8/19/2010. Computer Forensics File system forensics. Data analysis. Process of analysing data. Different layers of information.
|
|
|
- Christal Lewis
- 5 years ago
- Views:
Transcription
1 Computer Forensics File system forensics Thomas Mundt Data analysis Different layers of information. Application data analysis Swap space analysis File system analysis Database analysis Volume analysis Memory analysis Physical storage media analysis Network analysis Computer analysis 2 Process of analysing data HDD Physical media analysis Sectors Volume analysis Volume File system analysis File Application analysis 3 1
2 General guidelines Copy important data, put the original data in a safe place. Problems: Bad sectors, internal structure not always accessable. Use write blocking device for copying. Analyse the copy. Calculate hash values (eg. SHA-1) to prove that the data has not changed. Minimize write access when performing a live analysis. Prevent change of access times. Prevent any write operation because they could overwrite evidence in unallocated space. 4 General guidelines Isolate the analysis environment from both the suspect data and the network environment (internet etc.). Minimal system or virtual system (which can be reset to an initial state very easily). Isolation is impossible when analysing a live system. Correlate data with other independent sources. Log and document all own activities. 5 Data organization Remember Binary storage of information / data formats for INT, DOUBLE etc. Encoding of characters (eg. ASCII, ISO , UTF-8 etc.) Unicode v. 4.0 supports over 96,000 different characters Internationalization and different conventions (see 96,000 above, where the comma delimits between every thousands). Big endian / little endian. 6 2
3 Example UTF-32 stores each character as a 4-byte value. UTF-16 stores most heavily used characters in a 2-byte value and the lesser-used in a 4-byte value. UTF-8 uses 1, 2, or 4 bytes. 7 Example thm$ hexdump -C L2\ -\ File\ System\ Forensics.pptx b e PK...!..n c0 2a a e b 43.*...n...[C f 6e e 74 5f d 2e 78 6d ontent_types].xm c 20 a a l...( ASCII interpretation of the dumped data. 8 Data structures Layout of data is sometimes unclear because data are not generally preceded with data type and meaning. Example thm$ hexdump C xxx.db d e e Main St bit integer for number. 14 char (ASCII) for name of street is little endian (in this particular case). Need to know the structure of all data. 9 3
4 Data structures Most forensic data is stored on hard disc drives. In commercial use since Capacity increasing. 10 IDE HDD 11 Magnetic storage 12 4
5 Cylinder heads sectors blocks 13 ATA / SATA 14 SCSI 15 5
6 Types of sector addresses Each block typically consists of 512bytes CHS Cylinder Heads Sectors. ATA specification defines16bit cylinder value, 4bit head value, and 8bit sector value. BIOS use 10bit cylinder value, 8bit head value. And 6bit sector value. 1024*16*63*512byte = 504MiB limit for HDDs. LBA Logical Block Addressing LBA = (((C* heads_per_cyl) + H) * sectors_per_track) + S 1 Both methods are still in use. 16 Challenges when examining HDDs Encryption. Unknown file systems. Hidden information. Internal configuration of HDDs, such as dead sector mapping. 17 Hard disk passwords ATA-3 spec introduced optional security features. Passwords can be set to lock the HDD against reading / writing. Data recovery is still possible by opening the disk. 18 6
7 Host protected area HPA was added in ATA-4 spec. Computer vendors can store data that would not be erased when a user formats the HDD. 0 GB 199 GB 200 GB User addressable sectors HPA 19 Device configuration overlay DCO was added in ATA-6. DCO hides additional sectors at the end of disk. 0 GB 199 GB 200 GB 202 GB User addressable sectors HPA DCO 20 Bad sector mapping When a hard disk is manufactured, there are areas on the platter that have bad sectors. During the final test phases of a hard disk, the platters are scanned at the factory and the bad sectors are mapped out - these are generally called 'Primary Defects'. All modern drive have a spare sector pool. 21 7
8 BIOS versus direct access. Direct access to controller enables the OS to operate in special modes (LBA). BIOS access to controller uses software interrupt command 0x13 (INT13h CHS or extended INT13h with 64-bit LBA). 22 SCSI versus ATA SCSI is a different interface standard, usually found in servers. SCSI uses a bus and spec does not know a controller. Instead a bus system is used. Driver addresses each device. 23 Data acquisition Copying to keep the original untouched throughout the entire process of analysis. Write blockers are frequently used to prevent changes. Steps Reading the source data. Raw copy vs. copy on file level. Copying HPA and DCO (and possible bad blocks). Error handling (errors on sector level for instance could be logged and copied as zeros). Writing the data. To an image file. To another medium. 24 8
9 Tools DriveID diskstat from The Sleuth Kit hpa 25 Write blockers Hardware write blockers ATA / SCSI / Firewire commands are checked and only accepted when on a list of no-write-commands. Software write blockers Modified INT13h handler. Modified direct access drivers. 26 Image files Stores the entire partition / HDD (including HPA). Some image file formats are able to handle relocated data (bad blocks). Wiping the disk before writing image file, so that investigator can more easily testify that there could not have been any contamination. Different image file formats Raw image contains only the data from the source device. Embedded image contains data from the source device and descriptive data such as hash values, dates, and times. 27 9
10 Volume analysis A volume is a collection of addressable sectors that an operating system can use for data storage. Sectors in a volume need not to be consecutive on a physical storage device. A volume may also be the result of assembling smaller volumes. A partition is a special volume. It is a collection of consecutive sectors in a volume. 28 Partitions Usage File systems smaller than HDD. Storage of RAM content for sleep. Swap partition for OS that use memory pages. Each OS typically uses a different partitioning method. A table stores starting sector, ending sector, and type of partition. 29 Partitions Start End Type NTFS FAT Linux Partition 1 Partition 2 Partition
11 Example Partition 1 Partition 2 HDD volume 1 Partition 3 HDD volume 2 Partition 4 Partition 5 Intermediate volume FS volume File system volume 31 Example RAID Investigating a system with a RAID volume can be very difficult. Need to collect all devices. Hardware RAID is not fully standardized. 32 RAID 33 11
12 RAID Analysis basics Basic theory is very simple. Locate the partion tables. Process them. Identify disk layout. Layout is used in a file system analysis. In some cases data outside partitions needs to be extracted. File system defines where data is located. In some cases data outside user accessable files needs to be extracted
13 Partion tables Consistency checks Valid Invalid Partition 1 Partition 2 Partition 3 Partition2 Partition1 37 Recovering deleted partitions A common technique that is used to thwart a forensic investigation is to repartition a disk. Similar problem is to recover a disk whose partition table has become corrupt. Some hints remain, for example FAT system has a field in each sector that identifies how many sectors are in a cluster, value is a power of 2. Any other value would indicate that the sector was not part of a FAT file system. Some file systems use specific magic signatures (FAT, for instance, has 0x55 and 0xAA in bytes 510 and 511 of the first sector). 38 Recovering deleted partitions Other tools use heuristics
14 PC based partitions DOS-style partitions (IA32). Apple partitions. Removable media. 40 DOS partitions No standard reference, no standard name. Many documents that discuss those partitions. Used by Windows and most LINUX and FreeBSD systems. Since Windows 2000 Microsoft differentiates between basic and dynamic disks. A basic disk refers to MBR or GPT disks, which are standalone. Dynamic disks can be combined and merged. 41 DOS partitions Microsoft calls disks using this type of partition Master Boot Record (MBR) disks. IA64 and Extensible Firmware Interface (substitute for BIOS) use GUID partition tables (GPT)
15 Basic MBR concepts A disk using DOS partitions has an MBR in the first 512- byte sector. The MBR contains boot code, a partition table, and a signature value. The boot code contains instructions that tell the computer how to process the partition table and locate the operating system on the partition marked as active. 43 Basic MBR concepts Partition table has four entries, each can describe a DOS partition. Each entry consists of Starting CHS address. Ending CHS address. Starting LBA address. Number of sectors in partition. Type of partition. Flags. 44 Type of DOS partitions 0 Empty 1e Hidden W95 FAT1 80 Old Minix bf Solaris 1 FAT12 24 NEC DOS 81 Minix / old c1 DRDOS/sec Lin (FAT- 2 XENIX root 39 Plan 9 82 Linux swap / So c4 DRDOS/sec (FAT- 3 XENIX usr 3c PartitionMagic 83 Linux c6 DRDOS/sec (FAT- 4 FAT16 <32M 40 Venix OS/2 hidden c7 Syrinx C: 5 Extended 41 PPC PReP Boot 85 Linux extended da Non-FS data 6 FAT16 42 SFS 86 NTFS volume set db CP/M / CTOS /. 7 HPFS/NTFS 4d QNX4.x 87 NTFS volume set de Dell Utility 8 AIX 4e QNX4.x 88 Linux plaintext df BootIt 2nd part 9 AIX 4f QNX4.x 3rd part 8e Linux LVM e1 DOS access bootable a OS/2 Boot Manag 50 OnTrack DM 93 Amoeba e3 DOS R/O b W95 FAT32 51 OnTrack DM6 94 Amoeba e4 SpeedStor Aux BBT c W95 FAT32 52 CP/M 9f BSD/OS eb BeOS fs (LBA) e W95 FAT16 (LBA) 53 OnTrack DM6 Aux a0 IBM Thinkpad hi ee EFI GPT f W95 Ext'd (LBA) 54 OnTrackDM6 a5 FreeBSD ef EFI (FAT-12/16/ 10 OPUS 55 EZ-Drive a6 OpenBSD f0 Linux/PA-RISC b 11 Hidden FAT12 56 Golden Bow a7 NeXTSTEP f1 SpeedStor 12 Compaq diagnost 5c Priam Edisk a8 Darwin UFS f4 SpeedStor 14 Hidden FAT16 <3 61 SpeedStor a9 NetBSD f2 DOS secondary 16 Hidden FAT16 63 GNU HURD or ab Darwin boot fb VMware VMFS Sys 17 Hidden HPFS/NTF 64 Novell Netware b7 BSDI fs fc VMware VMKCORE 18 AST SmartSleep 65 Novell Netware b8 BSDI swap fd Linux raid auto 1b Hidden W95 FAT3 70 DiskSecure Mult bb Boot Wizard hid fe LANstep 1c Hidden W95 FAT3 75 PC/IX be Solaris boot ff BBT 45 15
16 Extended partition concepts MBR is a simple method allowing up to four partitions. More partitions can be defined by creating an extended partition. Partition 1 Partition 2 Partition 3 Extended partition 46 Extended partitions Extended partition Partition 4 Partition 5 Partition 6 47 Example 48 16
17 Apple partitions Apple partitions are described in the partition map structure, which is located at the beginning of the disk. No boot code necessary, all in firmware. First entry defines maximum size of the partition map. 49 Apple partion map entry Byte Range Description Essential 0-1 Signature value (Ox504D) No 2-3 Reserved No 4-7 Total Number of partitions Yes 8-11 Starting sector of partition Yes Size of partition in sectors Yes Name of partition in ASCII No Type of partition in ASCII No Starting sector of data area in partition No Size of data area in sectors. No Status of partition (see table 5-8) No Starting sector of boot code No Size of boot code in sectors No Address of boot loader code No Reserved No Boot code entry point No Reserved No Boot code checksum No Processor type No Reserved No 50 Example Apple partition map Slot Start End Length Description 00: Unallocated 01: Apple_partition_map 02: Table 03: Unallocated 04: Apple_Driver43 05: Apple_Driver43 06: Apple_Driver_ATA 07: Apple_Driver_ATA 08: Apple_FWDriver 09: Apple_Driver_IOKit 10: Apple_Patches 11: Apple_HFS 12: Apple_Free 51 17
18 Removable media Most removable medai also have partitions. They use the same structures that HDDs use. Floppy disks are formatted for FAT12. They do not have a partition table, the entire disk is treated like a single partition. CDs use ISO 9660, Joliet, or even Apple HFS+ format. Recordable CDs have a notion of a session. Each session could be considered as a single partition. 52 BSD partitions FreeBSD uses DOS partitions and BSD partitions together. BSD partitions (UFS) are defined inside a BSD DOS partition. BSD uses partition tables. 53 BSD partitions NetBSD / OpenBSD partitions are also located inside a DOS partition (on IA32 systems). Partitions can be located anywhere on the disk
19 Logical Volume Manager LVM DOS partitions (type 0x8e) are devided into physical extents. A logical volume is made up of logical extents. Configuration files are stored in on both the local file system and the disks / partitions. 55 File system analysis After analysing the partition structure the file system inside the partition has to be analysed. A file system porovides a mechanism for users to store data in a hierarchy. A filesystem connects files with the sectors of a storage media. It adds meta-data to the file (dates, rights etc.) 56 Logical file system address File systems use logical volume addresses and assign logical file system addresses. Logical volume addresses are relative to the start of the volume. In some file systems every sector in the volume is assigned to a logical file system address
20 Logical file address Logical file address is relative to the start of a file. 58 Slack space Slack space occurs when the size of a file is not a multiple of a data unit. A file must allocate a full data unit. DOS and early Windows fill slack space with data from memory. Some Oses wipe empty sectors, others ignore them. 59 Allocation strategies Typically, an OS allocates consecutive data units. This is not always possible. Deleted files leave a hole. Results in fragmentation. Strategies are First available. Next available. Best fit or mimumum free space. Maximum free space
21 Sparse files Sparse files attemt to store data more efficiently. Empty blocks are not physically allocated. Most modern file systems (NTFS, ext3/4 support sparse files) 61 FAT Used by many (all) Microsoft Operating Systems. Also used by most flash memory devices (USB, Compact Flash). Every file and directory is allocated a directory entry. Content is stored in clusters. 62 FAT file system layout 63 21
22 FAT example 64 FAT cluster address of first cluster In FAT12/16, cluster 2 follows the root directory, in FAT32 cluster 2 is the first sector of the data area. 65 FAT allocation algorithms Most Oses seem to use next available algorithm for allocation of a cluster
23 FAT directory entry Byte Description 0-0 First character of file name in ASCII and allocation status (Oxe5 or OxOO if unallocated) 1-10 Characters 2 to 11 of file name in ASCII File Attributes Reserved Created time (tenths of second) Created time (hours, minutes, seconds) Created day Accessed day High 2 bytes of first cluster address (0 for FAT12 and FATl6) Written time (hours, minutes, seconds) Written day Low 2 bytes of first cluster address Size of file (0 for directories) 67 FAT dates 68 FAT times 69 23
24 Flag values Flag value Description Essential (0x01) Read only No (0x02) Hidden file No (0x04) System file No (0x08) Volume label Yes (0x0f) Long file name Yes (0x10) Directory Yes (0x20) Archive No 70 NTFS New Technology File System. Used by all modern versions of Windows. Badly documented by Microsoft. Open source teams re-engineered the file system now available for Unix / MacOS etc. 71 NTFS Every information about files and directories is stored in the Master File Table (and a backup copy of it). Each MFT entry is given an address. All entries have been 1024 bytes in size (exact size is defined in the boot sector). NTFS uses clusters
25 MFT 73 NFTS The first 16 MFT entries are reserved for file system metadata files (readable in the root directory, but usually hidden from the user). 74 NTFS file system metadata files Entry File Name Description $MFT The entry for the MFT itself. $MFTMirr Contains a backup of the first entries in the MFT. $LogFile Contains the journal that records the metadata transactions. $Volume Contains the volume information such as the label, identifier, and version. $AttrDef Contains the attribute information, such as the identifier values, name, and sizes.. Contains the root directory of the file system. $Bitmap Contains the allocation status of each cluster in the file system. $Boot Contains the boot sector and boot code for the file system. $Baddus Contains the clusters that have bad sectors. $Secure Contains information about the security and access control for the files (Windows 2000 and XP version only). $Upcase Contains the uppercase version of every Unicode character. $Extend A directory that contains files for optional extensions. Microsoft does not typically place the files in this 75 directory into the reserved MFT entries. 25
26 Typical file systems exist to read and write file content, but NTFS exists to read and write attributes, one of which contains file content. 76 Name $STANDARD_INFORMATION $ATTRIBUTE_LIST $FILE_NAME $VOLUME_VERSION $OBJECT_ID $SECURITY_DESCRIPTOR $VOLUME_NAME $VOLUME_INFORMATION $DATA $INDEX_ROOT $INDEX_ALLOCATION $BITMAP 77 Description General information, such as flags; the last accessed, written, and created times; and the owner and security ID. List where other attributes for ftle can be found. File name, in Unicode, and the last accessed, written, and created times. Volume information. A 16-byte unique identifier for the file or directory. The access control and security properties of the file. Volume name. File system version and other flags. File contents. Root node of an index tree. Nodes of an index tree rooted in $INDEX_ROOT attribute. A bitmap for the $MFT file and for indexes
27 NTFS and sparse files 79 NTFS and sparse files 80 B-Tree NTFS uses B-Trees for indexing
28 Allocation NTFS implementations seem to use the best-fit algorithm on most implementations. 82 NTFS example 83 NTFS example 84 28
29 ext2 / ext3 / extx Derived from UFS. Used by a variety of Linux distributions as default file system. Many optional features. Journaling. Sparse files. Large files (>4GB). Implementation depends on Linux distribution (or even the currently installed kernel features). 85 extx concepts / example Super block (equivalent to boot sector) contains information about the file system. 86 extx concepts / example File system is devided into groups, each group has the same layout. Files are supposed to be stored in the same block group, when they belong together (avoids the HDDs heads to be moved too much)
30 extx concepts / example Every block group contains a backup copy of the super block and the group description table. 88 extx concepts / example Meta information is stored in inodes. Each inode represents one file. 89 extx concepts / example Bigger files are adressed indirectly by using blocks to link to further data content
31 extx concepts / example Directory entries contain the file name and inode. They also contain a pointer to the next entry. Unused entries are skipped over by increasing the pointer of the previous entry. 91 Countermeasures and problems Wiping. Encryption. Compression. 92 Plausible deniability Deniability is the avoidance of being blamed to know something / to possess somthing / to have something done. Plausible Deniability means that there is no way to prove that someone has knowledge / did something. Plausibility is the key concept of plausible deniability Often used in politics / espionage / business 93 31
32 Reasons Prosecutor (or similar entity such as journalist) cannot prove that information is present (at least beyond reasonable doubt) Some countries changed rules regarding encrypted material UK law enformecment officers can require the disclosure of keys Regulation of Investigatory Powers Act Part III - Investigation of electronic data protected by encryption etc. - Power to require disclosure 94 Methods No written documents Verbal agreements beside written documents 95 Presence of information What is information? Shannon: Frequently the messages have meaning; that is they refer to or are correlated according to some system with certain physical or conceptual entities. These semantic aspects of communication are irrelevant to the engineering problem. The significant aspect is that the actual message is one selected from a set of possible messages. The choice of a logarithmic base corresponds to the choice of a unit for measuring information. If the base 2 is used the resulting units may be called binary digits, or more briefly bits, a word suggested by J. W. Tukey. A device with two stable positions, such as a relay or a flip-flop circuit, can store one bit of information. N such devices can store N bits The Bell System Technical Journal, Vol. 27, p. 379, (July 1948)
33 Data, Information, Knowledge Data is the lowest level of abstraction, information is the next level, and finally, knowledge is the highest level among all three. Is this data? Is this information? 69ba 90eb 44a e0e4 1d8c 9fb ed5a 967f c4e2 78ac 2d56 7e05 152f 1ba0 bf37 61d1 b564 cc7b 22dd 1828 c9cd ba14 d130 2f9c 6fe b1ad 3afd 9ee8 4fb7 6fd2 f835 f656 76e6 1f12 a38c 76cc d4cf 336b 1afe f018 9e44 ef00 26bb 97 Information Is this information? -bash-3.2$ hexdump /dev/urandom 69ba 90eb 44a e0e4 1d8c 9fb ed5a 967f c4e2 78ac 2d56 7e05 152f 1ba0 bf37 61d1 b564 cc7b 22dd 1828 c9cd ba14 d130 2f9c 6fe b1ad 3afd 9ee8 4fb7 6fd2 f835 f656 76e6 1f12 a38c 76cc d4cf 336b 1afe f018 9e44 ef00 26bb 98 Implementation 1st step encrypted volumes 2nd step hidden volumes 3rd step hidden volume inside encrypted cover volume No part of the hidden volume can be distinguished from random data (they pass the chi-square-randomness test) Tools FreeOTFE ToolCrypt 99 33
34 Implementation From TrueCrypt Documentation 100 Cryptography Volumes are encrypted with a key depending on the user s password. 101 Problems Random Number Generator needed to deliver background noise Header structures Traces in RAM / Swap files / Paging files / Hibernation files Malware Relocated sectors Hard disks Special wear leveling file systems Journaling file systems
35 Random Number Generator Needs to be non-deterministic Has to pass chi-square-randomness test 103 Header structures All information needs to be encrypted The entire volume needs to look chaotic 104 Page files Encryption tools need to lock their memory from paging Tools cannot guarantee that user process will not store unencrypted data in a paging file
36 Hibernation files Tools cannot control creation of hibernation files (suspend to disk) Entire content of RAM is written to file Tools could put hibernation files in an encrypted volume Secure operating systems needed 106 Dump files Operating system might create a dump of memory onto hard disk Preventing OS to do so needs to be configured 107 RAM Tools cannot guarantee that RAM is being copied during operation Physical security is needed
37 Wear leveling / sector relocation / Journaling file systems Tools cannot guarantee that data is really overwritten Avoid wear those file systems Journalling Flash File System jffs 109 Further problems Changing passwords Backup Copied volumes (brute force against passwords)
jfield Documentation Release 1 Jason Field
 jfield Documentation Release 1 Jason Field Oct 25, 2017 Contents 1 linux 3 1.1 LVM................................................... 3 1.1.1 Create.............................................. 3 1.1.2
jfield Documentation Release 1 Jason Field Oct 25, 2017 Contents 1 linux 3 1.1 LVM................................................... 3 1.1.1 Create.............................................. 3 1.1.2
Using iscsi On Debian Lenny (Initiator And Target)
 By Falko Timme Published: 2009-03-10 20:05 Using iscsi On Debian Lenny (Initiator And Target) Version 1.0 Author: Falko Timme Last edited 02/24/2009 This guide explains how
By Falko Timme Published: 2009-03-10 20:05 Using iscsi On Debian Lenny (Initiator And Target) Version 1.0 Author: Falko Timme Last edited 02/24/2009 This guide explains how
List of partition identifiers for Pcs
 List of partition identifiers for Pcs ID Name 00 Empty 01 DOS 12-bit FAT 02 XENIX root 03 XENIX /usr 04 DOS 3.0+ 16-bit FAT (up to 32M) 05 DOS 3.3+ Extended Partition 06 DOS 3.31+ 16-bit FAT (over 32M)
List of partition identifiers for Pcs ID Name 00 Empty 01 DOS 12-bit FAT 02 XENIX root 03 XENIX /usr 04 DOS 3.0+ 16-bit FAT (up to 32M) 05 DOS 3.3+ Extended Partition 06 DOS 3.31+ 16-bit FAT (over 32M)
Chapter Two File Systems. CIS 4000 Intro. to Forensic Computing David McDonald, Ph.D.
 Chapter Two File Systems CIS 4000 Intro. to Forensic Computing David McDonald, Ph.D. 1 Learning Objectives At the end of this section, you will be able to: Explain the purpose and structure of file systems
Chapter Two File Systems CIS 4000 Intro. to Forensic Computing David McDonald, Ph.D. 1 Learning Objectives At the end of this section, you will be able to: Explain the purpose and structure of file systems
파일 : E:\ghcstop\AESOP_ghcstop_doc\usb_gadget\S3C2410_S3C2440_2.6.13_usb_gadget_howto.txt , 2:30:10 오후
 linux kernel 2.6.13 usb le-storage gadget howto - 2005.12.26 - http://www.aesop-embedded.org - godori usb_gadget_1.txt 파일을수정한것이다. 참고할것. * usb le-storage gadget 이란 usb device 를가지고있는 cpu
linux kernel 2.6.13 usb le-storage gadget howto - 2005.12.26 - http://www.aesop-embedded.org - godori usb_gadget_1.txt 파일을수정한것이다. 참고할것. * usb le-storage gadget 이란 usb device 를가지고있는 cpu
Advanced Operating Systems
 Advanced Operating Systems File Systems: File Allocation Table, Linux File System, NTFS Lecture 10 Case Studies of File Systems File Allocation Table (FAT) Unix File System Berkeley Fast File System Linux
Advanced Operating Systems File Systems: File Allocation Table, Linux File System, NTFS Lecture 10 Case Studies of File Systems File Allocation Table (FAT) Unix File System Berkeley Fast File System Linux
o o o o /dev/hdx /dev/sdx fdisk m
 /dev/sdx /dev/hdx rt@debian:~# fdisk -l Disk /dev/sdb: 8 GiB, 8589934592 bytes, 16777216 sectrs Disk /dev/sda: 10 GiB, 10737418240 bytes, 20971520 sectrs Disklabel type: ds Disk identifier: 0x717aa925
/dev/sdx /dev/hdx rt@debian:~# fdisk -l Disk /dev/sdb: 8 GiB, 8589934592 bytes, 16777216 sectrs Disk /dev/sda: 10 GiB, 10737418240 bytes, 20971520 sectrs Disklabel type: ds Disk identifier: 0x717aa925
CSN08101 Digital Forensics. Module Leader: Dr Gordon Russell Lecturers: Robert Ludwiniak
 CSN08101 Digital Forensics Lecture 8: File Systems Module Leader: Dr Gordon Russell Lecturers: Robert Ludwiniak Objectives Investigative Process Analysis Framework File Systems FAT NTFS EXT2/EXT3 last
CSN08101 Digital Forensics Lecture 8: File Systems Module Leader: Dr Gordon Russell Lecturers: Robert Ludwiniak Objectives Investigative Process Analysis Framework File Systems FAT NTFS EXT2/EXT3 last
Introduction to Volume Analysis, Part I: Foundations, The Sleuth Kit and Autopsy. Digital Forensics Course* Leonardo A. Martucci *based on the book:
 Part I: Foundations, Introduction to Volume Analysis, The Sleuth Kit and Autopsy Course* Leonardo A. Martucci *based on the book: File System Forensic Analysis by Brian Carrier LAM 2007 1/12h Outline Part
Part I: Foundations, Introduction to Volume Analysis, The Sleuth Kit and Autopsy Course* Leonardo A. Martucci *based on the book: File System Forensic Analysis by Brian Carrier LAM 2007 1/12h Outline Part
Vorlesung Computerforensik. Kapitel 7: NTFS-Analyse
 Harald Baier FAT-Analyse / SS 2016 1/64 Vorlesung Computerforensik Kapitel 7: NTFS-Analyse Harald Baier Hochschule Darmstadt, CRISP SS 2016 Harald Baier FAT-Analyse / SS 2016 2/64 General information about
Harald Baier FAT-Analyse / SS 2016 1/64 Vorlesung Computerforensik Kapitel 7: NTFS-Analyse Harald Baier Hochschule Darmstadt, CRISP SS 2016 Harald Baier FAT-Analyse / SS 2016 2/64 General information about
File System Case Studies. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
Digital Forensics Lecture 02- Disk Forensics
 Digital Forensics Lecture 02- Disk Forensics Hard Disk Data Acquisition Akbar S. Namin Texas Tech University Spring 2017 Analysis of data found on a storage device It is more common to do dead analysis
Digital Forensics Lecture 02- Disk Forensics Hard Disk Data Acquisition Akbar S. Namin Texas Tech University Spring 2017 Analysis of data found on a storage device It is more common to do dead analysis
GJU IT-forensics course. Storage medium analysis
 Harald Baier Storage medium analysis / 2014-04-02 1/32 GJU IT-forensics course Storage medium analysis Harald Baier Hochschule Darmstadt, CASED 2014-04-02 Partitions Harald Baier Storage medium analysis
Harald Baier Storage medium analysis / 2014-04-02 1/32 GJU IT-forensics course Storage medium analysis Harald Baier Hochschule Darmstadt, CASED 2014-04-02 Partitions Harald Baier Storage medium analysis
On-disk filesystem structures
 On-disk filesystem structures Jan van Wijk Filesystem on-disk structures for FAT, HPFS, NTFS, JFS, EXTn and ReiserFS Presentation contents Generic filesystem architecture (Enhanced) FAT(32), File Allocation
On-disk filesystem structures Jan van Wijk Filesystem on-disk structures for FAT, HPFS, NTFS, JFS, EXTn and ReiserFS Presentation contents Generic filesystem architecture (Enhanced) FAT(32), File Allocation
Operating Systems. Lecture File system implementation. Master of Computer Science PUF - Hồ Chí Minh 2016/2017
 Operating Systems Lecture 7.2 - File system implementation Adrien Krähenbühl Master of Computer Science PUF - Hồ Chí Minh 2016/2017 Design FAT or indexed allocation? UFS, FFS & Ext2 Journaling with Ext3
Operating Systems Lecture 7.2 - File system implementation Adrien Krähenbühl Master of Computer Science PUF - Hồ Chí Minh 2016/2017 Design FAT or indexed allocation? UFS, FFS & Ext2 Journaling with Ext3
File Systems. What do we need to know?
 File Systems Chapter 4 1 What do we need to know? How are files viewed on different OS s? What is a file system from the programmer s viewpoint? You mostly know this, but we ll review the main points.
File Systems Chapter 4 1 What do we need to know? How are files viewed on different OS s? What is a file system from the programmer s viewpoint? You mostly know this, but we ll review the main points.
File System Case Studies. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
COMP091 Operating Systems 1. File Systems
 COMP091 Operating Systems 1 File Systems Media File systems organize the storage space on persistent media such as disk, tape, CD/DVD/BD, USB etc. Disk, USB drives, and virtual drives are referred to as
COMP091 Operating Systems 1 File Systems Media File systems organize the storage space on persistent media such as disk, tape, CD/DVD/BD, USB etc. Disk, USB drives, and virtual drives are referred to as
Hard Disk Organization. Vocabulary
 Hard Disk Organization Vocabulary Platter: one ceramic plate, covered with magnetizable film where the bits are actually stored. Both sides of a platter can be used. Increasing the number of platters is
Hard Disk Organization Vocabulary Platter: one ceramic plate, covered with magnetizable film where the bits are actually stored. Both sides of a platter can be used. Increasing the number of platters is
File Management. Ezio Bartocci.
 File Management Ezio Bartocci ezio.bartocci@tuwien.ac.at Cyber-Physical Systems Group Institute for Computer Engineering Faculty of Informatics, TU Wien Motivation A process can only contain a limited
File Management Ezio Bartocci ezio.bartocci@tuwien.ac.at Cyber-Physical Systems Group Institute for Computer Engineering Faculty of Informatics, TU Wien Motivation A process can only contain a limited
Typical File Extensions File Structure
 CS 355 Operating Systems File Systems File Systems A file is a collection of data records grouped together for purpose of access control and modification A file system is software responsible for creating,
CS 355 Operating Systems File Systems File Systems A file is a collection of data records grouped together for purpose of access control and modification A file system is software responsible for creating,
File Systems. Martin Děcký. DEPARTMENT OF DISTRIBUTED AND DEPENDABLE SYSTEMS
 File Systems Martin Děcký DEPARTMENT OF DISTRIBUTED AND DEPENDABLE SYSTEMS http://d3s.mff.cuni.cz/ CHARLES UNIVERSITY IN PRAGUE FACULTY OF MATHEMATICS AND PHYSICS MS-DOS FAT History 1977 1996 FAT32 FAT12
File Systems Martin Děcký DEPARTMENT OF DISTRIBUTED AND DEPENDABLE SYSTEMS http://d3s.mff.cuni.cz/ CHARLES UNIVERSITY IN PRAGUE FACULTY OF MATHEMATICS AND PHYSICS MS-DOS FAT History 1977 1996 FAT32 FAT12
ECE 598 Advanced Operating Systems Lecture 14
 ECE 598 Advanced Operating Systems Lecture 14 Vince Weaver http://www.eece.maine.edu/~vweaver vincent.weaver@maine.edu 19 March 2015 Announcements Homework #4 posted soon? 1 Filesystems Often a MBR (master
ECE 598 Advanced Operating Systems Lecture 14 Vince Weaver http://www.eece.maine.edu/~vweaver vincent.weaver@maine.edu 19 March 2015 Announcements Homework #4 posted soon? 1 Filesystems Often a MBR (master
Acronis Disk Director 11 Home. Quick Start Guide
 Acronis Disk Director 11 Home Quick Start Guide Copyright Acronis, Inc., 2000-2010. All rights reserved. "Acronis", "Acronis Compute with Confidence", "Acronis Recovery Manager", "Acronis Secure Zone",
Acronis Disk Director 11 Home Quick Start Guide Copyright Acronis, Inc., 2000-2010. All rights reserved. "Acronis", "Acronis Compute with Confidence", "Acronis Recovery Manager", "Acronis Secure Zone",
Booting, Partitioning and File Systems. Part I. Booting and hard disks. Booting. Table of Contents. Nothing is what it seems.
 Booting, Partitioning and File Systems Nothing is what it seems Karst Koymans Part I Booting and hard disks Informatics Institute University of Amsterdam (version 1.7, 2010/10/10 12:32:58) Friday, October
Booting, Partitioning and File Systems Nothing is what it seems Karst Koymans Part I Booting and hard disks Informatics Institute University of Amsterdam (version 1.7, 2010/10/10 12:32:58) Friday, October
CHAPTER 11: IMPLEMENTING FILE SYSTEMS (COMPACT) By I-Chen Lin Textbook: Operating System Concepts 9th Ed.
 CHAPTER 11: IMPLEMENTING FILE SYSTEMS (COMPACT) By I-Chen Lin Textbook: Operating System Concepts 9th Ed. File-System Structure File structure Logical storage unit Collection of related information File
CHAPTER 11: IMPLEMENTING FILE SYSTEMS (COMPACT) By I-Chen Lin Textbook: Operating System Concepts 9th Ed. File-System Structure File structure Logical storage unit Collection of related information File
21/02/2012. BIOS and boot process Storage devices Partitions. CSN08101 Digital Forensics Lecture 5A: PC Boot Sequence and Storage Devices.
 CSN08101 Digital Forensics Lecture 5A: PC Boot Sequence and Storage Devices Module Leader: Dr Gordon Russell Lecturers: Robert Ludwiniak Objectives BIOS and boot process Storage devices Partitions Computer
CSN08101 Digital Forensics Lecture 5A: PC Boot Sequence and Storage Devices Module Leader: Dr Gordon Russell Lecturers: Robert Ludwiniak Objectives BIOS and boot process Storage devices Partitions Computer
UNIX File Systems. How UNIX Organizes and Accesses Files on Disk
 UNIX File Systems How UNIX Organizes and Accesses Files on Disk Why File Systems File system is a service which supports an abstract representation of the secondary storage to the OS A file system organizes
UNIX File Systems How UNIX Organizes and Accesses Files on Disk Why File Systems File system is a service which supports an abstract representation of the secondary storage to the OS A file system organizes
412 Notes: Filesystem
 412 Notes: Filesystem A. Udaya Shankar shankar@cs.umd.edu December 5, 2012 Contents 1 Filesystem interface 2 2 Filesystem implementation 3 3 FAT (mostly from Wikepedia) 5 4 UFS (mostly from Wikepedia)
412 Notes: Filesystem A. Udaya Shankar shankar@cs.umd.edu December 5, 2012 Contents 1 Filesystem interface 2 2 Filesystem implementation 3 3 FAT (mostly from Wikepedia) 5 4 UFS (mostly from Wikepedia)
Operating Systems. Operating Systems Professor Sina Meraji U of T
 Operating Systems Operating Systems Professor Sina Meraji U of T How are file systems implemented? File system implementation Files and directories live on secondary storage Anything outside of primary
Operating Systems Operating Systems Professor Sina Meraji U of T How are file systems implemented? File system implementation Files and directories live on secondary storage Anything outside of primary
OPERATING SYSTEMS CS136
 OPERATING SYSTEMS CS136 Jialiang LU Jialiang.lu@sjtu.edu.cn Based on Lecture Notes of Tanenbaum, Modern Operating Systems 3 e, 1 Chapter 4 FILE SYSTEMS 2 File Systems Many important applications need to
OPERATING SYSTEMS CS136 Jialiang LU Jialiang.lu@sjtu.edu.cn Based on Lecture Notes of Tanenbaum, Modern Operating Systems 3 e, 1 Chapter 4 FILE SYSTEMS 2 File Systems Many important applications need to
CS370 Operating Systems
 CS370 Operating Systems Colorado State University Yashwant K Malaiya Spring 2018 Lecture 22 File Systems Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 Disk Structure Disk can
CS370 Operating Systems Colorado State University Yashwant K Malaiya Spring 2018 Lecture 22 File Systems Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 Disk Structure Disk can
File System Interpretation
 File System Interpretation Part III. Advanced Techniques and Tools for Digital Forensics CSF: Forensics Cyber-Security Fall 2018 Nuno Santos Previously: Introduction to Android forensics! How does Android
File System Interpretation Part III. Advanced Techniques and Tools for Digital Forensics CSF: Forensics Cyber-Security Fall 2018 Nuno Santos Previously: Introduction to Android forensics! How does Android
File system internals Tanenbaum, Chapter 4. COMP3231 Operating Systems
 File system internals Tanenbaum, Chapter 4 COMP3231 Operating Systems Architecture of the OS storage stack Application File system: Hides physical location of data on the disk Exposes: directory hierarchy,
File system internals Tanenbaum, Chapter 4 COMP3231 Operating Systems Architecture of the OS storage stack Application File system: Hides physical location of data on the disk Exposes: directory hierarchy,
makes floppy bootable o next comes root directory file information ATTRIB command used to modify name
 File Systems File system o Designed for storing and managing files on disk media o Build logical system on top of physical disk organization Tasks o Partition and format disks to store and retrieve information
File Systems File system o Designed for storing and managing files on disk media o Build logical system on top of physical disk organization Tasks o Partition and format disks to store and retrieve information
File System Case Studies. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
File Systems and Volumes
 File Systems and Volumes Section II. Basic Forensic Techniques and Tools CSF: Forensics Cyber-Security MSIDC, Spring 2015 Nuno Santos Summary! Data organization in storage systems! File deletion and recovery!
File Systems and Volumes Section II. Basic Forensic Techniques and Tools CSF: Forensics Cyber-Security MSIDC, Spring 2015 Nuno Santos Summary! Data organization in storage systems! File deletion and recovery!
The FAT File System. 1. FAT Overview. 2. Boot Sector, FAT, Root Directory, and Files The FAT F 䤀耄 le System
 CIS 24 Home http://www.c jump.com/cis24/cis24syllabus.htm The FAT File System 1. FAT Overview 2. Boot Sector, FAT, Root Directory, and Files 3. FAT File System Layout 4. FAT Clusters and Sectors 5. FAT,
CIS 24 Home http://www.c jump.com/cis24/cis24syllabus.htm The FAT File System 1. FAT Overview 2. Boot Sector, FAT, Root Directory, and Files 3. FAT File System Layout 4. FAT Clusters and Sectors 5. FAT,
Booting, Partitioning and File Systems. Part I. Booting and hard disks. Booting. Table of Contents. Nothing is what it seems.
 Booting, Partitioning and File Systems Nothing is what it seems Karst Koymans Part I Booting and hard disks Informatics Institute University of Amsterdam (version 1.10, 2011/10/10 13:15:34) Friday, October
Booting, Partitioning and File Systems Nothing is what it seems Karst Koymans Part I Booting and hard disks Informatics Institute University of Amsterdam (version 1.10, 2011/10/10 13:15:34) Friday, October
Example Implementations of File Systems
 Example Implementations of File Systems Last modified: 22.05.2017 1 Linux file systems ext2, ext3, ext4, proc, swap LVM Contents ZFS/OpenZFS NTFS - the main MS Windows file system 2 Linux File Systems
Example Implementations of File Systems Last modified: 22.05.2017 1 Linux file systems ext2, ext3, ext4, proc, swap LVM Contents ZFS/OpenZFS NTFS - the main MS Windows file system 2 Linux File Systems
CS370 Operating Systems
 CS370 Operating Systems Colorado State University Yashwant K Malaiya Fall 2017 Lecture 24 File Systems Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 Questions from last time How
CS370 Operating Systems Colorado State University Yashwant K Malaiya Fall 2017 Lecture 24 File Systems Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 Questions from last time How
Introduction to OS. File Management. MOS Ch. 4. Mahmoud El-Gayyar. Mahmoud El-Gayyar / Introduction to OS 1
 Introduction to OS File Management MOS Ch. 4 Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Mahmoud El-Gayyar / Introduction to OS 1 File Management Objectives Provide I/O support for a variety of storage device
Introduction to OS File Management MOS Ch. 4 Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Mahmoud El-Gayyar / Introduction to OS 1 File Management Objectives Provide I/O support for a variety of storage device
File system internals Tanenbaum, Chapter 4. COMP3231 Operating Systems
 File system internals Tanenbaum, Chapter 4 COMP3231 Operating Systems Summary of the FS abstraction User's view Hierarchical structure Arbitrarily-sized files Symbolic file names Contiguous address space
File system internals Tanenbaum, Chapter 4 COMP3231 Operating Systems Summary of the FS abstraction User's view Hierarchical structure Arbitrarily-sized files Symbolic file names Contiguous address space
Persistent Storage - Datastructures and Algorithms
 Persistent Storage - Datastructures and Algorithms Seite 1 L 07: Case Study: Unix FS Seite 2 Questions: Encoding What is an encoding? Name some examples of codes Which are used in computers? Seite 3 Questions:
Persistent Storage - Datastructures and Algorithms Seite 1 L 07: Case Study: Unix FS Seite 2 Questions: Encoding What is an encoding? Name some examples of codes Which are used in computers? Seite 3 Questions:
File System Concepts File Allocation Table (FAT) New Technology File System (NTFS) Extended File System (EXT) Master File Table (MFT)
 File System Concepts File Allocation Table (FAT) New Technology File System (NTFS) Extended File System (EXT) Master File Table (MFT) 1 FILE SYSTEM CONCEPTS: FILE ALLOCATION TABLE (FAT) Alex Applegate
File System Concepts File Allocation Table (FAT) New Technology File System (NTFS) Extended File System (EXT) Master File Table (MFT) 1 FILE SYSTEM CONCEPTS: FILE ALLOCATION TABLE (FAT) Alex Applegate
Chapter 10: Mass-Storage Systems
 Chapter 10: Mass-Storage Systems Silberschatz, Galvin and Gagne 2013 Chapter 10: Mass-Storage Systems Overview of Mass Storage Structure Disk Structure Disk Attachment Disk Scheduling Disk Management Swap-Space
Chapter 10: Mass-Storage Systems Silberschatz, Galvin and Gagne 2013 Chapter 10: Mass-Storage Systems Overview of Mass Storage Structure Disk Structure Disk Attachment Disk Scheduling Disk Management Swap-Space
Chapter. Chapter. Magnetic and Solid-State Storage Devices
 Chapter Chapter 9 Magnetic and Solid-State Storage Devices Objectives Explain how magnetic principles are applied to data storage. Explain disk geometry. Identify disk partition systems. Recall common
Chapter Chapter 9 Magnetic and Solid-State Storage Devices Objectives Explain how magnetic principles are applied to data storage. Explain disk geometry. Identify disk partition systems. Recall common
Initial Bootloader. On power-up, when a computer is turned on, the following operations are performed:
 Initial Bootloader Introduction On power-up, when a computer is turned on, the following operations are performed: 1. The computer performs a power on self test (POST) to ensure that it meets the necessary
Initial Bootloader Introduction On power-up, when a computer is turned on, the following operations are performed: 1. The computer performs a power on self test (POST) to ensure that it meets the necessary
CISC 7310X. C11: Mass Storage. Hui Chen Department of Computer & Information Science CUNY Brooklyn College. 4/19/2018 CUNY Brooklyn College
 CISC 7310X C11: Mass Storage Hui Chen Department of Computer & Information Science CUNY Brooklyn College 4/19/2018 CUNY Brooklyn College 1 Outline Review of memory hierarchy Mass storage devices Reliability
CISC 7310X C11: Mass Storage Hui Chen Department of Computer & Information Science CUNY Brooklyn College 4/19/2018 CUNY Brooklyn College 1 Outline Review of memory hierarchy Mass storage devices Reliability
EI 338: Computer Systems Engineering (Operating Systems & Computer Architecture)
 EI 338: Computer Systems Engineering (Operating Systems & Computer Architecture) Dept. of Computer Science & Engineering Chentao Wu wuct@cs.sjtu.edu.cn Download lectures ftp://public.sjtu.edu.cn User:
EI 338: Computer Systems Engineering (Operating Systems & Computer Architecture) Dept. of Computer Science & Engineering Chentao Wu wuct@cs.sjtu.edu.cn Download lectures ftp://public.sjtu.edu.cn User:
Digital forensics. Andrej Brodnik. Andrej Brodnik: Digital Forensics
 Digital forensics Andrej Brodnik Computer pre-knowledge: architecture of computers basics (BIOS) operating system secondary memory (disc) and its organization file systems chapter 15 Startup startup steps
Digital forensics Andrej Brodnik Computer pre-knowledge: architecture of computers basics (BIOS) operating system secondary memory (disc) and its organization file systems chapter 15 Startup startup steps
Boot Process in details for (X86) Computers
 Boot Process in details for (X86) Computers Hello,,, Let's discuss what happens between the time that you power up your PC and when the desktop appears. In fact we should know that the boot process differs
Boot Process in details for (X86) Computers Hello,,, Let's discuss what happens between the time that you power up your PC and when the desktop appears. In fact we should know that the boot process differs
Chapter 10: Mass-Storage Systems. Operating System Concepts 9 th Edition
 Chapter 10: Mass-Storage Systems Silberschatz, Galvin and Gagne 2013 Chapter 10: Mass-Storage Systems Overview of Mass Storage Structure Disk Structure Disk Attachment Disk Scheduling Disk Management Swap-Space
Chapter 10: Mass-Storage Systems Silberschatz, Galvin and Gagne 2013 Chapter 10: Mass-Storage Systems Overview of Mass Storage Structure Disk Structure Disk Attachment Disk Scheduling Disk Management Swap-Space
File Systems Forensics
 File Systems Forensics Section II. Basic Forensic Techniques and Tools CSF: Forensics Cyber-Security MSIDC, Spring 2017 Nuno Santos Summary! Analysis of file systems! Recovery of deleted files 2 Recall
File Systems Forensics Section II. Basic Forensic Techniques and Tools CSF: Forensics Cyber-Security MSIDC, Spring 2017 Nuno Santos Summary! Analysis of file systems! Recovery of deleted files 2 Recall
Guide to Computer Forensics and Investigations Fourth Edition. Chapter 6 Working with Windows and DOS Systems
 Guide to Computer Forensics and Investigations Fourth Edition Chapter 6 Working with Windows and DOS Systems Understanding Disk Drives Disk drives are made up of one or more platters coated with magnetic
Guide to Computer Forensics and Investigations Fourth Edition Chapter 6 Working with Windows and DOS Systems Understanding Disk Drives Disk drives are made up of one or more platters coated with magnetic
WINDISK: A File and disk Editor
 s WINDISK: A File and disk Editor Table of content Introduction Loading a file Saving the edited file DBCS files DBCS language selection SBCS files Disk geometry Print view Printer Setup Save view to file
s WINDISK: A File and disk Editor Table of content Introduction Loading a file Saving the edited file DBCS files DBCS language selection SBCS files Disk geometry Print view Printer Setup Save view to file
File Systems Management and Examples
 File Systems Management and Examples Today! Efficiency, performance, recovery! Examples Next! Distributed systems Disk space management! Once decided to store a file as sequence of blocks What s the size
File Systems Management and Examples Today! Efficiency, performance, recovery! Examples Next! Distributed systems Disk space management! Once decided to store a file as sequence of blocks What s the size
FILE SYSTEM IMPLEMENTATION. Sunu Wibirama
 FILE SYSTEM IMPLEMENTATION Sunu Wibirama File-System Structure Outline File-System Implementation Directory Implementation Allocation Methods Free-Space Management Discussion File-System Structure Outline
FILE SYSTEM IMPLEMENTATION Sunu Wibirama File-System Structure Outline File-System Implementation Directory Implementation Allocation Methods Free-Space Management Discussion File-System Structure Outline
CS609 Final Term Subjective Paper Solved with references March (2014)
 CS609 Final Term Subjective Paper Solved with references March (2014) Solved by: Saher/Aqualeo www.freeittips.com Q:1 How large file contents can be managed using FAT? 2 marks Larger files would be comprised
CS609 Final Term Subjective Paper Solved with references March (2014) Solved by: Saher/Aqualeo www.freeittips.com Q:1 How large file contents can be managed using FAT? 2 marks Larger files would be comprised
Chapter 8: Filesystem Implementation
 ADRIAN PERRIG & TORSTEN HOEFLER ( 252-0062-00 ) Networks and Operating Systems Chapter 8: Filesystem Implementation source: xkcd.com Access Control 1 Protection File owner/creator should be able to control:
ADRIAN PERRIG & TORSTEN HOEFLER ( 252-0062-00 ) Networks and Operating Systems Chapter 8: Filesystem Implementation source: xkcd.com Access Control 1 Protection File owner/creator should be able to control:
File System Basics. Farmer & Venema. Mississippi State University Digital Forensics 1
 File System Basics Farmer & Venema 1 Alphabet Soup of File Systems More file systems than operating systems Microsoft has had several: FAT16, FAT32, HPFS, NTFS, NTFS2 UNIX certainly has its share, in typical
File System Basics Farmer & Venema 1 Alphabet Soup of File Systems More file systems than operating systems Microsoft has had several: FAT16, FAT32, HPFS, NTFS, NTFS2 UNIX certainly has its share, in typical
HARD DISK MANAGER 11 / FULL FEATURES LIST. HDM 11 Professional. HDM 11 Server. Features. Virtualization. Add-on. Drive Partitioning
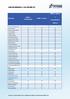 HDM 11 Server Features HDM 11 Professional HDM 11 Server + Virtualization Add-on Drive Partitioning Create Partition Express Create Partition Format Partition Delete Partition Undelete Partition Move/Resize
HDM 11 Server Features HDM 11 Professional HDM 11 Server + Virtualization Add-on Drive Partitioning Create Partition Express Create Partition Format Partition Delete Partition Undelete Partition Move/Resize
Microsoft File Allocation Table
 Microsoft File Allocation Table CSC362, Information Security originally appeared in late 1970s for small disks with simple folder structures uses a FAT to index files (naturally) the original FAT- 12 gave
Microsoft File Allocation Table CSC362, Information Security originally appeared in late 1970s for small disks with simple folder structures uses a FAT to index files (naturally) the original FAT- 12 gave
Da-Wei Chang CSIE.NCKU. Professor Hao-Ren Ke, National Chiao Tung University Professor Hsung-Pin Chang, National Chung Hsing University
 Chapter 11 Implementing File System Da-Wei Chang CSIE.NCKU Source: Professor Hao-Ren Ke, National Chiao Tung University Professor Hsung-Pin Chang, National Chung Hsing University Outline File-System Structure
Chapter 11 Implementing File System Da-Wei Chang CSIE.NCKU Source: Professor Hao-Ren Ke, National Chiao Tung University Professor Hsung-Pin Chang, National Chung Hsing University Outline File-System Structure
Windows File System. File allocation table (FAT) NTFS - New Technology File System. used in Windows 95, and MS-DOS
 Windows File System Windows File System File allocation table (FAT) used in Windows 95, and MS-DOS NTFS - New Technology File System 2 Key features of NTFS NTFS uses clusters(rather than sectors) as units
Windows File System Windows File System File allocation table (FAT) used in Windows 95, and MS-DOS NTFS - New Technology File System 2 Key features of NTFS NTFS uses clusters(rather than sectors) as units
CIS-331 Exam 2 Fall 2015 Total of 105 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
File Systems: Fundamentals
 File Systems: Fundamentals 1 Files! What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks)! File attributes Ø Name, type, location, size, protection, creator,
File Systems: Fundamentals 1 Files! What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks)! File attributes Ø Name, type, location, size, protection, creator,
15: Filesystem Examples: Ext3, NTFS, The Future. Mark Handley. Linux Ext3 Filesystem
 15: Filesystem Examples: Ext3, NTFS, The Future Mark Handley Linux Ext3 Filesystem 1 Problem: Recovery after a crash fsck on a large disk can be extremely slow. An issue for laptops. Power failure is common.
15: Filesystem Examples: Ext3, NTFS, The Future Mark Handley Linux Ext3 Filesystem 1 Problem: Recovery after a crash fsck on a large disk can be extremely slow. An issue for laptops. Power failure is common.
17: Filesystem Examples: CD-ROM, MS-DOS, Unix
 17: Filesystem Examples: CD-ROM, MS-DOS, Unix Mark Handley CD Filesystems ISO 9660 Rock Ridge Extensions Joliet Extensions 1 ISO 9660: CD-ROM Filesystem CD is divided into logical blocks of 2352 bytes.
17: Filesystem Examples: CD-ROM, MS-DOS, Unix Mark Handley CD Filesystems ISO 9660 Rock Ridge Extensions Joliet Extensions 1 ISO 9660: CD-ROM Filesystem CD is divided into logical blocks of 2352 bytes.
File System: Interface and Implmentation
 File System: Interface and Implmentation Two Parts Filesystem Interface Interface the user sees Organization of the files as seen by the user Operations defined on files Properties that can be read/modified
File System: Interface and Implmentation Two Parts Filesystem Interface Interface the user sees Organization of the files as seen by the user Operations defined on files Properties that can be read/modified
Hard facts. Hard disk drives
 Hard facts Text by PowerQuest, photos and drawings Vlado Damjanovski 2004 What is a hard disk? A hard disk or hard drive is the part of your computer responsible for long-term storage of information. Unlike
Hard facts Text by PowerQuest, photos and drawings Vlado Damjanovski 2004 What is a hard disk? A hard disk or hard drive is the part of your computer responsible for long-term storage of information. Unlike
WipeDrive Home 9. IMPORTANT! PLEASE READ CAREFULLY:... 3 General Information... 3 WipeDrive Overview... 3 System Requirements...
 Table of Contents IMPORTANT! PLEASE READ CAREFULLY:... 3 General Information... 3 WipeDrive... 3 Overview... 3 System Requirements... 3 Key Features... 4 Secure Removal of HPA and DCO... 4 Secure Erase
Table of Contents IMPORTANT! PLEASE READ CAREFULLY:... 3 General Information... 3 WipeDrive... 3 Overview... 3 System Requirements... 3 Key Features... 4 Secure Removal of HPA and DCO... 4 Secure Erase
Computer Forensics: Investigating Data and Image Files, 2nd Edition. Chapter 3 Forensic Investigations Using EnCase
 Computer Forensics: Investigating Data and Image Files, 2nd Edition Chapter 3 Forensic Investigations Using EnCase Objectives After completing this chapter, you should be able to: Understand evidence files
Computer Forensics: Investigating Data and Image Files, 2nd Edition Chapter 3 Forensic Investigations Using EnCase Objectives After completing this chapter, you should be able to: Understand evidence files
Segmentation with Paging. Review. Segmentation with Page (MULTICS) Segmentation with Page (MULTICS) Segmentation with Page (MULTICS)
 Review Segmentation Segmentation Implementation Advantage of Segmentation Protection Sharing Segmentation with Paging Segmentation with Paging Segmentation with Paging Reason for the segmentation with
Review Segmentation Segmentation Implementation Advantage of Segmentation Protection Sharing Segmentation with Paging Segmentation with Paging Segmentation with Paging Reason for the segmentation with
Implementing Hard Drives
 Implementing Hard Drives Chapter 12 Overview In this chapter, you will learn how to Explain the partitions available in Windows Discuss hard drive formatting options Partition and format hard drives Maintain
Implementing Hard Drives Chapter 12 Overview In this chapter, you will learn how to Explain the partitions available in Windows Discuss hard drive formatting options Partition and format hard drives Maintain
THOMAS RUSSELL, Information Technology Teacher
 THOMAS RUSSELL, Information Technology Teacher Historical/Conceptual After installing the hard drive it needs to be partitioned. Partitioning is the process of electronically subdividing the physical hard
THOMAS RUSSELL, Information Technology Teacher Historical/Conceptual After installing the hard drive it needs to be partitioned. Partitioning is the process of electronically subdividing the physical hard
CIS-331 Spring 2016 Exam 1 Name: Total of 109 Points Version 1
 Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems
 IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems 5.0 Introduction 1. What controls almost all functions on a computer? The operating system 5.1 Explain the purpose of an operating system 2.
IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems 5.0 Introduction 1. What controls almost all functions on a computer? The operating system 5.1 Explain the purpose of an operating system 2.
CIS-331 Fall 2013 Exam 1 Name: Total of 120 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Operating Systems. Week 9 Recitation: Exam 2 Preview Review of Exam 2, Spring Paul Krzyzanowski. Rutgers University.
 Operating Systems Week 9 Recitation: Exam 2 Preview Review of Exam 2, Spring 2014 Paul Krzyzanowski Rutgers University Spring 2015 March 27, 2015 2015 Paul Krzyzanowski 1 Exam 2 2012 Question 2a One of
Operating Systems Week 9 Recitation: Exam 2 Preview Review of Exam 2, Spring 2014 Paul Krzyzanowski Rutgers University Spring 2015 March 27, 2015 2015 Paul Krzyzanowski 1 Exam 2 2012 Question 2a One of
There is a general need for long-term and shared data storage: Files meet these requirements The file manager or file system within the OS
 Why a file system? Why a file system There is a general need for long-term and shared data storage: need to store large amount of information persistent storage (outlives process and system reboots) concurrent
Why a file system? Why a file system There is a general need for long-term and shared data storage: need to store large amount of information persistent storage (outlives process and system reboots) concurrent
Xen Live Migration Of An LVM-Based Virtual Machine With iscsi On Debian Lenny
 By Falko Timme Published: 2009-04-28 18:16 Xen Live Migration Of An LVM-Based Virtual Machine With iscsi On Debian Lenny Version 1.0 Author: Falko Timme Last edited 04/16/2009
By Falko Timme Published: 2009-04-28 18:16 Xen Live Migration Of An LVM-Based Virtual Machine With iscsi On Debian Lenny Version 1.0 Author: Falko Timme Last edited 04/16/2009
Chapter 12: File System Implementation
 Chapter 12: File System Implementation Silberschatz, Galvin and Gagne 2013 Chapter 12: File System Implementation File-System Structure File-System Implementation Allocation Methods Free-Space Management
Chapter 12: File System Implementation Silberschatz, Galvin and Gagne 2013 Chapter 12: File System Implementation File-System Structure File-System Implementation Allocation Methods Free-Space Management
File systems Computer Forensics
 Mag. iur. Dr. techn. Michael Sonntag File systems Computer Forensics E-Mail: sonntag@fim.uni-linz.ac.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor
Mag. iur. Dr. techn. Michael Sonntag File systems Computer Forensics E-Mail: sonntag@fim.uni-linz.ac.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor
Chapter 11: Implementing File Systems
 Chapter 11: Implementing File Systems Operating System Concepts 99h Edition DM510-14 Chapter 11: Implementing File Systems File-System Structure File-System Implementation Directory Implementation Allocation
Chapter 11: Implementing File Systems Operating System Concepts 99h Edition DM510-14 Chapter 11: Implementing File Systems File-System Structure File-System Implementation Directory Implementation Allocation
Veritas System Recovery Disk Help
 Veritas System Recovery Disk Help About recovering a computer If Windows fails to start or does not run normally, you can still recover your computer. You can use the Veritas System Recovery Disk and an
Veritas System Recovery Disk Help About recovering a computer If Windows fails to start or does not run normally, you can still recover your computer. You can use the Veritas System Recovery Disk and an
File Systems: Fundamentals
 1 Files Fundamental Ontology of File Systems File Systems: Fundamentals What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type,
1 Files Fundamental Ontology of File Systems File Systems: Fundamentals What is a file? Ø A named collection of related information recorded on secondary storage (e.g., disks) File attributes Ø Name, type,
ECE 598 Advanced Operating Systems Lecture 18
 ECE 598 Advanced Operating Systems Lecture 18 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 5 April 2016 Homework #7 was posted Project update Announcements 1 More like a 571
ECE 598 Advanced Operating Systems Lecture 18 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 5 April 2016 Homework #7 was posted Project update Announcements 1 More like a 571
Format Hard Drive Using Windows 7 Recovery Disk
 Format Hard Drive Using Windows 7 Recovery Disk Jun 8, 2015. If it's not possible to create a recovery disk using this method, is it possible to backup Hey guys, I'm looking to format my hard-drive and
Format Hard Drive Using Windows 7 Recovery Disk Jun 8, 2015. If it's not possible to create a recovery disk using this method, is it possible to backup Hey guys, I'm looking to format my hard-drive and
V. Mass Storage Systems
 TDIU25: Operating Systems V. Mass Storage Systems SGG9: chapter 12 o Mass storage: Hard disks, structure, scheduling, RAID Copyright Notice: The lecture notes are mainly based on modifications of the slides
TDIU25: Operating Systems V. Mass Storage Systems SGG9: chapter 12 o Mass storage: Hard disks, structure, scheduling, RAID Copyright Notice: The lecture notes are mainly based on modifications of the slides
Motivation. Operating Systems. File Systems. Outline. Files: The User s Point of View. File System Concepts. Solution? Files!
 Motivation Operating Systems Process store, retrieve information Process capacity restricted to vmem size When process terminates, memory lost Multiple processes share information Systems (Ch 0.-0.4, Ch.-.5)
Motivation Operating Systems Process store, retrieve information Process capacity restricted to vmem size When process terminates, memory lost Multiple processes share information Systems (Ch 0.-0.4, Ch.-.5)
Thanks for the feedback! Chapter 8: Filesystem Implementation. File system operations. Acyclic-Graph Directories. General Graph Directory
 ADRIAN PERRIG & TORSTEN HOEFLER ( 252-0062-00 ) Networks and Operating Systems Chapter 8: Filesystem Implementation Thanks for the feedback! Some answers: I ll provide references to books (I m not only
ADRIAN PERRIG & TORSTEN HOEFLER ( 252-0062-00 ) Networks and Operating Systems Chapter 8: Filesystem Implementation Thanks for the feedback! Some answers: I ll provide references to books (I m not only
Partitioning a disk prior to Linux Installation
 Partitioning a disk prior to Linux Installation by Andy Pepperdine This paper will describe how to partition a disk how you want it before you install Linux. The partitioning process may be initiated either
Partitioning a disk prior to Linux Installation by Andy Pepperdine This paper will describe how to partition a disk how you want it before you install Linux. The partitioning process may be initiated either
Project 3: An Introduction to File Systems. COP 4610 / CGS 5765 Principles of Operating Systems
 Project 3: An Introduction to File Systems COP 4610 / CGS 5765 Principles of Operating Systems Introduction Project 3 learning objectives File system design and implementation File system testing Data
Project 3: An Introduction to File Systems COP 4610 / CGS 5765 Principles of Operating Systems Introduction Project 3 learning objectives File system design and implementation File system testing Data
CS 4284 Systems Capstone
 CS 4284 Systems Capstone Disks & File Systems Godmar Back Filesystems Files vs Disks File Abstraction Byte oriented Names Access protection Consistency guarantees Disk Abstraction Block oriented Block
CS 4284 Systems Capstone Disks & File Systems Godmar Back Filesystems Files vs Disks File Abstraction Byte oriented Names Access protection Consistency guarantees Disk Abstraction Block oriented Block
MASS-STORAGE STRUCTURE
 UNIT IV MASS-STORAGE STRUCTURE Mass-Storage Systems ndescribe the physical structure of secondary and tertiary storage devices and the resulting effects on the uses of the devicesnexplain the performance
UNIT IV MASS-STORAGE STRUCTURE Mass-Storage Systems ndescribe the physical structure of secondary and tertiary storage devices and the resulting effects on the uses of the devicesnexplain the performance
Veritas System Recovery Disk Help
 Veritas System Recovery Disk Help About recovering a computer If Windows fails to start or does not run normally, you can still recover your computer. You can use the Veritas System Recovery Disk and an
Veritas System Recovery Disk Help About recovering a computer If Windows fails to start or does not run normally, you can still recover your computer. You can use the Veritas System Recovery Disk and an
NTFS Fundamentals. [Kevin s Attic for Security Research]
![NTFS Fundamentals. [Kevin s Attic for Security Research] NTFS Fundamentals. [Kevin s Attic for Security Research]](/thumbs/74/70081591.jpg) [] NTFS Fundamentals kevinkoo001@gmail.com DO NOT FORGET TO REMAIN THE ORIGINAL SOURCE WHEN YOU MAKE USE OF THIS MATERIAL OR (RE)DISTRIBUTE IT. What to Cover 1. Information with Tools 2. NTFS Layout 3.
[] NTFS Fundamentals kevinkoo001@gmail.com DO NOT FORGET TO REMAIN THE ORIGINAL SOURCE WHEN YOU MAKE USE OF THIS MATERIAL OR (RE)DISTRIBUTE IT. What to Cover 1. Information with Tools 2. NTFS Layout 3.
Operating System Concepts Ch. 11: File System Implementation
 Operating System Concepts Ch. 11: File System Implementation Silberschatz, Galvin & Gagne Introduction When thinking about file system implementation in Operating Systems, it is important to realize the
Operating System Concepts Ch. 11: File System Implementation Silberschatz, Galvin & Gagne Introduction When thinking about file system implementation in Operating Systems, it is important to realize the
CS609 FINAL TERM CURRENT 2014 SUBJECTIVE PAPERS
 CS609 FINAL TERM CURRENT 2014 SUBJECTIVE PAPERS Current papers of CS609 CS609 SUBJECTIVE CURRENT PAPERS SOLVED BY GHAZAL KANGAN Solved Subjective Current Papers Question:1 How large file contents can be
CS609 FINAL TERM CURRENT 2014 SUBJECTIVE PAPERS Current papers of CS609 CS609 SUBJECTIVE CURRENT PAPERS SOLVED BY GHAZAL KANGAN Solved Subjective Current Papers Question:1 How large file contents can be
