OrangeCRM Business Intelligence API IMPLEMENTATION GUIDE
|
|
|
- Edwin Bailey
- 6 years ago
- Views:
Transcription
1 OrangeCRM Business Intelligence API IMPLEMENTATION GUIDE VERSION 1.01 October 17, 2016
2 API UPDATES V1.01 Implementation 2 P age
3 API ACTIONS The following actions can be performed by the Business Intelligence API: SQL_QRY_URL Sends Business Intelligence a request for a URL to be generated and handed back. This URL will then be able to execute a pre-built stored procedure from MS-SQL and hand back a file with the information. REPORT_URL (TO BE IMPLEMENTED IN VERSION 1.02) 3 P age
4 DEVELOPERS To access the Business Intelligence gateway, developers would design a script that does the following: 1. Securely obtains all of the information needed to process the request 2. Initiates an HTTPS form POST from your server to: INTELLIGENCE_URL]/rptbiapi 3. Receives the response from Business Intelligence and processes the response to display the appropriate result to the end user. REQUEST FORMAT To send a request to Business Intelligence, you must first initiate a secure socket connection via the URL above. Using port 443 (HTTPS), establish a socket connection to your Business Intelligence server cluster. You are now ready to transmit the request information. Example Post String: &q_system_key=yn12qa&q_action=sql_qry_url&q_rpt_begindate= &q_rpt_enddate= ANSWER FORMAT After a request is submitted, the gateway server will respond with the results in a few seconds. It is up to your program to interpret the results and route the customer accordingly. Here are some sample responses: <html> <head> </head> <body text="#000000"> &code=1&result=complete&reason=url returned&answer= crmdemocrm&sp=510041f572&parm=63f4351ed62b11f785256fef c~066bb6a4ff6d6b4e85257b ffd~20 16/01/01~2016/12/12&PARMCNT=4 </body> </html> Note: If the gateway is down and unable to process requests, the answer response may be as below. If this occurs please contact customer service for assistance. HTTP/ OK Server: Lotus-Domino Date: Thu, 05 Jun :25:39 GMT Content-Type: text/html Content-Length: 158 <html><head></head><body text= # ><h2>agent done</h2></body></html> See Appendix for Sample Code 4 Page
5 STANDARD REQUEST SUBMISSION API The Standard Request Submission API defines the information that can be submitted to the gateway. The API consists of a set of fields that are required for every request and a set of fields that are optional. Under the API, the gateway accepts a NAME/VALUE pair. The NAME is the field name and indicates to the gateway what information is being submitted. VALUE contains the contents of the field. API ACCOUNT INFORMATION The following fields in the API allow the system to identify the application submitting the request and the state of the application s account on the gateway. Field Used For Value Size Description q_system_key All Requests Token assigned in the application by the Business Intelligence Admin. 32 Pass the system key (token) obtained from the Business Intelligence Admin for this request type. This key will identify the SQL URL or the Report URL that you are requesting. A Unique Key is assigned to each stored procedure or Report. q_action All Requests One of the following: SQL_QRY_URL N/A Indicates the type of request being sent. If the value does not match any of the values stated, the request will be rejected. 5 P age
6 REQUEST SQL QUERY URL Request Post String: &q_system_key=ae8v83 &q_action= SQL_QRY_URL &Q_RPT_BEGINDATE= &Q_RPT_ENDDATE= &Q_RPT_PROGRAM=63F4351ED62B11F785256FEF C Note: All fields are optional depending on the request being sent in. An API will reject any request that is lacking the required fields, and will ignore any fields sent to it that are not specified for that query. Field Used For Value Length Description Q_RPT_BEGINDATE SQL_QRY_URL YYYYMMDD HH:mm:ss 17 Start date for your time frame Q_RPT_ENDDATE SQL_QRY_URL YYYYMMDD HH:mm:ss 17 Stop date for your time frame Q_RPT_ACQUISITIONCENTER SQL_QRY_URL GUID 32 Alpha-numeric value that uniquely identifies the acquisition center group GUID. If an acquisition center has not been assigned to a specific group, the GUID of the acquisition center is used. Q_RPT_PROGRAM SQL_QRY_URL GUID 32 Alpha-numeric value that uniquely identifies the Program for the requested information. In some cases a request can be made for all programs - The 32 character alpha-numeric value is then: XX5221F875C2F7FC852570A F006A7644. Q_RPT_USERID SQL_QRY_URL GUID 32 Alpha-numeric value that uniquely identifies the ACL User whom this request is for. This can be used for security purposes, to ensure users only obtain data that they have permission to see. Q_RPT_GROUP SQL_QRY_URL Any string 80 The CSR Group name. Q_RPT_DATEFIELD SQL_QRY_URL DateCreated DateOrdered DateResolved DateFinish DateIssue 8-12 Specifies which date field to use in a query. For example, when a transaction was issued or when it finished with a full response from the bank. Q_RPT_FILTER SQL_QRY_URL Any predefined string 80 A specific filter set against a query. Q_RPT_BANKID SQL_QRY_URL GUID 32 GUID of the Merchant Bank (not to be confused with the Bank Performance Group GUID). 6 P age
7 RESPONSE FIELDS RETURNED Position Field Description 1 code Indicates the result of the request: 1 = ACCEPTED 2 = REFUSED 3 = ERROR 4 = DUPLICATE 2 result Brief description of the result code. 3 reason Text message from the gateway. Answer URL A URL that can be run to download the requested file. This will include temporary access to SQL, i.e. the URL will not function for more than 24 hours. 7 P age
8 APPENDIX Command Line CURL Samples: curl.exe k -d " &q_system_key=ae8v83 &q_action=sql_qry_url &Q_RPT_USERID=066BB6A4FF6D6B4E85257B FFD &Q_RPT_BEGINDATE= &Q_RPT_ENDDATE= &Q_RPT_PROGRAM=63F4351ED62B11F785256FEF C " >a.txt PHP Sample Code: function REQUEST URL ($fields, $q_system_key, $conn) { extract($fields); $postdata[ q_system_key ] = $q_system_key; $postdata[ q_action ]= SQL_QRY_URL ; $postdata[ q_rpt_userid ] = $r_userid; $postdata[ q_rpt_program ] = $r_programid; $postdata[ q_rpt_begindate ] = $r_startdate; $postdata[ q_rpt_enddate ] = $r_stopdate; } 8 P age
NTP Software VFM Administration Web Site
 NTP Software VFM Administration Web Site User Manual Version 7.1 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator s perspective. Upon completion of
NTP Software VFM Administration Web Site User Manual Version 7.1 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator s perspective. Upon completion of
API Spec Sheet For HLR v1.4
 API Spec Sheet For HLR v1.4 INTRODUCTION The Wholesale SMS HLR API provides an easy to use method of accessing the HLR (Home Location Register) for all networks worldwide that support HLR. For large batch
API Spec Sheet For HLR v1.4 INTRODUCTION The Wholesale SMS HLR API provides an easy to use method of accessing the HLR (Home Location Register) for all networks worldwide that support HLR. For large batch
API Spec Sheet For Version 2.5
 INTRODUCTION The Wholesale SMS API is ideally suited for sending individual sms messages and/or automated responses through our premium routes. To send bulk messages through the API you can set your server
INTRODUCTION The Wholesale SMS API is ideally suited for sending individual sms messages and/or automated responses through our premium routes. To send bulk messages through the API you can set your server
HTTPS File Transfer. Specification
 HTTPS File Transfer Specification Version 1.4 5-Apr-2017 Date Version Description 30-Aug-2010 1.0 Original Version 30-Jun-2011 1.1 Added FAQ 29-Jun-2015 1.2 ilink administration added 1-Sep-2015 1.3 Updated
HTTPS File Transfer Specification Version 1.4 5-Apr-2017 Date Version Description 30-Aug-2010 1.0 Original Version 30-Jun-2011 1.1 Added FAQ 29-Jun-2015 1.2 ilink administration added 1-Sep-2015 1.3 Updated
NTP Software VFM. Administration Web Site for EMC Atmos User Manual. Version 6.1
 NTP Software VFM Administration Web Site for EMC Atmos User Manual Version 6.1 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator s perspective. Upon
NTP Software VFM Administration Web Site for EMC Atmos User Manual Version 6.1 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator s perspective. Upon
CSCE 548 Building Secure Software SQL Injection Attack
 CSCE 548 Building Secure Software SQL Injection Attack Professor Lisa Luo Spring 2018 Previous class DirtyCOW is a special type of race condition problem It is related to memory mapping We learned how
CSCE 548 Building Secure Software SQL Injection Attack Professor Lisa Luo Spring 2018 Previous class DirtyCOW is a special type of race condition problem It is related to memory mapping We learned how
Guide for Administrators
 novaresourcesync v.4.2 Guide for Administrators Updated May 9, 2013 Page 1 of 24 Copyright, Trademarks, and Legal Tempus Nova Inc. 1755 Blake Street Denver, CO 80202 www.tempusnova.com May 9, 2013 Copyright
novaresourcesync v.4.2 Guide for Administrators Updated May 9, 2013 Page 1 of 24 Copyright, Trademarks, and Legal Tempus Nova Inc. 1755 Blake Street Denver, CO 80202 www.tempusnova.com May 9, 2013 Copyright
NTP Software VFM Administration Web Site For Microsoft Azure
 NTP Software VFM Administration Web Site For Microsoft Azure User Manual Revision 1.1. - July 2015 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator
NTP Software VFM Administration Web Site For Microsoft Azure User Manual Revision 1.1. - July 2015 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator
Configuring User Defined Patterns
 The allows you to create customized data patterns which can be detected and handled according to the configured security settings. The uses regular expressions (regex) to define data type patterns. Custom
The allows you to create customized data patterns which can be detected and handled according to the configured security settings. The uses regular expressions (regex) to define data type patterns. Custom
TACACS Support APIs. curl -k -v -u "admin:cisco123" -H Accept:application/vnd.yang.data+xml -H ContentType:application/vnd.yang.
 Table 1: Action Method Payload Required API To configure TACACS server POST Yes To configure TACACS server PUT Yes To configure TACACS server DELETE No To view TACACS server configuration GET No Example:
Table 1: Action Method Payload Required API To configure TACACS server POST Yes To configure TACACS server PUT Yes To configure TACACS server DELETE No To view TACACS server configuration GET No Example:
SOAP API. The correct URL has been hidden. Please contact your account manager for the full URL information.
 SMS Help Guides TNZ Group Limited sales@tnz.co.nz +64 9 9293000 +64 9 522 8839 SOAP API SOAP is a simple way of sending SMS/TXT messages via the internet. It is a great solution for integration into existing
SMS Help Guides TNZ Group Limited sales@tnz.co.nz +64 9 9293000 +64 9 522 8839 SOAP API SOAP is a simple way of sending SMS/TXT messages via the internet. It is a great solution for integration into existing
Agenda. Page. IDD Mobile User Guide Version 1.0
 Agenda Page IDD Mobile User Guide Version 1.0 This presentation was prepared exclusively for the benefit and internal use of the J.P. Morgan client to whom it is directly addressed and delivered including
Agenda Page IDD Mobile User Guide Version 1.0 This presentation was prepared exclusively for the benefit and internal use of the J.P. Morgan client to whom it is directly addressed and delivered including
Crystal Enterprise. Overview. Contents. Web Server Overview - Internet Information System (IIS)
 Overview Contents This document provides an overview to web server technology particularly Microsoft s Internet Information Server (IIS) and its relationship with. Although this article has been written
Overview Contents This document provides an overview to web server technology particularly Microsoft s Internet Information Server (IIS) and its relationship with. Although this article has been written
COSC 2206 Internet Tools. The HTTP Protocol
 COSC 2206 Internet Tools The HTTP Protocol http://www.w3.org/protocols/ What is TCP/IP? TCP: Transmission Control Protocol IP: Internet Protocol These network protocols provide a standard method for sending
COSC 2206 Internet Tools The HTTP Protocol http://www.w3.org/protocols/ What is TCP/IP? TCP: Transmission Control Protocol IP: Internet Protocol These network protocols provide a standard method for sending
NTP Software VFM. Administration Web Site for NetAppS3. User Manual. Version 5.1
 NTP Software VFM Administration Web Site for NetAppS3 User Manual Version 5.1 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator s perspective. Upon
NTP Software VFM Administration Web Site for NetAppS3 User Manual Version 5.1 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator s perspective. Upon
NTP Software VFM. Administration Web Site for Atmos. User Manual. Version 5.1
 NTP Software VFM Administration Web Site for Atmos User Manual Version 5.1 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator s perspective. Upon completion
NTP Software VFM Administration Web Site for Atmos User Manual Version 5.1 This guide details the method for using NTP Software VFM Administration Web Site, from an administrator s perspective. Upon completion
The HTTP Protocol HTTP
 The HTTP Protocol HTTP Copyright (c) 2013 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later
The HTTP Protocol HTTP Copyright (c) 2013 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later
Creating Data Driven Websites with Dreamweaver CS4: Using ColdFusion, PHP or ASP
 Creating Data Driven Websites with Dreamweaver CS4: Using ColdFusion, PHP or ASP published by Antall Training http://www.scottantall.com info@scottantall.com 440/623-3738 1.0.0 Copyright 2003-2009 Antall
Creating Data Driven Websites with Dreamweaver CS4: Using ColdFusion, PHP or ASP published by Antall Training http://www.scottantall.com info@scottantall.com 440/623-3738 1.0.0 Copyright 2003-2009 Antall
Combating Common Web App Authentication Threats
 Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
HTTP Console Documentation
 HTTP Console Documentation Release 1.0.0 Ahmad Nassri April 02, 2014 Contents 1 text/html 1 2 text/plain 3 3 application/php 5 4 application/xml 7 5 application/json 9 6 API Reference 11 6.1 /ip.....................................................
HTTP Console Documentation Release 1.0.0 Ahmad Nassri April 02, 2014 Contents 1 text/html 1 2 text/plain 3 3 application/php 5 4 application/xml 7 5 application/json 9 6 API Reference 11 6.1 /ip.....................................................
text2reach2 SMS API Sep 5, 2013 v1.1 This document describes application interface (API) between SMS service provider (SP) and SMS gateway (SMSGW).
 text2reach2 SMS API Sep 5, 2013 v1.1 This document describes application interface (API) between SMS service provider (SP) and SMS gateway (SMSGW). Table of Contents API Interface Types...3 Bulk SMS interface...3
text2reach2 SMS API Sep 5, 2013 v1.1 This document describes application interface (API) between SMS service provider (SP) and SMS gateway (SMSGW). Table of Contents API Interface Types...3 Bulk SMS interface...3
Black Box DCX3000 / DCX1000 Using the API
 Black Box DCX3000 / DCX1000 Using the API updated 2/22/2017 This document will give you a brief overview of how to access the DCX3000 / DCX1000 API and how you can interact with it using an online tool.
Black Box DCX3000 / DCX1000 Using the API updated 2/22/2017 This document will give you a brief overview of how to access the DCX3000 / DCX1000 API and how you can interact with it using an online tool.
Dynamic Documents. Kent State University Dept. of Math & Computer Science. CS 4/55231 Internet Engineering. What is a Script?
 CS 4/55231 Internet Engineering Kent State University Dept. of Math & Computer Science LECT-12 Dynamic Documents 1 2 Why Dynamic Documents are needed? There are many situations when customization of the
CS 4/55231 Internet Engineering Kent State University Dept. of Math & Computer Science LECT-12 Dynamic Documents 1 2 Why Dynamic Documents are needed? There are many situations when customization of the
PHPKB API Reference Guide
 PHPKB API Reference Guide KB Administrator Fri, Apr 9, 09 User Manual 96 0 This document provides details on how to use the API available in PHPKB knowledge base management software. It acts as a reference
PHPKB API Reference Guide KB Administrator Fri, Apr 9, 09 User Manual 96 0 This document provides details on how to use the API available in PHPKB knowledge base management software. It acts as a reference
ForeScout CounterACT. Configuration Guide. Version 3.4
 ForeScout CounterACT Open Integration Module: Data Exchange Version 3.4 Table of Contents About the Data Exchange Module... 4 About Support for Dual Stack Environments... 4 Requirements... 4 CounterACT
ForeScout CounterACT Open Integration Module: Data Exchange Version 3.4 Table of Contents About the Data Exchange Module... 4 About Support for Dual Stack Environments... 4 Requirements... 4 CounterACT
ForeScout Open Integration Module: Data Exchange Plugin
 ForeScout Open Integration Module: Data Exchange Plugin Version 3.2.0 Table of Contents About the Data Exchange Plugin... 4 Requirements... 4 CounterACT Software Requirements... 4 Connectivity Requirements...
ForeScout Open Integration Module: Data Exchange Plugin Version 3.2.0 Table of Contents About the Data Exchange Plugin... 4 Requirements... 4 CounterACT Software Requirements... 4 Connectivity Requirements...
Lecture 7b: HTTP. Feb. 24, Internet and Intranet Protocols and Applications
 Internet and Intranet Protocols and Applications Lecture 7b: HTTP Feb. 24, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu WWW - HTTP/1.1 Web s application layer protocol
Internet and Intranet Protocols and Applications Lecture 7b: HTTP Feb. 24, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu WWW - HTTP/1.1 Web s application layer protocol
NAB TRANSACT. Direct Post v2.1.2 Integration Guide
 NAB TRANSACT Direct Post v2.1.2 Integration Guide CONTENTS 1 Introduction 4 1.1 What is Direct Post? 4 1.2 Requirements for Implementation 4 1.2.1 Public Test Account Details 4 1.3 Card Types Accepted
NAB TRANSACT Direct Post v2.1.2 Integration Guide CONTENTS 1 Introduction 4 1.1 What is Direct Post? 4 1.2 Requirements for Implementation 4 1.2.1 Public Test Account Details 4 1.3 Card Types Accepted
All requests must be authenticated using the login and password you use to access your account.
 The REST API expects all text to be encoded as UTF-8, it is best to test by sending a message with a pound sign ( ) to confirm it is working as expected. If you are having issues sending as plain text,
The REST API expects all text to be encoded as UTF-8, it is best to test by sending a message with a pound sign ( ) to confirm it is working as expected. If you are having issues sending as plain text,
Slybroadcast Global API Documentation Version 3.0 June 2018
 Slybroadcast Global API Documentation Version 3.0 June 2018 MobileSphere 7 Faneuil Hall Marketplace, 4 th Floor Boston, MA 617.399.9980 1 Slybroadcast API 1. MobileSphere s slybroadcast API MobileSphere
Slybroadcast Global API Documentation Version 3.0 June 2018 MobileSphere 7 Faneuil Hall Marketplace, 4 th Floor Boston, MA 617.399.9980 1 Slybroadcast API 1. MobileSphere s slybroadcast API MobileSphere
WWW. HTTP, Ajax, APIs, REST
 WWW HTTP, Ajax, APIs, REST HTTP Hypertext Transfer Protocol Request Web Client HTTP Server WSGI Response Connectionless Media Independent Stateless Python Web Application WSGI : Web Server Gateway Interface
WWW HTTP, Ajax, APIs, REST HTTP Hypertext Transfer Protocol Request Web Client HTTP Server WSGI Response Connectionless Media Independent Stateless Python Web Application WSGI : Web Server Gateway Interface
Web Security. Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le
 Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
USER MANUAL TABLE OF CONTENTS. Store Error Log Manager. Version: 0.1.1
 USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Store Error Log Manager... 1 Installation& Activation... 2 Installation Steps... 2 Extension Activation... 3 Configuration... 5 Quick Notes...
USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Store Error Log Manager... 1 Installation& Activation... 2 Installation Steps... 2 Extension Activation... 3 Configuration... 5 Quick Notes...
CGI / HTTP(s) GET NETIO M2M API protocols docs
 CGI / HTTP(s) GET NETIO M2M API protocols docs Short summary CGI protocol is one way control only, command based M2M API protocol, where NETIO device is HTTP(s) server accepting commands sent over HTTP(s)
CGI / HTTP(s) GET NETIO M2M API protocols docs Short summary CGI protocol is one way control only, command based M2M API protocol, where NETIO device is HTTP(s) server accepting commands sent over HTTP(s)
HTTP Authentication API
 HTTP Authentication API Note: Both GET (URL format) and POST http requests are supported. Note that POST is considered better security as URL data can be cached in the browser. HTTP URL Format http(s)://your_securenvoy_server/secserver?flag=desktop&version=2.0&status=auth&userid=(my_userid)&passcode=(6
HTTP Authentication API Note: Both GET (URL format) and POST http requests are supported. Note that POST is considered better security as URL data can be cached in the browser. HTTP URL Format http(s)://your_securenvoy_server/secserver?flag=desktop&version=2.0&status=auth&userid=(my_userid)&passcode=(6
Lecture 9a: Sessions and Cookies
 CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
RESTFUL WEB SERVICES - INTERVIEW QUESTIONS
 RESTFUL WEB SERVICES - INTERVIEW QUESTIONS http://www.tutorialspoint.com/restful/restful_interview_questions.htm Copyright tutorialspoint.com Dear readers, these RESTful Web services Interview Questions
RESTFUL WEB SERVICES - INTERVIEW QUESTIONS http://www.tutorialspoint.com/restful/restful_interview_questions.htm Copyright tutorialspoint.com Dear readers, these RESTful Web services Interview Questions
Direct Post Integration Guide
 Direct Post Integration Guide Page 1 of 34 Document Control This is a control document DESCRIPTION Direct Post Integration Guide CREATION DATE 20/12/2011 CREATED BY SecurePay VERSION 1.4 DATE UPDATED 28/02/2017
Direct Post Integration Guide Page 1 of 34 Document Control This is a control document DESCRIPTION Direct Post Integration Guide CREATION DATE 20/12/2011 CREATED BY SecurePay VERSION 1.4 DATE UPDATED 28/02/2017
ANZ EGATE MERCHANT ADMINISTRATION QUICK REFERENCE GUIDE
 ANZ EGATE MERCHANT ADMINISTRATION QUICK REFERENCE GUIDE PURPOSE The purpose of this Quick Reference Guide is to provide the user with a quick reference to using the ANZ egate Merchant Administration. COPYRIGHT
ANZ EGATE MERCHANT ADMINISTRATION QUICK REFERENCE GUIDE PURPOSE The purpose of this Quick Reference Guide is to provide the user with a quick reference to using the ANZ egate Merchant Administration. COPYRIGHT
PHP by Pearson Education, Inc. All Rights Reserved.
 PHP 1992-2012 by Pearson Education, Inc. All Client-side Languages User-agent (web browser) requests a web page JavaScript is executed on PC http request Can affect the Browser and the page itself http
PHP 1992-2012 by Pearson Education, Inc. All Client-side Languages User-agent (web browser) requests a web page JavaScript is executed on PC http request Can affect the Browser and the page itself http
Web Security Service. Near Real-Time Log Sync Solution Brief. Version /OCT
 Web Security Service Near Real-Time Log Sync Solution Brief Version 6.10.4.1/OCT.12.2018 Symantec Web Security Service/Page 2 Page 3 Copyrights Copyright 2018 Symantec Corp. All rights reserved. Symantec,
Web Security Service Near Real-Time Log Sync Solution Brief Version 6.10.4.1/OCT.12.2018 Symantec Web Security Service/Page 2 Page 3 Copyrights Copyright 2018 Symantec Corp. All rights reserved. Symantec,
IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3.1 April 07, Integration Guide IBM
 IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3.1 April 07, 2017 Integration Guide IBM Note Before using this information and the product it supports, read the information
IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3.1 April 07, 2017 Integration Guide IBM Note Before using this information and the product it supports, read the information
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
SpeedChex EasyLink API
 SpeedChex EasyLink API Implementation Instructions Version 1.0 SpeedChex is an information capture and processing service that allows consumers to pay for goods or services over the Internet by check without
SpeedChex EasyLink API Implementation Instructions Version 1.0 SpeedChex is an information capture and processing service that allows consumers to pay for goods or services over the Internet by check without
In order to install mypos Checkout plugin please follow the steps below:
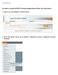 Installation In order to install mypos Checkout plugin please follow the steps below: 1. Sign in to your Magento Admin Panel. 2. From the admin menu, go to System > Magento connect > Magento Connect Manager.
Installation In order to install mypos Checkout plugin please follow the steps below: 1. Sign in to your Magento Admin Panel. 2. From the admin menu, go to System > Magento connect > Magento Connect Manager.
RAP as a Service for. Team Foundation Server. Prerequisites
 RAP as a Service for Team Foundation Server Prerequisites Download the latest prerequisites from: http://www.microsoft.com/en-us/download/details.aspx?id=34698 Last modified: Oct 12, 2017 Internet connectivity
RAP as a Service for Team Foundation Server Prerequisites Download the latest prerequisites from: http://www.microsoft.com/en-us/download/details.aspx?id=34698 Last modified: Oct 12, 2017 Internet connectivity
CORS Attacks. Author: Milad Khoshdel Blog: P a g e. CORS Attacks
 Author: Milad Khoshdel Blog: https://blog.regux.com Email: miladkhoshdel@gmail.com 1 P a g e Contents What is CORS?...3 How to Test?...4 CORS Checker Script...6 References...9 2 P a g e What is CORS? CORS
Author: Milad Khoshdel Blog: https://blog.regux.com Email: miladkhoshdel@gmail.com 1 P a g e Contents What is CORS?...3 How to Test?...4 CORS Checker Script...6 References...9 2 P a g e What is CORS? CORS
HOW ADMINISTRATORS WITH ALLOWABLE RIGHTS CAN SETUP, ASSIGN, EDIT OR DELETE ASSIGNMENTS OF CONTRACTORS IN LCPTRACKER
 HOW ADMINISTRATORS WITH ALLOWABLE RIGHTS CAN SETUP, ASSIGN, EDIT OR DELETE ASSIGNMENTS OF CONTRACTORS IN LCPTRACKER CHOOSE SETUP THEN CONTRACTOR SETUP Click on you Set Up tab and the click on Contractor
HOW ADMINISTRATORS WITH ALLOWABLE RIGHTS CAN SETUP, ASSIGN, EDIT OR DELETE ASSIGNMENTS OF CONTRACTORS IN LCPTRACKER CHOOSE SETUP THEN CONTRACTOR SETUP Click on you Set Up tab and the click on Contractor
Using the vrealize Orchestrator Operations Client. vrealize Orchestrator 7.5
 Using the vrealize Orchestrator Operations Client vrealize Orchestrator 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Using the vrealize Orchestrator Operations Client vrealize Orchestrator 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Note: Any references in the documentation to the Hyperion Download Center pertain if your site has access.
 Hyperion System 9 Master Data Management Release 9.2 Readme Readme File This file contains the following sections: Purpose... 1 New Features... 1 Installer Option to Save Database Scripts... 2 Gateway
Hyperion System 9 Master Data Management Release 9.2 Readme Readme File This file contains the following sections: Purpose... 1 New Features... 1 Installer Option to Save Database Scripts... 2 Gateway
StorageGRID Webscale NAS Bridge Management API Guide
 StorageGRID Webscale NAS Bridge 2.0.3 Management API Guide January 2018 215-12414_B0 doccomments@netapp.com Table of Contents 3 Contents Understanding the NAS Bridge management API... 4 RESTful web services
StorageGRID Webscale NAS Bridge 2.0.3 Management API Guide January 2018 215-12414_B0 doccomments@netapp.com Table of Contents 3 Contents Understanding the NAS Bridge management API... 4 RESTful web services
IBM Campaign Version-independent Integration with IBM Watson Campaign Automation Version 1 Release 1.5 February, Integration Guide IBM
 IBM Campaign Version-independent Integration with IBM Watson Campaign Automation Version 1 Release 1.5 February, 2018 Integration Guide IBM Note Before using this information and the product it supports,
IBM Campaign Version-independent Integration with IBM Watson Campaign Automation Version 1 Release 1.5 February, 2018 Integration Guide IBM Note Before using this information and the product it supports,
Real Application Security Administration
 Oracle Database Real Application Security Administration Console (RASADM) User s Guide 12c Release 2 (12.2) E85615-01 June 2017 Real Application Security Administration Oracle Database Real Application
Oracle Database Real Application Security Administration Console (RASADM) User s Guide 12c Release 2 (12.2) E85615-01 June 2017 Real Application Security Administration Oracle Database Real Application
Cisco Encryption
 This chapter contains the following sections: Overview of, page 1 How to Encrypt Messages with a Local Key Server, page 2 Encrypting Messages using the Email Security Appliance, page 3 Determining Which
This chapter contains the following sections: Overview of, page 1 How to Encrypt Messages with a Local Key Server, page 2 Encrypting Messages using the Email Security Appliance, page 3 Determining Which
EPHP a tool for learning the basics of PHP development. Nick Whitelegg School of Media Arts and Technology Southampton Solent University
 EPHP a tool for learning the basics of PHP development Nick Whitelegg School of Media Arts and Technology Southampton Solent University My background Lecturer at Southampton Solent University since 2003
EPHP a tool for learning the basics of PHP development Nick Whitelegg School of Media Arts and Technology Southampton Solent University My background Lecturer at Southampton Solent University since 2003
Guide for Administrators. Updated November 12, Page 1 of 31
 novaresourcesync v.5.3 Guide for Administrators Updated November 12, 2013 Page 1 of 31 Copyright, Trademarks, and Legal Tempus Nova Inc. 1755 Blake Street Denver, CO 80202 www.tempusnova.com November 12,
novaresourcesync v.5.3 Guide for Administrators Updated November 12, 2013 Page 1 of 31 Copyright, Trademarks, and Legal Tempus Nova Inc. 1755 Blake Street Denver, CO 80202 www.tempusnova.com November 12,
Way2mint SMS Mobile Terminate (MT) API Guide for HTTP / HTTPS
 Way2mint SMS Mobile Terminate (MT) API Guide for HTTP / HTTPS 10/1/2009 Way2mint Services Prepared by: Mohit Jaswani Copyright Way2mint Services The content of this document are copyright and remain the
Way2mint SMS Mobile Terminate (MT) API Guide for HTTP / HTTPS 10/1/2009 Way2mint Services Prepared by: Mohit Jaswani Copyright Way2mint Services The content of this document are copyright and remain the
Web Development. With PHP. Web Development With PHP
 Web Development With PHP Web Development With PHP We deliver all our courses as Corporate Training as well if you are a group interested in the course, this option may be more advantageous for you. 8983002500/8149046285
Web Development With PHP Web Development With PHP We deliver all our courses as Corporate Training as well if you are a group interested in the course, this option may be more advantageous for you. 8983002500/8149046285
AIM Application v. 2.4 User Manual
 AIM Application v. 2.4 User Manual Prepared by: HP Enterprise Services/DMDC 1600 N. Beauregard Street Alexandria, VA 22311 Abstract This guide describes how to use the AIM system, which provides for managing
AIM Application v. 2.4 User Manual Prepared by: HP Enterprise Services/DMDC 1600 N. Beauregard Street Alexandria, VA 22311 Abstract This guide describes how to use the AIM system, which provides for managing
CNIT 129S: Securing Web Applications. Ch 10: Attacking Back-End Components
 CNIT 129S: Securing Web Applications Ch 10: Attacking Back-End Components Injecting OS Commands Web server platforms often have APIs To access the filesystem, interface with other processes, and for network
CNIT 129S: Securing Web Applications Ch 10: Attacking Back-End Components Injecting OS Commands Web server platforms often have APIs To access the filesystem, interface with other processes, and for network
CS 161 Computer Security
 Nick Weaver Fall 2018 CS 161 Computer Security Homework 3 Due: Friday, 19 October 2018, at 11:59pm Instructions. This homework is due Friday, 19 October 2018, at 11:59pm. No late homeworks will be accepted
Nick Weaver Fall 2018 CS 161 Computer Security Homework 3 Due: Friday, 19 October 2018, at 11:59pm Instructions. This homework is due Friday, 19 October 2018, at 11:59pm. No late homeworks will be accepted
OTP Issuance/Use Manual
 For B2B Administrators of Samsung Electronics Online Customer DB OTP Issuance/Use Manual (Windows Type) Contents 3 1. OVERVIEW OF OTP ISSUANCE/INSTALLATION 4 4 5 6 7 9 12 12 2. OTP ISSUANCE/INSTALLATION
For B2B Administrators of Samsung Electronics Online Customer DB OTP Issuance/Use Manual (Windows Type) Contents 3 1. OVERVIEW OF OTP ISSUANCE/INSTALLATION 4 4 5 6 7 9 12 12 2. OTP ISSUANCE/INSTALLATION
LMEdprs Operating & Technical Guide
 LMEdprs Operating & Technical Guide May 2016 Please respond to: Market Surveillance +44 (0) 207 113 8203 LMEdprs Operating & Technical Guide Version 2.0 Table of Contents 1 Introduction... 4 2 Overview
LMEdprs Operating & Technical Guide May 2016 Please respond to: Market Surveillance +44 (0) 207 113 8203 LMEdprs Operating & Technical Guide Version 2.0 Table of Contents 1 Introduction... 4 2 Overview
Use a class C setting for maximum security. The class C setting is Click RoomWizard Setup.
 Use a class C setting for maximum security. The class C setting is 255.255.255.0. 2 Click RoomWizard Setup. The Default Gateway is the IP address of the router or gateway that provides internet access.
Use a class C setting for maximum security. The class C setting is 255.255.255.0. 2 Click RoomWizard Setup. The Default Gateway is the IP address of the router or gateway that provides internet access.
Oracle Database. Installation and Configuration of Real Application Security Administration (RASADM) Prerequisites
 Oracle Database Real Application Security Administration 12c Release 1 (12.1) E61899-04 May 2015 Oracle Database Real Application Security Administration (RASADM) lets you create Real Application Security
Oracle Database Real Application Security Administration 12c Release 1 (12.1) E61899-04 May 2015 Oracle Database Real Application Security Administration (RASADM) lets you create Real Application Security
CA Nimsoft Monitor. Implementing CA Nimsoft Monitor for Citrix CloudPlatform powered by Apache CloudStack
 CA Nimsoft Monitor Implementing CA Nimsoft Monitor for Citrix CloudPlatform powered by Apache CloudStack October 2013 Document Revision History Document Version Date Changes 1.00 Oct. 1, 2013 First edition
CA Nimsoft Monitor Implementing CA Nimsoft Monitor for Citrix CloudPlatform powered by Apache CloudStack October 2013 Document Revision History Document Version Date Changes 1.00 Oct. 1, 2013 First edition
vfire 9.8 Release Notes Version 1.5
 9.8 Release Notes 9.8 Release Notes Table of Contents Version Details for 9.8 Release Notes 4 Copyright 5 About this Document 6 Intended Audience 6 Standards and Conventions 6 Introducing 9.8 7 Installation
9.8 Release Notes 9.8 Release Notes Table of Contents Version Details for 9.8 Release Notes 4 Copyright 5 About this Document 6 Intended Audience 6 Standards and Conventions 6 Introducing 9.8 7 Installation
Protocols. Application Layer FTP, HTTP, SSH, IMAP. Transport Layer TCP, UDP. Internet Layer IP. Link Layer Ethernet, WiFi
 HTTP Protocols Application Layer FTP, HTTP, SSH, IMAP Transport Layer TCP, UDP Internet Layer IP Link Layer Ethernet, WiFi TCP/IP Transmission Control Protocol. Connection-Oriented Reliable source address
HTTP Protocols Application Layer FTP, HTTP, SSH, IMAP Transport Layer TCP, UDP Internet Layer IP Link Layer Ethernet, WiFi TCP/IP Transmission Control Protocol. Connection-Oriented Reliable source address
Server-Side Web Programming: Python (Part 1) Copyright 2017 by Robert M. Dondero, Ph.D. Princeton University
 Server-Side Web Programming: Python (Part 1) Copyright 2017 by Robert M. Dondero, Ph.D. Princeton University 1 Objectives You will learn about Server-side web programming in Python Common Gateway Interface
Server-Side Web Programming: Python (Part 1) Copyright 2017 by Robert M. Dondero, Ph.D. Princeton University 1 Objectives You will learn about Server-side web programming in Python Common Gateway Interface
A10 Thunder ADC with Oracle E-Business Suite 12.2 DEPLOYMENT GUIDE
 A10 Thunder ADC with Oracle E-Business Suite 12.2 DEPLOYMENT GUIDE Table of Contents 1. Introduction... 2 2 Deployment Prerequisites... 2 3 Oracle E-Business Topology... 3 4 Accessing the Thunder ADC Application
A10 Thunder ADC with Oracle E-Business Suite 12.2 DEPLOYMENT GUIDE Table of Contents 1. Introduction... 2 2 Deployment Prerequisites... 2 3 Oracle E-Business Topology... 3 4 Accessing the Thunder ADC Application
John Coggeshall Copyright 2006, Zend Technologies Inc.
 PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
Guest Book. The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
 License Guest Book Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction,
License Guest Book Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction,
Nasuni Data API Nasuni Corporation Boston, MA
 Nasuni Corporation Boston, MA Introduction The Nasuni API has been available in the Nasuni Filer since September 2012 (version 4.0.1) and is in use by hundreds of mobile clients worldwide. Previously,
Nasuni Corporation Boston, MA Introduction The Nasuni API has been available in the Nasuni Filer since September 2012 (version 4.0.1) and is in use by hundreds of mobile clients worldwide. Previously,
Web Technology. COMP476 Networked Computer Systems. Hypertext and Hypermedia. Document Representation. Client-Server Paradigm.
 Web Technology COMP476 Networked Computer Systems - Paradigm The method of interaction used when two application programs communicate over a network. A server application waits at a known address and a
Web Technology COMP476 Networked Computer Systems - Paradigm The method of interaction used when two application programs communicate over a network. A server application waits at a known address and a
Avoiding Web Application Flaws In Embedded Devices. Jake Edge LWN.net URL for slides:
 Avoiding Web Application Flaws In Embedded Devices Jake Edge LWN.net jake@lwn.net URL for slides: http://lwn.net/talks/elce2008 Overview Examples embedded devices gone bad Brief introduction to HTTP Authentication
Avoiding Web Application Flaws In Embedded Devices Jake Edge LWN.net jake@lwn.net URL for slides: http://lwn.net/talks/elce2008 Overview Examples embedded devices gone bad Brief introduction to HTTP Authentication
Introduction to Cisco TV CDS Software APIs
 CHAPTER 1 Cisco TV Content Delivery System (CDS) software provides two sets of application program interfaces (APIs): Monitoring Real Time Streaming Protocol (RTSP) Stream Diagnostics The Monitoring APIs
CHAPTER 1 Cisco TV Content Delivery System (CDS) software provides two sets of application program interfaces (APIs): Monitoring Real Time Streaming Protocol (RTSP) Stream Diagnostics The Monitoring APIs
We currently are able to offer three different action types:
 SMS Inbound Introduction SMS Inbound provides a simple to use interface for receiving inbound MMS messages. Inbound Message Actions Inbound Message Actions in SMS Inbound are things that our system can
SMS Inbound Introduction SMS Inbound provides a simple to use interface for receiving inbound MMS messages. Inbound Message Actions Inbound Message Actions in SMS Inbound are things that our system can
Web logs (blogs. blogs) Feed support BLOGS) WEB LOGS (BLOGS
 Web logs (blogs blogs) You can create your own personal Web logs (blogs) using IBM Lotus Notes. Using the blog template (dominoblog.ntf), you create a blog application, such as myblog.nsf, which you can
Web logs (blogs blogs) You can create your own personal Web logs (blogs) using IBM Lotus Notes. Using the blog template (dominoblog.ntf), you create a blog application, such as myblog.nsf, which you can
Backend Development. SWE 432, Fall 2017 Design and Implementation of Software for the Web
 Backend Development SWE 432, Fall 2017 Design and Implementation of Software for the Web Real World Example https://qz.com/1073221/the-hackers-who-broke-into-equifax-exploited-a-nine-year-old-security-flaw/
Backend Development SWE 432, Fall 2017 Design and Implementation of Software for the Web Real World Example https://qz.com/1073221/the-hackers-who-broke-into-equifax-exploited-a-nine-year-old-security-flaw/
CMPE 151: Network Administration. Servers
 CMPE 151: Network Administration Servers Announcements Unix shell+emacs tutorial. Basic Servers Telnet/Finger FTP Web SSH NNTP Let s look at the underlying protocols. Client-Server Model Request Response
CMPE 151: Network Administration Servers Announcements Unix shell+emacs tutorial. Basic Servers Telnet/Finger FTP Web SSH NNTP Let s look at the underlying protocols. Client-Server Model Request Response
Comprehensive Spam Quarantine Setup Guide on Security Appliance (ESA) and Security Management Appliance (SMA)
 Comprehensive Spam Quarantine Setup Guide on Email Security Appliance (ESA) and Security Management Appliance (SMA) Contents Introduction Procedure Configure Local Spam Quarantine on the ESA Enable Quarantine
Comprehensive Spam Quarantine Setup Guide on Email Security Appliance (ESA) and Security Management Appliance (SMA) Contents Introduction Procedure Configure Local Spam Quarantine on the ESA Enable Quarantine
How to Integrate. REVE Secure 2FA App. with Dashboard.
 How to Integrate REVE Secure 2FA App with Dashboard REVE Secure Software Token supports widely deployed mobile platforms like ios, Android, Windows, etc. and uses time-based algorithm to support 2FA. This
How to Integrate REVE Secure 2FA App with Dashboard REVE Secure Software Token supports widely deployed mobile platforms like ios, Android, Windows, etc. and uses time-based algorithm to support 2FA. This
Front Office for NetBackup Guide Self-service backup & restore
 Front Office for NetBackup Guide Self-service backup & restore Last updated August 6 2014 Contents 1.0 Solution Positioning... 3 1.1 For Service Providers... 3 1.2 For Enterprises... 3 2.0 Standard Services...
Front Office for NetBackup Guide Self-service backup & restore Last updated August 6 2014 Contents 1.0 Solution Positioning... 3 1.1 For Service Providers... 3 1.2 For Enterprises... 3 2.0 Standard Services...
PROCE55 Mobile: Web API App. Web API. https://www.rijksmuseum.nl/api/...
 PROCE55 Mobile: Web API App PROCE55 Mobile with Test Web API App Web API App Example This example shows how to access a typical Web API using your mobile phone via Internet. The returned data is in JSON
PROCE55 Mobile: Web API App PROCE55 Mobile with Test Web API App Web API App Example This example shows how to access a typical Web API using your mobile phone via Internet. The returned data is in JSON
RESTful Application Protocols
 RESTful Application Protocols Ian Robinson http://iansrobinson.com @iansrobinson iansrobinson@gmail.com Who am I? Global Bank Integration REST in Practice: A Tutorial on Web- based Distributed Systems
RESTful Application Protocols Ian Robinson http://iansrobinson.com @iansrobinson iansrobinson@gmail.com Who am I? Global Bank Integration REST in Practice: A Tutorial on Web- based Distributed Systems
SECURE CODING ESSENTIALS
 SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
Create and Apply Clientless SSL VPN Policies for Accessing. Connection Profile Attributes for Clientless SSL VPN
 Create and Apply Clientless SSL VPN Policies for Accessing Resources, page 1 Connection Profile Attributes for Clientless SSL VPN, page 1 Group Policy and User Attributes for Clientless SSL VPN, page 3
Create and Apply Clientless SSL VPN Policies for Accessing Resources, page 1 Connection Profile Attributes for Clientless SSL VPN, page 1 Group Policy and User Attributes for Clientless SSL VPN, page 3
Nasuni Data API Nasuni Corporation Boston, MA
 Nasuni Corporation Boston, MA Introduction The Nasuni API has been available in the Nasuni Filer since September 2012 (version 4.0.1) and is in use by hundreds of mobile clients worldwide. Previously,
Nasuni Corporation Boston, MA Introduction The Nasuni API has been available in the Nasuni Filer since September 2012 (version 4.0.1) and is in use by hundreds of mobile clients worldwide. Previously,
Alpha College of Engineering and Technology. Question Bank
 Alpha College of Engineering and Technology Department of Information Technology and Computer Engineering Chapter 1 WEB Technology (2160708) Question Bank 1. Give the full name of the following acronyms.
Alpha College of Engineering and Technology Department of Information Technology and Computer Engineering Chapter 1 WEB Technology (2160708) Question Bank 1. Give the full name of the following acronyms.
BulkSMS Marketo Gateway
 BulkSMS Marketo Gateway Integration Guide Page 1 Contents Introduction... 4 About the BulkSMS Gateway for Marketo... 4 Advanced Group Messaging Key Features... 4 Use any or all of our other products and
BulkSMS Marketo Gateway Integration Guide Page 1 Contents Introduction... 4 About the BulkSMS Gateway for Marketo... 4 Advanced Group Messaging Key Features... 4 Use any or all of our other products and
Deployment Guide AX Series with Oracle E-Business Suite 12
 Deployment Guide AX Series with Oracle E-Business Suite 12 DG_OEBS_032013.1 TABLE OF CONTENTS 1 Introduction... 4 2 Deployment Prerequisites... 4 3 Oracle E-Business Topology... 5 4 Accessing the AX Series
Deployment Guide AX Series with Oracle E-Business Suite 12 DG_OEBS_032013.1 TABLE OF CONTENTS 1 Introduction... 4 2 Deployment Prerequisites... 4 3 Oracle E-Business Topology... 5 4 Accessing the AX Series
TWO-FACTOR AUTHENTICATION Version 1.1.0
 TWO-FACTOR AUTHENTICATION Version 1.1.0 User Guide for Magento 1.9 Table of Contents 1..................... The MIT License 2.................... About JetRails 2FA 4................. Installing JetRails
TWO-FACTOR AUTHENTICATION Version 1.1.0 User Guide for Magento 1.9 Table of Contents 1..................... The MIT License 2.................... About JetRails 2FA 4................. Installing JetRails
Application Security through a Hacker s Eyes James Walden Northern Kentucky University
 Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
TABLE OF CONTENTS. ICANN Pre- Delegation Testing System. A User s Guide. Release version May- 03
 ICANN Pre- Delegation Testing System A User s Guide Release version 1.5 2013- May- 03 TABLE OF CONTENTS 1 Introduction... 2 2 Activate your account and log in... 3 3 Application overview and status...
ICANN Pre- Delegation Testing System A User s Guide Release version 1.5 2013- May- 03 TABLE OF CONTENTS 1 Introduction... 2 2 Activate your account and log in... 3 3 Application overview and status...
Master Calendar Integrated Authentication Configuration Instructions. Dean Evans & Associates, Inc.
 Master Calendar Integrated Authentication Configuration Instructions Dean Evans & Associates, Inc. Copyright Copyright 2013 Dean Evans & Associates, Inc. All rights reserved. No part of this document may
Master Calendar Integrated Authentication Configuration Instructions Dean Evans & Associates, Inc. Copyright Copyright 2013 Dean Evans & Associates, Inc. All rights reserved. No part of this document may
Creating a Reimbursement Request
 Working with Reimbursement Requests Quick Start Guide If your organization is set up to use reimbursement requests, you can use Works to request a reimbursement for purchases you made with your personal
Working with Reimbursement Requests Quick Start Guide If your organization is set up to use reimbursement requests, you can use Works to request a reimbursement for purchases you made with your personal
Technical Note. Isilon OneFS. Isilon Swift Technical Note. Release number July, 2015
 Isilon OneFS Release number 7.2.0 Isilon Swift July, 2015 This section contains the following topics: Introduction... 2 Supported libraries and authentication methods... 2 Object data storage overview...
Isilon OneFS Release number 7.2.0 Isilon Swift July, 2015 This section contains the following topics: Introduction... 2 Supported libraries and authentication methods... 2 Object data storage overview...
GET /index.php HTTP/1.1 Host: User- agent: Mozilla/4.0
 State management GET /index.php HTTP/1.1 Host: www.mtech.edu User- agent: Mozilla/4.0 HTTP/1.1 200 OK Date: Thu, 17 Nov 2011 15:54:10 GMT Server: Apache/2.2.16 (Debian) Content- Length: 285 Set- Cookie:
State management GET /index.php HTTP/1.1 Host: www.mtech.edu User- agent: Mozilla/4.0 HTTP/1.1 200 OK Date: Thu, 17 Nov 2011 15:54:10 GMT Server: Apache/2.2.16 (Debian) Content- Length: 285 Set- Cookie:
OCLQS Portal ODJFS Add/Remove a System User
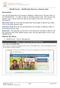 Description: OCLQS Portal ODJFS Add/Remove a System User This Job Aid describes the process of Adding or Removing a System User on the OCLQS Portal. In order to edit an existing system user, first remove
Description: OCLQS Portal ODJFS Add/Remove a System User This Job Aid describes the process of Adding or Removing a System User on the OCLQS Portal. In order to edit an existing system user, first remove
FortiBalancer 8.4 Web UI Handbook
 FortiBalancer 8.4 Web UI Handbook FortiBalancer 8.4 Web UI Handbook 18 March 2013 1 st Edition Copyright 2013 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, and FortiGuard are registered trademarks
FortiBalancer 8.4 Web UI Handbook FortiBalancer 8.4 Web UI Handbook 18 March 2013 1 st Edition Copyright 2013 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, and FortiGuard are registered trademarks
