Your Reputa+on Precedes You Friday, 7 th October 9:30-10:00am. 10/13/11 Copyright 2010 Damballa, Inc. All Rights Reserved Worldwide.
|
|
|
- Primrose Farmer
- 6 years ago
- Views:
Transcription
1 Your Reputa+on Precedes You Friday, 7 th October 9:30-10:00am 10/13/11 Copyright 2010 Damballa, Inc. All Rights Reserved Worldwide. 1
2 About Gunter Ollmann VP of Research, Damballa Inc. Board of Advisors, IOAc;ve Inc. Brief Bio: Been in IT industry for 2+ decades Built and run interna;onal pentest teams, R&D groups and consul;ng prac;ces around the world. Formerly Chief Security Strategist for IBM, Director of X- Force for ISS, Professional Services Director for NGS SoOware, Head of AQack Services EMEA, etc. Frequent writer, columnist and blogger with lots of whitepapers hqp://blog.damballa.com & hqp://technicalinfodotnet.blogspot.com/
3 (Brief) Background to Reputa+on The minimum stuff you need to know to understand the rest of the material 10/13/11 3
4 Reputation? Reputa+on systems: Basically a summary of past ac;ons Past context to make decisions today Sta+c reputa+on Tradi;onal list of known good/bad Binary view (listed or not) Dynamic reputa+on Sliding windows and aggregate scoring live reputa;on scores 10/13/11 4
5 Blacklists (& Whitelists) Most common form of reputa+on system Blacklists = stuff you don t want Whitelists = stuff you don t want to interrupt Sta;c reputa;on Used in all sorts of places: Firewall filtering File inspec;on Web filtering Training sets for dynamic reputa;on systems 10/13/11 5
6 Obvious Limitations Frequency of monitoring Frequency of updates Passive or ac+ve monitoring Visibility and coverage Local spam in China? IP assignment NAT & DHCP 10/13/11 6
7 Static vs. Dynamic Reputation Accuracy Dynamic Reputa;on API- driven & live window Sta;c Reputa;on List of malicious domains Time 10/13/11 7
8 Static vs. Dynamic Reputation Δt Accuracy Updated List New blacklist gets applied Time 10/13/11 8
9 Static vs. Dynamic Reputation Known Sta;c Reputa;on List of malicious domains FP TP Dynamic Reputa;on API- driven & live window Unknown 10/13/11 9
10 Static vs. Dynamic Reputation Known FP Aging Effects List of malicious domains TP Unknown 10/13/11 10
11 Gunter Ollmann The Agile Threat What the badguys do to make things hard for reputa+on systems 10/13/11 11
12 Where s the CnC Where is evil.blah.com? A TTL: 3600 Authorita;ve Name Server Alterna;ve address. Assigned round- robin. CnC Server CnC Server 10/13/11 12
13 Fast Flux Where is evil.blah.com? TTL: 5 Authorita;ve Name Server Very short TTL Bot infected computer serves as a proxy CnC Server CnC Server 10/13/11 13
14 Fast Flux Where is evil.blah.com? TTL: 5 Authorita;ve Name Server CnC Server Hopping between mul;ple proxy- bots CnC Server 10/13/11 14
15 Double Flux Authorita;ve Name Server Bots proxy NS lookups too CnC Server CnC Server 10/13/11 15
16 Domain Wildcarding Mass registra+ons PaQern to domains Mix of characters/numbers Some;mes dic;onary words May be free DDNS too freakyfriday23a.3322.cn freakyfriday24d.3322.cn freakyfriday23a.ddns.com freakyfriday24d.ddns.com freakyfriday23a.dyn- dns.com command.blah a.com command.blah b.com command.blah a.com command.blah b.com command.blah e.com cnc.a0a01603e2ff.blah.com cnc.a0a01603e3ff.blah.com cnc.a0a01603e4ff.blah.com cnc.a0b21603e2ff.blah.com cnc.a0b ff.blah.com freakyfriday23a.blah.com freakyfriday24d.blah.com freakyfriday33t.blah.com freakyfriday25m.blah.com freakyfriday28k.blah.com 10/13/11 16
17 DGA s Domain Genera+on Algorithm (DGA) Mathema;cal algorithm date/;me based Generate 10 s thousands, try a few hundred Customize seeds in some malware DIY kits May use DDNS or personalized 3LD services 10/13/11 17
18 DGA examples 10/13/11 18 q6obbbx.r00t.la 5w61675.themafia.info qr1agp1.servepics.com 081a4jh.serveOp.com eet88nd.shell.la cwlhuwl.sexypenguins.com 9t9iw4u.serveblog.net cz46ht0.lamer.la 41stwa1.sexypenguins.com tsz1twx.sytes.net Bobax Variant osudhnmqjsrsip.info osudhnmqjsrsip.com wumlmmrsywkempx.net wumlmmrsywkempx.biz wnxfsorevnomago.info wnxfsorevnomago.com kmssxphuszhnhrb.org kmssxphuszhnhrb.com diuuvkgvszqproh.biz diuuvkgvszqproh.org Murofet rdixtxezwt.com vmithskvme.com ocefytqmf.com vifqgbccxg.com slwamznmcq.com knbriyfnsq.com oqabpwrxxa.com wwtnekmjij.com sztxlixtnt.com lbqghhpudt.com Sinowal mdecub- ydyg.ru mgefa- bugin.com mkoza- diqyk.com mmoby- do;r.com mpodod- axoz.ru msofy- debef.com mvahif- ufum.ru mzakef- ihos.ru mfenaf- anyg.ru mjepuf- erin.ru mleraf- yvot.ru mpetyf- uxeb.ru mryvof- ibuh.ru mvyzyf- ofop.ru Unknown
19 Snow-shoe Technique to spread traffic over array of IP s OOen associated with spam delivery Mul;ple blocks of IP s used Mul+ple domains related to IP s Further obfusca;on of aqack traffic Fake domain whois data 10/13/11 19
20 Hacked Servers Mass hacks of popular/legit servers Web servers are most common Target servers that have been around for a while Mass hacks of virtual host servers 10/13/11 20
21 Rapid Registration It takes +me to build/distribute blacklists Badguys just have to be faster than the list Registering faster Automated domain registra;on Free dynamic DNS DNS wildcarding 10/13/11 21
22 Blacklisting Badguys maintain their own blacklists Firewall drop- list scripts (pastebin) X- morphic delivery engine updates 10/13/11 22
23 The Dynamic Network Gunter Ollmann Dynamic network The Dynamic Network Even without the badguys, network dynamics are a problem 10/13/11 23
24 The Dynamic Network It s tough enough without the bad guys! Internet is dynamic Changes to the core Transi;on from IPv4 to IPv6 Cloud compu;ng Anycast rou;ng 10/13/11 24
25 IPv6 IPv6 address space is HUGE! = 340,282,366,920,938,463,463,374,607,431,768,211,456 Plenty of places to run & hide Subnets allocated to residen;al larger than IPv4 Scanning & probing empty space infeasible No marked history No basis for blacklists Too small for many dynamic reputa;on approaches 10/13/11 25
26 IPv4 Available IPv4 Space in /8s The IANA pool of IPv4 address space depleted on February 3, This slide shows the steady deple;on of that pool over ;me. 10/13/11 26
27 Trading IPv4 Ranges 10/13/11 27
28 Trading Forums Matching buyers & sellers 10/13/11 28
29 In to the cloud Commercial cloud providers being abused Convenient hos;ng for criminals Easy to tear- down and restart elsewhere in cloud Mul;ple (dynamic) egress IP s Co- located with legi;mate businesses Reputa+on systems stalled Dynamic IP s = can t blacklist (all or nothing) history element hard to nail down 10/13/11 29
30 Dynamic Reputation Gunter Ollmann Dynamic Reputa+on Applying reputa+on to dynamic networks and threats 10/13/11 30
31 Dynamic Reputation Dynamic reputa+on for dynamic threats live reputa;on scoring Dynamic window of threat observa;ons Transi+on from have to have seen it before Predic've scoring based upon history, context, and known Internet structure (good/bad/gray) Dynamic reputa+ons: For IP For Domains For DNS IP or Domain, by themselves, is of limited value in a threat context 10/13/11 31
32 Dynamic reputation Newest approaches: comprehensive reputa+on for DNS Notos Exposure Notos Outputs reputa;on scores for domains. Use network and zone based features Threat- oriented learning system High fidelity classifica+on and scoring very low FP% (0.3846%) and high TP% (96.8%). Spot fraudulent domain names weeks before appearance on blacklists
33 Notos Features Overview Reputa;on score between 0 & 1 These 3 vectors are: Network Based Feature Vector [18], Zone Based Feature Vector [17] and the Evidence Based Feature Vector [6]
34 Clustering for reputation Labeled and unlabeled RRs clustering results from Zeus related domain names 200 Clustering The Zeus Botnet 0 CMD 2D Scale (1) CMD 2D Scale (2) Labeled Zeus Unlabeled Zeus 10/13/11 34
35 Scoring accuracy 1 False Positive Rate vs True Positive Rate True Positive Rate Precision TP over All Pos. vs Threshold ROC Threshold False Positive Rate ROC FP%=0.3849% and TP%=96.8%. 10/13/11 35
36 Conclusions Gunter Ollmann Conclusions Light at the end of the tunnel 10/13/11 36
37 Changing times Adrenaline injec+on for blacklists Adding ;me element depreciate dated views Reduces false posi;ves Transi+on from sta+c to dynamic reputa+on Requires real- ;me feeds and updates API vs list approach Movement away from domain/ip holis;c maps of the Internet & threats Dynamic reputa;on for DNS 10/13/11 37
38 Death of binary decisions Past reputa+on approaches have been binary On the list = bad Not on the list = Ok/unknown/don t care Reputa+on scores Scoring of malicious intent Forecas;ng criminal usage Threat category determina;on 10/13/11 38
39 Thank You! Any ques+ons? Gunter Ollmann VP Research, Damballa 10/13/11 39
Size Matters Measuring a Botnet Operator s Pinkie
 VB2010, Vancouver Size Matters Measuring a Botnet Operator s Pinkie Gunter Ollmann, VP Research gollmann@damballa.com About Gunter Ollmann VP of Research, Damballa Inc. Board of Advisors, IOActive Inc.
VB2010, Vancouver Size Matters Measuring a Botnet Operator s Pinkie Gunter Ollmann, VP Research gollmann@damballa.com About Gunter Ollmann VP of Research, Damballa Inc. Board of Advisors, IOActive Inc.
Botnet Communication Topologies
 Understanding the intricacies of botnet Command-and-Control By Gunter Ollmann, VP of Research, Damballa, Inc. Introduction A clear distinction between a bot agent and a common piece of malware lies within
Understanding the intricacies of botnet Command-and-Control By Gunter Ollmann, VP of Research, Damballa, Inc. Introduction A clear distinction between a bot agent and a common piece of malware lies within
Automating Security Response based on Internet Reputation
 Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
Discovering new malicious domains using DNS and big data Case study: Fast Flux domains. Dhia Mahjoub OpenDNS May 25 th, 2013
 Discovering new malicious domains using DNS and big data Case study: Fast Flux domains Dhia Mahjoub OpenDNS May 25 th, 2013 Background A@ackers seek to keep their operabons online at all Bmes The Network
Discovering new malicious domains using DNS and big data Case study: Fast Flux domains Dhia Mahjoub OpenDNS May 25 th, 2013 Background A@ackers seek to keep their operabons online at all Bmes The Network
DNS Firewall with Response Policy Zone. Suman Kumar Saha bdcert Amber IT Limited
 DNS Firewall with Response Policy Zone Suman Kumar Saha bdcert suman@bdcert.org Amber IT Limited suman@amberit.com.bd DNS Response Policy Zone(RPZ) as Firewall RPZ allows a recursive server to control
DNS Firewall with Response Policy Zone Suman Kumar Saha bdcert suman@bdcert.org Amber IT Limited suman@amberit.com.bd DNS Response Policy Zone(RPZ) as Firewall RPZ allows a recursive server to control
Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science
 Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science 310 Million + Current Domain Names 11 Billion+ Historical Domain Profiles 5 Million+ New Domain Profiles Daily
Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science 310 Million + Current Domain Names 11 Billion+ Historical Domain Profiles 5 Million+ New Domain Profiles Daily
Imperva Incapsula Website Security
 Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
How to Configure DNS Sinkholing in the Firewall
 UDP DNS traffic handled by the Firewall service is monitored and, if a domain is found that is considered to be malicious, the A and AAAA DNS response is replaced by fake IP addresses. An access rule blocks
UDP DNS traffic handled by the Firewall service is monitored and, if a domain is found that is considered to be malicious, the A and AAAA DNS response is replaced by fake IP addresses. An access rule blocks
Improved C&C Traffic Detection Using Multidimensional Model and Network Timeline Analysis
 Improved C&C Traffic Detection Using Multidimensional Model and Elad Menahem Avidan Avraham Modern Threats Are More Sophisticated & Evasive CYBER KILL CHAIN: Infection Phase Post-Infection Recon Weaponization
Improved C&C Traffic Detection Using Multidimensional Model and Elad Menahem Avidan Avraham Modern Threats Are More Sophisticated & Evasive CYBER KILL CHAIN: Infection Phase Post-Infection Recon Weaponization
RSA Web Threat Detection
 RSA Web Threat Detection Online Threat Detection in Real Time Alaa Abdulnabi. CISSP, CIRM RSA Pre-Sales Manager, TEAM Region 1 Web Threat Landscape In the Wild Begin Session Login Transaction Logout Web
RSA Web Threat Detection Online Threat Detection in Real Time Alaa Abdulnabi. CISSP, CIRM RSA Pre-Sales Manager, TEAM Region 1 Web Threat Landscape In the Wild Begin Session Login Transaction Logout Web
Reduce Your Network's Attack Surface
 WHITE PAPER Reduce Your Network's Attack Surface Ixia's ThreatARMOR Frees Up Security Resources and Personnel The Threat Landscape When you re dealing with network security, one of the primary measurements
WHITE PAPER Reduce Your Network's Attack Surface Ixia's ThreatARMOR Frees Up Security Resources and Personnel The Threat Landscape When you re dealing with network security, one of the primary measurements
HOW TO CHOOSE A NEXT-GENERATION WEB APPLICATION FIREWALL
 HOW TO CHOOSE A NEXT-GENERATION WEB APPLICATION FIREWALL CONTENTS EXECUTIVE SUMMARY 1 WEB APPLICATION SECURITY CHALLENGES 2 INSIST ON BEST-IN-CLASS CORE CAPABILITIES 3 HARNESSING ARTIFICIAL INTELLIGENCE
HOW TO CHOOSE A NEXT-GENERATION WEB APPLICATION FIREWALL CONTENTS EXECUTIVE SUMMARY 1 WEB APPLICATION SECURITY CHALLENGES 2 INSIST ON BEST-IN-CLASS CORE CAPABILITIES 3 HARNESSING ARTIFICIAL INTELLIGENCE
Maximum Security with Minimum Impact : Going Beyond Next Gen
 SESSION ID: SP03-W10 Maximum Security with Minimum Impact : Going Beyond Next Gen Wendy Moore Director, User Protection Trend Micro @WMBOTT Hyper-competitive Cloud Rapid adoption Social Global Mobile IoT
SESSION ID: SP03-W10 Maximum Security with Minimum Impact : Going Beyond Next Gen Wendy Moore Director, User Protection Trend Micro @WMBOTT Hyper-competitive Cloud Rapid adoption Social Global Mobile IoT
Intelligent and Secure Network
 Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Botnet Detection. Botnet Detection for Communications Service Providers
 Botnet Detection Botnet Detection for Communications Service Providers Table of Contents Introduction:... 3 Beyond the Enterprise Network... 4 Network-based Botnet Detection... 5 CnC Communication Identification...
Botnet Detection Botnet Detection for Communications Service Providers Table of Contents Introduction:... 3 Beyond the Enterprise Network... 4 Network-based Botnet Detection... 5 CnC Communication Identification...
Detecting and Quantifying Abusive IPv6 SMTP!
 Detecting and Quantifying Abusive IPv6 SMTP Casey Deccio Verisign Labs Internet2 2014 Technical Exchange October 30, 2014 Spam, IPv4 Reputation and DNSBL Spam is pervasive Annoying (pharmaceuticals) Dangerous
Detecting and Quantifying Abusive IPv6 SMTP Casey Deccio Verisign Labs Internet2 2014 Technical Exchange October 30, 2014 Spam, IPv4 Reputation and DNSBL Spam is pervasive Annoying (pharmaceuticals) Dangerous
Vincent van Kooten, EMEA North Fraud & Risk Intelligence Specialist RSA, The Security Division of EMC
 Vincent van Kooten, EMEA North Fraud & Risk Intelligence Specialist RSA, The Security Division of EMC 1 2013 2 3 in 4 3 5.900.000.000 $ 4 RSA s Top 10 List 5 RSA s top 10 phishing list Copyright 2014 EMC
Vincent van Kooten, EMEA North Fraud & Risk Intelligence Specialist RSA, The Security Division of EMC 1 2013 2 3 in 4 3 5.900.000.000 $ 4 RSA s Top 10 List 5 RSA s top 10 phishing list Copyright 2014 EMC
PineApp Mail Secure SOLUTION OVERVIEW. David Feldman, CEO
 PineApp Mail Secure SOLUTION OVERVIEW David Feldman, CEO PineApp Mail Secure INTRODUCTION ABOUT CYBONET CORE EXPERIENCE PRODUCT LINES FACTS & FIGURES Leader Product Company Servicing Multiple Vertical
PineApp Mail Secure SOLUTION OVERVIEW David Feldman, CEO PineApp Mail Secure INTRODUCTION ABOUT CYBONET CORE EXPERIENCE PRODUCT LINES FACTS & FIGURES Leader Product Company Servicing Multiple Vertical
Insight Frequently Asked Questions version 2.0 (8/24/2011)
 Insight Frequently Asked Questions version 2.0 (8/24/2011) Insight Overview 1. What is a reputation system and how does it work? Insight, our reputation system, leverages anonymous telemetry data from
Insight Frequently Asked Questions version 2.0 (8/24/2011) Insight Overview 1. What is a reputation system and how does it work? Insight, our reputation system, leverages anonymous telemetry data from
Cisco Cloud Security. How to Protect Business to Support Digital Transformation
 Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Behavior Based Malware Analysis: A Perspective From Network Traces and Program Run-Time Structure
 Behavior Based Malware Analysis: A Perspective From Network Traces and Program Run-Time Structure Chun-Ying Huang chuang@ntou.edu.tw Assistant Professor Department of Computer Science and Engineering National
Behavior Based Malware Analysis: A Perspective From Network Traces and Program Run-Time Structure Chun-Ying Huang chuang@ntou.edu.tw Assistant Professor Department of Computer Science and Engineering National
August 14th, 2018 PRESENTED BY:
 August 14th, 2018 PRESENTED BY: APPLICATION LAYER ATTACKS 100% 80% 60% 40% 20% 0% DNS is the second most targeted protocol after HTTP. DNS DoS techniques range from: Flooding requests to a given host.
August 14th, 2018 PRESENTED BY: APPLICATION LAYER ATTACKS 100% 80% 60% 40% 20% 0% DNS is the second most targeted protocol after HTTP. DNS DoS techniques range from: Flooding requests to a given host.
How to Configure ATP in the HTTP Proxy
 Configure when and which types of files are uploaded to the Barracuda ATP Cloud for traffic passing through the HTTP proxy service. Users will receive downloaded files immediately. When files with a risk
Configure when and which types of files are uploaded to the Barracuda ATP Cloud for traffic passing through the HTTP proxy service. Users will receive downloaded files immediately. When files with a risk
State of the Internet Security Q Mihnea-Costin Grigore Security Technical Project Manager
 State of the Internet Security Q2 2017 Mihnea-Costin Grigore Security Technical Project Manager Topics 1. Introduction 2. DDoS Attack Trends 3. Web Application Attack Trends 4. Spotlights 5. Resources
State of the Internet Security Q2 2017 Mihnea-Costin Grigore Security Technical Project Manager Topics 1. Introduction 2. DDoS Attack Trends 3. Web Application Attack Trends 4. Spotlights 5. Resources
A SUBSYSTEM FOR FAST (IP) FLUX BOTNET DETECTION
 Chapter 6 A SUBSYSTEM FOR FAST (IP) FLUX BOTNET DETECTION 6.1 Introduction 6.1.1 Motivation Content Distribution Networks (CDNs) and Round-Robin DNS (RRDNS) are the two standard methods used for resource
Chapter 6 A SUBSYSTEM FOR FAST (IP) FLUX BOTNET DETECTION 6.1 Introduction 6.1.1 Motivation Content Distribution Networks (CDNs) and Round-Robin DNS (RRDNS) are the two standard methods used for resource
Tracking Evil with Passive DNS
 Tracking Evil with Passive DNS Bojan Ždrnja, CISSP, GCIA, GCIH Bojan.Zdrnja@infigo.hr INFIGO IS http://www.infigo.hr Who am I? Senior information security consultant with INFIGO IS (Croatia) Mainly doing
Tracking Evil with Passive DNS Bojan Ždrnja, CISSP, GCIA, GCIH Bojan.Zdrnja@infigo.hr INFIGO IS http://www.infigo.hr Who am I? Senior information security consultant with INFIGO IS (Croatia) Mainly doing
Behavioral Analytics A Closer Look
 SESSION ID: GPS2-F03 Behavioral Analytics A Closer Look Mike Huckaby VP, Global Systems Engineering RSA The world is full of obvious things which nobody by any chance ever observes. Sherlock Holmes 2 Patterns
SESSION ID: GPS2-F03 Behavioral Analytics A Closer Look Mike Huckaby VP, Global Systems Engineering RSA The world is full of obvious things which nobody by any chance ever observes. Sherlock Holmes 2 Patterns
Seceon s Open Threat Management software
 Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
(Botnets and Malware) The Zbot attack. Group 7: Andrew Mishoe David Colvin Hubert Liu George Chen John Marshall Buck Scharfnorth
 (Botnets and Malware) The Zbot attack Group 7: Andrew Mishoe David Colvin Hubert Liu George Chen John Marshall Buck Scharfnorth What Happened? Type of Attack Botnet - refers to group of compromised computers
(Botnets and Malware) The Zbot attack Group 7: Andrew Mishoe David Colvin Hubert Liu George Chen John Marshall Buck Scharfnorth What Happened? Type of Attack Botnet - refers to group of compromised computers
Security Architect Northeast US Enterprise CISSP, GCIA, GCFA Cisco Systems. BRKSEC-2052_c Cisco Systems, Inc. All rights reserved.
 Web 2.0 Security Recommendations Ken Kaminski Security Architect Northeast US Enterprise CISSP, GCIA, GCFA Cisco Systems 1 Agenda Reputation Services Web application security Secure Coding and Web Application
Web 2.0 Security Recommendations Ken Kaminski Security Architect Northeast US Enterprise CISSP, GCIA, GCFA Cisco Systems 1 Agenda Reputation Services Web application security Secure Coding and Web Application
The Internet Evolution and Opportunity
 The Internet Evolution and Opportunity Leslie Daigle, Chief Internet Technology Officer, ISOC W3C Technical Plenary week, Developers Meeting November 5, 2009. The Internet Society Founded in 1992 A global
The Internet Evolution and Opportunity Leslie Daigle, Chief Internet Technology Officer, ISOC W3C Technical Plenary week, Developers Meeting November 5, 2009. The Internet Society Founded in 1992 A global
CYBER ANALYTICS. Architecture Overview. Technical Brief. May 2016 novetta.com 2016, Novetta
 CYBER ANALYTICS Architecture Overview Technical Brief May 2016 novetta.com 2016, Novetta Novetta Cyber Analytics: Technical Architecture Overview 1 INTRODUCTION 2 CAPTURE AND PROCESS ALL NETWORK TRAFFIC
CYBER ANALYTICS Architecture Overview Technical Brief May 2016 novetta.com 2016, Novetta Novetta Cyber Analytics: Technical Architecture Overview 1 INTRODUCTION 2 CAPTURE AND PROCESS ALL NETWORK TRAFFIC
Cyber Vigilantes. Rob Rachwald Director of Security Strategy. Porto Alegre, October 5, 2011
 Cyber Vigilantes Rob Rachwald Director of Security Strategy Porto Alegre, October 5, 2011 Hacking: Industry Analysis Hacking has become industrialized. Attack techniques and vectors keep changing with
Cyber Vigilantes Rob Rachwald Director of Security Strategy Porto Alegre, October 5, 2011 Hacking: Industry Analysis Hacking has become industrialized. Attack techniques and vectors keep changing with
Configuring the Botnet Traffic Filter
 CHAPTER 46 Malware is malicious software that is installed on an unknowing host. Malware that attempts network activity such as sending private data (passwords, credit card numbers, key strokes, or proprietary
CHAPTER 46 Malware is malicious software that is installed on an unknowing host. Malware that attempts network activity such as sending private data (passwords, credit card numbers, key strokes, or proprietary
MEASURING AND FINGERPRINTING CLICK-SPAM IN AD NETWORKS
 MEASURING AND FINGERPRINTING CLICK-SPAM IN AD NETWORKS Vacha Dave *, Saikat Guha and Yin Zhang * * The University of Texas at Austin Microsoft Research India Internet Advertising Today 2 Online advertising
MEASURING AND FINGERPRINTING CLICK-SPAM IN AD NETWORKS Vacha Dave *, Saikat Guha and Yin Zhang * * The University of Texas at Austin Microsoft Research India Internet Advertising Today 2 Online advertising
Botnets Behavioral Patterns in the Network
 Botnets Behavioral Patterns in the Network Garcia Sebastian @eldracote Hack.Lu 2014 CTU University, Czech Republic. UNICEN University, Argentina. October 23, 2014 How are we detecting malware and botnets?
Botnets Behavioral Patterns in the Network Garcia Sebastian @eldracote Hack.Lu 2014 CTU University, Czech Republic. UNICEN University, Argentina. October 23, 2014 How are we detecting malware and botnets?
Quick Lockdown Guide. Firmware 6.4
 Bosch Security Bosch Security Systems System Video Systems Video Systems Bosch Security Systems Video Systems Quick Lockdown Guide Firmware 6.4 Overview The purpose of this technical brief is to provide
Bosch Security Bosch Security Systems System Video Systems Video Systems Bosch Security Systems Video Systems Quick Lockdown Guide Firmware 6.4 Overview The purpose of this technical brief is to provide
Automated Threat Management - in Real Time. Vectra Networks
 Automated Threat Management - in Real Time Security investment has traditionally been in two areas Prevention Phase Active Phase Clean-up Phase Initial Infection Key assets found in the wild $$$$ $$$ $$
Automated Threat Management - in Real Time Security investment has traditionally been in two areas Prevention Phase Active Phase Clean-up Phase Initial Infection Key assets found in the wild $$$$ $$$ $$
Stop Ransomware In Its Tracks. Chris Chaves Channel Sales Engineer
 Stop Ransomware In Its Tracks Chris Chaves Channel Sales Engineer Agenda Ransomware A Brief Introduction Why Are Ransomware Attacks so Successful? How Does a Ransomware Attack Happen? How to Stop Ransomware
Stop Ransomware In Its Tracks Chris Chaves Channel Sales Engineer Agenda Ransomware A Brief Introduction Why Are Ransomware Attacks so Successful? How Does a Ransomware Attack Happen? How to Stop Ransomware
A brief Incursion into Botnet Detection
 A brief Incursion into Anant Narayanan Advanced Topics in Computer and Network Security October 5, 2009 What We re Going To Cover 1 2 3 Counter-intelligence 4 What Are s? Networks of zombie computers The
A brief Incursion into Anant Narayanan Advanced Topics in Computer and Network Security October 5, 2009 What We re Going To Cover 1 2 3 Counter-intelligence 4 What Are s? Networks of zombie computers The
Analytics Driven, Simple, Accurate and Actionable Cyber Security Solution CYBER ANALYTICS
 Analytics Driven, Simple, Accurate and Actionable Cyber Security Solution CYBER ANALYTICS Overview Cyberattacks are increasingly getting more frequent, more sophisticated and more widespread than ever
Analytics Driven, Simple, Accurate and Actionable Cyber Security Solution CYBER ANALYTICS Overview Cyberattacks are increasingly getting more frequent, more sophisticated and more widespread than ever
John Munro / Jason Trost / FlonCon 2013 January 7 10 Albuquerque, New Mexico
 John Munro / jmunro@endgame.com Jason Trost / jtrost@endgame.com FlonCon 2013 January 7 10 Albuquerque, New Mexico Introductions John Munro (jmunro@endgame.com) Network Security Researcher and Data Scientist
John Munro / jmunro@endgame.com Jason Trost / jtrost@endgame.com FlonCon 2013 January 7 10 Albuquerque, New Mexico Introductions John Munro (jmunro@endgame.com) Network Security Researcher and Data Scientist
IBM Security Network Protection Open Mic - Thursday, 31 March 2016
 IBM Security Network Protection Open Mic - Thursday, 31 March 2016 Application Control and IP Reputation on the XGS Demystified Panelists Tanmay Shah, Presenter IPS/Network Protection Product Lead Bill
IBM Security Network Protection Open Mic - Thursday, 31 March 2016 Application Control and IP Reputation on the XGS Demystified Panelists Tanmay Shah, Presenter IPS/Network Protection Product Lead Bill
Configuring NAT for IP Address Conservation
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
Finding Feature Information
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
Mul$media Networking. #9 CDN Solu$ons Semester Ganjil 2012 PTIIK Universitas Brawijaya
 Mul$media Networking #9 CDN Solu$ons Semester Ganjil 2012 PTIIK Universitas Brawijaya Schedule of Class Mee$ng 1. Introduc$on 2. Applica$ons of MN 3. Requirements of MN 4. Coding and Compression 5. RTP
Mul$media Networking #9 CDN Solu$ons Semester Ganjil 2012 PTIIK Universitas Brawijaya Schedule of Class Mee$ng 1. Introduc$on 2. Applica$ons of MN 3. Requirements of MN 4. Coding and Compression 5. RTP
McAfee Endpoint Security
 McAfee Endpoint Security Frequently Asked Questions Overview You re facing new challenges in light of the increase of advanced malware. Limited integration between threat detection, network, and endpoint
McAfee Endpoint Security Frequently Asked Questions Overview You re facing new challenges in light of the increase of advanced malware. Limited integration between threat detection, network, and endpoint
Cisco Threat Intelligence Director (TID)
 The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Requirements for Threat Intelligence Director, page 4 How To Set Up, page 6 Analyze TID Incident
The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Requirements for Threat Intelligence Director, page 4 How To Set Up, page 6 Analyze TID Incident
TempR: Application of Stricture Dependent Intelligent Classifier for Fast Flux Domain Detection
 I. J. Computer Network and Information Security, 2016, 10, 37-44 Published Online October 2016 in MECS (http://www.mecs-press.org/) DOI: 10.5815/ijcnis.2016.10.05 TempR: Application of Stricture Dependent
I. J. Computer Network and Information Security, 2016, 10, 37-44 Published Online October 2016 in MECS (http://www.mecs-press.org/) DOI: 10.5815/ijcnis.2016.10.05 TempR: Application of Stricture Dependent
Large-Scale Internet Crimes Global Reach, Vast Numbers, and Anonymity
 Computer Crime and Intellectual Property Section Large-Scale Internet Crimes Global Reach, Vast Numbers, and Anonymity Anthony V. Teelucksingh Computer Crime and Intellectual Property Section (CCIPS) Criminal
Computer Crime and Intellectual Property Section Large-Scale Internet Crimes Global Reach, Vast Numbers, and Anonymity Anthony V. Teelucksingh Computer Crime and Intellectual Property Section (CCIPS) Criminal
On Measuring the Client- Side DNS Infrastructure Kyle Schomp, Tom Callahan, Michael Rabinovich, Mark Allman
 On Measuring the Client- Side DNS Infrastructure Kyle Schomp, Tom Callahan, Michael Rabinovich, Mark Allman Case Western Reserve University Interna@onal Computer Science Ins@tute 10/23/2013 ACM IMC 2013
On Measuring the Client- Side DNS Infrastructure Kyle Schomp, Tom Callahan, Michael Rabinovich, Mark Allman Case Western Reserve University Interna@onal Computer Science Ins@tute 10/23/2013 ACM IMC 2013
The SANS Institute Top 20 Critical Security Controls. Compliance Guide
 The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
Next Generation Endpoint Security Confused?
 SESSION ID: CEM-W06 Next Generation Endpoint Security Confused? Greg Day VP & Chief Security Officer, EMEA Palo Alto Networks @GreDaySecurity Brief Intro Questions we will answer Do I need a new (NG) endpoint
SESSION ID: CEM-W06 Next Generation Endpoint Security Confused? Greg Day VP & Chief Security Officer, EMEA Palo Alto Networks @GreDaySecurity Brief Intro Questions we will answer Do I need a new (NG) endpoint
Protect vital DNS assets and identify malware
 N2 THREATAVERT Protect vital DNS assets and identify malware Service Providers recognize network security drives brand equity because it directly impacts subscriber satisfaction. Secure networks are also
N2 THREATAVERT Protect vital DNS assets and identify malware Service Providers recognize network security drives brand equity because it directly impacts subscriber satisfaction. Secure networks are also
Reducing the Cost of Incident Response
 Reducing the Cost of Incident Response Introduction Cb Response is the most complete endpoint detection and response solution available to security teams who want a single platform for hunting threats,
Reducing the Cost of Incident Response Introduction Cb Response is the most complete endpoint detection and response solution available to security teams who want a single platform for hunting threats,
Detecting DGA Malware Traffic Through Behavioral Models. Erquiaga, María José Catania, Carlos García, Sebastían
 Detecting DGA Malware Traffic Through Behavioral Models Erquiaga, María José Catania, Carlos García, Sebastían Outline Introduction Detection Method Training the threshold Dataset description Experiment
Detecting DGA Malware Traffic Through Behavioral Models Erquiaga, María José Catania, Carlos García, Sebastían Outline Introduction Detection Method Training the threshold Dataset description Experiment
Enhancing Threat Intelligence Data. 05/24/2017 DC416
 Enhancing Threat Intelligence Data By @3ncr1pted 05/24/2017 DC416 Security consultant researcher/analyst in Threat Intel. Loves APTs, mainframes, ICS SCADA & creating security awareness StarTrek! Boldly
Enhancing Threat Intelligence Data By @3ncr1pted 05/24/2017 DC416 Security consultant researcher/analyst in Threat Intel. Loves APTs, mainframes, ICS SCADA & creating security awareness StarTrek! Boldly
Cisco s Appliance-based Content Security: IronPort and Web Security
 Cisco s Appliance-based Content Security: IronPort E-mail and Web Security Hrvoje Dogan Consulting Systems Engineer, Security, Emerging Markets East 2010 Cisco and/or its affiliates. All rights reserved.
Cisco s Appliance-based Content Security: IronPort E-mail and Web Security Hrvoje Dogan Consulting Systems Engineer, Security, Emerging Markets East 2010 Cisco and/or its affiliates. All rights reserved.
10x Increase Your Team s Effectiveness by Automating the Boring Stuff
 SESSION ID: TTA-R02 10x Increase Your Team s Effectiveness by Automating the Boring Stuff Jonathan Trull Chief Cybersecurity Advisor Microsoft @jonathantrull Vidhi Agarwal Senior Program Manager Microsoft
SESSION ID: TTA-R02 10x Increase Your Team s Effectiveness by Automating the Boring Stuff Jonathan Trull Chief Cybersecurity Advisor Microsoft @jonathantrull Vidhi Agarwal Senior Program Manager Microsoft
Naming in Distributed Systems
 Naming in Distributed Systems Dr. Yong Guan Department of Electrical and Computer Engineering & Information Assurance Center Iowa State University Outline for Today s Talk Overview: Names, Identifiers,
Naming in Distributed Systems Dr. Yong Guan Department of Electrical and Computer Engineering & Information Assurance Center Iowa State University Outline for Today s Talk Overview: Names, Identifiers,
Trend Micro and IBM Security QRadar SIEM
 Trend Micro and IBM Security QRadar SIEM Ellen Knickle, PM QRadar Integrations Robert Tavares, VP IBM Strategic Partnership February 19, 2014 1 Agenda 1. Nature of the IBM Relationship with Trend Micro
Trend Micro and IBM Security QRadar SIEM Ellen Knickle, PM QRadar Integrations Robert Tavares, VP IBM Strategic Partnership February 19, 2014 1 Agenda 1. Nature of the IBM Relationship with Trend Micro
Cato Cloud. Software-defined and cloud-based secure enterprise network. Solution Brief
 Cato Cloud Software-defined and cloud-based secure enterprise network Solution Brief Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise Cato Networks: Software-defined and Cloud-based
Cato Cloud Software-defined and cloud-based secure enterprise network Solution Brief Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise Cato Networks: Software-defined and Cloud-based
NetWitness Overview. Copyright 2011 EMC Corporation. All rights reserved.
 NetWitness Overview 1 The Current Scenario APT Network Security Today Network-layer / perimeter-based Dependent on signatures, statistical methods, foreknowledge of adversary attacks High failure rate
NetWitness Overview 1 The Current Scenario APT Network Security Today Network-layer / perimeter-based Dependent on signatures, statistical methods, foreknowledge of adversary attacks High failure rate
Configuring the Botnet Traffic Filter
 CHAPTER 51 Malware is malicious software that is installed on an unknowing host. Malware that attempts network activity such as sending private data (passwords, credit card numbers, key strokes, or proprietary
CHAPTER 51 Malware is malicious software that is installed on an unknowing host. Malware that attempts network activity such as sending private data (passwords, credit card numbers, key strokes, or proprietary
Threat Detection and Mitigation for IoT Systems using Self Learning Networks (SLN)
 Threat Detection and Mitigation for IoT Systems using Self Learning Networks (SLN) JP Vasseur, PhD - Cisco Fellow jpv@cisco.com Maik G. Seewald, CISSP Sr. Technical Lead maseewal@cisco.com June 2016 Cyber
Threat Detection and Mitigation for IoT Systems using Self Learning Networks (SLN) JP Vasseur, PhD - Cisco Fellow jpv@cisco.com Maik G. Seewald, CISSP Sr. Technical Lead maseewal@cisco.com June 2016 Cyber
TREND MICRO SMART PROTECTION SUITES
 SOLUTION BROCHURE TREND MICRO SMART ROTECTION SUITES Maximum endpoint security from your proven security partner Get smarter security that goes where your users go The threat landscape is constantly changing,
SOLUTION BROCHURE TREND MICRO SMART ROTECTION SUITES Maximum endpoint security from your proven security partner Get smarter security that goes where your users go The threat landscape is constantly changing,
Security with FailSafe
 Email Security with FailSafe Anti spam and anti virus protection and email continuity for your mail server Email Security provides comprehensive and highly effective virus, spam and content filtering of
Email Security with FailSafe Anti spam and anti virus protection and email continuity for your mail server Email Security provides comprehensive and highly effective virus, spam and content filtering of
Threat Centric Network Security
 BRKSEC-2056 Threat Centric Network Security Ted Bedwell, Principal Engineer Network Threat Defence Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
BRKSEC-2056 Threat Centric Network Security Ted Bedwell, Principal Engineer Network Threat Defence Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
A Comprehensive CyberSecurity Policy
 A Comprehensive CyberSecurity Policy Review of ALL NGFW Capabilities Attack Surface Reduction From Complex to Comprehensive Before and After of a PANW customer 1 2 1 Enhanced Policy on the L7 layer Leverage
A Comprehensive CyberSecurity Policy Review of ALL NGFW Capabilities Attack Surface Reduction From Complex to Comprehensive Before and After of a PANW customer 1 2 1 Enhanced Policy on the L7 layer Leverage
Choose Your Battles How To Fight The Right Wars. Eyal Paz, Security Researcher
 Choose Your Battles How To Fight The Right Wars Eyal Paz, Security Researcher whoami Security Researcher at Check Point B.Sc. in Software Engineering, studying towards M.Sc. in Computer Science Information
Choose Your Battles How To Fight The Right Wars Eyal Paz, Security Researcher whoami Security Researcher at Check Point B.Sc. in Software Engineering, studying towards M.Sc. in Computer Science Information
Herd Intelligence: true protection from targeted attacks. Ryan Sherstobitoff, Chief Corporate Evangelist
 Herd Intelligence: true protection from targeted attacks Ryan Sherstobitoff, Chief Corporate Evangelist Complexity Web Based Malware Attacks Crimeware Intelligent Botnets Vulnerabilities Worm/ Outbreaks
Herd Intelligence: true protection from targeted attacks Ryan Sherstobitoff, Chief Corporate Evangelist Complexity Web Based Malware Attacks Crimeware Intelligent Botnets Vulnerabilities Worm/ Outbreaks
Threat Intel for All: There s More to Your Data than Meets the Eye
 Threat Intel for All: There s More to Your Data than Meets the Eye By @3ncr1pted 07/28/2017 Wall of Sheep Security consultant researcher/analyst in Threat Intel. Loves APTs, mainframes, ICS SCADA & creating
Threat Intel for All: There s More to Your Data than Meets the Eye By @3ncr1pted 07/28/2017 Wall of Sheep Security consultant researcher/analyst in Threat Intel. Loves APTs, mainframes, ICS SCADA & creating
Symantec Ransomware Protection
 Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
Symantec Endpoint Protection 14
 Symantec Endpoint Protection Cloud Security Made Simple Symantec Endpoint Protection 14 Data Data Sheet: Sheet: Endpoint Endpoint Security Security Overview Last year, we saw 431 million new malware variants,
Symantec Endpoint Protection Cloud Security Made Simple Symantec Endpoint Protection 14 Data Data Sheet: Sheet: Endpoint Endpoint Security Security Overview Last year, we saw 431 million new malware variants,
File Reputation Filtering and File Analysis
 This chapter contains the following sections: Overview of, page 1 Configuring File Reputation and Analysis Features, page 5 File Reputation and File Analysis Reporting and Tracking, page 14 Taking Action
This chapter contains the following sections: Overview of, page 1 Configuring File Reputation and Analysis Features, page 5 File Reputation and File Analysis Reporting and Tracking, page 14 Taking Action
OODA Security. Taking back the advantage!
 OODA Security Taking back the advantage! About Me Kevin Fiscus Owner Cyber Defense Advisors 24 Years in IT 13 Years in security SANS Certified Instructor GIAC Security Expert Cyber Guardian Red/Blue Team
OODA Security Taking back the advantage! About Me Kevin Fiscus Owner Cyber Defense Advisors 24 Years in IT 13 Years in security SANS Certified Instructor GIAC Security Expert Cyber Guardian Red/Blue Team
Update from the RIPE NCC
 Update from the RIPE NCC INEX Meeting, Dublin, 14 December 2011 Mirjam Kühne, RIPE NCC Outline RIPE Labs - Background, Purpose, Content, Participation IPv6 Activities and Statistics RIPE Atlas RIPEstat
Update from the RIPE NCC INEX Meeting, Dublin, 14 December 2011 Mirjam Kühne, RIPE NCC Outline RIPE Labs - Background, Purpose, Content, Participation IPv6 Activities and Statistics RIPE Atlas RIPEstat
RSA Advanced Security Operations Richard Nichols, Director EMEA. Copyright 2015 EMC Corporation. All rights reserved. 1
 RSA Advanced Security Operations Richard Nichols, Director EMEA 1 What is the problem we need to solve? 2 Attackers Are Outpacing Defenders..and the Gap is Widening Attacker Capabilities The defender-detection
RSA Advanced Security Operations Richard Nichols, Director EMEA 1 What is the problem we need to solve? 2 Attackers Are Outpacing Defenders..and the Gap is Widening Attacker Capabilities The defender-detection
Synchronized Security
 Synchronized Security 2 Endpoint Firewall Synchronized Security Platform and Strategy Admin Manage All Sophos Products Self Service User Customizable Alerts Partner Management of Customer Installations
Synchronized Security 2 Endpoint Firewall Synchronized Security Platform and Strategy Admin Manage All Sophos Products Self Service User Customizable Alerts Partner Management of Customer Installations
TREND MICRO SMART PROTECTION SUITES
 SOLUTION BROCHURE TREND MICRO SMART ROTECTION SUITES Maximum Trend Micro XGen security from your proven security partner Get smarter security that goes where your users go The threat landscape is constantly
SOLUTION BROCHURE TREND MICRO SMART ROTECTION SUITES Maximum Trend Micro XGen security from your proven security partner Get smarter security that goes where your users go The threat landscape is constantly
Kaspersky Security Network
 The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
Beyond Blind Defense: Gaining Insights from Proactive App Sec
 Beyond Blind Defense: Gaining Insights from Proactive App Sec Speaker Rami Essaid CEO Distil Networks Blind Defense Means Trusting Half Your Web Traffic 46% of Web Traffic is Bots Source: Distil Networks
Beyond Blind Defense: Gaining Insights from Proactive App Sec Speaker Rami Essaid CEO Distil Networks Blind Defense Means Trusting Half Your Web Traffic 46% of Web Traffic is Bots Source: Distil Networks
ConnectWise Automate. What is ConnectWise Automate?
 What is ConnectWise Automate? ConnectWise Automate is a remote monitoring and management tool (RMM) that allows us to actively track the health and performance of your IT network. We compile that data
What is ConnectWise Automate? ConnectWise Automate is a remote monitoring and management tool (RMM) that allows us to actively track the health and performance of your IT network. We compile that data
Advanced Endpoint Protection
 Advanced Endpoint Protection Protecting Endpoints and Servers Nick Levay, Chief Security Officer, Bit9 @rattle1337 2014 Bit9. All Rights Reserved About Me Chief Security Officer, Bit9
Advanced Endpoint Protection Protecting Endpoints and Servers Nick Levay, Chief Security Officer, Bit9 @rattle1337 2014 Bit9. All Rights Reserved About Me Chief Security Officer, Bit9
Norse IPViking Technical Overview
 Norse IPViking Technical Overview WHITE PAPER Table of Contents Introduction Gathering Dark Intelligence Global Coverage and Sample Rate Strategically Located High Performance Infrastructure Big Data and
Norse IPViking Technical Overview WHITE PAPER Table of Contents Introduction Gathering Dark Intelligence Global Coverage and Sample Rate Strategically Located High Performance Infrastructure Big Data and
SSAC Fast Flux Activities
 SSAC Fast Flux Activities Dave Piscitello ICANN SSAC ICANN SSAC, Cairo Nov 2008 Page 1 Long and Winding Road January 2008: SAC 025 Fast Flux Hosting and DNS Result of 4 month study and cooperative work
SSAC Fast Flux Activities Dave Piscitello ICANN SSAC ICANN SSAC, Cairo Nov 2008 Page 1 Long and Winding Road January 2008: SAC 025 Fast Flux Hosting and DNS Result of 4 month study and cooperative work
WINNERS AND LOSERS OF THE 2018 CYBERTHREAT ROLLERCOASTER. Claudio Tosi, Sales Engineer, Malwarebytes
 WINNERS AND LOSERS OF THE 2018 CYBERTHREAT ROLLERCOASTER Claudio Tosi, Sales Engineer, Malwarebytes 1 Why are businesses getting hit with so much malware? 2 BUSINESS DETECTION 2017/2018 Silent Threats
WINNERS AND LOSERS OF THE 2018 CYBERTHREAT ROLLERCOASTER Claudio Tosi, Sales Engineer, Malwarebytes 1 Why are businesses getting hit with so much malware? 2 BUSINESS DETECTION 2017/2018 Silent Threats
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
Cisco Ransomware Defense The Ransomware Threat Is Real
 Cisco Ransomware Defense The Ransomware Threat Is Real Seguridad Integrada Abril 2018 Ransomware B Malicious Software Encrypts Critical Data Demands Payment Permanent Data Loss Business Impacts Ramifications
Cisco Ransomware Defense The Ransomware Threat Is Real Seguridad Integrada Abril 2018 Ransomware B Malicious Software Encrypts Critical Data Demands Payment Permanent Data Loss Business Impacts Ramifications
Securing the SMB Cloud Generation
 Securing the SMB Cloud Generation Intelligent Protection Against the New Generation of Threats Colin Brackman, National Distribution Manager, Consumer Sales, Symantec Christopher Covert Principal Product
Securing the SMB Cloud Generation Intelligent Protection Against the New Generation of Threats Colin Brackman, National Distribution Manager, Consumer Sales, Symantec Christopher Covert Principal Product
RSA Fraud & Risk Intelligence Solutions
 RSA Fraud & Risk Intelligence Solutions Separating Customers from Criminals May 2015 1 Mobile Social Identities IOT Alternative Authentication Market Disruptors Biometrics Cross Channel Intelligence Sharing
RSA Fraud & Risk Intelligence Solutions Separating Customers from Criminals May 2015 1 Mobile Social Identities IOT Alternative Authentication Market Disruptors Biometrics Cross Channel Intelligence Sharing
Additional Security Services on AWS
 Additional Security Services on AWS Bertram Dorn Specialized Solutions Architect Security / Compliance / DataProtection AWS EMEA The Landscape The Paths Application Data Path Path Cloud Managed by Customer
Additional Security Services on AWS Bertram Dorn Specialized Solutions Architect Security / Compliance / DataProtection AWS EMEA The Landscape The Paths Application Data Path Path Cloud Managed by Customer
Business Logic Attacks BATs and BLBs
 Business Logic Attacks BATs and BLBs Noa Bar-Yosef Security Research Engineer Imperva 12/02/2009 noa@imperva.com Copyright The Foundation Permission is granted to copy, distribute and/or modify this document
Business Logic Attacks BATs and BLBs Noa Bar-Yosef Security Research Engineer Imperva 12/02/2009 noa@imperva.com Copyright The Foundation Permission is granted to copy, distribute and/or modify this document
Identifying and Disrupting Mirai Botnets. Chuck McAuley
 Identifying and Disrupting Mirai Botnets Chuck McAuley Who me? Chuck McAuley Principal Threat Researcher at Ixia s Application Threat Intelligence team Talks to all the people Goes to all the places Does
Identifying and Disrupting Mirai Botnets Chuck McAuley Who me? Chuck McAuley Principal Threat Researcher at Ixia s Application Threat Intelligence team Talks to all the people Goes to all the places Does
Detecting Spammers with SNARE: Spatio-temporal Network-level Automatic Reputation Engine
 Detecting Spammers with SNARE: Spatio-temporal Network-level Automatic Reputation Engine Shuang Hao, Nadeem Ahmed Syed, Nick Feamster, Alexander G. Gray, Sven Krasser Motivation Spam: More than Just a
Detecting Spammers with SNARE: Spatio-temporal Network-level Automatic Reputation Engine Shuang Hao, Nadeem Ahmed Syed, Nick Feamster, Alexander G. Gray, Sven Krasser Motivation Spam: More than Just a
Neustar Security Solutions Overview
 Neustar Security Solutions Overview Our digital, hyperconnected world is a world of opportunity, but also one of anonymity and criminal activity. Your job is to minimize risk and enforce an acceptable
Neustar Security Solutions Overview Our digital, hyperconnected world is a world of opportunity, but also one of anonymity and criminal activity. Your job is to minimize risk and enforce an acceptable
The Interactive Guide to Protecting Your Election Website
 The Interactive Guide to Protecting Your Election Website 1 INTRODUCTION Cloudflare is on a mission to help build a better Internet. Cloudflare is one of the world s largest networks. Today, businesses,
The Interactive Guide to Protecting Your Election Website 1 INTRODUCTION Cloudflare is on a mission to help build a better Internet. Cloudflare is one of the world s largest networks. Today, businesses,
SentinelOne Technical Brief
 SentinelOne Technical Brief SentinelOne unifies prevention, detection and response in a fundamentally new approach to endpoint protection, driven by machine learning and intelligent automation. By rethinking
SentinelOne Technical Brief SentinelOne unifies prevention, detection and response in a fundamentally new approach to endpoint protection, driven by machine learning and intelligent automation. By rethinking
Automated Context and Incident Response
 Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
DomainTools for Splunk
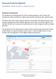 DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
