Empower your phone to open new doors
|
|
|
- Bennett Fleming
- 6 years ago
- Views:
Transcription
1 Empower your phone to open new doors Introducing BlueDiamond Mobile
2 Unmatched experience in mobile applications BlueDiamond Mobile leverages United Technologies Corporation s 17 years of experience developing mobile credentialing technology. With over 1,000,000 locking devices deployed across multiple industries including Energy, Financial, Hospitality and Real Estate United Technologies is well-versed in cloud-based key credentialing and has been a Bluetooth technology leader since 2010.
3 Mobilize your access control As smartphones and tablets become central to everyday life, Lenel is leveraging new technologies to provide access control. BlueDiamond Mobile delivers a smart alternative to plastic badges, offering greater convenience without compromising security. Since people are rarely without their phones, this solution gives them another access option in addition to their keycards. Benefits across the board Unlike many other solutions, BlueDiamond Mobile credentials can be allocated to new phones or people as needed, and can be remotely deactivated. And since smartphones can require a security code or biometric for access as well as possession of the phone, app, and downloaded credential, the solution can provide multi-factor authentication. For an additional layer of protection, BlueDiamond Mobile credentials are automatically deactivated if not periodically refreshed by the cloud server. This helps provide enhanced security by ensuring deactivated credentials are removed from deauthorized devices. BlueDiamond Mobile readers support mobile and wearable devices including ios devices, Apple Watch and Android along with a wide range of traditional proximity and smart cards. For administrators, this means simplified credential management with no procurement, storage, handling, shipping or printing of physical badges. It s just one more way BlueDiamond Mobile is ideally suited for multiple applications and venues in today s enterprise environments.
4 A comprehensive system for mobile credentials The complete BlueDiamond Mobile offering includes the BlueDiamond Mobile smartphone app, BlueDiamond Mobile BlueTooth /RFID readers and BlueDiamond Mobile credentials, all tied together by the cloud server. These components tightly integrate with Lenel s industry-leading OnGuard security management system, allowing one-click issuance and management of mobile credentials. 1. With a single click, the OnGuard administrator issues a virtual credential to a user. 2a. OnGuard automatically s a badge invitation to the cardholder and sends the badge number information to the BlueDiamond cloud server. 2b. At the same time, OnGuard automatically sends the user s badge number and access assignments to a Lenel controller. INVITE 3. The user receives an with a link to download the BlueDiamond Mobile app, as well as an authorization code to activate the credential. The code is periodically refreshed by the cloud server and automatically deactivated when requested through OnGuard, or if not refreshed by the cloud server. 4. As the user approaches an access point, readers are detected and displayed on his or her smartphone or watch. The user taps the desired reader icon to show intent to enter that door. 5. The app authenticates to the reader, and the OnGuard Badge ID is transferred to the access panel. Authorization is granted or denied by the Lenel controller based on OnGuard access levels.
5 Mini-Mullion Form Factor Single Gang Form Factor Single Gang with Backlit Keypad Bluetooth add-on for existing readers Readers that support Bluetooth and beyond For completely flexible migration to mobile credentialing, BlueDiamond readers work with both existing badges and mobile devices, and include a wide range of options that support Bluetooth 4.0 Low Energy. All BlueDiamond Mobile readers feature a sleek, compact design and durable, proven electronics. A special version of the BlueDiamond Mobile reader can be hidden in a wall or ceiling or installed next to an existing reader without replacing it. This add-on reader provides Bluetooth capability to most existing installations, allowing you to protect your investment in current readers and badges. Supporting simple configuration The BlueDiamond Mobile Toolkit is a Windows app used by the installer and designed to make deployment and configuration of BlueDiamond Mobile readers easy and convenient. Using a Bluetooth dongle to communicate to the reader, the app can run on Windows PCs, laptops or tablets. The toolkit also connects readers to the cloud, with reader names and details loaded into the service for quick, efficient management. Technologies supported include: Smart Card (13.56 MHz) Mifare DESFire, Mifare, ISO and ISO Card Serial Number Proximity (125 khz) HID Proximity, CE/CASI Proxlite and AWID Proximity Reader Output OSDP, OSDP Secure Channel and Weigand High Frequency DESFire EV1 Application Mifare Classic Sector ISO 14443A Serial Number ISO Serial Number Low Frequency HID Proximity AWID Prox LenelProx Proxlite
6 Lenel is a global leader in advanced security systems and services, developing innovative solutions to protect buildings, people and assets. Incorporating open architecture and third-party interfacing, Lenel s enterprise software manages multiple best-in-class systems to provide a single, seamless security solution for customers worldwide. Lenel is a part of UTC Climate, Controls & Security, a unit of United Technologies Corporation a leading provider to the aerospace and building systems industries worldwide. lenel.com Specifications subject to change without notice United Technologies Corporation. All rights reserved. All trademarks are the property of their respective owners. Lenel is a part of UTC Climate, Controls & Security, a unit of United Technologies Corporation /08 (GSP-2020)
Empower your phone to open new doors
 Empower your phone to open new doors Introducing Lenel BlueDiamond Unmatched experience in mobile credentialing BlueDiamond leverages United Technologies Corporation s 17 years of experience developing
Empower your phone to open new doors Introducing Lenel BlueDiamond Unmatched experience in mobile credentialing BlueDiamond leverages United Technologies Corporation s 17 years of experience developing
Powering the enterprise-grade mobile access experience.
 Brochure Mobile Reader Pro The new standard for mobile access. Powering the enterprise-grade mobile access experience. Finally, a mobile access solution that integrates seamlessly with existing access
Brochure Mobile Reader Pro The new standard for mobile access. Powering the enterprise-grade mobile access experience. Finally, a mobile access solution that integrates seamlessly with existing access
iclass SE Platform Solutions The New Standard in Access Control
 iclass SE Platform Solutions The New Standard in Access Control iclass SE Platform iclass SE SOLUTIONS Next generation access control solutions for increased security, adaptability, and enhanced performance.
iclass SE Platform Solutions The New Standard in Access Control iclass SE Platform iclass SE SOLUTIONS Next generation access control solutions for increased security, adaptability, and enhanced performance.
New Product Announcement
 New Product Announcement EntraPass v7.30 Software Tyco Security Products is pleased to announce version 7.30 of Kantech s flagship EntraPass security management system software. We continue to build upon
New Product Announcement EntraPass v7.30 Software Tyco Security Products is pleased to announce version 7.30 of Kantech s flagship EntraPass security management system software. We continue to build upon
Identiv FICAM Readers
 Identiv FICAM Readers Ordering Guide August 2017 Table of Contents Overview.....1 Basic FICAM Implementation.....3 Migration Strategies... 4 Perimeter Access... 4 Update Readers and Controllers... 4 Ad
Identiv FICAM Readers Ordering Guide August 2017 Table of Contents Overview.....1 Basic FICAM Implementation.....3 Migration Strategies... 4 Perimeter Access... 4 Update Readers and Controllers... 4 Ad
Access control made for the modern world
 Access control made for the modern world TruPortal delivers user-friendly operation while expanding features and functionality to meet more application needs Effective, intuitive access control for today
Access control made for the modern world TruPortal delivers user-friendly operation while expanding features and functionality to meet more application needs Effective, intuitive access control for today
Identiv TS Readers. Ordering Guide. October 2016
 Identiv TS Readers Ordering Guide October 2016 Table of Contents Introduction... 3 Identiv TS Readers Description... 3 TS Reader Ordering Processes... 5 Installation and User Manual... 9 Compliance and
Identiv TS Readers Ordering Guide October 2016 Table of Contents Introduction... 3 Identiv TS Readers Description... 3 TS Reader Ordering Processes... 5 Installation and User Manual... 9 Compliance and
Readers and Credentials. from Security Technologies
 Readers and Credentials from Security Technologies Simplifying the security industry like never before. Ingersoll Rand s aptiq and XceedID readers and credentials not only feature cutting-edge security
Readers and Credentials from Security Technologies Simplifying the security industry like never before. Ingersoll Rand s aptiq and XceedID readers and credentials not only feature cutting-edge security
Mobile Access is the Killer App The Path to Flexible, Secure Credentials Brandon Arcement Senior Director, Product Marketing April 8, 2019
 Powering the trusted identities of the world s people, places & things Mobile Access is the Killer App The Path to Flexible, Secure Credentials Brandon Arcement Senior Director, Product Marketing April
Powering the trusted identities of the world s people, places & things Mobile Access is the Killer App The Path to Flexible, Secure Credentials Brandon Arcement Senior Director, Product Marketing April
Readers and credentials
 Readers and Simplifying the security industry like never before. Allegion s aptiq and XceedID readers and not only feature cutting-edge security technology, but are transforming basic access control products
Readers and Simplifying the security industry like never before. Allegion s aptiq and XceedID readers and not only feature cutting-edge security technology, but are transforming basic access control products
Improving the Student Experience with a Unified Credential. Jeff Staples VP Market Development Blackboard Transact
 Improving the Student Experience with a Unified Credential Jeff Staples VP Market Development Blackboard Transact 93% High school students who say campus technology is a key factor in their college selection
Improving the Student Experience with a Unified Credential Jeff Staples VP Market Development Blackboard Transact 93% High school students who say campus technology is a key factor in their college selection
New Product Announcement. Flexible iosmart Card Readers and Cards
 New Product Announcement Flexible iosmart Card Readers and Cards Tyco Security Products is pleased to announce Kantech iosmart Card Readers and Cards. Based on MIFARE Plus, Kantech s iosmart Card Readers
New Product Announcement Flexible iosmart Card Readers and Cards Tyco Security Products is pleased to announce Kantech iosmart Card Readers and Cards. Based on MIFARE Plus, Kantech s iosmart Card Readers
Overview. Premium Data Sheet. DigitalPersona. DigitalPersona s Composite Authentication transforms the way IT
 DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
STid presents the new upgradable range. identify. touch. control
 identify. touch. control 18 STid presents the new upgradable range of High Security card readers that use RFID, MIFARE and Bluetooth Smart (Low Energy) technologies. Architect Blue is a secure and user-friendly
identify. touch. control 18 STid presents the new upgradable range of High Security card readers that use RFID, MIFARE and Bluetooth Smart (Low Energy) technologies. Architect Blue is a secure and user-friendly
Beyond Payment: Secure NFC applications and their relation to RFID
 Powering the trusted identities of the world s people, places & things Beyond Payment: Secure NFC applications and their relation to RFID Richard Aufreiter, Director Product Management - IDT June 27, 2017
Powering the trusted identities of the world s people, places & things Beyond Payment: Secure NFC applications and their relation to RFID Richard Aufreiter, Director Product Management - IDT June 27, 2017
Student ID card and campus security solutions. Colleges and universities
 Student ID card and campus security solutions Colleges and universities Student ID card and campus security solutions for colleges and universities College students today expect convenience. They want
Student ID card and campus security solutions Colleges and universities Student ID card and campus security solutions for colleges and universities College students today expect convenience. They want
multiclass MHz Contactless and 125 khz Proximity Cards and Readers
 multiclass 13.56 MHz Contactless and 125 khz Proximity Cards and Readers With our unique card technology read selection feature, customers have endless card management flexibility, with security and simplicity.
multiclass 13.56 MHz Contactless and 125 khz Proximity Cards and Readers With our unique card technology read selection feature, customers have endless card management flexibility, with security and simplicity.
Multi Card Technology
 PRX-TSEC tsec Card Reader Sleek and stylish, and with a range of optional features, the tsec series has a solution for everyone. Available in three sizes, multiple card capabilities, with an optional keypad,
PRX-TSEC tsec Card Reader Sleek and stylish, and with a range of optional features, the tsec series has a solution for everyone. Available in three sizes, multiple card capabilities, with an optional keypad,
Logical Access How to Order Guide D00538, Release E.5 September 2018
 Logical Access How to Order Guide D00538, Release E.5 September 2018 The most current version of this document is available for download at: https://www.hidglobal.com/document-library Register and check
Logical Access How to Order Guide D00538, Release E.5 September 2018 The most current version of this document is available for download at: https://www.hidglobal.com/document-library Register and check
aptiq Multi-technology readers Overview Features and benefits Accommodates interior, exterior, metal, and non-metal installation environments
 aptiq Multi-technology readers Overview Features and benefits aptiq multi-technology readers by Allegion are designed to simplify your access control solutions. Transition your system from proximity to
aptiq Multi-technology readers Overview Features and benefits aptiq multi-technology readers by Allegion are designed to simplify your access control solutions. Transition your system from proximity to
ACCESS CONTROL Products 2017
 Page 1 of 8 NESS Access Controllers 101-102 NESS MCP-040 ACCESS CONTROLLER Including 12V 6A power supply and high-tech metal housing Supports 4 x Wiegand Readers Supports 8 x RS-485 Readers 4 Lock Outputs
Page 1 of 8 NESS Access Controllers 101-102 NESS MCP-040 ACCESS CONTROLLER Including 12V 6A power supply and high-tech metal housing Supports 4 x Wiegand Readers Supports 8 x RS-485 Readers 4 Lock Outputs
The Next Generation of Credential Technology
 The Next Generation of Credential Technology Seos Credential Technology from HID Global The Next Generation of Credential Technology Seos provides the ideal mix of security and flexibility for any organization.
The Next Generation of Credential Technology Seos Credential Technology from HID Global The Next Generation of Credential Technology Seos provides the ideal mix of security and flexibility for any organization.
Solution. Imagine... a New World of Authentication.
 A Solution Imagine... a New World of Authentication. Imagine a World Where Passwords can t be hacked People can t share credentials Users can t pretend to be someone else Where authentication is more Secure
A Solution Imagine... a New World of Authentication. Imagine a World Where Passwords can t be hacked People can t share credentials Users can t pretend to be someone else Where authentication is more Secure
iclass SE How to Order Guide
 iclass SE How to Order Guide D0055, Release D. December 0 The most current version of this document is available for download at: https://www.hidglobal.com/document-library To check order status go to:
iclass SE How to Order Guide D0055, Release D. December 0 The most current version of this document is available for download at: https://www.hidglobal.com/document-library To check order status go to:
USB Enrollment Reader
 USB Enrollment Reader Keri Part Number - RDR-ENR1 The RF Ideas pcprox Plus is a cutting edge USB enrollment reader that is capable of reading both 125KHz proximity cards and 13.56MHz contactless cards
USB Enrollment Reader Keri Part Number - RDR-ENR1 The RF Ideas pcprox Plus is a cutting edge USB enrollment reader that is capable of reading both 125KHz proximity cards and 13.56MHz contactless cards
iclass SE How to Order Guide
 iclass SE How to Order Guide D0055, Release E.0 November 05 The most current version of this document is available for download at: https://www.hidglobal.com/document-library To check order status go to:
iclass SE How to Order Guide D0055, Release E.0 November 05 The most current version of this document is available for download at: https://www.hidglobal.com/document-library To check order status go to:
ABOUT CIVINTEC PLATFORM PRODUCT RANGE CIVINTEC GLOBAL. World Leading OEM/ODM Designer & Manufacturer
 CIVINTEC GLOBAL 01 World Leading OEM/ODM Designer & Manufacturer ABOUT CIVINTEC CIVINTEC is the world leading designer and manufacturer of smart card terminals and devices, established in 2006 and focusing
CIVINTEC GLOBAL 01 World Leading OEM/ODM Designer & Manufacturer ABOUT CIVINTEC CIVINTEC is the world leading designer and manufacturer of smart card terminals and devices, established in 2006 and focusing
New Product Announcement: AC2000 v7.1 Integrations
 New Product Announcement: AC2000 v7.1 Integrations CEM Systems is pleased to announce the release of the latest integrations update for AC2000 v7.1 suite of access control and security management software
New Product Announcement: AC2000 v7.1 Integrations CEM Systems is pleased to announce the release of the latest integrations update for AC2000 v7.1 suite of access control and security management software
BluePass 2-N-1 BluePass Multi-Tech Reader Manual. User s Guide. Copyright 2018 Nortek Security and Control LLC P/N: X16
 BluePass 2-N-1 BluePass Multi-Tech Reader Manual User s Guide P/N: 10019180 X16 Contents Overview...ii Setting up Your Dealer Portal Account...ii Setting Up your Organization and Readers... 1 Setting up
BluePass 2-N-1 BluePass Multi-Tech Reader Manual User s Guide P/N: 10019180 X16 Contents Overview...ii Setting up Your Dealer Portal Account...ii Setting Up your Organization and Readers... 1 Setting up
Biometric Technology
 Biometric Technology Contents Biometric Technology M2SYS is a leading global provider of biometric technology and software solutions with 16 years of real-world experience. Our experience enables us to
Biometric Technology Contents Biometric Technology M2SYS is a leading global provider of biometric technology and software solutions with 16 years of real-world experience. Our experience enables us to
Sphinx Feature List. Summary. Windows Logon Features. Card-secured logon to Windows. End-user managed Windows logon data
 Sphinx List Summary Version Order # Included software components Sphinx Enterprise S-30 Install Sphinx Logon Manager software and desktop card readers on end-user computers. Pre-configured Sphinx CardMaker
Sphinx List Summary Version Order # Included software components Sphinx Enterprise S-30 Install Sphinx Logon Manager software and desktop card readers on end-user computers. Pre-configured Sphinx CardMaker
Logical Access How to Order Guide
 Logical Access How to Order Guide D00538, Release E.3 July 2017 The most current version of this document is available for download at: https://www.hidglobal.com/document-library Register and check your
Logical Access How to Order Guide D00538, Release E.3 July 2017 The most current version of this document is available for download at: https://www.hidglobal.com/document-library Register and check your
hidglobal.com HID ActivOne USER FRIENDLY STRONG AUTHENTICATION
 HID ActivOne USER FRIENDLY STRONG AUTHENTICATION We understand IT security is one of the TOUGHEST business challenges today. HID Global is your trusted partner in the fight against data breach due to misused
HID ActivOne USER FRIENDLY STRONG AUTHENTICATION We understand IT security is one of the TOUGHEST business challenges today. HID Global is your trusted partner in the fight against data breach due to misused
Enabling Compliance for Physical and Cyber Security in Mobile Devices
 Enabling Compliance for Physical and Cyber Security in Mobile Devices Brandon Arcement & Chip Epps HID Global Sept 12, 2016 1630-1730 ET Agenda Smart Devices vs. Traditional Cards Mobility Infrastructure
Enabling Compliance for Physical and Cyber Security in Mobile Devices Brandon Arcement & Chip Epps HID Global Sept 12, 2016 1630-1730 ET Agenda Smart Devices vs. Traditional Cards Mobility Infrastructure
Bluetooth mobile solutions APPLICATION NOTE / FAQ. Page 1 on 24
 Bluetooth mobile solutions APPLICATION NOTE / FAQ Page 1 on 24 Table of Contents I. Introduction... 5 II. Bluetooth Smart technology General principles... 5 III. Frequently Asked Questions... 5 A. STid
Bluetooth mobile solutions APPLICATION NOTE / FAQ Page 1 on 24 Table of Contents I. Introduction... 5 II. Bluetooth Smart technology General principles... 5 III. Frequently Asked Questions... 5 A. STid
S700e Intelligent IP Reader S700 Exit Reader
 New Product Announcement: S700e Intelligent IP Reader S700 Exit Reader CEM Systems is pleased to announce the release of the S700e and companion S700 Exit Reader for use with the AC2000 suite of access
New Product Announcement: S700e Intelligent IP Reader S700 Exit Reader CEM Systems is pleased to announce the release of the S700e and companion S700 Exit Reader for use with the AC2000 suite of access
pivclass How to Order Guide
 pivclass How to Order Guide D00546, B.3 January 2014 The most current version of this document is available for download at http://www.hidglobal.com > Government > PIV & FIPS Solutions. To check order
pivclass How to Order Guide D00546, B.3 January 2014 The most current version of this document is available for download at http://www.hidglobal.com > Government > PIV & FIPS Solutions. To check order
VANDERBILT PRODUCT CATALOGUE
 VANDERBILT PRODUCT CATALOGUE Panels & Keypads Standalone single- Door Solutions Readers & Controllers ACTsmart Readers & Controller Flush or surface mounted digital Keypad polycarbonate housing, IP67 Proximity
VANDERBILT PRODUCT CATALOGUE Panels & Keypads Standalone single- Door Solutions Readers & Controllers ACTsmart Readers & Controller Flush or surface mounted digital Keypad polycarbonate housing, IP67 Proximity
Credential Programmer How to Order Guide
 Credential Programmer How to Order Guide D0054, B.2 December 203 The most current version of this document is available for download at: http://www.hidglobal.com/documents/credential_programmer_htog_en.pdf
Credential Programmer How to Order Guide D0054, B.2 December 203 The most current version of this document is available for download at: http://www.hidglobal.com/documents/credential_programmer_htog_en.pdf
Power LogOn s Features - Check List
 s s - Check List Versions The software is available in two versions, to meet the needs of all types and sizes of organizations. The list below indicates the features that are included in each version.
s s - Check List Versions The software is available in two versions, to meet the needs of all types and sizes of organizations. The list below indicates the features that are included in each version.
Connecting to the future ELATEC RFID SYSTEMS
 Connecting to the future ELATEC RFID SYSTEMS ELATEC GmbH Enabling success RFID SYSTEMS Focus on the goal Adaptable to our customer s requirements, Elatec products and technologies are the core that has
Connecting to the future ELATEC RFID SYSTEMS ELATEC GmbH Enabling success RFID SYSTEMS Focus on the goal Adaptable to our customer s requirements, Elatec products and technologies are the core that has
Security Solutions for Mobile Users in the Workplace
 Security Solutions for Mobile Users in the Workplace 1 1 Multitasking means multiple devices for busy end users Introduction Cloud computing helps organizations operate with less infrastructure, reducing
Security Solutions for Mobile Users in the Workplace 1 1 Multitasking means multiple devices for busy end users Introduction Cloud computing helps organizations operate with less infrastructure, reducing
Overcoming Objections to Smartphones as Your Credential
 Overcoming Objections to Smartphones as Your Credential Security Industry Association By Suzi Abell, 3xLOGIC on September 14, 2018 Could the phone replace your access control card or fob? Moore s Law notwithstanding,
Overcoming Objections to Smartphones as Your Credential Security Industry Association By Suzi Abell, 3xLOGIC on September 14, 2018 Could the phone replace your access control card or fob? Moore s Law notwithstanding,
Asure ID 7. C a rd Pers o n aliz at io n S o f twa re
 Asure ID 7 C a rd Pers o n aliz at io n S o f twa re Asure ID 7 Card Personalization Software 1 2 TOOLS AT YOUR FINGERTIPS HID Global software engineers collaborated with usability experts to give Asure
Asure ID 7 C a rd Pers o n aliz at io n S o f twa re Asure ID 7 Card Personalization Software 1 2 TOOLS AT YOUR FINGERTIPS HID Global software engineers collaborated with usability experts to give Asure
Idesco OEM modules. Compact Module: 40,9 x 39,0 mm. Module: 72 x 37,8 x18 mm. 125 khz Prox. 13,56 MHz UID. MIFARE DESFire. MIFARE DESFire LEGIC - 1 -
 : Compact : 40,9 x 39,0 mm 125 khz Prox 13,56 MHz UID LEGIC - 1 - 7 AH EM4102, Sokymat Unique, Hitag2, HIDProx RS-232, Wiegand, USB, Clock&Data, USB Hi on request. 2 FET outputs, 1 General purpose input
: Compact : 40,9 x 39,0 mm 125 khz Prox 13,56 MHz UID LEGIC - 1 - 7 AH EM4102, Sokymat Unique, Hitag2, HIDProx RS-232, Wiegand, USB, Clock&Data, USB Hi on request. 2 FET outputs, 1 General purpose input
L-1 Fingerprint Reader Solutions. V-Flex 4G
 L- Fingerprint Reader Solutions V-Flex 4G 4G Biometric Performance Redefined with a Flexible and Powerful Device to Secure any Size Premises Advanced Features Large Template Storage Capacity (0,000 in
L- Fingerprint Reader Solutions V-Flex 4G 4G Biometric Performance Redefined with a Flexible and Powerful Device to Secure any Size Premises Advanced Features Large Template Storage Capacity (0,000 in
Real-time access control by your side!
 Real-time access control by your side! SMARTair Pro Wireless Online, flexible online control for smart facilities. ASSA ABLOY, the global leader in door opening solutions 1 Be smart in a busy and constantly
Real-time access control by your side! SMARTair Pro Wireless Online, flexible online control for smart facilities. ASSA ABLOY, the global leader in door opening solutions 1 Be smart in a busy and constantly
ML V/24V Electro-Magnetic Internal Door Lock
 www.turnstiles.us / www.entrapass.com / 8641 S. Warhawk Road, Conifer, CO 80433 / 303-670-1099 ML 600 12V/24V Electro-Magnetic Internal Door Lock Powerful electro-magnetic door locks are the most convenient
www.turnstiles.us / www.entrapass.com / 8641 S. Warhawk Road, Conifer, CO 80433 / 303-670-1099 ML 600 12V/24V Electro-Magnetic Internal Door Lock Powerful electro-magnetic door locks are the most convenient
hidglobal.com Still Going Strong SECURITY TOKENS FROM HID GLOBAL
 Still Going Strong SECURITY TOKENS FROM HID GLOBAL Contents Protecting Identities and sensitive data 03 Defining the Right Approach 05 HID Global Authentication Devices 06 HID Global Authentication Ecosystem
Still Going Strong SECURITY TOKENS FROM HID GLOBAL Contents Protecting Identities and sensitive data 03 Defining the Right Approach 05 HID Global Authentication Devices 06 HID Global Authentication Ecosystem
IDCore. Flexible, Trusted Open Platform. financial services & retail. Government. telecommunications. transport. Alexandra Miller
 IDCore Flexible, Trusted Open Platform financial services & retail enterprise > SOLUTION Government telecommunications transport Trusted Open Platform Java Card Alexandra Miller >network identity >smart
IDCore Flexible, Trusted Open Platform financial services & retail enterprise > SOLUTION Government telecommunications transport Trusted Open Platform Java Card Alexandra Miller >network identity >smart
INCREASE APPLICATION SECURITY FOR PCI DSS VERSION 3.1 SUCCESS AKAMAI SOLUTIONS BRIEF INCREASE APPLICATION SECURITY FOR PCI DSS VERSION 3.
 INCREASE APPLICATION SECURITY FOR PCI DSS VERSION 3.1 SUCCESS Protect Critical Enterprise Applications and Cardholder Information with Enterprise Application Access Scope and Audience This guide is for
INCREASE APPLICATION SECURITY FOR PCI DSS VERSION 3.1 SUCCESS Protect Critical Enterprise Applications and Cardholder Information with Enterprise Application Access Scope and Audience This guide is for
The Zebra DsD/rouTe accounting Mobile computing portfolio Zebra Technologies
 The ZEBRA DSD/Route Accounting Mobile Computing Portfolio The ZEBRA DSD/Route Accounting Regardless of how simple or complex your DSD/route accounting applications are or how demanding the environment
The ZEBRA DSD/Route Accounting Mobile Computing Portfolio The ZEBRA DSD/Route Accounting Regardless of how simple or complex your DSD/route accounting applications are or how demanding the environment
Overview. DigitalPersona Logon for Windows Data Sheet. DigitalPersona s Composite Authentication transforms
 DigitalPersona Logon for Windows Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond two-factor
DigitalPersona Logon for Windows Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond two-factor
This is Cansec s 25th anniversary. Many of
 This is Cansec s 25th anniversary. Many of their employees have been there for the entire ride. Something more interesting is that some of their products have been in the field working for the full 25
This is Cansec s 25th anniversary. Many of their employees have been there for the entire ride. Something more interesting is that some of their products have been in the field working for the full 25
Supra ekey 5.0. Quick Guide. Contents. Install the Supra ekey App. Requirements. Steps
 Supra ekey 5.0 Quick Guide These instructions provide a quick overview for how to install and use common features of the Supra ekey 5.0 app for Android and Apple products. Individual user experience may
Supra ekey 5.0 Quick Guide These instructions provide a quick overview for how to install and use common features of the Supra ekey 5.0 app for Android and Apple products. Individual user experience may
EXECUTIVE BRIEF. The Evolution of Cards and Credentials in Physical Access. In this Paper
 Sponsored by The Evolution of Cards and Credentials EXECUTIVE BRIEF In this Paper Despite effective, newer options, many organizations are still using outdated and vulnerable access control technology.
Sponsored by The Evolution of Cards and Credentials EXECUTIVE BRIEF In this Paper Despite effective, newer options, many organizations are still using outdated and vulnerable access control technology.
Printing & Encoding Solutions
 Printing & Encoding Solutions FARGO Direct-to-Card Printers The right choice for easy printing, encoding and/or laminating ID cards across your organization. Versatility meets simplicity The new advanced
Printing & Encoding Solutions FARGO Direct-to-Card Printers The right choice for easy printing, encoding and/or laminating ID cards across your organization. Versatility meets simplicity The new advanced
HID Proximity. 125 khz Cards and Readers ACCESS SECURE IDENTITY
 HID Proximity 125 khz Cards and Readers ACCESS SECURE IDENTITY HID Proximity 125 khz Proximity Cards and Readers For security managers, dealers, integrators and OEMs, HID proximity cards and readers are
HID Proximity 125 khz Cards and Readers ACCESS SECURE IDENTITY HID Proximity 125 khz Proximity Cards and Readers For security managers, dealers, integrators and OEMs, HID proximity cards and readers are
Security Expert Smartcard Reader Mini
 [ MINI ] Security Expert 1 Security Expert Smartcard Reader Mini The Security Expert Smartcard Reader provides a complete multi-technology smart card RFID solution. Compatible with all Wiegand data capable
[ MINI ] Security Expert 1 Security Expert Smartcard Reader Mini The Security Expert Smartcard Reader provides a complete multi-technology smart card RFID solution. Compatible with all Wiegand data capable
Allegion AD-300 Installation Application Note. 1.0 Hardware Requirements. 2.0 Software/Licensing Requirements
 Allegion Schlage AD-300 networked, hardwired locks can be integrated seamlessly with the Doors.NET software when used with the NXT-MSC (Mercury-Powered controllers). You can connect and communicate with
Allegion Schlage AD-300 networked, hardwired locks can be integrated seamlessly with the Doors.NET software when used with the NXT-MSC (Mercury-Powered controllers). You can connect and communicate with
How does it work? The users access right are written on the credential The credential collects informations from offline readers.
 1 30 August 2017 How does it work? I can open door 3 From 8.00 until 18.30 I am lock number 3 My time now is 14.00 on April 2, 2014 I OPEN F9000 Key I write on the card that at 14.00 on April 2 2014 it
1 30 August 2017 How does it work? I can open door 3 From 8.00 until 18.30 I am lock number 3 My time now is 14.00 on April 2, 2014 I OPEN F9000 Key I write on the card that at 14.00 on April 2 2014 it
2N Helios IP Advanced Training
 2N Helios IP Advanced Training Agenda Licensing Features Use scenarios Software Live demo Configuration training Firmware & Licensing Vario/Force/Safety use the same firmware (same binary file); upgrades
2N Helios IP Advanced Training Agenda Licensing Features Use scenarios Software Live demo Configuration training Firmware & Licensing Vario/Force/Safety use the same firmware (same binary file); upgrades
Installing. Download the O365 suite including OneDrive for Business: 1. Open the Google Play Store on your Android device
 Mobile Microsoft OneDrive for Business is a part of Office 365 (O365) and is your private professional document library, it uses O365 to store your work files in the cloud and is designed to make working
Mobile Microsoft OneDrive for Business is a part of Office 365 (O365) and is your private professional document library, it uses O365 to store your work files in the cloud and is designed to make working
Secure Card Reader Authenticators
 Secure Card Reader Authenticators When it comes to card reading security and reliability Merchants, retailers and financial institutions rely on MagTek. Secure card reader authenticators (SCRAs) capture
Secure Card Reader Authenticators When it comes to card reading security and reliability Merchants, retailers and financial institutions rely on MagTek. Secure card reader authenticators (SCRAs) capture
Electronic Access Control Catalogue
 Electronic Access Control Catalogue Issue September 2010 Make the most of your energy 2 Schneider Electric the Single Source for all Your Electronic Access Needs This catalogue presents the electronic
Electronic Access Control Catalogue Issue September 2010 Make the most of your energy 2 Schneider Electric the Single Source for all Your Electronic Access Needs This catalogue presents the electronic
HID Mobile Access. Simple. Secure. Smart.
 HID Mobile Access Simple. Secure. Smart. Physical Access for a Modern Mobile World Physical Access the Smart Way With Mobile Mobile connectivity has changed the way we live, work and play. From smartphones
HID Mobile Access Simple. Secure. Smart. Physical Access for a Modern Mobile World Physical Access the Smart Way With Mobile Mobile connectivity has changed the way we live, work and play. From smartphones
IT Admin User Guide. Knox Developers App (KDA) User Guide v1.0
 IT Admin User Guide Knox Developers App (KDA) User Guide v1.0 December 2017 Samsung Knox Deployment App (KDA) User Guide Copyright Notice Copyright 2017 Samsung Electronics Co., Ltd. All rights reserved.
IT Admin User Guide Knox Developers App (KDA) User Guide v1.0 December 2017 Samsung Knox Deployment App (KDA) User Guide Copyright Notice Copyright 2017 Samsung Electronics Co., Ltd. All rights reserved.
BlackBerry Enterprise Identity
 Datasheet BlackBerry Enterprise Identity The Challenge: Cloud services are critical in today s enterprises, yet a reliance on the cloud comes with real and growing security risks. Enterprises want a simple,
Datasheet BlackBerry Enterprise Identity The Challenge: Cloud services are critical in today s enterprises, yet a reliance on the cloud comes with real and growing security risks. Enterprises want a simple,
MEDIUM ENTERPRISE SOLUTION. TBS TOUCHLESS BIOMETRIC SYSTEMS SWITZERLAND /
 MEDIUM ENTERPRISE SOLUTION TBS TOUCHLESS BIOMETRIC SYSTEMS SWITZERLAND tbs@tbs-biometrics.com / www.tbs-biometrics.com 08/2016 MEDIUM ENTERPRISE SOLUTION Requirements for access and time & attendance solutions
MEDIUM ENTERPRISE SOLUTION TBS TOUCHLESS BIOMETRIC SYSTEMS SWITZERLAND tbs@tbs-biometrics.com / www.tbs-biometrics.com 08/2016 MEDIUM ENTERPRISE SOLUTION Requirements for access and time & attendance solutions
iclass Seos July 2014 Introducing the HID Global iclass Seos Card
 July 2014 iclass Seos Introducing the HID Global iclass Seos Card This whitepaper introduces the HID Global iclass Seos Card. It positions the card as the flagship Genuine HID Credential and articulates
July 2014 iclass Seos Introducing the HID Global iclass Seos Card This whitepaper introduces the HID Global iclass Seos Card. It positions the card as the flagship Genuine HID Credential and articulates
CRESCENDO SERIES Smart Cards. Smart Card Solutions
 CRESCENDO SERIES Smart Cards Smart Card Solutions Crescendo offers the lowest total cost of ownership (TCO) for a combined logical and physical access control solution. Crescendo smart cards allow me to
CRESCENDO SERIES Smart Cards Smart Card Solutions Crescendo offers the lowest total cost of ownership (TCO) for a combined logical and physical access control solution. Crescendo smart cards allow me to
**Enclosed are the changes to your existing price list** **Please Do Not discard your existing Price List**
 Price List Changes What s New/Changed All Products **Enclosed are the changes to your existing price list** **Please Do Not discard your existing Price List** July 0, 07 Changes to the Price List Price
Price List Changes What s New/Changed All Products **Enclosed are the changes to your existing price list** **Please Do Not discard your existing Price List** July 0, 07 Changes to the Price List Price
ACR1255U-J1 Secure Bluetooth NFC Reader
 ACR1255U-J1 Secure Bluetooth NFC Reader Technical Specifications V1.07 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 1.1. Smart Card Reader... 3 1.2. Compact Design...
ACR1255U-J1 Secure Bluetooth NFC Reader Technical Specifications V1.07 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 1.1. Smart Card Reader... 3 1.2. Compact Design...
Introduction to Device Trust Architecture
 Introduction to Device Trust Architecture July 2018 www.globalplatform.org 2018 GlobalPlatform, Inc. THE TECHNOLOGY The Device Trust Architecture is a security framework which shows how GlobalPlatform
Introduction to Device Trust Architecture July 2018 www.globalplatform.org 2018 GlobalPlatform, Inc. THE TECHNOLOGY The Device Trust Architecture is a security framework which shows how GlobalPlatform
Intelligent Access Terminal
 Intelligent Access Terminal A world of possibilities at your fingertips emerald is a multi functional touch screen access terminal with fully integrated biometric* that is revolutionizing the security
Intelligent Access Terminal A world of possibilities at your fingertips emerald is a multi functional touch screen access terminal with fully integrated biometric* that is revolutionizing the security
"How-To-Order" Guide - Bioscrypt Biometric Readers
 "How-To-Order" Guide - Bioscrypt Biometric Readers Bioscrypt, a world renowned manufacturer of Biometric Access Control devices, has been the market leader for biometrics in access control since 2006,
"How-To-Order" Guide - Bioscrypt Biometric Readers Bioscrypt, a world renowned manufacturer of Biometric Access Control devices, has been the market leader for biometrics in access control since 2006,
Put Time Back on your Side
 Access Control Put Time Back on your Side When it comes to ensuring safety, preparing for emergencies and protecting your people and assets, time is of the essence. Avigilon Access Control Manager (ACM)
Access Control Put Time Back on your Side When it comes to ensuring safety, preparing for emergencies and protecting your people and assets, time is of the essence. Avigilon Access Control Manager (ACM)
FACIAL RECOGNITION TERMINAL SYSTEM
 StoneLock is a global leader in designing and manufacturing secure access control solutions. We are proud to build and design the most secure, reliable and user-friendly access control products for both
StoneLock is a global leader in designing and manufacturing secure access control solutions. We are proud to build and design the most secure, reliable and user-friendly access control products for both
Applying biometric authentication to physical access control systems
 Applying biometric authentication to physical access control systems Published on 24 Jul 2018 Over the past few years, biometrics has rapidly expanded into consumer applications, like the financial market
Applying biometric authentication to physical access control systems Published on 24 Jul 2018 Over the past few years, biometrics has rapidly expanded into consumer applications, like the financial market
Smart Payments. Generating a seamless experience in a digital world.
 Smart Payments Generating a seamless experience in a digital world www.infineon.com/payment Trends Rising need for security The trends highlighted opposite are heightening the need for security and performance,
Smart Payments Generating a seamless experience in a digital world www.infineon.com/payment Trends Rising need for security The trends highlighted opposite are heightening the need for security and performance,
Secure Card Reader Authenticators
 Secure Card Reader Authenticators The Evolution of Card Reading Technology: MagneSafe technology has evolved exponentially from its inception in 2006 when it delivered the industry s first secure card
Secure Card Reader Authenticators The Evolution of Card Reading Technology: MagneSafe technology has evolved exponentially from its inception in 2006 when it delivered the industry s first secure card
Electronic Lock System
 Electronic Lock System COPYRIGHT: Information in this document is subject to change without further notice. No part of this document can be reproduced or transmitted in any form or by any means, electronic
Electronic Lock System COPYRIGHT: Information in this document is subject to change without further notice. No part of this document can be reproduced or transmitted in any form or by any means, electronic
Compatibility Chart for GV-AS Controllers
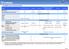 Compatibility Chart for GV-AS Controllers Models GV-AS100 / 110 / 120 GV-AS1010 GV-AS1110 GV-AS210 / 2110 / 2120 / 2121 / 410 / 4110 / 810 / 8110 (Control Panel & Kit) GV-EV48 GV-CS1320 Built-in Reader
Compatibility Chart for GV-AS Controllers Models GV-AS100 / 110 / 120 GV-AS1010 GV-AS1110 GV-AS210 / 2110 / 2120 / 2121 / 410 / 4110 / 810 / 8110 (Control Panel & Kit) GV-EV48 GV-CS1320 Built-in Reader
Secure, cloud-based workflow, alert, and notification platform built on top of Amazon Web Services (AWS)
 Technical Overview Secure, cloud-based workflow, alert, and notification platform built on top of Amazon Web Services (AWS) Copyright 2017 by Bluetooth SIG, Inc. The Bluetooth word mark and logos are owned
Technical Overview Secure, cloud-based workflow, alert, and notification platform built on top of Amazon Web Services (AWS) Copyright 2017 by Bluetooth SIG, Inc. The Bluetooth word mark and logos are owned
Adopting Mobile Credentials Into Your Access Control Infrastructure
 Adopting Mobile Credentials Into Your Access Control Infrastructure Jeremy Earles Credentials Business Leader, Allegion 1 Overview Security Where do we start? Evolution of the credential Convenience The
Adopting Mobile Credentials Into Your Access Control Infrastructure Jeremy Earles Credentials Business Leader, Allegion 1 Overview Security Where do we start? Evolution of the credential Convenience The
BULLETPROOF365 SECURING YOUR IT. Bulletproof365.com
 BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
Access Control Technology Ltd. reserve the right to change the contents of this manual and the system it applies to without prior notice.
 Installation Manual Operating & Installation Instructions This manual refers to the ACTpro elock Hub, a TCP/IP based control unit supporting up to 32 elock doors. Access Control Technology Ltd. reserve
Installation Manual Operating & Installation Instructions This manual refers to the ACTpro elock Hub, a TCP/IP based control unit supporting up to 32 elock doors. Access Control Technology Ltd. reserve
Easily add high-performance UHF RFID and bar code capture to the mobile devices
 AT RFD 8500 Series Easily add high-performance UHF RFID and bar code capture to the mobile devices With the RFD8500 compatible third-party mobile devices, tablets and smart phones with enterprise-class
AT RFD 8500 Series Easily add high-performance UHF RFID and bar code capture to the mobile devices With the RFD8500 compatible third-party mobile devices, tablets and smart phones with enterprise-class
BioStar 2. Web-based Open Integrated Security Platform
 BioStar 2 Web-based Open Integrated Security Platform Centralized System I Access Control and Time & Attendance Management With Suprema's CoreStation and readers, you can build a centralized system, which
BioStar 2 Web-based Open Integrated Security Platform Centralized System I Access Control and Time & Attendance Management With Suprema's CoreStation and readers, you can build a centralized system, which
Thin Desktop - The business case for using a PC or Thin Client as the user access device in a virtualization deployment
 Thin Desktop - The business case for using a PC or Thin Client as the user access device in a virtualization deployment Mike Cardinal General Manager ThinLaunch Software, LLC January, 2009 Contents Executive
Thin Desktop - The business case for using a PC or Thin Client as the user access device in a virtualization deployment Mike Cardinal General Manager ThinLaunch Software, LLC January, 2009 Contents Executive
USER MANUAL Argo 2.0
 USER MANUAL Argo 2.0 2 About this manual Dear Customer, Thanks for choosing this innovative ISEO product, designed and developed following the highest standard of production, for an effective user-friendly
USER MANUAL Argo 2.0 2 About this manual Dear Customer, Thanks for choosing this innovative ISEO product, designed and developed following the highest standard of production, for an effective user-friendly
INDIA The Changing Face of the Workplace: Going Light and Mobile
 An IDC InfoBrief May 2016 Commissioned by Executive Summary In today s hypercompetitive business environment, organizations are pushing for greater efficiencies to drive business growth. The growing diversity
An IDC InfoBrief May 2016 Commissioned by Executive Summary In today s hypercompetitive business environment, organizations are pushing for greater efficiencies to drive business growth. The growing diversity
Single Secure Credential to Access Facilities and IT Resources
 Single Secure Credential to Access Facilities and IT Resources HID PIV Solutions Securing access to premises, applications and networks Organizational Challenges Organizations that want to secure access
Single Secure Credential to Access Facilities and IT Resources HID PIV Solutions Securing access to premises, applications and networks Organizational Challenges Organizations that want to secure access
Enabling Compliance for Physical and Cyber Security in Mobile Devices. Chip Epps & Daniel Bailin HID Global
 Enabling Compliance for Physical and Cyber Security in Mobile Devices Chip Epps & Daniel Bailin HID Global 1 Agenda Managing Identities Traditional cards for PACS and IT Smart Devices Convergence & Compliance
Enabling Compliance for Physical and Cyber Security in Mobile Devices Chip Epps & Daniel Bailin HID Global 1 Agenda Managing Identities Traditional cards for PACS and IT Smart Devices Convergence & Compliance
April 2015 PRICE SCHEDULE A 2.0 Stand-Alone Access Control
 Section A6 This Price Schedule is effective April 1, 2015. Date Page Comment 4-1-15 All April, 2015 Price Schedule update. 5-8-15 3 Removed model 1503. Added models 1509 / 1515 (Pg 15) to the TOC. 8-10-15
Section A6 This Price Schedule is effective April 1, 2015. Date Page Comment 4-1-15 All April, 2015 Price Schedule update. 5-8-15 3 Removed model 1503. Added models 1509 / 1515 (Pg 15) to the TOC. 8-10-15
BULLETPROOF365 SECURING YOUR IT. Bulletproof365.com
 BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
Door release elements and Multitechnology-Reader
 Door release elements and Multitechnology-Reader High secure door release control deister electronic is an established supplier of RFID based readers. doorloxx supports all card technologies in the market
Door release elements and Multitechnology-Reader High secure door release control deister electronic is an established supplier of RFID based readers. doorloxx supports all card technologies in the market
70% of professionals will conduct their work on personal smart devices by 2018 (Source: Gartner)
 Corporate Profile PRINT SIMPLY ANYWHERE Increase mobility and ensure print productivity for your organization PrinterOn is Secure Print, Tracking and Management - with Mobile First PrinterOn is the premier
Corporate Profile PRINT SIMPLY ANYWHERE Increase mobility and ensure print productivity for your organization PrinterOn is Secure Print, Tracking and Management - with Mobile First PrinterOn is the premier
NFC Identity and Access Control
 NFC Identity and Access Control Peter Cattaneo Vice President, Business Development Agenda Basics NFC User Interactions Architecture (F)ICAM Physical Access Logical Access Future Evolution 2 NFC Identity
NFC Identity and Access Control Peter Cattaneo Vice President, Business Development Agenda Basics NFC User Interactions Architecture (F)ICAM Physical Access Logical Access Future Evolution 2 NFC Identity
13.56 MHz Contactless Technology How to Order Guide
 3.56 MHz Contactless Technology How to Order Guide D00529, Release B.8 September 9, 2008 The most current version of this document is always available for download at: www.hidcorp.com/support To check
3.56 MHz Contactless Technology How to Order Guide D00529, Release B.8 September 9, 2008 The most current version of this document is always available for download at: www.hidcorp.com/support To check
