/****************************************************************************\ DAS Release for Solaris, Linux, and Windows
|
|
|
- Dwain Wheeler
- 5 years ago
- Views:
Transcription
1 /****************************************************************************\ DAS Release for Solaris, Linux, and Windows Copyright Information Security Corp. All rights reserved. This document was last modified on: 14 December 2012 \****************************************************************************/ 1 Version New Features and Operational Changes Added support for processes acting on behalf of authorized entities with proxy authenticators Added proxy ticket and signature audit trails (disabled by default) Check membership service can now be independently enabled Removed path validation and authenticator configuration from New CoI page; default settings are no path validation and no authenticator Updated management API to support proxy authenticators Updated the sample program that illustrates use of the management API (das/sample/dasmanagementsample.java) Updated the default XML configuration file (das/conf/das.xml): o added a proxy-authenticators element (with attributes requireall and enabled) to the coi element o added proxy elements to the audit trail section Updated the configuration DTD file (das/conf/das.dtd) Capabilities section renamed Protocols on New CoI and Edit CoI pages 1.2 Installation This DAS release is distributed as a compressed tar or zip archive whose name indicates the specific target platform on which the package is to be installed: das sol.tar.gz das lnx.tar.gz das win.zip Solaris/SPARC Linux x86 (Intel) Windows For full/upgrade installation instructions, please refer to the separate installation document: DAS.pdf 1.3 Known Issues LDAP authenticator using TLS client authentication At runtime, the client keystore location and password are stored in the Java system variables isc.das.ldaps.keystore and isc.das.ldaps.keystorepassword respectively. We recommend using the same client key to authenticate to all LDAP servers when multiple CoIs are set up to use different LDAP authenticators with TLS client authentication enabled. Make sure that the TLS port you specify for an LDAP authenticator actually supports the selected authentication scheme. DAS may hang if a non-tls port is specified for an LDAP authenticator configured to use TLS, or if a TLS port is specified for an LDAP authenticator configured to use anonymous binding or simple authentication.
2 2 Version History 2.1 Version AES-256, rather than AES-192, is now used for the encryption of private key material as CMS PDUs Added support for custom authenticators Added support for multiple authenticators per CoI Added service redirection functionality Added support for uploading DAS credentials in PKCS#12 format Added ECDH key derivation Added Trusted CA page to the sysadmin interface: o added management of trusted Java keystore o added subordinate CA list for path validation Added path validation for certificates in the key admin, CoI admin, and CoI manager ACLs Added an option to generate a self-signed CoI certificate with the CoI name as an othername field in its subjectaltname extension Added support for CoI key pair generation based on a self-signed certificate or certificate request CoI name no longer allows leading or trailing spaces Updated HyperSQL database library to version Updated management API to support service redirection, multiple authenticators, custom authenticators, and PKCS#12 DAS credentials upload Updated the sample program that illustrates use of the management API (das/sample/dasmanagementsample.java) Updated the default XML configuration file (das/conf/das.xml): o added an authenticators element with requireall attribute to the coi element o all authenticator elements (null-auth, ldap-auth, db-auth and local-db-auth) moved to children of the authenticators element o added custom-auth elements Updated the configuration DTD file (das/conf/das.dtd) Updated the administration site interface Removed daskg program from the distribution Removed support for CoI certificates on DSA keys Rekey operation now rewraps the encrypted HSM PIN for a CoI that uses HSM credentials 2.2 Version A Windows installer was added to the automated installation process Added support for a local database that optionally starts when DAS does Added a Local Database authenticator option to the CoI configuration settings; if enabled, a Local Database item will now appear in the Authenticator drop-down list The Database authenticator of previous versions has been renamed and is now referred to as a Network Database authenticator (to distinguish it from the local database option) Updated the sample program that illustrates use of the management API (das/sample/dasmanagementsample.java) Updated the default XML configuration file (das/conf/das.xml): o added a local-database-file element to the das section o added an optional local-db-auth element to the coi element Updated the configuration DTD file (das/conf/das.dtd)
3 2.3 Version JRE 1.5 or above is now required for proper operation of DAS (JRE 1.4.x is no longer supported) Dropped SecretAgent from the product name; it s now just DAS Updated key generation command line utility (<das home>/tools/daskg) When the DAS server shuts down, a 32-byte persistent pseudo-random seed is written to the file <das home>/bin/.entropy. Upon restart, DAS seeds its internal pseudo-random number generator (PRNG) with the contents of that file (if exists), and always pulls additional entropy from dev/random and dev/urandom. This updating of the internal state of the PRNG is performed prior to its use for asymmetric key generation. Added support for CoI certificates with the CoI name specified within a subjectaltname extension as an othername value prefixed by the OID CoI certificates generated from the administrative web interface will have both encryption and signing capabilities (key usage: key encipherment, key agreement, digital signature and nonrepudiation) rather than just encryption capability If an error occurs during the processing of a rewrap request, the server will return one of the following customized HTTP status codes (rather than simply returning 400:bad request ): o 600: system PIN/password has not been set o 601: CoI not found o 602: user is not member of the CoI o 603: path validation of user certificate failed o 604: rewrap failed o 605: invalid request (one of the required parameters is missing) o 606: unknown (any unexpected/runtime error) o 607: rewrap request disabled Added signature API to sign a supplied message digest value if user is a member of the specified CoI Added check membership API to check if a user is a member of the specified CoI. Added the ability to individually enable/disable CoI capabilities: rewrap, sign and check membership Status section on CoI page replaced by Capabilities section with rewrap, sign and check membership options Changed default key sizes for RSA to 2048 (from 1024) Updated the management API o added ability to update member certificate path validation setting o added ability to update CoI s capabilities (rewrap, sign and check membership) Updated the management API sample program file (das/sample/dasmanagementsample.java) Updated the default configuration XML file (das/conf/das.xml) o added rewrap-request, sign-request, check-membership elements to audit trail section o removed enable attribute from coi element o added capabilities attribute to coi element Updated the configuration DTD file (das/conf/das.dtd) 2.4 Version Added support for dynamic groups to the LDAP authenticator: o Added Include static groups with member attribute and Include dynamic groups with memberurl attribute options to the LDAP authenticator section of CoI page Restricted the CoI manager role to the management of a particular CoI (rather than all of them): o Enable/disable CoI
4 o Manage CoI credentials o Manage path validation settings o Manage authenticator Added a CoI admin role: o Create and remove CoIs o Administrate all CoIs and their settings o Maintain CoI manager ACLs: Added CoI Manager ACL section to the CoI page Updated the default configuration XML file (das/conf/das.xml) Updated the configuration DTD file (das/conf/das.dtd) Updated management API: o Added required parameter coiname when uploading a certificate to the CoI manager ACL using action=uploadcoimanagercert o Support uploading a certificate to the CoI admin ACL using action=uploadcoiadmincert o Rename groupattr parameter to staticgroupattr when creating a new CoI with LDAP authenticator using action=createcoildapauth Updated the management API sample program file (das/sample/dasmanagementsample.java) 2.5 Version Added support for CoI credential creation and installation: o Added a Create New Credentials option to the Create a New CoI page as well as to the CoI Add Credentials page o Added a Create New Credentials page to generate a new key pair and either a self-signed certificate or a certificate request o Added an Install button to the Credentials page to replace a pending certificate request with the corresponding certificate once it has been issued Added interface elements that allow CoI credentials to be installed in PKCS#12 format: o Added an Upload a PKCS#12 File option to the Create a New CoI and Add Credentials pages to allow credentials to be uploaded in PKCS#12 format (the correct password must be provided) o Management API: updated to support the installation of PKCS#12 credentials Added a View button to the CoI page to view all HSM-based credentials that match the CoI name Added an Export button to the CoI Credentials page to support the saving of CoI certificates and certificate requests to specified locations Log4j engine: updated from version to version Updated audit trail: o Events can be rolled over daily or stored in a single file o Updated audit trail view: if daily rollover of logs is enabled, the user can specify the dates for which log file entries will be displayed: today, last 7 days, last 30 days, or custom from/to dates Created a new Key Management Utility (das/tools/kmu.bat or.sh) o A quick start option creates DAS system, SSL server, and administrator credentials as well as the required Java keystore to jumpstart the installation/configuration process o A second option facilitates management of the Java keystore Added a new web interface for management of the CoI membership database: o Added a View Members button to the Create a New CoI and database authenticator selection pages o Added a Manage Members button to the database authenticator section on the View CoI page to manage the membership list
5 CA certificates are now ignored when user certificates are installed into the keyadmin and CoI manager ACLs. Similarly, end-user certificates are ignored when installing trusted CA certificates to be used for certificate path validation of CoI members AES-192 rather than DES3 (TDES) is now used for the encryption of private key material as CMS PDUs Updated the configuration DTD file (das/conf/das.dtd) Java system property isc.das.home must be set to the DAS installation directory when starting the webserver 2.6 Version LDAP authenticator now supports TLS with client authentication. Administrative interface now permits the creation of CoIs with HSM-based credentials. HSM PINs are encrypted using the DAS system key and stored in the configuration file. Database Server Utility (das/tools/dbserver.sh or.bat) enhancements: o manager command launches the DAS Database Manager Utility instead of the DAS Database Authenticator Manager; the Database Manager provides an interface to more easily manage user accounts while still providing access to the Database Authenticator Manager. o Removed the add/remove user commands. o Removed the change user password command. o init command no longer accepts a password parameter; it defaults to password. o stop command accepts an optional password parameter; if a password is not specified, the user will be prompted for it. Audit Trail page: added Export button to save the log to a file. Hypersonic SQL Database Engine: updated from version to version Management API: updated to permit the creation of CoIs using the database authenticator. The configuration DTD file (das/conf/das.dtd): updated. A new script (das/tools/version.sh or.bat) has been added to display the current DAS release number. 2.7 Version Supports database authenticator Supports DAS HSM Proxy Added administrative interface for sysadmins o Add, remove, and rekey DAS Credentials o Rekey CoI credentials and authenticator passwords o Manage keyadmin access control list Allows creation of CoIs using null and LDAP authenticators without binding information if DAS credentials have not been set or system password has not been entered. Allows creation of CoIs if DAS certificate has been uploaded but the private key has not Updated management interface o Changed upload DAS Credentials task Role requirement is changed from keyadmin to sysadmin private key parameter changed from prv or p7m to prvkey o Added the ability to rekey DAS (HSM) credentials with a new HSM certificate o Added the ability to upload a certificate to the keyadmin access control list o Updated sample/managementsample.java CoI name accepts a-z, A-Z, 0-9, ' ', '.', '-' and '_' characters. Updated audit trail format
6 Updated configuration file DTD (das/conf/das.dtd).
Document Access Servlet (DAS)
 Document Access Servlet (DAS) Sharing Sensitive Documents Within Communities of Interest and Facilitating Role-Based Signing Version 3.0.0 July 30, 2013 Abstract: This document explains how an easily-maintained
Document Access Servlet (DAS) Sharing Sensitive Documents Within Communities of Interest and Facilitating Role-Based Signing Version 3.0.0 July 30, 2013 Abstract: This document explains how an easily-maintained
How to Share Sensitive Documents Within Communities of Interest Using SecretAgent 5.9
 SecretAgent Document Access Servlet 1.2 or How to Share Sensitive Documents Within Communities of Interest Using SecretAgent 5.9 Version 1.2.0 Sept. 21, 2005 Abstract: This document explains how a easily-maintained
SecretAgent Document Access Servlet 1.2 or How to Share Sensitive Documents Within Communities of Interest Using SecretAgent 5.9 Version 1.2.0 Sept. 21, 2005 Abstract: This document explains how a easily-maintained
CertAgent. Administrator Guide
 CertAgent Administrator Guide Version 7.0.1 August 3, 2016 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security Corporation.
CertAgent Administrator Guide Version 7.0.1 August 3, 2016 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security Corporation.
CertAgent. Certificate Authority Guide
 CertAgent Certificate Authority Guide Version 6.0.0 December 12, 2013 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security
CertAgent Certificate Authority Guide Version 6.0.0 December 12, 2013 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security
CertAgent. Administrator Guide
 CertAgent Administrator Guide Version 7.0 July 5, 2018 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security Corporation.
CertAgent Administrator Guide Version 7.0 July 5, 2018 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security Corporation.
Entrust Connector (econnector) Venafi Trust Protection Platform
 Entrust Connector (econnector) For Venafi Trust Protection Platform Installation and Configuration Guide Version 1.0.5 DATE: 17 November 2017 VERSION: 1.0.5 Copyright 2017. All rights reserved Table of
Entrust Connector (econnector) For Venafi Trust Protection Platform Installation and Configuration Guide Version 1.0.5 DATE: 17 November 2017 VERSION: 1.0.5 Copyright 2017. All rights reserved Table of
Sophos Mobile Control Installation guide
 Sophos Mobile Control Installation guide Product version: 1.0 Document date: May 2011 Contents 1 Introduction... 3 2 The Sophos Mobile Control server... 4 3 Set up Sophos Mobile Control... 13 4 Apple Push
Sophos Mobile Control Installation guide Product version: 1.0 Document date: May 2011 Contents 1 Introduction... 3 2 The Sophos Mobile Control server... 4 3 Set up Sophos Mobile Control... 13 4 Apple Push
FIPS Security Policy UGS Teamcenter Cryptographic Module
 FIPS 140-2 Security Policy UGS Teamcenter Cryptographic Module UGS Corp 5800 Granite Parkway, Suite 600 Plano, TX 75024 USA May 18, 2007 Version 1.3 containing OpenSSL library source code This product
FIPS 140-2 Security Policy UGS Teamcenter Cryptographic Module UGS Corp 5800 Granite Parkway, Suite 600 Plano, TX 75024 USA May 18, 2007 Version 1.3 containing OpenSSL library source code This product
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
VMware AirWatch Content Gateway for Linux. VMware Workspace ONE UEM 1811 Unified Access Gateway
 VMware AirWatch Content Gateway for Linux VMware Workspace ONE UEM 1811 Unified Access Gateway You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware AirWatch Content Gateway for Linux VMware Workspace ONE UEM 1811 Unified Access Gateway You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
CertAgent. Certificate Authority Guide
 CertAgent Certificate Authority Guide Version 7.0 July 5, 2018 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security Corporation.
CertAgent Certificate Authority Guide Version 7.0 July 5, 2018 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security Corporation.
BlackBerry Enterprise Server for IBM Lotus Domino Version: 5.0. Administration Guide
 BlackBerry Enterprise Server for IBM Lotus Domino Version: 5.0 Administration Guide SWDT487521-636611-0528041049-001 Contents 1 Overview: BlackBerry Enterprise Server... 21 Getting started in your BlackBerry
BlackBerry Enterprise Server for IBM Lotus Domino Version: 5.0 Administration Guide SWDT487521-636611-0528041049-001 Contents 1 Overview: BlackBerry Enterprise Server... 21 Getting started in your BlackBerry
Odette CA Help File and User Manual
 How to Order and Install Odette Certificates For a German version of this file please follow this link. Odette CA Help File and User Manual 1 Release date 31.05.2016 Contents Preparation for Ordering an
How to Order and Install Odette Certificates For a German version of this file please follow this link. Odette CA Help File and User Manual 1 Release date 31.05.2016 Contents Preparation for Ordering an
MarkLogic Server. Security Guide. MarkLogic 9 May, Copyright 2017 MarkLogic Corporation. All rights reserved.
 Security Guide 1 MarkLogic 9 May, 2017 Last Revised: 9.0-3, September, 2017 Copyright 2017 MarkLogic Corporation. All rights reserved. Table of Contents Table of Contents Security Guide 1.0 Introduction
Security Guide 1 MarkLogic 9 May, 2017 Last Revised: 9.0-3, September, 2017 Copyright 2017 MarkLogic Corporation. All rights reserved. Table of Contents Table of Contents Security Guide 1.0 Introduction
Cisco Desktop Collaboration Experience DX650 Security Overview
 White Paper Cisco Desktop Collaboration Experience DX650 Security Overview Cisco Desktop Collaboration Experience DX650 Security Overview The Cisco Desktop Collaboration Experience DX650 (Cisco DX650)
White Paper Cisco Desktop Collaboration Experience DX650 Security Overview Cisco Desktop Collaboration Experience DX650 Security Overview The Cisco Desktop Collaboration Experience DX650 (Cisco DX650)
Digital Certificates Demystified
 Digital Certificates Demystified Ross Cooper, CISSP IBM Corporation RACF/PKI Development Poughkeepsie, NY Email: rdc@us.ibm.com August 9 th, 2012 Session 11622 Agenda Cryptography What are Digital Certificates
Digital Certificates Demystified Ross Cooper, CISSP IBM Corporation RACF/PKI Development Poughkeepsie, NY Email: rdc@us.ibm.com August 9 th, 2012 Session 11622 Agenda Cryptography What are Digital Certificates
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide
 Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
Steel Belted Radius. Release Notes SBR 6.24 Build 1. Release, Build Published Document Version Build 1 May,
 Steel Belted Radius Release Notes SBR 6.24 Build 1 Release, Build Published Document Version 6.24 Build 1 May, 2017 2.0 Contents Steel-Belted Radius Release - 6.2 Release Notes... 3 System Requirements...
Steel Belted Radius Release Notes SBR 6.24 Build 1 Release, Build Published Document Version 6.24 Build 1 May, 2017 2.0 Contents Steel-Belted Radius Release - 6.2 Release Notes... 3 System Requirements...
Adding value to your MS customers
 Securing Microsoft Adding value to your MS customers Authentication - Identity Protection Hardware Security Modules DataSecure - Encryption and Control Disc Encryption Offering the broadest range of authentication,
Securing Microsoft Adding value to your MS customers Authentication - Identity Protection Hardware Security Modules DataSecure - Encryption and Control Disc Encryption Offering the broadest range of authentication,
IBM Security Access Manager Version November Advanced Access Control Configuration topics IBM
 IBM Security Access Manager Version 9.0.2 November 2016 Advanced Access Control Configuration topics IBM IBM Security Access Manager Version 9.0.2 November 2016 Advanced Access Control Configuration topics
IBM Security Access Manager Version 9.0.2 November 2016 Advanced Access Control Configuration topics IBM IBM Security Access Manager Version 9.0.2 November 2016 Advanced Access Control Configuration topics
Steel-Belted RADIUS. Release Notes SBR 6.25-R R1 August, Release, Build Published Document Version
 3 Steel-Belted RADIUS s SBR 6.25-R1 Release, Build Published Document Version 6.25-R1 August, 2018 1.0 Pulse Secure, LLC 2700 Zanker Road, Suite 200 San Jose, CA 95134 https://www.pulsesecure.net. Pulse
3 Steel-Belted RADIUS s SBR 6.25-R1 Release, Build Published Document Version 6.25-R1 August, 2018 1.0 Pulse Secure, LLC 2700 Zanker Road, Suite 200 San Jose, CA 95134 https://www.pulsesecure.net. Pulse
BusinessObjects Enterprise XI Release 1 and Release 2
 BusinessObjects Enterprise XI Release 1 and Release 2 Overview Contents This document provides information and instructions for setting up Lightweight Directory Access Protocol (LDAP) authentication in
BusinessObjects Enterprise XI Release 1 and Release 2 Overview Contents This document provides information and instructions for setting up Lightweight Directory Access Protocol (LDAP) authentication in
IBM Security Access Manager Version May Advanced Access Control Configuration topics IBM
 IBM Security Access Manager Version 9.0.3 May 2017 Advanced Access Control Configuration topics IBM IBM Security Access Manager Version 9.0.3 May 2017 Advanced Access Control Configuration topics IBM
IBM Security Access Manager Version 9.0.3 May 2017 Advanced Access Control Configuration topics IBM IBM Security Access Manager Version 9.0.3 May 2017 Advanced Access Control Configuration topics IBM
Security context. Technology. Solution highlights
 Code42 CrashPlan Security Code42 CrashPlan provides continuous, automatic desktop and laptop backup. Our layered approach to security exceeds industry best practices and fulfills the enterprise need for
Code42 CrashPlan Security Code42 CrashPlan provides continuous, automatic desktop and laptop backup. Our layered approach to security exceeds industry best practices and fulfills the enterprise need for
Cloud Access Manager Configuration Guide
 Cloud Access Manager 8.1.3 Configuration Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
Cloud Access Manager 8.1.3 Configuration Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
ENTRUST CONNECTOR Installation and Configuration Guide Version April 21, 2017
 ENTRUST CONNECTOR Installation and Configuration Guide Version 0.5.1 April 21, 2017 2017 CygnaCom Solutions, Inc. All rights reserved. Contents What is Entrust Connector... 4 Installation... 5 Prerequisites...
ENTRUST CONNECTOR Installation and Configuration Guide Version 0.5.1 April 21, 2017 2017 CygnaCom Solutions, Inc. All rights reserved. Contents What is Entrust Connector... 4 Installation... 5 Prerequisites...
Certificate Management in Cisco ISE-PIC
 A certificate is an electronic document that identifies an individual, a server, a company, or other entity and associates that entity with a public key. Public Key Infrastructure (PKI) is a cryptographic
A certificate is an electronic document that identifies an individual, a server, a company, or other entity and associates that entity with a public key. Public Key Infrastructure (PKI) is a cryptographic
ArcGIS Server and Portal for ArcGIS An Introduction to Security
 ArcGIS Server and Portal for ArcGIS An Introduction to Security Jeff Smith & Derek Law July 21, 2015 Agenda Strongly Recommend: Knowledge of ArcGIS Server and Portal for ArcGIS Security in the context
ArcGIS Server and Portal for ArcGIS An Introduction to Security Jeff Smith & Derek Law July 21, 2015 Agenda Strongly Recommend: Knowledge of ArcGIS Server and Portal for ArcGIS Security in the context
Policy Manager for IBM WebSphere DataPower 7.2: Configuration Guide
 Policy Manager for IBM WebSphere DataPower 7.2: Configuration Guide Policy Manager for IBM WebSphere DataPower Configuration Guide SOAPMDP_Config_7.2.0 Copyright Copyright 2015 SOA Software, Inc. All rights
Policy Manager for IBM WebSphere DataPower 7.2: Configuration Guide Policy Manager for IBM WebSphere DataPower Configuration Guide SOAPMDP_Config_7.2.0 Copyright Copyright 2015 SOA Software, Inc. All rights
Manage Certificates. Certificates Overview
 Certificates Overview, page 1 Show Certificates, page 3 Download Certificates, page 4 Install Intermediate Certificates, page 4 Delete a Trust Certificate, page 5 Regenerate a Certificate, page 6 Upload
Certificates Overview, page 1 Show Certificates, page 3 Download Certificates, page 4 Install Intermediate Certificates, page 4 Delete a Trust Certificate, page 5 Regenerate a Certificate, page 6 Upload
Alliance Key Manager AKM for AWS Quick Start Guide. Software version: Documentation version:
 Alliance Key Manager AKM for AWS Quick Start Guide Software version: 4.0.0 Documentation version: 4.0.0.002 Townsend Security www.townsendsecurity.com 800.357.1019 +1 360.359.4400 Alliance Key Manager
Alliance Key Manager AKM for AWS Quick Start Guide Software version: 4.0.0 Documentation version: 4.0.0.002 Townsend Security www.townsendsecurity.com 800.357.1019 +1 360.359.4400 Alliance Key Manager
Venafi Server Agent Agent Overview
 Venafi Server Agent Agent Overview Venafi Server Agent Agent Intro Agent Architecture Agent Grouping Agent Prerequisites Agent Registration Process What is Venafi Agent? The Venafi Agent is a client/server
Venafi Server Agent Agent Overview Venafi Server Agent Agent Intro Agent Architecture Agent Grouping Agent Prerequisites Agent Registration Process What is Venafi Agent? The Venafi Agent is a client/server
User s Guide. PolicyAgent and Key Recovery for SecretAgent 5.9 and SpyProof! 1.3
 User s Guide PolicyAgent and Key Recovery for SecretAgent 5.9 and SpyProof! 1.3 Information in this document is subject to change without notice and does not represent a commitment on the part of Information
User s Guide PolicyAgent and Key Recovery for SecretAgent 5.9 and SpyProof! 1.3 Information in this document is subject to change without notice and does not represent a commitment on the part of Information
PKI Knowledge Dissemination Program. PKI Standards. Dr. Balaji Rajendran Centre for Development of Advanced Computing (C-DAC) Bangalore
 PKI Standards Dr. Balaji Rajendran Centre for Development of Advanced Computing (C-DAC) Bangalore Under the Aegis of Controller of Certifying Authorities (CCA) Government of India 1 PKCS Why PKCS? Even
PKI Standards Dr. Balaji Rajendran Centre for Development of Advanced Computing (C-DAC) Bangalore Under the Aegis of Controller of Certifying Authorities (CCA) Government of India 1 PKCS Why PKCS? Even
AirWatch Mobile Device Management
 RSA Ready Implementation Guide for 3rd Party PKI Applications Last Modified: November 26 th, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description
RSA Ready Implementation Guide for 3rd Party PKI Applications Last Modified: November 26 th, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description
Securing ArcGIS Services
 Federal GIS Conference 2014 February 10 11, 2014 Washington DC Securing ArcGIS Services James Cardona Agenda Security in the context of ArcGIS for Server Background concepts Access Securing web services
Federal GIS Conference 2014 February 10 11, 2014 Washington DC Securing ArcGIS Services James Cardona Agenda Security in the context of ArcGIS for Server Background concepts Access Securing web services
Contents. Notices Terms and conditions for product documentation.. 45 Trademarks Index iii
 Overview IBM ii Overview Contents Product overview........... 1 What's new in this release.......... 1 Supported languages........... 3 Features overview............ 3 Key serving.............. 4 Encryption-enabled
Overview IBM ii Overview Contents Product overview........... 1 What's new in this release.......... 1 Supported languages........... 3 Features overview............ 3 Key serving.............. 4 Encryption-enabled
ADFS Setup (SAML Authentication)
 ADFS Setup (SAML Authentication) Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval
ADFS Setup (SAML Authentication) Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval
SAML-Based SSO Configuration
 Prerequisites, page 1 SAML SSO Configuration Task Flow, page 5 Reconfigure OpenAM SSO to SAML SSO Following an Upgrade, page 9 SAML SSO Deployment Interactions and Restrictions, page 9 Prerequisites NTP
Prerequisites, page 1 SAML SSO Configuration Task Flow, page 5 Reconfigure OpenAM SSO to SAML SSO Following an Upgrade, page 9 SAML SSO Deployment Interactions and Restrictions, page 9 Prerequisites NTP
VMware AirWatch Integration with RSA PKI Guide
 VMware AirWatch Integration with RSA PKI Guide For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
VMware AirWatch Integration with RSA PKI Guide For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
ELIMINATE SECURITY BLIND SPOTS WITH THE VENAFI AGENT
 ELIMINATE SECURITY BLIND SPOTS WITH THE VENAFI AGENT less discovery can t find all keys and certificates Key and certificate management is no longer just an IT function. So it cannot be treated the same
ELIMINATE SECURITY BLIND SPOTS WITH THE VENAFI AGENT less discovery can t find all keys and certificates Key and certificate management is no longer just an IT function. So it cannot be treated the same
FUSION REGISTRY COMMUNITY EDITION SETUP GUIDE VERSION 9. Setup Guide. This guide explains how to install and configure the Fusion Registry.
 FUSION REGISTRY COMMUNITY EDITION VERSION 9 Setup Guide This guide explains how to install and configure the Fusion Registry. FUSION REGISTRY COMMUNITY EDITION SETUP GUIDE Fusion Registry: 9.2.x Document
FUSION REGISTRY COMMUNITY EDITION VERSION 9 Setup Guide This guide explains how to install and configure the Fusion Registry. FUSION REGISTRY COMMUNITY EDITION SETUP GUIDE Fusion Registry: 9.2.x Document
SOA Software Policy Manager Agent v6.1 for WebSphere Application Server Installation Guide
 SOA Software Policy Manager Agent v6.1 for WebSphere Application Server Installation Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software,
SOA Software Policy Manager Agent v6.1 for WebSphere Application Server Installation Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software,
User s Guide. PolicyAgent and Key Recovery for SecretAgent 5.8 and SpyProof! 1.2
 User s Guide PolicyAgent and Key Recovery for SecretAgent 5.8 and SpyProof! 1.2 Information in this document is subject to change without notice and does not represent a commitment on the part of Information
User s Guide PolicyAgent and Key Recovery for SecretAgent 5.8 and SpyProof! 1.2 Information in this document is subject to change without notice and does not represent a commitment on the part of Information
BlackBerry Enterprise Server Express for Microsoft Exchange
 BlackBerry Enterprise Server Express for Microsoft Exchange Version: 5.0 Service Pack: 3 Feature and Technical Overview Published: 2011-04-11 SWDT305802-1526466-0411010819-001 Contents 1 Overview: BlackBerry
BlackBerry Enterprise Server Express for Microsoft Exchange Version: 5.0 Service Pack: 3 Feature and Technical Overview Published: 2011-04-11 SWDT305802-1526466-0411010819-001 Contents 1 Overview: BlackBerry
IBM i Version 7.2. Security Digital Certificate Manager IBM
 IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
CLEO VLTrader Made Simple Guide
 CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
VMware Identity Manager Connector Installation and Configuration (Legacy Mode)
 VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
CertAgent. Installation, Configuration, and Management Guide
 CertAgent Installation, Configuration, and Management Guide Version 6.0.0 April 2, 2013 Information in this document is subject to change without notice and does not represent a commitment on the part
CertAgent Installation, Configuration, and Management Guide Version 6.0.0 April 2, 2013 Information in this document is subject to change without notice and does not represent a commitment on the part
Certificate Properties File Realm
 Certificate Properties File Realm {scrollbar} This realm type allows you to configure Web applications to authenticate users against it. To get to that point, you will need to first configure Geronimo
Certificate Properties File Realm {scrollbar} This realm type allows you to configure Web applications to authenticate users against it. To get to that point, you will need to first configure Geronimo
Venafi HSM Safenet HSM Integration Guide
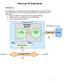
 This document provides a step by step guide for integrating SafeNet s Luna SA 4 Hardware Security Module (HSM) with Venafi Encryption Director 6. Overview Venafi Encryption Director stores sensitive information
This document provides a step by step guide for integrating SafeNet s Luna SA 4 Hardware Security Module (HSM) with Venafi Encryption Director 6. Overview Venafi Encryption Director stores sensitive information
PGP Command Line Version 10.0 Release Notes
 PGP Command Line Version 10.0 Release Notes Thank you for using this PGP Corporation product. These Release Notes contain important information regarding this release of PGP Command Line Software Development
PGP Command Line Version 10.0 Release Notes Thank you for using this PGP Corporation product. These Release Notes contain important information regarding this release of PGP Command Line Software Development
This help covers the ordering, download and installation procedure for Odette Digital Certificates.
 This help covers the ordering, download and installation procedure for Odette Digital Certificates. Answers to Frequently Asked Questions are available online CONTENTS Preparation for Ordering an Odette
This help covers the ordering, download and installation procedure for Odette Digital Certificates. Answers to Frequently Asked Questions are available online CONTENTS Preparation for Ordering an Odette
GSI Online Credential Retrieval Requirements. Jim Basney
 GSI Online Credential Retrieval Requirements Jim Basney jbasney@ncsa.uiuc.edu http://www.ncsa.uiuc.edu/~jbasney/ Online Credential Retrieval Defined Client Server Authenticate Request Credential Verify
GSI Online Credential Retrieval Requirements Jim Basney jbasney@ncsa.uiuc.edu http://www.ncsa.uiuc.edu/~jbasney/ Online Credential Retrieval Defined Client Server Authenticate Request Credential Verify
VMware AirWatch Content Gateway Guide for Linux For Linux
 VMware AirWatch Content Gateway Guide for Linux For Linux Workspace ONE UEM v9.7 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Content Gateway Guide for Linux For Linux Workspace ONE UEM v9.7 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
IBM Systems and Technology Group
 IBM Systems and Technology Group Encryption Facility for z/os Update Steven R. Hart srhart@us.ibm.com 2013 IBM Corporation Topics Encryption Facility for z/os EF OpenPGP Support X.509 vs. OpenPGP Certificates
IBM Systems and Technology Group Encryption Facility for z/os Update Steven R. Hart srhart@us.ibm.com 2013 IBM Corporation Topics Encryption Facility for z/os EF OpenPGP Support X.509 vs. OpenPGP Certificates
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
VMware Horizon JMP Server Installation and Setup Guide. 13 DEC 2018 VMware Horizon 7 7.7
 VMware Horizon JMP Server Installation and Setup Guide 13 DEC 2018 VMware Horizon 7 7.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
VMware Horizon JMP Server Installation and Setup Guide 13 DEC 2018 VMware Horizon 7 7.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
Using the vrealize Orchestrator Operations Client. vrealize Orchestrator 7.5
 Using the vrealize Orchestrator Operations Client vrealize Orchestrator 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Using the vrealize Orchestrator Operations Client vrealize Orchestrator 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
SAML-Based SSO Configuration
 Prerequisites, page 1 SAML SSO Configuration Workflow, page 5 Reconfigure OpenAM SSO to SAML SSO After an Upgrade, page 9 Prerequisites NTP Setup In SAML SSO, Network Time Protocol (NTP) enables clock
Prerequisites, page 1 SAML SSO Configuration Workflow, page 5 Reconfigure OpenAM SSO to SAML SSO After an Upgrade, page 9 Prerequisites NTP Setup In SAML SSO, Network Time Protocol (NTP) enables clock
SSL Configuration Oracle Banking Liquidity Management Release [April] [2017]
![SSL Configuration Oracle Banking Liquidity Management Release [April] [2017] SSL Configuration Oracle Banking Liquidity Management Release [April] [2017]](/thumbs/74/70574223.jpg) SSL Configuration Oracle Banking Liquidity Management Release 12.4.0.0.0 [April] [2017] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP SSL ON ORACLE
SSL Configuration Oracle Banking Liquidity Management Release 12.4.0.0.0 [April] [2017] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP SSL ON ORACLE
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.4.0 Revision B Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
NGFW Security Management Center Release Notes 6.4.0 Revision B Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
VMware Enterprise Systems Connector Installation and Configuration. JULY 2018 VMware Identity Manager 3.2 VMware Identity Manager VMware AirWatch 9.
 VMware Enterprise Systems Connector Installation and Configuration JULY 2018 VMware Identity Manager 3.2 VMware Identity Manager VMware AirWatch 9.3 You can find the most up-to-date technical documentation
VMware Enterprise Systems Connector Installation and Configuration JULY 2018 VMware Identity Manager 3.2 VMware Identity Manager VMware AirWatch 9.3 You can find the most up-to-date technical documentation
User Guide. Version R94. English
 AuthAnvil User Guide Version R94 English March 8, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated
AuthAnvil User Guide Version R94 English March 8, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated
SOA Software Policy Manager Agent v6.1 for tc Server Application Server Installation Guide
 SOA Software Policy Manager Agent v6.1 for tc Server Application Server Installation Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software,
SOA Software Policy Manager Agent v6.1 for tc Server Application Server Installation Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software,
Contents. Configuring SSH 1
 Contents Configuring SSH 1 Overview 1 How SSH works 1 SSH authentication methods 2 SSH support for Suite B 3 FIPS compliance 3 Configuring the device as an SSH server 4 SSH server configuration task list
Contents Configuring SSH 1 Overview 1 How SSH works 1 SSH authentication methods 2 SSH support for Suite B 3 FIPS compliance 3 Configuring the device as an SSH server 4 SSH server configuration task list
How to Set Up External CA VPN Certificates
 To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
Sharing Secrets using Encryption Facility - Handson
 Sharing Secrets using Encryption Facility - Handson Lab Steven R. Hart IBM March 12, 2014 Session Number 14963 Encryption Facility for z/os Encryption Facility for z/os is a host based software solution
Sharing Secrets using Encryption Facility - Handson Lab Steven R. Hart IBM March 12, 2014 Session Number 14963 Encryption Facility for z/os Encryption Facility for z/os is a host based software solution
CA SiteMinder Federation
 CA SiteMinder Federation Partnership Federation Guide 12.52 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
CA SiteMinder Federation Partnership Federation Guide 12.52 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
Release Notes. Lavastorm Analytics Engine 6.1.3
 Release Notes Lavastorm Analytics Engine 6.1.3 Lavastorm Analytics Engine 6.1.3: Release Notes Legal notice Copyright THE CONTENTS OF THIS DOCUMENT ARE THE COPYRIGHT OF LIMITED. ALL RIGHTS RESERVED. THIS
Release Notes Lavastorm Analytics Engine 6.1.3 Lavastorm Analytics Engine 6.1.3: Release Notes Legal notice Copyright THE CONTENTS OF THIS DOCUMENT ARE THE COPYRIGHT OF LIMITED. ALL RIGHTS RESERVED. THIS
BIG-IP System: SSL Administration. Version
 BIG-IP System: SSL Administration Version 13.0.0 Table of Contents Table of Contents About SSL Administration on the BIG-IP System...7 About SSL administration on the BIG-IP system... 7 Device Certificate
BIG-IP System: SSL Administration Version 13.0.0 Table of Contents Table of Contents About SSL Administration on the BIG-IP System...7 About SSL administration on the BIG-IP system... 7 Device Certificate
Server Installation Guide
 Server Installation Guide Server Installation Guide Legal notice Copyright 2018 LAVASTORM ANALYTICS, INC. ALL RIGHTS RESERVED. THIS DOCUMENT OR PARTS HEREOF MAY NOT BE REPRODUCED OR DISTRIBUTED IN ANY
Server Installation Guide Server Installation Guide Legal notice Copyright 2018 LAVASTORM ANALYTICS, INC. ALL RIGHTS RESERVED. THIS DOCUMENT OR PARTS HEREOF MAY NOT BE REPRODUCED OR DISTRIBUTED IN ANY
Using SSL/TLS with Active Directory / LDAP
 Purpose This document describes how to install the required certificate on the for use with LDAP or Active Directory (AD) Integration in. This process is required if your LDAP / AD server has a self signed
Purpose This document describes how to install the required certificate on the for use with LDAP or Active Directory (AD) Integration in. This process is required if your LDAP / AD server has a self signed
SAML 2.0 SSO. Set up SAML 2.0 SSO. SAML 2.0 Terminology. Prerequisites
 SAML 2.0 SSO Agiloft integrates with a variety of SAML authentication providers, or Identity Providers (IdPs). SAML-based SSO is a leading method for providing federated access to multiple applications
SAML 2.0 SSO Agiloft integrates with a variety of SAML authentication providers, or Identity Providers (IdPs). SAML-based SSO is a leading method for providing federated access to multiple applications
Venafi Trust Protection Platform 18.1 Common Criteria Guidance
 Venafi Trust Protection Platform 18.1 Common Criteria Guidance Acumen Security, LLC. Document Version: 1.1 1 Table Of Contents 1 Overview... 4 1.1 Evaluation Platforms... 4 1.2 Technical Support... 4 2
Venafi Trust Protection Platform 18.1 Common Criteria Guidance Acumen Security, LLC. Document Version: 1.1 1 Table Of Contents 1 Overview... 4 1.1 Evaluation Platforms... 4 1.2 Technical Support... 4 2
Contents. Notices Terms and conditions for product documentation.. 43 Trademarks Index iii
 Overview IBM ii Overview Contents Product overview........... 1 What's new in this release.......... 1 License usage metrics........... 2 Supported languages........... 3 Features overview............
Overview IBM ii Overview Contents Product overview........... 1 What's new in this release.......... 1 License usage metrics........... 2 Supported languages........... 3 Features overview............
Certificate Enrollment- and Signing Services for the Cloud. A behind-the-scenes presentation of a successful cooperation between
 Certificate Enrollment- and Signing Services for the Cloud A behind-the-scenes presentation of a successful cooperation between Introduction Based on our experience and the request from the market we would
Certificate Enrollment- and Signing Services for the Cloud A behind-the-scenes presentation of a successful cooperation between Introduction Based on our experience and the request from the market we would
Prophet 21 Middleware Installation Guide. version 12.16
 version 12.16 Disclaimer This document is for informational purposes only and is subject to change without notice. This document and its contents, including the viewpoints, dates and functional content
version 12.16 Disclaimer This document is for informational purposes only and is subject to change without notice. This document and its contents, including the viewpoints, dates and functional content
Echidna Concepts Guide
 Salt Group Concepts Guide Version 15.1 May 2015 2015 Salt Group Proprietary Limited. All rights reserved. Information in this document is subject to change without notice. The software described in this
Salt Group Concepts Guide Version 15.1 May 2015 2015 Salt Group Proprietary Limited. All rights reserved. Information in this document is subject to change without notice. The software described in this
Security 3. NiFi Authentication. Date of Publish:
 3 Date of Publish: 2018-08-13 http://docs.hortonworks.com Contents... 3 Enabling SSL with a NiFi Certificate Authority... 5 Enabling SSL with Existing Certificates... 5 (Optional) Setting Up Identity Mapping...6
3 Date of Publish: 2018-08-13 http://docs.hortonworks.com Contents... 3 Enabling SSL with a NiFi Certificate Authority... 5 Enabling SSL with Existing Certificates... 5 (Optional) Setting Up Identity Mapping...6
BIG-IP System: SSL Administration. Version
 BIG-IP System: SSL Administration Version 13.1.0 Table of Contents Table of Contents About SSL Administration on the BIG-IP System...7 About SSL administration on the BIG-IP system... 7 Device Certificate
BIG-IP System: SSL Administration Version 13.1.0 Table of Contents Table of Contents About SSL Administration on the BIG-IP System...7 About SSL administration on the BIG-IP system... 7 Device Certificate
XenApp 5 Security Standards and Deployment Scenarios
 XenApp 5 Security Standards and Deployment Scenarios 2015-03-04 20:22:07 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents XenApp 5 Security Standards
XenApp 5 Security Standards and Deployment Scenarios 2015-03-04 20:22:07 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents XenApp 5 Security Standards
Securing U2 Soap Server
 Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Configuring the Cisco APIC-EM Settings
 Logging into the Cisco APIC-EM, page 1 Quick Tour of the APIC-EM Graphical User Interface (GUI), page 2 Configuring the Prime Infrastructure Settings, page 3 Discovery Credentials, page 4 Security, page
Logging into the Cisco APIC-EM, page 1 Quick Tour of the APIC-EM Graphical User Interface (GUI), page 2 Configuring the Prime Infrastructure Settings, page 3 Discovery Credentials, page 4 Security, page
IBM Secure Proxy. Advanced edge security for your multienterprise. Secure your network at the edge. Highlights
 IBM Secure Proxy Advanced edge security for your multienterprise data exchanges Highlights Enables trusted businessto-business transactions and data exchange Protects your brand reputation by reducing
IBM Secure Proxy Advanced edge security for your multienterprise data exchanges Highlights Enables trusted businessto-business transactions and data exchange Protects your brand reputation by reducing
Administration Guide. Lavastorm Analytics Engine 6.1.1
 Administration Guide Lavastorm Analytics Engine 6.1.1 Lavastorm Analytics Engine 6.1.1: Administration Guide Legal notice Copyright THE CONTENTS OF THIS DOCUMENT ARE THE COPYRIGHT OF LIMITED. ALL RIGHTS
Administration Guide Lavastorm Analytics Engine 6.1.1 Lavastorm Analytics Engine 6.1.1: Administration Guide Legal notice Copyright THE CONTENTS OF THIS DOCUMENT ARE THE COPYRIGHT OF LIMITED. ALL RIGHTS
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.3.4 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 5 New features on page 5
NGFW Security Management Center Release Notes 6.3.4 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 5 New features on page 5
RealPresence Access Director System Administrator s Guide
 [Type the document title] Polycom RealPresence Access Director System Administrator s Guide 2.1.0 March 2013 3725-78703-001A Polycom Document Title 1 Trademark Information POLYCOM and the names and marks
[Type the document title] Polycom RealPresence Access Director System Administrator s Guide 2.1.0 March 2013 3725-78703-001A Polycom Document Title 1 Trademark Information POLYCOM and the names and marks
IBM Security Access Manager Version January Federation Administration topics IBM
 IBM Security Access Manager Version 9.0.2.1 January 2017 Federation Administration topics IBM IBM Security Access Manager Version 9.0.2.1 January 2017 Federation Administration topics IBM ii IBM Security
IBM Security Access Manager Version 9.0.2.1 January 2017 Federation Administration topics IBM IBM Security Access Manager Version 9.0.2.1 January 2017 Federation Administration topics IBM ii IBM Security
Configure IBM Rational Synergy with 3 rd Party LDAP Server. Release
 Configure IBM Rational Synergy with 3 rd Party LDAP Server. Release 7.2.1.7 Author: Rooble Babu Madeckal March 29, 2018 This edition applies to IBM Rational Synergy version 7.2.1.7, and to all subsequent
Configure IBM Rational Synergy with 3 rd Party LDAP Server. Release 7.2.1.7 Author: Rooble Babu Madeckal March 29, 2018 This edition applies to IBM Rational Synergy version 7.2.1.7, and to all subsequent
IBM Single Sign On for Bluemix Version December Identity Bridge Configuration topics
 IBM Single Sign On for Bluemix Version 2.0 28 December 2014 Identity Bridge Configuration topics IBM Single Sign On for Bluemix Version 2.0 28 December 2014 Identity Bridge Configuration topics ii IBM
IBM Single Sign On for Bluemix Version 2.0 28 December 2014 Identity Bridge Configuration topics IBM Single Sign On for Bluemix Version 2.0 28 December 2014 Identity Bridge Configuration topics ii IBM
BlackBerry Enterprise Server for Microsoft Office 365. Version: 1.0. Administration Guide
 BlackBerry Enterprise Server for Microsoft Office 365 Version: 1.0 Administration Guide Published: 2013-01-29 SWD-20130131125552322 Contents 1 Related resources... 18 2 About BlackBerry Enterprise Server
BlackBerry Enterprise Server for Microsoft Office 365 Version: 1.0 Administration Guide Published: 2013-01-29 SWD-20130131125552322 Contents 1 Related resources... 18 2 About BlackBerry Enterprise Server
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
BlackBerry Enterprise Server Express for IBM Lotus Domino
 BlackBerry Enterprise Server Express for IBM Lotus Domino Version: 5.0 Service Pack: 3 Feature and Technical Overview Published: 2011-04-11 SWDT305802-1526466-0411011002-001 Contents 1 Overview: BlackBerry
BlackBerry Enterprise Server Express for IBM Lotus Domino Version: 5.0 Service Pack: 3 Feature and Technical Overview Published: 2011-04-11 SWDT305802-1526466-0411011002-001 Contents 1 Overview: BlackBerry
UC for Enterprise (UCE) NEC Centralized Authentication Service (NEC CAS)
 UC for Enterprise (UCE) NEC Centralized Authentication Service (NEC CAS) Installation Guide NEC NEC Corporation October 2010 NDA-30362, Revision 15 Liability Disclaimer NEC Corporation reserves the right
UC for Enterprise (UCE) NEC Centralized Authentication Service (NEC CAS) Installation Guide NEC NEC Corporation October 2010 NDA-30362, Revision 15 Liability Disclaimer NEC Corporation reserves the right
Public Key Infrastructure PKI. National Digital Certification Center Information Technology Authority Sultanate of Oman
 Public Key Infrastructure PKI National Digital Certification Center Information Technology Authority Sultanate of Oman Agenda Objectives PKI Features etrust Components Government eservices Oman National
Public Key Infrastructure PKI National Digital Certification Center Information Technology Authority Sultanate of Oman Agenda Objectives PKI Features etrust Components Government eservices Oman National
scconnect v1.x ADMINISTRATION, INSTALLATION, AND USER GUIDE
 scconnect v1.x ADMINISTRATION, INSTALLATION, AND USER GUIDE GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800)
scconnect v1.x ADMINISTRATION, INSTALLATION, AND USER GUIDE GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800)
Centralized Credential Management Servlet (CCMS) Quick Start Guide
 Centralized Credential Management Servlet (CCMS) Quick Start Guide Facilitating the Deployment of X.509 Credentials with Centralized Key Generation and PKI Management Version 3.1.1 November 5, 2014 Information
Centralized Credential Management Servlet (CCMS) Quick Start Guide Facilitating the Deployment of X.509 Credentials with Centralized Key Generation and PKI Management Version 3.1.1 November 5, 2014 Information
