Using TU Eindhoven s VPN with Ubuntu
|
|
|
- Annabel Whitehead
- 6 years ago
- Views:
Transcription
1 Using TU Eindhoven's VPN with Ubuntu or TU Eindhoven s Virtual Private Networking (VPN) service can be used on Linux computers. This document describes how to do it using Ubuntu or with its default GUI environment (Unity). Table of Contents Using TU Eindhoven's VPN with Ubuntu or Installing VPN client software on Ubuntu... 1 Configuring VPN to TU/e on Ubuntu using the GUI... 1 Configuring VPN to TU/e on Ubuntu using the command line... 9 Installing VPN client software on Ubuntu We need to be sure software is installed is for Cisco AnyConnect Compatible VPN (openconnect). To do this, install the Ubuntu package named network-manager-openconnect-gnome (with its dependencies). One way to do this is by opening a terminal (e.g. by typing Ctrl-Alt-T), then typing sudo apt-get -y install network-manager-openconnect-gnome and supplying your password. Another way is using the Ubuntu Software Center. Once this is done, you can create a VPN connection of the right type. Configuring VPN to TU/e on Ubuntu using the GUI To configure a VPN connection, on your Ubuntu desktop, click on the networking icon in the top right-hand menu (the icon shape varies depending on the state of your networking connections). A menu will open. In that menu, Enable Networking and Enable Wi-Fi can be enabled or disabled by clicking on them. Of course, Enable Networking must be enabled, and you need a working Internet connection (by cable or Wi-Fi) before you can use a VPN connection. Now, select VPN Connections. Initially, no VPN connection will be shown. Using TU Eindhoven s VPN with Ubuntu version: March 23, 2018 page 1
2 Depending on which software you have installed, a menu item Configure VPN...: may be shown. If present, you can use this to configure the TU/e VPN connection. Alternatively, click on Edit Connections menu item, then Add, or to go to System Settings Network, then click +, select VPN and press Create : Using TU Eindhoven s VPN with Ubuntu version: March 23, 2018 page 2
3 You will be asked to choose a connection type. Select Cisco AnyConnect Compatible VPN (openconnect): Click Create. The following dialog appears: Using TU Eindhoven s VPN with Ubuntu version: March 23, 2018 page 3
4 (On Ubuntu 14.04, the Software Token Authentication part is missing.) Fill in a connection name of your preference. As the gateway, fill in vpn2.tue.nl. You don't need to specify a certificate. 1 Click Save. 1 If you do, select /etc/ssl/certs/digicert_assured_id_root_ca.pem. Using TU Eindhoven s VPN with Ubuntu version: March 23, 2018 page 4
5 or You now have a new item in the VPN Connections submenu. Select it to enable it: Using TU Eindhoven s VPN with Ubuntu version: March 23, 2018 page 5
6 The following dialog will pop up (Ubuntu shown on the left, Ubuntu on the right): Next to GROUP, select the range of traffic you want to go through the VPN connection. Specify your TUE domain username and password. If you check Save passwords, your password will saved in your login keyring, which is encrypted, but automatically unlocked when you log into the Ubuntu GUI. 2 Then, click Login. If your credentials are correct, the connection will be established: 2 This will allow anyone who cracks your Ubuntu account to use your TUE password on every service for which it is used, unless you set a password on the keyring. Using TU Eindhoven s VPN with Ubuntu version: March 23, 2018 page 6
7 To break the VPN connection, select the checked vpn2.tue.nl menu item. Using TU Eindhoven s VPN with Ubuntu version: March 23, 2018 page 7
8 The low-level VPN connection name is vpn0: Using TU Eindhoven s VPN with Ubuntu version: March 23, 2018 page 8
9 Configuring VPN to TU/e on Ubuntu using the command line Instead of using GUI configuration, you can connect and disconnect using the openconnect command line application, which is installed by installing Ubuntu's openconnect package. A script to automate connecting to vpn2.win.tue.nl using this command can be found at To use it: 1. download it 2. make it executable 3. inspect its contents (in case it has been tampered with) 4. run it from the command line: vpn2 start # to create a VPN connection to vpn2.tue.nl 5. vpn2 stop # to break it if it exists 6. vpn2 restart # to stop, then start It creates a networking interface called tun0 rather than vpn0. Other than that, the effect appears to be the same as by using the GUI. Using TU Eindhoven s VPN with Ubuntu version: March 23, 2018 page 9
Using MFA with the Pulse Client
 Using MFA with the Pulse Client 1. Launch the Pulse client and open your preferred connection. 2. A new pre-sign in notification will display similar to the one shown below. This page explains your options
Using MFA with the Pulse Client 1. Launch the Pulse client and open your preferred connection. 2. A new pre-sign in notification will display similar to the one shown below. This page explains your options
Manual for configuring VPN in Windows 7
 Manual for configuring VPN in Windows 7 A. Installing the User Digital Signing Certificate (DSC) 1. Once your receive the DSC, please acknowledge it by replying it to the same email address to get the
Manual for configuring VPN in Windows 7 A. Installing the User Digital Signing Certificate (DSC) 1. Once your receive the DSC, please acknowledge it by replying it to the same email address to get the
Configuring and Using your Nationwide Extranet Virtual Machine
 Configuring and Using your Nationwide Extranet Virtual Machine V8.16.17 OVERVIEW To access your Nationwide email, you must configure your PC. This is required whenever you are accessing from a new machine
Configuring and Using your Nationwide Extranet Virtual Machine V8.16.17 OVERVIEW To access your Nationwide email, you must configure your PC. This is required whenever you are accessing from a new machine
How to Configure the Barracuda VPN Client for Windows
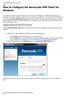 How to Configure the Barracuda VPN Client for Windows Barracuda VPN Control is the user interface of the VPN Client for Windows for configuring VPN profiles and Barracuda VPN adapter settings as well as
How to Configure the Barracuda VPN Client for Windows Barracuda VPN Control is the user interface of the VPN Client for Windows for configuring VPN profiles and Barracuda VPN adapter settings as well as
Installing and Connecting to the SOM VPN using the Cisco AnyConnect version 4.x Client (Windows)
 Installing and Connecting to the SOM VPN using the Cisco AnyConnect version 4.x Client (Windows) This document is for you if: - You connect to the SOM VPN via the Cisco AnyConnect Client - Your PC is running
Installing and Connecting to the SOM VPN using the Cisco AnyConnect version 4.x Client (Windows) This document is for you if: - You connect to the SOM VPN via the Cisco AnyConnect Client - Your PC is running
Windows 8.1 and Windows 10 a) Connect to wireless network Click on the wireless icon in taskbar. Select detnsw and click on Connect.
 1 HSHS BYOD Wireless Connection Windows 8.1 and Windows 10 a) Connect to wireless network Click on the wireless icon in taskbar. Windows 8.1 icon: Windows 10 icon: Select detnsw and click on Connect. or
1 HSHS BYOD Wireless Connection Windows 8.1 and Windows 10 a) Connect to wireless network Click on the wireless icon in taskbar. Windows 8.1 icon: Windows 10 icon: Select detnsw and click on Connect. or
Contents. Download... 2 OpenVPN Clients... 2
 Contents Download... 2 OpenVPN Clients... 2 Notes... 11 Prior to using VPN 1 at IST Austria, please make sure you have read and you do comply to the VPN Policy. The VPN service based on OpenVPN is provided
Contents Download... 2 OpenVPN Clients... 2 Notes... 11 Prior to using VPN 1 at IST Austria, please make sure you have read and you do comply to the VPN Policy. The VPN service based on OpenVPN is provided
SSL VPN Service. Once you have installed the AnyConnect Secure Mobility Client, this document is available by clicking on the Help icon on the client.
 Contents Introduction... 2 Prepare Work PC for Remote Desktop... 4 Add VPN url as a Trusted Site in Internet Explorer... 5 VPN Client Installation... 5 Starting the VPN Application... 6 Connect to Work
Contents Introduction... 2 Prepare Work PC for Remote Desktop... 4 Add VPN url as a Trusted Site in Internet Explorer... 5 VPN Client Installation... 5 Starting the VPN Application... 6 Connect to Work
Getting Started with VPN
 What is a VPN? VPN (Virtual Private Network) provides you with a way to connect to the HBU campus server securely over the internet in order to access your work computer and shared drives from home. VPN
What is a VPN? VPN (Virtual Private Network) provides you with a way to connect to the HBU campus server securely over the internet in order to access your work computer and shared drives from home. VPN
Using CSE Cisco Anyconnect with 2FA
 Using CSE Cisco Anyconnect with 2FA If you are using the Duo Mobile App in push mode: you open Anyconnect. 3. Enter your CSE UserName for the Username. 4. A new window will open. 5. Enter your CSE UserName
Using CSE Cisco Anyconnect with 2FA If you are using the Duo Mobile App in push mode: you open Anyconnect. 3. Enter your CSE UserName for the Username. 4. A new window will open. 5. Enter your CSE UserName
MAC OSx (Mountain Lion) is not supported by ICTS. Therefore, please consider this manual a courtesy.
 MAC OSx (Mountain Lion) is not supported by ICTS. Therefore, please consider this manual a courtesy. A Virtual Private Network (VPN) is best described as a tunnel to MAASnet, the university network. After
MAC OSx (Mountain Lion) is not supported by ICTS. Therefore, please consider this manual a courtesy. A Virtual Private Network (VPN) is best described as a tunnel to MAASnet, the university network. After
Simulation Manager Configuration Guide
 Cornell University College of Veterinary Medicine Student Training Simulation Project Simulation Manager Configuration Guide 2018-Oct-1 Version 1.9 Prepared by: I-Town Design David Weiner 117 Burleigh
Cornell University College of Veterinary Medicine Student Training Simulation Project Simulation Manager Configuration Guide 2018-Oct-1 Version 1.9 Prepared by: I-Town Design David Weiner 117 Burleigh
CKHS VPN Connection Instructions
 CKHS VPN Connection Instructions This document provides all authorized colleagues with instruction for accessing the CKHS network via a Virtual Private Network. Connection Prerequisites: 1. Operating System:
CKHS VPN Connection Instructions This document provides all authorized colleagues with instruction for accessing the CKHS network via a Virtual Private Network. Connection Prerequisites: 1. Operating System:
Procedure to Connect NIC VPN in Windows for ebiz
 Procedure to Connect NIC VPN in Windows for ebiz This procedure is a step by step guide for ebiz users to connect NIC VPN on Windows machines to access the ebiz services. It is prepared for end users like
Procedure to Connect NIC VPN in Windows for ebiz This procedure is a step by step guide for ebiz users to connect NIC VPN on Windows machines to access the ebiz services. It is prepared for end users like
Remote Access VPN Setup
 Remote Access VPN Setup MWI Animal Health provides remote access to the MWI network using a VPN (virtual private network). Use the information on this site to setup and connect to the MWI VPN. Before You
Remote Access VPN Setup MWI Animal Health provides remote access to the MWI network using a VPN (virtual private network). Use the information on this site to setup and connect to the MWI VPN. Before You
What this Guide Covers. Additional Info. 1. Linux based Servers. 2. Windows Servers. 3. GoldLite and Virtual Servers. 4. Other servers. 5.
 This guide is designed to assist in shutting down the Gold Servers ensuring a clean reboot of the systems. This should be done by the System Administrators with all users logged off the system and any
This guide is designed to assist in shutting down the Gold Servers ensuring a clean reboot of the systems. This should be done by the System Administrators with all users logged off the system and any
Cisco s AnyConnect VPN Client (version 2.4)
 Table of Contents [TOC]: Introduction Getting Started Installation Overview Using the Softphone System Requirements Introduction: Valley City State University is deploying Cisco s AnyConnect Virtual Private
Table of Contents [TOC]: Introduction Getting Started Installation Overview Using the Softphone System Requirements Introduction: Valley City State University is deploying Cisco s AnyConnect Virtual Private
Client VPN OS Configuration. Android
 Client VPN OS Configuration This article outlines instructions to configure a client VPN connection on commonly-used operating systems. For more information about client VPN, please refer to our documentation.
Client VPN OS Configuration This article outlines instructions to configure a client VPN connection on commonly-used operating systems. For more information about client VPN, please refer to our documentation.
USER GUIDE WWPass Security for (Thunderbird)
 USER GUIDE WWPass Security for Email (Thunderbird) TABLE OF CONTENTS Chapter 1 Welcome... 3 Introducing WWPass Security for Email (Thunderbird)... 4 Connecting Your PassKey to Your Computer... 4 Need Assistance?...
USER GUIDE WWPass Security for Email (Thunderbird) TABLE OF CONTENTS Chapter 1 Welcome... 3 Introducing WWPass Security for Email (Thunderbird)... 4 Connecting Your PassKey to Your Computer... 4 Need Assistance?...
APSCN VPN Settings for Windows 7 2. APSCN VPN Settings for Windows XP 8. APSCN VPN Settings for MAC OS 15
 APSCN VPN Settings for Windows 7 2 1. Creating a VPN Connection 2 2. Disconnecting the VPN 6 3. Connecting to an existing VPN Connection 7 APSCN VPN Settings for Windows XP 8 1. Creating a VPN Connection
APSCN VPN Settings for Windows 7 2 1. Creating a VPN Connection 2 2. Disconnecting the VPN 6 3. Connecting to an existing VPN Connection 7 APSCN VPN Settings for Windows XP 8 1. Creating a VPN Connection
VPN Connection - Instructional Document
 VPN Connection - Instructional Document INTRODUCTION PPTP or "Point to Point Tunneling Protocol" allows your computer to connect to the Pelco s Partner Integration Lab and access resources that are only
VPN Connection - Instructional Document INTRODUCTION PPTP or "Point to Point Tunneling Protocol" allows your computer to connect to the Pelco s Partner Integration Lab and access resources that are only
Adding a VPN connection in Windows XP
 Adding a VPN connection in Windows XP Open up the Control Panel by selecting Start, Settings, Control Panel (in Classic Menu view) or Start, Control Panel (in XP Menu view). Double click on Network Connections.
Adding a VPN connection in Windows XP Open up the Control Panel by selecting Start, Settings, Control Panel (in Classic Menu view) or Start, Control Panel (in XP Menu view). Double click on Network Connections.
SET UP VPN FOR WINDOWS 10
 SET UP VPN FOR WINDOWS 10 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure
SET UP VPN FOR WINDOWS 10 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure
Connect to the Cambridge network
 Connect to the Cambridge network You can connect to the University network from home or another location so that you can access files and use common software, for example Word, Excel, PowerPoint and CHRIS.
Connect to the Cambridge network You can connect to the University network from home or another location so that you can access files and use common software, for example Word, Excel, PowerPoint and CHRIS.
Installing and Configuring Cisco Unified Real-Time Monitoring Tool
 CHAPTER 2 Installing and Configuring Cisco Unified Real-Time Monitoring Tool You can install Cisco Unified Real-Time Monitoring Tool (RTMT), which works for resolutions 800*600 and above, on a computer
CHAPTER 2 Installing and Configuring Cisco Unified Real-Time Monitoring Tool You can install Cisco Unified Real-Time Monitoring Tool (RTMT), which works for resolutions 800*600 and above, on a computer
Cisco Stand-Alone Installation Instructions Windows OS
 Cisco Stand-Alone Installation Instructions Windows OS IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice at IBM s sole discretion. Information
Cisco Stand-Alone Installation Instructions Windows OS IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice at IBM s sole discretion. Information
Cisco Stand-Alone Installation Instructions Linux 64-bit OS
 Cisco Stand-Alone Installation Instructions Linux 64-bit OS IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice at IBM s sole discretion. Information
Cisco Stand-Alone Installation Instructions Linux 64-bit OS IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice at IBM s sole discretion. Information
Setup Citrix Receiver Standalone App
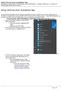 Setup Citrix Receiver Standalone App This guide demonstrates how to setup the standalone version of the Citrix Receiver application on Windows to enable direct access to EPIC (VPN is required for off-site
Setup Citrix Receiver Standalone App This guide demonstrates how to setup the standalone version of the Citrix Receiver application on Windows to enable direct access to EPIC (VPN is required for off-site
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide
 STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
FIREWALLS & NETWORK SECURITY with Intrusion Detection and VPNs, 2 nd ed. Chapter 10 Authenticating Users
 FIREWALLS & NETWORK SECURITY with Intrusion Detection and VPNs, 2 nd ed. Chapter 10 Authenticating Users Learning Objectives Explain why authentication is a critical aspect of network security Explain
FIREWALLS & NETWORK SECURITY with Intrusion Detection and VPNs, 2 nd ed. Chapter 10 Authenticating Users Learning Objectives Explain why authentication is a critical aspect of network security Explain
UNT System Campus VPN Guide
 Contents Introduction... 3 SSL Web Portal... 4 Installing AnyConnect VPNClient... 12 Connecting AnyConnect VPN client... 16 IPSec Client Configuration... 18 Apple OS X Configuration... 21 Android Configuration...
Contents Introduction... 3 SSL Web Portal... 4 Installing AnyConnect VPNClient... 12 Connecting AnyConnect VPN client... 16 IPSec Client Configuration... 18 Apple OS X Configuration... 21 Android Configuration...
1. A broadband connection. 2. Windows Vista (for these instructions; other operating systems have other instructions).
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
Configure Settings and Customize Notifications on FindIT Network Probe
 Configure Email Settings and Customize Email Notifications on FindIT Network Probe Objective Cisco FindIT Network Probe equips a network administrator with indispensable tools that help securely monitor
Configure Email Settings and Customize Email Notifications on FindIT Network Probe Objective Cisco FindIT Network Probe equips a network administrator with indispensable tools that help securely monitor
Eduroam network configuration using Linux
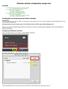 Contents Eduroam network configuration using Linux 1 Configuration by using the gnome network manager 1.1 Configuring the Eduroam connection 2 Configuration by using Kubuntu 10.10 2.1 Step 1: Installation
Contents Eduroam network configuration using Linux 1 Configuration by using the gnome network manager 1.1 Configuring the Eduroam connection 2 Configuration by using Kubuntu 10.10 2.1 Step 1: Installation
HLZA HOW-TO S SETTING UP AND USING REMOTE ACCESS. July 10, 2014
 HLZA HOW-TO S SETTING UP AND USING REMOTE ACCESS July 10, 2014 Installing the VPN Software These steps must only be performed during the initial setup of any computer being used for remote access from
HLZA HOW-TO S SETTING UP AND USING REMOTE ACCESS July 10, 2014 Installing the VPN Software These steps must only be performed during the initial setup of any computer being used for remote access from
29 March 2017 SECURITY SERVER INSTALLATION GUIDE
 29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
Contents. Windows 7 Instructions Windows 10 Instructions Android Instructions Mac OS Instructions ios Instructions...
 The following provides instructions on how to connect to the SJCD-Secure Wireless Network from a variety of operating systems and devices. If you experience any difficulty with these instructions, please
The following provides instructions on how to connect to the SJCD-Secure Wireless Network from a variety of operating systems and devices. If you experience any difficulty with these instructions, please
3.1 Getting Software and Certificates
 3 Configuring the Remote Client On the remote client you have to download the Sophos SSL VPN Client software including configuration data from the UTM User Portal. Then you install the software package
3 Configuring the Remote Client On the remote client you have to download the Sophos SSL VPN Client software including configuration data from the UTM User Portal. Then you install the software package
Microsoft Remote Desktop Installation and Setup for Analysis VMs
 IMB Microscopy now has three Dell r740 Analysis Servers for analysis of microscopy data. These servers have 1TB or more of RAM and three very powerful graphics cards for viewing and processing your data.
IMB Microscopy now has three Dell r740 Analysis Servers for analysis of microscopy data. These servers have 1TB or more of RAM and three very powerful graphics cards for viewing and processing your data.
The SSID to use and the credentials required to be used are listed below for each type of account: SSID TO CREDENTIALS TO BE USED:
 Installation Guides - Information required for connection to the Central Regional TAFE Kalgoorlie Campus Wireless Network Wireless Network Names and Credentials There are two wireless networks operating
Installation Guides - Information required for connection to the Central Regional TAFE Kalgoorlie Campus Wireless Network Wireless Network Names and Credentials There are two wireless networks operating
Installing and Configuring Cisco Unified Real-Time Monitoring Tool
 CHAPTER 2 Installing and Configuring Cisco Unified Real-Time Monitoring Tool You can install Cisco Unified Real-Time Monitoring Tool (RTMT), which works for resolutions 800*600 and above, on a computer
CHAPTER 2 Installing and Configuring Cisco Unified Real-Time Monitoring Tool You can install Cisco Unified Real-Time Monitoring Tool (RTMT), which works for resolutions 800*600 and above, on a computer
Anvil: HCC's Cloud. June Workshop Series - June 26th
 Anvil: HCC's Cloud June Workshop Series - June 26th Anvil: HCC's Cloud OpenStack Cloud Resource offering customizable virtual machines For projects not well served by a traditional Linux environment: Software
Anvil: HCC's Cloud June Workshop Series - June 26th Anvil: HCC's Cloud OpenStack Cloud Resource offering customizable virtual machines For projects not well served by a traditional Linux environment: Software
NexiDesktop. Quick User Guide
 NexiDesktop Quick User Guide May, 2015 NexiDesktop enables you to easily join Nexi conference calls, either as a guest or as a registered user, make point-to-point calls, invite others to your meetings,
NexiDesktop Quick User Guide May, 2015 NexiDesktop enables you to easily join Nexi conference calls, either as a guest or as a registered user, make point-to-point calls, invite others to your meetings,
How to Connect the VPN at Windows Logon Document Version : Revision Date : 15/05/2011
 Overview Please use this process all the time when operating remotely from the Office. This process allows all machines to connect to the corporate network and stops passwords becoming out of sync with
Overview Please use this process all the time when operating remotely from the Office. This process allows all machines to connect to the corporate network and stops passwords becoming out of sync with
Configuring WPA2 for Windows XP
 Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
Establishing two-factor authentication with Cisco and HOTPin authentication server from Celestix Networks
 Establishing two-factor authentication with Cisco and HOTPin authentication server from Celestix Networks Contact Information www.celestix.com Celestix Networks USA Celestix Networks EMEA Celestix Networks
Establishing two-factor authentication with Cisco and HOTPin authentication server from Celestix Networks Contact Information www.celestix.com Celestix Networks USA Celestix Networks EMEA Celestix Networks
BT MobileXpress App V2 for Android Quick Guide
 BT MobileXpress App V2 for Android Quick Guide 2 P a g e Overview This quick guide provides an overview on how to use the BT MobileXpress App to connect to the BT MobileXpress Wi-Fi service. While the
BT MobileXpress App V2 for Android Quick Guide 2 P a g e Overview This quick guide provides an overview on how to use the BT MobileXpress App to connect to the BT MobileXpress Wi-Fi service. While the
Aventail Connect Client with Smart Tunneling
 Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
TCC College WiFi and Printer Setup 07/11/2018 College WiFi and Printer Setup Guide
 College WiFi and Printer Setup Guide **Please note that the below instructions need to be followed by you only when you are at the college** 1 College WiFi and Printer Setup **Please note that the below
College WiFi and Printer Setup Guide **Please note that the below instructions need to be followed by you only when you are at the college** 1 College WiFi and Printer Setup **Please note that the below
Wireless LAN Profile Setup
 Wireless LAN Profiles, page 1 Network Access Profile Settings, page 2 Wireless LAN Profile Settings, page 3 Wireless LAN Profile Group Settings, page 6 Create Network Access Profile, page 6 Create Wireless
Wireless LAN Profiles, page 1 Network Access Profile Settings, page 2 Wireless LAN Profile Settings, page 3 Wireless LAN Profile Group Settings, page 6 Create Network Access Profile, page 6 Create Wireless
Go Ahead Bring Your Own Device to Work... 1 Requirements... 1
 Table of Contents Go Ahead Bring Your Own Device to Work... 1 Requirements... 1 1: Activate AT&T Toggle... 1 1.1: Welcome Email with ORANGE Banner... 1 1.2: Welcome Email with BLUE Banner... 2 1.3: Orange
Table of Contents Go Ahead Bring Your Own Device to Work... 1 Requirements... 1 1: Activate AT&T Toggle... 1 1.1: Welcome Email with ORANGE Banner... 1 1.2: Welcome Email with BLUE Banner... 2 1.3: Orange
How to connect to Wi-Fi
 41 How to connect to Wi-Fi LSBU uses the eduroam service to connect Wi-Fi devices. Once you are set up you will automatically be connected whenever you are in range. Wireless Internet access is available
41 How to connect to Wi-Fi LSBU uses the eduroam service to connect Wi-Fi devices. Once you are set up you will automatically be connected whenever you are in range. Wireless Internet access is available
MyFloridaNet-2 (MFN-2) Remote Access VPN Reference Guide
 MyFloridaNet-2 (MFN-2) Remote Access VPN Reference Guide Document Control Number: 7055011 Contract Number: DMS-13/14-024 Prepared for: Florida Department of Management Services Division of Departmental
MyFloridaNet-2 (MFN-2) Remote Access VPN Reference Guide Document Control Number: 7055011 Contract Number: DMS-13/14-024 Prepared for: Florida Department of Management Services Division of Departmental
AT&T Global Network Client Domain Logon Guide. Version 9.7
 Version 9.7 AT&T Global Network Client Domain Logon Guide 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T Intellectual
Version 9.7 AT&T Global Network Client Domain Logon Guide 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T Intellectual
How do I Install and Use the Cisco VPN Any Connect Client for the Berkeley Campus?
 How do I Install and Use the Cisco VPN Any Connect Client for the Berkeley Campus? The Cisco virtual private network (VPN) client allows a computer to make secure network connections via specific equipment
How do I Install and Use the Cisco VPN Any Connect Client for the Berkeley Campus? The Cisco virtual private network (VPN) client allows a computer to make secure network connections via specific equipment
IHSVPN IHS Secure Network Access
 IHSVPN IHS Secure Network Access Updated 2017-03-17 Type of VPN: VPN Server/Gateway: IHS network drives: Recommended setup: Secure Socket Tunneling Protocol SSTP (Secure Socket Tunneling Protocol) vpn.ihs.ac.at
IHSVPN IHS Secure Network Access Updated 2017-03-17 Type of VPN: VPN Server/Gateway: IHS network drives: Recommended setup: Secure Socket Tunneling Protocol SSTP (Secure Socket Tunneling Protocol) vpn.ihs.ac.at
FH Remote Access Last Updated: July 3, 2013
 FH Remote Access Last Updated: July 3, 2013 1. Remote Access at Fraser Health... 1 2. Cisco VPN Client Software on an FH Laptop... 1 3. Cisco VPN Client Software on a Non-FH Computer/Laptop... 1 1. Download
FH Remote Access Last Updated: July 3, 2013 1. Remote Access at Fraser Health... 1 2. Cisco VPN Client Software on an FH Laptop... 1 3. Cisco VPN Client Software on a Non-FH Computer/Laptop... 1 1. Download
WDC RDS Connection for Android Users
 WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
Certificate authority proxy function
 Certificate authority proxy function This chapter provides information about the certificate authority proxy function. About certificate authority proxy function, page 1 Cisco Unified IP Phone and CAPF
Certificate authority proxy function This chapter provides information about the certificate authority proxy function. About certificate authority proxy function, page 1 Cisco Unified IP Phone and CAPF
UCL Remote Access VPN Service Linux User Guide
 INFORMATION SERVICES DIVISION (ISD) NETWORK SERVICES GROUP UCL Remote Access VPN Service Linux User Guide Version 1.1 Date 22 nd June 2012 Author DP Document Details N/A Last Updated 26 May 2017 Page 1
INFORMATION SERVICES DIVISION (ISD) NETWORK SERVICES GROUP UCL Remote Access VPN Service Linux User Guide Version 1.1 Date 22 nd June 2012 Author DP Document Details N/A Last Updated 26 May 2017 Page 1
Changing passwords on Windows Customized for D-MTEC Users
 Changing passwords on Windows Customized for D-MTEC Users BYOD (Bring Your Own Device)... 1 Wi-Fi 2 Windows Credential Manager... 4 Microsoft Outlook Mail Account... 5 PIA printers... 5 Network drives...
Changing passwords on Windows Customized for D-MTEC Users BYOD (Bring Your Own Device)... 1 Wi-Fi 2 Windows Credential Manager... 4 Microsoft Outlook Mail Account... 5 PIA printers... 5 Network drives...
Internet access system through the Wireless Network of the University of Bologna
 Internet access system through the Wireless Network of the University of Bologna (last update 6/3/2017) Printable service summary document: the updated version is available online at the address http://www.unibo.it/almawifi
Internet access system through the Wireless Network of the University of Bologna (last update 6/3/2017) Printable service summary document: the updated version is available online at the address http://www.unibo.it/almawifi
Cisco VXC VPN. Cisco VXC Requirements. Cisco VXC Firmware
 Cisco VXC Requirements, page 1 Set Up, page 3 Limitations and Restrictions, page 7 Cisco VXC Requirements The feature provides integrated VPN functionality for Cisco Virtualization Experience Clients (Cisco
Cisco VXC Requirements, page 1 Set Up, page 3 Limitations and Restrictions, page 7 Cisco VXC Requirements The feature provides integrated VPN functionality for Cisco Virtualization Experience Clients (Cisco
Windows File Services Mac OS, Linux and Windows Share Mount Procedure. Queen Mary, University of London Version: 5.3 Technical Author:
 Windows File Services Mac OS, Linux and Windows Share Mount Procedure Queen Mary, University of London Version: 5.3 Technical Author: ISO Document Revision History Date Revision Distribution Overview 13/05/2014
Windows File Services Mac OS, Linux and Windows Share Mount Procedure Queen Mary, University of London Version: 5.3 Technical Author: ISO Document Revision History Date Revision Distribution Overview 13/05/2014
NT 0018 Instructions for Setting Up UoE_Secure (XP)
 Academic Services Information & Computing Services Division Network Team NT 0018 Instructions for Setting Up UoE_Secure (XP) Document reference: Document type: Document status: Review period: NT0018 Network
Academic Services Information & Computing Services Division Network Team NT 0018 Instructions for Setting Up UoE_Secure (XP) Document reference: Document type: Document status: Review period: NT0018 Network
Cisco Unity Express Windows and Menus
 Last updated: June 21, 2007 This chapter describes the windows, menus, and icons available in the Cisco Unity Express voice-mail system and contains the following sections: Navigating Through the Cisco
Last updated: June 21, 2007 This chapter describes the windows, menus, and icons available in the Cisco Unity Express voice-mail system and contains the following sections: Navigating Through the Cisco
VPN Logon Process. Contents. VPN Logon Process 1
 Contents Contents 1 Purpose of this document and audience... 1 Revision history... 1 Definitions... 1 Process overview... 1 Concepts... 2 VPN access... 2 Hard-wired or wireless... 2 Connection speed...
Contents Contents 1 Purpose of this document and audience... 1 Revision history... 1 Definitions... 1 Process overview... 1 Concepts... 2 VPN access... 2 Hard-wired or wireless... 2 Connection speed...
Instructions for connecting to winthropsecure
 Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Windows 10 Quick Connect Windows 10 Wireless Set Up Apple Quick Connect Apple Settings Check Windows
Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Windows 10 Quick Connect Windows 10 Wireless Set Up Apple Quick Connect Apple Settings Check Windows
Connecting to ehoundnet-fsa
 Connecting to ehoundnet-fsa Encrypted Wi-Fi at Loyola for Faculty, Administrators, Staff, & other Employees Contents Connecting with a Loyola-Issued PC... 2 Connecting with a Non-Loyola Issued PC... 4
Connecting to ehoundnet-fsa Encrypted Wi-Fi at Loyola for Faculty, Administrators, Staff, & other Employees Contents Connecting with a Loyola-Issued PC... 2 Connecting with a Non-Loyola Issued PC... 4
VIN Service: Multiple Connections. Mac
 VIN Service: Multiple Connections Mac Version 2.0 Release 1.2.13.0 April 2016 Copyright 2016 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored
VIN Service: Multiple Connections Mac Version 2.0 Release 1.2.13.0 April 2016 Copyright 2016 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored
Hollins University VPN
 Hollins University VPN Hollins is now using Palo Alto for its network security and VPN gateway. You will need to install the new VPN client called GlobalProtect to gain access to the Hollins network remotely.
Hollins University VPN Hollins is now using Palo Alto for its network security and VPN gateway. You will need to install the new VPN client called GlobalProtect to gain access to the Hollins network remotely.
The Wifidog project is an open source captive portal solution It consists of two components:
 Captive Portal System typically used by business centers, airports, hotel lobbies, coffee shops, and other venues which offer Wi-Fi hot spots for Internet users It permits to authenticate a client by username
Captive Portal System typically used by business centers, airports, hotel lobbies, coffee shops, and other venues which offer Wi-Fi hot spots for Internet users It permits to authenticate a client by username
Guide Installation and User Guide - Linux
 Guide Installation and User Guide - Linux With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
Guide Installation and User Guide - Linux With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
INTERNET VPN REMOTE ACCESS CLIENT USER GUIDE
 INTERNET VPN REMOTE ACCESS CLIENT USER GUIDE WELCOME TO THE INTERNET VPN REMOTE ACCESS CLIENT USER GUIDE Note: This user guide is provided for trial and evaluation purposes only and is subject to change
INTERNET VPN REMOTE ACCESS CLIENT USER GUIDE WELCOME TO THE INTERNET VPN REMOTE ACCESS CLIENT USER GUIDE Note: This user guide is provided for trial and evaluation purposes only and is subject to change
MULTI FACTOR AUTHENTICATION USING THE NETOP PORTAL. 31 January 2017
 MULTI FACTOR AUTHENTICATION USING THE NETOP PORTAL 31 January 2017 Contents 1 Introduction... 2 1.1 Prerequisite for configuring the multi-factor authentication:... 2 1.1.1 On the Guest side... 2 1.1.2
MULTI FACTOR AUTHENTICATION USING THE NETOP PORTAL 31 January 2017 Contents 1 Introduction... 2 1.1 Prerequisite for configuring the multi-factor authentication:... 2 1.1.1 On the Guest side... 2 1.1.2
CONNECTING TO YOUR VIRTUAL MACHINE 2 CHANGING YOUR NETWORK PASSWORD 7 ADDITIONAL RESOURCES 8
 For assistance please contact the AIMS Help Desk: 608.265.6900, help@aims.wisc.edu In this document An AIMS Virtual Machine, or virtual PC, is a copy of Microsoft Windows running on a server at a remote
For assistance please contact the AIMS Help Desk: 608.265.6900, help@aims.wisc.edu In this document An AIMS Virtual Machine, or virtual PC, is a copy of Microsoft Windows running on a server at a remote
Shellfire VPN IPSec Setup ios
 Shellfire VPN IPSec Setup ios This guide explains how to configure your ios device to work with Shellfire VPN via ikev1 (Cisco) Ipsec. We recommend this procedure for advanced users only. Setting up a
Shellfire VPN IPSec Setup ios This guide explains how to configure your ios device to work with Shellfire VPN via ikev1 (Cisco) Ipsec. We recommend this procedure for advanced users only. Setting up a
Connecting to the NJITSecure wireless network.
 Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
How to Update Your CHI Network Password and Avoid Lockouts
 How to Update Your CHI Network Password and Avoid Lockouts Remember to Remove and Reconnect to CHI Wi-Fi Networks on Mobile Devices The account you use to log on to your CHI computer (also the account
How to Update Your CHI Network Password and Avoid Lockouts Remember to Remove and Reconnect to CHI Wi-Fi Networks on Mobile Devices The account you use to log on to your CHI computer (also the account
Checkpoint Vpn Domain Manually Defined
 Checkpoint Vpn Domain Manually Defined Configuring Site to Site VPN with a Preshared Secret. Use these details to manually connect your Check Point 1100 Appliance to Cloud Services. topology: manully defined
Checkpoint Vpn Domain Manually Defined Configuring Site to Site VPN with a Preshared Secret. Use these details to manually connect your Check Point 1100 Appliance to Cloud Services. topology: manully defined
Installation and use of the UMass Dartmouth VPN Client (for Windows 10) Installing the VPN client
 Installation and use of the UMass Dartmouth VPN Client (for Windows 10) This document will help you install and use the Check Point Capsule VPN Client on Microsoft Windows 10 machines. Note: The following
Installation and use of the UMass Dartmouth VPN Client (for Windows 10) This document will help you install and use the Check Point Capsule VPN Client on Microsoft Windows 10 machines. Note: The following
Configure your office PC Allow remote connections to your office PC How to verify that it s set up correctly My Computer Properties Remote
 Configure your office PC 1 Allow remote connections to your office PC By default, your office PC doesn t accept remotee connections. Only members of the Technology Department can change this setting, so
Configure your office PC 1 Allow remote connections to your office PC By default, your office PC doesn t accept remotee connections. Only members of the Technology Department can change this setting, so
Gateway Guide. Leostream Gateway. Advanced Capacity and Connection Management for Hybrid Clouds
 Gateway Guide Leostream Gateway Advanced Capacity and Connection Management for Hybrid Clouds Version 9.0 June 2018 Contacting Leostream Leostream Corporation 271 Waverley Oaks Rd Suite 206 Waltham, MA
Gateway Guide Leostream Gateway Advanced Capacity and Connection Management for Hybrid Clouds Version 9.0 June 2018 Contacting Leostream Leostream Corporation 271 Waverley Oaks Rd Suite 206 Waltham, MA
The Python Mini-Degree Development Environment Guide
 The Python Mini-Degree Development Environment Guide By Zenva Welcome! We are happy to welcome you to the premiere Python development program available on the web The Python Mini-Degree by Zenva. This
The Python Mini-Degree Development Environment Guide By Zenva Welcome! We are happy to welcome you to the premiere Python development program available on the web The Python Mini-Degree by Zenva. This
Connect to eduroam WiFi
 Connect to eduroam WiFi List Procedure for Windows 10... 2 Procedure for Windows 8... 4 Procedure for Windows 7... 6 Procedure for Mac... 11 Procedure for iphone, ipod Touch and ipad... 15 Procedure for
Connect to eduroam WiFi List Procedure for Windows 10... 2 Procedure for Windows 8... 4 Procedure for Windows 7... 6 Procedure for Mac... 11 Procedure for iphone, ipod Touch and ipad... 15 Procedure for
Remote Desktop Access
 Ready Reference 100208 Remote Desktop Access Introduction Remote Desktop Access for Windows XP Professional or Windows Vista Business provides access to a Windows session that is running on your computer
Ready Reference 100208 Remote Desktop Access Introduction Remote Desktop Access for Windows XP Professional or Windows Vista Business provides access to a Windows session that is running on your computer
ONESolution 16.1 Desktop Client Installation
 You must have FULL Administrator privileges to your PC, in order to install this software AND have completed the ONESolution training class with your attendance confirmed. If you do not have FULL Administrator
You must have FULL Administrator privileges to your PC, in order to install this software AND have completed the ONESolution training class with your attendance confirmed. If you do not have FULL Administrator
Student and Staff VPN User Documentation
 Student and Staff VPN User Documentation This document is broken down into the following sections for your convenience. 1) Quick start guide 2) Installing the VPN software (detailed version) 3) Using the
Student and Staff VPN User Documentation This document is broken down into the following sections for your convenience. 1) Quick start guide 2) Installing the VPN software (detailed version) 3) Using the
NetIQ Advanced Authentication Framework - Extensible Authentication Protocol Server. Administrator's Guide. Version 5.1.0
 NetIQ Advanced Authentication Framework - Extensible Authentication Protocol Server Administrator's Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Support
NetIQ Advanced Authentication Framework - Extensible Authentication Protocol Server Administrator's Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Support
AT&T Global Network Client for Mac User s Guide Version 2.0.0
 Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 2.0.0 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 2.0.0 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
MULTI-FACTOR AUTHENTICATION SET-UP
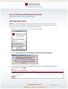 MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application FIRST TIME ENROLLMENT NOTE: Your computer settings cannot be set to clear cookies upon exit, otherwise you will be prompted to enter
MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application FIRST TIME ENROLLMENT NOTE: Your computer settings cannot be set to clear cookies upon exit, otherwise you will be prompted to enter
AT&T Global Network Client for Mac User s Guide Version 1.7.3
 Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 1.7.3 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 1.7.3 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Remote Access via Cisco VPN Client
 Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Sophos Connect. help
 help Contents About... 1 Installing...1 Uninstalling... 1 Connections...3 Import connection... 3 Connect...4 Connection options...7 Events...9 Troubleshooting events... 10 General troubleshooting... 13
help Contents About... 1 Installing...1 Uninstalling... 1 Connections...3 Import connection... 3 Connect...4 Connection options...7 Events...9 Troubleshooting events... 10 General troubleshooting... 13
User guide AppGate version 11.3-LTS-u1
 User guide AppGate version 11.3-LTS-u1 User guide Table of Contents 1. About this user guide... 1 1.1. Who should use this user guide... 1 2. What is AppGate security server... 2 2.1. User account... 2
User guide AppGate version 11.3-LTS-u1 User guide Table of Contents 1. About this user guide... 1 1.1. Who should use this user guide... 1 2. What is AppGate security server... 2 2.1. User account... 2
Login Defender. Quick Guide. Copyright by Cryptware di Ugo Chirico
 Login Defender Quick Guide Copyright 2006-2012 by Cryptware di Ugo Chirico Cryptware - http://www.cryptware.it 5/12/2012 Index 1 Introduction... 3 1.1 Main features... 3 2 Installation... 3 3 Control Panel...
Login Defender Quick Guide Copyright 2006-2012 by Cryptware di Ugo Chirico Cryptware - http://www.cryptware.it 5/12/2012 Index 1 Introduction... 3 1.1 Main features... 3 2 Installation... 3 3 Control Panel...
System Requirements for Mac OS X Clients. Download View Client Package. **Take note: This guide is not a detailed step by step guide.
 **Take note: This guide is not a detailed step by step guide. System Requirements for Mac OS X Clients Download View Client Package 1. Launch Safari. 2. Please click on FAQs, navigate to How-to sub-category
**Take note: This guide is not a detailed step by step guide. System Requirements for Mac OS X Clients Download View Client Package 1. Launch Safari. 2. Please click on FAQs, navigate to How-to sub-category
Outside Access System Manual
 Outside Access System Manual Contents table 1. Outside Access System Web Sing in 2. SBC System Access 3. SBC System Usage 4. SmartPhone (Android) Access 5. SmartPhone (iphone,ipad) Access 2016. 01 Security
Outside Access System Manual Contents table 1. Outside Access System Web Sing in 2. SBC System Access 3. SBC System Usage 4. SmartPhone (Android) Access 5. SmartPhone (iphone,ipad) Access 2016. 01 Security
CS Druva insync User Guide. 28 th Oct. 2011
 CS Druva insync User Guide 28 th Oct. 2011 Contents Installing the Druva insync Client... 1 1. Installation Prerequisites... 1 2. Installation on Microsoft Windows 7/ Vista/ XP... 1 3. Installation on
CS Druva insync User Guide 28 th Oct. 2011 Contents Installing the Druva insync Client... 1 1. Installation Prerequisites... 1 2. Installation on Microsoft Windows 7/ Vista/ XP... 1 3. Installation on
Manage End Users. End User Overview. End User Management Tasks. End User Overview, on page 1 End User Management Tasks, on page 1
 End User Overview, on page 1 End User Management Tasks, on page 1 End User Overview When administering an up and running system, you may need to make updates to the list of configured end users in your
End User Overview, on page 1 End User Management Tasks, on page 1 End User Overview When administering an up and running system, you may need to make updates to the list of configured end users in your
