Uniform Resource Locators (URL)
|
|
|
- Madeline Hodges
- 6 years ago
- Views:
Transcription
1 The World Wide Web
2 Web Web site consists of simply of pages of text and images A web pages are render by a web browser Retrieving a webpage online: Client open a web browser on the local machine The web browser need to determine the ipaddress of the web server that is hosting the webpage ( Web browser contacted the DNS to reslovename space to IP addresses
3 Uniform Resource Locators (URL) The URL used by the web browser to identify a webpage The protocol used in the above example is the Hypertext transfer protocol The domain name is The web browser is requesting the content of file.htmlwhich is stored in the directory folder of a web server file.htmlis a file that describe text and images using the html (Hypertext markup language)format
4 Connecting to Web Server URLis used by the HTTP to access web information on a remote machine (web server) Resolving name space to IP address: The web browser check it DNS cache to resolve name space to IP address If no address is found the web browser send a DNS request Client-server TCP connection: The client make a TCP request on port 80 for HTTP HTTP requests: HTTP requests are encapsulated in the TCP packets HTTP request usually begin with commands such as POST or GET
5 Hypertext Mark up Language (HTML) Each HTTP response include a header Information in the HTTP response header includes: Information about the web server Software type and version number (Apache, Google GWS) The size of the payload The main body of the webpage in HTML source code
6 HTTP Request
7 HTML Coding HTML use a structural description of a document using special tags: Text formatting <i> text </i> for italics and <b> text </b> for bold Itemized lists is presented as: <ul> <li> first-item </li> <li> second-item </li> </ul> Hyperlinks is presented as: <a href= web-page-url >Description of the other page</a> Embedding images: <img src= URL-of the-image > Scripting code is represented as: <script> computer code </script>
8 HTML forms HTML forms allow user of the web to submit inputs to variables provided by the web server Server-side code is used by the web server to process user inputs Two methods to submit user inputted data: GET POST GET variables are recommended for querying a database POST variables are recommended when inserting or sending an . The browser will promote the user if he wish to submit the information
9 HTML GET method
10 HTML code with a form
11
12 Vulnerabilities in HTTP HTTP request and response packets are send in clear text The lack of encryption allow an attacker to eavesdrop on the communication and capture the payload Therefore sensitive data should transmitted using HTTPS
13 HTTPS HTTPS uses the secure socket layer (SSL) or transport layer security to secure data in transit Establishing a secure connection: 1. The browser provide the web server with a list of security primitives that are supported on the client machine. Hash function Crypto algorithms 2. The web server chooses the strongest cipher and hash that are supported by the client machine. 3. The web server send a certificate HTTPS Client HTTPS web server Supported hash and cipher Choose the strongest hash and cipher Send a certificate
14 HTTPS 1. Client verify the certificate 2. Client and web server generate a shared key 3. Symmetric encryption is used to transfer data over the secure channel HTTPS Client HTTPS web server Client send a random number E(R, P s) Server and client set a shared key Shared key and MAC is used to encrypt and verify the integrity of the data
15
16 Web Server Certificate Certificates are used to enable a client to verify the identity of web site Certificates are digitally signed by a certificates authority (CA) A website obtain a certificate by submitting a certificate signing request The certificate include the following information: Name of the CA Serial number of the certificate Experiation date Domain name of the web site Identifier of the public key scheme Public key Identifier of the crypto and hash algorithm Digital signature over the certificate data
17
18 Extended Validation Certificate Extended validation certificate can only be signed by high-profile CAs Extended validation certificate are designated in the CA field
19 Certificate Hierarchy Low-level certificates are signed by intermediary CA Top-level certificate is known as root certificate Root certificates for top-level domain are called anchor point Anchor points are usually stored in the OS.
20
21 Invalid certificate
22 Dynamic Content Web content could be: Static Dynamic Scripting languages allowed a computer code executed by a module of the browser Client-side scripting executed by the browser Server-side scripting executed by the server hiding the code from the user and only providing the user with the output
23 Document Object Model (DOM) The content of the web page can presented as in an organized way HTML code is presented in an object-oriented way Tags and page elements are represented as parent-child relationship
24 Java script Interactive and dynamic web browsing capacities are introduced through a scripting languages called java script
25
26
27
CNIT 129S: Securing Web Applications. Ch 3: Web Application Technologies
 CNIT 129S: Securing Web Applications Ch 3: Web Application Technologies HTTP Hypertext Transfer Protocol (HTTP) Connectionless protocol Client sends an HTTP request to a Web server Gets an HTTP response
CNIT 129S: Securing Web Applications Ch 3: Web Application Technologies HTTP Hypertext Transfer Protocol (HTTP) Connectionless protocol Client sends an HTTP request to a Web server Gets an HTTP response
recall: a Web page is a text document that contains additional formatting information in the HyperText Markup Language (HTML)
 HTML & Web Pages recall: a Web page is a text document that contains additional formatting information in the HyperText Markup Language (HTML) HTML specifies formatting within a page using tags in its
HTML & Web Pages recall: a Web page is a text document that contains additional formatting information in the HyperText Markup Language (HTML) HTML specifies formatting within a page using tags in its
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):ekk.worldtravelink.com
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
CSC 121 Computers and Scientific Thinking
 CSC 121 Computers and Scientific Thinking Fall 2005 HTML and Web Pages 1 HTML & Web Pages recall: a Web page is a text document that contains additional formatting information in the HyperText Markup Language
CSC 121 Computers and Scientific Thinking Fall 2005 HTML and Web Pages 1 HTML & Web Pages recall: a Web page is a text document that contains additional formatting information in the HyperText Markup Language
WHY CSRF WORKS. Implicit authentication by Web browsers
 WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
How A Website Works. - Shobha
 How A Website Works - Shobha Synopsis 1. 2. 3. 4. 5. 6. 7. 8. 9. What is World Wide Web? What makes web work? HTTP and Internet Protocols. URL s Client-Server model. Domain Name System. Web Browser, Web
How A Website Works - Shobha Synopsis 1. 2. 3. 4. 5. 6. 7. 8. 9. What is World Wide Web? What makes web work? HTTP and Internet Protocols. URL s Client-Server model. Domain Name System. Web Browser, Web
A Balanced Introduction to Computer Science, 3/E
 A Balanced Introduction to Computer Science, 3/E David Reed, Creighton University 2011 Pearson Prentice Hall ISBN 978-0-13-216675-1 Chapter 2 HTML and Web Pages 1 HTML & Web Pages recall: a Web page is
A Balanced Introduction to Computer Science, 3/E David Reed, Creighton University 2011 Pearson Prentice Hall ISBN 978-0-13-216675-1 Chapter 2 HTML and Web Pages 1 HTML & Web Pages recall: a Web page is
and the World Wide Web
 The Internet 1 The Internet and the World Wide Web The Internet is a global collection of interconnected networks Originally ARPNET had only four host computers on the network. Now tens of millions 1 http://computer.howstuffworks.com/internet-infrastructure.htm
The Internet 1 The Internet and the World Wide Web The Internet is a global collection of interconnected networks Originally ARPNET had only four host computers on the network. Now tens of millions 1 http://computer.howstuffworks.com/internet-infrastructure.htm
1.264 Lecture 12. HTML Introduction to FrontPage
 1.264 Lecture 12 HTML Introduction to FrontPage HTML Subset of Structured Generalized Markup Language (SGML), a document description language SGML is ISO standard Current version of HTML is version 4.01
1.264 Lecture 12 HTML Introduction to FrontPage HTML Subset of Structured Generalized Markup Language (SGML), a document description language SGML is ISO standard Current version of HTML is version 4.01
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
ICS 351: Today's plan. IPv6 routing protocols (summary) HTML HTTP web scripting languages certificates (review) cookies
 ICS 351: Today's plan IPv6 routing protocols (summary) HTML HTTP web scripting languages certificates (review) cookies IPv6 routing almost the same routing protocols as for IPv4: RIPng, OSPFv6, BGP with
ICS 351: Today's plan IPv6 routing protocols (summary) HTML HTTP web scripting languages certificates (review) cookies IPv6 routing almost the same routing protocols as for IPv4: RIPng, OSPFv6, BGP with
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Scan Report Executive Summary
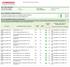 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Question No: 2 Which identifier is used to describe the application or process that submitted a log message?
 Volume: 65 Questions Question No: 1 Which definition of a fork in Linux is true? A. daemon to execute scheduled commands B. parent directory name of a file pathname C. macros for manipulating CPU sets
Volume: 65 Questions Question No: 1 Which definition of a fork in Linux is true? A. daemon to execute scheduled commands B. parent directory name of a file pathname C. macros for manipulating CPU sets
(1) I (2) S (3) P allow subscribers to connect to the (4) often provide basic services such as (5) (6)
 Collection of (1) Meta-network That is, a (2) of (3) Uses a standard set of protocols Also uses standards d for structuring t the information transferred (1) I (2) S (3) P allow subscribers to connect
Collection of (1) Meta-network That is, a (2) of (3) Uses a standard set of protocols Also uses standards d for structuring t the information transferred (1) I (2) S (3) P allow subscribers to connect
As we design and build out our HTML pages, there are some basics that we may follow for each page, site, and application.
 Extra notes - Client-side Design and Development Dr Nick Hayward HTML - Basics A brief introduction to some of the basics of HTML. Contents Intro element add some metadata define a base address
Extra notes - Client-side Design and Development Dr Nick Hayward HTML - Basics A brief introduction to some of the basics of HTML. Contents Intro element add some metadata define a base address
Cryptography SSL/TLS. Network Security Workshop. 3-5 October 2017 Port Moresby, Papua New Guinea
 Cryptography SSL/TLS Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 History Secure Sockets Layer was developed by Netscape in 1994 as a protocol which permitted persistent
Cryptography SSL/TLS Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 History Secure Sockets Layer was developed by Netscape in 1994 as a protocol which permitted persistent
The Structure of the Web. Jim and Matthew
 The Structure of the Web Jim and Matthew Workshop Structure 1. 2. 3. 4. 5. 6. 7. What is a browser? HTML CSS Javascript LUNCH Clients and Servers (creating a live website) Build your Own Website Workshop
The Structure of the Web Jim and Matthew Workshop Structure 1. 2. 3. 4. 5. 6. 7. What is a browser? HTML CSS Javascript LUNCH Clients and Servers (creating a live website) Build your Own Website Workshop
Scan Report Executive Summary. Part 2. Component Compliance Summary IP Address :
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
No, the bogus packet will fail the integrity check (which uses a shared MAC key).!
 1. High level questions a. Suppose Alice and Bob are communicating over an SSL session. Suppose an attacker, who does not have any of the shared keys, inserts a bogus TCP segment into a packet stream with
1. High level questions a. Suppose Alice and Bob are communicating over an SSL session. Suppose an attacker, who does not have any of the shared keys, inserts a bogus TCP segment into a packet stream with
M3-R3: INTERNET AND WEB DESIGN
 M3-R3: INTERNET AND WEB DESIGN NOTE: 1. There are TWO PARTS in this Module/Paper. PART ONE contains FOUR questions and PART TWO contains FIVE questions. 2. PART ONE is to be answered in the TEAR-OFF ANSWER
M3-R3: INTERNET AND WEB DESIGN NOTE: 1. There are TWO PARTS in this Module/Paper. PART ONE contains FOUR questions and PART TWO contains FIVE questions. 2. PART ONE is to be answered in the TEAR-OFF ANSWER
COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS. Web Access: HTTP Mehmet KORKMAZ
 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Web Access: HTTP 16501018 Mehmet KORKMAZ World Wide Web What is WWW? WWW = World Wide Web = Web!= Internet Internet is a global system of interconnected computer
COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Web Access: HTTP 16501018 Mehmet KORKMAZ World Wide Web What is WWW? WWW = World Wide Web = Web!= Internet Internet is a global system of interconnected computer
and the World Wide Web
 The Internet 1 The Internet and the World Wide Web The Internet is a global collection of interconnected networks Originally ARPNET had only four host computers on the network. Now over a billion people
The Internet 1 The Internet and the World Wide Web The Internet is a global collection of interconnected networks Originally ARPNET had only four host computers on the network. Now over a billion people
Web as a Distributed System
 Web as a Distributed System The World Wide Web is a large distributed system. In 1998 comprises 70-75% of Internet traffic. With large transfers of streaming media and p2p, no longer a majority of bytes,
Web as a Distributed System The World Wide Web is a large distributed system. In 1998 comprises 70-75% of Internet traffic. With large transfers of streaming media and p2p, no longer a majority of bytes,
Scan Report Executive Summary
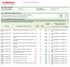 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
WWW, REST, and Web Services
 WWW, REST, and Web Services Instructor: Yongjie Zheng Aprile 18, 2017 CS 5553: Software Architecture and Design World Wide Web (WWW) What is the Web? What challenges does the Web have to address? 2 What
WWW, REST, and Web Services Instructor: Yongjie Zheng Aprile 18, 2017 CS 5553: Software Architecture and Design World Wide Web (WWW) What is the Web? What challenges does the Web have to address? 2 What
The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to
 1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
CS 470 Spring Distributed Web and File Systems. Mike Lam, Professor. Content taken from the following:
 CS 470 Spring 2017 Mike Lam, Professor Distributed Web and File Systems Content taken from the following: "Distributed Systems: Principles and Paradigms" by Andrew S. Tanenbaum and Maarten Van Steen (Chapters
CS 470 Spring 2017 Mike Lam, Professor Distributed Web and File Systems Content taken from the following: "Distributed Systems: Principles and Paradigms" by Andrew S. Tanenbaum and Maarten Van Steen (Chapters
UR what? ! URI: Uniform Resource Identifier. " Uniquely identifies a data entity " Obeys a specific syntax " schemename:specificstuff
 CS314-29 Web Protocols URI, URN, URL Internationalisation Role of HTML and XML HTTP and HTTPS interacting via the Web UR what? URI: Uniform Resource Identifier Uniquely identifies a data entity Obeys a
CS314-29 Web Protocols URI, URN, URL Internationalisation Role of HTML and XML HTTP and HTTPS interacting via the Web UR what? URI: Uniform Resource Identifier Uniquely identifies a data entity Obeys a
A HTML document has two sections 1) HEAD section and 2) BODY section A HTML file is saved with.html or.htm extension
 HTML Website is a collection of web pages on a particular topic, or of a organization, individual, etc. It is stored on a computer on Internet called Web Server, WWW stands for World Wide Web, also called
HTML Website is a collection of web pages on a particular topic, or of a organization, individual, etc. It is stored on a computer on Internet called Web Server, WWW stands for World Wide Web, also called
CS 470 Spring Distributed Web and File Systems. Mike Lam, Professor. Content taken from the following:
 CS 470 Spring 2018 Mike Lam, Professor Distributed Web and File Systems Content taken from the following: "Distributed Systems: Principles and Paradigms" by Andrew S. Tanenbaum and Maarten Van Steen (Chapters
CS 470 Spring 2018 Mike Lam, Professor Distributed Web and File Systems Content taken from the following: "Distributed Systems: Principles and Paradigms" by Andrew S. Tanenbaum and Maarten Van Steen (Chapters
Computer Networking. Chapter #1. Dr. Abdulrhaman Alameer
 Computer Networking Chapter #1 Dr. Abdulrhaman Alameer What is Computer Network? It is a collection of computers and devices interconnected by communications channels that facilitate communications among
Computer Networking Chapter #1 Dr. Abdulrhaman Alameer What is Computer Network? It is a collection of computers and devices interconnected by communications channels that facilitate communications among
Global Servers. The new masters
 Global Servers The new masters Course so far General OS principles processes, threads, memory management OS support for networking Protocol stacks TCP/IP, Novell Netware Socket programming RPC - (NFS),
Global Servers The new masters Course so far General OS principles processes, threads, memory management OS support for networking Protocol stacks TCP/IP, Novell Netware Socket programming RPC - (NFS),
CSc 450/550 Computer Networks Network Architectures & Client-Server Model
 CSc 450/550 Computer Networks Network Architectures & Client-Server Model Jianping Pan Summer 2007 5/17/07 CSc 450/550 1 Last lectures So far, nuts and bolts views of the Internet Internet evolution and
CSc 450/550 Computer Networks Network Architectures & Client-Server Model Jianping Pan Summer 2007 5/17/07 CSc 450/550 1 Last lectures So far, nuts and bolts views of the Internet Internet evolution and
Transport Layer Security
 CEN585 Computer and Network Security Transport Layer Security Dr. Mostafa Dahshan Department of Computer Engineering College of Computer and Information Sciences King Saud University mdahshan@ksu.edu.sa
CEN585 Computer and Network Security Transport Layer Security Dr. Mostafa Dahshan Department of Computer Engineering College of Computer and Information Sciences King Saud University mdahshan@ksu.edu.sa
Traditional Web Based Systems
 Chapter 12 Distributed Web Based Systems 1 Traditional Web Based Systems The Web is a huge distributed system consisting of millions of clients and servers for accessing linked documents Servers maintain
Chapter 12 Distributed Web Based Systems 1 Traditional Web Based Systems The Web is a huge distributed system consisting of millions of clients and servers for accessing linked documents Servers maintain
3. WWW and HTTP. Fig.3.1 Architecture of WWW
 3. WWW and HTTP The World Wide Web (WWW) is a repository of information linked together from points all over the world. The WWW has a unique combination of flexibility, portability, and user-friendly features
3. WWW and HTTP The World Wide Web (WWW) is a repository of information linked together from points all over the world. The WWW has a unique combination of flexibility, portability, and user-friendly features
Ethical Hacking and Countermeasures: Web Applications, Second Edition. Chapter 3 Web Application Vulnerabilities
 Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
Midterm 1 Review Sheet CSS 305 Sp 06
 This is a list of topics that we have covered so far. This is not all inclusive of every detail and there may be items on the exam that are not explicitly listed here, but these are the primary topics
This is a list of topics that we have covered so far. This is not all inclusive of every detail and there may be items on the exam that are not explicitly listed here, but these are the primary topics
Securing Internet Communication: TLS
 Securing Internet Communication: TLS CS 161: Computer Security Prof. David Wagner March 11, 2016 Today s Lecture Applying crypto technology in practice Two simple abstractions cover 80% of the use cases
Securing Internet Communication: TLS CS 161: Computer Security Prof. David Wagner March 11, 2016 Today s Lecture Applying crypto technology in practice Two simple abstractions cover 80% of the use cases
Web Engineering (Lecture 01)
 Web Engineering (Lecture 01) By: Kamran Ullah Lecturer (CS) Class BS(CS)-5 th semester Web Engineering Definition 1: Web Engineering is the application of systematic and disciplined approaches to the design,
Web Engineering (Lecture 01) By: Kamran Ullah Lecturer (CS) Class BS(CS)-5 th semester Web Engineering Definition 1: Web Engineering is the application of systematic and disciplined approaches to the design,
Computer Security 3e. Dieter Gollmann. Chapter 18: 1
 Computer Security 3e Dieter Gollmann www.wiley.com/college/gollmann Chapter 18: 1 Chapter 18: Web Security Chapter 18: 2 Web 1.0 browser HTTP request HTML + CSS data web server backend systems Chapter
Computer Security 3e Dieter Gollmann www.wiley.com/college/gollmann Chapter 18: 1 Chapter 18: Web Security Chapter 18: 2 Web 1.0 browser HTTP request HTML + CSS data web server backend systems Chapter
Welcome to the OWASP TOP 10
 Welcome to the OWASP TOP 10 Secure Development for Java Developers Dominik Schadow 03/20/2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART WIEN 1 AGENDA
Welcome to the OWASP TOP 10 Secure Development for Java Developers Dominik Schadow 03/20/2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART WIEN 1 AGENDA
Management Information Systems
 Management Information Systems Hands-On: HTML Basics Dr. Shankar Sundaresan 1 Elements, Tags, and Attributes Tags specify structural elements in a document, such as headings: tags and Attributes
Management Information Systems Hands-On: HTML Basics Dr. Shankar Sundaresan 1 Elements, Tags, and Attributes Tags specify structural elements in a document, such as headings: tags and Attributes
But where'd that extra "s" come from, and what does it mean?
 SSL/TLS While browsing Internet, some URLs start with "http://" while others start with "https://"? Perhaps the extra "s" when browsing websites that require giving over sensitive information, like paying
SSL/TLS While browsing Internet, some URLs start with "http://" while others start with "https://"? Perhaps the extra "s" when browsing websites that require giving over sensitive information, like paying
What You Will Learn Today
 CS101 Lecture 03: The World Wide Web and HTML Aaron Stevens 23 January 2011 1 What You Will Learn Today Is it the Internet or the World Wide Web? What s the difference? What is the encoding scheme behind
CS101 Lecture 03: The World Wide Web and HTML Aaron Stevens 23 January 2011 1 What You Will Learn Today Is it the Internet or the World Wide Web? What s the difference? What is the encoding scheme behind
Index. alt, 38, 57 class, 86, 88, 101, 107 href, 24, 51, 57 id, 86 88, 98 overview, 37. src, 37, 57. backend, WordPress, 146, 148
 Index Numbers & Symbols (angle brackets), in HTML, 47 : (colon), in CSS, 96 {} (curly brackets), in CSS, 75, 96. (dot), in CSS, 89, 102 # (hash mark), in CSS, 87 88, 99 % (percent) font size, in CSS,
Index Numbers & Symbols (angle brackets), in HTML, 47 : (colon), in CSS, 96 {} (curly brackets), in CSS, 75, 96. (dot), in CSS, 89, 102 # (hash mark), in CSS, 87 88, 99 % (percent) font size, in CSS,
Overview of SSL/TLS. Luke Anderson. 12 th May University Of Sydney.
 Overview of SSL/TLS Luke Anderson luke@lukeanderson.com.au 12 th May 2017 University Of Sydney Overview 1. Introduction 1.1 Raw HTTP 1.2 Introducing SSL/TLS 2. Certificates 3. Attacks Introduction Raw
Overview of SSL/TLS Luke Anderson luke@lukeanderson.com.au 12 th May 2017 University Of Sydney Overview 1. Introduction 1.1 Raw HTTP 1.2 Introducing SSL/TLS 2. Certificates 3. Attacks Introduction Raw
Chapter 4: Networking and the Internet. Figure 4.1 Network topologies. Network Classifications. Protocols. (continued)
 Chapter 4: Networking and the Internet Computer Science: An Overview Eleventh Edition by J. Glenn Brookshear Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3 The World
Chapter 4: Networking and the Internet Computer Science: An Overview Eleventh Edition by J. Glenn Brookshear Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3 The World
Chapter 4: Networking and the Internet
 Chapter 4: Networking and the Internet Computer Science: An Overview Eleventh Edition by J. Glenn Brookshear Copyright 2012 Pearson Education, Inc. Chapter 4: Networking and the Internet 4.1 Network Fundamentals
Chapter 4: Networking and the Internet Computer Science: An Overview Eleventh Edition by J. Glenn Brookshear Copyright 2012 Pearson Education, Inc. Chapter 4: Networking and the Internet 4.1 Network Fundamentals
Application Layer & Sockets
 Chapter 4 Application Layer & Sockets If you ever write Internet code, almost surely it will be application layer code. 4.1 HTTP Today a large majority of all data is transferred using the HTTP protocol,
Chapter 4 Application Layer & Sockets If you ever write Internet code, almost surely it will be application layer code. 4.1 HTTP Today a large majority of all data is transferred using the HTTP protocol,
Objectives. Connecting with Computer Science 2
 Objectives Learn what the Internet really is Become familiar with the architecture of the Internet Become familiar with Internet-related protocols Understand how the TCP/IP protocols relate to the Internet
Objectives Learn what the Internet really is Become familiar with the architecture of the Internet Become familiar with Internet-related protocols Understand how the TCP/IP protocols relate to the Internet
1/27/2013. Outline. Basic Links. Links and Navigations INTRODUCTION TO WEB DEVELOPMENT AND HTML
 Outline Links and Navigation: Basic Links E-mail links, Directory Structure and URLs Exercise INTRODUCTION TO WEB DEVELOPMENT AND HTML Lecture 04 - Spring 2013 Basic Links A link is specified with the
Outline Links and Navigation: Basic Links E-mail links, Directory Structure and URLs Exercise INTRODUCTION TO WEB DEVELOPMENT AND HTML Lecture 04 - Spring 2013 Basic Links A link is specified with the
(Refer Slide Time: 01:41) (Refer Slide Time: 01:42)
 Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #14 HTML -Part II We continue with our discussion on html.
Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #14 HTML -Part II We continue with our discussion on html.
Web Technology. COMP476 Networked Computer Systems. Hypertext and Hypermedia. Document Representation. Client-Server Paradigm.
 Web Technology COMP476 Networked Computer Systems - Paradigm The method of interaction used when two application programs communicate over a network. A server application waits at a known address and a
Web Technology COMP476 Networked Computer Systems - Paradigm The method of interaction used when two application programs communicate over a network. A server application waits at a known address and a
Application Layer & Sockets
 4.1. HTTP 29 a non-default port is used, a query-string to pass arguments to a resource, and a fragment describing which part of the resource is of interest: scheme://user:password@host:port/path?query#fragment.
4.1. HTTP 29 a non-default port is used, a query-string to pass arguments to a resource, and a fragment describing which part of the resource is of interest: scheme://user:password@host:port/path?query#fragment.
World Wide Web. Hypertext
 World Wide Web HTTP, HTTPS SSL, TLS URL, Hypertext WWW s and Browsers Proxy, Plugin, Cookie Hypertext The WWW implementation of documents which include hyperlinks referencing other documents on the system.
World Wide Web HTTP, HTTPS SSL, TLS URL, Hypertext WWW s and Browsers Proxy, Plugin, Cookie Hypertext The WWW implementation of documents which include hyperlinks referencing other documents on the system.
AGENDA. HTML CODING YOUR HOMEPAGE [ Part IV ] :: NAVIGATION <nav> :: CSS CODING FOR HOMEPAGE [ <nav> & child elements ] CLASS :: 13.
![AGENDA. HTML CODING YOUR HOMEPAGE [ Part IV ] :: NAVIGATION <nav> :: CSS CODING FOR HOMEPAGE [ <nav> & child elements ] CLASS :: 13. AGENDA. HTML CODING YOUR HOMEPAGE [ Part IV ] :: NAVIGATION <nav> :: CSS CODING FOR HOMEPAGE [ <nav> & child elements ] CLASS :: 13.](/thumbs/89/100176654.jpg) :: DIGITAL IMAGING FUNDAMENTALS :: CLASS NOTES CLASS :: 13 04.26 2017 3 Hours AGENDA HTML CODING YOUR HOMEPAGE [ Part IV ] :: NAVIGATION home works
:: DIGITAL IMAGING FUNDAMENTALS :: CLASS NOTES CLASS :: 13 04.26 2017 3 Hours AGENDA HTML CODING YOUR HOMEPAGE [ Part IV ] :: NAVIGATION home works
HP Instant Support Enterprise Edition (ISEE) Security overview
 HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
Unit 3 - Week 2 lectures: Building your webapp
 X Courses» Modern Application Development Announcements Course Forum Progress Mentor Discourse forum Discussion Forum Unit 3 - Week 2 lectures: Building your webapp Course outline How to access the portal?
X Courses» Modern Application Development Announcements Course Forum Progress Mentor Discourse forum Discussion Forum Unit 3 - Week 2 lectures: Building your webapp Course outline How to access the portal?
Chapter 4: Networking and the Internet
 Chapter 4: Networking and the Internet 2015 Pearson Education Limited 2015 Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3 The World Wide Web 4.4 Internet Protocols
Chapter 4: Networking and the Internet 2015 Pearson Education Limited 2015 Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3 The World Wide Web 4.4 Internet Protocols
HTML + CSS. ScottyLabs WDW. Overview HTML Tags CSS Properties Resources
 HTML + CSS ScottyLabs WDW OVERVIEW What are HTML and CSS? How can I use them? WHAT ARE HTML AND CSS? HTML - HyperText Markup Language Specifies webpage content hierarchy Describes rough layout of content
HTML + CSS ScottyLabs WDW OVERVIEW What are HTML and CSS? How can I use them? WHAT ARE HTML AND CSS? HTML - HyperText Markup Language Specifies webpage content hierarchy Describes rough layout of content
Tabular Presentation of the Application Software Extended Package for Web Browsers
 Tabular Presentation of the Application Software Extended Package for Web Browsers Version: 2.0 2015-06-16 National Information Assurance Partnership Revision History Version Date Comment v 2.0 2015-06-16
Tabular Presentation of the Application Software Extended Package for Web Browsers Version: 2.0 2015-06-16 National Information Assurance Partnership Revision History Version Date Comment v 2.0 2015-06-16
HTML CS 4640 Programming Languages for Web Applications
 HTML CS 4640 Programming Languages for Web Applications 1 Anatomy of (Basic) Website Your content + HTML + CSS = Your website structure presentation A website is a way to present your content to the world,
HTML CS 4640 Programming Languages for Web Applications 1 Anatomy of (Basic) Website Your content + HTML + CSS = Your website structure presentation A website is a way to present your content to the world,
The Web. Session 4 INST 301 Introduction to Information Science
 The Web Session 4 INST 301 Introduction to Information Science Outline Using The Internet The Web Creating Web pages TCP/IP layer architecture Application Virtual network service Application Transport
The Web Session 4 INST 301 Introduction to Information Science Outline Using The Internet The Web Creating Web pages TCP/IP layer architecture Application Virtual network service Application Transport
2. Introduction to Internet Applications
 2. Introduction to Internet Applications 1. Representation and Transfer 2. Web Protocols 3. Some Other Application Layer Protocols 4. Uniform Resource Identifiers (URIs) 5. Uniform Resource Locators (URLs)
2. Introduction to Internet Applications 1. Representation and Transfer 2. Web Protocols 3. Some Other Application Layer Protocols 4. Uniform Resource Identifiers (URIs) 5. Uniform Resource Locators (URLs)
Introduction to Computer Science. William Hsu Department of Computer Science and Engineering National Taiwan Ocean University
 Introduction to Computer Science William Hsu Department of Computer Science and Engineering National Taiwan Ocean University Chapter 4: Networking and the Internet No one owns the Internet, and only one
Introduction to Computer Science William Hsu Department of Computer Science and Engineering National Taiwan Ocean University Chapter 4: Networking and the Internet No one owns the Internet, and only one
HTTP & Websites. Web Browsers. Web Servers vs. Web sites. World Wide Web. Internet Explorer. Surfing the World Wide Web. Part 4. The World Wide Web
 HTTP & Websites Web Browsers Part 4 Surfing the World Wide Web World Wide Web Web Servers vs. Web sites The World Wide Web massive collection of websites on the Internet they link to each other and form
HTTP & Websites Web Browsers Part 4 Surfing the World Wide Web World Wide Web Web Servers vs. Web sites The World Wide Web massive collection of websites on the Internet they link to each other and form
P2_L12 Web Security Page 1
 P2_L12 Web Security Page 1 Reference: Computer Security by Stallings and Brown, Chapter (not specified) The web is an extension of our computing environment, because most of our daily tasks involve interaction
P2_L12 Web Security Page 1 Reference: Computer Security by Stallings and Brown, Chapter (not specified) The web is an extension of our computing environment, because most of our daily tasks involve interaction
Module 1: Understanding and Installing Internet Information Services
 Course Outline Module 1: Understanding and Installing Internet Information Services In this module, you will learn about the infrastructure prerequisites for using Microsoft Internet Information Services
Course Outline Module 1: Understanding and Installing Internet Information Services In this module, you will learn about the infrastructure prerequisites for using Microsoft Internet Information Services
Browser behavior can be quite complex, using more HTTP features than the basic exchange, this trace will show us how much gets transferred.
 Lab Exercise HTTP Objective HTTP (HyperText Transfer Protocol) is the main protocol underlying the Web. HTTP functions as a request response protocol in the client server computing model. A web browser,
Lab Exercise HTTP Objective HTTP (HyperText Transfer Protocol) is the main protocol underlying the Web. HTTP functions as a request response protocol in the client server computing model. A web browser,
1. The basic building block of an HTML document is called a(n) a. tag. b. element. c. attribute. d. container. Answer: b Page 5
 Name Date Final Exam Prep Questions Worksheet #1 1. The basic building block of an HTML document is called a(n) a. tag. b. element. c. attribute. d. container. Answer: b Page 5 2. Which of the following
Name Date Final Exam Prep Questions Worksheet #1 1. The basic building block of an HTML document is called a(n) a. tag. b. element. c. attribute. d. container. Answer: b Page 5 2. Which of the following
A Brief Introduction to HTML
 A P P E N D I X HTML SuMMAry J A Brief Introduction to HTML A web page is written in a language called HTML (Hypertext Markup Language). Like Java code, HTML code is made up of text that follows certain
A P P E N D I X HTML SuMMAry J A Brief Introduction to HTML A web page is written in a language called HTML (Hypertext Markup Language). Like Java code, HTML code is made up of text that follows certain
Notes beforehand... For more details: See the (online) presentation program.
 Notes beforehand... Notes beforehand... For more details: See the (online) presentation program. Topical overview: main arcs fundamental subjects advanced subject WTRs Lecture: 2 3 4 5 6 7 8 Today: the
Notes beforehand... Notes beforehand... For more details: See the (online) presentation program. Topical overview: main arcs fundamental subjects advanced subject WTRs Lecture: 2 3 4 5 6 7 8 Today: the
Network Security. Thierry Sans
 Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
Transport Level Security
 2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
A Security Evaluation of DNSSEC with NSEC Review
 A Security Evaluation of DNSSEC with NSEC Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka November 16, 2011 1 Introduction to the topic and the reason for the topic being
A Security Evaluation of DNSSEC with NSEC Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka November 16, 2011 1 Introduction to the topic and the reason for the topic being
11. HTML5 and Future Web Application
 11. HTML5 and Future Web Application 1. Where to learn? http://www.w3schools.com/html/html5_intro.asp 2. Where to start: http://www.w3schools.com/html/html_intro.asp 3. easy to start with an example code
11. HTML5 and Future Web Application 1. Where to learn? http://www.w3schools.com/html/html5_intro.asp 2. Where to start: http://www.w3schools.com/html/html_intro.asp 3. easy to start with an example code
Session 2. Background. Lecture Objectives
 Session 2 Background 1 Lecture Objectives Understand how an Internet resource is accessed Understand the high level structure of the Internet cloud Understand the high level structure of the TCP/IP protocols
Session 2 Background 1 Lecture Objectives Understand how an Internet resource is accessed Understand the high level structure of the Internet cloud Understand the high level structure of the TCP/IP protocols
WEB TECHNOLOGIES CHAPTER 1
 WEB TECHNOLOGIES CHAPTER 1 WEB ESSENTIALS: CLIENTS, SERVERS, AND COMMUNICATION Modified by Ahmed Sallam Based on original slides by Jeffrey C. Jackson THE INTERNET Technical origin: ARPANET (late 1960
WEB TECHNOLOGIES CHAPTER 1 WEB ESSENTIALS: CLIENTS, SERVERS, AND COMMUNICATION Modified by Ahmed Sallam Based on original slides by Jeffrey C. Jackson THE INTERNET Technical origin: ARPANET (late 1960
Chapter 4 The Internet
 Chapter 4 The Internet Dr. Farzana Rahman Assistant Professor Department of Computer Science James Madison University Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3
Chapter 4 The Internet Dr. Farzana Rahman Assistant Professor Department of Computer Science James Madison University Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3
CST272 Getting Started Page 1
 CST272 Getting Started Page 1 1 2 3 5 6 8 10 Introduction to ASP.NET and C# CST272 ASP.NET ASP.NET Server Controls (Page 1) Server controls can be Buttons, TextBoxes, etc. In the source code, ASP.NET controls
CST272 Getting Started Page 1 1 2 3 5 6 8 10 Introduction to ASP.NET and C# CST272 ASP.NET ASP.NET Server Controls (Page 1) Server controls can be Buttons, TextBoxes, etc. In the source code, ASP.NET controls
The Cisco HCM-F Administrative Interface
 CHAPTER 5 This chapter contains information on the following topics: Overview of Cisco HCM-F Administrative Interface, page 5-1 Browser Support, page 5-2 Login and Logout, page 5-4 Online Help, page 5-5
CHAPTER 5 This chapter contains information on the following topics: Overview of Cisco HCM-F Administrative Interface, page 5-1 Browser Support, page 5-2 Login and Logout, page 5-4 Online Help, page 5-5
Web Programming Paper Solution (Chapter wise)
 Introduction to web technology Three tier/ n-tier architecture of web multitier architecture (often referred to as n-tier architecture) is a client server architecture in which presentation, application
Introduction to web technology Three tier/ n-tier architecture of web multitier architecture (often referred to as n-tier architecture) is a client server architecture in which presentation, application
Securing Internet Communication
 Securing Internet Communication CS 161 - Computer Security Profs. Vern Paxson & David Wagner TAs: John Bethencourt, Erika Chin, Matthew Finifter, Cynthia Sturton, Joel Weinberger http://inst.eecs.berkeley.edu/~cs161/
Securing Internet Communication CS 161 - Computer Security Profs. Vern Paxson & David Wagner TAs: John Bethencourt, Erika Chin, Matthew Finifter, Cynthia Sturton, Joel Weinberger http://inst.eecs.berkeley.edu/~cs161/
LECT 8 WEB SECURITY BROWSER SECURITY. Repetition Lect 7. WEB Security
 Repetition Lect 7 LECT 8 WEB SECURITY Access control Runtime protection Trusted computing Java as basic model for signed code Trusted Computing Group TPM ARM TrustZone Mobile Network security GSM security
Repetition Lect 7 LECT 8 WEB SECURITY Access control Runtime protection Trusted computing Java as basic model for signed code Trusted Computing Group TPM ARM TrustZone Mobile Network security GSM security
Creating Web Pages. Getting Started
 Creating Web Pages Getting Started Overview What Web Pages Are How Web Pages are Formatted Putting Graphics on Web Pages How Web Pages are Linked Linking to other Files What Web Pages Are Web Pages combine
Creating Web Pages Getting Started Overview What Web Pages Are How Web Pages are Formatted Putting Graphics on Web Pages How Web Pages are Linked Linking to other Files What Web Pages Are Web Pages combine
Data Communication & Computer Networks MCQ S
 Data Communication & Computer Networks MCQ S 1. The translates internet domain and host names to IP address. a) domain name system b) routing information protocol c) network time protocol d) internet relay
Data Communication & Computer Networks MCQ S 1. The translates internet domain and host names to IP address. a) domain name system b) routing information protocol c) network time protocol d) internet relay
SC/CSE 3213 Winter Sebastian Magierowski York University CSE 3213, W13 L8: TCP/IP. Outline. Forwarding over network and data link layers
 SC/CSE 3213 Winter 2013 L8: TCP/IP Overview Sebastian Magierowski York University 1 Outline TCP/IP Reference Model A set of protocols for internetworking The basis of the modern IP Datagram Exchange Examples
SC/CSE 3213 Winter 2013 L8: TCP/IP Overview Sebastian Magierowski York University 1 Outline TCP/IP Reference Model A set of protocols for internetworking The basis of the modern IP Datagram Exchange Examples
Introduction to using HTML to design webpages
 Introduction to using HTML to design webpages #HTML is the script that web pages are written in. It describes the content and structure of a web page so that a browser is able to interpret and render the
Introduction to using HTML to design webpages #HTML is the script that web pages are written in. It describes the content and structure of a web page so that a browser is able to interpret and render the
Web Publishing Basics I
 Web Publishing Basics I Jeff Pankin Information Services and Technology Contents Course Objectives... 2 Creating a Web Page with HTML... 3 What is Dreamweaver?... 3 What is HTML?... 3 What are the basic
Web Publishing Basics I Jeff Pankin Information Services and Technology Contents Course Objectives... 2 Creating a Web Page with HTML... 3 What is Dreamweaver?... 3 What is HTML?... 3 What are the basic
UFCEKG Lecture 2. Mashups N. H. N. D. de Silva (Slides adapted from Prakash Chatterjee, UWE)
 UFCEKG 20 2 Data, Schemas & Applications Lecture 2 Introduction to thewww WWW, URLs, HTTP, Services and Mashups N. H. N. D. de Silva (Slides adapted from Prakash Chatterjee, UWE) Suppose all the information
UFCEKG 20 2 Data, Schemas & Applications Lecture 2 Introduction to thewww WWW, URLs, HTTP, Services and Mashups N. H. N. D. de Silva (Slides adapted from Prakash Chatterjee, UWE) Suppose all the information
Motivation For Networking. Information access Interaction among cooperative application programs Resource sharing
 Motivation For Networking Information access Interaction among cooperative application programs Resource sharing CS422 -- PART 1 13 2003 Practical Results E-mail File transfer/access Web browsing Remote
Motivation For Networking Information access Interaction among cooperative application programs Resource sharing CS422 -- PART 1 13 2003 Practical Results E-mail File transfer/access Web browsing Remote
Markup Language. Made up of elements Elements create a document tree
 Patrick Behr Markup Language HTML is a markup language HTML markup instructs browsers how to display the content Provides structure and meaning to the content Does not (should not) describe how
Patrick Behr Markup Language HTML is a markup language HTML markup instructs browsers how to display the content Provides structure and meaning to the content Does not (should not) describe how
AGENDA :: MULTIMEDIA TOOLS :: CLASS NOTES
 CLASS :: 14 04.28 2017 3 Hours AGENDA CREATE A WORKS PAGE [ HTML ] :: Open index.html :: Save As works.html :: Edit works.html to modify header, 3 divisions for works, then add your content :: Edit index.html
CLASS :: 14 04.28 2017 3 Hours AGENDA CREATE A WORKS PAGE [ HTML ] :: Open index.html :: Save As works.html :: Edit works.html to modify header, 3 divisions for works, then add your content :: Edit index.html
Mac OS X Server Web Technologies Administration. For Version 10.3 or Later
 Mac OS X Server Web Technologies Administration For Version 10.3 or Later apple Apple Computer, Inc. 2003 Apple Computer, Inc. All rights reserved. The owner or authorized user of a valid copy of Mac OS
Mac OS X Server Web Technologies Administration For Version 10.3 or Later apple Apple Computer, Inc. 2003 Apple Computer, Inc. All rights reserved. The owner or authorized user of a valid copy of Mac OS
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
ICS 351: Today's plan. web scripting languages HTTPS: SSL and TLS certificates cookies DNS reminder
 ICS 351: Today's plan web scripting languages HTTPS: SSL and TLS certificates cookies DNS reminder 1 web scripting languages web content described by HTML was originally static, corresponding to files
ICS 351: Today's plan web scripting languages HTTPS: SSL and TLS certificates cookies DNS reminder 1 web scripting languages web content described by HTML was originally static, corresponding to files
Data Security and Privacy. Topic 14: Authentication and Key Establishment
 Data Security and Privacy Topic 14: Authentication and Key Establishment 1 Announcements Mid-term Exam Tuesday March 6, during class 2 Need for Key Establishment Encrypt K (M) C = Encrypt K (M) M = Decrypt
Data Security and Privacy Topic 14: Authentication and Key Establishment 1 Announcements Mid-term Exam Tuesday March 6, during class 2 Need for Key Establishment Encrypt K (M) C = Encrypt K (M) M = Decrypt
