Contents. SSL-Based Services: HTTPS and FTPS 2. Generating A Certificate 2. Creating A Self-Signed Certificate 3. Obtaining A Signed Certificate 4
|
|
|
- Carmel Maxwell
- 5 years ago
- Views:
Transcription
1 Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 SSL/TLS Security Level 5 A Note About Ports 6 Connecting Via Web Browser 7 Connecting Via FTP Client 8 Additional Web (HTTP) Options 8 SFTP 10 Public/Private Key Authentication Over SFTP 10 Maxum Development Corp.
2 SSL-Based Services: HTTPS and FTPS Rumpus supports SSL (Secure Sockets Layer) encryption for both Web and FTP file transfers. Virtually all modern Web browsers support HTTPS (secure HTTP), and many standard FTP clients support FTPS (secure FTP). In both cases, all critical information is encrypted, including file data, usernames and passwords, directory listing contents, and file management activity. To configure secure services in Rumpus, open the Network Settings window and flip to the Secure Services tab. Configuring secure services Generating A Certificate SSL encryption is based on public key/private key cryptography. Your server will need 2 keys, one public and one private, which will be used to encrypt data. When clients connect, they will download the public key and use it to encode data being uploaded to your server (or decode downloaded data). Only the matching private key can be used to decode the data (or encode data sent by the server). All of this work is performed automatically by software running on the client computer, so no extra effort will be required on the part of your external users. However, as the server administrator, you are responsible for generating a certificate which includes the public key and other data about your organization, and a matching private key. The process of installing a certificate and private key is very particular and can be frustrating, but Rumpus includes tools to make the job easier. Maxum Development Corp. "2
3 To create a certificate and private key, click the Generate A Certificate button. The certificate generation sheet Creating A Self-Signed Certificate The easiest way to install a certificate is to generate your own self-signed certificate. Because you will be creating this type of certificate yourself, with no 3rd party vouching for your server s authenticity, a self-signed certificate will not automatically be trusted by Web browsers and FTP clients. Using a selfsigned certificate still provides strong data encryption and a high level of security, but clients will usually display a warning when they connect, informing the user that no recognized authority has verified the server s authenticity. In most cases, when first setting up a server or new secure services, installing a self-signed certificate is a good way to get started. To create and install the certificate, choose the Generate A Self-Signed (Untrusted) Certificate option, and complete the remaining fields describing your organization. Once the simple form is complete, click Generate Certificate and Rumpus will create and install the certificate and private key. The certificate will include the public key which matches the private key generated at the same time. Maxum Development Corp. "3
4 Obtaining A Signed Certificate To allow Web browsers and FTP clients to automatically accept your certificate, the certificate must be purchased from a recognized authority. There are many authorities, including Thawte, GoDaddy, QualitySSL, VeriSign, and others. Google SSL certificate for additional information and numerous provider options. When you purchase a certificate, the provider will ask you for a CSR, or Certificate Signing Request. To generate the CSR, click the Generate Certificate button, select the Generate A CSR For Purchase Of A Trusted Certificate option, and complete the form. Rumpus will generate a private key and a matching CSR, then display the CSR. You can copy and paste the CSR from the text area on the display, or you can click the Save CSR To Text File to save it for uploading. Use whichever method is easiest based on how the CSR will be sent to your chosen authority. Important! Signing authorities do not provide you with a private key. What you get back from the authority will be an SSL certificate, which will need to match the private key generated along with the CSR. Do not use the Generate Certificate function after generating your CSR. If you do, a new private key will be created and installed, and it will not match the certificate sent by the authority. After completing the application and sending the CSR, you will receive a certificate from the authority. Click the View/Load Certificate button and then click Load Certificate. Select the certificate file sent to your organization by the authority. The authority may also provide an intermediate (also known as chaining ) certificate. Rumpus will allow you to select it, as well. Alternatively, you can copy and paste the certificate directly into the Certificate text area. Be sure to paste in the entire certificate, including the --- Begin --- and --- End --- lines. If your authority provided you with an intermediate certificate, paste it into the Certificate text area, too, immediately following your own. In this case, the --- Begin --- line of the intermediate chain certificate will immediately follow the --- End --- line of your own. The authority should never send you a private key (it is, after all, private). The private key is generated by Rumpus and should never leave the server. It should be kept safe and secret. Do not load any information sent to you by the authority as the Certificate Key. Maxum Development Corp. "4
5 Enabling Secure Services Once a certificate and key have been installed (by either method), enabling secure services is as easy as checking a couple of checkboxes. To enable secure Web connections, turn on the Enable Secure Web Service option. Then, if you need to force all Web connections to the secure channel, turn on the Direct All Web Connections To HTTPS option. There are 2 methods of establishing secure FTP service, and both are supported by Rumpus. The first method is called simply FTPS, or sometimes FTP with TLS/SSL. FTPS sessions are carried out over the usual FTP port (by default, 21). In this case, clients essentially connect using standard FTP, and then upgrade to a secure connection as soon as the session begins. This is the more modern, and preferred mechanism for providing secure FTP service. The second option is referred to as Implicit FTPS. Implicit FTPS connections use an alternate port (990, by default) which is distinct from standard FTP. While this method is less common and no longer recommended, it is provided for backward compatibility with older clients. For newly deployed FTPS servers, consider leaving Implicit Secure FTP off and recommending to clients that they use the more common form of FTPS. SSL/TLS Security Level The SSL/TLS protocol that implements secure connections between two computers has continually evolved since first introduced decades ago. Specifically, various problems with the protocol have been corrected, key strength has improved, etc. So, to provide the optimum level of security, the most up-todate SSL capabilities should be used. However, clients (Web browsers, primarily) that were released before recent improvements in SSL/TLS lack these more advanced features. Allowing these older clients to connect constitutes a security threat, because by allowing old clients to connect and use weaker and potentially buggy security protocols, those sessions are potentially vulnerable. So there is a basic choice you need to make as the server administrator, between supporting older clients and enforcing more modern security protocols. In Rumpus, you make this choice using the "SSL/TLS Security Level" option on the Network Settings window, Secure Services tab. Maxum Development Corp. "5
6 Keep in mind that even older SSL protocols are far more secure than plain text connections, so if you need to support a wide variety of clients (Windows XP users, for example), setting the security level to "Support Ancient Clients (Least Secure)" should not necessarily be considered "insecure". Highly sophisticated attacks against your server may be possible in this case, but if the content of your server doesn't warrant extremely high security, this may be a perfectly acceptable trade-off that allows virtually anyone, even those using very old computers, to access the server with security that is much better than plain HTTP. On the other hand, if the content on your server is sensitive, or you are at a high risk of being hacked, choosing "Require Up To Date Clients (Most Secure)" is probably the right choice. In this case, Rumpus restricts clients to only the most secure cipher suites, stronger keys, etc. which ensures the greatest level of security between the client and server, but requires that clients also be running software capable of these advanced algorithms. In between these extremes fall two other choices. "Support Older Clients" eliminates many of the most likely possible SSL exploits and implements reasonably strong keys, while allowing the large majority of clients in use today to connect to the server securely. "Support Modern Clients" provides excellent security by requiring strong, modern cipher suites and very strong key lengths, while still supporting access by a wide range of modern devices. A Note About Ports By default, HTTP service is provided on port 80, FTP on port 21, HTTPS on port 443 and Implicit FTPS on port 990. (Standard FTPS, as an extension to non-secure FTP, uses 21.) It is important to note, however, that these are merely defaults. There is nothing special about port 80, 21, 443 or 990. In particular, ports 443 and 990 are not intrinsically secure. For example, secure HTTP service is not created merely by running a Web service on port on port 443. Do not set the HTTP Port Number (on the Options tab of the Web Settings window) to 443 or set the HTTPS Port to 80. The HTTP and HTTPS servers are separate, and if they are assigned the same port number, a conflict will arise. Similarly, make sure that the Implicit FTPS Port does not conflict with the standard FTP port specified on the FTP Settings window. Of course, there are a number of reasons for running any of these services on non-standard ports, and changing ports is fully supported in Rumpus. However, it s important to note that port selection does not determine whether or not data is encrypted or secured. When possible, use the default port for each offered service (HTTP, HTTPS, FTP and Implicit FTPS), and be sure that each service is assigned a unique port number to avoid conflicts. Maxum Development Corp. "6
7 Connecting Via Web Browser Even if your users primarily access your Rumpus server via FTP, we recommend that you first test your SSL encrypted server using a Web browser. Browsers almost universally support HTTPS (HTTP encrypted using SSL), and do so in a standard way that is simpler than FTP. Once you have confirmed that the SSL is functioning correctly via Web browser, you can then move on to connecting with a compatible FTP client. On another computer on your network, open a Web browser and enter the connection URL as: Note the s in which tells the browser to make the connection via the SSL encrypted channel. Most Web browsers will display a lock icon somewhere on the display to indicate that the connection is secure. The WFM session will continue normally, the lock icon being the primary visible evidence that data is now being transferred securely. Client connections via https will be secured Maxum Development Corp. "7
8 Connecting Via FTP Client While many FTP clients support FTPS, not all do, so the first step in establishing a secure FTPS connection is to confirm that you are using an FTPS-compatible client. On the Mac, both Fetch and Transmit, as well as several other popular clients, support FTPS. In most cases, the option to connect securely is provided on the connection window, along with the server name, username and password. The option may be labelled Connect using, and will usually be called either FTPS or FTP with TLS/SSL. An option called FTP with Implicit SSL may also be offered, and may be used if Implicit FTP has been enabled in Rumpus. Additional Web (HTTP) Options When you enable HTTPS, there are two additional options that improve security on servers that accept and store sensitive data. Direct All Connections To HTTPS When this option is enabled, users who connect via HTTP (non-secured Web session) will be automatically redirected to HTTPS. In other words, all users will automatically be connected securely, even if the user accesses the server by it's non-secure URL. Unlike FTP, where "redirection" isn't possible, Web users who connect on an unencrypted channel will be gracefully guided to a secure session. Most users, in fact, may not even realize the change has been made. The only down-side to this is that some clients may be able to connect via HTTP but not HTTPS, due to firewall restrictions, for example. This not very common on modern networks, though, since so many Web sites only allow HTTPS sessions. Note: Do note enable this option until HTTPS access has been set up, tested, and is known to be working as expected. If HTTPS is not working perfectly, enabling this option will essentially prevent any user from accessing the system, since all users will be redirected to the non-functioning HTTPS service. Enable HTTP Strict Transport Security If your server has HTTPS enabled, and requires all users to connect securely (which means that you have most likely enabled "Redirect All Connections To HTTPS"), you may also choose to enable Strict Transport Security. The feature prevents several classes of potential attacks for users on public networks by alerting the browser to the fact that all connections to the server must be performed securely. Maxum Development Corp. "8
9 Maxum Development Corp. "9
10 SFTP It is important to understand the difference between FTPS, which is SSL-encrypted FTP, and SFTP, which is the file transfer module that is part of the SSH protocol. Rumpus supports both FTPS and SFTP, but the two protocols are entirely different, which is an important point when clients attempt to connect since many clients support both. FTPS is built on top of SSL, and is described in the sections above. Despite the fact that SFTP is a technically very different from FTP, it is configured in Rumpus on the FTP Settings window, SFTP tab. Like SSL, SSH requires the use of a private/public key pair. Keys are typically associated with a user account defined on the server, but since Rumpus provides service for any number of users, it requires it s own host key and then requires each user to authenticate by specifying their name and password. To generate a host key for Rumpus, just click the Generate Key Files button, which causes both RSA and DSA keys to be stored in the Rumpus configuration folder ( /usr/local/rumpus/ ). With keys generated, click Enable SFTP Service to turn on the SFTP engine in Rumpus. The port used for SFTP (by default, 22) and the number of SFTP users allowed to access the server at any one time, are also configurable. All regular Rumpus privileges and other functions are applied as you would expect. SFTP users will have access only to their own Home Folder, their user account privileges will be enforced (including assigned Folder Sets), uploaded files will trigger Event Notices, etc. In short, enabling SFTP simply provides an alternative to regular FTP, offering greater security, but in all other ways behaving in exactly the same manner. Public/Private Key Authentication Over SFTP "Authentication" is essentially any mechanism that securely identifies a client. We most often think of authentication as being performed via username and password. For example, when you run a Rumpus server, whether the client connects via Web, FTP, WebDAV, or any other protocol, a username and password is required to log in. The username and password serves to securely and uniquely identify the person accessing the server, authenticating them and granting the privileges associated with that user account. SFTP supports another method: Public/Private Key Authentication. In this case, clients can connect without a username and password, as long as the client possesses a carefully guarded key file that is used in place of the username and password. It can be handy, especially for automated clients or clients who will be frequently accessing the server, as it improves security and simplifies the login process. Maxum Development Corp. "10
11 Public/Private key authentication requires 2 key files: a public key which will be stored on the server and a private key which will be kept on the client. It is crucial that the private key be carefully guarded and kept only on the client computer that is authorized to access the Rumpus server. Like a stolen username and password, if a private key is obtained by a non-authorized person, it can be used to access the Rumpus server with authorization rights associated with that key. Quick Setup Steps When a client sends you a public key and asks that you install it so they can access the server, follow these steps: 1. Create a user account on the Define Users window, with the Home Folder, privileges, and other user settings set to properly control the client's access. Use the password generator to assign a long random string, preventing the account from being used via standard name/password login. 2. Open the Rumpus config folder (choose "Open Config Folder" from the "File" menu in Rumpus) then move into the "sshkeys" folder. 3. Copy the public key into that folder and name it the same as the user account you defined in Rumpus, with ".pub" appended to the name (as in "AcmeWidgets.pub"). 4. Click "Stop Server" and "Start Server" to ensure that the Rumpus service loads the new key. These steps are described in more detail, including generating a private/public key pair yourself, below. Setup Details First, on the server, create a user account for the client that will authenticate using the public/private key pair. While a username and password won't be necessary, an account is required so that you can define access permissions, the Home Folder for the client, Event Notices to be triggered, etc. For example, you might create a user account in Rumpus named "AcmeWidgets", with a long random password (so that the account isn't accidentally used via username/password authentication) and all other account settings specified for the client's access. The private key/public key pair will be generated on the client, so that the client can keep the private key private. There are a variety of tools for generating SSH keys. Which is best depends on the platform and experience of the client. On a Mac/Unix system, an SSH pair can be generated in the Terminal with the command: ssh-keygen -t rsa Maxum Development Corp. "11
12 You will next be prompted for a filename. Have the client supply a filename that matches the user account name in Rumpus. In the example above, the filename would be "AcmeWidgets". Next, you'll be prompted for a passphrase, which for these purposes should be left blank. The result will be 2 files, in this case, "AcmeWidgets" and "AcmeWidgets.pub". "AcmeWidgets", the private key file, should be kept secure on the client computer. Have the client send "AcmeWidgets.pub" to you, the Rumpus server administrator. Note that while it is a "public" key, it should be maintained with a reasonable level of care as well. It is conceivable that if the public key were to be installed on some other server, and the client was tricked into connecting to that other server, the client could unknowingly transfer sensitive data to that server. This scenario is generally not likely, but it is best to ensure that the public key is sent only to the Rumpus administrator, for use only on the server to which the client plans to connect. When you, as the Rumpus administrator, receive the key, put it on the server. In Rumpus, choose "Open Config Folder" from the "File" menu and move down into the "sshkeys" folder. Put the public key file in that folder. Note that the filename must match exactly the user account name in Rumpus, and must end in ".pub". So, in the "Acme Widgets" example, the public key file must be placed in the "sshkeys" folder in the Rumpus config folder, and must be named exactly "AcmeWidgets.pub". Rumpus supports up to 32 loaded public keys. After installing a public key, click "Stop Server" and "Start Server" to force Rumpus to identify and load the new key before having the client connect. Connecting The client can now connect using their private key to authenticate. For example, on Mac/Unix systems in the Terminal, and SFTP session can be initiated using: SFTP -i AcmeWidgets In this example, "AcmeWidgets" represents the name of the private key file and " " represents the server name or IP address to which the connection should be made. Note: The public and private key represent two pieces that make a whole, and should be kept separate. On the client, do not keep the public and private key together in the same place. This is more than just good security practice, as the SFTP utility will not correctly connect to the server when the public key and private key are kept in the same folder. As always, if you have problems or questions, please contact Maxum Technical Support at support@maxum.com. Maxum Development Corp. "12
Contents. SSL-Based Services: HTTPS and FTPS 2. Generating A Certificate 2. Creating A Self-Signed Certificate 3. Obtaining A Signed Certificate 4
 Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 A Note About Ports 5 Connecting
Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 A Note About Ports 5 Connecting
Managing User Accounts
 Contents User Accounts 2 Passwords 3 Common User Account Settings 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. The basic operation of a file transfer server boils
Contents User Accounts 2 Passwords 3 Common User Account Settings 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. The basic operation of a file transfer server boils
Managing User Accounts
 Contents User Accounts 2 Passwords 3 Common User Account Settings 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. The basic operation of a file transfer server boils
Contents User Accounts 2 Passwords 3 Common User Account Settings 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. The basic operation of a file transfer server boils
Contents. Is Rumpus Secure? 2. Use Care When Creating User Accounts 2. Managing Passwords 3. Watch Out For Symbolic Links 4. Deploy A Firewall 5
 Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Symbolic Links 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical
Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Symbolic Links 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical
Contents. Configuring Remote Administration 2. Using Rumpus Remote Administration 6. Administration Groups 7
 Web User Account Management Contents Configuring Remote Administration 2 Using Rumpus Remote Administration 6 Administration Groups 7 Allowing Users To Change Their Own Passwords 8 Maxum Development Corp.
Web User Account Management Contents Configuring Remote Administration 2 Using Rumpus Remote Administration 6 Administration Groups 7 Allowing Users To Change Their Own Passwords 8 Maxum Development Corp.
Managing User Accounts
 Contents User Accounts 2 Passwords 3 Home Folders 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. ! Managing User Accounts The basic operation of a file transfer
Contents User Accounts 2 Passwords 3 Home Folders 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. ! Managing User Accounts The basic operation of a file transfer
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
Using Rumpus On Private Networks
 Using Rumpus On Private Networks Contents How Port Forwarding Works 2 Configuring Your Router 3 Rumpus Setup 4 On Networks With A Dynamic IP Address 4 Testing And Troubleshooting Your Server 4 Maxum Development
Using Rumpus On Private Networks Contents How Port Forwarding Works 2 Configuring Your Router 3 Rumpus Setup 4 On Networks With A Dynamic IP Address 4 Testing And Troubleshooting Your Server 4 Maxum Development
SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security
 SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security Consider 2. Based on DNS, identified the IP address of www.cuhk.edu.hk is 137.189.11.73. 1. Go to http://www.cuhk.edu.hk 3. Forward the
SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security Consider 2. Based on DNS, identified the IP address of www.cuhk.edu.hk is 137.189.11.73. 1. Go to http://www.cuhk.edu.hk 3. Forward the
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
Evaluating the Security Risks of Static vs. Dynamic Websites
 Evaluating the Security Risks of Static vs. Dynamic Websites Ballard Blair Comp 116: Introduction to Computer Security Professor Ming Chow December 13, 2017 Abstract This research paper aims to outline
Evaluating the Security Risks of Static vs. Dynamic Websites Ballard Blair Comp 116: Introduction to Computer Security Professor Ming Chow December 13, 2017 Abstract This research paper aims to outline
WHITE PAPER. Authentication and Encryption Design
 WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
AN IPSWITCH WHITEPAPER. The Definitive Guide to Secure FTP
 AN IPSWITCH WHITEPAPER The Definitive Guide to Secure FTP The Importance of File Transfer Are you concerned with the security of file transfer processes in your company? According to a survey of IT pros
AN IPSWITCH WHITEPAPER The Definitive Guide to Secure FTP The Importance of File Transfer Are you concerned with the security of file transfer processes in your company? According to a survey of IT pros
C1: Define Security Requirements
 OWASP Top 10 Proactive Controls IEEE Top 10 Software Security Design Flaws OWASP Top 10 Vulnerabilities Mitigated OWASP Mobile Top 10 Vulnerabilities Mitigated C1: Define Security Requirements A security
OWASP Top 10 Proactive Controls IEEE Top 10 Software Security Design Flaws OWASP Top 10 Vulnerabilities Mitigated OWASP Mobile Top 10 Vulnerabilities Mitigated C1: Define Security Requirements A security
Contents. Before You Start 2. Configuring Rumpus 3. Testing Accessible Directory Service Access 5. Specifying Home Folders 6
 Contents Before You Start 2 Configuring Rumpus 3 Testing Accessible Directory Service Access 5 Specifying Home Folders 6 Active Directory Groups 7 Specifying An Alternate Users Container 8 Maxum Development
Contents Before You Start 2 Configuring Rumpus 3 Testing Accessible Directory Service Access 5 Specifying Home Folders 6 Active Directory Groups 7 Specifying An Alternate Users Container 8 Maxum Development
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
Authentication CHAPTER 17
 Authentication CHAPTER 17 Authentication Authentication is the process by which you decide that someone is who they say they are and therefore permitted to access the requested resources. getting entrance
Authentication CHAPTER 17 Authentication Authentication is the process by which you decide that someone is who they say they are and therefore permitted to access the requested resources. getting entrance
Recommendations for Device Provisioning Security
 Internet Telephony Services Providers Association Recommendations for Device Provisioning Security Version 2 May 2017 Contact: team@itspa.org.uk Contents Summary... 3 Introduction... 3 Risks... 4 Automatic
Internet Telephony Services Providers Association Recommendations for Device Provisioning Security Version 2 May 2017 Contact: team@itspa.org.uk Contents Summary... 3 Introduction... 3 Risks... 4 Automatic
Configuring the CSS for Device Management
 CHAPTER 2 Configuring the CSS for Device Management Before you can use the WebNS Device Management user interface software, you need to perform the tasks described in the following sections: WebNS Device
CHAPTER 2 Configuring the CSS for Device Management Before you can use the WebNS Device Management user interface software, you need to perform the tasks described in the following sections: WebNS Device
Generating Certificate Signing Requests
 SSL Generating Certificate Signing Requests Page 1 Contents Introduction... 1 What is a CSR?... 2 IIS 8... 2 IIS 7... 7 Apache... 12 Generate a Key Pair... 12 Generate to CSR... 13 Backup your private
SSL Generating Certificate Signing Requests Page 1 Contents Introduction... 1 What is a CSR?... 2 IIS 8... 2 IIS 7... 7 Apache... 12 Generate a Key Pair... 12 Generate to CSR... 13 Backup your private
Accessing the Ministry Secure File Delivery Service (SFDS)
 Ministry of Health Services Accessing the Ministry Secure File Delivery Service (SFDS) A Guide for New Users To SFDS And Digital Certificate Installation May 2004 Preface Purpose Audience Structure This
Ministry of Health Services Accessing the Ministry Secure File Delivery Service (SFDS) A Guide for New Users To SFDS And Digital Certificate Installation May 2004 Preface Purpose Audience Structure This
Distributed Systems. 25. Authentication Paul Krzyzanowski. Rutgers University. Fall 2018
 Distributed Systems 25. Authentication Paul Krzyzanowski Rutgers University Fall 2018 2018 Paul Krzyzanowski 1 Authentication For a user (or process): Establish & verify identity Then decide whether to
Distributed Systems 25. Authentication Paul Krzyzanowski Rutgers University Fall 2018 2018 Paul Krzyzanowski 1 Authentication For a user (or process): Establish & verify identity Then decide whether to
Content and Purpose of This Guide... 1 User Management... 2
 Contents Introduction--1 Content and Purpose of This Guide........................... 1 User Management........................................ 2 Security--3 Security Features.........................................
Contents Introduction--1 Content and Purpose of This Guide........................... 1 User Management........................................ 2 Security--3 Security Features.........................................
CS November 2018
 Authentication Distributed Systems 25. Authentication For a user (or process): Establish & verify identity Then decide whether to allow access to resources (= authorization) Paul Krzyzanowski Rutgers University
Authentication Distributed Systems 25. Authentication For a user (or process): Establish & verify identity Then decide whether to allow access to resources (= authorization) Paul Krzyzanowski Rutgers University
Datasheet - Sitekit CMS Secure Forms
 Datasheet - Sitekit CMS Secure Forms Registered Office Business Unit Role Document Type Document Author Document Checked by Sitekit Ltd Sitekit House Broom Place Portree Isle of Skye IV51 9HL Sitekit.Solutions
Datasheet - Sitekit CMS Secure Forms Registered Office Business Unit Role Document Type Document Author Document Checked by Sitekit Ltd Sitekit House Broom Place Portree Isle of Skye IV51 9HL Sitekit.Solutions
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
Transport Level Security
 2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to
 1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
CPSC 467: Cryptography and Computer Security
 CPSC 467: Cryptography and Computer Security Michael J. Fischer Lecture 24a December 2, 2013 CPSC 467, Lecture 24a 1/20 Secure Shell (SSH) Transport Layer Security (TLS) Digital Rights Management and Trusted
CPSC 467: Cryptography and Computer Security Michael J. Fischer Lecture 24a December 2, 2013 CPSC 467, Lecture 24a 1/20 Secure Shell (SSH) Transport Layer Security (TLS) Digital Rights Management and Trusted
PDxxxxx {P/N} {Doc Description} PRELIMINARY PDS-104_SECURED_WEB_BROWSING_UG. PDS-104G - Secured web browsing certificate management.
 PDS-104G - Secured web browsing certificate management User Guide TABLE OF CONTENTS PDS-104_SECURED_WEB_BROWSING_UG 1 INTRODUCTION...2 1.1 GENERAL... 2 1.2 ENFORCING SECURED WEB BROWSING... 2 1.3 SECURED
PDS-104G - Secured web browsing certificate management User Guide TABLE OF CONTENTS PDS-104_SECURED_WEB_BROWSING_UG 1 INTRODUCTION...2 1.1 GENERAL... 2 1.2 ENFORCING SECURED WEB BROWSING... 2 1.3 SECURED
WHITE PAPER. Secure communication. - Security functions of i-pro system s
 WHITE PAPER Secure communication - Security functions of i-pro system s Panasonic Video surveillance systems Table of Contents 1. Introduction... 1 2. Outline... 1 3. Common security functions of the i-pro
WHITE PAPER Secure communication - Security functions of i-pro system s Panasonic Video surveillance systems Table of Contents 1. Introduction... 1 2. Outline... 1 3. Common security functions of the i-pro
Fasthosts Customer Support Generating Certificate Signing Requests
 Fasthosts Customer Support Generating Certificate Signing Requests Generating a CSR is the first step to take when you want to apply an SSL certificate to a domain on your server. This manual covers how
Fasthosts Customer Support Generating Certificate Signing Requests Generating a CSR is the first step to take when you want to apply an SSL certificate to a domain on your server. This manual covers how
Trusted Identities. Foundational to Cloud Services LILA KEE CHIEF PRODUCT OFFICER GLOBALSIGN
 Trusted Identities Foundational to Cloud Services LILA KEE CHIEF PRODUCT OFFICER GLOBALSIGN WHAT YOU WILL LEARN TODAY Strong identity verification as a security measure and business enabler Authentication
Trusted Identities Foundational to Cloud Services LILA KEE CHIEF PRODUCT OFFICER GLOBALSIGN WHAT YOU WILL LEARN TODAY Strong identity verification as a security measure and business enabler Authentication
Security Guide. security
 Security Guide security PREFACE Every effort has been made to ensure that the information in this document is complete, accurate, and up-to-date. The manufacturer assumes no responsibility for the results
Security Guide security PREFACE Every effort has been made to ensure that the information in this document is complete, accurate, and up-to-date. The manufacturer assumes no responsibility for the results
Installation and usage of SSL certificates: Your guide to getting it right
 Installation and usage of SSL certificates: Your guide to getting it right So, you ve bought your SSL Certificate(s). Buying your certificate is only the first of many steps involved in securing your website.
Installation and usage of SSL certificates: Your guide to getting it right So, you ve bought your SSL Certificate(s). Buying your certificate is only the first of many steps involved in securing your website.
Data Security and Privacy. Topic 14: Authentication and Key Establishment
 Data Security and Privacy Topic 14: Authentication and Key Establishment 1 Announcements Mid-term Exam Tuesday March 6, during class 2 Need for Key Establishment Encrypt K (M) C = Encrypt K (M) M = Decrypt
Data Security and Privacy Topic 14: Authentication and Key Establishment 1 Announcements Mid-term Exam Tuesday March 6, during class 2 Need for Key Establishment Encrypt K (M) C = Encrypt K (M) M = Decrypt
VMware Horizon JMP Server Installation and Setup Guide. 13 DEC 2018 VMware Horizon 7 7.7
 VMware Horizon JMP Server Installation and Setup Guide 13 DEC 2018 VMware Horizon 7 7.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
VMware Horizon JMP Server Installation and Setup Guide 13 DEC 2018 VMware Horizon 7 7.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
Cryptography (Overview)
 Cryptography (Overview) Some history Caesar cipher, rot13 substitution ciphers, etc. Enigma (Turing) Modern secret key cryptography DES, AES Public key cryptography RSA, digital signatures Cryptography
Cryptography (Overview) Some history Caesar cipher, rot13 substitution ciphers, etc. Enigma (Turing) Modern secret key cryptography DES, AES Public key cryptography RSA, digital signatures Cryptography
Nigori: Storing Secrets in the Cloud. Ben Laurie
 Nigori: Storing Secrets in the Cloud Ben Laurie (benl@google.com) April 23, 2013 1 Introduction Secure login is something we would clearly like, but achieving it practically for the majority users turns
Nigori: Storing Secrets in the Cloud Ben Laurie (benl@google.com) April 23, 2013 1 Introduction Secure login is something we would clearly like, but achieving it practically for the majority users turns
WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution
 WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. We have been
WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. We have been
SECURITY AND DATA REDUNDANCY. A White Paper
 SECURITY AND DATA REDUNDANCY A White Paper Security and Data Redundancy Whitepaper 2 At MyCase, Security is Our Top Priority. Here at MyCase, we understand how important it is to keep our customer s data
SECURITY AND DATA REDUNDANCY A White Paper Security and Data Redundancy Whitepaper 2 At MyCase, Security is Our Top Priority. Here at MyCase, we understand how important it is to keep our customer s data
EasyMorph Server Administrator Guide
 EasyMorph Server Administrator Guide Version 3.9.2 December, 24 th 2018 Table of Contents TABLE OF CONTENTS... 1 PREREQUISITES... 2 Memory requirements... 2 INSTALLATION... 2 License key... 3 SERVER SERVICE
EasyMorph Server Administrator Guide Version 3.9.2 December, 24 th 2018 Table of Contents TABLE OF CONTENTS... 1 PREREQUISITES... 2 Memory requirements... 2 INSTALLATION... 2 License key... 3 SERVER SERVICE
FEPS. SSH Access with Two-Factor Authentication. RSA Key-pairs
 FEPS SSH Access with Two-Factor Authentication RSA Key-pairs access.eps.surrey.ac.uk Contents: Introduction - 3 RSA Key-pairs - 3 Where can I use my RSA Key-Pair? - 3 Step 1 Prepare to generate your RSA
FEPS SSH Access with Two-Factor Authentication RSA Key-pairs access.eps.surrey.ac.uk Contents: Introduction - 3 RSA Key-pairs - 3 Where can I use my RSA Key-Pair? - 3 Step 1 Prepare to generate your RSA
Information Security CS 526
 Information Security CS 526 Topic 14: Key Distribution & Agreement, Secure Communication Topic 14: Secure Communication 1 Readings for This Lecture On Wikipedia Needham-Schroeder protocol (only the symmetric
Information Security CS 526 Topic 14: Key Distribution & Agreement, Secure Communication Topic 14: Secure Communication 1 Readings for This Lecture On Wikipedia Needham-Schroeder protocol (only the symmetric
Project #6: Using ssh, scp and sftp with Key-Based Authentication
 Project #6: Using ssh, scp and sftp with Key-Based Authentication ssh, scp and sftp Going beyond Password Protection Creating Keys Creating Keys with a Passphrase Using Key-Based Authentication in Our
Project #6: Using ssh, scp and sftp with Key-Based Authentication ssh, scp and sftp Going beyond Password Protection Creating Keys Creating Keys with a Passphrase Using Key-Based Authentication in Our
Orbital provide a secure (SSL) Mailserver to protect your privacy and accounts.
 Email Configuration This document is designed to help our clients in setting up email accounts on popular devices and email client software. Orbital provide a secure (SSL) Mailserver to protect your privacy
Email Configuration This document is designed to help our clients in setting up email accounts on popular devices and email client software. Orbital provide a secure (SSL) Mailserver to protect your privacy
UCS Manager Communication Services
 Communication Protocols, page 1 Communication Services, page 1 Non-Secure Communication Services, page 3 Secure Communication Services, page 5 Network-Related Communication Services, page 12 Communication
Communication Protocols, page 1 Communication Services, page 1 Non-Secure Communication Services, page 3 Secure Communication Services, page 5 Network-Related Communication Services, page 12 Communication
SECURE Gateway v4.7. TLS configuration guide
 SECURE Email Gateway v4.7 TLS configuration guide November 2017 Copyright Published by Clearswift Ltd. 1995 2017 Clearswift Ltd. All rights reserved. The materials contained herein are the sole property
SECURE Email Gateway v4.7 TLS configuration guide November 2017 Copyright Published by Clearswift Ltd. 1995 2017 Clearswift Ltd. All rights reserved. The materials contained herein are the sole property
Getting Started with Soonr
 WWW.SOONR.COM Getting Started with Soonr A Quick Start Guide for New Users Soonr Inc. 12/19/2012 Revision 1.1 Copyright 2012, Soonr Inc., all rights reserved. Table of Contents 1 How Soonr Workplace Works...
WWW.SOONR.COM Getting Started with Soonr A Quick Start Guide for New Users Soonr Inc. 12/19/2012 Revision 1.1 Copyright 2012, Soonr Inc., all rights reserved. Table of Contents 1 How Soonr Workplace Works...
SONOTON storage server
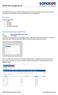 The SONOTON storage server offers different protocols which all use SSL secured communications. All protocols will work with the login details given to you by SONOTON. Overview: Protocols supported: HTTPS
The SONOTON storage server offers different protocols which all use SSL secured communications. All protocols will work with the login details given to you by SONOTON. Overview: Protocols supported: HTTPS
Linux Network Administration
 Secure Remote Connections with OpenSSH Objective At the conclusion of this module, the student will be able to: Configure the ssh daemon start, stop, and restart sshd 17 January 2005 NETW 111 - SSH 2 SSH
Secure Remote Connections with OpenSSH Objective At the conclusion of this module, the student will be able to: Configure the ssh daemon start, stop, and restart sshd 17 January 2005 NETW 111 - SSH 2 SSH
VSP16. Venafi Security Professional 16 Course 04 April 2016
 VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
Kenna Platform Security. A technical overview of the comprehensive security measures Kenna uses to protect your data
 Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Best Practices for Security Certificates w/ Connect
 Application Note AN17038 MT AppNote 17038 (AN 17038) September 2017 Best Practices for Security Certificates w/ Connect Description: This Application Note describes the process and best practices for using
Application Note AN17038 MT AppNote 17038 (AN 17038) September 2017 Best Practices for Security Certificates w/ Connect Description: This Application Note describes the process and best practices for using
Authentication in real world: Kerberos, SSH and SSL. Zheng Ma Apr 19, 2005
 Authentication in real world: Kerberos, SSH and SSL Zheng Ma Apr 19, 2005 Where are we? After learning all the foundation of modern cryptography, we are ready to see some real world applications based
Authentication in real world: Kerberos, SSH and SSL Zheng Ma Apr 19, 2005 Where are we? After learning all the foundation of modern cryptography, we are ready to see some real world applications based
Securing ArcGIS Services
 Federal GIS Conference 2014 February 10 11, 2014 Washington DC Securing ArcGIS Services James Cardona Agenda Security in the context of ArcGIS for Server Background concepts Access Securing web services
Federal GIS Conference 2014 February 10 11, 2014 Washington DC Securing ArcGIS Services James Cardona Agenda Security in the context of ArcGIS for Server Background concepts Access Securing web services
Key File Generation. November 14, NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171
 Key File Generation NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171 Table of Contents Introduction... 2 PuTTY Installation... 2 Key Generation... 7 Configuring PuTTY
Key File Generation NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171 Table of Contents Introduction... 2 PuTTY Installation... 2 Key Generation... 7 Configuring PuTTY
CyberLynk FTP Service Functional Description
 CyberLynk FTP Service Functional Description - November 3, 2005 - Version 2.7 Presented by CyberLynk Network 10125 S. 52 nd Street Franklin, WI 53132 P: 414.858.9335 - F: 414.858.9336 www.cyberlynk.net
CyberLynk FTP Service Functional Description - November 3, 2005 - Version 2.7 Presented by CyberLynk Network 10125 S. 52 nd Street Franklin, WI 53132 P: 414.858.9335 - F: 414.858.9336 www.cyberlynk.net
Cloud FastPath: Highly Secure Data Transfer
 Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
Message Networking 5.2 Administration print guide
 Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Mitel MiVoice Connect Security Certificates
 Application Note - AN16036 MT App Note 16036 (AN 16036) May, 2018 Mitel MiVoice Connect Security Certificates Description: This Application Note describes the use of security certificates in Mitel MiVoice
Application Note - AN16036 MT App Note 16036 (AN 16036) May, 2018 Mitel MiVoice Connect Security Certificates Description: This Application Note describes the use of security certificates in Mitel MiVoice
Virtual CD TS 1 Introduction... 3
 Table of Contents Table of Contents Virtual CD TS 1 Introduction... 3 Document Conventions...... 4 What Virtual CD TS Can Do for You...... 5 New Features in Version 10...... 6 Virtual CD TS Licensing......
Table of Contents Table of Contents Virtual CD TS 1 Introduction... 3 Document Conventions...... 4 What Virtual CD TS Can Do for You...... 5 New Features in Version 10...... 6 Virtual CD TS Licensing......
The Invisible Threat of Modern Malware Lee Gitzes, CISSP Comm Solutions Company
 The Invisible Threat of Modern Malware Lee Gitzes, CISSP Comm Solutions Company November 12, 2014 Malware s Evolution Why the change? Hacking is profitable! Breaches and Malware are Projected to Cost $491
The Invisible Threat of Modern Malware Lee Gitzes, CISSP Comm Solutions Company November 12, 2014 Malware s Evolution Why the change? Hacking is profitable! Breaches and Malware are Projected to Cost $491
The Cisco HCM-F Administrative Interface
 CHAPTER 5 This chapter contains information on the following topics: Overview of Cisco HCM-F Administrative Interface, page 5-1 Browser Support, page 5-2 Login and Logout, page 5-4 Online Help, page 5-5
CHAPTER 5 This chapter contains information on the following topics: Overview of Cisco HCM-F Administrative Interface, page 5-1 Browser Support, page 5-2 Login and Logout, page 5-4 Online Help, page 5-5
LevelOne. User Manual. WAP Mbps PoE Wireless AP V3.0.0
 LevelOne WAP-0005 108Mbps PoE Wireless AP User Manual V3.0.0 i TABLE OF CONTENTS CHAPTER 1 INTRODUCTION... 1 FIGURE 1: WIRELESS ACCESS POINT... 1 FEATURES OF YOUR WIRELESS ACCESS POINT... 1 Security Features...
LevelOne WAP-0005 108Mbps PoE Wireless AP User Manual V3.0.0 i TABLE OF CONTENTS CHAPTER 1 INTRODUCTION... 1 FIGURE 1: WIRELESS ACCESS POINT... 1 FEATURES OF YOUR WIRELESS ACCESS POINT... 1 Security Features...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
NAMI Affiliate Profile Center Contact Manual
 NAMI Affiliate Profile Center Contact Manual Standards of Excellence/Center for Excellence November 2013 Table of Contents Chapter Page I. NAMI Affiliate Profile Center Contact Training Timetable 3 II.
NAMI Affiliate Profile Center Contact Manual Standards of Excellence/Center for Excellence November 2013 Table of Contents Chapter Page I. NAMI Affiliate Profile Center Contact Training Timetable 3 II.
Overview of SSL/TLS. Luke Anderson. 12 th May University Of Sydney.
 Overview of SSL/TLS Luke Anderson luke@lukeanderson.com.au 12 th May 2017 University Of Sydney Overview 1. Introduction 1.1 Raw HTTP 1.2 Introducing SSL/TLS 2. Certificates 3. Attacks Introduction Raw
Overview of SSL/TLS Luke Anderson luke@lukeanderson.com.au 12 th May 2017 University Of Sydney Overview 1. Introduction 1.1 Raw HTTP 1.2 Introducing SSL/TLS 2. Certificates 3. Attacks Introduction Raw
Xton Access Manager GETTING STARTED GUIDE
 Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
User Authentication Principles and Methods
 User Authentication Principles and Methods David Groep, NIKHEF User Authentication - Principles and Methods 1 Principles and Methods Authorization factors Cryptographic methods Authentication for login
User Authentication Principles and Methods David Groep, NIKHEF User Authentication - Principles and Methods 1 Principles and Methods Authorization factors Cryptographic methods Authentication for login
Quick Reference Guide. Online Courier: File Transfer Protocol (FTP) Signing On. Using FTP Pickup
 Quick Reference Guide Online Courier: File Transfer Protocol (FTP) With SunTrust Online Courier, you can have reports and files delivered to you using a File Transfer Protocol (FTP) connection. There are
Quick Reference Guide Online Courier: File Transfer Protocol (FTP) With SunTrust Online Courier, you can have reports and files delivered to you using a File Transfer Protocol (FTP) connection. There are
Sichere Software vom Java-Entwickler
 Sichere Software vom Java-Entwickler Dominik Schadow Java Forum Stuttgart 05.07.2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART WIEN We can no longer
Sichere Software vom Java-Entwickler Dominik Schadow Java Forum Stuttgart 05.07.2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART WIEN We can no longer
Securing Internet Communication: TLS
 Securing Internet Communication: TLS CS 161: Computer Security Prof. David Wagner March 11, 2016 Today s Lecture Applying crypto technology in practice Two simple abstractions cover 80% of the use cases
Securing Internet Communication: TLS CS 161: Computer Security Prof. David Wagner March 11, 2016 Today s Lecture Applying crypto technology in practice Two simple abstractions cover 80% of the use cases
TELNET is short for Terminal Network Enables the establishment of a connection to a remote system, so that the local terminal appears to be the
 Telnet/SSH TELNET is short for Terminal Network Enables the establishment of a connection to a remote system, so that the local terminal appears to be the terminal at the remote location. Usually establishes
Telnet/SSH TELNET is short for Terminal Network Enables the establishment of a connection to a remote system, so that the local terminal appears to be the terminal at the remote location. Usually establishes
Are You Avoiding These Top 10 File Transfer Risks?
 Are You Avoiding These Top 10 File Transfer Risks? 1. 2. 3. 4. Today s Agenda Introduction 10 Common File Transfer Risks Brief GoAnywhere MFT Overview Question & Answer HelpSystems Corporate Overview.
Are You Avoiding These Top 10 File Transfer Risks? 1. 2. 3. 4. Today s Agenda Introduction 10 Common File Transfer Risks Brief GoAnywhere MFT Overview Question & Answer HelpSystems Corporate Overview.
H O W T O I N S T A L L A N S S L C E R T I F I C A T E V I A C P A N E L
 H O W T O I N S T A L L A N S S L C E R T I F I C A T E V I A C P A N E L A R E S O U R C E F R O M M A K E M E B A I T. C O M B Y R A K T I M D U T T A How to Activate & Install an SSL Certificate in
H O W T O I N S T A L L A N S S L C E R T I F I C A T E V I A C P A N E L A R E S O U R C E F R O M M A K E M E B A I T. C O M B Y R A K T I M D U T T A How to Activate & Install an SSL Certificate in
Cryptography Application : SSH. Cyber Security & Network Security March, 2017 Dhaka, Bangladesh
 Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
Sentry Power Manager (SPM) Software Security
 Sentry Power Manager (SPM) Software Security Purpose This technical note is a detailed review of the security areas of the SPM enterprise software product, version 6.0 and greater, and provides a brief
Sentry Power Manager (SPM) Software Security Purpose This technical note is a detailed review of the security areas of the SPM enterprise software product, version 6.0 and greater, and provides a brief
Getting Started. Opening TM Control Panel. TM Control Panel User Guide Getting Started 1
 TM Control Panel User Guide Getting Started 1 Getting Started Opening TM Control Panel To open TM Control Panel (CP), perform the following steps: 1 In the browser address field, type https://cp.netmyne.net.
TM Control Panel User Guide Getting Started 1 Getting Started Opening TM Control Panel To open TM Control Panel (CP), perform the following steps: 1 In the browser address field, type https://cp.netmyne.net.
User Guide. Version 3.0
 User Guide Version 3.0 CONTENTS CHAPTER 1 - INTRODUCTION...3 SYSTEM REQUIREMENTS...3 PROFESSIONAL LICENSE...3 CHAPTER 2 - ACTIVE DIRECTORY INTEGRATION...4 HOW IT WORKS...4 ACTIVE DIRECTORY REQUIREMENTS...4
User Guide Version 3.0 CONTENTS CHAPTER 1 - INTRODUCTION...3 SYSTEM REQUIREMENTS...3 PROFESSIONAL LICENSE...3 CHAPTER 2 - ACTIVE DIRECTORY INTEGRATION...4 HOW IT WORKS...4 ACTIVE DIRECTORY REQUIREMENTS...4
Area Access Manager User Guide
 Area Access Manager User Guide Area Access Manager User Guide Table of Contents Chapter 1: Introduction...9 Conventions Used in this Documentation... 9 Getting Started... 10 Licensing Requirements...
Area Access Manager User Guide Area Access Manager User Guide Table of Contents Chapter 1: Introduction...9 Conventions Used in this Documentation... 9 Getting Started... 10 Licensing Requirements...
Ubiquity Server Manual
 Ubiquity Server Manual Compatible with version 9.0 Introduction Ubiquity is the ASEM software solution for remote access and remote assistance on Industrial PCs and operator panels based on Windows operating
Ubiquity Server Manual Compatible with version 9.0 Introduction Ubiquity is the ASEM software solution for remote access and remote assistance on Industrial PCs and operator panels based on Windows operating
CLEO VLTrader Made Simple Guide
 CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
SBCC Web File System - Xythos
 Table of Contents Table of Contents...1 Purpose...1 Login Procedure...1 Creating and Sharing a Web Folder for MAT153...2 Dreamweaver Remote Info...4 I Forgot My Pipeline Credentials...6 Purpose This purpose
Table of Contents Table of Contents...1 Purpose...1 Login Procedure...1 Creating and Sharing a Web Folder for MAT153...2 Dreamweaver Remote Info...4 I Forgot My Pipeline Credentials...6 Purpose This purpose
Vault. Vault. End User Guide END USER GUIDE. L o r e. (For Standard, Professional & Enterprise Editions)
 L o r e L END USER GUIDE (For Standard, Professional & Enterprise Editions) Table of contents 1. Introduction 2. Important terms 3. Sign up instructions 4. Basic settings Initiate sharing Configure two-factor
L o r e L END USER GUIDE (For Standard, Professional & Enterprise Editions) Table of contents 1. Introduction 2. Important terms 3. Sign up instructions 4. Basic settings Initiate sharing Configure two-factor
Adobe Marketing Cloud Using FTP and sftp with the Adobe Marketing Cloud
 Adobe Marketing Using FTP and sftp with the Adobe Marketing Contents Using FTP and sftp with the Adobe Marketing...3 Setting Up FTP Accounts Hosted by Adobe...3 Classifications...3 Data Sources...4 Data
Adobe Marketing Using FTP and sftp with the Adobe Marketing Contents Using FTP and sftp with the Adobe Marketing...3 Setting Up FTP Accounts Hosted by Adobe...3 Classifications...3 Data Sources...4 Data
Business Insights Dashboard
 Business Insights Dashboard Sage 500 ERP 2000-2013 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product and service names mentioned herein are registered trademarks or trademarks
Business Insights Dashboard Sage 500 ERP 2000-2013 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product and service names mentioned herein are registered trademarks or trademarks
Outline Definition of Dreamweaver Site... 1 Setup of a Faculty/Staff Website... 2
 Outline Definition of Dreamweaver Site... 1 Setup of a Faculty/Staff Website... 2 Local Info... 2 Remote Server Setup... 3 Test your connection... 4 Your web address... 4 Setup of a Departmental Website...
Outline Definition of Dreamweaver Site... 1 Setup of a Faculty/Staff Website... 2 Local Info... 2 Remote Server Setup... 3 Test your connection... 4 Your web address... 4 Setup of a Departmental Website...
Installation guide for Choic Multi User Edition
 Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Internet Script Editor
 ISE Application, page 1 ISE Functionality, page 1 ISE Requirements, page 2 TLS Requirements for ISE, page 2 ISE Installation and Upgrades, page 5 Troubleshooting Tools for, page 7 ISE Application You can
ISE Application, page 1 ISE Functionality, page 1 ISE Requirements, page 2 TLS Requirements for ISE, page 2 ISE Installation and Upgrades, page 5 Troubleshooting Tools for, page 7 ISE Application You can
X-Payments:FAQ. X-Payments user manual
 X-Payments:FAQ X-Payments user manual 1. X-Payments:General information How It Works Key features 2. What's New What's New in X-Payments 3.1 What's New in X-Payments 3.0 3. System requirements System requirements
X-Payments:FAQ X-Payments user manual 1. X-Payments:General information How It Works Key features 2. What's New What's New in X-Payments 3.1 What's New in X-Payments 3.0 3. System requirements System requirements
SECURITY STORY WE NEVER SEE, TOUCH NOR HOLD YOUR DATA
 SECURITY STORY WE NEVER SEE, TOUCH NOR HOLD YOUR DATA CTO Office www.digi.me another Engineering Briefing digi.me keeping your data secure at all times ALL YOUR DATA IN ONE PLACE TO SHARE WITH PEOPLE WHO
SECURITY STORY WE NEVER SEE, TOUCH NOR HOLD YOUR DATA CTO Office www.digi.me another Engineering Briefing digi.me keeping your data secure at all times ALL YOUR DATA IN ONE PLACE TO SHARE WITH PEOPLE WHO
System Administration
 Most of SocialMiner system administration is performed using the panel. This section describes the parts of the panel as well as other administrative procedures including backup and restore, managing certificates,
Most of SocialMiner system administration is performed using the panel. This section describes the parts of the panel as well as other administrative procedures including backup and restore, managing certificates,
Configuring SSH and Telnet
 6 CHAPTER This chapter describes how to configure Secure Shell Protocol (SSH) and Telnet on Cisco NX-OS devices. This chapter includes the following sections: Information About SSH and Telnet, page 6-1
6 CHAPTER This chapter describes how to configure Secure Shell Protocol (SSH) and Telnet on Cisco NX-OS devices. This chapter includes the following sections: Information About SSH and Telnet, page 6-1
How to Stay Safe on Public Wi-Fi Networks
 How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 24 April 16, 2012 CPSC 467b, Lecture 24 1/33 Kerberos Secure Shell (SSH) Transport Layer Security (TLS) Digital Rights Management
CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 24 April 16, 2012 CPSC 467b, Lecture 24 1/33 Kerberos Secure Shell (SSH) Transport Layer Security (TLS) Digital Rights Management
0. Introduction On-demand. Manual Backups Full Backup Custom Backup Store Your Data Only Exclude Folders.
 Backup & Restore 0. Introduction..2 1. On-demand. Manual Backups..3 1.1 Full Backup...3 1.2 Custom Backup 5 1.2.1 Store Your Data Only...5 1.2.2 Exclude Folders.6 1.3 Restore Your Backup..7 2. On Schedule.
Backup & Restore 0. Introduction..2 1. On-demand. Manual Backups..3 1.1 Full Backup...3 1.2 Custom Backup 5 1.2.1 Store Your Data Only...5 1.2.2 Exclude Folders.6 1.3 Restore Your Backup..7 2. On Schedule.
Architecture. Steven M. Bellovin October 31,
 Architecture Steven M. Bellovin October 31, 2016 1 Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache
Architecture Steven M. Bellovin October 31, 2016 1 Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache
Niagara AX Hardening Guide. Tips to Secure a Niagara AX System
 Tips to Secure a Niagara AX System July 03 Table of Contents Introduction... 3 Passwords... 3 Change the Default Platform Credentials... 4 Use Strong Passwords... 5 Enable the Account Lockout Feature...
Tips to Secure a Niagara AX System July 03 Table of Contents Introduction... 3 Passwords... 3 Change the Default Platform Credentials... 4 Use Strong Passwords... 5 Enable the Account Lockout Feature...
