Lecture 17 Bit Operations
|
|
|
- Daniella Walsh
- 5 years ago
- Views:
Transcription
1 Lecture 17 Bit Operations In this lecture Background Left Shifting Negative Numbers, one s complement and two s complement Right Shifting Bit Operators Masking the Bits Getting the Bits Setting the Bits Binary Files Bit fields More Exercises C is a powerful language and allows programmer many operations for bit manipulation. Data can be accessed at the bit level to make operations and storage more efficient. As you will see, bit operations can be used to do many things including setting flags, encrypting and decrypting images as we will implement in one of the lab assignments. Bit operations can also be used to efficiently pack data into a more compressed form. For example, an entire array of 16 boolean values can be represented by just 2 bytes of data or an IP address such as can be packed into 32 bits of storage. This can come very handy in cases where data needs to be transmitted through a limited bandwidth network or in cases where we simply need to store data more efficiently for better memory management in the application. For example, when programming mobile devices with limited memory, you may want to work at the bit level to make things more efficient and save memory. Also understanding bit operations can be useful in writing device drivers and many other low level applications. First we will discuss the bit shift operations. Left Shifting Think of the following possibility. Suppose we want to multiply an unsigned integer by 2. We can simply shift all bits to the left by one position (assuming no overflow). For example, if a 32-bit unsigned integer 73 is given as
2 Then shifting the bits by 1 position to the left gives us the bit pattern for unsigned So we can write unsigned int x = 73; x = x<<1; or simply x <<= 1; The operator << is used to shift the bit patterns of a variable. For example, x << n shifts the bit patterns of x by n positions resulting in the number x*2 n assuming there is no overflow. It should be noted that as we left shift, the missing bits on the right are filled by 0 s. Negative Numbers, One s Complement and Two s Complement Signed data is generally represented in the computer in their two s complement. Two s complement of a number is obtained by adding 1 to its one s complement. So how do we find one s complement of a number? Here is the definition One s complement of x is given by ~x. Obtain the one s complement of a number by negating each of its binary bits. For example one s complement of 30 is (represented as a 16- bit short int) 30 = = binary 30 ~30 = its one s complement The two s complement of the number is obtained by adding 1 to its one s complement. That is, the two s complement of 30 is obtained as follows Hence -30 is represented as its two s complement, that is ~ = Exercise 17.1: Perform binary addition of 34 + (-89) using two s complement of the negative number.
3 Right Shifting The bit pattern of a variable can be shifted right using bit operations. For example, x >> n, shifts the bit pattern of x by n positions to the right. The missing bits on the left are filled by the value of the highest order bit (0 or 1). Example: -73 is represented as Using a 2 s complement. -73 >> 2 will result in the bit pattern Question: What number does this represents? Bit Operators Table Operator Meaning << Left Shift >> Right Shift Bitwise OR & Bitwise AND ^ Exclusive OR ~ One s complement 1+~x Two s complement of x We have learned the basic bit operations such as left shift (<<), right shift (>>), and the above table gives other bit operations such as bitwise OR ( ) and bitwise AND (&) etc. The basic logic circuits for AND, OR or NEGATION are given as follows The Bitwise AND (&) A b a & b
4 The Bitwise OR ( ) A b a b The Bitwise NEGATION (~) A ~a We note that just applying a bit operation to a variable x, does not change its value. That is, x 2 gives a value equivalent to 2 nd bit of x set to 1. But it does not change the value of x, unless we do; x = 2 ; Meaning that x = x 2 Each one is clearly useful for many operations that require bit extraction and masking of bits. For example, to extract the j th bit of a variable w, one can shift w to right by j places and then bitwise AND with 1. That is,(w>>j)&1 is either 1 or 0 depending on j th bit of w is 1 or 0. We can set the first 4 bits of x to 1 by doing x 0x0F In this case, 0x0F represents a hex value of one byte where first 4 bits are 1 s and next 4 bits are 0 s. That is Exercise 17.2: What would be the outcome of x & 0x0F? Exercise 17.3: What would be the outcome of x & 0127, where 0127 represents the number 127 that is in octal form?
5 XOR operation Another operator of interest is the XOR gate. The bitwise exclusive OR operator is given by ^ Here is the table for XOR First bit a Second bit b XOR a^b Example: 0001 ^ 0101 will result in 0100 Adding Two Numbers We can use ^ operator to implement a function that adds two numbers, bit by bit. For example, sum of just two bits x and y is given by x^y with a carry x&y. A full adder that goes through all bits and adds values is given as follows. A i denotes the i th bit of A and B i denotes the i th bit of B and C in denotes the carry in and C out denotes the carry out. S i = (A i ^ B i ) ^ C in C out = (A i & B i ) ((A i ^ B i ) & C in ) We will not go into the details of how to derive the sum and carry functions as shown above. However, completing a table that shows bit values, carry in, sum and carry out may give some insight into how formulas are derived. See classwork folder in democode for an implementation of addition for two bytes. Masking the Bits In many instances we need to find a specific bit or a group of bits. For example, given an IP address as a 32-bit unsigned int we may want to extract 192 or last 8 bits of the 32-bit word. This can be done using an appropriate mask (perhaps with shifting) and applying a bitwise AND operation. Another interesting application of bit manipulation is finding the remainder of an unsigned integer when divided by, say 2. You simply have to find out the first bit of the number. We can accomplish this by masking the number with specific value. Lets us consider 73. The bit pattern is
6 Suppose we take bitwise AND or apply operator & as follows = 73 & = 1 This results in the value 0 or 1 depending on the last bit of 73. In this case we get 1. Therefore the remainder when 73 divided by 2 is 1. For example we can test if a number of odd or even by simply saying, int x = 73; if (x&1) printf( The number is odd\n ); else printf( the number is even\n ); Accessing Bits Masking a variable allows us to look at individual bits of the variable. For example, let us assume that we need to write a function called getbit(int w, unsigned j) that allows us to access the j th bit of an int variable w. The following code does it. #define MASK(j) (1<<j) int getbit(int w, unsigned j){ return (( w & MASK(j)) == 0)? 0 : 1; } Note that 1 is shifted to left by j bits and then taken bitwise & with w. Alternatively, we can write a macro getbit(w,i) as follows. #define getbit(w,i) ((w>>i)&1) Exercise 17.4: Write a function, printbinary(unsigned int w) that prints the binary representation of w.
7 Setting the Bits Another useful application of bit operations is setting the bits of a variable. For example, UNIX file system uses a 16-bit quantity known as the file mode. Assuming a 16-bit word, f e d c b a The bits 0-8 are reserved for file access permission r w x for other, group and owner. The next 3 bits are reserved for the execution style, and the last 4 bits are reserved for the file type. For example, a file that gives read, write, execute access to group, other and owner may have its file access permission as rwxrwxrwx (bits 0-8) A good application to use setbit is to consider the chmod command chmod 761 file.txt; sets the rights to the file.txt as follows. -rwxrw---x 1 guna staff 3 Feb 19 12:07 file.txt This would require us to set the bits of the word that represents the file access permission. So if we are writing our own chmod function, we can manipulate the bits of the file access permission structure to achieve the results. First, let us learn how to set a specific bit of a word. We can use the following function. #define MASK(j) (1<<j) int setbit(int w, unsigned j, short value){ if (value == 0) return (w & ~MASK(j)); else if (value == 1) return w MASK(j); else return w; } So to set the bit 4 of w = to 1, we can use w = setbit(w,4,1) The result is w = In this function we introduced a new bit operator, the bitwise OR or Bitwise applies the OR operator to each corresponding bit of the two words x and y. For example =
8 Binary Files Any file can be regarded as a stream of bytes. If the format of the file is understood, like an ASCII file, then we can use functions like fscanf or fprintf to read and write formatted I/O. However, a binary file is regarded just as a string of bytes. So how do we read files that are considered binary files such as a.bmp file? The header file <stdio.h> contains a function fread that can be used to read data from a binary file. The fread and fwrite prototypes are given as follows. NAME fread, fwrite - binary stream input/output SYNOPSIS #include <stdio.h> size_t fread(void *ptr, size_t size, size_t nmemb, FILE *stream); size_t fwrite(const void *ptr, size_t size, size_t nmemb, FILE *stream); DESCRIPTION The function fread reads nmemb elements of data, each size bytes long, from the stream pointed to by stream, storing them at the location given by ptr. The function fwrite writes nmemb elements of data, each size bytes long, to the stream pointed to by stream, obtaining them from the location given by ptr. In order to use the fread function, we need to define an array of bytes, say ptr, and allocate enough memory to hold nitems of size each. All bytes will come from a FILE stream. For example, suppose we would like to read first 54 bytes of image.bmp file. The first 54 bytes hold the header information of the file. FILE* infile = fopen( image.bmp, r ); void* ptr = malloc(54); fread(ptr,54,1,infile); Upon successful completion of the fread function, it returns the number of items read. If a read error occurs or end-of-file encountered, then it returns a number less than nitems. Similarly, the function fwrite can be used to write binary output to an output stream.
9 Bit Fields In implementing something like UNIX file access information, we can use a concept called Bit Fields. Bit fields provide a way to pack integer components into a memory block that is smaller than the size typically required. For example, we can define struct { unsigned leading : 3; unsigned flag1 : 1; unsigned flag2 : 1; trailing : 11; } flags; This packs three fields into 16-bits. The :3 indicates for example, 3 bits are assigned for the leading field. The fields can be accessed by flags.leading = 1; flags.flag1 = 0; etc. However the fields within the struct are not variables and therefore cannot be used with & the address operator. The whole struct cannot be printed using printf, but individual fields can be printed using printf as follows. printf( The leading field is %d \n, flags.leading); We can also print the bit pattern of flags.leading using the getbit function defined as follows. #define MASK(j) (1<<j) int getbit(int w, unsigned j){ return (( w & MASK(j)) == 0)? 0 : 1; } for (i=2;i>=0;i--) printf( %d,getbit(flags.leading,i)); The bit packing is an efficient way to package data so the technique can be used in a device with limited memory or where bandwidth for sending data is limited (eg: Bluetooth). Bit packing is used in maintaining file permission of a file in the unix system as follows. For example access rights to a file can be stored using a structure as follows. struct access { unsigned int o_x : 1; // execute permission for others unsigned int o_w: 1; // write permission for others unsigned int o_r : 1; // read permission for others unsigned int g_x: 1; // execute permission for group unsigned int g_w : 1; // write permission for group unsigned int g_r: 1; // read permission for group
10 unsigned int u_x : 1; // execute permission for owner unsigned int u_w: 1; // write permission for owner unsigned int u_r : 1; // read permission for owner unsigned trailing : 7; // some bits for other fields } access; The 1-bit fields are aligned in the word starting with the lowest order bit. For example to give execute rights to other we can do the following. access.o_x = 1; More Exercises Write a function that prints an unsigned integer in its octal representation (without using %o). Hint: shifting can be used here Write a function that prints an unsigned integer in its hexadecimal representation(without using %x) 17.6 Write a function that multiplies two unsigned short ints using just bit shifting and bit addition. Hint: Any number can be represented as a sum of the powers of two Write a function setbits(w,i,j,value) that sets the bits from i to j (inclusive) to given value (0 or 1). Assume w is an unsigned int (32-bits). Check the ranges to make sure i and j falls within the range Explain how you can use the bit operators to see if a number is a power of Find the sum of 67 + (-32) using bitwise addition Write a function, int countbits(w,value) that counts and returns the bits of w that are set to value. Assume w is a 32-bit unsigned int and value can be 0 or A device controller is a program that communicates with Operating system to make sure it provides correct information about the device to the OS so the operating system can perform the functions required by the device. For example, device variables (or flags) such as device_ready(1-
11 bit),device_spinning(1-bit),device_error(1- bit),write_protected(1-bit), device_sector(5- bits),device_errorcode(8-bits), device_command(5- bits),device_track(8-bits)etc..can use bit fields to pack information about the status of these flags. Describe how you would pack all this information into a 32-bit register. Based on your design, write the functions, setflag(w,flag_type) and getflag(w,flag_type) that returns the value of a flag (ready, sector, errorcode etc) using a mask flag_type needs to be sent over a low bandwidth communication network. Three parameters, flag1, flag2 and flag3 needs to be packed into a struct flagtype. The value ranges for flag1, flag2, and flag3 are 0-7, 0-63, and respectively. Design the smallest possible struct that can hold a record that contains flag1, flag2 and flag Suppose you are to write a function, setflag(unsigned value, unsigned flag) that assigns the value to a specific flag. The flag can be 1, 2, or 3. Your function needs to check the value ranges to make sure the flag values are valid Write a function getflag(unsigned flag, unsigned start, unsigned end), that will print the bit pattern of flag from start to end. Flag is given as 1,2, or 3. You need to check if start and end falls within the limits of the specific flag.
Lecture 13 Bit Operations
 Lecture 13 Bit Operations C is a powerful language as it provides the programmer with many operations for bit manipulation. Data can be accessed at the bit level to make operations more efficient. As you
Lecture 13 Bit Operations C is a powerful language as it provides the programmer with many operations for bit manipulation. Data can be accessed at the bit level to make operations more efficient. As you
Lecture 03 Bits, Bytes and Data Types
 Lecture 03 Bits, Bytes and Data Types Computer Languages A computer language is a language that is used to communicate with a machine. Like all languages, computer languages have syntax (form) and semantics
Lecture 03 Bits, Bytes and Data Types Computer Languages A computer language is a language that is used to communicate with a machine. Like all languages, computer languages have syntax (form) and semantics
CSE 351: The Hardware/Software Interface. Section 2 Integer representations, two s complement, and bitwise operators
 CSE 351: The Hardware/Software Interface Section 2 Integer representations, two s complement, and bitwise operators Integer representations In addition to decimal notation, it s important to be able to
CSE 351: The Hardware/Software Interface Section 2 Integer representations, two s complement, and bitwise operators Integer representations In addition to decimal notation, it s important to be able to
Binary Values. CSE 410 Lecture 02
 Binary Values CSE 410 Lecture 02 Lecture Outline Binary Decimal, Binary, and Hexadecimal Integers Why Place Value Representation Boolean Algebra 2 First: Why Binary? Electronic implementation Easy to store
Binary Values CSE 410 Lecture 02 Lecture Outline Binary Decimal, Binary, and Hexadecimal Integers Why Place Value Representation Boolean Algebra 2 First: Why Binary? Electronic implementation Easy to store
CSE 303 Lecture 18. Bitwise operations. reading: Programming in C Ch. 12. slides created by Marty Stepp
 CSE 33 Lecture 8 Bitwise operations reading: Programming in C Ch. 2 slides created by Marty Stepp http://www.cs.washington.edu/33/ A puzzle... A king wishes to throw a grand party tomorrow in his castle.
CSE 33 Lecture 8 Bitwise operations reading: Programming in C Ch. 2 slides created by Marty Stepp http://www.cs.washington.edu/33/ A puzzle... A king wishes to throw a grand party tomorrow in his castle.
Beginning C Programming for Engineers
 Beginning Programming for Engineers R. Lindsay Todd Lecture 6: Bit Operations R. Lindsay Todd () Beginning Programming for Engineers Beg 6 1 / 32 Outline Outline 1 Place Value Octal Hexadecimal Binary
Beginning Programming for Engineers R. Lindsay Todd Lecture 6: Bit Operations R. Lindsay Todd () Beginning Programming for Engineers Beg 6 1 / 32 Outline Outline 1 Place Value Octal Hexadecimal Binary
CS 253. January 14, 2017
 CS 253 Department of Computer Science College of Engineering Boise State University January 14, 2017 1/30 Motivation Most programming tasks can be implemented using abstractions (e.g. representing data
CS 253 Department of Computer Science College of Engineering Boise State University January 14, 2017 1/30 Motivation Most programming tasks can be implemented using abstractions (e.g. representing data
Goals for this Week. CSC 2400: Computer Systems. Bits, Bytes and Data Types. Binary number system. Finite representations of binary integers
 CSC 2400: Computer Systems Bits, Bytes and Data Types 1 Goals for this Week Binary number system Why binary? Converting between decimal and binary and octal and hexadecimal number systems Finite representations
CSC 2400: Computer Systems Bits, Bytes and Data Types 1 Goals for this Week Binary number system Why binary? Converting between decimal and binary and octal and hexadecimal number systems Finite representations
Expression and Operator
 Expression and Operator Examples: Two types: Expressions and Operators 3 + 5; x; x=0; x=x+1; printf("%d",x); Function calls The expressions formed by data and operators An expression in C usually has a
Expression and Operator Examples: Two types: Expressions and Operators 3 + 5; x; x=0; x=x+1; printf("%d",x); Function calls The expressions formed by data and operators An expression in C usually has a
Computer Organization & Systems Exam I Example Questions
 Computer Organization & Systems Exam I Example Questions 1. Pointer Question. Write a function char *circle(char *str) that receives a character pointer (which points to an array that is in standard C
Computer Organization & Systems Exam I Example Questions 1. Pointer Question. Write a function char *circle(char *str) that receives a character pointer (which points to an array that is in standard C
EE292: Fundamentals of ECE
 EE292: Fundamentals of ECE Fall 2012 TTh 10:00-11:15 SEB 1242 Lecture 22 121115 http://www.ee.unlv.edu/~b1morris/ee292/ 2 Outline Review Binary Number Representation Binary Arithmetic Combinatorial Logic
EE292: Fundamentals of ECE Fall 2012 TTh 10:00-11:15 SEB 1242 Lecture 22 121115 http://www.ee.unlv.edu/~b1morris/ee292/ 2 Outline Review Binary Number Representation Binary Arithmetic Combinatorial Logic
The Design of C: A Rational Reconstruction
 The Design of C: A Rational Reconstruction 1 Goals of this Lecture Help you learn about: The decisions that were available to the designers of C The decisions that were made by the designers of C and thereby
The Design of C: A Rational Reconstruction 1 Goals of this Lecture Help you learn about: The decisions that were available to the designers of C The decisions that were made by the designers of C and thereby
CS 241 Data Organization Binary
 CS 241 Data Organization Binary Brooke Chenoweth University of New Mexico Fall 2017 Combinations and Permutations In English we use the word combination loosely, without thinking if the order of things
CS 241 Data Organization Binary Brooke Chenoweth University of New Mexico Fall 2017 Combinations and Permutations In English we use the word combination loosely, without thinking if the order of things
Arithmetic Operators. Portability: Printing Numbers
 Arithmetic Operators Normal binary arithmetic operators: + - * / Modulus or remainder operator: % x%y is the remainder when x is divided by y well defined only when x > 0 and y > 0 Unary operators: - +
Arithmetic Operators Normal binary arithmetic operators: + - * / Modulus or remainder operator: % x%y is the remainder when x is divided by y well defined only when x > 0 and y > 0 Unary operators: - +
ECE 2020B Fundamentals of Digital Design Spring problems, 6 pages Exam Two Solutions 26 February 2014
 Problem 1 (4 parts, 21 points) Encoders and Pass Gates Part A (8 points) Suppose the circuit below has the following input priority: I 1 > I 3 > I 0 > I 2. Complete the truth table by filling in the input
Problem 1 (4 parts, 21 points) Encoders and Pass Gates Part A (8 points) Suppose the circuit below has the following input priority: I 1 > I 3 > I 0 > I 2. Complete the truth table by filling in the input
Binary Arithmetic CS 64: Computer Organization and Design Logic Lecture #2
 Binary Arithmetic CS 64: Computer Organization and Design Logic Lecture #2 Ziad Matni Dept. of Computer Science, UCSB Adding this Class The class is full I will not be adding more ppl L Even if others
Binary Arithmetic CS 64: Computer Organization and Design Logic Lecture #2 Ziad Matni Dept. of Computer Science, UCSB Adding this Class The class is full I will not be adding more ppl L Even if others
Binary Arithmetic CS 64: Computer Organization and Design Logic Lecture #2 Fall 2018
 Binary Arithmetic CS 64: Computer Organization and Design Logic Lecture #2 Fall 2018 Ziad Matni, Ph.D. Dept. of Computer Science, UCSB Administrative Stuff The class is full I will not be adding more ppl
Binary Arithmetic CS 64: Computer Organization and Design Logic Lecture #2 Fall 2018 Ziad Matni, Ph.D. Dept. of Computer Science, UCSB Administrative Stuff The class is full I will not be adding more ppl
Binary representation of integer numbers Operations on bits
 Outline Binary representation of integer numbers Operations on bits The Bitwise AND Operator The Bitwise Inclusive-OR Operator The Bitwise Exclusive-OR Operator The Ones Complement Operator The Left Shift
Outline Binary representation of integer numbers Operations on bits The Bitwise AND Operator The Bitwise Inclusive-OR Operator The Bitwise Exclusive-OR Operator The Ones Complement Operator The Left Shift
Basic operators, Arithmetic, Relational, Bitwise, Logical, Assignment, Conditional operators. JAVA Standard Edition
 Basic operators, Arithmetic, Relational, Bitwise, Logical, Assignment, Conditional operators JAVA Standard Edition Java - Basic Operators Java provides a rich set of operators to manipulate variables.
Basic operators, Arithmetic, Relational, Bitwise, Logical, Assignment, Conditional operators JAVA Standard Edition Java - Basic Operators Java provides a rich set of operators to manipulate variables.
Intermediate Programming, Spring 2017*
 600.120 Intermediate Programming, Spring 2017* Misha Kazhdan *Much of the code in these examples is not commented because it would otherwise not fit on the slides. This is bad coding practice in general
600.120 Intermediate Programming, Spring 2017* Misha Kazhdan *Much of the code in these examples is not commented because it would otherwise not fit on the slides. This is bad coding practice in general
Few reminders and demos
 15-123 Effective Programming in C and Unix Learning Objectives At the end of this lecture, you should be able to Understand how data is represented Understand how integers are represented Understand how
15-123 Effective Programming in C and Unix Learning Objectives At the end of this lecture, you should be able to Understand how data is represented Understand how integers are represented Understand how
The Design of C: A Rational Reconstruction"
 The Design of C: A Rational Reconstruction 1 Goals of this Lecture Help you learn about: The decisions that were available to the designers of C The decisions that were made by the designers of C and thereby
The Design of C: A Rational Reconstruction 1 Goals of this Lecture Help you learn about: The decisions that were available to the designers of C The decisions that were made by the designers of C and thereby
2.1. Unit 2. Integer Operations (Arithmetic, Overflow, Bitwise Logic, Shifting)
 2.1 Unit 2 Integer Operations (Arithmetic, Overflow, Bitwise Logic, Shifting) 2.2 Skills & Outcomes You should know and be able to apply the following skills with confidence Perform addition & subtraction
2.1 Unit 2 Integer Operations (Arithmetic, Overflow, Bitwise Logic, Shifting) 2.2 Skills & Outcomes You should know and be able to apply the following skills with confidence Perform addition & subtraction
JAVA OPERATORS GENERAL
 JAVA OPERATORS GENERAL Java provides a rich set of operators to manipulate variables. We can divide all the Java operators into the following groups: Arithmetic Operators Relational Operators Bitwise Operators
JAVA OPERATORS GENERAL Java provides a rich set of operators to manipulate variables. We can divide all the Java operators into the following groups: Arithmetic Operators Relational Operators Bitwise Operators
Introduction to Computing Systems Fall Lab # 3
 EE 1301 UMN Introduction to Computing Systems Fall 2013 Lab # 3 Collaboration is encouraged. You may discuss the problems with other students, but you must write up your own solutions, including all your
EE 1301 UMN Introduction to Computing Systems Fall 2013 Lab # 3 Collaboration is encouraged. You may discuss the problems with other students, but you must write up your own solutions, including all your
Advanced C Programming Topics
 Introductory Medical Device Prototyping Advanced C Programming Topics, http://saliterman.umn.edu/ Department of Biomedical Engineering, University of Minnesota Operations on Bits 1. Recall there are 8
Introductory Medical Device Prototyping Advanced C Programming Topics, http://saliterman.umn.edu/ Department of Biomedical Engineering, University of Minnesota Operations on Bits 1. Recall there are 8
Computer Architecture and System Software Lecture 02: Overview of Computer Systems & Start of Chapter 2
 Computer Architecture and System Software Lecture 02: Overview of Computer Systems & Start of Chapter 2 Instructor: Rob Bergen Applied Computer Science University of Winnipeg Announcements Website is up
Computer Architecture and System Software Lecture 02: Overview of Computer Systems & Start of Chapter 2 Instructor: Rob Bergen Applied Computer Science University of Winnipeg Announcements Website is up
UNIX input and output
 UNIX input and output Disk files In UNIX a disk file is a finite sequence of bytes, usually stored on some nonvolatile medium. Disk files have names, which are called paths. We won t discuss file naming
UNIX input and output Disk files In UNIX a disk file is a finite sequence of bytes, usually stored on some nonvolatile medium. Disk files have names, which are called paths. We won t discuss file naming
60-265: Winter ANSWERS Exercise 4 Combinational Circuit Design
 60-265: Winter 2010 Computer Architecture I: Digital Design ANSWERS Exercise 4 Combinational Circuit Design Question 1. One-bit Comparator [ 1 mark ] Consider two 1-bit inputs, A and B. If we assume that
60-265: Winter 2010 Computer Architecture I: Digital Design ANSWERS Exercise 4 Combinational Circuit Design Question 1. One-bit Comparator [ 1 mark ] Consider two 1-bit inputs, A and B. If we assume that
CS240: Programming in C
 CS240: Programming in C Lecture 15: Unix interface: low-level interface Cristina Nita-Rotaru Lecture 15/Fall 2013 1 Streams Recap Higher-level interface, layered on top of the primitive file descriptor
CS240: Programming in C Lecture 15: Unix interface: low-level interface Cristina Nita-Rotaru Lecture 15/Fall 2013 1 Streams Recap Higher-level interface, layered on top of the primitive file descriptor
Bits, Words, and Integers
 Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
ECE 2020B Fundamentals of Digital Design Spring problems, 6 pages Exam Two 26 February 2014
 Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
CSCI 2212: Intermediate Programming / C Chapter 15
 ... /34 CSCI 222: Intermediate Programming / C Chapter 5 Alice E. Fischer October 9 and 2, 25 ... 2/34 Outline Integer Representations Binary Integers Integer Types Bit Operations Applying Bit Operations
... /34 CSCI 222: Intermediate Programming / C Chapter 5 Alice E. Fischer October 9 and 2, 25 ... 2/34 Outline Integer Representations Binary Integers Integer Types Bit Operations Applying Bit Operations
File (1A) Young Won Lim 11/25/16
 File (1A) Copyright (c) 2010-2016 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version
File (1A) Copyright (c) 2010-2016 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version
Under the Hood: Data Representations, Memory and Bit Operations. Computer Science 104 Lecture 3
 Under the Hood: Data Representations, Memory and Bit Operations Computer Science 104 Lecture 3 Homework #1 Due Feb 6 Reading TAs Finish Chapter 1 Start Chapter 2 Admin +1 UTA: Michael Zhou Lindsay is Head
Under the Hood: Data Representations, Memory and Bit Operations Computer Science 104 Lecture 3 Homework #1 Due Feb 6 Reading TAs Finish Chapter 1 Start Chapter 2 Admin +1 UTA: Michael Zhou Lindsay is Head
Effective Programming in C and UNIX Lab 6 Image Manipulation with BMP Images Due Date: Sunday April 3rd, 2011 by 11:59pm
 15-123 Effective Programming in C and UNIX Lab 6 Image Manipulation with BMP Images Due Date: Sunday April 3rd, 2011 by 11:59pm The Assignment Summary: In this assignment we are planning to manipulate
15-123 Effective Programming in C and UNIX Lab 6 Image Manipulation with BMP Images Due Date: Sunday April 3rd, 2011 by 11:59pm The Assignment Summary: In this assignment we are planning to manipulate
25.2 Opening and Closing a File
 Lecture 32 p.1 Faculty of Computer Science, Dalhousie University CSCI 2132 Software Development Lecture 32: Dynamically Allocated Arrays 26-Nov-2018 Location: Chemistry 125 Time: 12:35 13:25 Instructor:
Lecture 32 p.1 Faculty of Computer Science, Dalhousie University CSCI 2132 Software Development Lecture 32: Dynamically Allocated Arrays 26-Nov-2018 Location: Chemistry 125 Time: 12:35 13:25 Instructor:
Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location What to bring:
 ECE 120 Midterm 1 HKN Review Session Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location: Your Room on Compass What to bring: icard, pens/pencils, Cheat sheet (Handwritten) Overview of Review Binary IEEE
ECE 120 Midterm 1 HKN Review Session Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location: Your Room on Compass What to bring: icard, pens/pencils, Cheat sheet (Handwritten) Overview of Review Binary IEEE
Low-Level Programming
 Programming for Electrical and Computer Engineers Low-Level Programming Dr. D. J. Jackson Lecture 15-1 Introduction Previous chapters have described C s high-level, machine-independent features. However,
Programming for Electrical and Computer Engineers Low-Level Programming Dr. D. J. Jackson Lecture 15-1 Introduction Previous chapters have described C s high-level, machine-independent features. However,
CSI 402 Lecture 2 (More on Files) 2 1 / 20
 CSI 402 Lecture 2 (More on Files) 2 1 / 20 Files A Quick Review Type for file variables: FILE * File operations use functions from stdio.h. Functions fopen and fclose for opening and closing files. Functions
CSI 402 Lecture 2 (More on Files) 2 1 / 20 Files A Quick Review Type for file variables: FILE * File operations use functions from stdio.h. Functions fopen and fclose for opening and closing files. Functions
1010 2?= ?= CS 64 Lecture 2 Data Representation. Decimal Numbers: Base 10. Reading: FLD Digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9
 CS 64 Lecture 2 Data Representation Reading: FLD 1.2-1.4 Decimal Numbers: Base 10 Digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9 Example: 3271 = (3x10 3 ) + (2x10 2 ) + (7x10 1 ) + (1x10 0 ) 1010 10?= 1010 2?= 1
CS 64 Lecture 2 Data Representation Reading: FLD 1.2-1.4 Decimal Numbers: Base 10 Digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9 Example: 3271 = (3x10 3 ) + (2x10 2 ) + (7x10 1 ) + (1x10 0 ) 1010 10?= 1010 2?= 1
CSE 410: Systems Programming
 CSE 410: Systems Programming Input and Output Ethan Blanton Department of Computer Science and Engineering University at Buffalo I/O Kernel Services We have seen some text I/O using the C Standard Library.
CSE 410: Systems Programming Input and Output Ethan Blanton Department of Computer Science and Engineering University at Buffalo I/O Kernel Services We have seen some text I/O using the C Standard Library.
The Design of C: A Rational Reconstruction
 The Design of C: A Rational Reconstruction 2 Goals of this Lecture Help you learn about: The decisions that were available to the designers of C The decisions that were made by the designers of C and thereby
The Design of C: A Rational Reconstruction 2 Goals of this Lecture Help you learn about: The decisions that were available to the designers of C The decisions that were made by the designers of C and thereby
Applied Computer Programming
 Applied Computer Programming Representation of Numbers. Bitwise Operators Course 07 Lect.eng. Adriana ALBU, PhD Politehnica University Timisoara Internal representation All data, of any type, processed
Applied Computer Programming Representation of Numbers. Bitwise Operators Course 07 Lect.eng. Adriana ALBU, PhD Politehnica University Timisoara Internal representation All data, of any type, processed
Do not start the test until instructed to do so!
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
COMP2611: Computer Organization. Data Representation
 COMP2611: Computer Organization Comp2611 Fall 2015 2 1. Binary numbers and 2 s Complement Numbers 3 Bits: are the basis for binary number representation in digital computers What you will learn here: How
COMP2611: Computer Organization Comp2611 Fall 2015 2 1. Binary numbers and 2 s Complement Numbers 3 Bits: are the basis for binary number representation in digital computers What you will learn here: How
Slide Set 8. for ENCM 339 Fall 2017 Section 01. Steve Norman, PhD, PEng
 Slide Set 8 for ENCM 339 Fall 2017 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary October 2017 ENCM 339 Fall 2017 Section 01 Slide
Slide Set 8 for ENCM 339 Fall 2017 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary October 2017 ENCM 339 Fall 2017 Section 01 Slide
Computer Architecture
 Computer Architecture Binary data S. Coudert and R. Pacalet January 4, 2018..................... Outline Notations Handling binary data A particular data type: addresses and address space 2/31..........................
Computer Architecture Binary data S. Coudert and R. Pacalet January 4, 2018..................... Outline Notations Handling binary data A particular data type: addresses and address space 2/31..........................
Number System. Introduction. Decimal Numbers
 Number System Introduction Number systems provide the basis for all operations in information processing systems. In a number system the information is divided into a group of symbols; for example, 26
Number System Introduction Number systems provide the basis for all operations in information processing systems. In a number system the information is divided into a group of symbols; for example, 26
Computer Systems Programming. Practice Midterm. Name:
 Computer Systems Programming Practice Midterm Name: 1. (4 pts) (K&R Ch 1-4) What is the output of the following C code? main() { int i = 6; int j = -35; printf( %d %d\n,i++, ++j); i = i >
Computer Systems Programming Practice Midterm Name: 1. (4 pts) (K&R Ch 1-4) What is the output of the following C code? main() { int i = 6; int j = -35; printf( %d %d\n,i++, ++j); i = i >
ECE264 Fall 2013 Exam 3, November 20, 2013
 ECE264 Fall 2013 Exam 3, November 20, 2013 In signing this statement, I hereby certify that the work on this exam is my own and that I have not copied the work of any other student while completing it.
ECE264 Fall 2013 Exam 3, November 20, 2013 In signing this statement, I hereby certify that the work on this exam is my own and that I have not copied the work of any other student while completing it.
BINARY SYSTEM. Binary system is used in digital systems because it is:
 CHAPTER 2 CHAPTER CONTENTS 2.1 Binary System 2.2 Binary Arithmetic Operation 2.3 Signed & Unsigned Numbers 2.4 Arithmetic Operations of Signed Numbers 2.5 Hexadecimal Number System 2.6 Octal Number System
CHAPTER 2 CHAPTER CONTENTS 2.1 Binary System 2.2 Binary Arithmetic Operation 2.3 Signed & Unsigned Numbers 2.4 Arithmetic Operations of Signed Numbers 2.5 Hexadecimal Number System 2.6 Octal Number System
Microcomputers. Outline. Number Systems and Digital Logic Review
 Microcomputers Number Systems and Digital Logic Review Lecture 1-1 Outline Number systems and formats Common number systems Base Conversion Integer representation Signed integer representation Binary coded
Microcomputers Number Systems and Digital Logic Review Lecture 1-1 Outline Number systems and formats Common number systems Base Conversion Integer representation Signed integer representation Binary coded
Lecture 2: Number Systems
 Lecture 2: Number Systems Syed M. Mahmud, Ph.D ECE Department Wayne State University Original Source: Prof. Russell Tessier of University of Massachusetts Aby George of Wayne State University Contents
Lecture 2: Number Systems Syed M. Mahmud, Ph.D ECE Department Wayne State University Original Source: Prof. Russell Tessier of University of Massachusetts Aby George of Wayne State University Contents
More on C programming
 Applied mechatronics More on C programming Sven Gestegård Robertz sven.robertz@cs.lth.se Department of Computer Science, Lund University 2017 Outline 1 Pointers and structs 2 On number representation Hexadecimal
Applied mechatronics More on C programming Sven Gestegård Robertz sven.robertz@cs.lth.se Department of Computer Science, Lund University 2017 Outline 1 Pointers and structs 2 On number representation Hexadecimal
The Design of C: A Rational Reconstruction" Jennifer Rexford!
 The Design of C: A Rational Reconstruction" Jennifer Rexford! 1 Goals of this Lecture"" Number systems! Binary numbers! Finite precision! Binary arithmetic! Logical operators! Design rationale for C! Decisions
The Design of C: A Rational Reconstruction" Jennifer Rexford! 1 Goals of this Lecture"" Number systems! Binary numbers! Finite precision! Binary arithmetic! Logical operators! Design rationale for C! Decisions
2. MACHINE REPRESENTATION OF TYPICAL ARITHMETIC DATA FORMATS (NATURAL AND INTEGER NUMBERS).
 2. MACHINE REPRESENTATION OF TYPICAL ARITHMETIC DATA FORMATS (NATURAL AND INTEGER NUMBERS). 2.. Natural Binary Code (NBC). The positional code with base 2 (B=2), introduced in Exercise, is used to encode
2. MACHINE REPRESENTATION OF TYPICAL ARITHMETIC DATA FORMATS (NATURAL AND INTEGER NUMBERS). 2.. Natural Binary Code (NBC). The positional code with base 2 (B=2), introduced in Exercise, is used to encode
Today s Learning Objectives
 Today s Learning Objectives 15-123 Systems Skills in C and Unix We will Review ints and modular arithmetic Learn basic Data types and Formats How Conditionals and loops work How Arrays are defined, accessed,
Today s Learning Objectives 15-123 Systems Skills in C and Unix We will Review ints and modular arithmetic Learn basic Data types and Formats How Conditionals and loops work How Arrays are defined, accessed,
Binary Adders: Half Adders and Full Adders
 Binary Adders: Half Adders and Full Adders In this set of slides, we present the two basic types of adders: 1. Half adders, and 2. Full adders. Each type of adder functions to add two binary bits. In order
Binary Adders: Half Adders and Full Adders In this set of slides, we present the two basic types of adders: 1. Half adders, and 2. Full adders. Each type of adder functions to add two binary bits. In order
T02 Tutorial Slides for Week 2
 T02 Tutorial Slides for Week 2 ENEL 353: Digital Circuits Fall 2017 Term Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary 19 September, 2017
T02 Tutorial Slides for Week 2 ENEL 353: Digital Circuits Fall 2017 Term Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary 19 September, 2017
Lecture Topics. Announcements. Today: Integer Arithmetic (P&H ) Next: continued. Consulting hours. Introduction to Sim. Milestone #1 (due 1/26)
 Lecture Topics Today: Integer Arithmetic (P&H 3.1-3.4) Next: continued 1 Announcements Consulting hours Introduction to Sim Milestone #1 (due 1/26) 2 1 Overview: Integer Operations Internal representation
Lecture Topics Today: Integer Arithmetic (P&H 3.1-3.4) Next: continued 1 Announcements Consulting hours Introduction to Sim Milestone #1 (due 1/26) 2 1 Overview: Integer Operations Internal representation
UNIT- 3 Introduction to C++
 UNIT- 3 Introduction to C++ C++ Character Sets: Letters A-Z, a-z Digits 0-9 Special Symbols Space + - * / ^ \ ( ) [ ] =!= . $, ; : %! &? _ # = @ White Spaces Blank spaces, horizontal tab, carriage
UNIT- 3 Introduction to C++ C++ Character Sets: Letters A-Z, a-z Digits 0-9 Special Symbols Space + - * / ^ \ ( ) [ ] =!= . $, ; : %! &? _ # = @ White Spaces Blank spaces, horizontal tab, carriage
Chapter 5, Standard I/O. Not UNIX... C standard (library) Why? UNIX programmed in C stdio is very UNIX based
 Chapter 5, Standard I/O Not UNIX... C standard (library) Why? UNIX programmed in C stdio is very UNIX based #include FILE *f; Standard files (FILE *varname) variable: stdin File Number: STDIN_FILENO
Chapter 5, Standard I/O Not UNIX... C standard (library) Why? UNIX programmed in C stdio is very UNIX based #include FILE *f; Standard files (FILE *varname) variable: stdin File Number: STDIN_FILENO
Bits, Bytes and Integers
 Bits, Bytes and Integers Computer Systems Organization (Spring 2016) CSCI-UA 201, Section 2 Instructor: Joanna Klukowska Slides adapted from Randal E. Bryant and David R. O Hallaron (CMU) Mohamed Zahran
Bits, Bytes and Integers Computer Systems Organization (Spring 2016) CSCI-UA 201, Section 2 Instructor: Joanna Klukowska Slides adapted from Randal E. Bryant and David R. O Hallaron (CMU) Mohamed Zahran
Chapter 1 Review of Number Systems
 1.1 Introduction Chapter 1 Review of Number Systems Before the inception of digital computers, the only number system that was in common use is the decimal number system which has a total of 10 digits
1.1 Introduction Chapter 1 Review of Number Systems Before the inception of digital computers, the only number system that was in common use is the decimal number system which has a total of 10 digits
1. NUMBER SYSTEMS USED IN COMPUTING: THE BINARY NUMBER SYSTEM
 1. NUMBER SYSTEMS USED IN COMPUTING: THE BINARY NUMBER SYSTEM 1.1 Introduction Given that digital logic and memory devices are based on two electrical states (on and off), it is natural to use a number
1. NUMBER SYSTEMS USED IN COMPUTING: THE BINARY NUMBER SYSTEM 1.1 Introduction Given that digital logic and memory devices are based on two electrical states (on and off), it is natural to use a number
Lecture 6: Signed Numbers & Arithmetic Circuits. BCD (Binary Coded Decimal) Points Addressed in this Lecture
 Points ddressed in this Lecture Lecture 6: Signed Numbers rithmetic Circuits Professor Peter Cheung Department of EEE, Imperial College London (Floyd 2.5-2.7, 6.1-6.7) (Tocci 6.1-6.11, 9.1-9.2, 9.4) Representing
Points ddressed in this Lecture Lecture 6: Signed Numbers rithmetic Circuits Professor Peter Cheung Department of EEE, Imperial College London (Floyd 2.5-2.7, 6.1-6.7) (Tocci 6.1-6.11, 9.1-9.2, 9.4) Representing
CS33 Project Gear Up. Data
 CS33 Project Gear Up Data Project Overview You will be solving a series of puzzles using your knowledge of data representations. IMPORTANT: Collaboration This project has a different collaboration policy
CS33 Project Gear Up Data Project Overview You will be solving a series of puzzles using your knowledge of data representations. IMPORTANT: Collaboration This project has a different collaboration policy
Bits and Bytes. Bit Operators in C/C++
 Bits and Bytes The byte is generally the smallest item of storage that is directly accessible in modern computers, and symbiotically the byte is the smallest item of storage used by modern programming
Bits and Bytes The byte is generally the smallest item of storage that is directly accessible in modern computers, and symbiotically the byte is the smallest item of storage used by modern programming
CS 326 Operating Systems C Programming. Greg Benson Department of Computer Science University of San Francisco
 CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
EECS2031. Modifiers. Data Types. Lecture 2 Data types. signed (unsigned) int long int long long int int may be omitted sizeof()
 Warning: These notes are not complete, it is a Skelton that will be modified/add-to in the class. If you want to us them for studying, either attend the class or get the completed notes from someone who
Warning: These notes are not complete, it is a Skelton that will be modified/add-to in the class. If you want to us them for studying, either attend the class or get the completed notes from someone who
Unit 2: Data Storage CS 101, Fall 2018
 Unit 2: Data Storage CS 101, Fall 2018 Learning Objectives After completing this unit, you should be able to: Evaluate digital circuits that use AND, OR, XOR, and NOT. Convert binary integers to/from decimal,
Unit 2: Data Storage CS 101, Fall 2018 Learning Objectives After completing this unit, you should be able to: Evaluate digital circuits that use AND, OR, XOR, and NOT. Convert binary integers to/from decimal,
Main Program. C Programming Notes. #include <stdio.h> main() { printf( Hello ); } Comments: /* comment */ //comment. Dr. Karne Towson University
 C Programming Notes Dr. Karne Towson University Reference for C http://www.cplusplus.com/reference/ Main Program #include main() printf( Hello ); Comments: /* comment */ //comment 1 Data Types
C Programming Notes Dr. Karne Towson University Reference for C http://www.cplusplus.com/reference/ Main Program #include main() printf( Hello ); Comments: /* comment */ //comment 1 Data Types
Java provides a rich set of operators to manipulate variables. We can divide all the Java operators into the following groups:
 Basic Operators Java provides a rich set of operators to manipulate variables. We can divide all the Java operators into the following groups: Arithmetic Operators Relational Operators Bitwise Operators
Basic Operators Java provides a rich set of operators to manipulate variables. We can divide all the Java operators into the following groups: Arithmetic Operators Relational Operators Bitwise Operators
BIL 104E Introduction to Scientific and Engineering Computing. Lecture 12
 BIL 104E Introduction to Scientific and Engineering Computing Lecture 12 Files v.s. Streams In C, a file can refer to a disk file, a terminal, a printer, or a tape drive. In other words, a file represents
BIL 104E Introduction to Scientific and Engineering Computing Lecture 12 Files v.s. Streams In C, a file can refer to a disk file, a terminal, a printer, or a tape drive. In other words, a file represents
Writing an ANSI C Program Getting Ready to Program A First Program Variables, Expressions, and Assignments Initialization The Use of #define and
 Writing an ANSI C Program Getting Ready to Program A First Program Variables, Expressions, and Assignments Initialization The Use of #define and #include The Use of printf() and scanf() The Use of printf()
Writing an ANSI C Program Getting Ready to Program A First Program Variables, Expressions, and Assignments Initialization The Use of #define and #include The Use of printf() and scanf() The Use of printf()
Work relative to other classes
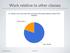 Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
P( Hit 2nd ) = P( Hit 2nd Miss 1st )P( Miss 1st ) = (1/15)(15/16) = 1/16. P( Hit 3rd ) = (1/14) * P( Miss 2nd and 1st ) = (1/14)(14/15)(15/16) = 1/16
 CODING and INFORMATION We need encodings for data. How many questions must be asked to be certain where the ball is. (cases: avg, worst, best) P( Hit 1st ) = 1/16 P( Hit 2nd ) = P( Hit 2nd Miss 1st )P(
CODING and INFORMATION We need encodings for data. How many questions must be asked to be certain where the ball is. (cases: avg, worst, best) P( Hit 1st ) = 1/16 P( Hit 2nd ) = P( Hit 2nd Miss 1st )P(
Introduction to Computers and Programming. Numeric Values
 Introduction to Computers and Programming Prof. I. K. Lundqvist Lecture 5 Reading: B pp. 47-71 Sept 1 003 Numeric Values Storing the value of 5 10 using ASCII: 00110010 00110101 Binary notation: 00000000
Introduction to Computers and Programming Prof. I. K. Lundqvist Lecture 5 Reading: B pp. 47-71 Sept 1 003 Numeric Values Storing the value of 5 10 using ASCII: 00110010 00110101 Binary notation: 00000000
Computer Systems C S Cynthia Lee
 Computer Systems C S 1 0 7 Cynthia Lee 2 Today s Topics LAST TIME: Number representation Integer representation Signed numbers with two s complement THIS TIME: Number representation The integer number
Computer Systems C S 1 0 7 Cynthia Lee 2 Today s Topics LAST TIME: Number representation Integer representation Signed numbers with two s complement THIS TIME: Number representation The integer number
Programming refresher and intro to C programming
 Applied mechatronics Programming refresher and intro to C programming Sven Gestegård Robertz sven.robertz@cs.lth.se Department of Computer Science, Lund University 2018 Outline 1 C programming intro 2
Applied mechatronics Programming refresher and intro to C programming Sven Gestegård Robertz sven.robertz@cs.lth.se Department of Computer Science, Lund University 2018 Outline 1 C programming intro 2
Number representations
 Number representations Number bases Three number bases are of interest: Binary, Octal and Hexadecimal. We look briefly at conversions among them and between each of them and decimal. Binary Base-two, or
Number representations Number bases Three number bases are of interest: Binary, Octal and Hexadecimal. We look briefly at conversions among them and between each of them and decimal. Binary Base-two, or
Data III & Integers I
 Data III & Integers I CSE 351 Spring 2017 Instructor: Ruth Anderson Teaching Assistants: Dylan Johnson Kevin Bi Linxing Preston Jiang Cody Ohlsen Yufang Sun Joshua Curtis Administrivia Everyone has VM
Data III & Integers I CSE 351 Spring 2017 Instructor: Ruth Anderson Teaching Assistants: Dylan Johnson Kevin Bi Linxing Preston Jiang Cody Ohlsen Yufang Sun Joshua Curtis Administrivia Everyone has VM
Number Systems for Computers. Outline of Introduction. Binary, Octal and Hexadecimal numbers. Issues for Binary Representation of Numbers
 Outline of Introduction Administrivia What is computer architecture? What do computers do? Representing high level things in binary Data objects: integers, decimals, characters, etc. Memory locations (We
Outline of Introduction Administrivia What is computer architecture? What do computers do? Representing high level things in binary Data objects: integers, decimals, characters, etc. Memory locations (We
Bits and Bytes. Why bits? Representing information as bits Binary/Hexadecimal Byte representations» numbers» characters and strings» Instructions
 Bits and Bytes Topics Why bits? Representing information as bits Binary/Hexadecimal Byte representations» numbers» characters and strings» Instructions Bit-level manipulations Boolean algebra Expressing
Bits and Bytes Topics Why bits? Representing information as bits Binary/Hexadecimal Byte representations» numbers» characters and strings» Instructions Bit-level manipulations Boolean algebra Expressing
Arithmetic and Bitwise Operations on Binary Data
 Arithmetic and Bitwise Operations on Binary Data CSCI 2400: Computer Architecture ECE 3217: Computer Architecture and Organization Instructor: David Ferry Slides adapted from Bryant & O Hallaron s slides
Arithmetic and Bitwise Operations on Binary Data CSCI 2400: Computer Architecture ECE 3217: Computer Architecture and Organization Instructor: David Ferry Slides adapted from Bryant & O Hallaron s slides
CS113: Lecture 3. Topics: Variables. Data types. Arithmetic and Bitwise Operators. Order of Evaluation
 CS113: Lecture 3 Topics: Variables Data types Arithmetic and Bitwise Operators Order of Evaluation 1 Variables Names of variables: Composed of letters, digits, and the underscore ( ) character. (NO spaces;
CS113: Lecture 3 Topics: Variables Data types Arithmetic and Bitwise Operators Order of Evaluation 1 Variables Names of variables: Composed of letters, digits, and the underscore ( ) character. (NO spaces;
Chapter 2: Number Systems
 Chapter 2: Number Systems Logic circuits are used to generate and transmit 1s and 0s to compute and convey information. This two-valued number system is called binary. As presented earlier, there are many
Chapter 2: Number Systems Logic circuits are used to generate and transmit 1s and 0s to compute and convey information. This two-valued number system is called binary. As presented earlier, there are many
CSC209H Lecture 3. Dan Zingaro. January 21, 2015
 CSC209H Lecture 3 Dan Zingaro January 21, 2015 Streams (King 22.1) Stream: source of input or destination for output We access a stream through a file pointer (FILE *) Three streams are available without
CSC209H Lecture 3 Dan Zingaro January 21, 2015 Streams (King 22.1) Stream: source of input or destination for output We access a stream through a file pointer (FILE *) Three streams are available without
CS 261 Fall Mike Lam, Professor. Structs and I/O
 CS 261 Fall 2018 Mike Lam, Professor Structs and I/O Typedefs A typedef is a way to create a new type name Basically a synonym for another type Useful for shortening long types or providing more meaningful
CS 261 Fall 2018 Mike Lam, Professor Structs and I/O Typedefs A typedef is a way to create a new type name Basically a synonym for another type Useful for shortening long types or providing more meaningful
Embedded Systems - FS 2018
 Institut für Technische Informatik und Kommunikationsnetze Prof. L. Thiele Embedded Systems - FS 2018 Lab 0 Date : 28.2.2018 Prelab Filling the gaps Goals of this Lab You are expected to be already familiar
Institut für Technische Informatik und Kommunikationsnetze Prof. L. Thiele Embedded Systems - FS 2018 Lab 0 Date : 28.2.2018 Prelab Filling the gaps Goals of this Lab You are expected to be already familiar
Integer Representation
 Integer Representation Announcements assign0 due tonight assign1 out tomorrow Labs start this week SCPD Note on ofce hours on Piazza Will get an email tonight about labs Goals for Today Introduction to
Integer Representation Announcements assign0 due tonight assign1 out tomorrow Labs start this week SCPD Note on ofce hours on Piazza Will get an email tonight about labs Goals for Today Introduction to
Inf2C - Computer Systems Lecture 2 Data Representation
 Inf2C - Computer Systems Lecture 2 Data Representation Boris Grot School of Informatics University of Edinburgh Last lecture Moore s law Types of computer systems Computer components Computer system stack
Inf2C - Computer Systems Lecture 2 Data Representation Boris Grot School of Informatics University of Edinburgh Last lecture Moore s law Types of computer systems Computer components Computer system stack
Chapter 4. Operations on Data
 Chapter 4 Operations on Data 1 OBJECTIVES After reading this chapter, the reader should be able to: List the three categories of operations performed on data. Perform unary and binary logic operations
Chapter 4 Operations on Data 1 OBJECTIVES After reading this chapter, the reader should be able to: List the three categories of operations performed on data. Perform unary and binary logic operations
CMSC 313 Fall2009 Midterm Exam 1 Section 01 October 12, 2009
 CMSC 313 Fall2009 Midterm Exam 1 Section 01 October 12, 2009 Name Score UMBC Username Notes: a. Please write clearly. Unreadable answers receive no credit. b. For short answer questions your answer should
CMSC 313 Fall2009 Midterm Exam 1 Section 01 October 12, 2009 Name Score UMBC Username Notes: a. Please write clearly. Unreadable answers receive no credit. b. For short answer questions your answer should
UNIT-V CONSOLE I/O. This section examines in detail the console I/O functions.
 UNIT-V Unit-5 File Streams Formatted I/O Preprocessor Directives Printf Scanf A file represents a sequence of bytes on the disk where a group of related data is stored. File is created for permanent storage
UNIT-V Unit-5 File Streams Formatted I/O Preprocessor Directives Printf Scanf A file represents a sequence of bytes on the disk where a group of related data is stored. File is created for permanent storage
Chapter 3: Operators, Expressions and Type Conversion
 101 Chapter 3 Operators, Expressions and Type Conversion Chapter 3: Operators, Expressions and Type Conversion Objectives To use basic arithmetic operators. To use increment and decrement operators. To
101 Chapter 3 Operators, Expressions and Type Conversion Chapter 3: Operators, Expressions and Type Conversion Objectives To use basic arithmetic operators. To use increment and decrement operators. To
CSci 4061 Introduction to Operating Systems. Input/Output: High-level
 CSci 4061 Introduction to Operating Systems Input/Output: High-level I/O Topics First, cover high-level I/O Next, talk about low-level device I/O I/O not part of the C language! High-level I/O Hide device
CSci 4061 Introduction to Operating Systems Input/Output: High-level I/O Topics First, cover high-level I/O Next, talk about low-level device I/O I/O not part of the C language! High-level I/O Hide device
Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
 Chapter 18 I/O in C Standard C Library I/O commands are not included as part of the C language. Instead, they are part of the Standard C Library. A collection of functions and macros that must be implemented
Chapter 18 I/O in C Standard C Library I/O commands are not included as part of the C language. Instead, they are part of the Standard C Library. A collection of functions and macros that must be implemented
PROGRAMMAZIONE I A.A. 2017/2018
 PROGRAMMAZIONE I A.A. 2017/2018 INPUT/OUTPUT INPUT AND OUTPUT Programs must be able to write data to files or to physical output devices such as displays or printers, and to read in data from files or
PROGRAMMAZIONE I A.A. 2017/2018 INPUT/OUTPUT INPUT AND OUTPUT Programs must be able to write data to files or to physical output devices such as displays or printers, and to read in data from files or
