Basic guidelines on RouterOS configuration and debugging. Pauls Jukonis MikroTik, Latvia
|
|
|
- Cameron Lloyd
- 6 years ago
- Views:
Transcription
1 Basic guidelines on RouterOS configuration and debugging Pauls Jukonis MikroTik, Latvia Kathmandu, Nepal June 2017
2 RouterOS is the same everywhere
3 RouterOS management tools
4 RouterOS management CLI (Command Line Interface) Webfig TikApp Winbox
5 QuickSet The fastest way how to configure device
6 Simple security
7 Simple security Specify user password /user set admin password=*** Use different username /user set admin name=martins
8 Simple security Specify password for wireless access /interface wireless security-profiles set default= authentication-types=wpa2-psk mode=dynamic-keys wpa2-pre-shared-key=********
9 Simple security Disable unused interfaces /interface ethernet disable ether3,ether5,sfp1 Disable unused packages (mainly IPv6) /system package disable hotspot,ipv6,mpls,ppp,routing
10 Simple security Disable IP/Services /ip service disable api,api-ssl,ftp,www-ssl
11 Simple security Adjust MAC access /tool mac-server set [ find default=yes ] disabled=yes /tool mac-server add interface=bridge /tool mac-server mac-winbox set [ find default=yes ] disabled=yes /tool mac-server mac-winbox add interface=bridge
12 Simple security Hide device in Neighbor Discovery /ip neighbor discovery set ether1 discover=no
13 Simple security Disable serial port if not used (and if included) /system console disable [find where port=serial0] Disable LCD /lcd set enabled=no /lcd set touch-screen=disabled
14 Simple security Protect reset button /system routerboard settings set protected-routerboot=enabled reformat-holdbutton=30s der
15 Firewall
16 Firewall Two approaches Drop not trusted and allow trusted Allow trusted and drop untrusted /ip firewall filter add chain=forward action=accept src-address= outinterface=ether1 /ip firewall filter add chain=forward action=drop src-address= /24 outinterface=ether1
17 Firewall Secure input /ip firewall filter add chain=input action=accept protocol=icmp add chain=input action=accept connection-state=established,related add chain=input action=drop in-interface=ether1
18 Firewall Secure forward /ip firewall filter add chain=forward action=accept connection-state=established,related add chain=forward action=drop connection-state=invalid add chain=forward action=drop connection-state=new connection-nat-state=! dstnat in-interface=ether1
19 Firewall NAT to outside (if you can, use src-nat instead of masquerade) /ip firewall nat add chain=srcnat out-interface=ether1 action=masquerade
20 Firewall
21 Firewall NAT to LAN /ip firewall nat add chain=dstnat in-interface=ether1 protocol=tcp dst-port=22 action=dst-nat dst-address= to-address= Note: In order to make port forwarding work you have to: Have dst-nat Have src-nat Accept traffic in forward chain (example in previous slides)
22 Firewall Hairpin NAT (access local resource through public IP)
23 Firewall Block specific traffic /ip firewall address-list add list=blocked address= /ip firewall filter add chain=forward action=drop dst-address-list=blocked outinterface=ether1
24 Firewall Protect device against attacks if you allow particular access /ip firewall filter add chain=input protocol=tcp dst-port=22 src-address-list=ssh_blacklist action=drop add chain=input protocol=tcp dst-port=22 connection-state=new src-addresslist=ssh_stage2 action=add-src-to-address-list address-list=ssh_blacklist addresslist-timeout=10d add chain=input protocol=tcp dst-port=22 connection-state=new src-addresslist=ssh_stage1 action=add-src-to-address-list address-list=ssh_stage2 address-listtimeout=1m add chain=input protocol=tcp dst-port=22 connection-state=new action=add-srcto-address-list address-list=ssh_stage1 address-list-timeout=1m
25 Handle bandwidth
26 FastTrack Remember this rule? /ip firewall filter add chain=forward action=accept connection-state=established,related Add FastTrack rule before previous one /ip firewall filter add chain=forward action=fasttrack-connection connectionstate=established,related
27 Queues Add queues to limit traffic for specific resources /queue simple add name=private target= max-limit=5m/5m
28 Queues Add queues to limit traffic equally (PCQ) /queue simple add target-addresses= /24 queue=pcq-uploaddefault/pcq-download-default Few advices about queues d_users_of_routeros#queues
29 What to do when problem appears?
30 Logging Use logging for firewall /ip firewall filter set [find where src-address-list=ssh_blacklist] log=yes logprefix=blacklisted: Use logging for debug topics /system logging add topics=l2pt,debug action=memory Logging to disk or remote server /system logging action set disk disk-file-name=l2tp_logs disk-file-count=5 disk-linesper-file=1000 /system logging action set remote remote=
31 Logging
32 Debugging tools Torch Analyse processed traffic rch.29
33 Debugging tools Sniffer Analyse processed packets tool_sniffer.29
34 Debugging tools Profiler Find out current CPU usage
35 Debugging tools Graphing Find out information about Interfaces/Queues/Resources per interval:
36 Debugging tools The Dude Powerful network monitor tool:
37 Keep features and fixes up-to-date
38 Upgrade device Release candidate The most up-to-date version (hardly tested) with all possible features (also half-implemented) and fixes Current Latest full release (tested on many different scenarios for long time) with all fully implemented features Bugfix Latest full release (tested on many different scenarios for long time and admitted as trustworthy) with all safe fixes
39 Upgrade device
40 What to do when software stops working?
41 Resolve problems Backup RouterBOOT 1) Power device off, press and hold reset button 2) Power device on and after 1-2 seconds release button Netinstall 1) Test Netinstall 2) Try to re-install any other router Reset device
42 Resolve problems Serial port 1) Shows all available information (also booting) 2) Will work if problem is related to Layer2/Layer3 connectivity and/or interfaces themselves Exchange device Choose more powerful device (or multiple devices)
43 I can not figure it out by myself
44 Configuration issues Consultants/Distributors: Ask for help in forum: Look for an answer in manual
45 What to do when hardware stops working?
46 Hardware issues Replace involved accessories Power adapter PoE Cables Interfaces (SFP modules, wireless cards, etc.) Power source
47 Support
48 Software issues Configuration is not working properly Logs and supout file; Out of memory 1) Upgrade device (mandatory) 2) Reboot device and generate supout file (normal situation) 3) When RAM is almost full generate another supout file (problematic situation)
49 Support Briefly explain what has happened When it happens What did you do to make it happen Send all files (mentioned in previous slides depending on problem) Do everything what is asked, if it is possible Make notes and document results (even if problem persists) Make new files after configuration changes Reply within same ticket and provide new information
50 Feature requests? Suggestions? Thank you!
Hardening MikroTik RouterOS
 Hardening MikroTik RouterOS April 24, 2017 MUM Phnom Penh, Cambodia By Sarpich RATH (Peter) About PPIC Qualified and Vocational IT Training Center Found in late 2013. Offer service in June 2014 Partners
Hardening MikroTik RouterOS April 24, 2017 MUM Phnom Penh, Cambodia By Sarpich RATH (Peter) About PPIC Qualified and Vocational IT Training Center Found in late 2013. Offer service in June 2014 Partners
Configuring Mikrotik router with 3CX
 Configuring Mikrotik router with 3CX Presented by 4 Emina Crescent, Off Toyin Street, Ikeja, Lagos, Nigeria Instructor: Ajibola Olayemi Prepared by: Bruce Folashade Configuring MikroTik with 3CX Introduction
Configuring Mikrotik router with 3CX Presented by 4 Emina Crescent, Off Toyin Street, Ikeja, Lagos, Nigeria Instructor: Ajibola Olayemi Prepared by: Bruce Folashade Configuring MikroTik with 3CX Introduction
Most underused and overused RouterOS features. My holy war against masquerade. MUM, Europe 2017
 Most underused and overused RouterOS features OR My holy war against masquerade MUM, Europe 2017 Objectives To help you understand and diagnose most common RouterOS configurations issues Show the proper
Most underused and overused RouterOS features OR My holy war against masquerade MUM, Europe 2017 Objectives To help you understand and diagnose most common RouterOS configurations issues Show the proper
MikroTik Router Certified Network Associate (MTCNA) + Unifi Wifi Access Point (only got at CISMIC)
 MikroTik Router Certified Network Associate (MTCNA) + Unifi Wifi Access Point (only got at CISMIC) Course s Course Outline By the end of this training session, the student will be familiar with Router
MikroTik Router Certified Network Associate (MTCNA) + Unifi Wifi Access Point (only got at CISMIC) Course s Course Outline By the end of this training session, the student will be familiar with Router
Routerboard Security. Barry Higgins Allness IT. UK MuM 2018
 Routerboard Security Barry Higgins Allness IT Who am I? Barry Higgins Made a living from I.T. since 1996 Started a WISP in 2009 MikroTik consultant since 2015 Independent UK MikroTik Trainer since 2016
Routerboard Security Barry Higgins Allness IT Who am I? Barry Higgins Made a living from I.T. since 1996 Started a WISP in 2009 MikroTik consultant since 2015 Independent UK MikroTik Trainer since 2016
MikroTik Security : The Forgotten Things
 Michael Takeuchi, MTC(ALL)E, CEH MikroTik Security : The Forgotten Things 21 January 2019, Phnom Penh MikroTik User Meeting Cambodia MikroTik Certified Engineer (ALL) (MTCNA, MTCRE, MTCINE, MTCWE, MTCUME,
Michael Takeuchi, MTC(ALL)E, CEH MikroTik Security : The Forgotten Things 21 January 2019, Phnom Penh MikroTik User Meeting Cambodia MikroTik Certified Engineer (ALL) (MTCNA, MTCRE, MTCINE, MTCWE, MTCUME,
MikroTik RouterOS Training Class. MTCNA Townet Wispmax 3 Febbraio 2010
 MikroTik RouterOS Training Class MTCNA Townet Wispmax 3 Febbraio 2010 Schedule Training day: 9AM - 6PM 30 minute Breaks: 10:30AM and 4PM 1 hour Lunch: 01:00PM 2 Course Objective Overview of RouterOS software
MikroTik RouterOS Training Class MTCNA Townet Wispmax 3 Febbraio 2010 Schedule Training day: 9AM - 6PM 30 minute Breaks: 10:30AM and 4PM 1 hour Lunch: 01:00PM 2 Course Objective Overview of RouterOS software
How to Protecting your Mikrotik Router From Brutes-Force Attack. By : Teddy Yuliswar May 8, 2017 Vientiane, Laos
 How to Protecting your Mikrotik Router From Brutes-Force Attack By : Teddy Yuliswar May 8, 2017 Vientiane, Laos Where I Come From? Please visit to my hometown : Tanah Datar regency, West Sumatra Pariangan
How to Protecting your Mikrotik Router From Brutes-Force Attack By : Teddy Yuliswar May 8, 2017 Vientiane, Laos Where I Come From? Please visit to my hometown : Tanah Datar regency, West Sumatra Pariangan
Certified Network Associate (MTCNA) Riga, Latvia January 1 - January 3, 2016
 Certified Network Associate (MTCNA) Riga, Latvia January 1 - January 3, 2016 About the Trainer Name Experience Your photo 2 Course Objectives Provide an overview of RouterOS software and RouterBOARD products
Certified Network Associate (MTCNA) Riga, Latvia January 1 - January 3, 2016 About the Trainer Name Experience Your photo 2 Course Objectives Provide an overview of RouterOS software and RouterBOARD products
MUM Ho Chi Minh, Vietnam January Sao Thiên Vương - 1
 MUM Ho Chi Minh, Vietnam January 2019 Sao Thiên Vương - http://switch-router.com 1 My name: Binh Nguyen Dang Thai Email: binhndt@uranus.com.vn Cellphone: 0909006026 Working for: URANUS INFORMATION TECHNOLOGY
MUM Ho Chi Minh, Vietnam January 2019 Sao Thiên Vương - http://switch-router.com 1 My name: Binh Nguyen Dang Thai Email: binhndt@uranus.com.vn Cellphone: 0909006026 Working for: URANUS INFORMATION TECHNOLOGY
Features and usage examples of wap device
 Features and usage examples of wap device Maris Bulans MikroTik, Latvia MUM Korea June 2017 Overview l Gift from MikroTik wap l Repeater Setup l CAPsMAN overview and basic config wap Black and White edition
Features and usage examples of wap device Maris Bulans MikroTik, Latvia MUM Korea June 2017 Overview l Gift from MikroTik wap l Repeater Setup l CAPsMAN overview and basic config wap Black and White edition
MikroTik Security : Built-in Default Configuration
 MikroTik Security : Built-in Default Configuration Erick Setiawan - erick.setiawan@icloud.com - 2019 Maxindo Mitra Solusi www.maxindo.net.id Objective Explain default configuration in general and deeper
MikroTik Security : Built-in Default Configuration Erick Setiawan - erick.setiawan@icloud.com - 2019 Maxindo Mitra Solusi www.maxindo.net.id Objective Explain default configuration in general and deeper
Load Balancing and Fail-Over in Router Os
 Load Balancing and Fail-Over in Router Os Presented By Ambrose Ahurra Simplifinetworks Ltd. About Simplifinetworks Largest Mikrotik Routerboard Distributor in E/A. WiFi AP, PTP, PTMP, Security Address
Load Balancing and Fail-Over in Router Os Presented By Ambrose Ahurra Simplifinetworks Ltd. About Simplifinetworks Largest Mikrotik Routerboard Distributor in E/A. WiFi AP, PTP, PTMP, Security Address
MikroTik lifehacking. Daniel Starnowski
 MikroTik lifehacking Daniel Starnowski About me Daniel Starnowski MikroTik user since 2008 MikroTik trainer since 2011 daniel@startik.net What is lifehacking MikroTik lifehacking MikroTik live hacking
MikroTik lifehacking Daniel Starnowski About me Daniel Starnowski MikroTik user since 2008 MikroTik trainer since 2011 daniel@startik.net What is lifehacking MikroTik lifehacking MikroTik live hacking
Securing Mikrotik
 Securing Mikrotik Router @VALENSRIYADI Valens Riyadi Twitter & IG: @valensriyadi info@mikrotik.co.id MikroTik Certified Trainer Citra.net.id WISP CEO Expert on IT for Disaster Relief, Digital Forensic,
Securing Mikrotik Router @VALENSRIYADI Valens Riyadi Twitter & IG: @valensriyadi info@mikrotik.co.id MikroTik Certified Trainer Citra.net.id WISP CEO Expert on IT for Disaster Relief, Digital Forensic,
By M.Sc. I.T Alaa A. Mahdi
 University of Babylon, IT College Information Network Dep., Third Class, Second Semester MTCNA Course MikroTik Certified Network Associate 2014-2015 By M.Sc. I.T Alaa A. Mahdi Objectives Upgrade RouterOS
University of Babylon, IT College Information Network Dep., Third Class, Second Semester MTCNA Course MikroTik Certified Network Associate 2014-2015 By M.Sc. I.T Alaa A. Mahdi Objectives Upgrade RouterOS
Configuration of Access Points and Clients. Training materials for wireless trainers
 Configuration of Access Points and Clients Training materials for wireless trainers Goals To provide a simple procedure for the basic configuration of WiFi Access Points (and clients) To review the main
Configuration of Access Points and Clients Training materials for wireless trainers Goals To provide a simple procedure for the basic configuration of WiFi Access Points (and clients) To review the main
RouterOs L2 filtering
 RouterOs L2 filtering Massimo Nuvoli TRAINER #TR0368 MUM Europe 2018 Berlin Massimo Nuvoli (maxnuv) Owner of Progetto Archivio SRL and DICOBIT System Engineer System Architect 2 3 Today goals Know about
RouterOs L2 filtering Massimo Nuvoli TRAINER #TR0368 MUM Europe 2018 Berlin Massimo Nuvoli (maxnuv) Owner of Progetto Archivio SRL and DICOBIT System Engineer System Architect 2 3 Today goals Know about
Configuration of Access Points and Clients. Training materials for wireless trainers
 Configuration of Access Points and Clients Training materials for wireless trainers Goals to provide a simple procedure for the basic configuration of WiFi Access Points (and clients) to review the main
Configuration of Access Points and Clients Training materials for wireless trainers Goals to provide a simple procedure for the basic configuration of WiFi Access Points (and clients) to review the main
MikroTik RouterOS Training. Routing. Schedule. Instructors. Housekeeping. Introduce Yourself. Course Objective 7/4/ :00 10:30 Morning Session I
 MikroTik RouterOS Training Routing Schedule 09:00 10:30 Morning Session I 10:30 11:00 Morning Break 11:00 12:30 Morning Session II 12:30 13:30 Lunch Break 13:30 15:00 Afternoon Session I 15:00 15:30 Afternoon
MikroTik RouterOS Training Routing Schedule 09:00 10:30 Morning Session I 10:30 11:00 Morning Break 11:00 12:30 Morning Session II 12:30 13:30 Lunch Break 13:30 15:00 Afternoon Session I 15:00 15:30 Afternoon
Workshop Firewall Drop port scanners /ip firewall filter add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list addresslist="port
 Workshop Firewall Drop port scanners /ip firewall filter add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list addresslist="port scanners" address-list-timeout=2w comment="port scanners
Workshop Firewall Drop port scanners /ip firewall filter add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list addresslist="port scanners" address-list-timeout=2w comment="port scanners
Most underused MikroTik hardware and software features. The path between fastpath and advanced features. MUM, Mexico 2018
 Most underused MikroTik hardware and software features OR The path between fastpath and advanced features MUM, Mexico 2018 Objectives To help you understand and combine FastPath and SlowPath features.
Most underused MikroTik hardware and software features OR The path between fastpath and advanced features MUM, Mexico 2018 Objectives To help you understand and combine FastPath and SlowPath features.
RouterOS, Firewall, and Beyond: Maintain IP Reputation Over the Internet By Michael Takeuchi 20 October 2018, Yogyakarta MikroTik User Meeting
 RouterOS, Firewall, and Beyond: Maintain IP Reputation Over the Internet By Michael Takeuchi 20 October 2018, Yogyakarta MikroTik User Meeting Indonesia 2018 1 Little Things About Me Was MikroTik Certified
RouterOS, Firewall, and Beyond: Maintain IP Reputation Over the Internet By Michael Takeuchi 20 October 2018, Yogyakarta MikroTik User Meeting Indonesia 2018 1 Little Things About Me Was MikroTik Certified
Configuration of Access Points and Clients
 Configuration of Access Points and Clients Training materials for wireless trainers This talk covers the procedure of configuring APs and clients. It is intended to follow the lecture Introduction to WiFi
Configuration of Access Points and Clients Training materials for wireless trainers This talk covers the procedure of configuring APs and clients. It is intended to follow the lecture Introduction to WiFi
Fast Path, Fast Track and ISP Network Design
 Fast Path, Fast Track and ISP Network Design sekuritim.com Telefon: 0216 302 22 21 E-Mail: himmet.turkan@sekuritim.com Youtube: MikroTik Türkiye Facebook: /mikrotikturkiye Türkiye - 2018 Himmet TÜRKAN
Fast Path, Fast Track and ISP Network Design sekuritim.com Telefon: 0216 302 22 21 E-Mail: himmet.turkan@sekuritim.com Youtube: MikroTik Türkiye Facebook: /mikrotikturkiye Türkiye - 2018 Himmet TÜRKAN
Mikrotik in Network Operations in NZ - Learnings and Tricks
 Mikrotik in Network Operations in NZ - Learnings and Tricks Or How I Stopped Worrying and Learned to Love Tricks By Alexander Neilson, Network Manager Contents General Warnings Network Tricks: Triple NAT
Mikrotik in Network Operations in NZ - Learnings and Tricks Or How I Stopped Worrying and Learned to Love Tricks By Alexander Neilson, Network Manager Contents General Warnings Network Tricks: Triple NAT
Manual:IP/Firewall/Filter
 Manual:IP/Firewall/Filter 1 Manual:IP/Firewall/Filter Applies to RouterOS: v3, v4 Summary Sub-menu: /ip firewall filter The firewall implements packet filtering and thereby provides security functions
Manual:IP/Firewall/Filter 1 Manual:IP/Firewall/Filter Applies to RouterOS: v3, v4 Summary Sub-menu: /ip firewall filter The firewall implements packet filtering and thereby provides security functions
Firewall and QoS in Enterprise Network
 Firewall and QoS in Enterprise Network www.trisat com.net About Me Abiola Oseni CEO, Trisat Communications Limited, Nigeria Using Mikrotik RouterOS since 2005 Mikrotik Certified Consultant since 2007 Mikrotik
Firewall and QoS in Enterprise Network www.trisat com.net About Me Abiola Oseni CEO, Trisat Communications Limited, Nigeria Using Mikrotik RouterOS since 2005 Mikrotik Certified Consultant since 2007 Mikrotik
TCP 135. /ip firewall filter add chain=forward dst-port=135 protocol=tcp action=drop
 Filter Document revision 2.7 (Fri Nov 04 16:04:37 GMT 2005) This document applies to V2.9 Table of Contents Table of Contents Summary Quick Setup Guide Specifications Related Documents Firewall Filter
Filter Document revision 2.7 (Fri Nov 04 16:04:37 GMT 2005) This document applies to V2.9 Table of Contents Table of Contents Summary Quick Setup Guide Specifications Related Documents Firewall Filter
MikroTik RouterOS v3. New Obvious and Obscure Mikrotik RouterOS v3.0 features
 MikroTik RouterOS v3 New Obvious and Obscure Mikrotik RouterOS v3.0 features MikroTik RouterOS 2007 Kernel RouterOS 2.9.39 Linux kernel version 2.4.31 RouterOS 3.0beta5 Linux kernel version 2.6.19 For
MikroTik RouterOS v3 New Obvious and Obscure Mikrotik RouterOS v3.0 features MikroTik RouterOS 2007 Kernel RouterOS 2.9.39 Linux kernel version 2.4.31 RouterOS 3.0beta5 Linux kernel version 2.6.19 For
MikroTik RouterOS v3. New Obvious and Obscure Mikrotik RouterOS v3.0 features
 MikroTik RouterOS v3 New Obvious and Obscure Mikrotik RouterOS v3.0 features MikroTik RouterOS 2007 Kernel RouterOS 2.9.43 Linux kernel version 2.4.31 RouterOS 3.0beta8 Linux kernel version 2.6.20 For
MikroTik RouterOS v3 New Obvious and Obscure Mikrotik RouterOS v3.0 features MikroTik RouterOS 2007 Kernel RouterOS 2.9.43 Linux kernel version 2.4.31 RouterOS 3.0beta8 Linux kernel version 2.6.20 For
RouterBOARD 751 series
 RouterBOARD 751 series User's Manual Copyright and Warranty Information Copyright and Trademarks. Copyright MikroTikls SIA. This manual contains information protected by copyright law. No part of it may
RouterBOARD 751 series User's Manual Copyright and Warranty Information Copyright and Trademarks. Copyright MikroTikls SIA. This manual contains information protected by copyright law. No part of it may
Security in an IPv6 World Myth & Reality
 Security in an IPv6 World Myth & Reality DGI Washington D.C. August 2014 Chris Grundemann MYTH: IPv6 Has Security Designed In MYTH: IPv6 Has Security Designed In IPSEC IS NOT NEW IPsec exists for IPv4
Security in an IPv6 World Myth & Reality DGI Washington D.C. August 2014 Chris Grundemann MYTH: IPv6 Has Security Designed In MYTH: IPv6 Has Security Designed In IPSEC IS NOT NEW IPsec exists for IPv4
/ip firewall filter add chain=forward dst-port=135 protocol=tcp action=drop. /ip firewall filter add chain=input protocol=tcp dst-port=23 action=drop
 Filter Document revision 2.8 (February 11, 2008, 4:14 GMT) This document applies to V3.0 Table of Contents Table of Contents Summary Quick Setup Guide Specifications Firewall Filter Description Property
Filter Document revision 2.8 (February 11, 2008, 4:14 GMT) This document applies to V3.0 Table of Contents Table of Contents Summary Quick Setup Guide Specifications Firewall Filter Description Property
By M.Sc. I.T AlaaA. Mahdi
 University of Babylon, IT College Information Network Dep., Third Class, Second Semester MTCNA Course MikroTik Certified Network Associate 2015-2016 By M.Sc. I.T AlaaA. Mahdi Objectives Upgrade RouterOS;
University of Babylon, IT College Information Network Dep., Third Class, Second Semester MTCNA Course MikroTik Certified Network Associate 2015-2016 By M.Sc. I.T AlaaA. Mahdi Objectives Upgrade RouterOS;
Basic MikroTik Router s Security. Tsoft IT 1
 Tsoft IT 1 Presented by: Titas Sarker Founder (Tsoft IT) System administrator (Enosis Solutions) Certificates:(MTCNA,MTCRE,RHCE) 2 Agenda LCMC Reason for security 04 Page no How to secure our network?
Tsoft IT 1 Presented by: Titas Sarker Founder (Tsoft IT) System administrator (Enosis Solutions) Certificates:(MTCNA,MTCRE,RHCE) 2 Agenda LCMC Reason for security 04 Page no How to secure our network?
2017/05/12 20:51 1/11 Mikrotik -> Basic
 2017/05/12 20:51 1/11 Mikrotik -> Basic Mikrotik -> Basic Introduction With this scenario we assume you have: A recent installation of RADIUSdesk which includes Dynamic RADIUS Clients support. We will
2017/05/12 20:51 1/11 Mikrotik -> Basic Mikrotik -> Basic Introduction With this scenario we assume you have: A recent installation of RADIUSdesk which includes Dynamic RADIUS Clients support. We will
MikroTik SwOS Basic VLAN Configuration
 MikroTik SwOS Basic VLAN Configuration By : Adhie Lesmana Manila, Philippines January 16, 2018 Speaker Profile Adhie Lesmana MTCNA, MTCWE, MTCTCE, MTCRE, MTCINE PowerNet Liberia, West Africa Technical
MikroTik SwOS Basic VLAN Configuration By : Adhie Lesmana Manila, Philippines January 16, 2018 Speaker Profile Adhie Lesmana MTCNA, MTCWE, MTCTCE, MTCRE, MTCINE PowerNet Liberia, West Africa Technical
KRAUSS INTERNATIONAL. Firewall for ISP/TSP/OSPs
 KRAUSS INTERNATIONAL CALL FOR SALES: 9717387778 / 9910416231 EMAIL: SALES@KC-INDIA.COM Firewall for ISP/TSP/OSPs PRESENTED BY MANKOMAL SINGH (KRAUSS INTERNATIONAL) About the speaker! Has been a student(yes
KRAUSS INTERNATIONAL CALL FOR SALES: 9717387778 / 9910416231 EMAIL: SALES@KC-INDIA.COM Firewall for ISP/TSP/OSPs PRESENTED BY MANKOMAL SINGH (KRAUSS INTERNATIONAL) About the speaker! Has been a student(yes
MikroTik RouterOS Training User Management. VRProService Co.,Ltd.
 MikroTik RouterOS Training User Management VRProService Co.,Ltd. Class Setup VRProService Co.,Ltd. 2 Class setup Lab (cont.) Set system identity of the board and wireless radio name to XY_.
MikroTik RouterOS Training User Management VRProService Co.,Ltd. Class Setup VRProService Co.,Ltd. 2 Class setup Lab (cont.) Set system identity of the board and wireless radio name to XY_.
WELCOME TO MUM INDIA 2015 TARA CONSULTANTS PVT LTD
 WELCOME TO TARA CONSULTANTS PVT LTD WELCOME TO About Us Tara Consultants Pvt Ltd, a multi-faceted and multi-activity Group, a trusted name in developing Mass Marketing Concepts, Software Development. Networking
WELCOME TO TARA CONSULTANTS PVT LTD WELCOME TO About Us Tara Consultants Pvt Ltd, a multi-faceted and multi-activity Group, a trusted name in developing Mass Marketing Concepts, Software Development. Networking
MIKROTIK ROUTER SETUP USERS MANUAL
 14 November, 2017 MIKROTIK ROUTER SETUP USERS MANUAL Document Filetype: PDF 110.52 KB 0 MIKROTIK ROUTER SETUP USERS MANUAL Detailed step-by-step instructions and screenshots are included to make your MIKROTIK
14 November, 2017 MIKROTIK ROUTER SETUP USERS MANUAL Document Filetype: PDF 110.52 KB 0 MIKROTIK ROUTER SETUP USERS MANUAL Detailed step-by-step instructions and screenshots are included to make your MIKROTIK
MikroTik User Meeting
 MikroTik User Meeting More than 80 MUM events MikroTik MikroTik is located in Latvia (Europe) More than 150 employees Established 1996 RouterOS created in 1997 RouterBOARD created in 2002 First MUM in
MikroTik User Meeting More than 80 MUM events MikroTik MikroTik is located in Latvia (Europe) More than 150 employees Established 1996 RouterOS created in 1997 RouterBOARD created in 2002 First MUM in
Bienvenue au CAMEROUN
 Bienvenue au CAMEROUN MikroTik FIREWALL ET GESTION DE BANDE PASSANTE M i k r o t i k M U M Y a o u n d é J a n u a r y 2 6, 2 0 1 8 MikroTik FIREWALL AND BANDWIDTH MANAGEMENT M i k r o t i k M U M Y a
Bienvenue au CAMEROUN MikroTik FIREWALL ET GESTION DE BANDE PASSANTE M i k r o t i k M U M Y a o u n d é J a n u a r y 2 6, 2 0 1 8 MikroTik FIREWALL AND BANDWIDTH MANAGEMENT M i k r o t i k M U M Y a
SECURITY IN AN IPv6 WORLD MYTH & REALITY. RIPE 68 Warsaw May 2014 Chris Grundemann
 SECURITY IN AN IPv6 WORLD MYTH & REALITY RIPE 68 Warsaw May 2014 Chris Grundemann WHO AM I? DO Director @ Internet Society CO ISOC Founding Chair RMv6TF Board NANOG PC NANOG-BCOP Chair IPv6 Author (Juniper
SECURITY IN AN IPv6 WORLD MYTH & REALITY RIPE 68 Warsaw May 2014 Chris Grundemann WHO AM I? DO Director @ Internet Society CO ISOC Founding Chair RMv6TF Board NANOG PC NANOG-BCOP Chair IPv6 Author (Juniper
MikroTik, A Router for Today & Tomorrow
 MikroTik, A Router for Today & Tomorrow By- Md. Shaqul Hasan hasan@aitlbd.com Aftab IT Limited MUM Bangladesh 2016 Routing The World Millions of RouterOS powered devices currently routing the world MikroTik
MikroTik, A Router for Today & Tomorrow By- Md. Shaqul Hasan hasan@aitlbd.com Aftab IT Limited MUM Bangladesh 2016 Routing The World Millions of RouterOS powered devices currently routing the world MikroTik
LevelOne. Quick Installation Guide. WHG series Secure WLAN Controller. Introduction. Getting Started. Hardware Installation
 Introduction LevelOne WHG series Secure WLAN Controller LevelOne Secure WLAN Controller is the most advanced yet simple deployment and cost-effective wireless solution; it is an ideal security solution
Introduction LevelOne WHG series Secure WLAN Controller LevelOne Secure WLAN Controller is the most advanced yet simple deployment and cost-effective wireless solution; it is an ideal security solution
MikroTik SwOS Basic VLAN Configuration
 MikroTik SwOS Basic VLAN Configuration By : Adhie Lesmana Nairobi, Kenya January 30, 2018 Speaker Profile Adhie Lesmana MTCNA, MTCWE, MTCTCE, MTCRE, MTCINE PowerNet Liberia, West Africa Technical & Operation
MikroTik SwOS Basic VLAN Configuration By : Adhie Lesmana Nairobi, Kenya January 30, 2018 Speaker Profile Adhie Lesmana MTCNA, MTCWE, MTCTCE, MTCRE, MTCINE PowerNet Liberia, West Africa Technical & Operation
Routeros Firewall Mikrotik
 Routeros Firewall Mikrotik 1 / 6 2 / 6 3 / 6 Routeros Firewall Mikrotik Miscellaneous. Zone Based Firewall - ZBF; Basic universal firewall script; Attempt To Detect And Block Bad Hosts; Securing A New
Routeros Firewall Mikrotik 1 / 6 2 / 6 3 / 6 Routeros Firewall Mikrotik Miscellaneous. Zone Based Firewall - ZBF; Basic universal firewall script; Attempt To Detect And Block Bad Hosts; Securing A New
Configuring your MikroTik as a Standard LucidView Enforcer
 MANUAL Configuring your MikroTik as a Standard LucidView Enforcer Version 6 Table of Contents STANDARD LUCIDVIEW ENFORCER 2 Guide version 2 About 2 Standard vs. Bolt-On Enforcer 2 GENERATING & DOWNLOADING
MANUAL Configuring your MikroTik as a Standard LucidView Enforcer Version 6 Table of Contents STANDARD LUCIDVIEW ENFORCER 2 Guide version 2 About 2 Standard vs. Bolt-On Enforcer 2 GENERATING & DOWNLOADING
Quick Start Guide for Standalone EAP
 Quick Start Guide for Standalone EAP CHAPTERS 1. Determine the Management Method 2. Build the Network Topology 3. Log In to the EAP 4. Edit the SSID 5. Configure and Manage the EAP This guide applies to:
Quick Start Guide for Standalone EAP CHAPTERS 1. Determine the Management Method 2. Build the Network Topology 3. Log In to the EAP 4. Edit the SSID 5. Configure and Manage the EAP This guide applies to:
Encapto WiFi. Integration Guide. Mikrotik Routerboard Provisioning. For Release and above Document Version 7 PUBLIC DOCUMENT
 Encapto WiFi Integration Guide Mikrotik Routerboard Provisioning For Release 1.3.1 and above Document Version 7 PUBLIC DOCUMENT Contents 1. What you will need 3 2. Firewall configuration 4 3. Connecting
Encapto WiFi Integration Guide Mikrotik Routerboard Provisioning For Release 1.3.1 and above Document Version 7 PUBLIC DOCUMENT Contents 1. What you will need 3 2. Firewall configuration 4 3. Connecting
WITELCOM USER MANUAL WISE-1200
 WITELCOM USER MANUAL WISE-1200 Remote Administration Configuration Management General Information Summary This manual introduces you with commands which are used to perform the following functions: system
WITELCOM USER MANUAL WISE-1200 Remote Administration Configuration Management General Information Summary This manual introduces you with commands which are used to perform the following functions: system
Juniper Netscreen Security Device. How to Enable IPv6 Page-51
 Juniper Netscreen Security Device Page-51 Netscreen Firewall - Interfaces Below is a screen shot for a Netscreen Firewall interface. All interfaces have an IPv6 address except ethernet0/0. We will step
Juniper Netscreen Security Device Page-51 Netscreen Firewall - Interfaces Below is a screen shot for a Netscreen Firewall interface. All interfaces have an IPv6 address except ethernet0/0. We will step
Configuring Failover. Understanding Failover CHAPTER
 CHAPTER 14 This chapter describes the security appliance failover feature, which lets you configure two security appliances so that one takes over operation if the other one fails. The ASA 5505 series
CHAPTER 14 This chapter describes the security appliance failover feature, which lets you configure two security appliances so that one takes over operation if the other one fails. The ASA 5505 series
Questions and Answers
 Questins and Answers 1. Actin = Redirect is applied in A. Chain=srcnat B. Chain=dstnat C. Chain=fward 2. Chse all valid hsts address range fr subnet 15.242.55.62/27 A. 15.242.55.31-15.242.55.62 B. 15.242.55.32-15.242.55.63
Questins and Answers 1. Actin = Redirect is applied in A. Chain=srcnat B. Chain=dstnat C. Chain=fward 2. Chse all valid hsts address range fr subnet 15.242.55.62/27 A. 15.242.55.31-15.242.55.62 B. 15.242.55.32-15.242.55.63
Deep-dive: IPSec & Xauth mode-config. Your guide to IPSec and VPNs
 Deep-dive: IPSec & Xauth mode-config Your guide to IPSec and VPNs Presenter information Tomas Kirnak System Architect Automation & Monitoring MikroTik Certified Trainer MikroTik Certified Consultant About
Deep-dive: IPSec & Xauth mode-config Your guide to IPSec and VPNs Presenter information Tomas Kirnak System Architect Automation & Monitoring MikroTik Certified Trainer MikroTik Certified Consultant About
Grandstream Networks, Inc. GWN7000 Command Line Guide
 Grandstream Networks, Inc. Table of Contents INTRODUCTION... 3 CONNECTING AND ACCESSING THE GWN7XXX... 4 Connecting the GWN7000... 4 SSH Access... 5 USING THE CLI MENU... 6 Menu Structure And Navigation...
Grandstream Networks, Inc. Table of Contents INTRODUCTION... 3 CONNECTING AND ACCESSING THE GWN7XXX... 4 Connecting the GWN7000... 4 SSH Access... 5 USING THE CLI MENU... 6 Menu Structure And Navigation...
MAC Address Filtering Setup (3G18Wn)
 MAC Address Filtering Setup (3G18Wn) MAC Address Filtering MAC address filtering refers to the process of allowing (or denying) access to your wireless network based on the hardware address of the device
MAC Address Filtering Setup (3G18Wn) MAC Address Filtering MAC address filtering refers to the process of allowing (or denying) access to your wireless network based on the hardware address of the device
Hello! My name is Karl Auer. I'm with Into6. But today is about MikroTik. - and about networking Into6 (
 Hello! My name is Karl Auer I'm with Into6 But today is about MikroTik - and about networking... 2013 Into6 (www.into6.com.au) Slide #1 Latvian company; www.mikrotik.com Started in 1995, manufacturer since
Hello! My name is Karl Auer I'm with Into6 But today is about MikroTik - and about networking... 2013 Into6 (www.into6.com.au) Slide #1 Latvian company; www.mikrotik.com Started in 1995, manufacturer since
Enterprise wireless with CAPsMAN and Windows NPS. Rein Põdra Trainer / Consultant Berlin 2018
 Enterprise wireless with CAPsMAN and Windows NPS Rein Põdra Trainer / Consultant rein.podra@ccisrd.eu Berlin 2018 Wireless security Open wireless - no security at all. WEP - minimal security. (Deprecated)
Enterprise wireless with CAPsMAN and Windows NPS Rein Põdra Trainer / Consultant rein.podra@ccisrd.eu Berlin 2018 Wireless security Open wireless - no security at all. WEP - minimal security. (Deprecated)
New Features and Updates in RouterOS
 New Features and Updates in RouterOS About MikroTik SA Independent Network Specialist company Not owned by / affiliated to MikroTik Latvia Official training and support partner for MikroTik Specialist
New Features and Updates in RouterOS About MikroTik SA Independent Network Specialist company Not owned by / affiliated to MikroTik Latvia Official training and support partner for MikroTik Specialist
Using Diagnostic Tools
 Using Diagnostic Tools The Tools System Diagnostics page on the INVESTIGATE view provides several diagnostic tools that help troubleshoot various kinds of network problems and process monitors. Tech Support
Using Diagnostic Tools The Tools System Diagnostics page on the INVESTIGATE view provides several diagnostic tools that help troubleshoot various kinds of network problems and process monitors. Tech Support
Managing Standalone EAP
 CHAPTERS 1. Manage System Logs 2. Configure Web Server 3. Configure Management Access 4. Configure Trunk (For EAP330) 5. Configure LED 6. Configure PoE (For EAP225-Wall) 7. Configure SSH 8. Configure Management
CHAPTERS 1. Manage System Logs 2. Configure Web Server 3. Configure Management Access 4. Configure Trunk (For EAP330) 5. Configure LED 6. Configure PoE (For EAP225-Wall) 7. Configure SSH 8. Configure Management
Manual:Interface/Bridge - MikroTik Wiki
 1 of 14 3/22/2015 11:57 AM Manual:Interface/Bridge From MikroTik Wiki < Manual:Interface Summary Ethernet-like networks (Ethernet, Ethernet over IP, IEEE802.11 in ap-bridge or bridge mode, WDS, VLAN) can
1 of 14 3/22/2015 11:57 AM Manual:Interface/Bridge From MikroTik Wiki < Manual:Interface Summary Ethernet-like networks (Ethernet, Ethernet over IP, IEEE802.11 in ap-bridge or bridge mode, WDS, VLAN) can
Logical Connectivity Diagrams
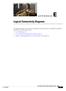 APPENDIXE This appendix provides logical connectivity diagrams and related software commands for integrated controllers. It contains these sections: Cisco WiSM, page E-3 Cisco 28/37/38xx Integrated Services
APPENDIXE This appendix provides logical connectivity diagrams and related software commands for integrated controllers. It contains these sections: Cisco WiSM, page E-3 Cisco 28/37/38xx Integrated Services
Security SSID Selection: Broadcast SSID:
 69 Security SSID Selection: Broadcast SSID: WMM: Encryption: Select the SSID that the security settings will apply to. If Disabled, then the device will not be broadcasting the SSID. Therefore it will
69 Security SSID Selection: Broadcast SSID: WMM: Encryption: Select the SSID that the security settings will apply to. If Disabled, then the device will not be broadcasting the SSID. Therefore it will
MikroWall Hotspot Router and Firewall System
 MikroWall Hotspot Router and Firewall System Installation and configuration guide Contents: 1.0 The Device:...2 1.1 The MikroWall Wireless...2 1.2 MikroWall Standard...2 2.0 Installation...2 2.1 Before
MikroWall Hotspot Router and Firewall System Installation and configuration guide Contents: 1.0 The Device:...2 1.1 The MikroWall Wireless...2 1.2 MikroWall Standard...2 2.0 Installation...2 2.1 Before
Bhaukaal Baba Technologies Pvt. Ltd.
 Bhaukaal Baba Technologies Pvt. Ltd. www.bhaukaalbaba.com About Bhaukaal Baba ITIL certified IT Resources and Network management and monitoring solutions Integrated Services and Solutions Provider Network
Bhaukaal Baba Technologies Pvt. Ltd. www.bhaukaalbaba.com About Bhaukaal Baba ITIL certified IT Resources and Network management and monitoring solutions Integrated Services and Solutions Provider Network
Configuring General Settings for the EN-4000
 EN-4000 Reference Manual Document 4 Configuring General Settings for the EN-4000 T he EN-4000 is the newest member of Encore Networks family of routers. It provides wireless and cabled connections to a
EN-4000 Reference Manual Document 4 Configuring General Settings for the EN-4000 T he EN-4000 is the newest member of Encore Networks family of routers. It provides wireless and cabled connections to a
Configuring High Availability (HA)
 4 CHAPTER This chapter covers the following topics: Adding High Availability Cisco NAC Appliance To Your Network, page 4-1 Installing a Clean Access Manager High Availability Pair, page 4-3 Installing
4 CHAPTER This chapter covers the following topics: Adding High Availability Cisco NAC Appliance To Your Network, page 4-1 Installing a Clean Access Manager High Availability Pair, page 4-3 Installing
CRS328 as a Layer 2 Switch UK MUM 2018
 CRS328 as a Layer 2 Switch UK MUM 2018 Oct 2018 Jono Thompson BirchenallHowden Ltd Jono Thompson Networking background started as a Cisco Engineer Started using ROS June 2010 MikroTik Consultant Since
CRS328 as a Layer 2 Switch UK MUM 2018 Oct 2018 Jono Thompson BirchenallHowden Ltd Jono Thompson Networking background started as a Cisco Engineer Started using ROS June 2010 MikroTik Consultant Since
Copyright Link Technologies, Inc.
 3/15/2011 Mikrotik Certified Trainer / Engineer MikroTik Certified Dude Consultant Consulting Since 1997 Enterprise Class Networks WAN Connectivity Certifications Cisco, Microsoft, MikroTik BGP/OSPF Experience
3/15/2011 Mikrotik Certified Trainer / Engineer MikroTik Certified Dude Consultant Consulting Since 1997 Enterprise Class Networks WAN Connectivity Certifications Cisco, Microsoft, MikroTik BGP/OSPF Experience
Interconnecting Cisco Networking Devices Part 1 ICND1
 Interconnecting Cisco Networking Devices Part 1 ICND1 Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco Networking Devices, Part 1 (ICND1) v3.0
Interconnecting Cisco Networking Devices Part 1 ICND1 Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco Networking Devices, Part 1 (ICND1) v3.0
Click on Close button to close Network Connection Details. You are back to the Local Area Connection Status window.
 How to configure EW-7228APn/EW-7416APn as a Repeater to extend wireless range This article can apply on EW-7228APn and EW-7416APn. We used screen shots of EW-7416APn in this instruction. We recommend you
How to configure EW-7228APn/EW-7416APn as a Repeater to extend wireless range This article can apply on EW-7228APn and EW-7416APn. We used screen shots of EW-7416APn in this instruction. We recommend you
Mikrotik Automation using Scripting, SSH, & API. Ahmad Rosid Komarudin, TR0574 Network Engineer & Trainer, ID-Networkers
 Mikrotik Automation using Scripting, SSH, & API Ahmad Rosid Komarudin, TR0574 Network Engineer & Trainer, ID-Networkers Introduction About ID-Networkers www.idn.id info@idn.id About SMP & SMK IDN About
Mikrotik Automation using Scripting, SSH, & API Ahmad Rosid Komarudin, TR0574 Network Engineer & Trainer, ID-Networkers Introduction About ID-Networkers www.idn.id info@idn.id About SMP & SMK IDN About
LevelOne. User Manual. WAP Mbps PoE Wireless AP V3.0.0
 LevelOne WAP-0005 108Mbps PoE Wireless AP User Manual V3.0.0 i TABLE OF CONTENTS CHAPTER 1 INTRODUCTION... 1 FIGURE 1: WIRELESS ACCESS POINT... 1 FEATURES OF YOUR WIRELESS ACCESS POINT... 1 Security Features...
LevelOne WAP-0005 108Mbps PoE Wireless AP User Manual V3.0.0 i TABLE OF CONTENTS CHAPTER 1 INTRODUCTION... 1 FIGURE 1: WIRELESS ACCESS POINT... 1 FEATURES OF YOUR WIRELESS ACCESS POINT... 1 Security Features...
Troubleshooting. General Troubleshooting Information
 General Information, page 1 Startup s, page 3 Phone Reset s, page 7 Phone Cannot Connect to LAN, page 9 Cisco IP Phone Security s, page 9 Video Call s, page 11 General Telephone Call s, page 12 Procedures,
General Information, page 1 Startup s, page 3 Phone Reset s, page 7 Phone Cannot Connect to LAN, page 9 Cisco IP Phone Security s, page 9 Video Call s, page 11 General Telephone Call s, page 12 Procedures,
How to configure a Point-to-Point link
 How to configure a Point-to-Point link SilverNet equipment comes Pre-configured on IP addresses 192.168.0.229 or 192.168.0.228. There may be some instances where you need to reset the unit or the unit
How to configure a Point-to-Point link SilverNet equipment comes Pre-configured on IP addresses 192.168.0.229 or 192.168.0.228. There may be some instances where you need to reset the unit or the unit
Peplink SD Switch User Manual. Published on October 25th, 2018
 Peplink SD Switch User Manual Published on October 25th, 2018 1 Table of Contents Switch Layout 4 Specifications 5 Hardware Overview 6 Quick Start Functions 7 Reset Switch 7 Connect Ethernet 7 Connect
Peplink SD Switch User Manual Published on October 25th, 2018 1 Table of Contents Switch Layout 4 Specifications 5 Hardware Overview 6 Quick Start Functions 7 Reset Switch 7 Connect Ethernet 7 Connect
VLAN & Wireless Infrastructure
 VLAN & Wireless Infrastructure VLAN tagged over Wireless Uplink (PtMP) & CAPsMAN (Layer 3) Who am I? Sun Sopheary Email: sunsopheary@gmail.com Mobile phone: 012779158 IT Manager at Angkor Hospital for
VLAN & Wireless Infrastructure VLAN tagged over Wireless Uplink (PtMP) & CAPsMAN (Layer 3) Who am I? Sun Sopheary Email: sunsopheary@gmail.com Mobile phone: 012779158 IT Manager at Angkor Hospital for
Configuring OfficeExtend Access Points
 Information About OfficeExtend Access Points, page 1 OEAP 600 Series Access Points, page 2 OEAP in Local Mode, page 3 Supported WLAN Settings for 600 Series OfficeExtend Access Point, page 3 WLAN Security
Information About OfficeExtend Access Points, page 1 OEAP 600 Series Access Points, page 2 OEAP in Local Mode, page 3 Supported WLAN Settings for 600 Series OfficeExtend Access Point, page 3 WLAN Security
PSGS-2610F L2+ Managed GbE PoE Switch
 PSGS-2610F L2+ Managed GbE PoE Switch Overview PSGS-2610F L2+ Managed PoE+ Switch is a next-generation Ethernet Switch offering full suite of L2 features, better PoE functionality and usability, including
PSGS-2610F L2+ Managed GbE PoE Switch Overview PSGS-2610F L2+ Managed PoE+ Switch is a next-generation Ethernet Switch offering full suite of L2 features, better PoE functionality and usability, including
Example: Configuring DHCP Snooping and DAI to Protect the Switch from ARP Spoofing Attacks
 Example: Configuring DHCP Snooping and DAI to Protect the Switch from ARP Spoofing Attacks In an ARP spoofing attack, the attacker associates its own MAC address with the IP address of a network device
Example: Configuring DHCP Snooping and DAI to Protect the Switch from ARP Spoofing Attacks In an ARP spoofing attack, the attacker associates its own MAC address with the IP address of a network device
Quality of Service Setup Guide (NB14 Series)
 Quality of Service Setup Guide (NB14 Series) About This Quality of Service (QoS) Guide Quality of Service refers to the reservation of bandwidth resources on the Nb14 Series router to provide different
Quality of Service Setup Guide (NB14 Series) About This Quality of Service (QoS) Guide Quality of Service refers to the reservation of bandwidth resources on the Nb14 Series router to provide different
User Meeting. Beirut, Lebanon June 2016
 User Meeting Beirut, Lebanon June 2016 Established 1996 RouterOS created in 1997 RouterBOARD created in 2002 First MUM event in Prague 2006 Biggest MUM in 2015, Indonesia - 2600+ people More than 170 employees
User Meeting Beirut, Lebanon June 2016 Established 1996 RouterOS created in 1997 RouterBOARD created in 2002 First MUM event in Prague 2006 Biggest MUM in 2015, Indonesia - 2600+ people More than 170 employees
Quick Setup Guide. for Standalone Omada Access Points. EAP110 / EAP115 / EAP225 / EAP245 / EAP320 / EAP330 / EAP115-Wall
 Quick Setup Guide for Standalone Omada Access Points EAP110 / EAP115 / EAP225 / EAP245 / EAP320 / EAP330 / EAP115-Wall EAP110-Outdoor / EAP225-Outdoor / EAP225-Wall 1910012420 REV1.0.1 May 2018 Omada EAP
Quick Setup Guide for Standalone Omada Access Points EAP110 / EAP115 / EAP225 / EAP245 / EAP320 / EAP330 / EAP115-Wall EAP110-Outdoor / EAP225-Outdoor / EAP225-Wall 1910012420 REV1.0.1 May 2018 Omada EAP
How to configure a Point-to-Multipoint link
 How to configure a Point-to-Multipoint link SilverNet equipment comes Pre-configured on IP addresses 192.168.0.229 or 192.168.0.228. There may be some instances where you need to reset the unit or the
How to configure a Point-to-Multipoint link SilverNet equipment comes Pre-configured on IP addresses 192.168.0.229 or 192.168.0.228. There may be some instances where you need to reset the unit or the
User Meeting. Portugal, Lisbon May 2016
 User Meeting Portugal, Lisbon May 2016 Established 1996 More than 160 employees RouterOS created in 1997 RouterBOARD created in 2002 First MUM event in Prague 2006 Biggest MUM in 2015, Indonesia 2600+
User Meeting Portugal, Lisbon May 2016 Established 1996 More than 160 employees RouterOS created in 1997 RouterBOARD created in 2002 First MUM event in Prague 2006 Biggest MUM in 2015, Indonesia 2600+
Wireless and Wired Bridging using Vlan.
 Wireless and Wired Bridging using Vlan. (A case study at Electrical Engineering UBAYA). MUM Yogyakarta 19-20 Oct 2018 1 Topics of Discussion Virtual LAN (VLAN) Wired and Wireless Trunk System (Bridge,
Wireless and Wired Bridging using Vlan. (A case study at Electrical Engineering UBAYA). MUM Yogyakarta 19-20 Oct 2018 1 Topics of Discussion Virtual LAN (VLAN) Wired and Wireless Trunk System (Bridge,
Package Management...23 General Information Installation (Upgrade)...24 Uninstal 25 Downg26 Software Package List...26
 Wandy RouterOS v2.8 Reference Manual - Written by Mikrotik - Table Of Contents Basic Setup Guide... 1 General Information... 1 Setting up Wandy RouterOS... 2 Logging into the Wandy Router...5 Adding Software
Wandy RouterOS v2.8 Reference Manual - Written by Mikrotik - Table Of Contents Basic Setup Guide... 1 General Information... 1 Setting up Wandy RouterOS... 2 Logging into the Wandy Router...5 Adding Software
On the left hand side of the screen, click on Setup Wizard and go through the Wizard.
 Q: How do I configure the TEW-435/504BRM (b1) to a DSL, PPPoE connection? A: Step 1 Open your web browser and type the IP address of the TEW-435/504BRM in the address bar. The default IP address is 192.168.0.1.
Q: How do I configure the TEW-435/504BRM (b1) to a DSL, PPPoE connection? A: Step 1 Open your web browser and type the IP address of the TEW-435/504BRM in the address bar. The default IP address is 192.168.0.1.
Certified Cisco Networking Associate v1.1 ( )
 Certified Cisco Networking Associate v1.1 (640-802) Exam Description: The Cisco Certified Networking Associate v1.1 640-802 is the composite exam that is associated with Cisco CCNA Routing and Switching
Certified Cisco Networking Associate v1.1 (640-802) Exam Description: The Cisco Certified Networking Associate v1.1 640-802 is the composite exam that is associated with Cisco CCNA Routing and Switching
Step 5: Plug the power adaptor into the PWR socket on the back of the modem. Plug the other end of the power adaptor into the wall socket.
 Before you start You will need your username and password from ISP. All devices on your phone line will need to have an ADSL line filter attached to them. This includes Telephones, Fax Machines, and Dial-up
Before you start You will need your username and password from ISP. All devices on your phone line will need to have an ADSL line filter attached to them. This includes Telephones, Fax Machines, and Dial-up
PPP Tunneling. Step by step explanation and configuration for creating PPP Tunnel
 PPP Tunneling Step by step explanation and configuration for creating PPP Tunnel 1 Point-to-Point Protocol Point-to-Point Protocol (PPP) is used to establish a tunnel (direct connection) between two nodes.
PPP Tunneling Step by step explanation and configuration for creating PPP Tunnel 1 Point-to-Point Protocol Point-to-Point Protocol (PPP) is used to establish a tunnel (direct connection) between two nodes.
LAPAC1200. AC1200 Dual Band Access Point. User's Guide
 LAPAC1200 AC1200 Dual Band Access Point User's Guide TABLE OF CONTENTS CHAPTER 1 QUICK START GUIDE... 1 Package Contents... 1 Physical Details... 1 Mounting Guide... 3 CHAPTER 2 ACCESS POINT SETUP...
LAPAC1200 AC1200 Dual Band Access Point User's Guide TABLE OF CONTENTS CHAPTER 1 QUICK START GUIDE... 1 Package Contents... 1 Physical Details... 1 Mounting Guide... 3 CHAPTER 2 ACCESS POINT SETUP...
VMware AirWatch Product Provisioning and Staging for Windows Rugged Guide Using Product Provisioning for managing Windows Rugged devices.
 VMware AirWatch Product Provisioning and Staging for Windows Rugged Guide Using Product Provisioning for managing Windows Rugged devices. AirWatch v9.2 Have documentation feedback? Submit a Documentation
VMware AirWatch Product Provisioning and Staging for Windows Rugged Guide Using Product Provisioning for managing Windows Rugged devices. AirWatch v9.2 Have documentation feedback? Submit a Documentation
MUM USA 2007 Tips and Tricks
 MUM USA 2007 Tips and Tricks Deploying and Managing a Wireless ISP with limited resources By David Savage Mikrotiksa.com Starting Up Starting up a Wireless Internet Service Provider can be both challenging
MUM USA 2007 Tips and Tricks Deploying and Managing a Wireless ISP with limited resources By David Savage Mikrotiksa.com Starting Up Starting up a Wireless Internet Service Provider can be both challenging
Configuring Logging for Access Lists
 CHAPTER 17 This chapter describes how to configure access list logging for extended access lists and Webytpe access lists, and it describes how to manage deny flows. This section includes the following
CHAPTER 17 This chapter describes how to configure access list logging for extended access lists and Webytpe access lists, and it describes how to manage deny flows. This section includes the following
MUM SAUDI ARABIA OCTOBER 2017
 MUM SAUDI ARABIA OCTOBER 2017 Jonathan JAY Soriano -Networking Enthusiast -MikroTik user since 2011 -Unofficial Trainer Identifying and Managing Traffic in RouterOS Challenge My applications are sometimes
MUM SAUDI ARABIA OCTOBER 2017 Jonathan JAY Soriano -Networking Enthusiast -MikroTik user since 2011 -Unofficial Trainer Identifying and Managing Traffic in RouterOS Challenge My applications are sometimes
