Software Engineering
|
|
|
- Reynold Melton
- 5 years ago
- Views:
Transcription
1 Software Engineering Lecture 16: Testing and Debugging Debugging Peter Thiemann University of Freiburg, Germany SS 2014
2 Today s Topic This Lecture Execution observation Tracking causes and effects
3 Central Problem How can we observe a program run?
4 Central Problem How can we observe a program run? Challenges/Obstacles Observation of intermediate state not part of functionality Observation can change the behavior Narrowing down to relevant time/state sections
5 The Naive Approach: Print Logging Println Debugging Manually add print statements at code locations to be observed System.out.println("size = "+ size);
6 The Naive Approach: Print Logging Println Debugging Manually add print statements at code locations to be observed System.out.println("size = "+ size); Simple and easy Can use any output channel No tools or infrastructure needed, works on any platform
7 The Naive Approach: Print Logging Println Debugging Manually add print statements at code locations to be observed System.out.println("size = "+ size); Simple and easy Can use any output channel No tools or infrastructure needed, works on any platform Code cluttering Output cluttering (at least need to use debug channel) Performance penalty, possibly changed behavior (timing,... ) Buffered output lost on crash Source code required, recompilation necessary
8 Logging Frameworks Example (Logging Framework for Java) java.util.logging Main principles of Java logging Each class can have its own Logger object Each logger is associated with a level and a handler Levels: FINEST < FINER < FINE < CONFIG < INFO < WARNING < SEVERE Handlers: j.u.l.consolehandler, j.u.l.filehandler Example: log message with mylogger and level INFO: mylogger.info(object message); Logging can be controlled by program or properties file: which logger, level, filter, formatting, handler, etc. No recompilation necessary for reconfiguration
9 Evaluation of Logging Frameworks Output cluttering can be mastered Small performance overhead Exceptions are loggable Log complete up to crash Instrumented source code reconfigurable w/o recompilation Code cluttering don t try to log everything! Code cluttering avoidable with aspects, but also with Debuggers
10 What is a Debugger? Basic Functionality of a Debugger Execution Control Stop execution on specified conditions: breakpoints Interpretation Step-wise execution of code State Inspection Observe value of variables and stack State Change Change state of stopped program Historical term Debugger is misnomer as there are many debugging tools
11 What is a Debugger? Basic Functionality of a Debugger Execution Control Stop execution on specified conditions: breakpoints Interpretation Step-wise execution of code State Inspection Observe value of variables and stack State Change Change state of stopped program Historical term Debugger is misnomer as there are many debugging tools
12 Evaluation of Debuggers Code cluttering completely avoided Prudent usage of breakpoints/watches reduces states to be inspected Full control over all execution aspects Debuggers are interactive tools, re-use and automation difficult Performance can degrade, disable unused watches Inspection of reference types (lists, etc.) is tedious
13 Evaluation of Debuggers Code cluttering completely avoided Prudent usage of breakpoints/watches reduces states to be inspected Full control over all execution aspects Debuggers are interactive tools, re-use and automation difficult Performance can degrade, disable unused watches Inspection of reference types (lists, etc.) is tedious Conclusions Both, logging and debuggers are necessary and complementary Need visualization tools to render complex data structures Minimal/small input, localisation of unit is important
14 Running Example 1 public static int search ( int [] array, 2 int target ) { 3 4 int low = 0; 5 int high = array. length ; 6 int mid ; 7 while ( low <= high ) { 8 mid = ( low + high ) /2; 9 if ( target < array [ mid ] ) { 10 high = mid - 1; 11 } else if ( target > array [ mid ] ) { 12 low = mid + 1; 13 } else { 14 return mid ; 15 } 16 } 17 return -1; 18 }
15 Testing Running a few test cases... search( {1,2}, 1 ) == 0
16 Testing Running a few test cases... search( {1,2}, 1 ) == 0 search( {1,2}, 2 ) == 1
17 Testing Running a few test cases... search( {1,2}, 1 ) == 0 search( {1,2}, 2 ) == 1 search( {1,2}, 4 ) throws ArrayIndexOutOfBoundsException: 3
18 Testing Running a few test cases... search( {1,2}, 1 ) == 0 search( {1,2}, 2 ) == 1 search( {1,2}, 4 ) throws ArrayIndexOutOfBoundsException: 3 Example taken from a published Java text book :-(
19 Tracking Causes and Effects Determine defect that is origin of failure Fundamental problem Program executes forward, but need to reason backwards from failure Example In search() the failure was caused by wrong value mid, but the real culprit was high
20 Effects of Statements Fundamental ways how statements may affect each other Write Change the program state Assign a new value to a variable read by another statement Control Change the program counter Determine which statement is executed next
21 Effects of Statements Fundamental ways how statements may affect each other Write Change the program state Assign a new value to a variable read by another statement Control Change the program counter Determine which statement is executed next Statements with Write Effect (in Java) Assignments I/O, because it affects buffer content new(), because object initialisation writes to fields
22 Effects of Statements Fundamental ways how statements may affect each other Write Change the program state Assign a new value to a variable read by another statement Control Change the program counter Determine which statement is executed next Statements with Control Effect (in Java) Conditionals, switches Loops: determine whether their body is executed Dynamic method calls: implicit case distinction on implementations Abrupt termination statements: break, return Exceptions: potentially at each object or array access!
23 Statement Dependencies Definition (Control Flow Graph (CFG)) The control flow graph of a method M is a directed graph (V, E) where the set V of vertices is the set of program points of M. It contains a designated entry vertex a designated exit vertex corresponding to the return statement a vertex for each primitive statement (e.g., an assignment) a vertex for each condition from an if or while statement the set E of edges contains an edge (v 1, v 2 ) iff v 2 may execute directly after v 1
24 Statement Dependencies CFG Example (potential) execution path = path in CFG
25 Statement Dependencies Definition (Data Dependency) Statement B is data dependent on statement A iff 1. A writes to a variable v that is read by B and 2. There is a path from A to B in the CFG in which v is not written to The outcome of A can directly influence a variable read in B Reaching definitions: the definition of v in A reaches B
26 Statement Dependencies Reaching Definitions Example 1: (x,?) (y,?) (a,?) (b,?) 2: (x,1) (y,?) (a,?) (b,?) 3: (x,1) (x,5) (y,2) (a,?) (a,4) (b,?) 4: (x,1) (x,5) (y,2) (a,?) (a,4) (b,?) 5: (x,1) (x,5) (y,2) (a,4) (b,?) Reaching definitions on entry to the respective node
27 Excursion: Computing Reaching Definitions Instance of static program analysis Given a method by CFG (V, E) Analysis domain: RD = Var ({?} V ) Analysis result: RDin, RDout : V RD Dataflow Equations RDin(entry) = Var {?} For each vertex v V \ {entry}: RDin(v) = (v,v) E RDout(v ) For each vertex v V : RDout(v) = (RDin(v) \ kill(v)) gen(v) kill(v) = {x} ({?} V ) if v = [x := t] kill(v) = otherwise gen(v) = {(x, v)} if v = [x := t] gen(v) = otherwise
28 Excursion: Computing Reaching Definitions Solving data flow equations Initialize For each v V RDin(v) = RDout(v) = Iterate For each v V apply the dataflow equation for RDin apply the dataflow equation for RDout until RDin and RDout do not change anymore Instance of a fixpoint analysis
29 Statement Dependencies Definition (Control Dependency) Statement B is control dependent on statement A iff There is a path from A to B in the CFG such that: For all statements S A on the path, all paths from S to the method exit pass through B and There is a path from A to the method exit that does not pass through B The outcome of A can influence whether B is executed
30 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = ( low + high ) /2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1;
31 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = (low + high)/2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; mid is data-dependent on this statement
32 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = ( low + high ) /2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; mid is control-dependent on the while statement
33 Computing Backward Dependencies Definition (Backward Dependency) Statement B is backward dependent on statement A iff There is a sequence of statements A = A 1, A 2,..., A n = B such that: 1. for all i, A i+1 is control dependent or data dependent on A i 2. there is at least one i with A i+1 being data dependent on A i The outcome of A can influence the program state in B
34 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = ( low + high ) /2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1;
35 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = (low + high)/2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; mid is backward-dependent on data- and control- dependent statement
36 Example 1 int low = 0; 2 int high = array.length; 3 int mid ; 4 while ( low <= high ) { 5 mid = (low + high)/2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; mid is backward-dependent on data- and control- dependent statement
37 Example 1 int low = 0; 2 int high = array.length; 3 int mid ; 4 while ( low <= high ) { 5 mid = (low + high)/2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; Backward-dependent statements for first execution of loop body
38 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = (low + high)/2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; Backward-dependent statements for repeated execution of loop body
39 Systematic Discovery of Defects Program State Time latest state known to be healthy earliest state known to be infected Separate healthy from infected states Separate relevant from irrelevant states
40 Systematic Discovery of Defects Program State Time Defect latest state known to be healthy earliest state known to be infected Separate healthy from infected states Separate relevant from irrelevant states
41 Systematic Discovery of Defects Program State Time Defect latest state known to be healthy earliest state known to be infected Separate healthy from infected states Separate relevant from irrelevant states Compute backward-dependent statements from infected locations
42 Algorithm: Systematic Discovery of Defects Invariant: I is a set of locations (variable set V and statement S) such that each v V is infected after executing S. 1. Initialize I := {infected location reported by failure} 2. Choose and remove an infected location L = (V, S) from I 3. Let C := accumulate a set of candidates 4. For each statement S that may contain origin of defect: S backwards depends on S in one step in execution path 4.1 Let V be the set of variables that is written in S and infected 4.2 If V let C := C {(V, S )} 5. If C (there are infected predecessors): 5.1 Let I := I C 5.2 Goto L depends only on healthy locations, it must be the infection site!
43 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = ( low + high ) /2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; mid is infected, mid==low==high==2
44 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = (low + high)/2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; Look for origins of low and high
45 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = (low + high)/2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; low was changed in previous loop execution, value low==1 seems healthy
46 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = (low + high)/2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; high ==2 set at start (if-branch not taken when target not found), infecte
47 Example 1 int low = 0; 2 int high = array. length ; 3 int mid ; 4 while ( low <= high ) { 5 mid = (low + high)/2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; high does not depend on any other location found infection site!
48 Example 1 int low = 0; 2 int high = array.length - 1 ; 3 int mid ; 4 while ( low <= high ) { 5 mid = ( low + high ) /2; 6 if ( target < array [ mid ] ) { 7 high = mid - 1; 8 } else if ( target > array [ mid ] ) { 9 low = mid + 1; 10 } else { 11 return mid ; 12 } 13 } 14 return -1; Fixed defect
49 After Fixing the Defect Failures that exhibited a defect become new test cases after the fix used for regression testing Use existing unit test cases to test a suspected method in isolation make sure that your bug fix did not introduce new bugs exclude wrong hypotheses about the defect
50 Open Questions 1. How is evaluation of test runs related to specification? So far: wrote oracle program or evaluated interactively How to check automatically whether test outcome conforms to spec? 2. It is tedious to write test cases by hand Easy to forget cases Java: aliasing, run-time exceptions 3. When does a program have no more bugs? How to prove correctness without executing many paths?
51 Literature for this Lecture Essential Zeller Why Programs Fail: A Guide to Systematic Debugging, Morgan Kaufmann, 2005 Chapters 7, 8, 9
Software Engineering
 Software Engineering Lecture 12: Testing and Debugging Debugging Peter Thiemann University of Freiburg, Germany 13.06.2013 Today s Topic Last Lecture Bug tracking Program control Design for Debugging Input
Software Engineering Lecture 12: Testing and Debugging Debugging Peter Thiemann University of Freiburg, Germany 13.06.2013 Today s Topic Last Lecture Bug tracking Program control Design for Debugging Input
Software Engineering Testing and Debugging Debugging
 Software Engineering Testing and Debugging Debugging Prof. Dr. Peter Thiemann Universität Freiburg 13.07.2009 Today s Topic Last Lecture Bug tracking Program control Design for Debugging Input simplification
Software Engineering Testing and Debugging Debugging Prof. Dr. Peter Thiemann Universität Freiburg 13.07.2009 Today s Topic Last Lecture Bug tracking Program control Design for Debugging Input simplification
Today s Topic. Software Engineering Testing and Debugging Debugging. Today s Topic. The Main Steps in Systematic Debugging
 Today s Topic Software Engineering Testing and Debugging Debugging Prof. Dr. Peter Thiemann Last Lecture Bug tracking Program control Design for Debugging Input simplification Universität Freiburg 22.06.2011
Today s Topic Software Engineering Testing and Debugging Debugging Prof. Dr. Peter Thiemann Last Lecture Bug tracking Program control Design for Debugging Input simplification Universität Freiburg 22.06.2011
Testing, Debugging, Program Verification
 Testing, Debugging, Program Verification Debugging Programs, Part II Wolfgang Ahrendt & Vladimir Klebanov & Moa Johansson & Gabriele Paganelli 14 November 2012 TDV: Debugging II /GU 2011-11-09 1 / 32 Today
Testing, Debugging, Program Verification Debugging Programs, Part II Wolfgang Ahrendt & Vladimir Klebanov & Moa Johansson & Gabriele Paganelli 14 November 2012 TDV: Debugging II /GU 2011-11-09 1 / 32 Today
Software Engineering
 Software Engineering Lecture 15: Testing and Debugging Debugging Peter Thiemann University of Freiburg, Germany SS 2014 Motivation Debugging is unavoidable and a major economical factor Software bugs cost
Software Engineering Lecture 15: Testing and Debugging Debugging Peter Thiemann University of Freiburg, Germany SS 2014 Motivation Debugging is unavoidable and a major economical factor Software bugs cost
Softwaretechnik. Lecture 08: Testing and Debugging Overview. Peter Thiemann SS University of Freiburg, Germany
 Softwaretechnik Lecture 08: Testing and Debugging Overview Peter Thiemann University of Freiburg, Germany SS 2012 Literature Essential Reading Why Programs Fail: A Guide to Systematic Debugging, A Zeller
Softwaretechnik Lecture 08: Testing and Debugging Overview Peter Thiemann University of Freiburg, Germany SS 2012 Literature Essential Reading Why Programs Fail: A Guide to Systematic Debugging, A Zeller
Softwaretechnik. Lecture 08: Testing and Debugging Overview. Peter Thiemann SS University of Freiburg, Germany
 Softwaretechnik Lecture 08: Testing and Debugging Overview Peter Thiemann University of Freiburg, Germany SS 2012 Literature Essential Reading Why Programs Fail: A Guide to Systematic Debugging, A Zeller
Softwaretechnik Lecture 08: Testing and Debugging Overview Peter Thiemann University of Freiburg, Germany SS 2012 Literature Essential Reading Why Programs Fail: A Guide to Systematic Debugging, A Zeller
Software Engineering
 Software Engineering Lecture 13: Testing and Debugging Testing Peter Thiemann University of Freiburg, Germany SS 2014 Recap Recap Testing detect the presence of bugs by observing failures Recap Testing
Software Engineering Lecture 13: Testing and Debugging Testing Peter Thiemann University of Freiburg, Germany SS 2014 Recap Recap Testing detect the presence of bugs by observing failures Recap Testing
Software Engineering Testing and Debugging Testing
 Software Engineering Testing and Debugging Testing Prof. Dr. Peter Thiemann Universitt Freiburg 08.06.2011 Recap Testing detect the presence of bugs by observing failures Debugging find the bug causing
Software Engineering Testing and Debugging Testing Prof. Dr. Peter Thiemann Universitt Freiburg 08.06.2011 Recap Testing detect the presence of bugs by observing failures Debugging find the bug causing
CS111: PROGRAMMING LANGUAGE II
 CS111: PROGRAMMING LANGUAGE II Computer Science Department Lecture 1(c): Java Basics (II) Lecture Contents Java basics (part II) Conditions Loops Methods Conditions & Branching Conditional Statements A
CS111: PROGRAMMING LANGUAGE II Computer Science Department Lecture 1(c): Java Basics (II) Lecture Contents Java basics (part II) Conditions Loops Methods Conditions & Branching Conditional Statements A
CSE 374 Programming Concepts & Tools
 CSE 374 Programming Concepts & Tools Hal Perkins Fall 2017 Lecture 11 gdb and Debugging 1 Administrivia HW4 out now, due next Thursday, Oct. 26, 11 pm: C code and libraries. Some tools: gdb (debugger)
CSE 374 Programming Concepts & Tools Hal Perkins Fall 2017 Lecture 11 gdb and Debugging 1 Administrivia HW4 out now, due next Thursday, Oct. 26, 11 pm: C code and libraries. Some tools: gdb (debugger)
A Tutorial for ECE 175
 Debugging in Microsoft Visual Studio 2010 A Tutorial for ECE 175 1. Introduction Debugging refers to the process of discovering defects (bugs) in software and correcting them. This process is invoked when
Debugging in Microsoft Visual Studio 2010 A Tutorial for ECE 175 1. Introduction Debugging refers to the process of discovering defects (bugs) in software and correcting them. This process is invoked when
DEBUGGING: OBSERVING AND TRACKING
 DEBUGGING: OBSERVING AND TRACKING WS 2017/2018 Martina Seidl Institute for Formal Models and Verification Observing a Program deduction tells what might happen observation tells what is actually happening
DEBUGGING: OBSERVING AND TRACKING WS 2017/2018 Martina Seidl Institute for Formal Models and Verification Observing a Program deduction tells what might happen observation tells what is actually happening
Program Analysis. Program Analysis
 Program Analysis Class #4 Program Analysis Dynamic Analysis 1 Static VS Dynamic Analysis Static analysis operates on a model of the SW (without executing it) If successful, produces definitive information
Program Analysis Class #4 Program Analysis Dynamic Analysis 1 Static VS Dynamic Analysis Static analysis operates on a model of the SW (without executing it) If successful, produces definitive information
Automated Adaptive Bug Isolation using Dyninst. Piramanayagam Arumuga Nainar, Prof. Ben Liblit University of Wisconsin-Madison
 Automated Adaptive Bug Isolation using Dyninst Piramanayagam Arumuga Nainar, Prof. Ben Liblit University of Wisconsin-Madison Cooperative Bug Isolation (CBI) ++branch_17[p!= 0]; if (p) else Predicates
Automated Adaptive Bug Isolation using Dyninst Piramanayagam Arumuga Nainar, Prof. Ben Liblit University of Wisconsin-Madison Cooperative Bug Isolation (CBI) ++branch_17[p!= 0]; if (p) else Predicates
First, let s just try to run the program. When we click the button we get the error message shown below:
 VB.NET Debugging Tool Appendix D If a program is not running the way you intend, then you will have to debug the program. Debugging is the process of finding and correcting the errors. There are two general
VB.NET Debugging Tool Appendix D If a program is not running the way you intend, then you will have to debug the program. Debugging is the process of finding and correcting the errors. There are two general
Part 5. Verification and Validation
 Software Engineering Part 5. Verification and Validation - Verification and Validation - Software Testing Ver. 1.7 This lecture note is based on materials from Ian Sommerville 2006. Anyone can use this
Software Engineering Part 5. Verification and Validation - Verification and Validation - Software Testing Ver. 1.7 This lecture note is based on materials from Ian Sommerville 2006. Anyone can use this
Supplement: Visual C++ Debugging
 Supplement: Visual C++ Debugging For Introduction to C++ Programming By Y. Daniel Liang Note: The screen shots are taken from VC++ 2010. It is the same for the later version. 1 Introduction The debugger
Supplement: Visual C++ Debugging For Introduction to C++ Programming By Y. Daniel Liang Note: The screen shots are taken from VC++ 2010. It is the same for the later version. 1 Introduction The debugger
Testing and Debugging
 Testing and Debugging Comp-303 : Programming Techniques Lecture 14 Alexandre Denault Computer Science McGill University Winter 2004 March 1, 2004 Lecture 14 Comp 303 : Testing and Debugging Page 1 Announcements...
Testing and Debugging Comp-303 : Programming Techniques Lecture 14 Alexandre Denault Computer Science McGill University Winter 2004 March 1, 2004 Lecture 14 Comp 303 : Testing and Debugging Page 1 Announcements...
Compiler Construction 2010/2011 Loop Optimizations
 Compiler Construction 2010/2011 Loop Optimizations Peter Thiemann January 25, 2011 Outline 1 Loop Optimizations 2 Dominators 3 Loop-Invariant Computations 4 Induction Variables 5 Array-Bounds Checks 6
Compiler Construction 2010/2011 Loop Optimizations Peter Thiemann January 25, 2011 Outline 1 Loop Optimizations 2 Dominators 3 Loop-Invariant Computations 4 Induction Variables 5 Array-Bounds Checks 6
Regression testing. Whenever you find a bug. Why is this a good idea?
 Regression testing Whenever you find a bug Reproduce it (before you fix it!) Store input that elicited that bug Store correct output Put into test suite Then, fix it and verify the fix Why is this a good
Regression testing Whenever you find a bug Reproduce it (before you fix it!) Store input that elicited that bug Store correct output Put into test suite Then, fix it and verify the fix Why is this a good
CSE 374 Programming Concepts & Tools. Brandon Myers Winter 2015 Lecture 11 gdb and Debugging (Thanks to Hal Perkins)
 CSE 374 Programming Concepts & Tools Brandon Myers Winter 2015 Lecture 11 gdb and Debugging (Thanks to Hal Perkins) Hacker tool of the week (tags) Problem: I want to find the definition of a function or
CSE 374 Programming Concepts & Tools Brandon Myers Winter 2015 Lecture 11 gdb and Debugging (Thanks to Hal Perkins) Hacker tool of the week (tags) Problem: I want to find the definition of a function or
Software Quality. Debugging " Martin Glinz. Chapter 4. Department of Informatics!
 Department of Informatics! Martin Glinz Software Quality Chapter 4 Debugging " 2014 Martin Glinz. All rights reserved. Making digital or hard copies of all or part of this work for educational, non-commercial
Department of Informatics! Martin Glinz Software Quality Chapter 4 Debugging " 2014 Martin Glinz. All rights reserved. Making digital or hard copies of all or part of this work for educational, non-commercial
Compiler Construction 2016/2017 Loop Optimizations
 Compiler Construction 2016/2017 Loop Optimizations Peter Thiemann January 16, 2017 Outline 1 Loops 2 Dominators 3 Loop-Invariant Computations 4 Induction Variables 5 Array-Bounds Checks 6 Loop Unrolling
Compiler Construction 2016/2017 Loop Optimizations Peter Thiemann January 16, 2017 Outline 1 Loops 2 Dominators 3 Loop-Invariant Computations 4 Induction Variables 5 Array-Bounds Checks 6 Loop Unrolling
Flow of Control: Loops
 Walter Savitch Frank M. Carrano Flow of Control: Loops Chapter 4 Java Loop Statements: Outline The while statement The do-while statement The for Statement Java Loop Statements A portion of a program that
Walter Savitch Frank M. Carrano Flow of Control: Loops Chapter 4 Java Loop Statements: Outline The while statement The do-while statement The for Statement Java Loop Statements A portion of a program that
Compiler Design Spring 2017
 Compiler Design Spring 2017 8.0 Data-Flow Analysis Dr. Zoltán Majó Compiler Group Java HotSpot Virtual Machine Oracle Corporation Admin issues There will be a code review session next week On Thursday
Compiler Design Spring 2017 8.0 Data-Flow Analysis Dr. Zoltán Majó Compiler Group Java HotSpot Virtual Machine Oracle Corporation Admin issues There will be a code review session next week On Thursday
Objectives. Chapter 19. Verification vs. validation. Topics covered. Static and dynamic verification. The V&V process
 Objectives Chapter 19 Verification and Validation Assuring that a software system meets a user s need are to introduce software verification and validation (V&V) and to discuss the distinction between
Objectives Chapter 19 Verification and Validation Assuring that a software system meets a user s need are to introduce software verification and validation (V&V) and to discuss the distinction between
Testing. ECE/CS 5780/6780: Embedded System Design. Why is testing so hard? Why do testing?
 Testing ECE/CS 5780/6780: Embedded System Design Scott R. Little Lecture 24: Introduction to Software Testing and Verification What is software testing? Running a program in order to find bugs (faults,
Testing ECE/CS 5780/6780: Embedded System Design Scott R. Little Lecture 24: Introduction to Software Testing and Verification What is software testing? Running a program in order to find bugs (faults,
Understanding the Program Run
 0/45 Understanding the Program Run Andreas Zeller Lehrstuhl Softwaretechnik Universität des Saarlandes, Saarbrücken Isolating Failure Causes 1/45 So far, we have seen how to isolate causes in the environment
0/45 Understanding the Program Run Andreas Zeller Lehrstuhl Softwaretechnik Universität des Saarlandes, Saarbrücken Isolating Failure Causes 1/45 So far, we have seen how to isolate causes in the environment
Fault, Error, and Failure
 Fault, Error, and Failure Testing, Quality Assurance, and Maintenance Winter 2018 Prof. Arie Gurfinkel based on slides by Prof. Lin Tan and others Terminology, IEEE 610.12-1990 Fault -- often referred
Fault, Error, and Failure Testing, Quality Assurance, and Maintenance Winter 2018 Prof. Arie Gurfinkel based on slides by Prof. Lin Tan and others Terminology, IEEE 610.12-1990 Fault -- often referred
Programming Studio #9 ECE 190
 Programming Studio #9 ECE 190 Programming Studio #9 Concepts: Functions review 2D Arrays GDB Announcements EXAM 3 CONFLICT REQUESTS, ON COMPASS, DUE THIS MONDAY 5PM. NO EXTENSIONS, NO EXCEPTIONS. Functions
Programming Studio #9 ECE 190 Programming Studio #9 Concepts: Functions review 2D Arrays GDB Announcements EXAM 3 CONFLICT REQUESTS, ON COMPASS, DUE THIS MONDAY 5PM. NO EXTENSIONS, NO EXCEPTIONS. Functions
The NetBeans IDE is a big file --- a minimum of around 30 MB. After you have downloaded the file, simply execute the file to install the software.
 Introduction to Netbeans This document is a brief introduction to writing and compiling a program using the NetBeans Integrated Development Environment (IDE). An IDE is a program that automates and makes
Introduction to Netbeans This document is a brief introduction to writing and compiling a program using the NetBeans Integrated Development Environment (IDE). An IDE is a program that automates and makes
Copyright Khronos Group, Page Graphic Remedy. All Rights Reserved
 Avi Shapira Graphic Remedy Copyright Khronos Group, 2009 - Page 1 2004 2009 Graphic Remedy. All Rights Reserved Debugging and profiling 3D applications are both hard and time consuming tasks Companies
Avi Shapira Graphic Remedy Copyright Khronos Group, 2009 - Page 1 2004 2009 Graphic Remedy. All Rights Reserved Debugging and profiling 3D applications are both hard and time consuming tasks Companies
Compiler Optimisation
 Compiler Optimisation 3 Dataflow Analysis Hugh Leather IF 1.18a hleather@inf.ed.ac.uk Institute for Computing Systems Architecture School of Informatics University of Edinburgh 2018 Introduction Optimisations
Compiler Optimisation 3 Dataflow Analysis Hugh Leather IF 1.18a hleather@inf.ed.ac.uk Institute for Computing Systems Architecture School of Informatics University of Edinburgh 2018 Introduction Optimisations
DySy: Dynamic Symbolic Execution for Invariant Inference
 DySy: Dynamic Symbolic Execution for Invariant Inference C. Csallner N. Tillmann Y. Smaragdakis Marc Egg Invariant Inference Object top() { if(empty) return null; return thearray[topofstack]; Invariant
DySy: Dynamic Symbolic Execution for Invariant Inference C. Csallner N. Tillmann Y. Smaragdakis Marc Egg Invariant Inference Object top() { if(empty) return null; return thearray[topofstack]; Invariant
Compiler Construction 2009/2010 SSA Static Single Assignment Form
 Compiler Construction 2009/2010 SSA Static Single Assignment Form Peter Thiemann March 15, 2010 Outline 1 Static Single-Assignment Form 2 Converting to SSA Form 3 Optimization Algorithms Using SSA 4 Dependencies
Compiler Construction 2009/2010 SSA Static Single Assignment Form Peter Thiemann March 15, 2010 Outline 1 Static Single-Assignment Form 2 Converting to SSA Form 3 Optimization Algorithms Using SSA 4 Dependencies
We first learn one useful option of gcc. Copy the following C source file to your
 Lecture 5 p.1 Faculty of Computer Science, Dalhousie University CSCI 2132 Software Development Lab 5: gcc and gdb tools 10-Oct-2018 Location: Teaching Labs Time: Thursday Instructor: Vlado Keselj Lab 5:
Lecture 5 p.1 Faculty of Computer Science, Dalhousie University CSCI 2132 Software Development Lab 5: gcc and gdb tools 10-Oct-2018 Location: Teaching Labs Time: Thursday Instructor: Vlado Keselj Lab 5:
Verification and Validation. Assuring that a software system meets a user s needs. Verification vs Validation. The V & V Process
 Verification and Validation Assuring that a software system meets a user s needs Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapters 19,20 Slide 1
Verification and Validation Assuring that a software system meets a user s needs Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapters 19,20 Slide 1
Recap: Pointers. int* int& *p &i &*&* ** * * * * IFMP 18, M. Schwerhoff
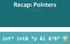 Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
Lab 8 - Vectors, and Debugging. Directions
 Lab 8 - Vectors, and Debugging. Directions The labs are marked based on attendance and effort. It is your responsibility to ensure the TA records your progress by the end of the lab. While completing these
Lab 8 - Vectors, and Debugging. Directions The labs are marked based on attendance and effort. It is your responsibility to ensure the TA records your progress by the end of the lab. While completing these
Debugging HPC Applications. David Lecomber CTO, Allinea Software
 Debugging HPC Applications David Lecomber CTO, Allinea Software david@allinea.com Agenda Bugs and Debugging Debugging parallel applications Debugging OpenACC and other hybrid codes Debugging for Petascale
Debugging HPC Applications David Lecomber CTO, Allinea Software david@allinea.com Agenda Bugs and Debugging Debugging parallel applications Debugging OpenACC and other hybrid codes Debugging for Petascale
CS553 Lecture Dynamic Optimizations 2
 Dynamic Optimizations Last time Predication and speculation Today Dynamic compilation CS553 Lecture Dynamic Optimizations 2 Motivation Limitations of static analysis Programs can have values and invariants
Dynamic Optimizations Last time Predication and speculation Today Dynamic compilation CS553 Lecture Dynamic Optimizations 2 Motivation Limitations of static analysis Programs can have values and invariants
Object Oriented Programming
 Object Oriented Programming Java lecture (10.1) Exception Handling 1 Outline Exception Handling Mechanisms Exception handling fundamentals Exception Types Uncaught exceptions Try and catch Multiple catch
Object Oriented Programming Java lecture (10.1) Exception Handling 1 Outline Exception Handling Mechanisms Exception handling fundamentals Exception Types Uncaught exceptions Try and catch Multiple catch
CSC Java Programming, Fall Java Data Types and Control Constructs
 CSC 243 - Java Programming, Fall 2016 Java Data Types and Control Constructs Java Types In general, a type is collection of possible values Main categories of Java types: Primitive/built-in Object/Reference
CSC 243 - Java Programming, Fall 2016 Java Data Types and Control Constructs Java Types In general, a type is collection of possible values Main categories of Java types: Primitive/built-in Object/Reference
Lecture 6 Binary Search
 Lecture 6 Binary Search 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning One of the fundamental and recurring problems in computer science is to find elements in collections, such
Lecture 6 Binary Search 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning One of the fundamental and recurring problems in computer science is to find elements in collections, such
Guidelines for Writing C Code
 Guidelines for Writing C Code Issue 01-bugfix Martin Becker Institute for Real-Time Computer Systems (RCS) Technische Universität München becker@rcs.ei.tum.de June 9, 2014 Contents 1 Introduction 1 2 Pragmatic
Guidelines for Writing C Code Issue 01-bugfix Martin Becker Institute for Real-Time Computer Systems (RCS) Technische Universität München becker@rcs.ei.tum.de June 9, 2014 Contents 1 Introduction 1 2 Pragmatic
An Introduction to Systematic Software Testing. Robert France CSU
 An Introduction to Systematic Software Testing Robert France CSU Why do we need to systematically test software? Poor quality products can Inconvenience direct and indirect users Result in severe financial
An Introduction to Systematic Software Testing Robert France CSU Why do we need to systematically test software? Poor quality products can Inconvenience direct and indirect users Result in severe financial
Faults, Errors, Failures
 Faults, Errors, Failures CS 4501 / 6501 Software Testing [Ammann and Offutt, Introduction to Software Testing ] 1 Software Testing Review Testing = process of finding input values to check against a software
Faults, Errors, Failures CS 4501 / 6501 Software Testing [Ammann and Offutt, Introduction to Software Testing ] 1 Software Testing Review Testing = process of finding input values to check against a software
Changing the Embedded World TM. Module 3: Getting Started Debugging
 Changing the Embedded World TM Module 3: Getting Started Debugging Module Objectives: Section 1: Introduce Debugging Techniques Section 2: PSoC In-Circuit Emulator (ICE) Section 3: Hands on Debugging a
Changing the Embedded World TM Module 3: Getting Started Debugging Module Objectives: Section 1: Introduce Debugging Techniques Section 2: PSoC In-Circuit Emulator (ICE) Section 3: Hands on Debugging a
Advanced Compiler Construction
 CS 526 Advanced Compiler Construction http://misailo.cs.illinois.edu/courses/cs526 INTERPROCEDURAL ANALYSIS The slides adapted from Vikram Adve So Far Control Flow Analysis Data Flow Analysis Dependence
CS 526 Advanced Compiler Construction http://misailo.cs.illinois.edu/courses/cs526 INTERPROCEDURAL ANALYSIS The slides adapted from Vikram Adve So Far Control Flow Analysis Data Flow Analysis Dependence
QUIZ Friends class Y;
 QUIZ Friends class Y; Is a forward declaration neeed here? QUIZ Friends QUIZ Friends - CONCLUSION Forward (a.k.a. incomplete) declarations are needed only when we declare member functions as friends. They
QUIZ Friends class Y; Is a forward declaration neeed here? QUIZ Friends QUIZ Friends - CONCLUSION Forward (a.k.a. incomplete) declarations are needed only when we declare member functions as friends. They
Isolating and Locating Cause-Effect Chains. bug.c. What is the cause of this failure? What do we do now? Andreas Zeller
 Isolating and Locating Cause-Effect Chains Andreas Zeller 1 bug.c double bug(double z[], int n) { int i, j; } i = 0; for (j = 0; j < n; j++) { i = i + j + 1; z[i] = z[i] * (z[0] + 1.0); } return z[n];
Isolating and Locating Cause-Effect Chains Andreas Zeller 1 bug.c double bug(double z[], int n) { int i, j; } i = 0; for (j = 0; j < n; j++) { i = i + j + 1; z[i] = z[i] * (z[0] + 1.0); } return z[n];
Program Design: Using the Debugger
 rogram Design, February 2, 2004 1 Program Design: Using the Debugger A debugger is an alternative to putting print (printf in C) statements in your program, recompiling and trying to find out what values
rogram Design, February 2, 2004 1 Program Design: Using the Debugger A debugger is an alternative to putting print (printf in C) statements in your program, recompiling and trying to find out what values
Announcements. Lab Friday, 1-2:30 and 3-4:30 in Boot your laptop and start Forte, if you brought your laptop
 Announcements Lab Friday, 1-2:30 and 3-4:30 in 26-152 Boot your laptop and start Forte, if you brought your laptop Create an empty file called Lecture4 and create an empty main() method in a class: 1.00
Announcements Lab Friday, 1-2:30 and 3-4:30 in 26-152 Boot your laptop and start Forte, if you brought your laptop Create an empty file called Lecture4 and create an empty main() method in a class: 1.00
Assertions. Assertions - Example
 References: internet notes; Bertrand Meyer, Object-Oriented Software Construction; 11/13/2003 1 Assertions Statements about input to a routine or state of a class Have two primary roles As documentation,
References: internet notes; Bertrand Meyer, Object-Oriented Software Construction; 11/13/2003 1 Assertions Statements about input to a routine or state of a class Have two primary roles As documentation,
Lab 5 : WordAnalyzer class
 Lab 5 : WordAnalyzer class Introduction READ THE INSTRUCTIONS FIRST! The WordAnalyzer class was written to perform a few different analyses of words: - identify the first repeated (adjacent) character
Lab 5 : WordAnalyzer class Introduction READ THE INSTRUCTIONS FIRST! The WordAnalyzer class was written to perform a few different analyses of words: - identify the first repeated (adjacent) character
Replaying and Isolating Failing Multi-Object Interactions. Martin Burger Andreas Zeller Saarland University
 Replaying and Isolating Failing Multi-Object Interactions Martin Burger Andreas Zeller Saarland University e-mail client written in Java 100,200 LOC ~ 1,600 Java classes 17 developers Actively developed
Replaying and Isolating Failing Multi-Object Interactions Martin Burger Andreas Zeller Saarland University e-mail client written in Java 100,200 LOC ~ 1,600 Java classes 17 developers Actively developed
Lecture 3 Local Optimizations, Intro to SSA
 Lecture 3 Local Optimizations, Intro to SSA I. Basic blocks & Flow graphs II. Abstraction 1: DAG III. Abstraction 2: Value numbering IV. Intro to SSA ALSU 8.4-8.5, 6.2.4 Phillip B. Gibbons 15-745: Local
Lecture 3 Local Optimizations, Intro to SSA I. Basic blocks & Flow graphs II. Abstraction 1: DAG III. Abstraction 2: Value numbering IV. Intro to SSA ALSU 8.4-8.5, 6.2.4 Phillip B. Gibbons 15-745: Local
G Programming Languages - Fall 2012
 G22.2110-003 Programming Languages - Fall 2012 Lecture 3 Thomas Wies New York University Review Last week Names and Bindings Lifetimes and Allocation Garbage Collection Scope Outline Control Flow Sequencing
G22.2110-003 Programming Languages - Fall 2012 Lecture 3 Thomas Wies New York University Review Last week Names and Bindings Lifetimes and Allocation Garbage Collection Scope Outline Control Flow Sequencing
printf Debugging Examples
 Programming Soap Box Developer Tools Tim Purcell NVIDIA Successful programming systems require at least three tools High level language compiler Cg, HLSL, GLSL, RTSL, Brook Debugger Profiler Debugging
Programming Soap Box Developer Tools Tim Purcell NVIDIA Successful programming systems require at least three tools High level language compiler Cg, HLSL, GLSL, RTSL, Brook Debugger Profiler Debugging
Laboratory 5: Implementing Loops and Loop Control Strategies
 Laboratory 5: Implementing Loops and Loop Control Strategies Overview: Objectives: C++ has three control structures that are designed exclusively for iteration: the while, for and do statements. In today's
Laboratory 5: Implementing Loops and Loop Control Strategies Overview: Objectives: C++ has three control structures that are designed exclusively for iteration: the while, for and do statements. In today's
CSE 501: Compiler Construction. Course outline. Goals for language implementation. Why study compilers? Models of compilation
 CSE 501: Compiler Construction Course outline Main focus: program analysis and transformation how to represent programs? how to analyze programs? what to analyze? how to transform programs? what transformations
CSE 501: Compiler Construction Course outline Main focus: program analysis and transformation how to represent programs? how to analyze programs? what to analyze? how to transform programs? what transformations
hw6, BFS, debugging CSE 331 Section 5 10/25/12 Slides by Kellen Donohue
 hw6, BFS, debugging CSE 331 Section 5 10/25/12 Slides by Kellen Donohue Agenda hw4 being graded hw5 may be graded first, for feedback to be used on hw6 hw6 due next week Today hw6 BFS Debugging hashcode()
hw6, BFS, debugging CSE 331 Section 5 10/25/12 Slides by Kellen Donohue Agenda hw4 being graded hw5 may be graded first, for feedback to be used on hw6 hw6 due next week Today hw6 BFS Debugging hashcode()
Repetition Structures
 Repetition Structures Chapter 5 Fall 2016, CSUS Introduction to Repetition Structures Chapter 5.1 1 Introduction to Repetition Structures A repetition structure causes a statement or set of statements
Repetition Structures Chapter 5 Fall 2016, CSUS Introduction to Repetition Structures Chapter 5.1 1 Introduction to Repetition Structures A repetition structure causes a statement or set of statements
Steps for project success. git status. Milestones. Deliverables. Homework 1 submitted Homework 2 will be posted October 26.
 git status Steps for project success Homework 1 submitted Homework 2 will be posted October 26 due November 16, 9AM Projects underway project status check-in meetings November 9 System-building project
git status Steps for project success Homework 1 submitted Homework 2 will be posted October 26 due November 16, 9AM Projects underway project status check-in meetings November 9 System-building project
UNIT 3
 UNIT 3 Presentation Outline Sequence control with expressions Conditional Statements, Loops Exception Handling Subprogram definition and activation Simple and Recursive Subprogram Subprogram Environment
UNIT 3 Presentation Outline Sequence control with expressions Conditional Statements, Loops Exception Handling Subprogram definition and activation Simple and Recursive Subprogram Subprogram Environment
Condition-Controlled Loop. Condition-Controlled Loop. If Statement. Various Forms. Conditional-Controlled Loop. Loop Caution.
 Repetition Structures Introduction to Repetition Structures Chapter 5 Spring 2016, CSUS Chapter 5.1 Introduction to Repetition Structures The Problems with Duplicate Code A repetition structure causes
Repetition Structures Introduction to Repetition Structures Chapter 5 Spring 2016, CSUS Chapter 5.1 Introduction to Repetition Structures The Problems with Duplicate Code A repetition structure causes
Outline. Computer programming. Debugging. What is it. Debugging. Hints. Debugging
 Outline Computer programming Debugging Hints Gathering evidence Common C errors "Education is a progressive discovery of our own ignorance." Will Durant T.U. Cluj-Napoca - Computer Programming - lecture
Outline Computer programming Debugging Hints Gathering evidence Common C errors "Education is a progressive discovery of our own ignorance." Will Durant T.U. Cluj-Napoca - Computer Programming - lecture
Softwaretechnik. Lecture 03: Types and Type Soundness. Peter Thiemann. University of Freiburg, Germany SS 2008
 Softwaretechnik Lecture 03: Types and Type Soundness Peter Thiemann University of Freiburg, Germany SS 2008 Peter Thiemann (Univ. Freiburg) Softwaretechnik SWT 1 / 35 Table of Contents Types and Type correctness
Softwaretechnik Lecture 03: Types and Type Soundness Peter Thiemann University of Freiburg, Germany SS 2008 Peter Thiemann (Univ. Freiburg) Softwaretechnik SWT 1 / 35 Table of Contents Types and Type correctness
Topic I (d): Static Single Assignment Form (SSA)
 Topic I (d): Static Single Assignment Form (SSA) 621-10F/Topic-1d-SSA 1 Reading List Slides: Topic Ix Other readings as assigned in class 621-10F/Topic-1d-SSA 2 ABET Outcome Ability to apply knowledge
Topic I (d): Static Single Assignment Form (SSA) 621-10F/Topic-1d-SSA 1 Reading List Slides: Topic Ix Other readings as assigned in class 621-10F/Topic-1d-SSA 2 ABET Outcome Ability to apply knowledge
An Overview of ABAP Debugger Settings and System Areas
 An Overview of ABAP Debugger Settings and System Areas An Overview of ABAP Debugger Settings and System Areas Authro The ABAP Debugger contains a wealth of settings and information about your ABAP environment
An Overview of ABAP Debugger Settings and System Areas An Overview of ABAP Debugger Settings and System Areas Authro The ABAP Debugger contains a wealth of settings and information about your ABAP environment
GDB Tutorial. A Walkthrough with Examples. CMSC Spring Last modified March 22, GDB Tutorial
 A Walkthrough with Examples CMSC 212 - Spring 2009 Last modified March 22, 2009 What is gdb? GNU Debugger A debugger for several languages, including C and C++ It allows you to inspect what the program
A Walkthrough with Examples CMSC 212 - Spring 2009 Last modified March 22, 2009 What is gdb? GNU Debugger A debugger for several languages, including C and C++ It allows you to inspect what the program
Preventing and Finding Bugs in Parallel Programs
 Preventing and Finding Bugs in Parallel Programs Charlie Peck Earlham College BW/UPEP Institute @ NCSA May, 2011 1 How Did We Get Here? Debugging serial programs can be hard; debugging parallel programs
Preventing and Finding Bugs in Parallel Programs Charlie Peck Earlham College BW/UPEP Institute @ NCSA May, 2011 1 How Did We Get Here? Debugging serial programs can be hard; debugging parallel programs
Jlint status of version 3.0
 Jlint status of version 3.0 Raphael Ackermann raphy@student.ethz.ch June 9, 2004 1 Contents 1 Introduction 3 2 Test Framework 3 3 Adding New Test Cases 6 4 Found Errors, Bug Fixes 6 4.1 try catch finally
Jlint status of version 3.0 Raphael Ackermann raphy@student.ethz.ch June 9, 2004 1 Contents 1 Introduction 3 2 Test Framework 3 3 Adding New Test Cases 6 4 Found Errors, Bug Fixes 6 4.1 try catch finally
CS 314 Principles of Programming Languages. Lecture 9
 CS 314 Principles of Programming Languages Lecture 9 Zheng Zhang Department of Computer Science Rutgers University Wednesday 5 th October, 2016 Zheng Zhang 1 CS@Rutgers University Class Information Homework
CS 314 Principles of Programming Languages Lecture 9 Zheng Zhang Department of Computer Science Rutgers University Wednesday 5 th October, 2016 Zheng Zhang 1 CS@Rutgers University Class Information Homework
Statistical Debugging Benjamin Robert Liblit. Cooperative Bug Isolation. PhD Dissertation, University of California, Berkeley, 2004.
 Statistical Debugging Benjamin Robert Liblit. Cooperative Bug Isolation. PhD Dissertation, University of California, Berkeley, 2004. ACM Dissertation Award (2005) Thomas D. LaToza 17-654 Analysis of Software
Statistical Debugging Benjamin Robert Liblit. Cooperative Bug Isolation. PhD Dissertation, University of California, Berkeley, 2004. ACM Dissertation Award (2005) Thomas D. LaToza 17-654 Analysis of Software
Verification and Validation
 Lecturer: Sebastian Coope Ashton Building, Room G.18 E-mail: coopes@liverpool.ac.uk COMP 201 web-page: http://www.csc.liv.ac.uk/~coopes/comp201 Verification and Validation 1 Verification and Validation
Lecturer: Sebastian Coope Ashton Building, Room G.18 E-mail: coopes@liverpool.ac.uk COMP 201 web-page: http://www.csc.liv.ac.uk/~coopes/comp201 Verification and Validation 1 Verification and Validation
In this Lecture you will Learn: Testing in Software Development Process. What is Software Testing. Static Testing vs.
 In this Lecture you will Learn: Testing in Software Development Process Examine the verification and validation activities in software development process stage by stage Introduce some basic concepts of
In this Lecture you will Learn: Testing in Software Development Process Examine the verification and validation activities in software development process stage by stage Introduce some basic concepts of
Benefits of object-orientationorientation
 ITEC 136 Business Programming Concepts Week 14, Part 01 Overview 1 Week 14 Overview Week 13 review What is an object? (three parts) State (properties) Identity (location in memory) Behavior (methods) 2
ITEC 136 Business Programming Concepts Week 14, Part 01 Overview 1 Week 14 Overview Week 13 review What is an object? (three parts) State (properties) Identity (location in memory) Behavior (methods) 2
Debugging. ICS312 Machine-Level and Systems Programming. Henri Casanova
 Debugging ICS312 Machine-Level and Systems Programming Henri Casanova (henric@hawaii.edu) Debugging Even when written in high-level languages, programs have bugs Recall the thought that when moving away
Debugging ICS312 Machine-Level and Systems Programming Henri Casanova (henric@hawaii.edu) Debugging Even when written in high-level languages, programs have bugs Recall the thought that when moving away
JCreator. Starting JCreator
 1 of 12 9/29/2005 2:31 PM JCreator JCreator is a commercial Java environment available from http://www.jcreator.com. Inexpensive academic licenses and a free "limited edition" are available. JCreator runs
1 of 12 9/29/2005 2:31 PM JCreator JCreator is a commercial Java environment available from http://www.jcreator.com. Inexpensive academic licenses and a free "limited edition" are available. JCreator runs
Lecture Compiler Middle-End
 Lecture 16-18 18 Compiler Middle-End Jianwen Zhu Electrical and Computer Engineering University of Toronto Jianwen Zhu 2009 - P. 1 What We Have Done A lot! Compiler Frontend Defining language Generating
Lecture 16-18 18 Compiler Middle-End Jianwen Zhu Electrical and Computer Engineering University of Toronto Jianwen Zhu 2009 - P. 1 What We Have Done A lot! Compiler Frontend Defining language Generating
Profile-Guided Program Simplification for Effective Testing and Analysis
 Profile-Guided Program Simplification for Effective Testing and Analysis Lingxiao Jiang Zhendong Su Program Execution Profiles A profile is a set of information about an execution, either succeeded or
Profile-Guided Program Simplification for Effective Testing and Analysis Lingxiao Jiang Zhendong Su Program Execution Profiles A profile is a set of information about an execution, either succeeded or
More Dataflow Analysis
 More Dataflow Analysis Steps to building analysis Step 1: Choose lattice Step 2: Choose direction of dataflow (forward or backward) Step 3: Create transfer function Step 4: Choose confluence operator (i.e.,
More Dataflow Analysis Steps to building analysis Step 1: Choose lattice Step 2: Choose direction of dataflow (forward or backward) Step 3: Create transfer function Step 4: Choose confluence operator (i.e.,
Run-time Environments. Lecture 13. Prof. Alex Aiken Original Slides (Modified by Prof. Vijay Ganesh) Lecture 13
 Run-time Environments Lecture 13 by Prof. Vijay Ganesh) Lecture 13 1 What have we covered so far? We have covered the front-end phases Lexical analysis (Lexer, regular expressions,...) Parsing (CFG, Top-down,
Run-time Environments Lecture 13 by Prof. Vijay Ganesh) Lecture 13 1 What have we covered so far? We have covered the front-end phases Lexical analysis (Lexer, regular expressions,...) Parsing (CFG, Top-down,
Flow of Control: Loops. Chapter 4
 Flow of Control: Loops Chapter 4 Java Loop Statements: Outline The while statement The do-while statement The for Statement Java Loop Statements A portion of a program that repeats a statement or a group
Flow of Control: Loops Chapter 4 Java Loop Statements: Outline The while statement The do-while statement The for Statement Java Loop Statements A portion of a program that repeats a statement or a group
CS 520 Theory and Practice of Software Engineering Fall 2018
 CS 520 Theory and Practice of Software Engineering Fall 2018 Nediyana Daskalova Monday, 4PM CS 151 Debugging October 30, 2018 Personalized Behavior-Powered Systems for Guiding Self-Experiments Help me
CS 520 Theory and Practice of Software Engineering Fall 2018 Nediyana Daskalova Monday, 4PM CS 151 Debugging October 30, 2018 Personalized Behavior-Powered Systems for Guiding Self-Experiments Help me
Overview Graph Coverage Criteria
 Overview Graph Coverage Criteria Graph Coverage Four Structures for Modeling Software Graphs Logic Input Space Syntax Applied to Applied to Source FSMs Applied to Specs DNF Source Specs Source Models Design
Overview Graph Coverage Criteria Graph Coverage Four Structures for Modeling Software Graphs Logic Input Space Syntax Applied to Applied to Source FSMs Applied to Specs DNF Source Specs Source Models Design
(See related materials in textbook.) CSE 435: Software Engineering (slides adapted from Ghezzi et al & Stirewalt
 Verification (See related materials in textbook.) Outline What are the goals of verification? What are the main approaches to verification? What kind of assurance do we get through testing? How can testing
Verification (See related materials in textbook.) Outline What are the goals of verification? What are the main approaches to verification? What kind of assurance do we get through testing? How can testing
QUIZ on Ch.5. Why is it sometimes not a good idea to place the private part of the interface in a header file?
 QUIZ on Ch.5 Why is it sometimes not a good idea to place the private part of the interface in a header file? Example projects where we don t want the implementation visible to the client programmer: The
QUIZ on Ch.5 Why is it sometimes not a good idea to place the private part of the interface in a header file? Example projects where we don t want the implementation visible to the client programmer: The
Verification and Validation. Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1
 Verification and Validation Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1 Verification vs validation Verification: "Are we building the product right?. The software should
Verification and Validation Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1 Verification vs validation Verification: "Are we building the product right?. The software should
Discover how to get up and running with the Java Development Environment and with the Eclipse IDE to create Java programs.
 Java SE11 Development Java is the most widely-used development language in the world today. It allows programmers to create objects that can interact with other objects to solve a problem. Explore Java
Java SE11 Development Java is the most widely-used development language in the world today. It allows programmers to create objects that can interact with other objects to solve a problem. Explore Java
Global Optimization. Lecture Outline. Global flow analysis. Global constant propagation. Liveness analysis. Local Optimization. Global Optimization
 Lecture Outline Global Optimization Global flow analysis Global constant propagation Liveness analysis Compiler Design I (2011) 2 Local Optimization Recall the simple basic-block optimizations Constant
Lecture Outline Global Optimization Global flow analysis Global constant propagation Liveness analysis Compiler Design I (2011) 2 Local Optimization Recall the simple basic-block optimizations Constant
Testing Reactive Programs. Designing Programmable debugger easily
 Outline Plan Debugging Reactive Programs Debugging Reactive Programs 3 orthogonal ideas 1 Debugging Reactive Programs 2 rdbg : a programmable debugger for reactive programs 3 The User point of view 4 The
Outline Plan Debugging Reactive Programs Debugging Reactive Programs 3 orthogonal ideas 1 Debugging Reactive Programs 2 rdbg : a programmable debugger for reactive programs 3 The User point of view 4 The
Test Automation. 20 December 2017
 Test Automation 20 December 2017 The problem of test automation Testing has repetitive components, so automation is justified The problem is cost-benefit evaluation of automation [Kaner] Time for: test
Test Automation 20 December 2017 The problem of test automation Testing has repetitive components, so automation is justified The problem is cost-benefit evaluation of automation [Kaner] Time for: test
DEBUGGING: STATIC ANALYSIS
 DEBUGGING: STATIC ANALYSIS WS 2017/2018 Martina Seidl Institute for Formal Models and Verification Deduction Techniques (1/2) basic idea: reasoning from abstract program to concrete program runs (program
DEBUGGING: STATIC ANALYSIS WS 2017/2018 Martina Seidl Institute for Formal Models and Verification Deduction Techniques (1/2) basic idea: reasoning from abstract program to concrete program runs (program
CS 231 Data Structures and Algorithms, Fall 2016
 CS 231 Data Structures and Algorithms, Fall 2016 Dr. Bruce A. Maxwell Department of Computer Science Colby College Course Description Focuses on the common structures used to store data and the standard
CS 231 Data Structures and Algorithms, Fall 2016 Dr. Bruce A. Maxwell Department of Computer Science Colby College Course Description Focuses on the common structures used to store data and the standard
CS 4387/5387 SOFTWARE V&V LECTURE 4 BLACK-BOX TESTING
 1 CS 4387/5387 SOFTWARE V&V LECTURE 4 BLACK-BOX TESTING Outline 2 Quiz Black-Box Testing Equivalence Class Testing (Equivalence Partitioning) Boundary value analysis Decision Table Testing 1 3 Quiz - 1
1 CS 4387/5387 SOFTWARE V&V LECTURE 4 BLACK-BOX TESTING Outline 2 Quiz Black-Box Testing Equivalence Class Testing (Equivalence Partitioning) Boundary value analysis Decision Table Testing 1 3 Quiz - 1
Testing. Prof. Clarkson Fall Today s music: Wrecking Ball by Miley Cyrus
 Testing Prof. Clarkson Fall 2017 Today s music: Wrecking Ball by Miley Cyrus Review Previously in 3110: Modules Specification (functions, modules) Today: Validation Testing Black box Glass box Randomized
Testing Prof. Clarkson Fall 2017 Today s music: Wrecking Ball by Miley Cyrus Review Previously in 3110: Modules Specification (functions, modules) Today: Validation Testing Black box Glass box Randomized
Randomised testing of a microprocessor model using SMT-solver state generation
 Randomised testing of a microprocessor model using SMT-solver state generation Brian Campbell Ian Stark LFCS, School of Informatics, University of Edinburgh, UK Rigorous Engineering for Mainstream Systems
Randomised testing of a microprocessor model using SMT-solver state generation Brian Campbell Ian Stark LFCS, School of Informatics, University of Edinburgh, UK Rigorous Engineering for Mainstream Systems
