SAS USER FORUM NORWAY 2017 USER FORUM. Show Off Your OAuth Authenticating to Web Services in SAS
|
|
|
- Daniella York
- 6 years ago
- Views:
Transcription
1 SAS USER FORUM USER FORUM Show Off Your OAuth
2 Who am I? Show Off Your Oauth My name is Jon Kolstad and I work as a Senior Technical Architect at SAS Institute Norway. Some of the things I do include: Planning of SAS Deployments, Installation and Custom Configuration of SAS Solutions Optimizing SAS and how SAS interacts with other components in the Enterprise Architecture
3 So you have SAS, what can you do with it? Virtually no limit to what you can build in SAS However, there are many online services already built that you are probably already using Online services that have an API makes programmatically access possible Find new uses for your SAS data! Get data from new sources into SAS!
4 Some examples of Web Services with API Online storage Box, Dropbox Cloud services Google, AWS, Azure Salesforce Soundcloud, Spotify
5 Security in Web Services TLS/SSL encryption for data in transit Application Authorization Client Authentication Industry standards OpenID, OAuth 1.0/2.0 Custom solutions Tokens, HTTP Basic
6 OAuth A security protocol that enables users to grant third-party access to their web resources without sharing Roles The Third-Party Application: "Client" The API: "Resource Server" The Authorization Server The User: "Resource Owner"
7 Configuring access to the resource follows a the valet-key principle. With a valet-key your car Can only be driven for 5 minutes Is only accessible by the doors, not the trunk Provide limited access to only the resources you define The valet-key in OAuth is essentially a token string The token string is included in an HTTP header All HTTP requests to the resource must have this header
8 How to get started? Find a useful service online Look for Developer or API access methods Follow the guidelines on configuring API access Demo Example using Google APIs to access Google Drive Same approach for all G-Suite services, Google Cloud Services
9 You need a valid Google account Go to
10 Configure a project (an application)
11
12
13
14
15
16
17
18
19
20
21
22 The client ID will be used in a third-party client The client secret should be stored in a file accessible by your third-party client In this demo, the third-party client is in both cases a SAS program When trying the demo on your own these two will be unique to you Make sure you update the SAS example code with your own values
23 Get an access code filename resptext TEMP; filename resphdrs TEMP; %let auth_url= %let client_id= id1rs7nasllprpks5e1jo8tb3dcfqom.apps.googleusercontent.com; %let redirect_uri=urn:ietf:wg:oauth:2.0:oob; %let drive_scope= %let url=&auth_url.?client_id=&client_id.%nrstr(&redirect_uri)=&redirect_uri.%nrstr(&res ponse_type=code&scope=openid%20 )%20&drive_scope.&state=security_token); proc http url="&url" headerout=resphdrs out=resptext; run; data _null_; infile resphdrs length=len scanover truncover; ' loc $varying1024. len; call symput('location',trim(loc)); put "&location"; run; options noxsync noxwait; x "start """" ""&location.""";
24 Complete the steps in a browser
25
26 Note the one-time code Repeat if you need a new code
27 %let code=4/t-3medrknb5ubifycrbz3j6cmhgxgs4wscb_wbaieki; /* You also need the application code returned by Google when you created the application /* /* This code may be stored in a file */ filename sec "C:\Users\norjko\Documents\SAS Forum Norway\secret.dat"; data _null_; length str $1024; fid = fopen("sec"); rc = fread(fid); rc = fget(fid, str, 256); call symput("client_secret",trim(str)); rc = fclose(fid); run; /* HTTP request for access_token, a token is valid for 1 hour (3600 seconds) */ filename resptext TEMP; filename resphdrs TEMP; proc http url=" method="post" out=resptext headerout=resphdrs ct="application/x-www-form-urlencoded" in="code=&code.%nrstr(&client_id)=&client_id.%nrstr(&client_secret)=&client_secret. %nrstr(&redirect_uri)=&redirect_uri.&grant_type=authorization_code"; run; %let client_secret=; data _null_; infile resphdrs truncover scanover length=len; ' t $varying1024. len; token = dequote(t); call symput("access_token",trim(token)); put "&access_token"; run;
28
29 Download the file filename sample "C:\Users\norjko\Documents\SAS Forum Norway\README.TXT"; proc http url=" ia" out=sample; headers "Authorization" = "Bearer &access_token"; run;
30
31 Generate some content in SAS ods rtf file="c:\users\norjko\documents\sas Forum Norway\CLASS Data.rtf"; title "Listing of CLASS Data"; proc print data=sashelp.class; run; ods rtf close;
32 Build HTTP request for upload to Drive filename file "C:\Users\norjko\Documents\SAS Forum Norway\CLASS Data.rtf"; filename request TEMP; %let boundary=foobar; /* Build the multipart request */ data _null_; infile file end=eof; file request; /* for each file we are sending, we need to add some special headers at the beginning*/ if _n_ = 1 then do; put "--foobar"; /* This separates each data piece as a separate entity. Must start with -- */ put "Content-Type: application/json"; put ; /* Must end with a CRLF signaling that what comes next is the actual entity */ put '{'; put '"name": "CLASS Data.rtf"'; put '}'; put ; put "--foobar"; put "Content-Type: application/rtf"; put ; end; input; put _infile_; /* add the actual file to be sent*/ /* the end of the multipart blob needs to be terminated */ if eof then do; put ; /* Must have a CRLF*/ put "--foobar--"; /* must start and end with --*/ end; run;
33 Complete the HTTP request and send it data _null_; length bytes $1024; fid = fopen("request"); rc = fread(fid); bytes = finfo(fid, 'File Size (bytes)'); call symput("content_length",trim(bytes)); rc = fclose(fid); put bytes; run; proc http method="post" url=" in = request out = resptext headerout = resphdrs; headers "Authorization" = "Bearer &access_token" "Content-Type" = "multipart/related; boundary=&boundary" "Content-Length" = "&content_length"; run;
34
35
36 Additional Inspiration This presentation was inspired by a SGF 17 paper by Joseph Henry Other related SAS papers
37 Thank you for attending!
Mobile Procurement REST API (MOBPROC): Access Tokens
 Mobile Procurement REST API (MOBPROC): Access Tokens Tangoe, Inc. 35 Executive Blvd. Orange, CT 06477 +1.203.859.9300 www.tangoe.com TABLE OF CONTENTS HOW TO REQUEST AN ACCESS TOKEN USING THE PASSWORD
Mobile Procurement REST API (MOBPROC): Access Tokens Tangoe, Inc. 35 Executive Blvd. Orange, CT 06477 +1.203.859.9300 www.tangoe.com TABLE OF CONTENTS HOW TO REQUEST AN ACCESS TOKEN USING THE PASSWORD
Using OAuth 2.0 to Access ionbiz APIs
 Using OAuth 2.0 to Access ionbiz APIs ionbiz APIs use the OAuth 2.0 protocol for authentication and authorization. ionbiz supports common OAuth 2.0 scenarios such as those for web server, installed, and
Using OAuth 2.0 to Access ionbiz APIs ionbiz APIs use the OAuth 2.0 protocol for authentication and authorization. ionbiz supports common OAuth 2.0 scenarios such as those for web server, installed, and
WEB API. Nuki Home Solutions GmbH. Münzgrabenstraße 92/ Graz Austria F
 WEB API v 1. 1 0 8. 0 5. 2 0 1 8 1. Introduction 2. Calling URL 3. Swagger Interface Example API call through Swagger 4. Authentication API Tokens OAuth 2 Code Flow OAuth2 Authentication Example 1. Authorization
WEB API v 1. 1 0 8. 0 5. 2 0 1 8 1. Introduction 2. Calling URL 3. Swagger Interface Example API call through Swagger 4. Authentication API Tokens OAuth 2 Code Flow OAuth2 Authentication Example 1. Authorization
Web Metrics at Scale: Using Base SAS to Access Google Analytics APIs
 Paper SAS2120-2018 Web Metrics at Scale: Using Base SAS to Access Google Analytics APIs ABSTRACT Chris Hemedinger, SAS Institute Inc., Cary, NC With SAS 9.4M4 and later, it's finally easy (relatively speaking)
Paper SAS2120-2018 Web Metrics at Scale: Using Base SAS to Access Google Analytics APIs ABSTRACT Chris Hemedinger, SAS Institute Inc., Cary, NC With SAS 9.4M4 and later, it's finally easy (relatively speaking)
Usage of "OAuth2" policy action in CentraSite and Mediator
 Usage of "OAuth2" policy action in CentraSite and Mediator Introduction Prerequisite Configurations Mediator Configurations watt.server.auth.skipformediator The pg.oauth2 Parameters Asset Creation and
Usage of "OAuth2" policy action in CentraSite and Mediator Introduction Prerequisite Configurations Mediator Configurations watt.server.auth.skipformediator The pg.oauth2 Parameters Asset Creation and
Tutorial: Building the Services Ecosystem
 Tutorial: Building the Services Ecosystem GlobusWorld 2018 Steve Tuecke tuecke@globus.org What is a services ecosystem? Anybody can build services with secure REST APIs App Globus Transfer Your Service
Tutorial: Building the Services Ecosystem GlobusWorld 2018 Steve Tuecke tuecke@globus.org What is a services ecosystem? Anybody can build services with secure REST APIs App Globus Transfer Your Service
A SAS Macro Utility to Modify and Validate RTF Outputs for Regional Analyses Jagan Mohan Achi, PPD, Austin, TX Joshua N. Winters, PPD, Rochester, NY
 PharmaSUG 2014 - Paper BB14 A SAS Macro Utility to Modify and Validate RTF Outputs for Regional Analyses Jagan Mohan Achi, PPD, Austin, TX Joshua N. Winters, PPD, Rochester, NY ABSTRACT Clinical Study
PharmaSUG 2014 - Paper BB14 A SAS Macro Utility to Modify and Validate RTF Outputs for Regional Analyses Jagan Mohan Achi, PPD, Austin, TX Joshua N. Winters, PPD, Rochester, NY ABSTRACT Clinical Study
Advanced API Security
 Advanced API Security ITANA Group Nuwan Dias Architect 22/06/2017 Agenda 2 HTTP Basic Authentication Authorization: Basic QWxhZGRpbjpPcGVuU2VzYW1l 3 API Security is about controlling Access Delegation
Advanced API Security ITANA Group Nuwan Dias Architect 22/06/2017 Agenda 2 HTTP Basic Authentication Authorization: Basic QWxhZGRpbjpPcGVuU2VzYW1l 3 API Security is about controlling Access Delegation
Integrating with ClearPass HTTP APIs
 Integrating with ClearPass HTTP APIs HTTP based APIs The world of APIs is full concepts that are not immediately obvious to those of us without software development backgrounds and terms like REST, RPC,
Integrating with ClearPass HTTP APIs HTTP based APIs The world of APIs is full concepts that are not immediately obvious to those of us without software development backgrounds and terms like REST, RPC,
Protect Your API with OAuth 2. Rob Allen
 Protect Your API with OAuth 2 Authentication Know who is logging into your API Rate limiting Revoke application access if its a problem Allow users to revoke 3rd party applications How? Authorization header:
Protect Your API with OAuth 2 Authentication Know who is logging into your API Rate limiting Revoke application access if its a problem Allow users to revoke 3rd party applications How? Authorization header:
NIELSEN API PORTAL USER REGISTRATION GUIDE
 NIELSEN API PORTAL USER REGISTRATION GUIDE 1 INTRODUCTION In order to access the Nielsen API Portal services, there are three steps that need to be followed sequentially by the user: 1. User Registration
NIELSEN API PORTAL USER REGISTRATION GUIDE 1 INTRODUCTION In order to access the Nielsen API Portal services, there are three steps that need to be followed sequentially by the user: 1. User Registration
API Gateway. Version 7.5.1
 O A U T H U S E R G U I D E API Gateway Version 7.5.1 15 September 2017 Copyright 2017 Axway All rights reserved. This documentation describes the following Axway software: Axway API Gateway 7.5.1 No part
O A U T H U S E R G U I D E API Gateway Version 7.5.1 15 September 2017 Copyright 2017 Axway All rights reserved. This documentation describes the following Axway software: Axway API Gateway 7.5.1 No part
Aruba Central Application Programming Interface
 Aruba Central Application Programming Interface User Guide Copyright Information Copyright 2016 Hewlett Packard Enterprise Development LP. Open Source Code This product includes code licensed under the
Aruba Central Application Programming Interface User Guide Copyright Information Copyright 2016 Hewlett Packard Enterprise Development LP. Open Source Code This product includes code licensed under the
OAuth and OpenID Connect (IN PLAIN ENGLISH)
 OAuth and OpenID Connect (IN PLAIN ENGLISH) NATE BARBETTINI @NBARBETTINI @OKTADEV A lot of confusion around OAuth. Terminology and jargon Incorrect advice Identity use cases (circa 2007) Simple login forms
OAuth and OpenID Connect (IN PLAIN ENGLISH) NATE BARBETTINI @NBARBETTINI @OKTADEV A lot of confusion around OAuth. Terminology and jargon Incorrect advice Identity use cases (circa 2007) Simple login forms
GPII Security. Washington DC, November 2015
 GPII Security Washington DC, November 2015 Outline User data User's device GPII Configuration use cases Preferences access and privacy filtering Work still to do Demo GPII User Data Preferences Device
GPII Security Washington DC, November 2015 Outline User data User's device GPII Configuration use cases Preferences access and privacy filtering Work still to do Demo GPII User Data Preferences Device
INTEGRATION MANUAL DOCUMENTATION E-COMMERCE
 INTEGRATION MANUAL DOCUMENTATION E-COMMERCE LOGIN: In order to use Inkapay's e-commerce payment API you should be registered and verified on Inkapay, otherwise you can do this by entering to www.inkapay.com.
INTEGRATION MANUAL DOCUMENTATION E-COMMERCE LOGIN: In order to use Inkapay's e-commerce payment API you should be registered and verified on Inkapay, otherwise you can do this by entering to www.inkapay.com.
PowerExchange for Facebook: How to Configure Open Authentication using the OAuth Utility
 PowerExchange for Facebook: How to Configure Open Authentication using the OAuth Utility 2013 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
PowerExchange for Facebook: How to Configure Open Authentication using the OAuth Utility 2013 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
What s New in GoAnywhere MFT 5.7
 What s New in GoAnywhere MFT 5.7 Today s Agenda 1. 2. 3. 4. New features and enhancements in GoAnywhere MFT 5.7 Live demo! How to get started Q&A HelpSystems Corporate Overview. All rights reserved. Today
What s New in GoAnywhere MFT 5.7 Today s Agenda 1. 2. 3. 4. New features and enhancements in GoAnywhere MFT 5.7 Live demo! How to get started Q&A HelpSystems Corporate Overview. All rights reserved. Today
OpenID Connect Opens the Door to SAS Viya APIs
 Paper SAS1737-2018 OpenID Connect Opens the Door to SAS Viya APIs Mike Roda, SAS Institute Inc. ABSTRACT As part of the strategy to be open and cloud-ready, SAS Viya services leverage OAuth and OpenID
Paper SAS1737-2018 OpenID Connect Opens the Door to SAS Viya APIs Mike Roda, SAS Institute Inc. ABSTRACT As part of the strategy to be open and cloud-ready, SAS Viya services leverage OAuth and OpenID
Exploring Web Services with SAS
 Paper 1937-2018 Exploring Web Services with SAS Richard Carey, Demarq ABSTRACT Web services are the building blocks of the APIs that drive the modern web. From Amazon Web Services to Philips Hue light
Paper 1937-2018 Exploring Web Services with SAS Richard Carey, Demarq ABSTRACT Web services are the building blocks of the APIs that drive the modern web. From Amazon Web Services to Philips Hue light
Salesforce IoT REST API Getting Started Guide
 Salesforce IoT REST API Getting Started Guide Version 42.0, Spring 18 @salesforcedocs Last updated: March 9, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered
Salesforce IoT REST API Getting Started Guide Version 42.0, Spring 18 @salesforcedocs Last updated: March 9, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered
SAS Viya 3.3 Administration: Authentication
 SAS Viya 3.3 Administration: Authentication Authentication: Overview...................................................................... 1 Authentication: How To........................................................................
SAS Viya 3.3 Administration: Authentication Authentication: Overview...................................................................... 1 Authentication: How To........................................................................
Connect. explained. Vladimir Dzhuvinov. :
 Connect explained Vladimir Dzhuvinov Email: vladimir@dzhuvinov.com : Twitter: @dzhivinov Married for 15 years to Java C Python JavaScript JavaScript on a bad day So what is OpenID Connect? OpenID Connect
Connect explained Vladimir Dzhuvinov Email: vladimir@dzhuvinov.com : Twitter: @dzhivinov Married for 15 years to Java C Python JavaScript JavaScript on a bad day So what is OpenID Connect? OpenID Connect
Oracle Fusion Middleware. API Gateway OAuth User Guide 11g Release 2 ( )
 Oracle Fusion Middleware API Gateway OAuth User Guide 11g Release 2 (11.1.2.2.0) August 2013 Oracle API Gateway OAuth User Guide, 11g Release 2 (11.1.2.2.0) Copyright 1999, 2013, Oracle and/or its affiliates.
Oracle Fusion Middleware API Gateway OAuth User Guide 11g Release 2 (11.1.2.2.0) August 2013 Oracle API Gateway OAuth User Guide, 11g Release 2 (11.1.2.2.0) Copyright 1999, 2013, Oracle and/or its affiliates.
SAS Event Stream Processing 4.2: Security
 SAS Event Stream Processing 4.2: Security Encryption on Sockets Overview to Enabling Encryption You can enable encryption on TCP/IP connections within an event stream processing engine. Specifically, you
SAS Event Stream Processing 4.2: Security Encryption on Sockets Overview to Enabling Encryption You can enable encryption on TCP/IP connections within an event stream processing engine. Specifically, you
Connecting To Twitter & Google+ Using Python
 Connecting To Twitter & Google+ Using Python +Wesley Chun @wescpy corepython.com OSCON, Jul 2012 I Teach (SF, Aug 1-3) 1 I Write (mainly Core Python books) I Code (now @ Google) 2 About You and This Talk
Connecting To Twitter & Google+ Using Python +Wesley Chun @wescpy corepython.com OSCON, Jul 2012 I Teach (SF, Aug 1-3) 1 I Write (mainly Core Python books) I Code (now @ Google) 2 About You and This Talk
Gmail Integration for Salesforce and Dynamics 365
 Gmail Integration for Salesforce and Dynamics 365 PRIVACY POLICY LAST MODIFIED: MARCH 12, 2019 2019 Introduction Welcome to Gmail Integration for Salesforce and Dynamics 365, a service provided by Akvelon,
Gmail Integration for Salesforce and Dynamics 365 PRIVACY POLICY LAST MODIFIED: MARCH 12, 2019 2019 Introduction Welcome to Gmail Integration for Salesforce and Dynamics 365, a service provided by Akvelon,
Authentication in the Cloud. Stefan Seelmann
 Authentication in the Cloud Stefan Seelmann Agenda Use Cases View Points Existing Solutions Upcoming Solutions Use Cases End user needs login to a site or service End user wants to share access to resources
Authentication in the Cloud Stefan Seelmann Agenda Use Cases View Points Existing Solutions Upcoming Solutions Use Cases End user needs login to a site or service End user wants to share access to resources
The production version of your service API must be served over HTTPS.
 This document specifies how to implement an API for your service according to the IFTTT Service Protocol. It is recommended that you treat this document as a reference and follow the workflow outlined
This document specifies how to implement an API for your service according to the IFTTT Service Protocol. It is recommended that you treat this document as a reference and follow the workflow outlined
About 1. Chapter 1: Getting started with odata 2. Remarks 2. Examples 2. Installation or Setup 2. Odata- The Best way to Rest 2
 odata #odata Table of Contents About 1 Chapter 1: Getting started with odata 2 Remarks 2 Examples 2 Installation or Setup 2 Odata- The Best way to Rest 2 Chapter 2: Azure AD authentication for Node.js
odata #odata Table of Contents About 1 Chapter 1: Getting started with odata 2 Remarks 2 Examples 2 Installation or Setup 2 Odata- The Best way to Rest 2 Chapter 2: Azure AD authentication for Node.js
Identity and Data Access: OpenID & OAuth
 Feedback: http://goo.gl/dpubh #io2011 #TechTalk Identity and Data Access: OpenID & OAuth Ryan Boyd @ryguyrg https://profiles.google.com/ryanboyd May 11th 2011 Agenda Feedback: http://goo.gl/dpubh #io2011
Feedback: http://goo.gl/dpubh #io2011 #TechTalk Identity and Data Access: OpenID & OAuth Ryan Boyd @ryguyrg https://profiles.google.com/ryanboyd May 11th 2011 Agenda Feedback: http://goo.gl/dpubh #io2011
ovirt SSO Specification
 ovirt SSO Specification Behavior Changes End user visible changes The password delegation checkbox at user portal login is now a profile setting. Sysadmin visible changes Apache negotiation URL change
ovirt SSO Specification Behavior Changes End user visible changes The password delegation checkbox at user portal login is now a profile setting. Sysadmin visible changes Apache negotiation URL change
Leveraging the Security of AWS's Own APIs for Your App. Brian Wagner Solutions Architect Serverless Web Day June 23, 2016
 Leveraging the Security of AWS's Own APIs for Your App Brian Wagner Solutions Architect Serverless Web Day June 23, 2016 AWS API Requests Access Key and Secret Key (access key and secret key have been
Leveraging the Security of AWS's Own APIs for Your App Brian Wagner Solutions Architect Serverless Web Day June 23, 2016 AWS API Requests Access Key and Secret Key (access key and secret key have been
Cloud object storage : the right way. Orit Wasserman Open Source Summit 2018
 Cloud object storage : the right way Orit Wasserman Open Source Summit 2018 1 About me 20+ years of development 10+ in open source: Nested virtualization for KVM Maintainer of live migration in Qemu/kvm
Cloud object storage : the right way Orit Wasserman Open Source Summit 2018 1 About me 20+ years of development 10+ in open source: Nested virtualization for KVM Maintainer of live migration in Qemu/kvm
User Directories. Overview, Pros and Cons
 User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
SignHero API v2. Protocol Design Principles. API Key Authentication
 SignHero API v2 Protocol Design Principles API Key Authentication Access Token Revocation Create Signature Flow Documents Create Signing Process Retrieve Signature Flow Search Signature Flows Cancel Signature
SignHero API v2 Protocol Design Principles API Key Authentication Access Token Revocation Create Signature Flow Documents Create Signing Process Retrieve Signature Flow Search Signature Flows Cancel Signature
Stateless Microservice Security via JWT, TomEE and MicroProfile
 Stateless Microservice Security via JWT, TomEE and MicroProfile Jean-Louis Monteiro Tomitribe Why am I here today? Microservices architecture case Security opeons OAuth2 with JWT HTTP Signatures Demo with
Stateless Microservice Security via JWT, TomEE and MicroProfile Jean-Louis Monteiro Tomitribe Why am I here today? Microservices architecture case Security opeons OAuth2 with JWT HTTP Signatures Demo with
Connect Your Clouds with Force.com
 Connect Your Clouds with Force.com Developer Track Jeff Douglas, Senior Technical Consultant, Appirio Safe Harbor Safe harbor statement under the Private Securities Litigation Reform Act of 1995: This
Connect Your Clouds with Force.com Developer Track Jeff Douglas, Senior Technical Consultant, Appirio Safe Harbor Safe harbor statement under the Private Securities Litigation Reform Act of 1995: This
Start To Develop THE NEXT LEVEL
 Start To Develop THE NEXT LEVEL 11.10.2017 OVERVIEW I. MARKET & REGISTRATION II. API SUBSCRIPTION III. API TYPES IV. CALLING API S V. SANDBOX VS LIVE VI. TOOLS 10/13/2017 NxtPort The Next Level 2 I. MARKET
Start To Develop THE NEXT LEVEL 11.10.2017 OVERVIEW I. MARKET & REGISTRATION II. API SUBSCRIPTION III. API TYPES IV. CALLING API S V. SANDBOX VS LIVE VI. TOOLS 10/13/2017 NxtPort The Next Level 2 I. MARKET
Azure Archival Installation Guide
 Azure Archival Installation Guide Page 1 of 23 Table of Contents 1. Add Dynamics CRM Active Directory into Azure... 3 2. Add Application in Azure Directory... 5 2.1 Create application for application user...
Azure Archival Installation Guide Page 1 of 23 Table of Contents 1. Add Dynamics CRM Active Directory into Azure... 3 2. Add Application in Azure Directory... 5 2.1 Create application for application user...
Oracle Fusion Middleware. Oracle API Gateway OAuth User Guide 11g Release 2 ( )
 Oracle Fusion Middleware Oracle API Gateway OAuth User Guide 11g Release 2 (11.1.2.3.0) April 2014 Oracle API Gateway OAuth User Guide, 11g Release 2 (11.1.2.3.0) Copyright 1999, 2014, Oracle and/or its
Oracle Fusion Middleware Oracle API Gateway OAuth User Guide 11g Release 2 (11.1.2.3.0) April 2014 Oracle API Gateway OAuth User Guide, 11g Release 2 (11.1.2.3.0) Copyright 1999, 2014, Oracle and/or its
Using Keycloak to Provide Authentication, Authorization, and Identity Management Services for Your Gateway
 Using Keycloak to Provide Authentication, Authorization, and Identity Management Services for Your Gateway Marcus Christie Science Gateways Research Center Indiana University EDS Consultant Award Number
Using Keycloak to Provide Authentication, Authorization, and Identity Management Services for Your Gateway Marcus Christie Science Gateways Research Center Indiana University EDS Consultant Award Number
Volante NACHA ISO20022 Validator AMI User Guide
 Volante NACHA ISO20022 Validator AMI User Guide 1. About Volante NACHA ISO20022 Validator AMI User Guide This document is referenced in the REST Services Deployment Guide. This outlines the available REST
Volante NACHA ISO20022 Validator AMI User Guide 1. About Volante NACHA ISO20022 Validator AMI User Guide This document is referenced in the REST Services Deployment Guide. This outlines the available REST
Box Connector. Version 2.0. User Guide
 Box Connector Version 2.0 User Guide 2016 Ping Identity Corporation. All rights reserved. PingFederate Box Connector User Guide Version 2.0 March, 2016 Ping Identity Corporation 1001 17th Street, Suite
Box Connector Version 2.0 User Guide 2016 Ping Identity Corporation. All rights reserved. PingFederate Box Connector User Guide Version 2.0 March, 2016 Ping Identity Corporation 1001 17th Street, Suite
FAS Authorization Server - OpenID Connect Onboarding
 FAS Authorization Server - OpenID Connect Onboarding Table of Contents Table of Contents 1 List of Figures 2 1 FAS as an authorization server 3 2 OpenID Connect Authorization Code Request and Response
FAS Authorization Server - OpenID Connect Onboarding Table of Contents Table of Contents 1 List of Figures 2 1 FAS as an authorization server 3 2 OpenID Connect Authorization Code Request and Response
Get the Most Out of GoAnywhere: Achieving Cloud File Transfers and Integrations
 Get the Most Out of GoAnywhere: Achieving Cloud File Transfers and Integrations Today s Presenter Dan Freeman, CISSP Senior Solutions Consultant HelpSystems Steve Luebbe Director of Development HelpSystems
Get the Most Out of GoAnywhere: Achieving Cloud File Transfers and Integrations Today s Presenter Dan Freeman, CISSP Senior Solutions Consultant HelpSystems Steve Luebbe Director of Development HelpSystems
FAS Authorization Server - OpenID Connect Onboarding
 FAS Authorization Server - OpenID Connect Onboarding Table of Contents Table of Contents 1 List of Figures 2 1 FAS as an authorization server 3 2 OpenID Connect Authorization Code Request and Response
FAS Authorization Server - OpenID Connect Onboarding Table of Contents Table of Contents 1 List of Figures 2 1 FAS as an authorization server 3 2 OpenID Connect Authorization Code Request and Response
Salesforce Files Connect Implementation Guide
 Salesforce Files Connect Implementation Guide Salesforce, Summer 18 @salesforcedocs Last updated: May 30, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Salesforce Files Connect Implementation Guide Salesforce, Summer 18 @salesforcedocs Last updated: May 30, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Integrate Salesforce. EventTracker v8.x and above
 EventTracker v8.x and above Publication Date: March 27, 2019 Abstract This guide provides instructions to configure Salesforce, to report its logs to EventTracker Enterprise. Scope The configurations detailed
EventTracker v8.x and above Publication Date: March 27, 2019 Abstract This guide provides instructions to configure Salesforce, to report its logs to EventTracker Enterprise. Scope The configurations detailed
E POSTBUSINESS API Login-API Reference. Version 1.1
 E POSTBUSINESS API Login-API Reference Imprint Software and documentation are protected by copyright and may not be copied, reproduced, stored, translated, or otherwise reproduced without the written approval
E POSTBUSINESS API Login-API Reference Imprint Software and documentation are protected by copyright and may not be copied, reproduced, stored, translated, or otherwise reproduced without the written approval
Xerox Connect App for Blackboard
 Xerox Connect App for Blackboard Information Assurance Disclosure Additional information, if needed, on one or more lines Month 00, 0000 2018 Xerox Corporation. All rights reserved. Xerox,
Xerox Connect App for Blackboard Information Assurance Disclosure Additional information, if needed, on one or more lines Month 00, 0000 2018 Xerox Corporation. All rights reserved. Xerox,
ClickToCall SkypeTest Documentation
 ClickToCall SkypeTest Documentation Release 0.0.1 Andrea Mucci August 04, 2015 Contents 1 Requirements 3 2 Installation 5 3 Database Installation 7 4 Usage 9 5 Contents 11 5.1 REST API................................................
ClickToCall SkypeTest Documentation Release 0.0.1 Andrea Mucci August 04, 2015 Contents 1 Requirements 3 2 Installation 5 3 Database Installation 7 4 Usage 9 5 Contents 11 5.1 REST API................................................
fredag 7 september 12 OpenID Connect
 OpenID Connect OpenID Connect Necessity for communication - information about the other part Trust management not solved! (1) OP discovery The user provides an identifier (for instance an email address)
OpenID Connect OpenID Connect Necessity for communication - information about the other part Trust management not solved! (1) OP discovery The user provides an identifier (for instance an email address)
NetIQ Access Manager 4.3. REST API Guide
 NetIQ Access Manager 4.3 REST API Guide Contents 1. Introduction... 3 2. API Overview... 3 3 Administration APIs... 3 3.1 Accessing the Administration APIs... 3 3.2 Detailed API Documentation... 4 3.3
NetIQ Access Manager 4.3 REST API Guide Contents 1. Introduction... 3 2. API Overview... 3 3 Administration APIs... 3 3.1 Accessing the Administration APIs... 3 3.2 Detailed API Documentation... 4 3.3
Info Input Express Network Edition
 Info Input Express Network Edition Administrator s Guide A-61892 Table of Contents Using Info Input Express to Create and Retrieve Documents... 9 Compatibility... 9 Contents of this Guide... 9 Terminology...
Info Input Express Network Edition Administrator s Guide A-61892 Table of Contents Using Info Input Express to Create and Retrieve Documents... 9 Compatibility... 9 Contents of this Guide... 9 Terminology...
Performance Platform Documentation
 Performance Platform Documentation Release 1.0 Performance Platform July 20, 2017 Contents 1 Adding data 3 2 Emptying a data set 5 3 Client implementations 7 4 Glossary 9 5 Get a Performance Platform
Performance Platform Documentation Release 1.0 Performance Platform July 20, 2017 Contents 1 Adding data 3 2 Emptying a data set 5 3 Client implementations 7 4 Glossary 9 5 Get a Performance Platform
Microsoft Graph API Deep Dive
 Microsoft Graph API Deep Dive Donald Hessing Lead Architect, Capgemini, The Netherlands Microsoft Certified Master (MCM) Agenda Introduction to Microsoft Graph API What is now and what is new in GA and
Microsoft Graph API Deep Dive Donald Hessing Lead Architect, Capgemini, The Netherlands Microsoft Certified Master (MCM) Agenda Introduction to Microsoft Graph API What is now and what is new in GA and
Using OpenID/OAuth to access Federated Data Services
 Using OpenID/OAuth to access Federated Data Services M. Benno Blumenthal IRI of Columbia University GO-ESSP 2011 10 May 2011 CMIP3 Pydap server: http://esgcet.llnl.gov/dap/ipcc4/?thredds THREDDS catalog
Using OpenID/OAuth to access Federated Data Services M. Benno Blumenthal IRI of Columbia University GO-ESSP 2011 10 May 2011 CMIP3 Pydap server: http://esgcet.llnl.gov/dap/ipcc4/?thredds THREDDS catalog
NetIQ Access Manager 4.4. REST API Guide
 NetIQ Access Manager 4.4 REST API Guide Contents 1. Introduction... 3 2. API Overview... 3 3 Administration APIs... 3 3.1 Accessing the Administration APIs... 3 3.2 Detailed API Documentation... 4 3.3
NetIQ Access Manager 4.4 REST API Guide Contents 1. Introduction... 3 2. API Overview... 3 3 Administration APIs... 3 3.1 Accessing the Administration APIs... 3 3.2 Detailed API Documentation... 4 3.3
HKWirelessHD API Specification
 HKWirelessHD API Specification Release 1.0 Harman International June 22, 2016 Contents 1 Overview 3 2 Contents 5 2.1 Introduction............................................... 5 2.2 HKWirelessHD Architecture
HKWirelessHD API Specification Release 1.0 Harman International June 22, 2016 Contents 1 Overview 3 2 Contents 5 2.1 Introduction............................................... 5 2.2 HKWirelessHD Architecture
Let SAS Help You Easily Find and Access Your Folders and Files
 Paper 11720-2016 Let SAS Help You Easily Find and Access Your Folders and Files ABSTRACT Ting Sa, Cincinnati Children s Hospital Medical Center In this paper, a SAS macro is introduced that can help users
Paper 11720-2016 Let SAS Help You Easily Find and Access Your Folders and Files ABSTRACT Ting Sa, Cincinnati Children s Hospital Medical Center In this paper, a SAS macro is introduced that can help users
for Salesforce Question-to-Case Connector
 for Salesforce Question-to-Case Connector Contents 2 Contents Cloud Help for Community Managers... 3 What is the Salesforce Question-to-Case Connector... 4 Setting up the Salesforce Question-to-Case Connector...5
for Salesforce Question-to-Case Connector Contents 2 Contents Cloud Help for Community Managers... 3 What is the Salesforce Question-to-Case Connector... 4 Setting up the Salesforce Question-to-Case Connector...5
Enhancing cloud applications by using external authentication services. 2015, 2016 IBM Corporation
 Enhancing cloud applications by using external authentication services After you complete this section, you should understand: Terminology such as authentication, identity, and ID token The benefits of
Enhancing cloud applications by using external authentication services After you complete this section, you should understand: Terminology such as authentication, identity, and ID token The benefits of
OAuth 2.0 Guide. ForgeRock Access Management 5.5. ForgeRock AS 201 Mission St, Suite 2900 San Francisco, CA 94105, USA (US)
 OAuth 2.0 Guide ForgeRock Access Management 5.5 ForgeRock AS 201 Mission St, Suite 2900 San Francisco, CA 94105, USA +1 415-599-1100 (US) www.forgerock.com Copyright 2011-2017 ForgeRock AS. Abstract Guide
OAuth 2.0 Guide ForgeRock Access Management 5.5 ForgeRock AS 201 Mission St, Suite 2900 San Francisco, CA 94105, USA +1 415-599-1100 (US) www.forgerock.com Copyright 2011-2017 ForgeRock AS. Abstract Guide
ArcGIS Enterprise Security: An Introduction. Gregory Ponto & Jeff Smith
 ArcGIS Enterprise Security: An Introduction Gregory Ponto & Jeff Smith Agenda ArcGIS Enterprise Security Model Portal for ArcGIS Authentication Authorization Building the Enterprise Encryption Collaboration
ArcGIS Enterprise Security: An Introduction Gregory Ponto & Jeff Smith Agenda ArcGIS Enterprise Security Model Portal for ArcGIS Authentication Authorization Building the Enterprise Encryption Collaboration
TELIA OPERATOR SERVICE PLATFORM
 TELIA OPERATOR SERVICE PLATFORM OMA Authorization REST API Guide Copyright 2017 Aepona Limited, and copyright 2017 Telia All rights reserved by respective owners. Revision: 6.0 Legal Information Legal
TELIA OPERATOR SERVICE PLATFORM OMA Authorization REST API Guide Copyright 2017 Aepona Limited, and copyright 2017 Telia All rights reserved by respective owners. Revision: 6.0 Legal Information Legal
SAS Viya 3.4 Administration: Authentication
 SAS Viya 3.4 Administration: Authentication Authentication: Overview...................................................................... 2 Authentication Options.......................................................................
SAS Viya 3.4 Administration: Authentication Authentication: Overview...................................................................... 2 Authentication Options.......................................................................
How to set up VMware Unified Access Gateway with OPSWAT MetaAccess Client
 How to set up VMware Unified Access Gateway with OPSWAT MetaAccess Client About This Guide... 2 Part 1: Enforce MetaAccess client installation... 3 Part 2: Enforce device compliance... 5 1 About This Guide
How to set up VMware Unified Access Gateway with OPSWAT MetaAccess Client About This Guide... 2 Part 1: Enforce MetaAccess client installation... 3 Part 2: Enforce device compliance... 5 1 About This Guide
Compute Service: A RESTful Approach to the SAS Programming Environment
 Paper SAS2083-2018 Compute Service: A RESTful Approach to the SAS Programming Environment Jason Spruill and Joseph Henry, SAS Institute Inc., Cary, NC ABSTRACT SAS Viya provides an open architecture that
Paper SAS2083-2018 Compute Service: A RESTful Approach to the SAS Programming Environment Jason Spruill and Joseph Henry, SAS Institute Inc., Cary, NC ABSTRACT SAS Viya provides an open architecture that
API Security Management SENTINET
 API Security Management SENTINET Overview 1 Contents Introduction... 2 Security Models... 2 Authentication... 2 Authorization... 3 Security Mediation and Translation... 5 Bidirectional Security Management...
API Security Management SENTINET Overview 1 Contents Introduction... 2 Security Models... 2 Authentication... 2 Authorization... 3 Security Mediation and Translation... 5 Bidirectional Security Management...
Disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no commitme
 SAAM2291BE Securing Access and Protecting Information in Office 365 with Workspace ONE Camilo Lotero Senior Technical Marketing Manager Adarsh Kesari Senior Systems Engineer #VMworld #SAAM2291BE Disclaimer
SAAM2291BE Securing Access and Protecting Information in Office 365 with Workspace ONE Camilo Lotero Senior Technical Marketing Manager Adarsh Kesari Senior Systems Engineer #VMworld #SAAM2291BE Disclaimer
Building the Modern Research Data Portal using the Globus Platform. Rachana Ananthakrishnan GlobusWorld 2017
 Building the Modern Research Data Portal using the Globus Platform Rachana Ananthakrishnan rachana@globus.org GlobusWorld 2017 Platform Questions How do you leverage Globus services in your own applications?
Building the Modern Research Data Portal using the Globus Platform Rachana Ananthakrishnan rachana@globus.org GlobusWorld 2017 Platform Questions How do you leverage Globus services in your own applications?
IBM Security Access Manager Version 9.0 October Product overview IBM
 IBM Security Access Manager Version 9.0 October 2015 Product overview IBM IBM Security Access Manager Version 9.0 October 2015 Product overview IBM ii IBM Security Access Manager Version 9.0 October 2015:
IBM Security Access Manager Version 9.0 October 2015 Product overview IBM IBM Security Access Manager Version 9.0 October 2015 Product overview IBM ii IBM Security Access Manager Version 9.0 October 2015:
API Security Management with Sentinet SENTINET
 API Security Management with Sentinet SENTINET Overview 1 Contents Introduction... 2 Security Mediation and Translation... 3 Security Models... 3 Authentication... 4 Authorization... 5 Bidirectional Security
API Security Management with Sentinet SENTINET Overview 1 Contents Introduction... 2 Security Mediation and Translation... 3 Security Models... 3 Authentication... 4 Authorization... 5 Bidirectional Security
Inland Revenue. Build Pack. Identity and Access Services. Date: 04/09/2017 Version: 1.5 IN CONFIDENCE
 Inland Revenue Build Pack Identity and Access Services Date: 04/09/2017 Version: 1.5 IN CONFIDENCE About this Document This document is intended to provide Service Providers with the technical detail required
Inland Revenue Build Pack Identity and Access Services Date: 04/09/2017 Version: 1.5 IN CONFIDENCE About this Document This document is intended to provide Service Providers with the technical detail required
RESTful Web Services. 20-Jan Gordon Dickens Chariot Solutions
 RESTful Web Services 20-Jan-2011 Gordon Dickens Chariot Solutions gdickens@chariotsolutions.com Instructor/Mentor at chariotsolutions.com/education Who Am I? Active Tweeter for Open Source Tech Topics
RESTful Web Services 20-Jan-2011 Gordon Dickens Chariot Solutions gdickens@chariotsolutions.com Instructor/Mentor at chariotsolutions.com/education Who Am I? Active Tweeter for Open Source Tech Topics
6/29/ :38 AM 1
 6/29/2017 11:38 AM 1 Creating an Event Hub In this lab, you will create an Event Hub. What you need for this lab An Azure Subscription Create an event hub Take the following steps to create an event hub
6/29/2017 11:38 AM 1 Creating an Event Hub In this lab, you will create an Event Hub. What you need for this lab An Azure Subscription Create an event hub Take the following steps to create an event hub
TACHO ONLINE API. TUNGVOGNSSPECIALISTEN APS Københavnsvej 265, DK-4000 Roskilde
 2018 TACHO ONLINE API TUNGVOGNSSPECIALISTEN APS Københavnsvej 265, DK-4000 Roskilde CONTENT What s new?... 5 Tacho activities... 5 Welcome... 5 More information... 5 Terminology... 5 TVS... 5 Tacho Online...
2018 TACHO ONLINE API TUNGVOGNSSPECIALISTEN APS Københavnsvej 265, DK-4000 Roskilde CONTENT What s new?... 5 Tacho activities... 5 Welcome... 5 More information... 5 Terminology... 5 TVS... 5 Tacho Online...
If the presented credentials are valid server will respond with a success response:
 Telema EDI REST API Telema EDI REST API allows client to send and receive document to and from Telema server. In order to use EDI REST API client must have correct channel configured in Telema system.
Telema EDI REST API Telema EDI REST API allows client to send and receive document to and from Telema server. In order to use EDI REST API client must have correct channel configured in Telema system.
Building the Modern Research Data Portal. Developer Tutorial
 Building the Modern Research Data Portal Developer Tutorial Thank you to our sponsors! U. S. DEPARTMENT OF ENERGY 2 Presentation material available at www.globusworld.org/workshop2016 bit.ly/globus-2016
Building the Modern Research Data Portal Developer Tutorial Thank you to our sponsors! U. S. DEPARTMENT OF ENERGY 2 Presentation material available at www.globusworld.org/workshop2016 bit.ly/globus-2016
Access Manager 4.4 Service Pack 1 Release Notes
 Access Manager 4.4 Service Pack 1 Release Notes March 2018 Access Manager 4.4 Service Pack (4.4.1) includes enhancements, improves usability, and resolves several previous issues. Many of these improvements
Access Manager 4.4 Service Pack 1 Release Notes March 2018 Access Manager 4.4 Service Pack (4.4.1) includes enhancements, improves usability, and resolves several previous issues. Many of these improvements
SAS Event Stream Processing 4.3: Security
 SAS Event Stream Processing 4.3: Security Enabling Encryption on Sockets Overview to Enabling Encryption You can enable encryption on TCP/IP connections within an event stream processing engine. Specifically,
SAS Event Stream Processing 4.3: Security Enabling Encryption on Sockets Overview to Enabling Encryption You can enable encryption on TCP/IP connections within an event stream processing engine. Specifically,
OAuth App Impersonation Attack
 OAuth App Impersonation Attack HOW TO LEAK A 100-MILLION-NODE SOCIAL GRAPH IN JUST ONE WEEK? A REFLECTION ON OAUTH AND API DESIGN IN ONLINE SOCIAL NETWORKS Pili Hu & Prof. Wing Cheong Lau The Chinese University
OAuth App Impersonation Attack HOW TO LEAK A 100-MILLION-NODE SOCIAL GRAPH IN JUST ONE WEEK? A REFLECTION ON OAUTH AND API DESIGN IN ONLINE SOCIAL NETWORKS Pili Hu & Prof. Wing Cheong Lau The Chinese University
The PureEngage Cloud API. Jim Crespino Director, Developer Enablement
 The PureEngage Cloud API Jim Crespino Director, Developer Enablement The PureEngage Cloud API Analogous to the Platform SDK for PureEngage Premise Monolithic (v8.5) -> Microservices (v9.0) Architecture
The PureEngage Cloud API Jim Crespino Director, Developer Enablement The PureEngage Cloud API Analogous to the Platform SDK for PureEngage Premise Monolithic (v8.5) -> Microservices (v9.0) Architecture
EMS Platform Services Installation & Configuration Guides
 EMS Platform Services Installation & Configuration Guides V44.1 Last Updated: August 7, 2018 EMS Software emssoftware.com/help 800.440.3994 2018 EMS Software, LLC. All Rights Reserved. Table of Contents
EMS Platform Services Installation & Configuration Guides V44.1 Last Updated: August 7, 2018 EMS Software emssoftware.com/help 800.440.3994 2018 EMS Software, LLC. All Rights Reserved. Table of Contents
This paper introduces the security policies, practices, and procedures of Lucidchart.
 Lucidchart Security Abstract This paper introduces the security policies, practices, and procedures of Lucidchart. The paper lays out the architecture security of this software-as-a-service product. It
Lucidchart Security Abstract This paper introduces the security policies, practices, and procedures of Lucidchart. The paper lays out the architecture security of this software-as-a-service product. It
Leveraging the Globus Platform in your Web Applications. GlobusWorld April 26, 2018 Greg Nawrocki
 Leveraging the Globus Platform in your Web Applications GlobusWorld April 26, 2018 Greg Nawrocki greg@globus.org Topics and Goals Platform Overview Why expose the APIs A quick touch of the Globus Auth
Leveraging the Globus Platform in your Web Applications GlobusWorld April 26, 2018 Greg Nawrocki greg@globus.org Topics and Goals Platform Overview Why expose the APIs A quick touch of the Globus Auth
Adding Users to Existing Match My Account
 Adding Users to Existing Match My Email Account 1. Cloud Admin for Match My Email logs in at https://matchmyemail.com 2. Navigate to Settings > Domains & Users OR 3. Add Domain with following steps. If
Adding Users to Existing Match My Email Account 1. Cloud Admin for Match My Email logs in at https://matchmyemail.com 2. Navigate to Settings > Domains & Users OR 3. Add Domain with following steps. If
Writing REST APIs with OpenAPI and Swagger Ada
 Writing REST APIs with OpenAPI and Swagger Ada Stéphane Carrez FOSDEM 2018 OpenAPI and Swagger Ada Introduction to OpenAPI and Swagger Writing a REST Ada client Writing a REST Ada server Handling security
Writing REST APIs with OpenAPI and Swagger Ada Stéphane Carrez FOSDEM 2018 OpenAPI and Swagger Ada Introduction to OpenAPI and Swagger Writing a REST Ada client Writing a REST Ada server Handling security
ProfileUnity with FlexApp Technology
 ProfileUnity with FlexApp Technology Using Cloud Storage with ProfileUnity Introduction This guide has been authored by experts at Liquidware in order to provide information and guidance concerning the
ProfileUnity with FlexApp Technology Using Cloud Storage with ProfileUnity Introduction This guide has been authored by experts at Liquidware in order to provide information and guidance concerning the
Generate and download a Doxxy report
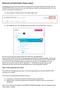 Generate and download a Doxxy report Developing reports and documents within the Doxxy tool is very easy thanks to the intuitive and user friendly APEX interface. At any time you can also review your report
Generate and download a Doxxy report Developing reports and documents within the Doxxy tool is very easy thanks to the intuitive and user friendly APEX interface. At any time you can also review your report
Getting notified by the Microsoft Graph with Webhooks. Elio Struyf U2U MVP September 9th, 2017
 Getting notified by the Microsoft Graph with Webhooks Elio Struyf Trainer @ U2U MVP September 9th, 2017 What are WebHooks? What are WebHooks? Event driven notifications AKA callbacks from the web Universal
Getting notified by the Microsoft Graph with Webhooks Elio Struyf Trainer @ U2U MVP September 9th, 2017 What are WebHooks? What are WebHooks? Event driven notifications AKA callbacks from the web Universal
Symantec Endpoint Protection Manager Quick Integration Guide. for PacketFence version 7.4.0
 Symantec Endpoint Protection Manager Quick Integration Guide for PacketFence version 7.4.0 Symantec Endpoint Protection Manager Quick Integration Guide by Inverse Inc. Version 7.4.0 - Jan 2018 Copyright
Symantec Endpoint Protection Manager Quick Integration Guide for PacketFence version 7.4.0 Symantec Endpoint Protection Manager Quick Integration Guide by Inverse Inc. Version 7.4.0 - Jan 2018 Copyright
What s New in GoAnywhere MFT 5.6?
 What s New in GoAnywhere MFT 5.6? Introductions Bob Luebbe, CISSP Chief Architect Steve Luebbe Director of Engineering Agenda Introduction to GoAnywhere MFT 5.6 Overview of new features Live demo How to
What s New in GoAnywhere MFT 5.6? Introductions Bob Luebbe, CISSP Chief Architect Steve Luebbe Director of Engineering Agenda Introduction to GoAnywhere MFT 5.6 Overview of new features Live demo How to
Black Box DCX3000 / DCX1000 Using the API
 Black Box DCX3000 / DCX1000 Using the API updated 2/22/2017 This document will give you a brief overview of how to access the DCX3000 / DCX1000 API and how you can interact with it using an online tool.
Black Box DCX3000 / DCX1000 Using the API updated 2/22/2017 This document will give you a brief overview of how to access the DCX3000 / DCX1000 API and how you can interact with it using an online tool.
Libelium Cloud Hive. Technical Guide
 Libelium Cloud Hive Technical Guide Index Document version: v7.0-12/2018 Libelium Comunicaciones Distribuidas S.L. INDEX 1. General and information... 4 1.1. Introduction...4 1.1.1. Overview...4 1.2. Data
Libelium Cloud Hive Technical Guide Index Document version: v7.0-12/2018 Libelium Comunicaciones Distribuidas S.L. INDEX 1. General and information... 4 1.1. Introduction...4 1.1.1. Overview...4 1.2. Data
Creating relying party clients using the Nimbus OAuth 2.0 SDK with OpenID Connect extensions
 Creating relying party clients using the Nimbus OAuth 2.0 SDK with OpenID Connect extensions 2013-05-14, Vladimir Dzhuvinov Goals of the SDK Full implementation of the OIDC specs and all related OAuth
Creating relying party clients using the Nimbus OAuth 2.0 SDK with OpenID Connect extensions 2013-05-14, Vladimir Dzhuvinov Goals of the SDK Full implementation of the OIDC specs and all related OAuth
Liferay Security Features Overview. How Liferay Approaches Security
 Liferay Security Features Overview How Liferay Approaches Security Table of Contents Executive Summary.......................................... 1 Transport Security............................................
Liferay Security Features Overview How Liferay Approaches Security Table of Contents Executive Summary.......................................... 1 Transport Security............................................
Spring Social: For the New Web of APIs
 Spring Social: For the New Web of APIs Craig Walls - SpringSource @habuma #springsocial 2011 SpringOne 2GX 2011. All rights reserved. Do not distribute without permission. Agenda Socializing Your Applications
Spring Social: For the New Web of APIs Craig Walls - SpringSource @habuma #springsocial 2011 SpringOne 2GX 2011. All rights reserved. Do not distribute without permission. Agenda Socializing Your Applications
Neos Google Analytics Integration
 Neos Google Analytics Integration Release dev-master The Neos Team Feb 25, 2018 Contents 1 Installation 3 2 Configuration 5 2.1 Statistics display inside Neos.................................... 5 2.2
Neos Google Analytics Integration Release dev-master The Neos Team Feb 25, 2018 Contents 1 Installation 3 2 Configuration 5 2.1 Statistics display inside Neos.................................... 5 2.2
