CIC Library Automation Directors Security/Authentication Issues in the CIC Virtual Electronic Library March 29, 1996
|
|
|
- Johnathan Jeffrey Underwood
- 5 years ago
- Views:
Transcription
1 CIC Library Automation Directors Security/Authentication Issues in the CIC Virtual Electronic Library March 29, 1996 This document outlines the major network security and authentication issues related to the CIC Virtual Electronic Library. The content reflects informal discussions of the CIC Library Automation Directors over the past several years. It is based on a working document developed in 1994 and updated recently into this version. The document has three parts: a continuum of security needs from those library systems/services requiring the least security over the network to those requiring the most security, a discussion of some important related issues, and finally a brief overview of security in the current CIC networked environment and some general observations. A. Continuum of needs for security from lowest to highest level of security. 1. Systems open to anyone: for example, online catalogs. Some systems are designed inherently to be secure and present no licensing issues so that open, unrestricted access is the goal. Our Z39.50 online catalog servers and their interfaces are a prime example. That said, library resources are limited and it could be possible that contention for access might force a CIC site to restrict access to local clients first, the CIC or other partners sites second, and to others on a space-available basis. 2. Useful to know who is using a resource (usually does not require identification of user by name/id) for statistics or other information gathering uses: for example, ERIC or local files created by the library. Some systems/services can be made widely available with no content restrictions, but the library will want to know in general terms who the users are to justify the expenses associated with offering the systems/service. In these cases, log files of IP addresses for analysis will be sufficient and may even be kept/analyzed on only a sampling basis. 3. Best effort to limit access to authorized users for licensed information (broad categories): for example, H. W. Wilson files, Encyclopaedia Britannica These systems need to be restricted to local campus and/or authorized campuses within CIC, but the suppliers of the data and/or search engines are comfortable with moderate "best efforts" at restricting access, such as domain name restrictions. The CIC institutions need to have a way to discriminate between "true" members of the campus community and "guest" members of the campus community. For these systems, typically, access is allowed by the non-cic community only when they are in a CIC library using a public workstation. 4. Meet password requirements of remote systems: for example, OCLC First Search, block search option; RLIN Eureka; Grateful Med over the Internet. These
2 systems require each user to sign on to the remote system. Each system has its own password requirements although anyone on the campus may have access if s/he has a valid password. These systems can require restricted manual distribution of individual passwords, sharing of single passwords across campus, programming of special password servers to distribute passwords, distribution of clients with, or capable of getting, the required passwords, or programming of a gateway machine that logs user in using a script. 5. Best effort to limit access to authorized users for licensed information (restricted categories): for example, LEXIS. Some services that the libraries use require restriction based upon rather fine distinctions but still access is allowed to broad categories of users. For example, a legal database or a subscription is available to faculty and students who are not in the law school and not available for research and business functions, including campus attorneys, of the institution. 6. Limit simultaneous access: for example, OCLC First Search or RLIN Eureka gateway service. Gateway services or server software can be priced according to the number of simultaneous users. In these instances the provider may well limit the number of simultaneous connections for the CIC or a campus, but CIC may need to further manage this traffic, e.g. to guarantee one or more connections to each participating library. In this model, timing-out users can be important to assure that ports are not being held needlessly by users. 7. Identify user as eligible to perform some general activity in order to be able to take responsibility for user's actions: for example, limit telnet or from Webbrowsers from library public workstations. The CIC libraries expect to provide access to most of their services via the Internet. Many CIC libraries expect that robust full-featured kiosk versions of Web-browsers will be used as graphical interfaces for public workstations. The needs to restrict functionality to provide a secure and responsible environment and to allow users the freedom to use all the library's services from any place are in conflict. The CIC security environment must address this problem in the context of the public outreach and/or land-grant tradition of the CIC members. 8. Identify user and log activity of account in order to be able to assign responsibility for problems or for billing/charge back: for example, to charge back electronic document requesting, printing, or downloading. The CIC libraries have recognized that the cost of some services can not be carried by the libraries on behalf of their users. Services such as printing and downloading may be passed on to the user. Copyright or delivery costs may be passed on to the user. As we contract for systems where each transaction carries an individual cost, the libraries may want to track these costs for other reasons, for example to identify users who abuse the privilege of access to a system/service.
3 9. Limit access user-by-user because of restrictions related to access to data: for example, Dept. of Defense files, some STN files. Some information sources and systems have externally imposed security restrictions. Users of the system must have government security clearances (DOD) or must be recipients of grant money from a particular agency to have access to a system. 10. Limit type of access and assign update/write capabilities to restrict access to remote systems: for example connecting to production systems for purpose of daily work. The library staff will use the network to connect to local and remote library management systems to perform work. Sharing cataloging expertise across the CIC means that catalogers from one site must be able to connect securely to the database at another site. Cooperative acquisitions programs may require access to other (sensitive) internal library records. Further, our users will need to connect securely to the local system and to remote systems to renew books themselves or to find out the status or items on loan, overdue etc. 11. Limit port access to a particular user or group of users: e.g. interlibrary loan staff connections to the ILL/DR server. Library systems sometimes have special characteristics or functionality built into particular ports. An example of this is the diacritic character set capability used by catalogers. Circulation staff must always have a port ready and waiting to do their work. In these instances a specialized port must be maintained and made available only to a limited set of users. 12. Maintain and provide secure proprietary (i.e. non-tcp/ip) networks for EDI: for example, for library purchasing and transferring financial data (fines, payments etc.) Most CIC libraries are looking to speed up local routines by using X.12 and other such schemes to transmit payment and billing information within the university, to other universities, and to vendors. B. Other related needs/issues. 1. Encryption of passwords or files, authentication of passwords across the network, sending passwords over the network, authentication of files and documents sent over the network or stored on the network. Both users and objects must be authenticated over the network. In some cases, encryption must be supported. Not only must we authenticate that an object is an authentic copy but also that it came from the place it was supposed to come from. 2. One time and multiple use authentication tokens. Network security must support both kinds of user authentication, one-time tokens for high risk systems and multiple use tokens for low-risk system. 3. Software distribution and dynamic/automatic updating of clients to current version. The CIC libraries will be distributing multiple specialized software clients, like Crossfire for Beilstein or Grateful Med for MEDLINE. These clients are upgraded from time to time. The libraries need not only efficient and secure ways
4 to distribute these clients to legitimate users but also to upgrade or replace all or part of a client on the users workstation. For example, the list of Z39.50 accessible databases stored in a Z39.50 client may need to be replaced because of new sites or changes made to existing sites. 4. Number of passwords a user must have. Clearly, the fewer the passwords and userids a user must have, the more likely s/he is to remember them and to keep them in a safe place. The more passwords s/he must have, the more likely are these to be written on post-its in offices or the more likely is the user to choose insecure passwords, like the names of pets. Since the average library user will probably need a dozen or more passwords, each with its own scheme, for access to the library systems and services, other alternatives than managing all these passwords must be found. 5. Limiting access by IP address or domain name. Increasingly we have put this method into use because it is the one method we have. At the same time, the CIC community is buying their home Internet connectivity from other sources (with our encouragement) because of stressed-out modem pools. As more and more of the CIC community get non-cic domains for their home access, the CIC must figure out how to use other methods to authenticate these users so that they can use library systems and services. Even in the library, library staff are relocated due to power outages, staff vacancies, and other needs, and require access to specialized ports from different machines. 6. Library public workstations. The anonymous Web-browsers or similar interfaces on library public workstations can present a major security loophole. The major one, of course, is the possibility to send anonymous electronic mail for nefarious purposes; at the same time, there are legitimate compelling reasons (the CIC interlibrary lending/document delivery project, for one) to provide this feature. How will CIC confront this? C. CIC Environment. Currently CICNet is primarily a trusted peer network environment. IP domain checking/firewall software is the major way we limit access. Therefore the expectation is that home domains authenticate users before they are allowed to connect to remote systems. This expectation is generally respected by the libraries, but has not been codified as a guiding principle of inter-cic security. There are many sources for authenticating the members of the CIC community: , X.500, or campus directories; computer accounting files; library patron files; and campus registration or payroll files. All of these are possible sources of authentication. There is a great need to decide what databases will be used for authentication. This is a very complicated issue that must be resolved soon. All the parties with strong interests, including of course the libraries, need to be involved in the process of deciding.
5 Not so long ago, we expected CIC to move to a Kerberos-type environment. We understand that there is less agreement among the campus-level technology experts now and wonder whether CIC will have a homogeneous or heterogeneous authentication environment. How will the libraries cooperate if multiple authentication routines, for example, Kerberos and DCE, are used? Kerberos needs a number of additional features in order to be useful for CIC: expansion of the number of users is an issue, ability to use multiple servers is an issue, the ability to carry tokens across the network and cash them in at designated remote systems is another one if we are to have full functionality in a distributed computer environment. The relationship of any chosen security method to other methods must be understood. For example, library vendors may provide systems which use proprietary packages such as Novell's RSA. We must be able to integrate these into the CIC Virtual Electronic Library. For the immediate future, it seems that linking Internet node (i.e. to a range of nodes within a given domain or set of domains) to authentication is the best first phase option. At least that way, we can look at sharing databases before most of us have authentication systems on the campus networks that can travel across the CIC and to the library's vendors of systems and services. Increasingly this is not enough as more and more of our legitimate users come in from domains outside the campus. Unfortunately, the other issues outlined in this paper are also becoming more pressing on our campuses and we can't put off dealing with them much longer. Committee on Institutional Cooperation 302 E. John St. / Suite 1705 Champaign, IL (21) cic@uiuc.edu
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
InCommon Federation: Participant Operational Practices
 InCommon Federation: Participant Operational Practices Participation in the InCommon Federation ( Federation ) enables a federation participating organization ( Participant ) to use Shibboleth identity
InCommon Federation: Participant Operational Practices Participation in the InCommon Federation ( Federation ) enables a federation participating organization ( Participant ) to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Most, but not all, state associations link to the VU web site.
 1 Most, but not all, state associations link to the VU web site. The graphic above was taken from the Arizona association which is one of the biggest promoters of the VU. If you Googled virtual university
1 Most, but not all, state associations link to the VU web site. The graphic above was taken from the Arizona association which is one of the biggest promoters of the VU. If you Googled virtual university
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
1. Federation Participant Information DRAFT
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES [NOTE: This document should be considered a as MIT is still in the process of spinning up its participation in InCommon.] Participation in InCommon
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES [NOTE: This document should be considered a as MIT is still in the process of spinning up its participation in InCommon.] Participation in InCommon
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Federated Authentication for E-Infrastructures
 Federated Authentication for E-Infrastructures A growing challenge for on-line e-infrastructures is to manage an increasing number of user accounts, ensuring that accounts are only used by their intended
Federated Authentication for E-Infrastructures A growing challenge for on-line e-infrastructures is to manage an increasing number of user accounts, ensuring that accounts are only used by their intended
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: University of Toronto Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name: University of Toronto Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Federated authentication for e-infrastructures
 Federated authentication for e-infrastructures 5 September 2014 Federated Authentication for E-Infrastructures Jisc Published under the CC BY 4.0 licence creativecommons.org/licenses/by/4.0/ Contents Introduction
Federated authentication for e-infrastructures 5 September 2014 Federated Authentication for E-Infrastructures Jisc Published under the CC BY 4.0 licence creativecommons.org/licenses/by/4.0/ Contents Introduction
CUHK Library Interlibrary Loan System ILLiad User Guide User Services Interlibrary loan and document delivery
 CUHK Library Interlibrary Loan System ILLiad User Guide User Services Interlibrary loan and document delivery Eligible Users ILLiad Features How to Use ILLiad Login One time Registration Add/Change Account
CUHK Library Interlibrary Loan System ILLiad User Guide User Services Interlibrary loan and document delivery Eligible Users ILLiad Features How to Use ILLiad Login One time Registration Add/Change Account
Canadian Access Federation: Trust Assertion Document (TAD)
 Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert authoritative and accurate identity attributes to resources being accessed, and that Participants
Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert authoritative and accurate identity attributes to resources being accessed, and that Participants
Privacy Policy- Introduction part Personal Information
 Privacy policy The Privacy Policy is applicable to the website www.mypitcrew.in registered as MyPitCrew. This privacy statement also does not apply to the websites of our business partners, corporate affiliates
Privacy policy The Privacy Policy is applicable to the website www.mypitcrew.in registered as MyPitCrew. This privacy statement also does not apply to the websites of our business partners, corporate affiliates
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: St. Thomas University Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name: St. Thomas University Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: British Columbia Institute of Technology Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation
Participant Name: British Columbia Institute of Technology Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation
Unit 2: Managing Patron Records
 LINCC Circulation Unit 2 Unit 2: Managing Patron Records This unit provides an overview of patron records and describes searching for a patron record, editing patron information, and adding a new patron
LINCC Circulation Unit 2 Unit 2: Managing Patron Records This unit provides an overview of patron records and describes searching for a patron record, editing patron information, and adding a new patron
What services do you get with a cataloging contract? US/cataloging subscription.html
 Agenda: Introductions Review of services and resources available for Illinois libraries Overview of WorldShare and WorldCat the intersection of workflow and data access Demonstration of the Illinois Group
Agenda: Introductions Review of services and resources available for Illinois libraries Overview of WorldShare and WorldCat the intersection of workflow and data access Demonstration of the Illinois Group
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: Trent University Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name: Trent University Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES (POP)
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES (POP) GALLAUDET UNIVERSITY Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant")
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES (POP) GALLAUDET UNIVERSITY Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant")
SirsiDynix Director s Station Measures
 SirsiDynix Director s Station Measures All Acquisitions Measures Information is taken directly from the order, fund, and vendor records that are entered into the Symphony database. Note: The information
SirsiDynix Director s Station Measures All Acquisitions Measures Information is taken directly from the order, fund, and vendor records that are entered into the Symphony database. Note: The information
Missouri Evergreen II. November, 2017
 Missouri Evergreen II November, 2017 1 Table of Contents Welcome Back 3 Patron Registration 3 Checking Out UPIs 5 Renewing Items 7 Renewing an Expired Account 10 Searching the Catalog and Placing a Hold
Missouri Evergreen II November, 2017 1 Table of Contents Welcome Back 3 Patron Registration 3 Checking Out UPIs 5 Renewing Items 7 Renewing an Expired Account 10 Searching the Catalog and Placing a Hold
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
Canadian Access Federation: Trust Assertion Document (TAD)
 Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert authoritative and accurate identity attributes to resources being accessed, and that Participants
Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert authoritative and accurate identity attributes to resources being accessed, and that Participants
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES There is also a glossary at the end of this document that defines terms shown in italics. Participation in the InCommon Federation ( Federation )
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES There is also a glossary at the end of this document that defines terms shown in italics. Participation in the InCommon Federation ( Federation )
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ( Participant ) to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ( Participant ) to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: Okanagan College Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name: Okanagan College Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Canadian Access Federation: Trust Assertion Document (TAD)
 1. Canadian Access Federation Participant Information 1.1.1. Organization name: DOUGLAS COLLEGE 1.1.2. Information below is accurate as of this date: November 16, 2017 1.2 Identity Management and/or Privacy
1. Canadian Access Federation Participant Information 1.1.1. Organization name: DOUGLAS COLLEGE 1.1.2. Information below is accurate as of this date: November 16, 2017 1.2 Identity Management and/or Privacy
Frequently Asked Questions About Getting On NCAtrak
 Frequently Asked Questions About Getting On NCAtrak Frequently Asked Questions About Getting on NCAtrak (technology reaching all kids) 1. What is NCAtrak? NCAtrak is a computerized, web-based case tracking
Frequently Asked Questions About Getting On NCAtrak Frequently Asked Questions About Getting on NCAtrak (technology reaching all kids) 1. What is NCAtrak? NCAtrak is a computerized, web-based case tracking
In this policy, whenever you see the words we, us, our, it refers to Ashby Concert Band Registered Charity Number
 ASHBY CONCERT BAND PRIVACY POLICY The privacy and security of your personal information is extremely important to us. This privacy policy explains how and why we use your personal data. We will keep this
ASHBY CONCERT BAND PRIVACY POLICY The privacy and security of your personal information is extremely important to us. This privacy policy explains how and why we use your personal data. We will keep this
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: University of Guelph Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name: University of Guelph Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
OCLC INTERLIBRARY LOAN
 OCLC INTERLIBRARY LOAN Procedures White Pine Library Cooperative PROCEDURES FOR SUPERIORLAND COOPERATIVE MEMBERS REVISED OCTOBER 2014 For items that cannot be filled through locally or through MelCat Last
OCLC INTERLIBRARY LOAN Procedures White Pine Library Cooperative PROCEDURES FOR SUPERIORLAND COOPERATIVE MEMBERS REVISED OCTOBER 2014 For items that cannot be filled through locally or through MelCat Last
It s still very important that you take some steps to help keep up security when you re online:
 PRIVACY & SECURITY The protection and privacy of your personal information is a priority to us. Privacy & Security The protection and privacy of your personal information is a priority to us. This means
PRIVACY & SECURITY The protection and privacy of your personal information is a priority to us. Privacy & Security The protection and privacy of your personal information is a priority to us. This means
Credentialing for InCommon
 Credentialing for InCommon Summary/Purpose: This policy describes the means by which user accounts and credentials are managed by the University of Mississippi, as related to participation in the InCommon
Credentialing for InCommon Summary/Purpose: This policy describes the means by which user accounts and credentials are managed by the University of Mississippi, as related to participation in the InCommon
USAHS Library Policy and Procedures on Circulation
 USAHS Library Policy and Procedures on Circulation The University of St. Augustine for Health Sciences (USAHS) Library lends books, DVDs, treatment tables, bone models, and other materials to students,
USAHS Library Policy and Procedures on Circulation The University of St. Augustine for Health Sciences (USAHS) Library lends books, DVDs, treatment tables, bone models, and other materials to students,
Use of Mobile Devices on Voice and Data Networks Policy
 World Agroforestry Centre Policy Series MG/C/4/2012 Use of Mobile Devices on Voice and Data Networks Policy One of the policies on information security and business continuity which will be audited by
World Agroforestry Centre Policy Series MG/C/4/2012 Use of Mobile Devices on Voice and Data Networks Policy One of the policies on information security and business continuity which will be audited by
Appendix B SUBSCRIPTION TERMS AND CONDITIONS. Addendum to British Columbia Electronic Library Network Electronic Products License Agreement
 Appendix B SUBSCRIPTION TERMS AND CONDITIONS Addendum to British Columbia Electronic Library Network Electronic Products License Agreement This Library econtent Addendum dated January 2013 hereby supplements
Appendix B SUBSCRIPTION TERMS AND CONDITIONS Addendum to British Columbia Electronic Library Network Electronic Products License Agreement This Library econtent Addendum dated January 2013 hereby supplements
Emily Kofoid Dawne Tortorella
 Emily Kofoid Emily is a Reference Librarian at the St. Charles Public Library; St. Charles, IL. Among her other reference duties, she is the Interlibrary Loan Coordinator at the Library and serves as the
Emily Kofoid Emily is a Reference Librarian at the St. Charles Public Library; St. Charles, IL. Among her other reference duties, she is the Interlibrary Loan Coordinator at the Library and serves as the
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Shaw Privacy Policy. 1- Our commitment to you
 Privacy Policy last revised on: Sept 16, 2016 Shaw Privacy Policy If you have any questions regarding Shaw s Privacy Policy please contact: privacy@shaw.ca or use the contact information shown on any of
Privacy Policy last revised on: Sept 16, 2016 Shaw Privacy Policy If you have any questions regarding Shaw s Privacy Policy please contact: privacy@shaw.ca or use the contact information shown on any of
QNB Bank-ONLINE AGREEMENT
 This is an Agreement between you and QNB Bank ("QNB"). It explains the rules of your electronic access to your accounts through QNB Online. By using QNB-Online, you accept all the terms and conditions
This is an Agreement between you and QNB Bank ("QNB"). It explains the rules of your electronic access to your accounts through QNB Online. By using QNB-Online, you accept all the terms and conditions
UCOP ITS Systemwide CISO Office Systemwide IT Policy
 UCOP ITS Systemwide CISO Office Systemwide IT Policy Revision History Date: By: Contact Information: Description: 08/16/17 Robert Smith robert.smith@ucop.edu Initial version, CISO approved Classification
UCOP ITS Systemwide CISO Office Systemwide IT Policy Revision History Date: By: Contact Information: Description: 08/16/17 Robert Smith robert.smith@ucop.edu Initial version, CISO approved Classification
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Canadian Access Federation: Trust Assertion Document (TAD)
 Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert authoritative and accurate identity attributes to resources being accessed, and that Participants
Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert authoritative and accurate identity attributes to resources being accessed, and that Participants
8/28/2014. Patron Records. About. Patron Records. Patron Records. Patron Records. Patron Records. Overview of Creating and Maintaining.
 About These instructions should serve as a basic overview of creating and updating patron accounts. Overview of Creating and Maintaining Please refer to the PINES Circulation Policies and Procedures Manual
About These instructions should serve as a basic overview of creating and updating patron accounts. Overview of Creating and Maintaining Please refer to the PINES Circulation Policies and Procedures Manual
Elders Estates Privacy Notice
 15A Bath Street, Ilkeston Derbyshire. DE7 8AH 01159 32 55 23 info@eldersestates.co.uk 31 Market Place, Ripley Derbyshire. DE5 3HA 01773 30 44 44 info@eldersestates.co.uk Elders Estates Privacy Notice Introduction
15A Bath Street, Ilkeston Derbyshire. DE7 8AH 01159 32 55 23 info@eldersestates.co.uk 31 Market Place, Ripley Derbyshire. DE5 3HA 01773 30 44 44 info@eldersestates.co.uk Elders Estates Privacy Notice Introduction
ISSP Network Security Plan
 ISSP-000 - Network Security Plan 1 CONTENTS 2 INTRODUCTION (Purpose and Intent)... 1 3 SCOPE... 2 4 STANDARD PROVISIONS... 2 5 STATEMENT OF PROCEDURES... 3 5.1 Network Control... 3 5.2 DHCP Services...
ISSP-000 - Network Security Plan 1 CONTENTS 2 INTRODUCTION (Purpose and Intent)... 1 3 SCOPE... 2 4 STANDARD PROVISIONS... 2 5 STATEMENT OF PROCEDURES... 3 5.1 Network Control... 3 5.2 DHCP Services...
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
ROCHESTER CITY SCHOOL DISTRICT INTERLIBRARY LOANS PROCEDURES
 ROCHESTER CITY SCHOOL DISTRICT INTERLIBRARY LOANS PROCEDURES Revised August 2011 Table of Contents About Destiny Page 3 About Textbook Catalog in Destiny Page 3 About FiveSystems Page 3 About Monroe County
ROCHESTER CITY SCHOOL DISTRICT INTERLIBRARY LOANS PROCEDURES Revised August 2011 Table of Contents About Destiny Page 3 About Textbook Catalog in Destiny Page 3 About FiveSystems Page 3 About Monroe County
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: Concordia University of Edmonton Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that
Participant Name: Concordia University of Edmonton Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
University of Wyoming Mobile Communication Device Policy Effective January 1, 2013
 University of Wyoming Mobile Communication Device Policy Effective January 1, 2013 Introduction and Purpose This policy allows the University to meet Internal Revenue Service (IRS) regulations and its
University of Wyoming Mobile Communication Device Policy Effective January 1, 2013 Introduction and Purpose This policy allows the University to meet Internal Revenue Service (IRS) regulations and its
Privacy Policy. Effective date: 21 May 2018
 Privacy Policy Effective date: 21 May 2018 We at Meetingbird know you care about how your personal information is used and shared, and we take your privacy seriously. Please read the following to learn
Privacy Policy Effective date: 21 May 2018 We at Meetingbird know you care about how your personal information is used and shared, and we take your privacy seriously. Please read the following to learn
Destiny Library Manager
 Destiny Library Manager Setting Up One Search Your teachers and students can take advantage of your school s subscription databases all in one place through Destiny One Search. One Search saves staff and
Destiny Library Manager Setting Up One Search Your teachers and students can take advantage of your school s subscription databases all in one place through Destiny One Search. One Search saves staff and
Interlibrary Loan: Book Request through the Digital Library
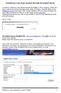 Interlibrary Loan: Book Request through the Digital Library To submit a interlibrary loan request through the DigiBib a TAN is required. Contact the library staff at the Central Information Desk, Bldg.
Interlibrary Loan: Book Request through the Digital Library To submit a interlibrary loan request through the DigiBib a TAN is required. Contact the library staff at the Central Information Desk, Bldg.
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: Acadia University Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name: Acadia University Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Privacy Policy May 2018
 Privacy Policy May 2018 Laser Surveys Ltd T/A Open Space Rooms Laser Surveys operates a privacy first approach to all our business activities and will only require the minimum information to perform our
Privacy Policy May 2018 Laser Surveys Ltd T/A Open Space Rooms Laser Surveys operates a privacy first approach to all our business activities and will only require the minimum information to perform our
We offer background check and identity verification services to employers, businesses, and individuals. For example, we provide:
 This Privacy Policy applies to the websites, screening platforms, mobile applications, and APIs (each, a Service ) owned and/or operated by Background Research Solutions, LLC ("we"/ BRS ). It also describes
This Privacy Policy applies to the websites, screening platforms, mobile applications, and APIs (each, a Service ) owned and/or operated by Background Research Solutions, LLC ("we"/ BRS ). It also describes
This regulation outlines the policy and procedures for the implementation of wireless networking for the University Campus.
 UAR NUMBER: 400.01 TITLE: Wireless Network Policy and Procedure INITIAL ADOPTION: 11/6/2003 REVISION DATES: PURPOSE: Set forth the policy for using wireless data technologies and assigns responsibilities
UAR NUMBER: 400.01 TITLE: Wireless Network Policy and Procedure INITIAL ADOPTION: 11/6/2003 REVISION DATES: PURPOSE: Set forth the policy for using wireless data technologies and assigns responsibilities
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
PADOR HELP GUIDE FOR CO-APPLICANTS
 PADOR HELP GUIDE FOR CO-APPLICANTS WHAT IS PADOR?... 1 WHO CAN REGISTER IN PADOR?... 1 WHY register my organisation in PADOR? Is registration obligatory?... 2 WHEN to register? When to update an account?...
PADOR HELP GUIDE FOR CO-APPLICANTS WHAT IS PADOR?... 1 WHO CAN REGISTER IN PADOR?... 1 WHY register my organisation in PADOR? Is registration obligatory?... 2 WHEN to register? When to update an account?...
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name:_Gale_Cengage Learning Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name:_Gale_Cengage Learning Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: CARLETON UNIVERSITY Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name: CARLETON UNIVERSITY Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Top-Down Network Design
 Top-Down Network Design Chapter Eight Developing Network Security Strategies Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Network Security Design The steps for security design are: 1. Identify
Top-Down Network Design Chapter Eight Developing Network Security Strategies Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Network Security Design The steps for security design are: 1. Identify
Echidna Concepts Guide
 Salt Group Concepts Guide Version 15.1 May 2015 2015 Salt Group Proprietary Limited. All rights reserved. Information in this document is subject to change without notice. The software described in this
Salt Group Concepts Guide Version 15.1 May 2015 2015 Salt Group Proprietary Limited. All rights reserved. Information in this document is subject to change without notice. The software described in this
WILIUG 2016 Lightning Round Diving into SkyRiver July 8, 2016
 The Waukegan Public Library dove right into SkyRiver! In June of 2015, we went live, and less than a month later, our contract with OCLC ended. Now a year has passed, and we re swimming along just fine.
The Waukegan Public Library dove right into SkyRiver! In June of 2015, we went live, and less than a month later, our contract with OCLC ended. Now a year has passed, and we re swimming along just fine.
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Welcome to the new BC Bid!
 BC Bid has a new design, new features and services, but most importantly, a new way of doing business. Beginning in early 2003, suppliers will be able to submit bids and proposals electronically in response
BC Bid has a new design, new features and services, but most importantly, a new way of doing business. Beginning in early 2003, suppliers will be able to submit bids and proposals electronically in response
FedMall Frequently Asked Questions
 HOMEPAGE: Q: Why can I not access the FAQs once I log into? A: The FAQ s are hosted on a public page, under News and Announcements topic Town Halls, you ll find a link into the most updated FAQs. Q: Why
HOMEPAGE: Q: Why can I not access the FAQs once I log into? A: The FAQ s are hosted on a public page, under News and Announcements topic Town Halls, you ll find a link into the most updated FAQs. Q: Why
Annals of Mathematics Electronic License Agreement
 Annals of Mathematics Electronic License Agreement Annals of Mathematics, Fine Hall-Washington Road, Princeton University, Princeton, NJ 08544-1000, USA. Fax: 1-609-258-1367 Phone: 1-609-258-4191. By this
Annals of Mathematics Electronic License Agreement Annals of Mathematics, Fine Hall-Washington Road, Princeton University, Princeton, NJ 08544-1000, USA. Fax: 1-609-258-1367 Phone: 1-609-258-4191. By this
When you provide personal information to us it will only be used in the ways described in this privacy policy.
 Website Privacy Policy Overview Welcome to this Global Payroll Management Institute website, owned and produced by the Global Payroll Management Institute, Inc. (GPMI). Our website is available to all
Website Privacy Policy Overview Welcome to this Global Payroll Management Institute website, owned and produced by the Global Payroll Management Institute, Inc. (GPMI). Our website is available to all
OAKLAND COUNTY, MICHIGAN GEOSPATIAL DATA ACCESS, DISTRIBUTION AND USE
 OAKLAND COUNTY, MICHIGAN GEOSPATIAL DATA ACCESS, DISTRIBUTION AND USE The following Geospatial Data Access, Distribution, and Use standard is designed to assist County employees and other approved users
OAKLAND COUNTY, MICHIGAN GEOSPATIAL DATA ACCESS, DISTRIBUTION AND USE The following Geospatial Data Access, Distribution, and Use standard is designed to assist County employees and other approved users
SYDNEY FESTIVAL PRIVACY POLICY
 1. Level 5, 10 Hickson Road The Rocks Sydney NSW 2000 Australia Phone 61 2 8248 6500 Fax 61 2 8248 6599 sydneyfestival.org.au ABN 60 070 285 344 SYDNEY FESTIVAL PRIVACY POLICY Our Commitment to your Privacy
1. Level 5, 10 Hickson Road The Rocks Sydney NSW 2000 Australia Phone 61 2 8248 6500 Fax 61 2 8248 6599 sydneyfestival.org.au ABN 60 070 285 344 SYDNEY FESTIVAL PRIVACY POLICY Our Commitment to your Privacy
WIRELESS DEVICES: ACCEPTABLE USE AND GUIDELINES
 Intermediate School District #917 WIRELESS DEVICES: ACCEPTABLE USE AND GUIDELINES Procedures Manual April 2009 Table of Contents Overview 3 Definitions 3 General Guidelines 4 Eligibility Requirements 5
Intermediate School District #917 WIRELESS DEVICES: ACCEPTABLE USE AND GUIDELINES Procedures Manual April 2009 Table of Contents Overview 3 Definitions 3 General Guidelines 4 Eligibility Requirements 5
IT Governance Committee Review and Recommendation
 IT Governance Committee Review and Recommendation Desired Change: Approval of this policy will establish Security Standards for the UCLA Logon Identity for anyone assigned a UCLA Logon ID/password and
IT Governance Committee Review and Recommendation Desired Change: Approval of this policy will establish Security Standards for the UCLA Logon Identity for anyone assigned a UCLA Logon ID/password and
The information we collect
 Phone: (02) 8035 8000 Web: www.carnextdoor.com.au Email: info@carnextdoor.com.au Address: Level 3, 55 Pyrmont Bridge Rd, Pyrmont, NSW, 2009 CAR NEXT DOOR PRIVACY POLICY AND CREDIT REPORTING POLICY Last
Phone: (02) 8035 8000 Web: www.carnextdoor.com.au Email: info@carnextdoor.com.au Address: Level 3, 55 Pyrmont Bridge Rd, Pyrmont, NSW, 2009 CAR NEXT DOOR PRIVACY POLICY AND CREDIT REPORTING POLICY Last
The Texas A&M University System. Internal Audit Department. Fiscal Year 2014 Audit Plan
 Introduction The purpose of the Audit Plan is to outline audits and other activities the System Internal Audit Department will conduct during fiscal year 2014. The plan is developed to satisfy responsibilities
Introduction The purpose of the Audit Plan is to outline audits and other activities the System Internal Audit Department will conduct during fiscal year 2014. The plan is developed to satisfy responsibilities
IMPLEMENTATION POLICY AND PROCEDURES FOR SECURING NETWORKED DEVICES
 UNIVERSITY OF CALIFORNIA, BERKELEY BERKELEY DAVIS IRVINE LOS ANGELES RIVERSIDE SAN DIEGO SAN FRANCISCO SANTA BARBARA SANTA CRUZ ECONOMETRICS LABORATORY Institute of Business and Economic Research ECONOMETRICS
UNIVERSITY OF CALIFORNIA, BERKELEY BERKELEY DAVIS IRVINE LOS ANGELES RIVERSIDE SAN DIEGO SAN FRANCISCO SANTA BARBARA SANTA CRUZ ECONOMETRICS LABORATORY Institute of Business and Economic Research ECONOMETRICS
Mobile Communication Devices. 1.0 Purpose. 2.0 Policy NO Virginia Polytechnic Institute and State University
 Mobile Communication Devices NO. 3960 Policy Effective Date: 3/8/2016 Last Revision Date: Policy Owner: Dwight Shelton Policy Author: (Contact Person) Savita Sharma Affected Parties: Faculty Staff 1.0
Mobile Communication Devices NO. 3960 Policy Effective Date: 3/8/2016 Last Revision Date: Policy Owner: Dwight Shelton Policy Author: (Contact Person) Savita Sharma Affected Parties: Faculty Staff 1.0
MOBILE.NET PRIVACY POLICY
 MOBILE.NET PRIVACY POLICY As the operator of the Mobile.net website (https://mobile.net.ltd/) (Website), ADX Labs, LLC. (Company, we or us) is committed to protecting and respecting your privacy. The data
MOBILE.NET PRIVACY POLICY As the operator of the Mobile.net website (https://mobile.net.ltd/) (Website), ADX Labs, LLC. (Company, we or us) is committed to protecting and respecting your privacy. The data
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: Conestoga College Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name: Conestoga College Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
