CPE702 Algorithm Analysis and Design Week 7 Algorithm Design Patterns
|
|
|
- Aldous Miller
- 5 years ago
- Views:
Transcription
1 CPE702 Algorithm Analysis and Design Week 7 Algorithm Design Patterns Pruet Boonma pruet@eng.cmu.ac.th Department of Computer Engineering Faculty of Engineering, Chiang Mai University Based on Slides by M.T. Goodrich and R. Tamassia
2 2 In this week Algorithm Design Patterns Brute-force Search Greedy method Divide-and-conquer
3 3 Brute-force Search AKA exhaustive search or generate and test. Brute-force method is a trivial method to enumerate all possible candidates for the solution. When all solutions are tested, the best one is picked. It is useful when the problem size is limited because the cost is usually grow (very) fast. Known as combinatorial explosion. E.g., if the problem has one solution variable, it will be O(z). But if it has two, it will be O(z n ) and so on; where z is the number of possible value of each variable.
4 4 The Greedy Method The greedy method is a general algorithm design paradigm, built on the following elements: configurations: different choices, collections, or values to find objective function: a score assigned to configurations, which we want to either maximize or minimize It works best when applied to problems with the greedy-choice property: a globally-optimal solution can always be found by a series of local improvements from a starting configuration.
5 5 Text Compression Given a string X, efficiently encode X into a smaller string Y Saves memory and/or bandwidth A good approach: Huffman encoding Compute frequency f(c) for each character c. Encode high-frequency characters with short code words No code word is a prefix for another code Use an optimal encoding tree to determine the code words
6 6 Encoding Tree Example A code is a mapping of each character of an alphabet to a binary code-word A prefix code is a binary code such that no code-word is the prefix of another code-word An encoding tree represents a prefix code Each external node stores a character The code word of a character is given by the path from the root to the external node storing the character (0 for a left child and 1 for a right child) a b c d e a d e b c
7 7 Encoding Tree Optimization Given a text string X, we want to find a prefix code for the characters of X that yields a small encoding for X Frequent characters should have long code-words Rare characters should have short code-words Example X = abracadabra T 1 encodes X into 29 bits T 2 encodes X into 24 bits T 1 T 2 c d b a b r a r c d
8 8 Huffman s Algorithm Given a string X, Huffman s algorithm construct a prefix code the minimizes the size of the encoding of X It runs in time O(n + d log d), where n is the size of X and d is the number of distinct characters of X A heap-based priority queue is used as an auxiliary structure Algorithm HuffmanEncoding(X) Input string X of size n Output optimal encoding trie for X C distinctcharacters(x) computefrequencies(c, X) Q new empty heap for all c C T new single-node tree storing c Q.insert(getFrequency(c), T) while Q.size() > 1 f 1 Q.minKey() T 1 Q.removeMin() f 2 Q.minKey() T 2 Q.removeMin() T join(t 1, T 2 ) Q.insert(f 1 + f 2, T) return Q.removeMin()
9 9 Example X = abracadabra Frequencies a a b c d r c d b r 6 a b c d r a c d b r a b c d r a c d b r
10 Extended Huffman Tree Example 10
11 11 The Knapsack Problem Given: A set S of n items, with each item i having b i - a positive benefit w i - a positive weight Goal: Choose items with maximum total benefit but with weight at most W. If we are allowed to take fractional amounts, then this is the fractional knapsack problem. In this case, we let x i denote the amount we take of item i Objective: maximize i S b ( x / w ) i i i Constraint: i S x i W
12 12 Example Given: A set S of n items, with each item i having b i - a positive benefit w i - a positive weight Goal: Choose items with maximum total benefit but with weight at most W. knapsack Items: Weight: Benefit: Value: 3 ($ per ml) ml 8 ml 2 ml 6 ml 1 ml $12 $32 $40 $30 $ ml Solution: 1 ml of 5 2 ml of 3 6 ml of 4 1 ml of 2
13 13 The Knapsack Algorithm Greedy choice: Keep taking item with highest value (benefit to weight ratio) Since i S Run time: O(n log n). Why? Correctness: Suppose there is a better solution there is an item i with higher value than a chosen item j, but x i <w i, x j >0 and v i <v j If we substitute some i with j, we get a better solution How much of i: min{w i -x i, x j } Thus, there is no better solution than the greedy one b ( x / w ) = ( b / w ) x i i i i S i i i Algorithm fractionalknapsack(s, W) Input: set S of items w/ benefit b i and weight w i ; max. weight W Output: amount x i of each item i to maximize benefit w/ weight at most W for each item i in S x i 0 v i b i / w i {value} w 0 {total weight} while w < W remove item i w/ highest v i x i min{w i, W - w} w w + min{w i, W - w}
14 14 Task Scheduling Given: a set T of n tasks, each having: A start time, s i A finish time, f i (where s i < f i ) Goal: Perform all the tasks using a minimum number of machines. Machine 3 Machine 2 Machine
15 15 Task Scheduling Algorithm Greedy choice: consider tasks by their start time and use as few machines as possible with this order. Run time: O(n log n). Why? Correctness: Suppose there is a better schedule. We can use k-1 machines The algorithm uses k Let i be first task scheduled on machine k Machine i must conflict with k-1 other tasks But that means there is no non-conflicting schedule using k-1 machines Algorithm taskschedule(t) Input: set T of tasks w/ start time s i and finish time f i Output: non-conflicting schedule with minimum number of machines m 0 {no. of machines} while T is not empty remove task i w/ smallest s i if there s a machine j for i then schedule i on machine j else m m + 1 schedule i on machine m
16 16 Example Given: a set T of n tasks, each having: A start time, s i A finish time, f i (where s i < f i ) [1,4], [1,3], [2,5], [3,7], [4,7], [6,9], [7,8] (ordered by start) Goal: Perform all tasks on min. number of machines Machine 3 Machine 2 Machine
17 17 Divide-and-Conquer Divide-and conquer is a general algorithm design paradigm: Divide: divide the input data S in two or more disjoint subsets S 1, S 2, Recur: solve the subproblems recursively Conquer: combine the solutions for S 1, S 2,, into a solution for S The base case for the recursion are subproblems of constant size Analysis can be done using recurrence equations
18 18 Merge-Sort Merge-sort on an input sequence S with n elements consists of three steps: Divide: partition S into two sequences S 1 and S 2 of about n/2 elements each Recur: recursively sort S 1 and S 2 Algorithm mergesort(s, C) Input sequence S with n elements, comparator C Output sequence S sorted according to C if S.size() > 1 (S 1, S 2 ) partition(s, n/2) mergesort(s 1, C) mergesort(s 2, C) S merge(s 1, S 2 ) Conquer: merge S 1 and S 2 into a unique sorted sequence
19 19 Merging Two Sorted Sequences The conquer step of merge-sort consists of merging two sorted sequences A and B into a sorted sequence S containing the union of the elements of A and B Merging two sorted sequences, each with n/2 elements and implemented by means of a doubly linked list, takes O(n) time Algorithm merge(a, B) Input sequences A and B with n/2 elements each Output sorted sequence of A B S empty sequence while A.isEmpty() B.isEmpty() if A.first().element() < B.first().element() S.insertLast(A.remove(A.first())) else S.insertLast(B.remove(B.first())) while A.isEmpty() S.insertLast(A.remove(A.first())) while B.isEmpty() S.insertLast(B.remove(B.first())) return S
20 20 Merge-Sort Tree An execution of merge-sort is depicted by a binary tree each node represents a recursive call of merge-sort and stores unsorted sequence before the execution and its partition sorted sequence at the end of the execution the root is the initial call the leaves are calls on subsequences of size 0 or
21 21 Execution Example Partition
22 22 Execution Example (cont.) Recursive call, partition
23 23 Execution Example (cont.) Recursive call, partition
24 24 Execution Example (cont.) Recursive call, base case
25 25 Execution Example (cont.) Recursive call, base case
26 26 Execution Example (cont.) Merge
27 27 Execution Example (cont.) Recursive call,, base case, merge
28 28 Execution Example (cont.) Merge
29 29 Execution Example (cont.) Recursive call,, merge, merge
30 30 Execution Example (cont.) Merge
31 31 Analysis of Merge-Sort The height h of the merge-sort tree is O(log n) at each recursive call we divide in half the sequence, The overall amount or work done at the nodes of depth i is O(n) we partition and merge 2 i sequences of size n/2 i we make 2 i+1 recursive calls Thus, the total running time of merge-sort is O(n log n) depth #seqs size 0 1 n 1 2 n/2 i 2 i n/2 i
32 32 Recurrence Equation Analysis The conquer step of merge-sort consists of merging two sorted sequences, each with n/2 elements and implemented by means of a doubly linked list, takes at most bn steps, for some constant b. Likewise, the basis case (n < 2) will take at b most steps. Therefore, if we let T(n) denote the running time of merge-sort: T ( n) = 2T ( n / b 2) + bn if if n < n 2 2 We can therefore analyze the running time of merge-sort by finding a closed form solution to the above equation. That is, a solution that has T(n) only on the left-hand side.
33 33 Iterative Substitution In the iterative substitution, or plug-and-chug, technique, we iteratively apply the recurrence equation to itself and see if we can find a pattern: T ( n) = 2T ( n / 2) + bn = = = = = = 2(2T ( n / T ( n / 2 T ( n / 2 T ( n / 2 i i 2 T ( n / 2 )) + b( n / 2)) + bn ) + 2bn ) + 3bn ) + 4bn ) + ibn Note that base, T(n)=b, case occurs when 2 i =n. That is, i = log n. So, T ( n) = bn + bn logn Thus, T(n) is O(n log n)
34 34 The Recursion Tree Draw the recursion tree for the recurrence relation and look for a pattern: depth T s size 0 1 n T ( n) = b 2T ( n / 2) + bn if if n n < 2 2 time bn 1 2 n/2 i 2 i n/2 i bn bn Total time = bn + bn log n (last level plus all previous levels)
Merge Sort fi fi fi 4 9. Merge Sort Goodrich, Tamassia
 Merge Sort 7 9 4 fi 4 7 9 7 fi 7 9 4 fi 4 9 7 fi 7 fi 9 fi 9 4 fi 4 Merge Sort 1 Divide-and-Conquer ( 10.1.1) Divide-and conquer is a general algorithm design paradigm: Divide: divide the input data S
Merge Sort 7 9 4 fi 4 7 9 7 fi 7 9 4 fi 4 9 7 fi 7 fi 9 fi 9 4 fi 4 Merge Sort 1 Divide-and-Conquer ( 10.1.1) Divide-and conquer is a general algorithm design paradigm: Divide: divide the input data S
Merge Sort Goodrich, Tamassia Merge Sort 1
 Merge Sort 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 2004 Goodrich, Tamassia Merge Sort 1 Review of Sorting Selection-sort: Search: search through remaining unsorted elements for min Remove: remove
Merge Sort 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 2004 Goodrich, Tamassia Merge Sort 1 Review of Sorting Selection-sort: Search: search through remaining unsorted elements for min Remove: remove
COMP251: Greedy algorithms
 COMP251: Greedy algorithms Jérôme Waldispühl School of Computer Science McGill University Based on (Cormen et al., 2002) Based on slides from D. Plaisted (UNC) & (goodrich & Tamassia, 2009) Disjoint sets
COMP251: Greedy algorithms Jérôme Waldispühl School of Computer Science McGill University Based on (Cormen et al., 2002) Based on slides from D. Plaisted (UNC) & (goodrich & Tamassia, 2009) Disjoint sets
Merge Sort Goodrich, Tamassia. Merge Sort 1
 Merge Sort 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Merge Sort 1 Divide-and-Conquer ( 10.1.1) Divide-and conquer is a general algorithm design paradigm: Divide: divide the input data S in two disjoint
Merge Sort 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Merge Sort 1 Divide-and-Conquer ( 10.1.1) Divide-and conquer is a general algorithm design paradigm: Divide: divide the input data S in two disjoint
Sorting. Data structures and Algorithms
 Sorting Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich, Tamassia and Mount (Wiley, 2004) Outline Bubble
Sorting Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich, Tamassia and Mount (Wiley, 2004) Outline Bubble
Merge Sort
 Merge Sort 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conuer Divide-and conuer is a general algorithm design paradigm: n Divide: divide the input data S in two disjoint subsets S 1 and
Merge Sort 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conuer Divide-and conuer is a general algorithm design paradigm: n Divide: divide the input data S in two disjoint subsets S 1 and
Lecture 19 Sorting Goodrich, Tamassia
 Lecture 19 Sorting 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 2004 Goodrich, Tamassia Outline Review 3 simple sorting algorithms: 1. selection Sort (in previous course) 2. insertion Sort (in previous
Lecture 19 Sorting 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 2004 Goodrich, Tamassia Outline Review 3 simple sorting algorithms: 1. selection Sort (in previous course) 2. insertion Sort (in previous
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Merge Sort 2015 Goodrich and Tamassia Merge Sort 1 Application: Internet Search
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Merge Sort 2015 Goodrich and Tamassia Merge Sort 1 Application: Internet Search
SORTING AND SELECTION
 2 < > 1 4 8 6 = 9 CHAPTER 12 SORTING AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN JAVA, GOODRICH, TAMASSIA AND GOLDWASSER (WILEY 2016)
2 < > 1 4 8 6 = 9 CHAPTER 12 SORTING AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN JAVA, GOODRICH, TAMASSIA AND GOLDWASSER (WILEY 2016)
Sorting. Divide-and-Conquer 1
 Sorting Divide-and-Conquer 1 Divide-and-Conquer 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conquer 2 Divide-and-Conquer Divide-and conquer is a general algorithm design paradigm: Divide:
Sorting Divide-and-Conquer 1 Divide-and-Conquer 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conquer 2 Divide-and-Conquer Divide-and conquer is a general algorithm design paradigm: Divide:
Sorting. Outline. Sorting with a priority queue Selection-sort Insertion-sort Heap Sort Quick Sort
 Sorting Hiroaki Kobayashi 1 Outline Sorting with a priority queue Selection-sort Insertion-sort Heap Sort Quick Sort Merge Sort Lower Bound on Comparison-Based Sorting Bucket Sort and Radix Sort Hiroaki
Sorting Hiroaki Kobayashi 1 Outline Sorting with a priority queue Selection-sort Insertion-sort Heap Sort Quick Sort Merge Sort Lower Bound on Comparison-Based Sorting Bucket Sort and Radix Sort Hiroaki
Recursive Sorts. Recursive Sorts. Divide-and-Conquer. Divide-and-Conquer. Divide-and-conquer paradigm:
 Recursive Sorts Recursive Sorts Recursive sorts divide the data roughly in half and are called again on the smaller data sets. This is called the Divide-and-Conquer paradigm. We will see 2 recursive sorts:
Recursive Sorts Recursive Sorts Recursive sorts divide the data roughly in half and are called again on the smaller data sets. This is called the Divide-and-Conquer paradigm. We will see 2 recursive sorts:
1. The Sets ADT. 1. The Sets ADT. 1. The Sets ADT 11/22/2011. Class Assignment Set in STL
 1. Sets 2. Sorting 1. The Sets ADT A set is a container of distinct objects. no duplicate no notation of key, or order. The operation of the set ADT: union: A B = {x:x A or x B} intersection: A B = {x:x
1. Sets 2. Sorting 1. The Sets ADT A set is a container of distinct objects. no duplicate no notation of key, or order. The operation of the set ADT: union: A B = {x:x A or x B} intersection: A B = {x:x
Divide-and-Conquer. Divide-and conquer is a general algorithm design paradigm:
 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Merge Sort 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9
Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Merge Sort 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9
Sorting Goodrich, Tamassia Sorting 1
 Sorting Put array A of n numbers in increasing order. A core algorithm with many applications. Simple algorithms are O(n 2 ). Optimal algorithms are O(n log n). We will see O(n) for restricted input in
Sorting Put array A of n numbers in increasing order. A core algorithm with many applications. Simple algorithms are O(n 2 ). Optimal algorithms are O(n log n). We will see O(n) for restricted input in
String Patterns and Algorithms on Strings
 String Patterns and Algorithms on Strings Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce the pattern matching problem and the important of algorithms
String Patterns and Algorithms on Strings Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce the pattern matching problem and the important of algorithms
DIVIDE AND CONQUER ALGORITHMS ANALYSIS WITH RECURRENCE EQUATIONS
 CHAPTER 11 SORTING ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY M. AMATO AND
CHAPTER 11 SORTING ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY M. AMATO AND
Data Structures and Algorithms " Sorting!
 Data Structures and Algorithms " Sorting! Outline" Merge Sort! Quick Sort! Sorting Lower Bound! Bucket-Sort! Radix Sort! Phạm Bảo Sơn DSA 2 Merge Sort" 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conquer
Data Structures and Algorithms " Sorting! Outline" Merge Sort! Quick Sort! Sorting Lower Bound! Bucket-Sort! Radix Sort! Phạm Bảo Sơn DSA 2 Merge Sort" 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conquer
SORTING, SETS, AND SELECTION
 CHAPTER 11 SORTING, SETS, AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM
CHAPTER 11 SORTING, SETS, AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM
CSED233: Data Structures (2017F) Lecture12: Strings and Dynamic Programming
 (2017F) Lecture12: Strings and Dynamic Programming Daijin Kim CSE, POSTECH dkim@postech.ac.kr Strings A string is a sequence of characters Examples of strings: Python program HTML document DNA sequence
(2017F) Lecture12: Strings and Dynamic Programming Daijin Kim CSE, POSTECH dkim@postech.ac.kr Strings A string is a sequence of characters Examples of strings: Python program HTML document DNA sequence
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, Merge Sort & Quick Sort
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Merge Sort & Quick Sort 1 Divide-and-Conquer Divide-and conquer is a general algorithm
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Merge Sort & Quick Sort 1 Divide-and-Conquer Divide-and conquer is a general algorithm
Sorting. Lecture10: Sorting II. Sorting Algorithms. Performance of Sorting Algorithms
 Sorting (2013F) Lecture10: Sorting II Bohyung Han CSE, POSTECH bhhan@postech.ac.kr Important operation when organizing data Ordering of elements Finding duplicate elements Ranking elements (i.e., n th
Sorting (2013F) Lecture10: Sorting II Bohyung Han CSE, POSTECH bhhan@postech.ac.kr Important operation when organizing data Ordering of elements Finding duplicate elements Ranking elements (i.e., n th
We can use a max-heap to sort data.
 Sorting 7B N log N Sorts 1 Heap Sort We can use a max-heap to sort data. Convert an array to a max-heap. Remove the root from the heap and store it in its proper position in the same array. Repeat until
Sorting 7B N log N Sorts 1 Heap Sort We can use a max-heap to sort data. Convert an array to a max-heap. Remove the root from the heap and store it in its proper position in the same array. Repeat until
Quick-Sort. Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm:
 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9
Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9
Sorting and Selection
 Sorting and Selection Introduction Divide and Conquer Merge-Sort Quick-Sort Radix-Sort Bucket-Sort 10-1 Introduction Assuming we have a sequence S storing a list of keyelement entries. The key of the element
Sorting and Selection Introduction Divide and Conquer Merge-Sort Quick-Sort Radix-Sort Bucket-Sort 10-1 Introduction Assuming we have a sequence S storing a list of keyelement entries. The key of the element
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 2015 Goodrich and Tamassia
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 2015 Goodrich and Tamassia
Comparison Sorts. Chapter 9.4, 12.1, 12.2
 Comparison Sorts Chapter 9.4, 12.1, 12.2 Sorting We have seen the advantage of sorted data representations for a number of applications Sparse vectors Maps Dictionaries Here we consider the problem of
Comparison Sorts Chapter 9.4, 12.1, 12.2 Sorting We have seen the advantage of sorted data representations for a number of applications Sparse vectors Maps Dictionaries Here we consider the problem of
Programming II (CS300)
 1 Programming II (CS300) Chapter 12: Sorting Algorithms MOUNA KACEM mouna@cs.wisc.edu Spring 2018 Outline 2 Last week Implementation of the three tree depth-traversal algorithms Implementation of the BinarySearchTree
1 Programming II (CS300) Chapter 12: Sorting Algorithms MOUNA KACEM mouna@cs.wisc.edu Spring 2018 Outline 2 Last week Implementation of the three tree depth-traversal algorithms Implementation of the BinarySearchTree
LECTURE NOTES OF ALGORITHMS: DESIGN TECHNIQUES AND ANALYSIS
 Department of Computer Science University of Babylon LECTURE NOTES OF ALGORITHMS: DESIGN TECHNIQUES AND ANALYSIS By Faculty of Science for Women( SCIW), University of Babylon, Iraq Samaher@uobabylon.edu.iq
Department of Computer Science University of Babylon LECTURE NOTES OF ALGORITHMS: DESIGN TECHNIQUES AND ANALYSIS By Faculty of Science for Women( SCIW), University of Babylon, Iraq Samaher@uobabylon.edu.iq
Algorithms Dr. Haim Levkowitz
 91.503 Algorithms Dr. Haim Levkowitz Fall 2007 Lecture 4 Tuesday, 25 Sep 2007 Design Patterns for Optimization Problems Greedy Algorithms 1 Greedy Algorithms 2 What is Greedy Algorithm? Similar to dynamic
91.503 Algorithms Dr. Haim Levkowitz Fall 2007 Lecture 4 Tuesday, 25 Sep 2007 Design Patterns for Optimization Problems Greedy Algorithms 1 Greedy Algorithms 2 What is Greedy Algorithm? Similar to dynamic
CSE 431/531: Algorithm Analysis and Design (Spring 2018) Greedy Algorithms. Lecturer: Shi Li
 CSE 431/531: Algorithm Analysis and Design (Spring 2018) Greedy Algorithms Lecturer: Shi Li Department of Computer Science and Engineering University at Buffalo Main Goal of Algorithm Design Design fast
CSE 431/531: Algorithm Analysis and Design (Spring 2018) Greedy Algorithms Lecturer: Shi Li Department of Computer Science and Engineering University at Buffalo Main Goal of Algorithm Design Design fast
Programming II (CS300)
 1 Programming II (CS300) Chapter 12: Sorting Algorithms MOUNA KACEM mouna@cs.wisc.edu Spring 2018 Outline 2 Last week Implementation of the three tree depth-traversal algorithms Implementation of the BinarySearchTree
1 Programming II (CS300) Chapter 12: Sorting Algorithms MOUNA KACEM mouna@cs.wisc.edu Spring 2018 Outline 2 Last week Implementation of the three tree depth-traversal algorithms Implementation of the BinarySearchTree
Introduction to Computers and Programming. Today
 Introduction to Computers and Programming Prof. I. K. Lundqvist Lecture 10 April 8 2004 Today How to determine Big-O Compare data structures and algorithms Sorting algorithms 2 How to determine Big-O Partition
Introduction to Computers and Programming Prof. I. K. Lundqvist Lecture 10 April 8 2004 Today How to determine Big-O Compare data structures and algorithms Sorting algorithms 2 How to determine Big-O Partition
Design and Analysis of Algorithms
 CSE 101, Winter 018 D/Q Greed SP s DP LP, Flow B&B, Backtrack Metaheuristics P, NP Design and Analysis of Algorithms Lecture 8: Greed Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Optimization
CSE 101, Winter 018 D/Q Greed SP s DP LP, Flow B&B, Backtrack Metaheuristics P, NP Design and Analysis of Algorithms Lecture 8: Greed Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Optimization
Greedy Algorithms. CLRS Chapters Introduction to greedy algorithms. Design of data-compression (Huffman) codes
 Greedy Algorithms CLRS Chapters 16.1 16.3 Introduction to greedy algorithms Activity-selection problem Design of data-compression (Huffman) codes (Minimum spanning tree problem) (Shortest-path problem)
Greedy Algorithms CLRS Chapters 16.1 16.3 Introduction to greedy algorithms Activity-selection problem Design of data-compression (Huffman) codes (Minimum spanning tree problem) (Shortest-path problem)
CS473-Algorithms I. Lecture 11. Greedy Algorithms. Cevdet Aykanat - Bilkent University Computer Engineering Department
 CS473-Algorithms I Lecture 11 Greedy Algorithms 1 Activity Selection Problem Input: a set S {1, 2,, n} of n activities s i =Start time of activity i, f i = Finish time of activity i Activity i takes place
CS473-Algorithms I Lecture 11 Greedy Algorithms 1 Activity Selection Problem Input: a set S {1, 2,, n} of n activities s i =Start time of activity i, f i = Finish time of activity i Activity i takes place
Analysis of Algorithms - Greedy algorithms -
 Analysis of Algorithms - Greedy algorithms - Andreas Ermedahl MRTC (Mälardalens Real-Time Reseach Center) andreas.ermedahl@mdh.se Autumn 2003 Greedy Algorithms Another paradigm for designing algorithms
Analysis of Algorithms - Greedy algorithms - Andreas Ermedahl MRTC (Mälardalens Real-Time Reseach Center) andreas.ermedahl@mdh.se Autumn 2003 Greedy Algorithms Another paradigm for designing algorithms
Practical Session 10 - Huffman code, Sort properties, QuickSort algorithm, Selection
 Practical Session 0 - Huffman code, Sort properties, QuickSort algorithm, Selection Huffman Code Algorithm Description Example Huffman coding is an encoding algorithm used for lossless data compression,
Practical Session 0 - Huffman code, Sort properties, QuickSort algorithm, Selection Huffman Code Algorithm Description Example Huffman coding is an encoding algorithm used for lossless data compression,
Design and Analysis of Algorithms
 Design and Analysis of Algorithms Instructor: SharmaThankachan Lecture 10: Greedy Algorithm Slides modified from Dr. Hon, with permission 1 About this lecture Introduce Greedy Algorithm Look at some problems
Design and Analysis of Algorithms Instructor: SharmaThankachan Lecture 10: Greedy Algorithm Slides modified from Dr. Hon, with permission 1 About this lecture Introduce Greedy Algorithm Look at some problems
Quick-Sort fi fi fi 7 9. Quick-Sort Goodrich, Tamassia
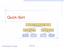 Quick-Sort 7 4 9 6 2 fi 2 4 6 7 9 4 2 fi 2 4 7 9 fi 7 9 2 fi 2 9 fi 9 Quick-Sort 1 Quick-Sort ( 10.2 text book) Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm: x
Quick-Sort 7 4 9 6 2 fi 2 4 6 7 9 4 2 fi 2 4 7 9 fi 7 9 2 fi 2 9 fi 9 Quick-Sort 1 Quick-Sort ( 10.2 text book) Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm: x
CS2223: Algorithms Sorting Algorithms, Heap Sort, Linear-time sort, Median and Order Statistics
 CS2223: Algorithms Sorting Algorithms, Heap Sort, Linear-time sort, Median and Order Statistics 1 Sorting 1.1 Problem Statement You are given a sequence of n numbers < a 1, a 2,..., a n >. You need to
CS2223: Algorithms Sorting Algorithms, Heap Sort, Linear-time sort, Median and Order Statistics 1 Sorting 1.1 Problem Statement You are given a sequence of n numbers < a 1, a 2,..., a n >. You need to
Greedy Algorithms CHAPTER 16
 CHAPTER 16 Greedy Algorithms In dynamic programming, the optimal solution is described in a recursive manner, and then is computed ``bottom up''. Dynamic programming is a powerful technique, but it often
CHAPTER 16 Greedy Algorithms In dynamic programming, the optimal solution is described in a recursive manner, and then is computed ``bottom up''. Dynamic programming is a powerful technique, but it often
16.Greedy algorithms
 16.Greedy algorithms 16.1 An activity-selection problem Suppose we have a set S = {a 1, a 2,..., a n } of n proposed activities that with to use a resource. Each activity a i has a start time s i and a
16.Greedy algorithms 16.1 An activity-selection problem Suppose we have a set S = {a 1, a 2,..., a n } of n proposed activities that with to use a resource. Each activity a i has a start time s i and a
EECS 2011M: Fundamentals of Data Structures
 M: Fundamentals of Data Structures Instructor: Suprakash Datta Office : LAS 3043 Course page: http://www.eecs.yorku.ca/course/2011m Also on Moodle Note: Some slides in this lecture are adopted from James
M: Fundamentals of Data Structures Instructor: Suprakash Datta Office : LAS 3043 Course page: http://www.eecs.yorku.ca/course/2011m Also on Moodle Note: Some slides in this lecture are adopted from James
Quick-Sort. Quick-Sort 1
 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Quick-Sort 1 Outline and Reading Quick-sort ( 4.3) Algorithm Partition step Quick-sort tree Execution example Analysis of quick-sort (4.3.1) In-place
Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Quick-Sort 1 Outline and Reading Quick-sort ( 4.3) Algorithm Partition step Quick-sort tree Execution example Analysis of quick-sort (4.3.1) In-place
We augment RBTs to support operations on dynamic sets of intervals A closed interval is an ordered pair of real
 14.3 Interval trees We augment RBTs to support operations on dynamic sets of intervals A closed interval is an ordered pair of real numbers ], with Interval ]represents the set Open and half-open intervals
14.3 Interval trees We augment RBTs to support operations on dynamic sets of intervals A closed interval is an ordered pair of real numbers ], with Interval ]represents the set Open and half-open intervals
( D. Θ n. ( ) f n ( ) D. Ο%
 CSE 0 Name Test Spring 0 Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to run the code below is in: for i=n; i>=; i--) for j=; j
CSE 0 Name Test Spring 0 Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to run the code below is in: for i=n; i>=; i--) for j=; j
Department of Computer Applications. MCA 312: Design and Analysis of Algorithms. [Part I : Medium Answer Type Questions] UNIT I
![Department of Computer Applications. MCA 312: Design and Analysis of Algorithms. [Part I : Medium Answer Type Questions] UNIT I Department of Computer Applications. MCA 312: Design and Analysis of Algorithms. [Part I : Medium Answer Type Questions] UNIT I](/thumbs/94/122075835.jpg) MCA 312: Design and Analysis of Algorithms [Part I : Medium Answer Type Questions] UNIT I 1) What is an Algorithm? What is the need to study Algorithms? 2) Define: a) Time Efficiency b) Space Efficiency
MCA 312: Design and Analysis of Algorithms [Part I : Medium Answer Type Questions] UNIT I 1) What is an Algorithm? What is the need to study Algorithms? 2) Define: a) Time Efficiency b) Space Efficiency
Analysis of Algorithms. Unit 4 - Analysis of well known Algorithms
 Analysis of Algorithms Unit 4 - Analysis of well known Algorithms 1 Analysis of well known Algorithms Brute Force Algorithms Greedy Algorithms Divide and Conquer Algorithms Decrease and Conquer Algorithms
Analysis of Algorithms Unit 4 - Analysis of well known Algorithms 1 Analysis of well known Algorithms Brute Force Algorithms Greedy Algorithms Divide and Conquer Algorithms Decrease and Conquer Algorithms
COMP 352 FALL Tutorial 10
 1 COMP 352 FALL 2016 Tutorial 10 SESSION OUTLINE Divide-and-Conquer Method Sort Algorithm Properties Quick Overview on Sorting Algorithms Merge Sort Quick Sort Bucket Sort Radix Sort Problem Solving 2
1 COMP 352 FALL 2016 Tutorial 10 SESSION OUTLINE Divide-and-Conquer Method Sort Algorithm Properties Quick Overview on Sorting Algorithms Merge Sort Quick Sort Bucket Sort Radix Sort Problem Solving 2
( ) + n. ( ) = n "1) + n. ( ) = T n 2. ( ) = 2T n 2. ( ) = T( n 2 ) +1
 CSE 0 Name Test Summer 00 Last Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose you are sorting millions of keys that consist of three decimal
CSE 0 Name Test Summer 00 Last Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose you are sorting millions of keys that consist of three decimal
TU/e Algorithms (2IL15) Lecture 2. Algorithms (2IL15) Lecture 2 THE GREEDY METHOD
 Algorithms (2IL15) Lecture 2 THE GREEDY METHOD x y v w 1 Optimization problems for each instance there are (possibly) multiple valid solutions goal is to find an optimal solution minimization problem:
Algorithms (2IL15) Lecture 2 THE GREEDY METHOD x y v w 1 Optimization problems for each instance there are (possibly) multiple valid solutions goal is to find an optimal solution minimization problem:
Algorithms for Data Science
 Algorithms for Data Science CSOR W4246 Eleni Drinea Computer Science Department Columbia University Thursday, October 1, 2015 Outline 1 Recap 2 Shortest paths in graphs with non-negative edge weights (Dijkstra
Algorithms for Data Science CSOR W4246 Eleni Drinea Computer Science Department Columbia University Thursday, October 1, 2015 Outline 1 Recap 2 Shortest paths in graphs with non-negative edge weights (Dijkstra
Algorithms Interview Questions
 Algorithms Interview Questions 1. Define the concept of an algorithm. An algorithm is any well-defined computational procedure that takes some value (or set of values) as input and produces some value
Algorithms Interview Questions 1. Define the concept of an algorithm. An algorithm is any well-defined computational procedure that takes some value (or set of values) as input and produces some value
PESIT Bangalore South Campus Hosur road, 1km before Electronic City, Bengaluru -100 Department of MCA
 INTERNAL ASSESSMENT TEST 2 Date : 30/3/15 Max Marks : 50 Name of faculty : Sabeeha Sultana Subject & Code : ADA(13MCA41) Answer any five full question: 1.Illustrate Mergesort for the dataset 8,3,2,9,7,1,5,4.
INTERNAL ASSESSMENT TEST 2 Date : 30/3/15 Max Marks : 50 Name of faculty : Sabeeha Sultana Subject & Code : ADA(13MCA41) Answer any five full question: 1.Illustrate Mergesort for the dataset 8,3,2,9,7,1,5,4.
Chapter 16: Greedy Algorithm
 Chapter 16: Greedy Algorithm 1 About this lecture Introduce Greedy Algorithm Look at some problems solvable by Greedy Algorithm 2 Coin Changing Suppose that in a certain country, the coin dominations consist
Chapter 16: Greedy Algorithm 1 About this lecture Introduce Greedy Algorithm Look at some problems solvable by Greedy Algorithm 2 Coin Changing Suppose that in a certain country, the coin dominations consist
QuickSort
 QuickSort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 1 QuickSort QuickSort on an input sequence S with n elements consists of three steps: n n n Divide: partition S into two sequences S 1 and S 2 of about
QuickSort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 1 QuickSort QuickSort on an input sequence S with n elements consists of three steps: n n n Divide: partition S into two sequences S 1 and S 2 of about
Chapter 9. Greedy Technique. Copyright 2007 Pearson Addison-Wesley. All rights reserved.
 Chapter 9 Greedy Technique Copyright 2007 Pearson Addison-Wesley. All rights reserved. Greedy Technique Constructs a solution to an optimization problem piece by piece through a sequence of choices that
Chapter 9 Greedy Technique Copyright 2007 Pearson Addison-Wesley. All rights reserved. Greedy Technique Constructs a solution to an optimization problem piece by piece through a sequence of choices that
Lecture: Analysis of Algorithms (CS )
 Lecture: Analysis of Algorithms (CS483-001) Amarda Shehu Spring 2017 1 The Fractional Knapsack Problem Huffman Coding 2 Sample Problems to Illustrate The Fractional Knapsack Problem Variable-length (Huffman)
Lecture: Analysis of Algorithms (CS483-001) Amarda Shehu Spring 2017 1 The Fractional Knapsack Problem Huffman Coding 2 Sample Problems to Illustrate The Fractional Knapsack Problem Variable-length (Huffman)
Lecture 3, Review of Algorithms. What is Algorithm?
 BINF 336, Introduction to Computational Biology Lecture 3, Review of Algorithms Young-Rae Cho Associate Professor Department of Computer Science Baylor University What is Algorithm? Definition A process
BINF 336, Introduction to Computational Biology Lecture 3, Review of Algorithms Young-Rae Cho Associate Professor Department of Computer Science Baylor University What is Algorithm? Definition A process
( ). Which of ( ) ( ) " #& ( ) " # g( n) ( ) " # f ( n) Test 1
 CSE 0 Name Test Summer 006 Last Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n x n matrices is: A. "( n) B. "( nlogn) # C.
CSE 0 Name Test Summer 006 Last Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n x n matrices is: A. "( n) B. "( nlogn) # C.
Chapter 4: Sorting. Spring 2014 Sorting Fun 1
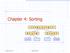 Chapter 4: Sorting 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Spring 2014 Sorting Fun 1 What We ll Do! Quick Sort! Lower bound on runtimes for comparison based sort! Radix and Bucket sort Spring 2014
Chapter 4: Sorting 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Spring 2014 Sorting Fun 1 What We ll Do! Quick Sort! Lower bound on runtimes for comparison based sort! Radix and Bucket sort Spring 2014
Algorithms and Data Structures (INF1) Lecture 7/15 Hua Lu
 Algorithms and Data Structures (INF1) Lecture 7/15 Hua Lu Department of Computer Science Aalborg University Fall 2007 This Lecture Merge sort Quick sort Radix sort Summary We will see more complex techniques
Algorithms and Data Structures (INF1) Lecture 7/15 Hua Lu Department of Computer Science Aalborg University Fall 2007 This Lecture Merge sort Quick sort Radix sort Summary We will see more complex techniques
Greedy Approach: Intro
 Greedy Approach: Intro Applies to optimization problems only Problem solving consists of a series of actions/steps Each action must be 1. Feasible 2. Locally optimal 3. Irrevocable Motivation: If always
Greedy Approach: Intro Applies to optimization problems only Problem solving consists of a series of actions/steps Each action must be 1. Feasible 2. Locally optimal 3. Irrevocable Motivation: If always
G205 Fundamentals of Computer Engineering. CLASS 21, Mon. Nov Stefano Basagni Fall 2004 M-W, 1:30pm-3:10pm
 G205 Fundamentals of Computer Engineering CLASS 21, Mon. Nov. 22 2004 Stefano Basagni Fall 2004 M-W, 1:30pm-3:10pm Greedy Algorithms, 1 Algorithms for Optimization Problems Sequence of steps Choices at
G205 Fundamentals of Computer Engineering CLASS 21, Mon. Nov. 22 2004 Stefano Basagni Fall 2004 M-W, 1:30pm-3:10pm Greedy Algorithms, 1 Algorithms for Optimization Problems Sequence of steps Choices at
The divide-and-conquer paradigm involves three steps at each level of the recursion: Divide the problem into a number of subproblems.
 2.3 Designing algorithms There are many ways to design algorithms. Insertion sort uses an incremental approach: having sorted the subarray A[1 j - 1], we insert the single element A[j] into its proper
2.3 Designing algorithms There are many ways to design algorithms. Insertion sort uses an incremental approach: having sorted the subarray A[1 j - 1], we insert the single element A[j] into its proper
CSE 421 Greedy Alg: Union Find/Dijkstra s Alg
 CSE 1 Greedy Alg: Union Find/Dijkstra s Alg Shayan Oveis Gharan 1 Dijkstra s Algorithm Dijkstra(G, c, s) { d s 0 foreach (v V) d[v] //This is the key of node v foreach (v V) insert v onto a priority queue
CSE 1 Greedy Alg: Union Find/Dijkstra s Alg Shayan Oveis Gharan 1 Dijkstra s Algorithm Dijkstra(G, c, s) { d s 0 foreach (v V) d[v] //This is the key of node v foreach (v V) insert v onto a priority queue
Data Structures and Algorithms Week 4
 Data Structures and Algorithms Week. About sorting algorithms. Heapsort Complete binary trees Heap data structure. Quicksort a popular algorithm very fast on average Previous Week Divide and conquer Merge
Data Structures and Algorithms Week. About sorting algorithms. Heapsort Complete binary trees Heap data structure. Quicksort a popular algorithm very fast on average Previous Week Divide and conquer Merge
Module 2: Classical Algorithm Design Techniques
 Module 2: Classical Algorithm Design Techniques Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Module
Module 2: Classical Algorithm Design Techniques Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Module
CHAPTER 11 SETS, AND SELECTION
 CHAPTER SETS, AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 00) AND SLIDES FROM JORY DENNY
CHAPTER SETS, AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 00) AND SLIDES FROM JORY DENNY
Problem. Input: An array A = (A[1],..., A[n]) with length n. Output: a permutation A of A, that is sorted: A [i] A [j] for all. 1 i j n.
![Problem. Input: An array A = (A[1],..., A[n]) with length n. Output: a permutation A of A, that is sorted: A [i] A [j] for all. 1 i j n. Problem. Input: An array A = (A[1],..., A[n]) with length n. Output: a permutation A of A, that is sorted: A [i] A [j] for all. 1 i j n.](/thumbs/84/89326706.jpg) Problem 5. Sorting Simple Sorting, Quicksort, Mergesort Input: An array A = (A[1],..., A[n]) with length n. Output: a permutation A of A, that is sorted: A [i] A [j] for all 1 i j n. 98 99 Selection Sort
Problem 5. Sorting Simple Sorting, Quicksort, Mergesort Input: An array A = (A[1],..., A[n]) with length n. Output: a permutation A of A, that is sorted: A [i] A [j] for all 1 i j n. 98 99 Selection Sort
Analysis of Algorithms Prof. Karen Daniels
 UMass Lowell Computer Science 91.503 Analysis of Algorithms Prof. Karen Daniels Spring, 2010 Lecture 2 Tuesday, 2/2/10 Design Patterns for Optimization Problems Greedy Algorithms Algorithmic Paradigm Context
UMass Lowell Computer Science 91.503 Analysis of Algorithms Prof. Karen Daniels Spring, 2010 Lecture 2 Tuesday, 2/2/10 Design Patterns for Optimization Problems Greedy Algorithms Algorithmic Paradigm Context
EE 368. Weeks 5 (Notes)
 EE 368 Weeks 5 (Notes) 1 Chapter 5: Trees Skip pages 273-281, Section 5.6 - If A is the root of a tree and B is the root of a subtree of that tree, then A is B s parent (or father or mother) and B is A
EE 368 Weeks 5 (Notes) 1 Chapter 5: Trees Skip pages 273-281, Section 5.6 - If A is the root of a tree and B is the root of a subtree of that tree, then A is B s parent (or father or mother) and B is A
1 Format. 2 Topics Covered. 2.1 Minimal Spanning Trees. 2.2 Union Find. 2.3 Greedy. CS 124 Quiz 2 Review 3/25/18
 CS 124 Quiz 2 Review 3/25/18 1 Format You will have 83 minutes to complete the exam. The exam may have true/false questions, multiple choice, example/counterexample problems, run-this-algorithm problems,
CS 124 Quiz 2 Review 3/25/18 1 Format You will have 83 minutes to complete the exam. The exam may have true/false questions, multiple choice, example/counterexample problems, run-this-algorithm problems,
15.4 Longest common subsequence
 15.4 Longest common subsequence Biological applications often need to compare the DNA of two (or more) different organisms A strand of DNA consists of a string of molecules called bases, where the possible
15.4 Longest common subsequence Biological applications often need to compare the DNA of two (or more) different organisms A strand of DNA consists of a string of molecules called bases, where the possible
( ) 1 B. 1. Suppose f x
 CSE Name Test Spring Last Digits of Student ID Multiple Choice. Write your answer to the LEFT of each problem. points each is a monotonically increasing function. Which of the following approximates the
CSE Name Test Spring Last Digits of Student ID Multiple Choice. Write your answer to the LEFT of each problem. points each is a monotonically increasing function. Which of the following approximates the
CSE Data Structures and Introduction to Algorithms... In Java! Instructor: Fei Wang. Mid-Term Exam. CSE2100 DS & Algorithms 1
 CSE 2100 Data Structures and Introduction to Algorithms...! In Java!! Instructor: Fei Wang! Mid-Term Exam CSE2100 DS & Algorithms 1 1. True or False (20%=2%x10)! (1) O(n) is O(n^2) (2) The height h of
CSE 2100 Data Structures and Introduction to Algorithms...! In Java!! Instructor: Fei Wang! Mid-Term Exam CSE2100 DS & Algorithms 1 1. True or False (20%=2%x10)! (1) O(n) is O(n^2) (2) The height h of
1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1
![1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1](/thumbs/85/92778785.jpg) Asymptotics, Recurrence and Basic Algorithms 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 2. O(n) 2. [1 pt] What is the solution to the recurrence T(n) = T(n/2) + n, T(1)
Asymptotics, Recurrence and Basic Algorithms 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 2. O(n) 2. [1 pt] What is the solution to the recurrence T(n) = T(n/2) + n, T(1)
1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1
![1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1](/thumbs/80/82301067.jpg) Asymptotics, Recurrence and Basic Algorithms 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 1. O(logn) 2. O(n) 3. O(nlogn) 4. O(n 2 ) 5. O(2 n ) 2. [1 pt] What is the solution
Asymptotics, Recurrence and Basic Algorithms 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 1. O(logn) 2. O(n) 3. O(nlogn) 4. O(n 2 ) 5. O(2 n ) 2. [1 pt] What is the solution
IN101: Algorithmic techniques Vladimir-Alexandru Paun ENSTA ParisTech
 IN101: Algorithmic techniques Vladimir-Alexandru Paun ENSTA ParisTech License CC BY-NC-SA 2.0 http://creativecommons.org/licenses/by-nc-sa/2.0/fr/ Outline Previously on IN101 Python s anatomy Functions,
IN101: Algorithmic techniques Vladimir-Alexandru Paun ENSTA ParisTech License CC BY-NC-SA 2.0 http://creativecommons.org/licenses/by-nc-sa/2.0/fr/ Outline Previously on IN101 Python s anatomy Functions,
) $ f ( n) " %( g( n)
 CSE 0 Name Test Spring 008 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to compute the sum of the n elements of an integer array is: # A.
CSE 0 Name Test Spring 008 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to compute the sum of the n elements of an integer array is: # A.
Scribe: Virginia Williams, Sam Kim (2016), Mary Wootters (2017) Date: May 22, 2017
 CS6 Lecture 4 Greedy Algorithms Scribe: Virginia Williams, Sam Kim (26), Mary Wootters (27) Date: May 22, 27 Greedy Algorithms Suppose we want to solve a problem, and we re able to come up with some recursive
CS6 Lecture 4 Greedy Algorithms Scribe: Virginia Williams, Sam Kim (26), Mary Wootters (27) Date: May 22, 27 Greedy Algorithms Suppose we want to solve a problem, and we re able to come up with some recursive
Greedy algorithms part 2, and Huffman code
 Greedy algorithms part 2, and Huffman code Two main properties: 1. Greedy choice property: At each decision point, make the choice that is best at the moment. We typically show that if we make a greedy
Greedy algorithms part 2, and Huffman code Two main properties: 1. Greedy choice property: At each decision point, make the choice that is best at the moment. We typically show that if we make a greedy
16 Greedy Algorithms
 16 Greedy Algorithms Optimization algorithms typically go through a sequence of steps, with a set of choices at each For many optimization problems, using dynamic programming to determine the best choices
16 Greedy Algorithms Optimization algorithms typically go through a sequence of steps, with a set of choices at each For many optimization problems, using dynamic programming to determine the best choices
IS 709/809: Computational Methods in IS Research. Algorithm Analysis (Sorting)
 IS 709/809: Computational Methods in IS Research Algorithm Analysis (Sorting) Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Sorting Problem Given an
IS 709/809: Computational Methods in IS Research Algorithm Analysis (Sorting) Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Sorting Problem Given an
15.4 Longest common subsequence
 15.4 Longest common subsequence Biological applications often need to compare the DNA of two (or more) different organisms A strand of DNA consists of a string of molecules called bases, where the possible
15.4 Longest common subsequence Biological applications often need to compare the DNA of two (or more) different organisms A strand of DNA consists of a string of molecules called bases, where the possible
Algorithm classification
 Types of Algorithms Algorithm classification Algorithms that use a similar problem-solving approach can be grouped together We ll talk about a classification scheme for algorithms This classification scheme
Types of Algorithms Algorithm classification Algorithms that use a similar problem-solving approach can be grouped together We ll talk about a classification scheme for algorithms This classification scheme
Multiple Choice. Write your answer to the LEFT of each problem. 3 points each
 CSE 0-00 Test Spring 0 Name Last 4 Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose f ( x) is a monotonically increasing function. Which of the
CSE 0-00 Test Spring 0 Name Last 4 Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose f ( x) is a monotonically increasing function. Which of the
Parallel Algorithms for (PRAM) Computers & Some Parallel Algorithms. Reference : Horowitz, Sahni and Rajasekaran, Computer Algorithms
 Parallel Algorithms for (PRAM) Computers & Some Parallel Algorithms Reference : Horowitz, Sahni and Rajasekaran, Computer Algorithms Part 2 1 3 Maximum Selection Problem : Given n numbers, x 1, x 2,, x
Parallel Algorithms for (PRAM) Computers & Some Parallel Algorithms Reference : Horowitz, Sahni and Rajasekaran, Computer Algorithms Part 2 1 3 Maximum Selection Problem : Given n numbers, x 1, x 2,, x
Lecture 5: Sorting Part A
 Lecture 5: Sorting Part A Heapsort Running time O(n lg n), like merge sort Sorts in place (as insertion sort), only constant number of array elements are stored outside the input array at any time Combines
Lecture 5: Sorting Part A Heapsort Running time O(n lg n), like merge sort Sorts in place (as insertion sort), only constant number of array elements are stored outside the input array at any time Combines
HEAPS: IMPLEMENTING EFFICIENT PRIORITY QUEUES
 HEAPS: IMPLEMENTING EFFICIENT PRIORITY QUEUES 2 5 6 9 7 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H., Wiley, 2014
HEAPS: IMPLEMENTING EFFICIENT PRIORITY QUEUES 2 5 6 9 7 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H., Wiley, 2014
Fast Sorting and Selection. A Lower Bound for Worst Case
 Lists and Iterators 0//06 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 0 Fast Sorting and Selection USGS NEIC. Public domain government
Lists and Iterators 0//06 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 0 Fast Sorting and Selection USGS NEIC. Public domain government
DATA STRUCTURES AND ALGORITHMS
 DATA STRUCTURES AND ALGORITHMS For COMPUTER SCIENCE DATA STRUCTURES &. ALGORITHMS SYLLABUS Programming and Data Structures: Programming in C. Recursion. Arrays, stacks, queues, linked lists, trees, binary
DATA STRUCTURES AND ALGORITHMS For COMPUTER SCIENCE DATA STRUCTURES &. ALGORITHMS SYLLABUS Programming and Data Structures: Programming in C. Recursion. Arrays, stacks, queues, linked lists, trees, binary
Introduction. e.g., the item could be an entire block of information about a student, while the search key might be only the student's name
 Chapter 7 Sorting 2 Introduction sorting fundamental task in data management well-studied problem in computer science basic problem given an of items where each item contains a key, rearrange the items
Chapter 7 Sorting 2 Introduction sorting fundamental task in data management well-studied problem in computer science basic problem given an of items where each item contains a key, rearrange the items
Operations on Heap Tree The major operations required to be performed on a heap tree are Insertion, Deletion, and Merging.
 Priority Queue, Heap and Heap Sort In this time, we will study Priority queue, heap and heap sort. Heap is a data structure, which permits one to insert elements into a set and also to find the largest
Priority Queue, Heap and Heap Sort In this time, we will study Priority queue, heap and heap sort. Heap is a data structure, which permits one to insert elements into a set and also to find the largest
looking ahead to see the optimum
 ! Make choice based on immediate rewards rather than looking ahead to see the optimum! In many cases this is effective as the look ahead variation can require exponential time as the number of possible
! Make choice based on immediate rewards rather than looking ahead to see the optimum! In many cases this is effective as the look ahead variation can require exponential time as the number of possible
Algorithm Analysis Advanced Data Structure. Chung-Ang University, Jaesung Lee
 Algorithm Analysis Advanced Data Structure Chung-Ang University, Jaesung Lee Priority Queue, Heap and Heap Sort 2 Max Heap data structure 3 Representation of Heap Tree 4 Representation of Heap Tree 5 Representation
Algorithm Analysis Advanced Data Structure Chung-Ang University, Jaesung Lee Priority Queue, Heap and Heap Sort 2 Max Heap data structure 3 Representation of Heap Tree 4 Representation of Heap Tree 5 Representation
Advanced Algorithms and Data Structures
 Advanced Algorithms and Data Structures Prof. Tapio Elomaa Course Basics A new 7 credit unit course Replaces OHJ-2156 Analysis of Algorithms We take things a bit further than OHJ-2156 We will assume familiarity
Advanced Algorithms and Data Structures Prof. Tapio Elomaa Course Basics A new 7 credit unit course Replaces OHJ-2156 Analysis of Algorithms We take things a bit further than OHJ-2156 We will assume familiarity
CS301 - Data Structures Glossary By
 CS301 - Data Structures Glossary By Abstract Data Type : A set of data values and associated operations that are precisely specified independent of any particular implementation. Also known as ADT Algorithm
CS301 - Data Structures Glossary By Abstract Data Type : A set of data values and associated operations that are precisely specified independent of any particular implementation. Also known as ADT Algorithm
( ) n 3. n 2 ( ) D. Ο
 CSE 0 Name Test Summer 0 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n n matrices is: A. Θ( n) B. Θ( max( m,n, p) ) C.
CSE 0 Name Test Summer 0 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n n matrices is: A. Θ( n) B. Θ( max( m,n, p) ) C.
