Example configuration files created with WSM v11.10.1 Revised 7/21/2015 Use Case In this use
Cryptography and Network Security. Sixth Edition by William Stallings
 Cryptography and Network Security Sixth Edition by William Stallings Chapter 20 IP Security If a secret piece of news is divulged by a spy before the time is ripe, he must be put to death, together with
Cryptography and Network Security Sixth Edition by William Stallings Chapter 20 IP Security If a secret piece of news is divulged by a spy before the time is ripe, he must be put to death, together with
Internet Security Firewalls
 Overview Internet Security Firewalls Ozalp Babaoglu Cryptographic technologies Secure Sockets Layer IPSec Exo-structures Firewalls Virtual Private Networks ALMA MATER STUDIORUM UNIVERSITA DI BOLOGNA 2
Overview Internet Security Firewalls Ozalp Babaoglu Cryptographic technologies Secure Sockets Layer IPSec Exo-structures Firewalls Virtual Private Networks ALMA MATER STUDIORUM UNIVERSITA DI BOLOGNA 2
Technical Support Information
 Technical Support Information Broadband Module/Broadband Module Plus Configuration Guidance Setting up Remote Access to a Network Device (Mail/File Server/Camera Etc) connected to the DMZ port of the Broadband
Technical Support Information Broadband Module/Broadband Module Plus Configuration Guidance Setting up Remote Access to a Network Device (Mail/File Server/Camera Etc) connected to the DMZ port of the Broadband
UIP1869V User Interface Guide
 UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
Chapter 8 roadmap. Network Security
 Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Message integrity 8.4 Securing e-mail 8.5 Securing TCP connections: SSL 8.6 Network layer security: IPsec 8.7 Securing
Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Message integrity 8.4 Securing e-mail 8.5 Securing TCP connections: SSL 8.6 Network layer security: IPsec 8.7 Securing
Juniper Netscreen Security Device. How to Enable IPv6 Page-51
 Juniper Netscreen Security Device Page-51 Netscreen Firewall - Interfaces Below is a screen shot for a Netscreen Firewall interface. All interfaces have an IPv6 address except ethernet0/0. We will step
Juniper Netscreen Security Device Page-51 Netscreen Firewall - Interfaces Below is a screen shot for a Netscreen Firewall interface. All interfaces have an IPv6 address except ethernet0/0. We will step
