Introduction. SSH Secure Shell Client 1
|
|
|
- Maurice Rodgers
- 6 years ago
- Views:
Transcription
1 SSH Secure Shell Client 1 Introduction An SSH Secure Shell Client is a piece of software that allows a user to do a number of functions. Some of these functions are: file transferring, setting permissions, accessing various file types, programming, sending , and many more. Furthermore, with this manual, I intend on coveringthe following topics: Accessing a Server Moving Around the Shell Transferring Files Using Text Editing and Creating Programs Setting Permissions Using In order to gain access, you must have an account that has the capabilities for UNIX commands. This is because the shell is command prompt. This means that in order to use the shell, you must have an understanding of a few basic UNIX commands. From there, you can do a number of UNIX based operations. If you have little or no experience with either UNIX, a command prompt environment, or file transferring, that is not a problem. The manual will cover these areas. Once you have an understanding of these areas, you will be able to use other programs that are similar to an SSH Secure Shell Client. This would include a variety of FTP programs or any basic UNIX shell. Throughout this manual, I will go on the assumption that you have a UNIX based account. Furthermore, I will assume that you have already downloaded the SSH Secure Shell Client program. If you do not, it can be downloaded from the SSH Secure Shell Client official site at for a free download.
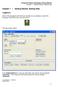
2 2 SSH Secure Shell Client Accessing a Server Using Quick Connect When first opening the SSH Secure Shell Client program, you need a simple way of signing into your account. The Quick Connect option allows for this, opening a window titled Connect to Remote Host: Click the Quick Connect icon, located in the upper left corner, to access this option. You can also access this by clicking the File Menu and then clicking Quick Connect. Entering Host Name Under the Connect to Remote Host window, you need to enter the host name of the server you want to access. Under the Host Name text field, enter in the specified host name for the server. Entering User Name Also under the Connect to Remote Host window, you need to enter your user name that the server can recognize. Under the User Name text field, enter in your user name for the server. Entering Port Number In the Connect to Remote Host window, you need to enter the specific home port number for the server you are trying to access. The program has a default of 22, which is the common port number for most servers. To input a specific port number, modify the Port Number text field.
3 SSH Secure Shell Client 3 Entering Authentication Method You need to specify a certain authentication method to access the server with. Although there are several options for this, it is recommended to choose the Password option. Under the Connect to Remote Host window, click the pull down menu under the Authentication Method label. Once open choose the Password option. This is an example of a correctly filled out Connect to Remote Host window Entering Password Once all of the above fields are filled in, press the Connect button. Once pressed the user will be prompted to enter a password. In the password text field, enter the password associated with your user name. Setting up Profiles A convenient way of storing server information is to establish a profile. This way, you don t have to enter the same server information mentioned above every time you open the SSH Secure Shell Client.
4 4 SSH Secure Shell Client Adding Profiles In order to add a profile, you must logged into the server you would like to add. There are a number of ways to add a profile: To access the add profile option, click the Profiles icon on the toolbar, and then click the Add Profile option. Another way of accessing the Add Profile option, is to go through the File Menu and click the Profiles menu. Under the Profiles menu, click the Add Profile option. Once Add Profile is open, enter desired Profile Name and click Add to Profiles button. Editing a Profile In order to edit a profile, you must already have an existing profile. Editing a profile allows you to make any modifications of Host Name, User Name, Port Number, and Authentication Method. To access the edit profile option, click the Profiles icon on the toolbar, and then click the Edit Profiles option.
5 SSH Secure Shell Client 5 Another way of accessing the Edit Profiles option, is to go through the File Menu and click the Profiles menu. Under the Profiles menu, click the Edit Profiles option. Make any desired changes.
6 6 SSH Secure Shell Client
7 SSH Secure Shell Client 7 Moving Around the Shell Understanding a Command Prompt Environment Sometimes it can be a difficult transition to go from a Windows environment to a UNIX environment. There are certain similarities between the two, however. In Windows, when you are viewing folders through the Explorer Program, these folders represent directories in UNIX. Directories are effectively the same things as folders. Here s a visual depicting this system: When you first log into the server, the server s host will have set the directory you re in. This directory is the current working directory for the user. Using UNIX Commands Here is a list of commonly used UNIX commands and their meanings: cd change directory ls list directory contents cat view contents of a file vi commonly used UNIX text editor chmod Change Permissions on a file cp make a copy of a file rm remove a file(s) mkdir create a directory
8 8 SSH Secure Shell Client Navigating through Directories It is vital to quickly and efficiently navigate through a server s directories. The command to do so is cd, which stands for change directory. There are several different ways of using this. cd [dirname] From your current working directory, this will move to the [dirname] directory. Note that [dirname] should be located in your current working directory. cd / This changes the current directory to the root directory. The root directory is the highest level directory hierarchy. cd.. This moves back to the previous directory you were in. Creating Directories mkdir is the command to make directories. The directory you are currently in will be the location of the directory you make. Here is the syntax for making directories: mkdir [dirname] [dirname] is the name of the directory you want to create Viewing Directory There are a number of ways to view the contents in a directory. The ls command is the most common way to do this, but there are a number of ways to use the ls command. ls (no parameters)
9 SSH Secure Shell Client 9 When this command is typed into the command prompt, the contents of the directory you are currently in will be displayed. It will also display permissions (more on permissions later). ls l This command displays all of the directory s contents, as well as file sizes, modification times, permissions and owners. pwd This doesn t necessarily list the contents of the directory, but it displays the pathname of your current directory starting from the root directory. Creating a File There are a number of ways to create a file. Text editors are used to create, edit, view, and save files. Vi is a very commonly used text editor. To create a file, in the command prompt, type in: vi [filename] The [filename] is whatever you want to name the file The type of file is up to the user. An extension is used to indicate the type of file. The format of the extension is as follows: [filename].[extension] The [extension] is typically a short abbreviation for the file type.
10 10 SSH Secure Shell Client Viewing a File There are several ways to view a file. A text editor allows you to view a file. The file must exist for this to work; otherwise this file will be created. Here s the format for viewing an existing file with vi: vi [filename] Another method of viewing a file is the cat command. This command will essentially um dump the contents of whatever file you want to see. Note that cat can only be used to view files and not to modify files. Here s the format for cat: cat [filename] Running Programs The general format for running a program from the command prompt is as follows: [progname] [param1] [param2] [progname] refers to the particular program you want to run. All of the parameters that follow it are necessary to the particular program. Here are a few examples: vi [filename] In this example the text editor vi is the program and [filename] is the parameter. This effectively states that vi will run the file with the filename. ls l In this example the ls command is considered the program and l is the parameter. This states that you would like to run ls with the condition of displaying more information about the contents of the directory.
11 SSH Secure Shell Client 11 Transferring Files Accessing Transfer Window The purpose of transferring files to/from your remote server is to preserve space on your home computer, and to provide accessibility to your files on any computer that has an SSH Secure Shell Client. There are several ways to open up the Transfer Files window: Along the toolbar, there is a folder icon labeled as New File Transfer Window. This will open up the SSH Secure File Transfer window, where the remote server s working directory will be the user s root directory. See image below: Another way of accessing the Secure File Transfer window, is to open up the Window menu and then choose New File Transfer. Like above, the remote server s working directory will be the user s root directory. It is also possible to open the Secure File Transfer window, such that the remote server s working directory is the current directory your command prompt is in. To access this feature, open the Window menu and choose New File Transfer in Current Directory. Getting accustomed to the Environment The file transfer environment has three distinct areas:
12 12 SSH Secure Shell Client Local Name This area contains the organization of your home computer s full structure. It contains all of the folders and files of your home computer. Remote Name This area contains the organization of the server s directory structure. Note that the current working directory is determined by how you opened up the transfer window (see above). Lastly, the Transfer/Queue area shows the progress of all uploads/downloads currently taking place. Much like in a Windows environment, accessing a folder moves down the directory.
13 SSH Secure Shell Client 13 Creating a New Directory The File Transfer program allows you to create new directories within your home computer (within the Local Name area). To create a new directory, click the new Folder icon along the Local Name toolbar. This will create a new directory within your current directory. Another way to create a new directory is to click the right mouse button and choose the New Folder option. This will also create a new directory within your current directory. Refreshing a Directory Refreshing a directory can be done in the Local Name area, and the Remote Name area. If any file transfers are made, or are currently being done, it is a wise option to refresh the directory to observer the current progress. To refresh either area (Local or Remote), click the Refresh Local icon on the toolbar of either area. Another way to refresh a directory is to click the right mouse button and choose the Refresh option. Deleting a Directory/File Note that this can only be done in the Local Name area (your own computer). Highlight the file/directory you would like to delete. In the toolbar under the Local Name area, click the red x icon. Another way to delete a file/directory is to right click on the particular file/ directory and choose the delete option. Defaulting to Home The SSH Secure File Transfer Window allows you to go back to your default directory for either the Local System or the Remote System. The home for your own computer will be the desktop and the home for the remote server will be your root directly of your account.
14 14 SSH Secure Shell Client In the toolbar for either area, there is a house icon that represents this option. This can also be done by right clicking the mouse button and choosing the Home option. Moving to the Previous Directory This can be done in either the Local or Remote System. It is an efficient way of navigating through directories. In the toolbar for either area, there is a folder with an arrow that represents this option. This can also be done by right clicking the mouse and choosing the Up option. Moving files from Local Name to Remote Name This process is known as uploading a file/directory to the remote server. There are several methods of achieving this. To upload a file/directory, first highlight what you would like to upload. Then click the up icon in the middle of the upper toolbar. This will upload the particular file into the current directory of the remote server. See image below: Another option is to right click on the file/directory you want to upload and choose the upload option. You can also click and drag the particular file/directory you would like to upload. Moving files from Remote Name to Local Name This process is known as downloading a file/directory to the local server. There are several methods of doing this.
15 SSH Secure Shell Client 15 To download a file/directory, highlight what you would like to download within the remote server. Then click the down icon in the middle of the upper toolbar. This will download into your current directory of your Local System. See image below: Another option is to right click on the file/directory you want to download and choose the download option. You can also click and drag the particular file/directory you would like to download. Understanding the File Transfer The Transfer/Queue area contains all the current uploads/downloads between your computer and the remote server. It is important to understand all the tabs in this section: Source File This tab contains the file name you are currently uploading/ downloading. Source Directory This tab contains the directory you are downloading from/ uploading to. Destination Directory This tab contains the directory you are downloading to/uploading from. Size This shows the size of the particular file being downloaded/uploaded. Status This shows the percentage done of the upload/download. Speed This shows the rate at which the upload/download is going at. It s typically measured in kilobytes per second. Time This shows the time remaining in the upload/download.
16 16 SSH Secure Shell Client
17 Using Text Editing and Creating Programs SSH Secure Shell Client 17 Opening Files Opening a file can either be considered creating a new file or opening an existing file. Regardless, the same command is used for both. Note that the text editor vi will be used to open files. This will all be done within the SSH Shell command prompt. Editing Files To open an existing file, the file must already exist. The command for this is as follows: vi [filename] To create a new file, the command is the same thing as above, but the file name used must not exist. Editing files can easily be done through vi. Note that there are two modes in vi: command mode or text mode. Text mode allows you to simply write whatever text you want. Under command mode, you can do such options as copying, pasting, various ways of deleting, various ways of inserting text, and many more similar options. The following commands (used only in command mode) illustrate a brief but effective way of using vi: Pressing the Esc key is the easiest way to get into command mode. a places the cursor ahead of the character you are currently at. Note that this automatically brings you into text mode. i places the cursor before the character you are currently at. Note that this automatically brings you into text mode. x deletes a character. Note that by indicating how many characters you would like to delete, before pressing x, will delete that amount of characters. r replaces the character you are currently at, with the character you type next. dd deletes the current line you are at. Note that by indicating how many lines you would like to delete, before pressing dd, will delete that many lines.
18 18 SSH Secure Shell Client 0 (zero) places the cursor to the start of the current line $ places the cursor to the end of the current line yy copies the current line into the buffer p places the line or lines in the buffer into the text after the current line :w this command acts as saving the file :q exits vi Understanding File Extensions for Programs There are a number of ways to build a program. The programming languages that will be discussed here are C, C++, and Java. The file extension for a C file is [filename].c The file extension for a C++ file is [filename].cpp The file extension for a java file is [filename].java Compiling Programs There are various ways to compile programs. The methods listed here are the most basic way to compile programs: For the C programming language: cc o [program] [filename].c Note that [program] will be the actual program to run For the C++ programming language: c++ o [program] [filename].cpp Note that [program] will be the actual program to run For the Java programming language: javac [filename].java
19 SSH Secure Shell Client 19 Running Programs To run a C program the compiled file, [program], will be the actual program. Follow the section on Running Programs, to see how to run the program. To run a C++ program the compiled file, [program], will be the actual program. Follow the section on Running Programs, to see how to run the program. Running a Java program is a little different. The Java Interpreter is what actually runs the Java program. Here s the syntax to run it: java [filename] Where filename is the compiled Java file.
20 20 SSH Secure Shell Client
21 SSH Secure Shell Client 21 Setting Permissions Understanding the Concept of Setting Permissions The primary purpose of permissions is to allow only certain types of people to have specific access of a file. This is important, for example, if you create a file on a server and only want to let other people read it but not write to it. Defining Permissions There are three types of groups involved in the setting of permissions: Owner The particular file s owner. Group This refers to anyone who belongs to a particular group of a particular file. Public Anybody who is not covered under Owner or Group. There are also three basic types of file permissions: Reading a File Writing to a File Executing a File These two different types of categories (user types and file permissions) essentially define setting permissions. A common way of defining a permission is by using an octal value Read allowed by owner 0200 Write allowed by owner 0100 Owner can execute file 0040 Read allowed by group 0020 Write allowed by group
22 22 SSH Secure Shell Client 0020 Write allowed by group 0010 Group member can execute file 0004 Other types of user can read file 0002 Other types of user can write file 0001 Other types of user can execute file The addition of any of these values produces the full permission setting on a file. For example, the value 0764 means that the owner can read, write, and execute the particular file, the group can read and write to the file and anybody else can just read it. Another example, the value 0273 means that the owner can write to the file, the group can read, write, and execute the file, and anyone else can read and write to it. Viewing Permissions The command ls l views a directory s contents including the file permissions of each file. To the left of each file, there are 10 characters defining the permissions. The first character will be d if that file is a directory; otherwise if it s a - then it s actually a file. The second, third, and fourth characters represent the permissions for the owner. The second character will be r or - representing that the owner can either read the file or can t, respectively. The third character will be w or - representing that the owner can either write to the file or can t, respectively. The fourth character will be x or - representing that the owner can either execute the file or can t, respectively. The fifth, sixth, and seventh characters represent the permissions for the group. They are defined in the same manner as the second, third, and fourth characters except they apply to the group. The eighth, ninth, and tenth characters represent the permissions for anybody else. They are defined in the same manner as the second, third, and fourth characters except they apply to anybody else.
23 SSH Secure Shell Client 23 The following image shows an example directory listing: As an example, the file flyer.pdf, whose permissions are rw-r--r--, states that this file can be read by the owner, the group, and anybody else, can only be written to by the owner and nobody can execute. Setting a Permission to a File The user can alter the permissions of existing files, as long as the user is the owner of the file. The command for setting a permission is: chmod [number] [filename].[extension] [number] is the octal value described above. See the example above on how to set specific permissions.
24 24 SSH Secure Shell Client
25 SSH Secure Shell Client 25 Using Accessing your Account Depending on what comes with your account, you can have the accessibility of e- mail. This would primarily be an issue with the institution or the provider from which you are getting access. For further information on this, consult your school or provider. Within the SSH Secure Shell Client, the primary program for checking e- mail is Pine. To open up Pine, type pine in the command prompt. View image here: Getting to know Pine Pine is a command based program. Instead of clicking icons to do processes, the program has single character shortcuts. The program lists most of these shortcuts on the bottom of the screen. Though each task within Pine may use different commands, the bottom screen serves as a helpful guide. The program also includes other various help within its help menu. Like other services, Pine allows you to do a number of tasks including: Sending Reading Creating folders for Messages Setting up an Address Book Setting up Personal Settings *Note that when Pine shows /\, it is referring to the Ctrl key on the keyboard.
26 26 SSH Secure Shell Client Sending In your main menu, go to the Compose Message option or press the C key on your keyboard. This will bring you to the form for an . To: refers to whom the is being sent. Cc: this refers to any additional addresses to which you would like the letter. This is otherwise known as forwarding. Make sure to separate addresses by commas. Attachmnt: this is any file(s) that will be sent within the . Rather than typing the location by verbatim, you should use the attachment function Pine offers. This can be accessed by choosing the operation Ctrl+J. Subject: the purpose of the . Message Text this will contain the body of the . Within the message text, you can change text styles, formats, and other text editing procedures.
27 SSH Secure Shell Client 27 Once all of the necessary fields are filled out, you are ready to send the . This can be done by choosing Ctrl+X. If there is any other option you would like to choose but do not see it on the bottom of the screen, choose Ctrl+G to get the Help Menu. Reading On the main menu, there is an option called Message Index. Either choose this option or choose I. Then highlight the you would like to read and hit enter. From there you can choose to read, reply to, or forward the . From the menu on the bottom you can do a number of things such as: read the next message, delete, and view attachments along with a number of other options. If there are any options not mentioned on the bottom you would like to get access to, choose?.
28 28 SSH Secure Shell Client Selecting a Mailbox Folder Pine gives you the option to choose one of the following folders directly: INBOX sent-mail saved-messages sent-mail-[last month]-[the year of last month] On the main menu screen, choose the Folder List or press the letter L. This will bring you to a screen which allows you to use the folder of your choice. From here you can do a number of options. If you want to choose a folder, you can highlight the particular folder and hit enter. This can also be done by using the keyboard shortcuts displayed on the bottom of the screen. You can also add ( a ) or delete a folder ( d ). As previously mentioned, if there are any other commands you would like to get access to, you can view the Help Menu (? ). Setting up your Address Book Like other services, Pine gives you the option of setting up an address book. The purpose is to look up someone s account without having to memorize their address and give you options to send s more efficiently and quickly. Also, you can set up a list as well. On the main menu screen, highlight the Address Book option and press enter or press the A key. In this example, I will show you how to enter a person into your address book. In the address book screen, (Shift+2). This will bring you to the Address Book Add screen. Enter in the following information (not all slots need to be filled): Nickname Name of list or a nickname for the person you are adding Fullname Names of person(s) who are being added Fcc I ll get back to you on that. Comment Any additional comments about the person(s) you are entering. Addresses The address of the person you are adding. If you are adding more than one address, separate addresses by commas.
29 SSH Secure Shell Client 29 Once the fields are filled out, press Ctrl +X to save the entry and exit out of the add screen. This will bring you back to the Address Book screen. If you would like to delete any names, highlight the desired name and press D. This command and many others can be found on the bottom of the screen. Setting up Personal Options On the main menu screen, highlight Setup or press S. This displays what you currently have for such helpful shortcuts as Exit Setup, Printer, Newpassword, Config, Signature, and many more. All these shortcuts are displayed on the bottom of the screen as well.
30 30 SSH Secure Shell Client Quitting Pine One shortcut that works continuously throughout each part of Pine is quitting the program. To quit Pine, press Q any time and the program will prompt you whether you want to close it. Press either Y for yes or N for No.
31 SSH Secure Shell Client 31 Glossary A Authentication Method A number of options that allow you to enter your password. These options are Password, Public Key, SecurID, PAM, Keyboard Interactive and <Profile Settings>. C Command Environment Type of computer environment where you operate by typing commands and shortcuts. A mouse is not used in this type of computer environment. D Directory Also known as a folder, contains either files or other directories. It is a helpful way to orgranize the contents of your computer. E (or ) Known as Electronic Mail, is a process of sending letters/messages through the Internet. F File Transfer A process which involves moving contents from your home computer to your remote server. File Extensions A way for the computer to recognize the function of a file. H Host Name The name of the server from which you are getting access from. L Local Name Otherwise known as your Home Computer, contains files and programs on your home machine. N New File Transfer window Begins a new file transfer session within the current server you are working from. P Permissions A way of authorizing access to a file for yourself, groups, and the public.
32 32 SSH Secure Shell Client Pine The primary program used within a UNIX Shell. Port Number Location where a particular server may be located on. The traditional port number for the SSH Secure Shell is 22. Profiles A way to store server information without having to enter it again. Q Quick Connect The primary window to connect to a server. You do have the option to create a default information in this window. R Remote Host window The window that displays information from the current server you are working from. Unless specified, it will open from your root directory. Remote Name The label given to the server under the File Transfer Protocol part of the SSH Secure Shell. Remote Server Otherwise known as the server, contains the directories and files of the server. Root The default starting point on you server. S Secure File Transfer window The window that allows for you to transfer files between you Local and Remote systems. T Transfer/Queue area The area in the file transfer section that displays the progress of the transfer.. The following information is within this area: Source File, Source Directory, Destination Directory, Siz, Status, Speed, and Time. U User Name The name recognized by the server to allow you access. UNIX Programming Language used to operate an SSH Secure Shell Client. V vi One of the many text editor programs found within an SSH Secure Shell Client.
33 SSH Secure Shell Client 33 Index A Authentication Method 3, 4 C Command Environment 1, 7, 9, 10, 11, 17, 25 compiling Programs 18 creating a new Directory 13 D defining Permissions 21 deleting a Directory/File 13 Directories creating 8 viewing 8 E editing Files 17 sending reading 27 address book 28 F file creating 9 viewing 10 File Extensions 18 File Transfer 11, 13, 15 Source File 15 Source Directory 15 Destination Directory 15 Size 15 Status 15 Speed 15 Time 15 H host name 1, 4 N navigating through Directories UNIX environment 8 File Transferring 14 New File Transfer Window 11 O opening Files 17 P Password screen 3 Permission Groups 21 Owner Group Public Pine 25-26, 28; quitting 30 sending 25, 26 reading 25, 27 creating folders for Messages 25, 28 selecting a Mailbox Folder (see creating folders for Messages) setting up an Address Book 25, setting up Personal Settings 25, 29 setting up Personal Options (see setting up Personal Settings) Port Number 1, 4 Profiles adding 4 editing 4-5 Q Quick Connect 2 S Secure File Transfer window 11, 13 setting Permissions 1, 21-23, to a file T Transfer/Queue area 12, 15 Transfer Window 11, 12 Transferring Files 1, 11, 15 U User Name 2, 3, 4 UNIX 1, 7 V vi 7 for text editing 9, 17 to create a file 9 for viewing a file 10 running programs 10 open existing file 17 how to use 17 to exit 18 Viewing Permissions L Local Name 13 moving files from Remote Name 14 M moving to the previous Directory 14 R refreshing a Directory 13 Remote Host window 2, 3 Remote Name 12, 13 moving Files from Local Name 14 Remote Server 11, 13, 14, 15 running Programs 10 programming 19
Using the Zoo Workstations
 Using the Zoo Workstations Version 1.86: January 16, 2014 If you ve used Linux before, you can probably skip many of these instructions, but skim just in case. Please direct corrections and suggestions
Using the Zoo Workstations Version 1.86: January 16, 2014 If you ve used Linux before, you can probably skip many of these instructions, but skim just in case. Please direct corrections and suggestions
Parish . User Manual
 Parish Email User Manual Table of Contents LOGGING IN TO PARISH EMAIL... 3 GETTING STARTED... 3 GENERAL OVERVIEW OF THE USER INTERFACE... 3 TERMINATE THE SESSION... 4 EMAIL... 4 MESSAGES LIST... 4 Open
Parish Email User Manual Table of Contents LOGGING IN TO PARISH EMAIL... 3 GETTING STARTED... 3 GENERAL OVERVIEW OF THE USER INTERFACE... 3 TERMINATE THE SESSION... 4 EMAIL... 4 MESSAGES LIST... 4 Open
Operating Systems. Copyleft 2005, Binnur Kurt
 3 Operating Systems Copyleft 2005, Binnur Kurt Content The concept of an operating system. The internal architecture of an operating system. The architecture of the Linux operating system in more detail.
3 Operating Systems Copyleft 2005, Binnur Kurt Content The concept of an operating system. The internal architecture of an operating system. The architecture of the Linux operating system in more detail.
Operating Systems 3. Operating Systems. Content. What is an Operating System? What is an Operating System? Resource Abstraction and Sharing
 Content 3 Operating Systems The concept of an operating system. The internal architecture of an operating system. The architecture of the Linux operating system in more detail. How to log into (and out
Content 3 Operating Systems The concept of an operating system. The internal architecture of an operating system. The architecture of the Linux operating system in more detail. How to log into (and out
CS Fundamentals of Programming II Fall Very Basic UNIX
 CS 215 - Fundamentals of Programming II Fall 2012 - Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the CS (Project) Lab (KC-265)
CS 215 - Fundamentals of Programming II Fall 2012 - Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the CS (Project) Lab (KC-265)
CS CS Tutorial 2 2 Winter 2018
 CS CS 230 - Tutorial 2 2 Winter 2018 Sections 1. Unix Basics and connecting to CS environment 2. MIPS Introduction & CS230 Interface 3. Connecting Remotely If you haven t set up a CS environment password,
CS CS 230 - Tutorial 2 2 Winter 2018 Sections 1. Unix Basics and connecting to CS environment 2. MIPS Introduction & CS230 Interface 3. Connecting Remotely If you haven t set up a CS environment password,
Introduction to Linux Workshop 1
 Introduction to Linux Workshop 1 The George Washington University SEAS Computing Facility Created by Jason Hurlburt, Hadi Mohammadi, Marco Suarez hurlburj@gwu.edu Logging In The lab computers will authenticate
Introduction to Linux Workshop 1 The George Washington University SEAS Computing Facility Created by Jason Hurlburt, Hadi Mohammadi, Marco Suarez hurlburj@gwu.edu Logging In The lab computers will authenticate
Getting Started With UNIX Lab Exercises
 Getting Started With UNIX Lab Exercises This is the lab exercise handout for the Getting Started with UNIX tutorial. The exercises provide hands-on experience with the topics discussed in the tutorial.
Getting Started With UNIX Lab Exercises This is the lab exercise handout for the Getting Started with UNIX tutorial. The exercises provide hands-on experience with the topics discussed in the tutorial.
Eudora Pro 4.0 for Macintosh
 FACULTY AND STAFF COMPUTER TRAINING @ DE ANZA COLLEGE Eudora Pro 4.0 for Macintosh Visit Our Training Web Site http://training.deanza.fhda.edu Copyright 1998 De Anza College Contents Getting Started 1
FACULTY AND STAFF COMPUTER TRAINING @ DE ANZA COLLEGE Eudora Pro 4.0 for Macintosh Visit Our Training Web Site http://training.deanza.fhda.edu Copyright 1998 De Anza College Contents Getting Started 1
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades Q2
 Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Office 365: . Accessing and Logging In. Mail
 Office 365: Email This class will introduce you to Office 365 and cover the email components found in Outlook on the Web. For more information about the Microsoft Outlook desktop client, register for a
Office 365: Email This class will introduce you to Office 365 and cover the email components found in Outlook on the Web. For more information about the Microsoft Outlook desktop client, register for a
Using LINUX a BCMB/CHEM 8190 Tutorial Updated (1/17/12)
 Using LINUX a BCMB/CHEM 8190 Tutorial Updated (1/17/12) Objective: Learn some basic aspects of the UNIX operating system and how to use it. What is UNIX? UNIX is the operating system used by most computers
Using LINUX a BCMB/CHEM 8190 Tutorial Updated (1/17/12) Objective: Learn some basic aspects of the UNIX operating system and how to use it. What is UNIX? UNIX is the operating system used by most computers
CS 215 Fundamentals of Programming II Spring 2019 Very Basic UNIX
 CS 215 Fundamentals of Programming II Spring 2019 Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the EECS labs that dual boot
CS 215 Fundamentals of Programming II Spring 2019 Very Basic UNIX This handout very briefly describes how to use Unix and how to use the Linux server and client machines in the EECS labs that dual boot
Microsoft SkyDrive Tutorial
 & Microsoft Live@edu SkyDrive Tutorial TABLE OF CONTENTS Introduction... 2 Logging In... 3 Logging In Through Your Faculty Portal... 7 Adding Documents to Your SkyDrive... 13 Create a Folder... 13 Share
& Microsoft Live@edu SkyDrive Tutorial TABLE OF CONTENTS Introduction... 2 Logging In... 3 Logging In Through Your Faculty Portal... 7 Adding Documents to Your SkyDrive... 13 Create a Folder... 13 Share
Session 1: Accessing MUGrid and Command Line Basics
 Session 1: Accessing MUGrid and Command Line Basics Craig A. Struble, Ph.D. July 14, 2010 1 Introduction The Marquette University Grid (MUGrid) is a collection of dedicated and opportunistic resources
Session 1: Accessing MUGrid and Command Line Basics Craig A. Struble, Ph.D. July 14, 2010 1 Introduction The Marquette University Grid (MUGrid) is a collection of dedicated and opportunistic resources
Introduction to UNIX. Logging in. Basic System Architecture 10/7/10. most systems have graphical login on Linux machines
 Introduction to UNIX Logging in Basic system architecture Getting help Intro to shell (tcsh) Basic UNIX File Maintenance Intro to emacs I/O Redirection Shell scripts Logging in most systems have graphical
Introduction to UNIX Logging in Basic system architecture Getting help Intro to shell (tcsh) Basic UNIX File Maintenance Intro to emacs I/O Redirection Shell scripts Logging in most systems have graphical
commandname flags arguments
 Unix Review, additional Unix commands CS101, Mock Introduction This handout/lecture reviews some basic UNIX commands that you should know how to use. A more detailed description of this and other commands
Unix Review, additional Unix commands CS101, Mock Introduction This handout/lecture reviews some basic UNIX commands that you should know how to use. A more detailed description of this and other commands
Introduction to the UNIX command line
 Introduction to the UNIX command line Steven Abreu Introduction to Computer Science (ICS) Tutorial Jacobs University s.abreu@jacobs-university.de September 19, 2017 Overview What is UNIX? UNIX Shell Commands
Introduction to the UNIX command line Steven Abreu Introduction to Computer Science (ICS) Tutorial Jacobs University s.abreu@jacobs-university.de September 19, 2017 Overview What is UNIX? UNIX Shell Commands
Contents. Note: pay attention to where you are. Note: Plaintext version. Note: pay attention to where you are... 1 Note: Plaintext version...
 Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Tutorial 1: Unix Basics
 Tutorial 1: Unix Basics To log in to your ece account, enter your ece username and password in the space provided in the login screen. Note that when you type your password, nothing will show up in the
Tutorial 1: Unix Basics To log in to your ece account, enter your ece username and password in the space provided in the login screen. Note that when you type your password, nothing will show up in the
Linux/Cygwin Practice Computer Architecture
 Linux/Cygwin Practice 2010 Computer Architecture Linux Login Use ssh client applications to connect (Port : 22) SSH Clients zterm ( http://www.brainz.co.kr/products/products4_2.php ) Putty ( http://kldp.net/frs/download.php/3411/hangulputty-0.58.h2.exe
Linux/Cygwin Practice 2010 Computer Architecture Linux Login Use ssh client applications to connect (Port : 22) SSH Clients zterm ( http://www.brainz.co.kr/products/products4_2.php ) Putty ( http://kldp.net/frs/download.php/3411/hangulputty-0.58.h2.exe
A Brief Introduction to the Linux Shell for Data Science
 A Brief Introduction to the Linux Shell for Data Science Aris Anagnostopoulos 1 Introduction Here we will see a brief introduction of the Linux command line or shell as it is called. Linux is a Unix-like
A Brief Introduction to the Linux Shell for Data Science Aris Anagnostopoulos 1 Introduction Here we will see a brief introduction of the Linux command line or shell as it is called. Linux is a Unix-like
Unix Introduction to UNIX
 Unix Introduction to UNIX Get Started Introduction The UNIX operating system Set of programs that act as a link between the computer and the user. Developed in 1969 by a group of AT&T employees Various
Unix Introduction to UNIX Get Started Introduction The UNIX operating system Set of programs that act as a link between the computer and the user. Developed in 1969 by a group of AT&T employees Various
CHE3935. Lecture 1. Introduction to Linux
 CHE3935 Lecture 1 Introduction to Linux 1 Logging In PuTTY is a free telnet/ssh client that can be run without installing it within Windows. It will only give you a terminal interface, but used with a
CHE3935 Lecture 1 Introduction to Linux 1 Logging In PuTTY is a free telnet/ssh client that can be run without installing it within Windows. It will only give you a terminal interface, but used with a
Intro to Linux. this will open up a new terminal window for you is super convenient on the computers in the lab
 Basic Terminal Intro to Linux ssh short for s ecure sh ell usage: ssh [host]@[computer].[otheripstuff] for lab computers: ssh [CSID]@[comp].cs.utexas.edu can get a list of active computers from the UTCS
Basic Terminal Intro to Linux ssh short for s ecure sh ell usage: ssh [host]@[computer].[otheripstuff] for lab computers: ssh [CSID]@[comp].cs.utexas.edu can get a list of active computers from the UTCS
Windows 8.1 User Guide for ANU Staff
 Windows 8.1 User Guide for ANU Staff This guide has been created to assist with basic tasks and navigating Windows 8.1. Further tips for using Windows 8.1 can be found on the IT Services website, or by
Windows 8.1 User Guide for ANU Staff This guide has been created to assist with basic tasks and navigating Windows 8.1. Further tips for using Windows 8.1 can be found on the IT Services website, or by
FILE MAINTENANCE COMMANDS
 Birla Institute of Technology & Science, Pilani Computer Programming (CS F111) Lab-2 ----------------------------------------------------------------------------------------------------------------------
Birla Institute of Technology & Science, Pilani Computer Programming (CS F111) Lab-2 ----------------------------------------------------------------------------------------------------------------------
Lab Working with Linux Command Line
 Introduction In this lab, you will use the Linux command line to manage files and folders and perform some basic administrative tasks. Recommended Equipment A computer with a Linux OS, either installed
Introduction In this lab, you will use the Linux command line to manage files and folders and perform some basic administrative tasks. Recommended Equipment A computer with a Linux OS, either installed
CENG 334 Computer Networks. Laboratory I Linux Tutorial
 CENG 334 Computer Networks Laboratory I Linux Tutorial Contents 1. Logging In and Starting Session 2. Using Commands 1. Basic Commands 2. Working With Files and Directories 3. Permission Bits 3. Introduction
CENG 334 Computer Networks Laboratory I Linux Tutorial Contents 1. Logging In and Starting Session 2. Using Commands 1. Basic Commands 2. Working With Files and Directories 3. Permission Bits 3. Introduction
Getting Started with Pine
 UNIX013 January 2002 Getting Started with Pine Introduction... 1 Starting Pine... 1 List of Messages... 2 Reading Messages... 3 Replying to Sender... 4 Composing a Message... 5 Deleting a Message... 7
UNIX013 January 2002 Getting Started with Pine Introduction... 1 Starting Pine... 1 List of Messages... 2 Reading Messages... 3 Replying to Sender... 4 Composing a Message... 5 Deleting a Message... 7
Basic Survival UNIX.
 Basic Survival UNIX Many Unix based operating systems make available a Graphical User Interface for the sake of providing an easy way for less experienced users to work with the system. Some examples are
Basic Survival UNIX Many Unix based operating systems make available a Graphical User Interface for the sake of providing an easy way for less experienced users to work with the system. Some examples are
Getting Started with UNIX
 Getting Started with UNIX What is UNIX? Boston University Information Services & Technology Course Number: 4000 Course Instructor: Kenny Burns Operating System Interface between a user and the computer
Getting Started with UNIX What is UNIX? Boston University Information Services & Technology Course Number: 4000 Course Instructor: Kenny Burns Operating System Interface between a user and the computer
Introduction to Unix and Linux. Workshop 1: Directories and Files
 Introduction to Unix and Linux Workshop 1: Directories and Files Genomics Core Lab TEXAS A&M UNIVERSITY CORPUS CHRISTI Anvesh Paidipala, Evan Krell, Kelly Pennoyer, Chris Bird Genomics Core Lab Informatics
Introduction to Unix and Linux Workshop 1: Directories and Files Genomics Core Lab TEXAS A&M UNIVERSITY CORPUS CHRISTI Anvesh Paidipala, Evan Krell, Kelly Pennoyer, Chris Bird Genomics Core Lab Informatics
OUTLOOK HOW DO I? 2013
 OUTLOOK HOW DO I? Click on a Link to take you to that Section OUTLOOK - GENERAL... 2 GENERAL How Do I Navigate the 2010 Outlook Screen?... 2 GENERAL: How Do I Change the Reading Pane View?... 7 GENERAL:
OUTLOOK HOW DO I? Click on a Link to take you to that Section OUTLOOK - GENERAL... 2 GENERAL How Do I Navigate the 2010 Outlook Screen?... 2 GENERAL: How Do I Change the Reading Pane View?... 7 GENERAL:
Exploring UNIX: Session 3
 Exploring UNIX: Session 3 UNIX file system permissions UNIX is a multi user operating system. This means several users can be logged in simultaneously. For obvious reasons UNIX makes sure users cannot
Exploring UNIX: Session 3 UNIX file system permissions UNIX is a multi user operating system. This means several users can be logged in simultaneously. For obvious reasons UNIX makes sure users cannot
Version Operator Orientation. TIMMS Client. A guide to using the TIMMS System. Training & Navigation Notes
 Version 7.2.4 Operator Orientation TIMMS Client A guide to using the TIMMS System Training & Navigation Notes Disprax Pty Ltd 2015 WHAT IS TIMMS? TIMMS Stands for: Total Industry Management and Marketing
Version 7.2.4 Operator Orientation TIMMS Client A guide to using the TIMMS System Training & Navigation Notes Disprax Pty Ltd 2015 WHAT IS TIMMS? TIMMS Stands for: Total Industry Management and Marketing
Using Your New Webmail
 Using Your New Webmail Table of Contents Composing a New Message... 2 Adding Attachments to a Message... 4 Inserting a Hyperlink... 6 Searching For Messages... 8 Downloading Email from a POP3 Account...
Using Your New Webmail Table of Contents Composing a New Message... 2 Adding Attachments to a Message... 4 Inserting a Hyperlink... 6 Searching For Messages... 8 Downloading Email from a POP3 Account...
: the User (owner) for this file (your cruzid, when you do it) Position: directory flag. read Group.
 CMPS 12L Introduction to Programming Lab Assignment 2 We have three goals in this assignment: to learn about file permissions in Unix, to get a basic introduction to the Andrew File System and it s directory
CMPS 12L Introduction to Programming Lab Assignment 2 We have three goals in this assignment: to learn about file permissions in Unix, to get a basic introduction to the Andrew File System and it s directory
Refresher workshop in programming for polytechnic graduates General Java Program Compilation Guide
 Refresher workshop in programming for polytechnic graduates General Java Program Compilation Guide Overview Welcome to this refresher workshop! This document will serve as a self-guided explanation to
Refresher workshop in programming for polytechnic graduates General Java Program Compilation Guide Overview Welcome to this refresher workshop! This document will serve as a self-guided explanation to
Note: In this guide, wherever you see an underlined letter as part of a command word (ex. File), that refers to the keyboard shortcut
 E-Mail Guide Using Microsoft Exchange New User Checklist If you are a new user to Microsoft Exchange, you should take the following steps to insure that your account remains secure, organized, and personalized:
E-Mail Guide Using Microsoft Exchange New User Checklist If you are a new user to Microsoft Exchange, you should take the following steps to insure that your account remains secure, organized, and personalized:
Outlook - an Introduction to Version 2003 Table of Contents
 Outlook - an Introduction to E-mail Version 2003 Table of Contents What is Outlook Starting Outlook The Navigation Pane Getting Help Creating and Sending a Message Using the College Exchange Directory
Outlook - an Introduction to E-mail Version 2003 Table of Contents What is Outlook Starting Outlook The Navigation Pane Getting Help Creating and Sending a Message Using the College Exchange Directory
Microsoft Office Outlook 2010
 Starting Microsoft Outlook 2010 with XP Click on Start, E-mail Microsoft Outlook or Start, All Programs, Microsoft Office, Microsoft Outlook. Starting Microsoft Outlook 2010 with Windows 7 Click on the
Starting Microsoft Outlook 2010 with XP Click on Start, E-mail Microsoft Outlook or Start, All Programs, Microsoft Office, Microsoft Outlook. Starting Microsoft Outlook 2010 with Windows 7 Click on the
Week 2 Lecture 3. Unix
 Lecture 3 Unix Terminal and Shell 2 Terminal Prompt Command Argument Result 3 Shell Intro A system program that allows a user to execute: shell functions (e.g., ls -la) other programs (e.g., eclipse) shell
Lecture 3 Unix Terminal and Shell 2 Terminal Prompt Command Argument Result 3 Shell Intro A system program that allows a user to execute: shell functions (e.g., ls -la) other programs (e.g., eclipse) shell
TABLE OF CONTENTS CHAPTER
 TABLE OF CONTENTS CHAPTER 1...1 A QUICK OVERVIEW OF THE MICROSOFT EXCHANGE CLIENT...1 BASIC CONCEPTS AND FEATURES...1 STARTING THE MICROSOFT EXCHANGE CLIENT...1 SETTING OPTIONS FOR YOUR MESSAGES...3 LOOKING
TABLE OF CONTENTS CHAPTER 1...1 A QUICK OVERVIEW OF THE MICROSOFT EXCHANGE CLIENT...1 BASIC CONCEPTS AND FEATURES...1 STARTING THE MICROSOFT EXCHANGE CLIENT...1 SETTING OPTIONS FOR YOUR MESSAGES...3 LOOKING
Introduction to Unix - Lab Exercise 0
 Introduction to Unix - Lab Exercise 0 Along with this document you should also receive a printout entitled First Year Survival Guide which is a (very) basic introduction to Unix and your life in the CSE
Introduction to Unix - Lab Exercise 0 Along with this document you should also receive a printout entitled First Year Survival Guide which is a (very) basic introduction to Unix and your life in the CSE
Helpful Tips for Labs. CS140, Spring 2015
 Helpful Tips for Labs CS140, Spring 2015 Linux/Unix Commands Creating, Entering, Changing Directories to Create a Directory (a Folder) on the command line type mkdir folder_name to Enter that Folder cd
Helpful Tips for Labs CS140, Spring 2015 Linux/Unix Commands Creating, Entering, Changing Directories to Create a Directory (a Folder) on the command line type mkdir folder_name to Enter that Folder cd
CpSc 1111 Lab 1 Introduction to Unix Systems, Editors, and C
 CpSc 1111 Lab 1 Introduction to Unix Systems, Editors, and C Welcome! Welcome to your CpSc 111 lab! For each lab this semester, you will be provided a document like this to guide you. This material, as
CpSc 1111 Lab 1 Introduction to Unix Systems, Editors, and C Welcome! Welcome to your CpSc 111 lab! For each lab this semester, you will be provided a document like this to guide you. This material, as
Windows 8.1 User Guide for ANU Staff
 Windows 8.1 User Guide for ANU Staff This guide has been created to assist with basic tasks and navigating Windows 8.1. Further tips for using Windows 8.1 can be found on the IT Services website, or by
Windows 8.1 User Guide for ANU Staff This guide has been created to assist with basic tasks and navigating Windows 8.1. Further tips for using Windows 8.1 can be found on the IT Services website, or by
Introduction to Linux
 Introduction to Linux The command-line interface A command-line interface (CLI) is a type of interface, that is, a way to interact with a computer. Window systems, punched cards or a bunch of dials, buttons
Introduction to Linux The command-line interface A command-line interface (CLI) is a type of interface, that is, a way to interact with a computer. Window systems, punched cards or a bunch of dials, buttons
Part I. Introduction to Linux
 Part I Introduction to Linux 7 Chapter 1 Linux operating system Goal-of-the-Day Familiarisation with basic Linux commands and creation of data plots. 1.1 What is Linux? All astronomical data processing
Part I Introduction to Linux 7 Chapter 1 Linux operating system Goal-of-the-Day Familiarisation with basic Linux commands and creation of data plots. 1.1 What is Linux? All astronomical data processing
Unix/Linux Primer. Taras V. Pogorelov and Mike Hallock School of Chemical Sciences, University of Illinois
 Unix/Linux Primer Taras V. Pogorelov and Mike Hallock School of Chemical Sciences, University of Illinois August 25, 2017 This primer is designed to introduce basic UNIX/Linux concepts and commands. No
Unix/Linux Primer Taras V. Pogorelov and Mike Hallock School of Chemical Sciences, University of Illinois August 25, 2017 This primer is designed to introduce basic UNIX/Linux concepts and commands. No
User Guide Version 2.0
 User Guide Version 2.0 Page 2 of 8 Summary Contents 1 INTRODUCTION... 3 2 SECURESHELL (SSH)... 4 2.1 ENABLING SSH... 4 2.2 DISABLING SSH... 4 2.2.1 Change Password... 4 2.2.2 Secure Shell Connection Information...
User Guide Version 2.0 Page 2 of 8 Summary Contents 1 INTRODUCTION... 3 2 SECURESHELL (SSH)... 4 2.1 ENABLING SSH... 4 2.2 DISABLING SSH... 4 2.2.1 Change Password... 4 2.2.2 Secure Shell Connection Information...
Introduction p. 1 Who Should Read This Book? p. 1 What You Need to Know Before Reading This Book p. 2 How This Book Is Organized p.
 Introduction p. 1 Who Should Read This Book? p. 1 What You Need to Know Before Reading This Book p. 2 How This Book Is Organized p. 2 Conventions Used in This Book p. 2 Introduction to UNIX p. 5 An Overview
Introduction p. 1 Who Should Read This Book? p. 1 What You Need to Know Before Reading This Book p. 2 How This Book Is Organized p. 2 Conventions Used in This Book p. 2 Introduction to UNIX p. 5 An Overview
FaxFinder Fax Servers
 FaxFinder Fax Servers Models: FF130 FF230 FF430 FF830 Client User Guide FaxFinder Client User Guide Fax Client Software for FaxFinder Series PN S000460B, Version B Copyright This publication may not be
FaxFinder Fax Servers Models: FF130 FF230 FF430 FF830 Client User Guide FaxFinder Client User Guide Fax Client Software for FaxFinder Series PN S000460B, Version B Copyright This publication may not be
Unix File System. Learning command-line navigation of the file system is essential for efficient system usage
 ULI101 Week 02 Week Overview Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages Text editing Common file utilities: cat,more,less,touch,file,find
ULI101 Week 02 Week Overview Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages Text editing Common file utilities: cat,more,less,touch,file,find
CSCI 161: Introduction to Programming I Lab 1a: Programming Environment: Linux and Eclipse
 CSCI 161: Introduction to Programming I Lab 1a: Programming Environment: Linux and Eclipse Goals - to become acquainted with the Linux/Gnome environment Overview For this lab, you will login to a workstation
CSCI 161: Introduction to Programming I Lab 1a: Programming Environment: Linux and Eclipse Goals - to become acquainted with the Linux/Gnome environment Overview For this lab, you will login to a workstation
Outlook Skills Tutor. Open Outlook
 Outlook Skills Tutor Lakewood School District Open Outlook Working with the Inbox Receiving new email Sorting your Inbox Reading email Using the Reading Pane Sending, replying to, and forwarding messages
Outlook Skills Tutor Lakewood School District Open Outlook Working with the Inbox Receiving new email Sorting your Inbox Reading email Using the Reading Pane Sending, replying to, and forwarding messages
Outlook Desktop Application for Windows
 Access Your Email There are two common ways to access your mail: via the Outlook Desktop Application and the Outlook Web Application. This document focuses on how to use the Outlook Desktop Application
Access Your Email There are two common ways to access your mail: via the Outlook Desktop Application and the Outlook Web Application. This document focuses on how to use the Outlook Desktop Application
h/w m/c Kernel shell Application s/w user
 Structure of Unix h/w m/c Kernel shell Application s/w. user While working with unix, several layers of interaction occur b/w the computer h/w & the user. 1. Kernel : It is the first layer which runs on
Structure of Unix h/w m/c Kernel shell Application s/w. user While working with unix, several layers of interaction occur b/w the computer h/w & the user. 1. Kernel : It is the first layer which runs on
Chapter 1 -- Getting Started, Getting Help
 Chapter 1 -- Getting Started, Getting Help Logging In Click on the Evergreen staff client icon located on your desktop or select the Evergreen Staff Client from your Start menu: The login screen opens:
Chapter 1 -- Getting Started, Getting Help Logging In Click on the Evergreen staff client icon located on your desktop or select the Evergreen Staff Client from your Start menu: The login screen opens:
A. Outlook Web App -
 A. Outlook Web App - Email 1. Outlook Web App (OWA) Vs. Outlook Outlook refers to an application that is physically installed on a computer. Whereas a Web Application is something that is not installed
A. Outlook Web App - Email 1. Outlook Web App (OWA) Vs. Outlook Outlook refers to an application that is physically installed on a computer. Whereas a Web Application is something that is not installed
CSCI 2132 Software Development. Lecture 5: File Permissions
 CSCI 2132 Software Development Lecture 5: File Permissions Instructor: Vlado Keselj Faculty of Computer Science Dalhousie University 14-Sep-2018 (5) CSCI 2132 1 Files and Directories Pathnames Previous
CSCI 2132 Software Development Lecture 5: File Permissions Instructor: Vlado Keselj Faculty of Computer Science Dalhousie University 14-Sep-2018 (5) CSCI 2132 1 Files and Directories Pathnames Previous
History. Terminology. Opening a Terminal. Introduction to the Unix command line GNOME
 Introduction to the Unix command line History Many contemporary computer operating systems, like Microsoft Windows and Mac OS X, offer primarily (but not exclusively) graphical user interfaces. The user
Introduction to the Unix command line History Many contemporary computer operating systems, like Microsoft Windows and Mac OS X, offer primarily (but not exclusively) graphical user interfaces. The user
Working with Basic Linux. Daniel Balagué
 Working with Basic Linux Daniel Balagué How Linux Works? Everything in Linux is either a file or a process. A process is an executing program identified with a PID number. It runs in short or long duration
Working with Basic Linux Daniel Balagué How Linux Works? Everything in Linux is either a file or a process. A process is an executing program identified with a PID number. It runs in short or long duration
Examples: Directory pathname: File pathname: /home/username/ics124/assignments/ /home/username/ops224/assignments/assn1.txt
 ULI101 Week 03 Week Overview Absolute and relative pathnames File name expansion Shell basics Command execution in detail Recalling and editing previous commands Quoting Pathnames A pathname is a list
ULI101 Week 03 Week Overview Absolute and relative pathnames File name expansion Shell basics Command execution in detail Recalling and editing previous commands Quoting Pathnames A pathname is a list
Outlook Web App User s Guide
 Outlook Web App User s Guide The new Outlook Web App will be replacing your old Outlook Web Access. This upgrade includes many new features that were only previously available through Microsoft Outlook.
Outlook Web App User s Guide The new Outlook Web App will be replacing your old Outlook Web Access. This upgrade includes many new features that were only previously available through Microsoft Outlook.
OUTLOOK 2010 QUICK GUIDE. Version 1.7
 OUTLOOK 2010 QUICK GUIDE Version 1.7 Table of Contents THE NAVIGATION PANE... 5 Mail... 5 Calendar... 5 Contacts... 5 Tasks... 5 Notes... 5 Folder List... 5 Shortcuts... 5 E-MAIL... 5 Create a new e-mail
OUTLOOK 2010 QUICK GUIDE Version 1.7 Table of Contents THE NAVIGATION PANE... 5 Mail... 5 Calendar... 5 Contacts... 5 Tasks... 5 Notes... 5 Folder List... 5 Shortcuts... 5 E-MAIL... 5 Create a new e-mail
Introduction. File System. Note. Achtung!
 3 Unix Shell 1: Introduction Lab Objective: Explore the basics of the Unix Shell. Understand how to navigate and manipulate file directories. Introduce the Vim text editor for easy writing and editing
3 Unix Shell 1: Introduction Lab Objective: Explore the basics of the Unix Shell. Understand how to navigate and manipulate file directories. Introduce the Vim text editor for easy writing and editing
This lab exercise is to be submitted at the end of the lab session! passwd [That is the command to change your current password to a new one]
![This lab exercise is to be submitted at the end of the lab session! passwd [That is the command to change your current password to a new one] This lab exercise is to be submitted at the end of the lab session! passwd [That is the command to change your current password to a new one]](/thumbs/93/111834574.jpg) Data and Computer Security (CMPD414) Lab II Topics: secure login, moving into HOME-directory, navigation on Unix, basic commands for vi, Message Digest This lab exercise is to be submitted at the end of
Data and Computer Security (CMPD414) Lab II Topics: secure login, moving into HOME-directory, navigation on Unix, basic commands for vi, Message Digest This lab exercise is to be submitted at the end of
Computer Architecture Lab 1 (Starting with Linux)
 Computer Architecture Lab 1 (Starting with Linux) Linux is a computer operating system. An operating system consists of the software that manages your computer and lets you run applications on it. The
Computer Architecture Lab 1 (Starting with Linux) Linux is a computer operating system. An operating system consists of the software that manages your computer and lets you run applications on it. The
When talking about how to launch commands and other things that is to be typed into the terminal, the following syntax is used:
 Linux Tutorial How to read the examples When talking about how to launch commands and other things that is to be typed into the terminal, the following syntax is used: $ application file.txt
Linux Tutorial How to read the examples When talking about how to launch commands and other things that is to be typed into the terminal, the following syntax is used: $ application file.txt
2013 edition (version 1.1)
 2013 edition (version 1.1) Contents 1 Introduction... 3 2 Signing in to your Office 365 account... 3 2.1 Acceptable Use Policy and Terms of Use... 4 3 Setting your profile and options... 4 3.1 Settings:
2013 edition (version 1.1) Contents 1 Introduction... 3 2 Signing in to your Office 365 account... 3 2.1 Acceptable Use Policy and Terms of Use... 4 3 Setting your profile and options... 4 3.1 Settings:
IBM Notes Client V9.0.1 Reference Guide
 IBM Notes Client V9.0.1 Reference Guide Revised 05/20/2016 1 Accessing the IBM Notes Client IBM Notes Client V9.0.1 Reference Guide From your desktop, double-click the IBM Notes icon. Logging in to the
IBM Notes Client V9.0.1 Reference Guide Revised 05/20/2016 1 Accessing the IBM Notes Client IBM Notes Client V9.0.1 Reference Guide From your desktop, double-click the IBM Notes icon. Logging in to the
Results Manager Step Sets for Classroom Interface
 How to Log In to SuccessMaker Enterprise: 1. Double-click the SuccessMaker Enterprise icon. The SuccessMaker Enterprise Log In screen appears. 2. Type in your user name and press Tab. 3. Type in your password
How to Log In to SuccessMaker Enterprise: 1. Double-click the SuccessMaker Enterprise icon. The SuccessMaker Enterprise Log In screen appears. 2. Type in your user name and press Tab. 3. Type in your password
Outlook Web Access Getting Started
 Getting Started Outlook Web Access Getting Started First, open up the web browser of your choice. Then, enter the following URL: http://mailserver.pts.edu Outlook Web Access Login To log in, you will simply
Getting Started Outlook Web Access Getting Started First, open up the web browser of your choice. Then, enter the following URL: http://mailserver.pts.edu Outlook Web Access Login To log in, you will simply
Outlook Web Access -User Guides-
 Nilai University College (Nilai Education Sdn. Bhd) Outlook Web Access -User Guides- Prepared By IT Department (Infrastructure Team) VERSION: 1.0 All rights reserved. This document is a proprietary product
Nilai University College (Nilai Education Sdn. Bhd) Outlook Web Access -User Guides- Prepared By IT Department (Infrastructure Team) VERSION: 1.0 All rights reserved. This document is a proprietary product
FIT 100: Fluency with Information Technology
 FIT 100: Fluency with Information Technology Lab 1: UW NetID, Email, Activating Student Web Pages Table of Contents: Obtain a UW Net ID (your email / web page identity):... 1 1. Setting Up An Account...
FIT 100: Fluency with Information Technology Lab 1: UW NetID, Email, Activating Student Web Pages Table of Contents: Obtain a UW Net ID (your email / web page identity):... 1 1. Setting Up An Account...
Getting Started with Network Access
 Getting Started with Network Access This document contains reference information about Triad s hardlines and lumber line of software products. The software described in this document, as well as the document
Getting Started with Network Access This document contains reference information about Triad s hardlines and lumber line of software products. The software described in this document, as well as the document
Find out where you currently are in the path Change directories to be at the root of your home directory (/home/username) cd ~
 CIS 105 Working with directories You have using directories in a Windows environment extensively. Often in Windows we are calling them folders. They are important in order to organize our files. It is
CIS 105 Working with directories You have using directories in a Windows environment extensively. Often in Windows we are calling them folders. They are important in order to organize our files. It is
The Command Shell. Fundamentals of Computer Science
 The Command Shell Fundamentals of Computer Science Outline Starting the Command Shell Locally Remote Host Directory Structure Moving around the directories Displaying File Contents Compiling and Running
The Command Shell Fundamentals of Computer Science Outline Starting the Command Shell Locally Remote Host Directory Structure Moving around the directories Displaying File Contents Compiling and Running
Setup Procedure for NEESPOP prior to Testing
 Setup Procedure for NEESPOP prior to Testing The following instructions describe the procedure to send data to the RDV (Remote Data Viewer). 1. Camera Setup 1.1. Put cameras on tripods in the desired location.
Setup Procedure for NEESPOP prior to Testing The following instructions describe the procedure to send data to the RDV (Remote Data Viewer). 1. Camera Setup 1.1. Put cameras on tripods in the desired location.
Week Overview. Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages
 ULI101 Week 02 Week Overview Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages Text editing Common file utilities: cat,more,less,touch,file,find
ULI101 Week 02 Week Overview Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages Text editing Common file utilities: cat,more,less,touch,file,find
2 Getting Started. Getting Started (v1.8.6) 3/5/2007
 2 Getting Started Java will be used in the examples in this section; however, the information applies to all supported languages for which you have installed a compiler (e.g., Ada, C, C++, Java) unless
2 Getting Started Java will be used in the examples in this section; however, the information applies to all supported languages for which you have installed a compiler (e.g., Ada, C, C++, Java) unless
You can use the WinSCP program to load or copy (FTP) files from your computer onto the Codd server.
 CODD SERVER ACCESS INSTRUCTIONS OVERVIEW Codd (codd.franklin.edu) is a server that is used for many Computer Science (COMP) courses. To access the Franklin University Linux Server called Codd, an SSH connection
CODD SERVER ACCESS INSTRUCTIONS OVERVIEW Codd (codd.franklin.edu) is a server that is used for many Computer Science (COMP) courses. To access the Franklin University Linux Server called Codd, an SSH connection
Recitation #1 Boot Camp. August 30th, 2016
 18-600 Recitation #1 Boot Camp August 30th, 2016 Welcome to 18-600! Purpose of recitation Useful tools, information pertaining to the labs Hands-on activities Problem solving and exam prep Last ~30 mins
18-600 Recitation #1 Boot Camp August 30th, 2016 Welcome to 18-600! Purpose of recitation Useful tools, information pertaining to the labs Hands-on activities Problem solving and exam prep Last ~30 mins
Helsinki 19 Jan Practical course in genome bioinformatics DAY 0
 Helsinki 19 Jan 2017 529028 Practical course in genome bioinformatics DAY 0 This document can be downloaded at: http://ekhidna.biocenter.helsinki.fi/downloads/teaching/spring2017/exercises_day0.pdf The
Helsinki 19 Jan 2017 529028 Practical course in genome bioinformatics DAY 0 This document can be downloaded at: http://ekhidna.biocenter.helsinki.fi/downloads/teaching/spring2017/exercises_day0.pdf The
Table of Contents. 3. Changing your Lotus Notes Password, page Choosing your Letterhead and Signature, page 6
 Table of Contents 1. Logging onto Lotus Notes, page 3 2. Logging out of Lotus Notes, page 3 3. Changing your Lotus Notes Password, page 4 4. Navigating in Lotus Notes, page 5 5. Choosing your Letterhead
Table of Contents 1. Logging onto Lotus Notes, page 3 2. Logging out of Lotus Notes, page 3 3. Changing your Lotus Notes Password, page 4 4. Navigating in Lotus Notes, page 5 5. Choosing your Letterhead
MCDOUGAL LITTELL EASYPLANNER USER S GUIDE
 MCDOUGAL LITTELL EASYPLANNER USER S GUIDE 1 Introduction The McDougal Littell EasyPlanner allows you to quickly and easily access Resource materials such as tests, quizzes, books, and other supporting
MCDOUGAL LITTELL EASYPLANNER USER S GUIDE 1 Introduction The McDougal Littell EasyPlanner allows you to quickly and easily access Resource materials such as tests, quizzes, books, and other supporting
Introduction to Unix CHAPTER 6. File Systems. Permissions
 CHAPTER 6 Introduction to Unix The Unix operating system is an incredibly powerful and complex system that is ideal for running a distributed system such as ours, particularly since we use computers primarily
CHAPTER 6 Introduction to Unix The Unix operating system is an incredibly powerful and complex system that is ideal for running a distributed system such as ours, particularly since we use computers primarily
Short Read Sequencing Analysis Workshop
 Short Read Sequencing Analysis Workshop Day 2 Learning the Linux Compute Environment In-class Slides Matt Hynes-Grace Manager of IT Operations, BioFrontiers Institute Review of Day 2 Videos Video 1 Introduction
Short Read Sequencing Analysis Workshop Day 2 Learning the Linux Compute Environment In-class Slides Matt Hynes-Grace Manager of IT Operations, BioFrontiers Institute Review of Day 2 Videos Video 1 Introduction
Chapter-3. Introduction to Unix: Fundamental Commands
 Chapter-3 Introduction to Unix: Fundamental Commands What You Will Learn The fundamental commands of the Unix operating system. Everything told for Unix here is applicable to the Linux operating system
Chapter-3 Introduction to Unix: Fundamental Commands What You Will Learn The fundamental commands of the Unix operating system. Everything told for Unix here is applicable to the Linux operating system
Web Mail Check v 1.0
 Web Mail Check v 1.0 TABLE OF CONTENTS LAUNCHING WEB MAIL CHECK... 3 HOME PAGE... 4 LOG IN... 4 LANGUAGE... 5 DIRECTIONS... 5 READING MESSAGES... 8 HEADERS... 10 PRINTER FRIENDLY VERSION... 11 REPLYING
Web Mail Check v 1.0 TABLE OF CONTENTS LAUNCHING WEB MAIL CHECK... 3 HOME PAGE... 4 LOG IN... 4 LANGUAGE... 5 DIRECTIONS... 5 READING MESSAGES... 8 HEADERS... 10 PRINTER FRIENDLY VERSION... 11 REPLYING
Getting Started (1.8.7) 9/2/2009
 2 Getting Started For the examples in this section, Microsoft Windows and Java will be used. However, much of the information applies to other operating systems and supported languages for which you have
2 Getting Started For the examples in this section, Microsoft Windows and Java will be used. However, much of the information applies to other operating systems and supported languages for which you have
Physics REU Unix Tutorial
 Physics REU Unix Tutorial What is unix? Unix is an operating system. In simple terms, its the set of programs that makes a computer work. It can be broken down into three parts. (1) kernel: The component
Physics REU Unix Tutorial What is unix? Unix is an operating system. In simple terms, its the set of programs that makes a computer work. It can be broken down into three parts. (1) kernel: The component
Getting Started With Web Mail Help Desk
 INET010 Feb 2008 Getting Started With Web Mail Help Desk Overview... 1 Login and Logout... 2 Basic Navigation... 2 Basic Tasks... 2 Using Folders... 5 Attachments... 7 Address Book... 8 Options and Other
INET010 Feb 2008 Getting Started With Web Mail Help Desk Overview... 1 Login and Logout... 2 Basic Navigation... 2 Basic Tasks... 2 Using Folders... 5 Attachments... 7 Address Book... 8 Options and Other
Linux Exercise. pwd answer: We call this directory (into which you get when you log in) your home directory.
 Linux Exercise The following steps will guide you through the most common Linux commands. If you are using windows (Library and any Windows lab on campus), then start with step 1. If you are using a linux
Linux Exercise The following steps will guide you through the most common Linux commands. If you are using windows (Library and any Windows lab on campus), then start with step 1. If you are using a linux
Introduction to the GroupWise and Calendar Program. Getting Started with GroupWise
 Introduction to the GroupWise Email and Calendar Program Main Window: the GroupWise Main Window displays the Toolbar(s), Folder List box and Item List box. Folder List box: the left panel of the main window
Introduction to the GroupWise Email and Calendar Program Main Window: the GroupWise Main Window displays the Toolbar(s), Folder List box and Item List box. Folder List box: the left panel of the main window
Introduction to Linux. Fundamentals of Computer Science
 Introduction to Linux Fundamentals of Computer Science Outline Operating Systems Linux History Linux Architecture Logging in to Linux Command Format Linux Filesystem Directory and File Commands Wildcard
Introduction to Linux Fundamentals of Computer Science Outline Operating Systems Linux History Linux Architecture Logging in to Linux Command Format Linux Filesystem Directory and File Commands Wildcard
Once you have installed MobaXterm, open MobaXterm. Go to Sessions -> New Session, and click on the SSH icon.
 Lab 1 In order to get credit for the lab, you need to be checked off by the end of lab. For nonzero labs, you can earn a maximum of 3 points for lab work completed outside of lab time, but you must finish
Lab 1 In order to get credit for the lab, you need to be checked off by the end of lab. For nonzero labs, you can earn a maximum of 3 points for lab work completed outside of lab time, but you must finish
Operating System Interaction via bash
 Operating System Interaction via bash bash, or the Bourne-Again Shell, is a popular operating system shell that is used by many platforms bash uses the command line interaction style generally accepted
Operating System Interaction via bash bash, or the Bourne-Again Shell, is a popular operating system shell that is used by many platforms bash uses the command line interaction style generally accepted
