AhnLab-V AntiVir Antiy-AVL Avast
|
|
|
- Colin Bailey
- 6 years ago
- Views:
Transcription
1 VT Community Sign in Languages Virustotal is a service that analyzes suspicious files and URLs and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware detected by antivirus engines. More information... 0 VT Community user(s) with a total of 0 reputation credit(s) say(s) this sample is goodware. 0 VT Community user(s) with a total of 0 reputation credit(s) say(s) this sample is malware. VT Community File name: Submission date: Current status: Result: BitWay_Backup_Scanner.exe :24:26 (UTC) finished 0/ 42 (0.0%) not reviewed Safety score: - Compact Print results Antivirus Version Last Update Result AhnLab-V AntiVir Antiy-AVL Avast AVG BitDefender ByteHero ClamAV Commtouch Comodo DrWeb Emsisoft esafe etrust-vet F-Prot F-Secure Fortinet GData / Ikarus T Jiangmin K7AntiVirus Kaspersky McAfee
2 McAfee-GW-Edition D Microsoft NOD Norman nprotect Panda PCTools Prevx Rising Sophos SUPERAntiSpyware Symantec TheHacker TrendMicro TrendMicro-HouseCall VBA VIPRE ViRobot VirusBuster Additional information Show all MD5 : 0e79a832003e1877b f10571f SHA1 : dd6dd67884da dbd68366de48ff0e6599 SHA256: 2f817d08a dec9a40d2f6e20787ce2d0da5d447e14d4c0e c04 ssdeep: 24576:rkEH+vtpHNpCBD6FhegDneu68zcCjS6LGJ/QiFq:rKvtNHe+zbjS6iJtFq File size : bytes First seen: :24:26 Last seen : :24:26 TrID: UPX compressed Win32 Executable (39.5%) Win32 EXE Yoda's Crypter (34.3%) Win32 Executable Generic (11.0%) Win32 Dynamic Link Library (generic) (9.8%) Generic Win/DOS Executable (2.5%) sigcheck: publisher...: BitWay copyright...: BitWay. All rights reserved. product...: BitWay Online Backup description..: BitWay Online Backup Vulnerability Scanner original name: SScanner.exe internal name: SScanner.exe file version.: comments...: n/a
3 signers...: - signing date.: - verified...: Unsigned PEiD: UPX 2.93 [LZMA] -> Markus Oberhumer, Laszlo Molnar & John Reiser packers (F-Prot): UPX_LZMA PEInfo: PE structure information [[ basic data ]] entrypointaddress: 0x3B7FA0 timedatestamp...: 0x4CF64020 (Wed Dec 01 12:31: ) machinetype...: 0x14c (I386) [[ 3 section(s) ]] name, viradd, virsiz, rawdsiz, ntropy, md5 UPX0, 0x1000, 0x2F8000, 0x0, 0.00, d41d8cd98f00b204e ecf8427e UPX1, 0x2F9000, 0xC0000, 0xBFC00, 8.00, 4d1c35fa0116fb4b21a3124e5df3efaf.rsrc, 0x3B9000, 0x4000, 0x3A00, 6.09, c12a903d7cfa5dafdabfab14f0 [[ 14 import(s) ]] KERNEL32.DLL: LoadLibraryA, GetProcAddress, VirtualProtect, VirtualAlloc, VirtualFree, ExitProcess ADVAPI32.dll: RegEnumKeyW COMCTL32.dll: _TrackMouseEvent COMDLG32.dll: GetFileTitleW GDI32.dll: LineTo IMM32.dll: ImmGetContext MSIMG32.dll: AlphaBlend ole32.dll: DoDragDrop OLEAUT32.dll: - SHELL32.dll: DragFinish SHLWAPI.dll: PathIsURLW USER32.dll: GetDC WINMM.dll: PlaySoundW WINSPOOL.DRV: ClosePrinter ExifTool: file metadata CharacterSet: Windows, Latin1 CodeSize: CompanyName: BitWay EntryPoint: 0x3b7fa0 FileDescription: BitWay Online Backup Vulnerability Scanner FileFlagsMask: 0x003f FileOS: Win32 FileSize: 782 kb FileSubtype: 0 FileType: Win32 EXE FileVersion: FileVersionNumber: ImageVersion: 0.0 InitializedDataSize: InternalName: SScanner.exe LanguageCode: English (U.S.) LegalCopyright: BitWay. All rights reserved. LinkerVersion: 9.0 MIMEType: application/octet-stream MachineType: Intel 386 or later, and compatibles
4 OSVersion: 5.0 ObjectFileType: Executable application OriginalFilename: SScanner.exe PEType: PE32 ProductName: BitWay Online Backup ProductVersion: ProductVersionNumber: Subsystem: Windows GUI SubsystemVersion: 5.0 TimeStamp: 2010:12:01 13:31:28+01:00 UninitializedDataSize: Symantec reputation:suspicious.insight VT Community This file has never been reviewed by any VT Community member. Be the first one to comment on it! VirusTotal Team Add your comment... Remember that when you write comments as an anonymous user they receive the lowest possible reputation. So if you have not signed in yet don't forget to do so. How to markup your comments? Goodware Malware Spam attachment/link P2P download Propagating via IM Network worm Drive-by-download Preview comment Post comment ATTENTION: VirusTotal is a free service offered by Hispasec Sistemas. There are no guarantees about the availability and continuity of this service. Although the detection rate afforded by the use of multiple antivirus engines is far superior to that offered by just one product, these results DO NOT guarantee the harmlessness of a file. Currently, there is not any solution that offers a 100% effectiveness rate for detecting viruses and malware.
5 VirusTotal Hispasec Sistemas - Blog - Twitter - Contact: info@virustotal.com - TOS & Privacy Policy
Language English. Server load. Suspicious file(s) to scan:
 Security risk found in message 'DHL customer services. You should get th... http://virscan.org/report/356346ab231bfab52fe5d0eaef8eb3f6.html 1 of 2 2/5/2010 11:11 AM Language English Server load Suspicious
Security risk found in message 'DHL customer services. You should get th... http://virscan.org/report/356346ab231bfab52fe5d0eaef8eb3f6.html 1 of 2 2/5/2010 11:11 AM Language English Server load Suspicious
Lab 1: UPX Program Packer. From what we see here Netcat s MD5 is (AB41B1E2DB77CEBD9E EE3915D)
 Lab 1: UPX Program Packer Lets use UPX Program Packer on Netcat and see what we happens. First lets get the MD5 hash of Netcat and see what it looks like. From what we see here Netcat s MD5 is (AB41B1E2DB77CEBD9E2779110EE3915D)
Lab 1: UPX Program Packer Lets use UPX Program Packer on Netcat and see what we happens. First lets get the MD5 hash of Netcat and see what it looks like. From what we see here Netcat s MD5 is (AB41B1E2DB77CEBD9E2779110EE3915D)
Analysis # Sample: Important_WellsFargo_Doc.exe (70e604777a66980bcc751dcb00eafee5) Analysis # /10/ :12 pm
 Analysis # 31139 06/10/2013 14:12 pm 1/11 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 Created Mutexes... 4 Created Mutexes... 4 Registry Activity... 5 Created
Analysis # 31139 06/10/2013 14:12 pm 1/11 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 Created Mutexes... 4 Created Mutexes... 4 Registry Activity... 5 Created
Analysis # Sample: Scan_ _29911.exe (8fcba93b00dba3d182b1228b529d3c9e) Analysis # /12/ :41 pm
 Analysis # 31187 06/12/2013 18:41 pm 1/12 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 File Activity... 4 Deleted Files... 4 Created Mutexes... 5 Created Mutexes...
Analysis # 31187 06/12/2013 18:41 pm 1/12 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 File Activity... 4 Deleted Files... 4 Created Mutexes... 5 Created Mutexes...
Analysis # Sample: ss32.exe ( a6e6d b453e73d) Analysis # /08/ :33 pm
 Analysis # 31607 07/08/2013 16:33 pm 1/14 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 File Activity... 4 Stored Modified Files... 4 Created Mutexes... 5 Created
Analysis # 31607 07/08/2013 16:33 pm 1/14 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 File Activity... 4 Stored Modified Files... 4 Created Mutexes... 5 Created
Analysis # Sample: google_born_help.exe (584fe856bb348e0089f7b59ec31881a5) Analysis # /05/ :34 pm
 Analysis # 20972 10/05/2012 16:34 pm 1/14 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 File Activity... 4 Deleted Files... 4 Stored Modified Files... 5 Created
Analysis # 20972 10/05/2012 16:34 pm 1/14 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 File Activity... 4 Deleted Files... 4 Stored Modified Files... 5 Created
1. I am a Computer Forensics Researcher with Kyrus Technology. I make this
 I, Jesse D. Kornblum, declare as follows: 1. I am a Computer Forensics Researcher with Kyrus Technology. I make this declaration in support of Plaintiffs Application For An Emergency Temporary Restraining
I, Jesse D. Kornblum, declare as follows: 1. I am a Computer Forensics Researcher with Kyrus Technology. I make this declaration in support of Plaintiffs Application For An Emergency Temporary Restraining
UC Davis UC Davis Previously Published Works
 UC Davis UC Davis Previously Published Works Title Multiprocess Malware Permalink https://escholarship.org/uc/item/0v40f6h3 Authors Ramilli, Marco Bishop, Matt Sun, Shining Publication Date 2011-10-01
UC Davis UC Davis Previously Published Works Title Multiprocess Malware Permalink https://escholarship.org/uc/item/0v40f6h3 Authors Ramilli, Marco Bishop, Matt Sun, Shining Publication Date 2011-10-01
A Study of the Relationship Between Antivirus Regressions and Label Changes
 A Study of the Relationship Between Antivirus Regressions and Label Changes Ilir Gashi 1, Bertrand Sobesto 2, Stephen Mason 1, Vladimir Stankovic 1, and Michel Cukier 2 1 Centre for Software Reliability,
A Study of the Relationship Between Antivirus Regressions and Label Changes Ilir Gashi 1, Bertrand Sobesto 2, Stephen Mason 1, Vladimir Stankovic 1, and Michel Cukier 2 1 Centre for Software Reliability,
Malware Initial Findings Report (MIFR)
 US-CERT MIFR-10124171 1 of 41 Malware Initial Findings Report (MIFR) - 10124171 2017-05-14 Notification This report is provided "as is" for informational purposes only. The Department of Homeland Security
US-CERT MIFR-10124171 1 of 41 Malware Initial Findings Report (MIFR) - 10124171 2017-05-14 Notification This report is provided "as is" for informational purposes only. The Department of Homeland Security
City, University of London Institutional Repository
 City Research Online City, University of London Institutional Repository Citation: Cukier, M., Gashi, I., Sobesto, B. & Stankovic, V. (2013). Does Malware Detection Improve With Diverse AntiVirus Products?
City Research Online City, University of London Institutional Repository Citation: Cukier, M., Gashi, I., Sobesto, B. & Stankovic, V. (2013). Does Malware Detection Improve With Diverse AntiVirus Products?
ID: Sample Name: adobe.snr.patchpainter.exe. Cookbook: default.jbs Time: 07:05:16 Date: 03/03/2018 Version:
 ID: 470 Sample Name: adobe.snr.patchpainter.exe Cookbook: default.jbs Time: 07:05:16 Date: 03/03/201 Version: 22.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 470 Sample Name: adobe.snr.patchpainter.exe Cookbook: default.jbs Time: 07:05:16 Date: 03/03/201 Version: 22.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence
ID: Sample Name: 2017_w2.exe Cookbook: default.jbs Time: 17:03:04 Date: 09/02/2018 Version:
 ID: 4572 Sample Name: 2017_w2.exe Cookbook: default.jbs Time: 17:03:04 Date: 0/02/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 4572 Sample Name: 2017_w2.exe Cookbook: default.jbs Time: 17:03:04 Date: 0/02/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
INCIDENT RESPONSE. Antiviral shortcomings with respect to real malware. Malware Detection. Gary Golomb
 INCIDENT RESPONSE Malware Detection Antiviral shortcomings with respect to real malware Gary Golomb President, Proventsure LLC, Baltimore, MD Jonathan Gross Senior
INCIDENT RESPONSE Malware Detection Antiviral shortcomings with respect to real malware Gary Golomb President, Proventsure LLC, Baltimore, MD Jonathan Gross Senior
ID: Sample Name: 11youtube3.com Cookbook: default.jbs Time: 08:17:42 Date: 12/04/2018 Version:
 ID: 54295 Sample Name: 11youtube3.com Cookbook: default.jbs Time: 08:1:42 Date: 12/04/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 54295 Sample Name: 11youtube3.com Cookbook: default.jbs Time: 08:1:42 Date: 12/04/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
Analysis # 1828 Sample: fax_ _ exe (4ba43f0b82f86efed437c8523f7a4dee) Analysis # /25/ :05 am
 Analysis # 1828 07252014 10:05 am 114 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 File Activity... 4 Deleted Files... 4 Stored Modified Files... 5 Created
Analysis # 1828 07252014 10:05 am 114 Table of Contents Analysis Summary... 3 Analysis Summary... 3 Digital Behavior Traits... 3 File Activity... 4 Deleted Files... 4 Stored Modified Files... 5 Created
Anti-Virus Comparative No.1
 Anti-Virus Comparative No.1 a) On-demand detection of virus/malware b) On-demand detection of dialers Shortened version Date of Test: 6 February 2004 (2004-02) Author: Andreas Clementi Website: http://www.av-comparatives.org
Anti-Virus Comparative No.1 a) On-demand detection of virus/malware b) On-demand detection of dialers Shortened version Date of Test: 6 February 2004 (2004-02) Author: Andreas Clementi Website: http://www.av-comparatives.org
Anti-Virus Testing and AMTSO
 Anti-Virus Testing and AMTSO Patrik Runald, Security Response Manager Helsinki Kuala Lumpur San Jose Tokyo London Paris Milan Hong Kong Mumbay Warsaw Munich Copenhagen Brussels Oulu Utrecht Oslo Stockholm
Anti-Virus Testing and AMTSO Patrik Runald, Security Response Manager Helsinki Kuala Lumpur San Jose Tokyo London Paris Milan Hong Kong Mumbay Warsaw Munich Copenhagen Brussels Oulu Utrecht Oslo Stockholm
Obfuscation and (non-)detection of malicious PDF files. Jose Miguel Esparza
 Obfuscation and (non-)detection of malicious PDF files Jose Miguel Esparza Agenda Introduction to the PDF format Obfuscation and evasion techniques Obfuscation vs. Antivirus Obfuscation vs. Analysis tools
Obfuscation and (non-)detection of malicious PDF files Jose Miguel Esparza Agenda Introduction to the PDF format Obfuscation and evasion techniques Obfuscation vs. Antivirus Obfuscation vs. Analysis tools
Acer LANScope Agent Acer LANScope Agent x64 Adaptive Security Analyzer 2.0 AEC TrustPort Antivirus
 Acer LANScope Agent 2.2.25.84 Acer LANScope Agent 2.2.25.84 x64 Adaptive Security Analyzer 2.0 AEC TrustPort Antivirus 2.8.0.2237 AEC TrustPort Personal Firewall 4.0.0.1305 AhnLab SpyZero 2007 and SmartUpdate
Acer LANScope Agent 2.2.25.84 Acer LANScope Agent 2.2.25.84 x64 Adaptive Security Analyzer 2.0 AEC TrustPort Antivirus 2.8.0.2237 AEC TrustPort Personal Firewall 4.0.0.1305 AhnLab SpyZero 2007 and SmartUpdate
ID: Sample Name: Renci.SshNet.dll Cookbook: default.jbs Time: 12:55:23 Date: 08/06/2018 Version:
 ID: 63205 Sample Name: Renci.SshNet.dll Cookbook: default.jbs Time: 12:55:23 Date: 0/06/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 63205 Sample Name: Renci.SshNet.dll Cookbook: default.jbs Time: 12:55:23 Date: 0/06/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: Sample Name: rufus-2.18.exe Cookbook: default.jbs Time: 16:39:27 Date: 21/11/2017 Version:
 ID: 37703 Sample Name: rufus-2.18.exe Cookbook: default.jbs Time: 16:3:27 Date: 21/11/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: 37703 Sample Name: rufus-2.18.exe Cookbook: default.jbs Time: 16:3:27 Date: 21/11/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: Sample Name: calc1 Cookbook: default.jbs Time: 14:46:00 Date: 13/07/2018 Version:
 ID: 98 Sample Name: calc1 Cookbook: default.jbs Time: 14:4:00 Date: 13/0/2018 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
ID: 98 Sample Name: calc1 Cookbook: default.jbs Time: 14:4:00 Date: 13/0/2018 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
A glance into the Eye Pyramid
 A glance into the Eye Pyramid RĂZVAN OLTEANU Security Reasercher We keep you safe and we keep it simple. 01 Introduction On January 11, 2017 Italian news agency AGI, published a court order regarding cyber-attacks
A glance into the Eye Pyramid RĂZVAN OLTEANU Security Reasercher We keep you safe and we keep it simple. 01 Introduction On January 11, 2017 Italian news agency AGI, published a court order regarding cyber-attacks
ID: Sample Name: ikeyhelper.exe Cookbook: default.jbs Time: 16:40:36 Date: 28/12/2017 Version:
 ID: 41186 Sample Name: ikeyhelper.exe Cookbook: default.jbs Time: 16:40:36 Date: 28/12/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview Information Detection Confidence
ID: 41186 Sample Name: ikeyhelper.exe Cookbook: default.jbs Time: 16:40:36 Date: 28/12/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview Information Detection Confidence
Abusing File Processing in Malware Detectors for Fun and Profit
 2012 IEEE Symposium on Security and Privacy Abusing File Processing in Malware Detectors for Fun and Profit Suman Jana and Vitaly Shmatikov The University of Texas at Austin Abstract We systematically
2012 IEEE Symposium on Security and Privacy Abusing File Processing in Malware Detectors for Fun and Profit Suman Jana and Vitaly Shmatikov The University of Texas at Austin Abstract We systematically
ID: Sample Name: adobe.snr.patch.v2.0-painter.exe Cookbook: default.jbs Time: 18:11:59 Date: 06/07/2018 Version:
 ID: 67068 Sample Name: adobe.snr.patch.v2.0-painter.exe Cookbook: default.jbs Time: 18:11:5 Date: 06/07/2018 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 67068 Sample Name: adobe.snr.patch.v2.0-painter.exe Cookbook: default.jbs Time: 18:11:5 Date: 06/07/2018 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence
China Region Malware Test 2010 May
 China Region Malware Test 2010 May Basic Introduction Test Time:May 4 th, 2010 Tester:PC Security Labs Test Platform:Windows XP SP3 Professional Simplified Chinese Test Methodology:On-demand scan (default
China Region Malware Test 2010 May Basic Introduction Test Time:May 4 th, 2010 Tester:PC Security Labs Test Platform:Windows XP SP3 Professional Simplified Chinese Test Methodology:On-demand scan (default
Products supported by ESAP FIREWALL PRODUCTS: Product Name. AOL Firewall (1.x) AOL Privacy Wall (2.x) AVG 8.0 [Firewall] (8.
![Products supported by ESAP FIREWALL PRODUCTS: Product Name. AOL Firewall (1.x) AOL Privacy Wall (2.x) AVG 8.0 [Firewall] (8. Products supported by ESAP FIREWALL PRODUCTS: Product Name. AOL Firewall (1.x) AOL Privacy Wall (2.x) AVG 8.0 [Firewall] (8.](/thumbs/71/65543884.jpg) Products supported by ESAP 1.4.0 FIREWALL PRODUCTS: Product Name AOL Firewall (1.x) AOL Privacy Wall (2.x) AVG 8.0 [Firewall] (8.x) AVG Firewall (7.x) AhnLab Security Pack (2.x) AhnLab V3 Internet Security
Products supported by ESAP 1.4.0 FIREWALL PRODUCTS: Product Name AOL Firewall (1.x) AOL Privacy Wall (2.x) AVG 8.0 [Firewall] (8.x) AVG Firewall (7.x) AhnLab Security Pack (2.x) AhnLab V3 Internet Security
ID: Sample Name: French.exe Cookbook: default.jbs Time: 15:57:57 Date: 24/03/2018 Version:
 ID: 51652 Sample Name: French.exe Cookbook: default.jbs Time: 15:57:57 Date: 24/03/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 51652 Sample Name: French.exe Cookbook: default.jbs Time: 15:57:57 Date: 24/03/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
Identifying Rootkit Infections Using Data Mining
 Identifying Rootkit Infections Using Data Mining Author Wu, Xin-Wen, Lobo, Desmond, Watters, Paul Published 2 Conference Title Proceedings of The 2 International Conference on Information Science and Applications
Identifying Rootkit Infections Using Data Mining Author Wu, Xin-Wen, Lobo, Desmond, Watters, Paul Published 2 Conference Title Proceedings of The 2 International Conference on Information Science and Applications
Anti-Virus Comparative No.7
 Anti-Virus Comparative No.7 On-demand detection of malicious software Date: August 2005 (2005-08) Last revision of this report: 26 th August 2005 Author: Andreas Clementi Website: http://www.av-comparatives.org
Anti-Virus Comparative No.7 On-demand detection of malicious software Date: August 2005 (2005-08) Last revision of this report: 26 th August 2005 Author: Andreas Clementi Website: http://www.av-comparatives.org
FILE :42: :44: Maldun. win7-sp1-x64 win7-sp1-x64 KVM :42: :44:39 10.
 FILE 2016-02-28 16:42:18 2016-02-28 16:44:39 141 1.4-Maldun win7-sp1-x64 win7-sp1-x64 KVM 2016-02-28 16:42:18 2016-02-28 16:44:39 10.0 invoice_copy_ppvpjb.js 9317 data CRC32 MD5 SHA1 SHA256 B05FA348 f12754f8912d54c1ede472fa56bfeec8
FILE 2016-02-28 16:42:18 2016-02-28 16:44:39 141 1.4-Maldun win7-sp1-x64 win7-sp1-x64 KVM 2016-02-28 16:42:18 2016-02-28 16:44:39 10.0 invoice_copy_ppvpjb.js 9317 data CRC32 MD5 SHA1 SHA256 B05FA348 f12754f8912d54c1ede472fa56bfeec8
Reviewer Integration and Performance Measurement for Malware Detection
 Reviewer Integration and Performance Measurement for Malware Detection Brad Miller 1, Alex Kantchelian 2, Michael Carl Tschantz 3, Sadia Afroz 3, Rekha Bachwani 4, Riyaz Faizullabhoy 2, Ling Huang 5, Vaishaal
Reviewer Integration and Performance Measurement for Malware Detection Brad Miller 1, Alex Kantchelian 2, Michael Carl Tschantz 3, Sadia Afroz 3, Rekha Bachwani 4, Riyaz Faizullabhoy 2, Ling Huang 5, Vaishaal
Honeypots observations and their usefulness
 Honeypots observations and their usefulness Gerard Wagener - TLP:WHITE CIRCL March 15, 2017 The Computer Incident Response Center Luxembourg (CIRCL) is a government-driven initiative designed to provide
Honeypots observations and their usefulness Gerard Wagener - TLP:WHITE CIRCL March 15, 2017 The Computer Incident Response Center Luxembourg (CIRCL) is a government-driven initiative designed to provide
CanSecWest/core06. Sascha Rommelfangen, Fred Arbogast. Zen and the art of collecting and analyzing malware
 CanSecWest/core06 Zen and the art of collecting and analyzing malware Sascha Rommelfangen, Fred Arbogast Outline Introduction Setup to collect malware Statistics Analysis Live Demo Future development early
CanSecWest/core06 Zen and the art of collecting and analyzing malware Sascha Rommelfangen, Fred Arbogast Outline Introduction Setup to collect malware Statistics Analysis Live Demo Future development early
ID: Sample Name: Updater.exe Cookbook: default.jbs Time: 21:09:59 Date: 18/05/2018 Version:
 ID: 6032 Sample Name: Updater.exe Cookbook: default.jbs Time: 21:09:59 Date: 1/05/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 6032 Sample Name: Updater.exe Cookbook: default.jbs Time: 21:09:59 Date: 1/05/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: Sample Name: TBSERV.exe Cookbook: default.jbs Time: 01:52:14 Date: 23/11/2017 Version:
 ID: 301 Sample Name: TBSERV.exe Cookbook: default.jbs Time: 01:52:14 Date: 23/11/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 301 Sample Name: TBSERV.exe Cookbook: default.jbs Time: 01:52:14 Date: 23/11/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: Sample Name: CRP_Force_Tool.exe Cookbook: default.jbs Time: 20:11:41 Date: 20/07/2018 Version:
 ID: 699 Sample Name: CRP_Force_Tool.exe Cookbook: default.jbs Time: 20:11:41 Date: 20/0/201 Version: 23.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 699 Sample Name: CRP_Force_Tool.exe Cookbook: default.jbs Time: 20:11:41 Date: 20/0/201 Version: 23.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
Anti-Virus Comparative No.8
 Anti-Virus Comparative No.8 Proactive/retrospective test (on-demand detection of virus/malware) Date: November 2005 (2005-11) Last revision: 28 th November 2005 Author: Andreas Clementi Website: http://www.av-comparatives.org
Anti-Virus Comparative No.8 Proactive/retrospective test (on-demand detection of virus/malware) Date: November 2005 (2005-11) Last revision: 28 th November 2005 Author: Andreas Clementi Website: http://www.av-comparatives.org
A Day in the Life of a Security Analyst. Your Guides Jer Kong Tony Townsend UVa Information Security
 A Day in the Life of a Security Analyst Your Guides Jer Kong Tony Townsend UVa Information Security Many Differing Perceptions of Our Role What Our Mothers Think We Do What Our Wives and Kids Think We
A Day in the Life of a Security Analyst Your Guides Jer Kong Tony Townsend UVa Information Security Many Differing Perceptions of Our Role What Our Mothers Think We Do What Our Wives and Kids Think We
F-PROT Antivirus Engine performance analysis
 F-PROT Antivirus Engine performance analysis By FRISK Software International For partners FRISK Software International FRISK Software International More than 20 years experience in the antivirus business
F-PROT Antivirus Engine performance analysis By FRISK Software International For partners FRISK Software International FRISK Software International More than 20 years experience in the antivirus business
Infosec Binary Analisys. dew.fgh
 dew.fgh MalFamily: Malicious MalScore: 100 File type: File size: PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive 344.03 KB (352285 bytes) Compile time: 2014-10-07
dew.fgh MalFamily: Malicious MalScore: 100 File type: File size: PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive 344.03 KB (352285 bytes) Compile time: 2014-10-07
Destructive Malware 12 February 2015
 JOINT INDIC ATOR BULLETIN Distributed as TLP: GREEN Reference Number: JIB-14-20199C Destructive Malware 12 February 2015 DISCLAIMER: This bulletin is provided as is for informational purposes only. The
JOINT INDIC ATOR BULLETIN Distributed as TLP: GREEN Reference Number: JIB-14-20199C Destructive Malware 12 February 2015 DISCLAIMER: This bulletin is provided as is for informational purposes only. The
CELAES Eusebio Sanchez Rafael Revert
 CELAES 2018 Riesgos reales en la ciberseguridad de la banca y qué acciones tomar frente a nuevos ciberataques Eusebio Sanchez eusebio.sanchezrodriguez@citibanamex.com Rafael Revert Rafael.revert@cyttek.com
CELAES 2018 Riesgos reales en la ciberseguridad de la banca y qué acciones tomar frente a nuevos ciberataques Eusebio Sanchez eusebio.sanchezrodriguez@citibanamex.com Rafael Revert Rafael.revert@cyttek.com
MRG Effitas Real Time Protection Test Project, First Quarter Q MRG Effitas Real Time Protection Test Project, First Quarter (Q2 2013)
 MRG Effitas Real Time Protection Test Project, First Quarter (Q2 2013) 1 Contents: Introduction 3 Security Applications Tested 3 Methodology used in the Test 4 Samples Used 5 Test Results 6 Conclusions
MRG Effitas Real Time Protection Test Project, First Quarter (Q2 2013) 1 Contents: Introduction 3 Security Applications Tested 3 Methodology used in the Test 4 Samples Used 5 Test Results 6 Conclusions
Why one virus engine is not enough
 GFI White Paper Why one virus engine is not enough Multiple virus engines are needed to reduce time lag between virus outbreak and signature update There is no single antivirus engine on the market that
GFI White Paper Why one virus engine is not enough Multiple virus engines are needed to reduce time lag between virus outbreak and signature update There is no single antivirus engine on the market that
Anti-Virus Comparative No.4
 Anti-Virus Comparative No.4 Proactive/retrospective test (on-demand detection of virus/malware) Date: November 2004 (2004-11) Last revision of this report: 1 st December 2004 Author: Andreas Clementi Website:
Anti-Virus Comparative No.4 Proactive/retrospective test (on-demand detection of virus/malware) Date: November 2004 (2004-11) Last revision of this report: 1 st December 2004 Author: Andreas Clementi Website:
ID: Sample Name: process.0xfffffa8004b x dmp Cookbook: default.jbs Time: 22:45:59 Date: 02/12/2017 Version: 20.0.
 ID: 38941 Sample Name: process.0xfffffa8004b120.0x480000.dmp Cookbook: default.jbs Time: 22:4:9 Date: 02/12/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information
ID: 38941 Sample Name: process.0xfffffa8004b120.0x480000.dmp Cookbook: default.jbs Time: 22:4:9 Date: 02/12/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information
RTTL Certification Test - March Language: English. March Last Revision: 8 th April
 RTTL Certification Test March 2016 Language: English March 2016 Last Revision: 8 th April 2016-1 - Introduction 1 st AMTSO Real Time Threat List (RTTL) based certification test What is the RTTL? The Real-Time
RTTL Certification Test March 2016 Language: English March 2016 Last Revision: 8 th April 2016-1 - Introduction 1 st AMTSO Real Time Threat List (RTTL) based certification test What is the RTTL? The Real-Time
Commtouch Messaging Security for Hosting Providers
 Commtouch Messaging Security for Hosting Providers September 2009 nospam@commtouch.com www.commtouch.com blog.commtouch.com About Commtouch Since 1991 NASDAQ: CTCH Profitable Double digit growth Over 100
Commtouch Messaging Security for Hosting Providers September 2009 nospam@commtouch.com www.commtouch.com blog.commtouch.com About Commtouch Since 1991 NASDAQ: CTCH Profitable Double digit growth Over 100
ID: Sample Name: filedata Cookbook: default.jbs Time: 03:13:04 Date: 23/01/2018 Version:
 ID: 4347 Sample Name: filedata Cookbook: default.jbs Time: 03:13:04 Date: 23/01/201 Version: 20.0.0 Table of Contents Analysis Report Overview Information Detection Confidence Classification Signature
ID: 4347 Sample Name: filedata Cookbook: default.jbs Time: 03:13:04 Date: 23/01/201 Version: 20.0.0 Table of Contents Analysis Report Overview Information Detection Confidence Classification Signature
ID: Sample Name: gt1dbsh09j.exe Cookbook: default.jbs Time: 19:08:18 Date: 31/08/2018 Version:
 ID: 4939 Sample Name: gt1dbsh09j.exe Cookbook: default.jbs Time: 19:0:1 Date: 31/0/201 Version: 23.0.0 Table of Contents Analysis Report gt1dbsh09j.exe Overview General Information Detection Confidence
ID: 4939 Sample Name: gt1dbsh09j.exe Cookbook: default.jbs Time: 19:0:1 Date: 31/0/201 Version: 23.0.0 Table of Contents Analysis Report gt1dbsh09j.exe Overview General Information Detection Confidence
Summary. Verdict: Malware CLASSIFICATION DETECTION SECTION HIGH LEVEL BEHAVIOR DISTRIBUTION ACTIVITY OVERVIEW
 Page 1 Summary File Name: ExternalToolz_0.8.exe File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows SHA1: 6c359ec1e0b099abf25c4f86dedb4df7dccaa62a MD5: d01dd75828dcc4ab7be745c15b4a8e35
Page 1 Summary File Name: ExternalToolz_0.8.exe File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows SHA1: 6c359ec1e0b099abf25c4f86dedb4df7dccaa62a MD5: d01dd75828dcc4ab7be745c15b4a8e35
ID: Sample Name: consulta.cpf- CNPJ.exe Cookbook: default.jbs Time: 21:07:22 Date: 14/10/2017 Version:
 ID: 34235 Sample Name: consulta.cpf- CNPJ.exe Cookbook: default.jbs Time: 21:07:22 Date: 14/10/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: 34235 Sample Name: consulta.cpf- CNPJ.exe Cookbook: default.jbs Time: 21:07:22 Date: 14/10/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: Sample Name: pccfvhbyjn.sample Cookbook: default.jbs Time: 13:15:27 Date: 18/01/2018 Version:
 ID: 43006 Sample Name: pccfvhbyjn.sample Cookbook: default.jbs Time: 13::27 Date: 1/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview Information Detection Confidence
ID: 43006 Sample Name: pccfvhbyjn.sample Cookbook: default.jbs Time: 13::27 Date: 1/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview Information Detection Confidence
Free antivirus software download windows 10
 Free antivirus software download windows 10 Search Free software download,the biggest software directory for freeware and shareware download at brothersoft.com. 2-3-2018 Protect your devices with the best
Free antivirus software download windows 10 Search Free software download,the biggest software directory for freeware and shareware download at brothersoft.com. 2-3-2018 Protect your devices with the best
Common Framework for Artifact Analysis Activities
 Common Framework for Artifact Analysis Activities European Union Agency for Network and Information Security www.enisa.europa.eu About ENISA The European Union Agency for Network and Information Security
Common Framework for Artifact Analysis Activities European Union Agency for Network and Information Security www.enisa.europa.eu About ENISA The European Union Agency for Network and Information Security
Norton Internet Security 2011 Removal Tool Windows 7
 Norton Internet Security 2011 Removal Tool Windows 7 Reg: 18-Oct-2011 log) to make sure they uncheck items so that the tool WON'T remove what it has detected. I'm 24/7 Internet worker (my own things) and
Norton Internet Security 2011 Removal Tool Windows 7 Reg: 18-Oct-2011 log) to make sure they uncheck items so that the tool WON'T remove what it has detected. I'm 24/7 Internet worker (my own things) and
ID: Sample Name: SKYDIGITAL- NEW PO.exe Cookbook: default.jbs Time: 15:55:01 Date: 15/01/2018 Version:
 ID: 42701 Sample Name: SKYDIGITAL- NEW PO.exe Cookbook: default.jbs Time: 15:55:01 Date: 15/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection
ID: 42701 Sample Name: SKYDIGITAL- NEW PO.exe Cookbook: default.jbs Time: 15:55:01 Date: 15/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection
ID: Sample Name: powershell.exe Cookbook: default.jbs Time: 11:15:45 Date: 18/02/2018 Version:
 ID: 4932 Sample Name: powershell.exe Cookbook: default.jbs Time: :1:4 Date: 18/02/2018 Version: 21.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 4932 Sample Name: powershell.exe Cookbook: default.jbs Time: :1:4 Date: 18/02/2018 Version: 21.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
Summary. Verdict: Malware CLASSIFICATION DETECTION SECTION HIGH LEVEL BEHAVIOR DISTRIBUTION ACTIVITY OVERVIEW
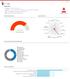 Page 1 Summary File Name: LMAOBOXPREMIUM.exe File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows SHA1: 24b8d0208fdc46b720d6c07b71949f0ebe792442 MD5: deff401baf9df67d9731da2b98407f14
Page 1 Summary File Name: LMAOBOXPREMIUM.exe File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows SHA1: 24b8d0208fdc46b720d6c07b71949f0ebe792442 MD5: deff401baf9df67d9731da2b98407f14
Accessing your Check Point VPN
 NOTE: The VPN only provides remote access to the network, any required native applications will need to be compatible with your local system. STEP 1 Open your Internet Explorer web browser and enter the
NOTE: The VPN only provides remote access to the network, any required native applications will need to be compatible with your local system. STEP 1 Open your Internet Explorer web browser and enter the
APatternRecognitionSystem for Malicious PDF Files Detection
 APatternRecognitionSystem for Malicious PDF Files Detection Davide Maiorca, Giorgio Giacinto, and Igino Corona Department of Electrical and Electronic Engineering (DIEE), University of Cagliari, Piazza
APatternRecognitionSystem for Malicious PDF Files Detection Davide Maiorca, Giorgio Giacinto, and Igino Corona Department of Electrical and Electronic Engineering (DIEE), University of Cagliari, Piazza
TERM OF REFERENCE PROVISION FOR DEVELOPMENT OF MyEMAS SYSTEM, CYBERSECURITY MALAYSIA
 1.0 BACKGROUND 1.1 ycert proposed to develop an appliance system to enhance the LebahNet v2 (Phase I Data Collection) system for Cyber Threat Research Centre research activities relating to HoneyNet project.
1.0 BACKGROUND 1.1 ycert proposed to develop an appliance system to enhance the LebahNet v2 (Phase I Data Collection) system for Cyber Threat Research Centre research activities relating to HoneyNet project.
Anti-Virus Comparative. Factsheet Business Test (August-September 2018) Last revision: 11 th October
 Anti-Virus Comparative Factsheet Business Test Language: English August-September 2018 Last revision: 11 th October 2018 https:// - 1 - Introduction This is a short fact sheet for our Business Main-Test
Anti-Virus Comparative Factsheet Business Test Language: English August-September 2018 Last revision: 11 th October 2018 https:// - 1 - Introduction This is a short fact sheet for our Business Main-Test
Anti-Virus Comparative
 Anti-Virus Comparative Malware Protection Test Consumer Products File Detection Test with Execution including false alarm test Language: English March 2018 Last Revision: 13 th April 2018 Table of Contents
Anti-Virus Comparative Malware Protection Test Consumer Products File Detection Test with Execution including false alarm test Language: English March 2018 Last Revision: 13 th April 2018 Table of Contents
Android Malware Detection Test 手机安全软件病毒检测率测试 Mar. Celebrating Technology Innovation
 Android Malware Detection Test 手机安全软件病毒检测率测试 2016 Mar Celebrating Technology Innovation 报告目录 Table of Contents P1 P2 P2 测试背景测试流程待测软件 Background Test Process Tested Software P3 P5 P5 测试结果相关信息权利说明 Test Result
Android Malware Detection Test 手机安全软件病毒检测率测试 2016 Mar Celebrating Technology Innovation 报告目录 Table of Contents P1 P2 P2 测试背景测试流程待测软件 Background Test Process Tested Software P3 P5 P5 测试结果相关信息权利说明 Test Result
J. Vilmsi Tallinn Estonia Flak Installation Guide
 Flak Installation Guide Table of Contents Terms and Definitions... 3 Flak description... 4 Flak's functions... 4 System Requirements for Flak Device... 4 Installation of Drivers... 5 Device Compatibility
Flak Installation Guide Table of Contents Terms and Definitions... 3 Flak description... 4 Flak's functions... 4 System Requirements for Flak Device... 4 Installation of Drivers... 5 Device Compatibility
PassMark S O F T W A R E
 PassMark S O F T W A R E Antivirus, Internet Security and Total Security Products Performance Benchmarking (2009) Vista/Dual Core Hardware March 2009 Document: Antivirus, Internet Security and Total Security
PassMark S O F T W A R E Antivirus, Internet Security and Total Security Products Performance Benchmarking (2009) Vista/Dual Core Hardware March 2009 Document: Antivirus, Internet Security and Total Security
ID: Sample Name: test Cookbook: default.jbs Time: 09:46:13 Date: 21/05/2018 Version:
 ID: 042 Sample Name: test Cookbook: default.jbs Time: 09:4:1 Date: 21/0/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: 042 Sample Name: test Cookbook: default.jbs Time: 09:4:1 Date: 21/0/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: Sample Name:.scr Cookbook: default.jbs Time: 09:33:32 Date: 24/12/2017 Version:
 ID: 40893 Sample Name:.scr Cookbook: default.jbs Time: 09:33:32 Date: 24/12/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
ID: 40893 Sample Name:.scr Cookbook: default.jbs Time: 09:33:32 Date: 24/12/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
ID: Sample Name: 29UPDYATHD.exe Cookbook: default.jbs Time: 19:03:31 Date: 06/04/2018 Version:
 ID: 5352 Sample Name: 29UPDYATHD.exe Cookbook: default.jbs Time: 19:03:31 Date: 06/04/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 5352 Sample Name: 29UPDYATHD.exe Cookbook: default.jbs Time: 19:03:31 Date: 06/04/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
Windows アンチウィルスインスペクタのサポートチャート
 1/46 ページ 索引 : ユーザ : エンドポイントセキュリティ : インスペクタ : アンチウィルスサポート表 : Windows アンチウィルスサポート表 > Windows アンチウィルスインスペクタのサポートチャート 今回のリリースでは FirePass は以下のアンチウィルスソフトウェアをサポートします テーブル内のプラスのサイン
1/46 ページ 索引 : ユーザ : エンドポイントセキュリティ : インスペクタ : アンチウィルスサポート表 : Windows アンチウィルスサポート表 > Windows アンチウィルスインスペクタのサポートチャート 今回のリリースでは FirePass は以下のアンチウィルスソフトウェアをサポートします テーブル内のプラスのサイン
Anti-Virus Comparative Summary Report 2008
 Anti-Virus Comparative Summary Report 2008 Awards, winners, comments Date: December 2008 Last revision: 9 th December 2008 Website: http://www.av-comparatives.org 1. Introduction At the end of every year,
Anti-Virus Comparative Summary Report 2008 Awards, winners, comments Date: December 2008 Last revision: 9 th December 2008 Website: http://www.av-comparatives.org 1. Introduction At the end of every year,
ID: Sample Name: owaauth.dll Cookbook: default.jbs Time: 06:38:57 Date: 27/04/2018 Version:
 ID: 593 Sample Name: owaauth.dll Cookbook: default.jbs Time: 0:3:5 Date: 2/04/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: 593 Sample Name: owaauth.dll Cookbook: default.jbs Time: 0:3:5 Date: 2/04/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification
AXIGEN Features and Supported Platforms
 AXIGEN Features and Supported Platforms GECAD Technologies 10A Dimitrie Pompei Blvd., BUCHAREST 2, ROMANIA Tel.: +40 21 303 20 80 +40 21 303 20 81 Last modified: 09/18/2007 Product Features v 4.0 and v
AXIGEN Features and Supported Platforms GECAD Technologies 10A Dimitrie Pompei Blvd., BUCHAREST 2, ROMANIA Tel.: +40 21 303 20 80 +40 21 303 20 81 Last modified: 09/18/2007 Product Features v 4.0 and v
Norton Internet Security 2008 Manual Uninstall Tools
 Norton Internet Security 2008 Manual Uninstall Tools To download, save and run the Norton Removal tool for versions 2003 to 2010, click Follow the on-screen instructions to uninstall Norton Internet Security.
Norton Internet Security 2008 Manual Uninstall Tools To download, save and run the Norton Removal tool for versions 2003 to 2010, click Follow the on-screen instructions to uninstall Norton Internet Security.
ID: Sample Name: dronefly.apk Cookbook: default.jbs Time: 10:24:54 Date: 07/06/2018 Version:
 ID: 001 Sample Name: dronefly.apk Cookbook: default.jbs Time: 10:24:4 Date: 0/0/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 001 Sample Name: dronefly.apk Cookbook: default.jbs Time: 10:24:4 Date: 0/0/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
Comparison Of Antivirus Software
 Comparison Of Antivirus Software 1 / 6 2 / 6 3 / 6 Comparison Of Antivirus Software This is a non-exhaustive list of notable antivirus and Internet Security software, in the form of comparison tables,
Comparison Of Antivirus Software 1 / 6 2 / 6 3 / 6 Comparison Of Antivirus Software This is a non-exhaustive list of notable antivirus and Internet Security software, in the form of comparison tables,
Antivirus. Sandbox evasion. 1
 Antivirus Sandbox evasion 1 Introduction Metasploit Metasploit Framework is a tool for developing and executing exploit code against a remote target machine. Also, Metasploit Framework provide the ability
Antivirus Sandbox evasion 1 Introduction Metasploit Metasploit Framework is a tool for developing and executing exploit code against a remote target machine. Also, Metasploit Framework provide the ability
COMPARATIVE REVIEW. WINDOWS SERVER 2003 John Hawes PLATFORM AND TEST SETS
 COMPARATIVE REVIEW WINDOWS SERVER 2003 John Hawes This month s platform is Windows Server 2003, which is not the very latest server offering from Microsoft indeed it has been succeeded by both Server 2008,
COMPARATIVE REVIEW WINDOWS SERVER 2003 John Hawes This month s platform is Windows Server 2003, which is not the very latest server offering from Microsoft indeed it has been succeeded by both Server 2008,
PCSL. PCSL IT Consulting Institute. Windows Virus Cleaning Test Report 感染型病毒清除测试报告. Celebrating Technology Innovation
 2015 IT Consulting Institute ❷ Windows Virus Cleaning Test Report 感染型病毒清除测试报告 Celebrating Technology Innovation 报告目录 Table of Contents P1 P2 P3 测试背景 Background 测试流程 Test Process 待测软件 Tested Software P4
2015 IT Consulting Institute ❷ Windows Virus Cleaning Test Report 感染型病毒清除测试报告 Celebrating Technology Innovation 报告目录 Table of Contents P1 P2 P3 测试背景 Background 测试流程 Test Process 待测软件 Tested Software P4
ID: Sample Name: MSVCR100.dll Cookbook: default.jbs Time: 16:59:36 Date: 30/04/2018 Version:
 ID: 5734 Sample Name: MSVCR100.dll Cookbook: default.jbs Time: 16:59:36 Date: 30/04/201 Version: 22.0.0 Table of Contents Analysis Report Overview Information Detection Confidence Classification Signature
ID: 5734 Sample Name: MSVCR100.dll Cookbook: default.jbs Time: 16:59:36 Date: 30/04/201 Version: 22.0.0 Table of Contents Analysis Report Overview Information Detection Confidence Classification Signature
Blackhole Networks. an Underestimated Source for Information Leaks. Alexandre Dulaunoy CIRCL - TLP:WHITE FIRST2017. Team CIRCL - Team Restena
 Blackhole Networks an Underestimated Source for Information Leaks Alexandre Dulaunoy CIRCL - TLP:WHITE Team CIRCL - Team Restena FIRST2017 Motivation and background IP darkspace or black hole is Routable
Blackhole Networks an Underestimated Source for Information Leaks Alexandre Dulaunoy CIRCL - TLP:WHITE Team CIRCL - Team Restena FIRST2017 Motivation and background IP darkspace or black hole is Routable
ID: Sample Name: meterpreter64bit.exe Cookbook: default.jbs Time: 16:01:45 Date: 24/11/2017 Version:
 ID: 0 Sample Name: meterpreter4bit.exe Cookbook: default.jbs Time: 1:01:4 Date: 24/11/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 0 Sample Name: meterpreter4bit.exe Cookbook: default.jbs Time: 1:01:4 Date: 24/11/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
Android Malware Detection Test 手机安全软件病毒检测率测试 Jun. Celebrating Technology Innovation
 Android Malware Detection Test 手机安全软件病毒检测率测试 2016 Jun Celebrating Technology Innovation 报告目录 Table of Contents P1 P2 P2 测试背景测试流程待测软件 Background Test Process Tested Software P3 P5 P5 测试结果相关信息权利说明 Test Result
Android Malware Detection Test 手机安全软件病毒检测率测试 2016 Jun Celebrating Technology Innovation 报告目录 Table of Contents P1 P2 P2 测试背景测试流程待测软件 Background Test Process Tested Software P3 P5 P5 测试结果相关信息权利说明 Test Result
How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro
 How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro Security Defender is a fake antivirus program, it should not be trusted, since it is a The program usually installs on PCs without
How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro Security Defender is a fake antivirus program, it should not be trusted, since it is a The program usually installs on PCs without
Targeted Ransomware No Longer a Future Threat
 REPORT Targeted Ransomware No Longer a Future Threat Analysis of a t argeted and manual ransomware campaign February 2016 Table of Contents Authors This report was researched and written by: Christiaan
REPORT Targeted Ransomware No Longer a Future Threat Analysis of a t argeted and manual ransomware campaign February 2016 Table of Contents Authors This report was researched and written by: Christiaan
Security Industry Market Share Analysis
 Security Industry Market Share Analysis December 2010 Introduction The Research OPSWAT releases quarterly market share reports for several sectors of the security industry. This quarter s report includes
Security Industry Market Share Analysis December 2010 Introduction The Research OPSWAT releases quarterly market share reports for several sectors of the security industry. This quarter s report includes
Prevx 3.0 v Product Overview - Core Functionality. April, includes overviews of. MyPrevx, Prevx 3.0 Enterprise,
 Prevx 3.0 v3.0.1.65 Product Overview - Core Functionality April, 2009 includes overviews of MyPrevx, Prevx 3.0 Enterprise, and Prevx 3.0 Banking and Ecommerce editions Copyright Prevx Limited 2007,2008,2009
Prevx 3.0 v3.0.1.65 Product Overview - Core Functionality April, 2009 includes overviews of MyPrevx, Prevx 3.0 Enterprise, and Prevx 3.0 Banking and Ecommerce editions Copyright Prevx Limited 2007,2008,2009
ID: Sample Name:.exe Cookbook: default.jbs Time: 17:05:50 Date: 25/12/2017 Version:
 ID: 40951 Sample Name:.exe Cookbook: default.jbs Time: 17:05:50 Date: 25/12/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
ID: 40951 Sample Name:.exe Cookbook: default.jbs Time: 17:05:50 Date: 25/12/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
How To Remove Personal Antivirus Security Pro Virus
 How To Remove Personal Antivirus Security Pro Virus When hackers break into government servers to steal your personal data, there's not a The independent labs uniformly heap praise on Kaspersky Anti-Virus
How To Remove Personal Antivirus Security Pro Virus When hackers break into government servers to steal your personal data, there's not a The independent labs uniformly heap praise on Kaspersky Anti-Virus
Firewall Antivirus For Windows Xp Avast 2012 With Key
 Firewall Antivirus For Windows Xp Avast 2012 With Key Provides also antispam and firewall protection from latest internet threats. You need at least Windows XP (with SP2) installed. Windows Vista, 7, 8,
Firewall Antivirus For Windows Xp Avast 2012 With Key Provides also antispam and firewall protection from latest internet threats. You need at least Windows XP (with SP2) installed. Windows Vista, 7, 8,
ENDPOINT SECURITY FOR BUSINESS: TECHNOLOGY IN ACTION
 ENDPOINT SECURITY FOR BUSINESS: TECHNOLOGY IN ACTION For the threats you can see and those you can t kaspersky.com/business CONTENTS Protect your business from the threats you can see and those you can
ENDPOINT SECURITY FOR BUSINESS: TECHNOLOGY IN ACTION For the threats you can see and those you can t kaspersky.com/business CONTENTS Protect your business from the threats you can see and those you can
ID: Sample Name: vscdme.exe Cookbook: default.jbs Time: 22:43:24 Date: 22/11/2017 Version:
 ID: 35 Sample Name: vscdme.exe Cookbook: default.jbs Time: 22:43:24 Date: 22//201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: 35 Sample Name: vscdme.exe Cookbook: default.jbs Time: 22:43:24 Date: 22//201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: Sample Name: MobaXterm_installer.dat Cookbook: default.jbs Time: 18:29:43 Date: 25/05/2018 Version:
 ID: 1259 Sample Name: MobaXterm_installer.dat Cookbook: default.jbs Time: 1:29:43 Date: 25/05/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection
ID: 1259 Sample Name: MobaXterm_installer.dat Cookbook: default.jbs Time: 1:29:43 Date: 25/05/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection
Firewall Antivirus For Windows Xp Full Version 2013
 Firewall Antivirus For Windows Xp Full Version 2013 Advanced Firewall, Antivirus & Anti-spyware Engine, Advanced Real-Time Antivirus, Enhanced Browser Protection, Identity Protection, Anti-Keylogging,
Firewall Antivirus For Windows Xp Full Version 2013 Advanced Firewall, Antivirus & Anti-spyware Engine, Advanced Real-Time Antivirus, Enhanced Browser Protection, Identity Protection, Anti-Keylogging,
VB100 COMPARATIVE REVIEW ON WINDOWS 7
 AUGUST 2012 Fighting malware and spam VB100 COMPARATIVE REVIEW ON WINDOWS 7 ISSN 1749-7027 INTRODUCTION A glance through the list of entrants for this desktop test shows a fairly familiar line-up. However,
AUGUST 2012 Fighting malware and spam VB100 COMPARATIVE REVIEW ON WINDOWS 7 ISSN 1749-7027 INTRODUCTION A glance through the list of entrants for this desktop test shows a fairly familiar line-up. However,
ID: Sample Name: 43letter.scr Cookbook: default.jbs Time: 11:20:31 Date: 22/12/2017 Version:
 ID: 40822 Sample Name: 43letter.scr Cookbook: default.jbs Time: 11:20:31 Date: 22/12/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: 40822 Sample Name: 43letter.scr Cookbook: default.jbs Time: 11:20:31 Date: 22/12/2017 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
