URL ATTACKS: Classification of URLs via Analysis and Learning
|
|
|
- Roger Bell
- 6 years ago
- Views:
Transcription
1 International Journal of Electrical and Computer Engineering (IJECE) Vol. 6, No. 3, June 2016, pp. 980 ~ 985 ISSN: , DOI: /ijece.v6i URL ATTACKS: Classification of URLs via Analysis and Learning M. Rajesh 1, R. Abhilash 2, R. Praveen Kumar 3 1 Department of Computer Engineering, M.A.M School of Engineering, India 2 Device Associate, Amazon Development Center, Chennai, India 3 Cognizant Technology Solutions, Chennai, India Article Info Article history: Received Dec 19, 2014 Revised Feb 1, 2016 Accepted Feb 16, 2016 Keyword: HTML Link Analysis Social networks Tiny URL URL attacks ABSTRACT Social Networks such as Twitter, Facebook play a remarkable growth in recent years. The ratio of tweets or messages in the form of URLs increases day by day. As the number of URL increases, the probability of fabrication also gets increased using their HTML content as well as by the usage of tiny URLs. It is important to classify the URLs by means of some modern techniques. Conditional redirection method is used here by which the URLs get classified and also the target page that the user needs is achieved. Learning methods also introduced to differentiate the URLs and there by the fabrication is not possible. Also the classifiers will efficiently detect the suspicious URLs using link analysis algorithm. Copyright 2016 Institute of Advanced Engineering and Science. All rights reserved. Corresponding Author: M. Rajesh, Departement of Computer Science, M.A.M School of Engineering, Tamil Nadu, India. rajesh.manoharan89@gmail.com 1. INTRODUCTION Social networking plays an important role in information sharing service for transferring of messages in the form of tweets or any other modes.when the social users need to share a URL with their close once then they formally use some of the shortening services. The proliferation of social networking [1] lead to increase in spam activity. The spammers send unsolicited messages for various purposes. Hash tags and shortened URLs [2] like t.co are frequently abused by the spammers. Hash tags are used to denote the topic or latest trend and they are abused by the spammers. The ability to disguise URL destination has made twitter or other social networks as an attractive target for the spammers. In the first study focusing on spam detection [3], we collect a number of users account. The users are considered as spammers by use of special methods and algorithms and to determine the false positive rate. Here we collect a specific number of users account such as in small environment like colleges or small scale industries to detect their spamming.this will act as the stand alone application for finding spam URLs. 2. RESEARCH METHOD 1. Conditional redirection scheme to ignore the suspicious URLs and there by fabrication is not possible anymore. 2. New features like learning concepts, classification and link analysis to differentiate the suspicious and unsuspicious URLs. 3. Data sets were taken that consist of URLs of suspicious and unsuspicious sites and they are classified by supervised learning methods. Journal homepage:
2 IJECE ISSN: The ultimate goal is to develop a conditional redirection to protect the suspicious URLs. The current visitor can be a normal browser.the normal browser will not know that the URL is being redirected to suspicious site and there by the user gets redirected to malicious page. Here the content of the suspicious URL is not retrieved, since they do not reveal their secrets to the normal browsers.so an analysis algorithm is needed for classification System details The proposed system consists of following components: data collection, extraction, learning and classification [4] (Figure 1) Data Collection In this phase, the URL messages are collected from the public and made for URL redirections. The tweets always follow streaming APIs and look up for IP addresses. It simply blocks up the IP addresses if seems to be malicious and they are skipped off. It is known that the crawlers cannot reach the malicious URLs [5] when conditional redirection is used. Table 1. Training data set Phases Label Users Training Spam 104 Non Spam 1483 Testing Spam 104 Non Spam Data extraction This phase involves grouping of domains and extracting future vectors. The phase also monitors the message queue. If several URLs share the same IP address then they replace the sites to the one which is in the data set found to be benign Learning Offline mode for supervised algorithm is used here to classify both URLs and also classification is made via rank basis (link analysis). For labeling, account status is used and so that URLs form suspended accounts are considered as suspicious where as from native accounts are considered as benign Classification Input vectors [6] are used to classify the suspicious and unsuspicious URLs. LIBLINEAR methods were used earlier to implement this classifier. The classifier algorithms such as Ada Boost,Naïve Bayes, Support Vector Classification(SVC) are compared and selected an link analysis based algorithm-power iteration that will classify the URLs effectively so that the false positive rate get decreased to a greater extent. Figure 1. System components URL ATTACKS: Classification of URLs via Analysis and Learning (M. Rajesh)
3 982 ISSN: The system components are described in Figure 1. In the data collection phase, tweets or mails with URL are collected for redirections that may be suspicious or unsuspicious. In extraction phase the domains that are identical are collected to classify them. Machine learning (supervised learning) is done in the next phase and classification is done at the termination level by link analysis algorithm Steps in machine learning with given data sets Supervised learning (machine learning) which will take a known set of inputs and known responses, and build a model that generates reasonable predictions for the response to new data. Known data Known Responses Model New Data Model Predicted Responses This method is based on prediction. Suppose if we take a real time example that the number of people will have heart attack within a year.this can be known by taking a trained data samples that consist of age, height, weight, blood pressure etc. So this will combine all the existing data into a model that can predict a person will have a heart attack within a year. Supervised learning splits into two broad categories: Classification for responses that consist of two values, such as 'true' or 'false'. Classification algorithms apply to nominal data sets.regression for responses that are considered as a real number, such as miles per gallon for a particular car. It is advised to create a regression model first, because they are often more computationally efficient. Link Analysis Suspicious /Tweet in URL URL CLASSIFICATION Learning Benign Figure2. URL Redirection scheme The data set will consist of a number of user accounts and from which spam accounts were detected. The data sets have been separated into two: training and testing. The features are further classified as Phishing dataset and legitimate dataset. Taking 1000 phishing and 1000 legitimate url s into account, the percentage of legitimate URL s is clearly increased by using power iteration method. Table 2. Legitimate and Phishing data in given data sets Types Legitimate Phishing IP Address 0% 0.04% Hexadecimal Character 0% 0.01% Suspicious symbol 0% 0.01% Age of domain 35% 75% Page rank feature 1.2% 88% IJECE Vol. 6, No. 3, June 2016 :
4 IJECE ISSN: Algorithm- Power Iteration method: Power iteration is based on Eigen value of a given matrix. The algorithm is mainly based on Eigen values and Eigen vectors which is also known as Von- Mises iteration. This method can be used when the sparse matrix is very large. It can compute only one Eigen value and lower convergence. The page rank iteration algorithm is given below by which the ranking equation is produced. Algorithm: Power iteration Initial Phase: Generate data sets that comprise of URLs with suspicious and unsuspicious links Classification Phase: Initially consider page count as 1. Increment the count as each user visit the page. Attempt to compare with the datasets obtained If successful, consider as normal Else, consider as spam. Power-Iterate(G) P e/n R 1 Repeat Pr (1-d)e+ da T Pr-1 Until Pr-Pr-1 < ε Return Pr After satisfying all the conditions, the page rank equation is produced: P = (1-d)e + da T P Where, P is the principal eigen vector and R is the initial count. e is the column vector and d is the damping factor. 3. RESULTS AND ANALYSIS As discussed earlier we use power iteration method because it shows highest AUC and lowest FP (False Positive). AUC is an area under ROC curve. The area under the ROC curve (AUC) is a measure of how well a parameter can distinguish between two diagnostic groups (diseased/normal).in our case we use phishing and legitimate URL s. We compared various classifiers like L1 Regularized and L2 Regularized and also SVC (Simple vector classification) and comparison table is obtained using the power iteration method. Here we took sample tweets and found tweets are benign and 156,896 were malicious. Table 3. Comparison with different classifiers CLASSIFIER AUC ACCURACY% FP% FN% L2R-LR L2-loss SVC Link Analysis SVC From the above table we can come to the conclusion that LINK ANALYSIS method will increase the accuracy level and thereby reducing the false positive rate Performance Analysis Considering the performance aspect of any proposed and implemented algorithm is one of the main criteria to be considered during the research. In our research, performance analysis has been carried out for the implemented algorithm using the open source performance testing tool JMeter. Pages for which the algorithm has been implemented are fetched as an input to the JMeter. The following Table 4 and Figure 3 have been obtained as the result of performance testing. Table 4. Performance Analysis Label Number Of Samples Average Response (Count) Time (Ms) Error% Home Page Classification Page Total URL ATTACKS: Classification of URLs via Analysis and Learning (M. Rajesh)
5 984 ISSN: Table 4 has been obtained as a result of performance testing from JMeter. Label indicates the pages for which the algorithm has been implemented. Number of Sample indicates, the number of virtually created users accessed the created page. Average Response time indicates the number of samples executed in particular instance. Error % indicates the amount of error occurred during the testing process. Figure 3 shows the graphical representation of performance analysis, which has been obtained from the JMeter. In the Figure 3, X axis indicates the page which has been tested and Y axis indicates the Response time in Milliseconds. Bar value indicates the average value of the response time (5446 ms for Home Page and 4256 ms for Classification page). Figure 3. Graphical Representation of Performance Analysis 3.2. Inferences From the Performance analysis made on the implemented algorithm, the following inferences were made. 1. The error % of performance analysis is 0 (Zero), this indicates that the application of the algorithm is functionally good. 2. The average response time of the implemented algorithm is 4851 ms for 1000 samples. From this we can infer that, for a single sample the response time is 4 seconds (less than 5 seconds). This indicates that the performance of the implemented algorithm holds good. 3. From the above two inference, It can be concluded that the implemented algorithm is functionally and non-functionally good Discussions The main goal our research is to propose and implement an algorithm which is Simple, Scalable and Highly efficient (Rate of Detection). Apart from these criteria, considering the performance of the implemented algorithm is very important aspect of the research work. Performance analysis of the implemented algorithm has been discussed in the section 6 of this paper. Here the implemented algorithm has been compared with the earlier research work made on in this area using the above narrated criteria. From our analysis the following Table 5 has been narrated which highlights the impact of the implemented algorithm is far better than the earlier research work which has been carried out. In Table 5 the value Yes, indicates that the criteria has been satisfied fully. No indicates that the criteria have not been considered or not satisfied. Partial indicates that the criteria have been partially satisfied. IJECE Vol. 6, No. 3, June 2016 :
6 IJECE ISSN: Table 5. Comparison of Implemented Algorithm Vs Earlier Research works S.No Research Work Simple Scalable Efficiency Performance 1 Dhanalkshmi Renganayakulu [1] Partial Partial No Yes 2 Jelena Isacenkova and Oliver Thonnard [2] Yes Partial Partial No 3 Kelin.F and Strohmaier.M [3] Partial Partial Partial Partial 4 Lee.S and Kim.J [4] Partial Partial No Yes 5 Nazpar Yazdanfar, Alex Thomo [5] Yes Partial Partial Yes 6 Stringhini.G, Kruegel.C and Vigna.C [6] Yes Yes Partial No 7 Song.J, Lee.S and Kim J [7] Yes Yes Yes No 8 Zachary Miller [8] Yes No Partial Partial 9 Our Work Yes Yes Yes Yes 4. CONCLUSION Table 5 has been derived by our analysis, from which we can infer that the implemented algorithm is simple, efficient, high performance, and scalable comparing to the earlier research works. A conventional method seems to be ineffective in their conditional redirection that separates normal users from being redirected to suspicious page. Unlike the convectional systems, classification via analysis is robust. The system accuracy and performance seems to be high this method by referring the statistical Table 3. In the future, process has to be extended to handle dynamic redirections. REFERENCES [1] D. Renganayakulu, Detecting Malicious URLs in , AASRI Procedia Elsevier, vol. 4, pp , [2] J. Isacenkova and O. Thonnard, Inside Scam Jungle: a closer look at 419 scam operations, URASIP journal of information security, [3] F. Kelin and M. Strohmaier, Short links under Attack: Geographical Analysis of Spam in URL Shortener Network, Proc.23 ACM Conf.Hypertext and Social media (HT), [4] S. Lee and J. Kim, Warning Bird: A Near Real-Time Detection System for Suspicious URLs in Twitter Stream, IEEE transactions on secure computing, vol/issue: 10(3), [5] N. Yazdanfar and A. Thomo, Collaborative-Filtering for Recommending URLs to Twitter Users, Procedia, vol/issue: 19(3), pp , [6] G. Stringhini, et al., Detecting Spammers on Social Networks, Proc.26 th Ann. Computer Security Applications Conf. (ACSAC), [7] J. Song, et al., Spam Filtering in Twitter Using Sender-Receiver Relationship, Proc.14 th International Symp. Recent Advances in Intrusion detection (RAID), [8] Z. Miller, Twitter spammer detection using data stream clustering, Information sciences Elsevier, vol. 260, pp , URL ATTACKS: Classification of URLs via Analysis and Learning (M. Rajesh)
ISSN: (Online) Volume 2, Issue 2, February 2014 International Journal of Advance Research in Computer Science and Management Studies
 ISSN: 2321-7782 (Online) Volume 2, Issue 2, February 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Paper / Case Study Available online at:
ISSN: 2321-7782 (Online) Volume 2, Issue 2, February 2014 International Journal of Advance Research in Computer Science and Management Studies Research Article / Paper / Case Study Available online at:
Survey Paper for WARNINGBIRD: Detecting Suspicious URLs in Twitter Stream
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 3 Issue 5, May 2014, Page No. 5866-5872 Survey Paper for WARNINGBIRD: Detecting Suspicious URLs in Twitter
www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 3 Issue 5, May 2014, Page No. 5866-5872 Survey Paper for WARNINGBIRD: Detecting Suspicious URLs in Twitter
Anti-Phishing Method for Detecting Suspicious URLs in Twitter
 Anti-Phishing Method for Detecting Suspicious URLs in Twitter Salu Sudhakar 1, Narasimhan T 2 P.G. Scholar, Dept of Computer Science, Mohandas College of engineering and technology Anad, TVM 1 Assistant
Anti-Phishing Method for Detecting Suspicious URLs in Twitter Salu Sudhakar 1, Narasimhan T 2 P.G. Scholar, Dept of Computer Science, Mohandas College of engineering and technology Anad, TVM 1 Assistant
Proximity Prestige using Incremental Iteration in Page Rank Algorithm
 Indian Journal of Science and Technology, Vol 9(48), DOI: 10.17485/ijst/2016/v9i48/107962, December 2016 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Proximity Prestige using Incremental Iteration
Indian Journal of Science and Technology, Vol 9(48), DOI: 10.17485/ijst/2016/v9i48/107962, December 2016 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Proximity Prestige using Incremental Iteration
Detecting Spam Bots in Online Social Networking Sites: A Machine Learning Approach
 Detecting Spam Bots in Online Social Networking Sites: A Machine Learning Approach Alex Hai Wang College of Information Sciences and Technology, The Pennsylvania State University, Dunmore, PA 18512, USA
Detecting Spam Bots in Online Social Networking Sites: A Machine Learning Approach Alex Hai Wang College of Information Sciences and Technology, The Pennsylvania State University, Dunmore, PA 18512, USA
A Performance Evaluation of Lfun Algorithm on the Detection of Drifted Spam Tweets
 A Performance Evaluation of Lfun Algorithm on the Detection of Drifted Spam Tweets Varsha Palandulkar 1, Siddhesh Bhujbal 2, Aayesha Momin 3, Vandana Kirane 4, Raj Naybal 5 Professor, AISSMS Polytechnic
A Performance Evaluation of Lfun Algorithm on the Detection of Drifted Spam Tweets Varsha Palandulkar 1, Siddhesh Bhujbal 2, Aayesha Momin 3, Vandana Kirane 4, Raj Naybal 5 Professor, AISSMS Polytechnic
Classification Methods for Spam Detection In Online Social Network
 International Research Journal of Engineering and Technology (IRJET) e-issn: 2395-56 Volume: 4 Issue: 7 July-217 www.irjet.net p-issn: 2395-72 Classification Methods for Spam Detection In Online Social
International Research Journal of Engineering and Technology (IRJET) e-issn: 2395-56 Volume: 4 Issue: 7 July-217 www.irjet.net p-issn: 2395-72 Classification Methods for Spam Detection In Online Social
A Comparative Study of Locality Preserving Projection and Principle Component Analysis on Classification Performance Using Logistic Regression
 Journal of Data Analysis and Information Processing, 2016, 4, 55-63 Published Online May 2016 in SciRes. http://www.scirp.org/journal/jdaip http://dx.doi.org/10.4236/jdaip.2016.42005 A Comparative Study
Journal of Data Analysis and Information Processing, 2016, 4, 55-63 Published Online May 2016 in SciRes. http://www.scirp.org/journal/jdaip http://dx.doi.org/10.4236/jdaip.2016.42005 A Comparative Study
A Supervised Method for Multi-keyword Web Crawling on Web Forums
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 2, February 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 2, February 2014,
Advances in Natural and Applied Sciences. Information Retrieval Using Collaborative Filtering and Item Based Recommendation
 AENSI Journals Advances in Natural and Applied Sciences ISSN:1995-0772 EISSN: 1998-1090 Journal home page: www.aensiweb.com/anas Information Retrieval Using Collaborative Filtering and Item Based Recommendation
AENSI Journals Advances in Natural and Applied Sciences ISSN:1995-0772 EISSN: 1998-1090 Journal home page: www.aensiweb.com/anas Information Retrieval Using Collaborative Filtering and Item Based Recommendation
Correlation Based Feature Selection with Irrelevant Feature Removal
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 4, April 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 4, April 2014,
CLASSIFICATION JELENA JOVANOVIĆ. Web:
 CLASSIFICATION JELENA JOVANOVIĆ Email: jeljov@gmail.com Web: http://jelenajovanovic.net OUTLINE What is classification? Binary and multiclass classification Classification algorithms Naïve Bayes (NB) algorithm
CLASSIFICATION JELENA JOVANOVIĆ Email: jeljov@gmail.com Web: http://jelenajovanovic.net OUTLINE What is classification? Binary and multiclass classification Classification algorithms Naïve Bayes (NB) algorithm
WarningBird MailAlert Based Malicious URLs Blocker System in Twitter
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 1, January 2014,
FPGA Based Distributed Network Intrusion Detection in Smart Grids Using Naives Bayes Classifier
 International Journal of Information & Computation Technology. ISSN 0974-2239 Volume 4, Number 7 (2014), pp. 747-752 International Research Publications House http://www. irphouse.com FPGA Based Distributed
International Journal of Information & Computation Technology. ISSN 0974-2239 Volume 4, Number 7 (2014), pp. 747-752 International Research Publications House http://www. irphouse.com FPGA Based Distributed
Novel Hybrid k-d-apriori Algorithm for Web Usage Mining
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 18, Issue 4, Ver. VI (Jul.-Aug. 2016), PP 01-10 www.iosrjournals.org Novel Hybrid k-d-apriori Algorithm for Web
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 18, Issue 4, Ver. VI (Jul.-Aug. 2016), PP 01-10 www.iosrjournals.org Novel Hybrid k-d-apriori Algorithm for Web
Trends Manipulation and Spam Detection in Twitter
 Trends Manipulation and Spam Detection in Twitter Dr. P. Maragathavalli 1, B. Lekha 2, M. Girija 3, R. Karthikeyan 4 1, 2, 3, 4 Information Technology, Pondicherry Engineering College, India Abstract:
Trends Manipulation and Spam Detection in Twitter Dr. P. Maragathavalli 1, B. Lekha 2, M. Girija 3, R. Karthikeyan 4 1, 2, 3, 4 Information Technology, Pondicherry Engineering College, India Abstract:
Research Article Combining Pre-fetching and Intelligent Caching Technique (SVM) to Predict Attractive Tourist Places
 Research Journal of Applied Sciences, Engineering and Technology 9(1): -46, 15 DOI:.1926/rjaset.9.1374 ISSN: -7459; e-issn: -7467 15 Maxwell Scientific Publication Corp. Submitted: July 1, 14 Accepted:
Research Journal of Applied Sciences, Engineering and Technology 9(1): -46, 15 DOI:.1926/rjaset.9.1374 ISSN: -7459; e-issn: -7467 15 Maxwell Scientific Publication Corp. Submitted: July 1, 14 Accepted:
A novel supervised learning algorithm and its use for Spam Detection in Social Bookmarking Systems
 A novel supervised learning algorithm and its use for Spam Detection in Social Bookmarking Systems Anestis Gkanogiannis and Theodore Kalamboukis Department of Informatics Athens University of Economics
A novel supervised learning algorithm and its use for Spam Detection in Social Bookmarking Systems Anestis Gkanogiannis and Theodore Kalamboukis Department of Informatics Athens University of Economics
Classifying Twitter Data in Multiple Classes Based On Sentiment Class Labels
 Classifying Twitter Data in Multiple Classes Based On Sentiment Class Labels Richa Jain 1, Namrata Sharma 2 1M.Tech Scholar, Department of CSE, Sushila Devi Bansal College of Engineering, Indore (M.P.),
Classifying Twitter Data in Multiple Classes Based On Sentiment Class Labels Richa Jain 1, Namrata Sharma 2 1M.Tech Scholar, Department of CSE, Sushila Devi Bansal College of Engineering, Indore (M.P.),
Iteration Reduction K Means Clustering Algorithm
 Iteration Reduction K Means Clustering Algorithm Kedar Sawant 1 and Snehal Bhogan 2 1 Department of Computer Engineering, Agnel Institute of Technology and Design, Assagao, Goa 403507, India 2 Department
Iteration Reduction K Means Clustering Algorithm Kedar Sawant 1 and Snehal Bhogan 2 1 Department of Computer Engineering, Agnel Institute of Technology and Design, Assagao, Goa 403507, India 2 Department
Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science
 Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science 310 Million + Current Domain Names 11 Billion+ Historical Domain Profiles 5 Million+ New Domain Profiles Daily
Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science 310 Million + Current Domain Names 11 Billion+ Historical Domain Profiles 5 Million+ New Domain Profiles Daily
Detecting Malicious Web Links and Identifying Their Attack Types
 Detecting Malicious Web Links and Identifying Their Attack Types Anti-Spam Team Cellopoint July 3, 2013 Introduction References A great effort has been directed towards detection of malicious URLs Blacklisting
Detecting Malicious Web Links and Identifying Their Attack Types Anti-Spam Team Cellopoint July 3, 2013 Introduction References A great effort has been directed towards detection of malicious URLs Blacklisting
A Comparative Study of Selected Classification Algorithms of Data Mining
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 6, June 2015, pg.220
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 6, June 2015, pg.220
A STUDY OF SOME DATA MINING CLASSIFICATION TECHNIQUES
 A STUDY OF SOME DATA MINING CLASSIFICATION TECHNIQUES Narsaiah Putta Assistant professor Department of CSE, VASAVI College of Engineering, Hyderabad, Telangana, India Abstract Abstract An Classification
A STUDY OF SOME DATA MINING CLASSIFICATION TECHNIQUES Narsaiah Putta Assistant professor Department of CSE, VASAVI College of Engineering, Hyderabad, Telangana, India Abstract Abstract An Classification
A SURVEY- WEB MINING TOOLS AND TECHNIQUE
 International Journal of Latest Trends in Engineering and Technology Vol.(7)Issue(4), pp.212-217 DOI: http://dx.doi.org/10.21172/1.74.028 e-issn:2278-621x A SURVEY- WEB MINING TOOLS AND TECHNIQUE Prof.
International Journal of Latest Trends in Engineering and Technology Vol.(7)Issue(4), pp.212-217 DOI: http://dx.doi.org/10.21172/1.74.028 e-issn:2278-621x A SURVEY- WEB MINING TOOLS AND TECHNIQUE Prof.
Countering Spam Using Classification Techniques. Steve Webb Data Mining Guest Lecture February 21, 2008
 Countering Spam Using Classification Techniques Steve Webb webb@cc.gatech.edu Data Mining Guest Lecture February 21, 2008 Overview Introduction Countering Email Spam Problem Description Classification
Countering Spam Using Classification Techniques Steve Webb webb@cc.gatech.edu Data Mining Guest Lecture February 21, 2008 Overview Introduction Countering Email Spam Problem Description Classification
WEB STRUCTURE MINING USING PAGERANK, IMPROVED PAGERANK AN OVERVIEW
 ISSN: 9 694 (ONLINE) ICTACT JOURNAL ON COMMUNICATION TECHNOLOGY, MARCH, VOL:, ISSUE: WEB STRUCTURE MINING USING PAGERANK, IMPROVED PAGERANK AN OVERVIEW V Lakshmi Praba and T Vasantha Department of Computer
ISSN: 9 694 (ONLINE) ICTACT JOURNAL ON COMMUNICATION TECHNOLOGY, MARCH, VOL:, ISSUE: WEB STRUCTURE MINING USING PAGERANK, IMPROVED PAGERANK AN OVERVIEW V Lakshmi Praba and T Vasantha Department of Computer
COMPARATIVE ANALYSIS OF POWER METHOD AND GAUSS-SEIDEL METHOD IN PAGERANK COMPUTATION
 International Journal of Computer Engineering and Applications, Volume IX, Issue VIII, Sep. 15 www.ijcea.com ISSN 2321-3469 COMPARATIVE ANALYSIS OF POWER METHOD AND GAUSS-SEIDEL METHOD IN PAGERANK COMPUTATION
International Journal of Computer Engineering and Applications, Volume IX, Issue VIII, Sep. 15 www.ijcea.com ISSN 2321-3469 COMPARATIVE ANALYSIS OF POWER METHOD AND GAUSS-SEIDEL METHOD IN PAGERANK COMPUTATION
Template Extraction from Heterogeneous Web Pages
 Template Extraction from Heterogeneous Web Pages 1 Mrs. Harshal H. Kulkarni, 2 Mrs. Manasi k. Kulkarni Asst. Professor, Pune University, (PESMCOE, Pune), Pune, India Abstract: Templates are used by many
Template Extraction from Heterogeneous Web Pages 1 Mrs. Harshal H. Kulkarni, 2 Mrs. Manasi k. Kulkarni Asst. Professor, Pune University, (PESMCOE, Pune), Pune, India Abstract: Templates are used by many
Twi$er s Trending Topics exploita4on pa$erns
 Twi$er s Trending Topics exploita4on pa$erns Despoina Antonakaki Paraskevi Fragopoulou, So6ris Ioannidis isocial Mee6ng, February 4-5th, 2014 Online Users World popula6ons percentage of online users: 39%
Twi$er s Trending Topics exploita4on pa$erns Despoina Antonakaki Paraskevi Fragopoulou, So6ris Ioannidis isocial Mee6ng, February 4-5th, 2014 Online Users World popula6ons percentage of online users: 39%
Classification of Page to the aspect of Crawl Web Forum and URL Navigation
 Classification of Page to the aspect of Crawl Web Forum and URL Navigation Yerragunta Kartheek*1, T.Sunitha Rani*2 M.Tech Scholar, Dept of CSE, QISCET, ONGOLE, Dist: Prakasam, AP, India. Associate Professor,
Classification of Page to the aspect of Crawl Web Forum and URL Navigation Yerragunta Kartheek*1, T.Sunitha Rani*2 M.Tech Scholar, Dept of CSE, QISCET, ONGOLE, Dist: Prakasam, AP, India. Associate Professor,
Anomaly Detection on Data Streams with High Dimensional Data Environment
 Anomaly Detection on Data Streams with High Dimensional Data Environment Mr. D. Gokul Prasath 1, Dr. R. Sivaraj, M.E, Ph.D., 2 Department of CSE, Velalar College of Engineering & Technology, Erode 1 Assistant
Anomaly Detection on Data Streams with High Dimensional Data Environment Mr. D. Gokul Prasath 1, Dr. R. Sivaraj, M.E, Ph.D., 2 Department of CSE, Velalar College of Engineering & Technology, Erode 1 Assistant
MALICIOUS URL DETECTION AND PREVENTION AT BROWSER LEVEL FRAMEWORK
 International Journal of Mechanical Engineering and Technology (IJMET) Volume 8, Issue 12, December 2017, pp. 536 541, Article ID: IJMET_08_12_054 Available online at http://www.iaeme.com/ijmet/issues.asp?jtype=ijmet&vtype=8&itype=12
International Journal of Mechanical Engineering and Technology (IJMET) Volume 8, Issue 12, December 2017, pp. 536 541, Article ID: IJMET_08_12_054 Available online at http://www.iaeme.com/ijmet/issues.asp?jtype=ijmet&vtype=8&itype=12
Mining User - Aware Rare Sequential Topic Pattern in Document Streams
 Mining User - Aware Rare Sequential Topic Pattern in Document Streams A.Mary Assistant Professor, Department of Computer Science And Engineering Alpha College Of Engineering, Thirumazhisai, Tamil Nadu,
Mining User - Aware Rare Sequential Topic Pattern in Document Streams A.Mary Assistant Professor, Department of Computer Science And Engineering Alpha College Of Engineering, Thirumazhisai, Tamil Nadu,
A Generic Statistical Approach for Spam Detection in Online Social Networks
 Final version of the accepted paper. Cite as: F. Ahmad and M. Abulaish, A Generic Statistical Approach for Spam Detection in Online Social Networks, Computer Communications, 36(10-11), Elsevier, pp. 1120-1129,
Final version of the accepted paper. Cite as: F. Ahmad and M. Abulaish, A Generic Statistical Approach for Spam Detection in Online Social Networks, Computer Communications, 36(10-11), Elsevier, pp. 1120-1129,
Secure Enhanced Authenticated Routing Protocol for Mobile Ad Hoc Networks
 Journal of Computer Science 7 (12): 1813-1818, 2011 ISSN 1549-3636 2011 Science Publications Secure Enhanced Authenticated Routing Protocol for Mobile Ad Hoc Networks 1 M.Rajesh Babu and 2 S.Selvan 1 Department
Journal of Computer Science 7 (12): 1813-1818, 2011 ISSN 1549-3636 2011 Science Publications Secure Enhanced Authenticated Routing Protocol for Mobile Ad Hoc Networks 1 M.Rajesh Babu and 2 S.Selvan 1 Department
IMPLEMENTATION OF CLASSIFICATION ALGORITHMS USING WEKA NAÏVE BAYES CLASSIFIER
 IMPLEMENTATION OF CLASSIFICATION ALGORITHMS USING WEKA NAÏVE BAYES CLASSIFIER N. Suresh Kumar, Dr. M. Thangamani 1 Assistant Professor, Sri Ramakrishna Engineering College, Coimbatore, India 2 Assistant
IMPLEMENTATION OF CLASSIFICATION ALGORITHMS USING WEKA NAÏVE BAYES CLASSIFIER N. Suresh Kumar, Dr. M. Thangamani 1 Assistant Professor, Sri Ramakrishna Engineering College, Coimbatore, India 2 Assistant
ANALYSIS COMPUTER SCIENCE Discovery Science, Volume 9, Number 20, April 3, Comparative Study of Classification Algorithms Using Data Mining
 ANALYSIS COMPUTER SCIENCE Discovery Science, Volume 9, Number 20, April 3, 2014 ISSN 2278 5485 EISSN 2278 5477 discovery Science Comparative Study of Classification Algorithms Using Data Mining Akhila
ANALYSIS COMPUTER SCIENCE Discovery Science, Volume 9, Number 20, April 3, 2014 ISSN 2278 5485 EISSN 2278 5477 discovery Science Comparative Study of Classification Algorithms Using Data Mining Akhila
AN EFFECTIVE SPAM FILTERING FOR DYNAMIC MAIL MANAGEMENT SYSTEM
 ISSN: 2229-6956(ONLINE) DOI: 1.21917/ijsc.212.5 ICTACT JOURNAL ON SOFT COMPUTING, APRIL 212, VOLUME: 2, ISSUE: 3 AN EFFECTIVE SPAM FILTERING FOR DYNAMIC MAIL MANAGEMENT SYSTEM S. Arun Mozhi Selvi 1 and
ISSN: 2229-6956(ONLINE) DOI: 1.21917/ijsc.212.5 ICTACT JOURNAL ON SOFT COMPUTING, APRIL 212, VOLUME: 2, ISSUE: 3 AN EFFECTIVE SPAM FILTERING FOR DYNAMIC MAIL MANAGEMENT SYSTEM S. Arun Mozhi Selvi 1 and
An Intelligent Clustering Algorithm for High Dimensional and Highly Overlapped Photo-Thermal Infrared Imaging Data
 An Intelligent Clustering Algorithm for High Dimensional and Highly Overlapped Photo-Thermal Infrared Imaging Data Nian Zhang and Lara Thompson Department of Electrical and Computer Engineering, University
An Intelligent Clustering Algorithm for High Dimensional and Highly Overlapped Photo-Thermal Infrared Imaging Data Nian Zhang and Lara Thompson Department of Electrical and Computer Engineering, University
Research on Applications of Data Mining in Electronic Commerce. Xiuping YANG 1, a
 International Conference on Education Technology, Management and Humanities Science (ETMHS 2015) Research on Applications of Data Mining in Electronic Commerce Xiuping YANG 1, a 1 Computer Science Department,
International Conference on Education Technology, Management and Humanities Science (ETMHS 2015) Research on Applications of Data Mining in Electronic Commerce Xiuping YANG 1, a 1 Computer Science Department,
Semi supervised clustering for Text Clustering
 Semi supervised clustering for Text Clustering N.Saranya 1 Assistant Professor, Department of Computer Science and Engineering, Sri Eshwar College of Engineering, Coimbatore 1 ABSTRACT: Based on clustering
Semi supervised clustering for Text Clustering N.Saranya 1 Assistant Professor, Department of Computer Science and Engineering, Sri Eshwar College of Engineering, Coimbatore 1 ABSTRACT: Based on clustering
Weka ( )
 Weka ( http://www.cs.waikato.ac.nz/ml/weka/ ) The phases in which classifier s design can be divided are reflected in WEKA s Explorer structure: Data pre-processing (filtering) and representation Supervised
Weka ( http://www.cs.waikato.ac.nz/ml/weka/ ) The phases in which classifier s design can be divided are reflected in WEKA s Explorer structure: Data pre-processing (filtering) and representation Supervised
Detecting Spammers with SNARE: Spatio-temporal Network-level Automatic Reputation Engine
 Detecting Spammers with SNARE: Spatio-temporal Network-level Automatic Reputation Engine Shuang Hao, Nadeem Ahmed Syed, Nick Feamster, Alexander G. Gray, Sven Krasser Motivation Spam: More than Just a
Detecting Spammers with SNARE: Spatio-temporal Network-level Automatic Reputation Engine Shuang Hao, Nadeem Ahmed Syed, Nick Feamster, Alexander G. Gray, Sven Krasser Motivation Spam: More than Just a
Collaborative Filtering using Euclidean Distance in Recommendation Engine
 Indian Journal of Science and Technology, Vol 9(37), DOI: 10.17485/ijst/2016/v9i37/102074, October 2016 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Collaborative Filtering using Euclidean Distance
Indian Journal of Science and Technology, Vol 9(37), DOI: 10.17485/ijst/2016/v9i37/102074, October 2016 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Collaborative Filtering using Euclidean Distance
Enhanced Web Usage Mining Using Fuzzy Clustering and Collaborative Filtering Recommendation Algorithms
 International Journal of Mathematics and Statistics Invention (IJMSI) E-ISSN: 2321 4767 P-ISSN: 2321-4759 Volume 4 Issue 10 December. 2016 PP-09-13 Enhanced Web Usage Mining Using Fuzzy Clustering and
International Journal of Mathematics and Statistics Invention (IJMSI) E-ISSN: 2321 4767 P-ISSN: 2321-4759 Volume 4 Issue 10 December. 2016 PP-09-13 Enhanced Web Usage Mining Using Fuzzy Clustering and
Anomaly Detection. You Chen
 Anomaly Detection You Chen 1 Two questions: (1) What is Anomaly Detection? (2) What are Anomalies? Anomaly detection refers to the problem of finding patterns in data that do not conform to expected behavior
Anomaly Detection You Chen 1 Two questions: (1) What is Anomaly Detection? (2) What are Anomalies? Anomaly detection refers to the problem of finding patterns in data that do not conform to expected behavior
An Enhanced Approach for Secure Pattern. Classification in Adversarial Environment
 Contemporary Engineering Sciences, Vol. 8, 2015, no. 12, 533-538 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ces.2015.5269 An Enhanced Approach for Secure Pattern Classification in Adversarial
Contemporary Engineering Sciences, Vol. 8, 2015, no. 12, 533-538 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ces.2015.5269 An Enhanced Approach for Secure Pattern Classification in Adversarial
Mining Data that Changes. 17 July 2015
 Mining Data that Changes 17 July 2015 Data is Not Static Data is not static New transactions, new friends, stop following somebody in Twitter, But most data mining algorithms assume static data Even a
Mining Data that Changes 17 July 2015 Data is Not Static Data is not static New transactions, new friends, stop following somebody in Twitter, But most data mining algorithms assume static data Even a
Best Customer Services among the E-Commerce Websites A Predictive Analysis
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 5 Issues 6 June 2016, Page No. 17088-17095 Best Customer Services among the E-Commerce Websites A Predictive
www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242 Volume 5 Issues 6 June 2016, Page No. 17088-17095 Best Customer Services among the E-Commerce Websites A Predictive
Mining Web Data. Lijun Zhang
 Mining Web Data Lijun Zhang zlj@nju.edu.cn http://cs.nju.edu.cn/zlj Outline Introduction Web Crawling and Resource Discovery Search Engine Indexing and Query Processing Ranking Algorithms Recommender Systems
Mining Web Data Lijun Zhang zlj@nju.edu.cn http://cs.nju.edu.cn/zlj Outline Introduction Web Crawling and Resource Discovery Search Engine Indexing and Query Processing Ranking Algorithms Recommender Systems
Detecting Spam Zombies By Monitoring Outgoing Messages
 International Refereed Journal of Engineering and Science (IRJES) ISSN (Online) 2319-183X, (Print) 2319-1821 Volume 5, Issue 5 (May 2016), PP.71-75 Detecting Spam Zombies By Monitoring Outgoing Messages
International Refereed Journal of Engineering and Science (IRJES) ISSN (Online) 2319-183X, (Print) 2319-1821 Volume 5, Issue 5 (May 2016), PP.71-75 Detecting Spam Zombies By Monitoring Outgoing Messages
SEOHUNK INTERNATIONAL D-62, Basundhara Apt., Naharkanta, Hanspal, Bhubaneswar, India
 SEOHUNK INTERNATIONAL D-62, Basundhara Apt., Naharkanta, Hanspal, Bhubaneswar, India 752101. p: 305-403-9683 w: www.seohunkinternational.com e: info@seohunkinternational.com DOMAIN INFORMATION: S No. Details
SEOHUNK INTERNATIONAL D-62, Basundhara Apt., Naharkanta, Hanspal, Bhubaneswar, India 752101. p: 305-403-9683 w: www.seohunkinternational.com e: info@seohunkinternational.com DOMAIN INFORMATION: S No. Details
A Comparison of Text-Categorization Methods applied to N-Gram Frequency Statistics
 A Comparison of Text-Categorization Methods applied to N-Gram Frequency Statistics Helmut Berger and Dieter Merkl 2 Faculty of Information Technology, University of Technology, Sydney, NSW, Australia hberger@it.uts.edu.au
A Comparison of Text-Categorization Methods applied to N-Gram Frequency Statistics Helmut Berger and Dieter Merkl 2 Faculty of Information Technology, University of Technology, Sydney, NSW, Australia hberger@it.uts.edu.au
Performance Evaluation of Various Classification Algorithms
 Performance Evaluation of Various Classification Algorithms Shafali Deora Amritsar College of Engineering & Technology, Punjab Technical University -----------------------------------------------------------***----------------------------------------------------------
Performance Evaluation of Various Classification Algorithms Shafali Deora Amritsar College of Engineering & Technology, Punjab Technical University -----------------------------------------------------------***----------------------------------------------------------
G(B)enchmark GraphBench: Towards a Universal Graph Benchmark. Khaled Ammar M. Tamer Özsu
 G(B)enchmark GraphBench: Towards a Universal Graph Benchmark Khaled Ammar M. Tamer Özsu Bioinformatics Software Engineering Social Network Gene Co-expression Protein Structure Program Flow Big Graphs o
G(B)enchmark GraphBench: Towards a Universal Graph Benchmark Khaled Ammar M. Tamer Özsu Bioinformatics Software Engineering Social Network Gene Co-expression Protein Structure Program Flow Big Graphs o
Efficacious Spam Filtering and Detection in Social Networks
 Indian Journal of Science and Technology, Vol 7(S7), 180 184, November 2014 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Efficacious Spam Filtering and Detection in Social Networks U. V. Anbazhagu
Indian Journal of Science and Technology, Vol 7(S7), 180 184, November 2014 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Efficacious Spam Filtering and Detection in Social Networks U. V. Anbazhagu
Sanitization Techniques against Personal Information Inference Attack on Social Network
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 12, December 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 12, December 2014,
Elimination of Duplicate Videos in Video Sharing Sites
 Elimination of Duplicate Videos in Video Sharing Sites Narendra Kumar S, Murugan S, Krishnaveni R Abstract - In some social video networking sites such as YouTube, there exists large numbers of duplicate
Elimination of Duplicate Videos in Video Sharing Sites Narendra Kumar S, Murugan S, Krishnaveni R Abstract - In some social video networking sites such as YouTube, there exists large numbers of duplicate
Lecture 25: Review I
 Lecture 25: Review I Reading: Up to chapter 5 in ISLR. STATS 202: Data mining and analysis Jonathan Taylor 1 / 18 Unsupervised learning In unsupervised learning, all the variables are on equal standing,
Lecture 25: Review I Reading: Up to chapter 5 in ISLR. STATS 202: Data mining and analysis Jonathan Taylor 1 / 18 Unsupervised learning In unsupervised learning, all the variables are on equal standing,
Developing Focused Crawlers for Genre Specific Search Engines
 Developing Focused Crawlers for Genre Specific Search Engines Nikhil Priyatam Thesis Advisor: Prof. Vasudeva Varma IIIT Hyderabad July 7, 2014 Examples of Genre Specific Search Engines MedlinePlus Naukri.com
Developing Focused Crawlers for Genre Specific Search Engines Nikhil Priyatam Thesis Advisor: Prof. Vasudeva Varma IIIT Hyderabad July 7, 2014 Examples of Genre Specific Search Engines MedlinePlus Naukri.com
Think before RT: An Experimental Study of Abusing Twitter Trends
 Think before RT: An Experimental Study of Abusing Twitter Trends Despoina Antonakaki 1, Iasonas Polakis 2, Elias Athanasopoulos 1, Sotiris Ioannidis 1, and Paraskevi Fragopoulou 1 1 FORTH-ICS, Greece {despoina,elathan,sotiris,fragopou}@ics.forth.gr
Think before RT: An Experimental Study of Abusing Twitter Trends Despoina Antonakaki 1, Iasonas Polakis 2, Elias Athanasopoulos 1, Sotiris Ioannidis 1, and Paraskevi Fragopoulou 1 1 FORTH-ICS, Greece {despoina,elathan,sotiris,fragopou}@ics.forth.gr
Study on Classifiers using Genetic Algorithm and Class based Rules Generation
 2012 International Conference on Software and Computer Applications (ICSCA 2012) IPCSIT vol. 41 (2012) (2012) IACSIT Press, Singapore Study on Classifiers using Genetic Algorithm and Class based Rules
2012 International Conference on Software and Computer Applications (ICSCA 2012) IPCSIT vol. 41 (2012) (2012) IACSIT Press, Singapore Study on Classifiers using Genetic Algorithm and Class based Rules
The Data Mining Application Based on WEKA: Geographical Original of Music
 Management Science and Engineering Vol. 10, No. 4, 2016, pp. 36-46 DOI:10.3968/8997 ISSN 1913-0341 [Print] ISSN 1913-035X [Online] www.cscanada.net www.cscanada.org The Data Mining Application Based on
Management Science and Engineering Vol. 10, No. 4, 2016, pp. 36-46 DOI:10.3968/8997 ISSN 1913-0341 [Print] ISSN 1913-035X [Online] www.cscanada.net www.cscanada.org The Data Mining Application Based on
Predictive Analysis: Evaluation and Experimentation. Heejun Kim
 Predictive Analysis: Evaluation and Experimentation Heejun Kim June 19, 2018 Evaluation and Experimentation Evaluation Metrics Cross-Validation Significance Tests Evaluation Predictive analysis: training
Predictive Analysis: Evaluation and Experimentation Heejun Kim June 19, 2018 Evaluation and Experimentation Evaluation Metrics Cross-Validation Significance Tests Evaluation Predictive analysis: training
Performance Based Study of Association Rule Algorithms On Voter DB
 Performance Based Study of Association Rule Algorithms On Voter DB K.Padmavathi 1, R.Aruna Kirithika 2 1 Department of BCA, St.Joseph s College, Thiruvalluvar University, Cuddalore, Tamil Nadu, India,
Performance Based Study of Association Rule Algorithms On Voter DB K.Padmavathi 1, R.Aruna Kirithika 2 1 Department of BCA, St.Joseph s College, Thiruvalluvar University, Cuddalore, Tamil Nadu, India,
Spam Classification Documentation
 Spam Classification Documentation What is SPAM? Unsolicited, unwanted email that was sent indiscriminately, directly or indirectly, by a sender having no current relationship with the recipient. Objective:
Spam Classification Documentation What is SPAM? Unsolicited, unwanted email that was sent indiscriminately, directly or indirectly, by a sender having no current relationship with the recipient. Objective:
Detecting Network Intrusions
 Detecting Network Intrusions Naveen Krishnamurthi, Kevin Miller Stanford University, Computer Science {naveenk1, kmiller4}@stanford.edu Abstract The purpose of this project is to create a predictive model
Detecting Network Intrusions Naveen Krishnamurthi, Kevin Miller Stanford University, Computer Science {naveenk1, kmiller4}@stanford.edu Abstract The purpose of this project is to create a predictive model
CS246: Mining Massive Datasets Jure Leskovec, Stanford University
 CS246: Mining Massive Datasets Jure Leskovec, Stanford University http://cs246.stanford.edu [Kumar et al. 99] 2/13/2013 Jure Leskovec, Stanford CS246: Mining Massive Datasets, http://cs246.stanford.edu
CS246: Mining Massive Datasets Jure Leskovec, Stanford University http://cs246.stanford.edu [Kumar et al. 99] 2/13/2013 Jure Leskovec, Stanford CS246: Mining Massive Datasets, http://cs246.stanford.edu
IJREAT International Journal of Research in Engineering & Advanced Technology, Volume 1, Issue 5, Oct-Nov, ISSN:
 IJREAT International Journal of Research in Engineering & Advanced Technology, Volume 1, Issue 5, Oct-Nov, 20131 Improve Search Engine Relevance with Filter session Addlin Shinney R 1, Saravana Kumar T
IJREAT International Journal of Research in Engineering & Advanced Technology, Volume 1, Issue 5, Oct-Nov, 20131 Improve Search Engine Relevance with Filter session Addlin Shinney R 1, Saravana Kumar T
International Journal of Software and Web Sciences (IJSWS)
 International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) ISSN (Print): 2279-0063 ISSN (Online): 2279-0071 International
International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) ISSN (Print): 2279-0063 ISSN (Online): 2279-0071 International
A Survey Of Different Text Mining Techniques Varsha C. Pande 1 and Dr. A.S. Khandelwal 2
 A Survey Of Different Text Mining Techniques Varsha C. Pande 1 and Dr. A.S. Khandelwal 2 1 Department of Electronics & Comp. Sc, RTMNU, Nagpur, India 2 Department of Computer Science, Hislop College, Nagpur,
A Survey Of Different Text Mining Techniques Varsha C. Pande 1 and Dr. A.S. Khandelwal 2 1 Department of Electronics & Comp. Sc, RTMNU, Nagpur, India 2 Department of Computer Science, Hislop College, Nagpur,
Top 10 Global Threat Rank by Source
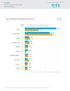 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
TERM BASED WEIGHT MEASURE FOR INFORMATION FILTERING IN SEARCH ENGINES
 TERM BASED WEIGHT MEASURE FOR INFORMATION FILTERING IN SEARCH ENGINES Mu. Annalakshmi Research Scholar, Department of Computer Science, Alagappa University, Karaikudi. annalakshmi_mu@yahoo.co.in Dr. A.
TERM BASED WEIGHT MEASURE FOR INFORMATION FILTERING IN SEARCH ENGINES Mu. Annalakshmi Research Scholar, Department of Computer Science, Alagappa University, Karaikudi. annalakshmi_mu@yahoo.co.in Dr. A.
Chapter 5: Summary and Conclusion CHAPTER 5 SUMMARY AND CONCLUSION. Chapter 1: Introduction
 CHAPTER 5 SUMMARY AND CONCLUSION Chapter 1: Introduction Data mining is used to extract the hidden, potential, useful and valuable information from very large amount of data. Data mining tools can handle
CHAPTER 5 SUMMARY AND CONCLUSION Chapter 1: Introduction Data mining is used to extract the hidden, potential, useful and valuable information from very large amount of data. Data mining tools can handle
Applications of Machine Learning on Keyword Extraction of Large Datasets
 Applications of Machine Learning on Keyword Extraction of Large Datasets 1 2 Meng Yan my259@stanford.edu 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37
Applications of Machine Learning on Keyword Extraction of Large Datasets 1 2 Meng Yan my259@stanford.edu 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37
SCALABLE KNOWLEDGE BASED AGGREGATION OF COLLECTIVE BEHAVIOR
 SCALABLE KNOWLEDGE BASED AGGREGATION OF COLLECTIVE BEHAVIOR P.SHENBAGAVALLI M.E., Research Scholar, Assistant professor/cse MPNMJ Engineering college Sspshenba2@gmail.com J.SARAVANAKUMAR B.Tech(IT)., PG
SCALABLE KNOWLEDGE BASED AGGREGATION OF COLLECTIVE BEHAVIOR P.SHENBAGAVALLI M.E., Research Scholar, Assistant professor/cse MPNMJ Engineering college Sspshenba2@gmail.com J.SARAVANAKUMAR B.Tech(IT)., PG
International Journal of Research in Advent Technology, Vol.7, No.3, March 2019 E-ISSN: Available online at
 Performance Evaluation of Ensemble Method Based Outlier Detection Algorithm Priya. M 1, M. Karthikeyan 2 Department of Computer and Information Science, Annamalai University, Annamalai Nagar, Tamil Nadu,
Performance Evaluation of Ensemble Method Based Outlier Detection Algorithm Priya. M 1, M. Karthikeyan 2 Department of Computer and Information Science, Annamalai University, Annamalai Nagar, Tamil Nadu,
Improving the Efficiency of Fast Using Semantic Similarity Algorithm
 International Journal of Scientific and Research Publications, Volume 4, Issue 1, January 2014 1 Improving the Efficiency of Fast Using Semantic Similarity Algorithm D.KARTHIKA 1, S. DIVAKAR 2 Final year
International Journal of Scientific and Research Publications, Volume 4, Issue 1, January 2014 1 Improving the Efficiency of Fast Using Semantic Similarity Algorithm D.KARTHIKA 1, S. DIVAKAR 2 Final year
Data Science Course Content
 CHAPTER 1: INTRODUCTION TO DATA SCIENCE Data Science Course Content What is the need for Data Scientists Data Science Foundation Business Intelligence Data Analysis Data Mining Machine Learning Difference
CHAPTER 1: INTRODUCTION TO DATA SCIENCE Data Science Course Content What is the need for Data Scientists Data Science Foundation Business Intelligence Data Analysis Data Mining Machine Learning Difference
Crawler with Search Engine based Simple Web Application System for Forum Mining
 IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 04, 2015 ISSN (online): 2321-0613 Crawler with Search Engine based Simple Web Application System for Forum Mining Parina
IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 04, 2015 ISSN (online): 2321-0613 Crawler with Search Engine based Simple Web Application System for Forum Mining Parina
Dynamically Building Facets from Their Search Results
 Dynamically Building Facets from Their Search Results Anju G. R, Karthik M. Abstract: People are very passionate in searching new things and gaining new knowledge. They usually prefer search engines to
Dynamically Building Facets from Their Search Results Anju G. R, Karthik M. Abstract: People are very passionate in searching new things and gaining new knowledge. They usually prefer search engines to
Hybrid Feature Selection for Modeling Intrusion Detection Systems
 Hybrid Feature Selection for Modeling Intrusion Detection Systems Srilatha Chebrolu, Ajith Abraham and Johnson P Thomas Department of Computer Science, Oklahoma State University, USA ajith.abraham@ieee.org,
Hybrid Feature Selection for Modeling Intrusion Detection Systems Srilatha Chebrolu, Ajith Abraham and Johnson P Thomas Department of Computer Science, Oklahoma State University, USA ajith.abraham@ieee.org,
Effect of Principle Component Analysis and Support Vector Machine in Software Fault Prediction
 International Journal of Computer Trends and Technology (IJCTT) volume 7 number 3 Jan 2014 Effect of Principle Component Analysis and Support Vector Machine in Software Fault Prediction A. Shanthini 1,
International Journal of Computer Trends and Technology (IJCTT) volume 7 number 3 Jan 2014 Effect of Principle Component Analysis and Support Vector Machine in Software Fault Prediction A. Shanthini 1,
Review on Text Mining
 Review on Text Mining Aarushi Rai #1, Aarush Gupta *2, Jabanjalin Hilda J. #3 #1 School of Computer Science and Engineering, VIT University, Tamil Nadu - India #2 School of Computer Science and Engineering,
Review on Text Mining Aarushi Rai #1, Aarush Gupta *2, Jabanjalin Hilda J. #3 #1 School of Computer Science and Engineering, VIT University, Tamil Nadu - India #2 School of Computer Science and Engineering,
In the recent past, the World Wide Web has been witnessing an. explosive growth. All the leading web search engines, namely, Google,
 1 1.1 Introduction In the recent past, the World Wide Web has been witnessing an explosive growth. All the leading web search engines, namely, Google, Yahoo, Askjeeves, etc. are vying with each other to
1 1.1 Introduction In the recent past, the World Wide Web has been witnessing an explosive growth. All the leading web search engines, namely, Google, Yahoo, Askjeeves, etc. are vying with each other to
Hybrid Approach for MRI Human Head Scans Classification using HTT based SFTA Texture Feature Extraction Technique
 Volume 118 No. 17 2018, 691-701 ISSN: 1311-8080 (printed version); ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu ijpam.eu Hybrid Approach for MRI Human Head Scans Classification using HTT
Volume 118 No. 17 2018, 691-701 ISSN: 1311-8080 (printed version); ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu ijpam.eu Hybrid Approach for MRI Human Head Scans Classification using HTT
An Efficient Decision Tree Model for Classification of Attacks with Feature Selection
 An Efficient Decision Tree Model for Classification of Attacks with Feature Selection Akhilesh Kumar Shrivas Research Scholar, CVRU, Bilaspur (C.G.), India S. K. Singhai Govt. Engineering College Bilaspur
An Efficient Decision Tree Model for Classification of Attacks with Feature Selection Akhilesh Kumar Shrivas Research Scholar, CVRU, Bilaspur (C.G.), India S. K. Singhai Govt. Engineering College Bilaspur
Quadratic Route Factor Estimation Technique for Routing Attack Detection in Wireless Adhoc Networks
 European Journal of Applied Sciences 8 (1): 41-46, 2016 ISSN 2079-2077 IDOSI Publications, 2016 DOI: 10.5829/idosi.ejas.2016.8.1.22852 Quadratic Route Factor Estimation Technique for Routing Attack Detection
European Journal of Applied Sciences 8 (1): 41-46, 2016 ISSN 2079-2077 IDOSI Publications, 2016 DOI: 10.5829/idosi.ejas.2016.8.1.22852 Quadratic Route Factor Estimation Technique for Routing Attack Detection
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
International Journal of Advanced Research in. Computer Science and Engineering
 Volume 4, Issue 1, January 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Design and Architecture
Volume 4, Issue 1, January 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Design and Architecture
Flight Recommendation System based on user feedback, weighting technique and context aware recommendation system
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 5 Issue 09 September 2016 Page No.17973-17978 Flight Recommendation System based on user feedback, weighting
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 5 Issue 09 September 2016 Page No.17973-17978 Flight Recommendation System based on user feedback, weighting
A New Technique to Optimize User s Browsing Session using Data Mining
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 3, March 2015,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 3, March 2015,
IJSRD - International Journal for Scientific Research & Development Vol. 4, Issue 03, 2016 ISSN (online):
 IJSRD - International Journal for Scientific Research & Development Vol. 4, Issue 03, 2016 ISSN (online): 2321-0613 Tweet Analysis for Malicious Content using Hybrid System Aditya Jadhav 1 Shital Salve
IJSRD - International Journal for Scientific Research & Development Vol. 4, Issue 03, 2016 ISSN (online): 2321-0613 Tweet Analysis for Malicious Content using Hybrid System Aditya Jadhav 1 Shital Salve
Fault Identification from Web Log Files by Pattern Discovery
 ABSTRACT International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2017 IJSRCSEIT Volume 2 Issue 2 ISSN : 2456-3307 Fault Identification from Web Log Files
ABSTRACT International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2017 IJSRCSEIT Volume 2 Issue 2 ISSN : 2456-3307 Fault Identification from Web Log Files
CSI5387: Data Mining Project
 CSI5387: Data Mining Project Terri Oda April 14, 2008 1 Introduction Web pages have become more like applications that documents. Not only do they provide dynamic content, they also allow users to play
CSI5387: Data Mining Project Terri Oda April 14, 2008 1 Introduction Web pages have become more like applications that documents. Not only do they provide dynamic content, they also allow users to play
Sathyamangalam, 2 ( PG Scholar,Department of Computer Science and Engineering,Bannari Amman Institute of Technology, Sathyamangalam,
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 8, Issue 5 (Jan. - Feb. 2013), PP 70-74 Performance Analysis Of Web Page Prediction With Markov Model, Association
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 8, Issue 5 (Jan. - Feb. 2013), PP 70-74 Performance Analysis Of Web Page Prediction With Markov Model, Association
Create an Account... 2 Setting up your account... 2 Send a Tweet... 4 Add Link... 4 Add Photo... 5 Delete a Tweet...
 Twitter is a social networking site allowing users to post thoughts and ideas in 140 characters or less. http://www.twitter.com Create an Account... 2 Setting up your account... 2 Send a Tweet... 4 Add
Twitter is a social networking site allowing users to post thoughts and ideas in 140 characters or less. http://www.twitter.com Create an Account... 2 Setting up your account... 2 Send a Tweet... 4 Add
Keywords Data alignment, Data annotation, Web database, Search Result Record
 Volume 5, Issue 8, August 2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Annotating Web
Volume 5, Issue 8, August 2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Annotating Web
Data Mining Concepts & Tasks
 Data Mining Concepts & Tasks Duen Horng (Polo) Chau Georgia Tech CSE6242 / CX4242 Sept 9, 2014 Partly based on materials by Professors Guy Lebanon, Jeffrey Heer, John Stasko, Christos Faloutsos Last Time
Data Mining Concepts & Tasks Duen Horng (Polo) Chau Georgia Tech CSE6242 / CX4242 Sept 9, 2014 Partly based on materials by Professors Guy Lebanon, Jeffrey Heer, John Stasko, Christos Faloutsos Last Time
