CSE 127 Computer Security
|
|
|
- Estella Butler
- 5 years ago
- Views:
Transcription
1 CSE 127 Computer Security Alex Gantman, Spring 2018, Lecture 19 SDLC: Secure Development Lifecycle
2 Defining Security Security is not a functionality feature Most of computer science is about providing functionality: User Interface, Software Design, Algorithms, Operating Systems/Networking, Compilers/PL, Microarchitecture Computer security is not about functionality It is about how the embodiment of functionality behaves in the presence of an adversary. Making sure the system does what it was supposed to do and only what it was supposed to do. Holistic property Software security is about integrating security practices into the way you build software, not integrating security features into your code Gary McGraw
3 Secure Development Lifecycle How can we develop more robust systems? Prevention How can we minimize the number of vulnerabilities introduced during development? Mitigation How can we minimize the impact of vulnerabilities that remain? Response How can we remediate newly discovered vulnerabilities in deployed products?
4 Secure Development Lifecycle Prevention Mitigation Response
5 Secure Development Lifecycle Nice story, but that s not how it works. It all begins with an incident E.g. vulnerability report, exploit release, etc.
6 Incident Response So you get a bug/vulnerability report Example: Meltdown/Spectre We have discovered that CPU data cache timing can be abused to efficiently leak information out of mis-speculated execution, leading to (at worst) arbitrary virtual memory read vulnerabilities across local security boundaries in various contexts.
7 Incident Response Step 1: What does it mean? What is the root cause of the vulnerability? Requires deep technical understanding of the system. Have to break through abstraction boundaries. What does it enable an attacker to do? Requires understanding of the threat model (what needs to be protected from whom) and modern exploitation techniques. What is the impact on the user? Requires understanding how products are used by real users.
8 Incident Response Step 2: Address the issue. Develop fix. Ideally, without introducing new bugs in the process. Properly understanding the vulnerability and exploitation techniques is necessary to develop a correct fix. Aside: what if the vulnerability is in third-party code? Propagate fix to impacted product variants. Depending on your industry, you may have many variations of the same software that need to be updated. Have to understand the entire software supply chain and lifecycle. From developer s keyboard to the landfill. Do you really know what is going into production? Patch/Notify customers.
9 Incident Response Step 3: Analyze the gap. Start working backwards to identify and address gaps in existing process. Response How could you have handled the response better? Mitigation What countermeasures would have mitigated the impact? Prevention How could you have prevented the vulnerability from being released?
10 Gap Analysis Prevention Mitigation Response
11 Gap Analysis: Response How can you learn about new incidents as early as possible? Was the issue reported privately? Did you learn about it from reading the news? Establish cooperative relationships with security researchers Easy to find web page with information on how to report vulnerabilities to the security team Responsive mail address Encourage/incentivize direct reporting of vulnerabilities If your security program is mature enough, consider a bug bounty Aside: Full Disclosure vs Responsible Disclosure vs Coordinated Disclosure If you discover a previously unpublished security vulnerability, I encourage you to report it to the system developers/maintainers Check following directories or try ing security@<domain>
12 Gap Analysis Prevention Mitigation Response
13 Gap Analysis: Mitigation What countermeasures would have mitigated the impact? Not all vulnerabilities will be discovered prior to release. Countermeasures can make reliable exploitation harder or mitigate the impact of remaining vulnerabilities. Can make exploit development more difficult and costly. Will not stop all exploits.
14 Gap Analysis: Mitigation Identify and implement available countermeasures. Need to understand the current state of the art, cost/benefit tradeoffs, constraints of your platform, etc. Some countermeasures may already be present and only need to be properly configured and enabled. Others may need to be re-implemented or ported on your particular platform. Need continuous process to test proper configuration. Research and develop new countermeasures. New offensive and defensive techniques are continuously being developed. Developers introduce new features. Attackers devise ways to exploit these features. Defenders devise new countermeasures. Attackers adapt to the new countermeasures, defenders refine their approach,
15 Gap Analysis Prevention Mitigation Response
16 Gap Analysis: Prevention How could you have prevented the vulnerability from being released? Secure Software Development training for engineers. Automated tools to detect vulnerabilities prior to release. Designing the system with security in mind.
17 Gap Analysis: Prevention Secure Software Training For the last 30 years, most CS graduates had no background in computer security No idea of what types of vulnerabilities are possible, how they are exploited, what they look like, how to fix them, etc. UCSD recently made security a required part of the curriculum. Companies develop custom training to fill the gap Using real in-house code helps make the training relevant. Focus on how to avoid, detect, and address typical software vulnerabilities.
18 Gap Analysis: Prevention Code reviews Automated tools to detect vulnerabilities prior to release. Static Analysis Dynamic Analysis
19 Gap Analysis: Prevention Code reviews Pros: A consistently high-yield approach to finding security vulnerabilities Only dependency is access to source No tools to configure, no build system to integrate with, Cons: Does not scale well There are a lot of developers writing a lot of code Easy to burn out from continuous code reviews Success highly dependent on expertise of the reviewer
20 Gap Analysis: Prevention To scale, we need to automate Static Analysis Compiler-like analysis of the source code, looking for error-prone areas Eg: Coverity, KLOCWork
21
22
23 Gap Analysis: Prevention Static Analysis Pros: Very good at finding some types of vulnerabilities. Custom checkers can be added to detect specific security issues. Cons: Can have high false positive rates. No tool works well out of the box. Need to be integrated with the build system and tuned to the idioms of the target codebase.
24 Gap Analysis: Prevention Some vulnerabilities may be easier to discover with dynamic testing Some may only be discoverable with dynamic testing Dynamic Analysis/Adversarial Testing/Fuzzing Subject system to _very_ large amounts of tests exercising edge and error cases Combine with instrumentation (sanitizers) Active area of research Example: AFL
25 Fuzzing Test case generation Random Mutational Start with a corpus of valid test cases and mutate them Generational Develop a model (grammar) for the input format and use it to generate test cases
26 Fuzzing Code coverage How to measure coverage? Line coverage Branch coverage Path coverage char bar[20]; if (j > 20) return; for (i = 0; i <= j; i++) bar[i] = foo[i]; Coverage can be a useful feedback function Guide the fuzzer to explore new areas of code The real goal though, is to find bugs, not maximize coverage
27 Gap Analysis: Prevention Fuzzing Pros: Very effective bug-finding technique Highly scalable, can run in the background Cons: Deep bugs are hard to trigger Concolic testing Crash overload
28 Gap Analysis: Prevention Designing the system for security and containment of compromise. Defining a threat model (what should be protected from whom) Identifying and evaluating risks Building in defenses
29 Risk Assessment Risk assessment/risk analysis process for assessing risk in a system: 1. Start by understanding system requirements 2. Identify assets and attackers 3. Establish security requirements 4. Evaluate system design 5. Identify threats and classify risks 6. Address identified risks
30 Gap Analysis: Prevention Building in defenses Isolation of components to contain damage from spill-over Hardening of security boundaries Re-architecting of high-risk components for sandboxing
31 Secure Development Lifecycle Prevention Mitigation Response
32 Secure Development Lifecycle A methodology for building more secure systems Many variations on the same theme Microsoft SDLC Cigital Touchpoints Building Security In Maturity Model (BSIMM) SafeCode
33 Secure Development Lifecycle Microsoft SDLC s and Code Red Bill Gates Trustworthy Computing Memo
34 Code Red On July 19, 2001 more than 359,000 computers were infected with the Code-Red (CRv2) worm in less than 14 hours. At the peak of the infection frenzy, more than 2,000 new hosts were infected each minute.
35 Bill Gates Trustworthy Computing Memo January 2002 So now, when we face a choice between adding features and resolving security issues, we need to choose security. Our products should emphasize security right out of the box, and we must constantly refine and improve that security as threats evolve If we discover a risk that a feature could compromise someone's privacy, that problem gets solved first. If there is any way we can better protect important data and minimize downtime, we should focus on this. These principles should apply at every stage of the development cycle of every kind of software we create, from operating systems and desktop applications to global Web services.
36 Secure Development Lifecycle Microsoft SDLC
37 Secure Development Lifecycle
38 Secure Development Lifecycle Cigital Touchpoints
39 Secure Development Lifecycle BSIMM multiyear study of [109] real-world software security initiatives 113 activities across 12 practices, organized into four domains
40 Secure Development Lifecycle Caveat emptor The real development process is much more complex Details will depend on the technology of your product, the nature of your business, culture of your company,
41
42 Close
43 Ethics In this class you learned how to attack the security of computer systems (and some physical systems) We learn attacks because it is needed to understand how to defend them You have an obligation to use this knowledge ethically You may not attack others Many good legitimate hacking challenges.
44 Exploit Playgrounds Wargames Reverse Engineering Challenges CTFs UCSD CTF:
45 Course Objectives A solid foundation of security concepts, backed by concrete examples Security mindset How to think like an attacker/ security engineer Looking beyond the system s intended functionality, to what it can be made to do Understanding how things work, how they break, and how to fix them Technical details of vulnerabilities, attacks, and defenses
46 Course Objectives During your career you will design and build complex systems. With probability asymptotically approaching 1, you will introduce numerous security vulnerabilities in the process. My goals are to help you: a) Minimize the number and severity of vulnerabilities you will introduce; b) Better understand the root causes and impact of vulnerabilities that are brought to your attention; c) Properly address identified vulnerabilities.
47 Prerequisites/Expectations You are expected to have a basic understanding of C and assembly Operating Systems Computer Architecture Networking Compilers Theory of Computation Operating Systems Security
48 Homework Final is on Saturday 6/9 3pm-6pm in WLH 2005 Covers everything: from first lecture up to, and including, today Similar format to the midterm You can bring in one sheet (8.5 x11 ) of paper with notes
49 Thank You
Product Security Program
 Product Security Program An overview of Carbon Black s Product Security Program and Practices Copyright 2016 Carbon Black, Inc. All rights reserved. Carbon Black is a registered trademark of Carbon Black,
Product Security Program An overview of Carbon Black s Product Security Program and Practices Copyright 2016 Carbon Black, Inc. All rights reserved. Carbon Black is a registered trademark of Carbon Black,
MARCH Secure Software Development WHAT TO CONSIDER
 MARCH 2017 Secure Software Development WHAT TO CONSIDER Table of Content Introduction... 2 Background... 3 Problem Statement... 3 Considerations... 4 Planning... 4 Start with security in requirements (Abuse
MARCH 2017 Secure Software Development WHAT TO CONSIDER Table of Content Introduction... 2 Background... 3 Problem Statement... 3 Considerations... 4 Planning... 4 Start with security in requirements (Abuse
CYSE 411/AIT 681 Secure Software Engineering. Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun
 CYSE 411/AIT 681 Secure Software Engineering Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun Reading This lecture [McGraw]: Ch. 7-9 2 Seven Touchpoints 1. Code review 2. Architectural
CYSE 411/AIT 681 Secure Software Engineering Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun Reading This lecture [McGraw]: Ch. 7-9 2 Seven Touchpoints 1. Code review 2. Architectural
It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to
 1 2 It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to keep putting garbage characters into the command
1 2 It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to keep putting garbage characters into the command
4. Risk-Based Security Testing. Reading. CYSE 411/AIT 681 Secure Software Engineering. Seven Touchpoints. Application of Touchpoints
 Reading This lecture [McGraw]: Ch. 7-9 CYSE 411/AIT 681 Secure Software Engineering Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun 2 Seven Touchpoints Application of Touchpoints
Reading This lecture [McGraw]: Ch. 7-9 CYSE 411/AIT 681 Secure Software Engineering Topic #6. Seven Software Security Touchpoints (III) Instructor: Dr. Kun Sun 2 Seven Touchpoints Application of Touchpoints
Secure Development Processes
 Secure Development Processes SecAppDev2009 What s the problem? Writing secure software is tough Newcomers often are overwhelmed Fear of making mistakes can hinder Tend to delve into security superficially
Secure Development Processes SecAppDev2009 What s the problem? Writing secure software is tough Newcomers often are overwhelmed Fear of making mistakes can hinder Tend to delve into security superficially
Development*Process*for*Secure* So2ware
 Development*Process*for*Secure* So2ware Development Processes (Lecture outline) Emphasis on building secure software as opposed to building security software Major methodologies Microsoft's Security Development
Development*Process*for*Secure* So2ware Development Processes (Lecture outline) Emphasis on building secure software as opposed to building security software Major methodologies Microsoft's Security Development
Security Testing. John Slankas
 Security Testing John Slankas jbslanka@ncsu.edu Course Slides adapted from OWASP Testing Guide v4 CSC 515 Software Security What is Security Testing? Validate security controls operate as expected What
Security Testing John Slankas jbslanka@ncsu.edu Course Slides adapted from OWASP Testing Guide v4 CSC 515 Software Security What is Security Testing? Validate security controls operate as expected What
cs642 /introduction computer security adam everspaugh
 cs642 computer security /introduction adam everspaugh ace@cs.wisc.edu definition Computer Security := understanding and improving the behavior of computing systems in the presence of adversaries adversaries
cs642 computer security /introduction adam everspaugh ace@cs.wisc.edu definition Computer Security := understanding and improving the behavior of computing systems in the presence of adversaries adversaries
Protect Your Organization from Cyber Attacks
 Protect Your Organization from Cyber Attacks Leverage the advanced skills of our consultants to uncover vulnerabilities our competitors overlook. READY FOR MORE THAN A VA SCAN? Cyber Attacks by the Numbers
Protect Your Organization from Cyber Attacks Leverage the advanced skills of our consultants to uncover vulnerabilities our competitors overlook. READY FOR MORE THAN A VA SCAN? Cyber Attacks by the Numbers
Software Security IV: Fuzzing
 1 Software Security IV: Fuzzing Chengyu Song Slides modified from Dawn Song 2 Administrivia Homework1 Due: Friday Oct 27 11:59pm Questions regarding reading materials Talk Security R&D in a Security Company:
1 Software Security IV: Fuzzing Chengyu Song Slides modified from Dawn Song 2 Administrivia Homework1 Due: Friday Oct 27 11:59pm Questions regarding reading materials Talk Security R&D in a Security Company:
113 BSIMM Activities at a Glance
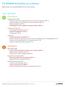 113 BSIMM Activities at a Glance (Red indicates most observed BSIMM activity in that practice) Level 1 Activities Governance Strategy & Metrics (SM) Publish process (roles, responsibilities, plan), evolve
113 BSIMM Activities at a Glance (Red indicates most observed BSIMM activity in that practice) Level 1 Activities Governance Strategy & Metrics (SM) Publish process (roles, responsibilities, plan), evolve
STUDENT LEARNING OUTCOMES Beacom College of Computer and Cyber Sciences
 STUDENT LEARNING OUTCOMES Beacom College of Computer and Cyber Sciences Undergraduate Programs - Bachelor B.S. Computer Game Design Upon completion of the B.S. degree in Computer Game Design, students
STUDENT LEARNING OUTCOMES Beacom College of Computer and Cyber Sciences Undergraduate Programs - Bachelor B.S. Computer Game Design Upon completion of the B.S. degree in Computer Game Design, students
Building Trustworthiness The Evolution of Secure Development. Glenn Pittaway and Alex Lucas Trustworthy Computing, Microsoft Corporation
 Building Trustworthiness The Evolution of Secure Development Glenn Pittaway and Alex Lucas Trustworthy Computing, Microsoft Corporation Goals Provide an understanding of the Microsoft view of security
Building Trustworthiness The Evolution of Secure Development Glenn Pittaway and Alex Lucas Trustworthy Computing, Microsoft Corporation Goals Provide an understanding of the Microsoft view of security
Surprisingly Successful: What Really Works in Cyber Defense. John Pescatore, SANS
 Surprisingly Successful: What Really Works in Cyber Defense John Pescatore, SANS 1 Largest Breach Ever 2 The Business Impact Equation All CEOs know stuff happens in business and in security The goal is
Surprisingly Successful: What Really Works in Cyber Defense John Pescatore, SANS 1 Largest Breach Ever 2 The Business Impact Equation All CEOs know stuff happens in business and in security The goal is
Brochure. Security. Fortify on Demand Dynamic Application Security Testing
 Brochure Security Fortify on Demand Dynamic Application Security Testing Brochure Fortify on Demand Application Security as a Service Dynamic Application Security Testing Fortify on Demand delivers application
Brochure Security Fortify on Demand Dynamic Application Security Testing Brochure Fortify on Demand Application Security as a Service Dynamic Application Security Testing Fortify on Demand delivers application
RiskSense Attack Surface Validation for IoT Systems
 RiskSense Attack Surface Validation for IoT Systems 2018 RiskSense, Inc. Surfacing Double Exposure Risks Changing Times and Assessment Focus Our view of security assessments has changed. There is diminishing
RiskSense Attack Surface Validation for IoT Systems 2018 RiskSense, Inc. Surfacing Double Exposure Risks Changing Times and Assessment Focus Our view of security assessments has changed. There is diminishing
C T I A CERTIFIED THREAT INTELLIGENCE ANALYST. EC-Council PROGRAM BROCHURE. Certified Threat Intelligence Analyst 1. Certified
 EC-Council C T Certified I A Threat Intelligence Analyst CERTIFIED THREAT INTELLIGENCE ANALYST PROGRAM BROCHURE 1 Predictive Capabilities for Proactive Defense! Cyber threat incidents have taken a drastic
EC-Council C T Certified I A Threat Intelligence Analyst CERTIFIED THREAT INTELLIGENCE ANALYST PROGRAM BROCHURE 1 Predictive Capabilities for Proactive Defense! Cyber threat incidents have taken a drastic
Maximum Security with Minimum Impact : Going Beyond Next Gen
 SESSION ID: SP03-W10 Maximum Security with Minimum Impact : Going Beyond Next Gen Wendy Moore Director, User Protection Trend Micro @WMBOTT Hyper-competitive Cloud Rapid adoption Social Global Mobile IoT
SESSION ID: SP03-W10 Maximum Security with Minimum Impact : Going Beyond Next Gen Wendy Moore Director, User Protection Trend Micro @WMBOTT Hyper-competitive Cloud Rapid adoption Social Global Mobile IoT
The Building Security In Maturity Model. Quality Assurance Perspective. Sammy Migues Principal Consultant, Cigital. Software Confidence. Achieved.
 The Building Security In Maturity Model Quality Assurance Perspective Software Confidence. Achieved. Sammy Migues Principal Consultant, Cigital March 31, 2009 Breaking new ground Building Security In Maturity
The Building Security In Maturity Model Quality Assurance Perspective Software Confidence. Achieved. Sammy Migues Principal Consultant, Cigital March 31, 2009 Breaking new ground Building Security In Maturity
Internet infrastructure
 Internet infrastructure Prof. dr. ir. André Mariën (c) A. Mariën 04/03/2014 1 Topic Vulnerability and patch management (c) A. Mariën 04/03/2014 2 Requirements Security principle: Everything can and will
Internet infrastructure Prof. dr. ir. André Mariën (c) A. Mariën 04/03/2014 1 Topic Vulnerability and patch management (c) A. Mariën 04/03/2014 2 Requirements Security principle: Everything can and will
Secure Development Lifecycle
 Secure Development Lifecycle Strengthening Cisco Products The Cisco Secure Development Lifecycle (SDL) is a repeatable and measurable process designed to increase Cisco product resiliency and trustworthiness.
Secure Development Lifecycle Strengthening Cisco Products The Cisco Secure Development Lifecycle (SDL) is a repeatable and measurable process designed to increase Cisco product resiliency and trustworthiness.
An SDLC for the DevSecOps Era Or SecDevOps, or DevOpsSec,
 An SDLC for the DevSecOps Era Or SecDevOps, or DevOpsSec, or zane@signalsciences.com @zanelackey Who you ll be heckling today Started out in offense Pentester / researcher at isec Partners / NCC Group
An SDLC for the DevSecOps Era Or SecDevOps, or DevOpsSec, or zane@signalsciences.com @zanelackey Who you ll be heckling today Started out in offense Pentester / researcher at isec Partners / NCC Group
CSE 544 Advanced Systems Security
 Systems and Internet Infrastructure Security Network and Security Research Center Department of Computer Science and Engineering Pennsylvania State University, University Park PA CSE 544 Advanced Systems
Systems and Internet Infrastructure Security Network and Security Research Center Department of Computer Science and Engineering Pennsylvania State University, University Park PA CSE 544 Advanced Systems
Threat Modeling. Bart De Win Secure Application Development Course, Credits to
 Threat Modeling Bart De Win bart.dewin@ascure.com Secure Application Development Course, 2009 Credits to Frank Piessens (KUL) for the slides 2 1 Overview Introduction Key Concepts Threats, Vulnerabilities,
Threat Modeling Bart De Win bart.dewin@ascure.com Secure Application Development Course, 2009 Credits to Frank Piessens (KUL) for the slides 2 1 Overview Introduction Key Concepts Threats, Vulnerabilities,
How to implement SDL and don t turn gray. Andrey Kovalev, Security Engineer
 How to implement SDL and don t turn gray Andrey Kovalev, Security Engineer Agenda SDL 101 Yandex approach SAST, DAST, FSR: drawbacks and solutions Summary 3 How to implement SDL and don t turn gray SDL
How to implement SDL and don t turn gray Andrey Kovalev, Security Engineer Agenda SDL 101 Yandex approach SAST, DAST, FSR: drawbacks and solutions Summary 3 How to implement SDL and don t turn gray SDL
Incident response in critical infrastructure. Margrete Raaum
 Incident response in critical infrastructure Margrete Raaum margrete.raaum@kraftcert.no Margrete.raaum@first.org Protection vs readiness There is no such thing as absolute security Perimeter protection
Incident response in critical infrastructure Margrete Raaum margrete.raaum@kraftcert.no Margrete.raaum@first.org Protection vs readiness There is no such thing as absolute security Perimeter protection
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE
 DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
SECURITY TRAINING SECURITY TRAINING
 SECURITY TRAINING SECURITY TRAINING Addressing software security effectively means applying a framework of focused activities throughout the software lifecycle in addition to implementing sundry security
SECURITY TRAINING SECURITY TRAINING Addressing software security effectively means applying a framework of focused activities throughout the software lifecycle in addition to implementing sundry security
Defend Against the Unknown
 Defend Against the Unknown Stay ahead of new threats with McAfee Endpoint Threat Defense solutions Targeted exploits. Ransomware. Explosive growth in zero-day malware. Organizations are locked in an ongoing
Defend Against the Unknown Stay ahead of new threats with McAfee Endpoint Threat Defense solutions Targeted exploits. Ransomware. Explosive growth in zero-day malware. Organizations are locked in an ongoing
Enhancing the Cybersecurity of Federal Information and Assets through CSIP
 TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
Cybersecurity Risk Mitigation: Protect Your Member Data. Introduction
 Cybersecurity Risk Mitigation: Protect Your Member Data Presented by Matt Mitchell, CISSP Knowledge Consulting Group Introduction Matt Mitchell- Director Risk Assurance 17 years information security experience
Cybersecurity Risk Mitigation: Protect Your Member Data Presented by Matt Mitchell, CISSP Knowledge Consulting Group Introduction Matt Mitchell- Director Risk Assurance 17 years information security experience
CYBER RESILIENCE & INCIDENT RESPONSE
 CYBER RESILIENCE & INCIDENT RESPONSE www.nccgroup.trust Introduction The threat landscape has changed dramatically over the last decade. Once the biggest threats came from opportunist attacks and preventable
CYBER RESILIENCE & INCIDENT RESPONSE www.nccgroup.trust Introduction The threat landscape has changed dramatically over the last decade. Once the biggest threats came from opportunist attacks and preventable
CS 161 Computer Security
 Popa & Wagner Spring 2016 CS 161 Computer Security Homework 2 Due: Monday, February 22nd, at 11:59pm Instructions. This homework is due Monday, February 22nd, at 11:59pm. It must be submitted electronically
Popa & Wagner Spring 2016 CS 161 Computer Security Homework 2 Due: Monday, February 22nd, at 11:59pm Instructions. This homework is due Monday, February 22nd, at 11:59pm. It must be submitted electronically
Plant Security Services Protecting productivity in the digital era October
 Plant Security Services Protecting productivity in the digital era October2017 Restricted www.siemens.com/plant-security-services Internet of (hacked) Things Page 2 Use case - No OT cybersecurity company
Plant Security Services Protecting productivity in the digital era October2017 Restricted www.siemens.com/plant-security-services Internet of (hacked) Things Page 2 Use case - No OT cybersecurity company
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
Disclaimer. This talk vastly over-simplifies things. See notes for full details and resources.
 Greg Kroah-Hartman Disclaimer This talk vastly over-simplifies things. See notes for full details and resources. https://github.com/gregkh/presentation-spectre Spectre Hardware bugs Valid code can be tricked
Greg Kroah-Hartman Disclaimer This talk vastly over-simplifies things. See notes for full details and resources. https://github.com/gregkh/presentation-spectre Spectre Hardware bugs Valid code can be tricked
Let's cyber: hacking, 0days and vulnerability research. PATROKLOS ARGYROUDIS CENSUS S.A.
 Let's cyber: hacking, 0days and vulnerability research PATROKLOS ARGYROUDIS CENSUS S.A. argp@census-labs.com www.census-labs.com Who am I Researcher at CENSUS S.A. - Vulnerability research, reverse engineering,
Let's cyber: hacking, 0days and vulnerability research PATROKLOS ARGYROUDIS CENSUS S.A. argp@census-labs.com www.census-labs.com Who am I Researcher at CENSUS S.A. - Vulnerability research, reverse engineering,
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS
 Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
TRAINING CURRICULUM 2017 Q2
 TRAINING CURRICULUM 2017 Q2 Index 3 Why Security Compass? 4 Discover Role Based Training 6 SSP Suites 7 CSSLP Training 8 Course Catalogue 14 What Can We Do For You? Why Security Compass? Role-Based Training
TRAINING CURRICULUM 2017 Q2 Index 3 Why Security Compass? 4 Discover Role Based Training 6 SSP Suites 7 CSSLP Training 8 Course Catalogue 14 What Can We Do For You? Why Security Compass? Role-Based Training
Automatizing vulnerability research
 Innova&on & Research Symposium Cisco and Ecole Polytechnique 8-9 April 2018 CEDRIC TESSIER INSTRUMENTATION TEAM LEADER / ctessier@quarkslab.com Automatizing vulnerability research to better face new software
Innova&on & Research Symposium Cisco and Ecole Polytechnique 8-9 April 2018 CEDRIC TESSIER INSTRUMENTATION TEAM LEADER / ctessier@quarkslab.com Automatizing vulnerability research to better face new software
How to spend $3.6M on one coding mistake and other fun stuff you can do with $3.6M. Matias Madou Ph.D., Secure Code Warrior
 How to spend $3.6M on one coding mistake and other fun stuff you can do with $3.6M Matias Madou Ph.D., Secure Code Warrior Matias Madou, Ph.D. CTO and Co-Founder Ph.D. in Computer Engineering from Ghent
How to spend $3.6M on one coding mistake and other fun stuff you can do with $3.6M Matias Madou Ph.D., Secure Code Warrior Matias Madou, Ph.D. CTO and Co-Founder Ph.D. in Computer Engineering from Ghent
Software Security Initiatives for Information Security Officers Marco Morana OWASP Cincinnati Chapter OWASP ISSA Cincinnati Chapter Meeting
 Software Security Initiatives for Information Security Officers Marco Morana OWASP Cincinnati Chapter OWASP ISSA Cincinnati Chapter Meeting July 14 th 2010 Copyright 2010 - The OWASP Foundation Permission
Software Security Initiatives for Information Security Officers Marco Morana OWASP Cincinnati Chapter OWASP ISSA Cincinnati Chapter Meeting July 14 th 2010 Copyright 2010 - The OWASP Foundation Permission
TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION
 INFORMATION TECHNOLOGY SECURITY GUIDANCE TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION ITSM.10.189 October 2017 INTRODUCTION The Top 10 Information Technology (IT) Security
INFORMATION TECHNOLOGY SECURITY GUIDANCE TOP 10 IT SECURITY ACTIONS TO PROTECT INTERNET-CONNECTED NETWORKS AND INFORMATION ITSM.10.189 October 2017 INTRODUCTION The Top 10 Information Technology (IT) Security
OWASP InfoSec Romania 2013
 OWASP InfoSec Romania 2013 Secure Development Lifecycle, The good, the bad and the ugly! October 25 th 2013 Martin Knobloch OWASP Netherlands Chapter Leader Applications are about information! 3 pillars
OWASP InfoSec Romania 2013 Secure Development Lifecycle, The good, the bad and the ugly! October 25 th 2013 Martin Knobloch OWASP Netherlands Chapter Leader Applications are about information! 3 pillars
A Strategic Approach to Web Application Security
 A STRATEGIC APPROACH TO WEB APP SECURITY WHITE PAPER A Strategic Approach to Web Application Security Extending security across the entire software development lifecycle The problem: websites are the new
A STRATEGIC APPROACH TO WEB APP SECURITY WHITE PAPER A Strategic Approach to Web Application Security Extending security across the entire software development lifecycle The problem: websites are the new
Building Security Into Applications
 Building Security Into Applications Cincinnati Chapter Meetings Marco Morana Chapter Lead Blue Ash, July 30 th 2008 Copyright 2008 The Foundation Permission is granted to copy, distribute and/or modify
Building Security Into Applications Cincinnati Chapter Meetings Marco Morana Chapter Lead Blue Ash, July 30 th 2008 Copyright 2008 The Foundation Permission is granted to copy, distribute and/or modify
Test Automation. 20 December 2017
 Test Automation 20 December 2017 The problem of test automation Testing has repetitive components, so automation is justified The problem is cost-benefit evaluation of automation [Kaner] Time for: test
Test Automation 20 December 2017 The problem of test automation Testing has repetitive components, so automation is justified The problem is cost-benefit evaluation of automation [Kaner] Time for: test
deep (i) the most advanced solution for managed security services
 deep (i) the most advanced solution for managed security services TM deep (i) suite provides unparalleled threat intelligence and incident response through cutting edge Managed Security Services Cybersecurity
deep (i) the most advanced solution for managed security services TM deep (i) suite provides unparalleled threat intelligence and incident response through cutting edge Managed Security Services Cybersecurity
CS 155: Real-World Security
 CS 155: Real-World Security April 14, 2016 Alex Stamos CSO, Facebook Why are you here? Agenda We are going to discuss: How bugs are found How defense works in the real world We will walk through some:
CS 155: Real-World Security April 14, 2016 Alex Stamos CSO, Facebook Why are you here? Agenda We are going to discuss: How bugs are found How defense works in the real world We will walk through some:
Case Study: The Evolution of EMC s Product Security Office. Dan Reddy, CISSP, CSSLP EMC Product Security Office
 Case Study: The Evolution of EMC s Product Security Office Dan Reddy, CISSP, CSSLP EMC Product Security Office 1 The Evolution of EMC Product Security 2000-2004 2005-2009 2010-Beyond External Drivers Hackers
Case Study: The Evolution of EMC s Product Security Office Dan Reddy, CISSP, CSSLP EMC Product Security Office 1 The Evolution of EMC Product Security 2000-2004 2005-2009 2010-Beyond External Drivers Hackers
UNCLASSIFIED R-1 ITEM NOMENCLATURE FY 2013 OCO
 Exhibit R-2, RDT&E Budget Item Justification: PB 2013 Office of Secretary Of Defense DATE: February 2012 0400: Research,, Test & Evaluation, Defense-Wide BA 3: Advanced Technology (ATD) COST ($ in Millions)
Exhibit R-2, RDT&E Budget Item Justification: PB 2013 Office of Secretary Of Defense DATE: February 2012 0400: Research,, Test & Evaluation, Defense-Wide BA 3: Advanced Technology (ATD) COST ($ in Millions)
Practical Threat Modeling. SecAppDev 2018
 Practical Threat Modeling SecAppDev 2018 Material tinyurl.com/secappdev2018 Sebastien Deleersnyder 5 years developer experience 15+ years information security experience Application security consultant
Practical Threat Modeling SecAppDev 2018 Material tinyurl.com/secappdev2018 Sebastien Deleersnyder 5 years developer experience 15+ years information security experience Application security consultant
Disclaimer. This talk vastly over-simplifies things. See notes for full details and resources.
 Greg Kroah-Hartman Disclaimer This talk vastly over-simplifies things. See notes for full details and resources. https://github.com/gregkh/presentation-spectre Spectre Hardware bugs Valid code can be tricked
Greg Kroah-Hartman Disclaimer This talk vastly over-simplifies things. See notes for full details and resources. https://github.com/gregkh/presentation-spectre Spectre Hardware bugs Valid code can be tricked
Threat Modeling for System Builders and System Breakers!! Dan Copyright 2014 Denim Group - All Rights Reserved
 Threat Modeling for System Builders and System Breakers!! Dan Cornell! @danielcornell Dan Cornell Dan Cornell, founder and CTO of Denim Group Software developer by background (Java,.NET, etc) OWASP San
Threat Modeling for System Builders and System Breakers!! Dan Cornell! @danielcornell Dan Cornell Dan Cornell, founder and CTO of Denim Group Software developer by background (Java,.NET, etc) OWASP San
McAfee Product Security Practices
 McAfee Product Security Practices 12 October 2017 McAfee Public Page 1 of 8 12 October 2017 Expires 12 Apr 2018 Importance of Security At McAfee (formerly Intel Security) we take product security very
McAfee Product Security Practices 12 October 2017 McAfee Public Page 1 of 8 12 October 2017 Expires 12 Apr 2018 Importance of Security At McAfee (formerly Intel Security) we take product security very
Securing Dynamic Data Centers. Muhammad Wajahat Rajab, Pre-Sales Consultant Trend Micro, Pakistan &
 Securing Dynamic Data Centers Muhammad Wajahat Rajab, Pre-Sales Consultant Trend Micro, Pakistan & Afghanistan @WajahatRajab Modern Challenges By 2020, 60% of Digital Businesses will suffer Major Service
Securing Dynamic Data Centers Muhammad Wajahat Rajab, Pre-Sales Consultant Trend Micro, Pakistan & Afghanistan @WajahatRajab Modern Challenges By 2020, 60% of Digital Businesses will suffer Major Service
Cybersecurity Today Avoid Becoming a News Headline
 Cybersecurity Today 2017 Avoid Becoming a News Headline Topics Making News Notable Incidents Current State of Affairs Common Points of Failure Three Quick Wins How to Prepare for and Respond to Cybersecurity
Cybersecurity Today 2017 Avoid Becoming a News Headline Topics Making News Notable Incidents Current State of Affairs Common Points of Failure Three Quick Wins How to Prepare for and Respond to Cybersecurity
Managed Endpoint Defense
 DATA SHEET Managed Endpoint Defense Powered by CB Defense Next-gen endpoint threat detection and response DEPLOY AND HARDEN. Rapidly deploy and optimize endpoint prevention with dedicated security experts
DATA SHEET Managed Endpoint Defense Powered by CB Defense Next-gen endpoint threat detection and response DEPLOY AND HARDEN. Rapidly deploy and optimize endpoint prevention with dedicated security experts
Hardening Attack Vectors to cars by Fuzzing
 Hardening Attack Vectors to cars by Fuzzing AESIN 2015 Ashley Benn, Regional Sales manager 29 th October, 2015 2015 Synopsys, Inc. 1 Today, there are more than 100m lines of code in cars 2015 Synopsys,
Hardening Attack Vectors to cars by Fuzzing AESIN 2015 Ashley Benn, Regional Sales manager 29 th October, 2015 2015 Synopsys, Inc. 1 Today, there are more than 100m lines of code in cars 2015 Synopsys,
Product Security. for Consumer Devices. Anton von Troyer Codenomicon. all rights reserved.
 Product Security Anton von Troyer for Consumer Devices About Codenomicon Founded in Autumn 2001 Commercialized the academic approach built since 1996 Technology leader in security test automation Model-based,
Product Security Anton von Troyer for Consumer Devices About Codenomicon Founded in Autumn 2001 Commercialized the academic approach built since 1996 Technology leader in security test automation Model-based,
Securing Digital Transformation
 September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
The Evolving Threat of Internet Worms
 The Evolving Threat of Internet Worms Jose Nazario, Arbor Networks Why Worm Based Intrusions Relative ease Write once, run everywhere promise can come true Penetration Right past firewalls
The Evolving Threat of Internet Worms Jose Nazario, Arbor Networks Why Worm Based Intrusions Relative ease Write once, run everywhere promise can come true Penetration Right past firewalls
Dr. Stephanie Carter CISM, CISSP, CISA
 Dr. Stephanie Carter CISM, CISSP, CISA Learning Objectives (LO) LO1 Will learn the theological and practitioner definition of cybersecurity LO2 Will learn the dependency between physical and cyber security
Dr. Stephanie Carter CISM, CISSP, CISA Learning Objectives (LO) LO1 Will learn the theological and practitioner definition of cybersecurity LO2 Will learn the dependency between physical and cyber security
NOTHING IS WHAT IT SIEMs: COVER PAGE. Simpler Way to Effective Threat Management TEMPLATE. Dan Pitman Principal Security Architect
 NOTHING IS WHAT IT SIEMs: COVER PAGE Simpler Way to Effective Threat Management TEMPLATE Dan Pitman Principal Security Architect Cybersecurity is harder than it should be 2 SIEM can be harder than it should
NOTHING IS WHAT IT SIEMs: COVER PAGE Simpler Way to Effective Threat Management TEMPLATE Dan Pitman Principal Security Architect Cybersecurity is harder than it should be 2 SIEM can be harder than it should
The Need for Confluence
 The Need for Confluence The Essential Role of Incident Response in Secure Software Development Why do security incidents occur? What is the root cause? Faulty software (more often than not) What is the
The Need for Confluence The Essential Role of Incident Response in Secure Software Development Why do security incidents occur? What is the root cause? Faulty software (more often than not) What is the
Firewalls (IDS and IPS) MIS 5214 Week 6
 Firewalls (IDS and IPS) MIS 5214 Week 6 Agenda Defense in Depth Evolution of IT risk in automated control systems Security Domains Where to put firewalls in an N-Tier Architecture? In-class exercise Part
Firewalls (IDS and IPS) MIS 5214 Week 6 Agenda Defense in Depth Evolution of IT risk in automated control systems Security Domains Where to put firewalls in an N-Tier Architecture? In-class exercise Part
Coding and Unit Testing! The Coding Phase! Coding vs. Code! Coding! Overall Coding Language Trends!
 Requirements Spec. Design Coding and Unit Testing Characteristics of System to be built must match required characteristics (high level) Architecture consistent views Software Engineering Computer Science
Requirements Spec. Design Coding and Unit Testing Characteristics of System to be built must match required characteristics (high level) Architecture consistent views Software Engineering Computer Science
Incident Response Services to Help You Prepare for and Quickly Respond to Security Incidents
 Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
Whiteboard Hacking / Hands-on Threat Modeling. Introduction
 Whiteboard Hacking / Hands-on Threat Modeling Introduction Sebastien Deleersnyder 5 years developer experience 15+ years information security experience Application security consultant Toreon Belgian OWASP
Whiteboard Hacking / Hands-on Threat Modeling Introduction Sebastien Deleersnyder 5 years developer experience 15+ years information security experience Application security consultant Toreon Belgian OWASP
ALTITUDE DOESN T MAKE YOU SAFE. Satcom Direct s Comprehensive Cyber Security Portfolio for Business Aviation
 ALTITUDE DOESN T MAKE YOU SAFE Satcom Direct s Comprehensive Cyber Security Portfolio for Business Aviation CYBER SECURITY IS THE GREATEST THREAT TO EVERY COMPANY IN THE WORLD. IBM CEO GINNI ROMETTY SD
ALTITUDE DOESN T MAKE YOU SAFE Satcom Direct s Comprehensive Cyber Security Portfolio for Business Aviation CYBER SECURITY IS THE GREATEST THREAT TO EVERY COMPANY IN THE WORLD. IBM CEO GINNI ROMETTY SD
Guide to Network Defense and Countermeasures Second Edition. Chapter 2 Security Policy Design: Risk Analysis
 Guide to Network Defense and Countermeasures Second Edition Chapter 2 Security Policy Design: Risk Analysis Objectives Explain the fundamental concepts of risk analysis Describe different approaches to
Guide to Network Defense and Countermeasures Second Edition Chapter 2 Security Policy Design: Risk Analysis Objectives Explain the fundamental concepts of risk analysis Describe different approaches to
KLEE Workshop Feeding the Fuzzers. with KLEE. Marek Zmysłowski MOBILE SECURITY TEAM R&D INSTITUTE POLAND
 Feeding the Fuzzers with KLEE Marek Zmysłowski MOBILE SECURITY TEAM R&D INSTITUTE POLAND This presentation was created with help and commitment of the Samsung R&D Poland Mobile Security team. KLEE and
Feeding the Fuzzers with KLEE Marek Zmysłowski MOBILE SECURITY TEAM R&D INSTITUTE POLAND This presentation was created with help and commitment of the Samsung R&D Poland Mobile Security team. KLEE and
Nebraska CERT Conference
 Nebraska CERT Conference Security Methodology / Incident Response Patrick Hanrion Security Center of Excellence Sr. Security Consultant Agenda Security Methodology Security Enabled Business Framework methodology
Nebraska CERT Conference Security Methodology / Incident Response Patrick Hanrion Security Center of Excellence Sr. Security Consultant Agenda Security Methodology Security Enabled Business Framework methodology
Certified Secure Web Application Engineer
 Certified Secure Web Application Engineer ACCREDITATIONS EXAM INFORMATION The Certified Secure Web Application Engineer exam is taken online through Mile2 s Assessment and Certification System ( MACS ),
Certified Secure Web Application Engineer ACCREDITATIONS EXAM INFORMATION The Certified Secure Web Application Engineer exam is taken online through Mile2 s Assessment and Certification System ( MACS ),
Transportation Security Risk Assessment
 Transportation Security Risk Assessment Presented to: Nuclear Waste Technical Review Board Presented by: Nancy Slater Thompson Office of National Transportation October 13, 2004 Salt Lake City, Utah Introduction
Transportation Security Risk Assessment Presented to: Nuclear Waste Technical Review Board Presented by: Nancy Slater Thompson Office of National Transportation October 13, 2004 Salt Lake City, Utah Introduction
Will your application be secure enough when Robots produce code for you?
 SESSION ID: ASD-W02 Will your application be secure enough when Robots produce code for you? Hasan Yasar Technical Manager, Faculty Member SEI CMU @securelifecycle With the speed of DevOps It is me! I
SESSION ID: ASD-W02 Will your application be secure enough when Robots produce code for you? Hasan Yasar Technical Manager, Faculty Member SEI CMU @securelifecycle With the speed of DevOps It is me! I
The 2017 State of Endpoint Security Risk
 The 2017 State of Endpoint Security Risk Attacks are evolving. As a result, today s organizations are struggling to secure their endpoints, and paying a steep cost for each successful attack. To discover
The 2017 State of Endpoint Security Risk Attacks are evolving. As a result, today s organizations are struggling to secure their endpoints, and paying a steep cost for each successful attack. To discover
ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE
 ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE TABLE OF CONTENTS Overview...3 A Multi-Layer Approach to Endpoint Security...4 Known Attack Detection...5 Machine Learning...6 Behavioral Analysis...7 Exploit
ENTERPRISE ENDPOINT PROTECTION BUYER S GUIDE TABLE OF CONTENTS Overview...3 A Multi-Layer Approach to Endpoint Security...4 Known Attack Detection...5 Machine Learning...6 Behavioral Analysis...7 Exploit
Threat Hunting in Modern Networks. David Biser
 Threat Hunting in Modern Networks David Biser What is Threat Hunting? The act of aggressively pursuing and eliminating cyber adversaries as early as possible in the Cyber Kill Chain. Why Perform Threat
Threat Hunting in Modern Networks David Biser What is Threat Hunting? The act of aggressively pursuing and eliminating cyber adversaries as early as possible in the Cyber Kill Chain. Why Perform Threat
CYBERSECURITY MATURITY ASSESSMENT
 CYBERSECURITY MATURITY ASSESSMENT ANTICIPATE. IMPROVE. PREPARE. The CrowdStrike Cybersecurity Maturity Assessment (CSMA) is unique in the security assessment arena. Rather than focusing solely on compliance
CYBERSECURITY MATURITY ASSESSMENT ANTICIPATE. IMPROVE. PREPARE. The CrowdStrike Cybersecurity Maturity Assessment (CSMA) is unique in the security assessment arena. Rather than focusing solely on compliance
Meeting PCI DSS 3.2 Compliance with RiskSense Solutions
 Meeting PCI DSS 3.2 Compliance with Solutions Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 2018, Inc. What s Changing with PCI DSS? Summary of PCI Business
Meeting PCI DSS 3.2 Compliance with Solutions Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 2018, Inc. What s Changing with PCI DSS? Summary of PCI Business
Web 2.0, Consumerization, and Application Security
 Web 2.0, Consumerization, and Application Security Chenxi Wang, Ph.D. Principal Analyst Forrester Research OWASP, New York City September 25, 2008 Today s enterprises face multitude of challenges Business-driven
Web 2.0, Consumerization, and Application Security Chenxi Wang, Ph.D. Principal Analyst Forrester Research OWASP, New York City September 25, 2008 Today s enterprises face multitude of challenges Business-driven
Advanced Security Tester Course Outline
 Advanced Security Tester Course Outline General Description This course provides test engineers with advanced skills in security test analysis, design, and execution. In a hands-on, interactive fashion,
Advanced Security Tester Course Outline General Description This course provides test engineers with advanced skills in security test analysis, design, and execution. In a hands-on, interactive fashion,
VULNERABILITY ASSESSMENT: SYSTEM AND NETWORK PENETRATION TESTING. Presented by: John O. Adeika Student ID:
 VULNERABILITY ASSESSMENT: SYSTEM AND NETWORK PENETRATION TESTING. Presented by: John O. Adeika Student ID: 000205600 What is Penetration A penetration test, is a method of evaluating the security of a
VULNERABILITY ASSESSMENT: SYSTEM AND NETWORK PENETRATION TESTING. Presented by: John O. Adeika Student ID: 000205600 What is Penetration A penetration test, is a method of evaluating the security of a
SOLUTION BRIEF esentire Risk Advisory and Managed Prevention (RAMP)
 SOLUTION BRIEF esentire Risk Advisory and Managed Prevention (RAMP) Adaptive Cybersecurity at the Speed of Your Business Attackers Evolve. Risk is in Constant Fluctuation. Security is a Never-ending Cycle.
SOLUTION BRIEF esentire Risk Advisory and Managed Prevention (RAMP) Adaptive Cybersecurity at the Speed of Your Business Attackers Evolve. Risk is in Constant Fluctuation. Security is a Never-ending Cycle.
Security. Made Smarter.
 Security. Made Smarter. Your job is to keep your organization safe from cyberattacks. To do so, your team has to review a monumental amount of data that is growing exponentially by the minute. Your team
Security. Made Smarter. Your job is to keep your organization safe from cyberattacks. To do so, your team has to review a monumental amount of data that is growing exponentially by the minute. Your team
Gujarat Forensic Sciences University
 Gujarat Forensic Sciences University Knowledge Wisdom Fulfilment Cyber Security Consulting Services Secure Software Engineering Infrastructure Security Digital Forensics SDLC Assurance Review & Threat
Gujarat Forensic Sciences University Knowledge Wisdom Fulfilment Cyber Security Consulting Services Secure Software Engineering Infrastructure Security Digital Forensics SDLC Assurance Review & Threat
Cyber Security School
 Cyber Cyber Security School FUTURE PROOF Y SECURITY TALENT "The UK needs to tackle the systemic issues at the heart of the Cyber skills shortage..." National Cyber Security Strategy 2016-2021, HM Government
Cyber Cyber Security School FUTURE PROOF Y SECURITY TALENT "The UK needs to tackle the systemic issues at the heart of the Cyber skills shortage..." National Cyber Security Strategy 2016-2021, HM Government
REDUCING RISK THROUGH CODE REVIEW. Gary Robinson (CISSP) OWASP
 REDUCING RISK THROUGH CODE REVIEW Gary Robinson (CISSP) OWASP WHAT ARE WE GOING TO DISCUSS Suggestions and practices for moving secure SDLC governance to the Code Review gate Methodologies brought together
REDUCING RISK THROUGH CODE REVIEW Gary Robinson (CISSP) OWASP WHAT ARE WE GOING TO DISCUSS Suggestions and practices for moving secure SDLC governance to the Code Review gate Methodologies brought together
The Perfect Storm Cyber RDT&E
 The Perfect Storm Cyber RDT&E NAVAIR Public Release 2015-87 Approved for public release; distribution unlimited Presented to: ITEA Cyber Workshop 25 February 2015 Presented by: John Ross NAVAIR 5.4H Cyberwarfare
The Perfect Storm Cyber RDT&E NAVAIR Public Release 2015-87 Approved for public release; distribution unlimited Presented to: ITEA Cyber Workshop 25 February 2015 Presented by: John Ross NAVAIR 5.4H Cyberwarfare
May 14, :30PM to 2:30PM CST. In Plain English: Cybersecurity and IT Exam Expectations
 May 14, 2018 1:30PM to 2:30PM CST In Plain English: Cybersecurity and IT Exam Expectations Options to Join Webinar and audio Click on the link: https://www.webcaster4.com/webcast/page/584/24606 Choose
May 14, 2018 1:30PM to 2:30PM CST In Plain English: Cybersecurity and IT Exam Expectations Options to Join Webinar and audio Click on the link: https://www.webcaster4.com/webcast/page/584/24606 Choose
Cybersecurity in Government
 Cybersecurity in Government Executive Development Course: Digital Government Ng Lup Houh, Principal Cybersecurity Specialist Cybersecurity Group 03 April 2018 Agenda Cyber Threats & Vulnerabilities Cyber
Cybersecurity in Government Executive Development Course: Digital Government Ng Lup Houh, Principal Cybersecurity Specialist Cybersecurity Group 03 April 2018 Agenda Cyber Threats & Vulnerabilities Cyber
Six Weeks to Security Operations The AMP Story. Mike Byrne Cyber Security AMP
 Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
Secure Product Development With Rapid Start Get started now and launch your secure product on-time. Hal Aldridge
 Secure Product Development With Rapid Start Get started now and launch your secure product on-time Hal Aldridge Secure Product Development With Rapid Start applications that communicate with Cloud services.
Secure Product Development With Rapid Start Get started now and launch your secure product on-time Hal Aldridge Secure Product Development With Rapid Start applications that communicate with Cloud services.
Security activities during development
 Secure Programming Lecture 9: Secure Development David Aspinall, Informatics @ Edinburgh 12th February 2016 Recap We ve looked in detail at two important vulnerability classes: overflows, stack and heap
Secure Programming Lecture 9: Secure Development David Aspinall, Informatics @ Edinburgh 12th February 2016 Recap We ve looked in detail at two important vulnerability classes: overflows, stack and heap
SDLC Maturity Models
 www.pwc.com SDLC Maturity Models SecAppDev 2017 Bart De Win Bart De Win? 20 years of Information Security Experience Ph.D. in Computer Science - Application Security Author of >60 scientific publications
www.pwc.com SDLC Maturity Models SecAppDev 2017 Bart De Win Bart De Win? 20 years of Information Security Experience Ph.D. in Computer Science - Application Security Author of >60 scientific publications
Computer Security Course. Midterm Review
 Computer Security Course. Dawn Song Midterm Review In class: Logistics On time: 4:10-5:30pm Wed 1 8x11 page cheat sheet allowed Special requirements: see TA Part I, II, III Scope Software Security Secure
Computer Security Course. Dawn Song Midterm Review In class: Logistics On time: 4:10-5:30pm Wed 1 8x11 page cheat sheet allowed Special requirements: see TA Part I, II, III Scope Software Security Secure
Software Architectural Risk Analysis (SARA): SSAI Roadmap
 Software Architectural Risk Analysis (SARA): SSAI Roadmap Frédéric Painchaud DRDC Valcartier / Systems of Systems November 2010 Agenda Introduction Software Architectural Risk Analysis Linking to SSAI
Software Architectural Risk Analysis (SARA): SSAI Roadmap Frédéric Painchaud DRDC Valcartier / Systems of Systems November 2010 Agenda Introduction Software Architectural Risk Analysis Linking to SSAI
