Introducing the PIC24F GB2 MCU Family: extreme Low Power with Hardware Crypto Engine
|
|
|
- Thomasina Maxwell
- 6 years ago
- Views:
Transcription
1 Introducing the PIC24F GB2 MCU Family: extreme Low Power with Hardware Crypto Engine Alexis Alcott, Product Marketing Manager, MCU16 Division June 24, 2014
2 2 Announcing at Sensors Expo PIC24F GB2 MCUs for Protecting Data in Embedded Applications Hardware crypto engine (Industry-standard AES, DES, 3DES) Random Number Generator (RNG) One-Time-Programmable (OTP) Key Storage extreme Low Power Extends Battery Life 18 na Sleep, 180 µa/mhz Run Enabling Integrity of Data without Sacrificing Power Consumption Connection to USB or Wireless Protocols Integrated USB 2.0 Device, Host, OTG Easy Connection to Certified Modules for Wi-Fi, ZigBee, Sub-GHz, Bluetooth LE Ideal for IoT Sensor Nodes, Access Control Systems, Door Locks
3 3 Example Applications Industrial Security door locks Access control systems Security cameras POS terminals Smartcard readers Heat/Gas meters IoT sensor nodes Computer PC peripherals Printers Portable accessories Medical/Fitness Pedometers Wearable fitness Handheld devices
4 4 Integrated Crypto Engine Hardware Crypto Engine Industry Standards for AES, DES, 3DES Encryption, Decryption & Authentication Secure Data Transfer & Storage Random Number Generator Supporting True-Random and Pseudo-Random Numbers Reach a Higher Level of Data Security Reduces Possibility of Hacking Secure Key Storage for Additional Protection 512 bits OTP Key Storage Once Written, Keys cannot be Read or Overwritten by Software Stores up to 4 AES Keys or 8 DES Keys Advantages of Hardware Crypto over Software Implementation Less Software Overhead Frees Up CPU Bandwidth & Memory Operate at a Lower CPU Frequency to Save Power Another Example of Microchip s Core Independent Peripherals
5 PIC24 GB2 Block Diagram 5
6 6 Application Example: Electronic Door Lock Encryption for Security Bluetooth LE RN4020 Uses Crypto, RNG & Key Storage User data is encrypted Near Field Communication (NFC) PIC24FJ128GB204 Secure key storage extreme Low Power Magnetic Card UART Hardware encryption/ Secure Key storage MCU Core Digital I/O Display Unit Low power extends battery life Vbat with RTCC for battery backup Access Options Enter code manually via keypad Magnetic keycard 128KB Flash Vbat Wirelessly via Smartphone Key pad control (touch) CTMU Power Interrupt Door Latch Motor Control Unit
7 7 Flexible Development Tools Main Development Board Explorer 16 Board DM $ Processor Plug-In Modules PICtail Plus Daughter Cards PIC24FJ128GB204 Plug-In Module (USB) MA $25.00 PIC24FJ128GA204 Plug-In Module (Non-USB) MA $25.00 USB PICtail Plus Daughter Board AC $60.00 Smart Card/SIM Card PICtail Daughter Board AC $29.99 Wireless Daughter Cards RN4020 Bluetooth LE PICtail/PICtail Plus RN-4020-PICtail $49.00 Wi-Fi PICtail RN-171-PICtail $ /ZigBee MRF24J40MA PICtail Plus AC $24.99 Sub-GHz MRF89XAM8A PICtail Plus AC $39.99
8 8 PIC24F GB2 MCU Family: Low Power with Crypto Engine Embedded Applications in the Internet-Connected World Demand Secure Data & Long Battery Life PIC24F GB2 for Secure Data Transfer & Storage Hardware Crypto Engine Random Number Generator & Secure Key Storage PIC24F GB2 for extreme Low Power Longer battery life for portable applications PIC24F GB2 for Easy Connections Integrated USB Easy interface to certified Wi-Fi or Bluetooth LE modules
9 Additional Materials Note: The Microchip name and logo, and PIC are registered trademarks of Microchip Technology Inc. in the U.S.A., and other countries. PICtail is a trademark of Microchip Technology Inc. in the U.S.A., and other countries. All other trademarks mentioned herein are property of their respective companies.
10 10 Availability & Pricing Part # USB Flash Pins Package PIC24FJ128GB204 Yes 128 KB 44 TQFP, QFN PIC24FJ128GB202 Yes 128 KB 28 SOIC, SSOP, QFN, SPDIP PIC24FJ64GB204 Yes 64 KB 44 TQFP, QFN PIC24FJ64GB202 Yes 64 KB 28 SOIC, SSOP, QFN, SPDIP PIC24FJ128GA204 No 128 KB 44 TQFP, QFN PIC24FJ128GA202 No 128 KB 28 SOIC, SSOP, QFN, SPDIP PIC24FJ64GA204 No 64 KB 44 TQFP, QFN PIC24FJ64GA202 No 64 KB 28 SOIC, SSOP, QFN, SPDIP Prices start at $1.30 in volume. All products available now for sampling & volume. Tape & Reel options available.
11 11 Support for All AES/DES Modes We support all of the modes within AES, DES, 3DES DES Encryption/Decryption Half-duplex operation Selectable between DES or Triple DES (3DES) 56-bit Key with support for 2-key or 3-key E-D-E/D-E-D Triple DES 64-bit Block Size ECB, CBC, CFB, OFB and CTR modes AES Encryption/Decryption Half-duplex operation 128-bit, 192-bit or 256-bit Key 128-bit Block Size ECB, CBC, CFB, OFB and CTR modes
12 Crypto Modes ECB Electronic codebook The simplest of the encryption modes is the electronic codebook (ECB) mode. The message is divided into blocks, and each block is encrypted separately. CBC Cipher-block chaining IBM invented the cipher-block chaining (CBC) mode of operation in In CBC mode, each block of plaintext is XORed with the previous ciphertext block before being encrypted. This way, each ciphertext block depends on all plaintext blocks processed up to that point. To make each message unique, an initialization vector must be used in the first block. CFB Cipher feedback The cipher feedback (CFB) mode, a close relative of CBC, makes a block cipher into a self-synchronizing stream cipher. Operation is very similar; in particular, CFB decryption is almost identical to CBC encryption performed in reverse. OFB Output feedback The output feedback (OFB) mode makes a block cipher into a synchronous stream cipher. It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext. Just as with other stream ciphers, flipping a bit in the ciphertext produces a flipped bit in the plaintext at the same location. This property allows many error correcting codes to function normally even when applied before encryption. CTR Counter Like OFB, counter mode turns a block cipher into a stream cipher. It generates the next keystream block by encrypting successive values of a "counter". The counter can be any function which produces a sequence which is guaranteed not to repeat for a long time, although an actual increment-by-one counter is the simplest and most popular. CTR mode has similar characteristics to OFB, but also allows a random access property during decryption. CTR mode (CM) is also known as integer counter mode (ICM) and segmented integer counter (SIC) mode. Modes of operation are nowadays defined by a number of national and internationally recognized standards bodies. Notable standards organizations include NIST, ISO (with ISO/IEC 10116), the IEC, the IEEE, the national ANSI, and the IETF Source: 12
13 13 Key Storage/Management Software Keys Keys stored in Flash or SRAM Keys are accessible by software Keys with 512-bit OTP Storage Keys are never exposed to software No key erase or modification Software only indicates which OTP key should be used Encrypted Software Keys Encrypted keys are stored in the Flash or SRAM OTP Key is dedicated as Key Encryption Key (KEK) Software is never exposed to unencrypted keys (programmatically secure) Randomly Generated Keys Keys are generated randomly by the hardware Software is never exposed to keys (programmatically secure) Can direct hardware to encrypt keys for transmission
14 14 Key Storage - OTP Stores up to 512 bits OTP 4 keys for AES (128 bit key) 2 keys for AES (256 bit key) 8 keys for DES (64 bit key) OTP One Time Programmable Fuse based Cannot be read or overwritten after locked
PIC32 MX1/MX2 Microcontrollers. Dave Richkas Product Marketing Manager High-Performance Microcontroller Division Microchip Technology Inc.
 PIC32 MX1/MX2 Microcontrollers Dave Richkas Product Marketing Manager High-Performance Microcontroller Division Microchip Technology Inc. 2 New PIC32MX1/MX2 Series The smallest and lowest-cost PIC32 microcontrollers
PIC32 MX1/MX2 Microcontrollers Dave Richkas Product Marketing Manager High-Performance Microcontroller Division Microchip Technology Inc. 2 New PIC32MX1/MX2 Series The smallest and lowest-cost PIC32 microcontrollers
CHAPTER 6. SYMMETRIC CIPHERS C = E(K2, E(K1, P))
 CHAPTER 6. SYMMETRIC CIPHERS Multiple encryption is a technique in which an encryption algorithm is used multiple times. In the first instance, plaintext is converted to ciphertext using the encryption
CHAPTER 6. SYMMETRIC CIPHERS Multiple encryption is a technique in which an encryption algorithm is used multiple times. In the first instance, plaintext is converted to ciphertext using the encryption
Introducing: New Low-Cost & Low Pin Count PIC Microcontrollers for the 8-, 16- & 32-bit Markets
 Introducing: New Low-Cost & Low Pin Count PIC Microcontrollers for the 8-, 16- & 32-bit Markets PIC MCU and dspic DSC Family Portfolio 2 New Low Cost, Low Pin-Count 8-, 16-, 32-bit Offerings 3 What Are
Introducing: New Low-Cost & Low Pin Count PIC Microcontrollers for the 8-, 16- & 32-bit Markets PIC MCU and dspic DSC Family Portfolio 2 New Low Cost, Low Pin-Count 8-, 16-, 32-bit Offerings 3 What Are
Block Cipher Operation. CS 6313 Fall ASU
 Chapter 7 Block Cipher Operation 1 Outline q Multiple Encryption and Triple DES q Electronic Codebook q Cipher Block Chaining Mode q Cipher Feedback Mode q Output Feedback Mode q Counter Mode q XTS-AES
Chapter 7 Block Cipher Operation 1 Outline q Multiple Encryption and Triple DES q Electronic Codebook q Cipher Block Chaining Mode q Cipher Feedback Mode q Output Feedback Mode q Counter Mode q XTS-AES
Block Cipher Modes of Operation
 Block Cipher Modes of Operation Luke Anderson luke@lukeanderson.com.au 24th March 2016 University Of Sydney Overview 1. Crypto-Bulletin 2. Modes Of Operation 2.1 Evaluating Modes 2.2 Electronic Code Book
Block Cipher Modes of Operation Luke Anderson luke@lukeanderson.com.au 24th March 2016 University Of Sydney Overview 1. Crypto-Bulletin 2. Modes Of Operation 2.1 Evaluating Modes 2.2 Electronic Code Book
Block Cipher Modes of Operation
 Block Cipher Modes of Operation Luke Anderson luke@lukeanderson.com.au 23 rd March 2018 University Of Sydney Overview 1. Crypto-Bulletin 2. Modes Of Operation 2.1 Evaluating Modes 2.2 Electronic Code Book
Block Cipher Modes of Operation Luke Anderson luke@lukeanderson.com.au 23 rd March 2018 University Of Sydney Overview 1. Crypto-Bulletin 2. Modes Of Operation 2.1 Evaluating Modes 2.2 Electronic Code Book
Content of this part
 UNIVERSITY OF MASSACHUSETTS Dept. of Electrical & Computer Engineering Introduction to Cryptography ECE 597XX/697XX Part 5 More About Block Ciphers Israel Koren ECE597/697 Koren Part.5.1 Content of this
UNIVERSITY OF MASSACHUSETTS Dept. of Electrical & Computer Engineering Introduction to Cryptography ECE 597XX/697XX Part 5 More About Block Ciphers Israel Koren ECE597/697 Koren Part.5.1 Content of this
Connectivity. Ethernet
 Connectivity Ethernet ENC624J600 Stand-Alone 10/100 Ethernet Controller Ethernet Family Roadmap Design Existing 10/100 Base-T Ethernet ENC624J600 24KB Buffer Encryption 44/64 pins NEW PIC32MX 32-bit w/
Connectivity Ethernet ENC624J600 Stand-Alone 10/100 Ethernet Controller Ethernet Family Roadmap Design Existing 10/100 Base-T Ethernet ENC624J600 24KB Buffer Encryption 44/64 pins NEW PIC32MX 32-bit w/
Symmetric Encryption. Thierry Sans
 Symmetric Encryption Thierry Sans Design principles (reminder) 1. Kerkoff Principle The security of a cryptosystem must not rely on keeping the algorithm secret 2. Diffusion Mixing-up symbols 3. Confusion
Symmetric Encryption Thierry Sans Design principles (reminder) 1. Kerkoff Principle The security of a cryptosystem must not rely on keeping the algorithm secret 2. Diffusion Mixing-up symbols 3. Confusion
ECE 646 Lecture 8. Modes of operation of block ciphers
 ECE 646 Lecture 8 Modes of operation of block ciphers Required Reading: I. W. Stallings, "Cryptography and Network-Security," 5 th and 6 th Edition, Chapter 6 Block Cipher Operation II. A. Menezes, P.
ECE 646 Lecture 8 Modes of operation of block ciphers Required Reading: I. W. Stallings, "Cryptography and Network-Security," 5 th and 6 th Edition, Chapter 6 Block Cipher Operation II. A. Menezes, P.
Introduction to Modern Cryptography. Lecture 2. Symmetric Encryption: Stream & Block Ciphers
 Introduction to Modern Cryptography Lecture 2 Symmetric Encryption: Stream & Block Ciphers Stream Ciphers Start with a secret key ( seed ) Generate a keying stream i-th bit/byte of keying stream is a function
Introduction to Modern Cryptography Lecture 2 Symmetric Encryption: Stream & Block Ciphers Stream Ciphers Start with a secret key ( seed ) Generate a keying stream i-th bit/byte of keying stream is a function
CSCI 454/554 Computer and Network Security. Topic 3.2 Secret Key Cryptography Modes of Operation
 CSCI 454/554 Computer and Network Security Topic 3.2 Secret Key Cryptography Modes of Operation Processing with Block Ciphers Most ciphers work on blocks of fixed (small) size How to encrypt long messages?
CSCI 454/554 Computer and Network Security Topic 3.2 Secret Key Cryptography Modes of Operation Processing with Block Ciphers Most ciphers work on blocks of fixed (small) size How to encrypt long messages?
Double-DES, Triple-DES & Modes of Operation
 Double-DES, Triple-DES & Modes of Operation Prepared by: Dr. Mohamed Abd-Eldayem Ref.: Cryptography and Network Security by William Stallings & Lecture slides by Lawrie Brown Multiple Encryption & DES
Double-DES, Triple-DES & Modes of Operation Prepared by: Dr. Mohamed Abd-Eldayem Ref.: Cryptography and Network Security by William Stallings & Lecture slides by Lawrie Brown Multiple Encryption & DES
Using block ciphers 1
 Using block ciphers 1 Using block ciphers DES is a type of block cipher, taking 64-bit plaintexts and returning 64-bit ciphetexts. We now discuss a number of ways in which block ciphers are employed in
Using block ciphers 1 Using block ciphers DES is a type of block cipher, taking 64-bit plaintexts and returning 64-bit ciphetexts. We now discuss a number of ways in which block ciphers are employed in
ECE596C: Handout #7. Analysis of DES and the AES Standard. Electrical and Computer Engineering, University of Arizona, Loukas Lazos
 ECE596C: Handout #7 Analysis of DES and the AES Standard Electrical and Computer Engineering, University of Arizona, Loukas Lazos Abstract. In this lecture we analyze the security properties of DES and
ECE596C: Handout #7 Analysis of DES and the AES Standard Electrical and Computer Engineering, University of Arizona, Loukas Lazos Abstract. In this lecture we analyze the security properties of DES and
Block cipher modes. Lecturers: Mark D. Ryan and David Galindo. Cryptography Slide: 75
 Block cipher modes Lecturers: Mark D. Ryan and David Galindo. Cryptography 2017. Slide: 75 Lecturers: Mark D. Ryan and David Galindo. Cryptography 2017. Slide: 76 Block cipher modes Block ciphers (like
Block cipher modes Lecturers: Mark D. Ryan and David Galindo. Cryptography 2017. Slide: 75 Lecturers: Mark D. Ryan and David Galindo. Cryptography 2017. Slide: 76 Block cipher modes Block ciphers (like
Chapter 8. Encipherment Using Modern Symmetric-Key Ciphers
 Chapter 8 Encipherment Using Modern Symmetric-Key Ciphers Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 8.1 Chapter 18 Objectives To show how modern standard
Chapter 8 Encipherment Using Modern Symmetric-Key Ciphers Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 8.1 Chapter 18 Objectives To show how modern standard
Crypto Library. Microchip Libraries for Applications (MLA) Copyright (c) 2012 Microchip Technology Inc. All rights reserved.
 Crypto Library Microchip Libraries for Applications (MLA) Copyright (c) 2012 Microchip Technology Inc. All rights reserved. MLA - Crypto Library Help Table of Contents 1 Crypto Library 6 1.1 Introduction
Crypto Library Microchip Libraries for Applications (MLA) Copyright (c) 2012 Microchip Technology Inc. All rights reserved. MLA - Crypto Library Help Table of Contents 1 Crypto Library 6 1.1 Introduction
New STM32WB Series MCU with Built-in BLE 5 and IEEE
 New STM32WB Series MCU with Built-in BLE 5 and IEEE 802.15.4 Make the Choice of STM32WB Series The 7 keys points to make the difference 2 Open 2.4 GHz radio Multi-protocol Dual-core / Full control Ultra-low-power
New STM32WB Series MCU with Built-in BLE 5 and IEEE 802.15.4 Make the Choice of STM32WB Series The 7 keys points to make the difference 2 Open 2.4 GHz radio Multi-protocol Dual-core / Full control Ultra-low-power
Chapter 6 Contemporary Symmetric Ciphers
 Chapter 6 Contemporary Symmetric Ciphers "I am fairly familiar with all the forms of secret writings, and am myself the author of a trifling monograph upon the subject, in which I analyze one hundred and
Chapter 6 Contemporary Symmetric Ciphers "I am fairly familiar with all the forms of secret writings, and am myself the author of a trifling monograph upon the subject, in which I analyze one hundred and
ECE 646 Lecture 7. Modes of Operation of Block Ciphers. Modes of Operation. Required Reading:
 C 646 Lecture 7 Modes of Operation of Block Ciphers Required Reading: I. W. Stallings, "Cryptography and Network-Security," 5th dition, Chapter 6 Block Cipher Operation II. A. Menezes, P. van Oorschot,
C 646 Lecture 7 Modes of Operation of Block Ciphers Required Reading: I. W. Stallings, "Cryptography and Network-Security," 5th dition, Chapter 6 Block Cipher Operation II. A. Menezes, P. van Oorschot,
CIS 6930/4930 Computer and Network Security. Topic 3.1 Secret Key Cryptography (Cont d)
 CIS 6930/4930 Computer and Network Security Topic 3.1 Secret Key Cryptography (Cont d) 1 Principles for S-Box Design S-box is the only non-linear part of DES Each row in the S-Box table should be a permutation
CIS 6930/4930 Computer and Network Security Topic 3.1 Secret Key Cryptography (Cont d) 1 Principles for S-Box Design S-box is the only non-linear part of DES Each row in the S-Box table should be a permutation
Processing with Block Ciphers
 AIT 682: Network and Systems Security Topic 3.2 Secret Cryptography Modes of Operation Instructor: r. Kun Sun rocessing with Block Ciphers Most ciphers work on blocks of fixed (small) size How to encrypt
AIT 682: Network and Systems Security Topic 3.2 Secret Cryptography Modes of Operation Instructor: r. Kun Sun rocessing with Block Ciphers Most ciphers work on blocks of fixed (small) size How to encrypt
CSC/ECE 574 Computer and Network Security. Processing with Block Ciphers. Issues for Block Chaining Modes
 CSC/C 574 Computer and Network Security Topic 3.2 Secret Cryptography Modes of Operation CSC/C 574 r. eng Ning 1 rocessing with Block Ciphers Most ciphers work on blocks of fixed (small) size How to encrypt
CSC/C 574 Computer and Network Security Topic 3.2 Secret Cryptography Modes of Operation CSC/C 574 r. eng Ning 1 rocessing with Block Ciphers Most ciphers work on blocks of fixed (small) size How to encrypt
3 Symmetric Key Cryptography 3.1 Block Ciphers Symmetric key strength analysis Electronic Code Book Mode (ECB) Cipher Block Chaining Mode (CBC) Some
 3 Symmetric Key Cryptography 3.1 Block Ciphers Symmetric key strength analysis Electronic Code Book Mode (ECB) Cipher Block Chaining Mode (CBC) Some popular block ciphers Triple DES Advanced Encryption
3 Symmetric Key Cryptography 3.1 Block Ciphers Symmetric key strength analysis Electronic Code Book Mode (ECB) Cipher Block Chaining Mode (CBC) Some popular block ciphers Triple DES Advanced Encryption
Understanding Cryptography A Textbook for Students and Practitioners by Christof Paar and Jan Pelzl
 Understanding Cryptography A Textbook for Students and Practitioners by Christof Paar and Jan Pelzl www.crypto-textbook.com Chapter 5 More About Block Ciphers ver. November 26, 2010 Last modified 10-2-17
Understanding Cryptography A Textbook for Students and Practitioners by Christof Paar and Jan Pelzl www.crypto-textbook.com Chapter 5 More About Block Ciphers ver. November 26, 2010 Last modified 10-2-17
ISO/IEC INTERNATIONAL STANDARD. Information technology Security techniques Modes of operation for an n-bit block cipher
 INTERNATIONAL STANDARD ISO/IEC 10116 Third edition 2006-02-01 Information technology Security techniques Modes of operation for an n-bit block cipher Technologies de l'information Techniques de sécurité
INTERNATIONAL STANDARD ISO/IEC 10116 Third edition 2006-02-01 Information technology Security techniques Modes of operation for an n-bit block cipher Technologies de l'information Techniques de sécurité
Introduction to Cryptography. Lecture 2. Benny Pinkas. Perfect Cipher. Perfect Ciphers. Size of key space
 Perfect Cipher Introduction to Cryptography Lecture 2 Benny Pinkas What type of security would we like to achieve? Given C, the adversary has no idea what M is Impossible since adversary might have a-priori
Perfect Cipher Introduction to Cryptography Lecture 2 Benny Pinkas What type of security would we like to achieve? Given C, the adversary has no idea what M is Impossible since adversary might have a-priori
Seminar: Mobile Systems. Krzysztof Dabkowski Supervisor: Fabio Hecht
 Personal Area Networks Seminar: Mobile Systems November 19th 2009 Krzysztof Dabkowski Supervisor: Fabio Hecht Agenda Motivation Application areas Historical and technical overview Security issues Discussion
Personal Area Networks Seminar: Mobile Systems November 19th 2009 Krzysztof Dabkowski Supervisor: Fabio Hecht Agenda Motivation Application areas Historical and technical overview Security issues Discussion
Secret Key Cryptography
 Secret Key Cryptography General Block Encryption: The general way of encrypting a 64-bit block is to take each of the: 2 64 input values and map it to a unique one of the 2 64 output values. This would
Secret Key Cryptography General Block Encryption: The general way of encrypting a 64-bit block is to take each of the: 2 64 input values and map it to a unique one of the 2 64 output values. This would
Advanced Encryption Standard and Modes of Operation. Foundations of Cryptography - AES pp. 1 / 50
 Advanced Encryption Standard and Modes of Operation Foundations of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) is a symmetric cryptographic algorithm AES has been originally requested
Advanced Encryption Standard and Modes of Operation Foundations of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) is a symmetric cryptographic algorithm AES has been originally requested
Lecture 2B. RTL Design Methodology. Transition from Pseudocode & Interface to a Corresponding Block Diagram
 Lecture 2B RTL Design Methodology Transition from Pseudocode & Interface to a Corresponding Block Diagram Structure of a Typical Digital Data Inputs Datapath (Execution Unit) Data Outputs System Control
Lecture 2B RTL Design Methodology Transition from Pseudocode & Interface to a Corresponding Block Diagram Structure of a Typical Digital Data Inputs Datapath (Execution Unit) Data Outputs System Control
MM23SC8128RM Flash Security Turbo Microcontroller Smart Card Chip With 1024 bit RSA & Maths Co-processor
 Flash Security Turbo Microcontroller Smart Card Chip With 1024 bit RSA & Maths Co-processor 08 September 2009 This document is property of My-MS and My-MS has the right to make any changes to the contents
Flash Security Turbo Microcontroller Smart Card Chip With 1024 bit RSA & Maths Co-processor 08 September 2009 This document is property of My-MS and My-MS has the right to make any changes to the contents
Security Policy for FIPS KVL 3000 Plus
 Security Policy for FIPS 140-2 KVL 3000 Plus Version 01.01.19 Motorola General Business Information 1 of 21 Motorola General Business Information 2 of 21 1 INTRODUCTION... 4 1.1 SCOPE... 4 1.2 OVERVIEW...
Security Policy for FIPS 140-2 KVL 3000 Plus Version 01.01.19 Motorola General Business Information 1 of 21 Motorola General Business Information 2 of 21 1 INTRODUCTION... 4 1.1 SCOPE... 4 1.2 OVERVIEW...
Stream Ciphers. Stream Ciphers 1
 Stream Ciphers Stream Ciphers 1 Stream Ciphers Generate a pseudo-random key stream & xor to the plaintext. Key: The seed of the PRNG Traditional PRNGs (e.g. those used for simulations) are not secure.
Stream Ciphers Stream Ciphers 1 Stream Ciphers Generate a pseudo-random key stream & xor to the plaintext. Key: The seed of the PRNG Traditional PRNGs (e.g. those used for simulations) are not secure.
page 1 Introduction to Cryptography Benny Pinkas Lecture 3 November 18, 2008 Introduction to Cryptography, Benny Pinkas
 Introduction to Cryptography Lecture 3 Benny Pinkas page 1 1 Pseudo-random generator Pseudo-random generator seed output s G G(s) (random, s =n) Deterministic function of s, publicly known G(s) = 2n Distinguisher
Introduction to Cryptography Lecture 3 Benny Pinkas page 1 1 Pseudo-random generator Pseudo-random generator seed output s G G(s) (random, s =n) Deterministic function of s, publicly known G(s) = 2n Distinguisher
CIS 6930/4930 Computer and Network Security. Topic 3.2 Secret Key Cryptography Modes of Operation
 CIS 6930/4930 Computer and Network Security Topic 3.2 Secret Key Cryptography Modes of Operation 1 Cipher Feedback Mode (CFB) IV Key 64 64 64 64 64 M 1 M 2 M 3 M 4 64 64 64 46 + padding 64 64 64 64 C 1
CIS 6930/4930 Computer and Network Security Topic 3.2 Secret Key Cryptography Modes of Operation 1 Cipher Feedback Mode (CFB) IV Key 64 64 64 64 64 M 1 M 2 M 3 M 4 64 64 64 46 + padding 64 64 64 64 C 1
Block Cipher Operation
 Block Cipher Operation Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: 6-1 Overview 1. Double DES, Triple
Block Cipher Operation Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: 6-1 Overview 1. Double DES, Triple
ACR1255U-J1 Secure Bluetooth NFC Reader
 ACR1255U-J1 Secure Bluetooth NFC Reader Technical Specifications V1.07 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 1.1. Smart Card Reader... 3 1.2. Compact Design...
ACR1255U-J1 Secure Bluetooth NFC Reader Technical Specifications V1.07 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 1.1. Smart Card Reader... 3 1.2. Compact Design...
Security Policy: Astro Subscriber Encryption Module Astro Spectra, Astro Saber, Astro Consolette, and Astro XTS3000. Version
 Security Policy: Astro Subscriber Encryption Module Astro Spectra, Astro Saber, Astro Consolette, and Astro XTS3000 Version 02.00.07 3/22/2004 1.0 Introduction 3 1.1 Scope 3 1.2 Overview 3 1.3 Astro Subscriber
Security Policy: Astro Subscriber Encryption Module Astro Spectra, Astro Saber, Astro Consolette, and Astro XTS3000 Version 02.00.07 3/22/2004 1.0 Introduction 3 1.1 Scope 3 1.2 Overview 3 1.3 Astro Subscriber
XMEGA Series Of AVR Processor. Presented by: Manisha Biyani ( ) Shashank Bolia (
 XMEGA Series Of AVR Processor Presented by: Manisha Biyani (200601217) Shashank Bolia (200601200 Existing Microcontrollers Problems with 8/16 bit microcontrollers: Old and inefficient architecture. Most
XMEGA Series Of AVR Processor Presented by: Manisha Biyani (200601217) Shashank Bolia (200601200 Existing Microcontrollers Problems with 8/16 bit microcontrollers: Old and inefficient architecture. Most
CIS 4360 Secure Computer Systems Symmetric Cryptography
 CIS 4360 Secure Computer Systems Symmetric Cryptography Professor Qiang Zeng Spring 2017 Previous Class Classical Cryptography Frequency analysis Never use home-made cryptography Goals of Cryptography
CIS 4360 Secure Computer Systems Symmetric Cryptography Professor Qiang Zeng Spring 2017 Previous Class Classical Cryptography Frequency analysis Never use home-made cryptography Goals of Cryptography
Chapter 3 Block Ciphers and the Data Encryption Standard
 Chapter 3 Block Ciphers and the Data Encryption Standard Last Chapter have considered: terminology classical cipher techniques substitution ciphers cryptanalysis using letter frequencies transposition
Chapter 3 Block Ciphers and the Data Encryption Standard Last Chapter have considered: terminology classical cipher techniques substitution ciphers cryptanalysis using letter frequencies transposition
Stream Ciphers and Block Ciphers
 Stream Ciphers and Block Ciphers Ruben Niederhagen September 18th, 2013 Introduction 2/22 Recall from last lecture: Public-key crypto: Pair of keys: public key for encryption, private key for decryption.
Stream Ciphers and Block Ciphers Ruben Niederhagen September 18th, 2013 Introduction 2/22 Recall from last lecture: Public-key crypto: Pair of keys: public key for encryption, private key for decryption.
Some Aspects of Block Ciphers
 Some Aspects of Block Ciphers Palash Sarkar Applied Statistics Unit Indian Statistical Institute, Kolkata India palash@isical.ac.in CU-ISI Tutorial Workshop on Cryptology, 17 th July 2011 Palash Sarkar
Some Aspects of Block Ciphers Palash Sarkar Applied Statistics Unit Indian Statistical Institute, Kolkata India palash@isical.ac.in CU-ISI Tutorial Workshop on Cryptology, 17 th July 2011 Palash Sarkar
Efficient HVAC System
 Efficient HVAC System Group 6 Sponsored by AC3 Development Group LLC Derick Holzmacher Cory Glass Andrew Mertens Joshua New Motivation HVAC systems are one of the leading energy consuming appliances in
Efficient HVAC System Group 6 Sponsored by AC3 Development Group LLC Derick Holzmacher Cory Glass Andrew Mertens Joshua New Motivation HVAC systems are one of the leading energy consuming appliances in
New STM32WB Series MCU with built-in Bluetooth 5 and IEEE
 New STM32WB Series MCU with built-in Bluetooth 5 and IEEE 802.15.4 Make the Choice of STM32WB Series The 7 keys points to make the difference 2 Open 2.4 GHz radio Multi-protocol Dual-core / Full control
New STM32WB Series MCU with built-in Bluetooth 5 and IEEE 802.15.4 Make the Choice of STM32WB Series The 7 keys points to make the difference 2 Open 2.4 GHz radio Multi-protocol Dual-core / Full control
Zatara Series ARM ASSP High-Performance 32-bit Solution for Secure Transactions
 1 ARM-BASED ASSP FOR SECURE TRANSACTIONS ZATARA SERIES 32-BIT ARM ASSP PB022106-1008 ZATARA SERIES ADVANTAGE SINGLE-CHIP SOLUTION BEST FEATURE SET IN POS PCIPED PRE-CERTIFIED EMV L1 CERTIFIED TOTAL SOLUTION
1 ARM-BASED ASSP FOR SECURE TRANSACTIONS ZATARA SERIES 32-BIT ARM ASSP PB022106-1008 ZATARA SERIES ADVANTAGE SINGLE-CHIP SOLUTION BEST FEATURE SET IN POS PCIPED PRE-CERTIFIED EMV L1 CERTIFIED TOTAL SOLUTION
ECE 545 Lecture 8b. Hardware Architectures of Secret-Key Block Ciphers and Hash Functions. George Mason University
 ECE 545 Lecture 8b Hardware Architectures of Secret-Key Block Ciphers and Hash Functions George Mason University Recommended reading K. Gaj and P. Chodowiec, FPGA and ASIC Implementations of AES, Chapter
ECE 545 Lecture 8b Hardware Architectures of Secret-Key Block Ciphers and Hash Functions George Mason University Recommended reading K. Gaj and P. Chodowiec, FPGA and ASIC Implementations of AES, Chapter
6 Block Ciphers. 6.1 Block Ciphers CA642: CRYPTOGRAPHY AND NUMBER THEORY 1
 CA642: CRYPTOGRAPHY AND NUMBER THEORY 1 6 Block Ciphers 6.1 Block Ciphers Block Ciphers Plaintext is divided into blocks of fixed length and every block is encrypted one at a time. A block cipher is a
CA642: CRYPTOGRAPHY AND NUMBER THEORY 1 6 Block Ciphers 6.1 Block Ciphers Block Ciphers Plaintext is divided into blocks of fixed length and every block is encrypted one at a time. A block cipher is a
Introduction to Cryptography. Lecture 3
 Introduction to Cryptography Lecture 3 Benny Pinkas March 6, 2011 Introduction to Cryptography, Benny Pinkas page 1 Pseudo-random generator seed s (random, s =n) Pseudo-random generator G Deterministic
Introduction to Cryptography Lecture 3 Benny Pinkas March 6, 2011 Introduction to Cryptography, Benny Pinkas page 1 Pseudo-random generator seed s (random, s =n) Pseudo-random generator G Deterministic
March 31, Announcing the PIC16(L)F170X/171X 8-bit MCU Family
 March 31, 2014 Announcing the PIC16(L)F170X/171X 8-bit MCU Family 2 Cost-Effective, Intelligent-Analog 8-bit MCUs Intelligent Analog Integration reduces system BOM cost and board space Two internal Op
March 31, 2014 Announcing the PIC16(L)F170X/171X 8-bit MCU Family 2 Cost-Effective, Intelligent-Analog 8-bit MCUs Intelligent Analog Integration reduces system BOM cost and board space Two internal Op
Microchip Technology Enhances Popular 16- and 32-bit Development Platform with Application-Specific Expansion Hardware
 Editorial Contact: Reader/Literature Inquiries: Eric Lawson 1-888-MCU-MCHP 480-792-7182 www.microchip.com/pictailplus eric.lawson@microchip.com Microchip Technology Enhances Popular 16- and 32-bit Development
Editorial Contact: Reader/Literature Inquiries: Eric Lawson 1-888-MCU-MCHP 480-792-7182 www.microchip.com/pictailplus eric.lawson@microchip.com Microchip Technology Enhances Popular 16- and 32-bit Development
3 Symmetric Cryptography
 CA4005: CRYPTOGRAPHY AND SECURITY PROTOCOLS 1 3 Symmetric Cryptography Symmetric Cryptography Alice Bob m Enc c = e k (m) k c c Dec m = d k (c) Symmetric cryptography uses the same secret key k for encryption
CA4005: CRYPTOGRAPHY AND SECURITY PROTOCOLS 1 3 Symmetric Cryptography Symmetric Cryptography Alice Bob m Enc c = e k (m) k c c Dec m = d k (c) Symmetric cryptography uses the same secret key k for encryption
ZLF645 Crimzon Flash Microcontroller with ZBase Database Industry Leading Universal Infrared Remote Control (UIR) Solution
 digital infrared Solutions CRIMZON ZLF645 Flash MCU uir solution with zbase database CRIMZON ZLF645 advantage 32/64 kb flash 512 b/1 kb ram crimzon z8 lxmc core ir transmission ir learning tuned ir amplifier
digital infrared Solutions CRIMZON ZLF645 Flash MCU uir solution with zbase database CRIMZON ZLF645 advantage 32/64 kb flash 512 b/1 kb ram crimzon z8 lxmc core ir transmission ir learning tuned ir amplifier
Introduction to Network Security Missouri S&T University CPE 5420 Data Encryption Standard
 Introduction to Network Security Missouri S&T University CPE 5420 Data Encryption Standard Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University of
Introduction to Network Security Missouri S&T University CPE 5420 Data Encryption Standard Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University of
Enabling IOT. IQRF Alliance Conference May Harald Weidinger Key Client Manager
 Enabling IOT IQRF Alliance Conference May 2016 Harald Weidinger Key Client Manager IQRF Alliance Conference, May 2016 2 Vision, Mission & Goals Vision : Make Microchip a leading provider of IoT ecosystems,
Enabling IOT IQRF Alliance Conference May 2016 Harald Weidinger Key Client Manager IQRF Alliance Conference, May 2016 2 Vision, Mission & Goals Vision : Make Microchip a leading provider of IoT ecosystems,
Symmetric Encryption Algorithms
 Symmetric Encryption Algorithms CS-480b Dick Steflik Text Network Security Essentials Wm. Stallings Lecture slides by Lawrie Brown Edited by Dick Steflik Symmetric Cipher Model Plaintext Encryption Algorithm
Symmetric Encryption Algorithms CS-480b Dick Steflik Text Network Security Essentials Wm. Stallings Lecture slides by Lawrie Brown Edited by Dick Steflik Symmetric Cipher Model Plaintext Encryption Algorithm
AES1. Ultra-Compact Advanced Encryption Standard Core AES1. General Description. Base Core Features. Symbol. Applications
 General Description The AES core implements Rijndael encoding and decoding in compliance with the NIST Advanced Encryption Standard. Basic core is very small (less than 3,000 gates). Enhanced versions
General Description The AES core implements Rijndael encoding and decoding in compliance with the NIST Advanced Encryption Standard. Basic core is very small (less than 3,000 gates). Enhanced versions
Block Ciphers. Advanced Encryption Standard (AES)
 Network Security - ISA 656 Angelos Stavrou September 28, 2008 Codes vs. K = {0, 1} l P = {0, 1} m C = {0, 1} n, C C E : P K C D : C K P p P, k K : D(E(p, k), k) = p It is infeasible to find F : P C K Let
Network Security - ISA 656 Angelos Stavrou September 28, 2008 Codes vs. K = {0, 1} l P = {0, 1} m C = {0, 1} n, C C E : P K C D : C K P p P, k K : D(E(p, k), k) = p It is infeasible to find F : P C K Let
Join the forward thinkers who rely on Toshiba for wireless connectivity ICs.
 ELECTRONIC COMPONENTS Wireless Communication Solutions Join the forward thinkers who rely on Toshiba for wireless connectivity ICs. Bluetooth Low Power Near Field Communications High Speed Wireless Power
ELECTRONIC COMPONENTS Wireless Communication Solutions Join the forward thinkers who rely on Toshiba for wireless connectivity ICs. Bluetooth Low Power Near Field Communications High Speed Wireless Power
Computer Security. 08. Cryptography Part II. Paul Krzyzanowski. Rutgers University. Spring 2018
 Computer Security 08. Cryptography Part II Paul Krzyzanowski Rutgers University Spring 2018 March 23, 2018 CS 419 2018 Paul Krzyzanowski 1 Block ciphers Block ciphers encrypt a block of plaintext at a
Computer Security 08. Cryptography Part II Paul Krzyzanowski Rutgers University Spring 2018 March 23, 2018 CS 419 2018 Paul Krzyzanowski 1 Block ciphers Block ciphers encrypt a block of plaintext at a
STM32 Cortex-M3 STM32F STM32L STM32W
 STM32 Cortex-M3 STM32F STM32L STM32W 01 01 STM32 Cortex-M3 introduction to family 1/2 STM32F combine high performance with first-class peripherals and lowpower, low-voltage operation. They offer the maximum
STM32 Cortex-M3 STM32F STM32L STM32W 01 01 STM32 Cortex-M3 introduction to family 1/2 STM32F combine high performance with first-class peripherals and lowpower, low-voltage operation. They offer the maximum
DataTraveler 5000 (DT5000) and DataTraveler 6000 (DT6000) Ultimate Security in a USB Flash Drive. Submitted by SPYRUS, Inc.
 Submitted by SPYRUS, Inc. Contents DT5000 and DT6000 Technology Overview...2 Why DT5000 and DT6000 Encryption Is Different...3 Why DT5000 and DT6000 Encryption Is Different - Summary...4 XTS-AES Sector-Based
Submitted by SPYRUS, Inc. Contents DT5000 and DT6000 Technology Overview...2 Why DT5000 and DT6000 Encryption Is Different...3 Why DT5000 and DT6000 Encryption Is Different - Summary...4 XTS-AES Sector-Based
Cypress PSoC 4 Microcontrollers
 Cypress PSoC 4 Microcontrollers Your Problem-Solver on Chip WWW.CYPRESS.COM/PSOC4 THE DIFFERENTIATION DILEMMA Embedded systems are rapidly advancing with innovative features added at each new product generation.
Cypress PSoC 4 Microcontrollers Your Problem-Solver on Chip WWW.CYPRESS.COM/PSOC4 THE DIFFERENTIATION DILEMMA Embedded systems are rapidly advancing with innovative features added at each new product generation.
Modes of Operation. Raj Jain. Washington University in St. Louis
 Modes of Operation Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at : http://www.cse.wustl.edu/~jain/cse567-06/
Modes of Operation Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at : http://www.cse.wustl.edu/~jain/cse567-06/
1 Achieving IND-CPA security
 ISA 562: Information Security, Theory and Practice Lecture 2 1 Achieving IND-CPA security 1.1 Pseudorandom numbers, and stateful encryption As we saw last time, the OTP is perfectly secure, but it forces
ISA 562: Information Security, Theory and Practice Lecture 2 1 Achieving IND-CPA security 1.1 Pseudorandom numbers, and stateful encryption As we saw last time, the OTP is perfectly secure, but it forces
Connectivity Solutions for Embedded Design:
 Connectivity Solutions Spring 2011 Connectivity Solutions for Embedded Design: USB, Ethernet, Wi-Fi, ZigBee, MiWi, CAN, LIN, IrDA and RS-485 Protocols www.microchip.com/connectivity Scalable and Integrated
Connectivity Solutions Spring 2011 Connectivity Solutions for Embedded Design: USB, Ethernet, Wi-Fi, ZigBee, MiWi, CAN, LIN, IrDA and RS-485 Protocols www.microchip.com/connectivity Scalable and Integrated
Data Encryption Standard (DES)
 Data Encryption Standard (DES) Best-known symmetric cryptography method: DES 1973: Call for a public cryptographic algorithm standard for commercial purposes by the National Bureau of Standards Goals:
Data Encryption Standard (DES) Best-known symmetric cryptography method: DES 1973: Call for a public cryptographic algorithm standard for commercial purposes by the National Bureau of Standards Goals:
TI SimpleLink dual-band CC1350 wireless MCU
 TI SimpleLink dual-band CC1350 wireless MCU Sub-1 GHz and Bluetooth low energy in a single-chip Presenter Low-Power Connectivity Solutions 1 SimpleLink ultra-low power platform CC2640: Bluetooth low energy
TI SimpleLink dual-band CC1350 wireless MCU Sub-1 GHz and Bluetooth low energy in a single-chip Presenter Low-Power Connectivity Solutions 1 SimpleLink ultra-low power platform CC2640: Bluetooth low energy
New 70 MIPS dspic33ep and PIC24EP Family High Performance, Integrated Analog, Easy Migration
 New 70 MIPS dspic33ep and PIC24EP Family High Performance, Integrated Analog, Easy Migration Charlie Ice, Product Marketing Microchip Technology Inc. 2 dspic33ep & PIC24EP Highlights 70MIPS of Performance
New 70 MIPS dspic33ep and PIC24EP Family High Performance, Integrated Analog, Easy Migration Charlie Ice, Product Marketing Microchip Technology Inc. 2 dspic33ep & PIC24EP Highlights 70MIPS of Performance
Block ciphers used to encode messages longer than block size Needs to be done correctly to preserve security Will look at five ways of doing this
 Lecturers: Mark D. Ryan and David Galindo. Cryptography 2015. Slide: 74 Block ciphers used to encode messages longer than block size Needs to be done correctly to preserve security Will look at five ways
Lecturers: Mark D. Ryan and David Galindo. Cryptography 2015. Slide: 74 Block ciphers used to encode messages longer than block size Needs to be done correctly to preserve security Will look at five ways
L9: Stream and Block Ciphers. Hui Chen, Ph.D. Dept. of Engineering & Computer Science Virginia State University Petersburg, VA 23806
 L9: Stream and Block Ciphers Hui Chen, Ph.D. Dept. of Engineering & Computer Science Virginia State University Petersburg, VA 23806 10/19/2016 CSCI 451 -Fall 2016 1 Acknowledgement Many slides are from
L9: Stream and Block Ciphers Hui Chen, Ph.D. Dept. of Engineering & Computer Science Virginia State University Petersburg, VA 23806 10/19/2016 CSCI 451 -Fall 2016 1 Acknowledgement Many slides are from
BlackBerry BlackBerry 10 OS, version continues to build on the BlackBerry 10 platform for the Z10, Q10 and Z30 devices.
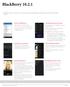 BlackBerry 10.2.1 BlackBerry 10 OS, version 10.2.1 continues to build on the BlackBerry 10 platform for the Z10, Q10 and Z30 devices. PINCH TO PRIORITIZE Don t miss important messages Pinch the Hub to
BlackBerry 10.2.1 BlackBerry 10 OS, version 10.2.1 continues to build on the BlackBerry 10 platform for the Z10, Q10 and Z30 devices. PINCH TO PRIORITIZE Don t miss important messages Pinch the Hub to
Introducing STM32 L0x Series. April
 Introducing STM32 L0x Series April 2014 www.emcu.it 20- to 80pins 20- to 100pins 48- to 144pins Memory size (Bytes) ST s Ultra-low-power Continuum (1/2) 2 512K 256K 192K STM32L0 Cortex TM -M0+ STM32L1
Introducing STM32 L0x Series April 2014 www.emcu.it 20- to 80pins 20- to 100pins 48- to 144pins Memory size (Bytes) ST s Ultra-low-power Continuum (1/2) 2 512K 256K 192K STM32L0 Cortex TM -M0+ STM32L1
Introduction to Symmetric Cryptography
 Introduction to Symmetric Cryptography Tingting Chen Cal Poly Pomona 1 Some slides are from Dr. Cliff Zou. www.cs.ucf.edu/~czou/cis3360-12/ch08-cryptoconcepts.ppt Basic Cryptography Private Key Cryptography
Introduction to Symmetric Cryptography Tingting Chen Cal Poly Pomona 1 Some slides are from Dr. Cliff Zou. www.cs.ucf.edu/~czou/cis3360-12/ch08-cryptoconcepts.ppt Basic Cryptography Private Key Cryptography
Connectivity Solutions for Embedded Design:
 Connectivity Solutions Summer 2010 Connectivity Solutions for Embedded Design: USB, Ethernet, Wi-Fi, ZigBee, MiWi, CAN, LIN, IrDA and RS-485 Protocols www.microchip.com/connectivity Scalable and Integrated
Connectivity Solutions Summer 2010 Connectivity Solutions for Embedded Design: USB, Ethernet, Wi-Fi, ZigBee, MiWi, CAN, LIN, IrDA and RS-485 Protocols www.microchip.com/connectivity Scalable and Integrated
Cypress PSoC 4 Microcontrollers
 Cypress PSoC Microcontrollers Your Problem-Solver on Chip WWW.CYPRESS.COM/PSOC THE DIFFERENTIATION DILEMMA Embedded systems are rapidly advancing with innovative features added at each new product generation.
Cypress PSoC Microcontrollers Your Problem-Solver on Chip WWW.CYPRESS.COM/PSOC THE DIFFERENTIATION DILEMMA Embedded systems are rapidly advancing with innovative features added at each new product generation.
Modern Symmetric Block cipher
 Modern Symmetric Block cipher 81 Shannon's Guide to Good Ciphers Amount of secrecy should determine amount of labour appropriate for encryption and decryption The set of keys and enciphering algorithm
Modern Symmetric Block cipher 81 Shannon's Guide to Good Ciphers Amount of secrecy should determine amount of labour appropriate for encryption and decryption The set of keys and enciphering algorithm
Introduction to Cryptography. Lecture 3
 Introduction to Cryptography Lecture 3 Benny Pinkas March 6, 2011 Introduction to Cryptography, Benny Pinkas page 1 Pseudo-random generator seed s (random, s =n) Pseudo-random generator G Deterministic
Introduction to Cryptography Lecture 3 Benny Pinkas March 6, 2011 Introduction to Cryptography, Benny Pinkas page 1 Pseudo-random generator seed s (random, s =n) Pseudo-random generator G Deterministic
Introduction to Cryptographic Systems. Asst. Prof. Mihai Chiroiu
 Introduction to Cryptographic Systems Asst. Prof. Mihai Chiroiu Vocabulary In cryptography, cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Decryption
Introduction to Cryptographic Systems Asst. Prof. Mihai Chiroiu Vocabulary In cryptography, cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Decryption
Network Security Essentials Chapter 2
 Network Security Essentials Chapter 2 Fourth Edition by William Stallings Lecture slides by Lawrie Brown Encryption What is encryption? Why do we need it? No, seriously, let's discuss this. Why do we need
Network Security Essentials Chapter 2 Fourth Edition by William Stallings Lecture slides by Lawrie Brown Encryption What is encryption? Why do we need it? No, seriously, let's discuss this. Why do we need
STM32F7 series ARM Cortex -M7 powered Releasing your creativity
 STM32F7 series ARM Cortex -M7 powered Releasing your creativity STM32 high performance Very high performance 32-bit MCU with DSP and FPU The STM32F7 with its ARM Cortex -M7 core is the smartest MCU and
STM32F7 series ARM Cortex -M7 powered Releasing your creativity STM32 high performance Very high performance 32-bit MCU with DSP and FPU The STM32F7 with its ARM Cortex -M7 core is the smartest MCU and
SAM A5 ARM Cortex - A5 MPUs
 SAM A5 ARM Cortex - A5 MPUs Industry s lowest-power MPUs Ideal for secure industry, IoT, wearable applications Operating at 600MHz/945DMIPS with low power consumption, the SAMA5 ARM Cortex-A5 based MPU
SAM A5 ARM Cortex - A5 MPUs Industry s lowest-power MPUs Ideal for secure industry, IoT, wearable applications Operating at 600MHz/945DMIPS with low power consumption, the SAMA5 ARM Cortex-A5 based MPU
CSC 474/574 Information Systems Security
 CSC 474/574 Information Systems Security Topic 2.2 Secret Key Cryptography CSC 474/574 Dr. Peng Ning 1 Agenda Generic block cipher Feistel cipher DES Modes of block ciphers Multiple encryptions Message
CSC 474/574 Information Systems Security Topic 2.2 Secret Key Cryptography CSC 474/574 Dr. Peng Ning 1 Agenda Generic block cipher Feistel cipher DES Modes of block ciphers Multiple encryptions Message
IDEA, RC5. Modes of operation of block ciphers
 C 646 - Lecture 8 IDA, RC5 Modes of operation of block ciphers Required Reading: I. W. Stallings, "Cryptography and Network-Security," 5th dition, Chapter 6 Block Cipher Operation II. A. Menezes, P. van
C 646 - Lecture 8 IDA, RC5 Modes of operation of block ciphers Required Reading: I. W. Stallings, "Cryptography and Network-Security," 5th dition, Chapter 6 Block Cipher Operation II. A. Menezes, P. van
Jaap van Ginkel Security of Systems and Networks
 Jaap van Ginkel Security of Systems and Networks November 4, 2013 Part 4 Modern Crypto Block Ciphers (Iterated) Block Cipher Plaintext and ciphertext consist of fixed-sized blocks Ciphertext obtained from
Jaap van Ginkel Security of Systems and Networks November 4, 2013 Part 4 Modern Crypto Block Ciphers (Iterated) Block Cipher Plaintext and ciphertext consist of fixed-sized blocks Ciphertext obtained from
Crypto: Symmetric-Key Cryptography
 Computer Security Course. Song Crypto: Symmetric-Key Cryptography Slides credit: Dan Boneh, David Wagner, Doug Tygar Overview Cryptography: secure communication over insecure communication channels Three
Computer Security Course. Song Crypto: Symmetric-Key Cryptography Slides credit: Dan Boneh, David Wagner, Doug Tygar Overview Cryptography: secure communication over insecure communication channels Three
An Introduction to Key Management for Secure Storage. Walt Hubis, LSI Corporation
 An Introduction to Key Management for Secure Storage Walt Hubis, LSI Corporation SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA. Member companies and individuals may
An Introduction to Key Management for Secure Storage Walt Hubis, LSI Corporation SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA. Member companies and individuals may
Stream Ciphers and Block Ciphers
 Stream Ciphers and Block Ciphers 2MMC10 Cryptology Fall 2015 Ruben Niederhagen October 6th, 2015 Introduction 2/32 Recall: Public-key crypto: Pair of keys: public key for encryption, private key for decryption.
Stream Ciphers and Block Ciphers 2MMC10 Cryptology Fall 2015 Ruben Niederhagen October 6th, 2015 Introduction 2/32 Recall: Public-key crypto: Pair of keys: public key for encryption, private key for decryption.
Acronyms. International Organization for Standardization International Telecommunication Union ITU Telecommunication Standardization Sector
 Acronyms 3DES AES AH ANSI CBC CESG CFB CMAC CRT DoS DEA DES DoS DSA DSS ECB ECC ECDSA ESP FIPS IAB IETF IP IPsec ISO ITU ITU-T Triple DES Advanced Encryption Standard Authentication Header American National
Acronyms 3DES AES AH ANSI CBC CESG CFB CMAC CRT DoS DEA DES DoS DSA DSS ECB ECC ECDSA ESP FIPS IAB IETF IP IPsec ISO ITU ITU-T Triple DES Advanced Encryption Standard Authentication Header American National
Corporate Profile. Applying minds to technology
 Corporate Profile AEM is the leading provider of indigenously designed & built technology solutions in India. We have addressed the most challenging real-time communication & collaboration needs of defense
Corporate Profile AEM is the leading provider of indigenously designed & built technology solutions in India. We have addressed the most challenging real-time communication & collaboration needs of defense
Stream ciphers. Lecturers: Mark D. Ryan and David Galindo. Cryptography Slide: 91
 Stream ciphers Lecturers: Mark D. Ryan and David Galindo. Cryptography 2017. Slide: 91 Lecturers: Mark D. Ryan and David Galindo. Cryptography 2017. Slide: 92 Stream Cipher Suppose you want to encrypt
Stream ciphers Lecturers: Mark D. Ryan and David Galindo. Cryptography 2017. Slide: 91 Lecturers: Mark D. Ryan and David Galindo. Cryptography 2017. Slide: 92 Stream Cipher Suppose you want to encrypt
Lecture 1 Applied Cryptography (Part 1)
 Lecture 1 Applied Cryptography (Part 1) Patrick P. C. Lee Tsinghua Summer Course 2010 1-1 Roadmap Introduction to Security Introduction to Cryptography Symmetric key cryptography Hash and message authentication
Lecture 1 Applied Cryptography (Part 1) Patrick P. C. Lee Tsinghua Summer Course 2010 1-1 Roadmap Introduction to Security Introduction to Cryptography Symmetric key cryptography Hash and message authentication
Network Security Essentials
 Network Security Essentials Applications and Standards Third Edition William Stallings Chapter 2 Symmetric Encryption and Message Confidentiality Dr. BHARGAVI H. GOSWAMI Department of Computer Science
Network Security Essentials Applications and Standards Third Edition William Stallings Chapter 2 Symmetric Encryption and Message Confidentiality Dr. BHARGAVI H. GOSWAMI Department of Computer Science
Homework 2. Out: 09/23/16 Due: 09/30/16 11:59pm UNIVERSITY OF MARYLAND DEPARTMENT OF ELECTRICAL AND COMPUTER ENGINEERING
 UNIVERSITY OF MARYLAND DEPARTMENT OF ELECTRICAL AND COMPUTER ENGINEERING ENEE 457 Computer Systems Security Instructor: Charalampos Papamanthou Homework 2 Out: 09/23/16 Due: 09/30/16 11:59pm Instructions
UNIVERSITY OF MARYLAND DEPARTMENT OF ELECTRICAL AND COMPUTER ENGINEERING ENEE 457 Computer Systems Security Instructor: Charalampos Papamanthou Homework 2 Out: 09/23/16 Due: 09/30/16 11:59pm Instructions
16-bit Embedded Control Solutions
 16-bit Microcontrollers and Digital Signal Controllers March 2008 16-bit Embedded Control Solutions PIC24 Microcontrollers dspic Digital Signal Controllers www.microchip.com/16bit 16-bit Embedded Control
16-bit Microcontrollers and Digital Signal Controllers March 2008 16-bit Embedded Control Solutions PIC24 Microcontrollers dspic Digital Signal Controllers www.microchip.com/16bit 16-bit Embedded Control
Sensor Networks. Xueying Zhang, Howard M. Heys, and Cheng Li. Electrical and Computer Engineering. Faculty of Engineering and Applied Science
 Energy Efficiency of Encryption Schemes Applied to Wireless Sensor Networks Xueying Zhang, Howard M. Heys, and Cheng Li Electrical and Computer Engineering Faculty of Engineering and Applied Science Memorial
Energy Efficiency of Encryption Schemes Applied to Wireless Sensor Networks Xueying Zhang, Howard M. Heys, and Cheng Li Electrical and Computer Engineering Faculty of Engineering and Applied Science Memorial
SmartBond DA Smallest, lowest power and most integrated Bluetooth 5 SoC. Applications DA14585
 SmartBond DA14585 Smallest, lowest power and most integrated Bluetooth 5 SoC Connected devices are constantly evolving. New generations appear that are smarter, more full featured and have longer battery
SmartBond DA14585 Smallest, lowest power and most integrated Bluetooth 5 SoC Connected devices are constantly evolving. New generations appear that are smarter, more full featured and have longer battery
Introduction to cryptology (GBIN8U16)
 Introduction to cryptology (GBIN8U16) Finite fields, block ciphers Pierre Karpman pierre.karpman@univ-grenoble-alpes.fr https://www-ljk.imag.fr/membres/pierre.karpman/tea.html 2018 01 31 Finite fields,
Introduction to cryptology (GBIN8U16) Finite fields, block ciphers Pierre Karpman pierre.karpman@univ-grenoble-alpes.fr https://www-ljk.imag.fr/membres/pierre.karpman/tea.html 2018 01 31 Finite fields,
