Towards Non-Observable Authentication for Mobile Devices
|
|
|
- Beverly Mills
- 5 years ago
- Views:
Transcription
1 Towards Non-Observable Authentication for Mobile Devices Flynn Wolf UMBC Baltimore, MD 21250, USA Ravi Kuber UMBC Baltimore, MD 21250, USA Adam J. Aviv USNA Annapolis, MD, 21402, USA Abstract When faced with the threat of observational attacks, mobile device users may attempt to mask the graphical interface to authenticate entry, to reduce the likelihood of third parties viewing and recreating the. However, interacting nonvisually with a mobile interface is not without its own challenges. In this paper, we describe a study examining the efficacy of authenticating entry using both PINs and graphical patterns when the mobile interface is outside of the line of sight of third parties and the user (i.e. in the user s pocket, bag, or shielded by the non-dominant hand). A tactile aid intended to provide awareness of the orientation of the mobile device and to support entry is also being evaluated as part of the research. Author Keywords Mobile Device; Non-Observable Interaction; User Authentication. ACM Classification Keywords H.5.2. User Interfaces; Copyright is held by the author/owner. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee. Poster presented at the 12th Symposium on Usable Privacy and Security (SOUPS 2016), June 22-24, 2016, Denver CO. Introduction As private or sensitive information is often stored on or accessed through mobile devices, users often secure entry to these technologies with PINs or graphical
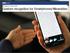
2 Figure 1: Entering while phone is in the trouser pocket. Figure 2: Entering while phone is in a bag near the user. patterns. As mobile devices are used in a variety of environments, users are particularly vulnerable to observational attacks from both physical observers (shoulder surfers) and hidden cameras which may record s, with the purpose of gaining unauthorized access. To better resist the threat of observational attacks, mobile device users attempt to modify their behavior when entering a busy or unfamiliar environment, by masking the screen of the device from onlookers. Examples highlighted in the study by Abdolrahmani et al. [2] include interacting with a mobile device within the pocket or bag (Figures 1 and 2). Others may attempt to shield the screen using their non-dominant hand to reduce the likelihood of finger movements on the interface being observed (Figure 3). However, interacting non-visually with a mobile interface presents a number of challenges, due to the lack of accessible feedback from the device. The user s own view of the graphical interface is masked, often leading to errors being made when an is entered. Non-observable authentication behaviors are rarely examined by mobile interface designers when evaluating their products. In this paper, we describe a study to determine the efficacy of authenticating entry to a mobile device in scenarios where the user may feel that they are at risk of an observational attack. A tactile aid, designed to support the user, is also being evaluated as part of this research. Related Work Researchers have examined the issues associated with observational attacks, and have designed solutions to limit the visibility of the whole or part of screen [10-12], detect the presence of shoulder surfers with the aim of alerting the user to modify their usage behavior accordingly [3,12], and developed solutions to support non-visual interaction to better support security in dynamic contexts [4,5]. Studies have also longitudinally characterized user perception of shoulder surfing as a threat, finding it a credible threat in 17% of real-world unlock actions [6]. If threats are anticipated or detected, workarounds are often used by mobile device users. For example, concealing the mobile device within the pocket or a bag enables users to interact with the interface, highlighted in the study by Abdolrahmani et al. [2], limits the abilities of third parties to view and recreate s. However, errors can be made when attempting to enter data with the absence of visual feedback. To address this issue, researchers have aimed to use tactile feedback to support interaction with eyes-free interfaces. Examples include the study by Hoggan et al. [7] where tactile icons (tactons) were developed to represent events and keys that exist on a mobile interface. Pielot et al. [9] developed PocketMenu, a menu optimized for in-pocket interactions with a touchscreen device. Tactile information is presented to convey the position and state of buttons. Findings from the researchers study showed that PocketMenu outperforms auditory output (VoiceOver) in terms of completion time, selection errors, and subjective usability, making it ideal for interactions where the user is on-the-go. To better support location awareness when non-visually exploring the mobile interface, tactile landmarks have been developed using low-tech tools. Examples include
3 the interface described by McGookin et al., [8], where adhesive plastic bumps have been affixed to a section of the screen enabling users to return to a home location for further interactions. Vibrational feedback indicating the position, such as the center of the phone, may offer considerable potential to users when attempting to orient position on the interface, with the goal of entering authentication data with minimal errors. Study Design The main objective of the study is to determine whether the type or design of impacts entry when the device is outside of the user s and third parties line of sight. For the with tactile condition, participants are asked to locate the center point of the screen. Short tactile bursts presented via the vibration actuators built into the phone (duration: 100ms) indicate the direction towards which the finger should move to locate the center of the screen (e.g. 1 buzz = move left, 2 buzzes = move right). Participants are asked to enter the same patterns and PINs as in the without tactile condition. Levels of accuracy and task time taken will then be compared. Each task is performed three times in randomized order, enabling us to examine whether performance improvements are evident over time. Participants are asked to think-aloud during the process of orienting position, to determine the process taken to support non-visual interaction with a mobile device. Figure 3: Entering while masking phone with non-dominant hand. Twenty four volunteers are being recruited to participate in the within-subjects study. Each participant is introduced to a mobile interface developed for the study, which collects positional data when interacting with a pattern unlock screen and PIN screen, enabling analysis of user movement when nonvisually interacting with the screen. Two tasks are presented, in randomized order. Task 1 The aim of the first task is to determine the efficacy of a tactile aid to support orientation. Two conditions are presented. For the without tactile condition, participants are asked to enter pre-defined s when the mobile device is located in a pocket affixed to their waist, a bag on their shoulder, or when the screen is obscured by the user s non-dominant hand. Task 2 Participants are asked to play the role of adversarial observer, and review a prepared video of a mobile device user attempting to authenticate entry while the device is located in the pocket, bag or shielded by the hand. A similar method to Ali et al. [1] has been adopted. Participants then attempt to identify s. The task may examine the impact of handedness, passcode length, and location on the interface. Questions are then presented to examine the ease with which s can be entered, and to determine the quality of the subjective interaction experience. Current Status and Future Work The study is currently underway. The findings will determine the efficacy of using different methods to authenticate non-visually with a mobile device.
4 Additional conditions may be applied to inquire about interaction with parameters of realistic mobile use, such as walking (e.g. while moving on a treadmill), and handheld devices with differing grip dimensions (e.g. width and depth). Also, differing interaction schemes may be considered, such as those offering a tactile cue at each passcode character entry, which may influence performance measures such as accuracy and completion time, as well as user preference. Insights from the study aim to offer guidance to users when selecting and entering s, with the aim of limiting errors and reducing the cognitive burden on users. Acknowledgements This work was supported by the Office of Naval Research (N ). References 1. Abdullah Ali, Ravi Kuber, and Adam J. Aviv Developing and evaluating a gestural and tactile mobile interface to support user authentication. In Proceedings of iconference' Ali Abdolrahmani, Ravi Kuber, and Amy Hurst An empirical investigation of the situationally-induced impairments experienced by blind mobile device users. In Proceedings of the 13th Web for All Conference (W4A'16). 3. Frederik Brudy, David Ledo, and Saul Greenberg Is anyone looking?: mediating shoulder surfing on public displays (the video). In CHI '14 Extended Abstracts on Human Factors in Computing Systems (CHI EA '14), Alexander De Luca, Emanuel von Zezschwitz, and Heinrich Hußmann Vibrapass: secure authentication based on shared lies. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (CHI '09), Alexander De Luca, Alina Hang, Frederik Brudy, Christian Lindner, and Heinrich Hussmann Touch me once and i know it's you!: implicit authentication based on touch screen patterns. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (CHI '12), Marian Harbach, Emanuel von Zezschwitz, Andreas Fichtner, Alexander De Luca, and Matthew Smith, It s a hard lock life: A field study of smartphone (un) locking behavior and risk perception. In Symposium on Usable Privacy and Security (SOUPS 2014), Eve Hoggan, Stephen A. Brewster, and Jody Johnston Investigating the effectiveness of tactile feedback for mobile touchscreens. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (CHI '08), David McGookin, Stephen Brewster, and WeiWei Jiang Investigating touchscreen accessibility for people with visual impairments. In Proceedings of the 5th Nordic Conference on Human-Computer Interaction: Building Bridges (NordiCHI '08), Martin Pielot, Anastasia Kazakova, Tobias Hesselmann, Wilko Heuten, and Susanne Boll PocketMenu: non-visual menus for touch screen devices. In Proceedings of the 14th International Conference on Human-Computer Interaction with Mobile Devices and Services (MobileHCI '12), George T. Probst Analysis of the effects of privacy filter use on horizontal deviations in posture
5 of VDT operators. Masters Thesis. Virginia Tech, Blacksburg, VA. 11. Peter Tarasewich, Jun Gong, and Richard Conlan Protecting private data in public. In CHI '06 Extended Abstracts on Human Factors in Computing Systems (CHI EA '06), Huiyuan Zhou, Khalid Tearo, Aniruddha Waje, Elham Alghamdi, Thamara Alves, Vinicius Ferreira, Kirstie Hawkey, and Derek Reilly Enhancing Mobile Content Privacy with Proxemics Aware Notifications and Protection. In Proceedings of the 2016 CHI Conference on Human Factors in Computing Systems (CHI '16),
MIBA: Multitouch Image-Based Authentication on Smartphones
 MIBA: Multitouch Image-Based Authentication on Smartphones Daniel Ritter daniel.ritter@uni-ulm.de Florian Schaub florian.schaub@uni-ulm.de Marcel Walch marcel.walch@uni-ulm.de Michael Weber michael.weber@uni-ulm.de
MIBA: Multitouch Image-Based Authentication on Smartphones Daniel Ritter daniel.ritter@uni-ulm.de Florian Schaub florian.schaub@uni-ulm.de Marcel Walch marcel.walch@uni-ulm.de Michael Weber michael.weber@uni-ulm.de
Tactile Web Browsing for Blind Users
 Pre-print: Kuber, R., Yu, W. & O Modhrain, M.S. 2010: Tactile Browsing for the Blind Community. In proceedings of the 5th International Workshop on Haptic Audio Interaction Design (Lecture Notes in Computer
Pre-print: Kuber, R., Yu, W. & O Modhrain, M.S. 2010: Tactile Browsing for the Blind Community. In proceedings of the 5th International Workshop on Haptic Audio Interaction Design (Lecture Notes in Computer
Investigating the User Experience of Smartphone Authentication Schemes - The Role of the Mobile Context
 Investigating the User Experience of Smartphone Authentication Schemes - The Role of the Mobile Context Matthias Baldauf Institute for Information and Process Management University of Applied Sciences
Investigating the User Experience of Smartphone Authentication Schemes - The Role of the Mobile Context Matthias Baldauf Institute for Information and Process Management University of Applied Sciences
Building Augmented You-are-here Maps through Collaborative Annotations for the Visually Impaired
 Building Augmented You-are-here Maps through Collaborative Annotations for the Visually Impaired Limin Zeng, Gerhard Weber Technische Universität Dresden Institut für Angewandte Informatik {limin.zeng,gerhard.weber}@tu-dresden.de
Building Augmented You-are-here Maps through Collaborative Annotations for the Visually Impaired Limin Zeng, Gerhard Weber Technische Universität Dresden Institut für Angewandte Informatik {limin.zeng,gerhard.weber}@tu-dresden.de
LetterScroll: Text Entry Using a Wheel for Visually Impaired Users
 LetterScroll: Text Entry Using a Wheel for Visually Impaired Users Hussain Tinwala Dept. of Computer Science and Engineering, York University 4700 Keele Street Toronto, ON, CANADA M3J 1P3 hussain@cse.yorku.ca
LetterScroll: Text Entry Using a Wheel for Visually Impaired Users Hussain Tinwala Dept. of Computer Science and Engineering, York University 4700 Keele Street Toronto, ON, CANADA M3J 1P3 hussain@cse.yorku.ca
Touchscreen Accessibility in Self-Service Terminals
 114 Touchscreen Accessibility in Self-Service Terminals Elina Jokisuu, Mike McKenna, Andrew W.D. Smith, Phil Day NCR Corporation, Dundee, United Kingdom elina.jokisuu@ncr.com, andrewwd.smith@ncr.com, phil.day@ncr.com
114 Touchscreen Accessibility in Self-Service Terminals Elina Jokisuu, Mike McKenna, Andrew W.D. Smith, Phil Day NCR Corporation, Dundee, United Kingdom elina.jokisuu@ncr.com, andrewwd.smith@ncr.com, phil.day@ncr.com
Interactively Displaying Maps on a Tactile Graphics Display
 Interactively Displaying Maps on a Tactile Graphics Display Bernhard Schmitz and Thomas Ertl Institute for Visualization and Interactive Systems, Universität Stuttgart {Bernhard.Schmitz, Thomas.Ertl}@vis.uni-stuttgart.de
Interactively Displaying Maps on a Tactile Graphics Display Bernhard Schmitz and Thomas Ertl Institute for Visualization and Interactive Systems, Universität Stuttgart {Bernhard.Schmitz, Thomas.Ertl}@vis.uni-stuttgart.de
Exploring Games for Improved Touchscreen Authentication on Mobile Devices
 Exploring Games for Improved Touchscreen Authentication on Mobile Devices Padmaja Scindia pscindia@nyit.edu Jonathan Voris jvoris@nyit.edu New York Institute of Technology Department of Computer Science
Exploring Games for Improved Touchscreen Authentication on Mobile Devices Padmaja Scindia pscindia@nyit.edu Jonathan Voris jvoris@nyit.edu New York Institute of Technology Department of Computer Science
Touch-Screens are Not Tangible: Fusing Tangible Interaction with Touch Glass in Readers for the Blind
 Touch-Screens are Not Tangible: Fusing Tangible Interaction with Touch Glass in Readers for the Blind Yasmine N. El-Glaly* Computer Science yasmineg@vt.edu Francis Quek* Computer Science quek@vt.edu Tonya
Touch-Screens are Not Tangible: Fusing Tangible Interaction with Touch Glass in Readers for the Blind Yasmine N. El-Glaly* Computer Science yasmineg@vt.edu Francis Quek* Computer Science quek@vt.edu Tonya
Evaluating Attack and Defense Strategies for Smartphone PIN Shoulder Surfing
 Evaluating Attack and Defense Strategies for Smartphone PIN Shoulder Surfing Hassan Khan, Urs Hengartner, Daniel Vogel Cheriton School of Computer Science University of Waterloo {h37khan, urs.hengartner,
Evaluating Attack and Defense Strategies for Smartphone PIN Shoulder Surfing Hassan Khan, Urs Hengartner, Daniel Vogel Cheriton School of Computer Science University of Waterloo {h37khan, urs.hengartner,
Dept. of computer Science & Engineering, VelTech Hightech Dr. Rangarajan Dr. Sakunthala Engineering College, Avadi, Chennai 2
 Secured pin entry method for ATM using steganopin and session key methods S. Shanmuga Priya 1*, Ancy Breen W 1, V.S Rajkumar 1, Latha 2 1 Dept. of computer Science & Engineering, VelTech Hightech Dr. Rangarajan
Secured pin entry method for ATM using steganopin and session key methods S. Shanmuga Priya 1*, Ancy Breen W 1, V.S Rajkumar 1, Latha 2 1 Dept. of computer Science & Engineering, VelTech Hightech Dr. Rangarajan
Design and Engineering of Software Applications for Touch Input Collection on Mobile Devices
 Design and Engineering of Software Applications for Touch Input Collection on Mobile Devices Bogdan Gheran MintViz Lab MANSiD Research Center University Ștefan cel Mare of Suceava, ROMANIA E-mail: bogdan.gheran[at]gmail.com
Design and Engineering of Software Applications for Touch Input Collection on Mobile Devices Bogdan Gheran MintViz Lab MANSiD Research Center University Ștefan cel Mare of Suceava, ROMANIA E-mail: bogdan.gheran[at]gmail.com
Thematic Graphical User Authentication: Graphical User Authentication Using Themed Images on Mobile Devices
 Int'l Conf. Security and Management SAM'17 273 Thematic Graphical User Authentication: Graphical User Authentication Using Themed Images on Mobile Devices Joshua Sherfield 1, Cheryl V. Hinds 2 1 Lawrence
Int'l Conf. Security and Management SAM'17 273 Thematic Graphical User Authentication: Graphical User Authentication Using Themed Images on Mobile Devices Joshua Sherfield 1, Cheryl V. Hinds 2 1 Lawrence
Just Gaze and Wave: Exploring the Use of Gaze and Gestures for Shoulder-surfing Resilient Authentication
 Just Gaze and Wave: Exploring the Use of Gaze and Gestures for Shoulder-surfing Resilient Authentication Yasmeen Abdrabou 1,2, Mohamed Khamis 3, Rana Mohamed Eisa 4, Sherif Ismail 1, Amr Elmougy 4 1 German
Just Gaze and Wave: Exploring the Use of Gaze and Gestures for Shoulder-surfing Resilient Authentication Yasmeen Abdrabou 1,2, Mohamed Khamis 3, Rana Mohamed Eisa 4, Sherif Ismail 1, Amr Elmougy 4 1 German
Voronoi Diagrams, Vectors and the Visually Impaired
 Voronoi Diagrams, Vectors and the Visually Impaired Christopher Power Computer Science University of Western Ontario London, ON N6A 5B7 Canada power1@csd.uwo.ca Dawn Gill Epidemiology and Biostatistics
Voronoi Diagrams, Vectors and the Visually Impaired Christopher Power Computer Science University of Western Ontario London, ON N6A 5B7 Canada power1@csd.uwo.ca Dawn Gill Epidemiology and Biostatistics
Revealing Hidden Context Improving Users Mental Models of Personal Firewalls
 University of British Columbia Revealing Hidden Context Improving Users Mental Models of Personal Firewalls Fahimeh Raja Kirstie Hawkey and Konstantin Beznosov 1 Outline Background Windows Vista firewall
University of British Columbia Revealing Hidden Context Improving Users Mental Models of Personal Firewalls Fahimeh Raja Kirstie Hawkey and Konstantin Beznosov 1 Outline Background Windows Vista firewall
Enhancing Click-Draw Based Graphical Passwords Using Multi-Touch on Mobile Phones
 Enhancing Click-Draw Based Graphical Passwords Using Multi-Touch on Mobile Phones Yuxin Meng 1, Wenjuan Li 2,andLam-ForKwok 1 1 Department of Computer Science, City University of Hong Kong, Hong Kong,
Enhancing Click-Draw Based Graphical Passwords Using Multi-Touch on Mobile Phones Yuxin Meng 1, Wenjuan Li 2,andLam-ForKwok 1 1 Department of Computer Science, City University of Hong Kong, Hong Kong,
Accessibility Problems of Blind MHealth Users, a Pilot Study
 Accessibility Problems of Blind MHealth Users, a Pilot Study Indicate Submission Type: Full paper Shrirang Sahasrabudhe University of North Carolina at Greensboro s_sahasr@uncg.edu Rahul Singh, PhD University
Accessibility Problems of Blind MHealth Users, a Pilot Study Indicate Submission Type: Full paper Shrirang Sahasrabudhe University of North Carolina at Greensboro s_sahasr@uncg.edu Rahul Singh, PhD University
TapLock: Exploit Finger Tap Events for Enhancing Attack Resilience of Smartphone Passwords
 TapLock: Exploit Finger Tap Events for Enhancing Attack Resilience of Smartphone Passwords Hongji Yang 1, Lin Chen 1,2, Kaigui Bian 1, Yang Tian 1,FanYe 3, Wei Yan 1, Tong Zhao 1, and Xiaoming Li 1 1 Institute
TapLock: Exploit Finger Tap Events for Enhancing Attack Resilience of Smartphone Passwords Hongji Yang 1, Lin Chen 1,2, Kaigui Bian 1, Yang Tian 1,FanYe 3, Wei Yan 1, Tong Zhao 1, and Xiaoming Li 1 1 Institute
The Shortcut Guide To. Protecting Against Web Application Threats Using SSL. Dan Sullivan
 tm The Shortcut Guide To Protecting Against Web Application Threats Using SSL Chapter 3: Planning, Deploying, and Maintaining SSL Certificates to Protect Against Inf ormation Loss and Build Customer Trust...
tm The Shortcut Guide To Protecting Against Web Application Threats Using SSL Chapter 3: Planning, Deploying, and Maintaining SSL Certificates to Protect Against Inf ormation Loss and Build Customer Trust...
Survival of the Shortest: A Retrospective Analysis of Influencing Factors on Password Composition
 Survival of the Shortest: A Retrospective Analysis of Influencing Factors on Password Composition Emanuel von Zezschwitz, Alexander De Luca, and Heinrich Hussmann University of Munich (LMU), Media Informatics
Survival of the Shortest: A Retrospective Analysis of Influencing Factors on Password Composition Emanuel von Zezschwitz, Alexander De Luca, and Heinrich Hussmann University of Munich (LMU), Media Informatics
Applying Usability to elearning
 Applying Usability to elearning 6 December 08 John Wooden, PhD Director of Usability Services Fredrickson Communications jwooden@fredcomm.com We make information useful! About Fredrickson Communications
Applying Usability to elearning 6 December 08 John Wooden, PhD Director of Usability Services Fredrickson Communications jwooden@fredcomm.com We make information useful! About Fredrickson Communications
Color Code PIN Authentication System Using. Multi-TouchTechnology
 Color Code PIN Authentication System Using Multi-TouchTechnology K. Abinaya 1, T. Pavithra 2, P. Divya 3, S.Hema malini 4 Mrs. S. Hema malini, Associate Professor, Dept. of Computer Science & Engineering,
Color Code PIN Authentication System Using Multi-TouchTechnology K. Abinaya 1, T. Pavithra 2, P. Divya 3, S.Hema malini 4 Mrs. S. Hema malini, Associate Professor, Dept. of Computer Science & Engineering,
A Grid-Based Extension to an Assistive Multimodal Interface
 Pre-print: Strain, P., McAllister, G., Murphy, E., Kuber, R. & Yu, W. 2007: A Grid-Based Extension to an Assistive Multimodal Interface. In Extended Abstracts of on Human Factors in Computing Systems -
Pre-print: Strain, P., McAllister, G., Murphy, E., Kuber, R. & Yu, W. 2007: A Grid-Based Extension to an Assistive Multimodal Interface. In Extended Abstracts of on Human Factors in Computing Systems -
RISKMAN REFERENCE GUIDE TO FEEDBACK MANAGEMENT
 Introduction This reference guide is aimed at Consumer Advocates or Risk/Quality Managers who are responsible for ensuring Feedback notifications have been followed up by the respective Line Managers,
Introduction This reference guide is aimed at Consumer Advocates or Risk/Quality Managers who are responsible for ensuring Feedback notifications have been followed up by the respective Line Managers,
Foundation Level Syllabus Usability Tester Sample Exam
 Foundation Level Syllabus Usability Tester Sample Exam Version 2017 Provided by German Testing Board Copyright Notice This document may be copied in its entirety, or extracts made, if the source is acknowledged.
Foundation Level Syllabus Usability Tester Sample Exam Version 2017 Provided by German Testing Board Copyright Notice This document may be copied in its entirety, or extracts made, if the source is acknowledged.
CPE/CSC 486: Human-Computer Interaction
 CPE/CSC 486: Human-Computer Interaction Franz J. Kurfess Computer Science Department California Polytechnic State University San Luis Obispo, CA, U.S.A. Course Overview Introduction Cognitive Foundations
CPE/CSC 486: Human-Computer Interaction Franz J. Kurfess Computer Science Department California Polytechnic State University San Luis Obispo, CA, U.S.A. Course Overview Introduction Cognitive Foundations
Heuristic Evaluation of Groupware. How to do Heuristic Evaluation of Groupware. Benefits
 Kimberly Tee ketee@ucalgary.ca CPSC 681 Topic Heuristic Evaluation of Groupware Heuristic evaluation [9] is a discount evaluation method for finding usability problems in a singleuser interface design.
Kimberly Tee ketee@ucalgary.ca CPSC 681 Topic Heuristic Evaluation of Groupware Heuristic evaluation [9] is a discount evaluation method for finding usability problems in a singleuser interface design.
MOBILE COMPUTING 2/14/17. System Structure. Context as Implicit Input. explicit input. explicit output. explicit input.
 MOBILE COMPUTING CSE 40814/60814 Spring 2017 System Structure explicit input explicit output Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
MOBILE COMPUTING CSE 40814/60814 Spring 2017 System Structure explicit input explicit output Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
RISKMAN REFERENCE GUIDE TO FEEDBACK MANAGEMENT
 Introduction Close the Feedback Notification This reference guide is aimed at Consumer Advocates or Risk/Quality Managers who are responsible for ensuring Feedback notifications have been followed up by
Introduction Close the Feedback Notification This reference guide is aimed at Consumer Advocates or Risk/Quality Managers who are responsible for ensuring Feedback notifications have been followed up by
Humanistic Multi-Factor Authentication (MFA) Why We Don't Use MFA
 SESSION ID: SEM-M01H Humanistic Multi-Factor Authentication (MFA) Why We Don't Use MFA Sanchari Das Doctoral Candidate Indiana University Bloomington @sancharidecrypt Authentication Technologies Something
SESSION ID: SEM-M01H Humanistic Multi-Factor Authentication (MFA) Why We Don't Use MFA Sanchari Das Doctoral Candidate Indiana University Bloomington @sancharidecrypt Authentication Technologies Something
Touchscreen Biometrics Across Multiple Devices
 Touchscreen Biometrics Across Multiple Devices Tuan Nguyen New York Institute of Technology Computer Science Department tnguye15@nyit.edu Jonathan Voris New York Institute of Technology Computer Science
Touchscreen Biometrics Across Multiple Devices Tuan Nguyen New York Institute of Technology Computer Science Department tnguye15@nyit.edu Jonathan Voris New York Institute of Technology Computer Science
Enhancing KLM (Keystroke-Level Model) to Fit Touch Screen Mobile Devices
 El Batran, Karim Mohsen Mahmoud and Dunlop, Mark (2014) Enhancing KLM (Keystroke-Level Model) to fit touch screen mobile devices. In: Proceedings of the 16th International Conference on Human-Computer
El Batran, Karim Mohsen Mahmoud and Dunlop, Mark (2014) Enhancing KLM (Keystroke-Level Model) to fit touch screen mobile devices. In: Proceedings of the 16th International Conference on Human-Computer
Defending Shoulder Surfing Attacks in Secure Transactions Using Session Key Method
 Defending Shoulder Surfing Attacks in Secure Transactions Using Session Key Method M. R.Divya, A.P.Janani, Abstract To improve the security of the various devices, the graphical password is a memorable
Defending Shoulder Surfing Attacks in Secure Transactions Using Session Key Method M. R.Divya, A.P.Janani, Abstract To improve the security of the various devices, the graphical password is a memorable
VPAT for Apple ipad mini 3
 VPAT for Apple ipad mini 3 The following Voluntary Product Accessibility information refers to the Apple ipad mini 3 running ios 8 or later. For more information on the accessibility features of the ipad
VPAT for Apple ipad mini 3 The following Voluntary Product Accessibility information refers to the Apple ipad mini 3 running ios 8 or later. For more information on the accessibility features of the ipad
Design and Analysis of Shoulder Surfing Resistant PIN based Authentication Mechanisms on Google Glass
 Design and Analysis of Shoulder Surfing Resistant PIN based Authentication Mechanisms on Google Glass Dhruv Kumar Yadav 1, Beatrice Ionascu 2, Sai Vamsi Krishna Ongole 3, Aditi Roy 3, and Nasir Memon 2,3
Design and Analysis of Shoulder Surfing Resistant PIN based Authentication Mechanisms on Google Glass Dhruv Kumar Yadav 1, Beatrice Ionascu 2, Sai Vamsi Krishna Ongole 3, Aditi Roy 3, and Nasir Memon 2,3
Enhancement of User Experience by Task Analysis:A Proposal
 Enhancement of User Experience by Task Analysis:A Proposal Khadija Fyiaz msit09153033@student.uol.edu.pk Aliza Basharat mscs09161007@student.uol.edu.pk Javed Anjum Sheikh Javed.anjum@cs.uol.edu.pk Anam
Enhancement of User Experience by Task Analysis:A Proposal Khadija Fyiaz msit09153033@student.uol.edu.pk Aliza Basharat mscs09161007@student.uol.edu.pk Javed Anjum Sheikh Javed.anjum@cs.uol.edu.pk Anam
MOBILE COMPUTING 2/11/18. System Structure. Context as Implicit Input. explicit input. explicit output. explicit input.
 MOBILE COMPUTING CSE 40814/60814 Spring 2018 System Structure explicit input explicit output Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
MOBILE COMPUTING CSE 40814/60814 Spring 2018 System Structure explicit input explicit output Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
Re-envisioning the Keyboard as a Spatial User Interface Carnegie Mellon University Duncan McIsaac Advisor: Dr. Jennifer Mankoff
 Re-envisioning the Keyboard as a Spatial User Interface Carnegie Mellon University Duncan McIsaac Advisor: Dr. Jennifer Mankoff ABSTRACT Current screen reader technology presents the content of web pages
Re-envisioning the Keyboard as a Spatial User Interface Carnegie Mellon University Duncan McIsaac Advisor: Dr. Jennifer Mankoff ABSTRACT Current screen reader technology presents the content of web pages
Symantec Endpoint Protection Family Feature Comparison
 Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
HSBC Talking ATMs. Instructions and Guidance Handbook
 HSBC Talking ATMs Instructions and Guidance Handbook This document provides detailed instructions and guidance on the use of our Talking ATMs. What is a Talking ATM? A Talking ATM is self-service machine
HSBC Talking ATMs Instructions and Guidance Handbook This document provides detailed instructions and guidance on the use of our Talking ATMs. What is a Talking ATM? A Talking ATM is self-service machine
A Framework for the Development of Distributed Interactive Applications
 A Framework for the Development of Distributed Interactive Applications Luca Frosini HIIS Laboratory ISTI-CNR Via G. Moruzzi, 1 56124 Pisa (Italy) luca.frosini@isti.cnr.it +39 050 621 2602 Marco Manca
A Framework for the Development of Distributed Interactive Applications Luca Frosini HIIS Laboratory ISTI-CNR Via G. Moruzzi, 1 56124 Pisa (Italy) luca.frosini@isti.cnr.it +39 050 621 2602 Marco Manca
Shafiq ur Rehman, Jane-Lisa Coughlan
 Design Aesthetics of Mobile Interface Shafiq ur Rehman, Jane-Lisa Coughlan Abstract Mobiles are considered to be the most frequently used electronic items in world after electricity. It is probably the
Design Aesthetics of Mobile Interface Shafiq ur Rehman, Jane-Lisa Coughlan Abstract Mobiles are considered to be the most frequently used electronic items in world after electricity. It is probably the
Usable Privacy and Security, Fall 2011 Nov. 10, 2011
 Usable Privacy and Security, Fall 2011 Nov. 10, 2011 YoungSeok Yoon (youngseok@cs.cmu.edu) Institute for Software Research School of Computer Science Carnegie Mellon University picture/photo based vs.
Usable Privacy and Security, Fall 2011 Nov. 10, 2011 YoungSeok Yoon (youngseok@cs.cmu.edu) Institute for Software Research School of Computer Science Carnegie Mellon University picture/photo based vs.
ios Accessibility Features
 1. Introduction Apple, since the birth of ios in 2007, has quietly been adding more and more sophisticated accessibility features to its mobile operating system. All of the following features are built
1. Introduction Apple, since the birth of ios in 2007, has quietly been adding more and more sophisticated accessibility features to its mobile operating system. All of the following features are built
IMB Apple Pay - Frequently Asked Questions
 About Apple Pay What is Apple Pay? Apple Pay offers an easy, secure, and private way to pay on iphone, ipad, Apple Watch, and Mac. It enables you to link your IMB Visa Debit card to a eligible Apple Device
About Apple Pay What is Apple Pay? Apple Pay offers an easy, secure, and private way to pay on iphone, ipad, Apple Watch, and Mac. It enables you to link your IMB Visa Debit card to a eligible Apple Device
VPAT for ipad Pro (12.9-inch) (2nd generation)
 VPAT for ipad Pro (12.9-inch) (2nd generation) The following Voluntary Product Accessibility information refers to the ipad Pro (12.9-inch) (2nd generation) running ios 10 or later. For more information
VPAT for ipad Pro (12.9-inch) (2nd generation) The following Voluntary Product Accessibility information refers to the ipad Pro (12.9-inch) (2nd generation) running ios 10 or later. For more information
Toward Spatial Information Awareness Map (SIAM) for the Visually Impaired
 1 ACCV2002: The 5 th Asian Conference on Computer Vision, 23 25 January 2002, Melbourne, Australia. Toward Spatial Information Awareness Map (SIAM) for the Visually Impaired Worapol Pongpech, Mohamed Bennamoun
1 ACCV2002: The 5 th Asian Conference on Computer Vision, 23 25 January 2002, Melbourne, Australia. Toward Spatial Information Awareness Map (SIAM) for the Visually Impaired Worapol Pongpech, Mohamed Bennamoun
Defending Shoulder Surfing Attacks in Secure Transactions using Multi Color Technique
 Defending Shoulder Surfing Attacks in Secure Transactions using Multi Color Technique 1 M.R.Divya, 2 A.P.Janani Department of Computer Science and Engineering, Sri Subramanya College of Engineering and
Defending Shoulder Surfing Attacks in Secure Transactions using Multi Color Technique 1 M.R.Divya, 2 A.P.Janani Department of Computer Science and Engineering, Sri Subramanya College of Engineering and
 www.hollieguard.com @hollie_guard Welcome to your User Guide Launched in October 2015, Hollie Guard is taking the mobile world by storm. With more than 20,000 downloads and users since its release. It
www.hollieguard.com @hollie_guard Welcome to your User Guide Launched in October 2015, Hollie Guard is taking the mobile world by storm. With more than 20,000 downloads and users since its release. It
Strathprints Institutional Repository
 Strathprints Institutional Repository Dunlop, Mark and Komninos, Andreas and Nicol, Emma and Hamilton, Iain (2014) Shake n Tap : a gesture enhanced keyboard for older adults. In: MobileHCI 14. ACM, New
Strathprints Institutional Repository Dunlop, Mark and Komninos, Andreas and Nicol, Emma and Hamilton, Iain (2014) Shake n Tap : a gesture enhanced keyboard for older adults. In: MobileHCI 14. ACM, New
Multi-Color Technique and Session Key Method to Prevent Shoulder Surfing Attacks in Secure Transactions M. R. Divya 1 A. P.
 IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 02, 2015 ISSN (online): 2321-0613 Multi-Color Technique and Session Key Method to Prevent Shoulder Surfing Attacks in Secure
IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 02, 2015 ISSN (online): 2321-0613 Multi-Color Technique and Session Key Method to Prevent Shoulder Surfing Attacks in Secure
Arranging Touch Screen Software Keyboard Split-keys based on Contact Surface
 CHI 21: Work-in-Progress (Spotlight on Posters Days 3 & 4) April 14 15, 21, Atlanta, GA, USA Arranging Touch Screen Software Keyboard Split-keys based on Contact Surface Acknowledgements Part of this work
CHI 21: Work-in-Progress (Spotlight on Posters Days 3 & 4) April 14 15, 21, Atlanta, GA, USA Arranging Touch Screen Software Keyboard Split-keys based on Contact Surface Acknowledgements Part of this work
A Tactile/Haptic Interface Object Reference Model
 A Tactile/Haptic Interface Object Reference Model Jim Carter USERLab, Department of Computer Science University of Saskatchewan Saskatoon, SK, CANADA (306) 966-4893 carter@cs.usask.ca ABSTRACT In this
A Tactile/Haptic Interface Object Reference Model Jim Carter USERLab, Department of Computer Science University of Saskatchewan Saskatoon, SK, CANADA (306) 966-4893 carter@cs.usask.ca ABSTRACT In this
Mobile Device Features - Android and ios
 Mobile Device Features - Android and ios Introduction In this lab, you will set the autorotation, brightness, and turn GPS on and off. Recommended Equipment The following equipment is required for this
Mobile Device Features - Android and ios Introduction In this lab, you will set the autorotation, brightness, and turn GPS on and off. Recommended Equipment The following equipment is required for this
A Non-Visual Approach To Improving Collaboration Between Blind And Sighted Internet Users
 A Non-Visual Approach To Improving Collaboration Between Blind And Sighted Internet Users Ravi Kuber, Wai Yu & Graham McAllister Sonic Arts Research Centre & Virtual Engineering Centre Queen s University
A Non-Visual Approach To Improving Collaboration Between Blind And Sighted Internet Users Ravi Kuber, Wai Yu & Graham McAllister Sonic Arts Research Centre & Virtual Engineering Centre Queen s University
SOC-2 Requirement Solution Brief. EventTracker 8815 Centre Park Drive, Columbia MD SOC-2
 Requirement Solution Brief 8815 Centre Park Drive, Columbia MD 21045 About delivers business critical software and services that transform high-volume cryptic log data into actionable, prioritized intelligence
Requirement Solution Brief 8815 Centre Park Drive, Columbia MD 21045 About delivers business critical software and services that transform high-volume cryptic log data into actionable, prioritized intelligence
Bridging the Paper and Electronic Worlds
 Bridging the Paper and Electronic Worlds Johnson, Jellinek, Klotz, Card. Aaron Zinman MAS.961 What its about Paper exists Its useful and persistent Xerox is concerned with doc management Scanning is problematic
Bridging the Paper and Electronic Worlds Johnson, Jellinek, Klotz, Card. Aaron Zinman MAS.961 What its about Paper exists Its useful and persistent Xerox is concerned with doc management Scanning is problematic
Improving Touch Based Gesture Interfaces Ridhô Jeftha University of Cape Town Computer Science Student Rondebosch Cape Town 03 July 2012
 Improving Touch Based Gesture Interfaces Ridhô Jeftha University of Cape Town Computer Science Student Rondebosch Cape Town 03 July 2012 mail@ridhojeftha.com ABSTRACT The lack of affordance in gesture
Improving Touch Based Gesture Interfaces Ridhô Jeftha University of Cape Town Computer Science Student Rondebosch Cape Town 03 July 2012 mail@ridhojeftha.com ABSTRACT The lack of affordance in gesture
Keyboard Clawing: Input Method by Clawing Key Tops
 Keyboard Clawing: Input Method by Clawing Key Tops Toshifumi Kurosawa, Buntarou Shizuki, and Jiro Tanaka University of Tsukuba, Japan {kurosawa,shizuki,jiro}@iplab.cs.tsukuba.ac.jp Abstract. We present
Keyboard Clawing: Input Method by Clawing Key Tops Toshifumi Kurosawa, Buntarou Shizuki, and Jiro Tanaka University of Tsukuba, Japan {kurosawa,shizuki,jiro}@iplab.cs.tsukuba.ac.jp Abstract. We present
Blobby: How to Guide a Blind Person Indoors
 Blobby: How to Guide a Blind Person Indoors Hugo Nicolau Tiago Guerreiro INESC-ID/IST/UTL. INESC-ID/IST/UTL. Avenida Professor Cavaco Silva. Avenida Professor Cavaco Silva. Tagus Park, Room 2-N9, Porto
Blobby: How to Guide a Blind Person Indoors Hugo Nicolau Tiago Guerreiro INESC-ID/IST/UTL. INESC-ID/IST/UTL. Avenida Professor Cavaco Silva. Avenida Professor Cavaco Silva. Tagus Park, Room 2-N9, Porto
Mitigating Risks with Cloud Computing Dan Reis
 Mitigating Risks with Cloud Computing Dan Reis Director of U.S. Product Marketing Trend Micro Agenda Cloud Adoption Key Characteristics The Cloud Landscape and its Security Challenges The SecureCloud Solution
Mitigating Risks with Cloud Computing Dan Reis Director of U.S. Product Marketing Trend Micro Agenda Cloud Adoption Key Characteristics The Cloud Landscape and its Security Challenges The SecureCloud Solution
S-K Smartphone Barcode Reader for Blind Users
 230 S-K Smartphone Barcode Reader for Blind Users Ender Tekin, David Vásquez, James M. Coughlan The Smith-Kettlewell Eye Research Institute ender@ski.org, david@ski.org, coughlan@ski.org Abstract We describe
230 S-K Smartphone Barcode Reader for Blind Users Ender Tekin, David Vásquez, James M. Coughlan The Smith-Kettlewell Eye Research Institute ender@ski.org, david@ski.org, coughlan@ski.org Abstract We describe
Glasgow eprints Service
 Kildal, J. and Brewster, S.A. (2006) Non-visual overviews of complex data sets. In, Conference on Human Factors in Computing Systems, 22-27 April 2006, pages pp. 947-952, Montréal, Québec, Canada. http://eprints.gla.ac.uk/3267/
Kildal, J. and Brewster, S.A. (2006) Non-visual overviews of complex data sets. In, Conference on Human Factors in Computing Systems, 22-27 April 2006, pages pp. 947-952, Montréal, Québec, Canada. http://eprints.gla.ac.uk/3267/
Margarita Grinvald. Gesture recognition for Smartphones/Wearables
 Margarita Grinvald Gesture recognition for Smartphones/Wearables Gestures hands, face, body movements non-verbal communication human interaction 2 Gesture recognition interface with computers increase
Margarita Grinvald Gesture recognition for Smartphones/Wearables Gestures hands, face, body movements non-verbal communication human interaction 2 Gesture recognition interface with computers increase
CHAPTER 4 HUMAN FACTOR BASED USER INTERFACE DESIGN
 CHAPTER 4 HUMAN FACTOR BASED USER INTERFACE DESIGN 4.1 Introduction Today one of the most important concerns is how to use the system with effectiveness, efficiency and satisfaction. The ease or comfort
CHAPTER 4 HUMAN FACTOR BASED USER INTERFACE DESIGN 4.1 Introduction Today one of the most important concerns is how to use the system with effectiveness, efficiency and satisfaction. The ease or comfort
Investigating the Effectiveness of Tactile Feedback for Mobile Touchscreens
 Investigating the Effectiveness of Tactile Feedback for Mobile Touchscreens Eve Hoggan, Stephen A. Brewster and Jody Johnston Glasgow Interactive Systems Group, Department of Computing Science University
Investigating the Effectiveness of Tactile Feedback for Mobile Touchscreens Eve Hoggan, Stephen A. Brewster and Jody Johnston Glasgow Interactive Systems Group, Department of Computing Science University
THE POWER OF TECH-SAVVY BOARDS:
 THE POWER OF TECH-SAVVY BOARDS: LEADERSHIP S ROLE IN CULTIVATING CYBERSECURITY TALENT SHANNON DONAHUE DIRECTOR, INFORMATION SECURITY PRACTICES 1 IT S A RISK-BASED WORLD: THE 10 MOST CRITICAL UNCERTAINTIES
THE POWER OF TECH-SAVVY BOARDS: LEADERSHIP S ROLE IN CULTIVATING CYBERSECURITY TALENT SHANNON DONAHUE DIRECTOR, INFORMATION SECURITY PRACTICES 1 IT S A RISK-BASED WORLD: THE 10 MOST CRITICAL UNCERTAINTIES
Frequently Asked Questions Retiro Móvil (Mobile Withdrawal)
 Frequently Asked Questions Retiro Móvil (Mobile Withdrawal) 1. What is Retiro Móvil (Mobile Withdrawal)? Retiro Móvil (Mobile Withdrawal) is a free service that allows you to schedule withdrawal requests
Frequently Asked Questions Retiro Móvil (Mobile Withdrawal) 1. What is Retiro Móvil (Mobile Withdrawal)? Retiro Móvil (Mobile Withdrawal) is a free service that allows you to schedule withdrawal requests
(2014) : '14. ACM, ISBN
 Dunlop, Mark and Komninos, Andreas and Nicol, Emma and Hamilton, Iain (2014) Shake 'n' Tap : a gesture enhanced keyboard for older adults. In: MobileHCI '14. ACM, New York, pp. 525-530. ISBN 9781450330046,
Dunlop, Mark and Komninos, Andreas and Nicol, Emma and Hamilton, Iain (2014) Shake 'n' Tap : a gesture enhanced keyboard for older adults. In: MobileHCI '14. ACM, New York, pp. 525-530. ISBN 9781450330046,
Duo Multi-Factor Authentication Enrolling an ipad. Introduction
 Duo Multi-Factor Authentication Enrolling an ipad Introduction Duo is a multi-factor authentication tool chosen by Towson University to help prevent data breaches. Duo is a tool that verifies someone s
Duo Multi-Factor Authentication Enrolling an ipad Introduction Duo is a multi-factor authentication tool chosen by Towson University to help prevent data breaches. Duo is a tool that verifies someone s
An Inconvenient Trust
 An Inconvenient Trust User Attitudes toward Security and Usability Tradeoffs for Key-Directory Encryption Systems Patrick Gage Kelley @patrickgage Assistant Professor, Computer Science joint work with
An Inconvenient Trust User Attitudes toward Security and Usability Tradeoffs for Key-Directory Encryption Systems Patrick Gage Kelley @patrickgage Assistant Professor, Computer Science joint work with
Interactive Campaign Planning for Marketing Analysts
 Interactive Campaign Planning for Marketing Analysts Fan Du University of Maryland College Park, MD, USA fan@cs.umd.edu Sana Malik Adobe Research San Jose, CA, USA sana.malik@adobe.com Eunyee Koh Adobe
Interactive Campaign Planning for Marketing Analysts Fan Du University of Maryland College Park, MD, USA fan@cs.umd.edu Sana Malik Adobe Research San Jose, CA, USA sana.malik@adobe.com Eunyee Koh Adobe
Accessibility Features
 , page 1 Hard of Hearing, page 3 Vision-Impaired and Blind, page 5 This chapter contains information about the accessibility features that are standard on the Cisco DX650. These phones provide accessibility
, page 1 Hard of Hearing, page 3 Vision-Impaired and Blind, page 5 This chapter contains information about the accessibility features that are standard on the Cisco DX650. These phones provide accessibility
Blind People Interacting with Large Touch Surfaces: Strategies for One-handed and Two-handed Exploration
 Blind People Interacting with Large Touch Surfaces: Strategies for One-handed and Two-handed Exploration Tiago Guerreiro 1, Kyle Montague 2, João Guerreiro 3, Rafael Nunes 1, Hugo Nicolau 1, Daniel Gonçalves
Blind People Interacting with Large Touch Surfaces: Strategies for One-handed and Two-handed Exploration Tiago Guerreiro 1, Kyle Montague 2, João Guerreiro 3, Rafael Nunes 1, Hugo Nicolau 1, Daniel Gonçalves
Toward Privacy Standards Based on Empirical Studies
 Toward Privacy Standards Based on Empirical Studies Serge Egelman and Erika McCallister National Institute of Standards and Technology 100 Bureau Drive Gaithersburg, MD 20899 {serge.egelman, erika.mccallister}@nist.gov
Toward Privacy Standards Based on Empirical Studies Serge Egelman and Erika McCallister National Institute of Standards and Technology 100 Bureau Drive Gaithersburg, MD 20899 {serge.egelman, erika.mccallister}@nist.gov
PIN Skimming: Exploiting the Ambient-Light Sensor in Mobile Devices
 W I S S E N T E C H N I K L E I D E N S C H A F T PIN Skimming: Exploiting the Ambient-Light Sensor in Mobile Devices IAIK, Graz University of Technology, Austria www.iaik.tugraz.at 2 Outline Introduction
W I S S E N T E C H N I K L E I D E N S C H A F T PIN Skimming: Exploiting the Ambient-Light Sensor in Mobile Devices IAIK, Graz University of Technology, Austria www.iaik.tugraz.at 2 Outline Introduction
UniGest: Text Entry Using Three Degrees of Motion
 UniGest: Text Entry Using Three Degrees of Motion Steven J. Castellucci Department of Computer Science and Engineering York University 4700 Keele St. Toronto, Ontario M3J 1P3 Canada stevenc@cse.yorku.ca
UniGest: Text Entry Using Three Degrees of Motion Steven J. Castellucci Department of Computer Science and Engineering York University 4700 Keele St. Toronto, Ontario M3J 1P3 Canada stevenc@cse.yorku.ca
Using surface markings to enhance accuracy and stability of object perception in graphic displays
 Using surface markings to enhance accuracy and stability of object perception in graphic displays Roger A. Browse a,b, James C. Rodger a, and Robert A. Adderley a a Department of Computing and Information
Using surface markings to enhance accuracy and stability of object perception in graphic displays Roger A. Browse a,b, James C. Rodger a, and Robert A. Adderley a a Department of Computing and Information
Welcome to Analytics. Welcome to Applause! Table of Contents:
 Welcome to Applause! Your success is our priority and we want to make sure Applause Analytics (ALX) provides you with actionable insight into what your users are thinking and saying about their experiences
Welcome to Applause! Your success is our priority and we want to make sure Applause Analytics (ALX) provides you with actionable insight into what your users are thinking and saying about their experiences
Phone Tilt. Dynamic UI Adaptations for single-handed smartphone interaction. Fasil Negash Mtr No.:
 1 Phone Tilt Dynamic UI Adaptations for single-handed smartphone interaction Fasil Negash Mtr No.: 2040556 fasil.negash@hs-augsburg.de WS 2018 / 2019 Hochschule Augsburg Interaction Engineering Prof. Dr.
1 Phone Tilt Dynamic UI Adaptations for single-handed smartphone interaction Fasil Negash Mtr No.: 2040556 fasil.negash@hs-augsburg.de WS 2018 / 2019 Hochschule Augsburg Interaction Engineering Prof. Dr.
DECOY APPLICATIONS FOR CONTINUOUS AUTHENTICATION ON MOBILE DEVICES
 DECOY APPLICATIONS FOR CONTINUOUS AUTHENTICATION ON MOBILE DEVICES WAY Workshop July 9 th, 2014 Malek Ben Salem Accenture Technology Labs Jonathan Voris and Salvatore J. Stolfo Allure Security Technology
DECOY APPLICATIONS FOR CONTINUOUS AUTHENTICATION ON MOBILE DEVICES WAY Workshop July 9 th, 2014 Malek Ben Salem Accenture Technology Labs Jonathan Voris and Salvatore J. Stolfo Allure Security Technology
Preliminary Evidence for Top-down and Bottom-up Processes in Web Search Navigation
 Preliminary Evidence for Top-down and Bottom-up Processes in Web Search Navigation Shu-Chieh Wu San Jose State University NASA Ames Research Center Moffett Field, CA 94035 USA scwu@mail.arc.nasa.gov Craig
Preliminary Evidence for Top-down and Bottom-up Processes in Web Search Navigation Shu-Chieh Wu San Jose State University NASA Ames Research Center Moffett Field, CA 94035 USA scwu@mail.arc.nasa.gov Craig
MIS Week 9 Host Hardening
 MIS 5214 Week 9 Host Hardening Agenda NIST Risk Management Framework A quick review Implementing controls Host hardening Security configuration checklist (w/disa STIG Viewer) NIST 800-53Ar4 How Controls
MIS 5214 Week 9 Host Hardening Agenda NIST Risk Management Framework A quick review Implementing controls Host hardening Security configuration checklist (w/disa STIG Viewer) NIST 800-53Ar4 How Controls
Binding an Handheld Device with its Owner
 Binding an Handheld Device with its Owner Maurício Sousa and Joaquim Jorge INESC-ID / IST-UTL antonio.sousa@ist.utl.pt,jaj@inesc-id.pt Abstract. We present a gesture based method to associate personal
Binding an Handheld Device with its Owner Maurício Sousa and Joaquim Jorge INESC-ID / IST-UTL antonio.sousa@ist.utl.pt,jaj@inesc-id.pt Abstract. We present a gesture based method to associate personal
Touch me once and I know it s you! Implicit Authentication based on Touch Screen Patterns
 Touch me once and I know it s you! Implicit Authentication based on Touch Screen Patterns Alexander De Luca, Alina Hang, Frederik Brudy, Christian Lindner, Heinrich Hussmann Media Informatics Group, University
Touch me once and I know it s you! Implicit Authentication based on Touch Screen Patterns Alexander De Luca, Alina Hang, Frederik Brudy, Christian Lindner, Heinrich Hussmann Media Informatics Group, University
Interactive Generation of Overview Information Using Speech
 Interactive Generation of Overview Information Using Speech Johan Kildal and Stephen A. Brewster Glasgow Interactive Systems Group Department of Computing Science University of Glasgow Glasgow, G12 8QQ,
Interactive Generation of Overview Information Using Speech Johan Kildal and Stephen A. Brewster Glasgow Interactive Systems Group Department of Computing Science University of Glasgow Glasgow, G12 8QQ,
Review of distracted driving factors. George Yannis, Associate Professor, NTUA
 Review of distracted driving factors George Yannis, Associate Professor, NTUA www.nrso.ntua.gr/geyannis Research Objectives Presentation Structure Research Objectives To provide a comprehensive picture
Review of distracted driving factors George Yannis, Associate Professor, NTUA www.nrso.ntua.gr/geyannis Research Objectives Presentation Structure Research Objectives To provide a comprehensive picture
1 / Spectrum Brands, Inc.
 1 / 11 2016 Spectrum Brands, Inc. 1 Prepare the door and check dimensions If drilling a new door, use the supplied template and the complete door drilling instructions available at www.kwikset.com/doorprep.
1 / 11 2016 Spectrum Brands, Inc. 1 Prepare the door and check dimensions If drilling a new door, use the supplied template and the complete door drilling instructions available at www.kwikset.com/doorprep.
GeoFARA (Geography Fieldwork Augmented Reality Application): design, development and evaluation
 GeoFARA (Geography Fieldwork Augmented Reality Application): design, development and evaluation Xiaoling Wang, Corné P.J.M. van Elzakker, Menno-Jan Kraak, Barend Köbben ICC 2017, 5 July, 2017 Washington,
GeoFARA (Geography Fieldwork Augmented Reality Application): design, development and evaluation Xiaoling Wang, Corné P.J.M. van Elzakker, Menno-Jan Kraak, Barend Köbben ICC 2017, 5 July, 2017 Washington,
Ultrabook Convertible Application Design Considerations
 Ultrabook Convertible Application Design Considerations Introduction With the introduction of Windows 8* and touch-enabled computers, like Intel Ultrabook devices, where touch is an additional input method,
Ultrabook Convertible Application Design Considerations Introduction With the introduction of Windows 8* and touch-enabled computers, like Intel Ultrabook devices, where touch is an additional input method,
Online Banking ENHANCEMENT
 Online Banking ENHANCEMENT Implementation: 12/13/2016 Table of Contents 1. User Interface Redesign... 3 2. Updated Log in Page... 3 3. Updated User Interface for Security Question Answers... 4 4. Updated
Online Banking ENHANCEMENT Implementation: 12/13/2016 Table of Contents 1. User Interface Redesign... 3 2. Updated Log in Page... 3 3. Updated User Interface for Security Question Answers... 4 4. Updated
Welcome to the Investor Experience
 Welcome to the Investor Experience Welcome to the Black Diamond Investor Experience, a platform that allows advisors to customize how they present information to their clients. This document provides important
Welcome to the Investor Experience Welcome to the Black Diamond Investor Experience, a platform that allows advisors to customize how they present information to their clients. This document provides important
Summary Table Voluntary Product Accessibility Template. Criteria Supporting Features Remarks and explanation
 The following Voluntary Product Accessibility information refers to the Apple ipad mini with Retina display running ios 7 or later. For more information on the accessibility features of the ipad mini and
The following Voluntary Product Accessibility information refers to the Apple ipad mini with Retina display running ios 7 or later. For more information on the accessibility features of the ipad mini and
Differential Processing of Facial Motion
 Differential Processing of Facial Motion Tamara L. Watson 1, Alan Johnston 1, Harold C.H Hill 2 and Nikolaus Troje 3 1 Department of Psychology, University College London, Gower Street, London WC1E 6BT
Differential Processing of Facial Motion Tamara L. Watson 1, Alan Johnston 1, Harold C.H Hill 2 and Nikolaus Troje 3 1 Department of Psychology, University College London, Gower Street, London WC1E 6BT
Security and Human Factors. Maritza Johnson
 Security and Human Factors Maritza Johnson maritzaj@cs.columbia.edu 1 2 Usability the extent to which a product can be used by specified users to achieve specified goals with effectiveness, efficiency
Security and Human Factors Maritza Johnson maritzaj@cs.columbia.edu 1 2 Usability the extent to which a product can be used by specified users to achieve specified goals with effectiveness, efficiency
Command composition approach in crossing interfaces. with more than two continuous goals
 Some Student November 30, 2010 CS 5317 Command composition approach in crossing interfaces with more than two continuous goals 1. INTRODUCTION Over the last decade, pen and touch-based interactions began
Some Student November 30, 2010 CS 5317 Command composition approach in crossing interfaces with more than two continuous goals 1. INTRODUCTION Over the last decade, pen and touch-based interactions began
BCS THE CHARTERED INSTITUTE FOR IT. BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 6 Professional Graduate Diploma in IT REALISING THE USER INTERFACE
 BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 6 Professional Graduate Diploma in IT REALISING THE USER INTERFACE Friday 1 st April 2016 - Morning Answer any THREE questions
BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 6 Professional Graduate Diploma in IT REALISING THE USER INTERFACE Friday 1 st April 2016 - Morning Answer any THREE questions
OPTIKAM ELECTRONIC CENTRATION GUIDE
 OPTIKAM ELECTRONIC CENTRATION GUIDE The EY-Stick The following EY-Stick components will be referred to throughout this document. Green Sensor Brake Arm Blue Sensor Wrap Arm Nasal Sensor Prism Swing Assembly
OPTIKAM ELECTRONIC CENTRATION GUIDE The EY-Stick The following EY-Stick components will be referred to throughout this document. Green Sensor Brake Arm Blue Sensor Wrap Arm Nasal Sensor Prism Swing Assembly
Generating and Using Results
 Background Generating and Using Results from Usability Evaluations Kasper Hornbæk University of Copenhagen www.kasperhornbaek.dk Associate professor in the Human computer Interaction group at Copenhagen
Background Generating and Using Results from Usability Evaluations Kasper Hornbæk University of Copenhagen www.kasperhornbaek.dk Associate professor in the Human computer Interaction group at Copenhagen
