Classifying Rogue Access Points
|
|
|
- Nicholas Stevens
- 6 years ago
- Views:
Transcription
1 Finding Feature Information, page 1 Information About, page 1 Restrictions on, page 4 How to Classify Rogue Access Points, page 5 Viewing and Classifying Rogue Devices (GUI), page 10 Examples:, page 12 Additional References for, page 12 Feature History and Information For, page 13 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to An account on Cisco.com is not required. Information About The controller software enables you to create rules that can organize and display rogue access points as Friendly, Malicious, or Unclassified. By default, none of the classification rules are enabled. Therefore, all unknown access points are categorized as Unclassified. When you create a rule, configure conditions for it, and enable the rule, the unclassified access points are reclassified. Whenever you change a rule, it is applied to all access points (friendly, malicious, and unclassified) in the Alert state only. 1
2 Information About If you move any rogue or ad hoc rogue manually to unclassified and Alert state, it means that the rogue is moved to the default state. Rogue rules apply to all the rogues that are manually moved to unclassified and Alert state. Note Rule-based rogue classification does not apply to ad hoc rogues and rogue clients. Note You can configure up to 64 rogue classification rules per controller. When the controller receives a rogue report from one of its managed access points, it responds as follows: 1 The controller verifies that the unknown access point is in the friendly MAC address list. If it is, the controller classifies the access point as Friendly. 2 If the unknown access point is not in the friendly MAC address list, the controller starts applying rogue classification rules. 3 If the rogue is already classified as Malicious, Alert or Friendly, Internal or External, the controller does not reclassify it automatically. If the rogue is classified differently, the controller reclassifies it automatically only if the rogue is in the Alert state. 4 The controller applies the first rule based on priority. If the rogue access point matches the criteria specified by the rule, the controller classifies the rogue according to the classification type configured for the rule. 5 If the rogue access point does not match any of the configured rules, the controller classifies the rogue as Unclassified. 6 The controller repeats the previous steps for all rogue access points. 7 If RLDP determines that the rogue access point is on the network, the controller marks the rogue state as Threat and classifies it as Malicious automatically, even if no rules are configured. You can then manually contain the rogue (unless you have configured RLDP to automatically contain the rogue), which would change the rogue state to Contained. If the rogue access point is not on the network, the controller marks the rogue state as Alert, and you can manually contain the rogue. 8 If desired, you can manually move the access point to a different classification type and rogue state. Table 1: Classification Mapping Rule-Based Classification Type Friendly Rogue States Internal If the unknown access point is inside the network and poses no threat to WLAN security, you would manually configure it as Friendly, Internal. An example is the access points in your lab network. External If the unknown access point is outside the network and poses no threat to WLAN security, you would manually configure it as Friendly, External. An example is an access point that belongs to a neighboring coffee shop. Alert The unknown access point is moved to Alert if it is not in the neighbor list or in the user-configured friendly MAC list. 2
3 Information About Rule-Based Classification Type Malicious Rogue States Alert The unknown access point is moved to Alert if it is not in the neighbor list or in the user-configured friendly MAC list. Threat The unknown access point is found to be on the network and poses a threat to WLAN security. Contained The unknown access point is contained. Contained Pending The unknown access point is marked Contained, but the action is delayed due to unavailable resources. Unclassified Pending On first detection, the unknown access point is put in the Pending state for 3 minutes. During this time, the managed access points determine if the unknown access point is a neighbor access point. Alert The unknown access point is moved to Alert if it is not in the neighbor list or in the user-configured friendly MAC list. Contained The unknown access point is contained. Contained Pending The unknown access point is marked Contained, but the action is delayed due to unavailable resources. The classification and state of the rogue access points are configured as follows: From Known to Friendly, Internal From Acknowledged to Friendly, External From Contained to Malicious, Contained As mentioned previously, the controller can automatically change the classification type and rogue state of an unknown access point based on user-defined rules, or you can manually move the unknown access point to a different classification type and rogue state. Table 2: Allowable Classification Type and Rogue State Transitions From Friendly (Internal, External, Alert) Friendly (Internal, External, Alert) Friendly (Alert) Malicious (Alert, Threat) Malicious (Contained, Contained Pending) Unclassified (Alert, Threat) To Malicious (Alert) Unclassified (Alert) Friendly (Internal, External) Friendly (Internal, External) Malicious (Alert) Friendly (Internal, External) 3
4 Restrictions on From Unclassified (Contained, Contained Pending) Unclassified (Alert) To Unclassified (Alert) Malicious (Alert) If the rogue state is Contained, you have to uncontain the rogue access point before you can change the classification type. If you want to move a rogue access point from Malicious to Unclassified, you must delete the access point and allow the controller to reclassify it. Restrictions on The following rules apply to this feature: Classifying Custom type rogues is tied to rogue rules. Therefore, it is not possible to manually classify a rogue as Custom. Custom class change can occur only using rogue rules. There are traps that are sent for containment by rule and for every 30 minutes for rogue classification change. For custom classification, the first trap does not contain the severity score because the trap has existed before the custom classification. The severity score is obtained from the subsequent trap that is generated after 30 minutes if the rogue is classified. Rogue rules are applied on every incoming new rogue report in the controller in the order of their priority. Once a rogue satisfies a higher priority rule and classified, it does not move down the priority list for the same report. Previously classified rogue gets re-classified on every new rogue report with the following restrictions: Rogues which are classified as friendly by rule and whose state is set to ALERT, go through re-classification on receiving the new rogue report. If a rogue is classified as friendly by the administrator manually, then the state is INTERNAL and it does not get re-classified on successive rogue reports. If rogue is classified as malicious, irrespective of the state it does not get re-classified on subsequent rogue reports. Transition of the rogue's state from friendly to malicious is possible by multiple rogue rules if some attribute is missing in new rogue report. Transition of the rogue's state from malicious to any other classification is not possible by any rogue rule. If a rogue AP is classified as friendly, it means that the rogue AP exists in the vicinity, is a known AP, and need not be tracked. Therefore, all the rogue clients are either deleted or not tracked if they are associated with the friendly rogue AP. When service set identifiers (SSIDs) are defined as part of a rogue rule, and details of the rogue rule are displayed using the show wireless wps rogue rule detailed command, the output differs in Cisco IOS XE Release 3.7E and prior releases and Cisco IOS XE Denali and later releases. 4
5 How to Classify Rogue Access Points The following is sample output from the show wireless wps rogue rule detailed command in Cisco IOS XE Release 3.6E and prior releases: Switch# show wireless wps rogue rule detailed test Priority : 1 Rule Name : wpstest State : Disabled Type : Pending Match Operation : Any Hit Count : 0 Total Conditions : 1 Condition : type : Ssid SSID Count : 2 SSID 1 : ssid1 SSID 2 : ssid2 The following is sample output from the show wireless wps rogue rule detailed command in Cisco IOS XE Denali and later releases: Switch# show wireless wps rogue rule detailed test Priority : 1 Rule Name : wpstest State : Disabled Type : Pending Match Operation : Any Hit Count : 0 Total Conditions : 1 Condition : type : Ssid SSID Count : 2 SSID : ssid1 SSID : ssid2 How to Classify Rogue Access Points Configuring Rogue Classification Rules (CLI) SUMMARY STEPS 1. configure terminal 2. wireless wps rogue rule rule-name priority priority 3. classify {friendly malicious} 4. condition {client-count duration encryption infrastructure rssi ssid} 5. match {all any} 6. default 7. exit 8. shutdown 9. end 10. configure terminal 11. wireless wps rogue rule shutdown 12. end 5
6 Configuring Rogue Classification Rules (CLI) DETAILED STEPS Step 1 Command or Action configure terminal Purpose Enters global configuration mode. Step 2 Step 3 Switch# configure terminal wireless wps rogue rule rule-name priority priority rule_3 priority 3 Switch(config-rule)# classify {friendly malicious} Creates or enables a rule. While creating a rule, you must enter priority for the rule. Note After creating the rule, if you are editing the rule, you can change the priority only for the rogue rules that are disabled. You cannot change priority for the rogue rules that are enabled. While editing, changing the priority for a rogue rule is optional. Classifies a rule. Step 4 rule_3 priority 3 Switch(config-rule)# classify friendly condition {client-count duration encryption infrastructure rssi ssid} rule_3 priority 3 Switch(config-rule)# condition client-count 5 Specifies to add the following conditions to a rule that the rogue access point must meet. client-count Requires that a minimum number of clients be associated to the rogue access point. For example, if the number of clients associated to the rogue access point is greater than or equal to the configured value, then the access point could be classified as malicious. If you choose this option, enter the minimum number of clients to be associated to the rogue access point for the condition_value parameter. The valid range is 1 to 10 (inclusive), and the default value is 0. duration Requires that the rogue access point be detected for a minimum period of time. If you choose this option, enter a value for the minimum detection period for the condition_value parameter. The valid range is 0 to 3600 seconds (inclusive), and the default value is 0 seconds. encryption Requires that the advertised WLAN does not have encryption enabled. infrastructure Requires the SSID to be known to the controller. rssi Requires that the rogue access point have a minimum RSSI value. For example, if the rogue access point has an RSSI that is greater than the configured value, then the access point could be classified as malicious. If you choose this option, enter the minimum RSSI value for the condition_value parameter. The valid range is 95 to 50 dbm (inclusive), and the default value is 0 dbm. ssid Requires that the rogue access point have a specific SSID. You should add SSIDs that are not managed by the controller. If 6
7 Configuring Rogue Classification Rules (CLI) Command or Action Purpose you choose this option, enter the SSID for the condition_value parameter. The SSID is added to the user-configured SSID list. Step 5 Step 6 match {all any} rule_3 priority 3 Switch(config-rule)# match all default Specifies whether a detected rogue access point must meet all or any of the conditions specified by the rule in order for the rule to be matched and the rogue access point to adopt the classification type of the rule. Specifies to set a command to its default. Step 7 rule_3 priority 3 Switch(config-rule)# default exit Specifies to exit the sub-mode. Step 8 Step 9 Step 10 rule_3 priority 3 Switch(config-rule)# exit Switch(config)# shutdown rule_3 priority 3 Switch(config-rule)# shutdown end Switch(config)# end configure terminal Specifies to disable a particular rogue rule. For example, the rule rule_3 is disabled. Returns to privileged EXEC mode. Alternatively, you can also press Ctrl-Z to exit global configuration mode. Enters global configuration mode. Step 11 Switch# configure terminal wireless wps rogue rule shutdown Specifies to disable all the rogue rules. Step 12 shutdown end Switch(config)# end Returns to privileged EXEC mode. Alternatively, you can also press Ctrl-Z to exit global configuration mode. 7
8 Configuring Rogue Classification Rules (GUI) Configuring Rogue Classification Rules (GUI) Step 1 Step 2 Step 3 Choose Security > Wireless Protection Policies > Rogue Policies > Rogue Rules to open the Rogue Rules page. Any rules that have already been created are listed in priority order. The name, type, and status of each rule is provided. Note If you ever want to delete a rule, hover your mouse cursor over the blue drop-down arrow for that rule and click Remove. Create a new rule as follows: a) Click Add Rule. An Add Rule section appears at the top of the page. b) In the Rule Name text box, enter a name for the new rule. Ensure that the name does not contain any spaces. c) From the Rule Type drop-down list, choose from the following options to classify rogue access points matching this rule as friendly or malicious: Friendly Malicious d) Click Add to add this rule to the list of existing rules, or click Cancel to discard this new rule. Edit a rule as follows: a) Click the name of the rule that you want to edit. The Rogue Rule > Edit page appears. b) From the Type drop-down list, choose from the following options to classify rogue access points matching this rule: Friendly Malicious c) From the Match Operation text box, choose one of the following: All If this rule is enabled, a detected rogue access point must meet all of the conditions specified by the rule in order for the rule to be matched and the rogue to adopt the classification type of the rule. Any If this rule is enabled, a detected rogue access point must meet any of the conditions specified by the rule in order for the rule to be matched and the rogue to adopt the classification type of the rule. This is the default value. d) To enable this rule, select the Enable Rule check box. The default value is unselected. e) To disable this particular rule, unselect the Enable Rule check box. Note You cannot disable all the rogue rule in one shot from GUI but you can disable all the rogue rules from CLI using the wireless wps rogue rule shutdown command. f) From the Add Condition drop-down list, choose one or more of the following conditions that the rogue access point must meet and click Add Condition. SSID Requires that the rogue access point have a specific user-configured SSID. If you choose this option, enter the SSID in the User Configured SSID text box, and click Add SSID. The user-configured SSIDs are added and listed. Note To delete an SSID, highlight the SSID and click Remove. The SSID applied on a WLAN cannot be applied for the rogue rule. RSSI Requires that the rogue access point have a minimum Received Signal Strength Indication (RSSI) value. For example, if the rogue access point has an RSSI that is greater than the configured value, then the access point could be classified as malicious. If you choose this option, enter the minimum RSSI value in the Minimum RSSI text box. The valid range is 95 to 50 dbm (inclusive), and the default value is 0 dbm. 8
9 Configuring Rogue Classification Rules (GUI) Duration Requires that the rogue access point be detected for a minimum period of time. If you choose this option, enter a value for the minimum detection period in the Time Duration text box. The valid range is 0 to 3600 seconds (inclusive), and the default value is 0 seconds. Client Count Requires that a minimum number of clients be associated to the rogue access point. For example, if the number of clients associated to the rogue access point is greater than or equal to the configured value, then the access point could be classified as malicious. If you choose this option, enter the minimum number of clients to be associated to the rogue access point in the Minimum Number of Rogue Clients text box. The valid range is 1 to 10 (inclusive), and the default value is 0. No Encryption Requires that the rogue access point s advertised WLAN does not have encryption enabled. If a rogue access point has encryption disabled, it is likely that more clients will try to associate to it. No further configuration is required for this option. Note Cisco Prime Infrastructure refers to this option as Open Authentication. Managed SSID Requires that the rogue access point s managed SSID (the SSID configured for the WLAN) be known to the controller. No further configuration is required for this option. Note The SSID and Managed SSID conditions cannot be used with the All operation because these two SSID lists are mutually exclusive. If you define a rule with Match All and have these two conditions configured, the rogue access points are never classified as friendly or malicious because one of the conditions can never be met. Note You can add up to six conditions per rule. When you add a condition, it appears under the Conditions section. If you ever want to delete a condition from this rule, click Remove near the condition. User configured SSID Requires that the rogue access point have a substring of the specific user-configured SSID. The controller searches the substring in the same occurrence pattern and returns a match if the substring is found in the whole string of an SSID. Step 4 g) Click Apply. If you want to change the priority in which rogue classification rules are applied, follow these steps: 1 Click Change Priority to access the Rogue Rules > Priority page. The rogue rules are listed in priority order in the Change Rules Priority text box. 2 Click on a specific rule for which you want to change the priority, and click Up to raise its priority in the list or Down to lower its priority in the list. Note You can change priority only for the disabled rule. You cannot change priority only for the enabled rule. 3 Click Apply. 9
10 Viewing and Classifying Rogue Devices (GUI) Viewing and Classifying Rogue Devices (GUI) Step 1 Step 2 Choose Monitor > Rogues. Choose the following options to view the different types of rogue access points detected by the controller: Friendly APs Malicious APs Unclassified APs The respective rogue APs pages provide the following information: the MAC address of the rogue access point, the number of radios that detected the rogue access point, the number of clients connected to the rogue access point, the current status of the rogue access point, and last heard. Step 3 Get more details about a rogue access point by clicking the MAC address of the access point. The Rogue AP Detail page appears. This page provides the following information: the MAC address of the rogue device, the type of rogue device (such as an access point), whether the rogue device is on the wired network, the dates and times when the rogue device was first and last reported, and the current status of the device. The Class Type text box shows the current classification for this rogue access point: Friendly An unknown access point that matches the user-defined friendly rules or an existing known and acknowledged rogue access point. Friendly access points cannot be contained. Malicious An unknown access point that matches the user-defined malicious rules or is moved manually by the user from the Friendly or Unclassified classification type. Note Once an access point is classified as Malicious, you cannot apply rules to it in the future, and it cannot be moved to another classification type. If you want to move a malicious access point to the Unclassified classification type, you must delete the access point and allow the controller to reclassify it. Unclassified An unknown access point that does not match the user-defined friendly or malicious rules. An unclassified access point can be contained. It can also be moved to the Friendly or Malicious classification type automatically in accordance with user-defined rules or manually by the user. Step 4 Step 5 If you want to change the classification of this device, choose a different classification from the Class Type drop-down list. Note A rogue access point cannot be moved to another class if its current state is Contain. From the Update Status drop-down list, choose one of the following options to specify how the controller should respond to this rogue access point: Internal The controller trusts this rogue access point. This option is available if the Class Type is set to Friendly. External The controller acknowledges the presence of this rogue access point. This option is available if the Class Type is set to Friendly. Contain The controller contains the offending device so that its signals no longer interfere with authorized clients. This option is available if the Class Type is set to Malicious or Unclassified. 10
11 Viewing and Classifying Rogue Devices (GUI) Alert The controller forwards an immediate alert to the system administrator for further action. This option is available if the Class Type is set to Malicious or Unclassified. The bottom of the page provides information on both the access points that detected this rogue access point and any clients that are associated to it. To see more details for any of the clients, click Edit to open the Rogue Client Detail page. Step 6 Step 7 Step 8 Step 9 Step 10 Click Apply. Click Save Configuration. See any adhoc rogues detected by the controller by choosing Adhoc Rogues. The Adhoc Rogues page appears. This page shows the following information: the MAC address, BSSID, and SSID of the adhoc rogue, the number of radios that detected the adhoc rogue, and the current status of the adhoc rogue. Obtain more details about an adhoc rogue by clicking the MAC address of the rogue. The Adhoc Rogue Detail page appears. This page provides the following information: the MAC address and BSSID of the adhoc rogue, the dates and times when the rogue was first and last reported, and the current status of the rogue. From the Update Status drop-down list, choose one of the following options to specify how the controller should respond to this adhoc rogue: Contain The controller contains the offending device so that its signals no longer interfere with authorized clients. Alert The controller forwards an immediate alert to the system administrator for further action. Internal The controller trusts this rogue access point. External The controller acknowledges the presence of this rogue access point. Step 11 Step 12 Step 13 Step 14 From the Maximum Number of APs to Contain the Rogue drop-down list, choose one of the following options to specify the maximum number of access points used to contain this adhoc rogue: 1, 2, 3, or 4. The bottom of the page provides information on the access points that detected this adhoc rogue. Click Apply. Click Save Configuration. View any access points that have been configured to be ignored by choosing Rogue AP Ignore-List. The Rogue AP Ignore-List page appears. This page shows the MAC addresses of any access points that are configured to be ignored. The rogue-ignore list contains a list of any autonomous access points that have been manually added to Cisco Prime Infrastructure maps by the users. The controller regards these autonomous access points as rogues even though the Prime Infrastructure is managing them. The rogue-ignore list allows the controller to ignore these access points. The list is updated as follows: When the controller receives a rogue report, it checks to see if the unknown access point is in the rogue-ignore access point list. If the unknown access point is in the rogue-ignore list, the controller ignores this access point and continues to process other rogue access points. If the unknown access point is not in the rogue-ignore list, the controller sends a trap to the Prime Infrastructure. If the Prime Infrastructure finds this access point in its autonomous access point list, the Prime Infrastructure sends a command to the controller to add this access point to the rogue-ignore list. This access point is then ignored in future rogue reports. 11
12 Examples: If a user removes an autonomous access point from the Prime Infrastructure, the Prime Infrastructure sends a command to the controller to remove this access point from the rogue-ignore list. Examples: This example shows how to create rule that can organize and display rogue access points as Friendly: Switch# configure terminal ap1 priority 1 Switch(config-rule)# classify friendly Switch(config-rule)# end This example shows how to apply condition that the rogue access point must meet: Switch# configure terminal ap1 priority 1 Switch(config-rule)# condition client-count 5 Switch(config-rule)# condition duration 1000 Switch(config-rule)# end Additional References for Related Documents Related Topic Security commands Document Title Security Command Reference Guide, Cisco IOS XE Release 3SE (Cisco WLC 5700 Series) Standards and RFCs Standard/RFC None Title MIBs MIB All supported MIBs for this release. MIBs Link To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: 12
13 Feature History and Information For Technical Assistance Description The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. Link Feature History and Information For Classifying Rogue Access Points Release Cisco IOS XE 3.3SE Feature Information This feature was introduced. 13
14 Feature History and Information For 14
Classifying Rogue Access Points
 Finding Feature Information, page 1 Information About, page 1 Restrictions for, page 4 How to Classify Rogue Access Points, page 5 Viewing and Classifying Rogue Devices (GUI), page 9 Examples:, page 11
Finding Feature Information, page 1 Information About, page 1 Restrictions for, page 4 How to Classify Rogue Access Points, page 5 Viewing and Classifying Rogue Devices (GUI), page 9 Examples:, page 11
Managing Rogue Devices
 Finding Feature Information, page 1 Information About Rogue Devices, page 1 How to Configure Rogue Detection, page 6 Monitoring Rogue Detection, page 8 Examples: Rogue Detection Configuration, page 9 Additional
Finding Feature Information, page 1 Information About Rogue Devices, page 1 How to Configure Rogue Detection, page 6 Monitoring Rogue Detection, page 8 Examples: Rogue Detection Configuration, page 9 Additional
Configuring Aggressive Load Balancing
 Finding Feature Information, on page 1 Restrictions for Aggressive Load Balancing, on page 1 Information for Parameters, on page 2 How to Configure Aggressive Load Balancing, on page 3 Monitoring Aggressive
Finding Feature Information, on page 1 Restrictions for Aggressive Load Balancing, on page 1 Information for Parameters, on page 2 How to Configure Aggressive Load Balancing, on page 3 Monitoring Aggressive
Configuring Access Point Groups
 Finding Feature Information, page 1 Prerequisites for Configuring AP Groups, page 1 Restrictions for, page 2 Information About Access Point Groups, page 2 How to Configure Access Point Groups, page 4 Additional
Finding Feature Information, page 1 Prerequisites for Configuring AP Groups, page 1 Restrictions for, page 2 Information About Access Point Groups, page 2 How to Configure Access Point Groups, page 4 Additional
Configuring Client Roaming
 Finding Feature Information, page 1 Restrictions for, page 1 Information About Client Roaming, page 2 How to Configure Layer 2 or Layer 3 Roaming, page 4 Monitoring Client Roaming Parameters, page 11 Monitoring
Finding Feature Information, page 1 Restrictions for, page 1 Information About Client Roaming, page 2 How to Configure Layer 2 or Layer 3 Roaming, page 4 Monitoring Client Roaming Parameters, page 11 Monitoring
Configuring Client Roaming
 Finding Feature Information, page 1 Restrictions for, page 1 Information About Client Roaming, page 2 How to Configure Layer 2 or Layer 3 Roaming, page 4 Monitoring Client Roaming Parameters, page 10 Monitoring
Finding Feature Information, page 1 Restrictions for, page 1 Information About Client Roaming, page 2 How to Configure Layer 2 or Layer 3 Roaming, page 4 Monitoring Client Roaming Parameters, page 10 Monitoring
Configuring Local Policies
 Finding Feature Information, on page 1 Restrictions for, on page 1 Information About, on page 2 How to Configure Local Policies, on page 3 Monitoring Local Policies, on page 8 Examples: Local Policies
Finding Feature Information, on page 1 Restrictions for, on page 1 Information About, on page 2 How to Configure Local Policies, on page 3 Monitoring Local Policies, on page 8 Examples: Local Policies
Configuring Access Point Groups
 Finding Feature Information, page 1 Prerequisites for Configuring AP Groups, page 1 Restrictions for, page 2 Information About Access Point Groups, page 2 How to Configure Access Point Groups, page 3 Additional
Finding Feature Information, page 1 Prerequisites for Configuring AP Groups, page 1 Restrictions for, page 2 Information About Access Point Groups, page 2 How to Configure Access Point Groups, page 3 Additional
Configuring WLAN Security
 Finding Feature Information, page 1 Prerequisites for Layer 2 Security, page 1 Information About AAA Override, page 2 How to Configure WLAN Security, page 3 Additional References, page 11 Feature Information
Finding Feature Information, page 1 Prerequisites for Layer 2 Security, page 1 Information About AAA Override, page 2 How to Configure WLAN Security, page 3 Additional References, page 11 Feature Information
Configuring DHCP for WLANs
 Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 1 Information About the Dynamic Host Configuration Protocol, page 2 How to Configure DHCP for WLANs, page 4 Additional
Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 1 Information About the Dynamic Host Configuration Protocol, page 2 How to Configure DHCP for WLANs, page 4 Additional
Managing Rogue Devices
 Information About Rogue Devices, page 1 Configuring Rogue Detection (GUI), page 5 Configuring Rogue Detection (CLI), page 8 Information About Rogue Devices Rogue access points can disrupt wireless LAN
Information About Rogue Devices, page 1 Configuring Rogue Detection (GUI), page 5 Configuring Rogue Detection (CLI), page 8 Information About Rogue Devices Rogue access points can disrupt wireless LAN
Configuring Administrator Usernames and Passwords
 Configuring Administrator Usernames and Passwords Finding Feature Information, on page 1 Information About, on page 1, on page 2 Examples: Administrator Usernames and Passwords Configuration, on page 4
Configuring Administrator Usernames and Passwords Finding Feature Information, on page 1 Information About, on page 1, on page 2 Examples: Administrator Usernames and Passwords Configuration, on page 4
RADIUS Route Download
 The feature allows users to configure their network access server (NAS) to direct RADIUS authorization. Finding Feature Information, page 1 Prerequisites for, page 1 Information About, page 1 How to Configure,
The feature allows users to configure their network access server (NAS) to direct RADIUS authorization. Finding Feature Information, page 1 Prerequisites for, page 1 Information About, page 1 How to Configure,
Configuring r BSS Fast Transition
 Finding Feature Information, on page 1 Restrictions for 802.11r Fast Transition, on page 1 Information About 802.11r Fast Transition, on page 2 How to Configure 802.11r Fast Transition, on page 4 Additional
Finding Feature Information, on page 1 Restrictions for 802.11r Fast Transition, on page 1 Information About 802.11r Fast Transition, on page 2 How to Configure 802.11r Fast Transition, on page 4 Additional
Configuring Location Settings
 Finding Feature Information, page 1 Information About, page 1 How to Configure Location Settings, page 2 Monitoring Location Settings and NMSP Settings, page 6 Examples: Location Settings Configuration,
Finding Feature Information, page 1 Information About, page 1 How to Configure Location Settings, page 2 Monitoring Location Settings and NMSP Settings, page 6 Examples: Location Settings Configuration,
Configuring the Cisco Discovery Protocol
 Finding Feature Information, page 1 Information About CDP, page 1 How to Configure CDP, page 3 Monitoring and Maintaining CDP, page 11 Additional References, page 12 Feature History and Information for
Finding Feature Information, page 1 Information About CDP, page 1 How to Configure CDP, page 3 Monitoring and Maintaining CDP, page 11 Additional References, page 12 Feature History and Information for
Configuring Local Authentication and Authorization
 Configuring Local Authentication and Authorization Finding Feature Information, page 1 How to Configure Local Authentication and Authorization, page 1 Monitoring Local Authentication and Authorization,
Configuring Local Authentication and Authorization Finding Feature Information, page 1 How to Configure Local Authentication and Authorization, page 1 Monitoring Local Authentication and Authorization,
The RNS (Robust Secure Network) IE must be enabled with an AES Cipher.
 Finding Feature Information, page 1 Prerequisites for 802.11w, page 1 Restrictions for 802.11w, page 2 Information About 802.11w, page 2 How to Configure 802.11w, page 3 Disabling 802.11w (CLI), page 5
Finding Feature Information, page 1 Prerequisites for 802.11w, page 1 Restrictions for 802.11w, page 2 Information About 802.11w, page 2 How to Configure 802.11w, page 3 Disabling 802.11w (CLI), page 5
Configuring parameters and Band Selection
 Configuring 802.11 parameters and Band Selection Finding Feature Information, page 1 Restrictions on Band Selection, 802.11 Bands, and Parameters, page 1 Information About Configuring Band Selection, 802.11
Configuring 802.11 parameters and Band Selection Finding Feature Information, page 1 Restrictions on Band Selection, 802.11 Bands, and Parameters, page 1 Information About Configuring Band Selection, 802.11
Configuring parameters and Band Selection
 Configuring 802.11 parameters and Band Selection Finding Feature Information, page 1 Restrictions on Band Selection, 802.11 Bands, and Parameters, page 1 Information About Configuring Band Selection, 802.11
Configuring 802.11 parameters and Band Selection Finding Feature Information, page 1 Restrictions on Band Selection, 802.11 Bands, and Parameters, page 1 Information About Configuring Band Selection, 802.11
Exclusive Configuration Change Access and Access Session Locking
 Exclusive Configuration Change Access and Access Session Locking Exclusive Configuration Change Access (also called the Configuration Lock feature) allows you to have exclusive change access to the Cisco
Exclusive Configuration Change Access and Access Session Locking Exclusive Configuration Change Access (also called the Configuration Lock feature) allows you to have exclusive change access to the Cisco
Password Strength and Management for Common Criteria
 Password Strength and Management for Common Criteria The Password Strength and Management for Common Criteria feature is used to specify password policies and security mechanisms for storing, retrieving,
Password Strength and Management for Common Criteria The Password Strength and Management for Common Criteria feature is used to specify password policies and security mechanisms for storing, retrieving,
Configuring the Service Discovery Gateway
 Finding Feature Information, page 1 Restrictions for, page 1 Information about the Service Discovery Gateway and mdns, page 2 How to Configure the Service Discovery Gateway, page 5 Monitoring Service Discovery
Finding Feature Information, page 1 Restrictions for, page 1 Information about the Service Discovery Gateway and mdns, page 2 How to Configure the Service Discovery Gateway, page 5 Monitoring Service Discovery
Exclusive Configuration Change Access and Access Session Locking
 Exclusive Configuration Change Access and Access Session Locking Exclusive Configuration Change Access (also called the Configuration Lock feature) allows you to have exclusive change access to the Cisco
Exclusive Configuration Change Access and Access Session Locking Exclusive Configuration Change Access (also called the Configuration Lock feature) allows you to have exclusive change access to the Cisco
Predownloading an Image to Access Points
 Finding Feature Information, page 1 Predownloading an Image to an Access Point, page 1 Restrictions for Predownloading an Image to an Access Point, page 2 How to Predownload an Image to an Access Point,
Finding Feature Information, page 1 Predownloading an Image to an Access Point, page 1 Restrictions for Predownloading an Image to an Access Point, page 2 How to Predownload an Image to an Access Point,
SSH Algorithms for Common Criteria Certification
 The feature provides the list and order of the algorithms that are allowed for Common Criteria Certification. This module describes how to configure the encryption, Message Authentication Code (MAC), and
The feature provides the list and order of the algorithms that are allowed for Common Criteria Certification. This module describes how to configure the encryption, Message Authentication Code (MAC), and
Encrypted Vendor-Specific Attributes
 The feature provides users with a way to centrally manage filters at a RADIUS server and supports the following types of string vendor-specific attributes (VSAs): Tagged String VSA, on page 2 (similar
The feature provides users with a way to centrally manage filters at a RADIUS server and supports the following types of string vendor-specific attributes (VSAs): Tagged String VSA, on page 2 (similar
Configuring Security Solutions
 3 CHAPTER This chapter describes the security solutions for wireless LANs. It contains the following sections: Cisco Unified Wireless Network Solution Security, page 3-1 Interpreting the Security Tab,
3 CHAPTER This chapter describes the security solutions for wireless LANs. It contains the following sections: Cisco Unified Wireless Network Solution Security, page 3-1 Interpreting the Security Tab,
AAA Dead-Server Detection
 The feature allows you to configure the criteria to be used to mark a RADIUS server as dead. If no criteria are explicitly configured, the criteria are computed dynamically on the basis of the number of
The feature allows you to configure the criteria to be used to mark a RADIUS server as dead. If no criteria are explicitly configured, the criteria are computed dynamically on the basis of the number of
Configuring EEE. Finding Feature Information. Information About EEE. EEE Overview
 Finding Feature Information, page 1 Information About EEE, page 1 Restrictions for EEE, page 2 How to Configure EEE, page 2 Monitoring EEE, page 3 Configuration Examples for, page 4 Additional References,
Finding Feature Information, page 1 Information About EEE, page 1 Restrictions for EEE, page 2 How to Configure EEE, page 2 Monitoring EEE, page 3 Configuration Examples for, page 4 Additional References,
Configuring Cache Services Using the Web Cache Communication Protocol
 Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
Configuring Online Diagnostics
 Finding Feature Information, page 1 Information About, page 1 How to Configure Online Diagnostics, page 2 Monitoring and Maintaining Online Diagnostics, page 6 Configuration Examples for Online Diagnostic
Finding Feature Information, page 1 Information About, page 1 How to Configure Online Diagnostics, page 2 Monitoring and Maintaining Online Diagnostics, page 6 Configuration Examples for Online Diagnostic
PPPoE Smart Server Selection
 The feature allows service providers to determine which Broadband Remote Access Server (BRAS) a PPP call will terminate on. The feature allows you to configure a specific PPP over Ethernet (PPPoE) Active
The feature allows service providers to determine which Broadband Remote Access Server (BRAS) a PPP call will terminate on. The feature allows you to configure a specific PPP over Ethernet (PPPoE) Active
PPPoE Smart Server Selection
 The feature allows service providers to determine which Broadband Remote Access Server (BRAS) a PPP call will terminate on. The feature allows you to configure a specific PPP over Ethernet (PPPoE) Active
The feature allows service providers to determine which Broadband Remote Access Server (BRAS) a PPP call will terminate on. The feature allows you to configure a specific PPP over Ethernet (PPPoE) Active
Configuring Security Solutions
 3 CHAPTER This chapter describes the security solutions for wireless LANs. It contains the following sections: Cisco Unified Wireless Network Solution Security, page 3-1 Interpreting the Security Dashboard,
3 CHAPTER This chapter describes the security solutions for wireless LANs. It contains the following sections: Cisco Unified Wireless Network Solution Security, page 3-1 Interpreting the Security Dashboard,
Configuring SDM Templates
 Finding Feature Information, page 1 Information About, page 1 How to Configure SDM Templates, page 4 Configuration Examples for SDM Templates, page 5 Additional References for SDM Templates, page 7 Feature
Finding Feature Information, page 1 Information About, page 1 How to Configure SDM Templates, page 4 Configuration Examples for SDM Templates, page 5 Additional References for SDM Templates, page 7 Feature
Configuring Voice and Video Parameters
 Finding Feature Information, page 1 Prerequisites for Voice and Video Parameters, page 1 Restrictions for Voice and Video Parameters, page 1 Information About, page 2 How to Configure Voice and Video Parameters,
Finding Feature Information, page 1 Prerequisites for Voice and Video Parameters, page 1 Restrictions for Voice and Video Parameters, page 1 Information About, page 2 How to Configure Voice and Video Parameters,
Configuring System MTU
 Finding Feature Information, page 1 Restrictions for System MTU, page 1 Information about the MTU, page 2 How to Configure System MTU, page 3 Configuration Examples for System MTU, page 4 Additional References
Finding Feature Information, page 1 Restrictions for System MTU, page 1 Information about the MTU, page 2 How to Configure System MTU, page 3 Configuration Examples for System MTU, page 4 Additional References
Configuring Right-To-Use Licenses
 Finding Feature Information, page 1 Restrictions for Configuring RTU Licenses, page 1 Information About Configuring RTU Licenses, page 2 How to Configure RTU Licenses, page 5 Monitoring and Maintaining
Finding Feature Information, page 1 Restrictions for Configuring RTU Licenses, page 1 Information About Configuring RTU Licenses, page 2 How to Configure RTU Licenses, page 5 Monitoring and Maintaining
NBAR2 HTTP-Based Visibility Dashboard
 The NBAR2 HTTP-based Visibility Dashboard provides a web interface displaying network traffic data and related information. The information is presented in an intuitive, interactive graphical format. Finding
The NBAR2 HTTP-based Visibility Dashboard provides a web interface displaying network traffic data and related information. The information is presented in an intuitive, interactive graphical format. Finding
Trusted AP Policies on a Wireless LAN Controller
 Trusted AP Policies on a Wireless LAN Controller Document ID: 100368 Contents Introduction Prerequisites Requirements Conventions Trusted AP Policies What is a Trusted AP? How to Configure an AP as a Trusted
Trusted AP Policies on a Wireless LAN Controller Document ID: 100368 Contents Introduction Prerequisites Requirements Conventions Trusted AP Policies What is a Trusted AP? How to Configure an AP as a Trusted
DMVPN Event Tracing. Finding Feature Information
 The feature provides a trace facility for troubleshooting Cisco IOS Dynamic Multipoint VPN (DMVPN). This feature enables you to monitor DMVPN events, errors, and exceptions. During runtime, the event trace
The feature provides a trace facility for troubleshooting Cisco IOS Dynamic Multipoint VPN (DMVPN). This feature enables you to monitor DMVPN events, errors, and exceptions. During runtime, the event trace
Configuring VLAN Trunks
 Finding Feature Information, page 1 Prerequisites for VLAN Trunks, page 1 Information About VLAN Trunks, page 2 How to Configure VLAN Trunks, page 5 Configuration Examples for VLAN Trunking, page 20 Where
Finding Feature Information, page 1 Prerequisites for VLAN Trunks, page 1 Information About VLAN Trunks, page 2 How to Configure VLAN Trunks, page 5 Configuration Examples for VLAN Trunking, page 20 Where
Configuring System MTU
 Restrictions for System MTU, on page 1 Information About the MTU, on page 1 How to Configure MTU, on page 2 Configuration Examples for System MTU, on page 4 Additional References for System MTU, on page
Restrictions for System MTU, on page 1 Information About the MTU, on page 1 How to Configure MTU, on page 2 Configuration Examples for System MTU, on page 4 Additional References for System MTU, on page
Configuring EEE. Finding Feature Information. Restrictions for EEE
 Finding Feature Information, page 1 Restrictions for EEE, page 1 Information About EEE, page 2 How to Configure EEE, page 2 Monitoring EEE, page 3 Configuration Examples for, page 4 Additional References,
Finding Feature Information, page 1 Restrictions for EEE, page 1 Information About EEE, page 2 How to Configure EEE, page 2 Monitoring EEE, page 3 Configuration Examples for, page 4 Additional References,
Cisco IOS Login Enhancements-Login Block
 The Cisco IOS Login Enhancements (Login Block) feature allows users to enhance the security of a router by configuring options to automatically block further login attempts when a possible denial-of-service
The Cisco IOS Login Enhancements (Login Block) feature allows users to enhance the security of a router by configuring options to automatically block further login attempts when a possible denial-of-service
802.1P CoS Bit Set for PPP and PPPoE Control Frames
 802.1P CoS Bit Set for PPP and PPPoE Control The 802.1P CoS Bit Set for PPP and PPPoE Control feature provides the ability to set user priority bits in the IEEE 802.1Q tagged frame to allow traffic prioritization.
802.1P CoS Bit Set for PPP and PPPoE Control The 802.1P CoS Bit Set for PPP and PPPoE Control feature provides the ability to set user priority bits in the IEEE 802.1Q tagged frame to allow traffic prioritization.
Configuring SDM Templates
 Finding Feature Information, on page 1 Information About, on page 1 How to Configure SDM Templates, on page 3 Monitoring and Maintaining SDM Templates, on page 4 Configuration Examples for SDM Templates,
Finding Feature Information, on page 1 Information About, on page 1 How to Configure SDM Templates, on page 3 Monitoring and Maintaining SDM Templates, on page 4 Configuration Examples for SDM Templates,
Configuring Secure Shell (SSH)
 Finding Feature Information, on page 1 Prerequisites for Configuring Secure Shell, on page 1 Restrictions for Configuring Secure Shell, on page 2 Information About Configuring Secure Shell, on page 2 How
Finding Feature Information, on page 1 Prerequisites for Configuring Secure Shell, on page 1 Restrictions for Configuring Secure Shell, on page 2 Information About Configuring Secure Shell, on page 2 How
Configuring Embedded Resource Manager-MIB
 The Embedded Resource Manager (ERM)-MIB feature introduces MIB support for the ERM feature. The ERM feature tracks resource usage information for every registered resource owner and resource user. The
The Embedded Resource Manager (ERM)-MIB feature introduces MIB support for the ERM feature. The ERM feature tracks resource usage information for every registered resource owner and resource user. The
Wireless Intrusion Detection System
 Management Frame Protection, on page 1 Client Exclusion Policies, on page 5 Rogue Management, on page 7 Cisco Intrusion Detection System, on page 33 IDS Signatures, on page 37 SNMP, on page 45 wips, on
Management Frame Protection, on page 1 Client Exclusion Policies, on page 5 Rogue Management, on page 7 Cisco Intrusion Detection System, on page 33 IDS Signatures, on page 37 SNMP, on page 45 wips, on
Alarms and Events. Using the Alarm Dashboard CHAPTER
 CHAPTER 14 This chapter describes the type of events and alarms reported, how to view alarms and events by product or entity and severity, and how to view IDS signature attacks. It contains these sections:
CHAPTER 14 This chapter describes the type of events and alarms reported, how to view alarms and events by product or entity and severity, and how to view IDS signature attacks. It contains these sections:
Prerequisites for Controlling Switch Access with Terminal Access Controller Access Control System Plus (TACACS+)
 Finding Feature Information, page 1 Prerequisites for Controlling Switch Access with Terminal Access Controller Access Control System Plus (TACACS+), page 1 Information About TACACS+, page 3 How to Configure
Finding Feature Information, page 1 Prerequisites for Controlling Switch Access with Terminal Access Controller Access Control System Plus (TACACS+), page 1 Information About TACACS+, page 3 How to Configure
Configuring DHCP Option 60 and Option 82 with VPN-ID Support for Transparent Automatic Logon
 Configuring DHCP Option 60 and Option 82 with VPN-ID Support for Transparent Automatic Logon Intelligent Services Gateway (ISG) is a Cisco software feature set that provides a structured framework in which
Configuring DHCP Option 60 and Option 82 with VPN-ID Support for Transparent Automatic Logon Intelligent Services Gateway (ISG) is a Cisco software feature set that provides a structured framework in which
Configuring Control Plane Policing
 Finding Feature Information, page 1 Restrictions for CoPP, page 1 Information About Control Plane Policing, page 2 How to Configure CoPP, page 5 Examples for Configuring CoPP, page 10 Monitoring CoPP,
Finding Feature Information, page 1 Restrictions for CoPP, page 1 Information About Control Plane Policing, page 2 How to Configure CoPP, page 5 Examples for Configuring CoPP, page 10 Monitoring CoPP,
Configuring Multicast VLAN Registration
 Finding Feature Information, page 1 Restrictions for MVR, page 1 Information About Multicast VLAN Registration, page 2 How to Configure MVR, page 5 Monitoring MVR, page 10 Configuration Examples for MVR,
Finding Feature Information, page 1 Restrictions for MVR, page 1 Information About Multicast VLAN Registration, page 2 How to Configure MVR, page 5 Monitoring MVR, page 10 Configuration Examples for MVR,
Encrypted Vendor-Specific Attributes
 Encrypted Vendor-Specific Attributes Last Updated: January 15, 2012 The Encrypted Vendor-Specific Attributes feature provides users with a way to centrally manage filters at a RADIUS server and supports
Encrypted Vendor-Specific Attributes Last Updated: January 15, 2012 The Encrypted Vendor-Specific Attributes feature provides users with a way to centrally manage filters at a RADIUS server and supports
Switches running the LAN Base feature set support only static routing on SVIs.
 Finding Feature Information, on page 1 Prerequisites for VLANs, on page 1 Restrictions for VLANs, on page 2 Information About VLANs, on page 2 How to Configure VLANs, on page 6 Monitoring VLANs, on page
Finding Feature Information, on page 1 Prerequisites for VLANs, on page 1 Restrictions for VLANs, on page 2 Information About VLANs, on page 2 How to Configure VLANs, on page 6 Monitoring VLANs, on page
Configuring Right-To-Use Licenses
 Finding Feature Information, page 1 Restrictions for Configuring RTU Licenses, page 1 Information About Configuring RTU Licenses, page 2 How to Configure RTU Licenses, page 3 CLI for Permissible License
Finding Feature Information, page 1 Restrictions for Configuring RTU Licenses, page 1 Information About Configuring RTU Licenses, page 2 How to Configure RTU Licenses, page 3 CLI for Permissible License
Configuring Secure Shell (SSH)
 Starting with Cisco IOS XE Denali 16.3.1, Secure Shell Version 1 (SSHv1) is deprecated. Finding Feature Information, on page 1 Prerequisites for Configuring Secure Shell, on page 1 Restrictions for Configuring
Starting with Cisco IOS XE Denali 16.3.1, Secure Shell Version 1 (SSHv1) is deprecated. Finding Feature Information, on page 1 Prerequisites for Configuring Secure Shell, on page 1 Restrictions for Configuring
IPv6 Client IP Address Learning
 Prerequisites for IPv6 Client Address Learning, on page 1 Information About IPv6 Client Address Learning, on page 1 Configuring IPv6 Unicast, on page 6 Configuring RA Guard Policy, on page 7 Applying RA
Prerequisites for IPv6 Client Address Learning, on page 1 Information About IPv6 Client Address Learning, on page 1 Configuring IPv6 Unicast, on page 6 Configuring RA Guard Policy, on page 7 Applying RA
Monitoring Dashboard. Figure 1: Monitoring Dashboard
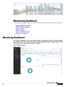 , on page 1 Network Summary, on page 4 Rogues, on page 5 Interferers, on page 5 Wireless Dashboard, on page 5 Best Practices, on page 6 Cisco Wireless Controller can be accessed using two modes Command
, on page 1 Network Summary, on page 4 Rogues, on page 5 Interferers, on page 5 Wireless Dashboard, on page 5 Best Practices, on page 6 Cisco Wireless Controller can be accessed using two modes Command
Contextual Configuration Diff Utility
 The feature provides the ability to perform a line-by-line comparison of any two configuration files (accessible through the Cisco IOS XE Integrated File System [IFS]) and generate a list of the differences
The feature provides the ability to perform a line-by-line comparison of any two configuration files (accessible through the Cisco IOS XE Integrated File System [IFS]) and generate a list of the differences
Controlling Switch Access with Passwords and Privilege Levels
 Controlling Switch Access with Passwords and Privilege Levels Finding Feature Information, page 1 Restrictions for Controlling Switch Access with Passwords and Privileges, page 1 Information About Passwords
Controlling Switch Access with Passwords and Privilege Levels Finding Feature Information, page 1 Restrictions for Controlling Switch Access with Passwords and Privileges, page 1 Information About Passwords
Alarms and Events. Using the Alarm Summary CHAPTER
 CHAPTER 16 This chapter describes the type of events and alarms reported, how to view alarms and events by product or entity and severity, and how to view IDS signature attacks. It contains these sections:
CHAPTER 16 This chapter describes the type of events and alarms reported, how to view alarms and events by product or entity and severity, and how to view IDS signature attacks. It contains these sections:
BGP Route-Map Continue
 The feature introduces the continue clause to BGP route-map configuration. The continue clause allows for more programmable policy configuration and route filtering and introduces the capability to execute
The feature introduces the continue clause to BGP route-map configuration. The continue clause allows for more programmable policy configuration and route filtering and introduces the capability to execute
BGP-RT and VPN Distinguisher Attribute Rewrite Wildcard
 BGP-RT and VPN Distinguisher Attribute Rewrite Wildcard The BGP RT and VPN Distinguisher Attribute Rewrite Wildcard feature introduces the ability to set a range of route target (RT) community attributes
BGP-RT and VPN Distinguisher Attribute Rewrite Wildcard The BGP RT and VPN Distinguisher Attribute Rewrite Wildcard feature introduces the ability to set a range of route target (RT) community attributes
Configuring Ethernet Management Port
 Finding Feature Information, page 1 Prerequisites for Ethernet Management Ports, page 1 Information about the Ethernet Management Port, page 1 How to Configure the Ethernet Management Port, page 4 Additional
Finding Feature Information, page 1 Prerequisites for Ethernet Management Ports, page 1 Information about the Ethernet Management Port, page 1 How to Configure the Ethernet Management Port, page 4 Additional
Configuring SDM Templates
 Information About, on page 1 How to Configure SDM Templates, on page 2 Monitoring and Maintaining SDM Templates, on page 3 Configuration Examples for SDM Templates, on page 4 Additional References for
Information About, on page 1 How to Configure SDM Templates, on page 2 Monitoring and Maintaining SDM Templates, on page 3 Configuration Examples for SDM Templates, on page 4 Additional References for
IP Overlapping Address Pools
 The feature improves flexibility in assigning IP addresses dynamically. This feature allows you to configure overlapping IP address pool groups to create different address spaces and concurrently use the
The feature improves flexibility in assigning IP addresses dynamically. This feature allows you to configure overlapping IP address pool groups to create different address spaces and concurrently use the
Dynamic Bandwidth Sharing
 The Cisco cbr series router enables dynamic bandwidth sharing (DBS) on integrated cable (IC) and wideband (WB) cable interfaces. Finding Feature Information Your software release may not support all the
The Cisco cbr series router enables dynamic bandwidth sharing (DBS) on integrated cable (IC) and wideband (WB) cable interfaces. Finding Feature Information Your software release may not support all the
Configuring Auto-QoS
 Finding Feature Information, page 1 Prerequisites for Auto-QoS, page 1 Restrictions for Auto-QoS, page 2 Information About, page 3 How to Configure Auto-QoS, page 6 Monitoring Auto-QoS, page 9 Configuration
Finding Feature Information, page 1 Prerequisites for Auto-QoS, page 1 Restrictions for Auto-QoS, page 2 Information About, page 3 How to Configure Auto-QoS, page 6 Monitoring Auto-QoS, page 9 Configuration
Configuring VLANs. Finding Feature Information. Prerequisites for VLANs
 Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 7 Monitoring VLANs, page 19 Where to Go Next,
Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 7 Monitoring VLANs, page 19 Where to Go Next,
Configuring the Physical Subscriber Line for RADIUS Access and Accounting
 Configuring the Physical Subscriber Line for RADIUS Access and Accounting Configuring a physical subscriber line for RADIUS Access and Accounting enables an L2TP access concentrator (LAC) and an L2TP network
Configuring the Physical Subscriber Line for RADIUS Access and Accounting Configuring a physical subscriber line for RADIUS Access and Accounting enables an L2TP access concentrator (LAC) and an L2TP network
Configuring LLDP, LLDP-MED, and Wired Location Service
 Configuring LLDP, LLDP-MED, and Wired Location Service Finding Feature Information, page 1 LLDP, LLDP-MED, and Wired Location Service Overview, page 1 How to Configure LLDP, LLDP-MED, and Wired Location
Configuring LLDP, LLDP-MED, and Wired Location Service Finding Feature Information, page 1 LLDP, LLDP-MED, and Wired Location Service Overview, page 1 How to Configure LLDP, LLDP-MED, and Wired Location
Configuring Secure Shell (SSH)
 Finding Feature Information, page 1 Prerequisites for Configuring the Switch for Secure Shell (SSH) and Secure Copy Protocol (SCP), page 1 Restrictions for Configuring the ControllerDevice for SSH, page
Finding Feature Information, page 1 Prerequisites for Configuring the Switch for Secure Shell (SSH) and Secure Copy Protocol (SCP), page 1 Restrictions for Configuring the ControllerDevice for SSH, page
Configuring Secure Shell (SSH)
 Finding Feature Information, page 1 Prerequisites for Configuring the Switch for Secure Shell (SSH) and Secure Copy Protocol (SCP), page 1 Restrictions for Configuring the Switch for SSH, page 2 Information
Finding Feature Information, page 1 Prerequisites for Configuring the Switch for Secure Shell (SSH) and Secure Copy Protocol (SCP), page 1 Restrictions for Configuring the Switch for SSH, page 2 Information
Configuring Secure Shell (SSH)
 Finding Feature Information, page 1 Prerequisites for Configuring Secure Shell, page 1 Restrictions for Configuring Secure Shell, page 2 Information about SSH, page 3 How to Configure SSH, page 5 Monitoring
Finding Feature Information, page 1 Prerequisites for Configuring Secure Shell, page 1 Restrictions for Configuring Secure Shell, page 2 Information about SSH, page 3 How to Configure SSH, page 5 Monitoring
IEEE 802.1X Open Authentication
 allows a host to have network access without having to go through IEEE 802.1X authentication. Open authentication is useful in an applications such as the Preboot Execution Environment (PXE), where a device
allows a host to have network access without having to go through IEEE 802.1X authentication. Open authentication is useful in an applications such as the Preboot Execution Environment (PXE), where a device
DHCP Server RADIUS Proxy
 The Dynamic Host Configuration Protocol (DHCP) Server RADIUS Proxy is a RADIUS-based address assignment mechanism in which a DHCP server authorizes remote clients and allocates addresses based on replies
The Dynamic Host Configuration Protocol (DHCP) Server RADIUS Proxy is a RADIUS-based address assignment mechanism in which a DHCP server authorizes remote clients and allocates addresses based on replies
Configuring IP SLA - Percentile Support for Filtering Outliers
 Configuring IP SLA - Percentile Support for Filtering Outliers This module describes how to configure the percentile option for IP SLAs to examine a set of network measurements that are within a specified
Configuring IP SLA - Percentile Support for Filtering Outliers This module describes how to configure the percentile option for IP SLAs to examine a set of network measurements that are within a specified
Per-User ACL Support for 802.1X/MAB/Webauth Users
 Per-User ACL Support for 802.1X/MAB/Webauth Users This feature allows per-user ACLs to be downloaded from the Cisco Access Control Server (ACS) as policy enforcement after authentication using IEEE 802.1X,
Per-User ACL Support for 802.1X/MAB/Webauth Users This feature allows per-user ACLs to be downloaded from the Cisco Access Control Server (ACS) as policy enforcement after authentication using IEEE 802.1X,
Configuring VLANs. Finding Feature Information. Prerequisites for VLANs
 Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 8 Monitoring VLANs, page 22 Where to Go Next,
Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 8 Monitoring VLANs, page 22 Where to Go Next,
Flow-Based per Port-Channel Load Balancing
 The feature allows different flows of traffic over a Gigabit EtherChannel (GEC) interface to be identified based on the packet header and then mapped to the different member links of the port channel.
The feature allows different flows of traffic over a Gigabit EtherChannel (GEC) interface to be identified based on the packet header and then mapped to the different member links of the port channel.
Configuring Secure Socket Layer HTTP
 Finding Feature Information, page 1 Information about Secure Sockets Layer (SSL) HTTP, page 1 How to Configure Secure HTTP Servers and Clients, page 5 Monitoring Secure HTTP Server and Client Status, page
Finding Feature Information, page 1 Information about Secure Sockets Layer (SSL) HTTP, page 1 How to Configure Secure HTTP Servers and Clients, page 5 Monitoring Secure HTTP Server and Client Status, page
Configuring DHCP. Finding Feature Information. Information About DHCP. DHCP Server. DHCP Relay Agent
 Finding Feature Information, on page 1 Information About DHCP, on page 1 How to Configure DHCP Features, on page 8 Server Port-Based Address Allocation, on page 17 Finding Feature Information Your software
Finding Feature Information, on page 1 Information About DHCP, on page 1 How to Configure DHCP Features, on page 8 Server Port-Based Address Allocation, on page 17 Finding Feature Information Your software
Configuring SDM Templates
 Information About, on page 1 How to Configure SDM Templates, on page 2 Monitoring and Maintaining SDM Templates, on page 3 Configuration Examples for SDM Templates, on page 4 Additional References for
Information About, on page 1 How to Configure SDM Templates, on page 2 Monitoring and Maintaining SDM Templates, on page 3 Configuration Examples for SDM Templates, on page 4 Additional References for
Configuring PoE. Information About PoE. PoE and PoE+ Ports. Supported Protocols and Standards
 Information About PoE, page 1 How to Configure PoE and UPoE, page 6 Monitoring Power Status, page 11 Additional References for PoE, page 11 Feature History and Information for PoE, page 12 Information
Information About PoE, page 1 How to Configure PoE and UPoE, page 6 Monitoring Power Status, page 11 Additional References for PoE, page 11 Feature History and Information for PoE, page 12 Information
Controlling Switch Access with Passwords and Privilege Levels
 Controlling Switch Access with Passwords and Privilege Levels Finding Feature Information, page 1 Restrictions for Controlling Switch Access with Passwords and Privileges, page 1 Information About Passwords
Controlling Switch Access with Passwords and Privilege Levels Finding Feature Information, page 1 Restrictions for Controlling Switch Access with Passwords and Privileges, page 1 Information About Passwords
Configuring Port-Based Traffic Control
 Overview of Port-Based Traffic Control, page 2 Finding Feature Information, page 2 Information About Storm Control, page 2 How to Configure Storm Control, page 4 Finding Feature Information, page 9 Information
Overview of Port-Based Traffic Control, page 2 Finding Feature Information, page 2 Information About Storm Control, page 2 How to Configure Storm Control, page 4 Finding Feature Information, page 9 Information
IPv6 Routing: RIP for IPv6
 IPv6 Routing Information Protocol (RIP) functions the same and offers the same benefits as IPv4 RIP. RIP enhancements for IPv6, detailed in RFC 2080, include support for IPv6 addresses and prefixes and
IPv6 Routing Information Protocol (RIP) functions the same and offers the same benefits as IPv4 RIP. RIP enhancements for IPv6, detailed in RFC 2080, include support for IPv6 addresses and prefixes and
Configuring Secure Shell (SSH)
 Finding Feature Information, page 1 Prerequisites for Configuring Secure Shell, page 1 Restrictions for Configuring Secure Shell, page 2 Information about SSH, page 2 How to Configure SSH, page 5 Monitoring
Finding Feature Information, page 1 Prerequisites for Configuring Secure Shell, page 1 Restrictions for Configuring Secure Shell, page 2 Information about SSH, page 2 How to Configure SSH, page 5 Monitoring
SIP ALG Resilience to DoS Attacks
 The feature provides protection against Session Initiation Protocol (SIP) application layer gateway (ALG) denial of service (DoS) attacks. This feature supports a configurable lock limit, a dynamic blacklist,
The feature provides protection against Session Initiation Protocol (SIP) application layer gateway (ALG) denial of service (DoS) attacks. This feature supports a configurable lock limit, a dynamic blacklist,
Configurable Number of Simultaneous Packets per Flow
 Configurable Number of Simultaneous Packets per Flow In zone-based policy firewalls, the number of simultaneous packets per flow is restricted to 25 and packets that exceed the limit are dropped. The dropping
Configurable Number of Simultaneous Packets per Flow In zone-based policy firewalls, the number of simultaneous packets per flow is restricted to 25 and packets that exceed the limit are dropped. The dropping
Configuring System Message Logs
 Finding Feature Information, page 1 Restrictions for, page 1 Information About, page 2 How to Configure System Message Logs, page 5 Monitoring and Maintaining System Message Logs, page 13 Configuration
Finding Feature Information, page 1 Restrictions for, page 1 Information About, page 2 How to Configure System Message Logs, page 5 Monitoring and Maintaining System Message Logs, page 13 Configuration
Configuring Switched Port Analyzer
 This document describes how to configure local Switched Port Analyzer (SPAN) and remote SPAN (RSPAN) on the router. Finding Feature Information, page 1 Prerequisites for Configuring Local Span and RSPAN,
This document describes how to configure local Switched Port Analyzer (SPAN) and remote SPAN (RSPAN) on the router. Finding Feature Information, page 1 Prerequisites for Configuring Local Span and RSPAN,
Autoroute Announce and Forwarding Adjacencies For OSPFv3
 Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Autoroute Announce and Forwarding Adjacencies For OSPFv3
 Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
Autoroute Announce and Forwarding The Autoroute Announce and Forwarding Adjacencies for OSPFv3 feature advertises IPv6 routes over MPLS/TE IPv4 tunnels. This module describes how to configure the Autoroute
OSPF Incremental SPF
 The Open Shortest Path First (OSPF) protocol can be configured to use an incremental SPF algorithm for calculating the shortest path first routes. Incremental SPF is more efficient than the full SPF algorithm,
The Open Shortest Path First (OSPF) protocol can be configured to use an incremental SPF algorithm for calculating the shortest path first routes. Incremental SPF is more efficient than the full SPF algorithm,
Call Flows for 3G and 4G Mobile IP Users
 This chapter provides various call flows for 3G and 4G mobile IP users, and contains the following sections: Finding Feature Information, on page 1 3G DHCP Discover Call Flow, on page 1 4G DHCP Discover
This chapter provides various call flows for 3G and 4G mobile IP users, and contains the following sections: Finding Feature Information, on page 1 3G DHCP Discover Call Flow, on page 1 4G DHCP Discover
