SHOULDER SURFING ATTACK PREVENTION USING COLOR PASS METHOD
|
|
|
- Thomasina Bryant
- 6 years ago
- Views:
Transcription
1 SHOULDER SURFING ATTACK PREVENTION USING COLOR PASS METHOD Bagade Om, Sonawane Anuja, Patil Akash, Patil Yogita, Maurya Jagruti Department of Computer Engineering Shram sadhana trust s college of engineering & technology, Bambhori, Jalgaon *** Abstract The traditional PIN mechanism is mostly used for authentication. It is popular method due to its usability and security. Though it is secure method, it often leads to direct observational attack, such as human shoulder-surfing and camera based recording. In this paper proposed system provides implementation of color pass methods to defend against shoulder surfing attack. User can enter the session without revealing the actual PIN. It provide strong security against shoulder surfing attacks and have intelligent user interface. Key Words Color PIN, User Interface, Lookup table, Shoulder surfing Attacks. 1. INTRODUCTION In shoulder surfing attack, the amount of internet users has been reportable as approximately a pair of 4 billion worldwide, and from 2000 to 2015, it's a staggering 566.4%increase. This huge range of users consists of various genuine users and malicious users as well which try to access sensitive and private data of other users. So its necessary to provide protection to the system so that genuine and malicious users are often identified properly. In computer security, authentication is such a technique by that the system identifies the real users. Among several authentication schemes, password based authentication method is still one of the mostly accepted solution due to its ease of use and value effectiveness. Though conventional PIN entry mechanism is mostly famous due to its easy usability, however it's prone to shoulder surfing attack during which an attacker will record the login procedure of a user for an entire session and can retrieve the users original PIN. based on the knowledge available to the attacker, secure login ways are often classified into two broad classes as totally observable and partially observable. In the first class, the attacker will totally observe the whole login procedure for a particular session and in the second, the attacker will partially observe the login procedure. The proposed Color Pass methodology implements onetime pass method. In this method corresponding to four color PINs, the user gets four challenges and enters four responses with respect to every challenge. The great benefit of Color Pass scheme is that it's easy to use and doesn't need any pre-knowledge. In addition to the presentations against shoulder surfing attack, it also provides equal password strength which is better than the traditional PIN entry scheme. 2. LITURATURE SURVEY L. Sobrado Graphical passwords, The Rutgers Scholar, an Electronic Bulletin for Undergraduate analysis proposed three shoulder surfing resistant graphical password schemes, the Movable Frame scheme, the Intersection scheme, and the Triangle scheme [6]. To overcome the drawbacks of Sobrado and Birgets scheme, the Convex Hull Click (CHC) is proposed by Wiedenbeck et al., 'Design and analysis of a shoulder-sarong resistant graphical password scheme'. Improved version of Triangle scheme with great security and usability [5]. Convex-Hull Click scheme has long login time. To overcome the shoulder surfing attack, a graphical password scheme which uses color login and provide resistant to the shoulder surfing attack is proposed by gao et al [1]. Design and analysis of a graphical password scheme. Background color could be a usable factor for reducing the login time. A text-based shoulder surfing resistant graphical password scheme in which the user has got to find his textual password and so follow a 2017, IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1367
2 special rule to mix his textual password to get a session password to login the system is proposed by H. Zhao and X. Li [2], S3PAS: A scalable shoulder-sarong resistant textual graphical password authentication scheme. A text-based shoulder surfing resistant graphical password scheme by using colors is proposed by Sreelatha et al. 'M. Sreelatha, M. Anirudh, Md. grand Turk Ahamer, and V. Manoj Kumar [3]. Authentication schemes for session passwords using color and images, International Journal of Network Security & Its applications'. Clearly, as the user has got to additionally study the order of many colours, the memory burden of the user is high. To avoid the above drawbacks we'll describe a straightforward and efficient technique for the shoulder surfing Attack using Texts and color primarily based graphical password scheme [4], it uses ten decimal numbers. 3. EXISTING SYSTEM Shoulder surfing attacks are not new. In literature, we find many graphics based techniques to prevent such shoulder surfing attacks. However, we will discuss here a number of the partially observable schemes to propose the color Pass scheme. It includes number of various techniques like Movable Frame theme, the Intersection theme, the triangle theme, convex Hull Click theme (CHC), graphical password scheme that uses color login but generally there's possibility of password recognized by the third person or hacker. The problem is password isn't protected by the existing techniques. The proposed solution is somewhat more efficient than the existing ones. Colorpass strategies are comparatively new fields of password preventions that are being explored for advancement within the existing preventive techniques. The colorpass strategies makes use of the concept of entering the PIN ofuser without revealing the actual PIN and hence prevent from shoulder surfing attacks. 4. PROPOSED SYSTEM A. System architecture: The proposed system is based on observable attacker model, In this attacker cannot identify the actual pin of the user but attacker can only see the response values entered by the user which are different than the original pin. Thus it's assumed that user gets the challenge digits for ensuring security against man-in-middle attack. This all replicated through the four methods as follows: 1. Mod ten table method. 2. Shoulder surfing Safe Login method. 3. BW method. 4. Color pass method. The general architecture of proposed system is as shown in following figure 4.1. Which takes input as account no if user has already registered otherwise he has to register first by entering all the information. After selecting the method which user wants he has to enter account number and the challenge digit which is automatically generated by selected method. According to challenge digit generated user will enter response value and then user will login to the system as an output of the proposed system. 2017, IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1368
3 1.1 System architecture of MOD10 table Method: Figure 4.1: General System architecture Figure 4.2 describes architecture of Mod ten table method. In Mod ten table method, firstly user enters his account number which is already stored in database. Then system generates challenge digits. After that, system generates MOD10 table from which user can enter correct look up value. Finally user will login the system. 1.2 System architecture of SSSL: Figure 4.2: System architecture of MOD10 table method Figure 4.3 describes architecture of SSSL method. In SSSL method firstly user enters his account number which is already stored in database. Then system generates challenge digits randomly. After that, table for orientation of digit and the computer keyboard structure for SSSL method display on screen. From which user calculate his response digits and press appropriate directions with respect to table. Finally user login the system. 2017, IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1369
4 1.3 System architecture of Black and White Method: Figure 4.3: System architecture of SSSL method Figure 4.4 describes architecture of Black and White method (BW). In BW method, firstly user enters his account number which is already stored in database. Then system generates challenge digits. After that, color boundary table is displayed from boundary table user enters proper color according to challenge digits. Finally user login the system. 1.4 System architecture of Colorpass Method: Figure 4.4: System architecture of BW method Figure 4.5 describes architecture of Color pass method. In colorpass method, firstly user enters his account number which is already stored in database. Then system generates challenge digits. After that, compare actual PIN predefined color table. Find no corresponding to that color in feature table. Then users enter the number on the respected color as his response value. Finally user login the system. Figure 4.5: System architecture of Colorpass Method. 2017, IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1370
5 B. METHODOLOGY: 1.1 Mod 10 table method : In this technique Perkovic proposed a concept of lookup table. If user selected PIN digit is nine and also the system generated challenge is six then the user looks in the row number six in the lookup table i.e. (Figure 4.6) and afterwards user finds the digit nine in that row i.e. in sixth row after that user can see for the respective column number where nine is placed (here one) and enter back 1 as response corresponding to the one challenge. If the digits in the top row of table are arranged in ascending order from zero to nine then it'll be equivalent as modulo ten additions. Hence the name of the table is justified. But one of the drawbacks of this method is login time during this method login time goes high with respect to modulo ten technique. 1.2 SSSL Method: Fig 4.6: User Lookup table In SSSL method user does not need to provide numbers as response instead of user enters some directions as response to the system. In this scheme user has to remember four digits PIN number. In orders to authenticate themselves the user needs to response to the challenge values shown to them with respect to the orientation table and arrow keyboard shown in Fig. 4.7 the table in SSSL method created in such a way that each digit i is a neighbour to alternative eight digits from the set 1, (see Fig. 4.7[a] i.e. Orientation of digits). User find the relative position of their original PIN digits and therefore the challenge values via keyboard shown in (Fig. 4.7[b] i.e. keyboard structure for SSSL) the subsequent example will provides a clear plan regarding SSSL methodology. For Example, Suppose the actual password of user is 3895 and the challenge digit generated by the system is The digit 1 is placed left side to the 1 in Fig. 4.7[a] so that the user press the left side arrow. Again actual PIN digit is 8 and challenge digit is 2 then press up arrow. When challenge digit and actual PIN are same then press self arrow. Fig. 4.7: (a) Orientation of digits (b) Keypad structure for SSSL 2017, IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1371
6 1.3 BW Method: We study the BW technique more and acquire the subsequent results, each by experimentation and on paper, regarding the scheme. The shoulder-surfing resilient versions hold severe round redundancy, and this can be exploited by adversaries. The black and white key presses throughout PIN entries are unbalanced, and this can be exploited by the adversaries. 1.4 PIN Entry Mechanism in Color Pass: Fig. 4.8: BW method In this scheme, the user chosen PIN is four colors. Throughout the login procedure, when the Feature Tables seem inside the screen then the system throws some challenge values to the user. Challenge values vary from 1 to 10. Supported the challenge worth the user has got to pick the corresponding Feature Table. As an example, challenge value four indicates that the user possesses to seem inside the Fourth Feature Table. User will receive challenge corresponding to every color of his PIN. The challenge values generates randomly by the system. Once getting each challenge value, user selects a Feature Table. Then corresponding to the chosen color PIN, he locates the color cell in that table. The user then finds the digit therein color cell and enters that digit as response to the challenge. Equally user will reply to the other three challenge values and may complete the login method. Valid response to the challenge values will authenticate the user. Fig. 4.9: User Interface On Screen 2017, IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1372
7 Fig. 4.10: Used colors for implementing feature tables For example, suppose actual PIN is 1,2,3,4 then first user look at in fig and conform the respective predefined colors then system generates the challenge digit. Suppose challenge digit is 6,7,8,9. After that, user selects the feature table Fig. 4.9 with respect to its challenge digits. Then the user gives the response value with respect to challenge digit and color to the system and user gets login. C. ALGORITHMS:[4] Algorithm for color pass method: Algorithm 1 :Generating tables in Color Pass Input: This algorithm can take array Color [0,1,...9] as input. Output: it will generate Feature Tables FT(0)...FT(9) for i = 0 to 9 do for j = 0 to 9 do FT(i).CELL(j).Color Color[j] FT(i).CELL(j).Value (i+j) mod 10; end for end for Algorithm 2: Evaluating User Response in Color Pass Input: This algorithm can take array UCOL, array CLICK and array RAN as input. Output: This algorithm can update value of array EVAL by one for each valid response. for i = 0 to 3 do K RAN[i] , IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1373
8 Valid (UCOL[i] + K) mod 10 if CLICK[i] := Valid then EVAL[i] 1 end if end for Algorithm 3: User Authentication Input: This algorithm can take array EVAL as input after executing algorithm two. Output: Decides whether user is allowed to Login. Initialize X := 0 for i = 0 to 3 do if EVAL[i] := 1 then X 1 else X 0 break end if end for if X := 1 then Allow user to Login else Disallow the user end if 5. RESULT: SSAPCM is used to prevent attackers to see the password while entering from behind. It is used for the security purpose of owners account. In this we implement four methods that Pare 1. Mod10 method 2. SSSL method 3. Color Pass Method 4. BW method 2017, IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1374
9 In this system, user's information is stored in Mysql database which is shown in Fig This database contain all the user's detail which is required for registration. Figure 5.1: User database Then user will select one of the method for login procedure and then they enter their account number such that after that system will generate a challenge digit randomly such as 3344 for above account number. Original pin is remembered by the user itself suppose it is 1234.Using that challenge digit and original pin user will perform calculation and get response value which they enter as their original pin and calculation is different for every method. After that user will safely login to the system. These methods provide security in their own way and thus differ from each other. From result, we compare four methods based on two parameters that are time complexity and user friendliness. The result of comparison is shown in below table 5.1. Table 5.1: Comparison between Method Methods Mod 10 Table method Time Consumption Less User Friendliness More SSSL Method More Less Colorpass Method Less Less BW Method Less More 6. CONCLUSION: Proposed system will implementing color pass mechanism for shoulder surfing attacks. In this color pass mechanism four methods that are SSSL, BW, Mod10 table & color pass are implemented to prevent shoulder surfing attacks. It provides an intelligent interface for users to login into system in a public domain. From security point of view these different methods are quite robust against some possible attacks such as shoulder surfing, guessing password, side channel attack, etc. And from usability point of view the scheme is user friendly and takes very less time for login. 2017, IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1375
10 7. REFERENCES [1] R. Dai, and H. Gao, Design and analysis of a graphical password scheme, Proc. of 4th Int. Conf. on Innovative Computing, data and control, pages , December [2] X. Li, and H. Zhao, S3pas: A {scalable shoulder-sur_ng resistant textual-graphical password authentication scheme, Proc. of 21st Int. Conf. on Advanced information Networking and Applications Workshops, 2:467472, May [3] M. Anirudh, and M. Sreelatha, Authentication schemes for session passwords using color and images, International Journal of Network Security and Its Applications, 3(3), May [4] Samrat Mondal, and Nilesh Chakraborty, Color pass: an intelligent user interface to resist shoulder surfing attack, IEEE, [5] J. Birget, and S. Wiedenbeck, design and analysis of a shoulder-surfing resistant graphical password scheme, proc. of working conf. on advanced visual interfaces. IEEE, pages 177{184, May 2006 }. [6] L. Sobrado, and Graphical passwords, the rutgers scholar, an electronic bulletin for undergraduate analysis, IEEE, 4, [7] Jin Hong, and Taekyoung Kwon, Analysis and improvement of a pin entry method resilient to shouldersurfing and recording attacks, IEEE, 10(2), february , IRJET Impact Factor value: ISO 9001:2008 Certified Journal Page 1376
Minimizing Shoulder Surfing Attack using Text and Color Based Graphical Password Scheme
 Minimizing Shoulder Surfing Attack using Text and Color Based Graphical Password Scheme 1 Prof. S. K. Sonkar, 2 Prof. R. L. Paikrao Computer Engineering Dept. Amrutvahini College of engineering Sangamner,
Minimizing Shoulder Surfing Attack using Text and Color Based Graphical Password Scheme 1 Prof. S. K. Sonkar, 2 Prof. R. L. Paikrao Computer Engineering Dept. Amrutvahini College of engineering Sangamner,
Simple Text Based Colour Shuffling Graphical Password Scheme
 Simple Text Based Colour Shuffling Graphical Password Scheme Nikita Parab 1, Ketan Gawde 2, Anshumaan Nalluri 3 1,2,3 Information Technology Dept., Universal College Of Engineering Vasai India, Abstract
Simple Text Based Colour Shuffling Graphical Password Scheme Nikita Parab 1, Ketan Gawde 2, Anshumaan Nalluri 3 1,2,3 Information Technology Dept., Universal College Of Engineering Vasai India, Abstract
3LAS (Three Level Authentication Scheme)
 3LAS (Three Level Authentication Scheme) Kunal Mulwani 1, Saurabh Naik 2, Navinkumar Gurnani 3, Dr. Nupur Giri 4, Prof. Sharmila Sengupta 5 1, 2,3,4,5 Vivekanand Education Society's Institute of Technology,
3LAS (Three Level Authentication Scheme) Kunal Mulwani 1, Saurabh Naik 2, Navinkumar Gurnani 3, Dr. Nupur Giri 4, Prof. Sharmila Sengupta 5 1, 2,3,4,5 Vivekanand Education Society's Institute of Technology,
USING EMOJI PICTURES TO STRENGTHEN THE IMMUNITY OF PASSWORDS AGAINST ATTACKERS
 USING EMOJI PICTURES TO STRENGTHEN THE IMMUNITY OF PASSWORDS AGAINST ATTACKERS Dr. Mohammed A. Fadhil Al-Husainy Raghda Ahmed Malih Department of Computer Science, Faculty of Information Technology, Middle
USING EMOJI PICTURES TO STRENGTHEN THE IMMUNITY OF PASSWORDS AGAINST ATTACKERS Dr. Mohammed A. Fadhil Al-Husainy Raghda Ahmed Malih Department of Computer Science, Faculty of Information Technology, Middle
Authentication Using Grid-Based Authentication Scheme and Graphical Password
 Authentication Using Grid-Based Authentication Scheme and Graphical Password Vijayshri D. Vaidya 1 Department of Computer engineering SND COE & RC Yeola, India Imaran R. Shaikh 2 Department of Computer
Authentication Using Grid-Based Authentication Scheme and Graphical Password Vijayshri D. Vaidya 1 Department of Computer engineering SND COE & RC Yeola, India Imaran R. Shaikh 2 Department of Computer
Graphical User Authentication System An Overview P. Baby Maruthi 1, Dr. K. Sandhya Rani 2
 Graphical User Authentication System An Overview P. Baby Maruthi 1, Dr. K. Sandhya Rani 2 1 Research Scholar: Dept of Computer Science S.P.M.V.V, Tirupati, Andhra Pradesh, India mail2maruthi03@gmail.com
Graphical User Authentication System An Overview P. Baby Maruthi 1, Dr. K. Sandhya Rani 2 1 Research Scholar: Dept of Computer Science S.P.M.V.V, Tirupati, Andhra Pradesh, India mail2maruthi03@gmail.com
NETWORK SECURITY - OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION
 NETWORK SECURITY - OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION P.Kiruthika R.Tamilarasi Department of Computer Applications, Dr.Mahalingam College Of Engineering and Technology,
NETWORK SECURITY - OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION P.Kiruthika R.Tamilarasi Department of Computer Applications, Dr.Mahalingam College Of Engineering and Technology,
A Hybrid Password Authentication Scheme Based on Shape and Text
 JOURNAL OF COMPUTERS, VOL. 5, NO. 5, MAY 2010 765 A Hybrid Password Authentication Scheme Based on Shape and Text Ziran Zheng School of Management & Economics Shandong Normal University, Jinan, China Email:
JOURNAL OF COMPUTERS, VOL. 5, NO. 5, MAY 2010 765 A Hybrid Password Authentication Scheme Based on Shape and Text Ziran Zheng School of Management & Economics Shandong Normal University, Jinan, China Email:
A SURVEY ON IMPROVEMENT OF A PIN- ENTRYMETHOD RESILIENT TO SHOULDER- SURFING ANDRECORDING ATTACKS
 A SURVEY ON IMPROVEMENT OF A PIN- ENTRYMETHOD RESILIENT TO SHOULDER- SURFING ANDRECORDING ATTACKS MAYUR SHINDE 1, ADITYA KULKARNI 2, HRUSHIKESH DOLAS 3,PALLAVI TEKE 4 1 Dept. of Computer Engineering, Sinhgad
A SURVEY ON IMPROVEMENT OF A PIN- ENTRYMETHOD RESILIENT TO SHOULDER- SURFING ANDRECORDING ATTACKS MAYUR SHINDE 1, ADITYA KULKARNI 2, HRUSHIKESH DOLAS 3,PALLAVI TEKE 4 1 Dept. of Computer Engineering, Sinhgad
DESIGN, IMPLEMENTATION AND EVALUATION OF A KNOWLEDGE BASED AUTHENTICATION SCHEME UPON COMPELLING PLAIT CLICKS
 http:// DESIGN, IMPLEMENTATION AND EVALUATION OF A KNOWLEDGE BASED AUTHENTICATION SCHEME UPON COMPELLING PLAIT CLICKS Chalichima Harshitha 1, Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor
http:// DESIGN, IMPLEMENTATION AND EVALUATION OF A KNOWLEDGE BASED AUTHENTICATION SCHEME UPON COMPELLING PLAIT CLICKS Chalichima Harshitha 1, Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor
SHOULDER SURFING RESISTANT GRAPHICAL PASSWORD
 SHOULDER SURFING RESISTANT GRAPHICAL PASSWORD Kruthi K 1, Kumuda B G 2, Nandhini N V 3, Mrs. R.Anitha 4 (Associate Professor) 1, 2, 3, 4 Department of Computer Science and Engineering, The National Institute
SHOULDER SURFING RESISTANT GRAPHICAL PASSWORD Kruthi K 1, Kumuda B G 2, Nandhini N V 3, Mrs. R.Anitha 4 (Associate Professor) 1, 2, 3, 4 Department of Computer Science and Engineering, The National Institute
MULTIPLE GRID BASED GRAPHICAL TEXT PASSWORD AUTHENTICATION
 MULTIPLE GRID BASED GRAPHICAL TEXT PASSWORD AUTHENTICATION Vinothini T 1, Rajesh I 2, Kirupa Rani D 3 1 PG Scholar, Dept of CSE, Knowledge Institute of Technology, Salem, Tamil Nadu, India 2 Associate
MULTIPLE GRID BASED GRAPHICAL TEXT PASSWORD AUTHENTICATION Vinothini T 1, Rajesh I 2, Kirupa Rani D 3 1 PG Scholar, Dept of CSE, Knowledge Institute of Technology, Salem, Tamil Nadu, India 2 Associate
Authentication schemes for session password using color and special characters
 Authentication schemes for session password using color and special characters Rohit Jagtap1, a, Vaibhav Ahirrao2,b Vinayak Kadam3,c Nilesh Aher4 1.Department of Computer Engineering, 2 Department of Computer
Authentication schemes for session password using color and special characters Rohit Jagtap1, a, Vaibhav Ahirrao2,b Vinayak Kadam3,c Nilesh Aher4 1.Department of Computer Engineering, 2 Department of Computer
A PIN Entry Scheme Resistant to Recording-based Shoulder-Surfing
 2009 Third International Conference on Emerging Security Information, Systems and Technologies A PIN Entry Scheme Resistant to Recording-based Shoulder-Surfing Peipei Shi, Bo Zhu, and Amr Youssef Concordia
2009 Third International Conference on Emerging Security Information, Systems and Technologies A PIN Entry Scheme Resistant to Recording-based Shoulder-Surfing Peipei Shi, Bo Zhu, and Amr Youssef Concordia
A Survey On Resisting Shoulder Surfing Attack Using Graphical. password
 A Survey On Resisting Shoulder Surfing Attack Using Graphical Password Mayuri Gawandi 1,Saloni Pate 2,Pokharkar Snehal 3,Prof.Said S.K. 4 Abstract Now a days India is moving towards a digital India while
A Survey On Resisting Shoulder Surfing Attack Using Graphical Password Mayuri Gawandi 1,Saloni Pate 2,Pokharkar Snehal 3,Prof.Said S.K. 4 Abstract Now a days India is moving towards a digital India while
Novel Shoulder-Surfing Resistant Authentication Schemes using Text-Graphical Passwords
 Institute of Advanced Engineering and Science International Journal of Information & Network Security (IJINS) Vol.1, No.3, August 2012, pp. 163~170 ISSN: 2089-3299 163 Novel Shoulder-Surfing Resistant
Institute of Advanced Engineering and Science International Journal of Information & Network Security (IJINS) Vol.1, No.3, August 2012, pp. 163~170 ISSN: 2089-3299 163 Novel Shoulder-Surfing Resistant
Graphical User Authentication Using Random Codes
 Graphical User Authentication Using Random Codes Mr.D.S.Gawande 1, Manisha P. Thote 2, Madhavi M. Jangam 3, Payal P. Khonde 4, Payal R. Katre 5, Rohini V. Tiwade 6 1Assistant Professor, Computer Science
Graphical User Authentication Using Random Codes Mr.D.S.Gawande 1, Manisha P. Thote 2, Madhavi M. Jangam 3, Payal P. Khonde 4, Payal R. Katre 5, Rohini V. Tiwade 6 1Assistant Professor, Computer Science
Usable Privacy and Security, Fall 2011 Nov. 10, 2011
 Usable Privacy and Security, Fall 2011 Nov. 10, 2011 YoungSeok Yoon (youngseok@cs.cmu.edu) Institute for Software Research School of Computer Science Carnegie Mellon University picture/photo based vs.
Usable Privacy and Security, Fall 2011 Nov. 10, 2011 YoungSeok Yoon (youngseok@cs.cmu.edu) Institute for Software Research School of Computer Science Carnegie Mellon University picture/photo based vs.
USER AUTHENTICATION USING NATIVE LANGUAGE PASSWORDS
 USER AUTHENTICATION USING NATIVE LANGUAGE PASSWORDS Sreelatha Malempati Dept. of Computer Science & Engineering R.V.R. & J.C. College of Engineering Chowdavaram, Guntur, A.P lathamoturi@rediffmail.com
USER AUTHENTICATION USING NATIVE LANGUAGE PASSWORDS Sreelatha Malempati Dept. of Computer Science & Engineering R.V.R. & J.C. College of Engineering Chowdavaram, Guntur, A.P lathamoturi@rediffmail.com
Defenses against Large Scale Online Password Guessing by Using Persuasive Cued Click Points
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Graphical Authentication System
 Graphical Authentication System A Sivasankar Reddy 1, M Kusuma 2 1 Student, Dept. of MCA, EAIMS 2 Professor, Dept. of MCA, EAIMS, Tirupati, A.P. Abstract- This evolution brings great convenience but also
Graphical Authentication System A Sivasankar Reddy 1, M Kusuma 2 1 Student, Dept. of MCA, EAIMS 2 Professor, Dept. of MCA, EAIMS, Tirupati, A.P. Abstract- This evolution brings great convenience but also
A Text based Authentication Scheme for Improving Security of Textual Passwords
 A Text based Authentication Scheme for Improving Security of Textual Passwords Shah Zaman Nizamani Department of Information Technology Quaid-e-Awam University of Engineering, Science & Technology, Pakistan
A Text based Authentication Scheme for Improving Security of Textual Passwords Shah Zaman Nizamani Department of Information Technology Quaid-e-Awam University of Engineering, Science & Technology, Pakistan
3D PASSWORD AUTHENTICATION FOR WEB SECURITY
 3D PASSWORD AUTHENTICATION FOR WEB SECURITY Sahana R.Gadagkar 1, Aditya Pawaskar 2, Mrs. Ranjeeta B. Pandhare 3 1,2 Department of Computer Science & Engineering, KIT s College of Engineering, Kolhapur,
3D PASSWORD AUTHENTICATION FOR WEB SECURITY Sahana R.Gadagkar 1, Aditya Pawaskar 2, Mrs. Ranjeeta B. Pandhare 3 1,2 Department of Computer Science & Engineering, KIT s College of Engineering, Kolhapur,
An image edge based approach for image password encryption
 SECURITY AND COMMUNICATION NETWORKS Security Comm. Networks 2016; 9:5733 5745 Published online 16 January 2017 in Wiley Online Library (wileyonlinelibrary.com)..1732 RESEARCH ARTICLE An image edge based
SECURITY AND COMMUNICATION NETWORKS Security Comm. Networks 2016; 9:5733 5745 Published online 16 January 2017 in Wiley Online Library (wileyonlinelibrary.com)..1732 RESEARCH ARTICLE An image edge based
Presented By: Miss Samya Ashraf Want Student ID
 Paper: Haichang Gao, Xiyang Liu, Sidong Wang and Honggang Liu, Ruyi Dai, Design and Analysis of a Graphical Password Scheme, Fourth International Conference on Innovative Computing, Information and Control,
Paper: Haichang Gao, Xiyang Liu, Sidong Wang and Honggang Liu, Ruyi Dai, Design and Analysis of a Graphical Password Scheme, Fourth International Conference on Innovative Computing, Information and Control,
ENHANCEMENT OF SECURITY FEATURE IN GRAPHICAL PASSWORD AUTHENTICATION
 International Journal of Computer Science Engineering and Information Technology Research (IJCSEITR) ISSN 2249-6831 Vol. 3, Issue 2, Jun 2013, 395-402 TJPRC Pvt. Ltd. ENHANCEMENT OF SECURITY FEATURE IN
International Journal of Computer Science Engineering and Information Technology Research (IJCSEITR) ISSN 2249-6831 Vol. 3, Issue 2, Jun 2013, 395-402 TJPRC Pvt. Ltd. ENHANCEMENT OF SECURITY FEATURE IN
II. LITERATURE SURVEY
 Secure Transaction By Using Wireless Password with Shuffling Keypad Shweta Jamkavale 1, Ashwini Kute 2, Rupali Pawar 3, Komal Jamkavale 4,Prashant Jawalkar 5 UG students 1,2,3,4, Guide 5, Department Of
Secure Transaction By Using Wireless Password with Shuffling Keypad Shweta Jamkavale 1, Ashwini Kute 2, Rupali Pawar 3, Komal Jamkavale 4,Prashant Jawalkar 5 UG students 1,2,3,4, Guide 5, Department Of
KNOWLEDGE BASED AUTHENTICATION SYSTEM DESIGN BASED ON PERSUASIVE CUED CLICK POINTS
 http:// KNOWLEDGE BASED AUTHENTICATION SYSTEM DESIGN BASED ON PERSUASIVE CUED CLICK POINTS G Anil Kumar 1, K Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor (CSE), Nalanda Institute of Engineering
http:// KNOWLEDGE BASED AUTHENTICATION SYSTEM DESIGN BASED ON PERSUASIVE CUED CLICK POINTS G Anil Kumar 1, K Devika Rani 2 1 Pursuing M.tech (CSE), 2 Assistant professor (CSE), Nalanda Institute of Engineering
Securing Web Accounts Using Graphical Password Authentication through MD5 Algorithm
 Securing Web Accounts Using Graphical Password Authentication through MD5 Algorithm Siddheshwar A. Suratkar Rahul A. Udgirkar Pratik D. Kale Amit A. Shelke Mohsin H. Shaikh Prof. D. C. Dhanwani Prof. CSE,
Securing Web Accounts Using Graphical Password Authentication through MD5 Algorithm Siddheshwar A. Suratkar Rahul A. Udgirkar Pratik D. Kale Amit A. Shelke Mohsin H. Shaikh Prof. D. C. Dhanwani Prof. CSE,
Graphical Password Authentication: Methods and Schemes
 Graphical Password Authentication: Methods and Schemes Geeta M. Rane, Student (BE) of Computer Science and Engineering, Shri Sant Gadge Baba College of Engineering & Technology, Bhusawal, North Maharashtra
Graphical Password Authentication: Methods and Schemes Geeta M. Rane, Student (BE) of Computer Science and Engineering, Shri Sant Gadge Baba College of Engineering & Technology, Bhusawal, North Maharashtra
International Journal of Emerging Technology in Computer Science & Electronics (IJETCSE) ISSN: Volume 14 Issue 2 APRIL 2015
 Persuasive Cued Click Point Authentication Mechanism with Sound Signature MOUNESHWAR KANAMADI 1,AMIT SAWANT 2,JAMDADE MARUTI 3,4 MEGHARANI BAMBUGADE, 5 ROKADE KOMAL 1 Department of CSE, Ashokrao Mane Group
Persuasive Cued Click Point Authentication Mechanism with Sound Signature MOUNESHWAR KANAMADI 1,AMIT SAWANT 2,JAMDADE MARUTI 3,4 MEGHARANI BAMBUGADE, 5 ROKADE KOMAL 1 Department of CSE, Ashokrao Mane Group
Cued Click Point Technique for Graphical Password Authentication
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Color Code PIN Authentication System Using. Multi-TouchTechnology
 Color Code PIN Authentication System Using Multi-TouchTechnology K. Abinaya 1, T. Pavithra 2, P. Divya 3, S.Hema malini 4 Mrs. S. Hema malini, Associate Professor, Dept. of Computer Science & Engineering,
Color Code PIN Authentication System Using Multi-TouchTechnology K. Abinaya 1, T. Pavithra 2, P. Divya 3, S.Hema malini 4 Mrs. S. Hema malini, Associate Professor, Dept. of Computer Science & Engineering,
Cryptography and Network Security. Prof. D. Mukhopadhyay. Department of Computer Science and Engineering. Indian Institute of Technology, Kharagpur
 Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 38 A Tutorial on Network Protocols
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 38 A Tutorial on Network Protocols
ABSTRACT I. INTRODUCTION
 2018 IJSRSET Volume 4 Issue 4 Print ISSN: 2395-1990 Online ISSN : 2394-4099 Themed Section : Engineering and Technology An Efficient Search Method over an Encrypted Cloud Data Dipeeka Radke, Nikita Hatwar,
2018 IJSRSET Volume 4 Issue 4 Print ISSN: 2395-1990 Online ISSN : 2394-4099 Themed Section : Engineering and Technology An Efficient Search Method over an Encrypted Cloud Data Dipeeka Radke, Nikita Hatwar,
A New Graphical Password: Combination of Recall & Recognition Based Approach
 A New Graphical Password: Combination of Recall & Recognition Based Approach Md. Asraful Haque, Babbar Imam International Science Index, Computer and Information Engineering waset.org/publication/9997703
A New Graphical Password: Combination of Recall & Recognition Based Approach Md. Asraful Haque, Babbar Imam International Science Index, Computer and Information Engineering waset.org/publication/9997703
Innovative Graphical Passwords using Sequencing and Shuffling Together
 Innovative Graphical Passwords using Sequencing and Shuffling Together Rashmi Wable 1, Dr.Suhas Raut 2 N.K. Orchid College of Engineering and Technology, Solapur ABSTRACT Graphical authentication technology
Innovative Graphical Passwords using Sequencing and Shuffling Together Rashmi Wable 1, Dr.Suhas Raut 2 N.K. Orchid College of Engineering and Technology, Solapur ABSTRACT Graphical authentication technology
Defending Shoulder Surfing Attacks in Secure Transactions using Multi Color Technique
 Defending Shoulder Surfing Attacks in Secure Transactions using Multi Color Technique 1 M.R.Divya, 2 A.P.Janani Department of Computer Science and Engineering, Sri Subramanya College of Engineering and
Defending Shoulder Surfing Attacks in Secure Transactions using Multi Color Technique 1 M.R.Divya, 2 A.P.Janani Department of Computer Science and Engineering, Sri Subramanya College of Engineering and
LOAD BALANCING AND DEDUPLICATION
 LOAD BALANCING AND DEDUPLICATION Mr.Chinmay Chikode Mr.Mehadi Badri Mr.Mohit Sarai Ms.Kshitija Ubhe ABSTRACT Load Balancing is a method of distributing workload across multiple computing resources such
LOAD BALANCING AND DEDUPLICATION Mr.Chinmay Chikode Mr.Mehadi Badri Mr.Mohit Sarai Ms.Kshitija Ubhe ABSTRACT Load Balancing is a method of distributing workload across multiple computing resources such
AN IMPROVED MAP BASED GRAPHICAL ANDROID AUTHENTICATION SYSTEM
 AN IMPROVED MAP BASED GRAPHICAL ANDROID AUTHENTICATION SYSTEM Safiyanu Ahmad (ahmadsafiyanu100@gmail.com) 1 ; Souley Boukari (bsouley2001@yahoo.com) 2 ; Samson Henry Dogo (dogojankasa@gmail.com) 1 and
AN IMPROVED MAP BASED GRAPHICAL ANDROID AUTHENTICATION SYSTEM Safiyanu Ahmad (ahmadsafiyanu100@gmail.com) 1 ; Souley Boukari (bsouley2001@yahoo.com) 2 ; Samson Henry Dogo (dogojankasa@gmail.com) 1 and
On Limitations of Designing Leakage-Resilient Password Systems: Attacks, Principles and Usability
 On Limitations of Designing Leakage-Resilient Password Systems: Attacks, Principles and Usability Qiang Yan, Jin Han, Yingjiu Li, Robert H. Deng School of Information Systems, Singapore Management University
On Limitations of Designing Leakage-Resilient Password Systems: Attacks, Principles and Usability Qiang Yan, Jin Han, Yingjiu Li, Robert H. Deng School of Information Systems, Singapore Management University
Multi-Color Technique and Session Key Method to Prevent Shoulder Surfing Attacks in Secure Transactions M. R. Divya 1 A. P.
 IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 02, 2015 ISSN (online): 2321-0613 Multi-Color Technique and Session Key Method to Prevent Shoulder Surfing Attacks in Secure
IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 02, 2015 ISSN (online): 2321-0613 Multi-Color Technique and Session Key Method to Prevent Shoulder Surfing Attacks in Secure
A Password Authentication Method Tolerant to Video-recording Attacks analyzing Multiple Authentication Operations
 A Password Authentication Method Tolerant to Video-recording Attacks analyzing Multiple Authentication Operations Yutaka Hirakawa, Yutaro Kogure, and Kazuo Ohzeki Abstract User authentication is widely
A Password Authentication Method Tolerant to Video-recording Attacks analyzing Multiple Authentication Operations Yutaka Hirakawa, Yutaro Kogure, and Kazuo Ohzeki Abstract User authentication is widely
ColorDots: An Intersection Analysis Resistant Graphical Password Scheme for the Prevention of Shoulder-surfing Attack
 UNF Digital Commons UNF Theses and Dissertations Student Scholarship 2012 ColorDots: An Intersection Analysis Resistant Graphical Password Scheme for the Prevention of Shoulder-surfing Attack Jim Littleton
UNF Digital Commons UNF Theses and Dissertations Student Scholarship 2012 ColorDots: An Intersection Analysis Resistant Graphical Password Scheme for the Prevention of Shoulder-surfing Attack Jim Littleton
Graphical password authentication using Pass faces
 RESEARCH ARTICLE OPEN ACCESS Graphical password authentication using Pass faces Ms Grinal Tuscano*, Aakriti Tulasyan**, Akshata Shetty**, Malvina Rumao**, Aishwarya Shetty ** *(Department of Information
RESEARCH ARTICLE OPEN ACCESS Graphical password authentication using Pass faces Ms Grinal Tuscano*, Aakriti Tulasyan**, Akshata Shetty**, Malvina Rumao**, Aishwarya Shetty ** *(Department of Information
AUTHENTICATION SCHEME USING ROTATING PATTERN PASSWORD MUHAMMAD FAISAL BIN DAUD
 AUTHENTICATION SCHEME USING ROTATING PATTERN PASSWORD MUHAMMAD FAISAL BIN DAUD BANCHELOR OF COMPUTER SCIENCE (NETWORK SECURITY) FACULTY INFORMATICS AND COMPUTING UNIVERSITI SULTAN ZAINAL ABIDIN 2018 DECLARATION
AUTHENTICATION SCHEME USING ROTATING PATTERN PASSWORD MUHAMMAD FAISAL BIN DAUD BANCHELOR OF COMPUTER SCIENCE (NETWORK SECURITY) FACULTY INFORMATICS AND COMPUTING UNIVERSITI SULTAN ZAINAL ABIDIN 2018 DECLARATION
Defending Shoulder Surfing Attacks in Secure Transactions Using Session Key Method
 Defending Shoulder Surfing Attacks in Secure Transactions Using Session Key Method M. R.Divya, A.P.Janani, Abstract To improve the security of the various devices, the graphical password is a memorable
Defending Shoulder Surfing Attacks in Secure Transactions Using Session Key Method M. R.Divya, A.P.Janani, Abstract To improve the security of the various devices, the graphical password is a memorable
A Multi-Grid Graphical Password Scheme
 A Multi-Grid Graphical Password Scheme Konstantinos CHALKIAS, Anastasios ALEXIADIS, George STEPHANIDES Dept. of Applied Informatics, Macedonia University, 156 Egnatia str., 540 06 Thessaloniki, Greece
A Multi-Grid Graphical Password Scheme Konstantinos CHALKIAS, Anastasios ALEXIADIS, George STEPHANIDES Dept. of Applied Informatics, Macedonia University, 156 Egnatia str., 540 06 Thessaloniki, Greece
Algorithm To Ensure And Enforce Brute-Force Attack-Resilient Password In Routers
 Algorithm To Ensure And Enforce Brute-Force Attack-Resilient Password In Routers Mohammed Farik, ABM Shawkat Ali Abstract: Issues of weak login passwords arising from default passwords in wired and wireless
Algorithm To Ensure And Enforce Brute-Force Attack-Resilient Password In Routers Mohammed Farik, ABM Shawkat Ali Abstract: Issues of weak login passwords arising from default passwords in wired and wireless
An Ancient Indian Board Game as a Tool for Authentication
 An Ancient Indian Board Game as a Tool for Authentication Sreelatha Malempati 1 and Shashi Mogalla 2 1 Department of Computer Science and Engineering RVR & JC College of Engineering, Guntur, A.P. e-mail:
An Ancient Indian Board Game as a Tool for Authentication Sreelatha Malempati 1 and Shashi Mogalla 2 1 Department of Computer Science and Engineering RVR & JC College of Engineering, Guntur, A.P. e-mail:
Graphical Password to Increase the Capacity of Alphanumeric Password
 Graphical Password to Increase the Capacity of Alphanumeric Password Gaddam Ramu Computer Science & Engineering. S.R.Engineering College, Warangal, Telangana, India. Goje Roopa(Asst.Prof) Computer Science
Graphical Password to Increase the Capacity of Alphanumeric Password Gaddam Ramu Computer Science & Engineering. S.R.Engineering College, Warangal, Telangana, India. Goje Roopa(Asst.Prof) Computer Science
PREVENTING HUMAN SHOULDER SURFING AND TO PROVIDE RESISTANCE AGAINST PIN ENTRY
 PREVENTING HUMAN SHOULDER SURFING AND TO PROVIDE RESISTANCE AGAINST PIN ENTRY J.Rajalakshmi and V.Valarmathi Assistant Professor ME, Computer Science and Engineering, SKR Engineering College, Chennai,
PREVENTING HUMAN SHOULDER SURFING AND TO PROVIDE RESISTANCE AGAINST PIN ENTRY J.Rajalakshmi and V.Valarmathi Assistant Professor ME, Computer Science and Engineering, SKR Engineering College, Chennai,
Palm Vein Extraction and Matching For Personal Identification
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. IX (Mar-Apr. 2014), PP 64-68 Palm Vein Extraction and Matching For Personal Identification
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. IX (Mar-Apr. 2014), PP 64-68 Palm Vein Extraction and Matching For Personal Identification
Pixel Value Graphical Password Scheme-Graphical Password Scheme Literature Review
 Australian Journal of Basic and Applied Sciences, 7(4): 688-695, 2013 ISSN 1991-8178 Pixel Value Graphical Password Scheme-Graphical Password Scheme Literature Review Mohd Afizi Bin Mohd Shukran, Mohd
Australian Journal of Basic and Applied Sciences, 7(4): 688-695, 2013 ISSN 1991-8178 Pixel Value Graphical Password Scheme-Graphical Password Scheme Literature Review Mohd Afizi Bin Mohd Shukran, Mohd
Introduction to Security and User Authentication
 Introduction to Security and User Authentication Brad Karp UCL Computer Science CS GZ03 / M030 14 th November 2016 Topics We ll Cover User login authentication (local and remote) Cryptographic primitives,
Introduction to Security and User Authentication Brad Karp UCL Computer Science CS GZ03 / M030 14 th November 2016 Topics We ll Cover User login authentication (local and remote) Cryptographic primitives,
DOUBLE CHECKING: MULTIMODAL, INTEGRATIVE & CONTINUOUS VERIFICATION TECHNOLOGY OF SIGNATURE & FINGER PRINT IDENTIFICATION
 DOUBLE CHECKING: MULTIMODAL, INTEGRATIVE & CONTINUOUS VERIFICATION TECHNOLOGY OF SIGNATURE & FINGER PRINT IDENTIFICATION 1 V.Rajesh, 2 V.Shyamsundar, 3 R.Naveenraj, 4 Mr.N.Karthik, 1,2,3 UG Scholars, Sri
DOUBLE CHECKING: MULTIMODAL, INTEGRATIVE & CONTINUOUS VERIFICATION TECHNOLOGY OF SIGNATURE & FINGER PRINT IDENTIFICATION 1 V.Rajesh, 2 V.Shyamsundar, 3 R.Naveenraj, 4 Mr.N.Karthik, 1,2,3 UG Scholars, Sri
SECURED PASSWORD MANAGEMENT TECHNIQUE USING ONE-TIME PASSWORD PROTOCOL IN SMARTPHONE
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 3, March 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 3, March 2014,
Keywords security model, online banking, authentication, biometric, variable tokens
 Volume 4, Issue 11, November 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Authentication
Volume 4, Issue 11, November 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Authentication
A Model to Restrict Online Password Guessing Attacks
 A Model to Restrict Online Password Guessing Attacks Aqib Malik, Dr. Sanjay Jamwal Department of Computer Science, Baba Ghulam Shah Badshah University, Rajouri, J&K, India Abstract Passwords are a critical
A Model to Restrict Online Password Guessing Attacks Aqib Malik, Dr. Sanjay Jamwal Department of Computer Science, Baba Ghulam Shah Badshah University, Rajouri, J&K, India Abstract Passwords are a critical
Divide and Conquer Approach for Solving Security and Usability Conflict in User Authentication
 Divide and Conquer Approach for Solving Security and Usability Conflict in User Authentication Shah Zaman Nizamani Waqas Ali Sahito Shafique Awan Department of IT Department of IT Department of Computer
Divide and Conquer Approach for Solving Security and Usability Conflict in User Authentication Shah Zaman Nizamani Waqas Ali Sahito Shafique Awan Department of IT Department of IT Department of Computer
Survey Paper on Efficient and Secure Dynamic Auditing Protocol for Data Storage in Cloud
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s
 CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
Types of Software Testing: Different Testing Types with Details
 Types of Software Testing: Different Testing Types with Details What are the different Types of Software Testing? We, as testers are aware of the various types of Software Testing such as Functional Testing,
Types of Software Testing: Different Testing Types with Details What are the different Types of Software Testing? We, as testers are aware of the various types of Software Testing such as Functional Testing,
A Secure Graphical Password Authentication System
 International Journal of Computational Intelligence Research ISSN 0973-1873 Volume 12, Number 2 (2016), pp. 197-201 Research India Publications http://www.ripublication.com A Secure Graphical Password
International Journal of Computational Intelligence Research ISSN 0973-1873 Volume 12, Number 2 (2016), pp. 197-201 Research India Publications http://www.ripublication.com A Secure Graphical Password
Recall Based Authentication System- An Overview
 Recall Based Authentication System- An Overview P. Baby Maruthi 1, Dr. K. Sandhya Rani 2 1 Research Scholar: Dept of Computer Science S.P.M.V.V, Tirupati, Andhra Pradesh, India 2 Professor: Dept of Computer
Recall Based Authentication System- An Overview P. Baby Maruthi 1, Dr. K. Sandhya Rani 2 1 Research Scholar: Dept of Computer Science S.P.M.V.V, Tirupati, Andhra Pradesh, India 2 Professor: Dept of Computer
A Modified Approach for Kerberos Authentication Protocol with Secret Image by using Visual Cryptography
 A Modified Approach for Kerberos Authentication Protocol with Secret Image by using Visual Cryptography Ashok Kumar J 1, and Gopinath Ganapathy 2 1,2 School of Computer Science, Engineering and Applications
A Modified Approach for Kerberos Authentication Protocol with Secret Image by using Visual Cryptography Ashok Kumar J 1, and Gopinath Ganapathy 2 1,2 School of Computer Science, Engineering and Applications
International Journal of Pure and Applied Sciences and Technology
 Int. J. Pure Appl. Sci. Technol., 1(2) (2010), pp. 60-66 International Journal of Pure and Applied Sciences and Technology ISSN 2229-6107 Available online at www.ijopaasat.in Research Paper Security Analysis
Int. J. Pure Appl. Sci. Technol., 1(2) (2010), pp. 60-66 International Journal of Pure and Applied Sciences and Technology ISSN 2229-6107 Available online at www.ijopaasat.in Research Paper Security Analysis
Dept. of computer Science & Engineering, VelTech Hightech Dr. Rangarajan Dr. Sakunthala Engineering College, Avadi, Chennai 2
 Secured pin entry method for ATM using steganopin and session key methods S. Shanmuga Priya 1*, Ancy Breen W 1, V.S Rajkumar 1, Latha 2 1 Dept. of computer Science & Engineering, VelTech Hightech Dr. Rangarajan
Secured pin entry method for ATM using steganopin and session key methods S. Shanmuga Priya 1*, Ancy Breen W 1, V.S Rajkumar 1, Latha 2 1 Dept. of computer Science & Engineering, VelTech Hightech Dr. Rangarajan
What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource.
 P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
FORTIFICATION AGAINST PASSWORD GUESSING ATTACKS IN ONLINE SYSTEM
 FORTIFICATION AGAINST PASSWORD GUESSING ATTACKS IN ONLINE SYSTEM V Anusha 1, T Lakshmi Priya 2 1 M.Tech Scholar (CSE), Nalanda Institute of Tech. (NIT), Siddharth Nagar, Guntur, A.P, (India) 2 Assistant
FORTIFICATION AGAINST PASSWORD GUESSING ATTACKS IN ONLINE SYSTEM V Anusha 1, T Lakshmi Priya 2 1 M.Tech Scholar (CSE), Nalanda Institute of Tech. (NIT), Siddharth Nagar, Guntur, A.P, (India) 2 Assistant
Secure PIN Authentication for ATM Transactions using Wireless Devices
 Secure PIN Authentication for ATM Transactions using Wireless Devices V.Varalakshmi 1, Mrs.P.Kanimozhi 2 1 PG Scholar, Department of Computer Science and Engineering, IFET College of Engineering, Villupuram.
Secure PIN Authentication for ATM Transactions using Wireless Devices V.Varalakshmi 1, Mrs.P.Kanimozhi 2 1 PG Scholar, Department of Computer Science and Engineering, IFET College of Engineering, Villupuram.
Summary
 The Imperva Application Defense Center (ADC) ADC White Paper Summary In December 2009, a major password breach occurred that led to the release of 32 million passwords 1. Further, the hacker posted to
The Imperva Application Defense Center (ADC) ADC White Paper Summary In December 2009, a major password breach occurred that led to the release of 32 million passwords 1. Further, the hacker posted to
Implementation of Secure ATM by Wireless Password Transfer and Shuffling Keypad
 Implementation of Secure ATM by Wireless Password Transfer and Shuffling Keypad 1 Kumaresan S, 2 Suresh Kumar K, 3 Dinesh Kumar G 1,2 M.E-VLSI Design, 3 Assistant Professor, Knowledge Institute of Technology,
Implementation of Secure ATM by Wireless Password Transfer and Shuffling Keypad 1 Kumaresan S, 2 Suresh Kumar K, 3 Dinesh Kumar G 1,2 M.E-VLSI Design, 3 Assistant Professor, Knowledge Institute of Technology,
Smart-card-loss-attack and Improvement of Hsiang et al. s Authentication Scheme
 Smart-card-loss-attack and Improvement of Hsiang et al. s Authentication Scheme Y.. Lee Department of Security Technology and Management WuFeng niversity, hiayi, 653, Taiwan yclee@wfu.edu.tw ABSTRAT Due
Smart-card-loss-attack and Improvement of Hsiang et al. s Authentication Scheme Y.. Lee Department of Security Technology and Management WuFeng niversity, hiayi, 653, Taiwan yclee@wfu.edu.tw ABSTRAT Due
Self Destruction Of Data On Cloud Computing
 Volume 118 No. 24 2018 ISSN: 1314-3395 (on-line version) url: http://www.acadpubl.eu/hub/ http://www.acadpubl.eu/hub/ Self Destruction Of Data On Cloud Computing Pradnya Harpale 1,Mohini Korde 2, Pritam
Volume 118 No. 24 2018 ISSN: 1314-3395 (on-line version) url: http://www.acadpubl.eu/hub/ http://www.acadpubl.eu/hub/ Self Destruction Of Data On Cloud Computing Pradnya Harpale 1,Mohini Korde 2, Pritam
Filtering Unwanted Messages from (OSN) User Wall s Using MLT
 Filtering Unwanted Messages from (OSN) User Wall s Using MLT Prof.Sarika.N.Zaware 1, Anjiri Ambadkar 2, Nishigandha Bhor 3, Shiva Mamidi 4, Chetan Patil 5 1 Department of Computer Engineering, AISSMS IOIT,
Filtering Unwanted Messages from (OSN) User Wall s Using MLT Prof.Sarika.N.Zaware 1, Anjiri Ambadkar 2, Nishigandha Bhor 3, Shiva Mamidi 4, Chetan Patil 5 1 Department of Computer Engineering, AISSMS IOIT,
ISSN: (Online) Volume 2, Issue 10, October 2014 International Journal of Advance Research in Computer Science and Management Studies
 ISSN: 2321-7782 (Online) Volume 2, Issue 10, October 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online
ISSN: 2321-7782 (Online) Volume 2, Issue 10, October 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online
A Block Cipher Basing Upon a Revisit to the Feistel Approach and the Modular Arithmetic Inverse of a Key Matrix
 IAENG International Journal of Computer Science, 32:4, IJCS_32_4_ A Block Cipher Basing Upon a Revisit to the Feistel Approach and the Modular Arithmetic Inverse of a Key Matrix S. Udaya Kumar V. U. K.
IAENG International Journal of Computer Science, 32:4, IJCS_32_4_ A Block Cipher Basing Upon a Revisit to the Feistel Approach and the Modular Arithmetic Inverse of a Key Matrix S. Udaya Kumar V. U. K.
A System for Joining and Recognition of Broken Bangla Numerals for Indian Postal Automation
 A System for Joining and Recognition of Broken Bangla Numerals for Indian Postal Automation K. Roy, U. Pal and B. B. Chaudhuri CVPR Unit; Indian Statistical Institute, Kolkata-108; India umapada@isical.ac.in
A System for Joining and Recognition of Broken Bangla Numerals for Indian Postal Automation K. Roy, U. Pal and B. B. Chaudhuri CVPR Unit; Indian Statistical Institute, Kolkata-108; India umapada@isical.ac.in
A SECURE PASSWORD-BASED REMOTE USER AUTHENTICATION SCHEME WITHOUT SMART CARDS
 ISSN 1392 124X INFORMATION TECHNOLOGY AND CONTROL, 2012, Vol.41, No.1 A SECURE PASSWORD-BASED REMOTE USER AUTHENTICATION SCHEME WITHOUT SMART CARDS Bae-Ling Chen 1, Wen-Chung Kuo 2*, Lih-Chyau Wuu 3 1
ISSN 1392 124X INFORMATION TECHNOLOGY AND CONTROL, 2012, Vol.41, No.1 A SECURE PASSWORD-BASED REMOTE USER AUTHENTICATION SCHEME WITHOUT SMART CARDS Bae-Ling Chen 1, Wen-Chung Kuo 2*, Lih-Chyau Wuu 3 1
Undergraduate Software Engineering Experience Developing an Authentication System
 96 Int'l Conf. Security and Management SAM'17 Undergraduate Software Engineering Experience Developing an Authentication System Suhair Amer and Wenxing Qiu Department of Computer Science, Southeast Missouri
96 Int'l Conf. Security and Management SAM'17 Undergraduate Software Engineering Experience Developing an Authentication System Suhair Amer and Wenxing Qiu Department of Computer Science, Southeast Missouri
AN ENHANCED HIGH LEVEL USER AUTHENTICATION AND DATA SECURITY USING BIOMETRIC INPUT
 AN ENHANCED HIGH LEVEL USER AUTHENTICATION AND DATA SECURITY USING BIOMETRIC INPUT P.Kannan*, Karthikeyan.P** School of Information Technology and Engineering, VITUniversity.Vellore pkarthikeyan@vit.ac.in,
AN ENHANCED HIGH LEVEL USER AUTHENTICATION AND DATA SECURITY USING BIOMETRIC INPUT P.Kannan*, Karthikeyan.P** School of Information Technology and Engineering, VITUniversity.Vellore pkarthikeyan@vit.ac.in,
DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS
 DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS Abdul Rasheed. Sk 1 Asst. Professor Narasaraopeta Engineering College, Narasaraopet. rasheed4321@gmail.com
DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS Abdul Rasheed. Sk 1 Asst. Professor Narasaraopeta Engineering College, Narasaraopet. rasheed4321@gmail.com
Multi-hashing for Protecting Web Applications from SQL Injection Attacks
 Multi-hashing for Protecting Web Applications from SQL Injection Attacks Yogesh Bansal, Jin H. Park* Computer Science, California State University, Fresno, CA 93740, U.S.A. * Corresponding author. Email:
Multi-hashing for Protecting Web Applications from SQL Injection Attacks Yogesh Bansal, Jin H. Park* Computer Science, California State University, Fresno, CA 93740, U.S.A. * Corresponding author. Email:
ISSN: (Online) Volume 3, Issue 5, May 2015 International Journal of Advance Research in Computer Science and Management Studies
 ISSN: 2321-7782 (Online) Volume 3, Issue 5, May 2015 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online at:
ISSN: 2321-7782 (Online) Volume 3, Issue 5, May 2015 International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online at:
User Authentication Protocol
 opass: A User Authentication Protocol Sao Vikram B., Gore Vishwanath P., Sankhe Bhakti A., Rananaware Rahul C., ABSTRACT Password security is significant for user authentication on small networking system
opass: A User Authentication Protocol Sao Vikram B., Gore Vishwanath P., Sankhe Bhakti A., Rananaware Rahul C., ABSTRACT Password security is significant for user authentication on small networking system
DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS
 DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS Chippy.T chippyrevathy@gmail.com Dhanalakshmi Srinivasan Engineering College R.Nagendran nanonagendran@gmail.com
DEFENSES AGAINST LARGE SCALE ONLINE PASSWORD GUESSING ATTACKS BY USING PERSUASIVE CLICK POINTS Chippy.T chippyrevathy@gmail.com Dhanalakshmi Srinivasan Engineering College R.Nagendran nanonagendran@gmail.com
Authentication Methods
 CERT-EU Security Whitepaper 16-003 Authentication Methods D.Antoniou, K.Socha ver. 1.0 20/12/2016 TLP: WHITE 1 Authentication Lately, protecting data has become increasingly difficult task. Cyber-attacks
CERT-EU Security Whitepaper 16-003 Authentication Methods D.Antoniou, K.Socha ver. 1.0 20/12/2016 TLP: WHITE 1 Authentication Lately, protecting data has become increasingly difficult task. Cyber-attacks
International Journal of Advance Engineering and Research Development. AN Optimal Matrix Approach for virtual load allocation and data sharing
 Scientific Journal of Impact Factor (SJIF): 5.71 International Journal of Advance Engineering and Research Development Volume 5, Issue 02, February -2018 e-issn (O): 2348-4470 p-issn (P): 2348-6406 AN
Scientific Journal of Impact Factor (SJIF): 5.71 International Journal of Advance Engineering and Research Development Volume 5, Issue 02, February -2018 e-issn (O): 2348-4470 p-issn (P): 2348-6406 AN
ECE596C: Handout #7. Analysis of DES and the AES Standard. Electrical and Computer Engineering, University of Arizona, Loukas Lazos
 ECE596C: Handout #7 Analysis of DES and the AES Standard Electrical and Computer Engineering, University of Arizona, Loukas Lazos Abstract. In this lecture we analyze the security properties of DES and
ECE596C: Handout #7 Analysis of DES and the AES Standard Electrical and Computer Engineering, University of Arizona, Loukas Lazos Abstract. In this lecture we analyze the security properties of DES and
Hosts have the top level of webinar control and can grant and revoke various privileges for participants.
 Introduction ClickMeeting is an easy-to-use SaaS webinar platform used worldwide. It was built using highend technology, with data security as the highest priority. The platform meets stringent security
Introduction ClickMeeting is an easy-to-use SaaS webinar platform used worldwide. It was built using highend technology, with data security as the highest priority. The platform meets stringent security
On Limitations of Designing LRPS: Attacks, Principles and Usability
 CAP6135 Malware & Software Vulnerability On Limitations of Designing LRPS: Attacks, Principles and Usability By Sagar Patel 04/21/2014 EECS Department Agenda Introduction Leakage-Resilient Password System
CAP6135 Malware & Software Vulnerability On Limitations of Designing LRPS: Attacks, Principles and Usability By Sagar Patel 04/21/2014 EECS Department Agenda Introduction Leakage-Resilient Password System
MODULE NO.28: Password Cracking
 SUBJECT Paper No. and Title Module No. and Title Module Tag PAPER No. 16: Digital Forensics MODULE No. 28: Password Cracking FSC_P16_M28 TABLE OF CONTENTS 1. Learning Outcomes 2. Introduction 3. Nature
SUBJECT Paper No. and Title Module No. and Title Module Tag PAPER No. 16: Digital Forensics MODULE No. 28: Password Cracking FSC_P16_M28 TABLE OF CONTENTS 1. Learning Outcomes 2. Introduction 3. Nature
Exercises with solutions, Set 3
 Exercises with solutions, Set 3 EDA625 Security, 2017 Dept. of Electrical and Information Technology, Lund University, Sweden Instructions These exercises are for self-assessment so you can check your
Exercises with solutions, Set 3 EDA625 Security, 2017 Dept. of Electrical and Information Technology, Lund University, Sweden Instructions These exercises are for self-assessment so you can check your
Client Scoring Application
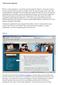 Client Scoring Application The new scoring application is a web-based system developed by Triple P to assist in the scoring of the many measures used in the delivery of Triple P. There are many advantages
Client Scoring Application The new scoring application is a web-based system developed by Triple P to assist in the scoring of the many measures used in the delivery of Triple P. There are many advantages
Towards Identifying Usability and Security Features of Graphical Password in Knowledge Based Authentication Technique
 Second Asia International Conference on Modelling & Simulation Towards Identifying Usability and Security Features of Graphical Password in Knowledge Based Authentication Technique Muhammad Daniel Hafiz
Second Asia International Conference on Modelling & Simulation Towards Identifying Usability and Security Features of Graphical Password in Knowledge Based Authentication Technique Muhammad Daniel Hafiz
MOBILE DEFEND. Powering Robust Mobile Security Solutions
 MOBILE DEFEND Powering Robust Mobile Security Solutions Table of Contents Introduction Trustlook SECURE ai Mobile Defend Who Uses SECURE ai Mobile Defend? How it Works o Mobile Device Risk Score o Mobile
MOBILE DEFEND Powering Robust Mobile Security Solutions Table of Contents Introduction Trustlook SECURE ai Mobile Defend Who Uses SECURE ai Mobile Defend? How it Works o Mobile Device Risk Score o Mobile
Options Sending to Printers Option 1: Campus Computers Option 2: BYO Devices (Web Print) Option 3: App... 22
 Printing Contents Enabling OneDrive Access (Once off Process)... 2 How to access the printers... 5 Option 1: User ID... 5 Option 2: Card ID (PAN)... 6 Option 3: App on your mobile... 7 Printer Functions
Printing Contents Enabling OneDrive Access (Once off Process)... 2 How to access the printers... 5 Option 1: User ID... 5 Option 2: Card ID (PAN)... 6 Option 3: App on your mobile... 7 Printer Functions
A Survey on Secure Sharing In Cloud Computing
 A Survey on Secure Sharing In Cloud Computing Aakanksha maliye, Sarita Patil Department of Computer Engineering, G.H.Raisoni College of Engineering & Management, Wagholi, India ABSTRACT: Cloud computing
A Survey on Secure Sharing In Cloud Computing Aakanksha maliye, Sarita Patil Department of Computer Engineering, G.H.Raisoni College of Engineering & Management, Wagholi, India ABSTRACT: Cloud computing
Highly Secure Authentication Scheme: A Review
 e-issn: 2349-9745 p-issn: 2393-8161 Scientific Journal Impact Factor (SJIF): 1.711 International Journal of Modern Trends in Engineering and Research www.ijmter.com Highly Secure Authentication Scheme:
e-issn: 2349-9745 p-issn: 2393-8161 Scientific Journal Impact Factor (SJIF): 1.711 International Journal of Modern Trends in Engineering and Research www.ijmter.com Highly Secure Authentication Scheme:
