S Computer Architecture. Computer architecture assignment E1 A subroutine, which searches for given byte pattern from an byte array.
|
|
|
- Frank Hicks
- 5 years ago
- Views:
Transcription
1 S Computer Architecture Computer architecture assignment E1 A subroutine, which searches for given byte pattern from an byte array. Mikko Vestola Student ID: xxxxx Department: xxxx xxxxx
2 Table of contents 1 Original assignment Function of the subroutine Description of the subroutine Testing Test case 1: Pattern in the middle of the array Test case 2: The pattern and the array are the same Test case 3: Search a byte found at the beginning of the byte array Test case 4: Search a pattern found at the beginning of the array Test case 5: Search a byte found at the end of the byte array Test case 6: Search a pattern at the end of the byte array Test case 7: Search a pattern that is not found in the array Test case 8: Search a pattern that is not entirely found in the array Test case 9: Search a pattern that is found two times from the array Test case 10: Search a pattern which exceeds beyond the array Test case 11: Search a pattern which is longer that the byte array Test case 12: Search a pattern with abnormal size parameters Test case 13: Search a pattern from array with size of Run-time log file Program code...10
3 1 1 Original assignment Computer architecture assignment E1 Write a subroutine, which searches for given byte pattern from an byte array. The arguments of the subroutine are passed as follows: $a0 contains the address of byte array $a1 contains the length of array $a2 contains the address of byte pattern $a3 contains the length of pattern Subroutine should not alter the array nor byte pattern. The C-prototype of the subroutine is as follows: int memmem(void *m1, int size1, void *m2, int size2); The subroutine should return in register $v0: 1) the address of first match or 2) zero, if there were no matches. Main program to test memmem().text.globl main main: Create a stack frame for main program subu $sp $sp,8 sw $ra 4($sp) return address sw $fp 0($sp) old frame pointer addu $fp $sp,8 update frame pointer Get arguments and call the memmem la $a0 mem_area li $a1 16 la $a2 search li $a3 4 jal memmem.data mem_area:.byte 0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15 search:.byte 5,6,7,8.text Check result la $t0 mem_area+5 bne $v0,$t0.failure1
4 2 Insert your own tests here Tell user that memmem works...data.ok:.asciiz "The memmem() passed all tests\n".text li $v0 4 la $a0.ok syscall Exit from test program.exit: li $v0 10 syscall Test failed.failure1:.data.fail1:.asciiz " The memmem() failed test 1.\n".text li $v0 4 la $a0.fail1 syscall j.exit The subroutine memmem - search for given memory area.text.globl memmem memmem: XXX jr $ra.end 2 Function of the subroutine The function of the subroutine is to search a given byte pattern from a byte array. The subroutine returns the memory address of the first occurrence of the byte pattern if it is found from the byte array. If there are more than one occurrences in the byte array, only the address of the first occurrence is returned. If the byte pattern is not found from the array, zero is returned. The C- prototype of the subroutine is as follows: int memmem(void *m1, int size1, void *m2, int size2);
5 3 So the function takes a pointer to the byte array, size of that array, pointer to where the byte pattern begins and its length. The parameters are saved respectively to registers $a0, $a1, $a2 and $a3. The return value (the memory address) is saved to register $v0. 3 Description of the subroutine Subroutine memmem searches a given byte pattern from a given byte array. For example, consider a byte array consisting from numbers 0,1,2,3,4,5,6,7 and a byte pattern 3,4,5. Subroutine tries to search the byte pattern, which now is found, and returns the memory address where the byte pattern starts in the array (which in this case equals: address of the array + 3). The array is just a line of bytes one after another. The pointer (or memory address) to the first byte of the array is given in parameters and also the size of the array (which tells how many bytes are in that array). Byte patterns is also just a series of bytes. A pointer to the first byte of the pattern and the pattern's length are given in the parameters. So at first, the subroutine tries to find the first byte of the pattern from the byte array by comparing the first byte values. If the byte is not found, it compares the second byte of the array to the first byte of the pattern. This continues when the first byte of the pattern is found (or may not be found at all). When it is found, its memory address is saved and the subroutine compares the second byte from the byte pattern to the next byte of the byte array. This is continued when the byte pattern ends (when the pattern is entirely found) or the bytes don't match (when the program starts again to find the first byte of the pattern from the byte array). The operation of the subroutine can be described by the following C-program: include <stdio.h> /* This function searches the given byte pattern * (beginning from pointer given at parameter m2) from * the given byte array (beginning from pointer given at parameter m1). * Parameter size1 is the size of the byte array (m1) and * size2 is the length of the byte pattern (m2). * Returns 0 (NULL pointer's memory address) if no occurrence of * the byte patterns was found. Otherwise returns the memory address * of the beginning of the first occurrence of the byte pattern * in the byte array. */ int memmem(void *m1, int size1, void *m2, int size2) { /* Check that the sizes are reasonable */
6 4 if (size2<=0 size1<=0) return 0; /* Cast void pointers to char pointers, * (char is 8 bits = 1 byte). */ char* btable = (char*) m1; char* bpattern = (char*) m2; /* Copy pointer of the beginning of the byte pattern.*/ char* bpatternbegin = bpattern; int i; /* byte array iterator */ int j = 0; /* byte pattern iterator */ /* The memory address of the first occurrence of * byte pattern is saved here. Initialized to zero * (NULL pointer's address).*/ int v = 0; /* Loop the whole byte array through to find the * byte pattern. */ for (i = 0; i< size1; i++) { /* If the remaining byte pattern is longer than the remaining * byte array, immediately return 0 since the pattern * can't be found. */ if (size2-j > size1-i) return 0; if (*btable!= *bpattern) { /* If the corresponding values of byte array and * byte pattern are not equal, move to next value * in byte array and set the byte pattern iterator * to 0 and also the pointer to the beginning on * the byte pattern (so we try to find the firs * byte of byte pattern from the byte array).*/ btable++; v=0; j=0; bpattern = bpatternbegin; } else { /* If v is 0, that means that we have found the * (possible) beginning of the byte pattern from * the byte array. So lets save it's memory address * (this must be returned if the byte pattern * is entirely found from byte array). */ if (v==0) { v=(int)&(*btable); } /* If byte pattern's value matches the byte array's * value, move the pointer to next cells and * increment the byte pattern iterator (because we * next compare the next value of the byte pattern * */ btable++; bpattern++; j++; /* If j equals to size of the byte pattern,
7 * that means we have found the entire byte pattern * from the byte array. So return with value v * where the beginning index of the byte pattern * in byte array is saved. */ if (j==size2) return v; } // end of for loop 5 } /* If the program loops the whole array through and does * not return any memory value, this means that the given * byte patterns was not found from the byte array. */ return 0; } int main (int argc, char *argv []) { /* Test the memmem function with these byte arrays * (strings are byte arrays, so pointers to the beginning * of the array). */ char *bytearray = " "; char *pattern = "10"; int occurence = memmem(bytearray, 9, pattern, 2); /* Count the index of bytearray where the byte pattern * starts. */ int index = occurence-(int)&(*bytearray); /* Print the results */ if (occurence!= 0) { printf("first occurence is at address %d (index %d)", occurence, index); } else printf("no byte pattern found!"); } return 0; So the subroutine memmem corresponds to the function int memmem(void *m1, int size1, void *m2, int size2). The function main runs the memmem function and prints the result of one test. The search algorithm is as simple as going through the byte array byte by byte. The search algorithm stops when it sees that the byte pattern is longer than the remaining length of the byte array, so it doesn't search the whole array in vane. In this case, this algorithm is the best choice when the byte array is quite short, and one doesn't know that is the byte array ordered (when a binary search might be efficient to find the first byte of the byte pattern). No need to build a more complicated algorithm - keep it simple method works also in software as well as in hardware.
8 6 The actual subroutine, written in MIPS assembly language, uses the following registers: $a0: The pointer to the byte array given in parameters. Corresponds to parameter void *m1 in C-code. $a1: The size of the byte array given in parameters. Corresponds to parameter int size1 in C-code. $a2: The pointer to the byte pattern given in parameters. Corresponds to parameter void *m2 in C-code. $a3: The size of the byte pattern given in parameters. Corresponds to parameter int size2 in C-code. $v0: The memory address of the first occurrence of the byte pattern in byte array (or 0 if the pattern is not found in the byte array). Corresponds to variable v in C-code. $t0: The byte array iterator. Corresponds to variable i in C-code. $t1: The byte pattern iterator. Corresponds to variable j in C-code. $t2: The memory address of the byte array's cell which value is compared (initialized as $a0). Corresponds to pointer btable in C-code. $t3: The memory address of the byte pattern's cell which value is compared (initialized as $a2). Corresponds to pointer bpattern in C-code. $t4: Temporal register, used to calculate if the remaining byte pattern is longer than the remaining byte array. Also used to load one byte from byte array. Corresponds to values size2-j and *btable in C-code. $t5: Temporal register, used to calculate if the remaining byte pattern is longer than the remaining byte array. Also used to load one byte from byte pattern. Corresponds to values size1-i and *bpattern in C-code. The subroutine does neither use any callee-saved registers ($sx) nor modify the argument registers ($ax). Therefore, a stack frame is not required. 4 Testing The purpose of the testing is to verify that the subroutine operates correctly and that all the branches of the subroutine will be tested. It is reasonable to presume that the pointers to byte arrays ($a0 and $a2) and their lengths ($a1 and $a3) are correct. Subroutine can't by no means figure out that is the pointer pointing to right memory location or is the size of that array given right. So these can't be
9 7 verified and the callee must give these parameters right if it wants to get right results. However, the subroutine does do a check that the size parameters are greater than zero, so abnormal size parameters return always zero. Thirteen different test cases were built. They were produced that they should cover all reasonable boundary cases. The test cases are performed at the beginning of the file one after another. The test just simply compares the memory address got as an output of the memmem subroutine (stored in $v0) and a hand written value (stored at $t0) which is the expected value. If the values are not the same, test fails. If one test fails, the program doesn't run the remaining test but exits the execution and prints out information about which test case failed. 4.1 Test case 1: Pattern in the middle of the array This test case tries to search a byte pattern that is found at the middle of the array. Byte pattern: 5,6,7,8 Byte pattern size: 4 Expected output: Pattern is found, $v0 = memory address of the byte array Test case 2: The pattern and the array are the same This test case tries to search a byte pattern that is the same as the byte array: Byte pattern: 0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15 Byte pattern size: 16 Expected output: Pattern is found, $v0 = memory address of the byte array 4.3 Test case 3: Search a byte found at the beginning of the byte array This test case tries to search only one byte that is found at the beginning of the byte array. Byte pattern: 0 Byte pattern size: 1 Expected output: Pattern is found, $v0 = memory address of the byte array
10 8 4.4 Test case 4: Search a pattern found at the beginning of the array This test case tries to search a pattern, length of three, that is found at the beginning of the array. Byte pattern: 0,1,2 Byte pattern size: 3 Expected output: Pattern is found, $v0 = memory address of the byte array 4.5 Test case 5: Search a byte found at the end of the byte array This test case tries to search only one byte that is found at the end of the byte array. Byte pattern: 15 Byte pattern size: 1 Expected output: Pattern is found, $v0 = memory address of the byte array Test case 6: Search a pattern at the end of the byte array This test case tries to search a pattern, length of three, that ends at the end of the byte array. Byte pattern: 13,14,15 Byte pattern size: 3 Expected output: Pattern is found, $v0 = memory address of the byte array Test case 7: Search a pattern that is not found in the array This test case tries to search a pattern that is not found from the byte array (none of the bytes in pattern are in the byte array). Byte pattern: 16,17 Byte pattern size: 2 Expected output: Pattern is not found, $v0 = 0
11 9 4.8 Test case 8: Search a pattern that is not entirely found in the array This test case tries to search a pattern that is not found from the byte array but some of the bytes in the pattern are found from the byte array. Byte pattern: 4,5,6,8 Byte pattern size: 4 Expected output: Pattern is not found, $v0 = Test case 9: Search a pattern that is found two times from the array This test case tries to search a pattern that is found two times from the byte array. This test case also tests how the subroutine works with strings as parameters (strings are also just arrays of bytes where one byte represents one letter). Byte array: "This is test test string" Byte array size: 24 Byte pattern: "test" Byte pattern size: 4 Expected output: Pattern is found, $v0 = memory address of the byte array Test case 10: Search a pattern which exceeds beyond the array This test case tries to search a pattern whose beginning is found at the end of the byte array but whose end exceeds beyond the array so the pattern is not found. Byte array: "This is test test string" Byte array size: 24 Byte pattern: "test string that fails" Byte pattern size: 22 Expected output: Pattern is not found, $v0 = Test case 11: Search a pattern which is longer that the byte array This test case tries to search a pattern which is longer than the byte array. Byte array: "This is test test string" Byte array size: 24 Byte pattern: "This string is too long!!" Byte pattern size: 25
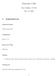
12 10 Expected output: Pattern is not found, $v0 = Test case 12: Search a pattern with abnormal size parameters This test case is the same as test case 9, so the pattern is found from the array, but now the given size parameters are abnormal (they must be greater than zero) so the subroutine should return zero. Byte array: "This is test test string" Byte array size: 0 Byte pattern: "test" Byte pattern size: 0 Expected output: Pattern is not found, $v0 = Test case 13: Search a pattern from array with size of 1 This test case tries to search a pattern, length of one, from an array with size of one. Byte array: 7 Byte array size: 1 Byte pattern: 7 Byte pattern size: 1 Expected output: Pattern is found, $v0 = memory address of the byte array 5 Run-time log file The following result was obtained while running the test program using SPIM on Windows XP. No test fails, so the memmem subroutine seems to be working OK. Picture 1: Console log after running the test program 6 Program code See the file memmem.s enclosed with the report. Also the C-prototype of the subroutine is enclosed as a file named memmem.c.
Lecture 5: Procedure Calls
 Lecture 5: Procedure Calls Today s topics: Procedure calls and register saving conventions 1 Example Convert to assembly: while (save[i] == k) i += 1; i and k are in $s3 and $s5 and base of array save[]
Lecture 5: Procedure Calls Today s topics: Procedure calls and register saving conventions 1 Example Convert to assembly: while (save[i] == k) i += 1; i and k are in $s3 and $s5 and base of array save[]
ECE 30 Introduction to Computer Engineering
 ECE 30 Introduction to Computer Engineering Study Problems, Set #3 Spring 2015 Use the MIPS assembly instructions listed below to solve the following problems. arithmetic add add sub subtract addi add
ECE 30 Introduction to Computer Engineering Study Problems, Set #3 Spring 2015 Use the MIPS assembly instructions listed below to solve the following problems. arithmetic add add sub subtract addi add
ECE/CS 314 Fall 2003 Homework 2 Solutions. Question 1
 ECE/CS 314 Fall 2003 Homework 2 Solutions Question 1 /* Equivalent C code with no loops (goto instead) char* strchr(char* pcstring, char csearchchr) strchr_loop: if (!*pcstring) return 0; if (*pcstring
ECE/CS 314 Fall 2003 Homework 2 Solutions Question 1 /* Equivalent C code with no loops (goto instead) char* strchr(char* pcstring, char csearchchr) strchr_loop: if (!*pcstring) return 0; if (*pcstring
Compiling Techniques
 Lecture 10: An Introduction to MIPS assembly 18 October 2016 Table of contents 1 Overview 2 3 Assembly program template.data Data segment: constant and variable definitions go here (including statically
Lecture 10: An Introduction to MIPS assembly 18 October 2016 Table of contents 1 Overview 2 3 Assembly program template.data Data segment: constant and variable definitions go here (including statically
Memory Usage 0x7fffffff. stack. dynamic data. static data 0x Code Reserved 0x x A software convention
 Subroutines Why we use subroutines more modular program (small routines, outside data passed in) more readable, easier to debug code reuse i.e. smaller code space Memory Usage A software convention stack
Subroutines Why we use subroutines more modular program (small routines, outside data passed in) more readable, easier to debug code reuse i.e. smaller code space Memory Usage A software convention stack
MIPS Functions and the Runtime Stack
 MIPS Functions and the Runtime Stack COE 301 Computer Organization Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
MIPS Functions and the Runtime Stack COE 301 Computer Organization Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
MIPS Programming. A basic rule is: try to be mechanical (that is, don't be "tricky") when you translate high-level code into assembler code.
 MIPS Programming This is your crash course in assembler programming; you will teach yourself how to program in assembler for the MIPS processor. You will learn how to use the instruction set summary to
MIPS Programming This is your crash course in assembler programming; you will teach yourself how to program in assembler for the MIPS processor. You will learn how to use the instruction set summary to
ECE 473 Computer Architecture and Organization Lab 4: MIPS Assembly Programming Due: Wednesday, Oct. 19, 2011 (30 points)
 ECE 473 Computer Architecture and Organization Lab 4: MIPS Assembly Programming Due: Wednesday, Oct. 19, 2011 (30 points) Objectives: Get familiar with MIPS instructions Assemble, execute and debug MIPS
ECE 473 Computer Architecture and Organization Lab 4: MIPS Assembly Programming Due: Wednesday, Oct. 19, 2011 (30 points) Objectives: Get familiar with MIPS instructions Assemble, execute and debug MIPS
Computer Science 2500 Computer Organization Rensselaer Polytechnic Institute Spring Topic Notes: MIPS Programming
 Computer Science 2500 Computer Organization Rensselaer Polytechnic Institute Spring 2009 Topic Notes: MIPS Programming We spent some time looking at the MIPS Instruction Set Architecture. We will now consider
Computer Science 2500 Computer Organization Rensselaer Polytechnic Institute Spring 2009 Topic Notes: MIPS Programming We spent some time looking at the MIPS Instruction Set Architecture. We will now consider
Lecture 5: Procedure Calls
 Lecture 5: Procedure Calls Today s topics: Memory layout, numbers, control instructions Procedure calls 1 Memory Organization The space allocated on stack by a procedure is termed the activation record
Lecture 5: Procedure Calls Today s topics: Memory layout, numbers, control instructions Procedure calls 1 Memory Organization The space allocated on stack by a procedure is termed the activation record
MIPS function continued
 MIPS function continued Review Functions Series of related instructions one after another in memory Called through the jal instruction Pointed to by a label like any other Returns by calling Stack Top
MIPS function continued Review Functions Series of related instructions one after another in memory Called through the jal instruction Pointed to by a label like any other Returns by calling Stack Top
Implement a C language function that computes the factorial of a number, recursively, according to the following prototype:
 McGill University Department of Electrical and Computer Engineering ECSE-221 Introduction to Computer Engineering Assignment 5 Assembly and Datapaths Due Date: Monday, November 30 th 2009 at 11:59PM Question
McGill University Department of Electrical and Computer Engineering ECSE-221 Introduction to Computer Engineering Assignment 5 Assembly and Datapaths Due Date: Monday, November 30 th 2009 at 11:59PM Question
Function Calls. 1 Administrivia. Tom Kelliher, CS 240. Feb. 13, Announcements. Collect homework. Assignment. Read
 Function Calls Tom Kelliher, CS 240 Feb. 13, 2002 1 Administrivia Announcements Collect homework. Assignment Read 3.7 9. From Last Time SPIM lab. Outline 1. Function calls: stack execution model, memory
Function Calls Tom Kelliher, CS 240 Feb. 13, 2002 1 Administrivia Announcements Collect homework. Assignment Read 3.7 9. From Last Time SPIM lab. Outline 1. Function calls: stack execution model, memory
ECE 30 Introduction to Computer Engineering
 ECE 30 Introduction to Computer Engineering Study Problems, Set #4 Spring 2015 Note: To properly study and understand the problems below, it is strongly recommended to implement and run your solution (and/or
ECE 30 Introduction to Computer Engineering Study Problems, Set #4 Spring 2015 Note: To properly study and understand the problems below, it is strongly recommended to implement and run your solution (and/or
ECE232: Hardware Organization and Design
 ECE232: Hardware Organization and Design Lecture 6: Procedures Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Procedures have different names in different languages Java:
ECE232: Hardware Organization and Design Lecture 6: Procedures Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Procedures have different names in different languages Java:
Winter 2003 MID-SESSION TEST Monday, March 10 6:30 to 8:00pm
 University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Instructors: Dr. S. A. Norman (L01) and Dr. S. Yanushkevich (L02) Winter 2003 MID-SESSION TEST Monday,
University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Instructors: Dr. S. A. Norman (L01) and Dr. S. Yanushkevich (L02) Winter 2003 MID-SESSION TEST Monday,
Computer Architecture Instruction Set Architecture part 2. Mehran Rezaei
 Computer Architecture Instruction Set Architecture part 2 Mehran Rezaei Review Execution Cycle Levels of Computer Languages Stored Program Computer/Instruction Execution Cycle SPIM, a MIPS Interpreter
Computer Architecture Instruction Set Architecture part 2 Mehran Rezaei Review Execution Cycle Levels of Computer Languages Stored Program Computer/Instruction Execution Cycle SPIM, a MIPS Interpreter
MIPS Procedure Calls - Review
 MIPS Stacks and Subroutine Calls Cptr280 Dr Curtis Nelson MIPS Procedure Calls - Review When making a procedure or function call, it is necessary to: Place parameters you wish to pass where they can be
MIPS Stacks and Subroutine Calls Cptr280 Dr Curtis Nelson MIPS Procedure Calls - Review When making a procedure or function call, it is necessary to: Place parameters you wish to pass where they can be
Computer Architecture I Midterm I
 Computer Architecture I Midterm I April 11 2017 Computer Architecture I Midterm I Chinese Name: Pinyin Name: E-Mail... @shanghaitech.edu.cn: Question Points Score 1 1 2 12 3 16 4 14 5 18 6 17 7 22 Total:
Computer Architecture I Midterm I April 11 2017 Computer Architecture I Midterm I Chinese Name: Pinyin Name: E-Mail... @shanghaitech.edu.cn: Question Points Score 1 1 2 12 3 16 4 14 5 18 6 17 7 22 Total:
Branch Addressing. Jump Addressing. Target Addressing Example. The University of Adelaide, School of Computer Science 28 September 2015
 Branch Addressing Branch instructions specify Opcode, two registers, target address Most branch targets are near branch Forward or backward op rs rt constant or address 6 bits 5 bits 5 bits 16 bits PC-relative
Branch Addressing Branch instructions specify Opcode, two registers, target address Most branch targets are near branch Forward or backward op rs rt constant or address 6 bits 5 bits 5 bits 16 bits PC-relative
We will study the MIPS assembly language as an exemplar of the concept.
 MIPS Assembly Language 1 We will study the MIPS assembly language as an exemplar of the concept. MIPS assembly instructions each consist of a single token specifying the command to be carried out, and
MIPS Assembly Language 1 We will study the MIPS assembly language as an exemplar of the concept. MIPS assembly instructions each consist of a single token specifying the command to be carried out, and
ECE 2035 Programming HW/SW Systems Spring problems, 7 pages Exam One Solutions 4 February 2013
 Problem 1 (3 parts, 30 points) Code Fragments Part A (5 points) Write a MIPS code fragment that branches to label Target when register $1 is less than or equal to register $2. You may use only two instructions.
Problem 1 (3 parts, 30 points) Code Fragments Part A (5 points) Write a MIPS code fragment that branches to label Target when register $1 is less than or equal to register $2. You may use only two instructions.
ECE 331 Hardware Organization and Design. Professor Jay Taneja UMass ECE - Discussion 3 2/8/2018
 ECE 331 Hardware Organization and Design Professor Jay Taneja UMass ECE - jtaneja@umass.edu Discussion 3 2/8/2018 Study Jams Leader: Chris Bartoli Tuesday 5:30-6:45pm Elab 325 Wednesday 8:30-9:45pm Elab
ECE 331 Hardware Organization and Design Professor Jay Taneja UMass ECE - jtaneja@umass.edu Discussion 3 2/8/2018 Study Jams Leader: Chris Bartoli Tuesday 5:30-6:45pm Elab 325 Wednesday 8:30-9:45pm Elab
From Code to Program: CALL Con'nued (Linking, and Loading)
 ecture 13 Computer Science 61C Spring 2017 February 15th, 2017 From Code to Program: CALL Con'nued (Linking, and Loading) 1 Administrivia We know it still sucks but: Waitlist students: Please be patient.
ecture 13 Computer Science 61C Spring 2017 February 15th, 2017 From Code to Program: CALL Con'nued (Linking, and Loading) 1 Administrivia We know it still sucks but: Waitlist students: Please be patient.
Orange Coast College. Business Division. Computer Science Department CS 116- Computer Architecture. The Instructions
 Orange Coast College Business Division Computer Science Department CS 116- Computer Architecture The Instructions 1 1 Topics: Assembly language, assemblers MIPS R2000 Assembly language Instruction set
Orange Coast College Business Division Computer Science Department CS 116- Computer Architecture The Instructions 1 1 Topics: Assembly language, assemblers MIPS R2000 Assembly language Instruction set
ECE260: Fundamentals of Computer Engineering. Supporting Procedures in Computer Hardware
 Supporting Procedures in Computer Hardware James Moscola Dept. of Engineering & Computer Science York College of Pennsylvania Based on Computer Organization and Design, 5th Edition by Patterson & Hennessy
Supporting Procedures in Computer Hardware James Moscola Dept. of Engineering & Computer Science York College of Pennsylvania Based on Computer Organization and Design, 5th Edition by Patterson & Hennessy
CSc 256 Midterm 1 Fall 2011
 CSc 256 Midterm 1 Fall 2011 NAME: Problem 1a: Given the C++ function prototype and variable declarations: int func(int arg0, int *arg1, int *arg2); int *ptr, n, arr[10]; which of the following statements
CSc 256 Midterm 1 Fall 2011 NAME: Problem 1a: Given the C++ function prototype and variable declarations: int func(int arg0, int *arg1, int *arg2); int *ptr, n, arr[10]; which of the following statements
comp 180 Lecture 10 Outline of Lecture Procedure calls Saving and restoring registers Summary of MIPS instructions
 Outline of Lecture Procedure calls Saving and restoring registers Summary of MIPS instructions Procedure Calls A procedure of a subroutine is like an agent which needs certain information to perform a
Outline of Lecture Procedure calls Saving and restoring registers Summary of MIPS instructions Procedure Calls A procedure of a subroutine is like an agent which needs certain information to perform a
SPIM & MIPS Programming
 Computer Organization and Structure 2012 SPIM & MIPS Programming Department of Information Management National Taiwan University Outline Introduction to Assembly Language SPIM Getting Started MIPS Assembly
Computer Organization and Structure 2012 SPIM & MIPS Programming Department of Information Management National Taiwan University Outline Introduction to Assembly Language SPIM Getting Started MIPS Assembly
SPIM Instruction Set
 SPIM Instruction Set This document gives an overview of the more common instructions used in the SPIM simulator. Overview The SPIM simulator implements the full MIPS instruction set, as well as a large
SPIM Instruction Set This document gives an overview of the more common instructions used in the SPIM simulator. Overview The SPIM simulator implements the full MIPS instruction set, as well as a large
Subroutines. int main() { int i, j; i = 5; j = celtokel(i); i = j; return 0;}
 Subroutines Also called procedures or functions Example C code: int main() { int i, j; i = 5; j = celtokel(i); i = j; return 0;} // subroutine converts Celsius to kelvin int celtokel(int i) { return (i
Subroutines Also called procedures or functions Example C code: int main() { int i, j; i = 5; j = celtokel(i); i = j; return 0;} // subroutine converts Celsius to kelvin int celtokel(int i) { return (i
COMP2421 COMPUTER ORGANZATION. Lab 3
 Lab 3 Objectives: This lab shows you some basic techniques and syntax to write a MIPS program. Syntax includes system calls, load address instruction, load integer instruction, and arithmetic instructions
Lab 3 Objectives: This lab shows you some basic techniques and syntax to write a MIPS program. Syntax includes system calls, load address instruction, load integer instruction, and arithmetic instructions
Rui Wang, Assistant professor Dept. of Information and Communication Tongji University.
 Instructions: ti Language of the Computer Rui Wang, Assistant professor Dept. of Information and Communication Tongji University it Email: ruiwang@tongji.edu.cn Computer Hierarchy Levels Language understood
Instructions: ti Language of the Computer Rui Wang, Assistant professor Dept. of Information and Communication Tongji University it Email: ruiwang@tongji.edu.cn Computer Hierarchy Levels Language understood
Review Session 1 Fri. Jan 19, 2:15 pm 3:05 pm Thornton 102
 Review Session 1 Fri. Jan 19, 2:15 pm 3:05 pm Thornton 102 1. Agenda Announcements Homework hints MIPS instruction set Some PA1 thoughts MIPS procedure call convention and example 1 2. Announcements Homework
Review Session 1 Fri. Jan 19, 2:15 pm 3:05 pm Thornton 102 1. Agenda Announcements Homework hints MIPS instruction set Some PA1 thoughts MIPS procedure call convention and example 1 2. Announcements Homework
2B 52 AB CA 3E A1 +29 A B C. CS120 Fall 2018 Final Prep and super secret quiz 9
 S2 Fall 28 Final Prep and super secret quiz 9 ) onvert 8-bit (2-digit) 2 s complement hex values: 4-29 inary: Hex: x29 2) onvert 8-bit 2 s complement hex to decimal: x3 inary: xe5 Decimal: 58 Note 3*6+
S2 Fall 28 Final Prep and super secret quiz 9 ) onvert 8-bit (2-digit) 2 s complement hex values: 4-29 inary: Hex: x29 2) onvert 8-bit 2 s complement hex to decimal: x3 inary: xe5 Decimal: 58 Note 3*6+
Computer Organization MIPS Architecture. Department of Computer Science Missouri University of Science & Technology
 Computer Organization MIPS Architecture Department of Computer Science Missouri University of Science & Technology hurson@mst.edu Computer Organization Note, this unit will be covered in three lectures.
Computer Organization MIPS Architecture Department of Computer Science Missouri University of Science & Technology hurson@mst.edu Computer Organization Note, this unit will be covered in three lectures.
MIPS Datapath. MIPS Registers (and the conventions associated with them) MIPS Instruction Types
 1 Lecture 08 Introduction to the MIPS ISA + Procedure Calls in MIPS Longer instructions = more bits to address registers MIPS Datapath 6 bit opcodes... 2 MIPS Instructions are 32 bits More ways to address
1 Lecture 08 Introduction to the MIPS ISA + Procedure Calls in MIPS Longer instructions = more bits to address registers MIPS Datapath 6 bit opcodes... 2 MIPS Instructions are 32 bits More ways to address
ECE260: Fundamentals of Computer Engineering
 Accessing and Addressing Memory James Moscola Dept. of Engineering & Computer Science York College of Pennsylvania Based on Computer Organization and Design, 5th Edition by Patterson & Hennessy American
Accessing and Addressing Memory James Moscola Dept. of Engineering & Computer Science York College of Pennsylvania Based on Computer Organization and Design, 5th Edition by Patterson & Hennessy American
Lec 10: Assembler. Announcements
 Lec 10: Assembler Kavita Bala CS 3410, Fall 2008 Computer Science Cornell University Announcements HW 2 is out Due Wed after Fall Break Robot-wide paths PA 1 is due next Wed Don t use incrementor 4 times
Lec 10: Assembler Kavita Bala CS 3410, Fall 2008 Computer Science Cornell University Announcements HW 2 is out Due Wed after Fall Break Robot-wide paths PA 1 is due next Wed Don t use incrementor 4 times
Problem maximum score 1 35pts 2 22pts 3 23pts 4 15pts Total 95pts
 University of California at Berkeley College of Engineering Department of Electrical Engineering and Computer Sciences CS61c Summer 2001 Woojin Yu Midterm Exam This is a closed-book exam. No calculators
University of California at Berkeley College of Engineering Department of Electrical Engineering and Computer Sciences CS61c Summer 2001 Woojin Yu Midterm Exam This is a closed-book exam. No calculators
MIPS Architecture and Assembly Language Overview
 MIPS Architecture and Assembly Language Overview Adapted from: http://edge.mcs.dre.g.el.edu/gicl/people/sevy/architecture/mipsref(spim).html [Register Description] [I/O Description] Data Types and Literals
MIPS Architecture and Assembly Language Overview Adapted from: http://edge.mcs.dre.g.el.edu/gicl/people/sevy/architecture/mipsref(spim).html [Register Description] [I/O Description] Data Types and Literals
MIPS R-format Instructions. Representing Instructions. Hexadecimal. R-format Example. MIPS I-format Example. MIPS I-format Instructions
 Representing Instructions Instructions are encoded in binary Called machine code MIPS instructions Encoded as 32-bit instruction words Small number of formats encoding operation code (opcode), register
Representing Instructions Instructions are encoded in binary Called machine code MIPS instructions Encoded as 32-bit instruction words Small number of formats encoding operation code (opcode), register
Procedure Calling. Procedure Calling. Register Usage. 25 September CSE2021 Computer Organization
 CSE2021 Computer Organization Chapter 2: Part 2 Procedure Calling Procedure (function) performs a specific task and return results to caller. Supporting Procedures Procedure Calling Calling program place
CSE2021 Computer Organization Chapter 2: Part 2 Procedure Calling Procedure (function) performs a specific task and return results to caller. Supporting Procedures Procedure Calling Calling program place
We can emit stack-machine-style code for expressions via recursion
 Code Generation The Main Idea of Today s Lecture We can emit stack-machine-style code for expressions via recursion (We will use MIPS assembly as our target language) 2 Lecture Outline What are stack machines?
Code Generation The Main Idea of Today s Lecture We can emit stack-machine-style code for expressions via recursion (We will use MIPS assembly as our target language) 2 Lecture Outline What are stack machines?
Instruction Set Architecture part 1 (Introduction) Mehran Rezaei
 Instruction Set Architecture part 1 (Introduction) Mehran Rezaei Overview Last Lecture s Review Execution Cycle Levels of Computer Languages Stored Program Computer/Instruction Execution Cycle SPIM, a
Instruction Set Architecture part 1 (Introduction) Mehran Rezaei Overview Last Lecture s Review Execution Cycle Levels of Computer Languages Stored Program Computer/Instruction Execution Cycle SPIM, a
ECE 2035 Programming HW/SW Systems Spring problems, 6 pages Exam Two 11 March Your Name (please print) total
 Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Review (1/2) IEEE 754 Floating Point Standard: Kahan pack as much in as could get away with. CS61C - Machine Structures
 Review (1/2) CS61C - Machine Structures Lecture 11 - Starting a Program October 4, 2000 David Patterson http://www-inst.eecs.berkeley.edu/~cs61c/ IEEE 754 Floating Point Standard: Kahan pack as much in
Review (1/2) CS61C - Machine Structures Lecture 11 - Starting a Program October 4, 2000 David Patterson http://www-inst.eecs.berkeley.edu/~cs61c/ IEEE 754 Floating Point Standard: Kahan pack as much in
Code Genera*on for Control Flow Constructs
 Code Genera*on for Control Flow Constructs 1 Roadmap Last *me: Got the basics of MIPS CodeGen for some AST node types This *me: Do the rest of the AST nodes Introduce control flow graphs Scanner Parser
Code Genera*on for Control Flow Constructs 1 Roadmap Last *me: Got the basics of MIPS CodeGen for some AST node types This *me: Do the rest of the AST nodes Introduce control flow graphs Scanner Parser
CENG3420 Lab 1-1: MIPS assembly language programing
 CENG3420 Lab 1-1: MIPS assembly language programing Haoyu YANG Department of Computer Science and Engineering The Chinese University of Hong Kong hyyang@cse.cuhk.edu.hk 2017 Spring 1 / 18 Overview SPIM
CENG3420 Lab 1-1: MIPS assembly language programing Haoyu YANG Department of Computer Science and Engineering The Chinese University of Hong Kong hyyang@cse.cuhk.edu.hk 2017 Spring 1 / 18 Overview SPIM
CS 2630 Computer Organization. Meeting 10/11: data structures in MIPS Brandon Myers University of Iowa
 CS 2630 Computer Organization Meeting 10/11: data structures in MIPS Brandon Myers University of Iowa Where we are going Compiler Instruction set architecture (e.g., MIPS) translating source code (C or
CS 2630 Computer Organization Meeting 10/11: data structures in MIPS Brandon Myers University of Iowa Where we are going Compiler Instruction set architecture (e.g., MIPS) translating source code (C or
CS 61C: Great Ideas in Computer Architecture CALL continued ( Linking and Loading)
 CS 61C: Great Ideas in Computer Architecture CALL continued ( Linking and Loading) Instructors: Nicholas Weaver & Vladimir Stojanovic http://inst.eecs.berkeley.edu/~cs61c/sp16 1 Where Are We Now? 2 Linker
CS 61C: Great Ideas in Computer Architecture CALL continued ( Linking and Loading) Instructors: Nicholas Weaver & Vladimir Stojanovic http://inst.eecs.berkeley.edu/~cs61c/sp16 1 Where Are We Now? 2 Linker
Function Calls. Tom Kelliher, CS 220. Oct. 24, SPIM programs due Wednesday. Refer to homework handout for what to turn in, and how.
 Function Calls Tom Kelliher, CS 220 Oct. 24, 2011 1 Administrivia Announcements Assignment SPIM programs due Wednesday. Refer to homework handout for what to turn in, and how. From Last Time Outline 1.
Function Calls Tom Kelliher, CS 220 Oct. 24, 2011 1 Administrivia Announcements Assignment SPIM programs due Wednesday. Refer to homework handout for what to turn in, and how. From Last Time Outline 1.
MIPS%Assembly% E155%
 MIPS%Assembly% E155% Outline MIPS Architecture ISA Instruction types Machine codes Procedure call Stack 2 The MIPS Register Set Name Register Number Usage $0 0 the constant value 0 $at 1 assembler temporary
MIPS%Assembly% E155% Outline MIPS Architecture ISA Instruction types Machine codes Procedure call Stack 2 The MIPS Register Set Name Register Number Usage $0 0 the constant value 0 $at 1 assembler temporary
Chapter 3. Instructions:
 Chapter 3 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very restrictive e.g., MIPS Arithmetic Instructions We ll be working with
Chapter 3 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very restrictive e.g., MIPS Arithmetic Instructions We ll be working with
Previously. CSE 2021: Computer Organization. Memory Organization. The Load/Store Family (1) 5/26/2011. Used to transfer data to/from DRAM.
 CSE 2021: Computer Organization Lecture-4 Code Translation-2 Memory, Data transfer instructions, Data segment,, Procedures, Stack Shakil M. Khan (adapted from Profs. Roumani & Asif) Previously Registers
CSE 2021: Computer Organization Lecture-4 Code Translation-2 Memory, Data transfer instructions, Data segment,, Procedures, Stack Shakil M. Khan (adapted from Profs. Roumani & Asif) Previously Registers
SPIM Procedure Calls
 SPIM Procedure Calls 22C:60 Jonathan Hall March 29, 2008 1 Motivation We would like to create procedures that are easy to use and easy to read. To this end we will discuss standard conventions as it relates
SPIM Procedure Calls 22C:60 Jonathan Hall March 29, 2008 1 Motivation We would like to create procedures that are easy to use and easy to read. To this end we will discuss standard conventions as it relates
EE 361 University of Hawaii Fall
 C functions Road Map Computation flow Implementation using MIPS instructions Useful new instructions Addressing modes Stack data structure 1 EE 361 University of Hawaii Implementation of C functions and
C functions Road Map Computation flow Implementation using MIPS instructions Useful new instructions Addressing modes Stack data structure 1 EE 361 University of Hawaii Implementation of C functions and
Prof. Kavita Bala and Prof. Hakim Weatherspoon CS 3410, Spring 2014 Computer Science Cornell University. See P&H 2.8 and 2.12, and A.
 Prof. Kavita Bala and Prof. Hakim Weatherspoon CS 3410, Spring 2014 Computer Science Cornell University See P&H 2.8 and 2.12, and A.5 6 compute jump/branch targets memory PC +4 new pc Instruction Fetch
Prof. Kavita Bala and Prof. Hakim Weatherspoon CS 3410, Spring 2014 Computer Science Cornell University See P&H 2.8 and 2.12, and A.5 6 compute jump/branch targets memory PC +4 new pc Instruction Fetch
1/26/2014. Previously. CSE 2021: Computer Organization. The Load/Store Family (1) Memory Organization. The Load/Store Family (2)
 CSE 202: Computer Organization Lecture-4 Code Translation-2 Memory, Data transfer instructions, Data segment,, Procedures, Stack Shakil M. Khan (adapted from Prof. Roumani) Previously Registers $s0 - $s7,
CSE 202: Computer Organization Lecture-4 Code Translation-2 Memory, Data transfer instructions, Data segment,, Procedures, Stack Shakil M. Khan (adapted from Prof. Roumani) Previously Registers $s0 - $s7,
ECE 2035 A Programming Hw/Sw Systems Spring problems, 8 pages Final Exam 29 April 2015
 Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
QtSPIM and MARS : MIPS Simulators
 QtSPIM and MARS : MIPS Simulators Learning MIPS & SPIM MIPS assembly is a low-level programming language The best way to learn any programming language is to write code We will get you started by going
QtSPIM and MARS : MIPS Simulators Learning MIPS & SPIM MIPS assembly is a low-level programming language The best way to learn any programming language is to write code We will get you started by going
ECE 2035 A Programming Hw/Sw Systems Fall problems, 8 pages Final Exam 9 December 2015
 Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Shift and Rotate Instructions
 Shift and Rotate Instructions Shift and rotate instructions facilitate manipulations of data (that is, modifying part of a 32-bit data word). Such operations might include: Re-arrangement of bytes in a
Shift and Rotate Instructions Shift and rotate instructions facilitate manipulations of data (that is, modifying part of a 32-bit data word). Such operations might include: Re-arrangement of bytes in a
ECE260: Fundamentals of Computer Engineering
 Accessing and Addressing Memory James Moscola Dept. of Engineering & Computer Science York College of Pennsylvania Based on Computer Organization and Design, 5th Edition by Patterson & Hennessy American
Accessing and Addressing Memory James Moscola Dept. of Engineering & Computer Science York College of Pennsylvania Based on Computer Organization and Design, 5th Edition by Patterson & Hennessy American
MIPS Assembly Programming
 COMP 212 Computer Organization & Architecture COMP 212 Fall 2008 Lecture 8 Cache & Disk System Review MIPS Assembly Programming Comp 212 Computer Org & Arch 1 Z. Li, 2008 Comp 212 Computer Org & Arch 2
COMP 212 Computer Organization & Architecture COMP 212 Fall 2008 Lecture 8 Cache & Disk System Review MIPS Assembly Programming Comp 212 Computer Org & Arch 1 Z. Li, 2008 Comp 212 Computer Org & Arch 2
COMP2611: Computer Organization MIPS function and recursion
 COMP2611 Fall2015 COMP2611: Computer Organization MIPS function and recursion Overview 2 You will learn the following in this lab: how to use MIPS functions in a program; the concept of recursion; how
COMP2611 Fall2015 COMP2611: Computer Organization MIPS function and recursion Overview 2 You will learn the following in this lab: how to use MIPS functions in a program; the concept of recursion; how
MIPS Assembly Language Programming
 MIPS Assembly Language Programming COE 308 Computer Architecture Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline Assembly
MIPS Assembly Language Programming COE 308 Computer Architecture Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline Assembly
ECE 2035 Programming HW/SW Systems Fall problems, 6 pages Exam Two 23 October Your Name (please print clearly) Signed.
 Your Name (please print clearly) This exam will be conducted according to the Georgia Tech Honor Code. I pledge to neither give nor receive unauthorized assistance on this exam and to abide by all provisions
Your Name (please print clearly) This exam will be conducted according to the Georgia Tech Honor Code. I pledge to neither give nor receive unauthorized assistance on this exam and to abide by all provisions
University of California, Berkeley College of Engineering
 University of California, Berkeley College of Engineering Department of Electrical Engineering and Computer Sciences Fall 2015 Instructors: Vladimir Stojanovic, John Wawrzynek 2015-09-06 L J After the
University of California, Berkeley College of Engineering Department of Electrical Engineering and Computer Sciences Fall 2015 Instructors: Vladimir Stojanovic, John Wawrzynek 2015-09-06 L J After the
Do-While Example. In C++ In assembly language. do { z--; while (a == b); z = b; loop: addi $s2, $s2, -1 beq $s0, $s1, loop or $s2, $s1, $zero
 Do-While Example In C++ do { z--; while (a == b); z = b; In assembly language loop: addi $s2, $s2, -1 beq $s0, $s1, loop or $s2, $s1, $zero 25 Comparisons Set on less than (slt) compares its source registers
Do-While Example In C++ do { z--; while (a == b); z = b; In assembly language loop: addi $s2, $s2, -1 beq $s0, $s1, loop or $s2, $s1, $zero 25 Comparisons Set on less than (slt) compares its source registers
MIPS Reference Guide
 MIPS Reference Guide Free at PushingButtons.net 2 Table of Contents I. Data Registers 3 II. Instruction Register Formats 4 III. MIPS Instruction Set 5 IV. MIPS Instruction Set (Extended) 6 V. SPIM Programming
MIPS Reference Guide Free at PushingButtons.net 2 Table of Contents I. Data Registers 3 II. Instruction Register Formats 4 III. MIPS Instruction Set 5 IV. MIPS Instruction Set (Extended) 6 V. SPIM Programming
CSC258: Computer Organization. Functions and the Compiler Tool Chain
 CSC258: Computer Organization Functions and the Compiler Tool Chain 1 A Note about This Week s Quiz There were very few exercises this week, except for writing substantial pieces of code. Instead, I provided
CSC258: Computer Organization Functions and the Compiler Tool Chain 1 A Note about This Week s Quiz There were very few exercises this week, except for writing substantial pieces of code. Instead, I provided
Chapter 2. Instructions:
 Chapter 2 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very restrictive e.g., MIPS Arithmetic Instructions We ll be working with
Chapter 2 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very restrictive e.g., MIPS Arithmetic Instructions We ll be working with
ENCM 369 Winter 2013: Reference Material for Midterm #2 page 1 of 5
 ENCM 369 Winter 2013: Reference Material for Midterm #2 page 1 of 5 MIPS/SPIM General Purpose Registers Powers of Two 0 $zero all bits are zero 16 $s0 local variable 1 $at assembler temporary 17 $s1 local
ENCM 369 Winter 2013: Reference Material for Midterm #2 page 1 of 5 MIPS/SPIM General Purpose Registers Powers of Two 0 $zero all bits are zero 16 $s0 local variable 1 $at assembler temporary 17 $s1 local
Implementing Procedure Calls
 1 / 39 Implementing Procedure Calls February 18 22, 2013 2 / 39 Outline Intro to procedure calls Caller vs. callee Procedure call basics Calling conventions The stack Interacting with the stack Structure
1 / 39 Implementing Procedure Calls February 18 22, 2013 2 / 39 Outline Intro to procedure calls Caller vs. callee Procedure call basics Calling conventions The stack Interacting with the stack Structure
Lecture 6: Assembly Programs
 Lecture 6: Assembly Programs Today s topics: Procedures Examples Large constants The compilation process A full example 1 Procedures Local variables, AR, $fp, $sp Scratchpad and saves/restores, $fp Arguments
Lecture 6: Assembly Programs Today s topics: Procedures Examples Large constants The compilation process A full example 1 Procedures Local variables, AR, $fp, $sp Scratchpad and saves/restores, $fp Arguments
Instruction Set Architectures (4)
 Computer Architecture Week 06 Instruction Set Architectures (4) College of Information Science and Engineering Ritsumeikan University subroutines functions, procedures remember the next instruction s address
Computer Architecture Week 06 Instruction Set Architectures (4) College of Information Science and Engineering Ritsumeikan University subroutines functions, procedures remember the next instruction s address
Programming with QtSpim: A User s Manual
 Programming with QtSpim: A User s Manual John McCranie November 15, 2013 1 1 Introduction to SPIM Spim is a self-contained simulator that runs MIPS32 programs. It utilizes the instruction set originally
Programming with QtSpim: A User s Manual John McCranie November 15, 2013 1 1 Introduction to SPIM Spim is a self-contained simulator that runs MIPS32 programs. It utilizes the instruction set originally
Lecture 7: MIPS Functions Part 2. Nested Function Calls. Lecture 7: Character and String Operations. SPIM Syscalls. Recursive Functions
 Part Part Part What if we need to call a function inside of a function? Will this work? int twofun(int a, int b) { int res; res = addfun(a, b) a / ; return res; } twofun: addi $sp, $sp, -4 sw $s0, 0($sp)
Part Part Part What if we need to call a function inside of a function? Will this work? int twofun(int a, int b) { int res; res = addfun(a, b) a / ; return res; } twofun: addi $sp, $sp, -4 sw $s0, 0($sp)
MIPS Assembly Language Programming
 MIPS Assembly Language Programming ICS 233 Computer Architecture and Assembly Language Dr. Aiman El-Maleh College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals [Adapted
MIPS Assembly Language Programming ICS 233 Computer Architecture and Assembly Language Dr. Aiman El-Maleh College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals [Adapted
MIPS Assembly (Functions)
 ECPE 170 Jeff Shafer University of the Pacific MIPS Assembly (Functions) 2 Lab Schedule This Week Activities Lab work time MIPS functions MIPS Random Number Generator Lab 11 Assignments Due Due by Apr
ECPE 170 Jeff Shafer University of the Pacific MIPS Assembly (Functions) 2 Lab Schedule This Week Activities Lab work time MIPS functions MIPS Random Number Generator Lab 11 Assignments Due Due by Apr
ECE 2035 Programming HW/SW Systems Fall problems, 6 pages Exam Two 21 October 2016
 Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
CENG3420 Computer Organization and Design Lab 1-2: System calls and recursions
 CENG3420 Computer Organization and Design Lab 1-2: System calls and recursions Wen Zong Department of Computer Science and Engineering The Chinese University of Hong Kong wzong@cse.cuhk.edu.hk Overview
CENG3420 Computer Organization and Design Lab 1-2: System calls and recursions Wen Zong Department of Computer Science and Engineering The Chinese University of Hong Kong wzong@cse.cuhk.edu.hk Overview
Computer Science and Engineering 331. Midterm Examination #1. Fall Name: Solutions S.S.#:
 Computer Science and Engineering 331 Midterm Examination #1 Fall 2000 Name: Solutions S.S.#: 1 41 2 13 3 18 4 28 Total 100 Instructions: This exam contains 4 questions. It is closed book and notes. Calculators
Computer Science and Engineering 331 Midterm Examination #1 Fall 2000 Name: Solutions S.S.#: 1 41 2 13 3 18 4 28 Total 100 Instructions: This exam contains 4 questions. It is closed book and notes. Calculators
ECE331: Hardware Organization and Design
 ECE331: Hardware Organization and Design Lecture 8: Procedures (cont d), Binary Numbers and Adders Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Review: Procedure Calling Steps
ECE331: Hardware Organization and Design Lecture 8: Procedures (cont d), Binary Numbers and Adders Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Review: Procedure Calling Steps
Code Generation. The Main Idea of Today s Lecture. We can emit stack-machine-style code for expressions via recursion. Lecture Outline.
 The Main Idea of Today s Lecture Code Generation We can emit stack-machine-style code for expressions via recursion (We will use MIPS assembly as our target language) 2 Lecture Outline What are stack machines?
The Main Idea of Today s Lecture Code Generation We can emit stack-machine-style code for expressions via recursion (We will use MIPS assembly as our target language) 2 Lecture Outline What are stack machines?
Review C program: foo.c Compiler Assembly program: foo.s Assembler Object(mach lang module): foo.o
 CS61C L18 Running a Program I (1) inst.eecs.berkeley.edu/~cs61c UC Berkeley CS61C : Machine Structures Lecture 19 Running a Program II aka Compiling, Assembling, Linking, Loading 2006-10-11 (aka 2006-0xB)
CS61C L18 Running a Program I (1) inst.eecs.berkeley.edu/~cs61c UC Berkeley CS61C : Machine Structures Lecture 19 Running a Program II aka Compiling, Assembling, Linking, Loading 2006-10-11 (aka 2006-0xB)
CS61C : Machine Structures
 inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures #13 Running a Program II aka Compiling, Assembling, Linking, Loading (CALL) 2007-7-17 Scott Beamer, Instructor Green Subscription Based PC Announced
inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures #13 Running a Program II aka Compiling, Assembling, Linking, Loading (CALL) 2007-7-17 Scott Beamer, Instructor Green Subscription Based PC Announced
Assembler. #13 Running a Program II
 CS61C L13 Running a Program II (1) inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures #13 Running a Program II aka Compiling, Assembling, Linking, Loading (CALL) 2007-7-17 Scott Beamer, Instructor
CS61C L13 Running a Program II (1) inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures #13 Running a Program II aka Compiling, Assembling, Linking, Loading (CALL) 2007-7-17 Scott Beamer, Instructor
Code Generation. Lecture 19
 Code Generation Lecture 19 Lecture Outline Topic 1: Basic Code Generation The MIPS assembly language A simple source language Stack-machine implementation of the simple language Topic 2: Code Generation
Code Generation Lecture 19 Lecture Outline Topic 1: Basic Code Generation The MIPS assembly language A simple source language Stack-machine implementation of the simple language Topic 2: Code Generation
Chapter 2. Computer Abstractions and Technology. Lesson 4: MIPS (cont )
 Chapter 2 Computer Abstractions and Technology Lesson 4: MIPS (cont ) Logical Operations Instructions for bitwise manipulation Operation C Java MIPS Shift left >>> srl Bitwise
Chapter 2 Computer Abstractions and Technology Lesson 4: MIPS (cont ) Logical Operations Instructions for bitwise manipulation Operation C Java MIPS Shift left >>> srl Bitwise
MIPS ISA and MIPS Assembly. CS301 Prof. Szajda
 MIPS ISA and MIPS Assembly CS301 Prof. Szajda Administrative HW #2 due Wednesday (9/11) at 5pm Lab #2 due Friday (9/13) 1:30pm Read Appendix B5, B6, B.9 and Chapter 2.5-2.9 (if you have not already done
MIPS ISA and MIPS Assembly CS301 Prof. Szajda Administrative HW #2 due Wednesday (9/11) at 5pm Lab #2 due Friday (9/13) 1:30pm Read Appendix B5, B6, B.9 and Chapter 2.5-2.9 (if you have not already done
Question 0. Do not turn this page until you have received the signal to start. (Please fill out the identification section above) Good Luck!
 CSC B58 Winter 2017 Final Examination Duration 2 hours and 50 minutes Aids allowed: none Last Name: Student Number: UTORid: First Name: Question 0. [1 mark] Read and follow all instructions on this page,
CSC B58 Winter 2017 Final Examination Duration 2 hours and 50 minutes Aids allowed: none Last Name: Student Number: UTORid: First Name: Question 0. [1 mark] Read and follow all instructions on this page,
Compiling Code, Procedures and Stacks
 Compiling Code, Procedures and Stacks L03-1 RISC-V Recap Computational Instructions executed by ALU Register-Register: op dest, src1, src2 Register-Immediate: op dest, src1, const Control flow instructions
Compiling Code, Procedures and Stacks L03-1 RISC-V Recap Computational Instructions executed by ALU Register-Register: op dest, src1, src2 Register-Immediate: op dest, src1, const Control flow instructions
MIPS Functions and Instruction Formats
 MIPS Functions and Instruction Formats 1 The Contract: The MIPS Calling Convention You write functions, your compiler writes functions, other compilers write functions And all your functions call other
MIPS Functions and Instruction Formats 1 The Contract: The MIPS Calling Convention You write functions, your compiler writes functions, other compilers write functions And all your functions call other
Calling Conventions. Hakim Weatherspoon CS 3410, Spring 2012 Computer Science Cornell University. See P&H 2.8 and 2.12
 Calling Conventions Hakim Weatherspoon CS 3410, Spring 2012 Computer Science Cornell University See P&H 2.8 and 2.12 Goals for Today Calling Convention for Procedure Calls Enable code to be reused by allowing
Calling Conventions Hakim Weatherspoon CS 3410, Spring 2012 Computer Science Cornell University See P&H 2.8 and 2.12 Goals for Today Calling Convention for Procedure Calls Enable code to be reused by allowing
Anne Bracy CS 3410 Computer Science Cornell University
 Anne Bracy CS 3410 Computer Science Cornell University The slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, McKee, and Sirer. See P&H 2.8 and 2.12, and
Anne Bracy CS 3410 Computer Science Cornell University The slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, McKee, and Sirer. See P&H 2.8 and 2.12, and
COMP 303 Computer Architecture Lecture 3. Comp 303 Computer Architecture
 COMP 303 Computer Architecture Lecture 3 Comp 303 Computer Architecture 1 Supporting procedures in computer hardware The execution of a procedure Place parameters in a place where the procedure can access
COMP 303 Computer Architecture Lecture 3 Comp 303 Computer Architecture 1 Supporting procedures in computer hardware The execution of a procedure Place parameters in a place where the procedure can access
ECE Exam I February 19 th, :00 pm 4:25pm
 ECE 3056 Exam I February 19 th, 2015 3:00 pm 4:25pm 1. The exam is closed, notes, closed text, and no calculators. 2. The Georgia Tech Honor Code governs this examination. 3. There are 4 questions and
ECE 3056 Exam I February 19 th, 2015 3:00 pm 4:25pm 1. The exam is closed, notes, closed text, and no calculators. 2. The Georgia Tech Honor Code governs this examination. 3. There are 4 questions and
MIPS Coding Snippets. Prof. James L. Frankel Harvard University. Version of 9:32 PM 14-Feb-2016 Copyright 2016 James L. Frankel. All rights reserved.
 MIPS Coding Snippets Prof. James L. Frankel Harvard University Version of 9:32 PM 14-Feb-2016 Copyright 2016 James L. Frankel. All rights reserved. Loading a 32-bit constant into a register # Example loading
MIPS Coding Snippets Prof. James L. Frankel Harvard University Version of 9:32 PM 14-Feb-2016 Copyright 2016 James L. Frankel. All rights reserved. Loading a 32-bit constant into a register # Example loading
