Decompression-free inspection: DPI for shared dictionary compression over HTTP
|
|
|
- Chester Snow
- 6 years ago
- Views:
Transcription
1 See discussions, stats, and author profiles for this publication at: Decompression-free inspection: DPI for shared dictionary compression over HTTP Article in Proceedings - IEEE INFOCOM March 2012 DOI: /INFCOM CITATIONS 2 READS 46 4 authors, including: Shimrit Tzur-David Jerusalem College of Engineering 1 PUBLICATION 2 CITATIONS Yaron Koral Princeton University 14 PUBLICATIONS 51 CITATIONS SEE PROFILE SEE PROFILE All in-text references underlined in blue are linked to publications on ResearchGate, letting you access and read them immediately. Available from: Anat Bremler-barr Retrieved on: 17 September 2016
2 Decompression-Free Inspection: DPI for Shared Dictionary Compression over HTTP Anat Bremler-Barr The Interdisciplinary Center Hertzelia, Israel Shimrit Tzur David The Interdisciplinary Center Hertzelia, Israel David Hay The Hebrew University Jerusalem, Israel Yaron Koral Tel Aviv University Tel Aviv, Israel Abstract Deep Packet Inspection (DPI) is the most time and resource consuming procedure in contemporary security tools such as Network Intrusion Detection/Prevention System (NIDS/IPS), Web Application Firewall (WAF), or Content Filtering Proxy. DPI consists of inspecting both the packet header and payload and alerting when signatures of malicious software appear in the traffic. These signatures are identified through pattern matching algorithms. The portion of compressed traffic of overall Internet traffic is constantly increasing. This paper focuses on traffic compressed using shared dictionary. Unlike traditional compression algorithms, this compression method takes advantage of the interresponse redundancy (e.g., almost the same data is sent over and over again) as in nowadays dynamic Data. Shared Dictionary Compression over HTTP (SDCH), introduced by Google in 2008, is the first algorithm of this type. SDCH works well with other compression algorithm (as Gzip), making it even more appealing. Performing DPI on any compressed traffic is considered hard, therefore today s security tools either do not inspect compressed data, alter HTTP headers to avoid compression, or decompress the traffic before inspecting it. We present a novel pattern matching algorithm that inspects SDCH-compressed traffic without decompressing it first. Our algorithm relies on offline inspection of the shared dictionary, which is common to all compressed traffic, and marking auxiliary information on it to speed up the online DPI inspection. We show that our algorithm works near the rate of the compressed traffic, implying a speed gain of SDCH s compression ratio (which is around 40%). We also discuss how to deal with SDCH compression over Gzip compression, and show how to perform regular expression matching with about the same speed gain. I. INTRODUCTION Many networking devices inspect the content of packets for security hazards and balancing decisions. These devices reside between the server and the client and perform Deep Packet Inspection (DPI). Using DPI, a device can examine the payload (and possibly also the header) of a packet, searching for protocol non-compliance, viruses, spam, intrusions, or other predefined criteria to decide whether the packet can pass, if it needs to be dropped or be routed to a different destination. One of the challenges in performing DPI is traffic compression. In order to save bandwidth and to speed up web browsing, most major sites use compression. W3Techs published on July 2011 a ranking breakdown report [1] which shows that 38% of the websites compress their traffic; when focusing on the top 1,000 sites, a remarkable 78% of the sites compress their traffic. As the majority of this information is dynamic, it does not lend itself to conventional caching technologies. Therefore, compression is a top issue in the Web community. The first generation of compression is intra-file compression, i.e. the file has references to back addresses. Two very common compression methods of the first generation are Gzip [2] and Deflate [3] which have been both developed in the 90 s and are very common in HTTP compression. Both methods use combination of the LZ77 algorithm and the Huffman coding. LZ77 Compression [4] reduces the string presentation size by spotting repeated strings within a sliding window of the uncompressed data. The algorithm replaces the repeated strings by (distance, length) pair, where distance indicates the distance in bytes of the repeated string and length indicates the string s length. Huffman Coding [5] receives the LZ77 symbols as input and reduces the symbol coding size by encoding frequent symbols with fewer bits. Gzip or Deflate work well as the compression for each individual response, but in many cases there is a lot of common data shared by a group of pages, namely inter-response redundancy. Therefore, compression methods of the next generation are inter-file, where there is one dictionary that can be referenced by several files. An example of a compression method that uses a shared dictionary is SDCH. Shared Dictionary Compression over HTTP (SDCH) [6] was proposed by Google Inc, thus, Google Chrome (Google s browser) supports it by default. The forecasts, by a report from Sure Start [7], are that Chrome will most likely surpass Firefox by the end of 2011 and Microsoft Internet Explorer in Thus, the spread of SDCH compression should increase to the same degree. Android is a software stack for mobile devices that includes an operating system, middleware and key applications. The Android operating system, was also introduced by Google and it is currently the world s best-selling Smartphone platform with 38.1% market share in the USA [8], [9]. SDCH code appears also in the Android platform and it is likely to be used in the near future. Therefore, a solution for pattern matching on shared dictionary compressed data is essential for this platform as well. SDCH is complement to Gzip or Deflate, i.e. it could be used before applying Gzip. On webpages containing Google search results, the data size reduction when adding SDCH compression before Gzip is about 40% better than Gzip alone. The idea of the shared dictionary approach is to transmit the data that is common to each response once and after that send
3 only the parts of the response that differ. In SDCH notations, the common data is called the dictionary and the differences are stored in a delta file. Specifically, a dictionary is composed of the data used by the compression algorithm, as well as metadata describing its scope and lifetime. The scope is specified by the domain and path attributes, thus, a user can download several dictionaries, even from the same server. Multi-patterns matching on compressed traffic requires two time-consuming phases: traffic decompression and pattern matching. Currently most security tools either do not scan compressed traffic, or they ensure that there will not be compressed traffic by re-writing the HTTP header between the original client and server. The first method harms security and may be the cause to miss-detection of malicious activity, while the second one harms the performance and bandwidth of both client and server. The few security tools that handle HTTP compressed traffic, first construct the full page by decompressing it, and then perform signatures scan. Since security tools should operate in the network speed, this option is usually not feasible. In this paper we present a novel pattern matching algorithm on SDCH. Our algorithm operates in two phases, the offline phase and the online phase. The offline phase starts when the device gets the dictionary. In this phase the algorithm uses Aho-Corasick [10] pattern matching algorithm (see details in Section II-C) to scan the dictionary for patterns and marks auxiliary information to facilitate the scan of the delta files. Upon receiving the delta file, it is scanned online using Aho- Corasick algorithm. Since the delta file eliminates repetitions of strings using references to the common strings in the dictionary, our algorithm tries to skip these reference, so each plain-text byte is scanned only once (either in the offline or the online phases). We show that we skip up to 99% of the referenced data and gain up to 56% improvement in the performance of the multi-patterns matching algorithm, compared with scanning the plain-text directly. A. Related Work String matching algorithm is an essential building block for numerous applications, therefore, it has been extensively studied [11]. Some of the fundamental algorithms are Boyer- Moore [12], which solve the problem for a single pattern and Aho-Corasick [10] and Wu-Manber [13] for multi-patterns. The basic idea of the Boyer-Moore algorithm is that more information is gained by matching patterns from the right than from the left. This allows to heuristically reduce the number of the required comparisons. The Wu-Manber algorithm uses the same observation; however, it provides a solution for the multi-pattern matching problem. The Aho-Corasick algorithm builds a Deterministic Finite Automaton (DFA) based on the patterns. Thereafter, while scanning an input text, the DFA is processed in a single pass. There are also several works that target the problem of pattern matching on Lempel-Ziv compressed data [14], [15], [16], [17]. Specifically, a solution for Gzip HTTP traffic, called ACCH, was presented in [18]. This solution utilizes the fact that the Gzip compression algorithm works by eliminating repetitions of strings using back-references (pointers) to the repeated strings. ACCH stores information produced by the pattern matching algorithm, for the already scanned uncompressed traffic, and then in case of pointers, it uses this data in order to determine if there is a possibility of finding a match or it can skip scanning this area. This solution shows that pattern matching on Gzip compressed HTTP traffic with the overhead of decompression is faster than performing pattern matching on regular traffic. A similar conclusion regards files (as opposed to traffic) was previously presented in papers [19] [21]. However, all these algorithms are geared for first-generation compression methods, while there is no pattern matching algorithms for inter-file compression schemes, such as the rapidly-spreading SDCH. B. Our Contributions We are the first to address the problem of pattern matching algorithm for shared dictionary compressed traffic. As mentioned, the spread of this approach increases rapidly, thus, a dedicated solution is essential. In addition, we have designed a novel algorithm that scans only a negligible amount of bytes more than once, as our evaluations confirm (see Section V). This is a remarkable result considering the fact that bytes in the dictionary can be referenced multiple times by different positions in one delta file and moreover, by different delta files. SDCH compression ratio is about 44%, implying that 56% of the data is copied from the dictionary. Thus, our single scan implies that our algorithm achieves 56% improvement in performance compared to scanning the plain-text file. Our algorithm also has low memory consumption. Our algorithm stores only the dictionary being used (along with some auxiliary information per dictionary). In the case of SDCH, since it was developed for web traffic, one dictionary usually supports many connections. In other words, the memory consumption depends on the number of the dictionaries and their sizes and not in the number of connections, which is the case in intra-file compression methods. Finally, an important contribution is a mechanism to deal with matching regular-expression signatures in SDCHcompressed traffic. Regular expression signatures gain an increasing popularity due to their superior expressibility [22]. We show how to use our algorithm as a building block for regular expression matching. Our experiments show that our regular expression matching mechanism gains a similar 56% boost in performance. A. The SDCH Framework II. BACKGROUND SDCH is a new compression mechanism proposed by Google Inc. In SDCH, a dictionary is downloaded (as a file) by the user agent from the server. The dictionary contains strings which are likely to appear in subsequent HTTP responses. If, for example, the header, footer, JavaScript and CSS are stored in a dictionary possessed by both user agent and server, the server can construct a delta file by substituting these elements 2
4 with references to the dictionary, and the user agent can reconstruct the original page from the delta file using these references. By substituting dictionary references for repeated elements in HTTP responses, the payload size is reduced and we can save the cross-payload redundancy. In order to use SDCH, the user agent adds the label SDCH in the Accept- Encoding field of the HTTP header. The scope of a dictionary is specified by the domain and path attributes, thus, one server may have several dictionaries and the user agent has to have a specific dictionary in order to decompress the server s compressed traffic. If the user agent already has a dictionary from the negotiated server, it adds the dictionary id as a value to the header Avail-Dictionary. If the user agent does not have the specific dictionary that was used by the server, the server sends an HTTP response with the header Get-Dictionary and the dictionary path; now, the user agent can construct a request to get the dictionary. We note that our pattern matching can run in a different machine than the server and the client (e.g., in a a security tool that operates as a proxy between them). Since our algorithm needs the correct dictionary, it can force the server to send a response with the Get-Dictionary header by deleting the Avail- Dictionary field in the client s request. B. The VCDIFF Compression Algorithm SDCH encoding is built upon the VCDIFF compression data format. VCDIFF encoding process uses three types of instructions, called delta instructions: ADD, RUN and COPY. ADD(i, str) means to append to the output i bytes, which are specified in parameter str. RUN(i,b) means to append i times the byte b. Finally, COPY(p, x) means that the interval [p, p + x) should be copied from the dictionary (that is, x bytes starting at position p). The delta file contains the list of instructions with their arguments and the dictionary is one long string composed of the characters that can be referenced by the COPY instructions in the delta file. In the rest of the paper, we ignore the RUN instruction since it is barely used and can be replaced with an equivalent ADD for our purposes. For example, suppose that the dictionary is DBEAACDBCABC, and the delta file is given by the following commands: 1. ADD (3,ABD) 2. COPY (0,5) 3. ADD (1,A) 4. COPY (4,5) 5. ADD (2,AB) 6. COPY (9,3) 7. ADD (4,AACB) 8. COPY (5,3) 9. ADD (1,A) 10. COPY (6,3) Thus, the plain-text that should be considered is therefore (bolded bytes were copied from the dictionary): ABDDBEAAAACDBCABABCAACBCDBADBC C. The Aho-Corasick Algorithm and Automaton Any networking device that is based on DPI uses some sort of a pattern matching algorithm. One of the fundamental approaches is the Aho-Corasick [10] algorithm, which our algorithm uses. The Aho-Corasick algorithm matches multiple patterns simultaneously, by first constructing a Deterministic Finite Automaton (DFA) representing the patterns set, and then, with this DFA on its disposal, processing the text in a single pass. Specifically, the DFA construction is done in two phases. First, the algorithm builds a trie of the pattern set: All the patterns are added from the root as chains, where each state corresponds to one symbol. When patterns share a common prefix, they also share the corresponding set of states in the trie. The edges of the first phase are called forward transitions. In the second phase, failure transitions are added to the trie. These edges deal with situations where, given an input symbol b and a state s, there is no forward transition from s using b. In such a case, the DFA should follow the failure transition to some state s and take a forward transition from there. This process is repeated until a forward transition is found or until the root is reached, leading to possible failure paths. The DFA in Fig. 1 was constructed for patterns set {E,BE,BD,BCD,BCAA,CDBCAB}. Solid black edges are forward transitions while red scattered edges are failure transitions. Let the label of a state s, denoted by L(s), be the concatenation of symbols along the path from the root to s. Furthermore, let the depth of a state s be the length of the label L(s). The failure transition from s is always to a state s, whose label L(s ) is the longest suffix of L(s) among all other DFA states. This implies the following property of the Aho-Corasick DFA: Property 1 If L(s ) is a suffix of L(s) then there is a failure path (namely, a path comprised only of failure transitions) from state s to state s. The DFA is traversed starting from root. When the traversal goes through an accepting state, it indicates that some patterns are a suffix of the input; one of these patterns always corresponds to the label of the accepting state. Formally, we denote by s.out put the set of patterns matched by state s; if s is not an accepting state then s.out put = /0. Finally, we denote by scan(s, b), the AC procedure when reading input symbol b while in state s; namely, transiting to a new state s after traversing failure transitions and a forward transition as necessary, and reporting matched patterns in case s.out put /0. scan(s,b) returns the new state s as an output. The correctness of the AC algorithm essentially stems from the following simple property: Property 2 Let b 1,...b n be the input, and let s 1,...,s n be the sequence of states the AC algorithm goes through, after scanning the symbols one by one (starting from the root of the DFA). For any i {0,...,n}, L(s i ) is a suffix of b 1,...,b i ; furthermore, it is the longest such suffix among all other states of the DFA. III. OUR DECOMPRESSION-FREE ALGORITHM A. Motivating Example We demonstrate the insights behind our algorithm using the following motivating example. 3
5 of COPY instructions in the delta file. Essentially, this follows from the fact that any scan that starts in the middle of the dictionary will reach states whose labels are suffixes of the states we store (recall Property 2). This, in turn, implies that there is a failure path between the states we store to the corresponding states had the scan was started in the middle of the dictionary (Property 1). The results of the scan on the above-mentioned example are as follow: (0) D (1) B (2) E (3) A (4) A (5) C (6) D (7) B (8) C s 0 s 2 s 3 s 0 s 0 s 7 s 8 s 9 s 10 (9) A (10) B (11) C s 11 s 12 s 5 Fig. 1. The Aho-Corasick Automaton corresponding to the pattern set {E,BE,BD,BCD,BCAA,CDBCAB}. Solid black edges correspond to forward transitions, while scattered red edges correspond to failure transitions. Assume that the patterns set is {E,BE,BD,BCD,BCAA,CDBCAB}, whose corresponding Aho-Corasick automaton is depicted in Fig. 1. In addition, assume the same dictionary and delta file as in the example of Section II-B. The plain-text that should be considered is: ABDDBEAAAACDBCABABCAACBCDBADBC, where we marked in bold the symbols that were copied from the dictionary, and in underline patterns that should be matched. We notice four kinds of matches: 1) Patterns that are fully contained within an ADD instruction. For example, the pattern BD is fully contained within the first instruction. 2) Patterns that are fully contained within a COPY instruction. For example, the pattern BE is fully contained within the second instruction. 3) Patterns whose prefix is within a COPY instruction. For example, the prefix of the pattern CDBCAB is within the fourth instruction. 4) Patterns whose suffix is within a COPY instruction. For example, the suffix of the pattern BCD is within the eighth instruction. Notice that there might be pattern which fall both in the third and in the fourth category (that is, their prefix is within one COPY instruction, and their suffix is within another COPY instruction). Our algorithm works in two phases. First, we preprocess the dictionary. Since the dictionary is common to many delta files, this phase runs offline. Then, we process the delta file online. We next describe the two phases, motivating by our example. The Offline Phase: In the offline phase (Pseudo code in Algorithm 1), the dictionary is scanned from the first symbol using the Aho-Corasick algorithm. For each symbol of the dictionary we store the state in which the algorithm was while scanning that symbol. In addition, we keep an ordered list of indices in which a match was found. We will show later that this information is sufficient to skip almost all the symbols Next we denote by State[ j] the state corresponding to the j-th symbol of the dictionary. If the scan reaches an accepting state (that is, a pattern was found within the dictionary), we save it in a list called Matched. In that list, we store the index of the last symbol of the matched pattern along with the pattern itself (or, equivalently, a pointer to the pattern). The list is sorted by the index of the symbol. In our example, there are two matches, implying that Matched = [ 2,{E,BE}, 10,{CDBCAB} ]. The Online Phase: In the online phase (Pseudo code in Algorithm 2), we are scanning the delta file, using the Aho- Corasick algorithm. Since the data in the ADD instruction is new (that is, it was not scanned in the offline phase), we simply scan it by traversing the automaton. When encountering a COPY (x, p) instruction, which copies the symbols b p,...,b p+x 1 from the dictionary, we are doing the following three steps: Step 1: Scan the copied symbols from the dictionary one by one, until when scanning a symbol b p+i we reach a state in the automaton whose depth is less or equal to i. As we shall prove later, in this scan we ensure to find all patterns whose suffix is within this COPY instruction (the fourth category of patterns). Notice that the depth of a state essentially indicates the length of meaningful suffix of the input when reaching this state. Therefore, if we reach a state whose depth is less than the number of copied symbols scanned so far, any pattern that ends within the COPY instruction is fully contained in it (the second category). If we reached the end of the copied data (that is, symbol b p+x 1 ) before encountering such a small depth state, we naturally proceed to the next instruction as all the copied symbol were scanned. Otherwise, we proceed to the next steps. Step 2: We check the Matched list to find any patterns in the dictionary that ends within interval [x,x + p). If such patterns are found, we check by their length that they are indeed fully contained within that interval. Hence, we are ensured to find all the patterns of the second category. Step 3: We obtain the state State[p + x 1]; namely, the state corresponding to the last copied symbol. From that state, we follow failure transitions in the automaton, until we reach a state s whose depth is less or equal to x. (since all failure 4
6 TABLE I STEP BY STEP EXECUTION OF OUR ALGORITHM ON THE EXAMPLE OF SECTION III-A 1. ADD (3,ABD) s 0 A s0 B s2 D s4 Report pattern BD (by state s 4 ) 2. COPY (0,5) s 4 D s0. Stop scanning copied bytes (depth(s 0 ) 1). Check Matched for indices [0, 5). Report patterns E, BE (from Matched list). Go to State[4] = s 0. depth(s 0 ) ADD (1,A) s 0 A s0 4. COPY (4,5) No scanning of copied bytes (depth(s 0 ) 0). Check Matched for indices [4, 9). Go to State[8] = s 10. depth(s 10 ) = ADD (2,AB) s 10 A s11 B s12 Report pattern CDBCAB (by state s 12 ) 6. COPY (9,3) s 12 A s0. Stop scanning copied bytes (depth(s 0 ) 1). Check Matched for indices [9, 12). Match was found, but does not fit the interval. Go to State[11] = s 5. depth(s 5 ) = ADD (4,AACB) s 5 A s13 A s14. Report pattern BCAA (by state s 14 ) s 14 C s7 B s2. 8. COPY (5,3) s 2 C s5 D s6 Report pattern BCD (by state s 6 ) s 6 B s9 (reached end of instruction) A 9. ADD (1,A) s 9 s0 10. COPY (6,3) No scanning of copied bytes (depth(s 0 ) 0). Check Matched for indices [6, 9). Go to State[8] = s 10. depth(s 10 ) = 4 > 3. f ailure s 10 s 5. depth(s 5 ) = 2 3. paths in the automaton end in the root whose depth is 0, we are guaranteed to eventually stop). Properties 1 and 2 yield that L(s) is the longest suffix of b p,...,b p+x 1 (among all states labels). Since we have dealt in Step 1 with all patterns that begin before b p, the meaningful suffix of the input starts after b p. This implies that the Aho-Corasick algorithm would have been also in state s, had it scanned all the symbols b p,...,b p+x 1 one by one. Therefore, when processing the next instructions the algorithm behaves exactly the same, guaranteeing to find all patterns of the third category. In addition, this implies identical scans also on ADD instructions, therefore guaranteeing to find all patterns of the first category. Table I shows a step-by-step execution of our algorithm on the above mentioned delta file. The algorithm reports the same matched patterns, and reaches the same state (s 5 ) as if it scanned the plain-text. However, the algorithm skips most of the symbols (14 out of 19) within the COPY instructions. We will further investigate the portion of skipped symbol in Section V. B. Correctness The pseudo-code of the offline phase is presented in Algorithm 1, while Algorithm 2 depicts the online phase. Given a dictionary and a delta-file, we denote by b 1,...,b n, the plain-text string obtained by applying the instructions of the delta-file. A symbol b i is scanned if Algorithm 2 applies Aho-Corasick scan operation to obtain the next state after reading b i (that is, either in Line 6, Line 9, or Line 14 of Algorithm 2); otherwise, we say that the symbol b i is Algorithm 1 The Offline Phase 1: Patterns[] getpatterns(patternsfile) 2: AC new Aho Corasick() 3: AC.CreateTree(Patterns[]) 4: Dict loaddictionary(dictfile) 5: cur state AC.root 6: for i = 0;i < dict.length;i + + do 7: cur state AC.scan(cur state, dict[i]) 8: State[i] cur state 9: if cur state.out put /0 then 10: Matched.addLast( i, cur state.out put ) Algorithm 2 The Online Phase 1: cur state AC.root 2: while hasnextinstruction(deltafile) do 3: inst getnextinstruction(deltafile) inst is a structure containing the instruction along with its parameters 4: if inst.type==add then inst.str is the string to append, inst.len is its length 5: for i = 0;i < inst.len;i + + do 6: cur state AC.scan(cur state, inst.str[i]) 7: else if inst.type==run then inst.literal is the symbol to append, inst.len is the number of times 8: for i = 0;i < len;i + + do 9: cur state AC.scan(cur state, inst.literal) 10: else inst.type is COPY. inst.addr is the starting position; inst.len is the length of the copied string 11: literals Dict[inst.addr,..., inst.addr+inst.len 1] 12: i = 0 13: while (cur state.depth > i and i inst.len) do 14: cur state AC.scan(cur state, literals[i]) 15: i : if i inst.len then 17: target state State[inst.addr + inst.len 1] 18: while target state.depth > inst.len do 19: target state target state. f ailure the failure transition of traget state 20: cur state target state 21: for all x,p Matched do 22: if x [inst.addr, inst.addr+inst.len 1] then 23: for all p P do 24: if x p.length inst.addr then 25: report pattern p skipped. Notice that all skipped symbols were copied from the dictionary using a COPY instruction. We further denote by z 0,z 1,...,z n the states which Aho-Corasick algorithm traverses when running on the plain text string b 1,...,b n (note that z 0 = s 0, the initial state before reading b 1 ). Finally, we assume, without loss of generality and only for the ease of notations, that the first symbol of a COPY instruction is scanned (this holds anyway, unless the automaton is in state s 0 before the COPY instruction). Lemma 1 Before each scanned symbol b j, Algorithm 2 is in state z j 1. Proof: For each scanned symbol in b j {b 1,...,b n }, let pos(b j ) be the number of scanned symbol before b j. The proof follows by induction on pos(b j ). 5
7 Initially, Algorithm 2 is in state s 0 = z 0 and the claim follows since the first symbol is scanned. Assume now that the claim holds for all scanned symbols whose pos value is less than pos(b j ). We next prove it holds for b j by distinguishing between the following two cases: First, if b j 1 is a scanned symbol, then, by the induction hypothesis, Algorithm 2 is in state z j 2 before reading b j 1. Since b j 1 is a scanned symbol, Algorithm 2 applies, by definition, Aho-Corasick scan operation to obtain the next state after reading b j 1, and therefore transits to state z j 1, and the claim follows. Otherwise, the state before reading b j was set in Line 20 of Algorithm 2, which was executed while processing a COPY instruction. Denote by a the index (in the plain text) of the first symbol that was copied by that COPY instruction; the copied symbols are therefore b a,...,b j 1. Notice that Line 20 is reached only if the value of i in Line 16 is less than or equal to j a. This implies that all the symbols b a,...,b a+i 1 are scanned, and that the label of the state after scanning b a+i 1 is a proper suffix of b a,...,b a+i 1 (otherwise the condition in Line 13 does not hold). By the induction hypothesis, since b a+i 1 is a scanned symbol that precedes b j, Algorithm 2 is in state z a+i 2 before scanning b a+i 1, and in state z a+i 1 after applying the scan procedure in Line 14. This implies that L(z a+i 1 ) is a proper suffix of b a,...,b a+i 1. Notice that when scanning the j (i a) symbols b i+a,...,b j 1, the depth of the state can increase by at most j (i a). Hence L(z j 1 ) is a proper suffix of b a,...,b j 1 ; since these symbols are a suffix of the plain text, L(z j 1 ) is the longest such suffix among all states of the automaton (recall Property 2 in Section II-C). It is important to notice that all these bytes were copied from the dictionary; denote by c x,...,c y their corresponding indices in the dictionary. Consider now the value of State[y], which obtained by scanning the same DFA from the beginning. Property 2 implies that L(State[y]) is the longest suffix, among all DFA s states, of the sequence c 1,...,c y, which implies that L(z j 1 ) is a suffix of L(State[y]). Thus, by Property 1, there is a path of failure transitions on the automaton from State[y] to z j 1 ; this path is traversed in Lines Since L(z j 1 ) is the longest such suffix with length less than j a, the traversal is stopped exactly in z j 1. Thus, Algorithm 2 transits to state z j 1 also in this case, concluding our proof. Lemma 2 All matched patterns that end with a skipped symbol are fully contained within a single COPY instruction. Proof: Assume towards a contradiction that this is not a case, and consider the other three possibilities. First, for patterns that are fully contained within an ADD instruction, all symbols of ADD instructions are scanned and therefore these patterns cannot end with a skipped symbol. Similarly, for patterns whose prefix is within a COPY instruction and suffix is in an ADD instruction, the last symbol of these patterns is always scanned. Finally, we deal with patterns whose suffix is within a COPY instruction, but are not entirely within that COPY instruction. Consider the symbols b a,...,b j 1 which were copied in that COPY instruction, and assume that b k is the last symbol of the pattern within these symbol (a k < j). Since the pattern exceeds the copied symbols, it implies that L(z k ) is longer than k a symbols. Since a depth of successive states can increase only by one, it implies that the depth of all states z l for a l k is strictly larger than l a. This implies that the condition of Line 13 holds for all these states, including b k. This, in turn, implies that b k is scanned (in Line 14), contradicting the assumption that it was skipped. Notice that all patterns that are fully contained within a single COPY instruction are found using the Matched list in Lines Hence, Lemmas 1 and 2 along with this fact, immediately yield the following theorem: Theorem 3 Our algorithm reports exactly the same matched patterns as Aho-Corasick algorithm, which runs on the plaintext. C. Optimizations In this section, we will present several optimizations to our basic algorithm to enhance its online running time. These optimizations trade running time with modest memory increase. 1) Efficient pattern lookups in the Matched list: Let n be the length of the Matched list. The pattern lookups in the Matched list is performed in Lines of Algorithm 2 and runs in O(n). A common way to reduce this running time is to save the Matched list as a balanced tree or as a skip list [23]. In such a case, the running time to find the first index which is larger than the copied address is only O(logn); then, the elements of Matched are checked one by one until the first element with index outsize the copied data is encountered. Another option, that trades memory with time, is to add an array of pointers, denoted by MatchedPointers, of the dictionary size (that is, with the same size as the State array). Element MatchedPointers[i] contains a pointer to an element x,p Matched such that x is the smallest index that is greater or equal to i. This data structure reduces the running time to find the first index which is larger than the copied address to O(1) (a single lookup in the MatchedPointers array). Alternatively, given a COPY (x, p) instruction, one can cache the corresponding internal matches within [p, p + x 1] in a hash-table whose key is (x, p). In such a case, when the exact COPY appears again, one can obtain all the matches in a single access to that hash-table. Since the dictionary usually contains common phrases (e.g., HTML commands) that are used again and again, our experiments show that such a cache is extremely efficient. Specifically, during a search on 100 delta files with the same dictionary, the portion of cache hits rises very fast and becomes almost 100%. After a sharp learning curve, the average cache hits on the last 90 files was 99.4% and the average on the last 50 files was 99.7%. 2) Eliminating the traversal of failures paths: Failure path traversal is done at the end of the COPY instruction processing in Lines of Algorithm 2. 6
8 Notice that the failure paths depends only on the state saved by Algorithm 1, thus one can perform the failure path traversal in the offline phase and save the entire path in the State array. For example, State[8] of the example of Section III-A, which contains the state s 10 can be replaced by the entire failure path starting at s 10 : (s 10,s 5,s 7,s 0 ). Furthermore, this path can be saved in a tree-based structure according to the depth of the different states. Thus, in order to find the appropriate state in Line 20, one should only perform a logarithmic (in the failure path length) number of operations. In practice, failure path traversals impose almost no overhead on the running time of Algorithm 2, as we detail in Section V. D. Dealing with Gzip over SDCH SDCH delta file are usually compressed by Gzip to decrease its size even further. In such a case, the client needs to first decompress (using Gzip) the file and then to decompress it using the dictionary to get the plain-text. Our algorithm requires that the compressed traffic has to be unzipped first; then, instead of decompress the SDCH compression, the resulting delta file is passed to our algorithm. We note that Gzip decompression is a cheap operation compared to pattern matching. Furthermore, as mentioned above, SDCH compression ratio is around 44%, i.e. 56% of the data is copied from the dictionary. This numbers imply that even if the algorithm has to unzip the delta file before it scans it, we still improve the performance by around 56%. IV. REGULAR EXPRESSIONS INSPECTION Regular expressions become an integral part of patterns that are used for security purposes. In Snort, an open source network intrusion prevention and detection system [24], 55% of the rules contain regular expression. Each regular expression pattern contains one or more string tokens along with one or more regular expression tokens. For example the regular expression \d{6}abcde\s \d*xyz$ has the string tokens ABCDE, , XYZ, and the regular expression tokens \d{6}, \s+ and \d*. Like Snort, we treat the string tokens as anchors and insert them to the DFA. Only when all the anchors of a single regular expression pattern are matched, the regular expression tokens are examined (e.g., using a regular expressions engine). Furthermore, in most cases, we can limit the pattern search in at least one direction; namely, if before the first (resp., after the last) anchor, all tokens have a limited size (i.e., do not contain + or * ), there is a bounded number of characters we should examine before (resp., after) the matched position of the anchor. In the above example, if we matched the anchor ABCDE at position x 1 and the anchor XYZ at position x 2, the left bound, l bound is x 1 10 and the right bound, r bound, is x 2. Thus, the interval [x 1 10,x 2 ] should be passed to the regular expressions engine for re-examination. Note that l bound can be 0 and r bound can be the size of the file if there is an unlimited length token before the first anchor or after the last anchor. To conclude, our regular expression inspection works as follows: First, constant strings (a.k.a anchors) are extracted from the regular expression offline. Then, our algorithm is applied on the SDCH-compressed traffic with the anchors as the patterns set. The anchors have to be matched in the same order of there appearances in the pattern. We save all the possible l bound values (derived by the matched positions of the first anchor) and the maximal value of r bound. Finally, we check if there is a regular expression which all its anchors were matched. If there is, for each l bound value, we run an offthe-shelf regular expression engine from this value until, either we scan a character that yields a mismatch, or we have a full pattern match. In most of the cases, as we detail in Section V, we are scanning a few bytes for each l bound value, and the total number of scanned bytes in the interval is significantly less than its size. Note that since we match the anchors at the correct order, the last scan is guaranteed to end before r bound. V. EXPERIMENTAL RESULTS Data Sets: Nowadays, Google s servers are the most prominent web servers that use shared dictionary compressed traffic. Furthermore, Google search is a fertile ground for popups, banners or any objectionable content. Thus, we evaluate our algorithm with Google search result files. We first downloaded the dictionary from google.com and used the 1000 most popular Google search queries (for each such query, we constructed an HTTP request and got a SDCH-compressed webpage, which we use as an input file). The signatures data sets are drawn from a snapshot of Snort rules as of October 2010 [24]. We note that shared dictionary compressed traffic is mainly used on the traffic from the server side to the client side, which is not the case supported by most of the underlying rules within Snort. Still, in order to perform experiments using regular expressions we have extracted all Perl Compatible Regular Expressions (PCREs) from rules matching two header groups differing in the destination port (any and $HTTP PORTS). There are 40 rules from the former group and 423 rules from the latter. Since the input files do not contain many matches, specifically long matches are rare, we also constructed for each input file a synthetic patterns file, in the following manner: We calculated the length distribution of Snort s patterns and we randomly pick lengths from this distribution. For each length value l, we took a sequence of l characters from the uncompressed version of the input file and add them as a pattern to the patterns file for the specific input file. We stop when the total length of the selected patterns is equal to the input file size. As a result, we have 1000 input files, each with its own patterns file, such that each pattern in that file has at least one match in the corresponding input file. We call this case the synthetic case. Time Reduction: We compared the execution time of our algorithm to an execution time of a naïve algorithm that first decompresses the file and then applies the Aho-Corasick algorithm on the plain-text. Our experiments show a significant improvement: on average, the execution time of our algorithm 7
9 25 20 States Depth Depth after One Failure Transition Depth after Two Failure Transition Copy Value Length Regular Files Synthetic Case Optimal Ratio 0.65 % of Files Scan Ratio State Depth/Copy Value Length Compression Ratio Fig. 2. The depth of first three states of each failure path (synthetic case) compared to the length of the COPY instructions. is only 34% of the time it takes the naïve algorithm to complete. It is important to note that some components of the naïve implementation are done using off-the-shelf software. Hence, we chose to take the following conservative approach in estimating the time reduction; our approach ignores completely the decompression stage of the naïve implementation and therefore it underestimates our performance gain. Notice that our algorithm run time depends on the number of scanned bytes (Algorithm 2, Lines 6, 9, and 14) and the failure transitions it takes (Algorithm 2, Lines 18 19). Thus, our main figure of interest is the ratio between the number of the bytes our algorithm scans and these failure transitions, in addition to the size of the plain text (scanned by the naïve algorithm); namely, scan-ratio = scanned bytes + failure transitions taken size of the plain text Note that the different bytes of the plain-text can be classified by the type of their corresponding SDCH instruction. Let add be the number of bytes generated by either ADD or RUN instruction (the number of bytes generated by a RUN instruction is negligible) and copy be the number of bytes generated by a COPY instruction. Furthermore, we denote by copy scanned the number of bytes generated by a COPY instruction and scanned by our algorithm (that is, in Line 14). Thus, Equation (1) can be rewritten as scan-ratio = add + copy scanned + failure transitions taken add + copy Our experiments show that even in the synthetic case in most of the files the algorithm takes no more than 2 failure transitions. The maximum number of failure transitions the algorithm takes is 19 (it occurs only in a single file), and the average number of transitions per file is 2.35; this is extremely low considering an average of 557 COPY instructions per file. This low number is explained by examining the relation between the length of the COPY instructions and the depth of the states in the State array (corresponding to the dictionary file), as shown in Fig. 2. In any case where that length is larger than the depth of the state, no failure transition is taken (recall Line 18 in Algorithm 2). We also depicted the histograms (1) Fig. 3. Comparison between the scan-ratio and compression-ratio for the real-life and synthetic cases. The line depicts the best achievable scan-ratio. of depth after a single failure transition and after two failure transitions; these histograms show that even in the rare case where a failure transition is taken, the failure path traversal is stopped almost immediately. We compare the scan-ratio with the compression-ratio add /( add + copy ); namely, the fraction of bytes that were generated using ADD instructions compared to the total number of bytes (or equivalently, the ratio between the size of the compressed text and the plain text). Note that the best achievable scan-ratio is equal to the compression-ratio (when copy scanned = 0). Furthermore, the better the compression-ratio, the better the scan-ratio is, because more bytes are copied and therefore, potentially, less bytes should be scanned. Fig. 3 presents this exact relation for the input files with Snort s patterns and for the input files in the synthetic case. With Snort s patterns, the input files do not contain long patterns so the algorithm does not reach states with high depth. Therefore, the condition in Line 13 of Algorithm 2 rarely holds and the scan-ratio almost equals the compression-ratio for any compression-ratio value. In the synthetic case, the input files contain patterns of all lengths and the algorithm reaches states with high depth. In this case, the algorithm has to scan several bytes until the number of scanned bytes is equal or greater than the depth of the current state. Thus, for the synthetic case, the scan-ratio is between 1.05 to 1.2 times the compression-ratio, and it depends on the compression-ratio value. To conclude, these figures imply that we achieve almost optimal time reduction, which equals to the compression ratio. Regular Expressions: In order to evaluate the scan ratio with the regular expression patterns, we have to calculate the number of extra bytes the algorithm scans when it matches all the anchors of such a pattern. Since matches are in general infrequent [25], the regular expression engine is not executed often (on average, we have only 5 executions per file). Furthermore, even when all the anchors are matched, the engine will not have scan more than a few bytes. Let regexp scan be the bytes that are scanned by the regular expression engine. The scan ratio from Equation V is redefined to include these characters by adding regexp scan to its numerator. Fig. 4 presents the relation between the compression ratio to the 8
10 Scan Ratio Regular Expression Scan Optimal Ratio Compression Ratio Fig. 4. Comparison between the scan-ratio when considering also regular expression matching and compression-ratio for the real-life case. redefined scan ratio. On average, the overhead of the regular expression is around 1% which is almost negligible; the scanratio stays remarkably close to the optimal value. Note that the minimal scan ratio of any regular expression engine that scans the uncompressed file is 100%, i.e. every byte is scanned at least once. An engine that performs one full scan for the anchors and then a scan for regular expression tokens (like Snort), inspects all bytes once, in the case where not all string anchoress are matched, and more than once otherwise. Memory Consumption: Let n be the size of the dictionary, k be the size of the Matched list, and p the number of bits required to represent a pointer in the system. The memory consumption of our algorithm is np+2kp, where the first term is for holding the values of the elements in State array, and the second term is for the Matched list (each of its k element holds a pointer to the dictionary and a pointer to the patterns). Searching for Snort patterns on google.com dictionary yields a Matched list of size approximately (we ignored matches of patterns of length 1 which can be dealt separately). In our given input, we need no more than 17 bits to address either a byte in a dictionary or a state in the DFA, therefore the memory consumption is bits = 420 KB for n = 116 KB. This memory consumption can be further reduced using a variable-length pointer encoding. VI. CONCLUSIONS This paper presents a novel pattern matching algorithm on shared dictionary compressed traffic, which scans 99% of the bytes only once: around 56% of these bytes are scanned in an offline phase, implying that it gain up to 56% improvement in the performance over multi-patterns matching algorithm that scans the plain-text. In addition, our algorithm has low memory consumption (around 420 KB for today s dictionary). Our algorithm can run on two different environments. First, it can run within a security tool that performs DPI and therefore has to be deployed with a pattern matching algorithm. In addition, it can run in a single user environment, such as PC, tablet or cellular phone. The performance of all these tools is dominated by the speed of their stringmatching algorithms [26], therefore our algorithm provides a real improvement when dealing with SDCH-compressed traffic. In addition, due to its low memory footprint, the algorithm can be easily deployed in nowadays environments. Our future work includes methods to exploits the interplay between a Gzip compression which is performed over an SDCH-compressed file. REFERENCES [1] W3Techs, Usage of compression broken down by ranking. [Online]. Available: ranking [2] P. Deutsch, Rfc1952 gzip file format specification version 4.3, IETF RFC 1952, [3], Deflate compressed data format specification version 1.3, IETF RFC 1951, [4] J. Ziv and A. Lempel, A universal algorithm for sequential data compression, IEEE Trans. Inf. Theory, pp , May [5] D. Huffman, A method for the construction of minimum-redundancy codes, Proceedings of IRE, pp , [6] B. M. J. Butler, W. Lee and K. Mixter, A proposal for shared dictionary compression over http, Google Inc., Tech. Rep., [7] SureStart, Google chrome tops 20% market share for june [Online]. Available: google-chrome-tops-20-market-share-for-june-2011/ / [8] T. Virki and S. Carew, Google topples nokia from smartphones top spot, Reuters. [Online]. Available: /01/31/us-google-nokia-idUSTRE70U1VW [9] Canalys, Googles android becomes the worlds leading smart phone platform. [Online]. Available: r html [10] A. Aho and M. Corasick, Efficient string matching: an aid to bibliographic search, Commun. of the ACM, pp , [11] B. W. Watson and G. Zwaan, A taxonomy of keyword pattern matching algorithms, Eindhoven University of Technology, Tech. Rep. 27, [12] R. Boyer and J. Moore, A fast string searching algorithm, Commun. of the ACM, pp , October [13] S. Wu and U. Manber, A fast algorithm for multi-pattern searching, Department of Computer Science, University of Arizona, Arizona, Tech. Rep. TR-94-17, May [14] A. Amir, G. Benson, and M. Farach, Let sleeping files lie: Pattern matching in z-compressed files, J. Comput. Syst. Sci., pp , [15] T. Kida, M. Takeda, A. Shinohara, and S. Arikawa, Shift-and approach to pattern matching in lzw compressed text, in CPM, 1999, pp [16] G. Navarro and M. Raffinot, A general practical approach to pattern matching over ziv-lempel compressed text, in CPM, 1999, pp [17] G. Navarro and J. Tarhio, Boyer-moore string matching over ziv-lempel compressed text, in CPM, 2000, pp [18] A. Bremler-Barr and Y. Koral, Accelerating multi-patterns matching on compressed http traffic, in IEEE INFOCOM, 2009, pp [19] U. Manber, A text compression scheme that allows fast searching directly in the compressed file, ACM Trans. Inf. Syst., pp , [20] N. Ziviani, E. S. de Moura, G. Navarro, and R. Baeza-Yates, Compression: A key for next-generation text retrieval systems, Computer, vol. 33, pp , November [21] M. Takeda, Y. Shibata, T. Matsumoto, T. Kida, A. Shinohara, S. Fukamachi, T. Shinohara, and S. Arikawa, Speeding up string pattern matching by text compression. the dawn of a new era. Trans. Inf. Process. Soc. Jpn., no. 3, pp , [22] M. Becchi and S. Cadambi, Memory-efficient regular expression search using state merging, in IEEE INFOCOM, may 2007, pp [23] W. Pugh, Skip lists: A probabilistic alternative to balanced trees, Commun. of the ACM, no. 6, pp , [24] Snort, [25] A. Luchaup, R. Smith, C. Estan, and S. Jha, Speculative parallel pattern matching, will appear in June 2011 issue of the IEEE Transactions on Information Forensics and Security, [26] M. Fisk and G. Varghese, An analysis of fast string matching applied to content-based forwarding and intrusion detection, Techical Report CS (updated version),
Shift-based Pattern Matching for Compressed Web Traffic
 The Interdisciplinary Center, Herzlia Efi Arazi School of Computer Science Shift-based Pattern Matching for Compressed Web Traffic M.Sc. Dissertation for Research Project Submitted by Victor Zigdon Under
The Interdisciplinary Center, Herzlia Efi Arazi School of Computer Science Shift-based Pattern Matching for Compressed Web Traffic M.Sc. Dissertation for Research Project Submitted by Victor Zigdon Under
Towards A Fast Packet Inspection over Compressed HTTP Traffic
 Towards A Fast Packet Inspection over Compressed HTTP Traffic Xiuwen Sun, Kaiyu Hou, Hao Li, Chengchen Hu Department of Computer Science and Technology Xi an Jiaotong University Email: {silvin, immike}@stu.xjtu.edu.cn,
Towards A Fast Packet Inspection over Compressed HTTP Traffic Xiuwen Sun, Kaiyu Hou, Hao Li, Chengchen Hu Department of Computer Science and Technology Xi an Jiaotong University Email: {silvin, immike}@stu.xjtu.edu.cn,
Deep Packet Inspection of Next Generation Network Devices
 Deep Packet Inspection of Next Generation Network Devices Prof. Anat Bremler-Barr IDC Herzliya, Israel www.deepness-lab.org This work was supported by European Research Council (ERC) Starting Grant no.
Deep Packet Inspection of Next Generation Network Devices Prof. Anat Bremler-Barr IDC Herzliya, Israel www.deepness-lab.org This work was supported by European Research Council (ERC) Starting Grant no.
Project Proposal. ECE 526 Spring Modified Data Structure of Aho-Corasick. Benfano Soewito, Ed Flanigan and John Pangrazio
 Project Proposal ECE 526 Spring 2006 Modified Data Structure of Aho-Corasick Benfano Soewito, Ed Flanigan and John Pangrazio 1. Introduction The internet becomes the most important tool in this decade
Project Proposal ECE 526 Spring 2006 Modified Data Structure of Aho-Corasick Benfano Soewito, Ed Flanigan and John Pangrazio 1. Introduction The internet becomes the most important tool in this decade
Towards a Fast Regular Expression Matching Method over Compressed Traffic
 Towards a Fast Regular Expression Matching Method over Compressed Traffic Xiuwen Sun, Hao Li, Xingxing Lu, Dan Zhao, Zheng Peng, Chengchen Hu Department of Computer Science and Technology Ministry of Education
Towards a Fast Regular Expression Matching Method over Compressed Traffic Xiuwen Sun, Hao Li, Xingxing Lu, Dan Zhao, Zheng Peng, Chengchen Hu Department of Computer Science and Technology Ministry of Education
MODELING DELTA ENCODING OF COMPRESSED FILES. and. and
 International Journal of Foundations of Computer Science c World Scientific Publishing Company MODELING DELTA ENCODING OF COMPRESSED FILES SHMUEL T. KLEIN Department of Computer Science, Bar-Ilan University
International Journal of Foundations of Computer Science c World Scientific Publishing Company MODELING DELTA ENCODING OF COMPRESSED FILES SHMUEL T. KLEIN Department of Computer Science, Bar-Ilan University
Modeling Delta Encoding of Compressed Files
 Modeling Delta Encoding of Compressed Files EXTENDED ABSTRACT S.T. Klein, T.C. Serebro, and D. Shapira 1 Dept of CS Bar Ilan University Ramat Gan, Israel tomi@cs.biu.ac.il 2 Dept of CS Bar Ilan University
Modeling Delta Encoding of Compressed Files EXTENDED ABSTRACT S.T. Klein, T.C. Serebro, and D. Shapira 1 Dept of CS Bar Ilan University Ramat Gan, Israel tomi@cs.biu.ac.il 2 Dept of CS Bar Ilan University
Project Proposal. ECE 526 Spring Modified Data Structure of Aho-Corasick. Benfano Soewito, Ed Flanigan and John Pangrazio
 Project Proposal ECE 526 Spring 2006 Modified Data Structure of Aho-Corasick Benfano Soewito, Ed Flanigan and John Pangrazio 1. Introduction The internet becomes the most important tool in this decade
Project Proposal ECE 526 Spring 2006 Modified Data Structure of Aho-Corasick Benfano Soewito, Ed Flanigan and John Pangrazio 1. Introduction The internet becomes the most important tool in this decade
Small-Space 2D Compressed Dictionary Matching
 Small-Space 2D Compressed Dictionary Matching Shoshana Neuburger 1 and Dina Sokol 2 1 Department of Computer Science, The Graduate Center of the City University of New York, New York, NY, 10016 shoshana@sci.brooklyn.cuny.edu
Small-Space 2D Compressed Dictionary Matching Shoshana Neuburger 1 and Dina Sokol 2 1 Department of Computer Science, The Graduate Center of the City University of New York, New York, NY, 10016 shoshana@sci.brooklyn.cuny.edu
Multiple-Pattern Matching In LZW Compressed Files Using Aho-Corasick Algorithm ABSTRACT 1 INTRODUCTION
 Multiple-Pattern Matching In LZW Compressed Files Using Aho-Corasick Algorithm Tao Tao, Amar Mukherjee School of Electrical Engineering and Computer Science University of Central Florida, Orlando, Fl.32816
Multiple-Pattern Matching In LZW Compressed Files Using Aho-Corasick Algorithm Tao Tao, Amar Mukherjee School of Electrical Engineering and Computer Science University of Central Florida, Orlando, Fl.32816
Modeling Delta Encoding of Compressed Files
 Shmuel T. Klein 1, Tamar C. Serebro 1, and Dana Shapira 2 1 Department of Computer Science Bar Ilan University Ramat Gan, Israel tomi@cs.biu.ac.il, t lender@hotmail.com 2 Department of Computer Science
Shmuel T. Klein 1, Tamar C. Serebro 1, and Dana Shapira 2 1 Department of Computer Science Bar Ilan University Ramat Gan, Israel tomi@cs.biu.ac.il, t lender@hotmail.com 2 Department of Computer Science
Bit-Reduced Automaton Inspection for Cloud Security
 Bit-Reduced Automaton Inspection for Cloud Security Haiqiang Wang l Kuo-Kun Tseng l* Shu-Chuan Chu 2 John F. Roddick 2 Dachao Li 1 l Department of Computer Science and Technology, Harbin Institute of Technology,
Bit-Reduced Automaton Inspection for Cloud Security Haiqiang Wang l Kuo-Kun Tseng l* Shu-Chuan Chu 2 John F. Roddick 2 Dachao Li 1 l Department of Computer Science and Technology, Harbin Institute of Technology,
Indexing and Searching
 Indexing and Searching Introduction How to retrieval information? A simple alternative is to search the whole text sequentially Another option is to build data structures over the text (called indices)
Indexing and Searching Introduction How to retrieval information? A simple alternative is to search the whole text sequentially Another option is to build data structures over the text (called indices)
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006
 2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
Joint Entity Resolution
 Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
Fast Multi-Pattern Matching Algorithm on Compressed Network Traffic
 SECURITY SCHEMES AND SOLUTIONS Fast Multi-Pattern Matching Algorithm on Compressed Network Traffic Hao Peng, Jianxin Li, Bo Li, M. Hassan Arif School of Computer Science and Engineering, Beihang University,
SECURITY SCHEMES AND SOLUTIONS Fast Multi-Pattern Matching Algorithm on Compressed Network Traffic Hao Peng, Jianxin Li, Bo Li, M. Hassan Arif School of Computer Science and Engineering, Beihang University,
Hash-Based String Matching Algorithm For Network Intrusion Prevention systems (NIPS)
 Hash-Based String Matching Algorithm For Network Intrusion Prevention systems (NIPS) VINOD. O & B. M. SAGAR ISE Department, R.V.College of Engineering, Bangalore-560059, INDIA Email Id :vinod.goutham@gmail.com,sagar.bm@gmail.com
Hash-Based String Matching Algorithm For Network Intrusion Prevention systems (NIPS) VINOD. O & B. M. SAGAR ISE Department, R.V.College of Engineering, Bangalore-560059, INDIA Email Id :vinod.goutham@gmail.com,sagar.bm@gmail.com
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
Greedy Algorithms CHAPTER 16
 CHAPTER 16 Greedy Algorithms In dynamic programming, the optimal solution is described in a recursive manner, and then is computed ``bottom up''. Dynamic programming is a powerful technique, but it often
CHAPTER 16 Greedy Algorithms In dynamic programming, the optimal solution is described in a recursive manner, and then is computed ``bottom up''. Dynamic programming is a powerful technique, but it often
Space Efficient Linear Time Construction of
 Space Efficient Linear Time Construction of Suffix Arrays Pang Ko and Srinivas Aluru Dept. of Electrical and Computer Engineering 1 Laurence H. Baker Center for Bioinformatics and Biological Statistics
Space Efficient Linear Time Construction of Suffix Arrays Pang Ko and Srinivas Aluru Dept. of Electrical and Computer Engineering 1 Laurence H. Baker Center for Bioinformatics and Biological Statistics
Lecture 11: Packet forwarding
 Lecture 11: Packet forwarding Anirudh Sivaraman 2017/10/23 This week we ll talk about the data plane. Recall that the routing layer broadly consists of two parts: (1) the control plane that computes routes
Lecture 11: Packet forwarding Anirudh Sivaraman 2017/10/23 This week we ll talk about the data plane. Recall that the routing layer broadly consists of two parts: (1) the control plane that computes routes
Design of Deterministic Finite Automata using Pattern Matching Strategy
 Design of Deterministic Finite Automata using Pattern Matching Strategy V. N. V Srinivasa Rao 1, Dr. M. S. S. Sai 2 Assistant Professor, 2 Professor, Department of Computer Science and Engineering KKR
Design of Deterministic Finite Automata using Pattern Matching Strategy V. N. V Srinivasa Rao 1, Dr. M. S. S. Sai 2 Assistant Professor, 2 Professor, Department of Computer Science and Engineering KKR
An Enhanced Bloom Filter for Longest Prefix Matching
 An Enhanced Bloom Filter for Longest Prefix Matching Gahyun Park SUNY-Geneseo Email: park@geneseo.edu Minseok Kwon Rochester Institute of Technology Email: jmk@cs.rit.edu Abstract A Bloom filter is a succinct
An Enhanced Bloom Filter for Longest Prefix Matching Gahyun Park SUNY-Geneseo Email: park@geneseo.edu Minseok Kwon Rochester Institute of Technology Email: jmk@cs.rit.edu Abstract A Bloom filter is a succinct
A Performance Evaluation of the Preprocessing Phase of Multiple Keyword Matching Algorithms
 A Performance Evaluation of the Preprocessing Phase of Multiple Keyword Matching Algorithms Charalampos S. Kouzinopoulos and Konstantinos G. Margaritis Parallel and Distributed Processing Laboratory Department
A Performance Evaluation of the Preprocessing Phase of Multiple Keyword Matching Algorithms Charalampos S. Kouzinopoulos and Konstantinos G. Margaritis Parallel and Distributed Processing Laboratory Department
Hyper Text Transfer Protocol Compression
 Hyper Text Transfer Protocol Compression Dr.Khalaf Khatatneh, Professor Dr. Ahmed Al-Jaber, and Asma a M. Khtoom Abstract This paper investigates HTTP post request compression approach. The most common
Hyper Text Transfer Protocol Compression Dr.Khalaf Khatatneh, Professor Dr. Ahmed Al-Jaber, and Asma a M. Khtoom Abstract This paper investigates HTTP post request compression approach. The most common
Horn Formulae. CS124 Course Notes 8 Spring 2018
 CS124 Course Notes 8 Spring 2018 In today s lecture we will be looking a bit more closely at the Greedy approach to designing algorithms. As we will see, sometimes it works, and sometimes even when it
CS124 Course Notes 8 Spring 2018 In today s lecture we will be looking a bit more closely at the Greedy approach to designing algorithms. As we will see, sometimes it works, and sometimes even when it
Lossless Compression Algorithms
 Multimedia Data Compression Part I Chapter 7 Lossless Compression Algorithms 1 Chapter 7 Lossless Compression Algorithms 1. Introduction 2. Basics of Information Theory 3. Lossless Compression Algorithms
Multimedia Data Compression Part I Chapter 7 Lossless Compression Algorithms 1 Chapter 7 Lossless Compression Algorithms 1. Introduction 2. Basics of Information Theory 3. Lossless Compression Algorithms
CHAPTER 5 PROPAGATION DELAY
 98 CHAPTER 5 PROPAGATION DELAY Underwater wireless sensor networks deployed of sensor nodes with sensing, forwarding and processing abilities that operate in underwater. In this environment brought challenges,
98 CHAPTER 5 PROPAGATION DELAY Underwater wireless sensor networks deployed of sensor nodes with sensing, forwarding and processing abilities that operate in underwater. In this environment brought challenges,
Category: Informational May DEFLATE Compressed Data Format Specification version 1.3
 Network Working Group P. Deutsch Request for Comments: 1951 Aladdin Enterprises Category: Informational May 1996 DEFLATE Compressed Data Format Specification version 1.3 Status of This Memo This memo provides
Network Working Group P. Deutsch Request for Comments: 1951 Aladdin Enterprises Category: Informational May 1996 DEFLATE Compressed Data Format Specification version 1.3 Status of This Memo This memo provides
Applied Algorithm Design Lecture 3
 Applied Algorithm Design Lecture 3 Pietro Michiardi Eurecom Pietro Michiardi (Eurecom) Applied Algorithm Design Lecture 3 1 / 75 PART I : GREEDY ALGORITHMS Pietro Michiardi (Eurecom) Applied Algorithm
Applied Algorithm Design Lecture 3 Pietro Michiardi Eurecom Pietro Michiardi (Eurecom) Applied Algorithm Design Lecture 3 1 / 75 PART I : GREEDY ALGORITHMS Pietro Michiardi (Eurecom) Applied Algorithm
Packet Classification Using Dynamically Generated Decision Trees
 1 Packet Classification Using Dynamically Generated Decision Trees Yu-Chieh Cheng, Pi-Chung Wang Abstract Binary Search on Levels (BSOL) is a decision-tree algorithm for packet classification with superior
1 Packet Classification Using Dynamically Generated Decision Trees Yu-Chieh Cheng, Pi-Chung Wang Abstract Binary Search on Levels (BSOL) is a decision-tree algorithm for packet classification with superior
Tree-Based Minimization of TCAM Entries for Packet Classification
 Tree-Based Minimization of TCAM Entries for Packet Classification YanSunandMinSikKim School of Electrical Engineering and Computer Science Washington State University Pullman, Washington 99164-2752, U.S.A.
Tree-Based Minimization of TCAM Entries for Packet Classification YanSunandMinSikKim School of Electrical Engineering and Computer Science Washington State University Pullman, Washington 99164-2752, U.S.A.
University of Waterloo CS240R Fall 2017 Review Problems
 University of Waterloo CS240R Fall 2017 Review Problems Reminder: Final on Tuesday, December 12 2017 Note: This is a sample of problems designed to help prepare for the final exam. These problems do not
University of Waterloo CS240R Fall 2017 Review Problems Reminder: Final on Tuesday, December 12 2017 Note: This is a sample of problems designed to help prepare for the final exam. These problems do not
Lecture 5: Suffix Trees
 Longest Common Substring Problem Lecture 5: Suffix Trees Given a text T = GGAGCTTAGAACT and a string P = ATTCGCTTAGCCTA, how do we find the longest common substring between them? Here the longest common
Longest Common Substring Problem Lecture 5: Suffix Trees Given a text T = GGAGCTTAGAACT and a string P = ATTCGCTTAGCCTA, how do we find the longest common substring between them? Here the longest common
Binary Encoded Attribute-Pairing Technique for Database Compression
 Binary Encoded Attribute-Pairing Technique for Database Compression Akanksha Baid and Swetha Krishnan Computer Sciences Department University of Wisconsin, Madison baid,swetha@cs.wisc.edu Abstract Data
Binary Encoded Attribute-Pairing Technique for Database Compression Akanksha Baid and Swetha Krishnan Computer Sciences Department University of Wisconsin, Madison baid,swetha@cs.wisc.edu Abstract Data
An Cross Layer Collaborating Cache Scheme to Improve Performance of HTTP Clients in MANETs
 An Cross Layer Collaborating Cache Scheme to Improve Performance of HTTP Clients in MANETs Jin Liu 1, Hongmin Ren 1, Jun Wang 2, Jin Wang 2 1 College of Information Engineering, Shanghai Maritime University,
An Cross Layer Collaborating Cache Scheme to Improve Performance of HTTP Clients in MANETs Jin Liu 1, Hongmin Ren 1, Jun Wang 2, Jin Wang 2 1 College of Information Engineering, Shanghai Maritime University,
Entropy Coding. - to shorten the average code length by assigning shorter codes to more probable symbols => Morse-, Huffman-, Arithmetic Code
 Entropy Coding } different probabilities for the appearing of single symbols are used - to shorten the average code length by assigning shorter codes to more probable symbols => Morse-, Huffman-, Arithmetic
Entropy Coding } different probabilities for the appearing of single symbols are used - to shorten the average code length by assigning shorter codes to more probable symbols => Morse-, Huffman-, Arithmetic
3 No-Wait Job Shops with Variable Processing Times
 3 No-Wait Job Shops with Variable Processing Times In this chapter we assume that, on top of the classical no-wait job shop setting, we are given a set of processing times for each operation. We may select
3 No-Wait Job Shops with Variable Processing Times In this chapter we assume that, on top of the classical no-wait job shop setting, we are given a set of processing times for each operation. We may select
Text Analytics. Index-Structures for Information Retrieval. Ulf Leser
 Text Analytics Index-Structures for Information Retrieval Ulf Leser Content of this Lecture Inverted files Storage structures Phrase and proximity search Building and updating the index Using a RDBMS Ulf
Text Analytics Index-Structures for Information Retrieval Ulf Leser Content of this Lecture Inverted files Storage structures Phrase and proximity search Building and updating the index Using a RDBMS Ulf
Multi-pattern Signature Matching for Hardware Network Intrusion Detection Systems
 This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE GLOBECOM 5 proceedings. Multi-pattern Signature Matching for Hardware
This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE GLOBECOM 5 proceedings. Multi-pattern Signature Matching for Hardware
String Matching. Pedro Ribeiro 2016/2017 DCC/FCUP. Pedro Ribeiro (DCC/FCUP) String Matching 2016/ / 42
 String Matching Pedro Ribeiro DCC/FCUP 2016/2017 Pedro Ribeiro (DCC/FCUP) String Matching 2016/2017 1 / 42 On this lecture The String Matching Problem Naive Algorithm Deterministic Finite Automata Knuth-Morris-Pratt
String Matching Pedro Ribeiro DCC/FCUP 2016/2017 Pedro Ribeiro (DCC/FCUP) String Matching 2016/2017 1 / 42 On this lecture The String Matching Problem Naive Algorithm Deterministic Finite Automata Knuth-Morris-Pratt
University of Waterloo CS240R Winter 2018 Help Session Problems
 University of Waterloo CS240R Winter 2018 Help Session Problems Reminder: Final on Monday, April 23 2018 Note: This is a sample of problems designed to help prepare for the final exam. These problems do
University of Waterloo CS240R Winter 2018 Help Session Problems Reminder: Final on Monday, April 23 2018 Note: This is a sample of problems designed to help prepare for the final exam. These problems do
A New Platform NIDS Based On WEMA
 I.J. Information Technology and Computer Science, 2015, 06, 52-58 Published Online May 2015 in MECS (http://www.mecs-press.org/) DOI: 10.5815/ijitcs.2015.06.07 A New Platform NIDS Based On WEMA Adnan A.
I.J. Information Technology and Computer Science, 2015, 06, 52-58 Published Online May 2015 in MECS (http://www.mecs-press.org/) DOI: 10.5815/ijitcs.2015.06.07 A New Platform NIDS Based On WEMA Adnan A.
Advanced Pattern Based Virus Detection Algorithm for Network Security
 National Conference on Emerging Trends in VLSI, Embedded and Communication Systems-2013 37 Advanced Pattern Based Virus Detection Algorithm for Network Security T.B. Binroy and B. Lakshmanan Abstract---
National Conference on Emerging Trends in VLSI, Embedded and Communication Systems-2013 37 Advanced Pattern Based Virus Detection Algorithm for Network Security T.B. Binroy and B. Lakshmanan Abstract---
THE RELATIVE EFFICIENCY OF DATA COMPRESSION BY LZW AND LZSS
 THE RELATIVE EFFICIENCY OF DATA COMPRESSION BY LZW AND LZSS Yair Wiseman 1* * 1 Computer Science Department, Bar-Ilan University, Ramat-Gan 52900, Israel Email: wiseman@cs.huji.ac.il, http://www.cs.biu.ac.il/~wiseman
THE RELATIVE EFFICIENCY OF DATA COMPRESSION BY LZW AND LZSS Yair Wiseman 1* * 1 Computer Science Department, Bar-Ilan University, Ramat-Gan 52900, Israel Email: wiseman@cs.huji.ac.il, http://www.cs.biu.ac.il/~wiseman
NOISE ELIMINATION USING A BIT CAMS
 International Journal of VLSI Design, 2(2), 2011, pp. 97-101 NOISE ELIMINATION USING A BIT CAMS Sundar Srinivas Kuchibhotla 1 & Naga Lakshmi Kalyani Movva 2 1 Department of Electronics & Communication
International Journal of VLSI Design, 2(2), 2011, pp. 97-101 NOISE ELIMINATION USING A BIT CAMS Sundar Srinivas Kuchibhotla 1 & Naga Lakshmi Kalyani Movva 2 1 Department of Electronics & Communication
EXTREME POINTS AND AFFINE EQUIVALENCE
 EXTREME POINTS AND AFFINE EQUIVALENCE The purpose of this note is to use the notions of extreme points and affine transformations which are studied in the file affine-convex.pdf to prove that certain standard
EXTREME POINTS AND AFFINE EQUIVALENCE The purpose of this note is to use the notions of extreme points and affine transformations which are studied in the file affine-convex.pdf to prove that certain standard
Deep Packet Inspection as a Service
 Deep Packet Inspection as a Service Anat Bremler-Barr School of Computer Science The Interdisciplinary Center Herzliya, Israel bremler@idc.ac.il Yotam Harchol School of Computer Science and Engineering
Deep Packet Inspection as a Service Anat Bremler-Barr School of Computer Science The Interdisciplinary Center Herzliya, Israel bremler@idc.ac.il Yotam Harchol School of Computer Science and Engineering
Lecture 15 : Review DRAFT
 CS/Math 240: Introduction to Discrete Mathematics 3/10/2011 Lecture 15 : Review Instructor: Dieter van Melkebeek Scribe: Dalibor Zelený DRAFT Today slectureservesasareviewofthematerialthatwillappearonyoursecondmidtermexam.
CS/Math 240: Introduction to Discrete Mathematics 3/10/2011 Lecture 15 : Review Instructor: Dieter van Melkebeek Scribe: Dalibor Zelený DRAFT Today slectureservesasareviewofthematerialthatwillappearonyoursecondmidtermexam.
Scribe: Virginia Williams, Sam Kim (2016), Mary Wootters (2017) Date: May 22, 2017
 CS6 Lecture 4 Greedy Algorithms Scribe: Virginia Williams, Sam Kim (26), Mary Wootters (27) Date: May 22, 27 Greedy Algorithms Suppose we want to solve a problem, and we re able to come up with some recursive
CS6 Lecture 4 Greedy Algorithms Scribe: Virginia Williams, Sam Kim (26), Mary Wootters (27) Date: May 22, 27 Greedy Algorithms Suppose we want to solve a problem, and we re able to come up with some recursive
Advanced Pattern Based Virus Detection Algorithm for Network Security
 Advanced Pattern Based Virus Detection Algorithm for Network Security Binroy T.B. M.E. Communication Systems Department of Electronics and Communication Engineering RVS College of Engineering & Technology,
Advanced Pattern Based Virus Detection Algorithm for Network Security Binroy T.B. M.E. Communication Systems Department of Electronics and Communication Engineering RVS College of Engineering & Technology,
FUTURE communication networks are expected to support
 1146 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL 13, NO 5, OCTOBER 2005 A Scalable Approach to the Partition of QoS Requirements in Unicast and Multicast Ariel Orda, Senior Member, IEEE, and Alexander Sprintson,
1146 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL 13, NO 5, OCTOBER 2005 A Scalable Approach to the Partition of QoS Requirements in Unicast and Multicast Ariel Orda, Senior Member, IEEE, and Alexander Sprintson,
Switch and Router Design. Packet Processing Examples. Packet Processing Examples. Packet Processing Rate 12/14/2011
 // Bottlenecks Memory, memory, 88 - Switch and Router Design Dr. David Hay Ross 8b dhay@cs.huji.ac.il Source: Nick Mckeown, Isaac Keslassy Packet Processing Examples Address Lookup (IP/Ethernet) Where
// Bottlenecks Memory, memory, 88 - Switch and Router Design Dr. David Hay Ross 8b dhay@cs.huji.ac.il Source: Nick Mckeown, Isaac Keslassy Packet Processing Examples Address Lookup (IP/Ethernet) Where
Indexing. CS6200: Information Retrieval. Index Construction. Slides by: Jesse Anderton
 Indexing Index Construction CS6200: Information Retrieval Slides by: Jesse Anderton Motivation: Scale Corpus Terms Docs Entries A term incidence matrix with V terms and D documents has O(V x D) entries.
Indexing Index Construction CS6200: Information Retrieval Slides by: Jesse Anderton Motivation: Scale Corpus Terms Docs Entries A term incidence matrix with V terms and D documents has O(V x D) entries.
An introduction to suffix trees and indexing
 An introduction to suffix trees and indexing Tomáš Flouri Solon P. Pissis Heidelberg Institute for Theoretical Studies December 3, 2012 1 Introduction Introduction 2 Basic Definitions Graph theory Alphabet
An introduction to suffix trees and indexing Tomáš Flouri Solon P. Pissis Heidelberg Institute for Theoretical Studies December 3, 2012 1 Introduction Introduction 2 Basic Definitions Graph theory Alphabet
Accelerating Boyer Moore Searches on Binary Texts
 Accelerating Boyer Moore Searches on Binary Texts Shmuel T. Klein Miri Kopel Ben-Nissan Department of Computer Science, Bar Ilan University, Ramat-Gan 52900, Israel Tel: (972 3) 531 8865 Email: {tomi,kopel}@cs.biu.ac.il
Accelerating Boyer Moore Searches on Binary Texts Shmuel T. Klein Miri Kopel Ben-Nissan Department of Computer Science, Bar Ilan University, Ramat-Gan 52900, Israel Tel: (972 3) 531 8865 Email: {tomi,kopel}@cs.biu.ac.il
Compressing Data. Konstantin Tretyakov
 Compressing Data Konstantin Tretyakov (kt@ut.ee) MTAT.03.238 Advanced April 26, 2012 Claude Elwood Shannon (1916-2001) C. E. Shannon. A mathematical theory of communication. 1948 C. E. Shannon. The mathematical
Compressing Data Konstantin Tretyakov (kt@ut.ee) MTAT.03.238 Advanced April 26, 2012 Claude Elwood Shannon (1916-2001) C. E. Shannon. A mathematical theory of communication. 1948 C. E. Shannon. The mathematical
Indexing Variable Length Substrings for Exact and Approximate Matching
 Indexing Variable Length Substrings for Exact and Approximate Matching Gonzalo Navarro 1, and Leena Salmela 2 1 Department of Computer Science, University of Chile gnavarro@dcc.uchile.cl 2 Department of
Indexing Variable Length Substrings for Exact and Approximate Matching Gonzalo Navarro 1, and Leena Salmela 2 1 Department of Computer Science, University of Chile gnavarro@dcc.uchile.cl 2 Department of
A Hybrid Approach to CAM-Based Longest Prefix Matching for IP Route Lookup
 A Hybrid Approach to CAM-Based Longest Prefix Matching for IP Route Lookup Yan Sun and Min Sik Kim School of Electrical Engineering and Computer Science Washington State University Pullman, Washington
A Hybrid Approach to CAM-Based Longest Prefix Matching for IP Route Lookup Yan Sun and Min Sik Kim School of Electrical Engineering and Computer Science Washington State University Pullman, Washington
Lecture 15. Error-free variable length schemes: Shannon-Fano code
 Lecture 15 Agenda for the lecture Bounds for L(X) Error-free variable length schemes: Shannon-Fano code 15.1 Optimal length nonsingular code While we do not know L(X), it is easy to specify a nonsingular
Lecture 15 Agenda for the lecture Bounds for L(X) Error-free variable length schemes: Shannon-Fano code 15.1 Optimal length nonsingular code While we do not know L(X), it is easy to specify a nonsingular
Search Engines. Information Retrieval in Practice
 Search Engines Information Retrieval in Practice All slides Addison Wesley, 2008 Web Crawler Finds and downloads web pages automatically provides the collection for searching Web is huge and constantly
Search Engines Information Retrieval in Practice All slides Addison Wesley, 2008 Web Crawler Finds and downloads web pages automatically provides the collection for searching Web is huge and constantly
Unit 6 Chapter 15 EXAMPLES OF COMPLEXITY CALCULATION
 DESIGN AND ANALYSIS OF ALGORITHMS Unit 6 Chapter 15 EXAMPLES OF COMPLEXITY CALCULATION http://milanvachhani.blogspot.in EXAMPLES FROM THE SORTING WORLD Sorting provides a good set of examples for analyzing
DESIGN AND ANALYSIS OF ALGORITHMS Unit 6 Chapter 15 EXAMPLES OF COMPLEXITY CALCULATION http://milanvachhani.blogspot.in EXAMPLES FROM THE SORTING WORLD Sorting provides a good set of examples for analyzing
CS5371 Theory of Computation. Lecture 8: Automata Theory VI (PDA, PDA = CFG)
 CS5371 Theory of Computation Lecture 8: Automata Theory VI (PDA, PDA = CFG) Objectives Introduce Pushdown Automaton (PDA) Show that PDA = CFG In terms of descriptive power Pushdown Automaton (PDA) Roughly
CS5371 Theory of Computation Lecture 8: Automata Theory VI (PDA, PDA = CFG) Objectives Introduce Pushdown Automaton (PDA) Show that PDA = CFG In terms of descriptive power Pushdown Automaton (PDA) Roughly
9.1 Cook-Levin Theorem
 CS787: Advanced Algorithms Scribe: Shijin Kong and David Malec Lecturer: Shuchi Chawla Topic: NP-Completeness, Approximation Algorithms Date: 10/1/2007 As we ve already seen in the preceding lecture, two
CS787: Advanced Algorithms Scribe: Shijin Kong and David Malec Lecturer: Shuchi Chawla Topic: NP-Completeness, Approximation Algorithms Date: 10/1/2007 As we ve already seen in the preceding lecture, two
An Improved Measurement Placement Algorithm for Network Observability
 IEEE TRANSACTIONS ON POWER SYSTEMS, VOL. 16, NO. 4, NOVEMBER 2001 819 An Improved Measurement Placement Algorithm for Network Observability Bei Gou and Ali Abur, Senior Member, IEEE Abstract This paper
IEEE TRANSACTIONS ON POWER SYSTEMS, VOL. 16, NO. 4, NOVEMBER 2001 819 An Improved Measurement Placement Algorithm for Network Observability Bei Gou and Ali Abur, Senior Member, IEEE Abstract This paper
A Software-Defined Framework for Improved Performance and Security of Network Functions
 A Software-Defined Framework for Improved Performance and Security of Network Functions Thesis submitted for the degree of Doctor of Philosophy by Yotam Harchol Submitted to the Senate of The Hebrew University
A Software-Defined Framework for Improved Performance and Security of Network Functions Thesis submitted for the degree of Doctor of Philosophy by Yotam Harchol Submitted to the Senate of The Hebrew University
Log File Modification Detection and Location Using Fragile Watermark
 Log File Modification Detection and Location Using Fragile Watermark Liang Xu and Huiping Guo Department of Computer Science California State University at Los Angeles Los Angeles, CA, USA Abstract- In
Log File Modification Detection and Location Using Fragile Watermark Liang Xu and Huiping Guo Department of Computer Science California State University at Los Angeles Los Angeles, CA, USA Abstract- In
An Improved Upper Bound for the Sum-free Subset Constant
 1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 13 (2010), Article 10.8.3 An Improved Upper Bound for the Sum-free Subset Constant Mark Lewko Department of Mathematics University of Texas at Austin
1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 13 (2010), Article 10.8.3 An Improved Upper Bound for the Sum-free Subset Constant Mark Lewko Department of Mathematics University of Texas at Austin
Ch. 2: Compression Basics Multimedia Systems
 Ch. 2: Compression Basics Multimedia Systems Prof. Ben Lee School of Electrical Engineering and Computer Science Oregon State University Outline Why compression? Classification Entropy and Information
Ch. 2: Compression Basics Multimedia Systems Prof. Ben Lee School of Electrical Engineering and Computer Science Oregon State University Outline Why compression? Classification Entropy and Information
Multi-Cluster Interleaving on Paths and Cycles
 Multi-Cluster Interleaving on Paths and Cycles Anxiao (Andrew) Jiang, Member, IEEE, Jehoshua Bruck, Fellow, IEEE Abstract Interleaving codewords is an important method not only for combatting burst-errors,
Multi-Cluster Interleaving on Paths and Cycles Anxiao (Andrew) Jiang, Member, IEEE, Jehoshua Bruck, Fellow, IEEE Abstract Interleaving codewords is an important method not only for combatting burst-errors,
Performance Evaluation of XHTML encoding and compression
 Performance Evaluation of XHTML encoding and compression Sathiamoorthy Manoharan Department of Computer Science, University of Auckland, Auckland, New Zealand Abstract. The wireless markup language (WML),
Performance Evaluation of XHTML encoding and compression Sathiamoorthy Manoharan Department of Computer Science, University of Auckland, Auckland, New Zealand Abstract. The wireless markup language (WML),
Lecture 7 February 26, 2010
 6.85: Advanced Data Structures Spring Prof. Andre Schulz Lecture 7 February 6, Scribe: Mark Chen Overview In this lecture, we consider the string matching problem - finding all places in a text where some
6.85: Advanced Data Structures Spring Prof. Andre Schulz Lecture 7 February 6, Scribe: Mark Chen Overview In this lecture, we consider the string matching problem - finding all places in a text where some
Reduction of Periodic Broadcast Resource Requirements with Proxy Caching
 Reduction of Periodic Broadcast Resource Requirements with Proxy Caching Ewa Kusmierek and David H.C. Du Digital Technology Center and Department of Computer Science and Engineering University of Minnesota
Reduction of Periodic Broadcast Resource Requirements with Proxy Caching Ewa Kusmierek and David H.C. Du Digital Technology Center and Department of Computer Science and Engineering University of Minnesota
Optimal Parallel Randomized Renaming
 Optimal Parallel Randomized Renaming Martin Farach S. Muthukrishnan September 11, 1995 Abstract We consider the Renaming Problem, a basic processing step in string algorithms, for which we give a simultaneously
Optimal Parallel Randomized Renaming Martin Farach S. Muthukrishnan September 11, 1995 Abstract We consider the Renaming Problem, a basic processing step in string algorithms, for which we give a simultaneously
SIGNAL COMPRESSION Lecture Lempel-Ziv Coding
 SIGNAL COMPRESSION Lecture 5 11.9.2007 Lempel-Ziv Coding Dictionary methods Ziv-Lempel 77 The gzip variant of Ziv-Lempel 77 Ziv-Lempel 78 The LZW variant of Ziv-Lempel 78 Asymptotic optimality of Ziv-Lempel
SIGNAL COMPRESSION Lecture 5 11.9.2007 Lempel-Ziv Coding Dictionary methods Ziv-Lempel 77 The gzip variant of Ziv-Lempel 77 Ziv-Lempel 78 The LZW variant of Ziv-Lempel 78 Asymptotic optimality of Ziv-Lempel
Forwarding and Routers : Computer Networking. Original IP Route Lookup. Outline
 Forwarding and Routers 15-744: Computer Networking L-9 Router Algorithms IP lookup Longest prefix matching Classification Flow monitoring Readings [EVF3] Bitmap Algorithms for Active Flows on High Speed
Forwarding and Routers 15-744: Computer Networking L-9 Router Algorithms IP lookup Longest prefix matching Classification Flow monitoring Readings [EVF3] Bitmap Algorithms for Active Flows on High Speed
University of Waterloo CS240 Spring 2018 Help Session Problems
 University of Waterloo CS240 Spring 2018 Help Session Problems Reminder: Final on Wednesday, August 1 2018 Note: This is a sample of problems designed to help prepare for the final exam. These problems
University of Waterloo CS240 Spring 2018 Help Session Problems Reminder: Final on Wednesday, August 1 2018 Note: This is a sample of problems designed to help prepare for the final exam. These problems
Space-Time Tradeoffs in Software-Based Deep Packet Inspection
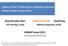 Space-Time Tradeoffs in Software-ased eep Packet Inspection nat remler-arr I Herzliya, Israel Yotam Harchol avid Hay Hebrew University, Israel. OWSP Israel 2011 (Was also presented in I HPSR 2011) Parts
Space-Time Tradeoffs in Software-ased eep Packet Inspection nat remler-arr I Herzliya, Israel Yotam Harchol avid Hay Hebrew University, Israel. OWSP Israel 2011 (Was also presented in I HPSR 2011) Parts
Fast Deep Packet Inspection with a Dual Finite Automata
 1 Fast Deep Packet Inspection with a Dual Finite Automata Cong Liu Jie Wu Sun Yat-sen University Temple University gzcong@gmail.com jiewu@temple.edu Abstract Deep packet inspection, in which packet payloads
1 Fast Deep Packet Inspection with a Dual Finite Automata Cong Liu Jie Wu Sun Yat-sen University Temple University gzcong@gmail.com jiewu@temple.edu Abstract Deep packet inspection, in which packet payloads
Analysis of the effects of removing redundant header information in persistent HTTP connections
 Analysis of the effects of removing redundant header information in persistent HTTP connections Timothy Bower, Daniel Andresen, David Bacon Department of Computing and Information Sciences 234 Nichols
Analysis of the effects of removing redundant header information in persistent HTTP connections Timothy Bower, Daniel Andresen, David Bacon Department of Computing and Information Sciences 234 Nichols
FERMA: An Efficient Geocasting Protocol for Wireless Sensor Networks with Multiple Target Regions
 FERMA: An Efficient Geocasting Protocol for Wireless Sensor Networks with Multiple Target Regions Young-Mi Song, Sung-Hee Lee, and Young-Bae Ko College of Information and Communication, Ajou University,
FERMA: An Efficient Geocasting Protocol for Wireless Sensor Networks with Multiple Target Regions Young-Mi Song, Sung-Hee Lee, and Young-Bae Ko College of Information and Communication, Ajou University,
Working with Compressed Concordances
 Miri Ben-Nissan and Shmuel T. Klein Department of Computer Science Bar Ilan University 52 900 Ramat-Gan Israel Tel: (972 3) 531 8865 Fax: (972 3) 736 0498 miribn@gmail.com, tomi@cs.biu.ac.il Abstract.
Miri Ben-Nissan and Shmuel T. Klein Department of Computer Science Bar Ilan University 52 900 Ramat-Gan Israel Tel: (972 3) 531 8865 Fax: (972 3) 736 0498 miribn@gmail.com, tomi@cs.biu.ac.il Abstract.
A New Compression Method Strictly for English Textual Data
 A New Compression Method Strictly for English Textual Data Sabina Priyadarshini Department of Computer Science and Engineering Birla Institute of Technology Abstract - Data compression is a requirement
A New Compression Method Strictly for English Textual Data Sabina Priyadarshini Department of Computer Science and Engineering Birla Institute of Technology Abstract - Data compression is a requirement
The Language for Specifying Lexical Analyzer
 The Language for Specifying Lexical Analyzer We shall now study how to build a lexical analyzer from a specification of tokens in the form of a list of regular expressions The discussion centers around
The Language for Specifying Lexical Analyzer We shall now study how to build a lexical analyzer from a specification of tokens in the form of a list of regular expressions The discussion centers around
Solutions to Midterm 2 - Monday, July 11th, 2009
 Solutions to Midterm - Monday, July 11th, 009 CPSC30, Summer009. Instructor: Dr. Lior Malka. (liorma@cs.ubc.ca) 1. Dynamic programming. Let A be a set of n integers A 1,..., A n such that 1 A i n for each
Solutions to Midterm - Monday, July 11th, 009 CPSC30, Summer009. Instructor: Dr. Lior Malka. (liorma@cs.ubc.ca) 1. Dynamic programming. Let A be a set of n integers A 1,..., A n such that 1 A i n for each
Trees. 3. (Minimally Connected) G is connected and deleting any of its edges gives rise to a disconnected graph.
 Trees 1 Introduction Trees are very special kind of (undirected) graphs. Formally speaking, a tree is a connected graph that is acyclic. 1 This definition has some drawbacks: given a graph it is not trivial
Trees 1 Introduction Trees are very special kind of (undirected) graphs. Formally speaking, a tree is a connected graph that is acyclic. 1 This definition has some drawbacks: given a graph it is not trivial
Full-Text Search on Data with Access Control
 Full-Text Search on Data with Access Control Ahmad Zaky School of Electrical Engineering and Informatics Institut Teknologi Bandung Bandung, Indonesia 13512076@std.stei.itb.ac.id Rinaldi Munir, S.T., M.T.
Full-Text Search on Data with Access Control Ahmad Zaky School of Electrical Engineering and Informatics Institut Teknologi Bandung Bandung, Indonesia 13512076@std.stei.itb.ac.id Rinaldi Munir, S.T., M.T.
Worst-case running time for RANDOMIZED-SELECT
 Worst-case running time for RANDOMIZED-SELECT is ), even to nd the minimum The algorithm has a linear expected running time, though, and because it is randomized, no particular input elicits the worst-case
Worst-case running time for RANDOMIZED-SELECT is ), even to nd the minimum The algorithm has a linear expected running time, though, and because it is randomized, no particular input elicits the worst-case
NEW STABILITY RESULTS FOR ADVERSARIAL QUEUING
 NEW STABILITY RESULTS FOR ADVERSARIAL QUEUING ZVI LOTKER, BOAZ PATT-SHAMIR, AND ADI ROSÉN Abstract. We consider the model of adversarial queuing theory for packet networks introduced by Borodin et al.
NEW STABILITY RESULTS FOR ADVERSARIAL QUEUING ZVI LOTKER, BOAZ PATT-SHAMIR, AND ADI ROSÉN Abstract. We consider the model of adversarial queuing theory for packet networks introduced by Borodin et al.
Network Working Group Request for Comments: January IP Payload Compression Using ITU-T V.44 Packet Method
 Network Working Group Request for Comments: 3051 Category: Informational J. Heath J. Border Hughes Network Systems January 2001 IP Payload Compression Using ITU-T V.44 Packet Method Status of this Memo
Network Working Group Request for Comments: 3051 Category: Informational J. Heath J. Border Hughes Network Systems January 2001 IP Payload Compression Using ITU-T V.44 Packet Method Status of this Memo
Theorem 2.9: nearest addition algorithm
 There are severe limits on our ability to compute near-optimal tours It is NP-complete to decide whether a given undirected =(,)has a Hamiltonian cycle An approximation algorithm for the TSP can be used
There are severe limits on our ability to compute near-optimal tours It is NP-complete to decide whether a given undirected =(,)has a Hamiltonian cycle An approximation algorithm for the TSP can be used
Packet Inspection on Programmable Hardware
 Abstract Packet Inspection on Programmable Hardware Benfano Soewito Information Technology Department, Bakrie University, Jakarta, Indonesia E-mail: benfano.soewito@bakrie.ac.id In the network security
Abstract Packet Inspection on Programmable Hardware Benfano Soewito Information Technology Department, Bakrie University, Jakarta, Indonesia E-mail: benfano.soewito@bakrie.ac.id In the network security
ACONCURRENT system may be viewed as a collection of
 252 IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 10, NO. 3, MARCH 1999 Constructing a Reliable Test&Set Bit Frank Stomp and Gadi Taubenfeld AbstractÐThe problem of computing with faulty
252 IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 10, NO. 3, MARCH 1999 Constructing a Reliable Test&Set Bit Frank Stomp and Gadi Taubenfeld AbstractÐThe problem of computing with faulty
Dictionary Based Compression for Images
 Dictionary Based Compression for Images Bruno Carpentieri Abstract Lempel-Ziv methods were original introduced to compress one-dimensional data (text, object codes, etc.) but recently they have been successfully
Dictionary Based Compression for Images Bruno Carpentieri Abstract Lempel-Ziv methods were original introduced to compress one-dimensional data (text, object codes, etc.) but recently they have been successfully
Abdullah-Al Mamun. CSE 5095 Yufeng Wu Spring 2013
 Abdullah-Al Mamun CSE 5095 Yufeng Wu Spring 2013 Introduction Data compression is the art of reducing the number of bits needed to store or transmit data Compression is closely related to decompression
Abdullah-Al Mamun CSE 5095 Yufeng Wu Spring 2013 Introduction Data compression is the art of reducing the number of bits needed to store or transmit data Compression is closely related to decompression
Packet classification using diagonal-based tuple space search q
 Computer Networks 50 (2006) 1406 1423 www.elsevier.com/locate/comnet Packet classification using diagonal-based tuple space search q Fu-Yuan Lee *, Shiuhpyng Shieh Department of Computer Science and Information
Computer Networks 50 (2006) 1406 1423 www.elsevier.com/locate/comnet Packet classification using diagonal-based tuple space search q Fu-Yuan Lee *, Shiuhpyng Shieh Department of Computer Science and Information
An On-line Variable Length Binary. Institute for Systems Research and. Institute for Advanced Computer Studies. University of Maryland
 An On-line Variable Length inary Encoding Tinku Acharya Joseph F. Ja Ja Institute for Systems Research and Institute for Advanced Computer Studies University of Maryland College Park, MD 242 facharya,
An On-line Variable Length inary Encoding Tinku Acharya Joseph F. Ja Ja Institute for Systems Research and Institute for Advanced Computer Studies University of Maryland College Park, MD 242 facharya,
EE-575 INFORMATION THEORY - SEM 092
 EE-575 INFORMATION THEORY - SEM 092 Project Report on Lempel Ziv compression technique. Department of Electrical Engineering Prepared By: Mohammed Akber Ali Student ID # g200806120. ------------------------------------------------------------------------------------------------------------------------------------------
EE-575 INFORMATION THEORY - SEM 092 Project Report on Lempel Ziv compression technique. Department of Electrical Engineering Prepared By: Mohammed Akber Ali Student ID # g200806120. ------------------------------------------------------------------------------------------------------------------------------------------
Optimization I : Brute force and Greedy strategy
 Chapter 3 Optimization I : Brute force and Greedy strategy A generic definition of an optimization problem involves a set of constraints that defines a subset in some underlying space (like the Euclidean
Chapter 3 Optimization I : Brute force and Greedy strategy A generic definition of an optimization problem involves a set of constraints that defines a subset in some underlying space (like the Euclidean
LZW Based Compressed Pattern Matching
 LZW Based Compressed attern Matching Tao Tao, Amar Mukherjee School of Electrical Engineering and Computer Science University of Central Florida, Orlando, Fl.32816 USA Email: (ttao+amar)@cs.ucf.edu Abstract
LZW Based Compressed attern Matching Tao Tao, Amar Mukherjee School of Electrical Engineering and Computer Science University of Central Florida, Orlando, Fl.32816 USA Email: (ttao+amar)@cs.ucf.edu Abstract
