Six Myths of Windows RT Revealed!
|
|
|
- Ethan Bryant
- 6 years ago
- Views:
Transcription
1 Si Myths of Windows RT Revealed!
2 Si Myths of Windows RT Revealed! There has been a lot of (mis)information being circulated about capabilities of Windows RT, the new Microsoft tablet operating system for tablets. This article should dispel a number of those myths and will highlight the robust capabilities of this new and eciting operating system powering the net generation of Dell Tablets. Myth # 1 Windows RT is not manageable Although Windows RT is not as openly manageable as a Windows 8 Pro or Windows 8 Enterprise enabled PC, IT Administrators will still be able to remotely manage many aspects of a Windows RT device. SCCM and InTune Microsoft System Center Configuration Manager (SCCM) and Microsoft s SaaS product, InTune, are widely adopted systems management solutions. Utilizing Echange Active Sync etensions, Windows RT will have built in hooks so that it is manageable by SCCM and InTune. For eample using Echange Server, SCCM and, InTune, the IT admin is able to configure a set of policies including: Allow Convenience Logon Maimum Failed Password Attempts Maimum Inactivity Time Lock Minimum Device Password Comple Characters Minimum Password Length Password Enabled Password Epiration Password History It also has the ability to query and report back: Drive Encryption Status Auto Update Status Antivirus Status AntiSpyWare Status This is just a start and in the future, there are many opportunities for Microsoft to open up additional management capabilities beyond these critical ones listed. As Windows RT becomes more mature, we epect Microsoft to continue epanding the list. Page 1 of 10
3 Myth #2 Windows RT is not secure Out of the bo, Windows RT is loaded with a number of built in security features that will appeal to a broad set of customers with varying levels of security enforcement policies. Secure Boot Secure Boot effectively locks down Windows RT devices by preventing it from loading (or booting for that matter) non-windows operating systems. This effectively stops users from loading rogue or pirated copies of OS onto Windows RT devices. This maintains the integrity of the operating system so that it can always be trusted. This same system also helps enforce that all applications be digitally signed using a trusted certificate before being installed into the device. It ensures authenticity (knowing where the app came from) and integrity (verifying the app hasn't been tampered with since its publication) of each application on a Windows RT device, preventing unauthorized applications to be installed. Windows Defender Although the Secure Boot system will prevent the majority of unauthorized applications from being installed, the net line of defense will be built-in Windows Defender, protecting the system against spyware and unwanted software. Windows Defender will continuously monitor and help remove malicious and potentially unwanted programs from the device. Full Device Encryption Protecting data on the system is important for a number of reasons, and encrypting the data on the end point is the most widely accepted method of securing private information. Windows RT comes preinstalled with full volume data encryption, which is based on their own Bitlocker technology (although will not be branded Bitlocker by Microsoft). This ensures that any sensitive data on the system will be inaccessible in the event the device is lost or stolen. The recovery key is stored on the users Skydrive account for easy access if needed. Remote Wipe of Company Sensitive Data In the event that a Windows RT device is lost or stolen, the user or IT Administrator with the proper credentials has the ability to remotely wipe EAS managed data (like , contacts, and calendar events) on the device, even though the data is encrypted (just to be safe!). If the applications were installed through the Enterprise Application Store, IT Admins will also be able to disable access to these LoB apps (see Myth #5 below). Multi-Factor Authentication Windows RT supports many forms of secure login, including picture password, typed password, biometric (fingerprint) and smartcards (PIV, GIDS) utilizing firmware TPM (depending on the hardware configuration). Through the InTune management console, IT Page 2 of 10
4 Admins can also force policies such as strong password, password epiration, inactivity time lock, etc. Separate user profiles are also supported which isolates and protects user s data from being accessed by other users logged into the device at the same time. Note: although separate local user profiles are possible, only one Enterprise Application Store credential is supported (i.e. authentication via AD). Firmware Trusted Platform Module (ftpm) Trusted Platform Modules are where devices to securely store cryptographic keys, such as password and login credentials (typed and smartcard based) and encryption keys. Windows RT support a firmware based TPM so that user s passwords and credentials remain secure and protected. Myth #3 Setting up Windows RT to work in an enterprise environment is difficult Windows RT comes with a number of built in, out of the bo tools that allow the device to easily connect the user to their enterprise environment and download LoB applications. So even though Windows RT does not directly support features like Domain Join, it is eceptionally enterprise ready. VPN Virtual Private Networking (VPN) creates a secure, reliable tunnel directly through a company s firewall that allows users to access corporate data and . Windows RT has a built in VPN that is compliant with the majority of advanced VPN systems in the marketplace today: Inbo VPN client included for Microsoft, Cisco, CheckPoint, and Juniper servers VPN protocols supported: L2TP, PPTP, SSTP, Ipsec (IKEv2) Multiple ways of configuration (client UX, scripts, or management infrastructure) Encryption protocols: WEP, WPA, WPA2, WPA-Enterprise, WPA2-Enterprise, 802.1X Certificate based authentication Using the built in management agent, Windows RT allows automatically configuration of VPN profiles for the user, so that Windows RT devices easily connect to a corporate network requiring little user action. Page 3 of 10
5 VDI Support For companies utilizing Virtual Desktop Infrastructure (VDI), Windows RT allows the user to connect directly to their full Windows Desktop and access legacy applications using the built in VDI receiver application. This allows for: Full VDI eperience Rich eperience everywhere (RemoteFX, USB redirection, Multi-touch remoting) Best value for VDI (Fairshare) Efficient management So even though legacy native apps written purely in native WIN32 code cannot eecute directly on Windows RT devices, these apps may still be accessible to the user through a connected VDI session. Plus, all the advantages of VDI such as session mobility, security, IT image management, etc. will be available to the Windows RT user through the built in VDI receiver. Myth #4 It s difficult to install Line of Business (LoB) apps on Windows RT Enterprise customers have many options available to distribute line of business applications to their employees (or students). One way is through the Windows Store or through the Dell Shop (store within a store) application. Although this method is a convenient way to discover and download most popular off the shelf apps, it does requires the user to log on using their personal Microsoft Live ID, which may not be appropriate for companies or school systems that have developed or negotiated separate volume license agreements for their LoB applications. Enterprise Application Store So by using the built in Windows RT Management Agent and Enterprise Application Store, a curated set of company approved LoB apps can be easily discovered, downloaded and installed directly to the device. Microsoft allows the user to browse and discover these types of LoB apps that have been made available to them by the IT admin: Internally-developed WinRT apps that are not published in the Windows Store Apps produced by independent software vendors that are licensed to the organization for internal distribution Web links that launch websites and web-based apps directly in the browser Links to app listings in the Windows Store. This is a convenient way for IT to make users aware of useful business apps that are publicly available. Discovering and downloading LoB applications on Windows RT devices is quite simple. The Windows RT Management Agent and Enterprise Application Store allows the user to simply enter their corporate address and password and the device will automatically present a set of LoB available for the user to download and install. Page 4 of 10
6 This same system also allows the IT Administrator to populate, manage, and audit which applications are available to each user. This is accomplished by simply adding the user s credentials to the Active Directory (AD) service in the SCCM or InTune console. By specifying which AD domain a particular user is a member of, IT Admins can offer different applications to different sets of users. For eample, they can offer epense management, contact management, and sales tracking applications to their road warriors and offer quality control, inventory management, and logistics applications to team members on the factory floor. Page 5 of 10
7 The Windows RT Management Agent also performs daily maintenance tasks updates downloaded applications and checks for new apps available to the user. It will also report back which apps are installed on which machine for inventory and software license audits. The result is a system in which enterprise customers can populate a set of curated LoB applications they want their users to discover, download, and use. Refer to the following blog for more information about managing LoB apps using the Enterprise Application Store. Ref: Managing "BYO" PCs in the enterprise (including WOA) Myth #5 Windows RT is not good for BYOD users The consumerization of IT trend in the marketplace is driving companies to adopt Bring Your Own Device (BYOD) policies. These companies in turn have been trending away from wholly managing devices to more monitoring and maintaining access controls to their applications and services, while leaving the user s personal applications and private data alone. Windows RT is a perfect complement to the Bring Your Own Device (BYOD) trend in the marketplace today, primarily because it has the consumer features end users desire and the enterprise enablers corporate customers require. Its main focus is on security, manageability, productivity, and application access, when and where appropriate to the company or user. If the company or end user (if in a BYOD environment) chooses to disconnect from the control and compliance of the enterprise, the IT Admin simply initiates a disconnection and the device which will: Remove the activation key that allowed the agent to install LoB apps. Once removed, any WinRT apps that were installed via the SSP and management client are deactivated. Remove any certificates that the agent has provisioned. Cease enforcement of the settings policies that the management infrastructure has applied. Report successful deactivation to the management infrastructure if the admin initiated the process. Remove the agent configuration, including the scheduled maintenance task. Once completed, the agent remains dormant unless the user reconnects it to the management infrastructure. This process will not touch the personally loaded applications the user purchased or downloaded through the Marketplace, but will effectively remove all corporate assets off of the employee owned device. Ref: Managing "BYO" PCs in the enterprise (including WOA) Page 6 of 10
8 Myth #6: Windows RT is not like having a full Windows OS The new Windows RT is a purpose built operating system designed specifically to be used on ARM based mobile and tablet devices. Its design intent was to leverage many of the advantages of that Windows 8 brings, but optimized for an ARM based processor. The WinRT Interface (formally known as the Metro UI) The new WinRT interface is the largest technology shift in the PC industry since Microsoft move away from DOS. But most legacy 86 software has a UI designed for keyboard and mouse interaction and therefore, customers would have to redesign the software for optimal finger touch eperience to be used on a tablet. WinRT apps are by default designed specifically for finger touch using the new WinRT interface. This new interface allows developers to design lightweight apps that are optimized to run connected or cloud based apps written in HTML5 instead of heavy C++ native applications. And since Windows RT can ONLY run WinRT apps, any application that is written for a Windows RT device can be easily ported to run on a full Windows 8 PC or in cases, eecute on either with no changes required. VDI As eplained earlier, there is yet another alternative to running 86 software on the tablet itself! When intermittent access to legacy 86 software is required on a tablet, consider VDI AND a Dell keyboard dock that comes with a touchpad. Windows 8 Feature Comparison Below is a line by line comparison of Windows RT versus the other versions of Windows 8. As you can see, Windows RT stacks up pretty well against its brethren: Feature name Windows 8 Windows 8 Pro Windows RT Upgrades from Windows 7 Starter, Home Basic, Home Premium Upgrades from Windows 7 Professional, Ultimate Start screen, Semantic Zoom, Live Tiles Windows Store Apps (Mail, Calendar, People, Messaging, Photos, SkyDrive, Reader, Music, Video) Microsoft Office (Word, Ecel, PowerPoint, OneNote) Internet Eplorer 10 Device encryption Page 7 of 10
9 Connected standby Microsoft account Desktop Installation of 86/64 and desktop software Updated Windows Eplorer Windows Defender SmartScreen Windows Update Enhanced Task Manager Switch languages on the fly (Language Packs) Better multiple monitor support Storage Spaces Windows Media Player Echange ActiveSync File history ISO / VHD mount Mobile broadband features Picture password Play To Remote Desktop (client) Reset and refresh your PC Snap Touch and Thumb keyboard Trusted boot VPN client BitLocker and BitLocker To Go Boot from VHD Client Hyper-V Domain Join Encrypting File System Group Policy Remote Desktop (host) Page 8 of 10
10 Ref: Announcing the Windows 8 Editions Summary In summary, the new Windows RT operating system powering Dell Tablets will allow users to work smarter by allowing easy, secure access to company applications & services while enabling rich content creation & consumption with built in Microsoft Office Suite - even in a BYOD environment. Key security features include built in secure boot, encryption, multi-factor authentication, and the industry acclaimed built in anti-spyware application, Windows Defender. Windows RT is manageable by the widely adopted Microsoft SCCM and for those companies who opt for a full SaaS systems management solution, Microsoft InTune. It is proven to be enterprise ready with out of the bo support for VPN, VDI and a system to discover, download, and install a curated set of Line of Business (LoB) applications. It is easy to use, thanks to the new WinRT touch optimized UI and its built in features compare well to the full version of Windows 8. Page 9 of 10
Windows ierīces Enterprise infrastruktūrā. Aris Dzērvāns Microsoft
 Windows ierīces Enterprise infrastruktūrā Aris Dzērvāns Microsoft Windows 8.1 Update the vision for everyone Designed for the way you live and work Brings together all you do On great devices Always business
Windows ierīces Enterprise infrastruktūrā Aris Dzērvāns Microsoft Windows 8.1 Update the vision for everyone Designed for the way you live and work Brings together all you do On great devices Always business
Phil Schwan Technical
 Phil Schwan Technical Architect pschwan@projectleadership.net @philschwan Today s challenges Users Devices Apps Data Users expect to be able to work in any location and have access to all their work resources.
Phil Schwan Technical Architect pschwan@projectleadership.net @philschwan Today s challenges Users Devices Apps Data Users expect to be able to work in any location and have access to all their work resources.
Windows 8 Deployment Best Practices and Lessons Learned. Martin Weber Technology Solution Professional Microsoft Switzerland GmbH
 Windows 8 Deployment Best Practices and Lessons Learned Martin Weber Technology Solution Professional Microsoft Switzerland GmbH Preparation is key Application Management Create repeatable, automated
Windows 8 Deployment Best Practices and Lessons Learned Martin Weber Technology Solution Professional Microsoft Switzerland GmbH Preparation is key Application Management Create repeatable, automated
Google Identity Services for work
 INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
Microsoft 365 Business FAQs
 Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
905M 67% of the people who use a smartphone for work and 70% of people who use a tablet for work are choosing the devices themselves
 67% of the people who use a smartphone for work and 70% of people who use a tablet for work are choosing the devices themselves 905M tablets in use for work and home globally by 2017 Before Now 32% of
67% of the people who use a smartphone for work and 70% of people who use a tablet for work are choosing the devices themselves 905M tablets in use for work and home globally by 2017 Before Now 32% of
BYOD Success Kit. Table of Contents. Current state of BYOD in enterprise Checklist for BYOD Success Helpful Pilot Tips
 Table of Contents Current state of BYOD in enterprise Checklist for BYOD Success Helpful Pilot Tips 2 Current State of BYOD in the Enterprise Defining BYOD Bring-Your-Own-Device (BYOD): a business practice
Table of Contents Current state of BYOD in enterprise Checklist for BYOD Success Helpful Pilot Tips 2 Current State of BYOD in the Enterprise Defining BYOD Bring-Your-Own-Device (BYOD): a business practice
Windows 10 Management Technologies: What s New. Michael Niehaus Senior Product Marketing Manager, Windows Microsoft
 Windows 10 Management Technologies: What s New Michael Niehaus Senior Product Marketing Manager, Windows Microsoft Business needs are evolving. Windows 10 offers to meet those needs. MANAGEMENT CHOICES
Windows 10 Management Technologies: What s New Michael Niehaus Senior Product Marketing Manager, Windows Microsoft Business needs are evolving. Windows 10 offers to meet those needs. MANAGEMENT CHOICES
MD-101: Modern Desktop Administrator Part 2
 Days: 5 Description: This five-day course is for Desktop Administrators that deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. As desktops has
Days: 5 Description: This five-day course is for Desktop Administrators that deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. As desktops has
Managing and Maintaining Windows 8
 Managing and Maintaining Windows 8 Number: 070-688 Passing Score: 700 Time Limit: 120 min File Version: 1.0 http://www.gratisexam.com/ All questions are taken from demo PDF files at: - Test4Actual - PassFine
Managing and Maintaining Windows 8 Number: 070-688 Passing Score: 700 Time Limit: 120 min File Version: 1.0 http://www.gratisexam.com/ All questions are taken from demo PDF files at: - Test4Actual - PassFine
12/5/2013. work-life blur. more mobile. digital generation. multiple devices. tech. fast savvy
 1 work-life blur more mobile digital generation multiple devices CONSUMERIZATION tech fast savvy VIRTUALIZATION CLOUD paced 2 By Avanade Global Research Study 2013 2 3 Embracing the consumerization of
1 work-life blur more mobile digital generation multiple devices CONSUMERIZATION tech fast savvy VIRTUALIZATION CLOUD paced 2 By Avanade Global Research Study 2013 2 3 Embracing the consumerization of
NotifyMDM Device Application User Guide Installation and Configuration for Android
 NotifyMDM Device Application User Guide Installation and Configuration for Android NotifyMDM for Android, Version 3.x NotifyMDM for Android 1 Table of Contents NotifyMDM for Android 3 Installation Instructions
NotifyMDM Device Application User Guide Installation and Configuration for Android NotifyMDM for Android, Version 3.x NotifyMDM for Android 1 Table of Contents NotifyMDM for Android 3 Installation Instructions
Securing Office 365 with MobileIron
 Securing Office 365 with MobileIron Introduction Office 365 is Microsoft s cloud-based productivity suite. It includes online versions of Microsoft s most popular solutions, like Exchange and SharePoint,
Securing Office 365 with MobileIron Introduction Office 365 is Microsoft s cloud-based productivity suite. It includes online versions of Microsoft s most popular solutions, like Exchange and SharePoint,
WHITE PAPER AIRWATCH SUPPORT FOR OFFICE 365
 WHITE PAPER AIRWATCH SUPPORT FOR OFFICE 365 Airwatch Support for Office 365 One of the most common questions being asked by many customers recently is How does AirWatch support Office 365? Customers often
WHITE PAPER AIRWATCH SUPPORT FOR OFFICE 365 Airwatch Support for Office 365 One of the most common questions being asked by many customers recently is How does AirWatch support Office 365? Customers often
70-697: Configuring Windows Devices Course 7 Managing Apps
 70-697: Configuring Windows Devices Course 7 Managing Apps Slide 1 Installing and Configuring Applications Working with Windows Store Apps Managing Web Browsers Slide 2 Applications are primary tools that
70-697: Configuring Windows Devices Course 7 Managing Apps Slide 1 Installing and Configuring Applications Working with Windows Store Apps Managing Web Browsers Slide 2 Applications are primary tools that
MCSA Windows 10. A Success Guide to Prepare- Microsoft Configuring Windows Devices. edusum.com
 70-697 MCSA Windows 10 A Success Guide to Prepare- Microsoft Configuring Windows Devices edusum.com Table of Contents Introduction to 70-697 Exam on Microsoft Configuring Windows Devices... 2 Microsoft
70-697 MCSA Windows 10 A Success Guide to Prepare- Microsoft Configuring Windows Devices edusum.com Table of Contents Introduction to 70-697 Exam on Microsoft Configuring Windows Devices... 2 Microsoft
Microsoft licensing for the Consumerization of IT
 Volume Licensing brief Microsoft licensing for the Consumerization of IT Table of Contents This brief applies to all Microsoft Volume Licensing programs. Summary... 1 What s New in This Brief... 1 Introduction...
Volume Licensing brief Microsoft licensing for the Consumerization of IT Table of Contents This brief applies to all Microsoft Volume Licensing programs. Summary... 1 What s New in This Brief... 1 Introduction...
Windows in the enterprise
 Windows in the enterprise Enabling flexible workstyles with Windows 8.1 Enterprise Terry Stein Territory Manager anywhere, anytime expectations BYOD goes mainstream enabling mobility critical for success
Windows in the enterprise Enabling flexible workstyles with Windows 8.1 Enterprise Terry Stein Territory Manager anywhere, anytime expectations BYOD goes mainstream enabling mobility critical for success
Managing and Maintaining Windows 8
 70-688 Managing and Maintaining Windows 8 New exam title: Supporting Windows 8.1 The following tables itemize changes to Exam 70-688. These changes will be made in January to include updates that relate
70-688 Managing and Maintaining Windows 8 New exam title: Supporting Windows 8.1 The following tables itemize changes to Exam 70-688. These changes will be made in January to include updates that relate
Microsoft IT deploys Work Folders as an enterprise client data management solution
 Microsoft IT deploys Work Folders as an enterprise client data management solution Published May 2014 The following content may no longer reflect Microsoft s current position or infrastructure. This content
Microsoft IT deploys Work Folders as an enterprise client data management solution Published May 2014 The following content may no longer reflect Microsoft s current position or infrastructure. This content
Exam Name: Microsoft Managing and Maintaining Windows 8
 Vendor: Microsoft Exam Code: 70-688 Exam Name: Microsoft Managing and Maintaining Windows 8 Version: DEMO QUESTION 1 Your company recently purchased 25 new laptops. All 25 laptops have the same hardware
Vendor: Microsoft Exam Code: 70-688 Exam Name: Microsoft Managing and Maintaining Windows 8 Version: DEMO QUESTION 1 Your company recently purchased 25 new laptops. All 25 laptops have the same hardware
Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering. Key Threats Internet was just growing Mail was on the verge
 Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
PCI DSS Compliance. White Paper Parallels Remote Application Server
 PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
PLATFORM CONVERGENCE JOURNEY
 Windows 10 Client PLATFORM CONVERGENCE JOURNEY Converged OS kernel Converged app model Windows 10 DEPLOYMENT CHOICES Wipe-and-Load In-Place Provisioning Traditional process Capture data and settings
Windows 10 Client PLATFORM CONVERGENCE JOURNEY Converged OS kernel Converged app model Windows 10 DEPLOYMENT CHOICES Wipe-and-Load In-Place Provisioning Traditional process Capture data and settings
ipad in Business Security Overview
 ipad in Business Security Overview ipad can securely access corporate services and protect data on the device. It provides strong encryption for data in transmission, proven authentication methods for
ipad in Business Security Overview ipad can securely access corporate services and protect data on the device. It provides strong encryption for data in transmission, proven authentication methods for
VMware Horizon Client for Windows 10 UWP User Guide. Modified on 21 SEP 2017 VMware Horizon Client for Windows 10 UWP 4.6
 VMware Horizon Client for Windows 10 UWP User Guide Modified on 21 SEP 2017 VMware Horizon Client for Windows 10 UWP 4.6 You can find the most up-to-date technical documentation on the VMware website at:
VMware Horizon Client for Windows 10 UWP User Guide Modified on 21 SEP 2017 VMware Horizon Client for Windows 10 UWP 4.6 You can find the most up-to-date technical documentation on the VMware website at:
benefits for customers with subscriptions in CSP
 Windows 10 upgrade benefits for customers with subscriptions in CSP Windows 10 upgrade benefits for customers Resources and guidance for organizations upgrading from Windows 7 and Windows 8/8.1 with subscriptions
Windows 10 upgrade benefits for customers with subscriptions in CSP Windows 10 upgrade benefits for customers Resources and guidance for organizations upgrading from Windows 7 and Windows 8/8.1 with subscriptions
Going Mobile with Windows
 Going Mobile with Windows Enabling Flexible Workstyles Emmanuele Silanesu Windows Commercial Product & Marketing Manager I want a tablet I need a PC Consumption Touch Beautiful Apps Companion Creation
Going Mobile with Windows Enabling Flexible Workstyles Emmanuele Silanesu Windows Commercial Product & Marketing Manager I want a tablet I need a PC Consumption Touch Beautiful Apps Companion Creation
GLOBALPROTECT. Key Usage Scenarios and Benefits. Remote Access VPN Provides secure access to internal and cloud-based business applications
 GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
VMware Enterprise Desktop Solutions. Tommy Walker Enterprise Desktop Specialist Engineer Desktop Platform Solutions
 VMware Enterprise Desktop Solutions Tommy Walker Enterprise Desktop Specialist Engineer Desktop Platform Solutions Agenda The Enterprise Desktop Market Assured Computing Environment (ACE) Virtual Desktop
VMware Enterprise Desktop Solutions Tommy Walker Enterprise Desktop Specialist Engineer Desktop Platform Solutions Agenda The Enterprise Desktop Market Assured Computing Environment (ACE) Virtual Desktop
Deploying VMware Workspace ONE Intelligent Hub. October 2018 VMware Workspace ONE
 Deploying VMware Workspace ONE Intelligent Hub October 2018 VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Workspace ONE Intelligent Hub October 2018 VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Windows 8/RT Features Matrix
 Windows 8/RT Features Matrix The following matrix shows what AirWatch features are available to the Windows 8.0/RT and the Windows 8.1/RT platforms. Feature Windows 8.0/RT Windows 8.1/RT Activation & Enrollment
Windows 8/RT Features Matrix The following matrix shows what AirWatch features are available to the Windows 8.0/RT and the Windows 8.1/RT platforms. Feature Windows 8.0/RT Windows 8.1/RT Activation & Enrollment
Colligo Briefcase. for Good Technology. Administrator Guide
 for Good Technology Administrator Guide Contents Introduction... 2 Target Audience... 2 Overview... 2 Key Features... 2 Platforms Supported... 2 SharePoint Security & Privileges... 3 for Good Technology...
for Good Technology Administrator Guide Contents Introduction... 2 Target Audience... 2 Overview... 2 Key Features... 2 Platforms Supported... 2 SharePoint Security & Privileges... 3 for Good Technology...
CONFIGURING BASIC MACOS MANAGEMENT: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE
 GUIDE FEBRUARY 2019 PRINTED 26 FEBRUARY 2019 CONFIGURING BASIC MACOS MANAGEMENT: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Purpose Audience
GUIDE FEBRUARY 2019 PRINTED 26 FEBRUARY 2019 CONFIGURING BASIC MACOS MANAGEMENT: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Purpose Audience
Mobile Security Overview Rob Greer, VP Endpoint Management and Mobility Product Management Dave Cole, Sr. Director Consumer Mobile Product Management
 Mobile Security Overview Rob Greer, VP Endpoint Management and Mobility Product Management Dave Cole, Sr. Director Consumer Mobile Product Management June 29, 2011 1 Forward-Looking Statements This presentation
Mobile Security Overview Rob Greer, VP Endpoint Management and Mobility Product Management Dave Cole, Sr. Director Consumer Mobile Product Management June 29, 2011 1 Forward-Looking Statements This presentation
Service Description VMware Workspace ONE
 VMware Workspace ONE Last Updated: 05 April 2018 The product described in this Service Description is protected by U.S. and international copyright and intellectual property laws. The product described
VMware Workspace ONE Last Updated: 05 April 2018 The product described in this Service Description is protected by U.S. and international copyright and intellectual property laws. The product described
Augmenting security and management of. Office 365 with Citrix XenMobile
 Office 365 with Citrix XenMobile Augmenting security and management of Office 365 with Citrix XenMobile There are quite a few reasons why Microsoft Office 365 is so popular with enterprise customers. Citrix.com
Office 365 with Citrix XenMobile Augmenting security and management of Office 365 with Citrix XenMobile There are quite a few reasons why Microsoft Office 365 is so popular with enterprise customers. Citrix.com
PMS 138 C Moto Black spine width spine width 100% 100%
 Series MOTOROLA and the Stylized M Logo are registered in the US Patent & Trademark Office. All other product or service names are the property of their respective owners. 2009 Motorola, Inc. Table of
Series MOTOROLA and the Stylized M Logo are registered in the US Patent & Trademark Office. All other product or service names are the property of their respective owners. 2009 Motorola, Inc. Table of
Sophos Mobile Control SaaS startup guide. Product version: 7
 Sophos Mobile Control SaaS startup guide Product version: 7 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your password...8 5 Change your login
Sophos Mobile Control SaaS startup guide Product version: 7 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your password...8 5 Change your login
Accessing CharityMaster data from another location
 Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
Managing Windows 8.1 Devices with XenMobile
 Managing Windows 8.1 Devices with XenMobile Mobile Device Management for Windows 8.1 Devices The Bring Your Own Device Challenge With the advent of the bring your own device (BYOD) trend, employees expect
Managing Windows 8.1 Devices with XenMobile Mobile Device Management for Windows 8.1 Devices The Bring Your Own Device Challenge With the advent of the bring your own device (BYOD) trend, employees expect
Sophos Mobile Control startup guide. Product version: 7
 Sophos Mobile Control startup guide Product version: 7 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 Sophos Mobile Control licenses...7 3.1 Trial licenses...7 3.2 Upgrade trial licenses
Sophos Mobile Control startup guide Product version: 7 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 Sophos Mobile Control licenses...7 3.1 Trial licenses...7 3.2 Upgrade trial licenses
Configuring Windows 10 Devices (697)
 Configuring Windows 10 Devices (697) Manage Identity Support Microsoft Store, Microsoft Store for Education, Microsoft Store for Business, and cloud apps. Install and manage software by using Microsoft
Configuring Windows 10 Devices (697) Manage Identity Support Microsoft Store, Microsoft Store for Education, Microsoft Store for Business, and cloud apps. Install and manage software by using Microsoft
2015 Mobiliya. All Rights Reserved Page 2
 Contents About this Guide... 3 Getting Started... 3 About Mobiliya Shoonya... 3 Key Features... 3 Add-on Features... 4 1. Sign In... 5 2. Admin Dashboard... 6 1. Licenses... 6 2. Users... 7 3. Devices...
Contents About this Guide... 3 Getting Started... 3 About Mobiliya Shoonya... 3 Key Features... 3 Add-on Features... 4 1. Sign In... 5 2. Admin Dashboard... 6 1. Licenses... 6 2. Users... 7 3. Devices...
Directory Integration with Okta. An Architectural Overview. Okta Inc. 301 Brannan Street San Francisco, CA
 Directory Integration with Okta An Architectural Overview Okta Inc. 301 Brannan Street San Francisco, CA 94107 info@okta.com 1-888-722-7871 Contents 1 User Directories and the Cloud: An Overview 3 Okta
Directory Integration with Okta An Architectural Overview Okta Inc. 301 Brannan Street San Francisco, CA 94107 info@okta.com 1-888-722-7871 Contents 1 User Directories and the Cloud: An Overview 3 Okta
Windows 8 and Windows RT
 Volume Licensing guide Windows 8 and Windows RT September 2012 i Table of Contents Introduction... 1 Windows 8 Editions, Windows RT, and Related Products... 2 Windows 8 Editions and Windows RT... 2 Windows
Volume Licensing guide Windows 8 and Windows RT September 2012 i Table of Contents Introduction... 1 Windows 8 Editions, Windows RT, and Related Products... 2 Windows 8 Editions and Windows RT... 2 Windows
Sophos Mobile Control SaaS startup guide. Product version: 6.1
 Sophos Mobile Control SaaS startup guide Product version: 6.1 Document date: September 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your
Sophos Mobile Control SaaS startup guide Product version: 6.1 Document date: September 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your
Paperspace. Deployment Guide. Cloud VDI. 20 Jay St. Suite 312 Brooklyn, NY Technical Whitepaper
 Deployment Guide Cloud VDI Copyright 2017 Paperspace, Co. All Rights Reserved September - 1-2017 Technical Whitepaper Whitepaper: Deployment Guide Paperspace Content 1. Overview... 3 2. User Management...
Deployment Guide Cloud VDI Copyright 2017 Paperspace, Co. All Rights Reserved September - 1-2017 Technical Whitepaper Whitepaper: Deployment Guide Paperspace Content 1. Overview... 3 2. User Management...
Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On- Premises Tools
 Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On- Premises Tools 20398BA - 5 Days - Instructor-led, Hands-on Introduction This five-day course teaches IT professionals
Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On- Premises Tools 20398BA - 5 Days - Instructor-led, Hands-on Introduction This five-day course teaches IT professionals
Google on BeyondCorp: Empowering employees with security for the cloud era
 SESSION ID: EXP-F02 Google on BeyondCorp: Empowering employees with security for the cloud era Jennifer Lin Director, Product Management, Security & Privacy Google Cloud What is BeyondCorp? Enterprise
SESSION ID: EXP-F02 Google on BeyondCorp: Empowering employees with security for the cloud era Jennifer Lin Director, Product Management, Security & Privacy Google Cloud What is BeyondCorp? Enterprise
2013 InterWorks, Page 1
 2013 InterWorks, Page 1 The BYOD Phenomenon 68% of devices used by information workers to access business applications are ones they own themselves, including laptops, smartphones, and tablets. IT organizations
2013 InterWorks, Page 1 The BYOD Phenomenon 68% of devices used by information workers to access business applications are ones they own themselves, including laptops, smartphones, and tablets. IT organizations
Planning for and Managing Devices in the Enterprise: Enterprise Management Suite (EMS) & On-Premises Tools
 Enterprise Management Suite (EMS) & On-Premises Tools Page 1 of 7 Planning for and Managing Devices in the Enterprise: Enterprise Management Suite (EMS) & On-Premises Tools Course 20398A: 4 days; Instructor-Led
Enterprise Management Suite (EMS) & On-Premises Tools Page 1 of 7 Planning for and Managing Devices in the Enterprise: Enterprise Management Suite (EMS) & On-Premises Tools Course 20398A: 4 days; Instructor-Led
Windows 10. Tech Note. Open the Window to Endless Possibilities. Windows for the Enterprise. Universal App Experience
 Windows 10 ENTERPRISE MOBILITY MANAGEMENT Tech Note Open the Window to Endless Possibilities Windows 10 shows a renewed focus on the Enterprise. It successfully harmonizes user experience and device management
Windows 10 ENTERPRISE MOBILITY MANAGEMENT Tech Note Open the Window to Endless Possibilities Windows 10 shows a renewed focus on the Enterprise. It successfully harmonizes user experience and device management
SECURE, CENTRALIZED, SIMPLE
 1 SECURE, CENTRALIZED, SIMPLE Multi-platform Enterprise Mobility Management Whitepaper 2 Controlling it all from one place BlackBerry Enterprise Service 10 (BES10) is an end-to-end, multi-platform, device,
1 SECURE, CENTRALIZED, SIMPLE Multi-platform Enterprise Mobility Management Whitepaper 2 Controlling it all from one place BlackBerry Enterprise Service 10 (BES10) is an end-to-end, multi-platform, device,
preview.windows.com preview.windows.com
 Windows 8 Consumer Preview Product Guide for Business II Table of Contents Innovative user interface 4 Line-of-business app development 4 Start screen 5 Touch-first experience 5 Choice in form factors
Windows 8 Consumer Preview Product Guide for Business II Table of Contents Innovative user interface 4 Line-of-business app development 4 Start screen 5 Touch-first experience 5 Choice in form factors
ForeScout Extended Module for VMware AirWatch MDM
 ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
Securing Today s Mobile Workforce
 WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
Ensuring Desktop Central Compliance to Payment Card Industry (PCI) Data Security Standard
 Ensuring Desktop Central Compliance to Payment Card Industry (PCI) Data Security Standard Introduction Manage Engine Desktop Central is part of ManageEngine family that represents entire IT infrastructure
Ensuring Desktop Central Compliance to Payment Card Industry (PCI) Data Security Standard Introduction Manage Engine Desktop Central is part of ManageEngine family that represents entire IT infrastructure
Six steps to control the uncontrollable
 Six steps to control the uncontrollable Learn how to use Microsoft Enterprise Mobility Suite to protect cloud apps, manage devices, and guard against advanced threats today Introduction Employees today
Six steps to control the uncontrollable Learn how to use Microsoft Enterprise Mobility Suite to protect cloud apps, manage devices, and guard against advanced threats today Introduction Employees today
Using Mobile Computers Lesson 12
 Using Mobile Computers Lesson 12 Objectives Understand wireless security Configure wireless networking Use Windows mobility controls Synchronize data Use BitLocker Drive Encryption Use remote network connections
Using Mobile Computers Lesson 12 Objectives Understand wireless security Configure wireless networking Use Windows mobility controls Synchronize data Use BitLocker Drive Encryption Use remote network connections
Yubico with Centrify for Mac - Deployment Guide
 CENTRIFY DEPLOYMENT GUIDE Yubico with Centrify for Mac - Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component
CENTRIFY DEPLOYMENT GUIDE Yubico with Centrify for Mac - Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component
Office 365: Modern Workplace
 Office 365: Modern Workplace November 8, 2018 Bruce Ward, VP of Business Strategy Helping you grow your business with scalable IT services & solutions for today s challenges & tomorrow s vision. 2018 Peters
Office 365: Modern Workplace November 8, 2018 Bruce Ward, VP of Business Strategy Helping you grow your business with scalable IT services & solutions for today s challenges & tomorrow s vision. 2018 Peters
Microsoft Upgrading Your Skills to MCSA Windows 8
 1800 ULEARN (853 276) www.ddls.com.au Microsoft 20689 - Upgrading Your Skills to MCSA Windows 8 Length 3 days Price $2750.00 (inc GST) Version D Overview This course is designed for experienced IT professionals
1800 ULEARN (853 276) www.ddls.com.au Microsoft 20689 - Upgrading Your Skills to MCSA Windows 8 Length 3 days Price $2750.00 (inc GST) Version D Overview This course is designed for experienced IT professionals
Windows 10 edition. Find out which. is right for you. Core features. Familar, and better than ever Home Pro Enterprise Education Mobile.
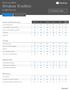 Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
Mobility has changed the way we live and work
 Take a Closer Look at Windows 8.1 PC Retreat 2014 Windows 8 is the best business platform we ve ever shipped. Buying Windows 7, when you could get Windows 8 is just leaving value on the table. Windows
Take a Closer Look at Windows 8.1 PC Retreat 2014 Windows 8 is the best business platform we ve ever shipped. Buying Windows 7, when you could get Windows 8 is just leaving value on the table. Windows
Windows 10 Basics For Windows 7 and 8 users
 Windows 10 Basics For Windows 7 and 8 users Introduction Windows 7/Vista/XP users first need to read Windows 10 Primer, particularly to understand Apps, User Accounts & One Drive. See also the Hints &
Windows 10 Basics For Windows 7 and 8 users Introduction Windows 7/Vista/XP users first need to read Windows 10 Primer, particularly to understand Apps, User Accounts & One Drive. See also the Hints &
EBOOK. Mobile Experience Virtualization: Extend Virtualized Windows Apps to Mobile
 EBOOK Mobile Experience Virtualization: Extend Virtualized Windows Apps to Mobile Table of Contents The Mobilization Dilemma Mobile User Experience Virtualization is not Mobilization Mobile Experience
EBOOK Mobile Experience Virtualization: Extend Virtualized Windows Apps to Mobile Table of Contents The Mobilization Dilemma Mobile User Experience Virtualization is not Mobilization Mobile Experience
WebSphere Puts Business In Motion. Put People In Motion With Mobile Apps
 WebSphere Puts Business In Motion Put People In Motion With Mobile Apps Use Mobile Apps To Create New Revenue Opportunities A clothing store increases sales through personalized offers Customers can scan
WebSphere Puts Business In Motion Put People In Motion With Mobile Apps Use Mobile Apps To Create New Revenue Opportunities A clothing store increases sales through personalized offers Customers can scan
Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On-Premises Tools
 Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On-Premises Tools OD20398B; On-Demand, Video-based Course Description This course teaches IT professionals how to
Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On-Premises Tools OD20398B; On-Demand, Video-based Course Description This course teaches IT professionals how to
Cloud Computing. An introduction using MS Office 365, Google, Amazon, & Dropbox.
 Cloud Computing An introduction using MS Office 365, Google, Amazon, & Dropbox. THIS COURSE Will introduce the benefits and limitations of adopting cloud computing for your business. Will introduce and
Cloud Computing An introduction using MS Office 365, Google, Amazon, & Dropbox. THIS COURSE Will introduce the benefits and limitations of adopting cloud computing for your business. Will introduce and
Mobility Windows 10 Bootcamp
 Mobility Windows 10 Bootcamp Length: 8 days Format: Bootcamp Time: Day About This Course This boot camp is designed to provide students with the knowledge and skills required to install and configure Windows
Mobility Windows 10 Bootcamp Length: 8 days Format: Bootcamp Time: Day About This Course This boot camp is designed to provide students with the knowledge and skills required to install and configure Windows
Use EMS to protect your mobile data and mobile app
 Use EMS to protect your mobile data and mobile app Peter Daalmans Senior Consultant, Enterprise Mobility MVP CTGlobal. pds@ctglobalservices.com PETER DAALMANS Enterprise Mobility MVP @ CTGlobal Blog: https://peterdaalmans.com
Use EMS to protect your mobile data and mobile app Peter Daalmans Senior Consultant, Enterprise Mobility MVP CTGlobal. pds@ctglobalservices.com PETER DAALMANS Enterprise Mobility MVP @ CTGlobal Blog: https://peterdaalmans.com
BYOD: BRING YOUR OWN DEVICE.
 white paper BYOD: BRING YOUR OWN DEVICE. On-BOaRDING and Securing DEVICES IN YOUR Corporate NetWORk PrepaRING YOUR NetWORk to MEEt DEVICE DEMaND The proliferation of smartphones and tablets brings increased
white paper BYOD: BRING YOUR OWN DEVICE. On-BOaRDING and Securing DEVICES IN YOUR Corporate NetWORk PrepaRING YOUR NetWORk to MEEt DEVICE DEMaND The proliferation of smartphones and tablets brings increased
Table of Contents. Installation and Software 1
 Table of Contents Table of Contents Installation and Software Bitlocker not does not give the PIN Protection Facility Do I need the System Reserved Partition when I install Windows? I am Running NetIntelligence
Table of Contents Table of Contents Installation and Software Bitlocker not does not give the PIN Protection Facility Do I need the System Reserved Partition when I install Windows? I am Running NetIntelligence
Fencing the Cloud. Roger Casals. Senior Director Product Management. Shared vision for the Identity: Fencing the Cloud 1
 Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
Android Enterprise Device Management with ZENworks 2017 Update 2
 Android Enterprise Device Management with ZENworks 2017 Update 2 Article IT Operations Management Article Android Enterprise Device Management with ZENworks 2017 Update 2 Introduction With the release
Android Enterprise Device Management with ZENworks 2017 Update 2 Article IT Operations Management Article Android Enterprise Device Management with ZENworks 2017 Update 2 Introduction With the release
Exam Questions
 Exam Questions 70-685 Pro: Windows 7, Enterprise Desktop Support Technician https://www.2passeasy.com/dumps/70-685/ 1.Portable computer users report that they can use Internet Explorer to browse Internet
Exam Questions 70-685 Pro: Windows 7, Enterprise Desktop Support Technician https://www.2passeasy.com/dumps/70-685/ 1.Portable computer users report that they can use Internet Explorer to browse Internet
Comodo IT and Security Manager Software Version 6.9
 Comodo IT and Security Manager Software Version 6.9 End User Guide Guide Version 6.9.072817 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Comodo IT and Security Manager Software Version 6.9 End User Guide Guide Version 6.9.072817 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Managing Devices and Corporate Data on ios
 Managing Devices and Corporate Data on ios Overview Businesses everywhere are empowering their employees with iphone and ipad. Contents Overview Management Basics Separating Work and Personal Data Flexible
Managing Devices and Corporate Data on ios Overview Businesses everywhere are empowering their employees with iphone and ipad. Contents Overview Management Basics Separating Work and Personal Data Flexible
SecureDoc: Making BitLocker simple, smart and secure for you. Your guide to encryption success
 SecureDoc: Making BitLocker simple, smart and secure for you Your guide to encryption success 1 It s time to unlock unbelievable new BitLocker advantages There is an encryption management solution out
SecureDoc: Making BitLocker simple, smart and secure for you Your guide to encryption success 1 It s time to unlock unbelievable new BitLocker advantages There is an encryption management solution out
The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication.
 The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions,
The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions,
Upgrading Your Skills to MCSA Windows 8 by Hikmat Nomat with 111 q
 Upgrading Your Skills to MCSA Windows 8 by Hikmat Nomat with 111 q Number: 70-689 Passing Score: 700 Time Limit: 120 min File Version: 1.2 http://www.gratisexam.com/ Upgrading Your Skills to MCSA Windows
Upgrading Your Skills to MCSA Windows 8 by Hikmat Nomat with 111 q Number: 70-689 Passing Score: 700 Time Limit: 120 min File Version: 1.2 http://www.gratisexam.com/ Upgrading Your Skills to MCSA Windows
1
 Best platform for modern business Affordable and innovative devices Highly mobile and built for agility Broadest range and selection Presented by Dmitri Milov Simple to setup and manage Setup out of the
Best platform for modern business Affordable and innovative devices Highly mobile and built for agility Broadest range and selection Presented by Dmitri Milov Simple to setup and manage Setup out of the
exam.21q Mobility and Devices Fundamentals
 98-368.exam.21q Number: 98-368 Passing Score: 800 Time Limit: 120 min 98-368 Mobility and Devices Fundamentals Exam A QUESTION 1 "Redundant" Microsoft Azure applications are able to meet increased demand
98-368.exam.21q Number: 98-368 Passing Score: 800 Time Limit: 120 min 98-368 Mobility and Devices Fundamentals Exam A QUESTION 1 "Redundant" Microsoft Azure applications are able to meet increased demand
Quo vadis? System Center Configuration Manager Full managed desktop. Mobile device management Light managed device policies, inventory,
 Quo vadis? System Center Configuration Manager Full managed desktop Mobile device management Light managed device policies, inventory, Hybrid management One pane of glass Integration of mobile device management
Quo vadis? System Center Configuration Manager Full managed desktop Mobile device management Light managed device policies, inventory, Hybrid management One pane of glass Integration of mobile device management
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes
 VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes Workspace ONE UEM v9.6 Have documentation feedback? Submit
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes Workspace ONE UEM v9.6 Have documentation feedback? Submit
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting
 Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
NotifyMDM Device Application User Guide Installation and Configuration for ios with TouchDown
 NotifyMDM Device Application User Guide Installation and Configuration for ios with TouchDown NotifyMDM for ios Devices, Version 3.x NotifyMDM for ios with TouchDown 1 Table of Contents NotifyMDM for ios
NotifyMDM Device Application User Guide Installation and Configuration for ios with TouchDown NotifyMDM for ios Devices, Version 3.x NotifyMDM for ios with TouchDown 1 Table of Contents NotifyMDM for ios
Professional Development
 Professional Development HOW TO LEVERAGE MICROSOFT TECHNOLOGIES TO SAVE MONEY AND BE MORE PRODUCTIVE Geoffrey Whidden & Dustin Miller Brockman Coats Gedelian & Co. (800) 686-2727 www.ohiocpa.com How to
Professional Development HOW TO LEVERAGE MICROSOFT TECHNOLOGIES TO SAVE MONEY AND BE MORE PRODUCTIVE Geoffrey Whidden & Dustin Miller Brockman Coats Gedelian & Co. (800) 686-2727 www.ohiocpa.com How to
Table of Contents. Page 1 of 6 (Last updated 27 April 2017)
 Table of Contents What is Connect?... 2 Physical Access Controls... 2 User Access Controls... 3 Systems Architecture... 4 Application Development... 5 Business Continuity Management... 5 Other Operational
Table of Contents What is Connect?... 2 Physical Access Controls... 2 User Access Controls... 3 Systems Architecture... 4 Application Development... 5 Business Continuity Management... 5 Other Operational
Flyer 1. Meet evolving enterprise mobility challenges with Samsung KNOX
 Flyer 1 Meet evolving enterprise mobility challenges with Samsung KNOX Solve today s dynamic enterprise mobility demands with the right solution platform Enterprise Mobility Trends The growth of enterprise
Flyer 1 Meet evolving enterprise mobility challenges with Samsung KNOX Solve today s dynamic enterprise mobility demands with the right solution platform Enterprise Mobility Trends The growth of enterprise
EXAM Upgrading Your Windows XP Skills to MCSA Windows 8.1. Buy Full Product.
 Microsoft EXAM - 70-692 Upgrading Your Windows XP Skills to MCSA Windows 8.1 Buy Full Product http://www.examskey.com/70-692.html Examskey Microsoft 70-692 exam demo product is here for you to test the
Microsoft EXAM - 70-692 Upgrading Your Windows XP Skills to MCSA Windows 8.1 Buy Full Product http://www.examskey.com/70-692.html Examskey Microsoft 70-692 exam demo product is here for you to test the
Comodo IT and Security Manager Software Version 6.4
 Comodo IT and Security Manager Software Version 6.4 End User Guide Guide Version 6.4.040417 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Comodo IT and Security Manager Software Version 6.4 End User Guide Guide Version 6.4.040417 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
VMware AirWatch Symbian Platform Guide Deploying and managing Symbian devices
 VMware AirWatch Symbian Platform Guide Deploying and managing Symbian devices AirWatch v8.1 and higher Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
VMware AirWatch Symbian Platform Guide Deploying and managing Symbian devices AirWatch v8.1 and higher Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
Introducing Windows 8 7
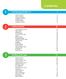 Contents 1 2 3 Contents Introducing Windows 8 7 What is Windows? 8 About Windows 8 9 Windows 8 Interface 10 Navigating Windows 8 12 PC Requirements 16 32-Bit versus 64-Bit 17 Installing Windows 8 18 Getting
Contents 1 2 3 Contents Introducing Windows 8 7 What is Windows? 8 About Windows 8 9 Windows 8 Interface 10 Navigating Windows 8 12 PC Requirements 16 32-Bit versus 64-Bit 17 Installing Windows 8 18 Getting
Comodo IT and Security Manager Software Version 6.6
 Comodo IT and Security Manager Software Version 6.6 End User Guide Guide Version 6.6.053117 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Comodo IT and Security Manager Software Version 6.6 End User Guide Guide Version 6.6.053117 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
hidglobal.com HID ActivOne USER FRIENDLY STRONG AUTHENTICATION
 HID ActivOne USER FRIENDLY STRONG AUTHENTICATION We understand IT security is one of the TOUGHEST business challenges today. HID Global is your trusted partner in the fight against data breach due to misused
HID ActivOne USER FRIENDLY STRONG AUTHENTICATION We understand IT security is one of the TOUGHEST business challenges today. HID Global is your trusted partner in the fight against data breach due to misused
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes
 VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes AirWatch v9.3 Have documentation feedback? Submit a Documentation
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes AirWatch v9.3 Have documentation feedback? Submit a Documentation
Windows 10 Pro device opportunity
 Windows 10 Pro device opportunity I m too limited in what I can do and what I can achieve on Chromebook. Corey Weathers, CEO Homegrown Trailers Work more securely Modern PCs can protect against botnets
Windows 10 Pro device opportunity I m too limited in what I can do and what I can achieve on Chromebook. Corey Weathers, CEO Homegrown Trailers Work more securely Modern PCs can protect against botnets
GSE/Belux Enterprise Systems Security Meeting
 MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
