Romain Thomas - Static instrumentation based on executable file formats
|
|
|
- Barbara Carroll
- 5 years ago
- Views:
Transcription
1 Romain Thomas - rthomas@quarkslab.com Static instrumentation based on executable file formats
2 About Romain Thomas - Security engineer at Quarkslab Working on various topics: Android, (de)obfuscation, software protection and reverse engineering Author of LIEF
3 Executable Formats Executable Formats: Overview
4 Executable Formats First layer of information when analysing a binary 1 entrypoint, libraries,
5 Executable Formats First layer of information when analysing a binary Provide metadata 1 used by the operating system to load the binary. 1 entrypoint, libraries,
6 Executable Formats OSX / ios: Mach-O Linux: ELF Windows: PE Android: ELF, OAT
7 Executable Formats Why modify formats?
8 Executable Formats Change segments Disable / sections ASLR permissions Userland More privileged area Format Loader Kernel Add shared libraries Load Perform shared relocations libraries Set Create Map permissions content Process
9 Executable Formats Change segments Disable / sections ASLR permissions Userland More privileged area Format Loader Kernel Add shared libraries Load Perform shared relocations libraries Set Create Map permissions content Process
10 Executable Formats Change segments Disable / sections ASLR permissions Userland More privileged area Format Loader Kernel Add shared libraries Load Perform shared relocations libraries Set Create Map permissions content Process
11 Executable Formats Change segments Disable / sections ASLR permissions Userland More privileged area Format Loader Kernel Add shared libraries Load Perform shared relocations libraries Set Create Map permissions content Process
12 Executable Formats Change segments Disable / sections ASLR permissions Userland More privileged area Format Loader Kernel Add shared libraries Load Perform shared relocations libraries Set Create Map permissions content Process
13 Executable Formats Change segments Disable / sections ASLR permissions Userland More privileged area Format Loader Kernel Add shared libraries Load Perform shared relocations libraries Set Create Map permissions content Process
14 Executable Formats Change segments Disable / sections ASLR permissions Userland More privileged area Format Loader Kernel Add shared libraries Load Perform shared relocations libraries Set Create Map permissions content Process
15 Executable Formats Change segments Disable / sections ASLR permissions Userland More privileged area Format Loader Kernel Add shared libraries Load Perform shared relocations libraries Set Create Map permissions content Process
16 Executable Formats Change segments Disable / sections ASLR permissions Userland More privileged area Format Loader Kernel Add shared libraries Load Perform shared relocations libraries Set Create Map permissions content Process
17 Executable Formats LIEF: Library to Instrument Executable Formats
18 LIEF One library to deal with ELF, PE, Mach-O Core in C++ Bindings for different languages: Python, C 2,... Enable modification on these formats User friendly API 2 C binding is not as mature as Python and C++
19 Executable Formats DEX File Object VDEX File Object ART File Object Parser ELF Binary Object PE Binary Object Mach-O Fat Binary Object OAT Binary Object Builder Abstract Binary Information extraction Information adding...
20 Executable Formats import lief target = lief.parse("elf/pe/mach-o/oat") print(target.entrypoint)
21 Executable Formats import lief target = lief.parse("elf/pe/mach-o/oat") for section in target.sections: print(section.virtual_address) process(section.content)
22 Executable Formats import lief target = lief.parse("some.exe") target.tls.callbacks.append(0x.) target.write("new.exe")
23 Executable Formats import lief target = lief.parse() section = lief.elf.section(".text2") section.content = [0x90] * 0x1000 target += section target.write("new.elf")
24 Executable Formats Next parts introduce interesting modifications on formats: Hooking Exporting hidden functions Code injection through shared libraries
25 PE Hooking PE Hooking
26 PE Hooking Regarding to PE files, LIEF enables to rebuild the import table elsewhere in the binary so that one can add new functions, new libraries or patch the Import Address Table.
27 Figure Original IAT Example
28 Example The following code patch the IAT entry of acrt_iob_func with a trampoline to the function 0x pe = lief.parse("some.exe") pe.hook_function(" acrt_iob_func", 0x ) builder = lief.pe.builder(pe) builder.build_imports(true).patch_imports(true) builder.build() builder.write("hooked.exe")
29 Example
30 Figure Original IAT patched with trampoline functions Example
31 Example Figure Trampoline for non-hooked function Figure Trampoline for hooked function
32 Example Limitations This method only works if accesses to the IAT are performed with call instructions. Especially it doesn t if there is lea on the original IAT
33 ELF Hooking Regarding to ELF files, hooking can be done with a patch of the plt/got.
34 ELF plt/got.text : jmp plt : jmp : push 0x b: jmp <.plt> 3.got : 0x400486
35 ELF plt/got.text : jmp plt : jmp : push 0x b: jmp <.plt> 3.got : 0x400486
36 ELF plt/got.text : jmp plt : jmp : push 0x b: jmp <.plt> 3.got : 0x400486
37 ELF plt/got.text : jmp plt : jmp : push 0x b: jmp <.plt> 3.got : 0x400486
38 Figure Relocations associated with plt/got ELF plt/got
39 ELF plt/got import lief elf = lief.parse("some_elf") elf.patch_pltgot("memcmp", 0xAAAAAAAA) elf.write("elf_modified")
40 ELF plt/got.text : jmp plt : jmp : push 0x b: jmp <.plt>.got : XXXXXX <memcmp@hook> 3.hook XXXXXX: memcmp hooked
41 ELF plt/got.text : jmp plt : jmp : push 0x b: jmp <.plt>.got : XXXXXX <memcmp@hook> 3.hook XXXXXX: memcmp hooked
42 ELF plt/got.text : jmp plt : jmp : push 0x b: jmp <.plt>.got : XXXXXX <memcmp@hook> 3.hook XXXXXX: memcmp hooked
43 ELF plt/got.text : jmp plt : jmp : push 0x b: jmp <.plt>.got : XXXXXX <memcmp@hook> 3.hook XXXXXX: memcmp hooked
44 Exporting Functions Exporting Functions
45 Idea
46 Idea
47 Example int main(int argc, char argv[]) { if (COMPLICATED CONDITION) { fuzz_me(argv[1]); } return 0; }
48 Example
49 Figure Original Symbol Table Example
50 Example import lief target = lief.parse("target") target.add_exported_function(0x63a, "to_fuzz") target.write("target_modified")
51 Example
52 Figure New Symbol Table Example
53 Example typedef void(*fnc_t)(const char*); // Access with dlopen / dlsym void* hdl = dlopen("./target_modified", RTLD_LAZY); fnc_t to_fuzz = (fnc_t)dlsym(hdl, "to_fuzz"); to_fuzz(to FEED);
54 Code injection Code injection through shared libraries
55 Context Different techniques exist to inject code: Using environment variables: LD_PRELOAD, DYLD_INSERT_LIBRARIES,... Using operating system API: WriteProcessMemory, ptrace,... Using custom kernel drivers Using executable formats
56 Context Depending on the scenario, methods can be suitable or not. Next part shows a method based on shared libraries and executable formats to leverage code injection.
57 Linked Libraries - Loading New library: libexample.so Userland More privileged area Format Loader Kernel Execute: my_constructor()
58 Injection process 1. Declare a constructor attribute ((constructor)) void my_constructor(void) { printf("run payload\n"); } gcc -fpic -shared libexample.c -o libexample.so gcc -fpic -shared libexample.c -o libexample.dylib
59 Injection process 2. Add a dependency import lief # ELF elf = lief.parse("/usr/bin/ssh") elf.add_library("libexample.so") elf.write("ssh_modified") # Mach-O macho = lief.parse("/bin/ls") macho.add_library("/users/romain/libexample.dylib") macho.write("ls_modified") # PE: Not implemented yet
60 Injection process
61 Injection process
62 Frida & LIEF Frida & LIEF: Frida injection in an Android application
63 Frida & LIEF Using the techniques previously described, we can use Frida on an APK having at least one native library without root privileges.
64 Figure Original APK Frida & LIEF
65 Frida & LIEF Figure Original APK Figure APK embedding Frida
66 Figure Original native library Frida & LIEF
67 Figure Modified native library Frida & LIEF
68 libgadget.config.so Frida & LIEF "interaction": { "type": "script", "path": "/data/local/tmp/myscript.js", "on_change": "reload" } /data/local/tmp/myscript.js Java.perform(function () { var Log = Java.use("android.util.Log"); var tag = "frida-lief"; Log.v(tag, "I'm in the process!"); Process.enumerateModules({ onmatch: function (module) { Log.v(tag, "Module: " + module.name); }, oncomplete: function () {} });});
69 Frida & LIEF Demo
70 Format modification Such modifications on formats are not new 34. However, it s implemented in LIEF with a new approach that doesn t rely on replacing existing entries, using padding, removing entries,... 3 Mayem Phrack #61 4
71 Format modification Instead, it keeps a consistent state of the format: Export trie Symbol hash tables Relocations Symbol versions Rebase opcodes...
72 What s next LIEF 0.9 comes with new formats related to Android: OAT VDEX DEX ART Modification of these formats is not available yet but further version will support it.
73 What s next How Samsung Secures Your Wallet & How To Break It - Black Hat 2017 Tencent s Xuanwu Lab
74 What s next Inside Android s SafetyNet Attestation: Attack and Defense - Ekoparty 2017 Collin Mulliner
75 What s next Next version will also include support for Mach-O modifications: Add unlimited number of Load commands Add libraries Change signature...
76 Thank You
77
LIEF: Library to Instrument Executable Formats
 RMLL 2017 Romain Thomas - rthomas@quarkslab.com LIEF: Library to Instrument Executable Formats Table of Contents Introduction Project Overview Demo Conclusion About Romain Thomas (rthomas@quarkslab.com)
RMLL 2017 Romain Thomas - rthomas@quarkslab.com LIEF: Library to Instrument Executable Formats Table of Contents Introduction Project Overview Demo Conclusion About Romain Thomas (rthomas@quarkslab.com)
Advances in Linux process forensics with ECFS
 Advances in Linux process forensics with ECFS Quick history Wanted to design a process snapshot format native to VMA Vudu http://www.bitlackeys.org/#vmavudu ECFS proved useful for other projects as well
Advances in Linux process forensics with ECFS Quick history Wanted to design a process snapshot format native to VMA Vudu http://www.bitlackeys.org/#vmavudu ECFS proved useful for other projects as well
Runtime Process Insemination
 Runtime Process Insemination Shawn lattera Webb SoldierX https://www.soldierx.com/ Who Am I? Just another blogger Professional Security Analyst Twelve-year C89 programmer Member of SoldierX, BinRev, and
Runtime Process Insemination Shawn lattera Webb SoldierX https://www.soldierx.com/ Who Am I? Just another blogger Professional Security Analyst Twelve-year C89 programmer Member of SoldierX, BinRev, and
A novel runtime technique for identifying malicious applications
 HUNTING ANDROID MALWARE A novel runtime technique for identifying malicious applications WHOAMI @brompwnie THANK YOU SensePost Heroku OUTLINE The... Problem Question Idea PoC Results Conclusion THE PROBLEM
HUNTING ANDROID MALWARE A novel runtime technique for identifying malicious applications WHOAMI @brompwnie THANK YOU SensePost Heroku OUTLINE The... Problem Question Idea PoC Results Conclusion THE PROBLEM
July 14, EPITA Systems/Security Laboratory (LSE) Code sandboxing. Alpha Abdoulaye - Pierre Marsais. Introduction. Solutions.
 EPITA Systems/Security Laboratory (LSE) July 14, 2017 1 / 34 2 / 34 What do we want? Limit usage of some resources such as system calls and shared object functions But not from the whole program (we trust
EPITA Systems/Security Laboratory (LSE) July 14, 2017 1 / 34 2 / 34 What do we want? Limit usage of some resources such as system calls and shared object functions But not from the whole program (we trust
First order of Business
 First order of Business First order of Business You probably feel like this MBE TA s Hardware Enforced Model 0: Privileged, Kernelspace 3: Restricted, Userspace Hardware Enforced Model 0: Privileged,
First order of Business First order of Business You probably feel like this MBE TA s Hardware Enforced Model 0: Privileged, Kernelspace 3: Restricted, Userspace Hardware Enforced Model 0: Privileged,
Reverse Engineering Malware Dynamic Analysis of Binary Malware II
 Reverse Engineering Malware Dynamic Analysis of Binary Malware II Jarkko Turkulainen F-Secure Corporation Protecting the irreplaceable f-secure.com Advanced dynamic analysis Debugger scripting Hooking
Reverse Engineering Malware Dynamic Analysis of Binary Malware II Jarkko Turkulainen F-Secure Corporation Protecting the irreplaceable f-secure.com Advanced dynamic analysis Debugger scripting Hooking
secubt Hacking the Hackers with User Space Virtualization
 secubt Hacking the Hackers with User Space Virtualization Mathias Payer Mathias Payer: secubt User Space Virtualization 1 Motivation Virtualizing and encapsulating running programs
secubt Hacking the Hackers with User Space Virtualization Mathias Payer Mathias Payer: secubt User Space Virtualization 1 Motivation Virtualizing and encapsulating running programs
Fixing/Making Holes in Binaries
 Fixing/Making Holes in Binaries The Easy, The Hard, The Time Consuming Shaun Clowes Ð shaun@securereality.com.au What are we doing? Changing the behaviour of programs Directly modifying the program in
Fixing/Making Holes in Binaries The Easy, The Hard, The Time Consuming Shaun Clowes Ð shaun@securereality.com.au What are we doing? Changing the behaviour of programs Directly modifying the program in
Hackveda Training - Ethical Hacking, Networking & Security
 Hackveda Training - Ethical Hacking, Networking & Security Day1: Hacking windows 7 / 8 system and security Part1 a.) Windows Login Password Bypass manually without CD / DVD b.) Windows Login Password Bypass
Hackveda Training - Ethical Hacking, Networking & Security Day1: Hacking windows 7 / 8 system and security Part1 a.) Windows Login Password Bypass manually without CD / DVD b.) Windows Login Password Bypass
syscall_intercept A user space library for intercepting system calls Author Name, Company Krzysztof Czuryło, Intel
 Talk syscall_intercept Title Here A user space library for intercepting system calls Author Name, Company Krzysztof Czuryło, Intel What it is? Provides a low-level interface for hooking Linux system calls
Talk syscall_intercept Title Here A user space library for intercepting system calls Author Name, Company Krzysztof Czuryło, Intel What it is? Provides a low-level interface for hooking Linux system calls
Protecting Against Unexpected System Calls
 Protecting Against Unexpected System Calls C. M. Linn, M. Rajagopalan, S. Baker, C. Collberg, S. K. Debray, J. H. Hartman Department of Computer Science University of Arizona Presented By: Mohamed Hassan
Protecting Against Unexpected System Calls C. M. Linn, M. Rajagopalan, S. Baker, C. Collberg, S. K. Debray, J. H. Hartman Department of Computer Science University of Arizona Presented By: Mohamed Hassan
Post exploitation techniques on OSX and Iphone. Vincenzo Iozzo
 Post exploitation techniques on OSX and Iphone Vincenzo Iozzo vincenzo.iozzo@zynamics.com Who I am Student at Politecnico di Milano Security Consultant at Secure Network srl Reverse Engineer at zynamics
Post exploitation techniques on OSX and Iphone Vincenzo Iozzo vincenzo.iozzo@zynamics.com Who I am Student at Politecnico di Milano Security Consultant at Secure Network srl Reverse Engineer at zynamics
VirtualSwindle: An Automated Attack Against In-App Billing on Android
 Northeastern University Systems Security Lab VirtualSwindle: An Automated Attack Against In-App Billing on Android ASIACCS 2014 Collin Mulliner, William Robertson, Engin Kirda {crm,wkr,ek}[at]ccs.neu.edu
Northeastern University Systems Security Lab VirtualSwindle: An Automated Attack Against In-App Billing on Android ASIACCS 2014 Collin Mulliner, William Robertson, Engin Kirda {crm,wkr,ek}[at]ccs.neu.edu
On The Effectiveness of Address-Space Randomization. H. Shacham, M. Page, B. Pfaff, E.-J. Goh, N. Modadugu, and D. Boneh Stanford University CCS 2004
 On The Effectiveness of Address-Space Randomization H. Shacham, M. Page, B. Pfaff, E.-J. Goh, N. Modadugu, and D. Boneh Stanford University CCS 2004 Code-Injection Attacks Inject malicious executable code
On The Effectiveness of Address-Space Randomization H. Shacham, M. Page, B. Pfaff, E.-J. Goh, N. Modadugu, and D. Boneh Stanford University CCS 2004 Code-Injection Attacks Inject malicious executable code
Link 8.A Dynamic Linking
 Link 8.A Dynamic Linking Young W. Lim 2019-01-04 Fri Young W. Lim Link 8.A Dynamic Linking 2019-01-04 Fri 1 / 42 Outline 1 Linking - 8.A Dynamic Linking Based on Dynamic linking with a shared library example
Link 8.A Dynamic Linking Young W. Lim 2019-01-04 Fri Young W. Lim Link 8.A Dynamic Linking 2019-01-04 Fri 1 / 42 Outline 1 Linking - 8.A Dynamic Linking Based on Dynamic linking with a shared library example
Incremental Linking with Gold
 Incremental Linking with Gold Linux Foundation Collaboration Summit April 5, 2012 Cary Coutant This work is licensed under the Creative Commons Attribution-NoDerivs 3.0 Unported License. To view a copy
Incremental Linking with Gold Linux Foundation Collaboration Summit April 5, 2012 Cary Coutant This work is licensed under the Creative Commons Attribution-NoDerivs 3.0 Unported License. To view a copy
Tackling runtime-based obfuscation in Android with TIRO
 Tackling runtime-based obfuscation in Android with Michelle Wong and David Lie University of Toronto Usenix Security 2018 Android malware and analysis Mobile devices are a valuable target for malware developers
Tackling runtime-based obfuscation in Android with Michelle Wong and David Lie University of Toronto Usenix Security 2018 Android malware and analysis Mobile devices are a valuable target for malware developers
Reverse Engineering Malware Binary Obfuscation and Protection
 Reverse Engineering Malware Binary Obfuscation and Protection Jarkko Turkulainen F-Secure Corporation Protecting the irreplaceable f-secure.com Binary Obfuscation and Protection What is covered in this
Reverse Engineering Malware Binary Obfuscation and Protection Jarkko Turkulainen F-Secure Corporation Protecting the irreplaceable f-secure.com Binary Obfuscation and Protection What is covered in this
Obtained the source code to gcc, one can just follow the instructions given in the INSTALL file for GCC.
 Building cross compilers Linux as the target platform Obtained the source code to gcc, one can just follow the instructions given in the INSTALL file for GCC. configure --target=i486-linux --host=xxx on
Building cross compilers Linux as the target platform Obtained the source code to gcc, one can just follow the instructions given in the INSTALL file for GCC. configure --target=i486-linux --host=xxx on
PRESS ROOT TO CONTINUE: DETECTING OSX AND WINDOWS BOOTKITS WITH RDFU
 Mario Vuksan & Tomislav PericinBlackHat USA 2013, Las Vegas PRESS ROOT TO CONTINUE: DETECTING OSX AND WINDOWS BOOTKITS WITH RDFU Agenda Our motivation Who are we Introduction to Unified extensible framework
Mario Vuksan & Tomislav PericinBlackHat USA 2013, Las Vegas PRESS ROOT TO CONTINUE: DETECTING OSX AND WINDOWS BOOTKITS WITH RDFU Agenda Our motivation Who are we Introduction to Unified extensible framework
A tale of ELFs and DWARFs
 A tale of ELFs and DWARFs A glimpse into the world of linkers, loaders and binary formats Volker Krause vkrause@kde.org @VolkerKrause Our Workflow Write code Run compiler... Run application Profit! Why
A tale of ELFs and DWARFs A glimpse into the world of linkers, loaders and binary formats Volker Krause vkrause@kde.org @VolkerKrause Our Workflow Write code Run compiler... Run application Profit! Why
Lecture 4 Processes. Dynamic Analysis. GDB
 Lecture 4 Processes. Dynamic Analysis. GDB Computer and Network Security 23th of October 2017 Computer Science and Engineering Department CSE Dep, ACS, UPB Lecture 4, Processes. Dynamic Analysis. GDB 1/45
Lecture 4 Processes. Dynamic Analysis. GDB Computer and Network Security 23th of October 2017 Computer Science and Engineering Department CSE Dep, ACS, UPB Lecture 4, Processes. Dynamic Analysis. GDB 1/45
String Oriented Programming Exploring Format String Attacks. Mathias Payer
 String Oriented Programming Exploring Format String Attacks Mathias Payer Motivation Additional protection mechanisms prevent many existing attack vectors Format string exploits are often overlooked Drawback:
String Oriented Programming Exploring Format String Attacks Mathias Payer Motivation Additional protection mechanisms prevent many existing attack vectors Format string exploits are often overlooked Drawback:
Android Dynamic Linker - Marshmallow
 Android Dynamic Linker - Marshmallow WANG Zhenhua, i@jackwish.net Abstract Dynamic linker, links shared libraries together to be able to run, has been a fundamental mechanism in modern operating system
Android Dynamic Linker - Marshmallow WANG Zhenhua, i@jackwish.net Abstract Dynamic linker, links shared libraries together to be able to run, has been a fundamental mechanism in modern operating system
Virtuoso: Narrowing the Semantic Gap in Virtual Machine Introspection
 Virtuoso: Narrowing the Semantic Gap in Virtual Machine Introspection Brendan Dolan-Gavitt *, Tim Leek, Michael Zhivich, Jonathon Giffin *, and Wenke Lee * * Georgia Institute of Technology MIT Lincoln
Virtuoso: Narrowing the Semantic Gap in Virtual Machine Introspection Brendan Dolan-Gavitt *, Tim Leek, Michael Zhivich, Jonathon Giffin *, and Wenke Lee * * Georgia Institute of Technology MIT Lincoln
Q: Exploit Hardening Made Easy
 Q: Exploit Hardening Made Easy E.J. Schwartz, T. Avgerinos, and D. Brumley. In Proc. USENIX Security Symposium, 2011. CS 6301-002: Language-based Security Dr. Kevin Hamlen Attacker s Dilemma Problem Scenario
Q: Exploit Hardening Made Easy E.J. Schwartz, T. Avgerinos, and D. Brumley. In Proc. USENIX Security Symposium, 2011. CS 6301-002: Language-based Security Dr. Kevin Hamlen Attacker s Dilemma Problem Scenario
Android Application Sandbox. Thomas Bläsing DAI-Labor TU Berlin
 Android Application Sandbox Thomas Bläsing DAI-Labor TU Berlin Agenda Introduction What is Android? Malware on smartphones Common countermeasures on the Android platform Use-Cases Design Conclusion Summary
Android Application Sandbox Thomas Bläsing DAI-Labor TU Berlin Agenda Introduction What is Android? Malware on smartphones Common countermeasures on the Android platform Use-Cases Design Conclusion Summary
Lecture 08 Control-flow Hijacking Defenses
 Lecture 08 Control-flow Hijacking Defenses Stephen Checkoway University of Illinois at Chicago CS 487 Fall 2017 Slides adapted from Miller, Bailey, and Brumley Control Flow Hijack: Always control + computation
Lecture 08 Control-flow Hijacking Defenses Stephen Checkoway University of Illinois at Chicago CS 487 Fall 2017 Slides adapted from Miller, Bailey, and Brumley Control Flow Hijack: Always control + computation
Security Workshop HTS. LSE Team. February 3rd, 2016 EPITA / 40
 Security Workshop HTS LSE Team EPITA 2018 February 3rd, 2016 1 / 40 Introduction What is this talk about? Presentation of some basic memory corruption bugs Presentation of some simple protections Writing
Security Workshop HTS LSE Team EPITA 2018 February 3rd, 2016 1 / 40 Introduction What is this talk about? Presentation of some basic memory corruption bugs Presentation of some simple protections Writing
Metasm. a ruby (dis)assembler. Yoann Guillot. 20 october 2007
 Metasm a ruby (dis)assembler Yoann Guillot 20 october 2007 Metasm Presentation I am Yoann Guillot I work for Sogeti/ESEC in the security R&D lab Metasm HACK.LU 2007 2 / 23 Plan Metasm 1 Metasm 2 Metasm
Metasm a ruby (dis)assembler Yoann Guillot 20 october 2007 Metasm Presentation I am Yoann Guillot I work for Sogeti/ESEC in the security R&D lab Metasm HACK.LU 2007 2 / 23 Plan Metasm 1 Metasm 2 Metasm
LIVEPATCH MODULE CREATION. LPC 2016 Josh Poimboeuf
 LPC 2016 Josh Poimboeuf Overview Review current approaches kpatch-build (out-of-tree) kbuild (in-tree) Propose common in-tree approach 2 kpatch-build $ kpatch-build dirtycow.patch Fedora/Red Hat distribution
LPC 2016 Josh Poimboeuf Overview Review current approaches kpatch-build (out-of-tree) kbuild (in-tree) Propose common in-tree approach 2 kpatch-build $ kpatch-build dirtycow.patch Fedora/Red Hat distribution
Writing Exploits. Nethemba s.r.o.
 Writing Exploits Nethemba s.r.o. norbert.szetei@nethemba.com Motivation Basic code injection W^X (DEP), ASLR, Canary (Armoring) Return Oriented Programming (ROP) Tools of the Trade Metasploit A Brief History
Writing Exploits Nethemba s.r.o. norbert.szetei@nethemba.com Motivation Basic code injection W^X (DEP), ASLR, Canary (Armoring) Return Oriented Programming (ROP) Tools of the Trade Metasploit A Brief History
Università Ca Foscari Venezia
 Stack Overflow Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction Buffer overflow is due to careless programming in unsafe languages like C
Stack Overflow Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction Buffer overflow is due to careless programming in unsafe languages like C
Implementing your own generic unpacker
 HITB Singapore 2015 Julien Lenoir - julien.lenoir@airbus.com October 14, 2015 Outline 1 Introduction 2 Test driven design 3 Fine tune algorithm 4 Demo 5 Results 6 Conclusion October 14, 2015 2 Outline
HITB Singapore 2015 Julien Lenoir - julien.lenoir@airbus.com October 14, 2015 Outline 1 Introduction 2 Test driven design 3 Fine tune algorithm 4 Demo 5 Results 6 Conclusion October 14, 2015 2 Outline
Pangu 9 Internals. Tielei Wang and Hao Xu
 Pangu 9 Internals Tielei Wang and Hao Xu Team Pangu Agenda ios Security Overview Pangu 9 Overview Userland Exploits Kernel Patching in Kernel Patch Protections Persistent Code Signing Bypass Conclusion
Pangu 9 Internals Tielei Wang and Hao Xu Team Pangu Agenda ios Security Overview Pangu 9 Overview Userland Exploits Kernel Patching in Kernel Patch Protections Persistent Code Signing Bypass Conclusion
Reverse Engineering Swift Apps. Michael Gianarakis Rootcon X 2016
 Reverse Engineering Swift Apps Michael Gianarakis Rootcon X 2016 # whoami @mgianarakis Director of SpiderLabs APAC at Trustwave SecTalks Organiser (@SecTalks_BNE) Flat Duck Justice Warrior #ducksec Motivation
Reverse Engineering Swift Apps Michael Gianarakis Rootcon X 2016 # whoami @mgianarakis Director of SpiderLabs APAC at Trustwave SecTalks Organiser (@SecTalks_BNE) Flat Duck Justice Warrior #ducksec Motivation
CMPSC 497 Buffer Overflow Vulnerabilities
 Systems and Internet Infrastructure Security Network and Security Research Center Department of Computer Science and Engineering Pennsylvania State University, University Park PA CMPSC 497 Buffer Overflow
Systems and Internet Infrastructure Security Network and Security Research Center Department of Computer Science and Engineering Pennsylvania State University, University Park PA CMPSC 497 Buffer Overflow
PROTOTYPING AND REVERSE ENGINEERING WITH FRIDA BSIDES LONDON 2017 JAHMEL HARRIS
 PROTOTYPING AND REVERSE ENGINEERING WITH FRIDA BSIDES LONDON 2017 JAHMEL HARRIS THIS WORKSHOP INTRODUCTION TO RAPID REVERSE ENGINEERING WITH FRIDA PRACTICAL EXERCISES (LIMIT THE THEORY) VIEW THE CODE!
PROTOTYPING AND REVERSE ENGINEERING WITH FRIDA BSIDES LONDON 2017 JAHMEL HARRIS THIS WORKSHOP INTRODUCTION TO RAPID REVERSE ENGINEERING WITH FRIDA PRACTICAL EXERCISES (LIMIT THE THEORY) VIEW THE CODE!
Link 8. Dynamic Linking
 Link 8. Dynamic Linking Young W. Lim 2018-12-27 Thr Young W. Lim Link 8. Dynamic Linking 2018-12-27 Thr 1 / 66 Outline 1 Linking - 8. Dynamic Linking Based on Dynamic linking with a shared library example
Link 8. Dynamic Linking Young W. Lim 2018-12-27 Thr Young W. Lim Link 8. Dynamic Linking 2018-12-27 Thr 1 / 66 Outline 1 Linking - 8. Dynamic Linking Based on Dynamic linking with a shared library example
Rootkits n Stuff
 Rootkits n Stuff www.sigmil.org What a rootkit is(n t) IS Software intended to conceal running processes, files, etc from the OS A way to maintain control of a system after compromising it. ISN T A buffer
Rootkits n Stuff www.sigmil.org What a rootkit is(n t) IS Software intended to conceal running processes, files, etc from the OS A way to maintain control of a system after compromising it. ISN T A buffer
Let's cyber: hacking, 0days and vulnerability research. PATROKLOS ARGYROUDIS CENSUS S.A.
 Let's cyber: hacking, 0days and vulnerability research PATROKLOS ARGYROUDIS CENSUS S.A. argp@census-labs.com www.census-labs.com Who am I Researcher at CENSUS S.A. - Vulnerability research, reverse engineering,
Let's cyber: hacking, 0days and vulnerability research PATROKLOS ARGYROUDIS CENSUS S.A. argp@census-labs.com www.census-labs.com Who am I Researcher at CENSUS S.A. - Vulnerability research, reverse engineering,
Link 7. Dynamic Linking
 Link 7. Dynamic Linking Young W. Lim 2018-10-05 Fri Young W. Lim Link 7. Dynamic Linking 2018-10-05 Fri 1 / 26 Outline 1 Linking - 7. Dynamic Linking Based on Dynamic Shared Library Examples Young W. Lim
Link 7. Dynamic Linking Young W. Lim 2018-10-05 Fri Young W. Lim Link 7. Dynamic Linking 2018-10-05 Fri 1 / 26 Outline 1 Linking - 7. Dynamic Linking Based on Dynamic Shared Library Examples Young W. Lim
CYSE 411/AIT681 Secure Software Engineering Topic #8. Secure Coding: Pointer Subterfuge
 CYSE 411/AIT681 Secure Software Engineering Topic #8. Secure Coding: Pointer Subterfuge Instructor: Dr. Kun Sun This lecture: [Seacord]: Chapter 3 Readings 2 Outline Secure Coding Topics String management
CYSE 411/AIT681 Secure Software Engineering Topic #8. Secure Coding: Pointer Subterfuge Instructor: Dr. Kun Sun This lecture: [Seacord]: Chapter 3 Readings 2 Outline Secure Coding Topics String management
Windows HIPS evaluation with Slipfest
 Windows HIPS evaluation with Slipfest Julien Tinnes, Yoann Guillot France Telecom R&D What is a HIPS? Host intrusion prevention system Tries to generically prevent the exploitation of security flaws Tries
Windows HIPS evaluation with Slipfest Julien Tinnes, Yoann Guillot France Telecom R&D What is a HIPS? Host intrusion prevention system Tries to generically prevent the exploitation of security flaws Tries
JUN-OH LEE JU-SEON LEE JEONG-MIN LEE
 CTF player in team CyKor Reverse engineer, Exploit Developer (prized in 2018 0ctf final and 2018 wctf) Institutor at Korea Univ. security class KITRI BoB Vulnerability Analysis track JUN-OH LEE JEONG-MIN
CTF player in team CyKor Reverse engineer, Exploit Developer (prized in 2018 0ctf final and 2018 wctf) Institutor at Korea Univ. security class KITRI BoB Vulnerability Analysis track JUN-OH LEE JEONG-MIN
Secure Coding Topics. Readings. CYSE 411/AIT681 Secure Software Engineering. Pointer Subterfuge. Outline. Data Locations (cont d) Data Locations
 This lecture: [Seacord]: Chapter 3 Readings CYSE 411/AIT681 Secure Software Engineering Topic #8. Secure Coding: Pointer Subterfuge Instructor: Dr. Kun Sun 2 Outline Secure Coding Topics String management
This lecture: [Seacord]: Chapter 3 Readings CYSE 411/AIT681 Secure Software Engineering Topic #8. Secure Coding: Pointer Subterfuge Instructor: Dr. Kun Sun 2 Outline Secure Coding Topics String management
Secure Coding Topics. CYSE 411/AIT681 Secure Software Engineering. Readings. Outline. This lecture: Topic #8. Secure Coding: Pointer Subterfuge
 CYSE 411/AIT681 Secure Software Engineering Topic #8. Secure Coding: Pointer Subterfuge Instructor: Dr. Kun Sun This lecture: [Seacord]: Chapter 3 Readings 2 Outline Secure Coding Topics String management
CYSE 411/AIT681 Secure Software Engineering Topic #8. Secure Coding: Pointer Subterfuge Instructor: Dr. Kun Sun This lecture: [Seacord]: Chapter 3 Readings 2 Outline Secure Coding Topics String management
A tool for the. Symbolic Execution. of Linux binaries
 A tool for the Symbolic Execution of Linux binaries About Symbolic Execution Dynamically explore all program branches. Inputs are considered symbolic variables. Symbols remain uninstantiated and become
A tool for the Symbolic Execution of Linux binaries About Symbolic Execution Dynamically explore all program branches. Inputs are considered symbolic variables. Symbols remain uninstantiated and become
Hack in the Box Trends and Tools. H D Moore
 Hack in the Box 2003 Advanced Exploit Development Trends and Tools H D Moore 1 Who Who am I? Co-founder of Digital Defense Security researcher (5+ years) Projects DigitalOffense.net Metasploit.com 2 What
Hack in the Box 2003 Advanced Exploit Development Trends and Tools H D Moore 1 Who Who am I? Co-founder of Digital Defense Security researcher (5+ years) Projects DigitalOffense.net Metasploit.com 2 What
Evinrude. How to build a Petri Net-Based IDS from Program Sources. MeFoSyLoMa Meeting
 MeFoSyLoMa Meeting Jean-Baptiste Voron - LIP6 (UPMC) Fabrice Kordon - LIP6 (UPMC) Liviu Iftode - DiscoLab (Rutgers University) Evinrude How to build a Petri Net-Based IDS from Program Sources December
MeFoSyLoMa Meeting Jean-Baptiste Voron - LIP6 (UPMC) Fabrice Kordon - LIP6 (UPMC) Liviu Iftode - DiscoLab (Rutgers University) Evinrude How to build a Petri Net-Based IDS from Program Sources December
PROGRAMMING IN C++ CVIČENÍ
 PROGRAMMING IN C++ CVIČENÍ INFORMACE Michal Brabec http://www.ksi.mff.cuni.cz/ http://www.ksi.mff.cuni.cz/~brabec/ brabec@ksi.mff.cuni.cz gmichal.brabec@gmail.com REQUIREMENTS FOR COURSE CREDIT Basic requirements
PROGRAMMING IN C++ CVIČENÍ INFORMACE Michal Brabec http://www.ksi.mff.cuni.cz/ http://www.ksi.mff.cuni.cz/~brabec/ brabec@ksi.mff.cuni.cz gmichal.brabec@gmail.com REQUIREMENTS FOR COURSE CREDIT Basic requirements
Advanced Mac OS X Rootkits. Dino Dai Zovi Chief Scientist Endgame Systems
 Advanced Mac OS X Rootkits Dino Dai Zovi Chief Scientist Endgame Systems Overview Mac OS X and Mach Why use Mach for rootkits? User-mode Mach rootkit techniques Kernel Mach rootkit techniques 2 WHAT IS
Advanced Mac OS X Rootkits Dino Dai Zovi Chief Scientist Endgame Systems Overview Mac OS X and Mach Why use Mach for rootkits? User-mode Mach rootkit techniques Kernel Mach rootkit techniques 2 WHAT IS
Buffer Overflows. A brief Introduction to the detection and prevention of buffer overflows for intermediate programmers.
 Buffer Overflows A brief Introduction to the detection and prevention of buffer overflows for intermediate programmers. By: Brian Roberts What is a buffer overflow? In languages that deal with data structures
Buffer Overflows A brief Introduction to the detection and prevention of buffer overflows for intermediate programmers. By: Brian Roberts What is a buffer overflow? In languages that deal with data structures
executable-only-memory-switch (XOM-Switch)
 executable-only-memory-switch (XOM-Switch) Hiding Your Code From Advanced Code Reuse Attacks in One Shot Mingwei Zhang, Ravi Sahita (Intel Labs) Daiping Liu (University of Delaware) 1 [Short BIO of Speaker]
executable-only-memory-switch (XOM-Switch) Hiding Your Code From Advanced Code Reuse Attacks in One Shot Mingwei Zhang, Ravi Sahita (Intel Labs) Daiping Liu (University of Delaware) 1 [Short BIO of Speaker]
ECE 598 Advanced Operating Systems Lecture 10
 ECE 598 Advanced Operating Systems Lecture 10 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 22 February 2018 Announcements Homework #5 will be posted 1 Blocking vs Nonblocking
ECE 598 Advanced Operating Systems Lecture 10 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 22 February 2018 Announcements Homework #5 will be posted 1 Blocking vs Nonblocking
Linkers and Loaders. CS 167 VI 1 Copyright 2008 Thomas W. Doeppner. All rights reserved.
 Linkers and Loaders CS 167 VI 1 Copyright 2008 Thomas W. Doeppner. All rights reserved. Does Location Matter? int main(int argc, char *[ ]) { return(argc); } main: pushl %ebp ; push frame pointer movl
Linkers and Loaders CS 167 VI 1 Copyright 2008 Thomas W. Doeppner. All rights reserved. Does Location Matter? int main(int argc, char *[ ]) { return(argc); } main: pushl %ebp ; push frame pointer movl
ARMv8.3 Pointer Authentication
 ARMv8.3 Pointer Authentication Mark Rutland Linux Security Summit September 14, 2017 ARM 2017 Background Memory protections are commonly deployed today... largely prevents code injection
ARMv8.3 Pointer Authentication Mark Rutland Linux Security Summit September 14, 2017 ARM 2017 Background Memory protections are commonly deployed today... largely prevents code injection
Unpacking the Packed Unpacker
 Unpacking the Packed Unpacker Reversing an Android Anti-Analysis Native Library Maddie Stone @maddiestone BlackHat USA 2018 Who am I? - Maddie Stone Reverse Engineer on Google s Android Security Team 5+
Unpacking the Packed Unpacker Reversing an Android Anti-Analysis Native Library Maddie Stone @maddiestone BlackHat USA 2018 Who am I? - Maddie Stone Reverse Engineer on Google s Android Security Team 5+
Lab 1: First Steps in C++ - Eclipse
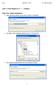 Lab 1: First Steps in C++ - Eclipse Step Zero: Select workspace 1. Upon launching eclipse, we are ask to chose a workspace: 2. We select a new workspace directory (e.g., C:\Courses ): 3. We accept the
Lab 1: First Steps in C++ - Eclipse Step Zero: Select workspace 1. Upon launching eclipse, we are ask to chose a workspace: 2. We select a new workspace directory (e.g., C:\Courses ): 3. We accept the
Building Advanced Coverage-guided Fuzzer for Program Binaries
 Building Advanced Coverage-guided Fuzzer for Program Binaries NGUYEN Anh Quynh WEI Lei 17/11/2017 Zero Nights, Moscow 2017 Self-introduction NGUYEN Anh Quynh, PhD
Building Advanced Coverage-guided Fuzzer for Program Binaries NGUYEN Anh Quynh WEI Lei 17/11/2017 Zero Nights, Moscow 2017 Self-introduction NGUYEN Anh Quynh, PhD
EDURange Student s Manual. September 14, 2015
 EDURange Student s Manual September 14, 2015 A Introduction This document will be updated as changes are made. EDURange is both a collection of interactive, collaborative cybersecurity exercises and a
EDURange Student s Manual September 14, 2015 A Introduction This document will be updated as changes are made. EDURange is both a collection of interactive, collaborative cybersecurity exercises and a
most elaborate jailbreak to ever hack your phone forbes Used 800,000 times in 6 hours after its release
 Brian Beckerle Latest iphone jailbreak, ios 6.1 Patched in latest version ios 6.1.3 4 of 6? Exploits fixed most elaborate jailbreak to ever hack your phone forbes Used 800,000 times in 6 hours after its
Brian Beckerle Latest iphone jailbreak, ios 6.1 Patched in latest version ios 6.1.3 4 of 6? Exploits fixed most elaborate jailbreak to ever hack your phone forbes Used 800,000 times in 6 hours after its
Reverse Engineering III: PE Format
 Reverse Engineering III: PE Format This document is only to be distributed to teachers and students of the Malware Analysis and Antivirus Technologies course and should only be used in accordance with
Reverse Engineering III: PE Format This document is only to be distributed to teachers and students of the Malware Analysis and Antivirus Technologies course and should only be used in accordance with
64-bit Imports Rebuilding and Unpacking
 64-bit Imports Rebuilding and Unpacking Sebastien Doucet ncircle 2010. All rights reserved. Who am I? Security Research Engineer at ncircle in Toronto My accent is from Montreal Used
64-bit Imports Rebuilding and Unpacking Sebastien Doucet ncircle 2010. All rights reserved. Who am I? Security Research Engineer at ncircle in Toronto My accent is from Montreal Used
The Attacker s POV Hacking Mobile Apps. in Your Enterprise to Reveal Real Vulns and Protect the Business. Tony Ramirez
 The Attacker s POV Hacking Mobile Apps in Your Enterprise to Reveal Real Vulns and Protect the Business Tony Ramirez AGENDA & SPEAKERS Introduction Attacks on Mobile Live Demo Recommendations Q&A Tony
The Attacker s POV Hacking Mobile Apps in Your Enterprise to Reveal Real Vulns and Protect the Business Tony Ramirez AGENDA & SPEAKERS Introduction Attacks on Mobile Live Demo Recommendations Q&A Tony
Secure Programming Lecture 3: Memory Corruption I (Stack Overflows)
 Secure Programming Lecture 3: Memory Corruption I (Stack Overflows) David Aspinall, Informatics @ Edinburgh 24th January 2017 Outline Roadmap Memory corruption vulnerabilities Instant Languages and Runtimes
Secure Programming Lecture 3: Memory Corruption I (Stack Overflows) David Aspinall, Informatics @ Edinburgh 24th January 2017 Outline Roadmap Memory corruption vulnerabilities Instant Languages and Runtimes
.kkapture: Guided tour
 Outline Introduction Basic principles The main idea Intercepting API calls kkapture piece by piece Video encoders Video APIs Audio Overview Learn what kkapture can do, how it does it...... and how to teach
Outline Introduction Basic principles The main idea Intercepting API calls kkapture piece by piece Video encoders Video APIs Audio Overview Learn what kkapture can do, how it does it...... and how to teach
Practical and Efficient Exploit Mitigation for Embedded Devices
 Practical and Efficient Exploit Mitigation for Embedded Devices Matthias Neugschwandtner IBM Research, Zurich Collin Mulliner Northeastern University, Boston Qualcomm Mobile Security Summit 2015 1 Embedded
Practical and Efficient Exploit Mitigation for Embedded Devices Matthias Neugschwandtner IBM Research, Zurich Collin Mulliner Northeastern University, Boston Qualcomm Mobile Security Summit 2015 1 Embedded
Lecture 9. PSiOS: Bring Your Own Privacy & Security to ios Devices. Tim Werthmann, Ralf Hund, Lucas Davi, Ahmad-Reza Sadeghi and Thorsten Holz
 Lecture 9 PSiOS: Bring Your Own Privacy & Security to ios Devices Tim Werthmann, Ralf Hund, Lucas Davi, Ahmad-Reza Sadeghi and Thorsten Holz Operating Systems Practical December 3, 2014 OSP Lecture 9,
Lecture 9 PSiOS: Bring Your Own Privacy & Security to ios Devices Tim Werthmann, Ralf Hund, Lucas Davi, Ahmad-Reza Sadeghi and Thorsten Holz Operating Systems Practical December 3, 2014 OSP Lecture 9,
Another introduction into radare2. {condret Lukas}
 Another introduction into radare2 {condret Lukas} Overview Features Components Api examples Introduction into Esil Problems Features Radare2 is not just one tool or a conglomeration of several tools. It
Another introduction into radare2 {condret Lukas} Overview Features Components Api examples Introduction into Esil Problems Features Radare2 is not just one tool or a conglomeration of several tools. It
CSC 405 Computer Security Shellcode
 CSC 405 Computer Security Shellcode Alexandros Kapravelos akaprav@ncsu.edu Attack plan Attack code Vulnerable code xor ebx, ebx xor eax, eax mov ebx,edi mov eax,edx sub eax,0x388 Vulnerable code xor ebx,
CSC 405 Computer Security Shellcode Alexandros Kapravelos akaprav@ncsu.edu Attack plan Attack code Vulnerable code xor ebx, ebx xor eax, eax mov ebx,edi mov eax,edx sub eax,0x388 Vulnerable code xor ebx,
McSema: Static Translation of X86 Instructions to LLVM
 McSema: Static Translation of X86 Instructions to LLVM ARTEM DINABURG, ARTEM@TRAILOFBITS.COM ANDREW RUEF, ANDREW@TRAILOFBITS.COM About Us Artem Security Researcher blog.dinaburg.org Andrew PhD Student,
McSema: Static Translation of X86 Instructions to LLVM ARTEM DINABURG, ARTEM@TRAILOFBITS.COM ANDREW RUEF, ANDREW@TRAILOFBITS.COM About Us Artem Security Researcher blog.dinaburg.org Andrew PhD Student,
Remix: On-demand Live Randomization
 Remix: On-demand Live Randomization Yue Chen, Zhi Wang, David Whalley, Long Lu* Florida State University, Stony Brook University* Background Buffer Overflow -> Code Injection Attack Background Buffer Overflow
Remix: On-demand Live Randomization Yue Chen, Zhi Wang, David Whalley, Long Lu* Florida State University, Stony Brook University* Background Buffer Overflow -> Code Injection Attack Background Buffer Overflow
Automatic Generation of Memory Analysis Plugins. Brendan Dolan-Gavitt OMFW 2011
 Automatic Generation of Memory Analysis Plugins Brendan Dolan-Gavitt OMFW 2011 Memory Analysis Challenges Creating new plugins can take a lot of work Generally needs access to symbols or source code Reverse
Automatic Generation of Memory Analysis Plugins Brendan Dolan-Gavitt OMFW 2011 Memory Analysis Challenges Creating new plugins can take a lot of work Generally needs access to symbols or source code Reverse
Giridhar Ravipati University of Wisconsin, Madison. The Deconstruction of Dyninst: Part 1- the SymtabAPI
 The Deconstruction of Dyninst Part 1: The SymtabAPI Giridhar Ravipati University of Wisconsin, Madison April 2007 Motivation Binary tools are increasingly common Two categories of operation Analysis :
The Deconstruction of Dyninst Part 1: The SymtabAPI Giridhar Ravipati University of Wisconsin, Madison April 2007 Motivation Binary tools are increasingly common Two categories of operation Analysis :
Buffer Overflow Vulnerability
 Buffer Overflow Vulnerability 1 Buffer Overflow Vulnerability Copyright c 2006 2014 Wenliang Du, Syracuse University. The development of this document is/was funded by three grants from the US National
Buffer Overflow Vulnerability 1 Buffer Overflow Vulnerability Copyright c 2006 2014 Wenliang Du, Syracuse University. The development of this document is/was funded by three grants from the US National
General ways to find and exploit directory traversals on Android. Xiang Xiaobo 360 Alpha Team
 General ways to find and exploit directory traversals on Android Xiang Xiaobo (Elphet) @ 360 Alpha Team About Us Alpha Team @360 Security 100+ Android vulnerabilities(google Qualcomm etc) Won the highest
General ways to find and exploit directory traversals on Android Xiang Xiaobo (Elphet) @ 360 Alpha Team About Us Alpha Team @360 Security 100+ Android vulnerabilities(google Qualcomm etc) Won the highest
Command Line Interface / Application Programming Interface (cliapi) Kevin Sheldrake rtfc.org.uk
 Command Line Interface / Application Programming Interface (cliapi) Kevin Sheldrake rtfc.org.uk WTF? cliapi is a tool that runs individual functions in an executable or library on linux. Sometimes a function
Command Line Interface / Application Programming Interface (cliapi) Kevin Sheldrake rtfc.org.uk WTF? cliapi is a tool that runs individual functions in an executable or library on linux. Sometimes a function
Win API hooking by using DBI: log me, baby!
 2009 ZARAGOZA Win API hooking by using DBI: log me, baby! Ricardo J. Rodríguez rjrodriguez@unizar.es All wrongs reversed CENTRO UNIVERSITARIO DE LA DEFENSA DOCENDI DISCENDI ANIMVS NOSVNIT NcN 2017 NoConName
2009 ZARAGOZA Win API hooking by using DBI: log me, baby! Ricardo J. Rodríguez rjrodriguez@unizar.es All wrongs reversed CENTRO UNIVERSITARIO DE LA DEFENSA DOCENDI DISCENDI ANIMVS NOSVNIT NcN 2017 NoConName
Roadmap: Security in the software lifecycle. Memory corruption vulnerabilities
 Secure Programming Lecture 3: Memory Corruption I (introduction) David Aspinall, Informatics @ Edinburgh 24th January 2019 Roadmap: Security in the software lifecycle Security is considered at different
Secure Programming Lecture 3: Memory Corruption I (introduction) David Aspinall, Informatics @ Edinburgh 24th January 2019 Roadmap: Security in the software lifecycle Security is considered at different
CNIT 127: Exploit Development. Ch 3: Shellcode. Updated
 CNIT 127: Exploit Development Ch 3: Shellcode Updated 1-30-17 Topics Protection rings Syscalls Shellcode nasm Assembler ld GNU Linker objdump to see contents of object files strace System Call Tracer Removing
CNIT 127: Exploit Development Ch 3: Shellcode Updated 1-30-17 Topics Protection rings Syscalls Shellcode nasm Assembler ld GNU Linker objdump to see contents of object files strace System Call Tracer Removing
Advanced Buffer Overflow
 Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2016/2017 Department of Electrical and Electronic Engineering
Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2016/2017 Department of Electrical and Electronic Engineering
Finding and Exploiting Access Control Vulnerabilities in Graphical User Interfaces
 Northeastern University Systems Security Lab Finding and Exploiting Access Control Vulnerabilities in Graphical User Interfaces Black Hat USA 2014 Collin Mulliner crm[at]ccs.neu.edu About Researcher at
Northeastern University Systems Security Lab Finding and Exploiting Access Control Vulnerabilities in Graphical User Interfaces Black Hat USA 2014 Collin Mulliner crm[at]ccs.neu.edu About Researcher at
March 10, Linux Live Patching. Adrien schischi Schildknecht. Why? Who? How? When? (consistency model) Conclusion
 March 10, 2015 Section 1 Why Goal: apply a binary patch to kernel on-line. is done without shutdown quick response to a small but critical issue the goal is not to avoid downtime Limitations: simple changes
March 10, 2015 Section 1 Why Goal: apply a binary patch to kernel on-line. is done without shutdown quick response to a small but critical issue the goal is not to avoid downtime Limitations: simple changes
Dirty COW Attack Lab
 SEED Labs Dirty COW Attack Lab 1 Dirty COW Attack Lab Copyright 2017 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation under Award
SEED Labs Dirty COW Attack Lab 1 Dirty COW Attack Lab Copyright 2017 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation under Award
Adaptive Android Kernel Live Patching
 USENIX Security Symposium 2017 Adaptive Android Kernel Live Patching Yue Chen 1, Yulong Zhang 2, Zhi Wang 1, Liangzhao Xia 2, Chenfu Bao 2, Tao Wei 2 Florida State University 1 Baidu X-Lab 2 Android Kernel
USENIX Security Symposium 2017 Adaptive Android Kernel Live Patching Yue Chen 1, Yulong Zhang 2, Zhi Wang 1, Liangzhao Xia 2, Chenfu Bao 2, Tao Wei 2 Florida State University 1 Baidu X-Lab 2 Android Kernel
Re-entrant code and Libraries
 Re-entrant code and Libraries A library is a collection of code that implements commonly used methods or patterns with a public API. Libraries facilitate code reuse. Libraries can be shared (also known
Re-entrant code and Libraries A library is a collection of code that implements commonly used methods or patterns with a public API. Libraries facilitate code reuse. Libraries can be shared (also known
The Terminator to Android Hardening Services. Yueqian Zhang, Xiapu Luo, Haoyang Yin Department of Computing The Hong Kong Polytechnic University
 The Terminator to Android Hardening Services Yueqian Zhang, Xiapu Luo, Haoyang Yin Department of Computing The Hong Kong Polytechnic University 1 Source: Trend Micro Percentage of top 10 apps in each category
The Terminator to Android Hardening Services Yueqian Zhang, Xiapu Luo, Haoyang Yin Department of Computing The Hong Kong Polytechnic University 1 Source: Trend Micro Percentage of top 10 apps in each category
Collect Linux Hardware Trace for ARMv8 User Space and Kernel Space Applications
 NXP Semiconductors Document Number: AN5129 Application Note Rev. 11.3.0, 12/2017 Collect Linux Hardware Trace for ARMv8 User Space and Kernel Space Applications 1 Introduction This document describes the
NXP Semiconductors Document Number: AN5129 Application Note Rev. 11.3.0, 12/2017 Collect Linux Hardware Trace for ARMv8 User Space and Kernel Space Applications 1 Introduction This document describes the
CSC 591 Systems Attacks and Defenses Stack Canaries & ASLR
 CSC 591 Systems Attacks and Defenses Stack Canaries & ASLR Alexandros Kapravelos akaprav@ncsu.edu How can we prevent a buffer overflow? Check bounds Programmer Language Stack canaries [...more ] Buffer
CSC 591 Systems Attacks and Defenses Stack Canaries & ASLR Alexandros Kapravelos akaprav@ncsu.edu How can we prevent a buffer overflow? Check bounds Programmer Language Stack canaries [...more ] Buffer
HW 8 CS681 & CS392 Computer Security Understanding and Experimenting with Memory Corruption Vulnerabilities DUE 12/18/2005
 HW 8 CS681 & CS392 Computer Security Understanding and Experimenting with Memory Corruption Vulnerabilities 1 Motivation DUE 12/18/2005 Memory corruption vulnerabilities to change program execution flow
HW 8 CS681 & CS392 Computer Security Understanding and Experimenting with Memory Corruption Vulnerabilities 1 Motivation DUE 12/18/2005 Memory corruption vulnerabilities to change program execution flow
Using Hashing to Improve Volatile Memory Forensic Analysis
 Using Hashing to Improve Volatile Memory Forensic Analysis American Academy of Forensic Sciences Annual Meeting February 21, 2008 AAron Walters awalters@volatilesystems.com Blake Matheny, LLC Center for
Using Hashing to Improve Volatile Memory Forensic Analysis American Academy of Forensic Sciences Annual Meeting February 21, 2008 AAron Walters awalters@volatilesystems.com Blake Matheny, LLC Center for
CS 220: Introduction to Parallel Computing. Beginning C. Lecture 2
 CS 220: Introduction to Parallel Computing Beginning C Lecture 2 Today s Schedule More C Background Differences: C vs Java/Python The C Compiler HW0 8/25/17 CS 220: Parallel Computing 2 Today s Schedule
CS 220: Introduction to Parallel Computing Beginning C Lecture 2 Today s Schedule More C Background Differences: C vs Java/Python The C Compiler HW0 8/25/17 CS 220: Parallel Computing 2 Today s Schedule
Outline. Format string attack layout. Null pointer dereference
 CSci 5271 Introduction to Computer Security Day 5: Low-level defenses and counterattacks Stephen McCamant University of Minnesota, Computer Science & Engineering Null pointer dereference Format string
CSci 5271 Introduction to Computer Security Day 5: Low-level defenses and counterattacks Stephen McCamant University of Minnesota, Computer Science & Engineering Null pointer dereference Format string
Outline. Outline. Common Linux tools to explore object/executable files. Revealing Internals of Loader. Zhiqiang Lin
 CS 6V81-05: System Security and Malicious Code Analysis Revealing Internals of Loader Zhiqiang Lin Department of Computer Science University of Texas at Dallas March 28 th, 2012 Common Linux tools to explore
CS 6V81-05: System Security and Malicious Code Analysis Revealing Internals of Loader Zhiqiang Lin Department of Computer Science University of Texas at Dallas March 28 th, 2012 Common Linux tools to explore
CSE 509: Computer Security
 CSE 509: Computer Security Date: 2.16.2009 BUFFER OVERFLOWS: input data Server running a daemon Attacker Code The attacker sends data to the daemon process running at the server side and could thus trigger
CSE 509: Computer Security Date: 2.16.2009 BUFFER OVERFLOWS: input data Server running a daemon Attacker Code The attacker sends data to the daemon process running at the server side and could thus trigger
C03c: Linkers and Loaders
 CISC 3320 MW3 C03c: Linkers and Loaders Hui Chen Department of Computer & Information Science CUNY Brooklyn College 2/4/2019 CUNY Brooklyn College: CISC 3320 OS 1 Outline Linkers and linking Loaders and
CISC 3320 MW3 C03c: Linkers and Loaders Hui Chen Department of Computer & Information Science CUNY Brooklyn College 2/4/2019 CUNY Brooklyn College: CISC 3320 OS 1 Outline Linkers and linking Loaders and
CS 326 Operating Systems C Programming. Greg Benson Department of Computer Science University of San Francisco
 CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
Are Your Mobile Apps Well Protected? Daniel Xiapu Luo Department of Computing The Hong Kong Polytechnic Unviersity
 Are Your Mobile Apps Well Protected? Daniel Xiapu Luo csxluo@comp.polyu.edu.hk Department of Computing The Hong Kong Polytechnic Unviersity 1 What if your mobile app is reverse-engineered by others? Core
Are Your Mobile Apps Well Protected? Daniel Xiapu Luo csxluo@comp.polyu.edu.hk Department of Computing The Hong Kong Polytechnic Unviersity 1 What if your mobile app is reverse-engineered by others? Core
